Abstract
In the sixth generation (6G) era, intelligent machine network (IMN) applications, such as intelligent transportation, require collaborative machines with communication, sensing, and computation (CSC) capabilities. This article proposes an integrated communication, sensing, and computation (ICSAC) framework for 6G to achieve the reciprocity among CSC functions to enhance the reliability and latency of communication, accuracy and timeliness of sensing information acquisition, and privacy and security of computing to realize the IMN applications. Specifically, the sensing and communication functions can merge into unified platforms using the same transmit signals, and the acquired real-time sensing information can be exploited as prior information for intelligent algorithms to enhance the performance of communication networks. This is called the computing-empowered integrated sensing and communications (ISAC) reciprocity. Such reciprocity can further improve the performance of distributed computation with the assistance of networked sensing capability, which is named the sensing-empowered integrated communications and computation (ICAC) reciprocity. The above ISAC and ICAC reciprocities can enhance each other iteratively and finally lead to the ICSAC reciprocity. To achieve these reciprocities, we explore the potential enabling technologies for the ICSAC framework. Finally, we present the evaluation results of crucial enabling technologies to show the feasibility of the ICSAC framework.
Keywords: 6G, integrated communication, sensing and computation (ICSAC) framework, integrated sensing and communications (ISAC), integrated communications and computation (ICAC)
1. Introduction
In the future sixth generation (6G) era, intelligent machine network (IMN) applications, such as intelligent vehicular networks, smart cities, and intelligent manufacturing, require intelligent machines (IMs) to possess autonomous environmental perception and collaboration abilities to perform complex tasks such as motion control [1]. To achieve intelligent applications, both communication and sensing capabilities are essential. Moreover, the cooperation among IMs will also enable multiple computation technologies, such as collaborative computing [2]. Integrated sensing and communications (ISAC) technology has already emerged as a promising technique and has been recognized as one of the six key scenarios and technologies for 6G by IMT-2030 [3].
Recently, there have been new trends in wireless networks [4]. For example, there have been studies in exploiting the intelligent computing capability to achieve joint gains between communication and sensing, thereby improving sensing accuracy and communication reliability [5]. Moreover, utilizing networking capabilities to achieve distributed intelligent signal processing, such as federated learning (FL), has also been a promising method to improve computing efficiency and the security of user privacy. These trends indicate the potential for mutual gains among communication, sensing, and computation (CSC) functions [6]. We refer to the signal processing techniques and networking protocols that achieve joint gains among CSC as integrated communication, sensing, and computation (ICSAC) technology.
To support future wireless communications, there are several challenges in achieving 6G IMN applications, which are elaborated as follows:
The scenarios and tasks of 6G are diverse and highly dynamic, especially in IMN scenarios, such as intelligent terrestrial and unmanned aerial vehicular networks, intelligent flexible manufacturing, and smart cities, etc. The dynamic features include highly dynamic channel state information (CSI) due to high mobility (related to sensing information) and rapidly changing network performance requirements due to time-varying task states or application demands [6].
The 6G IMN applications require closed-loop control, which involves a complete application control process, e.g., environmental sensing, sensing information transmission, decision command dissemination, and environmental sensing feedback [6]. The entire closed-loop control process requires high reliability and low latency for each step while minimizing the task completion time.
According to the above main features, the 6G networks naturally require the comprehensive optimization and collaboration of CSC functions to achieve the IMN applications. Nevertheless, for a long time, the sensing, communication, and computation functions have developed individually, which leads to great challenges for 6G network development. Moreover, in order to achieve the precise control involved in the above IMN applications, the 6G applications demand extremely high requirements for communication reliability (10−5 to 10−7), latency (sub-ms level), and sensing accuracy (sub-decimeter level) [3].
Therefore, to solve the above challenges of 6G networks, and meet the aforementioned trends in the ICSAC technology study, the ICSAC framework is proposed in this article to achieve joint gains in communication, sensing, and computation. We conduct an in-depth analysis of CSC functions, elucidating the mechanism of mutual gains in CSC capabilities. This enables the proposed ICSAC framework to be a guiding map for innovations in wireless signal processing. The main innovations of this framework are summarized as follows:
By exploiting the rapidly evolving intelligent computing capabilities to excavate the sensing information with high timeliness as prior information, the ICSAC framework can enhance communication reliability and network routing performance, as well as reduce latency. The enhanced communication networking capabilities further improve the performance of distributed computing architectures. The improvement in computing and communication networking capabilities, in turn, can further enhance the performance of networked sensing.
The joint gains of communication, sensing, and computation in the ICSAC framework are beneficial for meeting the challenge of highly dynamic task requirements of 6G IMN. In particular, ISAC enables simultaneous wireless communication and environmental sensing. The ICSAC network can leverage the sensing information with high timeliness to perform rapid intelligent network optimization using artificial intelligence (AI) technologies such as deep learning (DL) and reinforcement learning (RL). This enables the network to adapt to the rapid changes in the environment and requirements of 6G network scenarios.
The joint gains of CSC in the ICSAC framework can be used in closed-loop control applications. These applications require closed-loop optimization of the sensing information acquisition and transmission, decision-making based on sensing information, decision command dissemination, and environmental sensing feedback. The proper design of CSC functions in the ICSAC framework can comprehensively improve sensing accuracy, communication reliability and latency, and computation efficiency. This enhances the network’s robustness, reduces data retransmission, and decreases the latency in each stage of the closed-loop control application.
According to the above discussion, the ICSAC framework can achieve mutual benefits in CSC functions, enhancing the efficiency and reliability of communication and networking, and improving the accuracy of sensing and computation efficiency. Therefore, it is promising to become one of the mainstream orientations in 6G areas, particularly suitable for the application scenarios that require deep collaboration of communication, sensing, and computation to achieve autonomous control of intelligent machines, such as intelligent vehicular networks, unmanned aerial vehicle networks, intelligent manufacturing, etc.
The remaining parts of this article are arranged as follows. Section 2 introduces the ICSAC framework and its mechanism of achieving joint communication, sensing, and computation gains. Section 3 elaborates on the key enabling technologies and challenges of the ICSAC framework. Section 4 presents the evaluation performance of several key technologies to show the feasibility of the ICSAC framework. Section 5 concludes the entire article and provides an outlook on possible future work.
2. ICSAC Framework
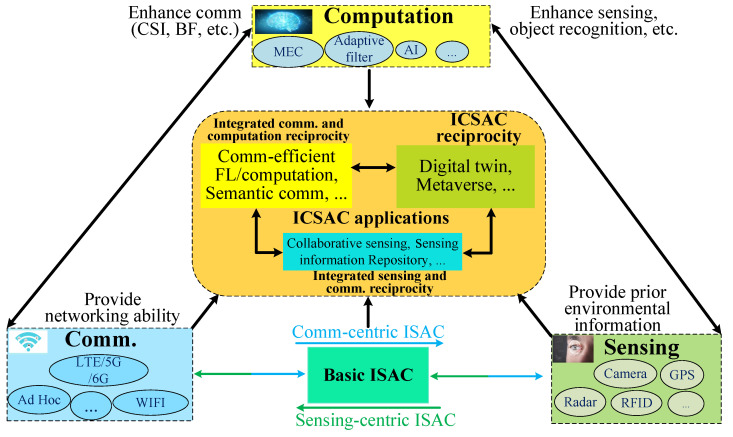
To achieve mutual enhancement among CSC functions and satisfy the requirements of 6G networks for high-reliability and low-latency communication, and high-accuracy sensing, we propose an ICSAC framework, as shown in Figure 1.
Figure 1.
ICSAC framework comprising communication, sensing, and computation functions, where the sensing function perceives the environmental information to provide prior knowledge for communication optimization and application decision-making; the computation function processes the sensing information to generate instructions for controlling actuators; and the communication function links different functions, transmitting data to processors and instructions to actuators.
The CSC functions are analog to human sensing organs, neural systems, and the brain, respectively. The sensing function perceives the environmental information to provide prior knowledge for decision-making. Then, the computation function processes environmental information and generates instruction signals based on application intents to control actuators to interact with the environment. To build the connection between the sensing and computation functions, the communication function transmits the environmental information to computation processors and instructions to the actuators.
Due to the complex intracell and intercell interference in wireless networks, it is necessary to optimize wireless resource allocation and use anti-noise signal processing methods to improve the quality of sensing information acquisition (such as sensing resolution and accuracy) as well as the reliability and capacity of communication. The intelligent computing power enabled by AI technologies, such as DL and RL, will significantly enhance the performance of sensing processing and improve the communication optimization with the assistance of the sensing prior information [7], which is called the computing-empowered ISAC reciprocity. In addition, based on reliable communication links and sensing information, nodes can form networks for distributed computation and cooperative sensing, which is called the sensing-empowered integrated communication and computation (ICAC) reciprocity. The above ISAC and ICAC reciprocities can enhance each other iteratively, leading to the combined ICSAC reciprocity.
Then, we introduce the main techniques of CSC functions and elaborate on the reciprocity among the CSC functions of the ICSAC framework.
2.1. Main Techniques of Communication, Sensing, and Computation
Sensing: We consider the sensing function of machines as ubiquitous spectrum sensing. For example, camera sensors capture physical images from visible-light spectrum information. Moreover, radar sensing can acquire physical information, such as angles, distances, and speeds, based on radio spectrum sensing. Furthermore, GPS can acquire location information. The above sensing information can be collected to form a sensing information repository that provides crucial prior environment knowledge for decision-making and network optimization.
Communication: Wireless communication has various regimes, among which mobile cellular communication networks and WiFi are the most dominant and both adopt the multi-input multi-output orthogonal frequency division multiplex (MIMO-OFDM) transceiver architecture. Wireless communication provides networking capabilities for multiple nodes to collaboratively form distributed systems.
Computation: The computation function is generally diverse. Centralized and distributed computation architectures coexist in a network system. The distributed computing architectures enable local decision-making and edge network optimization. Additionally, AI techniques can provide intelligent processing tools for decision-making, network optimization, and signal processing [8] empowered by prior sensing information.
2.2. ICSAC Framework
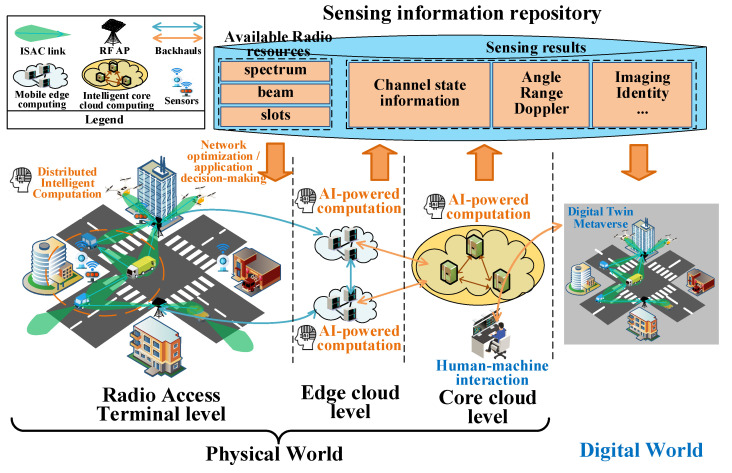
We use a typical application scenario of intelligent ground-air integrated vehicular networks (GAI-VeNet) to illustrate the reciprocities of communication, sensing, and computation in the ICSAC framework, as shown in Figure 2. Note that the vehicles refer to both the unmanned aerial vehicles (UAVs) and unmanned terrestrial vehicles (UTVs). Without the loss of generality, we refer to the vehicles as machine users (MUEs). The ICSAC framework contains two worlds, i.e., the physical world containing all the entities and environment of the networks, and the digital world which is the digital twin of the physical world. The physical world is composed of three levels, i.e., the radio access terminal (RAT) level, edge cloud level, and core cloud level.
Figure 2.
An illustration of the ICSAC framework.
The RAT level contains all the MUEs and access points (APs) in the physical world. Wireless users and APs can utilize ISAC techniques to achieve communication and sensing simultaneously. The wireless sensors also perceive the network environment. The neighbored MUEs or APs can form distributed intelligent computing networks to preprocess the sensing information efficiently. APs can collect the sensing information of MUEs and sensors, upload it to the edge cloud servers, or propagate the action instructions from higher levels to the RAT level.
The edge and core cloud levels are composed of the edge and core cloud server networks, respectively. The edge cloud level controls the operation of local wireless networks and the decision-making for concrete applications such as trajectory planning for the local MUEs. Moreover, the edge cloud level can excavate the sensing data collected from the RAT level and form local sensing information repositories providing prior information for network control and decision-making. The core cloud level converges all the sensing information repositories of edge servers to construct a global one that provides prior information for global network control and application decision-making. Moreover, the core cloud level uses AI techniques to form the digital twin of the physical world based on the global sensing information repository and provides the interaction interface to human users (HUEs) for human-machine interaction over the digital metaverse.
2.3. Reciprocity among the Communication, Sensing, and Computation Capabilities
We proceed to elaborate on the reciprocity among the communication, sensing, and computation achieved by the above ICSAC framework.
2.3.1. Computing-Empowered ISAC Reciprocity
The convergence of radio communication and sensing in terms of spectrum, transceivers, and digital signal processing lays the foundation for the hardware implementation of ISAC. ISAC achieves single-base active sensing by processing the autocorrelation between communication signal echoes and transmitted signals or achieves bi-static sensing by processing the received communication signals [9].
The communication networking capability can be utilized to realize networked sensing for ISAC nodes or sensors, which can efficiently solve insufficient sensing problems, such as obstruction in the single-node sensing scenario. Due to the diversity of the resources of sensing information, the obtained sensing information exhibits significant multi-modal characteristics. Specifically, the angles, locations, velocities of MUEs and environmental scatterers, CSI estimation, images, etc., are aggregated via the communication network at both the edge and core cloud levels, forming local and global sensing information repositories, respectively. CSIs, user locations, velocities, and other related information are useful for communication network optimization and application decision-making.
2.3.2. Sensing-Empowered ICAC Reciprocity
By exploiting communication networking capabilities, multiple nodes can collaborate to train distributed neural networks or other distributed computing architectures. Distributed learning enhances the efficiency and scalability of the training process, which is especially useful when dealing with massive datasets that would be impractical to transfer and process centrally. Since each network node is trained using its local data and only transmits model parameters without exposing the private data, distributed computing architectures can protect user data privacy and security.
There can be parallel multi-tasking requirements in the local computing network, such as the simultaneous transmission of sensing data and the relay of user communication data. In such cases, distributed intelligent computing can intelligently assign priorities of different tasks to each computing node based on the CSI estimation and the locations of information source and destination contained in the sensing information repository, thereby enhancing the efficiency of parallel task completion. Moreover, by using the semantic characteristics hidden within CSIs, transmitted signals, and sensing results, the intentions of machine applications can be disseminated more efficiently among MUEs, omitting the process of extracting human-type semantics based on sensing data for application control.
2.3.3. ICSAC Reciprocity
Intelligent computing technologies such as neural networks can be exploited to enhance the anti-noise performance of communication and sensing, improving CSI estimation accuracy, communication reliability, and sensing accuracy. By utilizing the enhanced MUEs’ location and CSI information as prior information, intelligent computing methods such as DL and RL can be used to improve the performance of network resource allocation, routing, beamforming, etc. The improvement in communication performance will further provide better reliability, capacity, and timeliness for networked sensing and distributed intelligent computation, thus achieving iterative ICSAC gain, which is beneficial for closed-loop applications that require low latency and high reliability.
By exploiting AI techniques to digest and enhance the multi-source sensing data, a high-quality digital twin can be achieved based on the global sensing information repository, which lays the foundation for realizing a highly immersive metaverse for HUEs.
3. Key Enabling Technologies and Main Challenges
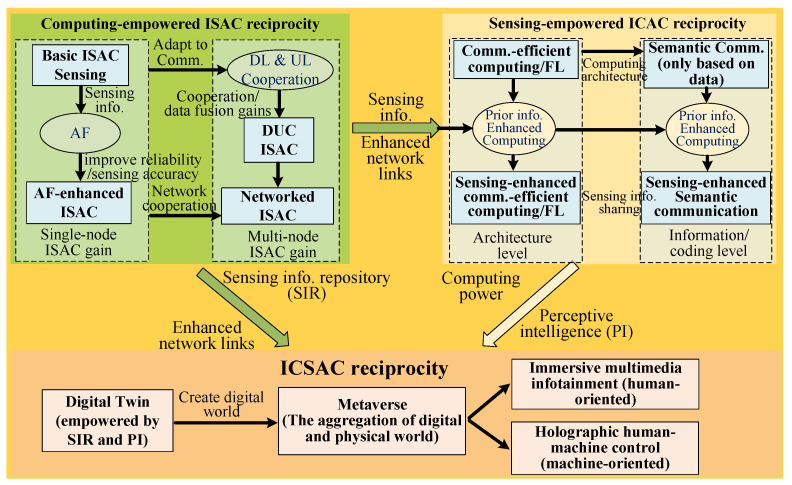
This section explores the key technologies and the corresponding main challenges for realizing the aforementioned reciprocity of the ICSAC framework, including the computing-empowered ISAC, sensing-empowered ICAC, and ICSAC techniques, which are outlined in Figure 3. The computing-empowered ISAC techniques offer sensing information and enhanced network links for realizing sensing-empowered ICAC and ICSAC techniques, while the sensing-empowered ICAC techniques provide computing architectures and perceptive intelligence for achieving the ICSAC techniques.
Figure 3.
The illustration of the potential enabling technologies for the ICSAC framework.
3.1. Computing-Empowered ISAC Techniques
This subsection presents the crucial techniques for achieving computing-empowered ISAC reciprocity in Section 2.2. We first introduce the basic ISAC sensing scheme and then elaborate on the adaptive filter (AF)-enhanced CSI enhancer for ISAC, downlink uplink cooperative (DUC) ISAC, and computing-empowered networked sensing.
3.1.1. Review of Basic ISAC Sensing Scheme
As both 6G and WiFi will adopt the MIMO-OFDM-based regimes in the future, we focus on the MIMO-OFDM-based ISAC sensing scheme. The most prevalent ISAC sensing scheme is the fast Fourier transform (FFT)-based sensing scheme that applies two-dimensional FFT (2D-FFT) to obtain the sensing spectrum for estimating range and Doppler [10]. This method has the lowest complexity, but its on-grid detection nature restricts its sensing accuracy by the range and Doppler resolutions defined by the number of subcarriers and OFDM symbols, respectively. Moreover, zero-padding FFT could alleviate this problem but introduce a large complexity increase. The subspace-based ISAC sensing scheme based on the super-resolution sensing method, such as multiple signal classification (MUSIC), can improve the sensing accuracy but with relatively high complexity when jointly estimating 2D range and Doppler [11]. The maximum likelihood estimation (MLE)-based ISAC sensing method was also proposed to estimate the range and velocity of scattering targets [12]. However, this method has to search the sensing results from an extremely large range of parameters, and the complexity increases exponentially with the increase in the number of sensing parameters. Moreover, the compressive sensing (CS)-based ISAC sensing method was also researched for achieving off-grid sensing estimation [13]. However, the sensing performance and complexity of this method will degrade rapidly with the increase in the number of sensing parameters.
Until now, the research on ISAC techniques for mobile networks mainly focuses on the achievement of sensing signal processing via individual downlink and uplink communication signals. Nevertheless, the communication performance improvement and cooperation of downlink and uplink communication processes have not been efficiently researched yet. Therefore, we further proposed the following key potential techniques for computing-empowered ISAC techniques to improve communication performance and exploit the networking features of communication networks.
3.1.2. AF-Enhanced ISAC
AF, such as the Kalman filter, Bayesian filter, and deep learning-based filter, can be used to enhance the CSI estimation for improving communication reliability by exploiting the angle-of-arrival (AoA), range, and Doppler estimation as the prior information, as well as suppressing the timing offset (TO) in the CSI to improve sensing accuracy by exploiting the Doppler estimation with carrier frequency offset (CFO) as the prior information [14]. This method can improve both communication and sensing performance significantly with the feature of linearity and is thus promising to be implemented in the ICSAC framework for 6G.
3.1.3. DUC ISAC
In mobile communication networks, the uplink (UL) and downlink (DL) channels between AP and MUE have time-division duplex (TDD) reciprocity. Within adjacent uplink and downlink time slots, the channel environment between the AP and UE remains unchanged. The active sensing conducted by AP in the downlink time slots and the bi-static sensing in the uplink time slots are independent sensing processes of the same physical environment. Therefore, we can improve the sensing performance via data fusion methods and enhance communication performance by exploiting the sensing information obtained in uplink and downlink ISAC as prior information [15].
3.1.4. Computing-Empowered Networked ISAC
By exploiting networked collaboration capabilities, multiple distributed sensors (including MUEs and APs that use ISAC) can cooperatively sense the same physical area, effectively reducing blind spots caused by obstruction and random deep fading in the single-sensor scenario [16]. Using distributed computing such as FL, collaborative MUEs can conduct distributed training, where they only need to exchange model parameters to share semantic information, thereby improving the efficiency of the sensing network and ensuring the security of data.
Challenges to the Computing-empowered ISAC techniques: 6G networks may encounter extremely dynamic scenarios characterized by rapidly changing environments. Therefore, all the above techniques necessitate the acquisition of sensing information with exceptional timeliness. Moreover, effective interference management and synchronization for networked sensing are also great challenges.
3.2. Sensing-Empowered ICAC Technique
This subsection presents the critical technique for realizing the ICAC reciprocity in Section 2.2, including the sensing-enhanced communication-efficient FL enhanced by semantic communications, which can achieve perceptive intelligence.
3.2.1. Review of the Typical ICAC Technique
We focus on reviewing the most typical ICAC technique, i.e., FL, to illustrate the challenges in the development of the ICAC techniques. FL provides a new way to protect user privacy and reduce communication costs. The core idea of FL is to keep data at the local servers and only share model parameters or updates among users [17]. Due to its lightweight deployment scheme, FL has become the mainstream solution and product choice in many privacy computing application scenarios. FL techniques can achieve multiple federated agencies to build a unified machine learning model among the safe and efficient multi-source data systems [18]. However, with the explosive increase in privacy computing platforms, the number of FL devices put into practical application gradually increases, the main bottleneck for the current FL technique is the huge communication overhead in optimizing and deploying the FL framework [19].
3.2.2. Sensing-Enhanced Communication-Efficient FL
Multiple collaborative intelligent MUEs can form a network for computing, where the network nodes collaborate to train neural networks by sharing model parameters without exposing private data [2]. The key issue is efficiently training neural network models while fully exploiting the communication performance and computational power among nodes. In the ICSAC architecture, networked sensing provides sensing information repositories. Exploiting the prior information on the positions of MUEs and CSI estimation, distributed MUEs can quickly select cooperative nodes with better communication quality for collaborative training, reducing control overhead and application latency. Moreover, with the sensing results, FL can be used for resource allocation predictions for solving wireless communication problems.
On the other hand, neural networks, auto-encoders/decoders, and other related techniques can extract the compressed model information as semantic features, and the goal is to maximize the semantic information while minimizing the data size [2]. In machine-type applications, motion control is a prominent requirement. Suppose the position, velocity, and posture information of the information source and sink MUEs can be integrated into the semantic extraction process. In that case, there is the potential to generate higher-efficiency semantic information for FL optimization and machine motion control.
Challenges to the Sensing-empowered ICAC Techniques: The accuracy, coverage, and timeliness of sensing information significantly impact the above sensing-empowered ICAC techniques. Ensuring timely and comprehensive updates of sensing information is a challenging issue to address. Moreover, the efficient exploitation of the communication network performance for distributed computing is also a great challenge in the highly dynamic environment.
3.3. ICSAC Techniques
Finally, we present the crucial techniques for achieving the ICSAC reciprocity mentioned in Section 2.3. As discussed above, the computing-empowered ISAC and sensing-empowered ICAC techniques can cooperatively obtain the local and global sensing information, construct communication and computing networks, and enhance their efficiency by exploiting the sensing information as the prior information. Based on the sensing information repository and the communication and computing infrastructures, the digital twin and metaverse can be enabled [20,21].
3.3.1. Digital Twin
Based on the computing-empowered ISAC and sensing-empowered ICAC techniques mentioned in Section 3.1 and Section 3.2, MUEs and APs can cooperate to obtain sensing data with high timeliness using networked sensing and preprocess the distributed sensing data with distributed computing, which can be aggregated and updated hierarchically at the edge cloud and core cloud levels, forming a global sensing information repository that contains information for constructing virtual models of physical entities. Therefore, based on the sensing information repository, we can utilize AI techniques embedded in the distributed or central ICAC computing infrastructures to build a digital virtual world corresponding to the physical world, enabling the realization of digital twin technology [22].
3.3.2. Metaverse
The high-fidelity digital world formed by digital twins can provide interfaces for intelligent interaction with humans. After semantic compilation, human instruction can interact with the digital twin world. Humans can collaborate or communicate in the digital world or conduct remote tasks via AI agents in the digital world. AI agents can generate network control signals based on human-machine interaction instructions to remotely operate the IMs through the ICSAC network infrastructure, enabling them to change the environment in the physical world. Moreover, based on the huge sensing information repository aggregated at the core cloud, the core cloud can use a generative adversarial network (GAN) or large pre-training model (LPTN) to generate synthetic media information for HUEs to enhance the experience of 6G immersive multimedia applications, such as holographic interactions [23].
3.3.3. Embodied Intelligence
Embodied intelligence refers to intelligent entities that have physical carriers and support physical interactions [24]. They are capable of multi-modal perception and interaction with the environment similar to humans, and possess autonomous planning, decision-making, and action abilities. The sensing information repositories provided by edge cloud and core cloud offer massive data for the training and evolution of embodied intelligent entities. The communication networking capabilities provide multi-agent collaboration and distributed computing capabilities, enabling the collaborative evolution of multiple embodied intelligent agents.
Challenges to the ICSAC Techniques: The interaction between the digital world and the physical world requires high timeliness and data reliability to ensure the realism of the digital world and guarantee user experience. Additionally, it is necessary to significantly enhance the security and privacy of network access to ensure the security of human-machine interaction in the real world [25].
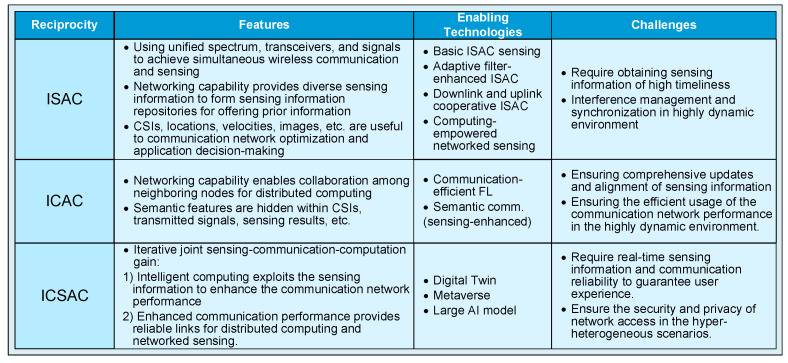
Finally, the features, enabling technologies, and challenges for achieving the aforementioned ISAC, ICAC, and ICSAC reciprocity are summarized in Figure 4.
Figure 4.
The key enabling technologies and challenges corresponding to the reciprocity of the ICSAC framework.
4. Evaluation Results
In this section, we present the evaluation results of several typical enabling technologies mentioned above to demonstrate the feasibility of the ICSAC framework.
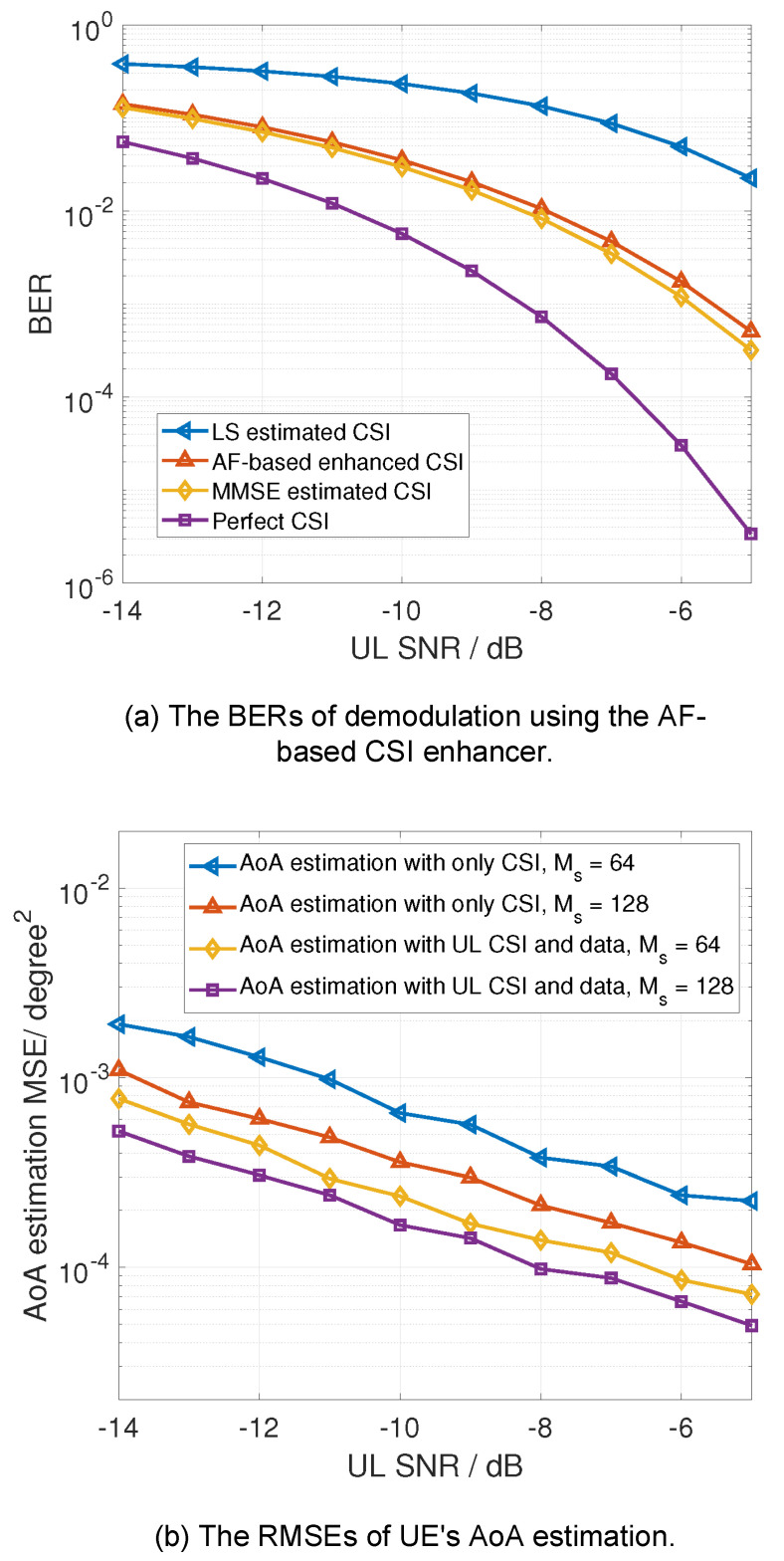
Figure 5 presents the mutual communication and sensing performance enhancement using the computing-empowered ISAC techniques in Section 3.1. Figure 5a presents the bit error rate (BER) performance of demodulation using the AF-based CSI enhancer mentioned in Section 3.1, which is one of the typical computing-empowered ISAC techniques. The least-square (LS) and minimum mean square error (MMSE) methods are adopted as the comparison methods to show the improvement of the proposed computing-empowered ISAC techniques. The AF-based CSI enhancer exploits the AoA sensing results as prior information to improve the CSI estimation accuracy. Figure 5b further presents the AoA estimation performance enhancement using the combined CSI estimation and the demodulated data signals enhanced by the AF-based CSI enhancer. The simulation settings for the results of Figure 5 are as follows. The OFDM signal is adopted. The subcarrier interval is 480 kHz, the number of used subcarriers is 256, the number of OFDM packets is 64, the frequency of the carrier is 28 GHz, the array size of the receiver (base station) is , and the array size of the transmitter (user equipment) is .
Figure 5.
The mutual communication and sensing performance enhancement. (a) The BER performance is enhanced by the AF-based CSI enhancer. (b) The AoA sensing performance is improved by using the combined UL CSI estimation and received data signals that are enhanced by the AF-based CSI enhancer.
Figure 5a shows that the AF-based enhancer requires about 3.5 dB lower signal-to-noise ratio (SNR) than the LS method, but 0.2 dB higher SNR than the MMSE method to achieve the given BER. This verifies that communication reliability can be improved with the assistance of sensing results via typical computing techniques. With the enhanced communication reliability, Figure 5b shows that the MSEs of AoA estimation based on the combined CSI and received data signals are lower than those only based on pure CSI estimation. Moreover, the larger number of packets, , results in lower AoA estimation MSEs. This is because a larger number of symbols can accumulate more effective energy for sensing. Specifically, the improved BER performance enhances the accuracy of data decoding, which further improves the estimation of correlation between the received data signals and the decoded data, thus improving the AoA estimation performance.
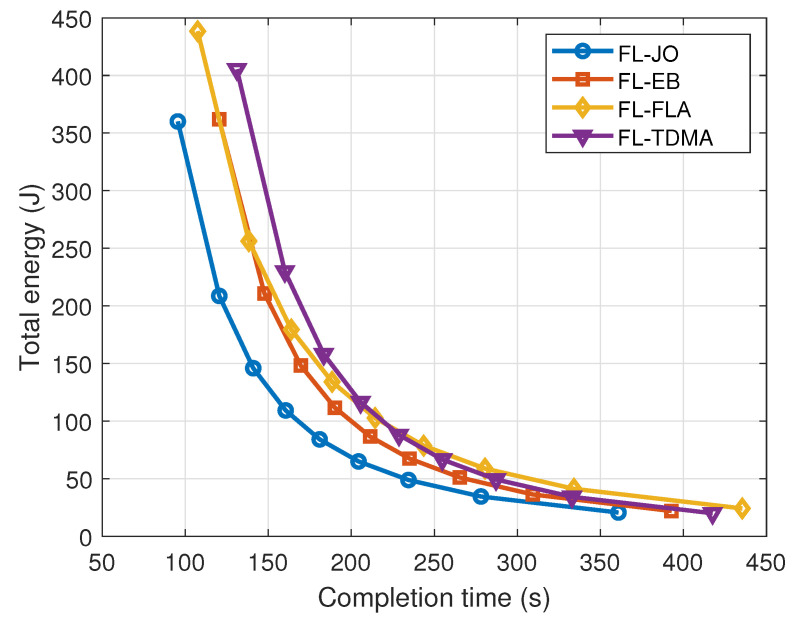
The performance of the communication-efficient FL mentioned in Section 3.2 is shown in Figure 6, where the total energy consumption versus the completion time for various FL resource allocation schemes for sensing is provided. ‘FL-JO’ stands for the FL with joint optimization of bandwidth and localization accuracy of the sensing tasks, ‘FL-EB’, ‘FL-FLA’, and ‘FL-TDMA’ stand for the schemes with equal bandwidth allocation for multiple users, with fixed localization accuracy of the sensing task, and with users using TDMA, respectively.
Figure 6.
Total energy versus the completion time for various FL resource allocation schemes. ‘FL-JO’ stands for the FL with joint optimization of bandwidth and localization accuracy of the sensing tasks, ‘FL-EB’, ‘FL-FLA’, and ‘FL-TDMA’ stand for the schemes with equal bandwidth allocation for multiple users, with fixed localization accuracy of the sensing task, and with users using TDMA, respectively.
In Figure 6, there are 50 users to perform FL, which are uniformly distributed in a circle area with a radius of 500 m. The wireless user location sensing dataset is adopted with 60,000 data samples. The maximum average transmit power of each user is 10 dBm and the computation capacity of each user is 2 GHz. The total energy/time includes the parts for both communication and computation. It is shown that the total energy decreases as the total completion time increases. This is because a long completion time can ensure a small transmit and computation power, thus reducing the total system energy. Moreover, FL-JO achieves the best performance, since the server can select the set of users with high communication channel gain, which can enhance the efficiency of communication-efficient FL based on the sensing information including the users’ locations and CSI estimation results.
5. Conclusions
In this article, we have proposed an ICSAC framework for 6G to realize the reciprocity among CSC functions to enhance the communication reliability and latency, timeliness and accuracy of sensing information acquisition, and privacy and security of computing to support the IMN and immersive applications. Furthermore, we have elaborated on the potential enabling technologies and outlined the corresponding challenges to achieve them. Evaluation results show the feasibility of the proposed enabling technologies. This article has drawn a blueprint for innovations of 6G IMN systems. In the future, the efficient algorithms that can exploit the reciprocity of CSC functions to enhance the overall performance and the theoretical bounds for CSC performance are the fundamental problems to be resolved.
Author Contributions
Conceptualization, X.C., Z.F. and Z.Y.; methodology, X.C., Z.F., Z.Y. and J.A.Z.; resources, X.C. and Z.Y.; writing—original draft preparation, X.C.; writing—review and editing, X.C., Z.Y., J.A.Z., X.Y., X.H. and P.Z.; supervision, Z.F. and P.Z.; project administration, Z.F.; funding acquisition, Z.F. All authors have read and agreed to the published version of the manuscript.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflict of interest.
Funding Statement
This research was supported by the National Key Research and Development Program of China under Grants {2020YFA0711302, and 2020YFA0711303}.
Footnotes
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
References
- 1.You X., Wang C.X., Huang J., Gao X., Zhang Z., Wang M., Huang Y., Zhang C., Jiang Y., Wang J., et al. Towards 6G wireless communication networks: Vision, enabling technologies, and new paradigm shifts. Sci. China Inf. Sci. 2021;64:110301. doi: 10.1007/s11432-020-2955-6. [DOI] [Google Scholar]
- 2.Xu W., Yang Z., Ng DW K., Levorato M., Eldar Y.C., Debbah M. Edge learning for B5G networks with distributed signal processing: Semantic communication, edge computing, and wireless sensing. IEEE J. Sel. Top. Signal Process. 2023;17:9–39. doi: 10.1109/JSTSP.2023.3239189. [DOI] [Google Scholar]
- 3.ITU Radiocommunication Study Groups . Framework and Overall Objectives of the Future Development of IMT for 2030 and Beyond. Electronic Publication; Geneva, Switzerland: 2023. [Google Scholar]
- 4.Liu F., Masouros C., Petropulu A.P., Griffiths H., Hanzo L. Joint radar and communication design: Applications, state-of-the-art, and the road ahead. IEEE Trans. Commun. 2020;68:3834–3862. doi: 10.1109/TCOMM.2020.2973976. [DOI] [Google Scholar]
- 5.Zong B., Fan C., Wang X., Duan X., Wang B., Wang J. 6G Technologies: Key Drivers, Core Requirements, System Architectures, and Enabling Technologies. IEEE Veh. Technol. Mag. 2019;14:18–27. doi: 10.1109/MVT.2019.2921398. [DOI] [Google Scholar]
- 6.Feng Z., Wei Z., Chen X., Yang H., Zhang Q., Zhang P. Joint Communication, Sensing, and Computation Enabled 6G Intelligent Machine System. IEEE Netw. 2021;35:34–42. doi: 10.1109/MNET.121.2100320. [DOI] [Google Scholar]
- 7.Zhang Z., Xiao Y., Ma Z., Xiao M., Ding Z., Lei X., Karagiannidis G.K., Fan P. 6G Wireless Networks: Vision, Requirements, Architecture, and Key Technologies. IEEE Veh. Technol. Mag. 2019;14:28–41. doi: 10.1109/MVT.2019.2921208. [DOI] [Google Scholar]
- 8.Elbir A.M., Mishra K.V., Shankar M.B., Ottersten B. A Family of Deep Learning Architectures for Channel stimation and Hybrid Beamforming in Multi-Carrier mm-Wave Massive MIMO. IEEE Trans. Cogn. Commun. Netw. 2022;8:642–656. doi: 10.1109/TCCN.2021.3132609. [DOI] [Google Scholar]
- 9.Liu B., Zhang Q., Jiang Z., Xue D., Xu C., Wang B., Peng J. Architecture for cellular enabled integrated communication and sensing services. China Commun. 2023;20:59–77. doi: 10.23919/JCC.fa.2023-0155.202309. [DOI] [Google Scholar]
- 10.Sturm C., Wiesbeck W. Waveform design and signal processing aspects for fusion of wireless communications and radar sensing. Proc. IEEE. 2011;99:1236–1259. doi: 10.1109/JPROC.2011.2131110. [DOI] [Google Scholar]
- 11.Liu Y., Liao G., Chen Y., Xu J., Yin Y. Super-resolution range and velocity estimations with OFDM integrated radar and communications waveform. IEEE Trans. Veh. Technol. 2020;69:11659–11672. doi: 10.1109/TVT.2020.3016470. [DOI] [Google Scholar]
- 12.Grossi E., Lops M., Venturino L., Zappone A. Opportunistic Radar in IEEE 802.11ad Networks. IEEE Trans. Signal Process. 2018;66:2441–2454. doi: 10.1109/TSP.2018.2813300. [DOI] [Google Scholar]
- 13.Rahman M.L., Zhang J.A., Huang X., Guo Y.J., Heath R.W. Heath Framework for a Perceptive Mobile Network Using Joint Communication and Radar Sensing. IEEE Trans. Aerosp. Electron. Syst. 2020;56:1926–1941. doi: 10.1109/TAES.2019.2939611. [DOI] [Google Scholar]
- 14.Chen X., Feng Z., Zhang J.A., Yuan X., Zhang P. Kalman Filter-based Sensing in Communication Systems with Clock Asynchronism. IEEE Trans. Commun. 2024;72:403–417. doi: 10.1109/TCOMM.2023.3318594. [DOI] [Google Scholar]
- 15.Ouyang C., Liu Y., Yang H. Performance of Downlink and Uplink Integrated Sensing and Communications (ISAC) Systems. IEEE Wirel. Commun. Lett. 2022;11:1850–1854. doi: 10.1109/LWC.2022.3184409. [DOI] [Google Scholar]
- 16.Jiang W., Wei Z., Li B., Feng Z., Fang Z. Improve Radar Sensing Performance of Multiple Roadside Units Cooperation via Space Registration. IEEE Trans. Veh. Technol. 2022;71:10975–10990. doi: 10.1109/TVT.2022.3184182. [DOI] [Google Scholar]
- 17.Liu Y., Yuan X., Xiong Z., Kang J., Wang X., Niyato D. Federated learning for 6G communications: Challenges, methods, and future directions. China Commun. 2020;17:105–118. doi: 10.23919/JCC.2020.09.009. [DOI] [Google Scholar]
- 18.Li A., Zhang L., Wang J., Han F., Li X.Y. Privacy-Preserving Efficient Federated-Learning Model Debugging. IEEE Trans. Parallel Distrib. Syst. 2022;33:2291–2303. doi: 10.1109/TPDS.2021.3137321. [DOI] [Google Scholar]
- 19.Wen J., Zhang Z., Lan Y., Cui Z., Cai J., Zhang W. A survey on federated learning: Challenges and applications. Int. J. Mach. Learn. Cyber. 2022;14:513–535. doi: 10.1007/s13042-022-01647-y. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 20.Qi Q., Tao F., Hu T., Anwer N., Liu A., Wei Y., Wang L. Nee Enabling technologies and tools for digital twin. J. Manuf. Syst. 2021;58:3–21. doi: 10.1016/j.jmsy.2019.10.001. [DOI] [Google Scholar]
- 21.Chen Z., Gan W., Wu J., Lin H., Chen C.M. Metaverse for smart cities: A survey. Internet Things Cyber-Phys. Syst. 2024;4:203–216. doi: 10.1016/j.iotcps.2023.12.002. [DOI] [Google Scholar]
- 22.Nguyen H.X., Trestian R., To D., Tatipamula M. Digital Twin for 5G and Beyond. IEEE Commun. Mag. 2021;59:10–15. doi: 10.1109/MCOM.001.2000343. [DOI] [Google Scholar]
- 23.Liu Y., Shen Y., Guo C., Tian Y., Wang X., Zhu Y., Wang F.Y. MetaSensing in Metaverses: See There, Be There, and Know There. IEEE Intell. Syst. 2022;37:7–12. doi: 10.1109/MIS.2022.3221844. [DOI] [Google Scholar]
- 24.Duan J., Yu S., Tan H.L., Zhu H., Tan C. A Survey of Embodied AI: From Simulators to Research Tasks. IEEE Trans. Emerg. Top. Comput. Intell. 2022;6:230–244. doi: 10.1109/TETCI.2022.3141105. [DOI] [Google Scholar]
- 25.Kang G., Koo J., Kim Y.G. Kim Security and Privacy Requirements for the Metaverse: A Metaverse Applications Perspective. IEEE Commun. Mag. 2024;62:148–154. doi: 10.1109/MCOM.014.2200620. [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Data are contained within the article.