Abstract
Recent progress studies in light of wireless communication systems mainly centred around two focuses: zero-energy consumption and ultra-reliable and low-latency communication (URLLC). Among various cutting-edge areas, exploiting ambient backscatter communication (Backcom) has recently been devised as one of the foremost solutions for achieving zero energy consumption through the viability of ambient radio frequency. Meanwhile, using short-packet communication (SPC) is the cheapest way to reach the goal of URLLCs. Upon these benefits, we investigate the feasibility of Backcom and SPC for symbiotic wireless sensor networks by analyzing the system performance. Specifically, we provide a highly approximated mathematical framework for evaluating the block-error rate (BLER) performance, followed by some useful asymptotic results. These results provide insights into the level of diversity and coding gain, as well as how packet design impacts BLER performance. Numerical results confirm the efficacy of the developed framework and the correctness of key insights gleaned from the asymptotic analyses.
1 Introduction
With the widespread adoption of the Internet-of-Things (IoT), next-generation wireless networks are seeing an influx of emerging IoT applications and services [1]. These applications and services are not limited to interactions between a specific system, such as wireless sensor networks (WSNs), cellular networks, or vehicle networks, but also extend to new categories such as telemetry, healthcare, smart grids, digital twins, and the metaverse [2]. In which, artificially intelligent technology plays a core role in controlling, collaborating and coordinating network components [3]. Along with the benefits brought by IoT context, it also renders several challenges to the development of physical wireless systems [4]. For instance, how to accommodate the increasing demand for connected devices when the current spectrum is full, prolong the activities of IoT devices with limited power resources, and provide ultra-reliable and low-latency wireless communication (URLLC).
Amidst the shortage of available radio frequencies, several efficient strategies have been proposed to tackle this challenge. The first aim is to line on full-duplex communication to increase spectrum efficiency [5] but requires refined successive interference cancellation (SIC) approaches to move residual interference it produces [6, 7]. Another strategy is to take advantage of multiple access technologies, such as non-orthogonal multiple access [8] and rate-splitting multiple access [9], which enable multiple users to communicate simultaneously using the same time and frequency resource block. However, exploiting such multiple access is tedious because it is only suitable for a single network. As a result, recent progress on multiple access typically combines it with two potential types of cognitive radio (CR) paradigms [10, 11], overlay and underlay. While underlay allows the secondary network to coexist with the primary network subject to power-tolerant constraints, overlay networks operate under free interference [12]. However, with the disadvantage characteristics by themselves, the realization of CR solutions also becomes controvertible [13, 14].
In the wake of energy constraints, energy harvesting (EH) solutions have emerged as an alternative that allows IoT devices to charge their batteries without human intervention [15]. Compared to charging energy from surrounding natural sources such as wind or sun, radio-frequency (RF) EH is voted as the most cost-effective solution, with two representations of wireless-power transfer communication network and simultaneously wireless information power transfer [16]. According to many reports in the literature [17–22], the nature of active communication enabled by RF signals consumes relatively high power, and this might not be favourable to large-scale IoT deployments in the long term. Thus, it raises the question of finding new alternatives with sustainable RF-EH capabilities and low power consumption.
Driven by the two necessities above, symbiotic communication, a new paradigm shift for passive IoT, has recently emerged as the ultimate solution to tackle the issues of spectrum scarcity and low-power consumption [23]. Symbiotic paradigm is a revolutionary concept that expertly blends the strengths of two existing paradigms [24], ambient backscatter communication (Backcom) and CR. In this paradigm, the backscatter device passively modifies the received signal from the primary transmitter with its information before sending it back to the secondary receiver [25], effectively changing its load impedance instead of using dedicated RF components. This allows Backcom to act similarly to CR paradigms while consuming zero energy. This functionality helps a symbiotic paradigm to achieve properties of mutualism, commensalism or parasitism [26]. Due to this prominent feature, the research on Backcom with symbiotic mediums has recently attracted significant momentum from both industrial and academia. For example, a full-duplex Backcom solution was proposed to symbiotic radio (SR) system [27]. In [28], three practical cooperative transmission schemes was proposed for symbiotic radio systems. The work in [29] provided a thorough and authoritative review of the systematic view for SR, along with critical discussions to enhance the backscattering link, achieve highly reliable communications, and effectively utilize reconfigurable intelligent surfaces. In [30], a novel beamforming design was proposed to multiple-input-multiple-output SR backscatter system. Meanwhile, the work in [31] studied SR communication system in the presence of multiuser multi- backscatter-device. In [32], two SR schemes were designed for a pair of backscatter devices, is that, opportunistic commensal and opportunistic parasitic. In [33], a symbiotic localization and Backcom architecture was developed for IoT localize target objects to achieve two mutual benefits: sensing and communication stage. In [34], an investigation of Backcom was put forward in symbiotic cell-free massive multiple-input multiple-output systems. Meanwhile, an innovative solutions for enhancing the security of low-power IoT devices using ambient backscatter communication was introduced in [35], with a strong focus on the balance between energy efficiency and security. In a very recent time, the work in [36] presented advances in enhancing the robustness of wireless communication systems against jamming attacks by designing a novel beamforming technique that utilizes the concept of symbiotic radio to effectively use the null space of interference, thereby enhancing safeguarding data transmission significantly.
On the other hand, to deal with stringent URLLC conditions, where transmission latency is expected to be less than 1 ms while reliability is from 99.9% to 99.9999%, recent efforts propose to rethink the design of packet size [37]. Specifically, reducing packet size to improve the physical layer transmission latency; however, this action results in a higher error rate transmission. In this case, there is no way to use a finite blocklength message coding scheme to boost reliable communication. Based on Polyanskiy’s novel infinite block length theory, published in 2010 [38], the research on short-packet communication (SPC) has recently emerged as a vital solution and is receiving considerable interest from research communities [39–42]. In that, block-error rate (BLER) is devised to be the key metric instead of using outage probability or ergodic Shannon capacity for the performance evaluation.
Towards a green IoT network for the future, the interplay between symbiotic Backcom and SPC becomes the pivotal direction. In the past, several works investigated the benefits brought by SPC with conventional Backcom systems (backscatter devices are deployed for enhancing communication coverage only), such as resource allocation [43], energy efficiency [44], and error performance for finite backscatter channels [45]. However, to the best of authors’ knowledge, the research on symbiotic Backcom systems with SPC remains unexplored in the literature. Therefore, this inspires us to investigate the feasibility of SPC in symbiotic Backcom systems. In particular, the main focus of this work is on the performance of symbiotic Backcom-empowered WSNs with SPC, where the secondary backscatter transmitter is parasitic from the primary network. Overall, the main contribution of this article can be outlined as follows:
Towards future green URLLC use cases, this article studies the performance of symbiotic backscatter-empowered WSNs, where a passive backscatter device with energy constraints in the secondary networks exploits ambient RF signals generated by the primary transmitter for the primary receiver as a green power source to be able to communicate with the secondary IoT receiver. To reject interference impacted by a primary transmitter’s RF signals, SIC enables the IoT receiver to decode its signal from a passive backscatter device.
- Aiming at characterizing the performance of the considered networks, we provide an efficiently approximated mathematical framework for the BLER performance evaluation without any simulations or empirical, where we first endeavour to seek a way to derive closed-form solutions for the signal-to-noise ratio (SNR) distributions received by the primary and secondary receivers, while putting all the remaining energies to the work of finding out the BLER approximation. Not only these, but we also provide some insightful asymptotic analyses, which allow us effortlessly to answer these critical questions:
- How much diversity and coding gains does the considered system achieve when compared to a system using uncoded transmission?
- How do the packet designs affect the BLER performance?
To validate our developed mathematical framework, we provide some extensive numerical results based on Monte-Carlo simulations method. It is interesting to show that this framework accurately predicts the actual result with very minor errors, even with a series of approximation approaches used. Besides, it also confirms the performance trend findings of the reflection coefficient designed at the backscatter device, the packet construction involving packet length and number of information bits, as well as the transmit power of the primary transmitter. Furthermore, we through numerical results have that when boosting the reflection coefficient exceeds 2.5 (unit), the BLER performance of the secondary IoT receiver converges to saturation.
The remainder of this article is covered as follows. Section 2 describes the system model, followed by the average BLER analysis in Section 3. Next, Section 5 provides some numerical results before concluding the article in Section 5.
2 System model
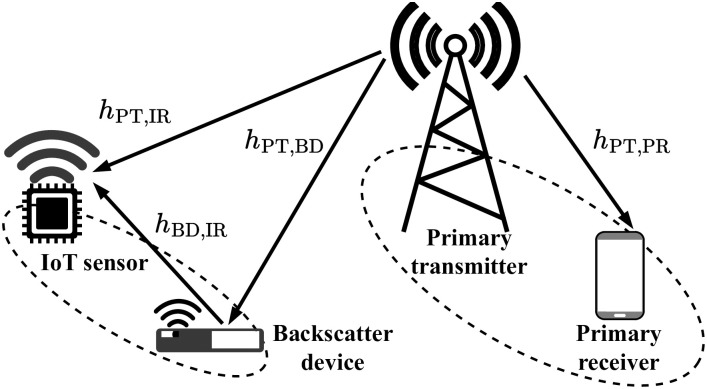
Let us consider a symbiotic backscatter communication system as shown in Fig 1, where the cellular network, called the primary network, coexists with an IoT sensor network, called the secondary network. In this setup, a backscatter device (named by BD) exploits the available RF signal when carrying a symbol x(t) sent from the primary transmitter (denoted by PT) to the primary receiver (called PR) to convey its symbol information c(t) to the secondary IoT sensor receiver (i.e., IR), with t being the time t. In which, the packet information sent by BD has data amount NIR bits with packet length LIR (or the equivalent terminologies: channel use or blocklength), while that of PT includes data amount NPR bits with packet length LPR. Due to the presence of the multiplicative fading phenomenon and long-distance communication, no interference occurs from BD to the signal of PR [27, 29, 33]. Meanwhile, there always exists interference from PT to IR, which therefore requires the adoption of SIC approach at IR to subtract x from the received signal before detecting c(t). In this investigation, all wireless channels are assumed to follow quasi-static Rayleigh block fadings, which means that channels vary very small or even with static. Thus, it is reasonable to consider the availability of global channel state information at the terminals via statistical channel measurement methods [39–42, 45].
Fig 1. Illustration of the considered system.
For the sake of analysis, we denote by hPT,PR, hPT,BD, hPT,IR, and hBD,IR the channels of links PT → PR, PT → BD, PT → IR, and BD → IR, respectively. Under Rayleigh fading assumptions, channel gains |h|2, h ∈ {hPT,PR, hPT,BD, hPT,IR, hBD,IR} will obey exponential distributions with the parameter λ ∈ {λPT,PR, λPT,BD, λPT,IR, λBD,IR}, and the respective probability density function (PDF) and the cumulative distribution function (CDF) are given by [46]
| (1) |
Under the path-loss measurement, we can model λ as λ = dβ [47], with d ∈ {dPT,PR, dPT,BD, dPT,IR, dBD,IR} is the physical distance of links h and β ∈ [2, 6] is the path-loss exponent.
Considering a block duration T > 0, the signal received at PR when sending x from PT with the transmit power PPT over channel hPT,PR at the time t ∈ T can be written as
| (2) |
where nPR is the additive White Gaussian noise (AWGN) with zero-mean and variance N0 and E{|x(t)|2} = 1, with E{⋅} being the expectation operator. On the foundation of (2), the signal-to-noise (SNR) ratio to decode x(t) can be written as
| (3) |
During the duration T, the communication between BD and IR goes through two stages. In particular, BD firstly collects the power signal from PT based on energy harvesting technology. Then, BD modulates its received signal power with c(t) and then backscatters it back to IR. As a result, the signal received at IR at the time t can be expressed as
| (4) |
where α ∈ (0, 1) is a reflection coefficient used to normalize c(t), τ is the processing delay at BD, and nIR is the AWGN with zero-mean and variance N0. In order to reduce the impact of interference, SIC is considered at IR with the decoding order x(t) → c(t). Thus, the corresponding signal-to-interference-plus-noise ratio (SINR) of decoding x(t) and SNR of decoding c(t) at IR can be written as
| (5) |
| (6) |
From the formula above, the signal at IR is said to be successfully decoded when x(t) and c(t) are perfectly decoded. Thus, the end-to-end SNR and SINR at IR can be claimed by
| (7) |
3 Average BLER analysis
When a packet having blocklength L is sent from the transmitter node to the receiver node with the SNR γ and error probability ϵ, Polyanskiy’s novel infinite block length theory said that the maximal channel coding ratio can be approximated as [38]
| (8) |
where C(x) = log2(1 + x) is the Shannon capacity, V(x) = (log2(e))2[1 − 1/(1 + x)2] is the channel dispersion, and Q−1(x) is the inverse of the Gaussian Q-function, i.e., .
Provided that a packet has NRx bits and packet length LRx, with Rx ∈ {PR, IR} and invoking the relation in (8), the average BLER at Rx can be written as [39–42]
| (9) |
with rRx = NRx/LRx. Unfortunately, the complex nature of the Q-function makes the mathematical analysis quite challenging. To end this, making use of the normal approximation method in [11] shows that can be linearly approximated by Ξ(rRx, LRx, γRx), i.e.,
| (10) |
where , , υRx = κRx − 1/(2ζRx), and ϑRx = κRx + 1/(2ζRx).
Pulling (9) and (10) together and applying the integral-by-parts method, the average BLER at Rx can be rearranged as
| (11) |
It is intuitively observed from (11) that finding the average BLER goes through two steps: 1) finding out the CDF of γRx and 2) deriving the average BLER based on the relation in (11). Consequently, we should recognize that most technical challenges come from finding the CDF characteristic, solving the integral of the average BLER or even both of them.
3.1 Average BLER analysis of Primary Receiver (PR)
3.1.1 Statistical analysis of SNR distribution
Based on the developed formula in (11), we in this subsection will focus on deriving the CDF of γPR, denoted by FγPR(x). Specifically, revising the SNR built-in (3), we can mathematically derive a closed-form solution for FγPR(x) as follows:
| (12) |
3.1.2 Average BLER analysis
Having obtained the CDF of γPR in hand, we are next so excited to derive the average BLER of PR by making use of the relation in (11).
Theorem 1. A closed-form solution for the average BLER of the primary receiver is formulated as
| (13) |
Proof. By injecting the developed CDF in (12) into the expression in (11), we can establish the following average BLER formulation
| (14) |
Applying the fact that ϑPR − υPR = 1/ζPR and for (14), we can obtain the final solution in (13). The proof is completed.
Having achieved Theorem 1, we are interested in concluding that the average BLER of PR can be characterized by a unique function involving all elementary functions. Thus, it is feasible to use common integrated software packages (i.e., Matlab, Maple, or Mathematica) to dissect the average BLER performance by this function without any simulation or actual testing. Yet, it would be extremely meaningful to explore or answer the questions of whether is there any simpler way to characterize the average BLER performance limits at a high SNR regime and how much performance gain the system can be achieved compared to an uncoded transmission.
To answer these questions, let us turn to evaluate the asymptotic BLER. To begin with, let us revisit the CDF of γPR in (12). By using the fact that 1 − exp(−x) ≃ x as x goes to 0, we can simplify the expression in (12) as
| (15) |
Combining this approximation with the formulation in (11), the asymptotic BLER can be computed as
| (16) |
Herein, the last step is obtained based on a basic equality that x2 − y2 = (x + y)(x − y). Accordingly, we have that . Recall that υRx = κRx − 1/(2ζRx) and ϑRx = κRx + 1/(2ζRx), with and , as provided in Eq (10). On that basis, we can obtain and ϑPR − υPR = 1/ζPR. Pulling all together yields . By comparing this result with step (*) in Eq (16), we can readily obtain the desired result.
From the formulation in (16), it is wonderful to show that the BLER performance of PR is dominated by three factors: the average SNR Ψ, the fading parameter λPR, and the coding ration rPR. For the characteristic of Ψ, it is found that the BLER performance is proportional to Ψ, which concludes the diversity gain of 1 and the respective coding gain is . For the characteristic of λPR, we notice that when the distance parameter dPT,PR increases, or PR moves far from the PT in other words, the ABLER increases, which completely accords the fact that the larger the communication coverage, the lower the performance quality. For the characteristic of rPR = NPR/LPR, we can readily observe from the definition that rPR is an increasing function of NPR but a decreasing function of LPR. This means that increasing the data amount makes the transmission more error. In contrast, increasing the block-length decreases the error data transmission, which then significantly enhances a reliable communication system.
3.2 Average BLER analysis of IoT sensor receiver
3.2.1 Statistical analysis of SNR distribution
Likewise, evaluating the average BLER at IR also requires the CDF of γIR, denoted by . Invoking the SNR built-in (7) and denoting by , we can express using the complementary probability property as follows:
| (17) |
where the last step is achieved based on the relation . Observing the above integral shows that to achieve the solution, the foremost important task is now to derive the joint PDF of |hPT,BD|2 and |hBD,IR|2. To proceed, let us consider the following derivation
| (18) |
where the joint CDF of Y can be obtained as [18]
| (19) |
with λPT→IR ≜ λPT,BDλBD,IR and being the first order modified Bessel function of the second kind.
Next, plugging (19) into (18) combined with the relation [48], we have that
| (20) |
Having developed the PDF of Y in hand, we can rewrite the CDF of γIR by injecting (20) into (17), which yields
| (21) |
where is the unit step function with
| (22) |
To get the final solution for (21), we conjure the three following transformations into the Meijer-G function as [49]
| (23) |
| (24) |
Applying the transformation into (21), we obtain
| (25) |
where the last step can be attained based on two identities [50, eq 2.3] and [51, eq. 1.7.1] and is the bi-variate Fox-H function.
3.2.2 Average BLER analysis
Having obtained the CDF of γIR in hand, we are next so excited to derive the average BLER of IR by making use of the relation in (11).
Theorem 2. A closed-form solution for the average BLER of the IoT sensor receiver can be formulated as
| (26) |
where K represents the complexity-accuracy trade-off parameter while ψl = cos(π(2k − 1)/[2K]).
Proof. By injecting the developed CDF in (25) into the expression in (11), we can establish the average BLER formulation as
| (27) |
However, due to the intractability of the H-fox function, we tackle the integral in (27) by applying the Gaussian-Chebyshev quadrature method.
Having achieved Theorem 2, we are interested in concluding that a unique function of all system parameters can characterize the average BLER of IR analytically. Nevertheless, the involvement of the H-fox form in in (25) makes the analysis quite complex; thus, it raises the question of figuring out a simpler BLER formulation. In response to this question, we make use of the equivalent infinitesimal 1/x ≃ 0 as x → ∞ to simplify the CDF of γIR in (21) as
| (28) |
where the last step is derived using the Meijer-G function transformations in (23) and (24) before applying the standard form in [48, eqs. (7.811.1) and (9.31.2)]. It is clear that the result in (28) has a simpler format compared to that of (25). However, the complex nature of the Meijer-G function still limits deriving the average BLER. To end this, we rely on the first-order Riemann integral approximation [11, Eq. (15)], which leads to
| (29) |
From the above formulation, it is interesting to show that the BLER performance exponentially decreases with the Ψ. Especially, when we let 1/Ψ = 0, an interesting result can be deduced from (29) that the average BLER will converge to a saturation, which is determined by
| (30) |
With this formulation, it is interesting to show that increasing NIR scales down the Meijer-G function, which is equivalent to increasing the BLER. In contrast, increasing LIR scales up the Meijer-G function, which then decreases the BLER.
4 Numerical results and discussions
This section provides some illustrative numerical results using Monte-Carlo simulations to validate our developed mathematical framework, where the number of used channel realization samples is 105. Without loss of generality, we consider the specific parameters for Rayleigh channels as follows: λPT,PR = 2, λPT,BD = 4, λPT,IR = 3, and λBD,IR = 5 (channel modeling has been early described at Eq 1). Unless otherwise specified, the key simulation parameters related to packet designs and transmit SNR are set as follows: α = 0.5, LRX = 256 c.u, NPR = 300 bits, NIR = 80 bits, and Ψ = 25 dB.
Fig 2 shows the average BLER versus α. We look at the case where PT sends 300 bits of data to PR, while BD produces 80 bits of data for command control sync. It is observed that the error performance of PR remains constant with respect to α since its receiving signal does not gain any backscattering signal from BD. Meanwhile, IR’s error performance tends to reduce with a small value of α and then become saturated. This is because on the one hand, scaling up α improves the received SNR signal to decode c(t) in (6) but decreases the received SINR signal to decode x(t) in (5) on the other hand. Recall that the SIC procedure dominates the decoding process at IR. Taking these together therefore explains why increasing α does not yield any error performance improvement.
Fig 2. Impact of α on BLER.
Fig 3 explores the impact of block-length LRX on the average BLER. From the figure, we can see that while the error performance of PR reduces considerably with an increase in LRX, that of IR decreases relatively low. The reasons are interpreted as follows: 1) for PR, the received SNR given in (3) does not suffer from any SIC, which gives PR a chance to decode x(t) without interference. Thus, it is safe to conclude that the more block-length (channel use) of the information transmission, the higher the reliability of the communication channel. Recall that, such phenomenon completely accords the analysis for the developed expression in (16). 2) for IR, its decoding process takes place in two phases of decoding x(t) and c(t), respectively. Thus, this process will increase an expected error during decoding c(t), making the error performance of IR to be reduced slowly. Recall that such a phenomenon can be directly explained from (29), where increasing LPR reduces the exponential component but scales up the Meijer-G component accordingly.
Fig 3. Impact of LRX on BLER.
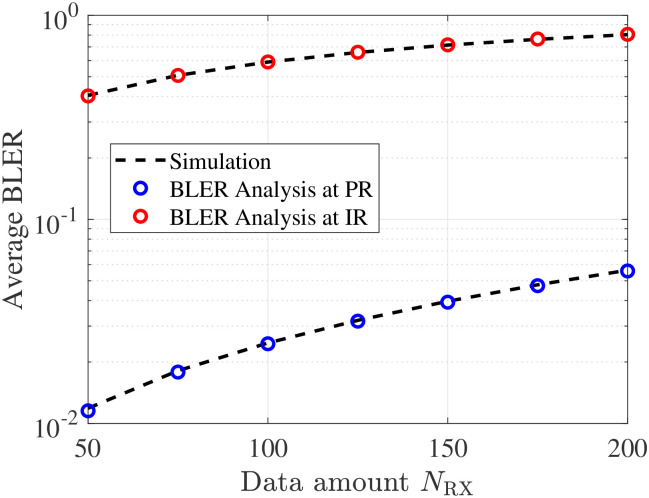
Fig 4 showcases the average BLER against data amount sent by PT and BD. As observed, conveying more data over a fixed channel use to the receiving node causes more errors during communication, thereby leading to an increase in the BLER trend. These trends are perfectly matched with our analyses for the expression in (16) and (29). In this case, a more channel should be allocated to boost reliable communication. Yet, this assignment might not be beneficial to the systems as it is equivalent to an increase in the transmission latency. Therefore, it is necessary to consider balancing such configuration for each application critically.
Fig 4. Impact of NRX on BLER, with LRX = 100 c.u.
Fig 5 depicts the impact of Ψ on the average BLER. Overall, we can find that increasing Ψ significantly improves the average BLER of PR and the trend is linearly decreasing. Clearly, this observation perfectly matches up with the developed formula in (16), where the error performance also becomes zero when we take into consideration 1/Ψ = 0. Meanwhile, varying PR only improves the BLER of IR in moderate SNR but saturates at high SNR, which perfectly agrees with the conclusion drawn on (30). On this basis, in order to improve the BLER of IR, we should take care of both increasing Ψ in conjunction with an increasing number of block-lengths.
Fig 5. Impact of Ψ on BLER, with LRX = 100 c.u and NRX = 150 bits.
5 Conclusion
In this work, we have studied the performance of symbiotic backscatter communication systems with short-packet transmissions. Particularly, aiming to characterize the system performance without performing any simulation, we derived closed-form approximate and asymptotic expressions of the average BLER for both the primary receiver and IoT sensor. These mathematical frameworks enable us to directly assess the system performance by the key parameters of the transmit power, fading parameters, data amount, and packet length. To ensure the correctness of the developed mathematical framework, we produced some illustrative simulation results based on the Monte-Carlo simulation while comparing the actual impact of system parameters on the BLER behaviour over the analysis outcome.
Supporting information
(ZIP)
Data Availability
We confirm that “All relevant data are within the manuscript and its Supporting information files.” We have also provided our simulation code as Supporting information Files.
Funding Statement
This work was supported by the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT) (No. 2022R1A2C1003549).
References
- 1. Nguyen DC, Ding M, Pathirana PN, Seneviratne A, Li J, et al. 6G Internet of Things: A Comprehensive Survey. IEEE IoT J. 2021;9(1):359–383. [Google Scholar]
- 2. De Alwis C, Kalla A, Pham QV, Kumar P, Dev K, et al. Survey on 6G Frontiers: Trends, Applications, Requirements, Technologies and Future Research. IEEE Open J Commun Soc. 2021;2:836–886. doi: 10.1109/OJCOMS.2021.3071496 [DOI] [Google Scholar]
- 3.Le M, Huynh-The T, Do-Duy T, Vu TH, Hwang WJ, Pham QV. Applications of Distributed Machine Learning for the Internet-of-Things: A Comprehensive Survey. arXiv preprint arXiv:231010549. 2023;.
- 4. Chowdhury MZ, Shahjalal Md, Ahmed S, Jang YM. 6G Wireless Communication Systems: Applications, Requirements, Technologies, Challenges, and Research Directions. IEEE Open J Commun Soc. 2020;1:957–975. doi: 10.1109/OJCOMS.2020.3010270 [DOI] [Google Scholar]
- 5. Liu G, Yu FR, Ji H, Leung VCM, Li X. In-Band Full-Duplex Relaying: A Survey, Research Issues and Challenges. IEEE Commun Surv Tutorials. 2015;17(2):500–524. doi: 10.1109/COMST.2015.2394324 [DOI] [Google Scholar]
- 6. Nguyen TN, Tu LT, Tran DH, Phan VD, Voznak M, et al. Outage Performance of Satellite Terrestrial Full-Duplex Relaying Networks With co-Channel Interference. IEEE Wireless Commun Lett. 2022;11(7):1478–1482. doi: 10.1109/LWC.2022.3175734 [DOI] [Google Scholar]
- 7. Tu LT, Phan VD, Nguyen TN, Tran PT, Duy TT, et al. Performance Analysis of Multihop Full-Duplex NOMA Systems with Imperfect Interference Cancellation and Near-Field Path-Loss. Sensors. 2023;23(1):524. doi: 10.3390/s23010524 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 8. Makki B, Chitti K, Behravan A, Alouini MS. A Survey of NOMA: Current Status and Open Research Challenges. IEEE Open J Commun Soc. 2020;1:179–189. doi: 10.1109/OJCOMS.2020.2969899 [DOI] [Google Scholar]
- 9. Mao Y, Dizdar O, Clerckx B, Schober R, Popovski P, et al. Rate-Splitting Multiple Access: Fundamentals, Survey, and Future Research Trends. IEEE Commun Surv Tutorials. 2022;24(4):2073–2126. doi: 10.1109/COMST.2022.3191937 [DOI] [Google Scholar]
- 10. Vu TH, Nguyen TV, Kim S. Wireless Powered Cognitive NOMA-Based IoT Relay Networks: Performance Analysis and Deep Learning Evaluation. IEEE IoT J. 2021;9(5):3913–3929. [Google Scholar]
- 11. Vu TH, Nguyen TV, Nguyen TT, Kim S. Performance Analysis and Deep Learning Design of Wireless Powered Cognitive NOMA IoT Short-Packet Communications With Imperfect CSI and SIC. IEEE IoT J. 2021;9(13):10464–10479. [Google Scholar]
- 12. Wang B, Liu KJR. Advances in cognitive radio networks: A survey. IEEE J Sel Top Signal Process. 2010;5(1):5–23. doi: 10.1109/JSTSP.2010.2093210 [DOI] [Google Scholar]
- 13. Nguyen H, Nguyen TN, Minh BV, Pham THT, Le AT, et al. Security-Reliability Analysis in CR-NOMA IoT Network Under I/Q Imbalance. IEEE Access. 2023;11:119045–119056. doi: 10.1109/ACCESS.2023.3327789 [DOI] [Google Scholar]
- 14. Tu LT, Nguyen TN, Duy TT, Tran PT, Voznak M, et al. Broadcasting in Cognitive Radio Networks: A Fountain Codes Approach. IEEE Trans Veh Technol. 2022;71(10):11289–11294. doi: 10.1109/TVT.2022.3188969 [DOI] [Google Scholar]
- 15. Sherazi HHR, Zorbas D, O’Flynn B. A Comprehensive Survey on RF Energy Harvesting: Applications and Performance Determinants. Sensors. 2022;22(8):2990. doi: 10.3390/s22082990 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 16. Vu TH, Kim S. Performance Evaluation of Power-Beacon-Assisted Wireless-Powered NOMA IoT-Based Systems. IEEE IoT J. 2021;8(14):11655–11665. [Google Scholar]
- 17. Nguyen TN, Tu LT, Fazio P, Van Chien T, Le CV, et al. On the Dilemma of Reliability or Security in Unmanned Aerial Vehicle Communications Assisted by Energy Harvesting Relaying. IEEE J Sel Areas Commun. 2023;42(1):52–67. doi: 10.1109/JSAC.2023.3322756 [DOI] [Google Scholar]
- 18. Tin PT, Dinh BH, Nguyen TN, Ha DH, Trang TT. Power Beacon-Assisted Energy Harvesting Wireless Physical Layer Cooperative Relaying Networks: Performance Analysis. Symmetry. 2020;12(1):106. doi: 10.3390/sym12010106 [DOI] [Google Scholar]
- 19. Nguyen TN, Tran DH, Van Chien T, Phan VD, Nguyen NT, et al. Physical Layer Security in AF-Based Cooperative SWIPT Sensor Networks. IEEE Sens J. 2022;23(1):689–705. doi: 10.1109/JSEN.2022.3224128 [DOI] [Google Scholar]
- 20. Vu TH, Nguyen TV, Kim S. Cooperative NOMA-Enabled SWIPT IoT Networks With Imperfect SIC: Performance Analysis and Deep Learning Evaluation. IEEE IoT J. 2021;9(3):2253–2266. [Google Scholar]
- 21. Vu TH, Jee A, da Costa DB, Kim S. STAR-RIS Empowered NOMA Systems With Caching and SWIPT. IEEE Open J Commun Soc. 2023;5:379–396. doi: 10.1109/OJCOMS.2023.3344582 [DOI] [Google Scholar]
- 22. Nguyen TN, Duy TT, Tran PT, Voznak M, Li X, et al. Partial and Full Relay Selection Algorithms for AF Multi-Relay Full-Duplex Networks With Self-Energy Recycling in Non-Identically Distributed Fading Channels. IEEE Trans Veh Technol. 2022;71(6):6173–6188. doi: 10.1109/TVT.2022.3158340 [DOI] [Google Scholar]
- 23. Liang YC, Long R, Zhang Q, Niyato D. Symbiotic Communications: Where Marconi Meets Darwin. IEEE Wireless Commun. 2022;29(1):144–150. doi: 10.1109/MWC.101.2100132 [DOI] [Google Scholar]
- 24. Long R, Liang YC, Guo H, Yang G, Zhang R. Symbiotic Radio: A New Communication Paradigm for Passive Internet of Things. IEEE IoT J. 2019;7(2):1350–1363. [Google Scholar]
- 25. Le AT, Nguyen TN, Tu LT, Tran TP, Duy TT, et al. Performance Analysis of RIS-Assisted Ambient Backscatter Communication Systems. IEEE Wireless Commun Lett. 2023;13(3):791–795. doi: 10.1109/LWC.2023.3344113 [DOI] [Google Scholar]
- 26.Janjua MB, Arslan H. Survey on symbiotic radio: A paradigm shift in spectrum sharing and coexistence. arXiv preprint arXiv:211108948. 2021;.
- 27. Long R, Guo H, Zhang L, Liang YC. Full-Duplex Backscatter Communications in Symbiotic Radio Systems. IEEE Access. 2019;7:21597–21608. doi: 10.1109/ACCESS.2019.2898474 [DOI] [Google Scholar]
- 28. Guo H, Liang YC, Long R, Zhang Q. Cooperative Ambient Backscatter System: A Symbiotic Radio Paradigm for Passive IoT. IEEE Wireless Commun Lett. 2019;8(4):1191–1194. doi: 10.1109/LWC.2019.2911500 [DOI] [Google Scholar]
- 29. Liang YC, Zhang Q, Larsson EG, Li GY. Symbiotic Radio: Cognitive Backscattering Communications for Future Wireless Networks. IEEE Trans Cognit Commun Networking. 2020;6(4):1242–1255. doi: 10.1109/TCCN.2020.3023139 [DOI] [Google Scholar]
- 30. Wu T, Jiang M, Zhang Q, Li Q, Qin J. Beamforming Design in Multiple-Input-Multiple-Output Symbiotic Radio Backscatter Systems. IEEE Commun Lett. 2021;25(6):1949–1953. doi: 10.1109/LCOMM.2021.3060468 [DOI] [Google Scholar]
- 31. Kuai X, Yuan X, Liang YC. Message-Passing Receiver Design for Multiuser Multi-Backscatter-Device Symbiotic Radio Communications. IEEE Trans Wireless Commun. 2021;21(6):4563–4578. doi: 10.1109/TWC.2021.3131244 [DOI] [Google Scholar]
- 32. Yang H, Ding H, Elkashlan M. Opportunistic Symbiotic Backscatter Communication Systems. IEEE Commun Lett. 2022;27(1):100–104. doi: 10.1109/LCOMM.2022.3202362 [DOI] [Google Scholar]
- 33. Ren C, Liu L. Toward Full Passive Internet of Things: Symbiotic Localization and Ambient Backscatter Communication. IEEE IoT J. 2023;10(22):19495–19506. [Google Scholar]
- 34. Ataeeshojai M, Elliott RC, Krzymień WA, Tellambura C, Maljević I. Symbiotic Backscatter Communication Underlying a Cell-Free Massive MIMO System. IEEE IoT J. 2023;10(19):16758–16777. [Google Scholar]
- 35. Li X, Jiang J, Wang H, Han C, Chen G, et al. Physical Layer Security for Wireless-Powered Ambient Backscatter Cooperative Communication Networks. IEEE Trans Cognit Commun Networking. 2023;9(4):927–939. doi: 10.1109/TCCN.2023.3270425 [DOI] [Google Scholar]
- 36. Ji B, Liu Y, Li T, Xing L, Wang W, et al. Anti-Jamming Null Space Projection Beamforming Based on Symbiotic Radio. CMES. 2023;138(1):679–689. doi: 10.32604/cmes.2023.028667 [DOI] [Google Scholar]
- 37. Bennis M, Debbah M, Poor HV. Ultrareliable and Low-Latency Wireless Communication: Tail, Risk, and Scale. Proc IEEE. 2018;106(10):1834–1853. doi: 10.1109/JPROC.2018.2867029 [DOI] [Google Scholar]
- 38. Polyanskiy Y, Poor HV, Verdu S. Channel Coding Rate in the Finite Blocklength Regime. IEEE Trans Inf Theory. 2010;56(5):2307–2359. doi: 10.1109/TIT.2010.2043769 [DOI] [Google Scholar]
- 39. Vu TH, Nguyen TV, da Costa DB, Kim S. Intelligent Reflecting Surface-Aided Short-Packet Non-Orthogonal Multiple Access Systems. IEEE Trans Veh Technol. 2022;71(4):4500–4505. doi: 10.1109/TVT.2022.3146856 [DOI] [Google Scholar]
- 40. Nguyen TT, Vu TH, da Costa DB, Nguyen PX, Ta HQ. Short-Packet Communications in IoT-Aided Cellular Cooperative Networks With Non-Orthogonal Multiple Access. IEEE Trans Veh Technol. 2022;72(1):1296–1301. doi: 10.1109/TVT.2022.3204460 [DOI] [Google Scholar]
- 41. Vu TH, Nguyen TT, Pham QV, da Costa DB, Kim S. A Novel Partial Decode-and-Amplify NOMA-Inspired Relaying Protocol for Uplink Short-Packet Communications. IEEE Wireless Commun Lett. 2023;12(7):1244–1248. doi: 10.1109/LWC.2023.3269501 [DOI] [Google Scholar]
- 42. Vu TH, Nguyen TV, Pham QV, da Costa DB, Kim S. STAR-RIS-Enabled Short-Packet NOMA Systems. IEEE Trans Veh Technol. 2023;72(10):13764–13769. doi: 10.1109/TVT.2023.3278737 [DOI] [Google Scholar]
- 43. Chu Z, Hao W, Xiao P, Khalily M, Tafazolli R. Resource Allocations for Symbiotic Radio With Finite Blocklength Backscatter Link. IEEE IoT J. 2020;7(9):8192–8207. [Google Scholar]
- 44. Yang H, Ye Y, Liang K, Chu X. Energy Efficiency Maximization for Symbiotic Radio Networks With Multiple Backscatter Devices. IEEE Open J Commun Soc. 2021;2:1431–1444. doi: 10.1109/OJCOMS.2021.3090836 [DOI] [Google Scholar]
- 45. Sui L, Lin Z, Xiao P, Poor HV, Vucetic B. Performance Analysis of Multiple-Antenna Ambient Backscatter Systems at Finite Blocklengths. IEEE IoT J. 2023;10(18):16061–16075. [Google Scholar]
- 46. Nguyen TN, Van Chien T, Tran DH, Phan VD, Voznak M, et al. Security-Reliability Tradeoffs for Satellite–Terrestrial Relay Networks With a Friendly Jammer and Imperfect CSI. IEEE Trans Aerosp Electron Syst. 2023;59(5):7004–7019. [Google Scholar]
- 47. Tse D, Viswanath P. Fundamentals of wireless communication. Cambridge university press; 2005. [Google Scholar]
- 48. Jeffrey A, Zwillinger D. Table of integrals, series, and products. Elsevier; 2007. [Google Scholar]
- 49. Prudnikov AP, Brychkov IA, Marichev OI. Integrals and series: special functions. vol. 2. CRC press; 1986. [Google Scholar]
- 50. Mittal P, Gupta K; Springer. An integral involving generalized function of two variables. Proceedings of the Indian academy of sciences-section A. 1972;75(3):117–123. doi: 10.1007/BF03049732 [DOI] [Google Scholar]
- 51. Ismail ME. The H-Function with Applications in Statistics and Other Disciplines. JSTOR; 1980. [Google Scholar]