Abstract
In this paper we present the design for a smart-mask to mitigate the impact of an airborne virus such as COVID-19. The design utilises recent results from feedback control theory over a distributed ledger that have been developed to enforce compliance in a pseudo-anonymous manner. The design is based on the use of the IOTA distributed ledger. A hardware-in-the-loop simulation based on indoor positioning, paired with Monte-Carlo simulations, is developed to demonstrate the efficacy of the designed prototype.
1 Introduction
During the COVID pandemic, mask wearing played a significant role in eventually controlling the spread of the virus [1]. According to European Centre for Disease Prevention and Control, from 31 December 2019 to 17 March 2022, 458,179,120 cases of COVID-19 (under the applied case definitions and testing strategies in the affected countries) have been reported, including 6,058,022 deaths; see for example, https://www.ecdc.europa.eu/en/geographical-distribution-2019-ncov-cases. If not properly controlled, the virus might once again emerge and spread across the population, leading to high mortality rates and hospitalisations. Even as the amount of infected people abates, the need to wear face-masks remains in many aspects of daily life in some countries; for example, in passenger planes, buses, and trains. In such situations, enforcement of mask wearing is the responsibility of observers, such as flight attendants, rather than the mask wearer. Often, this leads to situations where either compliance is not enforced, or where an unreasonable burden is placed on these observers. In this paper, we explore ways to encourage people to wear masks properly, especially in confined and crowded spaces (for example: airplanes). Importantly, we wish to design mechanisms where compliance with mask wearing (or more general social contracts) remains with the mask wearer, rather than with observers. To do this we build on our previous work done in [4], in which the authors discuss a general framework, based on control theory, to regulate compliance to social contracts in the sharing economy domain.
The objective of this paper is to present a Proof-of-Concept (PoC) smart mask that can detect people’s mask-wearing status, and then to incentivise people’s behaviour with a bonding mechanism to wear masks efficiently in confined and crowded spaces. By wearing masks correctly, we mean that people use a mask to cover both their mouth and nose at the same time as depicted by the person on the left in Fig 1. In contrast, the middle and right individuals in the same figure are illustrations of not proper mask wearing.
Fig 1. Correct and incorrect mask wearing.
Our work also builds on the idea of a personalised dynamic pricing strategy to assist in ensuring that agents in a population comply with a social contract. Here, by a social contract, we mean a set of guidelines that must be followed to ensure the proper utilisation of a resource or object. Such ideas are common in the sharing economy where goods should be returned on time and in good order, and in the circular economy where sorting of rubbish is incentivised using bonds (deposits) to encourage that consumers sort certain types of household waste. In our case, the agreement of wearing a mask correctly, in the context of COVID-19, is a social contract. While there are other papers on this and related topics-for example-see [2, 3], our work is based on a novel perspective on this problem that is presented in [4]. In [4], the authors propose a personalised feedback control based on a DLT system that encourages compliance with a social contract. The authors in this paper also provide a theoretical analysis of the designed system’s convergence. In the context of [4], the role of the DLT is to provide a more secure and privacy-aware structure than in centralised alternatives, and to provide a platform for creating a personalised economic commitment algorithm. For the convenience of remaining discussion in the present paper, we refer to the algorithm in [4] as Personalised Feedback Control Algorithm (PFCA). We note also that the idea of incentives is also being explored more widely in the circular economy and that similar ideas have appeared in various applications and prototypes [5, 6], such as Kupcrush (https://biotasphere.com/showcase/). Kupcrush uses DLTs to make cups into economic agents through the use of Digital Twins. Each cup is associated with a digital identity and a wallet. The aim is to incentivise the consumer who is using the cup to recycle it correctly by rewarding every actor in the circular economy with a micro-reward as the cup moves through the recycling chain until it is ultimately recycled into a new cup. Finally, we note that the issue of compliance has been discussed in other application domains [7, 8]. However, there are significant limitations in these works. For example, the systems advocated in these papers are often centralised and lack anonymity and other privacy guarantees. Accordingly, the main contributions of this paper are the following.
First, we propose a digital bonding system, based on the IOTA Tangle technology and using ideas from feedback theory, to encourage adherence of a population to a social contract; in this case wearing a smart mask [9–11].
Second, we present a smart mask design. The smart mask is designed to detect people’s mask wearing status. A prototype based on a Raspberry Pi 3B [12] hardware platform is described, complete with integration of the aforementioned digital bonding system.
Agent-based simulations, as well as hardware-in-the-loop simulations are presented to illustrate the efficacy of the proposed system.
In what follows we discuss the design of the aforementioned system. Before proceeding we make the following important comments.
A. Our smart mask system is designed to operate in sensitive situations; for example, in a passenger aircraft during a pandemic such as COVID-19. During COVID-19 it was frequently the case that users without a medical exemption would be expected to wear the mask as a condition of flying.
B. In our setting, agents (aircraft passengers) commit to wear a mask, through the staking of a digital bond or token, in much the same manner that deposits are used to encourage recycling in certain countries. If a user complies with the social contract, all of the bond is returned, otherwise some of the bond is not returned.
D. Our system goes beyond that used in traditional circular economy applications in two ways. We use a distributed ledger (DLT) to record transfer of tokens from the users to the agency defining the social contract. This achieves two objectives. First, it allows the transfer of tokens in an automated and pseudo-anonymous manner. Second, it allows the implementation of feedback strategies to adjust the price of non-compliance in a personalised manner (i.e. allows the implementation of polluter-pays type models), while achieving a certain level of aggregate compliance.
E. As we shall see no information is recorded on the DLT other than an average level of compliance, and all information is private and pseudo-anonymised. Specifically, even though our mask uses Carbon-dioxide (eCO2) and Total Volatile Organic Compounds (TVOC) information to detect whether a mask is worn correctly, none of this, or any user specific biological information, is recorded on the DLT.
F. Finally, we emphasise that we are not proposing any type of licensing system. A user stakes a bond as a promise to fulfil a contract. This bond is returned when the contract is fulfilled. The functioning of this digital token system is similar to the process of using a shopping trolley in some supermarkets. To utilise the trolley, one needs to deposit a coin, and upon returning it, the coin is refunded. In our context, the token is only meant to be used as a deposit and incentive for individuals to follow social distancing protocols in specific situations, like a crowded airplane.
The remainder of this paper is organised as follows. In Section 2, we give a brief description of DLTs and more specifically of the IOTA distributed ledger, also known as the IOTA Tangle. In Section 3, we provide an overview of relevant work from both pricing algorithm and smart mask design perspectives. In Section 4, we present the Personalised Feedback Control Algorithm (PFCA) and the smart mask model designed in this paper. Section 5 validates the efficacy of the proposed approach through hardware-in-the-loop simulations and agent-based simulations. Section 6 summarises the results discussed in this work and outlines future research directions.
Finally, we note also that a short version of this paper has been accepted at the BLOCKCHAIN’23: 5th International Congress on Blockchain and Applications. A short summary of the results in this paper will be published in the conference proceedings (Springer).
2 Background
2.1 IOTA Tangle
The term distributed ledger technology (DLT) refers to digital database architectures that are shared across many nodes in a peer-to-peer network [13]. DLTs have recently gained popularity in both industry and in academia, and have found many applications. For example, they have been used in the context of smart city domains [10], in supply chain applications [14], and in the health-care domain [15]. DLTs hold great potential in these sectors because of several desirable properties such as, decentralization, immutability of records, and transaction transparency. Although Blockchain is the best known DLT architecture, several limitations hinder its widespread application in an IoT context [16]. For example, the inherent sequential structure in Blockchain to add new transactions often results in a limited transaction rate and the heavy cryptography based Proof-of-Work (PoW) consensus mechanism leads to expensive computation power.
As alternative to Blockchain based architectures is a ledger such as the IOTA Tangle. The structure of the IOTA Tangle is a Directed Acyclic Graph (DAG). In this DAG-based ledger, widely referred to as the Tangle, information is stored in a graph based structure rather than a sequential set of blocks. In the IOTA DAG, vertices of this graph are blocks issued by network participants, and each block contains at most one transaction. The edges of the graph are formed by blocks (transactions) approving previous blocks that we call parents. All yet unapproved transactions are called tips and the set of all unapproved blocks is called the tips set. A node selects tips to approve through a tip selection algorithm. To issue a block a node selects k blocks from the tip-set. This process, called approval, is represented by an edge in the graph. If there exists a directed edge from vertex i to j, we say j is directly approved by i. If there is a directed path from i to j we say that j is indirectly approved by i.
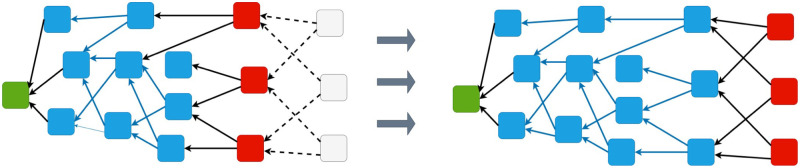
As an example of this process, Fig 2 shows an instance of the Tangle with three new incoming blocks (left panel). Blue blocks have already been approved, red blocks represent the current tips of the Tangle and grey blocks are incoming transactions. Full details of the IOTA DAG can be found in [17, 18] (a description of Tangle version 1.4.3 can be found at https://iota.org/IOTA_Whitepaper.pdf).
Fig 2. The Tangle structure.
3 Related work
We have already mentioned several related works in Section I. In particular, we mentioned that the notion of compliance arises in other application areas. In this section we also note that elements of related work can also be found in several other areas. For example, work based on pricing digital bonds are also related to other concepts in the literature [19, 20]. For example, our pricing algorithms are similar to work on dynamic pricing that can be found in several domains. One example of such work can be found in [21], where the author proposes a novel mechanism named User-Centric Dynamic Pricing (UCDP) to regulate the real-time urban traffic system. A novel dynamic toll-pricing algorithm is also proposed in [2] to alleviate traffic congestion. Similar concepts can be also found in the paper [3] which introduces a new smart parking system to allocate parking spaces. Other examples of related work in pricing can be found in [22, 23], where sellers to adopt flexible pricing policies according to different economic situations and customers’ specifications.
Other related work can be found in the area of smart mask design; especially in the context of COVID-19. [24] describes an active smart mask which is used for protecting people from coronaviruses and other airborne pathogens, such as pollutants or dust particles. A wearable smart mask integrated with a temperature sensor is described in [25] to continuously acquire human beings’ health data. To remotely measure temperature non-intrusively, especially to detect symptomatic people who might become infected with COVID-19 in public places, a smart mask prototype equipped with three thermistors is proposed in [26]. In [27], the author studied a smart mask prototype which integrates a reusable face mask shell and a sensing module that integrates with user-based mobile application. Although these works provide a solid foundation for our work, none address the issue of personalised compliance with social contracts.
There are also some works that approach the detection of mask-wearing, and enforcement of compliance with social contracts, through the use of Machine Learning (ML) techniques [28, 29]. For example, in [30], the author proposes an edge-computing-based mask (ECMask) identification framework, that uses facial recognition and deep learning methods to detect the mask wearing status. As another example in [31] the authors propose a system, also based on deep learning and computer vision technologies, that can achieve both mask face identification and temperature tracking. However, there are a number of differences between this approach and the one proposed in this paper, as well as limitations. Firstly, ML algorithms require a significant amount of data to build an accurate model. Secondly, in these approaches the authors do not make use of a pricing mechanism to regulate compliance with the social contract and they focus only on the detection of the mask status. Thirdly, most of the papers mentioned above require the use of face recognition methods, paired with ML algorithms to detect the status of the mask, whereas our proposals is based on hardware that detects locally the status of the mask, paired with the use of a token-based decentralised distributed ledger to protect the anonymity and the privacy of the users. Finally, in such situations, the ML technology simply detects non-compliance, and enforcement of mask wearing is the responsibility of observers, such as, for example, flight attendants, rather than the mask wearer (which is the main feature and advantage of our approach).
Other compliance related work appears in the context of game theory [7, 8]. However, there are also significant limitations within these works. For example, frequently such approaches are centralised; they are vulnerable to resource-rich attackers; they are often not anonymous because of unencrypted user addresses; and fairness is not addressed as they are not tailored according to the individual situation. All of these deficits can be addressed using the paradigm described in [4].
4 Mask model and algorithmic design
4.1 The PFCA algorithm
Before preceding to describe our mask design, we describe the motivation of employing PFCA algorithm. Although there are many works, such as game theoretic framework, privacy averse voting and recommendation platforms [7, 32], that aim to address the compliance issue, these strategies are vulnerable to manipulation by resource-abundant malicious actors, such as those making false recommendations. In contrast, the PFCA algorithm, which draws inspiration from stochastic approximations, hyperbolic discounting, and digital identity principles, adopts DLT and a series of control algorithms to enforce compliance without these drawbacks.
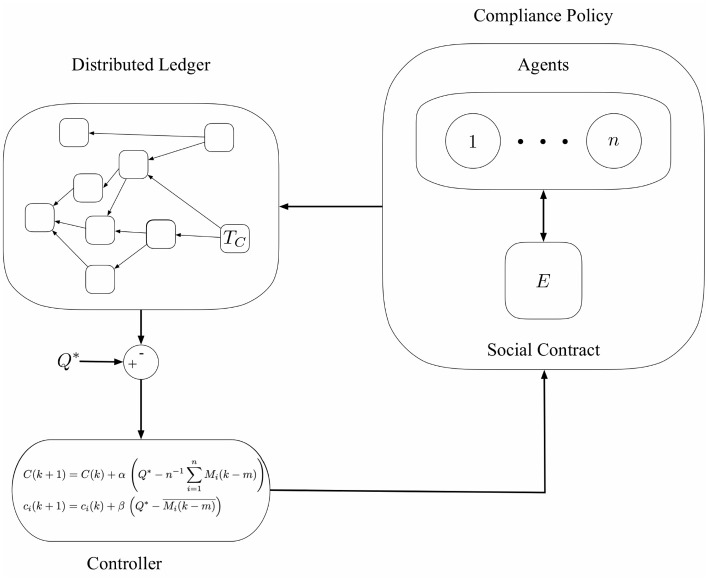
Our work builds on [4], where digital tokens are enforce social contracts. A social contract defines guidelines that must be followed to ensure an agreed utilization of a shared object. The basic idea is that agents deposit tokens as a bond as an guarantee that they will utilise a resource or object in an agreed manner. If the object, such as a mask, is used in a correct manner (i.e. not removed), then the tokens are returned in full, or in part. An algorithm from [4] is used to determine the returned tokens based on level of compliance. The architecture described in [4] is shown in Fig 3. The system in Fig 3 operates as follows. A distributed ledger is used as a communication layer (i.e., to record the deposit and the withdrawal of the tokens) and a controller is used to adjust the number of tokens deposited and achieve expected compliance level for the social contract (compliance policy), denoted E. Smart contracts mean that the entire system operates automatically. All operations are recorded on a DLT which is immutable and data are shared pseudo-anonymously among agents.
Fig 3. The functional components of the proposed compliance architecture are: The Distributed Ledger that acts as the communication backbone of the infrastructure, the compliance policy and the feedback controller [4].
A feedback mechanism for designing a proper value of the bond is adopted from [4]. We consider n agents here and for each agent i, we define a binary random variable for discrete values k as:
| (1) |
This model essentially assumes that all agents behave rationally and adopts the approach to behavioural modelling described in [33] and in the follow-on papers [34–36]. This models essentially use iterated function systems to capture the concept of a rational agent. In what follows qi is a constant parameter which represents the proclivity of each agent to comply with rules; C(k) and ci(k) represent, respectively, a global and an individual feedback signal whose purpose is to regulate the behaviour of each agent to achieve the desired level of compliance. The sum of C(k) and ci(k) represents the value of the token bond staked by agent i at time-step k; The combination qi + C(k) + ci(k) is the probability that agent i will comply with the rule at time-step k + 1. Then, (1) can be expressed as
| (2) |
with being a monotone increasing function (which is used to bind the probability between 0 and 1). C(k) and ci(k) denote a global and an individual feedback signal respectively, which are designed to regulate each agent’s behaviour to reach the desired compliance level. However, since the agents employ a Distributed Ledger as their communication medium, due to the intrinsic delays that characterise these systems, their access is restricted to previous compliance levels represented as . In this notation, m denotes a delay in the measurements, a consequence of the PoW mechanism, ledger synchronisation, and time required for verification. Accordingly, we consider the following control laws, and ∀i ∈ {1, …, n},
| (3) |
| (4) |
where α > 0 and β > 0 are two constants, and ∀i ∈ {1, …, n}, Q* ∈ [0, 1] is the desired level of compliance, and is a windowed time average of the compliance of agent i, which is defined as
| (5) |
where (1 − γ)−1 is the length of the window for the average, with γ < 1.
The design of the algorithm is such that the value of the bond staked by agent i depends not only on the overall compliance of all agents, but also and how agent i’s past behaviour. The use of both a global and an individual control signal can be used to enforce fairness and resiliency from pricing attacks.
4.2 Mask design
Given the general background described above, we consider scenarios where agents move within a confined and/or crowded space where the use of masks is mandatory, such as buses, the tube, or airplanes. The following steps are performed to encourage social compliance and the structure of the network is depicted in Fig 4.
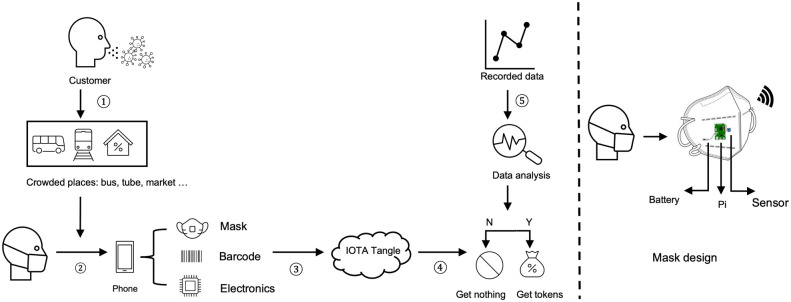
Fig 4. In the designed network structure, when customers enter into crowded places as shown in ①, such as bus, tube and markets, they are required to wear a mask paired with their phone as shown in ②.
Each mask has a unique barcode and reusable electronics. During ③, the status of mask wearing is uploaded to IOTA Tangle. These recorded data are attached through ④ and analysed through ⑤. According to the compliance of the customer, the token bond is returned in full, or in part. In the right hand of the figure, we show the specific electronics for the system realisation which includes a battery, a raspberry Pi and a sensor.
Agents entering a space where mask wearing is mandatory must wear a smart mask that is connected to an agents phone. The mask is connected to a digital wallet via an integrated chip and the smart phone.
An agent entering a restricted zone, deposits a number of tokens as a compliance bond. Smart contracts are used to automate this procedure.
The sensor chip monitors Carbon-dioxide (eCO2) and Total Volatile Organic Compounds (TVOC), whereas the Raspberry Pi performs computations and uploads data to the IOTA Tangle in real time.
If the agent wears the mask correctly, some, or all of its tokens are returned.
We now provide a brief description of the main hardware and software elements used for building the smart mask prototype.
We used the IOTA firefly digital wallet for our mask design.
A Raspberry Pi 3 is the main processing element to collect sensor data and to send and publish data to IOTA Tangle. The main task of the Pi is to implement the controller given in Eq (3). The controller could also be delegated to the smart-phone.
Gas sensors, such as the, CJMCU-811 is used to monitor the density of eCO2 and TVOC exhaled by an agent.
Communication is based on Message Queuing Telemetry Transport (MQTT) [37] and Masked Authenticated Messaging (MAM) [15]. MQTT is a standard IoT protocol, and MAM is the IOTA communication protocol Both are very low-power consumption protocols.
In conclusion, from a practical standpoint, the smart mask system requires two components: (a) a smartphone, to perform computations and with an integrated digital wallet to communicate with the IOTA DLT; and (b) a smart-mask which consists of wearable-class electronics and a sensor.
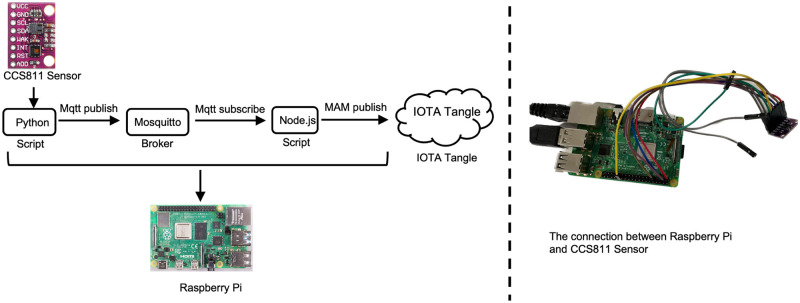
Fig 5 shows that the network flow of uploading data to the IOTA Tangle. Agent-data is collected from the CJMCU-811 sensor which is connected to the Raspberry Pi 3B. The lightweight open source MQTT architecture is adopted to transfer data in the network. MQTT adopts a publish and subscribe model, in which some devices publish messages on a topic, while some devices which have subscribed to this topic receive this message. After the Raspberry Pi gathers eCo2 and TVOC data from the sensor, it then publishes these data to a specific MQTT topic. Other IoT devices such as the ESP32, ESP8266 boards, and other sensors, such as temperature and humidity sensors can also be added to the system monitor customers’ status. The module (depicted in Fig 5) named Node.js is used as the back-end server to subscribe to this specific topic and publish contained data in this topic to the IOTA Tangle through a lightweight data transmission protocol-MAM (see below).
Fig 5. Implementation architecture including Raspberry Pi, CCS811 sensor and the communication protocol to IOTA Tangle.
MAM is a lightweight data transmission protocol designed by IOTA foundation. It enables nodes (any IoT device that can send or propagate transactions) to share encrypted data streams to each other node over the IOTA Tangle [38]. MAM is an important method for securing the transfer or accessing of the data stored in the IOTA Tangle. Nodes or devices, which are connected to the IOTA Tangle acting as publishers, broadcast their encrypted messages into a specified channel, while nodes that are interested in receiving the published messages can subscribe to the same channel [15]. There are three modes within MAM, including a Public mode, a Private mode, and a Restricted mode. For a public MAM mode, it employs the address of the transaction which is the same as Merkle Tree’s root [39]. The private MAM mode employs the addresses of transactions which is gained by hashing the root of the Merkle Tree, which means the message can be known only if the root of the Merkle Tree is obtained. For the restricted MAM mode, it employs the address of the transaction which is obtained by the hash of the Merkle tree’s root and a side key, which means the message can be known only if both the key and the root are known [40].
5 Experimental set-up
To illustrate the effectiveness of the designed algorithm, we set up two different types of simulations. The code can be found in https://github.com/Mona566/Mask-Paper.git.
Agent-based simulation: An agent-based simulation is employed to mimic the behaviour of multiple agents within a room. Each agent behaves according to the equations described in Section IV. This simulation shows that with the proposed control strategy, the desired compliance is achieved and the probability of people being infected is reduced.
Hardware-in-the-loop simulation: A user wears the mask prototype and its position and mask wearing status are respectively recorded to the IOTA Tangle and sent to the agent-based simulator in real time, as if the user was one of the agents of the simulations. This simulation is used to give real agents (people) the feeling of using a smart mask in a crowed area and to show that the interaction of the hardware and the control strategy works seamlessly.
In what follows, we provide a detailed description of each of these.
5.1 Agent-based simulation
We make use of an agent-based model to simulate the spread of COVID-19 within a confined space. In this experiment, we assume the number of agents is 500. Whenever agent i is in close range of agent j, i.e. when ||xi − xj||2 ≤ ϵ, there is a probability that agent i will become infected. This probability is defined as
| (6) |
where the base infection rate is denoted by P0 (the chance of being infected with no social distancing and mask wearing), mi ∈ [0, 1] is the effectiveness of the mask worn by agent i, and Mi(k) ∈ {0, 1} is a binary random variable that indicates whether agent i is wearing a mask at time instant k.
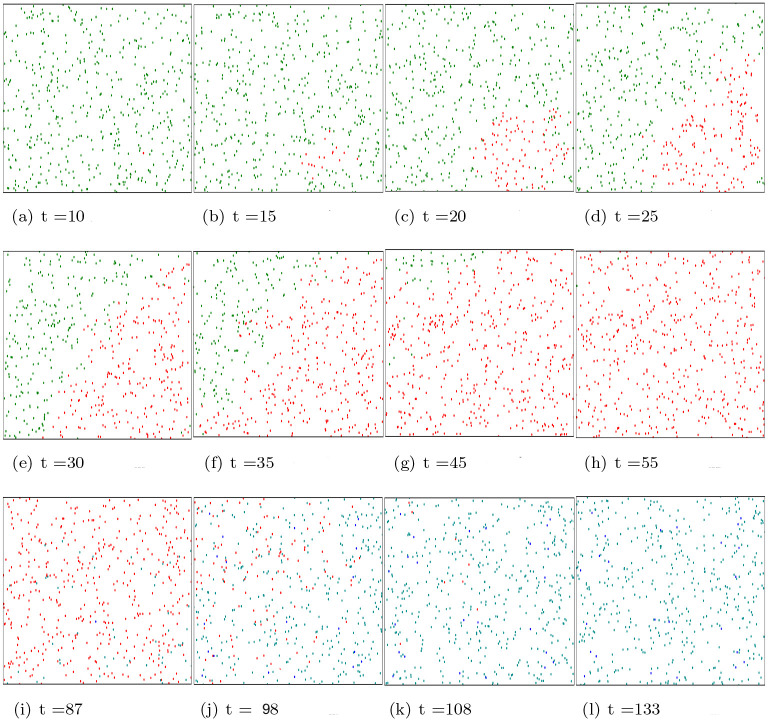
When no masks are worn the infection rate increases very quickly. As shown in Fig 6(a), we set up the model with a single infected individual, marked as the red dot. As depicted in Fig 6(b)–6(h) the virus spreads very quickly. At t = 30, as depicted in Fig 6(e), nearly half of people become infected and nearly all agents become infected from t = 55 as depicted in Fig 6(h).
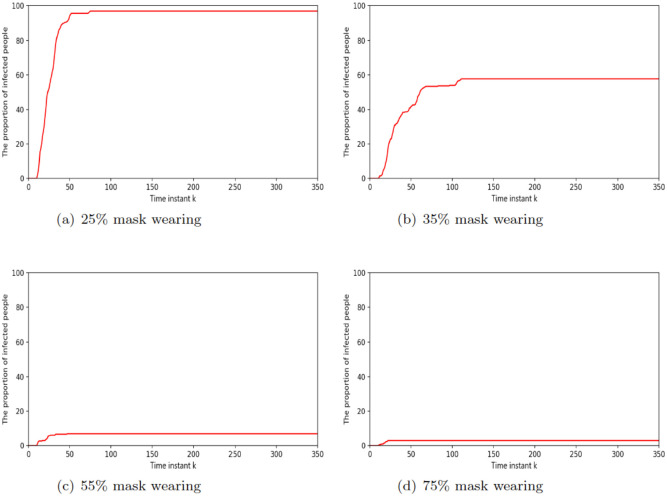
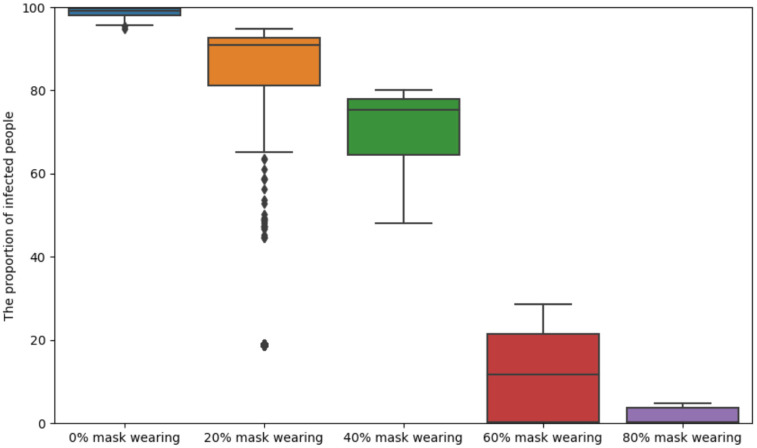
When agents, including healthy agents and infected agents wear masks effectively, the infection rate and serious infection rate increase at a slower rate. As depicted in Fig 7(a), when 25% of agents wear masks, the proportion of infected agents is almost 100% around 50 time instant. As depicted in Fig 7(b), when 35% of agents wear masks, the maximum percentage agents that become infected is also around 60%. As depicted in Fig 7(c), when 55% of agents are wearing masks, the maximum percentage of infected agents is only around 10% at 50 time instant. Finally, Fig 7(d) shows that the amount of infected agents is even lower if 75% people are wearing masks. Fig 8 displays the error bar for mask-wearing performance. The corresponding boxplot results are produced from 25 Monte Carlo simulations, each running 250 time units. When there is no compliance with mask wearing (0%), the infection rate is exceptionally high. The median proportion of infected individuals is approximately 90% under the scenario of 20% mask-wearing compliance, and median proportion of infected individuals is approximately 75% when the compliance with mask wearing increases to 40%. Notably, as mask-wearing compliance rises to 70%, there is a substantial reduction in the median infection rate to around 10%. Furthermore, when mask-wearing compliance reaches 80%, the maximum infection rate significantly decreases to approximately 5%.
Fig 6. The degree of infection among people when they do not wear masks properly at different time instants.
Green dots denote healthy people, red dots denote infected people, cyan dots denote immune people with slight possible sequelae, while blue dots denote immune people with serious sequelae.
Fig 7. The proportion of infected people, as a time series, in different mask wearing scenarios.
Fig 8. Boxplots corresponding to Fig 7.
Boxplot results are produced from 25 Monte Carlo simulations, each running 250 time units. When there is no compliance with mask wearing (0%), the infection rate is exceptionally high. The median proportion of infected individuals is approximately 90% under the scenario of 20% mask-wearing compliance, and median proportion of infected individuals is approximately 75% when the compliance with mask wearing increases to 40%. Notably, as mask-wearing compliance rises to 70%, there is a substantial reduction in the median infection rate to around 10%. Furthermore, when mask-wearing compliance reaches 80%, the maximum infection rate significantly decreases to approximately 5%.
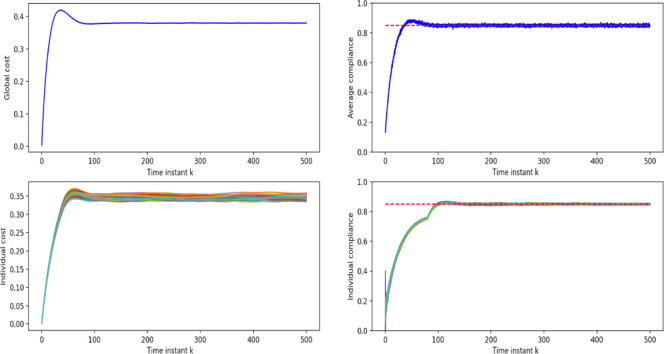
These simulations show, qualitatively, that high levels of compliance with social distancing norms lead to lower infection rates overall. This is the rationale behind the employment of the control laws described in Section II. In fact, as depicted in Fig 9, with PFCA including both a global and an individual cost signal, the desired level of compliance is achieved and the fairness of cost among all individuals is also ensured (as each individual will comply equally, regarding of their initial proclivity qi).
Fig 9. Global cost and individual cost.
The above plot is global cost which is calculated by Eq (3); The bottom plot is individual cost which is calculated by Eq (4); (b) Global compliance and individual compliance.
Remark: We want to emphasise that, the agent model used in this paper does not intend to be a realistic simulation of the dynamics of how COVID-19 spreads across a given population. Rather it is intended as a elementary model, to showcase how the control algorithm and the smart mask would work in a scenarios similar to a viral spread in a population of agents.
5.2 Hardware-in-the-loop simulations
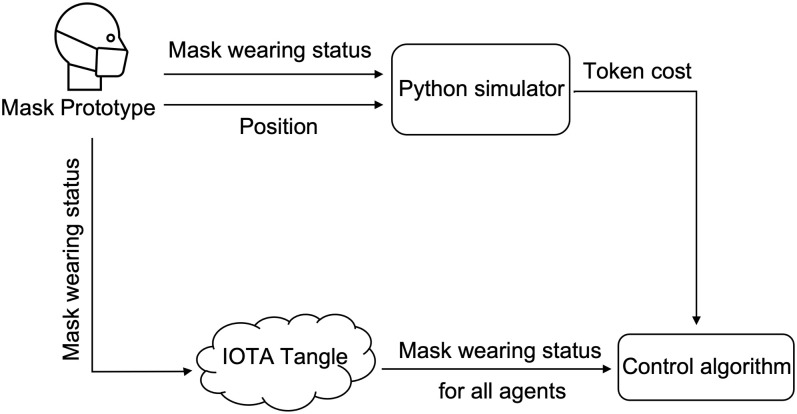
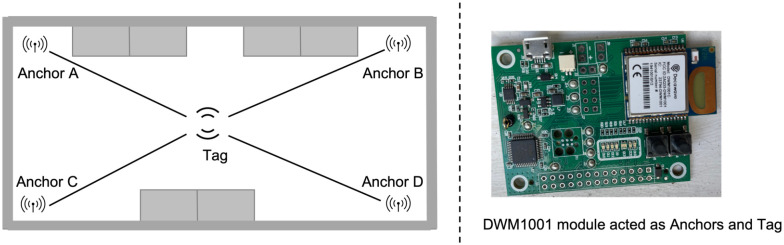
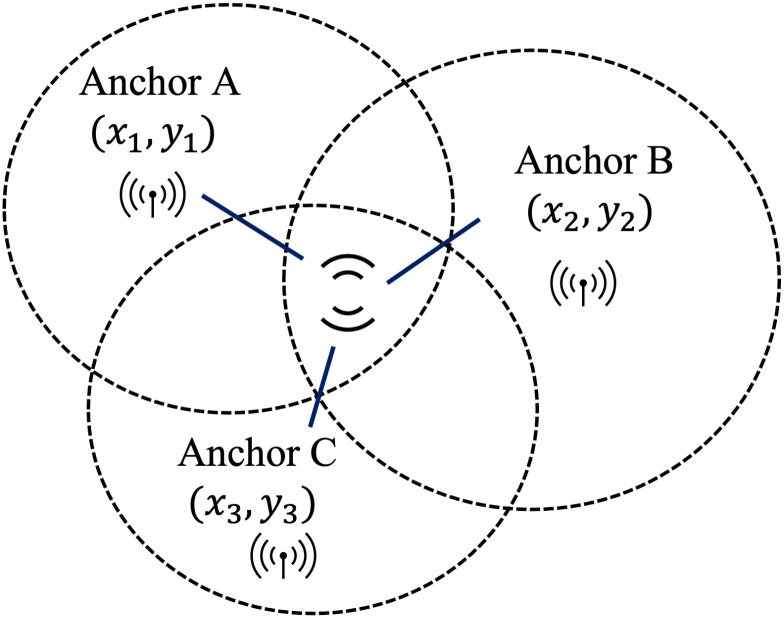
In the previous section, we showed that with the proposed control strategy, the desired compliance is achieved and the probability of people being infected is reduced. In order to give real agents (people) the feeling of using a smart mask in a crowed area, we develop a hardware-in-the-loop simulation based on indoor positioning. As shown in Fig 10, the hardware-in-the-loop simulation is used for monitoring the smart mask wearing position and status of a real agent. The position and the status of the mask are both sent to the IOTA Tangle and the python simulation in which a number of virtual agents are emulated, and all data for both real and virtual agents is sent to the IOTA Tangle. Detection of the mask position is based on Ultra-Wide Band (UWB) indoor positioning technology [41]. The equipment used in these experiments is the DW1001-DEV. We use the Decawave concepts of ‘Anchor’ and ‘Tag’ to denote different UWB nodes in the system. An ‘Anchor’ represents a fixed node whose position is known. Anchors use wireless signals from tags to determine the position of movable tags whose position is unknown. In this experiment, the architecture for indoor positioning is depicted in Fig 11. We set four DWM1001 modules as Anchors and one DWM1001 module as a tag (representing the customer moving within a closed space). Embedded firmware provides two-way ranging (TWR) and real time location system (RTLS) functionality are pre-loaded in the DWM1001 module; see https://www.Decawave.com. Note that Decawave adopts the TWR method which is based on time of flight (ToF) [42] to obtain range measurements. In addition, as shown in Fig 12, the triangulation technique is employed to determine the tag’s position within a 2-D environment that has three or more anchor points [43]. The distance measurement behind this method is that it takes the product of a measured time and the speed of light. The measured time is the radio signal that travels between an emitter and a receiver. The principle behind To measure distance, three messages named Poll, Response and Final need to be exchanged between anchors and tag. Anchor timestamps and tag timestamps are recorded and used to calculate the distance Dis.
Fig 10. The structure of hardware-in-the-loop simulation.
Fig 11. Experimental setup for indoor positioning system.
Fig 12. Utilizing ToF triangulation to perform object localization.
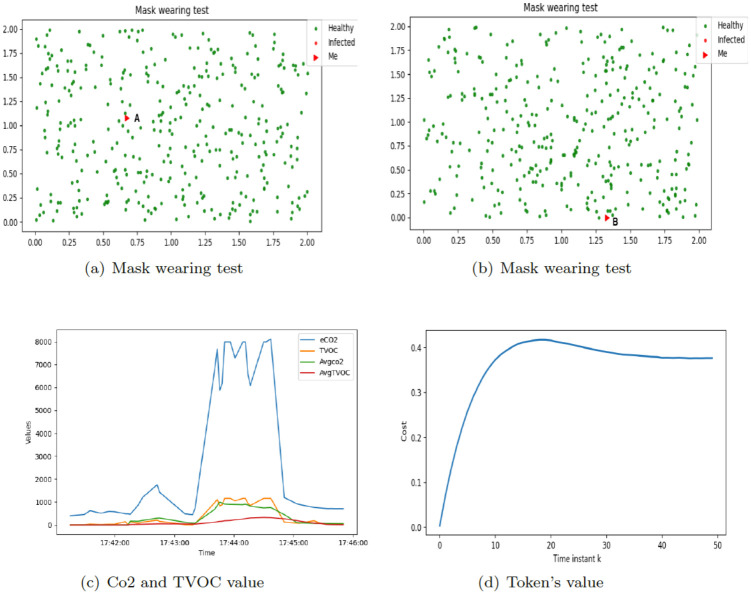
Experiments were conducted in a room at Imperial College London. There are four anchors named DW4105, DW9B10, DW4A2F (as initiator), DW4C15, and one Tag named DW181C. In Fig 13(a) and 13(b), the triangle depicts the position of the Tag (i.e., the PoC-based mask), while other dots denote other agents generated by the simulator. Fig 13(c) depicts the data collected by the gas sensor. The processing of the data is done as follows.
Fig 13. Mask wearing test.
(a) The red triangle depicts the position of the Tag, which is at point A. (b) The red triangle depicts the position of the Tag, which is at point B. Red and green dots denote other agents generated by the simulator, in which green dots present healthy agents and red dots denote infected agents. (C) The level of eCo2, TVOC, AvgCo2 and AvgTVOC. We use blue line for eCo2, red line for TVOC, yellow line for AvgCo2 and green line for AvgTVOC. (d) The variation of the individual cost.
In order to account for the noise from sensors we average the data, effectively applying a low pass filter to them, over a fixed window of time. For these experiments the time window was fixed at 10 samples.
In order to detect whether the mask was worn or not, we set two thresholds for eCo2 and TVOC. If the computed moving averages are above these thresholds we know that the mask was worn correctly. The two thresholds are set, respectively, at 500 ppm for eCo2 and 50 ppb for TVOC.
Remark: This experiment that we have described is designed to illustrate the main features of the operation of the system. In particular, the eCO2 and TVOC thresholds are chosen empirically. Any practical implementation of the system would require these factors to be selected in a more rigorous manner by considering factors such as the mask wearers’ age, health, and environmental conditions (e.g., air pressure).
As mentioned above, Fig 13(c) shows the values for Co2 and for TVOC, as detected from the mask. It is possible to appreciate, even by visual inspection, that the reading from the sensors increase drastically when somebody is wearing a mask, making it straightforward to detect, whether or not a user is complying. Finally, Fig 13(d) depicts the variation of individual cost, paid by the specific user according to the compliance.
6 Conclusion
In this paper, a smart mask prototype is designed to monitor people’s mask wearing status. The use of DLT-based IOTA Tangle, serves as both a communication layer for the control algorithm as well as ledger ensuring the security and immutability of data. The controller is used to form a feedback loop to regulate the network. The designed mechanism is validated through extensive simulations including a python-based one and a hardware-in-the-loop one. Planned future work includes evaluation of the mask in real urban settings, to develop the compliance policies developed in [3], and to evaluate user acceptance in population studies for the compliance based systems, all of which constitute limitations of the present work.
Data Availability
All relevant data are within the paper.
Funding Statement
Funded by IOTA Foundation. The funders had no role in the project conception, the design of experiments, data collection and analysis, decision to publish, or preparation of the manuscript.
References
- 1. Eikenberry SE, Mancuso M, Iboi E, Phan T, Eikenberry K, Kuang Y, et al. To mask or not to mask: Modeling the potential for face mask use by the general public to curtail the COVID-19 pandemic. Infectious Disease Modelling. 2020;5: 293–308. doi: 10.1016/j.idm.2020.04.001 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2.Phan T, Annaswamy AM, Yanakiev D, Tseng E. A model-based dynamic toll pricing strategy for controlling highway traffic. In Proceedings of the 2016 American Control Conference (ACC). IEEE; 2016. 6245–6252.
- 3. Kotb AO, Shen YC, Zhu X, Huang Y. iParker—A new smart car-parking system based on dynamic resource allocation and pricing. IEEE Transactions on Intelligent Transportation Systems. 2016;17(9): 2637–2647. doi: 10.1109/TITS.2016.2531636 [DOI] [Google Scholar]
- 4. Ferraro P, Zhao L, King C, Shorten R. Personalised feedback control, social contracts, and compliance strategies for ensembles. IEEE Internet of Things Journal. doi: 10.1109/JIOT.2023.3298516 [DOI] [Google Scholar]
- 5. Fischer A, Pascucci S. Institutional incentives in circular economy transition: The case of material use in the Dutch textile industry. Journal of Cleaner Production. 2017;155: 17–32. doi: 10.1016/j.jclepro.2016.12.038 [DOI] [Google Scholar]
- 6. Singh MP, Chakraborty A, Roy M. Developing an extended theory of planned behavior model to explore circular economy readiness in manufacturing Micro Small and Medium Enterprises (MSMEs), India. Resources, Conservation and Recycling. 2018;135: 313–322. doi: 10.1016/j.resconrec.2017.07.015 [DOI] [Google Scholar]
- 7. Ashby S, Chuah S-H, Hoffmann R. Industry self-regulation: A game-theoretic typology of strategic voluntary compliance. International Journal of the Economics of Business. 2004;11(1): 91–106. doi: 10.1080/1357151032000172255 [DOI] [Google Scholar]
- 8. Agarwal P, Hunt K, Srinivasan S, Zhuang J. Fire code inspection and compliance: A game-theoretic model between fire inspection agencies and building owners. Decision Analysis. 2020;17(3): 208–226. doi: 10.1287/deca.2020.0410 [DOI] [Google Scholar]
- 9. Moschella M, Ferraro P, Crisostomi E, Shorten R. Decentralized assignment of electric vehicles at charging stations based on personalized cost functions and distributed ledger technologies. IEEE Internet of Things Journal. 2021;8(14): 11112–11122. doi: 10.1109/JIOT.2021.3052045 [DOI] [Google Scholar]
- 10. Ferraro P, King C, Shorten R. Distributed ledger technology for smart cities, the sharing economy, and social compliance. IEEE Access. 2018;6: 62728–62746. doi: 10.1109/ACCESS.2018.2876766 [DOI] [Google Scholar]
- 11. Ferraro P, King C, and Shorten R. On the stability of unverified transactions in a dag-based distributed ledger. IEEE Transactions on Automatic Control. 2019;65(9): 3772–3783. [Google Scholar]
- 12. Naik S, Sudarshan E. Smart healthcare monitoring system using raspberry Pi on IoT platform. Asian Research Publishing Network (ARPN) Journal of Engineering and Applied Sciences. 2019;14(4): 872–876. [Google Scholar]
- 13. Kuhn R, Yaga D, Voas J. Rethinking distributed ledger technology. Computer. 2019;52(2): 68–72. doi: 10.1109/MC.2019.2898162 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 14. Suhail S, Hussain R, Khan A, Hong CS. Orchestrating product provenance story: When IOTA ecosystem meets electronics supply chain space. Computers in Industry. 2020;123: 103334. doi: 10.1016/j.compind.2020.103334 [DOI] [Google Scholar]
- 15. Brogan J, Baskaran I, Ramachandran N. Authenticating health activity data using distributed ledger technologies. Computational and Structural Biotechnology Journal. 2018;16: 257–266. doi: 10.1016/j.csbj.2018.06.004 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 16. Xiong Z, Feng S, Wang W, Niyato D, Wang P, Han Z. Cloud/fog computing resource management and pricing for blockchain networks. IEEE Internet of Things Journal. 2018;6(3): 4585–4600. doi: 10.1109/JIOT.2018.2871706 [DOI] [Google Scholar]
- 17. Müller S, Penzkofer A, Polyanskii N, Theis J, Sanders W, Moog H. Tangle 2.0 leaderless nakamoto consensus on the heaviest DAG. IEEE Access. 2022;10: 105807–105842. doi: 10.1109/ACCESS.2022.3211422 [DOI] [Google Scholar]
- 18.Lin BY, Dziubałtowska D, Macek P, Penzkofer A, Müller S. Robustness of the tangle 2.0 consensus. In Proceedings of the European Alliance for Innovation (EAI) International Conference on Performance Evaluation Methodologies and Tools. Springer; 2022;482: 259–276.
- 19. Annaswamy AM, Guan Y, Tseng HE, Zhou H, Phan T, Yanakiev D. Transactive control in smart cities. Proceedings of the IEEE. 2018;106(4): 518–537. doi: 10.1109/JPROC.2018.2790841 [DOI] [Google Scholar]
- 20.Katipamula S. Smart buildings can help smart grid: Transactive controls. 2012;1-1.
- 21.Bui KT, Huynh VA, Frazzoli E. Dynamic traffic congestion pricing mechanism with user-centric considerations. In Proceedings of the 2012 15th International IEEE Conference on Intelligent Transportation Systems. IEEE. 2012; 147–154.
- 22. Victor V, Thoppan JJ, Fekete-Farkas M, Grabara J. Pricing strategies in the era of digitalisation and the perceived shift in consumer behaviour of youth in Poland. Journal of International Studies. 2019;12(3): 2071–8330. doi: 10.14254/2071-8330.2019/12-3/7 [DOI] [Google Scholar]
- 23. Sharma NK, Gaur V, Bedi P. A dynamic personalised product pricing strategy using multiple attributes in agent mediated e-market–a neural approach. International Journal of Information and Decision Sciences. 2014;6(1): 46–69. doi: 10.1504/IJIDS.2014.059731 [DOI] [Google Scholar]
- 24. Kalavakonda RR, Masna NVR, Bhuniaroy A, Mandal S, Bhunia S. A smart mask for active defense against coronaviruses and other airborne pathogens. IEEE Consumer Electronics Magazine. 2020;10(2): 72–79. doi: 10.1109/MCE.2020.3033270 [DOI] [Google Scholar]
- 25. Selvadass S, Paul JJ, Bella Mary I T, Packiavathy I, Gautam S. IoT-Enabled smart mask to detect COVID19 outbreak. Health and Technology. 2022;12(5): 1025–1036. doi: 10.1007/s12553-022-00695-2 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 26. Lazaro M, Lazaro A, Villarino R, Girbau D. Smart face mask with an integrated heat flux sensor for fast and remote people’s healthcare monitoring. Sensors. 2021;21(22): 7472. doi: 10.3390/s21227472 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 27. Hyysalo J, Dasanayake S, Hannu J, Schuss C, Rajanen M, Leppänen T, et al. Smart mask–Wearable IoT solution for improved protection and personal health. Internet of Things. 2022;18: 100511. doi: 10.1016/j.iot.2022.100511 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 28. Loey M, Manogaran G, Taha MHN, Khalifa NEM. A hybrid deep transfer learning model with machine learning methods for face mask detection in the era of the COVID-19 pandemic. Measurement. 2021;167: 108288. doi: 10.1016/j.measurement.2020.108288 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 29. Mbunge E, Simelane S, Fashoto SG, Akinnuwesi B, Metfula AS. Application of deep learning and machine learning models to detect COVID-19 face masks–A review. Sustainable Operations and Computers. 2021;2: 235–245. doi: 10.1016/j.susoc.2021.08.001 [DOI] [Google Scholar]
- 30. Kong X, Wang K, Wang S, Wang X, Jiang X, Guo Y, et al. Real-time mask identification for COVID-19: An edge-computing-based deep learning framework. IEEE Internet of Things Journal. 2021;8(21): 15929–15938. doi: 10.1109/JIOT.2021.3051844 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 31.Sanal A, Udupa G. Machine learning based human body temperature measurement and mask detection by thermal imaging. In Proceedings of the 2022 Third International Conference on Intelligent Computing Instrumentation and Control Technologies (ICICICT). IEEE. 2022; 1339–1343.
- 32. Semper H, Povey R, Clark-Carter D. A systematic review of the effectiveness of smartphone applications that encourage dietary self-regulatory strategies for weight loss in overweight and obese adults. Obesity reviews. 2016;17(9): 895–906. doi: 10.1111/obr.12428 [DOI] [PubMed] [Google Scholar]
- 33. Fioravanti AR, Mareček J, Shorten RN, Souza M, Wirth FR. On the ergodic control of ensembles. Automatica. 2019;108: 108483. doi: 10.1016/j.automatica.2019.06.035 [DOI] [Google Scholar]
- 34. Kungurtsev V, Marecek J, Ghosh R, Shorten R. On the ergodic control of ensembles in the presence of non-linear filters. Automatica. 2023;152: 110946. doi: 10.1016/j.automatica.2023.110946 [DOI] [Google Scholar]
- 35. Mareček J, Roubalik M, Ghosh R, Shorten RN, Wirth FR. Predictability and fairness in load aggregation and operations of virtual power plants. Automatica. 2023;147: 110743. doi: 10.1016/j.automatica.2022.110743 [DOI] [Google Scholar]
- 36.Alleyne A, Allgöwer F, Ames A, Amin S, Anderson J, Annaswamy A, et al. Control for societal-scale challenges: road map 2030. In: 2022 IEEE CSS Workshop on Control for Societal-Scale Challenges. IEEE Control Systems Society; 2023.
- 37. Al-Masri E, Kalyanam KR, Batts J, Kim J, Singh S, Vo T, et al. Investigating messaging protocols for the IoT. IEEE Access. 2020;8: 94880–94911. doi: 10.1109/ACCESS.2020.2993363 [DOI] [Google Scholar]
- 38. Gangwani P, Perez-Pons A, Bhardwaj T, Upadhyay H, Joshi S, Lagos L. Securing environmental IoT data using masked authentication messaging protocol in a DAG-Based Blockchain: IOTA Tangle. Future Internet. 2021;13(12): 312. doi: 10.3390/fi13120312 [DOI] [Google Scholar]
- 39.Florea BC. Blockchain and Internet of Things data provider for smart applications. In Proceedings of the 2018 7th Mediterranean Conference on Embedded Computing (MECO). IEEE; 2018; 1–4.
- 40.Bhandary M, Parmar M, Ambawade D. A blockchain solution based on directed acyclic graph for IoT data security using IOTA tangle. In Proceedings of the 2020 5th International Conference on Communication and Electronics Systems (ICCES). IEEE; 2020; 827–832.
- 41. Zhu X, Yi J, Cheng J, He L. Adapted error map based mobile robot UWB indoor positioning. IEEE Transactions on Instrumentation and Measurement. 2020;69(9): 6336–6350. doi: 10.1109/TIM.2020.2967114 [DOI] [Google Scholar]
- 42. Lian Sang C, Adams M, Hörmann T, Hesse M, Porrmann M, Rückert U. Numerical and experimental evaluation of error estimation for two-way ranging methods. Sensors. 2019;19(3): 616. doi: 10.3390/s19030616 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 43. Che F, Ahmed QZ, Fontaine J, Van Herbruggen B, Shahid A, De Poorter E, et al. Feature-based generalized gaussian distribution method for Nonline-of-sight (NLoS) detection in ultra-wideband (UWB) indoor positioning system. IEEE Sensors Journal. 2022;22(19): 18726–18739. doi: 10.1109/JSEN.2022.3198680 [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
All relevant data are within the paper.