Abstract
The idiographic technical profiles of child sexual exploitation material (CSEM) offenders provide insight into their behaviours and context for their interactions with technology, but minimal quantitative work has been done to evaluate their sociability, technical ability and technophilia compared to non-offenders. This work used an online survey to compare an offender group consisting of English-speaking adults previously convicted of CSEM offenses (N = 78) with a reference population of non-offenders (N = 254). The survey assessed sociability, technical ability and technophilia through self-rating and information on occupation, level of education and device ownership. The study found that CSEM offenders had slightly lower sociability than non-offenders, though not at a level of clinical interest. Additionally, CSEM offenders had no statistically significant difference in technical ability and lower overall technophilia when compared to non-offenders. This study fails to support popular perceptions of CSEM offenders being technically savvy loners who are early adopters of new technologies.
Keywords: Child pornography, child sexual exploitation material, sociability, technical profiles, technophilia
Introduction
When asked to picture a child sexual exploitation material (CSEM) offender, the lay individual is potentially likely to picture a male loner in their 30s or 40s, surrounded by digital equipment, with strong technical skills. While the demographics of CSEM offenders have been extensively studied (e.g. Babchishin et al., 2011, 2015; Houtepen et al., 2014), and profiles based on content and history (Elbert et al., 2022) have been developed to address these stereotypes, the social and technical traits and abilities of CSEM offenders have not been comprehensively researched in relation to a non-offending population.
Evaluating the psychosocial and technical skills and behaviours of CSEM offenders is important, as misplaced stereotypes can drive investigative actions (e.g. planning investigations based on ‘early adopter’ assumptions about offenders: Bryant, 2016) deterrence efforts (e.g. increasing the technical difficulty of obtaining CSEM), probation decisions, and treatment efforts (e.g. treating sociability to enhance community engagement). Clinically, assessing the technical skills and sociability of CSEM offenders has been proposed as necessary in evaluating collections and collecting behaviours (Fortin & Proulx, 2019). Evaluation of these characteristics can be broken into three factors: sociability (the desire and tendency to seek out and engage in social relationships), technical ability (the skills needed to navigate the digital world), and ‘technophilia’ (the adoption and ownership of new technologies). All three factors have been previously identified as important characteristics of the digital profiles of cyber offenders, though they have not been empirically evaluated to-date (Steel, 2014).
For sociability, media reporting has at times overemphasised the ‘loner’ image. For example, one individual, arrested for possession of 7,000 images of CSEM, was described as ‘The defendant is a very sad and lonely man who has few friends. His motivation was not to see and use the images of the children, but to have some people to talk to so he posed as having an appetite for this sort of activity’ (Collie, 2008). Another offender, David Bennett, arrested for possession and prior production of CSEM, was described as ‘… a sad and lonely individual. This is a man who has never had any intimate relationship in his life. He has comparatively little contact with the outside world’ (Lloyd, 2015).
Other work has shown higher socioaffective needs within CSEM offenders (Magaletta et al., 2014), and social anxiety has been correlated with general problematic online pornography consumption (Wéry et al., 2020). Additionally, increased social engagement has been presented as a positive factor for desistance (Merdian et al., 2018). Previous findings, however, have shown that ‘online offenders do not either actively (or want to) avoid being with or talking to others’ (Armstrong & Mellor, 2016, p. 55). Although some treatment programmes have focused on increasing sociability for CSEM offenders (Dervley et al., 2017), there has been insufficient empirical work to date directly assessing the baseline sociability of CSEM offenders compared to the general public and confirming the widespread presence of deficits.
Technophilia has been used in a psychological context as a general favourable disposition toward technology and as a contrast to technophobia (Richards, 1993), and can be summarised as an individual’s innate desire to possess and interact with technology.1 Investigatively, high-technophilia individuals are likely to be early adopters of new technology and possess more and newer devices, potentially posing challenges related to the volume of content that needs to be reviewed, as well as forensic challenges related to encryption (Steel, 2014). The use of multiple devices has also had legal ramifications – while the courts have not fully resolved the issue, separate counts of a crime can be charged if different images are found on multiple devices (United States v. Kuhnel, 2020), encouraging investigators to examine all media seized. Individuals with high technophilia are more likely to have more devices (and applications on those devices). If each individual device or application has its own set of affordances, or potentials for action (Quayle, 2020), then more technophilia would be potentially associated with higher clinical risk of recidivism and escalation of actions. Behavioural modifications that address the acquisition and usage of technology may be potential treatment targets for these individuals.
Prior research studies, while not specifically targeting technophilia, have found preliminary results that are not consistent with increased ownership of new and sophisticated devices by CSEM offenders. The 2005 National Juvenile Online Victimization (N-JOV) study found, for example, that most individuals arrested for child pornography did not own sophisticated equipment, with 65% owning a basic computer system, 22% the system of a power user (an individual with more advanced computer skills and expertise), and 7% a sophisticated, expert computer system (Wolak et al., 2005). To date, there has been no research identified that directly measured the device ownership, application usage and self-identified technophilia in CSEM consumers.
Technical ability is separate but is related to technophilia. An individual can be technically proficient, but be prevented from owning the latest technologies due to socioeconomic factors. Additionally, an individual with high socioeconomic status may own numerous devices but not fully utilise them. Prior research has been mixed with regard to the technical skill of CSEM offenders. Wolak et al. (2005) found that more than half (54%) of CSEM offenders were scored by law enforcement as being very or extremely knowledgeable technology-wise. Similarly, Carr (2004) found that the self-reported computer literacy of CSEM offenders was mostly above average, with 30% of individuals rating themselves at a medium skill level and 32% at a high skill level, though self-reporting with a lack of specific rating scale limits cross-comparison. There has been no work, however, comparing the reports of technical ability within the CSEM offender community to those within a non-offending group.
This research evaluates the technical ability, technophilia and sociability of individuals in the United States previously convicted of CSEM offenses (N = 78) in comparison to a baseline reference group of non-offenders (N = 254). Both groups were asked a series of questions in an online questionnaire related to their Internet usage and asked to self-rate on each of the areas above. They were evaluated using an existing, validated instrument for sociability and single point evaluations of technophilia and technical ability. These were compared to demographic data related to their career field (technical v. non-technical) as well as their actual self-reported usage and ownership of various technologies. This research represents the first work to take an integrative look at sociability, technical ability and technophilia within the CSEM offender population.
Methodology
This research was part of a larger project looking at the technological behaviours and cognitions of CSEM offenders. The research consisted of online survey questions assessing the profiles of two different populations: one of the general public (used primarily as a baseline for reference purposes) and one of individuals previously convicted of child pornography possession offenses.
Data collection and population
This research was conducted using data obtained through two anonymous online surveys hosted through Qualtrics. Individuals on the sex offender registries of two States (‘offender sample’) who were previously convicted of child pornography possession offenses were sent a mail-based solicitation requesting them to complete an anonymous online survey for a chance to obtain one of two $150 Amazon gift certificates. Individuals completing the questions were provided a link to an optional, separate survey that was not connected to their responses and collected email addresses. An independent third party drew two of the email addresses from the respondents who chose to provide them, and they were sent the gift certificates electronically. The same questions were asked of non-offenders (‘reference sample’) who were identified by Qualtrics from their panel service (Online Panels: Get Responses for Surveys & Research|Qualtrics, n.d.). The populations for both surveys were English-speaking adults within the United States, and informed consent was solicited and required before participation. Both surveys contained demographic questions, as well as questions related to sociability, technical ability and technophilia, as noted below. The reference sample had 524 overall respondents. Of these, 254 individuals were matched to the offender sample based on gender identity (all of the offenders identified as male or gender variant/non-conforming), which included male (n = 253) and gender variant/non-conforming (n = 1) individuals.
Of the solicitations sent to the offender sample (n = 2,508), 141 individuals responded and began the surveys. Three respondents declined to accept the informed consent, and 40 respondents failed to complete the survey (partial responses were not maintained to allow individuals to opt out at any point). An additional 20 respondents failed the integrity checks, resulting in a total of 78 responses.
Sociability
To measure sociability, individuals were requested to rate themselves on a five-point Likert scale using the five sociability statements from the Shyness and Sociability Scales (which had a previously reported α = .7) (Cheek & Buss, 1981):
I like to be with people.
I welcome the opportunity to mix socially with people.
I prefer working with others rather than alone.
I find people more stimulating than anything else.
I'd be unhappy if I were prevented from making many social contacts.
For comparison purposes, individuals were asked about potential proxy behaviours that could be measured forensically. They were asked the volume of their personal daily email and text messaging communications and asked to select one of five ranked ranges of 0–10, 11–20, 21–30, 31–40, or over 40. For the average time they took responding to emails, they were asked to select if they generally responded in a matter of minutes, hours, within a day, or more than a day, and they were asked to provide a count of the number of social media accounts they held, based on the most commonly used mobile applications (Statista, 2019).
Technical ability
To baseline their technical ability, individuals were asked how others would rate their technical expertise in one of five ranked categories:
Novice – little to no technical ability.
Casual user – ability to use most computer services and technologies without assistance.
Power user – you frequently use most computing technologies; Others consult you for computing advice.
IT/computing professional – your career is focused on configuring, managing, or maintaining networks, hardware, or software.
Computer scientist – you develop new computing technologies or conduct peer-reviewed research into computing (Steel, 2014).
As potential corollaries of technical ability, individuals were asked to indicate their professions as well as their degree field. Professions within STEM (Science, Technology, Engineering, Math) fields as well as degrees within the STEM field were rated as a Boolean variable (technical or non-technical) based on the United States Department of Homeland Security STEM list (Department of Homeland Security, 2016).
Technophilia
Technophilia was evaluated through a self-assessment by participants who were asked to rate their adoption of new technology on a five-point Likert scale from Very Low to Very High as follows:
Very low – you own very few computing devices. You upgrade only when the existing device breaks or is no longer supported.
Low – you own computing devices in several of the major technology areas, but are frequently the last of your friends to start using a new technology.
Average – you own computing devices in most of the major technology areas, but hold off on purchases until technologies are mature and in widespread usage. You only upgrade devices when major new functionality is available.
High – you keep up with technology and own computing devices in all of the major technology areas. Some of the devices may be last year’s model, but you stay within one generation of the current release.
Very high – you are an early adopter and own computing devices in all of the major areas (smartphones, ereaders, tablets, laptops, home automation).
Additionally, the total number of devices owned based on a reference list of common technologies was obtained and compared between the groups. Because individuals with higher income could potentially afford more (and newer) computing devices, the correlation between the number of computing devices and income was calculated to identify any potential confound based on socioeconomic factors.
Analysis
Comparisons between populations were performed using a Welch’s one-tailed t test (for parametric data) or a two-tailed Mann-Whitney-Wilcoxon test (for non-parametric data). Correlations were performed using the Spearman method. All results were collected and analysed using R, with a p value of .01 used for statistical significance tests (where appropriate).
Ethics
Ethical approval was received from the Research Ethics Committee at the University of Edinburgh on 20 May 2020. Additionally, Institutional Review Board approval was received from George Mason University on 13 May 2020.
Results
The survey responses received on the public survey were diverse as to sex, sexual preference, age, relationship status, gender identity, race, employment and education. The responses received on the offender survey were consistent with the previously identified demographics of CSEM offenders (Faust et al., 2015; Reijnen et al., 2009). The full demographics are provided in the Appendix, and additional demographic analyses can be found in a related work (Steel, 2021). The Cheek and Buss (1981) scale was found to have a good Cronbach’s alpha consistency within both the offender (α = .82) and the reference (α = .89) samples.
Sociability
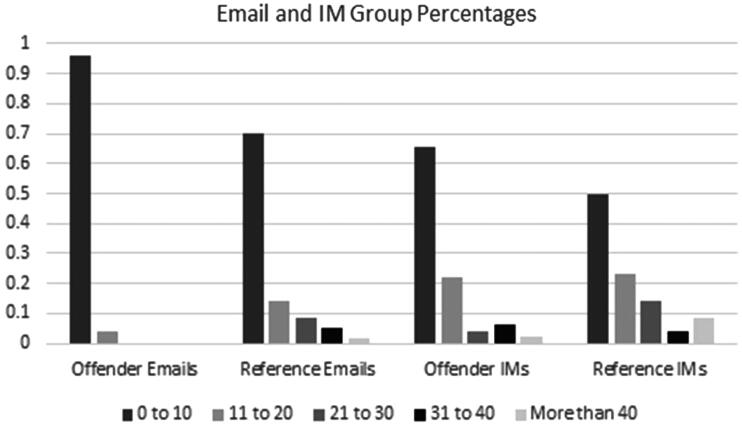
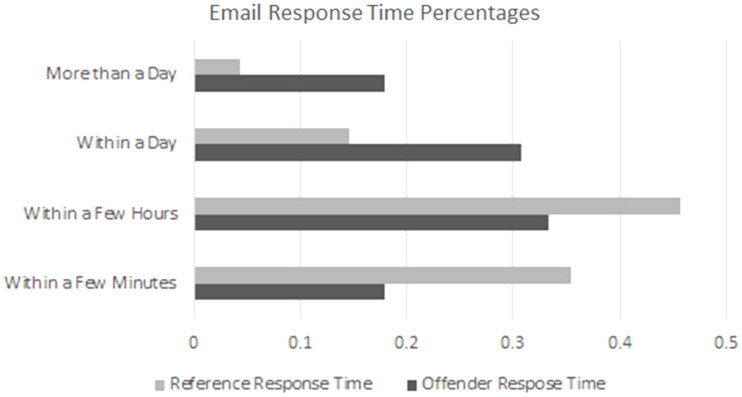
The sociability of the offender sample by the Cheek and Buss scale (1981) ranged from 0 to 20 points (M = 10.91, SD = 4.41), with higher scores indicating higher sociability, and was significantly less, t(142) = 2.54, p < .01, than the reference sample (M = 12.41, SD = 4.98). The number of social media accounts used by the offender sample (M = 3.71, SD = 3.15) was not significantly different from the reference sample (M = 4.54, SD = 3.77). Offenders sent significantly fewer personal emails per day (W = 12,549, p < .01) and Instant Messages (IMs) per day (W = 11,680, p < .01) than the reference group (Figure 1). Additionally, offenders’ response times on emails skewed toward longer delays than non-offenders (W = 6467, p < .01) (Figure 2), with substantially higher proportions of offenders taking more than a day (.18, n = 14) than non-offenders (.04, n = 11) and within a day (.31, n = 24) than non-offenders (.15, n = 37).
Figure 1.
Personal emails and IMs sent daily.
Figure 2.
Email response times.
Technical ability
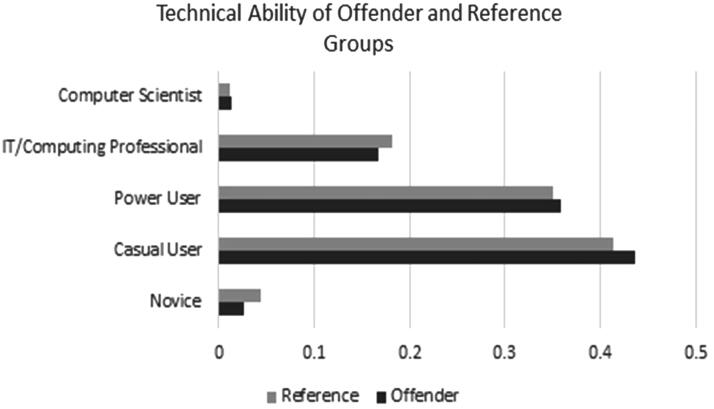
The overall technical ability of offenders did not differ significantly from that of the general public. The highest proportion of respondents for both the offender (.44, n = 34) and non-offender (.41, n = 105) samples were casual users, followed by power users at (.36, n = 28) and (.35, n = 89), respectively. Very few users of either the offender (.01, n = 1) or non-offender (.01, n = 3) groups had the highest level of technical ability (Figure 3). Slightly lower proportions of the offender group had STEM degrees (.17, n = 13) compared to the reference group (.18, n = 46), and slightly fewer worked in STEM occupations (.05, n = 5) compared to the reference group (.10, n = 25). This trend held even when normalised based on only those individuals with degrees and only those individuals currently employed (Table 1). Technical ability was correlated with having a technical occupation in the offender group (ρ = .48, p < .01) and the reference group (ρ = .48, p < .01), and a technical degree was correlated with technical ability in the public (ρ = .38, p < .01) but not the offender group (ρ = .31, p > .01).
Figure 3.
Breakdown of technical abilities of offender and reference groups.
Table 1.
STEM degrees and occupations.
| Offender |
Offender(normalised) |
Reference |
Reference(normalised) |
|||||
|---|---|---|---|---|---|---|---|---|
| proportion | n | proportion | n | proportion | n | proportion | n | |
| Tech degree | .17 | 13 | .28 | 13 | .18 | 46 | .35 | 46 |
| Tech occupation | .06 | 5 | .11 | 5 | .10 | 25 | .16 | 25 |
Note: Normalised results include only those with a degree/currently employed.
Technophilia
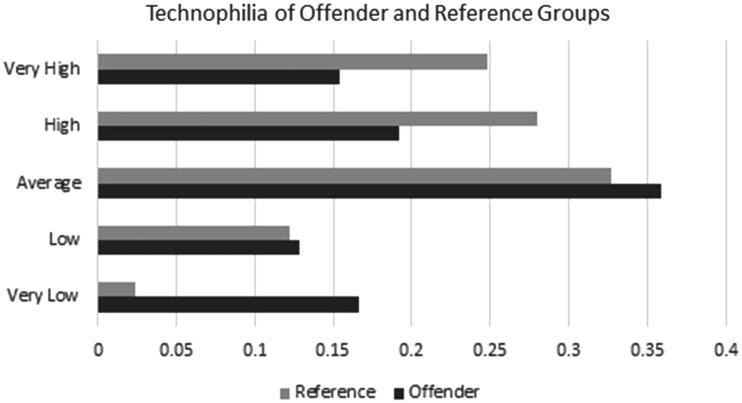
The technophilia of offenders was skewed significantly lower than that of non-offenders (W = 12,358, p < .01), with a higher proportion of offenders (.29, n = 23) reporting that they had below average technophilia compared to the reference group (.15, n = 37) (Figure 4). Offenders owned significantly, t(190) = –3.38, p < .01, fewer devices (M = 2.95, SD = 2.45) than the reference group (M = 4.17, SD = 3.65). Offender device ownership was not significantly correlated with income rank (ρ = .13, p > .01), however public device ownership was correlated with income rank (ρ = .35, p < .01).
Figure 4.
Overall self-rated technophilia.
Discussion
Individuals convicted of CSEM offenses had slightly lower sociability than the reference group, consistent with findings of Armstrong and Mellor (2016). While the difference in scores was statistically significant (10.9 v 12.4), the effect size was small (d = .32), and the differential is likely not of clinical significance. Offenders also sent fewer personal emails and IMs and took longer to respond to emails, than the reference group. This is consistent with reduced sociability scores, but the variance in scores was very high between the groups. Additionally, there have been subgroups of CSEM offenders that have been identified as highly social – seeking out forums and other interactive spaces (Merdian, 2012). This was borne out in this research as well – a substantial subset (.21, n = 16) of the offenders scored in the highest quartile on the sociability scale. As such, treatment programmes that focus on increasing general sociability (as opposed to targeting attachment style or specific relationships) would be better served by focusing only on individuals with a functional deficit due to low sociability, following an assessment. For investigative purposes, digital forensics findings showing higher-than-average communications history can be explored in an interview to evaluate the potential for trading or distribution and to identify other potential subjects.
Technical ability was not significantly different between the offender group and the reference group and did not support the belief that CSEM offenders are more adept at technology than are non-offenders. Since this was a measurement of general technical knowledge, it does not preclude CSEM offenders being more adept at domain-specific knowledge related to their area of criminality (Steel, 2014). Because of this, CSEM offenders may still develop highly specialised technical skills over time, related to conducting more effective searches or more effectively utilising niche technologies that facilitate further offending (Elliott & Beech, 2009; Quayle & Taylor, 2003). Additionally, moderate correlations existed between being employed in a STEM field for offenders and technical ability, showing that a priori information on employment may be an indicator for encountering an individual with greater technical sophistication. This may also impact the type of countermeasures employed, and the methods of accessing CSEM material, which are necessary for effective investigative planning. Because individuals in a STEM field are likely to need ongoing access to technology, tailored digital behavioural interventions need to balance potential access to CSEM with employment-related knowledge acquisition.
Separate from technical ability is technophilia. The offender group exhibited substantially lower technophilia than did the reference group, and the effect was not significantly correlated with income. The implications for this are important for future research. First, this supports the concept that CSEM offenders do not necessarily gravitate towards new technology, and continue their pattern of usage of older technology, despite the presence of objectively better options (Steel et al., 2020), which is important for search warrant planning. Second, if CSEM offenders are, on the whole, not early adopters, deterrence efforts focused on extant technologies are likely to continue to be effective with a smaller transference effect (e.g. driving individuals from one method of acquisition to another as opposed to stopping the activity). This is consistent with the drops in the offending usage of specific technologies due to interventions without a commensurate increase in other technologies (Steel, 2015), though exact measurement is difficult, as reporting improvements have shown conflicting results (Bursztein et al., 2019). Third, treatment targeting technology-specific behavioural interventions is also more viable, for the same reason as deterrence (i.e. less of a transference effect) if technophilia is lower.
Limitations
The pool of individuals arrested and convicted of CSEM offenses may not represent the most technically sophisticated offenders. It is possible that individuals with higher technical sophistication are less likely to be caught. While offenders sent fewer emails and IMs and took more time responding to emails, there are numerous potential confounding factors, ranging from employment status and field to preferences in methods of communicating, that may be present. Additionally, further research is needed to determine if the lower sociability is a post-prison effect related to sex offender registration (Tewksbury, 2005) or stigmatisation (Jahnke et al., 2015) or a stable, pre-existing trait. Additionally, this research examined the characteristics of individuals previously convicted of CSEM possession offenses – individuals who commit production and/or distribution offenses may have different characteristics.
The ratings rely on self-reporting of behaviour and are potentially subject to overestimates of skill, particularly related to technical ability. Additionally, the populations for the two surveys were all English-speaking individuals at least 18 years of age living in the United States, and caution should be used in any generalisation beyond that population.
This research was conducted during the 2020 Covid-19 pandemic. As such, there may have been impacts to the income levels of participants (Coibion et al., 2020), and there may also have been an impact on sociability based on social distancing restrictions (Folk et al., 2020). There is insufficient information available to determine if both groups were equally impacted, or if a disproportionate impact on one group may have influenced the results.
Conclusions
This research analysed the overall sociability, technical ability and technophilia of online CSEM offenders as compared to a non-offending population. For investigative planning purposes, the results of the analysis provide key insights. With regard to sociability, the average sociability of the offenders was close to that of the non-offending group; however, their use of messaging to communicate was lower than that of non-offenders. While this may be impacted by disrupted social networks post-conviction, it indicates that less extensive communication histories found forensically may not be abnormal. For a small but substantial subset of offenders with high sociability, however, there may be an increased likelihood that they are part of a network of offenders, though further research is needed to evaluate this. Additionally – of interest in planning search warrants – offenders did not exhibit an overall high degree of technical ability and exhibited lower technophilia and device ownership. This puts less onus on digital forensics teams to plan for high volumes of devices or for encounters with cutting-edge technology. Since technical ability was correlated with being in a technical occupation, however, this biographical information may be an indicator that more advanced technical planning is necessary.
For treatment, the general lack of clinical differences in sociability brings that into question as a general treatment target. At a minimum, testing for low sociability as well as any functional impact of low sociability would be necessary before including this in a treatment plan. For higher sociability individuals who use CSEM forums and networks as an outlet, there may additionally be a need to replace those social structures with more healthy alternatives. Additionally, lower technophilia and average technical abilities may indicate less desire to actively acquire and use new technologies, but more targeted domain-specific desires and risks. Avoidance-based approaches may be better suited to highly specific behavioural patterns (e.g. use of a particular application or engagement in a particular behaviour such as visiting non-mainstream adult websites), as opposed to more general technology restrictions.
Ethical standards
Declaration of conflicts of interest
Chad M.S. Steel has declared no conflicts of interest.
Emily Newman has declared no conflicts of interest.
Suzanne O’Rourke has declared no conflicts of interest.
Ethel Quayle has declared no conflicts of interest.
Ethical approval
All procedures performed in studies involving human participants were in accordance with the ethical standards of the institutional and/or national research boards of the University of Edinburgh and George Mason University and with the 1964 Helsinki declaration and its later amendments or comparable ethical standards.
Informed consent
Informed consent was obtained from all individual participants included in the study.
.
Appendix.
Sample demographics.
| Category | Offender (N = 78) |
Public – Gender matched (N = 254) |
||
|---|---|---|---|---|
| proportion | n | proportion | n | |
| Sexual orientation | ||||
| Bisexual | 0.14 | 11 | 0.03 | 7 |
| Heterosexual (straight) | 0.72 | 56 | 0.91 | 231 |
| Homosexual (gay) | 0.13 | 10 | 0.05 | 13 |
| Other | 0.01 | 1 | 0.01 | 3 |
| Prefer not to say | 0 | 0 | 0 | 0 |
| Age distribution | ||||
| 18–24 | 0.01 | 1 | 0.17 | 44 |
| 25–34 | 0.28 | 22 | 0.11 | 27 |
| 35–44 | 0.24 | 19 | 0.17 | 42 |
| 45–54 | 0.17 | 13 | 0.24 | 61 |
| 55–64 | 0.22 | 17 | 0.19 | 47 |
| 65 or older | 0.08 | 6 | 0.13 | 32 |
| Gender identity | ||||
| Female | 0 | 0 | 0 | 0 |
| Gender variant/non-conforming | 0.04 | 3 | 0 | 1 |
| Male | 0.95 | 74 | 1 | 253 |
| Not listed | 0.01 | 1 | 0 | 0 |
| Prefer not to answer | 0 | 0 | 0 | 0 |
| Transgender male | 0 | 0 | 0 | 0 |
| Relationship status | ||||
| Divorced | 0.23 | 18 | 0.09 | 23 |
| In a domestic partnership or civil union | 0.03 | 2 | 0.03 | 7 |
| Married | 0.23 | 18 | 0.48 | 122 |
| Other | 0 | 0 | 0 1 | |
| Separated | 0.04 | 3 | 0 | 1 |
| Single, but cohabiting with a significant other | 0.04 | 3 | 0.05 | 12 |
| Single, never married | 0.41 | 32 | 0.32 | 82 |
| Widowed | 0.03 | 2 | 0.02 | 6 |
| Race (multiple selections permitted) | ||||
| American Indian or Alaska Native | 0.01 | 1 | 0.02 | 5 |
| Asian | 0 | 0 | 0.04 | 9 |
| Black or African American | 0.01 | 1 | 0.17 | 42 |
| Hispanic or Latino | 0.12 | 9 | 0.07 | 19 |
| Native Hawaiian or Pacific Islander | 0.01 | 1 | 0 | 1 |
| Other | 0.01 | 1 | 0.01 | 3 |
| White or Caucasian | 0.88 | 69 | 0.75 | 191 |
| Employment status | ||||
| Not working (disabled) | 0.13 | 10 | 0.05 | 12 |
| Not working (looking for work) | 0.15 | 12 | 0.09 | 24 |
| Not working (other) | 0.04 | 3 | 0.02 | 6 |
| Not working (retired) | 0.09 | 7 | 0.17 | 43 |
| Not working (temporary layoff from a job) | 0.03 | 2 | 0.05 | 13 |
| Working (paid employee) | 0.49 | 38 | 0.54 | 137 |
| Working (self-employed) | 0.08 | 6 | 0.07 | 19 |
| Education level | ||||
| Less than high school diploma | 0 | 0 | 0.01 | 3 |
| High school graduate (high school diploma or equivalent including GED) | 0.13 | 10 | 0.24 | 62 |
| Some college but no degree | 0.29 | 23 | 0.19 | 49 |
| Associate degree in college (2-year) | 0.13 | 10 | 0.1 | 25 |
| Bachelor’s degree in college (4-year) | 0.33 | 26 | 0.26 | 67 |
| Master’s degree | 0.09 | 7 | 0.13 | 32 |
| Professional degree (JD, MD) | 0 | 0 | 0.03 | 7 |
| Doctoral degree | 0.01 | 1 | 0.04 | 9 |
| Degree field | ||||
| Business | 0.13 | 10 | 0.17 | 42 |
| Computer science | 0.06 | 5 | 0.07 | 19 |
| Education | 0.04 | 3 | 0.04 | 11 |
| Engineering | 0.08 | 6 | 0.06 | 16 |
| Government/political science | 0.03 | 2 | 0.02 | 5 |
| Liberal arts | 0.12 | 9 | 0.02 | 5 |
| Nursing | 0 | 0 | 0.01 | 3 |
| Other | 0.06 | 5 | 0.08 | 20 |
| Physical science | 0.03 | 2 | 0.02 | 5 |
| Psychology | 0 | 0 | 0.02 | 6 |
| Social sciences | 0.06 | 5 | 0.03 | 8 |
| Employment position | ||||
| Computer, engineering, and science | 0.06 | 5 | 0.1 | 25 |
| Construction and extraction | 0.03 | 2 | 0.04 | 11 |
| Education, legal, community service, arts, and media | 0 | 0 | 0.05 | 12 |
| Farming, fishing, and forestry | 0.01 | 1 | 0 | 0 |
| Healthcare practitioners and technical | 0.01 | 1 | 0.04 | 9 |
| Installation, maintenance, and repair | 0.06 | 5 | 0.01 | 2 |
| Management, business, and financial | 0.05 | 4 | 0.15 | 37 |
| Military | 0 | 0 | 0 | 1 |
| Office and administrative support | 0.05 | 4 | 0.03 | 7 |
| Production | 0.09 | 7 | 0.04 | 11 |
| Retired | 0.15 | 12 | 0.2 | 52 |
| Sales and related | 0.08 | 6 | 0.04 | 10 |
| Service | 0.09 | 7 | 0.11 | 27 |
| Transportation and material moving | 0.04 | 3 | 0.04 | 11 |
| Unemployed | 0.26 | 20 | 0.15 | 38 |
| Income | ||||
| $0–9,999 | 0.09 | 7 | 0.09 | 22 |
| $10,000–20,000 | 0.19 | 15 | 0.07 | 19 |
| $20,001–29,999 | 0.1 | 8 | 0.1 | 25 |
| $30,000–40,000 | 0.24 | 19 | 0.1 | 26 |
| $40,001–50,990 | 0.09 | 7 | 0.14 | 35 |
| $50,991–67,000 | 0.08 | 6 | 0.07 | 19 |
| $67,001–79,000 | 0.1 | 8 | 0.12 | 31 |
| $79,001–100,000 | 0.05 | 4 | 0.12 | 31 |
| $100,001–190,000 | 0.05 | 4 | 0.12 | 31 |
| Greater than $190,000 | 0 | 0 | 0.06 | 15 |
Footnotes
Technophilia in relation to CSEM has, alternatively, been described as a separate type of paraphilia by McLaughlin (McLaughlin, 1998); however, this definition is not widely adopted and is not used in this research.
References
- Armstrong, J., & Mellor, D. (2016). Internet child pornography offenders: An examination of attachment and intimacy deficits. Legal and Criminological Psychology, 21(1), 41–55. 10.1111/lcrp.12028 [DOI] [Google Scholar]
- Babchishin, K. M., Hanson, R. K., & Hermann, C. A. (2011). The characteristics of online sex offenders: A meta-analysis. Sexual Abuse, 23(1), 92–123. 10.1177/1079063210370708 [DOI] [PubMed] [Google Scholar]
- Babchishin, K. M., Hanson, R. K., & VanZuylen, H. (2015). Online child pornography offenders are different: A meta-analysis of the characteristics of online and offline sex offenders against children. Archives of Sexual Behavior, 44(1), 45–66. [DOI] [PubMed] [Google Scholar]
- Bryant, R. (2016). Policing digital crime. Routledge. [Google Scholar]
- Bursztein, E., Clarke, E., DeLaune, M., Elifff, D. M., Hsu, N., Olson, L., Shehan, J., Thakur, M., Thomas, K., & Bright, T. (2019). Rethinking the detection of child sexual abuse imagery on the internet. The World Wide Web Conference, 2601–2607. 10.1145/3308558.3313482 [DOI] [Google Scholar]
- Carr, A. (2004). Internet traders of child pornography and other censorship offenders in New Zealand. Department of Internal Affairs. [Google Scholar]
- Cheek, J. M., & Buss, A. H. (1981). Shyness and sociability. Journal of Personality and Social Psychology, 41(2), 330–339. 10.1037/0022-3514.41.2.330 [DOI] [Google Scholar]
- Coibion, O., Gorodnichenko, Y., & Weber, M. (2020). Labor markets during the COVID-19 crisis: A Preliminary View (No. 27017). National Bureau of Economic Research, 10.3386/w27017 [DOI]
- Collie, J. (2008, February 18). Loner “had 7,000 child porn images.” Oxford Mail. https://www.oxfordmail.co.uk/news/2053486.loner-had-7-000-child-porn-images/
- Department of Homeland Security (2016). October 5). STEM Designated Degree Program List. https://www.ice.gov/sites/default/files/documents/Document/2016/stem-list.pdf
- Dervley, R., Perkins, D., Whitehead, H., Bailey, A., Gillespie, S., & Squire, T. (2017). Themes in participant feedback on a risk reduction programme for child sexual exploitation material offenders. Journal of Sexual Aggression, 23(1), 46–61. 10.1080/13552600.2016.1269958 [DOI] [Google Scholar]
- Elbert, M. J., Drury, A. J., & DeLisi, M. (2022). Child pornography possession/receipt offenders: Developing a forensic profile. Psychology, and Law, 29(1), 93–106. 10.1080/13218719.2021.1904447 [DOI] [PMC free article] [PubMed] [Google Scholar]
- Elliott, I. A., & Beech, A. R. (2009). Understanding online child pornography use: Applying sexual offense theory to Internet offenders. Aggression and Violent Behavior, 14(3), 180–193. 10.1016/j.avb.2009.03.002 [DOI] [Google Scholar]
- Faust, E., Bickart, W., Renaud, C., & Camp, S. (2015). Child pornography possessors and child contact sex offenders: A multilevel comparison of demographic characteristics and rates of recidivism. Sexual Abuse, 27(5), 460–478. 10.1177/1079063214521469 [DOI] [PubMed] [Google Scholar]
- Folk, D., Okabe-Miyamoto, K., Dunn, E., & Lyubomirsky, S. (2020). Did social connection decline during the first wave of COVID-19?: The role of extraversion. Collabra, 6(1), 365. [DOI] [Google Scholar]
- Fortin, F., & Proulx, J. (2019). Sexual interests of Child Sexual Exploitation Material (CSEM) consumers: Four patterns of severity over time. International Journal of Offender Therapy and Comparative Criminology, 63(1), 55–76. [DOI] [PubMed] [Google Scholar]
- Houtepen, J. A. B. M., Sijtsema, J. J., & Bogaerts, S. (2014). From child pornography offending to child sexual abuse: A review of child pornography offender characteristics and risks for cross-over. Aggression and Violent Behavior, 19(5), 466–473. 10.1016/j.avb.2014.07.011 [DOI] [Google Scholar]
- Jahnke, S., Schmidt, A. F., Geradt, M., & Hoyer, J. (2015). Stigma-related stress and its correlates among men with pedophilic sexual interests. Archives of Sexual Behavior, 44(8), 2173–2187. [DOI] [PubMed] [Google Scholar]
- Lloyd, M. (2015, May 7). “Loner” caught with massive child porn stash including babies as young as two months old is jailed. Daily Mirror, https://www.mirror.co.uk/news/uk-news/loner-caught-massive-child-porn-5655362
- Magaletta, P. R., Faust, E., Bickart, W., & McLearen, A. M. (2014). Exploring clinical and personality characteristics of adult male internet-only child pornography offenders. International Journal of Offender Therapy and Comparative Criminology, 58(2), 137–153. [DOI] [PubMed] [Google Scholar]
- McLaughlin, J. F. (1998). Technophilia: A modern day paraphilia. Knight Stick, 51, 47–51. [Google Scholar]
- Merdian, H. L. (2012). Offenders who use child sexual exploitation material: Development of an integrated model for their classification, assessment, and treatment [University of Waikato]. https://researchcommons.waikato.ac.nz/handle/10289/6566
- Merdian, H. L., Perkins, D. E., Dustagheer, E., & Glorney, E. (2018). Development of a case formulation model for individuals who have viewed, distributed, and/or shared child sexual exploitation material. International Journal of Offender Therapy and Comparative Criminology, 64(10–11):1055–1073. 0306624X17748067. [DOI] [PubMed] [Google Scholar]
- Online Panels: Get Responses for Surveys & Research |Qualtrics. (n.d.). Qualtrics. Retrieved February 8, 2020, from https://www.qualtrics.com/research-services/online-sample/
- Quayle, E. (2020). Prevention, disruption and deterrence of online child sexual exploitation and abuse. ERA Forum, 21(3), 429–447. 10.1007/s12027-020-00625-7 [DOI] [Google Scholar]
- Quayle, E., & Taylor, M. (2003). Model of problematic Internet use in people with a sexual interest in children. Cyberpsychology & Behavior, 6(1), 93–106. 10.1089/109493103321168009 [DOI] [PubMed] [Google Scholar]
- Reijnen, L., Bulten, E., & Nijman, H. (2009). Demographic and personality characteristics of internet child pornography downloaders in comparison to other offenders. Journal of Child Sexual Abuse, 18(6), 611–622. [DOI] [PubMed] [Google Scholar]
- Richards, B. (1993). Technophobia and technophilia. British Journal of Psychotherapy, 10(2), 188–195. 10.1111/j.1752-0118.1993.tb00646.x [DOI] [Google Scholar]
- Steel, C. M. S. (2014). Idiographic digital profiling: Behavioral analysis based on digital forensics. Journal of Digital Forensics, Security and Law, 9(1), 1. 10.15394/jdfsl.2014.1160 [DOI] [Google Scholar]
- Steel, C. M. S. (2015). Web-based child pornography: The global impact of deterrence efforts and its consumption on mobile platforms. Child Abuse & Neglect, 44, 150–158. [DOI] [PubMed] [Google Scholar]
- Steel, C. M. S. (2021). Digital behaviours and cognitions of individuals convicted of online child pornography offences [The University of Edinburgh]. 10.7488/ERA/1634 [DOI]
- Steel, C. M. S., Newman, E., O’Rourke, S., & Quayle, E. (2020). An integrative review of historical technology and countermeasure usage trends in online child sexual exploitation material offenders. Forensic Science International, 33, 300971. [Google Scholar]
- Tewksbury, R. (2005). Collateral consequences of sex offender registration. Journal of Contemporary Criminal Justice, 21(1), 67–81. 10.1177/1043986204271704 [DOI] [Google Scholar]
- Statista . (2019). Top U.S. mobile social apps by users. https://www.statista.com/statistics/248074/most-popular-us-social-networking-apps-ranked-by-audience/
- United States v. Kuhnel, Criminal 17-158 (JRM/BRT) (D. Minnesota ). (2020). https://scholar.google.com/scholar_case?case=703769031736894297
- Wéry, A., Canale, N., Bell, C., Duvivier, B., & Billieux, J. (2020). Problematic online sexual activities in men: The role of self‐esteem, loneliness, and social anxiety. Human Behavior and Emerging Technologies, 2(3), 217–226. 10.1002/hbe2.193 [DOI] [Google Scholar]
- Wolak, J., Finkelhor, D., Mitchell, K. J. (2005). Child-pornography possessors arrested in internet-related crimes: Findings from the national juvenile online victimisation study. https://scholars.unh.edu/ccrc/33/