Abstract
In this article, we derive the Archimedean aggregation operators for complex intuitionistic fuzzy sets, for this, first, we evaluate some Archimedean operational laws based on complex intuitionistic fuzzy values and then we discuss their special cases because the Archimedean norms are the general form of all existing norms, for instance, algebraic, Einstein, Hamacher, and Frank operational laws. Furthermore, we present the complex intuitionistic fuzzy Archimedean Heronian aggregation operator and complex intuitionistic fuzzy weighted Archimedean Heronian aggregation operator. Several special cases and the basic properties of the above-proposed operators are also diagnosed, because proposing the Heronian mean operators based on Archimedean norms are very challenging and complicated tasks, because of their features and structure. Additionally, a decision-making process is developed under the identified operators by using complex intuitionistic fuzzy information. Finally, we illustrate several examples to show the multi-attribute decision-making technique is more flexible than the prevailing works with the help of sensitive analysis between explored and certain prevailing works.
Keywords: Complex intuitionistic fuzzy sets, Heronian mean operators, Archimedean t-norm and t-conorm, Decision-making techniques
1. Introduction
The decision-making procedure is a technique that contains a lot of types, for instance, MADM technique, MAGDM technique, MCDM technique, and many others, which are used for addressing the best optimal among the collection of finite decisions. In some cases, experts have lost a lot of data, if they use the classical information for evaluating the MADM procedure because in the case of classical set theory, experts have only two opinions like zero or one. Zadeh [1] extended the range of the classical set and derived the FS. The range of FS is unit interval instead of {0,1} and because of this reason, experts have a lot of space for taking their decision. Adjust the grade of falsity is a very challenging task for scholars, because in many cases the falsity grade played an important role, especially during the elections, For handling such kind of problems, Atanassov [2] computed the IFS with a well-known rule: , where and represents the TD and FD. Some extensions and implementations of IFS are as follows: IVIFSs [3], Dombi aggregation operators for IFSs [4], entropy measures for IVIFSs [5], Bipolar soft sets [6], failure mode and effects analysis [7], improved TODIM processes [8], operational laws for IFSs [9], aggregation and infinite chains for IFSs [10], parameterized IVIFSs [11], telecom services providers under the IFSs [12], MABAC method for IFSs [13], and distance measures for IVIFSs [14].
The TD in FS theory is computed in the form of a simple function that can easily deal with one-dimensional information, but in our daily life problems, experts have faced a lot of problems that are present in the shape of two-dimensional information. For managing such kinds of problems, we needed to find a structure that has computed in the shape of a complex number, where the complex number can easily depict the two-dimensional problem. Therefore, we found a novel concept of complex FS (CFS), which was invented by Ramot et al. [15]. The TD in CFS is arranged in the shape of polar coordinates. Furthermore, operation properties for CFS were explored by Zhang et al. [16], complex fuzzy logic was explored by Ramot et al. [17], systematic view of CFS was presented by Yazdanbakhsh and Disk [18], neuro-fuzzy architecture for CFSs was developed by Chan et al. [19], complex neuro-fuzzy ARIMA forecasting was initiated by Li and Chiang [20], Distance measures for CFS was proposed by Hu et al. [21], periodic factor based on CFS was investigated by Ma et al. [22], linguistic variable for CFS was explored by Alkouri and Salleh [23], cross-entropy measures for CFSs was developed by Liu et al. [24], and distance measures for interval-valued CFSs were presented Dai et al. [25]. But sometimes the principle of CFS is enabled to describe the ambiguity and inconsistency in genuine life dilemmas. For this, the principle of complex IFS (CIFS) was initiated by Alkouri and Salleh [26] by putting the FD in the region of CFSs, which covers only the TD with some well-known rules: and . CFSs are the specific part of the CIFSs, and numerous individuals have employed them in distinct regions. For illustration, information measures [27], robust correlation coefficient [28], generalized geometric aggregation operators [29], robust averaging/geometric aggregation operators [30], aggregation operators for generalized CIFSs [31], power aggregation operators [32], preference relation for CIFSs [33], and complex intuitionistic fuzzy soft sets [34].
The fundamental theory of Archimedean norms for IFS was proposed by Xia et al. [35], with the help of Archimedean norms, we can easily derive any kind of operators and their special cases. Furthermore, Luo et al. [36] initiated the exponential laws for IFS. Garg and Rani [37] elaborated on the generalized Bonferroni mean operators for IFSs. Moreover, Yu [38] initiated interval-valued multiplicative IFS based on Archimedean TN and TCN. Ma and Yang [39] presented the weighted mean operators using the Archimedean TN and TCN for IFSs. Liu et al. [40] derived the Quasi-OWA operators. Liu and Chen [41] proposed to the HM operators. Seikh and Mandal [42] evaluated the Frank operators for q-rung orthopair fuzzy sets and their application in decision-making. Recently, Seikh and Mandal [43] evaluated the Frank operators for picture fuzzy sets and their application in decision-making problems. After a brief discussion, we noticed that all experts have the following major issues, such as:
-
1)
How do we evaluate generalized operational laws for all t-norms and t-conorms?
-
2)
How do we propose generalized aggregation operators for CIFSs?
-
3)
How do we rank all the alternatives for evaluating the best optimal between a finite number of alternatives?
For dealing with the above three queries, we needed to develop the Archimedean Heronian mean operators for CIFSs because, with the help of these investigations, we can easily derive any kind of operators. It is clear that many scholars have invented the Heronian mean operators for FSs, and IFSs, but no one can derive it for CIFSs. Furthermore, the Archimedean operational laws for IFS have been proposed, but no one can derive them for CIFSs. Combining the Archimedean operational laws and Heronian mean operators with CIFS is very awkward and complicated because no one can derive it after the investigation of CIFS in 2012 up to yet. The proposed techniques are very reliable and dominant because of their structure, where many advantages follow, for instance, Archimedean aggregation operators, Heronian mean operators, Aggregation operators, Einstein aggregation operators, Hamacher aggregation operators, Frank aggregation operators, Heronian Aggregation operators, Einstein Heronian aggregation operators, Hamacher Heronian aggregation operators, and Frank Heronian aggregation operators for FSs, IFSs, CFSs, and CIFSs are exceptional cases of the derived work. Similarly, we have a lot of possibilities to derive different types of operators from the invented Archimedean Heronian mean operators based on CIFSs. Based on the above advantages, the major contributions of the derived operators are listed below:
-
1)
To propose the Archimedean operational laws based on CIF values.
-
2)
To derive the algebraic operational laws, Einstein operational laws, Hamacher operational laws, and Frank operational laws from the Archimedean operational laws by using different values of the functions in Archimedean operational laws.
-
3)
To evaluate the CIFAHA operator and CIFWAHA operator. Several special cases and the basic properties of the above-proposed operators are also diagnosed.
-
4)
To illustrate the MADM process is developed under the identified operators by using CIF information.
-
5)
To discover several examples to show the MADM technique is massively more flexible than the prevailing works with the help of sensitive analysis between explored and certain prevailing works. The major findings of the proposed theory are stated in Fig. 1.
Fig. 1.
Representation of the summery of the proposed approaches.
The major objective of this analysis is reviewed in the subsequent approaches: In section 2, we revised the prevailing principles of CIFSs and their algebraic laws. Moreover, the principle of HM operator, algebraic, Einstein, Hamacher, frank operational laws, and the generalized form of TN and TCN are also revised in this study. In section 3, we elaborated on the algebraic, Einstein, Hamacher, and Frank rules for the CIF setting. Numerous specific cases of the presented rules are also illustrated with the help of parameters. In section 4, we initiated the CIFAHA operator and the CIFWAHA operator. Several important properties and their related results are also diagnosed. In section 5, we developed a MADM process under the identified operators by using CIF information. We illustrated several examples to show the MADM technique is massive flexible than the prevailing works with the help of sensitive analysis between explored and certain prevailing works. In section 6, we employed the assumption of this analysis.
2. Preliminaries
In this analysis, we revised the prevailing principles of CIFSs and their algebraic laws. Moreover, the principle of HM operator, algebraic, Einstein, Hamacher, frank operational laws, and the generalized form of TN and TCN are also revised in this study. The term and , stated the TD and FD and the universal were invented by .
Definition 1
[26] An CIFS is invented by:
(1) where and , with and . The structure , conveyed the neutral grade. The CIFNs are mentioned by: .
Definition 2
[28] Choose any two CIFNs and , then
| (2) |
| (3) |
| (4) |
| (5) |
For more simplification, we justify the data in Def. (2) with the help of some suitable examples, for this we consider any two CIFNs, such as and with , then
Definition 3
[29] Choose any CIFN , then the score value (SV) is invented by:
| (6) |
where .
Definition 4
[30] Choose any CIFN , then the accuracy value (AV) is invented by:
| (7) |
where .
Keeping in mind Eqs. (1), (2), (3), (4), (5), we have the following notions.
Definition 5
[30] Choose any two CIFNs and , then by using Eq. (6) and Eq. (7), we initiate
- 1.
;
- 2.
;
- 3.
.
- i)
;- ii)
;- iii)
.
Definition 6
[40] Choose any group of integers (+ve) , thus
(8) Eq. (8) represents the HM operator, where . Furthermore, various valuable and well-known norms are stated below:
- 1.
Algebraic norms [41]:
(9)
(10)
- 2.
Einstein norms [41]:
(11)
(12)
- 3.
Hamacher norms [41]:
(13)
(14)
- 4.
Frank norms [41]:
(15)
(16) The modified and general form of TN and TCN is listed below in Eq. (17) and Eq. (18):
(17)
(18) where .
3. Archimedean operational laws for CIFSs
In this section, we discover the well-known and famous theory of algebraic, Einstein, Hamacher, and Frank's rules for CIF information. These operations play an essential role in the construction of any kind of aggregation operator.
Definition 7
Choose any two CIFNs and , then
(19)
(20)
(21)
(22) To select the data in Eq. (9) and Eq. (10), then the data in Eq. (19) to Eq. (22) will be transformed to Eq. (2) to Eq. (5), called algebraic laws, further, to select the data in Eq. (11) and Eq. (12), then the data in Eq. (19) to Eq. (22) will be transformed to Eq. (23) to Eq. (26), called Einstein laws, such as
(23)
(24)
(25)
(26) To select the data in Eq. (11) and Eq. (12), then the data in Eq. (19) to Eq. (22) will be transformed to Eq. (27) to Eq. (30), called Hamacher laws, such as
(27)
(28)
(29)
(30) To choose the value of in Eq. (27) to Eq. (30), we will get the data in Eq. (2) to Eq. (5), when we select the value of in Eq. (27) to Eq. (30), thus we will derive the data in Eq. (23) to Eq. (26). To consider the data in Eq. (13) and Eq. (14), then the data in Eq. (19) to Eq. (22) will be transformed to Eq. (31) to Eq. (34), called Frank laws, such as
(31)
(32)
(33)
(34)
4. Proposed archimedean operators for CIFSs
In this section, we discovered the CIFAHA operator, CIFWAHA operator, and their special cases with the help of some conditions. Several important properties and their related results are also diagnosed.
Definition 8
Choose any group of CIFNs , then the CIFAHA operator is invented by:
(35) where .
Theorem 1
Choose any group of CIFNs, then by using Eq. (35), we initiate
(36) Proof: Consider
then,
and,
Under Eq. (35) and Eq. (36), we employed some properties like idempotency, monotonicity, and boundedness.
Property 1
Choose any group of CIFNs. If, then
(37) Proof: By hypothesis , then
This proves Eq. (37).
Property 2
Choose any group of CIFNs. If, then
(38) Proof: By hypothesis, we know that if that's mean and , then
thus,
then,
thus,
therefore,
Similarly, we investigate for an unreal term, such that
Moreover, for real and unreal terms of FD, we have
and,
By using Eq. (6), we easily get the terms.
This proves Eq. (38).
Property 3
Choose any group of CIFNs. Ifand, then
(39) Proof: To prove Eq. (39), we proceed as follows:
By hypothesis and , then by using Property 2, we initiate
where and , then
Where various realistic cases are stated below:
- 1.
For , Eq. (36) will be transformed to
(40) Signified as a CIF generalized heavy-weighted averaging operator (CIFGHWAO).
- 2.
For , and , Eq. (36) will be transformed to
(41) Signified as a CIF heavy-weighted averaging operator (CIFHWAO).
- 3.
For , Eq. (36) will be transformed to
(42) Signified as a CIFGHWAO.
- 4.
For and , Eq. (36) will be transformed to
(43)
(44) Signified as a CIFHM operator.
(45) Where and .
Signified as a CIF Einstein HM operator.
(46) Where
and
Signified as a CIF Hamacher HM operator.
(47) Where
and
Signified as a CIF Frank HM operator.
Definition 9
Choose any group of CIFNs , then the CIFWAHA operator is invented by:
(48) Observed that , with , called weight vectors
Theorem 2
Choose any group of CIFNs, then by using Eq. (48), we initiate
(49) Proof: Skipped.
5. Decision-making procedure for derived operators
In this section, we concentrate on evaluating the MADM procedure in the presence of the invented operators for CIFSs. For this, we used the special cases of the proposed operators and tried to evaluate their decision matrix to enhance the stability and worth of the invented operators.
5.1. The procedure of the MADM technique
Consider the finite collection of alternatives and number of attributes with weight vector with a rule . For the above information, we compute the matrix by including their values in the shape of CIFNs, such as , where and , with and . For simplification of some numerical examples, we evaluate the procedure of decision-making techniques, such as
Stage 1: To select the CIFNs, we construct the matrix, if the matrix covers the cost type of data, then we normalize the matrix, such as
But in the case of benefit types of data, we are not required to normalize the data.
Stage 2: We aggregate the information in the matrix.
Stage 3: Derive or discover the score value (SV) of the above aggregated information.
Stage 4: For discovering the most preferable decision, based on the score values, we rank alternatives. The graphical representation of the proposed decision-making procedure is listed in Fig. 2.
Fig. 2.
Geometrical representation of the proposed decision-making procedure.
Finally, we analyze some examples based on the invented theory for evaluating the consistency and validity of the proposed operators as well as the decision-making procedure.
5.2. Analysis of best madia communications
Media communication covers numerous techniques and technologies for transmitting or showing information, data, material, or messages with the help of different sources like the internet, mobile phones, television, and different channels. All these channels are categorized into different kinds based on the medium or platform exploited for communications. The major influence of this application is to find the best kind of media communications among the five best, such as:
-
1)
Print Media “”.
-
2)
Broadcast Media “”.
-
3)
Digital Media “”.
-
4)
Social Media “”.
-
5)
Telecommunications “”.
To address the best one, we use some features as an attribute's values, such as : Growing analysis, : Community-governmental impact, : Ecological impact, and : others. To achieve our target, we consider the weight vectors, such as and . For simplification of some numerical examples, we evaluate the procedure of decision-making techniques, such as
Stage 1: To select the CIFNs, we construct the matrix, see Tables 1 and If the matrix covers the cost type of data, then we normalize the matrix, such as
Table 1.
The original matrix is given by the decision-maker.
|
|
|
|
But in the case of benefit types of data, we are not required to normalize the data. Anyhow the data in Table 1 is not required to be normalized.
Stage 2: To consider the data in Eq. (36) for , the aggregation values are listed below:
Stage 3: For ranking values, we expose the score values, such as
Stage 4: The ranking information is listed below:
Seen that is the best one. Further, to eliminate the phase term from the data in Table 1, we obtained the simple IFS, see Table 2.
Table 2.
The original matrix is given by the decision-maker.
To consider the data in Eq. (36) for , the aggregated values are listed below:
For ranking values, we expose the score values, such as
The ranking information is listed below:
Seen that is the best one. Moreover, we derive the comparison between proposed and existing operators to improve the worth of the derived theory.
5.3. Sensitive analysis
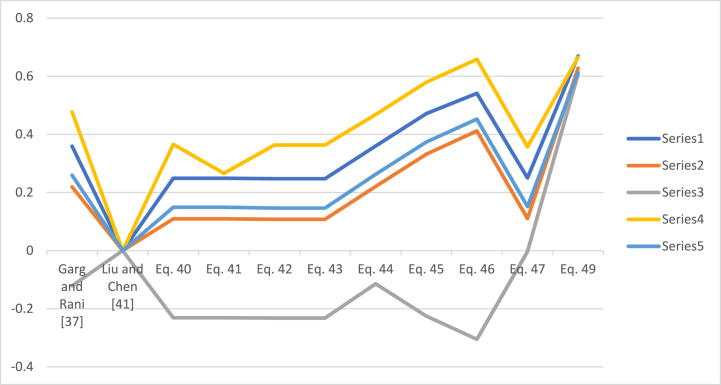
In this section, we compare the discovered operators with some prevailing operators based on the data in Table 1 with phase term and without phase term. For comparing the invented techniques with existing techniques, we consider some valuable and dominant techniques to improve the worth of the invented theory. For this, we consider the following existing techniques, such as Garg and Rani [37] elaborated generalized Bonferroni mean operators for CIFSs, Liu, and Chen [41] initiated the HM operators for IFSs, and proposed works based on CIFSs. To consider the data in Table 1, the comparative analysis is listed in Table 3.
Table 3.
Sensitive analysis (Table 1).
Seen that is the best one according to some operators and see that is the best one according to some operators. The geometrical interpretation of the data in Table 3 is listed in Fig. 3.
Fig. 3.
Geometrical representation of the data in Table 3.
Furthermore, we state the influence of the parameters and . For this, first, we fixed the value of , then for different values of , the ranking values are stated in Table 4.
Table 4.
Influence of the parameter , if , (Table 1).
| Parameter | Score Values | Ranking Values |
|---|---|---|
We fixed the value of , then the influence of the , stated in Table 5.
Table 5.
Influence of the parameter if , (Table 1).
| Parameter | Score Values | Ranking Values |
|---|---|---|
We fixed the value of , then the influence of the , stated in Table 6.
Table 6.
Influence of the parameter if , (Table 1).
| Parameter | Score Values | Ranking Values |
|---|---|---|
We fixed the value of , then the influence of the , stated in Table 7.
Table 7.
Influence of the parameter if , (Table 1).
| Parameter | Score Values | Ranking Values |
|---|---|---|
In the above investigation, we observed that for every value of parameters, we derive the same ranking results. The benefit of the proposed theory is that, with the help of proposed operators we can derive the ranking values of the many operators like algebraic, Einstein, Hamacher, and frank aggregation operators. Hence, the derived operator is more flexible and more dominant compared to other existing techniques.
6. Conclusion
Archimedean aggregation operators and Heronian mean operators are two different types of operators used for aggregating the collection of information into a singleton set. Keeping the advantages of the above operators, the major contributions of the derived operators are listed below:
-
1.
We proposed the Archimedean operational laws based on CIF values.
-
2.
We derived the algebraic operational laws, Einstein operational laws, Hamacher operational laws, and Frank operational laws from the Archimedean operational laws by using different values of the functions in Archimedean operational laws.
-
3.
We evaluated the CIFAHA operator and CIFWAHA operator. Several special cases and the basic properties of the above-proposed operators are also diagnosed.
-
4.
We illustrated the MADM process developed under the identified operators by using CIF information.
-
5.
We discovered several examples to show the MADM technique is massively more flexible than the prevailing works with the help of sensitive analysis between explored and certain prevailing works.
6.1. Limitations of the proposed works
The proposed Archimedean Heronian mean operators based on CIFS are very flexible and dominant because of their structure and features, but in complicated situations, these ideas have not worked properly, for instance, if we are faced the information in the shape of yes, abstinence, no, and refusal, then the proposed operators based on CIFS have been failed. For this, we are required to compute these operators based on complex T-spherical fuzzy sets and their extensions.
6.2. Future direction
In the upcoming time, the proposed operators based on CIFS will receive a lot of attraction because, with the help of these operators, we can easily depict unreliable and vague information. Further, these operators will be utilized in the circumstances of complex Pythagorean fuzzy sets and their extensions. With the help of the proposed work, we can easily evaluate the problem of machine learning, medical diagnosis, artificial intelligence, neural networks, and many others if someone provides practical data. Moreover, we will employ the principle of complex fuzzy sets [[44], [45], [46]] quasirung orthopair fuzzy sets [47,48], complex q-rung orthopair fuzzy sets [[49], [50], [51]], complex spherical and T-spherical fuzzy sets [52,53], T-spherical fuzzy sets [[54], [55], [56]], and linear Diophantine fuzzy sets [[57], [58], [59], [60], [61]] in the environment of medical diagnosis, pattern recognition, manufacturing science, and computer science to grow the excellence of the explore mechanisms.
Ethics declaration statement
The authors state that this is their original work, and it is neither submitted nor under consideration in any other journal simultaneously.
Data availability
The authors agree that the data used in this manuscript is available to everyone and anyone can use this data by just citing this article.
CRediT authorship contribution statement
Zeeshan Ali: Writing – review & editing, Writing – original draft, Resources, Methodology, Investigation, Formal analysis, Conceptualization. Walid Emam: Resources, Methodology, Investigation, Funding acquisition, Formal analysis. Tahir Mahmood: Writing – review & editing, Validation, Supervision, Project administration, Investigation, Formal analysis, Conceptualization. Haolun Wang: Validation, Resources, Methodology, Investigation, Formal analysis.
Declaration of competing interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Funding Acknowledgement
The study was funded by Researchers Supporting Project number (RSP2024R749), King Saud University, Riyadh, Saudi Arabia.
Contributor Information
Zeeshan Ali, Email: zeeshanalinsr@gmail.com.
Walid Emam, Email: wemam.c@ksu.edu.sa.
Tahir Mahmood, Email: tahirbakhat@iiu.edu.pk.
Haolun Wang, Email: hlwang71162@nchu.edu.cn.
References
- 1.Zadeh L.A. Fuzzy sets. Inf. Control. 1965;8(3):338–353. [Google Scholar]
- 2.Atanassov K. Intuitionistic fuzzy sets. Fuzzy Set Syst. 1986;20(1):87–96. [Google Scholar]
- 3.Huang W., Zhang F., Xu S. A complete ranking method for interval-valued intuitionistic fuzzy numbers and their applications to multicriteria decision making. Soft Comput. 2021;25(3):2513–2520. [Google Scholar]
- 4.Seikh M.R., Mandal U. Intuitionistic fuzzy Dombi aggregation operators and their application to multiple attribute decision-making. Granular Computing. 2021;6(3):473–488. [Google Scholar]
- 5.Tiwari P. Generalized entropy and Similarity measure for interval-valued intuitionistic fuzzy sets with application in decision making. Int. J. Fuzzy Syst. Appl. 2021;10(1):64–93. [Google Scholar]
- 6.Mahmood T. A novel approach towards bipolar soft sets and their applications. J. Math. 2020;2020 Article ID: 4690808, 2020. [Google Scholar]
- 7.Huang G., Xiao L. Failure mode and effect analysis: an interval-valued intuitionistic fuzzy cloud theory-based method. Appl. Soft Comput. 2021;98:106834–106857. [Google Scholar]
- 8.Zhao M., Wei G., Wei C., Wu J. Improved TODIM method for intuitionistic fuzzy MAGDM based on cumulative prospect theory and its application on stock investment selection. International Journal of Machine Learning and Cybernetics. 2021;12(3):891–901. [Google Scholar]
- 9.Du W.S. Subtraction and division operations on intuitionistic fuzzy sets derived from the Hamming distance. Inf. Sci. 2021;571:206–224. [Google Scholar]
- 10.Alcantud J.C.R., Khameneh A.Z., Kilicman A. Aggregation of infinite chains of intuitionistic fuzzy sets and their application to choices with temporal intuitionistic fuzzy information. Inf. Sci. 2020;514:106–117. [Google Scholar]
- 11.Aydın T., Enginoğlu S. Interval-valued intuitionistic fuzzy parameterized interval-valued intuitionistic fuzzy soft sets and their application in decision-making. J. Ambient Intell. Hum. Comput. 2021;12(1):1541–1558. [Google Scholar]
- 12.Rani P., Mishra A.R., Ansari M.D., Ali J. Assessment of performance of telecom service providers using intuitionistic fuzzy grey relational analysis framework (IF-GRA) Soft Comput. 2021;25(3):1983–1993. [Google Scholar]
- 13.Mishra A.R., Garg A.K., Purwar H., Rana P., Liao H., Mardani A. An extended intuitionistic fuzzy multi-attributive border approximation area comparison approach for smartphone selection using discrimination measures. Informatica. 2021;32(1):119–143. [Google Scholar]
- 14.Liu Y., Jiang W. A new distance measure of interval-valued intuitionistic fuzzy sets and its application in decision making. Soft Comput. 2020;24(9):6987–7003. [Google Scholar]
- 15.Ramot D., Milo R., Friedman M., Kandel A. Complex fuzzy sets. IEEE Trans. Fuzzy Syst. 2002;10(2):171–186. [Google Scholar]
- 16.Zhang G., Dillon T.S., Cai K.Y., Ma J., Lu J. Operation properties and δ-equalities of complex fuzzy sets. Int. J. Approx. Reason. 2009;50(8):1227–1249. [Google Scholar]
- 17.Ramot D., Friedman M., Langholz G., Kandel A. Complex fuzzy logic. IEEE Trans. Fuzzy Syst. 2003;11(4):450–461. [Google Scholar]
- 18.Yazdanbakhsh O., Dick S. A systematic review of complex fuzzy sets and logic. Fuzzy Set Syst. 2018;338:1–22. [Google Scholar]
- 19.Chen Z., Aghakhani S., Man J., Dick S. ANCFIS: a neuro-fuzzy architecture employing complex fuzzy sets. IEEE Trans. Fuzzy Syst. 2010;19(2):305–322. [Google Scholar]
- 20.Li C., Chiang T.W. Complex neuro-fuzzy ARIMA forecasting—a new approach using complex fuzzy sets. IEEE Trans. Fuzzy Syst. 2012;21(3):567–584. [Google Scholar]
- 21.Hu B., Bi L., Dai S., Li S. Distances of complex fuzzy sets and continuity of complex fuzzy operations. J. Intell. Fuzzy Syst. 2018;35(2):2247–2255. [Google Scholar]
- 22.Ma J., Zhang G., Lu J. A method for multiple periodic factor prediction problems using complex fuzzy sets. IEEE Trans. Fuzzy Syst. 2011;20(1):32–45. [Google Scholar]
- 23.Alkouri A.U.M., Salleh A.R. Linguistic variables, hedges, and several distances on complex fuzzy sets. J. Intell. Fuzzy Syst. 2014;26(5):2527–2535. [Google Scholar]
- 24.Liu P., Ali Z., Mahmood T. The distance measures and cross-entropy are based on complex fuzzy sets and their application in decision making. J. Intell. Fuzzy Syst. 2020;39(3):3351–3374. [Google Scholar]
- 25.Dai S., Bi L., Hu B. Distance measures between the interval-valued complex fuzzy sets. Mathematics. 2019;7(6):549–561. [Google Scholar]
- 26.Alkouri A.M.D.J.S., Salleh A.R. vol. 1482. American Institute of Physics; 2012. Complex intuitionistic fuzzy sets; pp. 464–470. (AIP Conference Proceedings). 1. [Google Scholar]
- 27.Garg H., Rani D. Some results on information measures for complex intuitionistic fuzzy sets. Int. J. Intell. Syst. 2019;34(10):2319–2363. [Google Scholar]
- 28.Garg H., Rani D. A robust correlation coefficient measure of complex intuitionistic fuzzy sets and their applications in decision-making. Appl. Intell. 2019;49(2):496–512. [Google Scholar]
- 29.Garg H., Rani D. Generalized geometric aggregation operators based on t-norm operations for complex intuitionistic fuzzy sets and their application to decision-making. Cognitive Computation. 2019;4(1):1–20. [Google Scholar]
- 30.Garg H., Rani D. Robust averaging–geometric aggregation operators for complex intuitionistic fuzzy sets and their applications to MCDM process. Arabian J. Sci. Eng. 2020;45(3):2017–2033. [Google Scholar]
- 31.Garg H., Rani D. Some generalized complex intuitionistic fuzzy aggregation operators and their application to multicriteria decision-making process. Arabian J. Sci. Eng. 2019;44(3):2679–2698. [Google Scholar]
- 32.Rani D., Garg H. Complex intuitionistic fuzzy power aggregation operators and their applications in multicriteria decision‐making. Expet Syst. 2018;35(6):e12325–e12348. [Google Scholar]
- 33.Rani D., Garg H. Complex intuitionistic fuzzy preference relations and their applications in individual and group decision‐making problems. Int. J. Intell. Syst. 2021;36(4):1800–1830. [Google Scholar]
- 34.Ali Z., Mahmood T., Aslam M., Chinram R. Another view of complex intuitionistic fuzzy soft sets based on prioritized aggregation operators and their applications to multiattribute decision making. Mathematics. 2021;9(16):1922–1949. [Google Scholar]
- 35.Xia M., Xu Z., Zhu B. Some issues on intuitionistic fuzzy aggregation operators based on Archimedean t-conorm and t-norm. Knowl. Base Syst. 2012;31:78–88. [Google Scholar]
- 36.Luo X., Xu Z., Gou X. Exponential operational laws and new aggregation operators of intuitionistic Fuzzy information based on Archimedean T-conorm and T-norm. International Journal of Machine Learning and Cybernetics. 2018;9(8):1261–1269. [Google Scholar]
- 37.Garg H., Rani D. New generalised Bonferroni mean aggregation operators of complex intuitionistic fuzzy information based on Archimedean t-norm and t-conorm. J. Exp. Theor. Artif. Intell. 2020;32(1):81–109. [Google Scholar]
- 38.Yu D. Group decision making under interval‐valued multiplicative intuitionistic fuzzy environment based on Archimedean t‐conorm and t‐norm. Int. J. Intell. Syst. 2015;30(5):590–616. [Google Scholar]
- 39.Ma Z.M., Yang W. Symmetric intuitionistic fuzzy weighted mean operators based on weighted Archimedean t-norms and t-conorms for multi-criteria decision making. Informatica. 2020;31(1):89–112. [Google Scholar]
- 40.Liu J., Lin S., Chen H., Zhou L. The continuous quasi-OWA operator and its application to group decision making. Group Decis. Negot. 2013;22(4):715–738. [Google Scholar]
- 41.Liu P., Chen S.M. Group decision making based on Heronian aggregation operators of intuitionistic fuzzy numbers. IEEE Trans. Cybern. 2016;47(9):2514–2530. doi: 10.1109/TCYB.2016.2634599. [DOI] [PubMed] [Google Scholar]
- 42.Seikh M.R., Mandal U. Q-rung orthopair fuzzy Frank aggregation operators and its application in multiple attribute decision-making with unknown attribute weights. Granular Computing. 2022:1–22. [Google Scholar]
- 43.Seikh M.R., Mandal U. Some picture fuzzy aggregation operators based on Frank t-norm and t-conorm: application to MADM process. Informatica. 2021;45(3) [Google Scholar]
- 44.Ozer O. Hamacher prioritized aggregation operators based on complex picture fuzzy sets and their applications in decision-making problems. Journal of Innovative Research in Mathematical and Computational Sciences. 2022;1(1):33–54. [Google Scholar]
- 45.Liaqat M., Yin S., Akmram M., Ijaz S. Aczel-alsina aggregation operators based on interval-valued complex single-valued neutrosophic information and their application in decision-making problems. Journal of Innovative Research in Mathematical and Computational Sciences. 2022;1(2):40–66. [Google Scholar]
- 46.Jaleel A. WASPAS technique utilized for agricultural robotics system based on Dombi aggregation operators under bipolar complex fuzzy soft information. Journal of Innovative Research in Mathematical and Computational Sciences. 2022;1(2):67–95. [Google Scholar]
- 47.Seikh M.R., Mandal U. Multiple attribute decision-making based on 3, 4-quasirung fuzzy sets. Granular Computing. 2022:1–14. [Google Scholar]
- 48.Seikh M.R., Mandal U. Multiple attribute group decision making based on quasirung orthopair fuzzy sets: application to electric vehicle charging station site selection problem. Eng. Appl. Artif. Intell. 2022;115 [Google Scholar]
- 49.Ali Z., Mahmood T., Ullah K., Khan Q. Einstein geometric aggregation operators using a novel complex interval-valued pythagorean fuzzy setting with application in green supplier chain management. Reports in Mechanical Engineering. 2021;2(1):105–134. [Google Scholar]
- 50.Ali Z., Mahmood T. Maclaurin symmetric mean operators and their applications in the environment of complex q-rung orthopair fuzzy sets. Comput. Appl. Math. 2020;39:1–27. [Google Scholar]
- 51.Rong Y., Liu Y., Pei Z. Complex q‐rung orthopair fuzzy 2‐tuple linguistic Maclaurin symmetric mean operators and its application to emergency program selection. Int. J. Intell. Syst. 2020;35(11):1749–1790. [Google Scholar]
- 52.Ali Z., Mahmood T., Yang M.S. TOPSIS method based on complex spherical fuzzy sets with Bonferroni mean operators. Mathematics. 2020;8(10):1739–1772. [Google Scholar]
- 53.Ali Z., Mahmood T., Yang M.S. Complex T-spherical fuzzy aggregation operators with application to multi-attribute decision making. Symmetry. 2020;12(8):1311–1342. [Google Scholar]
- 54.Mahmood T., Ullah K., Khan Q., Jan N. An approach toward decision-making and medical diagnosis problems using the concept of spherical fuzzy sets. Neural Comput. Appl. 2019;31(11):7041–7053. [Google Scholar]
- 55.Wu M.Q., Chen T.Y., Fan J.P. Divergence measure of T-spherical fuzzy sets and its applications in pattern recognition. IEEE Access. 2019;8:10208–10221. [Google Scholar]
- 56.Wu M.Q., Chen T.Y., Fan J.P. Similarity measures of T-spherical fuzzy sets based on the cosine function and their applications in pattern recognition. IEEE Access. 2020;8:98181–98192. [Google Scholar]
- 57.Riaz M., Hashmi M.R. Linear Diophantine fuzzy set and its applications towards multi-attribute decision-making problems. J. Intell. Fuzzy Syst. 2019;37(4):5417–5439. [Google Scholar]
- 58.Riaz M., Hashmi M.R., Kalsoom H., Pamucar D., Chu Y.M. Linear Diophantine fuzzy soft rough sets for the selection of sustainable material handling equipment. Symmetry. 2020;12(8):1215–1237. [Google Scholar]
- 59.Kamacı H. Linear Diophantine fuzzy algebraic structures. J. Ambient Intell. Hum. Comput. 2021;2(4):1–21. [Google Scholar]
- 60.Almagrabi A.O., Abdullah S., Shams M., Al-Otaibi Y.D., Ashraf S. A new approach to q-linear Diophantine fuzzy emergency decision support system for COVID19. J. Ambient Intell. Hum. Comput. 2021;2(3):1–27. doi: 10.1007/s12652-021-03130-y. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 61.Ayub S., Shabir M., Riaz M., Aslam M., Chinram R. Linear diophantine fuzzy relations and their algebraic properties with decision making. Symmetry. 2021;13(6):945–981. [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
The authors agree that the data used in this manuscript is available to everyone and anyone can use this data by just citing this article.