Abstract
The rise of Electric Vehicles (EVs) has introduced significant advancement and evolution in the electricity market. In smart transportation, the EVs have earned more popularity because of its numerous benefits including lower carbon footprints, higher performance, and sophisticated energy trading mechanisms. These potential benefits have resulted in widespread EV adoption across the world. Despite its benefits, energy management remains the biggest challenge in EVs and it is mainly because of the lack of Charging Stations (CSs) near EVs. This creates a demand for an effective, secure and reliable energy management framework for EVs. This study presents a secure data and energy trade paradigm based on Blockchain (BC) in the Internet of EVs (IoEV). BC technology prepares for the high volume of EV integration that serves as the foundation for the next generation, and to assist in developing unique privacy-protected BC-based D-Trading and storage Models. Entities evaluated for the proposed model include Trusted Authority (TA), Vehicles, Smart Meters, Roadside Units (RSU), BC, and Inter-Planetary File System (IPFS). In addition, E-trading involves several phases, including the acquiring E-trading demand requests, E-trading response requests, request matching and token assignment. Moreover, account mapping is performed using a Mayfly Pelican Optimization Algorithm (MPOA), which is created by merging the Mayfly Algorithm (MA) and Pelican Optimization Algorithm (POA). Various security features are used to protect data and energy trade in IoEV, including encryption, hashing, polynomials, and others. The testing results revealed that the MPOA outperformed the state-of-the-art results regarding memory consumption, trading rate, transaction cost, and trading energy volume with values of 4.605 MB, 91%, 0.654, and 90 kW, respectively.
Keywords: Internet of electric vehicles, Pelican Optimization Algorithm, Blockchain, Inter-planetary file system, Energy trading
Subject terms: Energy science and technology, Engineering
Introduction
The rapid development of vehicular telematics and its advanced technological characteristics has enabled vehicles to generate a wide range of data. Modern automobiles are refitted with communication and data exchange capabilities to interact with their surroundings. IoV is gaining popularity among academics and industry due to its significant research value and commercial potential1,2. In addition, IoV is steadily evolving due to vehicle data exchange and connectivity, allowing for an efficient and intelligent transportation system. However, the inclusion of Electric Vehicles (EVs) in IoV has resulted in the Internet of Electric Vehicles (IoEV)3,4. EVs are superior than traditional cars in terms of energy saving and environmental protection5,6. EVs can purchase power during periods of low voltage and sell it during periods of high voltage, fulfilling the function of “shaving peaks and eliminating valleys”3,6. Moreover, EVs are gaining popularity as a means of lowering total reliance on fossil fuel-powered vehicles and greenhouse gas emissions. However, as the number of EVs grows, unorganized charging generates a new peak load. The reason is that it produces significant energy instability in the distributed energy system. To address this issue, the power distribution capacity is upgraded to meet the needs of the new peak demand caused by unorganized EVs. However, this incurs a high infrastructure cost7,8. Compared to traditional gasoline vehicles, EVs are more environmentally beneficial since they have reduced operating expenses and emit nearly zero carbon dioxide. Furthermore, EVs play an important role in regulating smart cities’ energy needs9.
Nowadays, energy system reform for energy sharing amongst EVs is an essential issue that must be addressed. There are minimal energy sources available, but the need for energy is growing, which is a more significant issue in emerging nations. As a result, it is vital to create an energy-sharing system that balances demand and supply10. However, EVs need help with energy trading, which limits their participation in vehicle-to-grid (V2G) energy sharing9,11. Among these, when EVs sell energy via remote servers, security concerns remain the essential in successful transactions9. In this sense, BC has emerged as one of the most significant technologies, effectively addressing system security requirements9,12. Satoshi Nakamoto introduced the distributed ledger technology known as BC in 200813,14. BC is simply a distributed ledger database that uses a consensus technique to audit and preserve data consistency in each node, resulting in faithless consensus among trading partners15,16. The trading data in the BC can be traced and verified by connecting the blocks in chronological sequence and adding the previous block’s hash value to the next17,18. BC uses hashing algorithms and cryptographic signatures to ensure that data is not tampered with or falsified, hence ensuring trading security. Furthermore, the BC ensures the anonymity of the user’s identity by employing a fresh key pair in each transaction to protect privacy19.
BC-based energy trading platforms have transformed traditional energy markets into consumer-centric markets, allowing customers to trade and manage energy more effectively. In comparison to traditional energy trading systems, BC-based energy trading systems have evolved as innovative market designs to encourage local energy trade20. Other challenges with Vehicular Energy Networks (VENs) include selfish behavior of EVs and CSs, long distances between nodes, the cost of getting to the CSs, and so on. Numerous energy trade and secure data techniques are introduced To address the concerns21. An alternative approach is to take advantage of EVs’ two-way energy trading capability, which can be effectively used for grid peak load transfer, enhance energy efficiency, and minimize transmission loss, and during peak hours, energy is delivered back to the grid15,22. Furthermore, an incentive system, such as money or reputation, is provided to encourage nodes to conduct efficient energy trading21. Demand-response (DR) methods are presented, which allow EV owners to modify their energy usage based on charging time and price. Moreover, this method also allows customers to move their energy demand from peak to off-peak hours, lessening the strain on energy infrastructure and providing energy at a reasonable cost. However, other difficulties remain, such as privacy leakage, best pricing methods, and a need for customer satisfaction23. Noise-based techniques are also employed to achieve differential privacy in records; however, they do not give accurate information3. Privacy-preserving consortium BC energy trading mechanism is introduced in smart grid using BC to guarantee the anonymity of energy transactions that do not participate in the trading process6.
The primary goal of the work is to build a secure data transactions and energy trading model in IoEV based on BC. Here, account mapping is done by MPOA to collect coins based on predefined criteria throughout the transaction process, in which MA and POA hybridize MPOA. The POA aims to simulate pelicans’ normal hunting behaviors. In POA, search agents are pelicans looking for food supplies by balancing exploration and exploitation to provide optimal solutions for solving optimization issues. MA is inspired by the behavior of adult mayflies, including mutation, crossover, swarm gathering, and so on, and offers significant advantages for both local and global search capabilities. Thus, combining MA and POA provides better energy trading and secure data transactions. Moreover, the InterPlanetary File System (IPFS) enables fault-tolerant and reliable data storage with no single point of failure, ensuring consistent availability of traded data. This model considers two scenarios, one based on D-trading and storage and the other on E-trading, which uses trend screening to preserve EV anonymity.
The main contribution of this study is,
The MPOA for account mapping provides a safe data and energy model for IoEV-based BCs. To prevent data linkage assaults, this MPOA hides E-trading patterns using earlier EV trading records. MPOA is developed by combining the MA and the POA.
MA is inspired by the actual behavior of mayflies, precisely the attraction of males to females. It adheres to the concepts of crossover, mutation, and selection. MA outperforms in terms of transaction speed. Moreover, POA is a proper balance between the exploration and exploitation stages. Thus, it provides secure data transactions.
IPFS, an external distributed storage system is introduced to provide dependable and convenient access to traded data, ensuring availability. It allows concurrent access to uploaded files without any delays.
This paper is organized as follows: Section “Literature survey” contains literature evaluations of strategies based on BC with energy trading, and section “IoEV architecture” specifies the IoEV system design with model. Section “Proposed MPOA for BC-based data and energy trading” explains the MPOA for account mapping, Section “Results and discussion” discusses the findings of the built model, and Section “Results and discussion” concludes the paper.
Literature survey
Long Luo A et al.5 have introduced a BC-based architecture for exchanging power between vehicles and grids (V2V/V2G). EV energy transactions were recorded on the BC for privacy, and smart contracts were used to optimize price and energy allocation. In addition, a Bayesian game-enabled two-way auction mechanism and a novel pricing technique were devised to improve the transaction success rate. Each Local Energy Aggregator (LEAG) deploys a prewritten smart contract using a Bayesian game-based bidirectional auction algorithm to ensure transaction data dependability and security,. The method achieved higher social welfare and cost performance, but an energy trading network was still not created for charging and discharging EVs on the road.
Ayesha Sadiq et al.3 have used consortium BC to keep trade activity transparent and trustworthy. In addition, data duplication is validated at roadside units (RSUs) using a previously saved hash list and bloom filters for efficient search. Removing data duplication at an early stage lowers storage costs. A digital signature technique based on elliptic curve bilinear pairing was introduced to ensure the trustworthiness and integrity of traded data. Moreover, the InterPlanetary File System (IPFS) was utilized to enable fault-tolerant and reliable data storage with no single point of failure, ensuring consistent availability of traded data. Also, a generation approach was employed to mask energy trading tendencies. An EV generates new accounts based on its energy trading volume. This efficient method saves time and provides a trustworthy data-storing mechanism. However, the technique needed to implement a reliable and efficient service delivery mechanism, by introducing monitoring authority to ensure RSUs offer quality services.
Abid Jamal et al.13 devised a secure and efficient BC-based reputation management method for Vehicular Energy Network (VEN). This method secures vehicle reputations and prevents replay assaults. An Elliptic Curve Digital Signature Algorithm was introduced, enabling a pseudonym mechanism for conditional anonymity and vehicle tracing. Moreover, the InterPlanetary File System was utilized to store vehicle reputation information efficiently. The method reduces storage overhead but takes longer time to respond.
Muhammad Umar Javed et al.21 have developed a BC with energy trading algorithm that prioritizes necessary energy requests, discards duplicate ones, and determines the distance between EVs and Charging Stations (CS). Matching and Pairing Pool was also utilized for storing energy and payment requests. Moreover, a BC-based method was used to guarantee effective EV coordination at unsignalized crossings and crossroads. Before EVs are integrated into a VEN, the technique uses a Registration Authority (RA) to authenticate them. As the number of EVs grows, so does the volume of communications, causing data redundancy issues. The message filtration was used to resolve the issue. A Local Aggregator (LAG) also serves as an energy broker, overseeing trade events and transaction validation. The strategy lowered risk and saved time by storing fewer redundant data. However, recent attacks still need to be addressed to improve system security.
Haiqing Liu et al.6 developed EV power trading mechanism was developed by based on BC and smart contracts to achieve information equivalency and transparent openness of power trade. This model was built on the BC and innovative contract technology. To account for the unpredictable nature of EV charging and discharging, EV trading parties used a reverse auction with a dynamic pricing strategy to match transactions. This method benefits the less competitive power seller, but lowers the cost of electricity for the purchaser.
Yuancheng Li and Baiji Hu19 devised a better heuristic algorithm, named Adaptive Inertia Weight Krill Herd (KH) to address the mixed-integer programming (MIP) issue. To guarantee the security and privacy of two-way power trading between EVs and the smart grid, a decentralized trading architecture and associated electricity trading procedure was created based on the consortium BC. The method efficiently smooths power load variations and substantially improves the efficiency of the model solution. However, no economic incentives were included in this technique to encourage EVs to deliver vehicle-to-grid services to the smart grid.
Prince Waqas Khan and Yung-Cheol Byun14 have presented a BC-based peer-to-peer energy trade and charging payment system for electric cars. Users can sell excess electricity to charging stations through intelligent contracts. Electric vehicle customers can use electronic wallets to pay their charging bills. We created an automatic payment system for electric vehicles using Hyperledger Fabric, an open-source platform. The method has improved EV participant’s trust, transparency, and privacy by reducing human involvement. However, this method did not add cryptocurrency for EV charging payments.
A BC -based energy trading mechanism was developed by Tehreem Ashfaq et al.23 to ensure security. Within a VEN, this model addressed issues related to energy trade, such as insecure energy trading and ineffective EV charging systems. Moreover, BC enables effective communication between EVs and aggregators. Moreover, a branching idea was used to divide EV data into two branches: Integrity Chain (I-chain) and Fraud Chain (F-chain). This method improved storage efficiency and reduced the processing time. However, vehicular systems did not employ a revolutionary variable pricing structure, enabling customers to charge their automobiles at affordable rates. Table 1 shows the related work.
Table 1.
Relevant work.
| Author | Method | Advantages | Disadvantages |
|---|---|---|---|
| Long luo a et al.5 | Bayesian game-enabled two-way auction mechanism | The method works with several types of actual energy transactions | Cross-LEAG energy trade between EVs was not considered for better energy trading |
| Ayesha sadiq et al.3 | BC-based D-trading scheme | The EV trading trends were successfully hidden | Need to consider a rating-based reputation system to improve the system’s performance |
| Abid jamal et al.13 | BC-based secure and efficient reputation management method | Efficiently stored the IPFS hash data instead of the actual data on BC | Unavailability of data and the highest communication cost |
| Muhammad umar javed et al.21 | BC with energy trading algorithm | Addressed low and high-range anxiety produced by VENs | Took additional time at the charging entity |
| Haiqing liu et al.6 | EV power trading mechanism | The transaction was speedy | Failure to coordinate safety and efficiency |
| Yuancheng li and baiji hu19 | Adaptive Inertia Weight KH | Improved the speed, accuracy, and good scalability | Need more confirmation time |
| Prince waqas khan and yung-cheol byun14 | BC-based peer-to-peer energy trade and charging payment system | Addressed trust and privacy concerns with electric car charging | Need to consider machine learning for improved analysis, price prediction, and optimal routes to nearby charging stations |
| Tehreem ashfaq et al.23 | Secure energy trading method | Effectively decreased the charging costs and time in a VEN | Dependency of Timestamp, Re-entrancy vulnerability, Callstack depth vulnerability, and Dependency of Transaction ordering should have been tackled to improve the system’s performance |
Below are the difficulties encountered in the relevant job
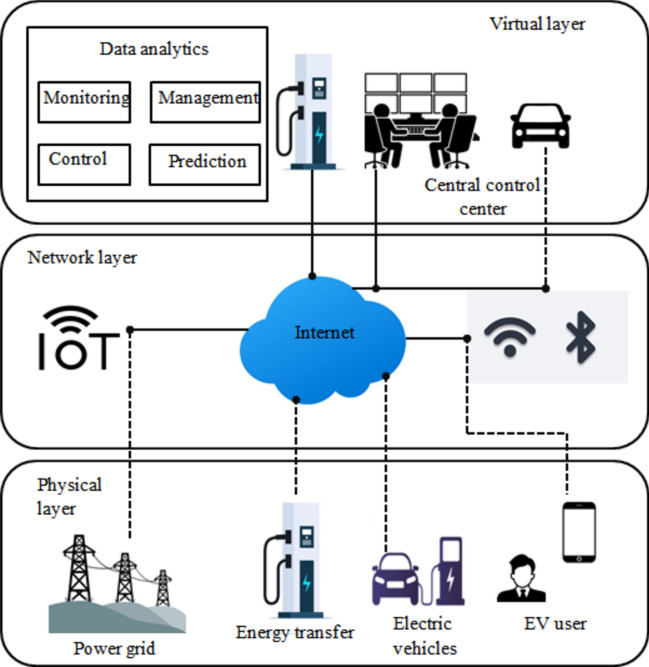
In recent years, many traditional vehicles have been converted into electric vehicles. These intelligent and electric vehicles come together to form a VEN. The interaction of automobiles in these networks is advantageous. However, there are also significant concerns with VENs, such as a need for charging stations, charging station load changes, ineffective energy management etc. Energy trading systems typically use a centralized approach to coordinate transactions between EVs and other IoV objects (such as charging stations). This technique increases the likelihood of a single point of failure, raising the associated cost. Within IoV applications, all EVs are viewed as fast-moving objects that frequently go along roads. Similarly, the operating speeds of the vehicles can vary, resulting in various mobility patterns, particularly for manually driven vehicles. The mobility of nodes in the IoV makes it difficult to analyze the number of nodes participating in the network accurately. Furthermore, even if vehicles have the necessary energy to use computational and communication resources when connecting with nearby objects, they need help maintaining consistent connections due to their variety and rapid mobility, which may pose additional challenges. One example is the difficulties of delivering crucial vehicle data due to limited transaction times induced by the cars’ previously described mobility issues. The IoV requires robust security and privacy solutions to avoid misleading and harmful information transfers between vehicles. Such incidents might cause accidents, endangering drivers, passengers, and pedestrians. IoV security concerns can be grouped into physical, communication, and application. At the physical level, the various IoV components (for example, EVs, Road Side Units (RSU), etc.) are vulnerable to unauthorized access and illegal conduct, resulting in a danger to data security and dependability.
IoEV architecture
Smart transportation
Smart transportation or intelligent transportation system indicates the integrated application of advanced technologies to control and regulate transportation systems to improve safety and efficiency. The primary objective of this smart system is to provide innovative services interconnecting different modes of traffic and transport management. This also provides better information to the users, which allows them to move more safely and conveniently around the city.
Charging stations
A charging station also known as the charge point is a power supply device that supplies electrical power for recharging plug-in EVs. Generally, there are two different kinds of EV chargers: Alternating Current (AC) CSs, and Direct Current (DC) CSs. EV batteries can only be charged by DC electricity but the power grid delivers only AC power. Thus, an AC-to-DC converter is integrated into the EVs.
IoEV
The IoEV is an intelligent network that connects EVs with other EVs over the internet connection. This connection enables the EVs to communicate and share data with other EVs, CCs, and power grids. To make this communication, the IoEV uses advanced technologies such as Internet of Things (IoT), cloud computing (CC), etc. Usually, an On-Board Unit (OBU) is incorporated in EVs, which allows Vehicle to Vehicle (V2V) and Vehicle to Infrastructure (V2I) communications. These communications help the vehicle to trade and share information in the IoEV framework. These features of IoEV help the EVs to find optimal routes, manage traffic and reduce charging time. This not only saves energy but also helps in enhancing the performance of the vehicles.
System model
In a transportation network, EVs are examined for travel from the source site to defined destinations. Network transportation is represented by a graph , where and denote sets of nodes and edges, respectively. A node might be a road intersection, an EV’s destination/starting point, or the location of the charging station. Here, an edge symbolizes a road segment that connects two close nodes. Consider two types of charging stations in network transportation. The Type-1 charging station is located in a suburb and is disconnected from the grid. This employs renewable energy to charge electric vehicles and has enough area to install energy-gathering devices such as solar panels and wind turbines. Type-1 charging stations do not purchase energy from EVs because they are installed to transfer captured renewable energy to EVs. Simultaneously, a type 2 charging station is positioned in an urban area with a decent power grid connection but limited space to install energy harvesting devices. Type 2 charging stations sell and buy electricity from electric vehicles. Type-2 charging stations are strategically placed so a fully charged EV has enough energy to go from one type-2 charging station to the next. Furthermore, EVs only charge at type-2 charging stations on their trip from source to destination 24.
The node sets used to install type-1 and type-2 charging stations are labeled as and . Furthermore, the selling price of electricity at all type-1 charging stations is the same, represented as . Furthermore, for type-2 charging stations, power selling and purchasing prices are denoted as and , respectively, which are believed to be equal for all type-2 charging stations. Additionally, electricity buying and selling prices for type-2 charging stations are indicated as and , presumed to be the same for each type-2 charging station. Furthermore, the sale price should not be less than the buying price, which means . Again, renewable energy has a low generation cost of type-1 charging stations, at type-1 charging stations are predicted to be substantially smaller than and . To continue traveling, an EV must also have non-zero leftover energy at the destination node. An EV should have remaining energy at the destination node, assuming simplicity without lossing generality. EV energy costs vary depending on charging decisions and routes. IoEV’s system model is depicted in Fig. 1.
Figure 1.
System model for IoEV.
IoEV problem definition
For problem formulation, stands for the set of all EVs in the system. When considering EVs, , the energy capacity is denoted as , the source node is , and the destination node is . In addition, the path with a sequence of nodes traversing to from is denoted as , and is defined as a collection of possible loop-free paths connecting nodes and . The charging stations set in the path are represented by the node sets and , which are installed with type-1 and type-2 stations in the path . is the number of charging stations set up in the path , which equals , and is the distance between and in the path .
Energy framework
The energy framework calculates the energy spent by cars throughout their driving pathways. Each EV selects only one path, which is formulated as,
| 1 |
The initial energy of the take path can be stated as,
| 2 |
where represents the EV’s preliminary energy at the source node, and represents the selected path . The energy of leaving and entering a node is given as,
| 3 |
where is the distance between nodes and , and represents the amount of energy EV utilizes per unit of distance. The energy of for learning is expressed as,
| 4 |
| 5 |
where is the energy upon entering the node . represents the energy of an EV charged at a type-2 charging station at a node . represents the energy of an EV discharged at a type-2 charging station placed at the node .
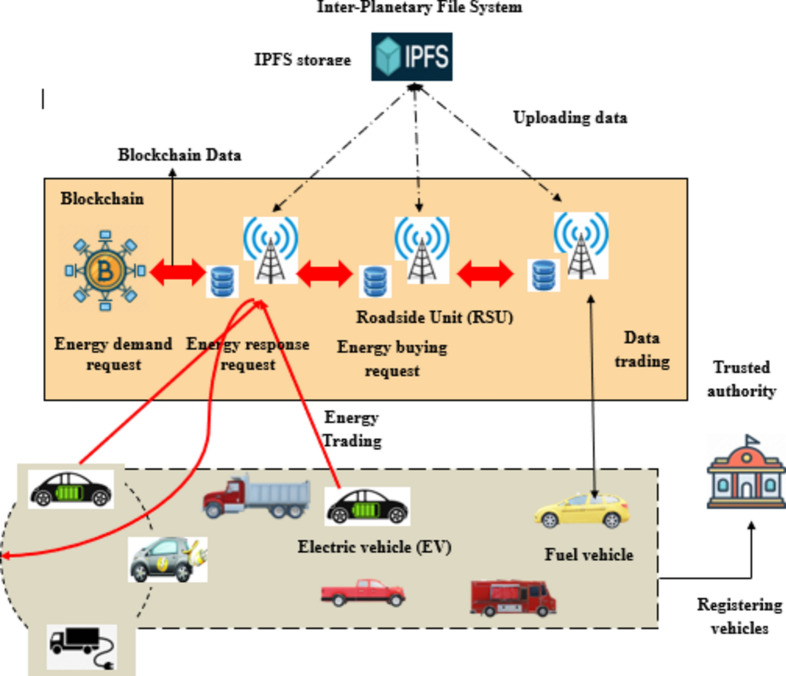
Proposed MPOA for BC-based data and energy trading
The goal is to create a revolutionary safe data and energy trading paradigm based on BC in IoEV, which provides a dispute-free trading environment with a trustworthy data storage mechanism. Thus, the account mapping is accomplished by developing an efficient model MPOA, created by merging the POA25 with MA26. The MPOA model consists of three layers: the lowest level vehicular layer, the intermediate infrastructure layer, and the top storage layer, as seen in Fig. 2. The vehicular layer consists of IoEV nodes or automobiles that communicate with one another via Vehicle-to-Infrastructure (V2I). RSUs form the infrastructure layer, with the consortium BC as the underlying technology, and they are linked directly to one another via a cable connection. The third layer is a storage layer built with IPFS to store trading data.
Figure 2.
Block diagram for MPOA in IoEV that uses BC technology to trade data and energy.
Blockchain
BC technology is being hailed as groundbreaking invention because of its potential features and performance in trustless contexts. It is a decentralized distributed ledger that stores time-stamped records. There is no central controlling authority, and each node keeps a copy of its digital ledger. All BC records are publicly verifiable and visible to all nodes in the network. After a successful transaction validation via a consensus method, a block is formed and added in chronological order. Each block is linked to the previous one via a unique cryptographic hash, making it unchangeable. The consensus method updates and synchronizes the public ledger across all nodes. The consensus method ensures that all participating nodes agree on the validity of transactions. There are various consensus methods, such as Proof of Authority (PoA), Proof of Stake (PoS), Delegated Proof of Stake (DPoS), and Proof of Work (PoW). The consensus technique is chosen based on network restrictions; nonetheless, PoW is considered more secure than alternative consensus algorithms. There are two ways to utilize BC. The first is permissionless BC, which allows nodes to join the BC network without requiring permission, also known as public BC. The second is permissioned BC, often known as private BC, which uses access control to limit the number of participating nodes. Only approved nodes can read and write on a private BC.
To integrate BC into the IoEV environment, a decentralized ledger was created that assumes all EVs and CSs as nodes within the blockchain. Then, the BC records all energy transfers between the buyers (EVs) and sellers (CSs) as transactions. These transactions are then added to the ledger after securing it using cryptographic techniques. Consequently, a consensus algorithm named PoW was employed for validating the transactions and creating a new block in the blockchain. This algorithm aims to bring all the nodes in the BC module in agreement (trust one another) and it verifies the transactions through the mining process. Mining indicates the process of solving computationally complex and challenging puzzles for creating new blocks in the BC module. The nodes engaged in the mining process are defined as miners. Thus, this protocol verifies each transaction within the IoEV network, offering security and data integrity. Thus, the integration of blockchain into the IoEV network offers a reliable and effective solution for data sharing between the EVs, CSs and energy providers.
Entities used in the developed model
The entities utilized in the developed framework are defined below,
Trusted authority (TA)
TA is responsible for registering the IoEV nodes in the network. In this process, the vehicles are registered as IoEV nodes, and RSUs as energy and data brokers. In addition, the TA is also responsible for mitigating malicious vehicles in the network; thus, it regulates the entire IoEV network by ensuring security and strength to the system. All incoming vehicles register themselves by offering their information to TA before joining the IoEV network. This registration process is typically done in offline mode and the vehicles provide important information such as mobile number, name, address, etc. After registration, TA provides initial security metrics to each vehicle. Because of its higher computational power, communication efficiencies and storage, TA is considered to be impenetrable to adversaries. Moreover, each state has its own TA that functions to validate each vehicle’s credentials from its corresponding registered state.
Vehicles
In the IoEV network, vehicles represent EVs and other fuel vehicles. The fuel vehicle has the capacity of performing D-trading, while the EVs can perform both D-trading and E-trading. However, in the proposed framework, EVs are made to perform only E-trading. Typically, in the D-trading process, the vehicles either act as data seller or buyer, while in E-trading the EVs act either as energy buyers or sellers depending upon the energy requirements. The communication and computational efficiency of OBU allows the vehicles to interact with RSUs for E-trading or D-trading.
Smart meters
In the IoEV network, the charging units are incorporated with a smart meter that measures the total energy traded by seller EVs. This measured energy volume assists buyer EVs to pay the amount or price for the traded energy.
RSUs
RSUs act as both energy and data brokers for managing and regulating the D-trading and E-trading requests. The RSUs work collaboratively with the BC. Hence, a common digital ledger is shared among all RSUs. Furthermore, they are responsible for regulating E-trading and D-trading requests, validating duplicate data, account mapping of vehicles, and uploading traded data to IPFS.
IPFS
IPFS is an open source, content addressable, P2P distributed network responsible for storing and sharing data. It employs a network of interconnected computers without any central coordinating entity. Each data stored in IPFS is given with a distinct cryptographic hash. Also, it utilizes the basic ideology of Distributed Hash Tables (DHTs) to access files in the network.
Illustration of the MPOA
The proposed Mayfly Pelican Optimization Algorithm (MPOA) combines the efficiency of Mayfly Algorithm (MA) and Pelican Optimization Algorithm (POA) for secure data sharing and trading in the BC-based IoEV system. MA is a meta-heuristic optimization approach that is modeled based on the movements of masculine and feminine mayflies. It is inspired from the flying characteristics and also the mating strategies of the mayflies. The major advantage of the MA approach is that it integrates other optimization techniques including swarm optimization (PSO) with the evolutionary algorithm (GA), offering improved solutions than the existing techniques. In addition, the movement of the mayflies replicates the nuptial dance model, which enhances the flexibility, and stability of the algorithm within the exploration and exploitation strategies. Also, it offers faster convergence, which helps in increasing the transaction speed. On the other hand, POA was a nature-inspired optimization algorithm designed based on the natural characteristics of the pelicans during foraging. In this approach, pelicans are search agents who search for food sources. In this algorithm, each member in the population is considered as the candidate solution, and they possess fitness value based on their position in the search space. Here, the exploitation phase defines the movement of candidate solutions towards the prey and the exploitation phase indicates winging on the water surface. The methodology is computationally effective and offers greater balance between exploitation and exploration phases.
In MPOA, the distinct features of MA and POA are integrated to optimally share and trade data and energy in the IoEV network. This merging enables the system to respond to the changing conditions such as energy demands, vehicle availability, energy availability, traffic records, etc. This improved adaptability of the proposed MPOA provides quick decision-making; thereby reducing the time consumption. Also, this hybrid algorithm helps the system to effectively manage complex interactions including handling energy demand requests, processing of trade requests, entity registration process, and data protection within the IoEV environment. This integration helps in addressing the scalability issue inherent within the blockchain technology by making the system more flexible over new different scenarios. In addition, this algorithm incorporates the computationally effective feature of POA, which enables the system to handle large volumes of transactions more quickly than conventional techniques.
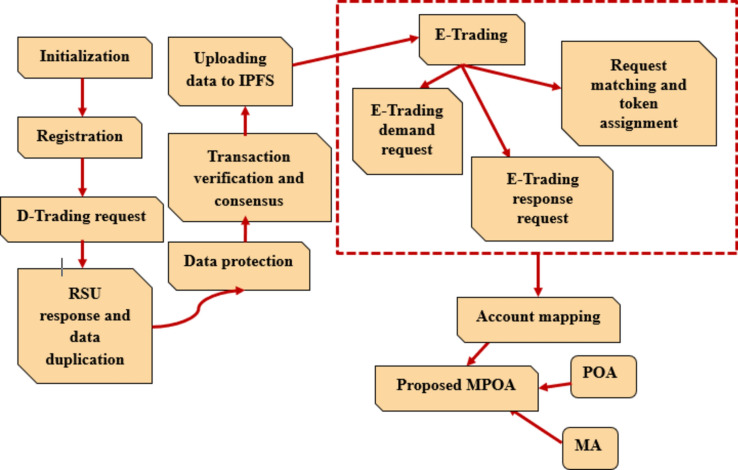
TA, smart meters, vehicles, BC, RSU, and IPFS are some entities considered in the MPOA model. It considers two main scenarios: D-trading and storage, Screening E-trading trends to protect the privacy of EVs. D-trading consists of eight processes, Initialization, registration, D-trading request, RSU response and data duplication validation, data protection, transaction verification and consensus, IPFS uploading, and E-trading. E-trading has three steps: demand requests, response requests, request matching and token assignment. Then, the account mapping is done based on the MPOA. The MPOA is the integration of POA and MA. To maintain data and energy trading in IoEV, the protection model employs a variety of security qualities such as encryption, hashing functions, and polynomials. Figure 3 displays the processing procedures for data security and energy trading in the IoEV.
Figure 3.
Diagrammatic representation of the produced MPOA.
The symbols used in the MPOA for data security and energy trade in BC with IoEV are described in Table 2.
Table 2.
IoEV energy trading symbols and description of the MPOA.
| Symbols | Descriptions |
|---|---|
| Verification message | |
| Hash function | |
| TA password | |
| TA ID | |
| Random numbers | |
| Vehicle ID | |
| Digital signature | |
| RSU password | |
| Data selling request | |
| Vehicle password | |
| RSU ID | |
| Data to be traded | |
| Certificate of vehicle | |
| Timestamp | |
| Chebyshev polynomial function | |
| Wallet address | |
| Encryption function | |
| Secret key | |
| Modulation function | |
| Interpolation function | |
| Data protected | |
| Current location of EV | |
| Payment message | |
| Key | |
| Response request | |
| Amount of Energy | |
| Energy buying price | |
| Parameter |
Initialization
The initialization process is carried out in TA. TA initializes the process using random numbers and a hash function in this case. Random numbers are , which fall within the range of , and the hash function is denoted as .
Registration
The second stage of BC-based safe data and energy trade is registration. The three stages that make up this registration procedure are explained below.
Registration between TA and IPFS
Registration between TA and IPFS considers various entities, including TA, BC, and IPFS. ID is initially produced in TA and designated as , which is then saved in BC as . Furthermore, this stored ID is preserved in IPFS as . In contrast, the password is created in TA and indicated as . This created password is stored in BC as , and then in IPFS as .Furthermore, IPFS generates a verification message , which is given by,
| 6 |
The verification message is created by hashing the stored IPFS ID , concatenating it with a random integer , and then XORing it with a random number . Next, an IPFS-generated verification message is saved in TA as , and this stored message is subsequently saved in IPFS as .
Moreover, IPFS, creates a random number by hashing the saved ID . This hashed result is then concatenated with a random number ; XORed with the generated verification message . The resulting Equation is as follows:
| 7 |
If the system generated random number matches the created random number , then TA is confirmed and registered with IPFS.
Registration between IPFS and RSU
Here, ID is produced in RSU and denoted as . This created ID is saved in TA as . Similarly, a password is established in RSU and represented as , which is then recorded in TA as .
| 8 |
The generated verification message is subsequently saved in RSU, and marked as . This saved verification message is again recorded in TA as .
Moreover, a random number is produced when the stored ID in TA is hashed using a hash function and concatenated with a random number . The verification message created in TA is then XORed with this hashed and concatenated result. The newly generated random number in TA is provided as,
| 9 |
Here, RSU is registered with TA if .
Vehicle and TA registration through RSU
Registration of Vehicle and TA via RSU is the third stage in the registration process between vehicle and TA via RSU, in which the ID and password are produced in the vehicle and denoted as and . This ID and password are kept in RSU as and , and then in BC as and . Additionally, the vehicle ID that is held in TA is hashed, concatenated with a random number , and then XORed with a random number . This creates verification message , which is expressed as
| 10 |
This verification message is saved as in the vehicle and in the TA. Here, a hashed vehicle ID that is kept in the TA is combined with a random number , XORed with a verification message , thus newly generated random number is generated. This is represented as,
| 11 |
Here, the equivalence of two random numbers is tested and if the freshly created random number equals the system random number , the vehicle is registered with TA.
D-Trading and storage
The D-trading and storage involves six major steps namely: (1) Initialization of system, (2) Registration, (3) D-trading request, (4) Validation of RSU response and data duplication, (5) Validation of transaction and consensus and (6) Uploading trading data to IPFS.
Step 1: System initialization
The TA yields two additive cyclic groups along with two generators for initializing the system. The generators create a third group of the same prime order. Then, the TA selects two random numbers as its master private keys for computing its public key and cryptographic hash function. Firstly, an EV submits its information for creating a pseudo-identifier and system parameters and the sequence of parameters published by TA include two generators, cyclic groups, hash function, and number of hash functions.
Step 2: Registration
When a vehicle joins the IoEV environment, the TA randomly selects a number and creates a secret key. Then, the TA allocates the pseudo-id to the vehicle instead of its original id for assuring anonymous communication within IoEV environment. In addition to this, TA controls the mapping between these two ids. The pseudo-ids are created for each vehicle in the network to confirm the validity of the data source.
Step 3: D-trading request
The vehicle generates a data-selling request at this phase, created by hashing the vehicle ID generated in the vehicle. The hashed output is concatenated with the trading data and the digital signature . Following this concatenation function, the produced outcome is linked with the hashed vehicle password and then joined with the time stamp . Finally, the generated outcome is used to create a data selling request, and then stored to RSU as . Lastly, a request for data selling is formed by the generated outcome. After that, this is stored in RSU as . In this case, a digital signature is created from a collection of vehicle certificates and a wallet address . The formula for D-trading requests is as follows:
| 12 |
where, .
Step 4: Validating RSU responses and the data duplication
This section discusses RSU responses and validates data duplication. First, RSU examines the time stamp and validity; if the result is yes, the session continues; otherwise, it is terminated. It also validates the vehicle password , which already exists in RSU, and if the seeking vehicle is not registered with TA, RSU refuses the trading request. Furthermore, if the vehicle password is correct, RSU determines whether data is already available, so data duplication is validated.
Data protection
RSU protects data by encrypting data to be traded and the key, which is represented as,
| 13 |
Here, represents the data to be traded, and the key is formed by XORing the interpolation term with the product of the Chebyshev polynomial function and the secret key saved in the RSU, and thus represented as
| 14 |
where denotes the Chebyshev polynomial function, is the interpolation term, and is the secret key stored in the RSU. Chebyshev polynomials are orthogonal polynomials with the largest possible leading coefficient whose absolute value on the interval [-1, 1] is bounded by 1. This function improves security by adding complexity to key generation by making the encryption and decryption more difficult. Thus, it restricts unauthorized access by third parties. The Chebyshev polynomial function and interpolation term are represented as follows:
| 15 |
| 16 |
The generated vehicle ID is concatenated with the secret key stored in RSU. Then, this result is modulated and hashed with a random number to create the parameter , which is represented as,
| 17 |
Step 5: Verification and consensus for transactions
The payment for the transaction is moved from the RSU to the data seller’s vehicle. First, the RSU hash function and concatenation function construct a payment message. The vehicle ID saved in RSU is concatenated with a random integer , which is then hashed and combined with the hashed secret key created in TA to form the payment message . The payment message created in RSU is as follows:
| 18 |
This RSU-generated payment message is recorded as in the vehicle and in BC. The previously saved payment message in the vehicle is saved again as in RSU. The payment message is then regenerated by comparing it to the previously saved payment message in RSU. Initial steps involve concatenating the vehicle ID stored in the RSU with a random number and hashing the result. The hashed result is then further linked with the hashed secret key, which is expressed as,
| 19 |
The payment transaction is validated and recorded in BC when the newly generated payment message and the saved payment message in RSU are equal . RSU also broadcasts data blocks for other RSUs to validate the block. Furthermore, BC rewards the winner RSU. In addition, the D-trading information is also recorded in the blockchain and trading transactions are validated by RSUs using PoW consensus mechanism. PoW approach validates the transactions and creates a new block in the blockchain. This technique brings all records in the BC module in agreement (trust one another) and it validates the transactions through the mining process. Mining indicates the process of solving computationally complex and challenging puzzles for creating new blocks in the BC module. The nodes engaged in the mining process are defined as miners. The usage of hash functions and consensus techniques prevents data duplications and unauthenticated data access. Also, it ensures data integrity and immutability to the transaction records.
Step 6: Data uploading to IPFS
When uploading data to IPFS, RSU uses a secret key to encrypt the data, which is then saved on IPFS through BC.
| 20 |
Here, IPFS stored data and stored keys are represented as and .
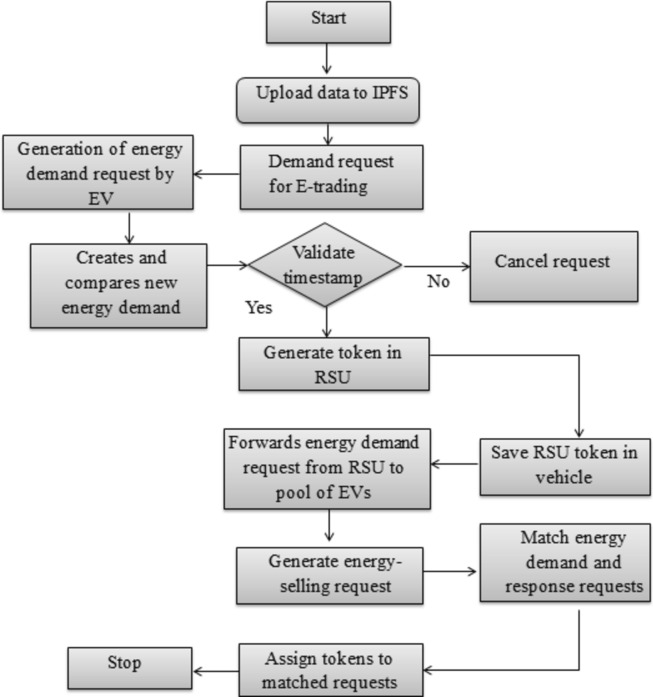
E-Trading
The E-trading procedure begins once the data is uploaded to IPFS. E-trading consists of E-trading demand requests, E-trading response requests, and request matching and token assignment.
Step 1: Upload the data into IPFS for initializing the E-trading process.
Step 2: Demand request for e-trading
- Generation of energy demand request by EV: When an EV consumes energy, it sends an energy purchase or demand request to RSU. The vehicle’s concatenation function generates the energy demand request in this case. The hashed vehicle ID is first concatenated with the EV’s current location, , and then with the energy buying price, . The produced result is then further concatenated with a time stamp and again concatenated with the amount of energy , forming energy demand request, which is represented as,
21 - RSU creates and compares new energy demand requests: Again, a freshly generated energy demand request is created in RSU and compared to the previously stored energy demand requests. First, the saved vehicle ID is concatenated and hashed with the EV’s current location, which is then concatenated with the energy purchase price. This concatenated result is then concatenated with the time stamp, forming a new energy demand request, and is expressed as,
22 -
RSU validates time stamp: RSU validates the time stamp, and if so, the session is continued; otherwise, it is canceled. If a newly generated energy demand request matches an existing recorded energy demand request in RSU , it is valid, and RSU assigns a token to the vehicle. In addition, the concatenation function generates tokens in RSU. Vehicle ID is first hashed, and this result is concatenated again with hashed vehicle password and further concatenated with energy purchase price, which produces the token and is denoted as,
23 The created RSU token is saved again in the vehicle as .
Step 3: Request for E-Trading response
- SU forwards energy demand request: When RSU receives an energy demand request from an EV, it forwards it to a pool of EVs. The received energy demand request from the RSU is generated by concatenating energy purchasing price, amount of energy, hashed energy demand request, and energy demand, represented by,
24 -
Generation of energy-selling request by EVs: In response to RSU’s forward request, EVs that want to sell energy send an energy-selling request to RSU. The response request is generated in the vehicle, which is formed by concatenating the hashed vehicle ID, amount of energy, and energy purchase price, and is presented as,
25 The resulting response request is then saved to RSU as .
Step 4: Request matching and token assignment
RSU matches requests and assigns tokens: RSU checks energy demand and response requests to match requests and assign tokens. Energy demand and response demand are matched, and if so, RSU determines energy and price. Following the matching, a token is allocated to both EVs, which is represented as,
| 26 |
A token is assigned in RSU by concatenating the hashed vehicle ID stored in RSU, the energy buying price, the current location of the EV, the amount of energy, , the hashed vehicle password and the time stamp contained in RSU. The generated token is then saved in the vehicle . The E-trading procedure is shown in Fig. 4.
Figure 4.
E-trading procedure.
Account mapping
In the account mapping technique, a coefficient of nuptial dance is used to determine whether coins should be transferred into a new or current account.
Case (i): If the number of coins sent is less than the coefficient of nuptial dance value, the transfer is made to the seller’s current account.
Case (ii): If the coin transfer amount exceeds the coefficient of nuptial dance value, a new account is opened for the seller EV.
The suggested MPOA, which is a combination of the MA and the POA, is used to detect the threshold value.
Determination of using MPOA
The nuptial ccoefficient value is required to determine whether coins should be transferred to the current account or a new account. This threshold value is thus found by a hybrid optimization algorithm, termed MPOA, which is combined by MA and POA. The POA algorithm considers pelicans as members of a population. In population-based algorithms, each member represents a candidate solution. Each population member suggests values for the optimization problem variables based on their position in the search space. Pelicans are highly skilled hunters due to their intelligence hunting habit and technique. Here, the POA is extremely efficient at addressing optimization concerns. MA draws inspiration from mayfly social behaviour, namely their mating process. The rate and speed of convergence are superior. The random flying and nuptial dance serve to make a better tradeoff between the exploitation and exploration phases, as well as to escape the local optima. Thus, combining the POA with MA improves overall system performance.
Initialization
The values of the lower and upper bound are used to initialize the population members, and the result is stated as,
| 27 |
where, represents the variable given by the candidate solution, the population member count, the problem variable count, the random number in , and and the lower and higher boundaries of .
Fitness computation
Fitness value represents the ideal answer for addressing the optimization problem and gives the best outcome for energy trading in the IoEV, formulated by,
| 28 |
where, and denotes the trading energy and rate.
Exploration phase
Following the fitness computation, the hunting strategy is initialized in two phases: exploration and exploitation. During the exploration phase, pelicans detect the specific position of prey by scanning the search space and then moving towards the selected places, improving the algorithm’s exploration capacity. Thus, the expression for pelicans moving towards the prey is depicted as,
| 29 |
When , the expression is provided by,
| 30 |
| 31 |
| 32 |
where, indicates the pelican new location in dimension for phase 1, provides the prey’s position in the dimension . To improve the POA exploration phase, the male mayfly’s movement update equation in MA is applied to POA update equation. According to MA, the male mayfly adjusts its location according on its own and its neighbor’s experiences. Let us consider represents the current position of the mayfly on the search space at time , and the position is adjusted by adding velocity to the current position, which is stated as,
| 33 |
The male mayfly’s velocity is stated as,
| 34 |
where, represents the velocity of the mayfly at time , represents the mayfly’s current position, and represents the positive attraction constants. Mayfly’s best personal solution is , and its greatest global solution is .
Here, the personal optimal solution is provided by,
| 35 |
The optimal global solution is provided by,
| 36 |
where, implies total number of mayflies.
The distance is provided as,
| 37 |
where, represents element of mayfly and is linked to or .
The best mayflies continuously modify their velocity, which is represented as,
| 38 |
where, denotes coefficient of nuptial dance, and be the random number range .
Substitute Eq. (34) into (33),
| 39 |
| 40 |
| 41 |
| 42 |
| 43 |
Substitute Eq. (43) in Eq. (32),
| 44 |
| 45 |
| 46 |
| 47 |
| 48 |
| 49 |
where, signifies the solution location in dimension at iteration, be the arbitrary constraint lies among . Thus, the Eq. (49) is the new update equation of MPOA.
Exploitation phase
After finding food, the pelicans stretched their wings throughout the water’s surface. Following that, the fish rise upwards in the water, allowing the pelicans to gather the fish in their pouch. This method in the proposed scheme increases the convergence rate in the hunting region. Furthermore, the exploitation phase boosts Pelicans’ search and exploitation rates. Furthermore, the mathematical description of the hunting process is given as:
| 50 |
where is the pelican new location in dimension for phase 2, is the constant, which is identical to 0.2, is the neighbourhood radius , is the iteration counter, and is the maximum number of iterations. In this phase, the update location is utilized to approve or reject the new position of the pelican, which is expressed as,
| 51 |
where, denotes the new pelican status, and denotes the phase 2 objective function. The security analysis of smart contracts demonstrates that they are bug-free and resistant to known threats.
Feasibility evaluation
Following the exploration and exploitation phases, the practicality of the MPOA is assessed using the fitness function. If the newly anticipated fitness exceeds the earlier values from the exploration and exploitation phases, the newly predicted value is considered ideal.
Termination condition
All of the aforementioned stages are repeated until a better solution is achieved. Algorithm 1 depicts the pseudocode of the MPOA algorithm.
Algorithm 1.
MPOA Pseudo code
In this study, the MPOA is developed by combining POA and MA, which is then used to find the coefficient of nuptial dance, allowing for secure data transaction and energy trading in IoEV.
Results and discussion
This section discusses the results and analysis of the MPOA for safe data and energy trade in the IoEV using BC technology.
Experimental setup
The proposed model is implemented in the MATLAB program using the Windows 10 operating system, an Intel core CPU, and 8 GB of RAM. The experiment is conducted using simulation, and the parameters used are listed in Table 3.
Table 3.
Parameter for simulation.
| Parameters for IoEV | |
|---|---|
| Stop time | 50 min |
| Number of vehicles | 100 |
| Spawn rate = No. of vehicles created per second | 6 |
| Iteration | 500 |
| Parameters for Lane | |
| Number of lanes | 2 |
| Length | 400 m |
| Width | 100 m |
Performance metrics
The performance of the MPOA is measured using trading energy volume, data trading rate, transaction cost, and memory consumption.
Trading Energy volume The distributed energy generation, combined with a large number of electrical loads, made energy supply and demand unstable and unpredictable. Trading energy volume is the volume that defines compensation for the energy required for trading and is measured in kilowatts (kW). This metric is determined by measuring the total amount of energy traded over the particular time period for increasing EV count. This involves the measurement of energy volume between the initial and final energy state.
Trading rate This parameter is thought to make EVs more accessible to a vast number of customers or businesses, encouraging them to start researching, producing, and developing EVs. For IoEV, the trading rate is expressed as a percentage. This is evaluated by dividing the number of successful transactions by the total number of transactions attempted and the obtained value is multiplied with 100 to express it in percentage.
Memory usage Memory usage is an important parameter since it is required to store operational data to achieve optimal energy trading data in IoEV, which is measured in MegaBytes (MB).
Transaction cost The cost added to the BC during the transaction process is the transaction cost, which is included in the deployment cost.
The evaluation of these metrics enables us to determine the performance and the robustness of the developed scheme in optimizing energy trading among the EVs in the IoEV environment.
Experimental outputs
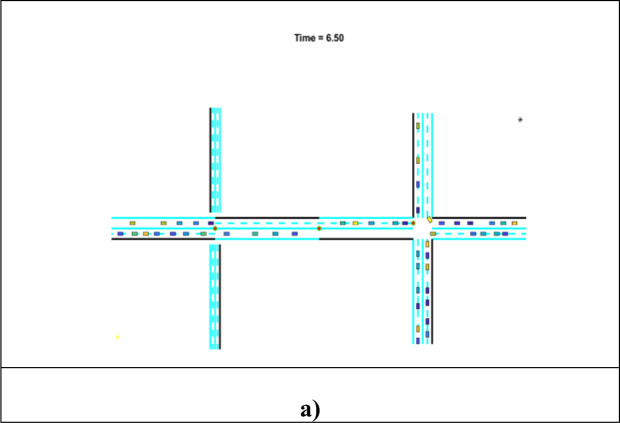
This section presents experimental results in a diagrammatic format, as seen in Fig. 5, for time intervals of 6.50 min. The star form represents the charging station, the rectangular shape with numerous colors represents vehicles traveling through the lane, and the blue dashed lines indicate the lane where two lanes are defined. In addition, an experimental setup is performed for every 0.50-min time interval, with 100 automobiles passing.
Figure 5.
Vehicles’ experimental outcomes at 6.50 min.
Evaluation of achievement
This section presents an analysis of the performance of the MPOA at different iterations (20, 40, 60, 80, and 100) with and without account mapping.
Performance Evaluation (in the presence of account mapping)
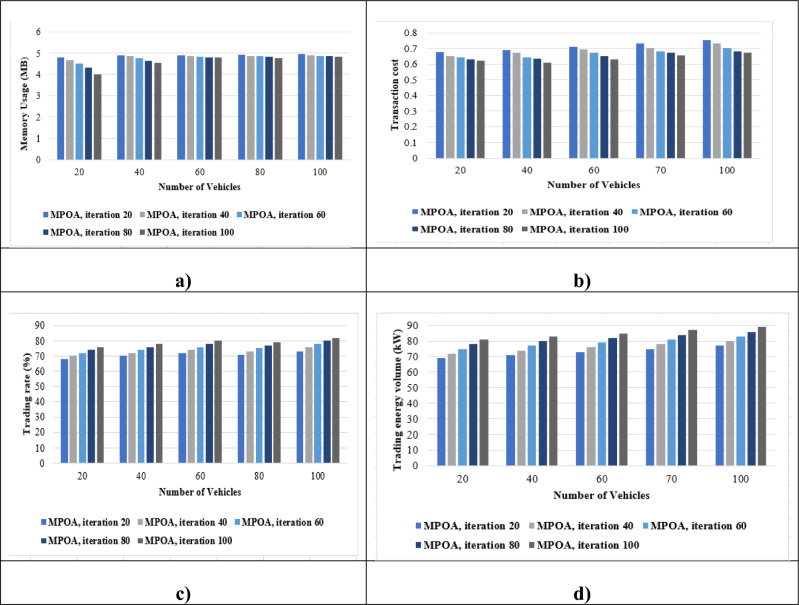
Evaluation in the presence of account mapping for the number of vehicles and several performance measures, such as trading rate, energy volume, transaction cost and memory consumption is shown in Fig. 6. Figure 6a depicts variations in memory consumption when compared to other approaches. When the number of vehicles is 60, memory utilization values are 4.791 MB for the MPOA with iteration 20, 4.9 MB for iteration 40, 4.861 MB for iteration 60, 4.829 MB for iteration 80, and 4.802 MB for iteration 100. Maximal memory usage grows with the increase number of vehicles. Figure 6b shows the transaction cost with account mapping. When the vehicle number is 40, the transaction cost for MPOA is 0.691, 0.671, 0.643, 0.634, and 0.61 for iterations (20, 40, 60, 80, and100). Increasing vehicles leads to linear decreases in storage costs, indicating scalability of the proposed system. Figure 6c depicts the trading rate of the MPOA with account mapping. When 60 vehicles are examined, the MPOA with iterations 20, 40, 60, 80, and 100 achieved 72%, 74%, 76%, 78%, and 80%. Only a few vehicles communicate with RSUs during certain periods to exchange data. The trading rate increases as the number of vehicles participating grows. When many vehicles share and trade data, the rate of D-trading may fluctuate due to data duplication. Increasing The number of vehicles leads to maximizing the rate of trading. Figure 6d depicts the performance analysis with account mapping regarding trading energy volume. When 20 represents vehicle numbers, the trading energy volume is 69 kW, 72 kW, 75 kW, 78 kW, and 81 kW for iterations of MPOA with 20, 40, 60, 80, and 100, respectively. The MPOA method is effective, as demonstrated by the results.
Figure 6.
Evaluation of the MPOA through account mapping (a) Memory usage (b) Transaction cost (c) Trading rate (d) Trading energy volume.
Performance Evaluation (in the absence of account mapping)
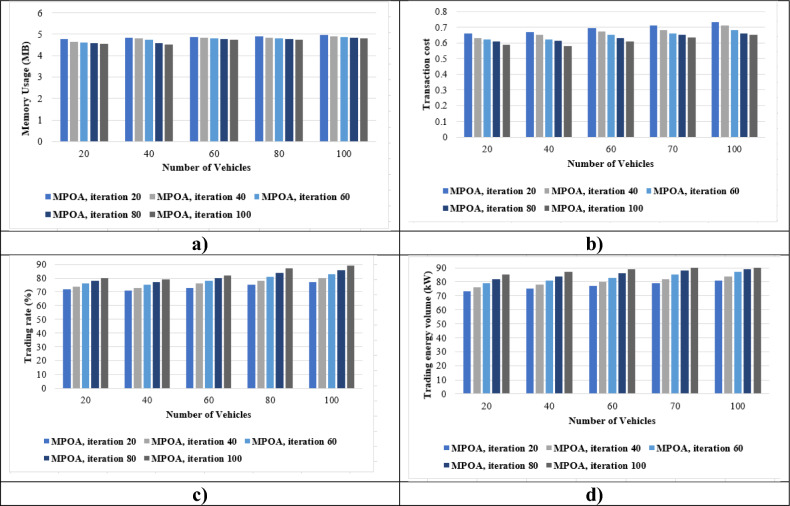
Figure 7 depicts the absence of account mapping, for the number of vehicles with energy volume, trade rate, memory use, and transaction cost. Figure 7a demonstrates alterations in memory consumption when compared to other methodologies. When there are 80 vehicles, the value of MPOA’s memory utilization is 4.881 MB for iteration 20, 4.841 MB for iteration 40, 4.796 MB for iteration 60, 4.771 MB for iteration 80, and 4.721 MB for iteration 100. Figure 7b illustrates the transaction cost without account mapping. When the vehicle number is 60, the transaction cost for MPOA is 0.693, 0.672, 0.654, 0.633, and 0.612 for each iteration. Figure 7c displays the MPOA’s trading rate without account mapping. When 60 vehicles were tested, the MPOA with iterations 20, 40, 60, 80, and 100 achieved 73%, 76%, 78%, 80%, and 82%. Figure 7d displays the performance analysis without account mapping in terms of trading energy volume. Increasing the energy trading volume balances rising household and commercial demand with energy generation. When vehicle numbers are represented by 20, the trade energy volume is 73 kW, 76 kW, 79 kW, 82 kW, and 85 kW for MPOA iterations with 20, 40, 60, 80, and 100. In addition to developing and upgrading the MPOA-based model, the model’s ability to trade energy is improved. Thus, the data transaction is secured with better energy trading system using BC-based MPOA.
Figure 7.
Performance evaluation without account mapping, (a) Memory usage, (b) Transaction cost, (c) Trading rate, (d) Trading energy volume.
Comparative methods
This section explains how the created MPOA compares to alternative methods, like Bayesian game-enabled two-way auction5, BC-based D-trading3, EV power trading6, and BC-based peer-to-peer energy trading14 in terms of the performance measures and number of vehicles. The comparison is performed in two scenarios: without and with account mapping.
Comparative assessment (in the absence of account mapping)
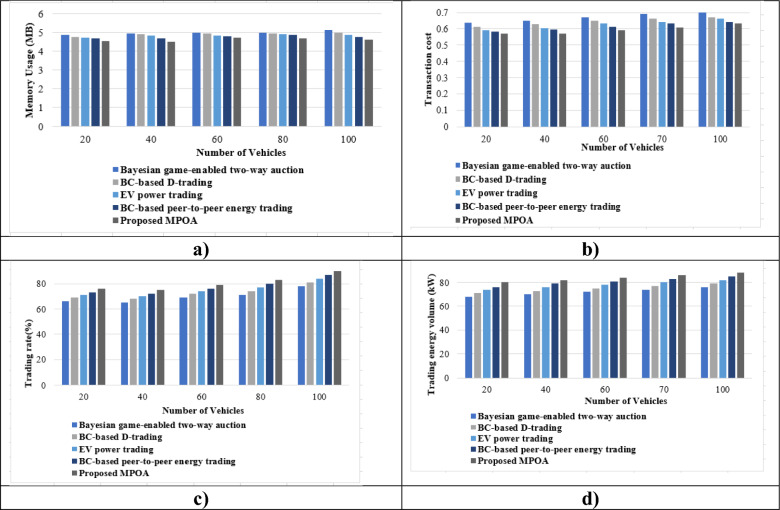
Comparative evaluation with mapping accounts based on the number of vehicles and different performance measures is shown in Fig. 8. Figure 8a depicts variations in memory consumption when compared to other approaches. When there are 80 vehicles, the memory use is 4.991 MB for the Bayesian game-enabled two-way auction, 4.951 MB for BC-based D-trading, 4.906 MB for the EV power trading, 4.881 MB for the BC-based peer-to-peer energy trading, and 4.701 MB for the MPOA. As the number of vehicles increases, the MPOA decreases; thus, the MPOA outperforms all existing methods, as demonstrated by the results. Figure 8b shows the transaction cost with account mapping, as compared to alternative methods. When there are 40 vehicles, the transaction cost for the MPOA is 0.570, but alternative techniques, such as the Bayesian game-enabled two-way auction, BC-based D-trading, EV power trading, and BC-based peer-to-peer energy trading, have transaction costs of 0.651, 0.631, 0.603, and 0.594, respectively. The transaction cost is a combination of deployment and function costs. The ‘Set reviews’ function incurs the highest execution and transaction costs due to the initialization of all resources, resulting in increased gas consumption. This effect speeds up data storage and reduces computational delays. Figure 8c depicts the trading rates of various approaches compared to the suggested model with account mapping. When the number of vehicles is 60, the Bayesian game-enabled two-way auction exhibits a trade rate of 69%, BC-based D-trading exhibits 72%, the EV power trading exhibits 74%, the BC-based peer-to-peer energy trading exhibits 76%, and the MPOA exhibits 79%. Figure 8d depicts trading energy volume with account mapping. When 20 is the number of vehicles, the trading energy volumes for all methods vary as follows: 68.042 kW for the Bayesian game-enabled two-way auction, 71.638 kW for BC-based D-trading, 74.414 kW for the EV power trading, 76.257 kW for the BC-based peer-to-peer energy trading, and 80.923 kW for the MPOA. Thus, the figure illustrates that the overall trading volume remains consistent when the number of EVs charged increases. When the quantity of EVs discharged is fixed, the overall energy supply remains constant. As the number of charging EVs grows, they can only provide a certain amount of energy. As a result, the overall trade volume can only match the total supply. Thus, MPOA is suitable for the real energy trading market.
Figure 8.
Evaluation of MPOA (a) Memory usage, (b) Transaction cost, (c) Trading rate, (d) Trading energy volume.
Comparative assessment (in the presence of account mapping)
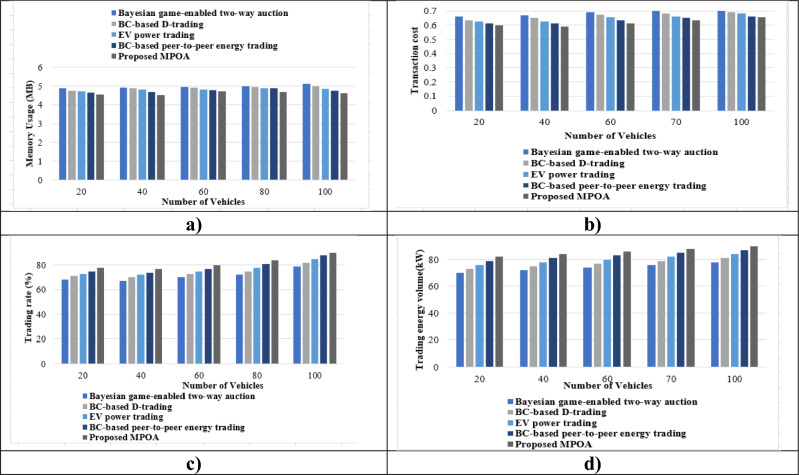
Comparative assessment is performed without considering mapping in terms of numerous metrics related to the number of vehicles and compared to other approaches is depicted in Fig. 9. Figure 9a shows memory utilization as compared to other approaches. When the number of vehicles equals 80, memory use is 4.981 MB for the Bayesian game-enabled two-way auction, 4.941 MB for BC-based D-trading, 4.896 MB for the EV power trading, 4.871 MB for the BC-based peer-to-peer energy trading, and 4.691 MB for the MPOA. While the memory usage of MPOA increases with the number of vehicles, performance is relatively stable. Figure 9b depicts the transaction cost without account mapping. When the number of vehicles is 40, the transaction cost for MPOA is 0.590, while other techniques yield values of 0.671, 0.651, 0.623, and 0.614 for the Bayesian game-enabled two-way auction, BC-based D-trading, EV power trading, and BC-based peer-to-peer energy trading, respectively. However, as the number of EVs increases, the benefits of MPOA become more significant. BC-based peer-to-peer energy trading and EV power trading could minimize the transaction cost. MPOA is useful for secure transactions with better energy trading, because it uses the coefficient of nuptial dance while integrating MA and POA. Figure 9c enumerates trading rate-based comparison with MPOA without account mapping. Here, when 60 = number of vehicles, then70% is trading rate for Bayesian game-enabled two-way auction, 73% for BC-based D-trading, 75% for EV power trading, 77% for BC-based peer-to-peer energy trading, and 80% for MPOA. Figure 9d depicts without account mapping in terms of trading energy volume. When 20 vehicle numbers are considered, the trading energy volumes for all methods are 70.033 kW for the Bayesian game-enabled two-way auction, 73.648 kW for BC-based D-trading, 76.424 kW for the EV power trading, 79.267 kW for the BC-based peer-to-peer energy trading, and 82.913 kW for the MPOA. Thus, the result clearly shows that MPOA in BC provides safe data storage, immutability, and transparency. The underlying work ensures secure and efficient coordination among EVs, charging stations, and aggregators. The suggested effort addresses communication concerns in VEN.
Figure 9.
Comparative evaluation of MPOA (a) Memory usage, (b) Transaction cost, (c) Trading rate, (d) Trading energy volume.
Comparative discussion
Table 4 compares of the MPOA assessment measures with and without account mapping. MPOA performed better in memory usage, transaction cost, trading rate, and trading energy volume in the presence of account mapping. The MPOA with account mapping has 4.605 MB memory usage, 0.654 transaction costs, a 91% trading rate, and 90 kW trading energy volume. Similarly, prior techniques, such as BC-based peer-to-peer energy trading, yielded memory usage values with account mapping are 5.123 MB, 4.981 MB, 4.851 MB, and 4.742 MB, transaction cost values of 0.734, 0.692, 0.681, and 0.662, trading rate values of 79%, 82%, 85%, and 88%, and trading energy volume values of 78 kW, 81 kW, 84 kW, and 87 kW. Furthermore, the transaction cost and trading energy volume for without account mapping are lower than with account mapping. The trading rate and trading energy volume are high with account mapping, owing to proper D-trading and E-trading operations. Finally, the transaction cost achieved in with account mapping is lower due to the MPOA. From the above discussion, it is clear that the presence of hybrid optimization utilized for account mapping yields better data transaction and energy trading. Moreover, RSUs validate data duplication during D-trading, that reduces storage and transaction costs. In addition, the usage of a hash list identifies duplicate trade data. The trading data is hashed and verified using a hash-list that prevents second-hand distribution. The MPOA with BC eliminates the need for a third-party transaction, compared to existing methods. Traditional trading schemes store transaction data in a central computer, making it opaque and vulnerable to forgery. The BC utilizes asymmetric cryptography, data signatures, and consensus processes to ensure transaction data is transparent, untampered, and traceable. Using MPOA, eliminates the need for mining and allows for faster transaction speeds.
Table 4.
Comparative discussion.
| Variations | Metrics | Bayesian game-enabled two-way auction | BC-based D-trading | EV power trading | BC-based peer-to-peer energy trading | MPOA |
|---|---|---|---|---|---|---|
| In the absence of account mapping | Memory usage (MB) | 5.133 | 4.991 | 4.861 | 4.752 | 4.601 |
| Transaction cost | 0.714 | 0.672 | 0.661 | 0.642 | 0.634 | |
| Trading rate (%) | 78 | 81 | 84 | 87 | 90 | |
| Trading energy volume (kW) | 76 | 79 | 82 | 85 | 88 | |
| In the presence of account mapping | Memory usage (MB) | 5.123 | 4.981 | 4.851 | 4.742 | 4.605 |
| Transaction cost | 0.734 | 0.692 | 0.681 | 0.662 | 0.654 | |
| Trading rate (%) | 79 | 82 | 85 | 88 | 91 | |
| Trading energy volume (kW) | 78 | 81 | 84 | 87 | 90 |
Significant values are in bold.
Comparison with current energy management schemes
In this section, the results of the presented framework were compared with existing current energy management schemes. The existing schemes include Blockchain with random forest classifier (BC-RF)27, Artificial Neural Network-enabled blockchain based electric vehicle integration system (ANN-BEVS)28, Deep Reinforcement Learning with Blockchain (DRL-BC)29, Multi-Objective Particle Swarm Optimization (MOPSO)30, and Directed Acyclic Graph-based V2G network (DV2G)31. The metrics used for comparative assessment include memory usage, trading rate, trading energy volume, and transaction cost. The performances of the existing approaches are obtained by implementing them on the same MATLAB platform by increasing the number of EVs.
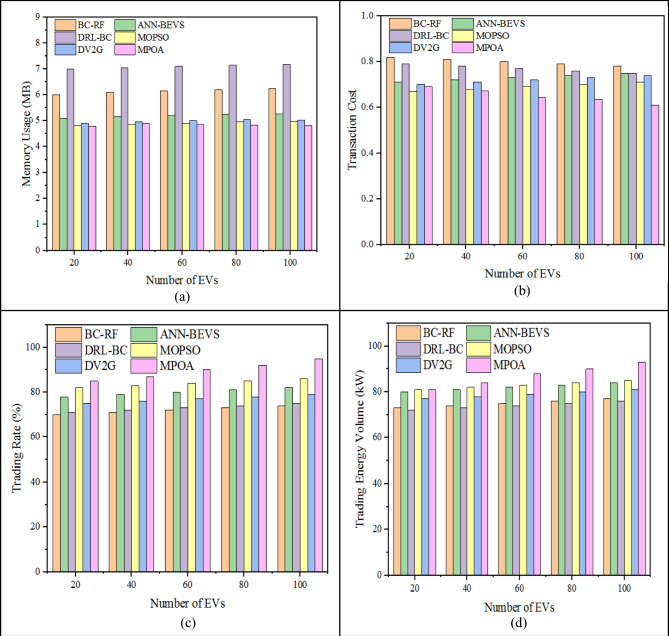
The memory usage metric measures the memory consumed by the model to store operation data in IoEV for trading data or energy. Figure 10a presents the comparison of memory usage. The existing energy management schemes including BC-RF, ANN-BEVS, DRL-BC, MOPSO, and DV2G achieved an average memory usage of 6.24 MB, 5.26 MB, 7.17 MB, 4.98 MB, and 5.02 MB, respectively, while the developed MPOA approach achieved an average memory usage of 4.601 MB. The reduction of memory usage demonstrates that the proposed method consumes less memory to store data during the trading process. Consequently, the transaction cost metric was validated with the existing approaches. The price of adding transactions on the blockchain is termed as transaction cost. The above-stated existing approaches and the developed algorithm obtained transaction cost of 0.84, 0.73, 0.81, 0.69, 0.72, and 0.634, respectively. The decrease of transaction cost in the proposed algorithm depicts that the price of adding transactions on the BC is low or minimal. Figure 10b presents the comparison of transaction cost of MPOA with the current models.
Figure 10.
Comparative assessment of MPOA with current models: (a) memory usage, (b) transaction cost, (c) trading rate, and (d) trading energy volume.
Similarly, the trading rate and trading energy volume are compared and validated across the existing models for increasing EVs. Figure 10c displays the comparison of the trading rate. Trading rate defines how fast the system trades energy. The currently available techniques such as BC-RF, ANN-BEVS, DRL-BC, MOPSO, DV2G and the developed MPOA obtained a trading rate of 72%, 80%, 73%, 84%, 77%, and 90%, respectively. The increased trading rate in the proposed strategy manifests its efficiency of fastly processing the transactions and trading energy or data. Finally, the trading energy volume defines the amount of electrical energy exchanged or transferred between EVs within the IoEV framework. Figure 10d displays the evaluation of trading energy volume and it is measured in kW. The above-defined existing techniques earned 75 kW, 82 kW, 74 kW, 83 kW, and 79 kW, respectively. The proposed strategy obtained a high trading energy volume of 88 kW, highlighting its effectiveness in sharing energy. Table 5 presents the comparison of performance with existing energy management schemes.
Table 5.
Comparison with current energy management schemes.
| Metrics | BC-RF | ANN-BEVS | DRL-BC | MOPSO | DV2G | Proposed MPOA |
|---|---|---|---|---|---|---|
| Memory usage (MB) | 6.24 | 5.26 | 7.17 | 4.98 | 5.02 | 4.601 |
| Transaction cost | 0.84 | 0.73 | 0.81 | 0.69 | 0.72 | 0.634 |
| Trading rate (%) | 72 | 80 | 73 | 84 | 77 | 90 |
| Trading energy volume (kW) | 75 | 82 | 74 | 83 | 79 | 88 |
Discussion
A novel approach was presented in this study to trade and share both energy and data within the IoEV environment based on blockchain. The proposed framework designs an innovative hybrid model named “MPOA”, by integrating the efficiency of two distinct meta-heuristic optimization algorithms such as MA and POA. The objective of this study is to enhance the security of transactions with reduced latency through optimal trading processes. The developed methodology integrates the blockchain technology, which offers transparency and immutability to the transaction records covering all energy transfer between the buyers and sellers. Further, the hybrid MPOA model is used for account mapping and decides whether the transaction needs to be added to the existing or new account of the EV seller. The presented framework was simulated in the MATLAB platform and the results are analyzed in two distinct cases: without account mapping and with account mapping. The results are examined using the metrics like transaction cost, trading rate, memory usage and trading energy volume. The experimental results demonstrated that the MPOA account mapping case offered better results, highlighting its effectiveness in optimizing the energy trading among EVs in the IoEV paradigm.
The results illustrated that the MPOA account mapping offered lower memory usage and transaction costs than without an account mapping case. Also, the proposed strategy offered higher trading rate, and trading energy volume than the without account mapping case. This illustrates the efficiency of the proposed MPOA in providing reliable data and energy sharing and trading across the EVs. Furthermore, the developed methodology almost provided consistent and stable performance across the increasing EVs, which highlights its scalability and sustainability in the real-world scenarios. In addition, a comprehensive comparative assessment was made with the existing strategies to validate the robustness of the proposed algorithm in energy management within the IoEV environment. The comparative analysis highlighted that the proposed MPOA approach obtained better results in terms of increased trading trade, high trading energy volume, lower memory usage and reduced transaction cost. These performances manifest the proposed MPOA highly efficient than the currently available energy management techniques in optimizing the energy trading among EVs.
Thus, the integration of MPOA with the blockchain offers a reliable and promising solution for secure data and energy trading in the IoEV environment. Since the MPOA combines the faster convergence and exploration and exploitation features of MA and POA, it reduces the scalability challenge inherent within the BC technology. Also, MPOA offers better adaptability, which enables the system to adapt to the changing factors like energy demands, energy availability, etc., in the IoEV. These increased scalability and adaptability makes the proposed framework highly reliable for real-world scenarios. Despite its advantages like increased scalability, less transaction cost, improved trading rate, and minimal memory usage, the developed methodology faces certain challenges in real-world scenarios. Although the model offered less memory usage than others, it demands a robust Information Technology (IT) infrastructure for the successful implementation of the integrated approach. Also, it demands high-performance processors, large storage modules, and fast network connectivity, which makes the system resource intensive. Secondly, the initial cost of implementing the MPOA with the blockchain is high and it requires long-term maintenance for proper functioning. Thirdly, the proposed framework is tested only under increasing EVs, but to demonstrate the scalability of the model in the real-world, it must be tested under different scenarios like increasing transaction volume, high energy demands, etc. Although the usage of blockchain technology offers security in the system, it faces issues in key management; thereby, limiting its performance in real-world scenarios.
Conclusion
BC technology has made it easier to trade EVs. This research investigates a safe authentication protocol for an energy trading model-based BC in the IoEV. This authentication method involves five entities: the RSU, vehicle, BC, IPFS, and TA. Here, the TA maintains the IoEV network and prevents the addition of rogue vehicles to ensure its strength and security. Moreover, EVs can either sell or buy energy depending on their needs. On Board Units (OBU’s) connectivity and computing capabilities allow vehicles to connect with RSUs for D-trading and E-trading. In addition, RSUs serve as both data and energy brokers, processing D-trading and E-trading requests. RSUs use the consortium BC to share a single digital ledger. BC enhances security by ensuring immutability, tamper-proof records, and transparency in commerce. It allows concurrent access to uploaded files without any delays. IPFS offers persistent data storage, making it a suitable platform for data exchange. The proposed model includes several phases, including initialization, registration, D-trading request, RSU response and data duplication validation, key generation, data protection, transaction verification and consensus, data uploading to IPFS, E-trading request, request matching and token assignment, and account mapping. Here, the account mapping is done by MPOA, which is a combination of MA and POA. Furthermore, the metrics, like memory consumption gained is 4.605 MB, trading rate shows a value of 91%, transaction cost achieved is 0.654, and trading energy volume gained is 90 kW.
Although the proposed methodology offered improved outcomes, it faces certain limitations such as huge hardware requirements, high implementation cost, and limited scalability. To address these issues, the future study should focus on developing a light-weight multi-objective approach for scalable and effective data and energy trading within IoEV.
Acknowledgements
This research was supported by the Researchers Supporting Project number (RSP2024R244), King Saud University, Riyadh, Saudi Arabia.
Author contributions
All the authors have contributed equally to this article.
Funding
No funding was supported for this research work.
Data availability
The data used to support the findings of this study are included in the article.
Competing interests
The authors declare no competing interests.
Footnotes
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
C. Dhanamjayulu, Email: dhanamjayulu29@gmail.com
Baseem Khan, Email: baseemkh@hu.edu.et.
References
- 1.Heidari, A., Navimipour, N. J., Dag, H., Talebi, S. & Unal, M. A novel blockchain-based deepfake detection method using federated and deep learning models. Cognit. Comput.16, 1073–1091 (2024). 10.1007/s12559-024-10255-7 [DOI] [Google Scholar]
- 2.Yahaya AS, Javaid N, Khalid R, Imran M, Naseer N., “A blockchain based privacy-preserving system for electric vehicles through local communication”, In Proceedings of ICC 2020–2020 IEEE International Conference on Communications (ICC), IEEE, pp 1–6, June 2020.
- 3.Sadiq, A. et al. Blockchain based data and energy trading in internet of electric vehicles. IEEE Access9, 7000–7020 (2020). 10.1109/ACCESS.2020.3048169 [DOI] [Google Scholar]
- 4.Heidari, A., Navimipour, N. J. & Unal, M. A secure intrusion detection platform using blockchain and radial basis function neural networks for internet of drones. IEEE Internet Things J.10(10), 8445–8454 (2023). 10.1109/JIOT.2023.3237661 [DOI] [Google Scholar]
- 5.Luo, L., Feng, J., Hongfang, Y. & Sun, G. Blockchain-enabled two-way auction mechanism for electricity trading in internet of electric vehicles. IEEE Internet Things J.9(11), 8105–8118 (2021). 10.1109/JIOT.2021.3082769 [DOI] [Google Scholar]
- 6.Liu, H., Zhang, Y., Zheng, S. & Li, Y. Electric vehicle power trading mechanism based on blockchain and smart contract in V2G network. IEEE Access7, 160546–160558 (2019). 10.1109/ACCESS.2019.2951057 [DOI] [Google Scholar]
- 7.Yahaya, A. S. et al. A secure and efficient energy trading model using blockchain for a 5g-deployed smart community. Wirel. Commun. Mobile Comput.2022, 6953125 (2022). 10.1155/2022/6953125 [DOI] [Google Scholar]
- 8.Zhang, J. & Meng, W. Blockchain-based authentication with optional privacy preservation for internet of vehicles. Math. Probl. Eng.1, 9954599 (2021). [Google Scholar]
- 9.Xue, F. et al. Blockchain smart contract-enabled secure energy trading for electric vehicles. Energies15(18), 6733 (2022). 10.3390/en15186733 [DOI] [Google Scholar]
- 10.Zhao, P., Zhang, G., Wan, S., Liu, G. & Umer, T. A survey of local differential privacy for securing internet of vehicles. J. Supercomput.76(11), 8391–8412 (2020). 10.1007/s11227-019-03104-0 [DOI] [Google Scholar]
- 11.Vakili, A. et al. A new service composition method in the cloud-based Internet of things environment using a grey wolf optimization algorithm and MapReduce framework. Concurr. Comput.: Pract. Exp.36(16), e8091 (2024). 10.1002/cpe.8091 [DOI] [Google Scholar]
- 12.Heidari, A., JafariNavimipour, N., Dag, H. & Unal, M. Deepfake detection using deep learning methods: A systematic and comprehensive review. Wiley Interdiscip. Rev.: Data Min. Knowl. Discov.14(2), e1520 (2024). [Google Scholar]
- 13.Jamal, A., Gurmani, M.U., Awan, S., Sajid, M.B.E., Amjad, S. & Javaid, N,Blockchain enabled secure and efficient reputation management for vehicular energy network,in complex, intelligent and software intensive systems: Proceedings of the 15th International Conference on Complex, Intelligent and Software Intensive Systems (CISIS-2021), Springer International Publishing, pp 406–416, 2021.
- 14.Khan, P. W. & Byun, Y. C. Blockchain-based peer-to-peer energy trading and charging payment system for electric vehicles. Sustainability13(14), 7962 (2021). 10.3390/su13147962 [DOI] [Google Scholar]
- 15.Amiri, Z., Heidari, A., Navimipour, N. J., Esmaeilpour, M. & Yazdani, Y. The deep learning applications in IoT-based bio-and medical informatics: A systematic literature review. Neural Comput. Appl.36(11), 5757–5797 (2024). 10.1007/s00521-023-09366-3 [DOI] [Google Scholar]
- 16.Amiri, Z., Heidari, A., Zavvar, M., Navimipour, N. J. & Esmaeilpour, M. The applications of nature-inspired algorithms in Internet of Things-based healthcare service: A systematic literature review. Trans. Emerg. Telecommun. Technol.35(6), e4969 (2024). 10.1002/ett.4969 [DOI] [Google Scholar]
- 17.Heidari, A., JafariNavimipour, N., Unal, M. & Zhang, G. Machine learning applications in internet-of-drones: Systematic review, recent deployments, and open issues. ACM Comput Surv55(12), 1–45 (2023). 10.1145/3571728 [DOI] [Google Scholar]
- 18.Xu, S., Chen, X. & He, Y. EVchain: An anonymous blockchain-based system for charging-connected electric vehicles. Tsinghua Sci. Technol.26(6), 845–856 (2021). 10.26599/TST.2020.9010043 [DOI] [Google Scholar]
- 19.Li, Y. & Baiji, Hu. An iterative two-layer optimization charging and discharging trading scheme for electric vehicle using consortium blockchain. IEEE Trans. Smart Grid11(3), 2627–2637 (2019). 10.1109/TSG.2019.2958971 [DOI] [Google Scholar]
- 20.Yi, H. et al. Energy trading IoT system based on blockchain. Swarm Evol. Comput.64, 100891 (2021). 10.1016/j.swevo.2021.100891 [DOI] [Google Scholar]
- 21.Javed MU, Javaid N, Malik MW, Akbar M, Samuel O, Yahaya AS, Othman JB, Blockchain based secure, efficient and coordinated energy trading and data sharing between electric vehicles, Cluster Comput., pp1–29, 2022.
- 22.Heidari, Arash, Nima Jafari Navimipour, and Akira Otsuki. Cloud-based non-destructive characterization. Non-destructive material characterization methods (2024): 727–765.
- 23.Ashfaq, T. et al. An efficient and secure energy trading approach with machine learning technique and consortium blockchain. Sensors22(19), 7263 (2022). 10.3390/s22197263 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 24.Heidari, A., Shishehlou, H., Darbandi, M., Navimipour, N. J. & Yalcin, S. A reliable method for data aggregation on the industrial internet of things using a hybrid optimization algorithm and density correlation degree. Cluster Comput.10.1007/s10586-024-04351-4 (2024). 10.1007/s10586-024-04351-4 [DOI] [Google Scholar]
- 25.Trojovský, P. & Dehghani, M. Pelican optimization algorithm: A novel nature-inspired algorithm for engineering applications. Sensors22(3), 855 (2022). 10.3390/s22030855 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 26.Zervoudakis, K. & Tsafarakis, S. A mayfly optimization algorithm. Comput. Ind. Eng.145, 106559 (2020). 10.1016/j.cie.2020.106559 [DOI] [Google Scholar]
- 27.Bhaskar, K. B. R., Prasanth, A. & Saranya, P. An energy-efficient blockchain approach for secure communication in IoT-enabled electric vehicles. Int. J. of Commun. Syst.35(11), e5189 (2022). 10.1002/dac.5189 [DOI] [Google Scholar]
- 28.Wang, Z. et al. AEBIS: AI-enabled blockchain-based electric vehicle integration system for power management in smart grid platform. IEEE Access8, 226409–226421 (2020). 10.1109/ACCESS.2020.3044612 [DOI] [Google Scholar]
- 29.Moniruzzaman, Md., Yassine, A. & Benlamri, R. Blockchain and federated reinforcement learning for vehicle-to-everything energy trading in smart grids. IEEE Trans. Artif. Intell.5(2), 839–853 (2023). 10.1109/TAI.2023.3262597 [DOI] [Google Scholar]
- 30.Liu, Z., Xu, Y., Zhang, C., Elahi, H. & Zhou, X. A blockchain-based trustworthy collaborative power trading scheme for 5G-enabled social internet of vehicles. Digit. Commun. Netw.8(6), 976–983 (2022). 10.1016/j.dcan.2022.10.014 [DOI] [Google Scholar]
- 31.Hassija, V. et al. A blockchain-based framework for lightweight data sharing and energy trading in V2G network. IEEE Trans. Veh. Technol.69(6), 5799–5812 (2020). 10.1109/TVT.2020.2967052 [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
The data used to support the findings of this study are included in the article.