Abstract
Traditional cloud-centric approaches to medical data sharing pose risks related to real-time performance, security, and stability. Medical and healthcare data encounter challenges like data silos, privacy breaches, and transmission latency. In response to these challenges, this paper introduces a blockchain-based framework for trustworthy medical data sharing in edge computing environments. Leveraging healthcare consortium edge blockchains, this framework enables fine-grained access control to medical data. Specifically, it addresses the real-time, multi-attribute authorization challenge in CP-ABE through a Distributed Attribute Authorization strategy (DAA) based on blockchain. Furthermore, it tackles the key security issues in CP-ABE through a Distributed Key Generation protocol (DKG) based on blockchain. To address computational resource constraints in CP-ABE, we enhance a Distributed Modular Exponentiation Outsourcing algorithm (DME) and elevate its verifiable probability to “1”. Theoretical analysis establishes the IND-CPA security of this framework in the Random Oracle Model. Experimental results demonstrate the effectiveness of our solution for resource-constrained end-user devices in edge computing environments.
Keywords: Trustworthy data sharing, Blockchain, CP-ABE, Distributed attribute authorization strategy, Distributed key generation protocol, Distributed modular exponentiation outsourcing algorithm
1. Introduction
The rapid proliferation of digitization in the healthcare sector has generated a vast amount of patient-related medical and health data. Responsible and ethical use of this information is critical to protecting the personal privacy of patients. Scholars have conducted significant research in the effective collection [1] and statistical classification [2] of medical data. However, there are currently various issues associated with the sharing of medical information. Medical data is susceptible to tampering or loss during transmission, making it challenging to facilitate seamless sharing. The phenomenon of ‘data silos' in various healthcare organizations is notably prevalent. Furthermore, most medical data is controlled by healthcare providers, raising concerns about data being transmitted and utilized without the patient's knowledge, leading to security risks and potential conflicts between healthcare providers and patients [3].
Compared to traditional healthcare systems that store user health data and health records in physical paper format, cloud-based healthcare systems have significantly improved efficiency and reduced storage costs over a period of time. However, with the explosive growth of medical data, cloud-based healthcare systems face challenges such as network latency, bandwidth limitations, privacy breaches, and security attacks.
First, the network latency and limited bandwidth of cloud storage can result in slower medical data transmission speeds, thereby reducing the real-time capabilities of healthcare systems. This is particularly critical for applications such as emergency care and surgery that require quickly access to patient data. In addition, medical data frequently needs to be shared among different systems and applications to support healthcare decisions. However, if cloud-based systems encounter network congestion, it can lead to the issue of inconsistencies in medical data, potentially resulting in inaccurate or outdated information.
Second, although outsourcing the storage of patient health data and EHRs to cloud service providers is convenient, efficient, and cost-effective, it results in users relinquishing control over their health data and EHRs upon digitization and cloud storage. On one hand, in the event of a security breach at a cloud service provider, there is a risk of exposing patient health data and other private information. Conversely, cloud service providers and healthcare organizations may face temptations to disclose patient health data or electronic health records for financial gain [4].
Third, cloud storage systems are vulnerable to security attacks. Traditionally, medical data has been predominantly housed in centralized databases or cloud storage systems, which introduce a singular point of vulnerability, leaving them exposed to various threats such as phishing, man-in-the-middle attacks, impersonation, and identity theft [5]. Furthermore, there is the overarching issue of attackers, malevolent users, and hackers cloning or duplicating a range of medical documents.
Yang et al. [6] introduced a CPRE scheme centered around cloud computing facilities, with support for user revocation in cloud environments. This proposed approach demonstrates reduced computational and communication overhead, facilitating easy access to cloud data using resource-constrained devices. Nevertheless, this cloud-centric data sharing strategy is susceptible to single points of failure and communication latency issues.
Edge computing, a technology designed to process data at the network's edge, overcomes the limitations of traditional cloud computing in terms of real-time processing and efficient bandwidth usage. Blockchain technology, recognized as a state-of-the-art approach for ensuring the security and immutability of data, has a broad range of applications in ensuring trust and sharing of data, spanning areas such as VANET [7] and healthcare. As a result, this paper introduces a blockchain-based architecture for secure sharing of medical data in edge computing environments, with the aim of improving both the efficiency and security of data processing in healthcare systems based on the cloud.
CP-ABE functions as a form of public key encryption, facilitating one-time encryption and multi-user sharing. This method plays a crucial role in enabling precise control over data access, ensuring the security of data sharing [8,9]. It has been widely applied in trustworthy data sharing scenarios within edge computing environments [10,11]. For instance, Suyel Namasudra et al. [12] have proposed a secure taxi-sharing system utilizing attribute-based encryption algorithms and re-encryption schemes integrated with blockchain technology. This system provides decentralization, immunity against single point of failure, resilience against collusion attacks, and data leakage prevention. Additionally, the encryption algorithms presented demonstrate remarkable scalability and can be applied to various domains, including the Internet of Things, big data, healthcare, and more.
However, there are several challenges in achieving trustworthy and secure data sharing based on CP-ABE in current edge computing environments:
First, traditional CP-ABE does not meet the real-time requirements of attribute authorization services in edge computing environments. In such environments, where data processing takes place at the network edge, there is a significant demand for real-time services. However, traditional MA-ABE schemes cannot satisfy this real-time requirement.
Second, there is the issue of unreliable edge nodes and the security of CP-ABE keys. In edge computing environments, edge nodes may be vulnerable to physical attacks, malware intrusion, and additional threats that could compromise the security of CP-ABE keys.
Finally, the contradiction between the resource-constrained end devices and the computational complexity of CP-ABE. CP-ABE requires substantial computational resources with the computational effort increasing linearly with the complexity of the attribute set or access policy [13]. This poses a challenge for resource-constrained end devices, especially in edge computing environments, where these devices have limited computational power, storage space, and battery life, making them unable to handle the extreme computational complexity of CP-ABE.
Therefore, the main focus of this paper is to address the challenge of achieving real-time, secure, and computationally efficient medical data sharing in edge computing environments by building on the foundation of CP-ABE data sharing mechanisms and incorporating blockchain technology. The primary contributions of this paper are as follows:
-
(1)
Propose a Blockchain-based Trusted Data Sharing Scheme in the Edge Computing Environment (BTDS), addressing privacy leakage and data silos issues in medical data sharing.
-
(2)
To address the real-time requirements of attribute authorization services in edge computing environments, this paper introduces a Distributed Attribute Authorization strategy based on blockchain (DAA). The distributed deployment strategy eliminates the central attribute authority while deploying the Attribute Authorization Center (AC) closer to end-users. This approach achieves a completely decentralized attribute authorization service and ensures real-time requirements for attribute authorization services in the edge computing environment.
-
(3)
To address the issue of key security in CP-ABE within edge environments, this paper presents a Distributed Key Generation protocol based on blockchain (DKG). This protocol ensures ‘useable but invisible’ privacy protection for the CP-ABE system's master key and user private keys, effectively resolving the problem of key storage in untrusted edge computing environments.
-
(4)
To address the issue of resource-constrained terminal devices, this paper combines blockchain technology to enhance a distributed modular exponentiation outsourcing algorithm (DME). This algorithm is applied to the encryption and decryption operations of CP-ABE, and its verifiability probability is improved to ‘1'.
-
(5)
This paper conducts a formal correctness and security analysis of the proposed BTDS architecture, along with the design of simulation experiments. The results demonstrate the effectiveness of the BTDS architecture for resource constrained end devices in edge computing environments.
The paper is structured as follows: In Section 2, we discuss relevant previous research. Section 3 provides the necessary background to comprehend the proposed architecture. Section 4 presents the system model, along with formal definitions and security considerations for the BTDS architecture. Section 5 delves into the specific implementation details of BTDS. Section 6 is dedicated to correctness and security proofs. Section 7 showcases the experimental results and offers a performance analysis. Finally, in Section 8, we draw our conclusions and outline directions for future research.
2. Related work
2.1. Medical data sharing based on blockchain
In the field of blockchain-based medical data sharing, numerous researchers have conducted valuable demonstration studies. Li et al. [14] introduced and implemented a lightweight blockchain-based solution for medical data sharing. They employed proxy re-encryption techniques to ensure secure data sharing among healthcare professionals and patients, as well as between patients themselves. VIKAS JAIMAN and colleagues [15] introduced a data sharing framework that incorporates standardized ontology consent and data request models, drawing from the DUO and ADA-M models. They also devised a smart contract to automate a universal consent model, which underwent testing on the LUCE data sharing platform.
Pratima Sharma et al. [16] conducted an analysis of the substantial security and privacy challenges encountered by traditional healthcare systems. Subsequently, they developed a contemporary decentralized application tailored for healthcare departments, harnessing blockchain-based Internet of Things (IoT) systems. PRATIMA SHARMA et al. [17] introduced a distributed architecture for a healthcare system featuring privacy protection, employing blockchain technology. They developed a distributed application designed for the creation and access of healthcare certificates. Renpeng Zou et al. [18] addressed the challenge of inefficient data retrieval in blockchain-based electronic health systems. They introduced an electronic health system named SPChain, which is built on blockchain technology and is dedicated to medical data sharing and privacy protection. To expedite data retrieval, the solution incorporates special key blocks and mini-blocks for patients to store their electronic medical records. Additionally, they implemented a reputation system to incentivize the participation of medical institutions in SPChain.
Exploring the integration of blockchain technology for medical data sharing within an edge computing environment is a pivotal research direction. Alaa Awad Abdellatif et al. [19] have introduced an innovative collaborative healthcare system that utilizes both edge computing and blockchain technologies to facilitate efficient and large-scale medical data exchange. RAIFA AKKAOUI et al. [20] have introduced an authentication and authorization framework known as EdgeMediChain for the sharing of health data. This comprehensive framework encompasses EMRs and PHD generated by Medical Internet of Things (MIoT) devices, utilizing the synergy of edge computing for scalability and blockchain technology for enhanced security.
2.2. Data sharing in edge computing environments based on CP-ABE
Considerable research efforts have been dedicated to addressing the challenge of data sharing based on CP-ABE within edge computing environments. In the context of real-time attribute authorization services in edge computing environments [21,22], Alshehri et al. [23] introduced the concept of fog node alliances and proposed a distributed authorization scheme based on blockchain and fog node alliances to tackle issues related to time delays and communication overhead among fog nodes. Additionally, Fargana J et al. [24] introduced a Fog Computing layer positioned between the cloud and users, aimed at mitigating the heightened risk of data errors occurring during network transmission.
In the realm of CP-ABE key security research [[25], [26], [27], [28]], Li et al. [29] introduced an innovative online/offline multi-authority CP-ABE scheme. This scheme leverages password reverse firewalls to safeguard against backdoor attacks and enhances the efficiency of MA-CP-ABE through an online/offline approach, consequently reducing storage and computational burdens for users. Remamany et al. [30] put forward a CP-ABE scheme based on Bloom filters. Within this scheme, the access policy is individually examined during the key generation process to ensure the integrity of access policies, thereby fortifying key security. Cheng et al. [31] introduced a CP-ABE scheme rooted in cloud-fog computing. This approach incorporates white-box tracing, maximum user access counts, and reward-penalty mechanisms to establish robust defenses against key leakage. Employing artificial intelligence to mitigate network security risks [32] is also a viable strategy for enhancing CP-ABE key security. For instance, Mohammad Kazim Hooshmand et al. [33] devised a method for network anomaly detection utilizing deep learning techniques.
Addressing the issue of resource-constrained devices in the edge computing environment, researchers have started exploring solutions focusing on the outsourcing of CP-ABE [[34], [35], [36], [37], [38], [39]]. A common approach in these studies is to offload some computational tasks to more powerful devices or cloud servers to reduce the computational burden on resource constrained devices. Touati et al. [40] enabled resource-constrained sensor nodes to implement CP-ABE within an Internet of Things (IoT) environment by orchestrating collaborative efforts among diverse nodes. This process entailed the delegation of computationally intensive operations to a group of auxiliary nodes.
Kiraz et al. [41] proposed a novel algorithm for outsourcing modular exponentiation operations securely to a single trusted cloud server while ensuring the correctness of computations. This algorithm is known to be the most efficient solution that utilizes a single untrusted server and provides the best verifiability probability. Moffat et al. [42] conducted an extensive review of CP-ABE applications in mobile cloud computing and the Internet of Things (IoT). The article underscores that, given the heterogeneity and resource limitations of IoT devices, applying research findings from mobile devices to attribute-based encryption within the IoT domain represents a significant avenue of research.
Li et al. [43] applied secure outsourcing algorithms for exponentiation to CP-ABE schemes and achieved the concealment of both the base and exponent information while supporting verifiability of the computation results. However, the probability of correct verification in their approach is only 1/2. Yan et al. [44] improved the modular exponentiation outsourcing algorithm based on the work of Li et al. [43] and applied it to the encryption and decryption phases of ciphertext-policy attribute-based encryption, increasing the verifiability probability to 1.
In summary, researchers have made valuable contributions to address the challenges associated with CP-ABE attribute authorization service real-time requirements in edge computing environments, protecting CP-ABE System Key security, and achieving efficient CP-ABE computation on resource constrained devices. However, these approaches, while partially addressing the aforementioned issues, still have limitations. While the work in Ref. [23] addressed the time delay and communication overhead between fog nodes, ensuring real-time attribute authorization services in large-scale edge computing environments remains a challenge. Although online/offline key generation techniques and cryptographic reverse firewalls, as seen in Refs. [[29], [30], [31]], can enhance the security of CP-ABE keys, preventing key leakage in an unreliable edge computing environment is an issue that needs additional attention. Additionally, while offloading some computational tasks to more powerful devices or cloud servers, as explored in Refs. [[40], [41], [42], [43], [44]], can alleviate the computational burden on resource-constrained devices, achieving efficient CP-ABE computations in edge environment while ensuring computational correctness remains an urgent challenge.
3. Preliminary knowledge
The notation used in this paper is presented in Table 1.
Table 1.
Symbol description.
| Symbol | Description | Symbol | Description |
|---|---|---|---|
| Security parameter | Plaintext | ||
| Public key | Access structure | ||
| Master private key | Ciphertext | ||
| System attributes | Intermediate ciphertext | ||
| User attributes | Partially decrypted ciphertext | ||
| Transformation key | Public key fragment | ||
| User private key | Private key fragment |
3.1. Bilinear mappings
According to the standardized definition provided in Ref. [45], let be a large prime number, and be two groups of order with operations called addition and multiplication, respectively. The bilinear map from to satisfies the following property [46].
-
(1)
Bilinear: The mapping is said to be bilinear if, for any and , , or and .
-
(2)
Non-degenerate: The map doesn't map all the elements in (that is, the even elements) to the unit in . Since is an order prime group, this means that if is a generator of , then is a generator of .
-
(3)
Computability: For any and in , there exists an effective algorithm to compute .
3.2. LSSS
A secret sharing scheme on a set of parties is referred to as a Linear Secret Sharing Scheme (LSSS) on if it satisfies the following conditions:
-
(1)
The secret share distributed to each entity consists of a vector in .
-
(2)
For a secret sharing scheme , there exists a matrix of , and the mapping function maps each row of the matrix to an associated party. For represents the participant associated with the row. Consider a column vector , where is the shared secret in , and is a random value for . According to the scheme , the matrix represents the secret being shared into secret shares, where represents the secret share held by participant .
-
(3)
In a linear secret sharing scheme with linear refactoring features, if is a set of access authorizations in , there exists a constant such that , where is an effective share of the secret held by participant , and .
3.3. Blockchain
Blockchain technology embodies an innovative distributed infrastructure and computational paradigm that harnesses the data structure of blockchain for data verification and storage. It employs a distributed node consensus algorithm to facilitate data generation and updates, while ensuring secure data transmission and access through cryptographic methods. Additionally, it relies on smart contracts, which consist of automated script code, for data programming and manipulation [47].
Blockchain functions as a decentralized ledger within a peer-to-peer network, with each participating node maintaining a complete copy of the ledger [48,49]. This redundancy guarantees data accessibility, even in the event of a single node failure, effectively mitigating the risk of data loss. Blockchain technology possesses several noteworthy characteristics, including decentralization, immutability, traceability, high trust, and high availability [50].
3.4. DBDHE
Let be a large prime number, and be two cyclic groups of order , and G be a generator of . We define as a bilinear mapping. Given a set of elements: , the objective of the decisional bilinear Diffie-Hellman problem is to determine whether or , where . The advantage of the attacker in solving the decisional bilinear Diffie-Hellman exponent (DBDHE) problem is defined as follows: . If is less than a negligible value, then the DBDHE problem is considered difficult.
3.5. Edge computing Outsourcing Framework
Li et al. [51] proposed a secure and verifiable framework for outsourcing edge computing tasks, utilizing multiple non-collusive edge nodes. The framework involves two types of participants. Users with limited computing resources aim to outsource computationally intensive tasks, denoted as , to edge nodes that possess substantial computational capabilities. However, due to concerns regarding trustworthiness, users cannot fully rely on the edge nodes. The edge nodes are assumed to be non-collusive, meaning they do not collaborate to compromise data privacy [52]. In order to safeguard the data privacy of the edge nodes, the user performs a transformation on the original input , resulting in a modified input denoted as . Following the transformation of the input , the user divides it into individual components . These components are then transmitted separately to the edge nodes, along with the computational task . Each edge node is responsible for executing the corresponding computation task using the received input . Upon completion, the edge node generates a response . Users can collect the responses and evaluate them to verify the correctness of the overall result . If the result is validated, the user can recover the real result from the evaluated result . Otherwise, if the validation fails, the user outputs “error” [53].
The proposed algorithm's overall framework consists of the following modules:
-
(1)
Precompute Module: This module precomputes static parameters to accelerate processing.
-
(2)
Problem Transformation Module: In this module, the user transforms the computational input into an encoded value . Additionally, the user generates and stores a secret value for the verification and recovery process.
-
(3)
Problem Resolution Module: In this module, the encoded input is divided into separate components . The user then transmits each component along with the computation task to the respective edge node.
-
(4)
Calculation Module: In this module, the edge nodes perform the computation task based on the received encoded input . Each edge node computes the result corresponding to its assigned component.
-
(5)
Results Module: In this module, the user collects the encoded results from the edge nodes. These results are then merged to obtain the overall encoded result .
-
(6)
Validation Module: In this module, the validity of the encoded result is verified using the secret value . If the encoded result is valid, the output is set to 1; otherwise, it is set to 0.
-
(7)
Recovery Module: In this module, the user can recover the true results based on the encoded result and the secret value .
4. Methodology
This section begins by describing the system model of BTDS, including the overall architecture, entity composition, and workflow. Subsequently, the algorithms involved in the scheme are formally defined. Finally, we present a security model for BTDS.
4.1. System architecture
The Trusted Medical Data Sharing Architecture in Edge Computing Environment (BTDS) in an edge computing environment is illustrated in Fig. 1. This architecture can be divided into three layers: End-user layer, edge service layer, and cloud storage layer. The End-user layer consists of Data Owners (DO) and Data Users (DU). The edge service layer includes Attribute Authorities (AA) and the Outsourcing Service Provider (OSP). The cloud storage layer comprises the Medical Cloud Computing Center (Cloud). The specific functions of the six participants in the BTDS architecture are as follows:
-
(1)
Data Owner (DO): DO, as the patient, is the owner of medical data (e.g., electronic health records) and holds the data's ownership. DO encrypts the original data by specifying access policies from electronic health records.
-
(2)
Data User (DU): DU, as a healthcare professional, typically a doctor, is the user of medical data. DU can only use the user's private key assigned by the medical institution alliance blockchain when their user attribute set (system privileges) satisfies the access policy set by the patient. This allows DU to further decrypt the ciphertext to obtain plaintext electronic health records.
-
(3)
Attribute Authorization Center (AC): Each healthcare institution serves as an Attribute Authority (AA) node in the CP-ABE algorithm. AA nodes elect shard representatives to act as Attribute Authorization Centers (AC) within the shard. ACs are responsible for providing attribute authentication and key distribution services to users within the shard.
-
(4)
Edge Blockchain (EBC): EBC is the edge blockchain composed of AA nodes, also known as the medical alliance blockchain. EBC has two roles: first, it adds an additional security verification mechanism to traditional medical cloud storage by storing cryptographic digests of medical data. Second, it provides distributed and secure key generation for CP-ABE.
-
(5)
Outsourcing Service Provider (OSP): OSP is a computing outsourcing service provider composed of AA nodes, responsible for the distributed execution of modular exponentiation operations outsourced by DO and DU.
-
(6)
Medical Cloud Computing Center (Cloud): Medical ciphertext data files uploaded by patient DO are stored on the medical cloud server.
Fig. 1.
The BTDS architecture.
The specific steps for patient A, who generates an electronic medical record at hospital A with doctor A, to share this record with doctor B at hospital B are shown in Fig. 1 as follows.
-
Step 1
Patient A arrives at hospital A for medical treatment, where doctor A generates electronic medical record information for patient A.
-
Step 2
After medical treatment, patient A can choose to synchronize their electronic medical record with the medical institution consortium, enabling future cross-domain medical treatment. The process of uploading an electronic medical record consists of using an edge outsourcing service on a patient's mobile device to upload an electronic medical record with attribute-based encryption to a medical cloud server. In addition, a cryptographic digest of the electronic medical records is uploaded to the Medical Institutions Alliance blockchain for verification.
-
Step 3
When patient A visits hospital B for medical treatment for the second time, doctor B can easily access patient A's electronic medical records from the medical cloud server using their own identity privileges, which are verified via the Medical Institutions Alliance blockchain.
The execution of CP-ABE encryption in BTDS architecture consists of three phases. The details of the process are as follows:
-
(1)
System Initialization Phase.
The BTDS architecture network is initially set up using the DAA sub-algorithm. Subsequently, the EBC initiates the system initialization smart contract of the CP-ABE master algorithm, leading to the distributed generation of the system's public key, master private key, and public parameters.
-
Step 1
Initially, the system employs the K-Means algorithm to perform preliminary partitioning of DUs and AAs based on their geographic association. Subsequently, within each partition, the AAs elect the AA with the best performance as the AC for that partition, which is responsible for serving the terminal users within that partition.
-
Step 2
The EBC executes the smart contract for system initialization within the CP-ABE algorithm, resulting in the generation of the system's public parameters. Each AA independently generates fragments of the system's public key and master private key. These key fragments are embedded within transaction blocks on the blockchain, while the fragments of the master private key are securely retained.
-
(2)
Data Encryption Phase.
The DO employs the CP-ABE main algorithm for attribute-based encryption on the original data. Subsequently, the encrypted data is uploaded to the medical cloud storage center. Simultaneously, the DO uploads the digest's hash value to the EBC. In this process, the DO utilizes the DME sub-algorithm to outsource the complex modular exponentiation computations to the OSP.
-
Step 1
The DO specifies the access policy and carries out simple exponentiation and XOR operations on the data.
-
Step 2
The DO utilizes the DME sub-algorithm to outsource the complex modular exponentiation computations to the OSP.
-
Step 3
The OSP returns a portion of the ciphertext for the data. The DO verifies the results returned by the OSP. Upon successful verification, the DO combines them with its own computed results to form the complete data ciphertext.
-
Step 4
The DO uploads the ciphertext to the Cloud and transmits the hash value of the data, which is packaged and then sent to the EBC.
-
(3)
Data Decryption Phase.
In the data decryption phase, the DU initially downloads the ciphertext from the medical cloud storage center and then sends a request for the decryption key to the AC associated with the corresponding shard. Subsequently, the DU executes the decryption algorithm provided by the CP-ABE scheme. Successful decryption is contingent on the attribute set of the DU aligning with the access structure defined for the ciphertext.
-
Step 1
The DU initiates a request for a private key from the AC node of their shard, providing their attribute set. The AC node subsequently returns the requested private key to the user.
-
Step 2
The DU proceeds to download the complete ciphertext from the Cloud and conducts a comparison between the hash of the downloaded ciphertext and the hash of the ciphertext stored on the EBC. If a match is found, the decryption process continues. However, in the event of a mismatch, the user's data access attempt fails, triggering a system alert.
-
Step 3
If the user's attribute set meets the access policy requirements defined in the ciphertext, the DU proceeds to outsource the exponentiation and bilinear pairing operations to the OSP. This is achieved using a transformation key to obtain partial plaintext results.
-
Step 4
The OSP returns the computation results, which are partial plaintext results. The DU utilizes the decryption key to compute the complete plaintext results.
4.2. Formal definition of main algorithm: CP-ABE
-
(1)
. The system invokes the sub-algorithm DAA to create the EBC. The algorithm for uploading the EBC is established, and the public parameter smart contract is executed by the designated endorsement node. The algorithm takes as input the security parameter and the system attribute set , yielding the system public parameter as the output.
-
(2)
. The algorithm is executed collaboratively by DO and OSP. The input to the algorithm includes the system public parameters , the plaintext , and the access structure . Initially, the DO triggers the DKG sub-algorithm to calculate the system public key and conduct partial encryption operations. Subsequently, the OSP employs the DME sub-algorithm to produce the partial data ciphertext, denoted as . Ultimately, the complete data ciphertext, denoted as , is generated through the encryption operation carried out by the DO.
-
(3)
. The key generation algorithm is executed by the AC fragment. It accepts the system public parameters and the user attribute set as inputs. DU initiates a request to AC for the key with its user attribute set . Subsequently, the AC initiates the DKG sub-algorithm to generate the user private key designated for DU.
-
(4)
. The algorithm is performed by OSP using the transformation key and the ciphertext . OSP executes the decryption operation to generate the converted ciphertext .
-
(5)
. The algorithm is performed by DU using the decryption key and the converted ciphertext . DU executes the decryption operation to generate the complete data plaintext .
4.3. Security model
-
A.
Goals of the Proposed Work.
The BTDS architecture outlines the following design objectives:
-
1)
Access control: Privacy breaches are the number one challenge for medical data sharing systems. Traditional medical cloud storage systems, which are based on cryptographic methods, do not allow users to decide the key-sharing process. When users upload their data to a cloud storage center, they relinquish control over their personal data, making it susceptible to potential data breaches. Therefore, the BTDS architecture, which relies on CP-ABE encryption, necessitates fine-grained access control to safeguard the data owner. This ensures that while achieving privacy protection for medical data, patients also retain autonomous control over their personal medical data.
-
2)
Security: Security during medical data sharing is one of the primary objectives of the BTDS architecture. The proposed CP-ABE scheme, which is based on blockchain and multiple attribute authorities, must ensure load balancing, verifiability, secrecy, and protection against collusion attacks.
-
3)
Performance: For edge computing with high real-time requirements, achieving lightweight and efficient CP-ABE is crucial. An efficient system is necessary, so efforts are made to ensure that the computational and communication overhead of the proposed BTDS architecture remains within reasonable limits.
-
B.
Correctness Definition
Definition 1: Correctness of BTDS, that is, assuming that each algorithm in the scheme is executed exactly, correct results will always be obtained. For example, is a negligible function of the security parameter .
| (1) |
-
C.
Security Definition
-
1)
Zero-Knowledge Property of DKG and DME
In the context of distributed key generation and distributed outsourcing of modular exponentiation computation, we aim to ensure that any participant in the system cannot acquire sensitive information (such as private keys) from other participants and cannot obtain any information about the plaintext from the OSP, while still being able to verify the correctness of the obtained results. In the following, we define the zero-knowledge property of distributed keys and outsourced computation results in this model through security experiments. The attacker is allowed to communicate with any participant in the system, including Attribute Authorization Centers (AC) and Outsourcing Service Providers (OSP). The task of is to attempt to obtain the private information of other participants, including private keys and detailed results of outsourced computations, while deceiving the system to verify the correctness of the computation results. The design of the security experiment is as follows:
| (2) |
In the above experiment, the attacker can communicate with any participant in the system, including access to private information and outsourced computational results. The challenger then executes the function to verify if the attacker has successfully obtained the private information. If the verification is successful, indicating that the attacker cannot obtain private information, the output is 1, indicating that the system satisfies the zero-knowledge property. If the verification fails, indicating that the attacker has successfully obtained private information, the output is 0, indicating that the system does not satisfy the zero-knowledge property. The advantage of the attacker is defined as follows:
| (3) |
Definition 2: If is extremely tiny and approaches zero, then the system possesses a strong zero-knowledge property, indicating that the attacker cannot acquire private information.
-
2)
Verifiability of DME
In the context of distributed modular exponentiation outsourcing, security definitions of verifiability focus on the confidentiality of the verification key and the correctness of the outsourced computation. The following security experiment is designed to define the verifiability of the outsourcing scheme.We define the attacker , where are two probabilistic polynomial-time simulators. The security experiment is structured as follows:
| (4) |
For any , the advantage of attacker in verifying the confidentiality of the verification key in DME is defined as follows:
| (5) |
Definition 3: If , where is a negligible function, then the DME scheme achieves verifiability in the outsourcing computation scheme.
-
3)
Confidentiality of BTDS
Definition 4: The privacy of encrypted data is defined using a security game that is not distinguishable under a chosen plaintext attack between the attacker and the challenger . Specifically, the scheme is considered indistinguishable under chosen plaintext attack (IND-CPA) secure if the absolute value of the difference between the probability is less than or equal to , where represents a negligible probability.
: The attacker initiates the interaction with the challenger by sending a set of attributes .
: The challenger executes the algorithm and generates the public parameters . The challenger then sends the public parameters to the attacker .
: The attacker queries the challenger for a decryption key . The challenger performs the key generation algorithm to generate the key , and sends it to the attacker .
: The attacker sends two plaintext messages of equal length to the challenger . The challenger randomly selects one of the plaintext messages and performs the encryption algorithm to generate the corresponding ciphertext.
: The attacker outputs a guessed value as their speculation for the value of . If , we consider the attacker to have won the game. The advantage of the attacker is defined as follows: .
5. Concrete scheme
This section is devoted to the specific details of the BTDS scheme, including the Medical Institution Alliance Edge blockchain, the Distributed Attribute Authorization Policy, the Distributed Key Generation Protocol, the Distributed Modular Exponential Outsourcing Algorithm, and the detailed construction of the CP-ABE master algorithm based on the blockchain and multiple authorization centers.
5.1. Medical Institution Alliance Edge Blockchain
The Medical Institution Alliance Edge Blockchain (EBC) is a consortium blockchain consisting of various healthcare institutions, deployed at the edge layer of the network, which is susceptible to network attacks. Each healthcare institution acts as an edge node, providing outsourced computing services to resource-constrained end users, including patients and doctors. Traditional healthcare institutions typically deploy internal networks to physically insulate themselves from cyber attacks. However, this network defense approach results in the inability of patient data to be shared among different healthcare institutions, leading to the phenomenon of “data silos” between them.
Some healthcare organizations have adopted cloud storage centers to alleviate this problem, but this approach simultaneously poses a risk of personal medical data leakage. Therefore, the BTDS architecture proposed in this paper leverages healthcare institutions as blockchain nodes, forming a Medical Institution Alliance Edge Blockchain (EBC). This approach maintains the existing cloud storage approach, while enhancing it with a blockchain verification mechanism. This ensures both data security and fine-grained access control for patients over their personal medical data.
As shown in Fig. 2, the EBC network architecture of the Medical Institutions Alliance Edge Blockchain utilizes the Hyperledger Fabric framework, a widely used open-source consortium blockchain framework known for its high configurability and scalability. It is highly suited for constructing medical consortium blockchains. The EBC network consists mainly of two types of nodes: super blockchain nodes and peer blockchain nodes.
-
1)
Super Blockchain Nodes (Government Nodes): These nodes are deployed in government regulatory departments or trusted institutions' data centers. They are responsible for storing the entire ledger information and overseeing network operations. These nodes should have a high degree of physical and cyber security.
-
2)
Peer Blockchain Nodes (Medical Institutions Nodes): These nodes are deployed in various medical institutions and serve as edge nodes. They provide outsourced computing services for patients and healthcare professionals while maintaining a portion of the ledger data. Each medical facility may have one or several nodes, depending on its size and requirements. In addition to storing ledger information, peer blockchain nodes may also undertake CP-ABE attribute authorization and key generation tasks. These nodes elect an Attribute Authorization Center (AC) within their respective shards based on their computational and storage capabilities. The AC is responsible for providing attribute authentication and key distribution services to users within the shard.
Fig. 2.
Example of EBC network deployment.
EBC (Medical Institutions Alliance Edge Blockchain) places a strong emphasis on security features such as data integrity, key security, and resistance to malicious intrusion attacks to ensure the privacy and trustworthiness of medical data. The following is a detailed description of the security properties of EBC:
-
1)
Data Verification Mechanism:
EBC leverages blockchain technology to verify and ensure the integrity of data stored on the blockchain through mechanisms such as hash values and blockchain fingerprints (e.g., Merkle trees). These mechanisms effectively detect data tampering and provide reliable verification of data integrity. In addition, EBC serves as a complementary verification mechanism for medical consortium blockchains, further preventing attackers from tampering with patient's personal data in the cloud and enhancing data security.
-
2)
Key Security:
EBC adopts the CP-ABE (Attribute-Based Encryption) system to achieve fine-grained data access control. Key security is crucial in edge computing environments. To mitigate the risk of key leakage, EBC introduces a distributed key generation protocol. This mechanism does not rely on a single Attribute Authorization Center (AC), ensuring that even if one AC experiences network failures or attacks, it will not lead to key leakage. EBC ensures that only legitimate users have access to the appropriate keys, thereby maintaining data confidentiality.
-
3)
Resistance to Malicious Intrusion Attacks:
EBC employs a decentralized architecture where data is no longer centrally stored on a single server, but distributed across multiple nodes. This architecture makes it difficult for an attacker to pinpoint a single intrusion target as the data is scattered throughout the network. To maintain network consistency and data trustworthiness, EBC applies consensus algorithms such as Byzantine Fault Tolerance (BFT) algorithms. Even if some nodes are attacked or compromised, the network can continue to function normally, ensuring data security and integrity.
5.2. Sub-algorithm DAA: distributed attribute authorization strategy
The distributed attribute authorization strategy in the blockchain-based scheme is implemented through AA nodes deployed in the edge layer, forming an Edge Blockchain (EBC). The system attribute set is agreed upon by the AA nodes and stored in the EBC for consensus. Following the principles of the K-Means clustering algorithm [54], the end-users and AA nodes are initially divided into shards based on their distance. Within each shard, an attribute authorization center (AC) is dynamically elected from the AA nodes as a representative. The AC is responsible for providing attribute authentication and key distribution services to the users within the shard. This distributed deployment strategy ensures that the AC is located closer to the end users, aligning with the concept of edge computing and meeting the real-time requirements of attribute authorization services in the edge computing environment.
-
(1)
Shard initialization
In the shard initialization algorithm, the topology of the nodes is based on the actual distribution of edge nodes in the medical data sharing consortium scenario, assuming that the IoT nodes are randomly distributed. This means that the node locations are randomly distributed and are not constrained by a particular mesh rule. In this scenario, the shard initialization algorithm remains applicable since it utilizes the K-means clustering algorithm, which can adapt to various node distribution patterns, including random distributions.
Suppose the system consists of AA nodes and terminal users(U). Each AA node, , can be represented by a two-dimensional coordinate . The distance between and is defined as follows: . The K-Means clustering algorithm divides AA nodes into shards. Initially, AA nodes are randomly selected as the initial shard representatives, also known as the shard's authorization center (AC), which provides services to the end users within the shard. The following two steps are then iterated until convergence:
-
①
Assign each AA node to the nearest shard representative.
-
②
Set the shard representative (AC) to the average position of all AA nodes in a shard.
Assumptions: The position of the end user is represented by the two-dimensional coordinates , and the position of the shard representative is represented by the two-dimensional coordinates . The distance between the end user and the shard representative nodes is defined as follows: , where and .
The K-Means clustering algorithm is used to divide users into shards according to the following steps:
-
a.
Randomly assign users to shards.
-
b.
Compute the distance between each user and its corresponding shard representative .
-
c.
Redistribute users: For each user , find the nearest shard representative , and redistribute the user to the shard represented by .
-
d.
Iteration: Repeat steps b and c until no shard changes occur for any user or until a predetermined maximum number of iterations is reached.
The algorithm in question, as depicted in the pseudocode provided in Table 2, is described as follows:
-
(2)
Dynamic Selection of Shard AC
Table 2.
Shard initialization Algorithm.
In the shard, a performance measurement function is defined based on the CPU, memory, bandwidth, and other performance indicators of AA nodes:
| (6) |
Among them, and are weight values that can be adjusted according to specific requirements. and represent the CPU performance, memory size, and bandwidth of node respectively.
Next, the performance score of each AA node is calculated and sorted in descending order. The AA node with the highest performance score is then selected as the shard representative.
The algorithm in question, as depicted in the pseudocode provided in Table 3, is described as follows:
-
(3)
Distributed Load Balancing
Table 3.
Shard AC Dynamic Election Algorithm.
We employ a distributed load balancing strategy, which distributes the load balancing task to individual shards for processing. Load balancing operations are performed based on node load information and utilize a sorted list to enhance lookup efficiency, reducing time complexity to O(log N), making it more suitable for large-scale network environments.
-
1)
For each shard:
-
①
Calculate the load of each AA node as follows:
| (7) |
Where, represents the CPU usage of the AA node, represents the memory usage of the AA node, and represents the network latency of the AA node. The parameters are weight factors used to adjust the influence of CPU usage, memory usage, and network latency on the load.
-
②
The average load for each shard is calculated as follows: , where is the number of nodes in a shard and .
-
2)
Set the load threshold based on the system's actual requirements and capabilities. When , triggering the load balancing operation:
-
①
Define a list of loaded nodes, , to store the load information of all nodes in the current shard.
-
②
For each AA node in the shard, the load information of the node is inserted into NodeList in sorted order.
-
③
Define a function to find the list of nodes in the shard with load below .
-
④
Define a function to find the list of nodes within the shard with loads above .
-
⑤
Execute the migration of nodes from to adjacent shards or perform other load balancing operations:
| (8) |
Alternatively, nodes can be migrated from HighLoadNodes to newly created shards, or additional load balancing operations can be performed:
| (9) |
The algorithm in question, as depicted in the pseudocode provided in Table 4, is described as follows:
-
(4)
Recovery of Shard AC Failure
Table 4.
Distributed Load Balancing Algorithm.
Assume that a shard can be in either a normal state (0) or a failed state (1) at any given time . The state of a shard can be represented as a binary random variable . If , it indicates that the shard is in a normal state at time . If , it indicates that the shard has failed at time .
For a failed shard, the failure recovery mechanism should elect the AA node with the best performance in the shard as the new shard representative, i.e., the AC node, to provide services for the users in the shard. Assuming that at time , the AC node of shard fails, the recovery process involves selecting the node with the highest performance score from the queue of AA nodes within the shard to serve as the new AC node.
Assuming that represents the AA node within shard , we can define a failover function . When the AC node fail , indicating that at time , the new AC node for shard is set to the AA node within the shard.
The algorithm in question, as depicted in the pseudocode provided in Table 5, is described as follows:
Table 5.
Shard AC fault recovery Algorithm.
5.3. Sub-algorithm DKG: distributed key generation protocol based on blockchain
Based on the distributed key generation protocol based on Generalized VSS introduced in Zhang et al.'s scheme [55], this paper incorporates blockchain as a trusted third party and presents a distributed key generation protocol based on blockchain. This protocol decentralizes the key management of CP-ABE across multiple participants, and the system public key is generated through consensus in the EBC. The system master key is not explicitly stored in any node, and the user private key can only be calculated when multiple AA nodes collaborate.
The system consists of participants, denoted as , which form the group . The participants have a monotone access structure, meaning that certain subsets of can collaborate to recover shared secrets. The base set represents the minimal set of elements under the inclusion relation in . In the system, each AA possesses a master private key denoted as , and the corresponding public key to the system is represented as .
-
(1)
Initialization phase
-
①
Selection of large prime numbers and such that .
-
②
Selecting a finite cyclic group based on the discrete logarithm problem, where the order is , and as generators of .
-
③
Choose a residue class ring modulo denoted by .
-
(2)
System master private key generation phase
-
①
generates a secret value for their access to the shared structure , where . The specific process is as follows:
-
a.
When wants to share a secret , it makes the following commitment: , where is a randomly chosen secret value from .
-
b.
stochastically selects a polynomial of degree from the ring , where represents a secret value. Subsequently, is computed. Afterwards, randomly selects and computes the commitment to as , which is then broadcasted to the participants.
-
c.
Generate where . For each minimal qualified subset , is represented by points: . By applying Lagrange interpolation, another -degree polynomial is calculated. The values of and are computed and publicly disclosed to all participants, where .
-
d.
securely transmits the secret share to for holding the share of the secret , where .
-
e.
Upon receiving its allocated share of the secret, validates the integrity of the share by verifying whether . For each minimum qualified subset , all participants have the ability to verify the integrity of the public data and by confirming whether . Here, and , where .
-
②
If the validation of fails (i.e., is invalid), broadcasts the values and files a complaint against .
-
③
In the event of a complaint from against , it is incumbent upon to broadcast the valid share it had provided to .
-
④
If receives complaints from all members of a qualified subset or is complained by some members and the broadcasted share in step③remains invalid, each member's share is reset to 0, i.e., . Simultaneously, sets the selected secret value to zero, and both and are treated as zero polynomials.
-
⑤
Each member performs calculations on their private key share and the sum of their random values . When a user needs to utilize the system's master private key, they can compute .
-
(3)
Extraction of the System Public Key Phase
-
①
Each attribute authorization node calculates its respective shard of the system public key as , where .
-
②
Each broadcasts its public key shard to the EBC.
-
③
After retrieving the public key shard from the EBC, when a user needs to use the private key, they compute . Additionally, because , the CP-ABE public key system parameter can be obtained.
-
(4)
User private key generation phase
-
①
The user (DU) sends the set of user attributes it possesses to the attribute authorization center (AC) of its shard. The AC then aggregates the set and uploads it to the Edge Blockchain (EBC).
-
②
Each attribute authorization node generates a partial user private key based on the master secret key () fragment and the attribute set it holds.
-
a.
For each attribute in the attribute set , attribute authorization node randomly selects a value . Then, it calculates the user's private key parameter as .
-
b.
Attribute authorization node utilizes its holdings of the fragment to calculate the user's private key parameters. It calculates .
-
c.
packages the calculated and and uploads them to the EBC.
-
③
Shard AC collects all the calculated from each member, as well as the corresponding for each attribute. Using Lagrange interpolation, it calculates , , and .
-
④
Shard AC randomly selects a conversion factor . It sets the converted keys as .
-
⑤
AC returns the user's private key to DU.
5.4. Sub-algorithm DME: distributed modular exponentiation outsourcing algorithm based on blockchain
Based on the scheme proposed in literature [51], the DME sub-algorithm enhances the secure outsourcing algorithm for distributed modular exponentiation based on blockchain. The algorithm can be described as follows:
-
(1)
This step is carried out by the User's User and the OSP. It involves performing a modular exponentiation operation on the base with the exponent modulo . The resulting value is the evaluation key , and it is accompanied by the verification key . The following details explain the process in more depth:
-
①
The User inputs the prime number and initiates the Rand subroutine to generate six blinds in the form of , where and .
-
②
The User selects a random number from the set to perform a logical division of the base :
| (10) |
Among them, the values of are calculated as follows: .
-
③
The load balancing smart contract in the EBC, which consists of computing nodes, will initiate the selection of computing nodes for this round. The specific steps are as follows:
Initially, a segmented approach is employed to achieve load balancing among the edge nodes. The load segmentation method is defined as follows: , where represents the exponent size, , (where and correspond to the cost of a modular square operation and a modular multiplication operation, respectively). The value denotes the segmentation points, with being the initial point. The compute nodes are launched, and the number of nodes is determined as .
-
④
The User partitions the logical indices into segments through binary decomposition:
| (11) |
⑤Let the verification key be denoted as , and the evaluation key as , which can be represented as ,
(2).
This step is carried out by the distributed computing nodes, which compute the results and generate evidence . Here are the detailed steps:
-
①
The compute nodes, denoted as , perform the following steps sequentially:
| (12) |
②The compute node returns the computed result and evidence as and , respectively.
-
(3)
.
This step involves the User verifying the correctness of the result, which is done as follows: The User computes . If , then output the final result ; otherwise, output .
5.5. Main algorithm: blockchain-based CP-ABE with multi-attribute authority center
The main algorithm of this paper's scheme is built upon the approach presented in Ref. [44]. Below, we provide a detailed description of the algorithm.
-
(1)
.
-
①
The algorithm takes as input the security parameters , the large prime number , and the system properties from the collection .
-
②
A prime order is selected, and is chosen as a generator element for the double linear group . A bilinear mapping is then generated.
-
③
A hash function is selected. Two collision-resistant hash functions and are chosen.
-
④
Randomly selecting a parameter , the system parameters can be defined.
-
(2)
.
The algorithm randomly selects , computes , and . Then it invokes the child algorithm DKG to compute the public key to the system as . Given a plaintext , DO calculates .
In this algorithm, represents a matrix with dimensions , and denotes an injective function that associates each row of matrix with its corresponding attribute. The encryption process can be outlined as follows:
-
①
Randomly select a vector to be used for sharing the encrypted exponent .
-
②
For each row of the matrix , denoted as , calculate the inner product , where ranges from 1 to and represents the -th row of matrix .
-
③
Randomly select from , and invoke the sub-algorithm DME. The User and OSP work together to compute the intermediate ciphertext .
The detailed process of the first sub-algorithm DME with is as follows:
-
a.
Execute the system initialization algorithm within the DME sub-algorithm. This process yields the verification key as , and the evaluation key as , .
-
b.
The distributed computing nodes on the OSP are deployed to execute the algorithm in a decentralized manner, resulting in the computed values and the corresponding evidence .
-
c.
Execute the algorithm to validate the calculated results obtained from outsourcing, and output the verification outcome.
In a similar manner, calculate and using the DME algorithm.
-
⑤
Upon successful execution of the computation by the OSP, the DO can generate the complete ciphertext , where are computed by the DO, and are computed by the OSP and subsequently verified by the DO.
-
(3)
.
DU initiates the process by submitting its attribute set to the respective shard AC node. The AC node then invokes the sub-algorithm DKG to generate the user's private key .
-
(4)
.
After obtaining the successful grant of , DU downloads the ciphertext from the Cloud and verifies its integrity by comparing the ciphertext hash stored in EBC. DU then combines the decryption key with the ciphertext and sends them to OSP for further processing. OSP invokes the child algorithm DME to unlock a portion of the ciphertext, resulting in the transformed ciphertext .
-
①
Let be defined as , where represents a subset of attributes from the system's complete attribute set.
-
②
When the user attribute set satisfies the access policy , and there exists a valid set of secret shares for the secret with respect to the access matrix , it is possible to compute a constant set in polynomial time, such that the linear combination is achieved.
-
③
The transformed ciphertext is computed according to the following procedure:
| (13) |
-
(5)
.
-
①
After receiving the partially decrypted ciphertext , DU performs the following computations: and .
-
②
If the calculated values of and validate the correctness of the OSP's computation, the decrypted plaintext is produced as the output.
6. Proof of correctness and security
6.1. Proof of correctness
This section will provide a proof of correctness for the proposed BTDS system. The fundamental CP-ABE algorithm used in BTDS is based on the classic paper by GREEN et al. [56], so there is no need to reprove its correctness. This section will mainly focus on demonstrating the correctness of BTDS architecture, particularly in the context of the improved distributed key generation and distributed modular exponentiation outsourcing as discussed in Ref. [56].
Theorem 1
Correctness of Algorithm DKG,if EBC performs this algorithm correctly, it can guarantee that the output key is always correct.
Proof: According to the description of the sub-algorithm DKG, the master private key parameter of the system is shared by all participants.
- a)
commits to a key : During the initialization phase, each publicly reveals a commitment , where is their chosen secret value, and is a randomly chosen secret value. This commitment ensures the relationship between and .
- b)
Polynomial Interpolation Calculation: In step (2)c, participants calculate a polynomial concerning the secret value through polynomial interpolation. This ensures that each participant has a portion of the polynomial , where denotes different minimum qualified subsets. Thus, each participant shares information about the secret value .
- c)
Secret Share Distribution and Verification: Participants send their secret shares to other participants. These shares include information about the secret value . Receivers verify the validity of these shares, ensuring that they satisfy the commitment relationship. This ensures that each participant holds valid secret shares.
- d)
Computation of the System Master Private Key Parameter :Each member calculates their share concerning the system's master private key parameter , represented as . This is achieved by adding up the secret shares, which are part of the information about each participant's secret value . Finally, by summing all shares, the system's master private key parameter is correctly reconstructed.
Thus, based on the above proof, Algorithm DKG guarantees the correctness of the system's master private key parameter . This also implies that, in theory, the correctness of the BTDS architecture is guaranteed only if the sub-algorithm DKG is executed exactly. It forms the basis for ensuring the correctness of the BTDS architecture.
Theorem 2
Correctness of Algorithm DME. Under the assumption of correct execution by OSP, Algorithm DME ensures the integrity and accuracy of the outsourced computation results.
Proof: For Algorithm DME, given the input , where and are variables, the correct computation can be performed by following these steps:
- ①
Correctness of blind segmentation: The base exponent can be accurately reconstructed after blind segmentation.
(14)
- ②
The accuracy of edge node computation: The sub-algorithm DME ensures the detection and resolution of potential errors in computation results provided by the edge nodes. This guarantee is established through a rigorous proof by contradiction. Suppose there is a scenario where a compute node deviates from the protocol during the execution of the sub-algorithm DME and produces incorrect computation results. In such a case, when DU performs the verification algorithm, a contradiction arises. Specifically, if does not equal , the program outputs and triggers the monitoring mechanism. OSP takes appropriate measures to penalize the erroneous node and initiates a new round of computation with a different compute node. This process is repeated until DU's verification equation holds, ensuring the output of the correct computation result .
Inference 1: Based on Theorem 1 and Theorem 2, it can be inferred that the correctness of BTDS is guaranteed. If the CP-ABE main algorithm based on blockchain and multi-attribute authorization center, as described in this paper, is executed correctly, then it ensures that the BTDS architecture will consistently share data correctly.
6.2. Security proof
Theorem 3
If there exists a probabilistic polynomial-time attacker such that , then can devise an algorithm to violate the zero-knowledge property of both DME and DKG.
Proof: To begin, it is necessary to construct an Challenger to challenge the zero-knowledge properties of DME and DKG. The objective is to prove that is negligible, meaning that Challenger cannot break the zero-knowledge properties within an ignorable amount.
:Attacker selects an attribute set to challenge and sends it to the challenger .
:Challenger runs the algorithm and sends the generated public parameters to attacker . During this phase, attacker cannot interfere with or influence the generation of system parameters since this is part of the zero-knowledge property.
:(1) Attacker sends a decryption key query to Challenger , and the challenger executes the key generation algorithm to generate the key , which is then sent to attacker .
- (2)
In this phase, there may be communication and interaction between attacker and challenger , but attacker cannot obtain the key or any other private information. If attacker can successfully challenge the zero-knowledge property of DME, it means that attacker c annot distinguish whether the key generated by challenger is real or not because attacker cannot access the detailed information of .
:Attacker sends two equally long plaintext messages to challenger ,and randomly selects one plaintext message and performs the encryption algorithm to generate a ciphertext.
:Attacker outputs a value as the guess for , and if ,then attacker wins the game.
If attacker can successfully challenge the zero-knowledge property of DME, it means that attacker cannot gain access to private information or other sensitive information. Therefore, attacker also cannot break the zero-knowledge properties of DME and DKG. Thus, DME and DKG satisfy zero-knowledge properties.
Theorem 4
If there exists a probabilistic polynomial-time attacker such that the advantage , then is capable of constructing an algorithm that undermines the -Verifiability property of the outsourced results of DME.
Proof: To begin, it is necessary to construct a Challenger to challenge the verifiability properties of DME. The objective is to prove that is negligible, meaning that Challenger cannot break the verifiability properties within an ignorable amount.
: Attacker selects a verification key secrecy experiment to challenge, denoted as DME,and sends it to the Challenger .
: Challenger randomly generates the public parameters for DME and DKG and sends them to attacker .
: Attacker executes the simulator to simulate the verification key secrecy experiment and generates a simulated verification key . Challenger randomly selects a bit .
: Challenger performs the outsourced computation and generates a computation result .
: Attacker executes the simulator to estimate whether the computation result generated by the challenger is correct, i.e., .
For any , , demonstrating that the DME scheme achieves the verifiability properties of the outsourced computation.
Theorem 5
Given the decidable hypothesis in the groups and , it can be concluded that the proposed BTDS scheme achieves IND-CPA security within the random oracle model.
Proof: Suppose there exists a polynomial-time attacker that breaks the BTDS scheme with a non-negligible advantage . In this case, we can construct a challenger algorithm that can solve the hard problem with a non-negligible advantage.
In the specific interactive game, a group is selected with a generator , and a bilinear mapping is established. The challenger is provided with a hardness input , where . Without possessing the knowledge of and , the challenger engages in an interactive game with the attacker and computes .
: The attacker selects an access strategy to challenge and sends it to the challenger .
: The challenger randomly selects , and computes the public parameters . These parameters are then sent to the attacker .
: The challenger initializes empty tables , an empty set , and an integer . The attacker is allowed to perform multiple queries on attribute sets according to the following rules.
- (1)
: If the entry exists in the table , it returns ; Otherwise, it randomly selects a value , records the entry in table , and returns .
- (2)
: If the entry exists in the table , it returns ; otherwise, it randomly selects a value , records the entry in table , and returns .
- (3)
: The attacker submits an attribute set to the challenger for private key inquiries. The challenger increments by 1. The challenger randomly selects a value and runs the algorithm. It sets the conversion key as and the private key as . Finally, the entry is stored in the table and returned to the attacker .
- (4)
: The challenger verifies whether there exists an entry in the table corresponding to the index . If such an entry is found, the challenger returns the private key to the attacker . Otherwise, the output is . : The attacker submits two plaintext messages of equal length, and , to the challenger . The challenger randomly selects one of the plaintext messages, denoted as , and encrypts it using the encryption algorithm . The resulting ciphertext is then transmitted to the attacker .
Guess: The attacker provides a value as their conjecture for . If , the challenger outputs 0, indicating that the conjecture for is correct. Otherwise, the challenger outputs 1, indicating that the conjecture for is a random element in the group . When , the challenger can provide a valid simulation, which leads to the following expression: . When is a random element, the value of is completely random to the attacker , thus we have: .
In summary, the challenger can successfully challenge and break the decidability of the hypothesis with a non-negligible advantage.
7. Simulation experiment and performance analysis
7.1. Comparison of schemes
Table 6 and 7 focus on the functional analysis and computational complexity analysis of the BTDS architecture. To facilitate quantitative comparison of the schemes, we denote by the exponentiation operation, the modular exponentiation operation, the bilinear pairing operation, the number of attributes used in the access strategy, and the number of rows in the access structure matrix based on LSSS.
Table 6.
Functional analysis.
Table 7.
Computational complexity analysis.
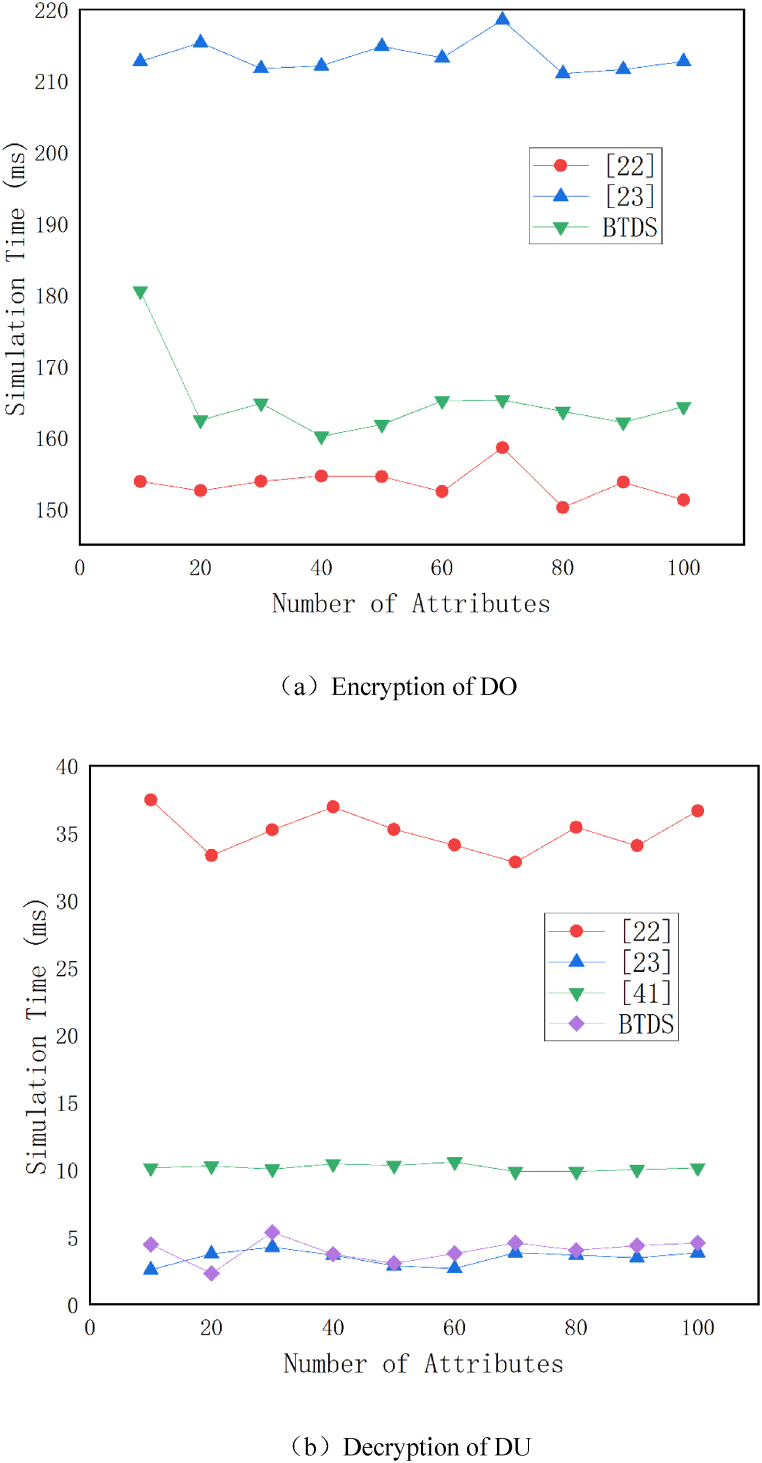
Green et al. [56] proposed the first ABE scheme with outsourced decryption. This scheme involves semi-trusted servers performing (2n + 1) bilinear pairing operations and 2n modular exponentiations to generate partially decrypted ciphertext. The user can then retrieve the original message with a single exponential operation. During the encryption process, the data owner requires (4 + 3n) exponentiation operations and one modular exponentiation.
Li et al. [43] outsourced both encryption and decryption operations to cloud servers, significantly reducing the computational load on user terminals. They not only support outsourced encryption and decryption operations, but also introduce two types of secure outsourced exponentiation algorithms for exponentiation operations in outsourced encryption. These algorithms use mathematical partitioning and blinding operations to hide the bases and exponents contained in the ciphertext components, thus ensuring data privacy. However, the correctness verification probabilities for multiple-base modular exponentiation secure outsourcing algorithms and single-base modular exponentiation secure outsourcing algorithms were only 2/5 and 1/2, respectively. In the [43] scheme, data owners were involved in only 2 exponentiation operations during the encryption computation phase, requiring 2 exponentiation operations and 1 modular multiplication operation in the encryption verification phase. Data users, on the other hand, require only one modular multiplication operation during the decryption computation, but five exponential operations and one bilinear pairing operation during the decryption verification phase. Bilinear pairing computations are significantly more expensive than modular multiplication computations.
Zhao et al. [57] proposed a fully outsourced ciphertext policy attribute-based encryption scheme that supports verifiable key generation, encryption, decryption computations, and the verification of outsourced computation results. During the encryption process, the data owner needs three exponentiation operations and one modular exponentiation operation. In the decryption phase, the data user needs only one exponentiation operation and one modular exponentiation operation.
The aforementioned works [43,56,57] are based on single-authority CP-ABE outsourcing schemes. Sana Belguith et al. [58] introduced a policy-hiding outsourced ABE scheme called PHOABE, based on multi-authority CP-ABE, which delegates the computationally expensive part of the decryption process to a semi-trusted cloud server. During the encryption phase, the data owner needs to perform five exponential operations and one modular exponential operation. Data users outsourced computationally expensive operations, including 3n bilinear pairing operations, 2 modular exponentiation operations, and 1 exponentiation operation, to semi-trusted cloud servers. As a result, the data user only needs to perform 1 exponentiation operation and 1 modular exponentiation operation during the decryption phase.
In this work, we replace the modular exponentiation outsourcing algorithm with a distributed modular exponentiation outsourcing algorithm more suitable for edge computing scenarios, based on the PHOABE scheme. In addition, we use a distributed key generation algorithm in conjunction with EBC to ensure key security while generating user private keys. Unlike the scheme in Ref. [43], our scheme requires data owners to perform 2 additional modular exponentiation operations when using the system public key for encryption operations for the first time. However, it only requires 3 modular exponentiation operations during the encryption verification phase. Data users require one additional modular exponentiation operation during decryption computations but perform fewer operations, including 3 exponentiation operations, 3 modular exponentiations, and 1 bilinear pairing operation, during the verification phase compared to the scheme in Ref. [43].
In addition, the communication overhead of outsourced computations in the BTDS architecture is another significant performance factor. A comprehensive analysis of the communication overhead of the DME algorithm reveals that the user needs to send of data to n edge computing nodes and all edge computing nodes together need to send of data to the user [51]. Thus, the communication cost can be considered negligible compared to the computational time cost within a reasonable healthcare scenario distance.
Finally, the implementation cost of EBC should not be neglected. The storage of ciphertext data copies in the blockchain has a negligible impact on the time cost of the system, since the BTDS architecture is an incremental improvement over the original healthcare cloud storage-based system. All operations take place in the background of the system and do not alter the user experience. Therefore, the primary consideration for the implementation cost of EBC lies in the key generation process when performing the CP-ABE algorithm. The DKG sub-algorithm is a distributed secure key generation protocol implemented on top of EBC, and it guarantees the ‘useable but invisible’ property of the entire CP-ABE algorithm execution. This means that no AA at risk of key leakage can have the system's master private key independently, yet they can still collaborate to generate the user's private key. During this process, the sharing of the system's public key and uploading to the blockchain consensus are performed offline during the system initialization phase, so the real-time cost of this part can be considered negligible. In the user private key generation process, each generates user private key parameters , which include the random selection of , computation of exponentiations , and uploading of these parameters to EBC. The computational cost of each depends on the required exponentiation and data transfer. However, since each AA node is responsible for generating a portion of the private key, the computational cost of a single AA is limited and this cost can also be considered negligible to some extent. The main cost in this section is concentrated in the Lagrangian interpolation computation of the AC ensemble and all partial private keys generated by the AAs. The time complexity of Lagrange interpolation in BTDS architecture mainly depends on the number of input points (AA nodes) and the distributed computing environment's setup. If the number of input points for Lagrange interpolation in BTDS is n, then theoretically, the time complexity of Lagrange interpolation is O(n). This is because the cost of computing each Lagrange basis function is O(1), and there are a total of n basis functions. However, BTDS operates in a distributed computing environment, where different nodes may be responsible for processing different input points. In such a scenario, each node can compute the basis functions it is responsible for in parallel, thus reducing the overall interpolation time cost. Taking everything into consideration, the cost of Lagrange interpolation in BTDS can be approximated as O(n), or even further improved through parallel computation.
Overall, when properly utilizing parallel computing to address the cost of Lagrange interpolation in distributed key generation, this paper's scheme, based on the foundation of literature [43], which incorporates distributed modular exponentiation outsourcing algorithms and distributed key generation protocols better suited for edge computing environments, performs better in terms of computational cost compared to the reference scheme. While it involves an additional computational cost for the public key to the system during the initial encryption operation, it guarantees a 100 % verification probability and significantly reduces the computational cost during the encryption verification phase, making the overall computational cost superior to the compared schemes.
7.2. Experimental analysis
Based on the theoretical analysis presented above, the proposed scheme is better suited for data trust sharing scenarios in edge computing environments in terms of functionality and computational cost. To further evaluate the practical performance of this scheme, this section conducts experiments to analyze the computational overhead on terminal devices, including the encryption time for data owners and the decryption time for data users, in comparison to the literature [43,44,57].
Experimental Environment: The experiments were conducted in a controlled environment using a Windows 10 operating system, an Intel(R) Core(TM) i5-8250U CPU @1.60 GHz 1.80 GHz processor, and 8 GB of memory. The code was developed and executed within the IntelliJ IDEA 2022 development environment, utilizing the JPBC-2.0.0 function library for implementation.
Experimental Setup: In the CP-ABE scheme, the encryption time and decryption time are influenced by the number of attributes. As this paper focuses on the application of CP-ABE in the edge computing environment, the encryption time and decryption time were specifically tested when the Data Owner (DO) and Data User (DU) were considered as terminal nodes. During the experiment, the number of attributes was gradually increased with an average increment of 10. The base value was set to 10, and the results were incremented by a factor of 10. The final experimental results were obtained by averaging the results of 10 iterations.
Fig. 3 consists of two sub-figures: sub-figure (a) shows the computational time comparison for DO during the encryption process, while sub-figure (b) presents the computational time comparison for DU during the decryption process. From Fig. 3, it can be observed that the time spent by DO during the encryption phase and DU during the decryption phase in both the literature [43,44,57] schemes and this paper's scheme does not increase with the number of attributes.
Fig. 3.
Comparison of simulation time.
In Fig. 3 (a), it is evident that the scheme presented in literature [57] outsources all CP-ABE key generation, encryption, and decryption operations to a cloud server, resulting in significantly lower encryption costs for data owners (DO) compared to the schemes in literature [43,44] and this paper's scheme. Literature [43,44] only outsources the computationally expensive modular exponentiation and bilinear pairing operations in the CP-ABE encryption and decryption phases to a cloud server. To better adapt to edge computing environments, this paper replaces the modular exponentiation outsourcing algorithm used in literature [43,44] with the distributed modular exponentiation outsourcing algorithm proposed in literature [51]. This approach outsources the modular exponentiation and bilinear pairing operations in the CP-ABE encryption and decryption phases to edge nodes for parallel computation. Compared to the DO encryption time in the literature [43] scheme, the literature [44] scheme requires more computational time due to the increased correctness probability. However, due to the reduction in DO verification time through the use of distributed modular exponentiation outsourcing, the encryption time is lower than that of the literature [44] scheme.
From Fig. 3 (b), it is evident that literature [43] requires significantly additional time for DU during the decryption and verification phase due to the need for one computationally expensive bilinear pairing operation. Consequently, the overall decryption time for literature [43] is much higher than that of literature [44,57], and this paper's scheme. The decryption time for this paper's scheme is almost identical to that of the literature [44] scheme and considerably lower than that of literature [57].
In summary, the computational time of DO and DU in the proposed scheme does not increase with the number of attributes or the complexity of the access strategy. In this paper, our scheme achieves critical security for CP-ABE at the edge and increases the verifiability probability of the distributed modular exponentiation outsourcing algorithm to 100 %. While maintaining security, the proposed scheme keeps the efficiency of the CP-ABE algorithm within a reasonable range. Therefore, based on these experiments, it is feasible to apply the proposed scheme for trusted sharing of medical data in an edge computing environment.
8. Conclusion
In this paper, we address the issue of trustworthy medical data sharing in edge computing environments and present a blockchain-based Trustworthy Medical Data Sharing (BTDS) solution. We begin by considering the real-time demands of attribute authorization services in edge computing environments and propose a Distributed Attribute Authorization (DAA) strategy based on blockchain. To mitigate the key security concerns of CP-ABE in edge environments, we introduce a Distributed Key Generation (DKG) protocol built on blockchain. To overcome resource limitations in end-user devices, we enhance a Distributed Modular Exponentiation (DME) outsourcing algorithm and apply it to the encryption and decryption outsourcing computations in CP-ABE.
Lastly, we prove the security of the BTDS architecture under the Random Oracle Model and conduct simulation experiments. The results indicate that the computational time for DO and DU in our solution does not increase with the growth in the number of attributes or the complexity of access policies. Instead, it remains within a reasonable and lower range. In summary, the proposed BTDS architecture aligns with the initial design intent of providing fine-grained data access control for resource-constrained end-user devices in edge computing environments.
However, there are some limitations to our study. For instance, the performance of our scheme in large-scale real-world edge computing environments and how to further optimize our scheme to accommodate more complex real-world edge computing scenarios are issues worth investigating. We hope that future research will contribute more in these areas.
Nevertheless, it is important to acknowledge the limitations of our study and identify potential avenues for future research. Specifically, the performance of our scheme in large-scale edge computing environments and the optimization of our scheme to cater to more intricate edge computing scenarios warrant further investigation. We encourage future researchers to delve deeper into these areas, aiming to make significant advancements and contribute valuable insights.
Data availability statement
Data related to this study has not been deposited in a publicly available repository, but will be available upon request.
Ethics declarations
This research study does not require review and/or approval from an ethics committee because it does not involve animal experiments, human subjects, behavioral research, clinical trials, or any form of medical research.
CRediT authorship contribution statement
Gaoyuan Quan: Writing – review & editing, Writing – original draft, Validation, Methodology, Formal analysis, Data curation, Conceptualization. Zhongyuan Yao: Writing – review & editing, Validation, Supervision, Methodology, Funding acquisition, Conceptualization. Longfei Chen: Visualization, Validation, Software, Funding acquisition, Data curation. Yonghao Fang: Visualization, Software, Data curation. Weihua Zhu: Supervision, Project administration, Funding acquisition. Xueming Si: Supervision, Resources, Project administration, Funding acquisition, Conceptualization. Min Li: Writing – review & editing, Investigation.
Declaration of competing interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Acknowledgements
This research was funded by Major Public Welfare Project of Henan Province, grant number 201300210300; Key Science and Technology Project of Henan Province, grant number 222102210168; Open Fund of Henan Key Laboratory of Network Cryptography Technology, grant number LNCT2022- A12, LNCT2021-A14; Postgraduate Research and Innovation Project of Zhongyuan University of Technology, grant number YKY2023ZK52.
Contributor Information
Gaoyuan Quan, Email: 2021116579@zut.edu.cn.
Zhongyuan Yao, Email: yaozhongyuan@zut.edu.cn.
Longfei Chen, Email: 2021016570@zut.edu.cn.
Yonghao Fang, Email: 2021016569@zut.edu.cn.
Weihua Zhu, Email: 9773@zut.edu.cn.
Xueming Si, Email: 9770@zut.edu.cn.
Min Li, Email: 2021116578@zut.edu.cn.
References
- 1.Elia Rafaella, et al. A real‐world data collection framework for a fused dataset creation for joint human and remotely operated vehicle monitoring and anomalous command detection. CAAI Transactions on Intelligence Technology. 2022;7(3):432–445. [Google Scholar]
- 2.Liu Xianchen. Real-world data for the drug development in the digital era. Journal of Artificial Intelligence and Technology. 2022;2(2):42–46. [Google Scholar]
- 3.Fang Liming, et al. Privacy protection for medical data sharing in smart healthcare. ACM Trans. Multimed Comput. Commun. Appl. 2020;16(3s):1–18. [Google Scholar]
- 4.Yang Pan, Xiong Naixue, Ren Jingli. Data security and privacy protection for cloud storage: a survey. IEEE Access. 2020;8:131723–131740. [Google Scholar]
- 5.Newaz AKM Iqtidar, et al. GLOBECOM 2020-2020 IEEE Global Communications Conference. IEEE; 2020. Adversarial attacks to machine learning-based smart healthcare systems. [Google Scholar]
- 6.Yang Yanjiang, et al. Cloud based data sharing with fine-grained proxy re-encryption. Pervasive Mob. Comput. 2016;28:122–134. [Google Scholar]
- 7.Wang Mingwei, et al. Review on offloading of vehicle edge computing. J. Artific. Intell. Technol. 2022;2:132–143. [Google Scholar]
- 8.Li Y., Dong Z., Sha K., Jiang C., Wan J., Wang Y. TMO: time domain outsourcing attribute-based encryption scheme for data acquisition in edge computing. IEEE Access. 2019;7:40240–40257. doi: 10.1109/ACCESS.2019.2907319. [DOI] [Google Scholar]
- 9.Abdollahi S., Mohajeri J., Salmasizadeh M. Highly efficient and revocable CP-ABE with outsourcing decryption for IoT[C]//2021 18th international ISC conference on information security and cryptology (ISCISC) IEEE. 2021:81–88. [Google Scholar]
- 10.Waters B. International Workshop on Public Key Cryptography. Springer Berlin Heidelberg; Berlin, Heidelberg: 2011, March. Ciphertext-policy attribute-based encryption: an expressive, efficient, and provably secure realization; pp. 53–70. [Google Scholar]
- 11.Gao H., Ma Z., Luo S., Xu Y., Wu Z. BSSPD: a blockchain-based security sharing scheme for personal data with fine-grained access control. Wireless Commun. Mobile Comput. 2021;2021:1–20. [Google Scholar]
- 12.Namasudra Suyel, Sharma Pratima Achieving a decentralized and secure cab sharing system using blockchain technology. IEEE Trans. Intell. Transport. Syst. 2022;99:1–10. [Google Scholar]
- 13.Yan L., Ge L., Wang Z., et al. Access control scheme based on blockchain and attribute-based searchable encryption in cloud environment. J. Cloud Comput. 2023;12:61. doi: 10.1186/s13677-023-00444-4. [DOI] [Google Scholar]
- 14.Liu Xiaoguang, et al. A blockchain-based medical data sharing and protection scheme. IEEE Access. 2019;7:118943–118953. [Google Scholar]
- 15.Jaiman Vikas, Urovi Visara. A consent model for blockchain-based health data sharing platforms. IEEE Access. 2020;8:143734–143745. [Google Scholar]
- 16.Sharma Pratima, et al. EHDHE: enhancing security of healthcare documents in IoT-enabled digital healthcare ecosystems using blockchain. Inf. Sci. 2023;629:703–718. [Google Scholar]
- 17.Sharma Pratima, et al. Blockchain-based privacy preservation for IoT-enabled healthcare system. ACM Trans. Sens. Netw. 2023;19(3):1–17. [Google Scholar]
- 18.Zou Renpeng, Lv Xixiang, Zhao Jingsong. SPChain: blockchain-based medical data sharing and privacy-preserving eHealth system. Inf. Process. Manag. 2021;58(4) [Google Scholar]
- 19.Abdellatif Alaa Awad, et al. Medge-chain: leveraging edge computing and blockchain for efficient medical data exchange. IEEE Internet Things J. 2021;8(21):15762–15775. [Google Scholar]
- 20.Akkaoui Raifa, Hei Xiaojun, Cheng Wenqing. EdgeMediChain: a hybrid edge blockchain-based framework for health data exchange. IEEE Access. 2020;8:113467–113486. [Google Scholar]
- 21.Li X., Liu T., Obaidat M.S., Wu F., Vijayakumar P., Kumar N. A lightweight privacy-preserving authentication protocol for VANETs. IEEE Syst. J. 2020;14(3):3547–3557. [Google Scholar]
- 22.Cao K., Liu Y., Meng G., Sun Q. An overview on edge computing research. IEEE Access. 2020;8:85714–85728. [Google Scholar]
- 23.Alshehri M., Panda B., Almakdi S., Alazeb A., Halawani H., Al Mudawi N., Khan R.U. A novel blockchain-based encryption model to protect fog nodes from behaviors of malicious nodes. Electronics. 2021;10(24):3135. [Google Scholar]
- 24.Abdullayeva Fargana J. Internet of Things‐based healthcare system on patient demographic data in Health 4.0. CAAI Transactions on Intelligence Technology. 2022;7(4):644–657. [Google Scholar]
- 25.Odelu Vanga, et al. Expressive CP-ABE scheme for mobile devices in IoT satisfying constant-size keys and ciphertexts. IEEE Access. 2017;5:3273–3283. [Google Scholar]
- 26.Jiang Y., Susilo W., Mu Y., Guo F. Ciphertext-policy attribute-based encryption against key-delegation abuse in fog computing. Future Generat. Comput. Syst. 2018;78:720–729. [Google Scholar]
- 27.Wang H., Zheng Z., Wu L., Wang Y. Adaptively secure outsourcing ciphertext-policy attribute-based encryption. J. Comput. Res. Dev. 2015;52(10):2270–2280. [Google Scholar]
- 28.Li Q., Ma J.F., Xiong J.B., Liu X.M., Ma J. An adaptively secure multi-authority ciphertext-policy ABE scheme on prime order groups. ACTA ELECTONICA SINICA. 2014;42(4):696. [Google Scholar]
- 29.Li J., Fan Y., Bian X., Yuan Q. Online/offline MA-CP-ABE with cryptographic reverse firewalls for IoT. Entropy. 2023;25(4):616. doi: 10.3390/e25040616. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 30.Priya Remamany K., Maheswari K., Ramesh Babu Durai C., Anushkannan N.K., Victoria D.R.S., Ben Othman M.T., Hamdi M., Hamam H. A localized Bloom filter-based CP-ABE in smart healthcare. Appl. Sci. 2022;12(24) [Google Scholar]
- 31.Cheng F., Ji S., Lai C.F. Efficient CP-ABE scheme resistant to key leakage for secure cloud-fog computing. J. Internet Technol. 2022;23(7):1461–1471. [Google Scholar]
- 32.Deng Yuli, et al. Problem-Based cybersecurity lab with knowledge graph as guidance. Journal of Artificial Intelligence and Technology. 2021;2:55–61. [Google Scholar]
- 33.Hooshmand Mohammad Kazim, Hosahalli Doreswamy. Network anomaly detection using deep learning techniques. CAAI Transactions on Intelligence Technology. 2022;7(2):228–243. [Google Scholar]
- 34.Yang H.K., Feng C.S., Jin Y.X., Wang L., Luo W.P., Deng H.H. ACP-ABE scheme with verifiable outsourced encryption and decryption. ACTA ELECTONICA SINICA. 2020;48(8):1545. [Google Scholar]
- 35.Sethi Kamalakanta, Pradhan Ankit, Bera Padmalochan. Practical traceable multi-authority CP-ABE with outsourcing decryption and access policy updation. J. Inf. Secur. Appl. 2020;51 [Google Scholar]
- 36.Zhao K.Q., Kang P., Liu B., Guo Z., Feng C.S., Qing Y. A CP-ABE scheme with cloud proxy Re-encryption. ACTA ELECTONICA SINICA. 2023;51(3):728. [Google Scholar]
- 37.Premkamal Praveen Kumar, Kumar Pasupuleti Syam, Alphonse P.J.A. Dynamic traceable CP‐ABE with revocation for outsourced big data in cloud storage. Int. J. Commun. Syst. 2021;34(2) [Google Scholar]
- 38.Jiangtao D.O.N.G., Peiwen Y.A.N., Ruizhong D.U. Verifiable access control scheme based on unpaired CP-ABE in fog computing. J. Commun. 2021;42(8):139–150. [Google Scholar]
- 39.Zou L.P., Feng C.S., Oin Z.G., Yuan D., Luo W.P., Li M. CP-ABE scheme with fast decryption for public cloud. RuanJian Xue Bao/Journal of Software. 2020;31(6):1817–1828. http://www.jos.org.cn/1000-9825/5704.htm (in Chinese) [Google Scholar]
- 40.Touati L., Challal Y., Bouabdallah A. IEEE; 2014. C-cp-abe: Cooperative Ciphertext Policy Attribute-Based Encryption for the Internet of things[C]//2014 International Conference on Advanced Networking Distributed Systems and Applications; pp. 64–69. [Google Scholar]
- 41.Kiraz M.S., Uzunkol O. Efficient and verifiable algorithms for secure outsourcing of cryptographic computations. Int. J. Inf. Secur. 2016;15:519–537. [Google Scholar]
- 42.Moffat S., Hammoudeh M., Hegarty R. 2017. A Survey on Ciphertext-Policy Attribute-Based Encryption (CP-ABE) Approaches to Data Security on Mobile Devices and its Application to IoT[C]//Proceedings of the International Conference on Future Networks and Distributed Systems. [Google Scholar]
- 43.Li Z., Li W., Jin Z., Zhang H., Wen Q. An efficient ABE scheme with verifiable outsourced encryption and decryption. IEEE Access. 2019;7:29023–29037. [Google Scholar]
- 44.Yan X.X., He G.H., Yu J.X. Secure and verifiable outsourced ciphertext policy attribute-based encryption. Journal of Cryptologic Research. 2020;7(5):628–642. doi: 10.13868/j.cnki.jcr.000395. [DOI] [Google Scholar]
- 45.Huang Haijun, et al. A traceable and verifiable CP-ABE scheme with blockchain in VANET. J. Supercomput. 2023:1–25. [Google Scholar]
- 46.Liu, Jianwei, et al. “Space-Air-Ground Integrated Network Security 9819911249, 9789819911240.” Ebin.pub, 25 June 406AD, ebin.pub/space-air-ground-integrated-network-security-9819911249-9789819911240.html. Accessed 3 November. 2023.
- 47.Zhou W., Wang H., Mohiuddin G., Chen D., Ren Y. Consensus mechanism of blockchain based on por with data deduplication. Intelligent Automation & Soft Computing. 2022;34(3):1473–1488. [Google Scholar]
- 48.Chen L., Yao Z., Si X., Zhang Q. Three-stage cross-chain protocol based on notary group. Electronics. 2023;12:2804. doi: 10.3390/electronics12132804. [DOI] [Google Scholar]
- 49.Liu Z., Pang H., Li Y., Li S. 2021 International Conference on Computer, Blockchain and Financial Development. CBFD); Nanjing, China: 2021. "Research on distributed energy network transaction model based on blockchain,"; pp. 311–314. [DOI] [Google Scholar]
- 50.Shao Q.F., Jin C.Q., Zhang Z., et al. Blockchain: architecture and research progress. Chin. J. Comput. 2018;41(5):969–988. [Google Scholar]
- 51.Li H., Yu J., Zhang H., et al. Privacy-preserving and distributed algorithms for modular exponentiation in IoT with edge computing assistance. IEEE Internet Things J. 2020;7(9):8769–8779. [Google Scholar]
- 52.Luo Sheng. User privacy protection scheme based on verifiable outsourcing attribute-based encryption. Secur. Commun. Network. 2021;2021 doi: 10.1155/2021/6617669. Article ID 6617669, 11 pages. [DOI] [Google Scholar]
- 53.Li H., Yu J., Zhang H., Yang M., Wang H. Privacy-Preserving and distributed algorithms for modular exponentiation in IoT with edge computing assistance. IEEE Internet Things J. Sept. 2020;7(9):8769–8779. doi: 10.1109/JIOT.2020.2995677. [DOI] [Google Scholar]
- 54.Lei X.F., Xie K.Q., Lin F., Xia Z.Y. An efficient clustering algorithm based on local optimality of K-Means. Journal of Software. 2008;19(7):1683–1692. http://www.jos.org.cn/1000-9825/19/1683.htm [Google Scholar]
- 55.Zhang F., Wang Y. Distributed key generation based on generalized verifiable secret sharing. ACTA ELECTONICA SINICA. 2003;31(4):580. [Google Scholar]
- 56.Green M., Hohenberger S., Waters B. vol. 11. USENIX Security; 2011. Outsourcing the decryption of {ABE} ciphertexts. (20th USENIX Security Symposium). [Google Scholar]
- 57.Zhao Z.Y., Wang J.H., Xu K., et al. Fully outsourced attribute-based encryption with verifiability for cloud storage. J. Comput. Res. Dev. 2019;56(2):442–452. [Google Scholar]
- 58.Belguith Sana, et al. Phoabe: securely outsourcing multi-authority attribute based encryption with policy hidden for cloud assisted iot. Comput. Network. 2018;133:141–156. [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Data related to this study has not been deposited in a publicly available repository, but will be available upon request.