Abstract
In this paper, we propose a new data-aided (DA) joint angle and delay (JADE) maximum likelihood (ML) estimator. The latter consists of a substantially modified and, hence, significantly improved gray wolf optimization (GWO) technique by fully integrating and embedding within it the powerful importance sampling (IS) concept. This new approach, referred to hereafter as GWOEIS (for “GWO embedding IS”), guarantees global optimality, and offers higher resolution capabilities over orthogonal frequency division multiplex (OFDM) (i.e., multi-carrier and multi-path) single-input multiple-output (SIMO) channels. The traditional GWO randomly initializes the wolfs’ positions (angles and delays) and, hence, requires larger packs and longer hunting (iterations) to catch the prey, i.e., find the correct angles of arrival (AoAs) and time delays (TDs), thereby affecting its search efficiency, whereas GWOEIS ensures faster convergence by providing reliable initial estimates based on a simplified importance function. More importantly, and beyond simple initialization of GWO with IS (coined as IS-GWO hereafter), we modify and dynamically update the conventional simple expression for the convergence factor of the GWO algorithm that entirely drives its hunting and tracking mechanisms by accounting for new cumulative distribution functions (CDFs) derived from the IS technique. Simulations unequivocally confirm these significant benefits in terms of increased accuracy and speed Moreover, GWOEIS reaches the Cramér–Rao lower bound (CRLB), even at low SNR levels.
Keywords: importance sampling (IS), gray wolf optimization (GWO), data-aided (DA), joint angle and delay estimation (JADE), maximum likelihood (ML), multi-carrier, orthogonal frequency division multiplex (OFDM), multi-path, single-input multiple-output (SIMO)
1. Introduction
JADE (For the reader’s convenience, please find and refer to the full list of all abbreviations adopted in this paper, at the very end, right before the bibliography section) is a crucial operation in many digital receivers. Highly accurate and computationally inexpensive JADE is required in many fields ranging from military applications such as RADAR or SONAR systems to wireless indoor positioning [1,2] and wireless communication systems [3]. Moreover, the estimation of AoAs and TDs enable the design of highly accurate localization techniques [4]. Many existing works have focused on solving the JADE problem. Most fall under the subspace-based category such as Multiple Signal Classification (MUSIC) [5], ESPRIT [6], and the 2D unitary matrix pencil (UMP) [7]. One of the iterative ML estimators based on the space-alternating generalized expectation maximization (SAGE) algorithm was proposed in [8]. The approach in [9] mainly targets only the DOA estimation. It introduces a DOA estimation algorithm in a full-dimension MIMO system by solving the maximum likelihood estimation using expectation-maximization (EM) algorithm. Recently, a tensor-based approach for channel and target parameter estimation was proposed in [10]. Also, a non-iterative ML estimator that tackles the JADE problem in a multi-carrier transmission context was developed in [11] using the IS technique. More recently, we proposed a new ML JADE solution in a non-DA (NDA) single-carrier scenario [12]. Shortly after, we have tackled the same scenario by making IS initialize the differential evolution (DE) technique in [13]. Referred to hereafter as IS-DE, it was a first attempt to tackle JADE by exploiting a bio-inspired optimization approach.
Under this category, GWO has notably been used to optimize and solve many engineering problems. The best-known applications are numerical simulations and stability fields [14,15], feature acquisition selection, dataset classification, neural networks training [16], etc. A multi-objective GWO was developed for cloud computing in [17], and for wireless sensor networks in [18]. It was adapted to a multi-robot application in [19], and to unmanned aerial vehicles (UAVs) in [20]. A GWO-based optimal channel estimation technique was proposed for large-scale MIMO in LTE networks in [21]. A dragonfly-evaluated gray wolf optimization (DA-GWO) model was introduced in [22], which hybridizes the concepts of dragonfly algorithm and GWO for channel estimation in millimeter wave massive MIMO system. In [23], we find also that the GWO algorithm was used only for direction of arrival (DoA) estimation.
Nevertheless, GWO suffers from slow convergence, limited solution accuracy, and susceptibility to getting trapped in local optima. Many improvements to GWO were proposed in different applications [24,25,26,27], but none were to tackle JADE, to the best of our knowledge.
In this paper, we exploit GWO [28] to solve JADE over OFDM SIMO transmissions in multi-path environments. The main idea consists of improving the GWO by initializing the wolf positions using the IS technique instead of random positions. More importantly, and beyond simple initialization of GWO with IS (coined as IS-GWO hereafter), we modify and dynamically update the conventional simple expression for the convergence factor of the GWO algorithm that entirely drives its hunting and tracking mechanisms by accounting for new CDFs derived from the IS technique. Numerical assessments will confirm the advantages of the proposed GWOEIS over IS, GWO, IS-GWO, DE, IS-DE, and other state-of-the-art JADE solutions in terms of estimation accuracy, population or sample size (e.g., number of wolves), global convergence, and convergence speed. The remainder of this paper is organized as follows. Section 2 introduces the multi-carrier SIMO system model in multi-path environments. Section 3 addresses JADE, first by deriving the concentrated likelihood function (CLF), then the IS technique, and ultimately the main common algorithmic steps and the key variations we introduced to some that ultimately encompass GWO, IS-GWO, and the proposed GWOEIS. Section 4 discusses our computer simulations and results, whereas Section 5 concludes our work.
The adopted notations are as follows. Vectors and matrices are represented in lower- and upper-case bold fonts, respectively. Moreover, and denote the conjugate and Hermitian (i.e., transpose conjugate) operators. The Euclidean norm of any vector is denoted as , and denotes the identity matrix. For any matrix , , and , denote its lth column and th entry, respectively. The kronecker product of any two matrices and is denoted as . For any vector , denotes its pth entry or element, and refers to the diagonal matrix whose elements are those of . Moreover, returns the modulus of any complex number. Finally, j is the pure imaginary number (i.e., ), and the notation ≜ is used for definitions.
2. System Model
We consider a SIMO OFDM system characterized by a single transmitting and P receiving antenna elements and K sub-carriers. At each time period, this system transmits over these sub-carriers K symbols , all belonging to an M-ary constellation alphabet , and are assumed to be known at pilot transmission periods (i.e., replaced a priori by 1) in the DA-type estimation scheme we are adopting here. The transmit data then goes through a multi-path channel consisting of different paths, whose number Q is assumed to be known.
The resulting multi-path SIMO channel is characterized by Q different AoAs ; Q different TDs , where can be chosen to be as large as desired; denotes a uniform distribution over the interval ; and Q complex gains . All these three parameter vectors are assumed to be unknown.
At the receiver side, the observation signal, , over the pth antenna and the kth sub-carrier, is given by:
| (1) |
where is an additive white Gaussian noise (AWGN) with zero mean and variance , and is the channel frequency response (CFR), defined as follows:
| (2) |
where is the sub-carrier spacing. By stacking, the scalar signal observation in (1) received at each kth sub-carrier into a single observation vector is modeled as follows:
| (3) |
where is an i.i.d. and spatially uncorrelated zero-mean Gaussian noise vector and is the CFR vector over all antennas, defined as:
| (4) |
| (5) |
where is a steering matrix, is the steering vector at AoA defined for simplicity and without loss of generality here over a uniform linear array (ULA) as:
and is the TDs matrix, in which is some index translation of (e.g., , if K is even, if K is odd, etc.), with no impact at all on what follows.
For an even more compact notation, we now stack the CFR vector over all sub-carriers to obtain the total CFR vector as follows:
| (6) |
where is the steering matrix defined as:
| (7) |
and is the TDs matrix defined as:
| (8) |
Hence, at pilot period transmissions where sub-carriers are not modulated (i.e., ), after we stack both and in the same way we did to transform into , we obtain:
| (9) |
3. Joint Angle and Delay Estimation (JADE)
3.1. Derivation of the CLF
At any given pilot transmission period, we can derive the log-likelihood function (LLF) that depends on all three unknown parameter vectors , , and as follows:
| (10) |
Hence, we can estimate using the least squares (LS) solution as follows:
| (11) |
where is the Moore–Penrose pseudo-inverse of . By injecting into (10), we obtain the CLF:
| (12) |
Hence, we can obtain the joint ML estimates of and as the optimal solution to the following optimization problem:
| (13) |
3.2. Overview/Summary of IS for ML DA JADE
We start by approximating in (12) as follows:
| (14) |
where denotes the identity matrix. Then, we plug (14) into (12) to obtain:
| (15) |
Now, injecting the expressions of and into (15), we obtain the approximate CLF:
| (16) |
where is the so-called periodogram of the observation signal [11] given by:
| (17) |
Relying on the observations made above, we summarize the IS process in [11] of generating the R realizations of the AoA-TD couples according to the following steps:
Step (1): we start by evaluating the periodogram in (17) at all grid points where denotes the set of points obtained over the interval with a uniform sampling step .
- Step (2): we evaluate the so-called joint pseudo-pdfs [11] set of values over the above AoA-TD grid as follows:
where is a design parameter to be chosen properly later on.(18) - Step (3): we evaluate the marginal pseudo-pdf of as follows:
(19)
Then, we can find the initial TD estimates that correspond to the Q maxima of (19) as:
| (20) |
where returns the Q maxima of the function f.
- Step (4): for , we compute the pseudo-CDF of as follows:
where(21) (22) - Step (5): For , we generate R realizations . Then, we apply a linear interpolation to obtain the rth TD realization:
(23) - Step (6): We evaluate the conditional pseudo-pdf of given for as follows:
(24)
Then, we obtain the initial Q AoA estimates as:
| (25) |
- Step (7): similarly to Step 4, we compute the conditional pseudo-CDF as:
where(26) (27) - Step (8): Similarly to Step 5, we generate R realizations for . Then, we apply a linear interpolation to obtain the rth AoA realization:
(28)
Thus, we are able to generate R JADE realizations as:
| (29) |
where is the AoAs vector estimate, and is the TDs vector estimate. These realizations readily enable the direct implementation of an IS ML solution to (13) as:
| (30) |
3.3. GWO vs. Combining|Embedding IS (IS-GWO|GWOEIS)
GWO is inspired by the leadership hierarchy and the hunting mechanism of gray wolves in nature [28]. In a pack or population of, say, individuals, we identify four types of gray wolves that emulate their leadership hierarchy: the -type are responsible for making hunting decisions (representing the solutions with best results). The -type help the -type in decision making and act as their best substitute-candidates when one of them becomes old or dies (second-best solutions in the population). The -type have only to submit to the - and -types (third-best solutions). And the -type are of the lowest rank, and must yield to the dominant ones. Guided by this “social” hierarchy’s rules, gray wolves proceed to hunt along three main and consecutive stages: (1) tracking, chasing, and approaching the prey; (2) pursuing, encircling, and harassing it once it stops moving; and (3) attacking it.
Mathematically and generally speaking, GWO translates the leadership hierarchy and the hunting mechanism summarily described above due to lack of space into an optimization by search (i.e., hunting) in any multi-dimensional space whose best solution (i.e., prey) that minimizes a given criterion (i.e., so-called “fitness function”) is found in an iterative manner by mimicking the gray wolves (i.e., search agents) hunting behavior (i.e., search adaptation rules).
In the present case, and in (13) stand, respectively, for the prey to be hunted and the fitness function to be minimized in a -dimensional space. Hence, GWO translates as follows:
Step (1): first, the wolves’ positions are initialized in the space according to one of the following cases (a) or (b).
Step (1.a) [GWO]: The conventional GWO initially places the wolves pack of individuals at random positions in the search space where and . Hence, it requires larger packs and longer hunting (iterations) to catch the prey, i.e., find the correct angles of arrival (AoAs) and time delays (TDs) without guaranteeing global convergence.
Step (1.b) [IS-GWO or GWOEIS]: Instead of random initial placement, IS-GWO and GWOEIS position the wolves at , stemming from the realizations generated in (29). Hence, even with relatively less realizations, this still guarantees global convergence, and it would always provide good-enough rough initialization values to GWOEIS to make the latter converge much faster and more accurately with relatively less hunting iterations.
Step (2): at each iteration over the hunt duration , is evaluated over each individual in the pack, and the fittest three that better minimize it are identified as , , and , respectively.
Step (3): the so-called convergence factor guiding the hunt is updated according to one of the following cases (a) or (b).
Step (3.a) [GWO or IS-GWO]: is simply set to decrease linearly from 2 to 0 over the hunt duration . Therefore, the positions of the wolves to converge to local minima.
- Step (3.b) [GWOEIS]: To improve and speed up convergence, instead of a common convergence factor, each realization or individual in the pack is assigned one of its own that accounts both for the AoA and TD pseudo-CDFs calculated in Steps (4) and (7) of the IS technique (cf. Section 3.2) as follows:
where , is the dimension index, and(31) (32)
where denotes the i-th element of the set . and are the initial TD and AoA IS estimates obtained in (20) and (25), respectively, and .(33)
When using the linearly decreasing factor in Step (3.a), the positions of the wolves can converge to local minima. To mitigate this issue, we generate for each individual a specific convergence factor that decreases with the iteration index while accounting through the pseud-CDF values for the distance between the gray wolves and the prey. As long as a wolf is far away from the prey, the uniform variable will generate realizations closer to 1. Once this wolf gets closer to the prey, the realization becomes quasi-static since, the convergence factor is then mainly scaled by .
Step (4): For each lead gray wolf , , or , we generate two random values, and in for the calculation of two update coefficients (or with respect to each realization or individual r in the pack), and according to one of the following cases (a) or (b).
- Step (4.a) [GWO or IS-GWO]:
(34)
In other words, the update coefficients and are assigned random values in and , respectively.
- Step (4.b) [GWOEIS]:
(35)
Here, is assigned a random value in .
Step (5): Let denote the distance between the lead wolf * and the rth individual in the pack (or search agent) across the j-th dimension. The lead wolves’ positions are then updated with respect to each realization r in the pack through intermediate variables according to one of the following cases (a) or (b).
- Step (5.a) [GWO or IS-GWO]:
(36) - Step (5.b) [GWOEIS]:
(37)
Hence, before coming back to Step (2) if , each individual’s location is updated in either case based on these intermediate variables as follows:
| (38) |
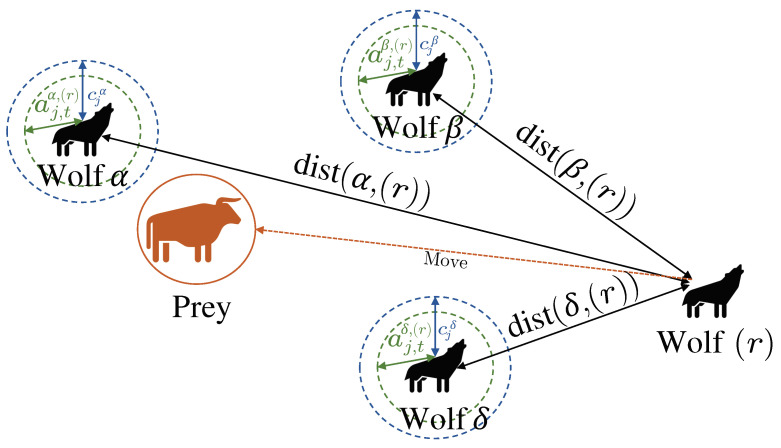
Figure 1 depicts the way to update a search agent’s position according to -type, -type, and -type wolves based on (37) and (38) for the proposed GWOEIS algorithm. Finally, the joint AoA-TD estimate is selected as the last position of the lead wolf :
| (39) |
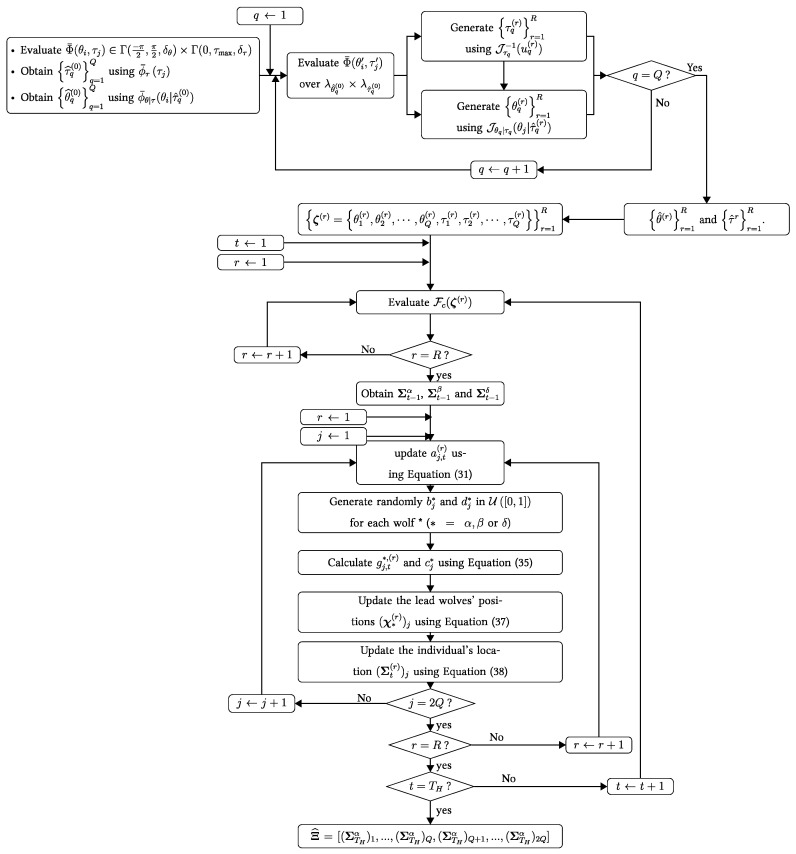
where the choice of Tech ∈ {“GW0”, “IS-GWO”, “GWOEIS”} determines the cases considered in Steps (1), (3), (4), and (5). We summarize the GWOEIS algorithm in Figure 2.
Figure 1.
Position updating in GWOEIS.
Figure 2.
Flow chart of GWOEIS algorithm.
4. Simulation Results
In this section, we assess the performance of the proposed GWOEIS solution and other key benchmarks for comparisons in terms of the root mean square error (RMSE) or the normalized MSE (NMSE) over a total number of Monte-Carlo runs . Following the IEEE 802.11ac standard (see [7] and first reference therein), we consider a bandwidth MHz with a sub-carrier spacing KHz giving a total of 256 sub-carriers, among which 11 are exploited for network signaling purposes and the remainder are payload carriers (i.e., ). We also consider antennas and equi-powered paths with AoAs and and TDs 25 ns and ns, respectively. Moreover, we set , ns, , ns, and .
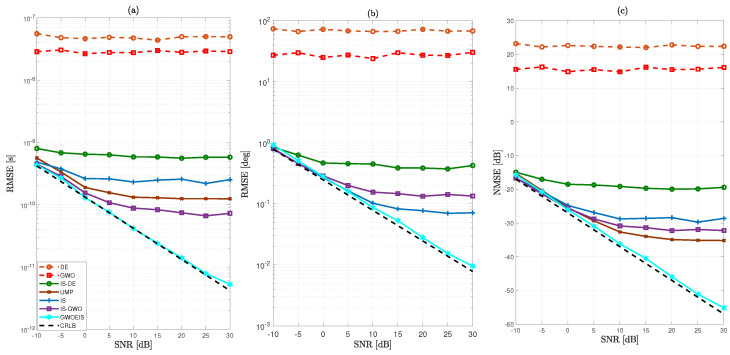
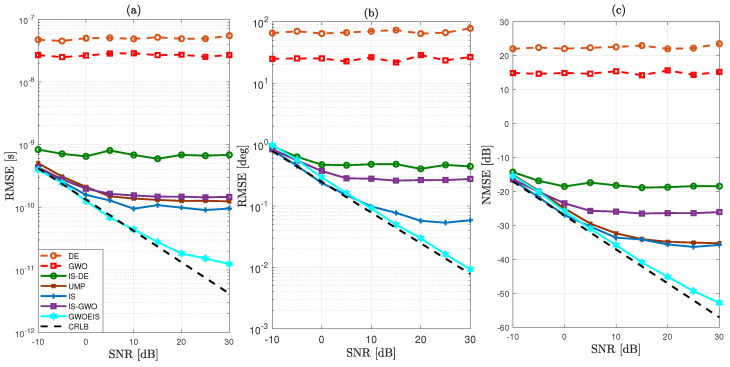
In Figure 3 and Figure 4, we evaluate the RMSE/NMSE performance versus the SNR to compare the new GWOEIS solution against the Cramér–Rao lower bound (CRLB) of [6], the UMP algorithm in [7], the classic GWO in [28], the classic DE [13], the IS technique in [11], IS-DE that simply combines DE with IS in [13], and another benchmark version developed here by simply combining this time IS with GWO, referred to as IS-GWO.
Figure 3.
MSE vs. the SNR in dB for (; = [25 ns, 62.5 ns]), , and of: (a) the Q TDs, (b) the Q AoAs, and (c) the channel coefficients (on average, per element, for all three parameter types).
Figure 4.
MSE vs. the SNR in dB for (; = [25 ns, 62.5 ns]), , and of: (a) the Q TDs, (b) the Q AoAs, and (c) the channel coefficients (on average, per element, for all three parameter types).
As shown in Figure 3 and Figure 4, our approach outperforms all other estimation techniques, both in terms of TD and AoA estimations. Additionally, it reaches the CRLB, even at low SNR levels and even with a very low value either parameter and . We also observe a severe performance degradation of the original GWO and DE techniques due to the high dimension (i.e., ) of the optimization problem. When combined with IS, IS-DE improves a little but is outperformed by IS-GWO, and more so by GWOEIS.
In Figure 3c and Figure 4c, we compare the channel NMSE using the estimates of the TDs and AoAs assuming a perfect knowledge of the channel gains. Our approach remarkably outperforms all other estimation techniques and reaches the lower bound, even at very low SNR levels and even with a very low value either parameter and .
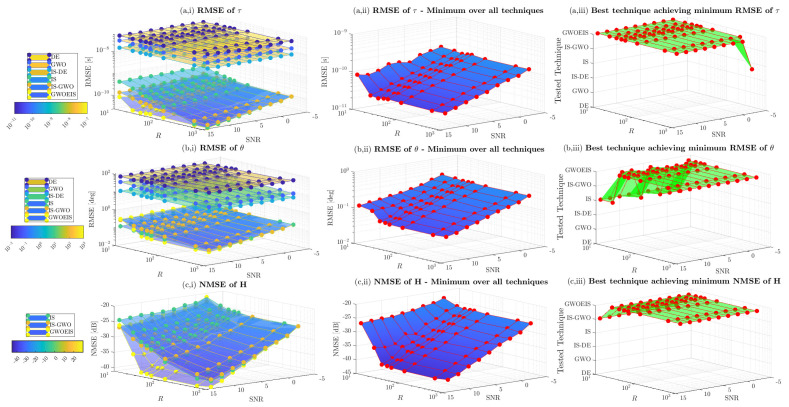
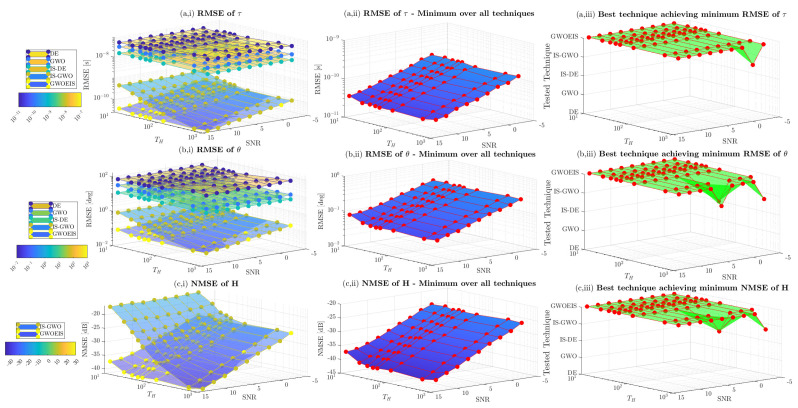
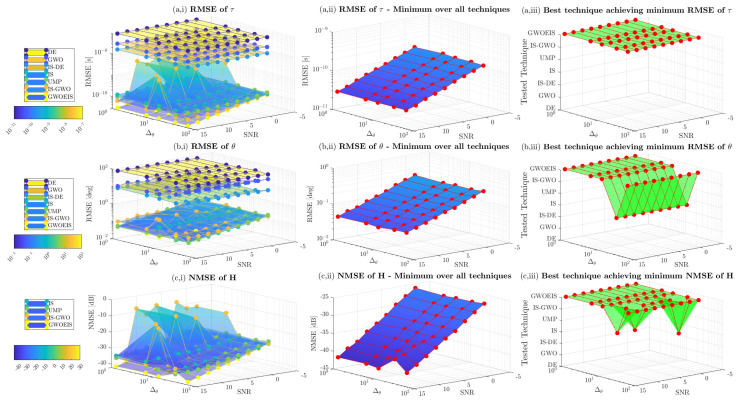
In Figure 5 and Figure 6, we assess the impact of the samples size R and the hunting duration on channel estimation performance versus the SNR. Here, the sample size R refers to the number of realizations with IS, to the wolves pack size with GWO, IS-GWO, and GWOEIS, or the number of individuals with DE and IS-DE. The number of iterations (e.g., ) is defined only for iterative approaches, i.e., GWO, IS-GWO, GOWEIS, DE, and IS-DE solutions. We notice that both parameters can have a detrimental effect on the exploration abilities of these techniques. Thus, they need to be set as large as possible to cover the widest area of the multidimensional space.
Figure 5.
MSE vs. the SNR in dB and the samples size R for (; = [25 ns, 62.5 ns]) and .
Figure 6.
MSE vs. the SNR in dB and the iterations number (e.g., ) for (; = [25 ns, 62.5 ns]) and .
In Figure 5(a,i,b,i,c,i), we assess the estimation performance of the TD, the AoA, and the channel, respectively. GWOEIS, IS-GWO, and IS performs better than DE, GWO, and IS-DE. Figure 5(a,ii,b,ii,c,ii) show the minimum RMSE over all techniques for TD, AoA, and channel estimation, respectively. The RMSE decreases when R and SNR increase. In Figure 5(a,iii,b,iii,c,iii), we can see that GWOEIS achieves the best performance in terms of TD, AoA, and channel estimation over and all SNR values. IS, IS-GWO, GWO, DE, and IS-DE can not match the performance of GWOEIS, even with , but at the expense of significant increase in computational cost.
In Figure 6, we assess the impact of on RMSE performance of the iterative techniques. Once again, GWOEIS outperforms all other iterative techniques in terms of TD, AoA, and channel estimation. By increasing the number of iterations, we reach the best performance for the all algorithms, as shown in Figure 6(a,ii,b,ii,c,ii). Moreover, in Figure 6(a,iii,b,iii,c,iii), we notice that a small order of 10 iterations is enough to put GWOEIS on the top of the rest, with estimation accuracy gains constantly increasing with , making its potential gains in computational complexity remarkably large when compared to other techniques that require a very high number of iterations.
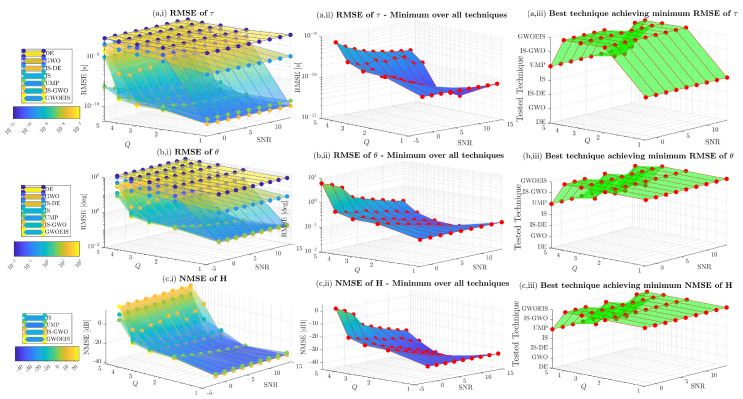
In Figure 7, we investigate the effect of the number of paths on the estimation performance. We observe that the new approach, GWOEIS, outperforms most of the benchmarks in the high and low SNR scenarios for TD, AoA, and channel estimation when .
Figure 7.
MSE vs. the SNR in dB and the number of paths Q for and .
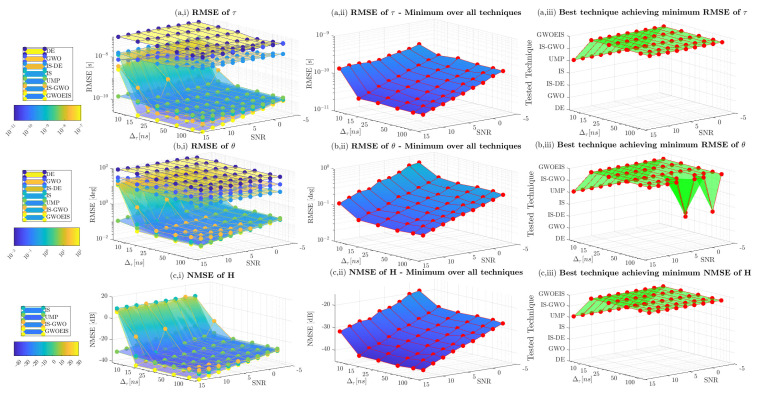
We consider also the same configuration to evaluate the performance of all of the approaches in terms of temporal and angular separations. In Figure 8, we fix the first delay at , and we vary the second delay at . It is clearly seen that our approach is still capable of achieving the CRLB, even in a challenging scenario with a very small temporal separations of . In Figure 9, we fix the first AoA at , and we vary the second AoA . Here, again, we can highlight the robustness and the super-resolution capacity of our approach, and to appreciate its superiority in challenging scenarios where the paths are closely spaced in both temporal and spatial domains. We have to mention that Figure 8(a,iii,b,iii,c,iii) show the superiority of UMP reaching the best techniques achieving minimum RMSE only when .
Figure 8.
RMSE vs. the SNR in dB and the temporal separation in ns with , , and .
Figure 9.
RMSE vs. the SNR in dB and the angular separation in degrees with , , and .
5. Conclusions
In this work, we presented a new DA ML JADE estimator over OFDM SIMO multi-path channels referred to as GWOEIS, whose key innovation lies in exploiting and embedding the powerful IS concept to avoid the random initialization issues of the traditional GWO, and to significantly improve the hunting mechanism. GWOEIS ensures faster convergence by providing initial estimates based on a simplified importance function. More importantly, and beyond simple initialization of GWO with IS, we modify and dynamically update the conventional simple expression for the convergence factor of the GWO algorithm that entirely drives its hunting and tracking mechanism by accounting for new CDFs derived from the IS technique. The latter significantly boost the estimation performance. Overall, the simulation results show more accurate estimation performance at faster convergence rates with GWOEIS.
Abbreviations
The following abbreviations are used in this manuscript:
| AoA | Angle of Arrival |
| AWGN | Additive White Gaussian Noise |
| CDF | Cumulative Distribution Function |
| CFR | Channel Frequency Response |
| CLF | Concentrated Likelihood Function |
| CRLB | Cramér–Rao Lower Bound |
| DA | Data-Aided |
| DE | Differential Evolution |
| DoA | Direction of Arrival |
| GWO | Gray Wolf Optimization |
| GWOEIS | Gray Wolf Optimization Embedding Importance Sampling |
| IS | Importance Sampling |
| IS-DE | Importance Sampling–Differential Evolution |
| IS-GWO | Importance Sampling–Gray Wolf Optimization |
| JADE | Joint Angle and Delay Estimation |
| LLF | Log-Likelihood Function |
| LS | Least Squares |
| ML | Maximum Likelihood |
| MSE | Mean Square Error |
| MUSIC | Multiple Signal Classification |
| NDA | Non-Data-Aided |
| NMSE | Normalized MSE |
| OFDM | Orthogonal Frequency-Division Multiplexing |
| Probability Density Function | |
| RMSE | Root Mean Square Error |
| SAGE | Space-Alternating Generalized Expectation |
| SIMO | Single Input Multiple Output |
| SNR | Signal-to-Noise Ratio |
| TD | Time Delay |
| UAV | Unmanned Aerial Vehicles |
| UMP | Unitary Matrix Pencil |
Author Contributions
Conceptualization, M.A., S.B.A. and S.A.; methodology, M.A., S.B.A. and S.A.; software, M.A.; validation, M.A., S.B.A. and S.A.; formal analysis, M.A.; data curation, M.A.; writing—original draft preparation, M.A.; writing—review and editing, M.A. and S.A.; supervision, S.A. All authors have read and agreed to the published version of the manuscript.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
All authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Funding Statement
Work supported in part by the Discovery Grants Program of NSERC (Natural Sciences and Engineering Research Council of Canada).
Footnotes
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
References
- 1.Pan M., Liu P., Liu S., Qi W., Huang Y., You X., Jia X., Li X. Efficient joint DOA and TOA estimation for indoor positioning with 5G picocell base stations. IEEE Trans. Instrum. Meas. 2022;71:1–19. doi: 10.1109/tim.2022.3191705. [DOI] [Google Scholar]
- 2.Yoon S., Lee K., Yun Y., Rhee I. ACMI: FM-Based indoor localization via autonomous fingerprinting. IEEE Trans. Mob. Comput. 2016;15:1318–1332. doi: 10.1109/tmc.2015.2465372. [DOI] [Google Scholar]
- 3.Xhafa A., del Peral-Rosado J.A., López-Salcedo J.A., Seco-Granados G. Evaluation of 5G positioning performance based on UTDoA, AoA and base-station selective exclusion. Sensors. 2021;22:101. doi: 10.3390/s22010101. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 4.Talvitie J., Levanen T., Koivisto M., Ihalainen T., Pajukoski K., Renfors M., Valkama M. Positioning and location-based beamforming for high speed trains in 5G NR networks; Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps); Abu Dhabi, United Arab Emirates. 9–13 December 2018; pp. 1–7. [Google Scholar]
- 5.Wang Y.Y., Chen J.T., Fang W.H. TST-MUSIC for joint DOA-delay estimation. IEEE Trans. Signal Process. 2001;49:721–729. doi: 10.1109/78.912916. [DOI] [Google Scholar]
- 6.Van der Veen A.J., Vanderveen M.C., Paulraj A. Joint angle and delay estimation using shift-invariance techniques. IEEE Trans. Signal Process. 1998;46:405–418. doi: 10.1109/78.655425. [DOI] [Google Scholar]
- 7.Gaber A., Omar A. A study of wireless indoor positioning based on joint TDOA and DOA estimation using 2-D matrix pencil algorithms and IEEE 802.11ac. IEEE Trans. Wirel. Commun. 2014;14:2440–2454. doi: 10.1109/twc.2014.2386869. [DOI] [Google Scholar]
- 8.Fleury B.H., Tschudin M., Heddergott R., Dahlhaus D., Pedersen K.I. Channel parameter estimation in mobile radio environments using the SAGE algorithm. IEEE J. Sel. Areas Commun. 1999;17:434–450. doi: 10.1109/49.753729. [DOI] [Google Scholar]
- 9.Zhou Z., Liu L., Zhang J. FD-MIMO via pilot-data superposition: Tensor-based DOA estimation and system performance. IEEE J. Sel. Top. Signal Process. 2019;13:931–946. doi: 10.1109/jstsp.2019.2938488. [DOI] [Google Scholar]
- 10.Zhang R., Cheng L., Wang S., Lou Y., Gao Y., Wu W., Ng D.W.K. Integrated sensing and communication with massive MIMO: A unified tensor approach for channel and target parameter estimation. IEEE Trans. Wirel. Commun. 2024;23:8571–8587. doi: 10.1109/twc.2024.3351856. [DOI] [Google Scholar]
- 11.Bellili F., Amor S.B., Affes S., Ghrayeb A. Maximum likelihood joint angle and delay estimation from multipath and multicarrier transmissions with application to indoor localization over IEEE 802.11ac radio. IEEE Trans. Mob. Comput. 2018;18:1116–1132. doi: 10.1109/tmc.2018.2854883. [DOI] [Google Scholar]
- 12.Abdelkhalek M., Amor S.B., Affes S. Blind maximum likelihood JADE in multipath environement using importance sampling; Proceedings of the 2019 IEEE 8th International Workshop on Computational Advances in Multi-Sensor Adaptive Processing (CAMSAP); Le Gosier, Guadeloupe. 15–18 December 2019; pp. 391–395. [Google Scholar]
- 13.Abdelkhalek M., Amor S.B., Affes S. Blind ML JADE in multipath environments using differential evolution; Proceedings of the ICC 2022-IEEE International Conference on Communications; Seoul, Republic of Korea. 16–20 May 2022; pp. 1787–1792. [Google Scholar]
- 14.Mahdy A.M.S., Lotfy K., Hassan W., El-Bary A.A. Analytical solution of magneto-photothermal theory during variable thermal conductivity of a semiconductor material due to pulse heat flux and volumetric heat source. Waves Random Complex Media. 2021;31:2040–2057. doi: 10.1080/17455030.2020.1717673. [DOI] [Google Scholar]
- 15.Khamis A.K., Lotfy K., El-Bary A.A., Mahdy A.M., Ahmed M.H. Thermal-piezoelectric problem of a semiconductor medium during photo-thermal excitation. Waves Random Complex Media. 2021;31:2499–2513. doi: 10.1080/17455030.2020.1757784. [DOI] [Google Scholar]
- 16.Zamfirache I.A., Precup R.E., Roman R.C., Petriu E.M. Policy iteration reinforcement learning-based control using a grey wolf optimizer algorithm. Inf. Sci. 2022;585:162–175. doi: 10.1016/j.ins.2021.11.051. [DOI] [Google Scholar]
- 17.Saif F.A., Latip R., Hanapi Z.M., Shafinah K. Multi-objective grey wolf optimizer algorithm for task scheduling in cloud-fog computing. IEEE Access. 2023;11:20635–20646. doi: 10.1109/access.2023.3241240. [DOI] [Google Scholar]
- 18.Rami Reddy M., Ravi Chandra M.L., Venkatramana P., Dilli R. Energy-efficient cluster head selection in wireless sensor networks using an improved grey wolf optimization algorithm. Computers. 2023;12:35. doi: 10.3390/computers12020035. [DOI] [Google Scholar]
- 19.Kumar R., Singh L., Tiwari R. Path planning for the autonomous robots using modified grey wolf optimization approach. J. Intell. Fuzzy Syst. 2021;40:9453–9470. doi: 10.3233/JIFS-201926. [DOI] [Google Scholar]
- 20.Liu X., Li G., Yang H., Zhang N., Wang L., Shao P. Agricultural UAV trajectory planning by incorporating multi-mechanism improved grey wolf optimization algorithm. Expert Syst. Appl. 2023;233:120946. doi: 10.1016/j.eswa.2023.120946. [DOI] [Google Scholar]
- 21.Patil R.A., Kavipriya P., Patil B.P. GWO based optimal channel estimation technique for large scale MIMO in LTE network. Int. J. Innov. Technol. Explor. Eng. 2019;8:5306–5314. doi: 10.35940/ijitee.l3733.1081219. [DOI] [Google Scholar]
- 22.Srinivasa Rao Y., Madhu R. Channel Estimation for Millimeter Wave Massive MIMO System: Proposed Hybrid Optimization with Heuristic-Enabled Precoding and Combining. Comput. J. 2022;65:1211–1224. doi: 10.1093/comjnl/bxaa170. [DOI] [Google Scholar]
- 23.Raghuvanshi A., Sharma A., Gupta M.K. Maximum likelihood direction of arrival estimation using GWO algorithm; Proceedings of the International Conference on Advances in Computing, Communication and Materials (ICACCM); Seoul, Republic of Korea. 16–20 May 2022; pp. 1–5. [Google Scholar]
- 24.Rodríguez L., Castillo O., Soria J., Melin P., Valdez F., Gonzalez C.I., Martinez G.E., Soto J. A fuzzy hierarchical operator in the grey wolf optimizer algorithm. Appl. Soft Comput. 2017;57:315–328. doi: 10.1016/j.asoc.2017.03.048. [DOI] [Google Scholar]
- 25.Wang Q., Wang M., Wang X. Improved grey wolf optimizer with convergence factor and proportional weight. Comput. Eng. Appl. 2019;55:60–65. [Google Scholar]
- 26.Yue Z., Zhang S., Xiao W. A novel hybrid algorithm based on grey wolf optimizer and fireworks algorithm. Sensors. 2020;20:2147. doi: 10.3390/s20072147. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 27.Wang S., Yang X., Wang X., Qian Z. A virtual force algorithm-Lévy-embedded grey wolf optimization algorithm for wireless sensor network coverage optimization. Sensors. 2019;19:2735. doi: 10.3390/s19122735. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 28.Faris H., Aljarah I., Al-Betar M.A., Mirjalili S. Grey wolf optimizer: A review of recent variants and applications. Neural Comput. Appl. 2018;30:413–435. doi: 10.1007/s00521-017-3272-5. [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Data are contained within the article.