Abstract
With the rapid development of artificial intelligence and Internet of Things (IoT) technologies, automotive companies are integrating federated learning into connected vehicles to provide users with smarter services. Federated learning enables vehicles to collaboratively train a global model without sharing sensitive local data, thereby mitigating privacy risks. However, the dynamic and open nature of the Internet of Vehicles (IoV) makes it vulnerable to potential attacks, where attackers may intercept or tamper with transmitted local model parameters, compromising their integrity and exposing user privacy. Although existing solutions like differential privacy and encryption can address these issues, they may reduce data usability or increase computational complexity. To tackle these challenges, we propose a conditional privacy-preserving identity-authentication scheme, CPPA-SM2, to provide privacy protection for federated learning. Unlike existing methods, CPPA-SM2 allows vehicles to participate in training anonymously, thereby achieving efficient privacy protection. Performance evaluations and experimental results demonstrate that, compared to state-of-the-art schemes, CPPA-SM2 significantly reduces the overhead of signing, verification and communication while achieving more security features.
Keywords: federated learning, Internet of Vehicles, authentication, certificateless-based cryptography
1. Introduction
With the rapid development of intelligent transportation systems and Internet of Things (IoT) technology, the Internet of Vehicles (IoV) has become an essential component of smart cities [1]. IoV enables real-time sharing of traffic information and intelligent coordination of vehicles through communication between vehicles and between vehicles and infrastructure. Additionally, with the advancement of machine learning technology, many automotive companies are leveraging machine learning in the IoV to provide more intelligent and efficient services to users [2]. By collecting a large amount of vehicle data to train models, they offer applications such as autonomous driving and traffic flow prediction [3]. However, traditional centralized model training requires gathering vehicle data to the central server for training. Since this vehicle data often contains a significant amount of personal information, such as driving habits, travel routes, home and work locations, many users are concerned about privacy breaches and are reluctant to send their data to the central server [4]. Moreover, recent data security regulations prohibit automotive companies from collecting user data without authorization. To address these privacy concerns, federated learning (FL) has emerged as a solution [5]. FL is a decentralized machine learning approach where multiple clients (such as smartphones, vehicles or other devices) collaboratively train a shared model under the orchestration of a central server while keeping the data localized [6]. Instead of sending raw data to a central server, each client processes the data locally and only shares the model updates (like gradients or parameters) with the central server. The server then aggregates these updates to form a global model. Currently, FL has been widely applied in various IoV scenarios, such as trajectory prediction, advanced driver-assistance systems and traffic flow prediction and management [7].
Although FL addresses the issue of data silos, researchers have found that without proper protection of the transmitted model parameters, attackers can still infer privacy information about user data [8]. Additionally, during the aggregation of parameters by the central server, there is a risk that the server may attempt to infer original data information from the uploaded model parameters. Moreover, due to the open nature of the IoV, attackers can easily eavesdrop on and manipulate messages transmitted between vehicles, gaining access to the vehicles’ real identities and further tracking their behaviors, posing a threat to user privacy [9].
To address the issue of privacy leakage in federated learning, existing solutions are mainly categorized into differential privacy (DP) [10,11,12] and encryption techniques [13,14,15,16,17,18]. DP protects the privacy of original data by adding random noise to model parameters. Wei et al. [10] proposed a differential privacy-based federated learning framework, which achieves different levels of differential privacy protection by adding artificial noise to client parameters before aggregation. Zhao et al. [11] combined DP with federated learning, proposing four localized differential privacy mechanisms to perturb gradients generated by vehicles, thereby preventing privacy leakage. Zhou et al. [12] achieved high-level privacy protection by adding noise and theoretically proved the convergence of their algorithm. Although DP-based solutions have been extended to all machine learning algorithms in deep learning, the added random noise can degrade model accuracy and extend the model convergence time. Encryption-based solutions can be divided into homomorphic encryption and secure multiparty computation (SMC). Zhou et al. [13] combined differential privacy, blinding and Paillier homomorphic encryption to resist model attacks and achieve secure aggregation of model parameters. Ma et al. [14] proposed a dual-trapdoor homomorphic encryption scheme, ShieldFL, which can defend against model poisoning attacks and protect privacy. They also introduced a secure cosine similarity method for Byzantine-robust aggregation. Hijazi et al. [15] introduce four different fully homomorphic encryption (FHE)-based methods for FL, which securely transmit model parameters in encrypted form, thereby enhancing robust privacy and security protection. Zhang et al. [16] present a lightweight dual-server secure aggregation protocol based on secret sharing, achieving both privacy protection and Byzantine robustness. A typical example is secret sharing. This method reduces computational overhead compared to homomorphic encryption but increases the number of communication rounds and communication overhead, thereby hindering the training efficiency of federated learning. Furthermore, encryption-based solutions prevent the cloud server from directly accessing plaintext local model parameters during aggregation. This hinders integration with Byzantine-robust federated learning defense mechanisms [17,18], as existing Byzantine-robust defense mechanisms focus on computing similarities directly on plaintext model parameters. Therefore, it is necessary to research a privacy-preserving federated learning solution suitable for the IoV that can balance efficiency and practicality.
To ensure the authenticity and integrity of communication data in the IoV, many identity-authentication protocols have been proposed [19]. Currently, existing identity-authentication protocols in the IoV can be primarily categorized into three types: public key infrastructure-based (PKI-based) [20], identity-based (ID-based) [21,22,23,24] and certificateless-based [25,26,27,28]. PKI-based identity-authentication protocols bind a vehicle’s identity to its public key through digital certificates. Vehicles use their private keys to sign messages, and verifiers use the public keys from the vehicle’s digital certificates to verify the signatures. The main drawback of this method is the significant storage and maintenance overhead associated with managing a large number of digital certificates and certificate revocation lists. Identity-based authentication protocols directly use the vehicle’s identity information as the public key, thereby avoiding the overhead of certificate management and maintenance. Zhao et al. [22] proposed an identity-based federated learning collaborative authentication protocol for shared data, achieving efficient anonymous authentication and key agreement between vehicles and other entities. Zhang et al. [23] proposed an ID-based conditional privacy-preserving identity-authentication scheme that does not require bilinear pairings or hash-to-point operations, enabling efficient vehicle authentication. Kanchan et al. [24] proposed a federated learning algorithm based on group signatures, enhancing the protection of node identities. Although ID-based identity-authentication schemes can achieve efficient vehicle authentication, they have the issue of key escrow. Therefore, certificateless identity-authentication schemes have been proposed as a promising solution. However, this approach has a key escrow problem, as the Trusted Authority (TA) has full control over the vehicle’s private keys and can generate legitimate signatures for any vehicle. To address the key escrow issue, certificateless authentication protocols have been proposed. In these protocols, a vehicle’s private key consists of two parts: one part is a secret value selected by the vehicle itself, and the other part is a partial private key generated by TA. Lin et al. [25] proposed a certificateless authentication and key agreement protocol for IoV based on blockchain. This protocol utilizes the decentralized architecture of blockchain to achieve decentralized trusted third-party services, thus mitigating issues such as single-point failure and the risk of trusted third-party disclosure. It aims to achieve efficient authentication between vehicles. Jiang et al. [26] proposed a certificateless anonymous identity-authentication scheme, which aims to anonymize the relationship between terminal identities and data. However, the use of bilinear pairing operations affects authentication efficiency. Ma et al. [27] extended Jiang’s work by proposing a certificateless identity-authentication scheme that does not require bilinear pairing operations and supports batch verification. However, this scheme lacks dynamic member-management capabilities, and the pseudonyms generated by vehicles cannot be dynamically updated. Currently, most existing certificateless authentication protocols use bilinear pairing operations or do not support batch verification, leading to low authentication efficiency. Additionally, most certificateless authentication protocols are independently designed and are not integrated with existing international standard cryptographic algorithms, making them inconvenient for practical application and widespread adoption. Therefore, it is necessary to study an efficient authentication protocol to establish a secure communication environment for the IoV.
To address the aforementioned challenges, we propose a conditional privacy-preserving authentication scheme called CPPA-SM2, which provides secure authentication and privacy protection for vehicle communication and federated learning in the IoV. Specifically, it is based on the fact that if vehicles send messages and participate in training anonymously, even if attackers or the cloud server obtain the plaintext local model parameters and infer some data information, they cannot associate this information with a specific real vehicle identity, thus achieving privacy protection. Our main contributions are as follows:
We propose a Conditional Privacy-Preserving Authentication scheme, CPPA-SM2, and integrate it with federated learning. Vehicles participate in federated learning training anonymously, obfuscating the link between local model parameters and the vehicle’s real identity, thus achieving privacy protection. Unlike existing privacy-preserving federated learning schemes, it does not require time-consuming encryption operations or add random noise that affects model performance. It maintains the efficiency of federated learning and has the potential to be integrated with Byzantine-robust defense mechanisms.
CPPA-SM2 is a certificateless identity-authentication scheme based on Elliptic Curve Cryptography, SM2 and the Chinese Remainder Theorem. It can verify the authenticity and integrity of the local model parameters uploaded by vehicles and supports batch verification. Unlike existing certificateless identity-authentication schemes, it integrates with the standard SM2 digital signature algorithm, facilitating practical application. Dynamic member management is achieved through the Chinese Remainder Theorem. When a malicious vehicle is detected in the system, TA can use the system master secret key to trace its real identity and then revoke it from the federated learning system.
We conducted a security proof and an informal security analysis of the CPPA-SM2 scheme. Additionally, we evaluated its performance through experiments and compared it with other schemes. The experimental results show that CPPA-SM2 can achieve efficient and secure authentication for vehicles while providing privacy protection for federated learning.
The remainder of this paper is organized as follows. Section 2 presents the notation definitions, mathematical background, system model, threat model, security model and design objectives. Section 3 details the implementation of the CPPA-SM2 scheme. Section 4 provides the correctness and security proof of the CPPA-SM2 scheme along with an informal security analysis. Section 5 evaluates the performance of the CPPA-SM2 scheme and compares it with other schemes. Section 6 concludes the paper.
2. Preliminaries
In this section, we mainly introduce the preliminary knowledge, system model, threat model, security model and design goals. The relevant symbols used in this paper are explained in Table 1.
Table 1.
Notations and definitions used.
| Notations | Definition |
|---|---|
| Security parameter | |
| System master secret key | |
| System public key | |
| TA’s public and private key pair | |
| RSU’s public and private key pair | |
| The -th vehicle | |
| Group key | |
| Group public key | |
| ’s full public key | |
| ’s full private key | |
| ’s secret key | |
| ’s real identity | |
| An pseudo-identity of vehicle | |
| Current timestamp | |
| Arrival time | |
| The validity period of the pseudo-identity | |
| The validity period of the group key | |
| Five one-way hash functions | |
| Concatenation operation | |
| Signature algorithm | |
| in round | |
| in round | |
2.1. Chinese Remainder Theorem
The Chinese Remainder Theorem (CRT) [23,28] is a theorem of number theory that allows one to solve systems of simultaneous congruences with different moduli. It asserts that if one knows the remainders of the division of an integer by several pairwise coprime integers, then one can determine uniquely the remainder of the division of that integer by the product of these integers, under certain conditions.
Let be pairwise co-prime positive numbers and be any given positive integers. Then, CRT asserts that the following simultaneous congruence equation
| (1) |
has a unique solution module , where , and the can be obtained by the following equation:
| (2) |
where and .
2.2. Elliptic Curve Cryptosystem
Consider a finite field determined by a prime number . Let be a set of elliptic curve points over defined by the equation , where and . The elliptic curve includes both scalar multiplication and point addition operations. is an additive cyclic group with order . The Elliptic Curve Discrete Logarithm Problem (ECDLP) is defined as follows: Given two random points on elliptic curve , where , it has been proven that calculating from is computationally difficult. In other words, it is infeasible to find in polynomial time with a non-negligible probability [29,30].
2.3. SM2 Digital Signature Algorithm
The SM2 digital signature algorithm [31] is a public key cryptographic algorithm based on elliptic curve cryptography, developed by the Chinese State Cryptography Administration. It is part of the Chinese National Standards (GB/T 32918.1-2016) [32] and is widely used for secure communications in China. The SM2 digital signature algorithm consists of three main phases: Key Generation, Signature Generation and Signature Verification.
Key Generation : Assume the signer of the message is user . TA chooses the elliptic curve parameters , selects a random integer as the private key and calculates the public key for user .
Signature Generation : Given a message . computes and , where represents two bytes converted from the bit length of user ’s identity , and are elements in that define an elliptic curve over , denotes the base point in the elliptic curve group and denotes user ‘s public key. Then, randomly chooses , calculates and . Finally calculates , where denotes user ’s private key. User ’s signature on the message is .
Signature Verification : Assume the verifier of the signature is user . Given user ’s signature on message , if , outputs false and exits. Then computes , and calculates . If , outputs false and exits. Finally, calculates and . If , outputs true; otherwise, it outputs false.
2.4. System Model
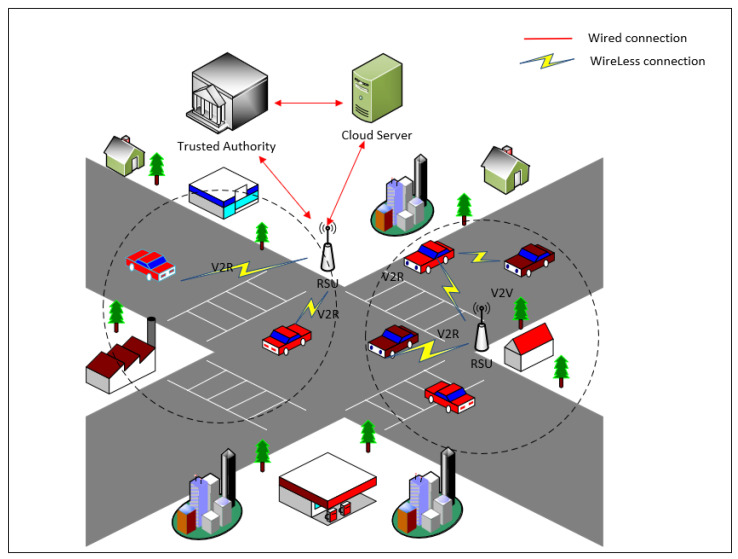
In the IoV, a federated learning system primarily includes four entities: a trusted authority (TA), cloud server (CS), roadside units (RSUs) and vehicles, as shown in Figure 1.
Figure 1.
Authentication scheme based on CPPA-SM2 for IoV.
TA: This is a trusted third party, typically the traffic-management department. It is primarily responsible for system initialization, registration of vehicles and RSUs, generating related keys for them and managing identities. In this paper, when a malicious vehicle uploads false local model parameters or forges identity information, the TA can trace its real identity and revoke it from the system.
Vehicles: These are the data owners and participants in federated learning. They use their locally collected data to train the global model received from CS, and then upload the local model parameters. In this paper, vehicles participate in federated learning using pseudonyms, sign the locally trained model parameters and then send them to the nearby RSU.
RSUs: These verify the authenticity and integrity of the local model parameters uploaded by vehicles. They use the FedAvg algorithm [5] to perform local aggregation on these parameters to obtain local aggregation results, which are then uploaded to the cloud server for global aggregation. Additionally, they broadcast the global model issued by TA to the vehicles within their communication range.
CS: Upon receiving the local aggregation results uploaded by RSUs, CS uses FedAvg to perform global aggregation to obtain the global model for the next round of training. The new global model is then distributed to the vehicles to begin the next training round. Through multiple iterations, the performance of the global model can be improved, enabling the cloud server to utilize the results for practical predictions, judgments and applications.
2.5. Threat Model and Security Model
In the threat model, CS and RSUs are considered honest-but-curious. This means they will honestly follow the protocol to verify vehicle identities and the authenticity and integrity of model parameters, and they will aggregate local models to obtain the global model [33]. However, they are curious about the private data owned by the vehicles and may attempt to recover the vehicles’ original data and reveal their true identities by analyzing the received model parameters. Therefore, they might pose a threat to vehicle privacy. Vehicles may be malicious and can launch free-riding attacks and data-poisoning attacks by uploading false model parameters. They may also forge identities and signatures to attempt to have fake messages successfully authenticated by RSUs. Additionally, they might try to infer the privacy information of other vehicles. Attackers can fully control the wireless communication channels between vehicles, RSUs, TA and CS. They can intercept messages on the channel, tamper with messages, replay old messages and attempt to impersonate other vehicles to send messages [34].
Based on the aforementioned threats and the certificateless signature security model [27,28,30], our proposed security model is as follows. The hash functions used in this model are assumed to be random oracles.
In the security model, we consider two types of adversaries, and . can launch public key-replacement attacks but cannot access system master secret key . can access the system master secret key but cannot perform public key-replacement attacks. Both types of adversaries will engage in two separate games with the challenger .
Game 1: This security game is executed between and . initializes the system using the security parameter generating system master secret key and system public parameters . secretly keeps and sends the public parameters to . can perform the following queries.
-
-
Hash queries: Upon receiving a query from , returns the corresponding hash values to .
-
-
Partial-Private-Key-Extract-queries: Upon receiving a query with a pseudonym , returns the partial private key of the vehicle to .
-
-
Public-Key-Extract-queries: Upon receiving a query with a pseudonym , returns the public key of the vehicle to .
-
-
Secret-Value-Extract-queries: Upon receiving a query with a pseudonym , returns the secret value of the vehicle to .
-
-
Public-Key-Replace-queries: Upon receiving a query with , replaces public key with the new public key .
-
-
Sign queries: After receiving a query from with , responds with a signature .
-
-
Forgery: Once has completed the desired queries, it outputs under the pseudo identity . wins the game if the following conditions are met:
-
-
passes verification.
-
-
Partial-Private-Key-Extract-queries oracle has not received the request with .
-
-
Sign queries oracle has not received the request with .
Definition 1.
CPPA-SM2 is existentially unforgeable under adaptive chosen-identity and chosen-message attacks if no polynomial-time adversary can win the above game with non-negligible advantage.
Game 2: This security game is executed between and . initializes the system using the security parameter generating system master secret key and system public parameters . sends them to .
-
-
Query: can perform all the queries from Game 1 except for Public-Key-Replace-queries.
-
-
Forgery: Once has completed the desired queries, it outputs under the pseudo identity . wins the game if the following conditions are met:
-
-
passes verification.
-
-
Secret-Value-Extract-queries oracle has not received the request with .
-
-
Sign queries oracle has not received the request with .
Definition 2.
CPPA-SM2 is existentially unforgeable under adaptive chosen-identity and chosen-message attacks if no polynomial-time adversary can win the above game with non-negligible advantage.
2.6. Design Goals
Under the security model, CPPA-SM2 primarily has the following design goals:
Anonymity and Privacy-Preserving: CPPA-SM2 should protect the privacy of vehicles participating in federated learning training. No entity other than TA should be able to infer the true identity of the vehicles.
Authenticity and Integrity: CPPA-SM2 should ensure that the local model parameters received by RSUs are from legitimate vehicles and that they have not been tampered with during transmission.
Un-linkability: Attackers cannot link any two messages sent by the same vehicle.
Un-forgeability: Attackers cannot forge signatures of other vehicles on messages, allowing RSUs to successfully verify the signatures.
Non-repudiation: Once a vehicle uploads local model parameters and they are authenticated, the vehicle cannot deny its contribution to the global model.
Forward Security: When a vehicle joins a group, it cannot access communications that occurred before its joining, meaning it cannot participate in previous federated learning training processes of the group.
Backward Security: When a vehicle leaves the group or is revoked by the TA, it cannot participate in the current model training process or access communications that occur after its departure from the group.
In addition to achieving the aforementioned security goals, CPPA-SM2 should also have efficient authentication efficiency and lower communication overhead to adapt to the communication environment of IoV. In particular, when a large number of vehicles participate in federated learning training, RSUs should be able to authenticate them in batches.
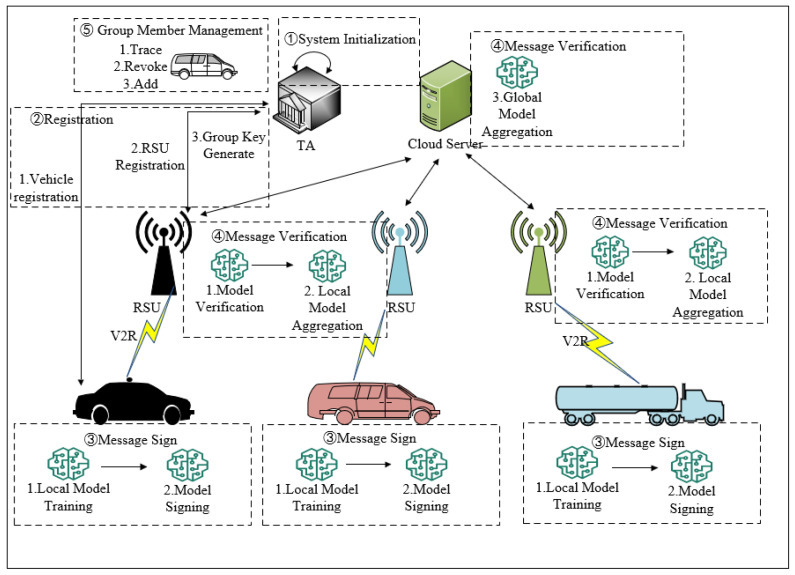
3. The Proposed Scheme
In this section, we present a certificateless conditional privacy-preserving identity-authentication protocol based on CRT and the SM2 digital signature algorithm, named CPPA-SM2. CPPA-SM2 aims to provide privacy protection for vehicles participating in federated learning. It consists of five phases: system initialization, registration, message sign, message verification and group member management. First, TA initializes the system and publishes the system’s public parameters. Then, vehicles and RSUs register with TA before participating in communications. Through registration, they obtain the public and private keys required for subsequent communications. In the message signing phase, vehicles train a model based on their local datasets and then sign the local model parameters before sending them to RSU. RSU, upon receiving the local model parameters from nearby vehicles, verifies the signatures and aggregates the verified local model parameters to obtain a local aggregation result. RSU then sends this local aggregation result to CS for global aggregation, resulting in the next round of the global model. If a malicious vehicle is detected uploading malicious model parameters or forging signatures, TA can trace its identity and revoke it from the system. The overall workflow of CPPA-SM2 is illustrated in Figure 2 and Protocol 1. The details of the scheme are as follows.
| Protocol 1 CPPA-SM2 |
1: Use to generate two large prime numbers and . 2: Randomly select and calculates . 3: Choose five one-way hash functions . 4: Publish .
1: randomly selects , calculates and send to TA. 2: Upon receiving , TA calculates , , and randomly selects . Then, TA sends , and to . 3: sets , and . For each RSU: 1: sends to TA. 2: TA generates a pair of public and private keys and sends them to . 3. sets . For TA: 1: Calculate , , and set , . 2: Randomly pick a group key and calculate the group public key and . 3: Sign , and the ’s valid period using its private key and broadcast the information to vehicles and RSUs in .
1: trains the global model using its local dataset to obtain the local model parameters . 2: randomly selects to generate a pseudo identity , where and . 3: calculates , and . 4: randomly selects , calculates , and . 5. obtains the signature of and sends messages to the nearby .
1: Upon receiving the messages from , first checks the validity of timestamp. If , where represents the arrival time, continues; otherwise, discards. 2: calculates , , , and . 3: checks the equality of for authentication and validity. 4: uses the FedAvg algorithm to locally aggregate the verified local model parameters , producing a local aggregation result . 5: signs this result with its private key and sends messages to CS. For CS: 1: CS performs a global aggregation on the verified local aggregation results to obtain the global model . 2: CS signs the global model with its private key and sends messages to the vehicles within the communication group via RSUs.
1: TA uses the system’s master private key to recover the vehicle’s true identity . Revoke: 1. TA first removes related to from by computing . 2: TA randomly selects a new group key , calculates new group public keys and , and broadcasts the updated information to vehicles and RSUs in . Add: 1. TA randomly selects a new group key and calculates , , , and . 2. TA computes new group public keys and , and broadcasts the updated information in . |
Figure 2.
Workflow of CPPA-SM2.
3.1. System Initialization
TA uses a security parameter to generate two large prime numbers and , where , . Let denote an elliptic curve over the finite field and denote a base point on the elliptic curve with order . Let be an additive cyclic group generated by . TA randomly selects as the system master secret key and calculates the system public key . Then, TA chooses five one-way hash functions . TA secretly holds and publishes the system’s public parameters .
3.2. Registration
In the registration phase, both vehicles and RSUs need to register with TA to obtain the relevant keys for subsequent communications. We assume that TA is fully trusted and that the entire registration phase is conducted over a secure channel, eliminating the risk of privacy leaks and security attacks.
3.2.1. Vehicle Registration
For a vehicle with its real identity , it first randomly selects as its secret value and calculates as its first part of the public key. Then, sends to TA. Upon receiving , TA calculates , and , where and serve as ’s partial private key and the second part of the public key. In addition, TA randomly selects a prime number as a secret key for . Completing these computations, TA returns , and to . Upon receiving , and , sets as its full private key, as its full public key and uses for subsequent group communications.
3.2.2. RSU Registration
For a roadside unit with its identity , TA generates a pair of public and private keys . Then, TA distributes them to . Here, we assume that all vehicles know the public keys of TA and RSUs.
3.2.3. Group Key Generate
To ensure that the uploaded local model parameters come from legitimate vehicles and to support efficient group communication, TA constructs a communication group for them based on the secret keys of vehicles and CRT. TA first calculates , and . TA sets , , where . Then, TA randomly picks a group key and calculates the group public key and . TA signs , and the ’s valid period using its private key and broadcasts the information to vehicles and RSUs in . Once receiving the broadcast information, any authorized vehicle in can obtain by performing a modulus operation according to CRT.
3.3. Message Sign
In the round of training, the vehicle trains the global model using its local dataset to obtain the local model parameters , i.e., . Before sending the local model parameter to the nearby , the vehicle signs it as follows to ensure the authenticity and integrity of .
randomly selects to generate a pseudo identity , where and . Then, calculates , and signature key , where represents two bytes converted from the bit length of , and are elements in that define an elliptic curve over and represents the current timestamp. Next, randomly selects and calculates , and . For simplicity, we omit the notation of , , , , , , and . Finally, obtains the signature of and sends messages to the nearby .
3.4. Message Verification
3.4.1. Single Message Verification
Upon receiving the messages from , first checks the validity of the timestamp. If , where represents the arrival time, it continues; otherwise, it discards. Then calculates , , , and . Finally, checks the equality of for authentication and validity.
3.4.2. Batch Messages Verification
When receiving a batch of messages , , …, from the vehicles , first checks the validity of timestamp , where . If is valid, it continues; otherwise, it discards. To prevent confusion attacks while ensuring non-repudiation, CPPA-SM2 uses a set of small exponents for batch verification [23,35], where and is a small integer. Next, calculates
| (3) |
and checks whether holds or not. If true, all messages are valid; otherwise, some of these messages are invalid. The detection algorithm for invalid message signatures has been proposed in [36]. The details of this algorithm are beyond the scope of this paper.
3.4.3. Local Model Aggregation
uses the FedAvg algorithm to locally aggregate the verified local model parameters , producing a local aggregation result , where and denotes the number of vehicles participating in the training within the ’s range. It then signs this result with its private key and sends messages to CS. Upon receiving the local aggregation result from RSUs, CS verifies its validity. It then performs a global aggregation on the verified local aggregation results to obtain the global model , where and denotes the number of RSUs. CS signs the global model with its private key and sends messages to the vehicles within the communication group via RSUs.
3.5. Group Member Management
3.5.1. Trace
When detects that a vehicle has uploaded malicious local model parameters or has engaged in identity forgery, it sends the vehicle’s pseudonym to TA. TA then uses the system’s master private key to recover the vehicle’s true identity .
3.5.2. Revoke
Upon obtaining the true identity of the malicious vehicle , TA can completely remove it from the federated learning system by revoking its legitimate information from the group. TA first removes related to from by computing . Then, TA randomly selects a new group key , calculates new group public keys and and broadcasts the updated information to vehicles and RSUs in . Upon receiving , the remaining vehicles in can use their secret key to compute the updated group key . Since no longer contains the legitimate information of , it cannot compute the new group key . When a vehicle leaves the communication group , TA can also revoke it in this way.
3.5.3. Add
When a vehicle applies to join the federated learning system, TA randomly selects a new group key and calculates , , , and . Then, TA computes new group public keys and , and broadcasts the updated information in . Upon receiving , vehicles in , it calculates the updated group key .
4. Correctness and Security Proof and Analysis
In this section, we first provide a proof of correctness for the proposed scheme. Then, under the random oracle model, we prove the security of the scheme. Finally, we conduct an informal security analysis of the scheme.
4.1. Correctness Proof
The correctness verification of the single message signature is ensured by Equations (4) and (5).
| (4) |
| (5) |
The correctness verification of the batch message signatures is ensured by Equations (6) and (7).
| (6) |
| (7) |
Based on the signing and verification process, if the local model parameter and signature transmitted by the vehicle have not been tampered with and the signature is generated using the legitimate vehicle’s private key, then according to (4)–(7), RSU can correctly compute that , thereby making .
The correctness of legitimate vehicles in obtaining the correct group key is ensured by Equation (8).
| (8) |
When vehicle is revoked from the group by TA, since , the revoked vehicle will be unable to obtain the correct group key according to Equation (9).
| (9) |
4.2. Security Proof
The security of CPPA-SM2 relies on the ECDLP. In the random oracle model, if there exist adversaries and who can win games 1 and 2 with non-negligible probabilities, respectively, then there exists a probabilistic polynomial-time simulator that can solve the ECDLP with non-negligible probability.
Theorem 1.
CPPA-SM2 is existentially unforgeable under adaptive chosen-identity and chosen-message attacks against with the assumption that ECDLP is hard to resolve.
Proof of Theorem 1.
Let be the solver of the ECDLP. Suppose that can succeed in forging a valid signature by interacting with . utilizes to solve the ECDLP. Here, we give an ECDLP instance . executes the simulation to compute through interacting with as follows.
- -
Setup: On input , sets and returns to . selects as a target vehicle. In addition, maintains five lists , , , , , which are empty initially.
- -
Query: can adaptively make the following queries:
- -
-queries: After receiving the queries from with , checks whether exists in . If it does, returns to . Otherwise, selects randomly and adds to . Then, returns to .
- -
-queries: When receiving the queries with from , checks whether exists in . If it does, returns to . Otherwise, selects randomly and adds to . Then, returns to .
- -
-queries: Upon receiving the queries from with , checks whether exists in . If it does, returns to . Otherwise, selects randomly and adds to . Then, returns to .
- -
-queries: Upon receiving the queries from with , checks whether exists in . If it does, returns to . Otherwise, selects randomly and adds to . Then, returns to .
- -
Partial-Private-Key-Extract-queries: After receiving the queries from with , checks whether exists in . If it does, returns to . Otherwise, selects randomly, computes , . Then, sets . After that, adds into and returns to .
- -
Public-Key-Extract-queries: After receiving the queries from with , checks whether exists in . If it does, returns to . Otherwise, does the Partial-Private-Key-Extract-queries to obtain . Then, selects randomly and computes , , . After that, adds into and returns to .
- -
Secret-Value-Extract-queries: After receiving the queries from with , checks whether exists in . If it does, returns to . Otherwise, does the Public-Key-Extract-queries to obtain . After that, adds into and returns to .
- -
Public-Key-Replace-queries: After receiving the queries from with , checks whether exists in . If it does, sets , , and updates into . Otherwise, sets , , and adds to .
- -
Sign queries: After receiving the queries from with , retrieves the lists , , , , randomly selects , , and sets , , , , . returns to and adds into . For the output of the signature oracle satisfies , .
- -
Forgery: After all queries have been completed, outputs a forged tuple . verifies whether , holds. If it does not hold, terminates the simulation. Otherwise, replays the above process by choosing different , and based on forking lemma. will output three other distinct valid signatures , and .
Finally, we can obtain four equations as below.
(10) In the above four equations, , , and represent the discrete logarithms of , , and , respectively, which are not known to . can obtain the four unknown values by solving the above four linear independent equations, where is the solution of ECDLP. □
Theorem 2.
CPPA-SM2 is existentially unforgeable under adaptive chosen-identity and chosen-message attacks against with the assumption that ECDLP is hard to resolve.
Proof of Theorem 2.
Let be the solver of the ECDLP. Suppose that can succeed in forging a valid signature by interacting with . utilizes to solve the ECDLP. Here, we give an ECDLP instance . executes the simulation to compute through interacting with as follows.
- -
Setup: On input , sets and returns to . selects as a target vehicle. In addition, maintains five lists , , , , , which are empty initially.
- -
Query: responds to --queries (), Partial-Private-Key-Extract-queries, Secret-Value-Extract-queries and Sign queries as in Theorem 1. responds to Public-Key-Extract-queries as follows.
- -
Public-Key-Extract-queries: After receiving the queries from with , checks whether exists in . If it does, returns to . Otherwise, does the Partial-Private-Key-Extract-queries to obtain .
- -
If , sets , , . adds into and sends to .
- -
If , chooses randomly, computes , , . After that, adds into and returns to .
- -
Forgery: After all queries have been completed, outputs a forged tuple . verifies whether , holds. If it does not hold, terminates the simulation. Otherwise, replays the above process by choosing different and based on forking lemma. will output two other distinct valid signatures and .
Finally, we can obtain three equations as below.
(11) In the above three equations, , and represent the discrete logarithms of , and , respectively, which are not known to . can obtain the three unknown values by solving the above three linear independent equations, where is the solution of ECDLP.
However, it is difficult to solve the ECDLP in polynomial time. So, under the random oracle model, CPPA-SM2 is existentially unforgeable under adaptive chosen-identity and chosen-message attacks. □
4.3. Informal Security Analysis
Anonymity and Privacy-Preserving: In the CPPA-SM2 scheme, vehicles use pseudonyms to communicate with other entities. To obtain the vehicle’s real identity , the adversary must compute . However, due to the hardness of the Computational Diffie–Hellman (CDH) problem, the adversary is unable to obtain , thereby protecting the vehicle’s identity privacy. Additionally, since vehicles participate in federated learning using pseudonyms, and these pseudonyms are updated with each message sent, even if external adversaries or RSUs gain access to the plaintext local model parameters, they cannot link them to specific vehicles. This prevents the inference of any private information, thus providing privacy protection during the federated learning process.
Traceability: When a vehicle with malicious behavior is detected, TA can trace its real identity from its pseudonym using the system’s master private key .
Message integrity and authentication: According to Theorem 1 and Theorem 2, as long as the ECDLP is hard to solve, the CPPA-SM2 scheme is existentially unforgeable under adaptive chosen-identity and chosen-message attacks against the attackers and .
Non-repudiation: Since only the message signer can compute the signature key , an adversary cannot forge valid signatures for a specific vehicle identity. Additionally, the TA can execute the Trace algorithm to obtain the vehicle’s real identity. Therefore, once a vehicle’s message passes the signature verification, it cannot be denied.
Un-linkability: Since the vehicle pseudonym identity is generated during the signing process and the random number used in the signature generation process is non-repetitive, each PID in every signature is unique. As a result, any adversary cannot link any number of signatures sent by the same vehicle.
Forward privacy: When a new vehicle joins the group , the new group key is randomly generated by the TA and is independent of the old group key . Therefore, the newly joined vehicle cannot access the group’s communications prior to joining.
Backward privacy: When a vehicle is revoked or leaves the group, the TA will remove the legitimate information associated with that vehicle from and compute a new group key and group public key and . Since the revoked vehicle cannot obtain the updated group key , it cannot access the communications after leaving the group.
Impersonation attack: If an adversary wants to impersonate vehicle to the RSUs nearby or other vehicles , they must generate a valid message that passes the verification algorithm. However, according to Theorem 1 and Theorem 2, it is evident that no polynomial adversary can forge a valid message.
Modification attack: According to Theorem 1 and Theorem 2, any modification of the message can be detected by the verification algorithm. Therefore, the proposed CPPA-SM2 scheme can withstand the modification attack.
Replay attack: In the proposed CPPA-SM2 scheme, vehicles use the current timestamp when generating message signatures. Therefore, message verifiers can resist replay attacks by verifying the freshness of the timestamp .
Collusion attack: Several vehicles would collaborate to try to compute the new group key after they left the group. However, since their legitimate information has been removed from , these leaving vehicles cannot conspire to calculate the new group key .
5. Performance Evaluation
In this section, we will evaluate the performance of the proposed CPPA-SM2 scheme from both security features, computation overhead and communication overhead perspectives, and compare and analyze it with the existing works. For bilinear pairings-based CPPA schemes for IoV, we construct a bilinear pairing , where is an additive group generated by a point with the order on the super singular elliptic curve with embedding degree 2, is a 512-bit prime number, is a 160-bit prime number. For ECC-based CPPA schemes for IoV, we construct an additive group generated by a point with the order on a non-singular elliptic curve , where are two 256-bit prime numbers and . We calculate the execution time of basic cryptographic operations using the MIRACL library in VS 2019 with Windows 11 operating system over an Intel(R) Core(TM) i7-9750H CPU @ 2.60GHz, as shown in Table 2.
Table 2.
Execution time of basic cryptographic operations and element size.
| Symbols | Meanings | Time (ms)/Size (Byte) |
|---|---|---|
| 0.0181 ms | ||
| 0.0020 ms | ||
| 0.0434 ms | ||
| 0.0044 ms | ||
| Encryption time of AES algorithm | 10.0761 ms | |
| Decryption time of AES algorithm | 0.1759 ms | |
| Time of XOR operation | 0.0009 ms | |
| Time of bilinear pairing | 8.7985 ms | |
| 0.1361 ms | ||
| 1.3451 ms | ||
| 0.0069 ms | ||
| 0.0869 ms | ||
| Time of scalar multiplication on ecliptic curve group | 1.4944 ms | |
| Time of point addition on ecliptic curve group | 0.1376 ms | |
| Time of one-way hash function | 0.3018 ms | |
| Time of hash mapped to point | 48.3228 ms | |
| Size of timestamp | 4 bytes | |
| Size of ID | 8 bytes | |
| The ciphertext size of AES algorithm | 32 bytes | |
| Size of elements on elliptic curve | 64 bytes | |
| Size of elements on bilinear group | 128 bytes | |
| Size of elements on bilinear group | 128 bytes | |
| 32 bytes | ||
| Output size of hash function | 32 bytes |
5.1. Computation Costs
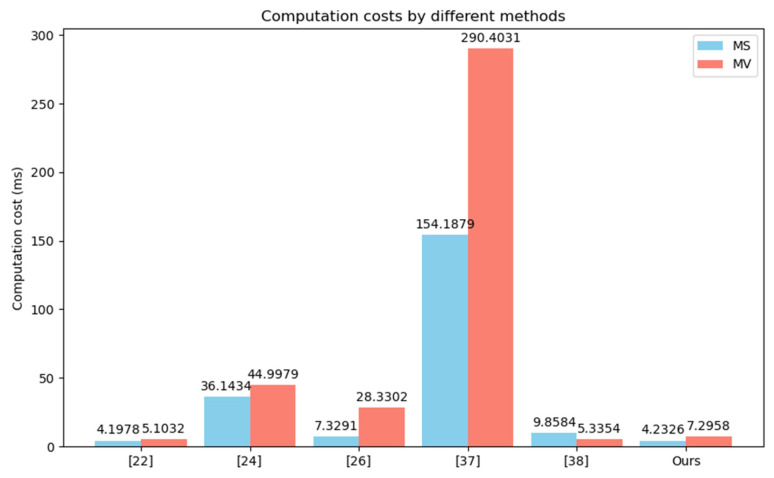
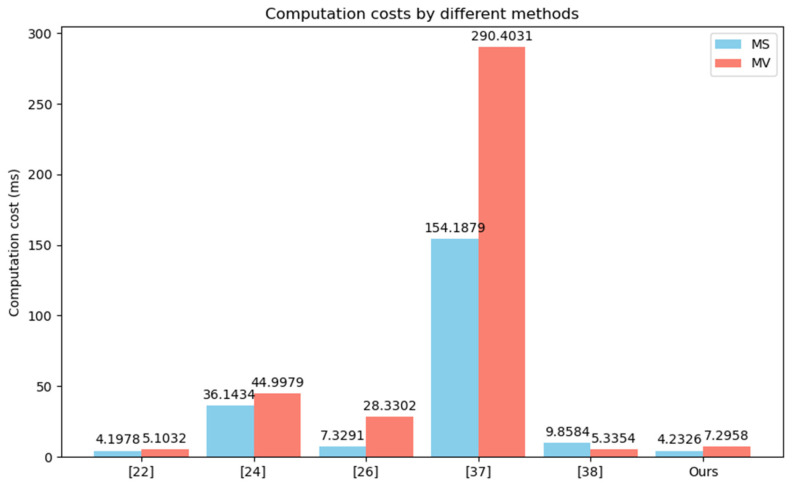
We compared the computational costs of the CPPA-SM2 scheme with other relevant schemes in terms of signature generation, single signature verification, batch verification and member management, as shown in Table 3 and Table 4, and Figure 3 and Figure 4, where “-” indicates that the property is not considered in the scheme, MS denotes the message sign and MV denotes the message verification.
Table 3.
Analysis of computation costs for different schemes.
Table 4.
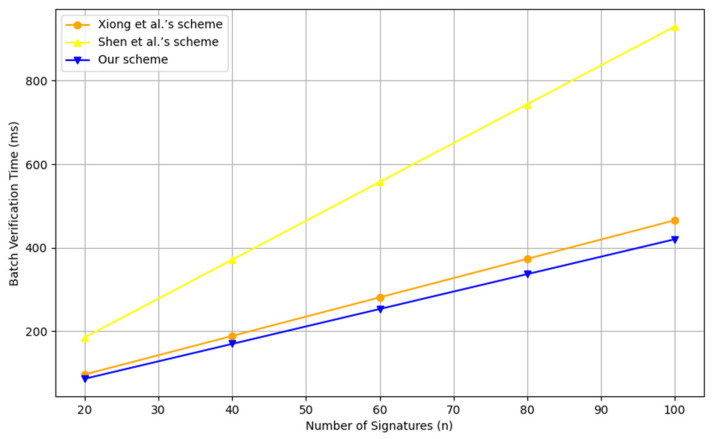
Comparison of batch-verification costs.
Figure 3.
Comparison of computation costs.
Figure 4.
Comparison of the scheme proposed by [28,39], and our scheme in batch validation time.
Zhao et al. scheme [22] offers relatively low computational overhead, but RSU needs to send a request to TA for each identity verification, and there is a key escrow issue. In Kanchan et al. scheme [24] based on bilinear pairings, group signature is used instead of an individual signature for message authentication, and the group manager achieves tracing of malicious vehicles. Generating a group signature requires performing . Verifying the group signature requires performing , resulting in a relatively high computational overhead. In Jiang et al. scheme [26], similarly, bilinear pairing operations are used, requiring computations to generate a signature and computations to verify the signature. In Yang et al. scheme [37], generating a signature requires performing . To verify the signature, operations are needed. Due to the involvement of bilinear pairings and hash-to-point mappings, this method incurs the highest computational overhead. In Lin et al. scheme [38], a vehicle calculates to generate the anonymous public keys and a signature. Upon receiving the signature, RSU verifies it by performing . Additionally, Zhao et al. scheme [22], Kanchan et al. scheme [24], Jiang et al. scheme [26] and Lin et al. scheme all require maintaining a revocation list for revocation purposes, which incurs additional lookup and maintenance overhead. CPPA-SM2 does not require bilinear pairings or hash-to-point mappings, relying only on basic ECC operations, thus reducing computational costs. Specifically, when a vehicle sends a message, it first generates an unlinkable pseudonym by performing one , one and one . Then, it generates the signature by performing three , one , four and one . Therefore, the computation cost for signature generation is . To authenticate the message sent by the vehicle, the RSU, upon receiving the message, needs to perform . Therefore, the total computation cost for signature generation and signature verification in CPPA-SM2 is . When RSU receives messages sent from vehicles, it performs batch verification of the messages by executing . To test the effectiveness of batch verification, we conducted experimental comparisons between CPPA-SM2 and Xiong et al. scheme [28] and Shen et al. scheme [39]. In batch verification, the RSU will verify the messages received simultaneously from vehicles, meaning represents both the number of signatures received by the RSU at the same time and the number of vehicles. In the experiment, we tested with set to 20, 40, 60 and 100, respectively. In CPPA-SM2, when RSU simultaneously receives messages from vehicles, it needs to compute three , two and two for each vehicle. Finally, it performs two and one to verify multiple messages. Therefore, the total cost of batch verification is . In Xiong et al. scheme [28], it performs four , two and three for each vehicle. Then, it also executes three and one . Therefore, the total cost of batch verification is . In Shen et al. scheme [39], RSU invokes one exponent operation, one bilinear pairing and one multiplication to confirm the equation . Its batch verification is based on , which needs times , times and . The results are shown in Table 4 and Figure 4. From the experimental results, it can be seen that the batch-verification performance of our scheme is better than these two schemes. In terms of tracing cost, Kanchan et al. scheme [24], Yang et al. scheme [37], Lin et al. scheme [38] and CPPA-SM2 are 1.3451 ms, 0.1759 ms, 1.6320 ms and 0.3027 ms, respectively. All these approaches can achieve fast identity tracing. But in terms of revocation, all schemes except CPPA-SM2 utilize revocation lists, leading to additional maintenance and lookup overheads, while CPPA-SM2 only requires a single modular operation to efficiently revoke vehicles. Therefore, overall, compared to other schemes, CPPA-SM2 not only reduces the computational costs of signature generation and verification, and supports batch verification, but it also achieves efficient tracing and revocation of vehicles while preserving vehicle privacy.
5.2. Communication Costs
We compared the communication costs of CPPA-SM2 with other schemes, mainly including the following: the size of single signature (SSS), the total number of transmitted messages (NTMs), their sizes (STMs) and the number of interactions (NIs). The results are shown in Table 5 and Figure 5. In Zhao et al. scheme [22], to complete the authentication, interaction is required four times, making it the highest number of interactions. Its total computational cost is 476 bytes. The communication overhead for the group signature generated in Kanchan et al. scheme [24] is the highest, at 576 bytes. Jiang et al. scheme [26], Yang et al. scheme [37] and CPPA-SM2 all require only one interaction to complete message authentication. In Lin et al. scheme [38], vehicles need to transmit for message authentication, with a total size of 480 bytes. In CPPA-SM2, the generated signature, denoted as , consists of two elements from ; hence, its size is merely 64 bytes. To authenticate the signature, three additional messages of size 228 bytes need to be transmitted, resulting in a total transmission cost of 292 bytes. In Yang et al. scheme [37], The generation of a single signature is denoted as , where , and belongs to ; thus, the size of is 384 bytes.
Table 5.
Comparison of communication costs for different schemes.
Figure 5.
Comparison of communication costs.
In Lin et al. scheme [38], the obtained signature is denoted as , with a length of 224 bytes. Additionally, to resist replay attacks, are also sent, making the total message length for transmission 356 bytes. From the experimental results, it can be observed that CPPA-SM2 has the smallest signature size and total cost of transmitting messages. This makes it more suitable for operation in bandwidth-constrained vehicular networking environments.
5.3. Security Features
We compared the security features (SFs) satisfied by these schemes, including the following: 1: anonymity; 2: traceability; 3: authenticity; 4: integrity; 5: non-repudiation; 6: un-linkability; 7: forward security; 8: backward security; 9: key escrow-free; 10: batch verification; 11: revocability; 12: dynamic member management; and 13: un-forgeability. The results are shown in Table 6, where 1–13 represent these security features in order, with √ indicating that the security feature is met and × indicating that it is not met. From the results, it can be seen that all schemes achieve 1: anonymity, 3: authenticity, 4: integrity and 6: un-linkability. Zhao et al. scheme [22], Kanchan et al. scheme [24], Jiang et al. scheme [26] and CPPA-SM2 use digital signatures to verify the authenticity and integrity of the local model parameters uploaded by vehicles. However, in Zhao et al. scheme [22] and Kanchan et al. scheme [24], since TA possesses all users’ private keys, there is a key escrow issue. Jiang et al. scheme [26] satisfies most of the security features; however, it uses a revocation list for identity management, resulting in additional verification and maintenance overhead. Furthermore, it does not support 12: dynamic member management. To achieve 6: un-linkability, Yang et al. scheme [37] and Lin et al. scheme [38] use a set of pseudonyms to hide real identities, whereas CPPA-SM2 achieves 6: un-linkability by randomly generating pseudonyms each time a signature is made. Overall, compared to these schemes, CPPA-SM2 achieves more comprehensive security attributes, supports 10: batch verification and 12: dynamic member management, and has lower computational and communication costs.
Table 6.
Security features.
Overall, compared to the state-of-the-art scheme, Jiang et al. scheme [26], CPPA-SM2 reduces the cost of single signature generation and verification by 42.25% and 74.25%, respectively. In terms of communication overhead, CPPA-SM2 reduces it by 60% and 39.17%, respectively. While the performance of CPPA-SM2 in batch verification is not as good as Jiang et al. scheme [26], it supports dynamic member management, enabling efficient member addition and revocation, which results in increased batch-verification costs.
6. Conclusions
In this paper, we propose a conditional privacy-preserving identity-authentication protocol that provides privacy protection for vehicles participating in federated learning in the IoV. Unlike most existing privacy-preserving federated learning schemes, it does not require complex cryptographic operations or the introduction of random noise. Instead, it achieves privacy protection by using dynamic pseudonyms to obscure the connection between model parameters and the real identities of vehicles, thereby maintaining federated learning efficiency.
Moreover, CPPA-SM2 is a certificateless authentication scheme based on ECC, CRT and the SM2 digital signature algorithm. It enables efficient identity authentication and dynamic member management, and supports batch verification. Security proofs and analyses demonstrate that it can ensure the authenticity and integrity of local model parameters, achieving secure vehicle authentication. Experimental results show that, compared to existing advanced schemes, CPPA-SM2 offers high computational efficiency and low communication overhead. Additionally, its integration with standard algorithms endows it with the potential for widespread application.
However, the focus of this paper is on identity-authentication schemes and privacy protection in the federated learning process. There are still some malicious clients in the federated learning process that may launch data-poisoning attacks by uploading malicious local model parameters, thereby affecting the performance of the global model. Therefore, future research could integrate Byzantine robust detection schemes to achieve privacy-preserving Byzantine robust federated learning. Additionally, with the development of post-quantum algorithms, the ECDLP may be efficiently solved by post-quantum algorithms, making ECC-based authentication schemes no longer secure. Future work can explore quantum-resistant identity-authentication schemes, such as lattice-based cryptography.
Author Contributions
Conceptualization, R.L. and S.X.; methodology, S.X.; formal analysis, R.L.; investigation, R.L.; resources, R.L. and S.X.; writing—original draft preparation, R.L.; writing—review and editing, R.L. and S.X.; supervision, S.X.; project administration, S.X.; funding acquisition, S.X. All authors have read and agreed to the published version of the manuscript.
Institutional Review Board Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
Funding Statement
This research was funded by the Ministry of Science and Technology of the People’s Republic of China, the Research on Digital Identity Trust System for Massive Heterogeneous Terminals in Road Traffic System (Grant No. 2022YFB3104402).
Footnotes
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
References
- 1.Duan W., Gu J., Wen M., Zhang G., Ji Y., Mumtaz S. Emerging Technologies for 5G-IoV Networks: Applications, Trends and Opportunities. IEEE Netw. 2020;34:283–289. doi: 10.1109/MNET.001.1900659. [DOI] [Google Scholar]
- 2.Elbir A.M., Soner B., Coleri S., Gunduz D., Bennis M. Federated Learning in Vehicular Networks; Proceedings of the 2022 IEEE International Mediterranean Conference on Communications and Networking (MeditCom); Athens, Greece. 5–8 September 2022; pp. 72–77. [DOI] [Google Scholar]
- 3.Khan L.U., Mustafa E., Shuja J., Rehman F., Bilal K., Han Z., Hong C.S. Federated Learning for Digital Twin-Based Vehicular Networks: Architecture and Challenges. IEEE Wirel. Commun. 2024;31:156–162. doi: 10.1109/MWC.012.2200373. [DOI] [Google Scholar]
- 4.Zhang X., Chang Z., Hu T., Chen W., Zhang X., Min G. Vehicle Selection and Resource Allocation for Federated Learning-Assisted Vehicular Network. IEEE Trans. Mob. Comput. 2023;23:3817–3829. doi: 10.1109/TMC.2023.3283295. [DOI] [Google Scholar]
- 5.Cao X., Başar T., Diggavi S., Eldar Y.C., Letaief K.B., Poor H.V., Zhang J. Communication-Efficient Distributed Learning: An Overview. IEEE J. Sel. Areas Commun. 2023;41:851–873. doi: 10.1109/JSAC.2023.3242710. [DOI] [Google Scholar]
- 6.Qu Z., Tang Y., Muhammad G., Tiwari P. Privacy protection in intelligent vehicle networking: A novel federated learning algorithm based on information fusion. Inf. Fusion. 2023;98:101824. doi: 10.1016/j.inffus.2023.101824. [DOI] [Google Scholar]
- 7.Ni R., Lu Y., Yang B., Yang C., Liu X. A federated pedestrian trajectory prediction model with data privacy protection. Complex Intell. Syst. 2024;10:1787–1799. doi: 10.1007/s40747-023-01239-5. [DOI] [Google Scholar]
- 8.XHu X., Li R., Wang L., Ning Y., Ota K. A Data Sharing Scheme Based on Federated Learning in IoV. IEEE Trans. Veh. Technol. 2023;72:11644–11656. doi: 10.1109/TVT.2023.3266100. [DOI] [Google Scholar]
- 9.Sikarwar H., Das D. A Novel MAC-Based Authentication Scheme (NoMAS) for Internet of Vehicles (IoV) IEEE Trans. Intell. Transp. Syst. 2023;24:4904–4916. doi: 10.1109/TITS.2023.3242291. [DOI] [Google Scholar]
- 10.Wei K., Li J., Ding M., Ma C., Yang H.H., Farokhi F., Jin S., Quek T.Q.S., Poor H.V. Federated Learning With Differential Privacy: Algorithms and Performance Analysis. IEEE Trans. Inf. Forensics Secur. 2020;15:3454–3469. doi: 10.1109/TIFS.2020.2988575. [DOI] [Google Scholar]
- 11.Zhao Y., Zhao J., Yang M., Wang T., Wang N., Lyu L., Niyato D., Lam K.-Y. Local Differential Privacy-Based Federated Learning for Internet of Things. IEEE Internet Things J. 2021;8:8836–8853. doi: 10.1109/JIOT.2020.3037194. [DOI] [Google Scholar]
- 12.Zhou H., Yang G., Dai H., Liu G. PFLF: Privacy-Preserving Federated Learning Framework for Edge Computing. IEEE Trans. Inf. Forensics Secur. 2022;17:1905–1918. doi: 10.1109/TIFS.2022.3174394. [DOI] [Google Scholar]
- 13.Zhou C., Fu A., Yu S., Yang W., Wang H., Zhang Y. Privacy-Preserving Federated Learning in Fog Computing. IEEE Internet Things J. 2020;7:10782–10793. doi: 10.1109/JIOT.2020.2987958. [DOI] [Google Scholar]
- 14.Ma Z., Ma J., Miao Y., Li Y., Deng R.H. ShieldFL: Mitigating Model Poisoning Attacks in Privacy-Preserving Federated Learning. IEEE Trans. Inf. Forensics Secur. 2022;17:1639–1654. doi: 10.1109/TIFS.2022.3169918. [DOI] [Google Scholar]
- 15.Hijazi N.M., Aloqaily M., Guizani M., Ouni B., Karray F. Secure Federated Learning with Fully Homomorphic Encryption for IoT Communications. IEEE Internet Things J. 2024;11:4289–4300. doi: 10.1109/JIOT.2023.3302065. [DOI] [Google Scholar]
- 16.ZZhang Z., Wu L., Ma C., Li J., Wang J., Wang Q., Yu S. LSFL: A Lightweight and Secure Federated Learning Scheme for Edge Computing. IEEE Trans. Inf. Forensics Secur. 2023;18:365–379. doi: 10.1109/TIFS.2022.3221899. [DOI] [Google Scholar]
- 17.Taheri R., Shojafar M., Alazab M., Tafazolli R. Fed-IIoT: A Robust Federated Malware Detection Architecture in Industrial IoT. IEEE Trans. Ind. Inform. 2021;17:8442–8452. doi: 10.1109/TII.2020.3043458. [DOI] [Google Scholar]
- 18.Taheri R., Arabikhan F., Gegov A., Akbari N. Robust Aggregation Function in Federated Learning. In: Saad I., Rosenthal-Sabroux C., Gargouri F., Chakhar S., Williams N., Haig E., editors. Advances in Information Systems, Artificial Intelligence and Knowledge Management. Volume 486. Springer; Cham, Switzerland: 2024. ICIKS 2023. Lecture Notes in Business Information Processing. [DOI] [Google Scholar]
- 19.Al Sibahee M.A., Nyangaresi V.O., Abduljabbar Z.A., Luo C., Zhang J., Ma J. Two-Factor Privacy-Preserving Protocol for Efficient Authentication in Internet of Vehicles Networks. IEEE Internet Things J. 2024;11:14253–14266. doi: 10.1109/JIOT.2023.3340259. [DOI] [Google Scholar]
- 20.Ou Z., Xing X., He S., Wang G. TDS-NA: Blockchain-based trusted data sharing scheme with PKI authentication. Comput. Commun. 2024;218:240–252. doi: 10.1016/j.comcom.2024.02.018. [DOI] [Google Scholar]
- 21.Chen Y., Su Y., Zhang M., Chai H., Wei Y., Yu S. FedTor: An Anonymous Framework of Federated Learning in Internet of Things. IEEE Internet Things J. 2022;9:18620–18631. doi: 10.1109/JIOT.2022.3162826. [DOI] [Google Scholar]
- 22.Zhao P., Huang Y., Gao J., Xing L., Wu H., Ma H. Federated Learning-Based Collaborative Authentication Protocol for Shared Data in Social IoV. IEEE Sens. J. 2022;22:7385–7398. doi: 10.1109/JSEN.2022.3153338. [DOI] [Google Scholar]
- 23.Zhang J., Cui J., Zhong H., Chen Z., Liu L. PA-CRT: Chinese Remainder Theorem Based Conditional Privacy-Preserving Authentication Scheme in Vehicular Ad-Hoc Networks. IEEE Trans. Dependable Secur. Comput. 2019;18:722–735. doi: 10.1109/TDSC.2019.2904274. [DOI] [Google Scholar]
- 24.Kanchan S., Choi B.J. An Efficient and Privacy-Preserving Federated Learning Scheme for Flying Ad Hoc Networks; Proceedings of the ICC 2022—IEEE International Conference on Communications; Seoul, Republic of Korea. 16–20 May 2022; pp. 1–6. [DOI] [Google Scholar]
- 25.Lin H.-T., Jhuang W.-L. Blockchain-Based Lightweight Certificateless Authenticated Key Agreement Protocol for V2V Communications in IoV. IEEE Internet Things J. 2022:15. doi: 10.1109/JIOT.2024.3400320. [DOI] [Google Scholar]
- 26.Jiang Y., Zhang K., Qian Y., Zhou L. Anonymous and Efficient Authentication Scheme for Privacy-Preserving Distributed Learning. IEEE Trans. Inf. Forensics Secur. 2022;17:2227–2240. doi: 10.1109/TIFS.2022.3181848. [DOI] [Google Scholar]
- 27.Ma Y., Cheng Q., Luo X. 2PCLA: Provable Secure and Privacy Preserving Enhanced Certificateless Authentication Scheme for Distributed Learning. IEEE Trans. Inf. Forensics Secur. 2023;18:5876–5889. doi: 10.1109/TIFS.2023.3318952. [DOI] [Google Scholar]
- 28.Xiong H., Chen J., Mei Q., Zhao Y. Conditional Privacy-Preserving Authentication Protocol With Dynamic Membership Updating for VANETs. IEEE Trans. Dependable Secur. Comput. 2020;19:2089–2104. doi: 10.1109/TDSC.2020.3047872. [DOI] [Google Scholar]
- 29.Zhong H., Wang L., Cui J., Zhang J., Bolodurina I. Secure Edge Computing-Assisted Video Reporting Service in 5G-Enabled Vehicular Networks. IEEE Trans. Inf. Forensics Secur. 2023;18:3774–3786. doi: 10.1109/TIFS.2023.3287731. [DOI] [Google Scholar]
- 30.Yuan X., Liu J., Wang B., Wang W., Li T., Ma X., Pedrycz W. FedComm: A Privacy-Enhanced and Efficient Authentication Protocol for Federated Learning in Vehicular Ad-Hoc Networks. IEEE Trans. Inf. Forensics Secur. 2023;19:777–792. doi: 10.1109/TIFS.2023.3324747. [DOI] [Google Scholar]
- 31.Zhang Y., Lei H., Wang B., Wang Q., Lu N., Shi W., Chen B., Yue Q. Traceable ring signature schemes based on SM2 digital signature algorithm and its applications in the data sharing scheme. Front. Comput. Sci. 2024;18:182815. doi: 10.1007/s11704-023-3318-z. [DOI] [Google Scholar]
- 32.SM2 Elliptic Curve Public Key Cryptographic Algorithm Part 2: Digital Signature Algorithm. National Standard of the People’s Republic of China; Beijing, China: 2012. [Google Scholar]
- 33.Eltaras T., Sabry F., Labda W., Alzoubi K., Ahmedeltaras Q. Efficient Verifiable Protocol for Privacy-Preserving Aggregation in Federated Learning. IEEE Trans. Inf. Forensics Secur. 2023;18:2977–2990. doi: 10.1109/TIFS.2023.3273914. [DOI] [Google Scholar]
- 34.Maurya C., Chaurasiya V.K. Efficient Anonymous Batch Authentication Scheme with Conditional Privacy in the Internet of Vehicles (IoV) Applications. IEEE Trans. Intell. Transp. Syst. 2023;24:9670–9683. doi: 10.1109/TITS.2023.3271355. [DOI] [Google Scholar]
- 35.Horng S.-J., Tzeng S.-F., Pan Y., Fan P., Wang X., Li T., Khan M.K. b-SPECS+: Batch Verification for Secure Pseudonymous Authentication in VANET. IEEE Trans. Inf. Forensics Secur. 2013;8:1860–1875. doi: 10.1109/TIFS.2013.2277471. [DOI] [Google Scholar]
- 36.Cui J., Zhang J., Zhong H., Xu Y. SPACF: A Secure Privacy-Preserving Authentication Scheme for VANET With Cuckoo Filter. IEEE Trans. Veh. Technol. 2017;66:10283–10295. doi: 10.1109/TVT.2017.2718101. [DOI] [Google Scholar]
- 37.Yang Y., Zhang L., Zhao Y., Choo K.-K.R., Zhang Y. Privacy-Preserving Aggregation-Authentication Scheme for Safety Warning System in Fog-Cloud Based VANET. IEEE Trans. Inf. Forensics Secur. 2021;17:317–331. doi: 10.1109/TIFS.2022.3140657. [DOI] [Google Scholar]
- 38.Lin C., Huang X., He D. EBCPA: Efficient Blockchain-based Conditional Privacy-preserving Authentication for VANETs. IEEE Trans. Dependable Secur. Comput. 2022;20:1818–1832. doi: 10.1109/TDSC.2022.3164740. [DOI] [Google Scholar]
- 39.Shen J., Liu D., Chen X., Li J., Kumar N., Vijayakumar P. Secure Real-Time Traffic Data Aggregation with Batch Verification for Vehicular Cloud in VANETs. IEEE Trans. Veh. Technol. 2019;69:807–817. doi: 10.1109/TVT.2019.2946935. [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Data are contained within the article.