Abstract
Due to its vulnerability to a variety of cyber attacks, research on cyber security for power systems has become especially crucial. In order to maintain the safe and stable operation of power systems, it is worthwhile to gain insight into the complex characteristics and behaviors of cyber attacks from the attacker’s perspective. The consensus-based distributed state estimation problem is investigated for power systems subject to collaborative attacks. In order to describe such attack behaviors, the denial of service (DoS) attack model for hybrid remote terminal unit (RTU) and phasor measurement unit (PMU) measurements, and the false data injection (FDI) attack model for neighboring estimation information, are constructed. By integrating these two types of attack models, a different consensus-based distributed estimator is designed to accurately estimate the state of the power system under collaborative attacks. Then, through Lyapunov stability analysis theory, a sufficient condition is provided to ensure that the proposed distributed estimator is stable, and a suitable consensus gain matrix is devised. Finally, to confirm the viability and efficacy of the suggested algorithm, a simulation experiment on an IEEE benchmark 14-bus power system is carried out.
Keywords: power systems, distributed state estimation, collaborative attacks, denial of service attack, false data injection attack
1. Introduction
Due to the requirements of energy conservation and low carbon, modern power systems have incorporated more and more renewable distributed generation, such as distributed photovoltaic generators and decentralized wind power, which inevitably transforms the power system into a complex large-scale system [1,2,3,4]. In order to monitor and control such systems efficiently and flexibly, the supervisory control and data acquisition system needs to be enhanced by utilizing advanced sensing and network technologies, especially the introduction of phasor measurement units (PMUs) and communication networks [5]. Compared with traditional remote terminal units (RTUs), PMUs have the advantage of being able to obtain the magnitude and phase of node voltage at a higher sampling frequency. In addition, by installing a sufficient number of PMUs in power systems, all system states can be observable and easily derived using linear measurement equations. With economic considerations, however, it is not feasible to switch out all of the traditional RTUs with PMUs anytime soon [6]. Consequently, it is important, yet difficult, to investigate power system issues using mixed RTU and PMU measurements.
Since advanced PMUs and communication networks have been widely used in power systems, the dynamic state estimators have been drawing a fast increasing amount of research interest [7,8,9]. In recent years, a large number of dynamic state estimation methods have been proposed, including Kalman filtering [10], robust filtering [11], adaptive filtering [12], etc. In such large-scale complex systems, the dynamic state estimator based on the centralized scheme is computationally burdened by the larger size of states and measurements, making it unsuitable for such systems. Different from the centralized one, the distributed estimation algorithm is more suitable for large-scale power systems due to its advantages in high computational efficiency, low communication burden, and strong robustness [13]. For example, the distributed algorithm based on the weighted least-square issue was proposed in [14,15,16], which was computationally capable of parallel and distributed processing of power system state estimation problems, thus improving the computational burden faced by centralized estimation. In [17], the authors investigated distributed state estimation issues by utilizing Least Absolute Value, improved the computational performance of large-scale power systems, and achieved real-time monitoring. Note that the above algorithms focus mainly on optimizing methods to control events with accuracy and timeliness by minimizing the energy consumption, ignoring the importance of information interaction and calculation in the distributed collaboration process. To compensate for this deficiency, the consensus-based distributed estimation method was proposed in [18,19,20]. The consensus-based distributed estimation algorithm was first designed to handle the distributed filtering problem in sensor networks, which realized the synchronization of estimation information of adjacent nodes by using multi-agent consensus theory and Kalman filter algorithm, also known as the Kalman consensus filter in numerous studies [21,22]. Due to its high reliability and scalability, many variations of consensus-based distributed estimation algorithms have been proposed to deal with various challenges, such as packet loss [23], event-triggered issues [23], and coupled measurements [24]. For large-scale power systems, therefore, investigating the consensus-based distributed estimation algorithm is an important, yet difficult, task.
The distributed nature of modern large-scale power system and the addition of communication networks make it vulnerable to cyber attacks, of which denial of service (DoS) and false data injection (FDI) attacks are the two main categories under which these attacks fall. FDI attacks, as one of the most common types of attacks in power systems, aim to intercept or maliciously change the signal to be transmitted, causing the estimated state to deviate from the actual state of the target [25,26,27], while DoS attacks aim to block the communication channel by frequently sending useless signals, thereby destroying the state estimation process and even making the system unstable in severe cases [28]. Various research results on FDI and DoS attacks for power systems are reported in recent years. For example, the security issue of dynamic state estimations in power systems was explored in [29] when sensors were compromised by completely stealthy FDI attacks. From the attacker’s perspective, the authors of [30] first designed an FDI attack strategy against power system state estimation, and then proposed an attack detection scheme based on deep reinforcement learning. In addition, for power systems subject to consecutive DoS attacks, a modified state estimation algorithm was proposed in [31] to defend against DoS attacks. For power grids vulnerable to time-constrained DoS attacks, the work in [32] discussed how to design robust load frequency control method, and provided a formal condition for stability and performance analysis. It is noted that most existing results focus on a single type of attack. However, with the development of communication and sensor technology, the practical power system is increasingly subject to multiple heterogeneous cyber attacks. Moreover, the distributed state estimation problem is further complicated by the influence of heterogeneous collaborative attacks because different types of attacks are difficult to handle uniformly.
Inspired by the above discussion on power systems, this paper attempts to address the consensus-based distributed estimation issue for power systems subject to heterogeneous collaborative attacks by utilizing mixed RTU and PMU measurements. The following is a summary of the main contributions of this paper:
A distributed estimation algorithm is proposed to deal with the dynamic state estimation problem of power system under FDI and DoS collaborative attacks. The considered collaborative attacks directly act on variables such as voltage, current, and power in the power system, which has stronger practical significance.
Different from [33], which only considered FDI attacks, and [34], which only considered DoS attacks, the designed distributed consensus estimator can still maintain high accuracy under the influence of FDI and DoS collaborative attacks. In addition, considering the actual deployment issues in large-scale power systems, this paper devises the suboptimal distributed estimator through an approximate method, which greatly reduces the computational cost.
This paper theoretically proves that the proposed distributed consensus estimator is stable, as long as the given conditions are satisfied by jointly designing the consensus gain matrix, collaborative attack parameters, and system model parameters.
The following will introduce the structure of the rest of the paper. Section 2 covers system and attack models, and introduces the research objective of the whole paper. Section 3 constructs the power system model based on hybrid RTU and PMU measurements. Section 4 proposes the distributed consensus estimation method under heterogeneous collaborative attacks. Then, Section 5 conducts the stability analysis for the proposed distributed consensus estimator. Finally, Section 6 verifies the effectiveness of the proposed algorithm through simulation experiments, and Section 7 provides the conclusion.
Notations: It is hereby declared that the notations used throughout the paper are completely standard. means the N-dimensional Euclidean space. is the transpose of the vector/matrix A, while the inverse matrix of an invertible matrix A is indicated by . denotes the trace of the matrix B. and are the expectation and probability density function of the random variable C, respectively. is used to define the Gaussian random variable with the mean value and covariance matrix R. represents an m-dimensional column vector, where all elements are 1. represents an m-dimensional column vector, where all elements are 0.
2. Problem Formulation and Preliminaries
2.1. System Description
For the purpose of designing a distributed estimator, this paper consider the following linear discrete-time systems:
| (1) |
| (2) |
where and represent the state variable of the system and the observed variable by the i-th sensor, respectively. is the variable that controls the trend behavior of the state trajectory [35]. A, B, and are the system, input, and measurement matrices, respectively. The system and measurement noise, denoted by the random variables and , respectively, are assumed to be mutually independent, and satisfy and .
We assume that the sensor network topology used to observe the above system is modeled as a fixed undirected graph , which consists of the index set of all sensors and the set of edges . The set containing all neighbors of node i is defined as .
Objectively speaking, distributed power systems have a huge amount of state and measurement data, which causes existing estimators to face severe computational and communication burdens [36]. In terms of that, this paper introduces the same distributed consensus estimator as in [37],
| (3) |
where represents the estimate of for the i-th estimator at time instant k. The matrices and denote the estimator gain and consensus gain to be determined, respectively.
2.2. Attack Model
As everyone knows, there are two groups of communication channels involved in distributed filtering across sensor networks. Measurement information is transmitted from the sensor to the estimator through one channel, which connects the sensor and the local estimator. Among the estimators is the other channel, which is used to exchange local estimation information. It is considered that attackers with the ability to alter the transmitted data on the channel may launch random attacks against either of the channels [38]. Therefore, in this paper, we consider that two groups of communication channels are subject to collaborative attacks by FDI and DoS.
- DoS attack: Assume that the innovation transmitted from the sensor to the estimator is subject to the DoS attack, i.e.,
where denotes the innovation under the DoS attack. The occurrence of DoS attacks is described by the random variable , which satisfies the Bernoulli distribution. Stated differently, indicates that the channel for transmitting innovation is under DoS attack; otherwise, . In addition, the probability density function of is defined as follows:(4)
Here, represents the probability that the transmitted innovation is not attacked, are assumed to be known to estimator designers. - FDI attack: Assume that the estimation information transmitted between nodes is subject to the FDI attack, i.e.,
where represents the estimation information of neighbor nodes transmitted when under FDI attack. is defined as the decision variable of the FDI attacker. That is, if , the attacker will invade the communication channel between nodes i and j at time instant k, and the estimation information transmitted between nodes i and j will be injected with a false signal; otherwise, . The that represents the injected false signal is a random variable that satisfies the Gaussian distribution with . Note that, here, is assumed to be uncorrelated with system and measurement noise.(5)
2.3. Problem Statement
In this section, taking into account the case where communication channels from the sensor to estimator and between estimators are subject to the DoS and FDI attacks, respectively, the distributed consensus estimation algorithm in (3) has been updated as follows:
| (6) |
As can be seen from the discussion above, this paper aims to find a feasible distributed consensus estimation algorithm to accurately estimate the state of the system under FDI and DoS collaborative attacks.
3. Power System Modeling
This paper assumes that the power network functions within quasi-steady states. These steady-state dynamics are generally distinct from the transient ones produced by electromechanical power systems [35]. The power system state considered in this paper is the bus voltage, which is defined as the vector consisting of the real and imaginary parts of all bus voltages, i.e.,
where and denote the vectors of the real and imaginary voltage, respectively.
Additionally, the power system measurement model constructed in this paper mainly consists of two aspects. One is the measurement collected by RTUs, which is defined as
Further, it has
| (7) |
where , , , , and denote the voltage magnitude measurement vector, the real and reactive bus power injections measurement vector, and the real and reactive transmission line power flows measurement vector, respectively. Additionally, , , and are regarded as the bus admittance connected to bus s, the series admittance and the half shunt admittance connecting bus s and bus t, respectively.
Therefore, derived from (7), the RTU measurement equation is summarized as follows:
| (8) |
The other is the measurement collected by PMUs, which is defined as
Further, it has
where
Immediately afterwards, the PMU measurement equation is derived as follows:
| (9) |
In this paper, combining (8) and (9), the following hybrid PMU and RTU measurement model is considered:
| (10) |
where . is the introduced noise variable. Furthermore, the linear power system measurement equation can be generated as follows by applying the same linearization technique as in [36,39],
| (11) |
where , and stands for the current operating point at time instant k. .
In power systems, the development of the local subsystem model is required to achieve distributed state estimation. Following [36,40], this section makes the same assumption, which is as follows:
and it has
| (12) |
4. Distributed Estimation Algorithm
In this section, first let and represent the estimation error of estimator i and cross estimation error covariance matrix between estimators i and j, which are defined as
Considering collaborative attacks, there are
Following that, in order to obtain the optimal state estimate, it will propose a theorem to derive the proper filter gain matrix and error covariance matrix.
Theorem 1.
For the power system, (1) and (12), with N buses and a fixed undirected communication graph , considering the collaborative impact of FDI attacks in (5) and DoS attacks in (4), the optimal filter gain to minimize the estimation error covariance is derived by
where .
Proof of Theorem 1.
Combining Equations (1) and (6) and the above definitions, we can obtain
(13) where
(14) Next, one can obtain the following estimation error covariance iteration equation:
(15) By setting , it can be transformed into
(16) where
It should be noted that the expression represents the overall estimation error for all nodes. Thus, the following optimization problem needs to be solved to obtain the optimal filter gain matrix:
Then, applying matrix calculus operation theory yields, as a result,
(17) where .
With Equation (17) rearranged and , we can naturally obtain
(18) where . This finishes the proof of Theorem 1. □
From Equation (18), in order to compute the optimal filter gain matrix , obtaining cross-covariance matrices beforehand are required, which are generally computationally costly. To compensate for this deficiency, a suboptimal filter gain with is devised, i.e., ignoring the impact of cross-covariance matrices in the filter gain design, to improve the computational burden [41]. In light of this, the distributed consensus estimation algorithm that follows is provided:
| (19) |
Remark 1.
Note that while the calculation complexity can be reduced by the approximations employed in (19), the stability of the proposed distributed estimator remains unaffected. As indicated by simulation results, the introduced error is reasonable. Furthermore, these approximations also help to simplify the structure of the suboptimal method, such that it is consistent with traditional Kalman filter.
5. Stability Analysis
For the proposed suboptimal distributed consensus estimation algorithm in (19), stability analysis is a difficult yet necessary field of research. In order to better carry out this study, the following assumptions and lemmas are proposed.
Assumption A1
([42]). The system matrix A is non-singular.
Assumption A2
([43]). The following inequalities hold for some positive real numbers:
Lemma 1
([44]). There is a random process , as well as real numbers and , that satisfy the following inequalities:
(20)
(21) and the random process is exponentially bounded in mean square, and is bounded with probability one.
Next, the following will present the main results of the stability analysis for the distributed consensus estimator.
Theorem 2.
For the power system, (1) and (12), with N buses and a fixed undirected communication graph , considering the collaborative impact of FDI attacks in (5) and DoS attacks in (4), as well as the suboptimal distributed consensus estimation algorithm proposed in (19), then under Assumptions 1 and 2, and setting the following condition:
where , the estimation error is exponentially bounded in the mean square, and is bounded with the probability one.
Proof of Theorem 2.
In order to make use of Lemma 1, first construct the following augmented estimation error and estimation error covariance for all estimators:
(22)
(23) Combining Equations (22) and (23), design the following Lyapunov function:
(24) With the help of Assumption 2, it can be easily verified that the designed Lyapunov function satisfies the condition defined in inequality (20) in Lemma 1, i.e.,
where and with and .
The next step is to confirm that if the Lyapunov function meets the second condition stated in Inequality (21) in Lemma 1. Towards this end, Equation (24) needs to be further expanded. Substituting Equation (13) into Equation (24) yields
(25) In order to simplify the terms on the right side of Equation (25), we first utilize Assumption 2 to scale the filter gain matrix in (19) to
(26) and the same approximation can be used by
(27) Then, it follows from Equation (19) and Inequality (27) that
(28) Further, Inequality (28) is rearranged into
(29) Thus, the first term of the Lyapunov function expansion in Equation (25) can be scaled as
(30) By defining the consensus gain matrix as , the third and fourth terms of the Lyapunov function expansion in Equation (25) are further arranged into
(31) where . is determined by the following inequality:
with .
In a similar way, the second term of the Lyapunov function expansion in Equation (25) yields
(32) Next, the remaining noise terms in the Lyapunov function expansion is addressed:
(33)
(34) Finally, through the combination of Inequalities (30)–(34), we can draw the conclusion as
(35) By comparing Inequalities (21) and (35), it can be found that the second condition in Lemma 1 satisfies when
(36)
(37) where .
In conclusion, the results confirmed that the estimation error is bounded with probability one and exponentially bounded in mean square, which completes this proof. □
6. Simulation Results
In this section, the IEEE 14-bus power system is introduced as a case study to verify the proposed algorithms. Taking into account the model of distributed power systems akin to [36], the related parameters are listed below:
where with p.u and p.u. The value of u in (1) is given by [36,39].
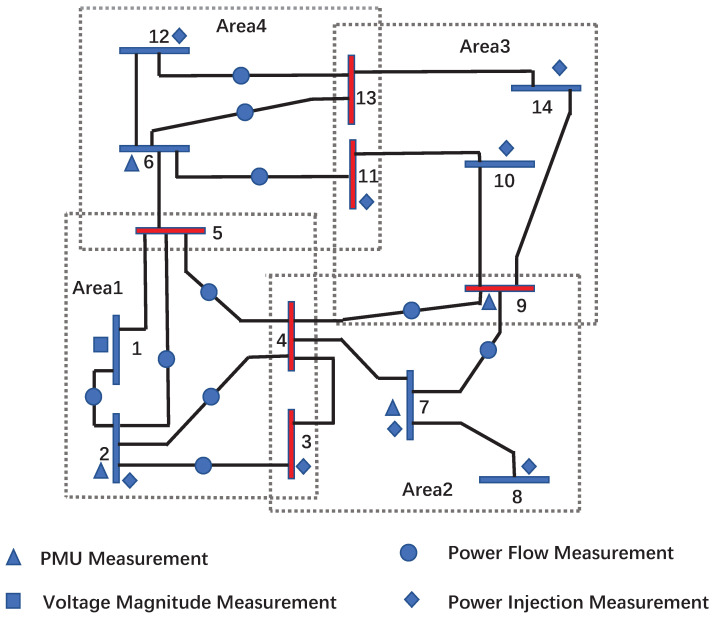
In addition, the measurement configuration of the experimental example comes from [45], which is shown in Figure 1. The measurement system includes both conventional RTUs and advanced PMUs, where RTU measurements are categorized into three different parts as follows:
The voltage magnitude data measured from bus 1;
Power injection data measured from buses 2, 3, 7, 8, 10, 11, 12, and 14;
Power flow data measured between bused 1 and 2, 2 and 3, 4 and 2, 4 and 7, 4 and 9, 5 and 2, 5 and 4, 5 and 6, 6 and 13, 7 and 9, 11 and 6, as well as 12 and 13.
Figure 1.
IEEE 14-bus system partitioned in 4 areas.
Furthermore, PMUs are placed on buses , and 9, allowing measurements of their voltage and current data.
In order to obtain the distributed measurement model described by Equation (12), the IEEE-14 bus power system shown in Figure 1 is divided into four interconnected subsystems.
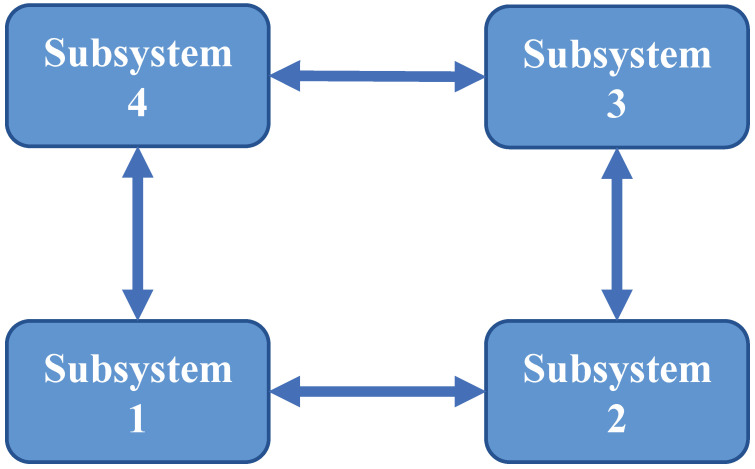
The communication topology of the interconnected subsystems is simplified as shown in Figure 2, where the FDI attack is considered to occur between subsystems 1 and 2, and the DoS attack is considered to occur in all subsystems. In addition, the measurement noise covariances of all subsystems are set to .
Figure 2.
The communication topology of the interconnected subsystems.
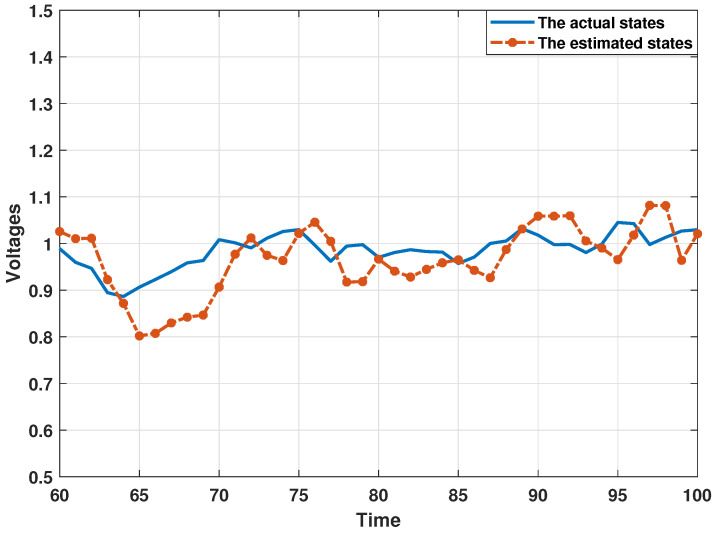
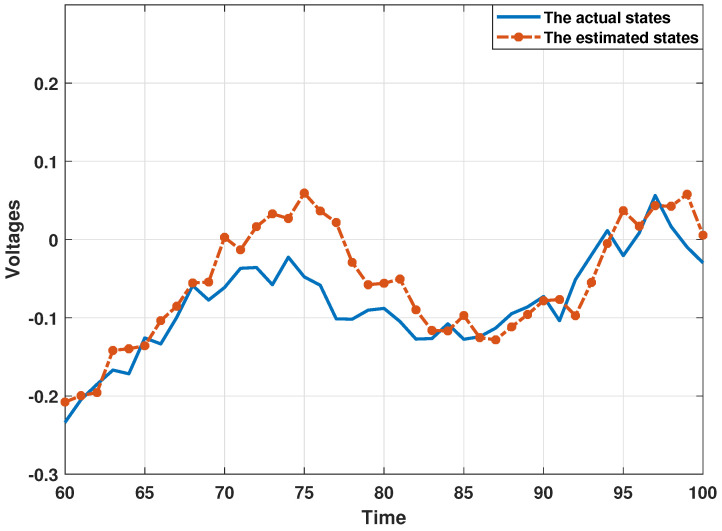
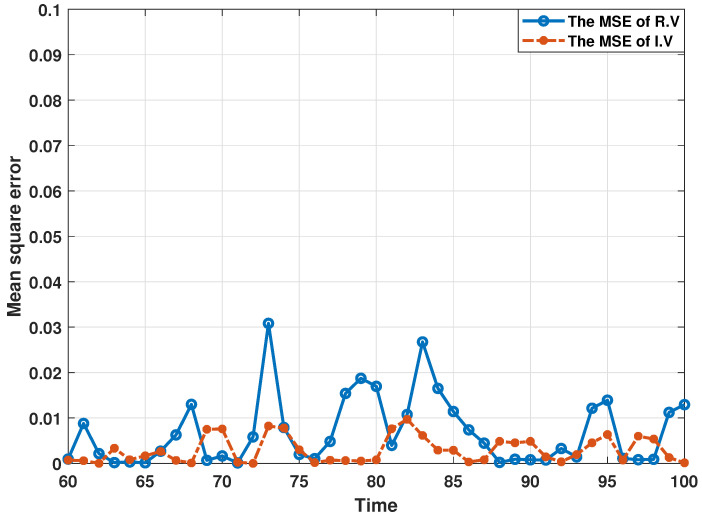
In order to demonstrate the estimation performance of the proposed distributed consensus estimation algorithm, the following experiments are all performed under the influence of collaborative attacks, where the probability that the transmitted innovation is not subject to the DoS attack is set as , and the covariance matrix of the FDI attack variable is set as . Then, this section presents the estimation results in Figure 3 and Figure 4 by using bus 1 as a representative bus. It can be found that the estimates of the real and imaginary parts of the state of bus 1 can track the actual state well, which shows that the proposed distributed estimation algorithm can effectively perform the estimation process under the influence of collaborative attacks. In addition, in order to analyze the estimation performance more thoroughly and eliminate the influence of other factors, this section uses the Monte Carlo simulation method in [36,39] to present the estimation results. In the Monte Carlo simulation method, the mean square error (MSE) is often used to describe the simulation results, which is defined in this paper as with . Here, the MSEs of the estimated real and imaginary parts of states from estimator 1 are shown in Figure 5. It can be seen that all MSEs are kept in a small range, which also illustrates the effectiveness of the proposed distributed estimation algorithm.
Figure 3.
The estimated values from the presented algorithm under collaborative attacks for the real parts of states at bus 1.
Figure 4.
The estimated values from the presented algorithm under collaborative attacks for the imaginary parts of states at bus 1.
Figure 5.
MSEs of the estimated real and imaginary parts of states at bus 1 under collaborative attacks.
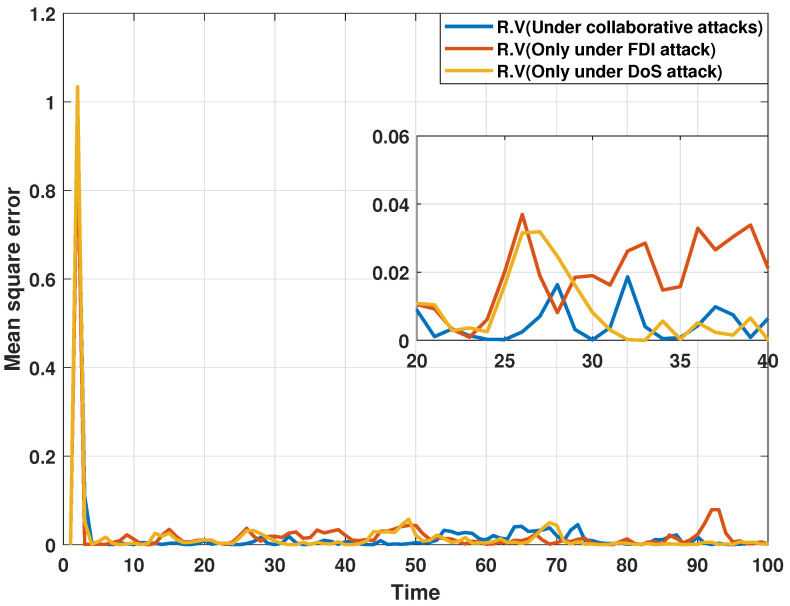
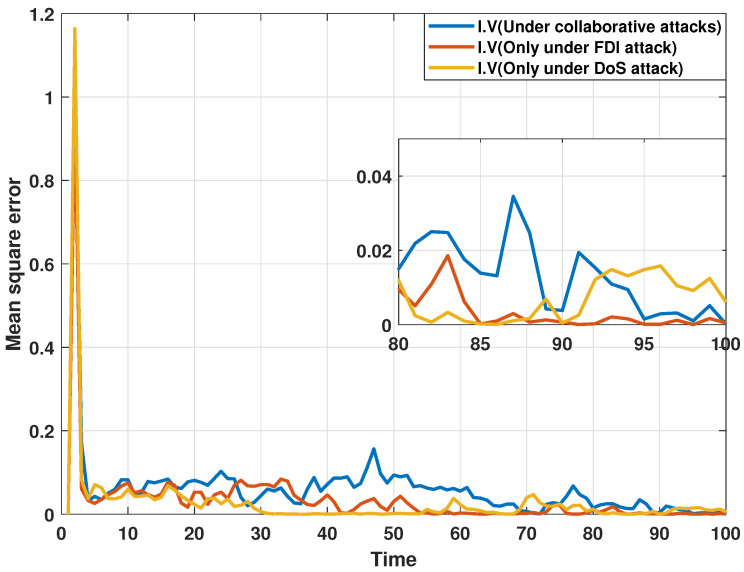
On the other hand, the estimation performance of the proposed distributed consensus estimation algorithm is compared under three attack cases. The first case, from [33], proposed a distributed estimator that is only subject to FDI attacks. The second case, from [34], focuses only on DoS attacks. The last case is from this paper. In order to show the results of the comparison, MSEs of the estimated real and imaginary parts of states at bus 1 under different attack cases are plotted in Figure 6 and Figure 7, respectively. It can be discovered that MSEs does not change significantly under the three different attack scenarios, which shows that the proposed distributed estimation algorithm can maintain the estimation accuracy under a single type of attack while resisting multiple types of collaborative attacks, indicating that the proposed algorithm has high robustness.
Figure 6.
MSEs of the estimated real parts of states at bus 1 under different attack cases.
Figure 7.
MSEs of the estimated imaginary parts of states at bus 1 under different attack cases.
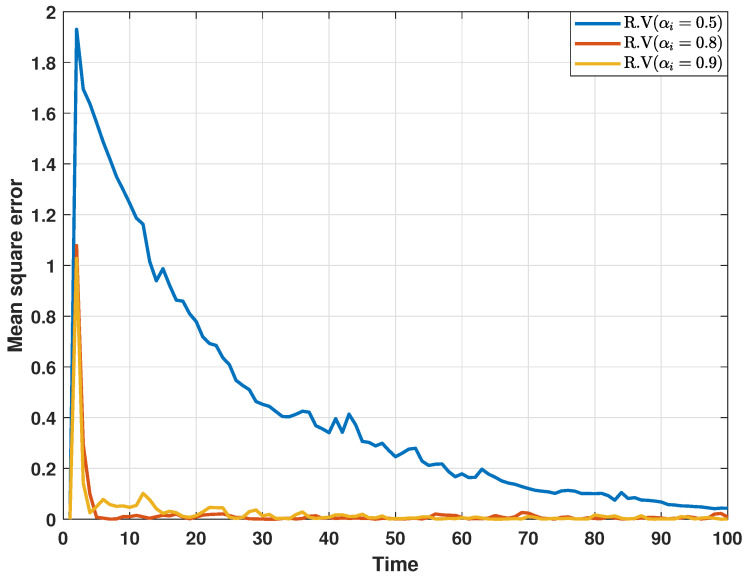
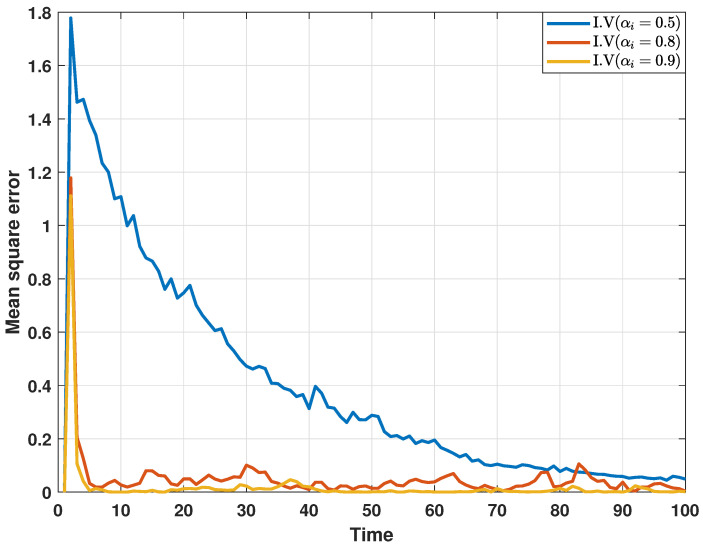
In addition, in order to further analyze the impact of collaborative attacks on the performance of the proposed distributed consensus estimation algorithm, a comparative experiment is performed under different DoS attack probabilities, and the estimation results are depicted in Figure 8 and Figure 9. Here, represents the probability that the transmitted innovation is not attacked.In other words, as the attack probability increases, the estimation performance becomes worse, which confirms that collaborative attacks will cause performance loss to the estimator.
Figure 8.
MSEs of the estimated real parts of states at bus 1 under different DoS attack probabilities.
Figure 9.
MSEs of the estimated imaginary parts of states at bus 1 different DoS attack probabilities.
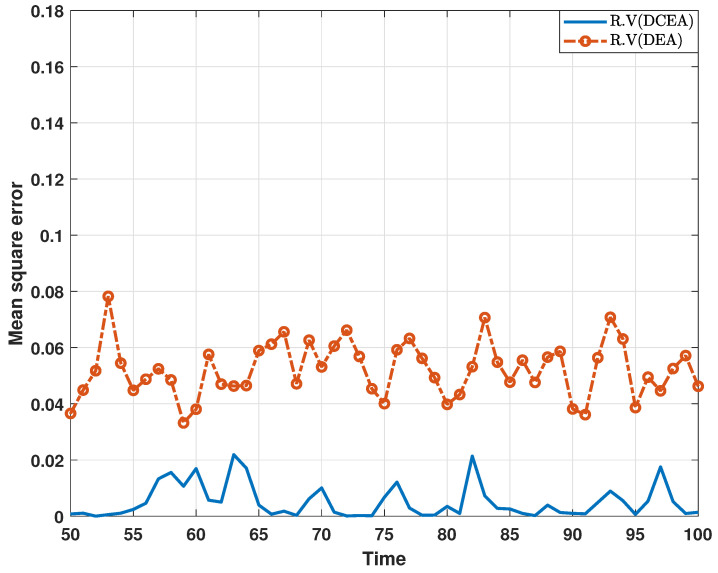
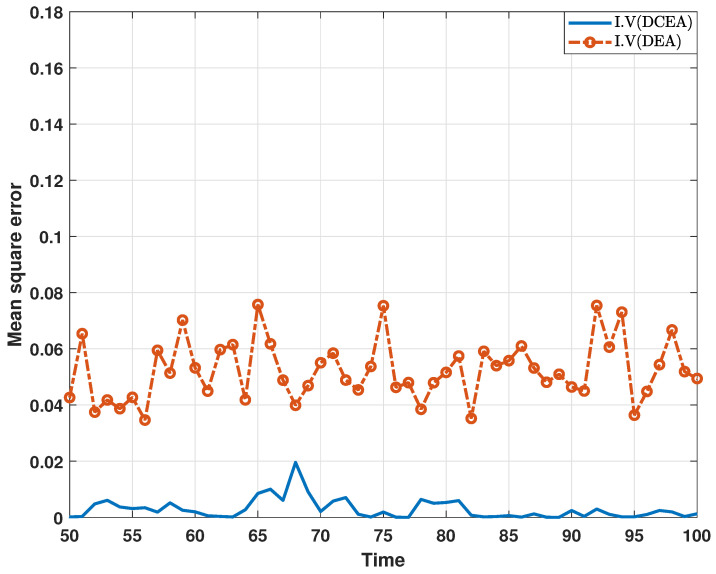
In the following, a comparative experiment on the estimation performance of the proposed algorithm and existing algorithm is performed. In Figure 10 and Figure 11, the comparison results with respect to the MSEs of the estimated real parts of states are depicted, where the distributed consensus estimation algorithm proposed in this paper is referred to as “DCEA”, and is implemented as shown in (19), and the other algorithm is referred to as “DEA”, and is implemented for each node in an isolated way [24]. According to the results, it can be found that the proposed distributed consensus estimation algorithm performs better than the existing algorithm. In particular, the consensus term helps to improve estimation performance when compared to the DEA in [24].
Figure 10.
MSEs of the estimated real parts of states at bus 1 under DCEA and DEA.
Figure 11.
MSEs of the estimated imaginary parts of states at bus 1 under DCEA and DEA.
7. Conclusions
This paper has presented a consensus-based distributed dynamic state estimation algorithm for power systems subject to collaborative attacks. According to the hybrid RTU and PMU measurements, as well as the neighboring estimation, DoS and FDI attack models have been constructed using random variables that satisfy the Gaussian distribution and the Bernoulli distribution, respectively. By incorporating a consensus strategy into the distributed Kalman filter, a distributed consensus estimator has been devised to improve the estimation performance of power systems under collaborative attacks. A suboptimal distributed estimator, as a simplified version of the optimal one, has been proposed to reduce the computational cost. A sufficient condition and a consensus gain matrix have been properly designed to ensure the stability of the proposed estimator. Future works will focus on extending linear multi-sensor systems to nonlinear systems. In addition, extending linear power systems to nonlinear systems will be the main focus of future research. In addition, the redundancy of system observability under sparse sensor attacks in [46] is also a focus of future attention.
Abbreviations
The following abbreviations are used in this manuscript:
| RTU | remote terminal unit |
| PMU | phasor measurement unit |
| FDI | false data injection |
| DoS | denial of service |
| MSE | mean square error |
Author Contributions
Conceptualization, Z.C., G.C. and H.R.; methodology, Z.C.; software, G.C. and X.-M.L.; validation, Z.C., G.C. and X.-M.L.; formal analysis, Z.C.; investigation, Z.C.; resources, X.-M.L.; data curation, H.R. and X.-M.L.; writing—original draft preparation, Z.C.; writing—review and editing, Z.C.; visualization, G.C.; supervision, H.R.; project administration, G.C.; funding acquisition, Z.C., X.-M.L. and H.R. All authors have read and agreed to the published version of the manuscript.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.
Conflicts of Interest
Author Guanjun Chen was employed by the company China State Shipbuilding Corporation Limited. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Funding Statement
This work was partially supported by the National Natural Science Foundation of China under Grants 62303121, 62473100, 62303125, 62373111, U23A20341, and U21A20522, the China Postdoctoral Science Foundation under Grants 2023M740750, and in part by the Guangdong Basic and Applied Basic Research Foundation under Grant 2022A1515110949.
Footnotes
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
References
- 1.Hu L., Wang Z., Liu X., Vasilakos A.V., Alsaadi F.E. Recent advances on state estimation for power grids with unconventional measurements. IET Control Theory Appl. 2017;11:3221–3232. doi: 10.1049/iet-cta.2017.0629. [DOI] [Google Scholar]
- 2.Jin M., Lavaei J., Johansson K.H. Power grid AC-based state estimation: Vulnerability analysis against cyber attacks. IEEE Trans. Autom. Control. 2019;64:1784–1799. doi: 10.1109/TAC.2018.2852774. [DOI] [Google Scholar]
- 3.She X., Ma H., Ren H., Li H. Vision-based adaptive prescribed-time control of UAV for uncooperative target tracking with performance constraint. J. Syst. Sci. Complex. 2024;37:1956–1977. doi: 10.1007/s11424-024-3443-2. [DOI] [Google Scholar]
- 4.Ren H., Liu Z., Liang H., Li H. Pinning-based neural control for multiagent systems with self-regulation intermediate event-triggered method. IEEE Trans. Neural Networks Learn. Syst. 2024 doi: 10.1109/TNNLS.2024.3386881. [DOI] [PubMed] [Google Scholar]
- 5.Cao B., Yan Y., Wang Y., Liu X., Lin J.C.W., Sangaiah A.K., Lv Z. A multi-objective intelligent decision-making method for multistage placement of PMU in power grid enterprises. IEEE Trans. Ind. Inform. 2023;19:7636–7644. doi: 10.1109/TII.2022.3215787. [DOI] [Google Scholar]
- 6.Khalili R., Abur A. PMU-based decoupled state estimation for unsymmetrical power systems. IEEE Trans. Power Syst. 2021;36:5359–5368. doi: 10.1109/TPWRS.2021.3069738. [DOI] [Google Scholar]
- 7.Zhao J., Gómez-Expósito A., Netto M., Mili L., Abur A., Terzija V., Kamwa I., Pal B., Singh A.K., Qi J., et al. Power system dynamic state estimation: Motivations, definitions, methodologies, and future work. IEEE Trans. Power Syst. 2019;34:3188–3198. doi: 10.1109/TPWRS.2019.2894769. [DOI] [Google Scholar]
- 8.Guo H., Cao D., Chen H., Lv C., Wang H., Yang S. Vehicle dynamic state estimation: State of the art schemes and perspectives. IEEE/CAA J. Autom. Sin. 2018;5:418–431. doi: 10.1109/JAS.2017.7510811. [DOI] [Google Scholar]
- 9.Luo A., Zhou Q., Ma H., Li H. Observer-based consensus control for MASs with prescribed constraints via reinforcement learning algorithm. IEEE Trans. Neural Networks Learn. Syst. 2023 doi: 10.1109/TNNLS.2023.3301538. [DOI] [PubMed] [Google Scholar]
- 10.Karimipour H., Dinavahi V. Extended Kalman filter-based parallel dynamic state estimation. IEEE Trans. Smart Grid. 2015;6:1539–1549. doi: 10.1109/TSG.2014.2387169. [DOI] [Google Scholar]
- 11.Zhao J., Netto M., Mili L. A robust iterated extended Kalman filter for power system dynamic state estimation. IEEE Trans. Power Syst. 2017;32:3205–3216. doi: 10.1109/TPWRS.2016.2628344. [DOI] [Google Scholar]
- 12.Akhlaghi S., Zhou N., Huang Z. A multi-step adaptive interpolation approach to mitigating the impact of nonlinearity on dynamic state estimation. IEEE Trans. Smart Grid. 2018;9:3102–3111. doi: 10.1109/TSG.2016.2627339. [DOI] [Google Scholar]
- 13.Chen B., Hu G., Ho D.W., Yu L. Distributed estimation and control for discrete time-varying interconnected systems. IEEE Trans. Autom. Control. 2022;67:2192–2207. doi: 10.1109/TAC.2021.3075198. [DOI] [Google Scholar]
- 14.Zhou X., Liu Z., Guo Y., Zhao C., Huang J., Chen L. Gradient-based multi-area distribution system state estimation. IEEE Trans. Smart Grid. 2020;11:5325–5338. doi: 10.1109/TSG.2020.3003897. [DOI] [Google Scholar]
- 15.Wang J., Li T. Distributed multi-area state estimation for power systems with switching communication graphs. IEEE Trans. Smart Grid. 2021;12:787–797. doi: 10.1109/TSG.2020.3018486. [DOI] [Google Scholar]
- 16.Vargas L., Moyano H. A novel multi-area distribution state estimation approach with nodal redundancy. Energies. 2023;16:4138. doi: 10.3390/en16104138. [DOI] [Google Scholar]
- 17.Yilmaz U.C., Abur A. A robust parallel distributed state estimation for large scale distribution systems. IEEE Trans. Power Syst. 2024;39:4437–4445. doi: 10.1109/TPWRS.2023.3292552. [DOI] [Google Scholar]
- 18.Zhou J., Gu G., Chen X. Distributed Kalman filtering over wireless sensor networks in the presence of data packet drops. IEEE Trans. Autom. Control. 2019;64:1603–1610. doi: 10.1109/TAC.2018.2854644. [DOI] [Google Scholar]
- 19.Yang H., Li H., Xia Y., Li L. Distributed Kalman filtering over sensor networks with transmission delays. IEEE Trans. Cybern. 2021;51:5511–5521. doi: 10.1109/TCYB.2020.2980582. [DOI] [PubMed] [Google Scholar]
- 20.Ren H., Zhang C., Ma H., Li H. Cloud-Based Distributed Group Asynchronous Consensus for Switched Nonlinear Cyber-Physical Systems. IEEE Trans. Ind. Inform. 2024 doi: 10.1109/TII.2024.3457811. [DOI] [Google Scholar]
- 21.Ma Y., Li Y., Wang N., Liang Y. Covariance Intersection-Based Kalman Consensus Filtering with Sequential Replay Attack Detection Over Sensor Networks. IEEE Sensors J. 2024;24:24880–24891. doi: 10.1109/JSEN.2024.3417511. [DOI] [Google Scholar]
- 22.Lian B., Wan Y., Zhang Y., Liu M., Lewis F.L., Chai T. Distributed Kalman consensus filter for estimation with moving targets. IEEE Trans. Cybern. 2022;52:5242–5254. doi: 10.1109/TCYB.2020.3029007. [DOI] [PubMed] [Google Scholar]
- 23.Priel A., Zelazo D. Event-triggered consensus Kalman filtering for time-varying networks and intermittent observations. Int. J. Robust Nonlinear Control. 2023;33:7430–7451. doi: 10.1002/rnc.6762. [DOI] [Google Scholar]
- 24.Li W., Xiong K., Jia Y., Du J. Distributed Kalman filter for multitarget tracking systems with coupled measurements. IEEE Trans. Syst. Man Cybern. Syst. 2021;51:6599–6604. doi: 10.1109/TSMC.2019.2960081. [DOI] [Google Scholar]
- 25.Sui T., Mo Y., Marelli D., Sun X., Fu M. The vulnerability of cyber-physical system under stealthy attacks. IEEE Trans. Autom. Control. 2021;66:637–650. doi: 10.1109/TAC.2020.2987307. [DOI] [Google Scholar]
- 26.Sui T., Sun X.M. The vulnerability of distributed state estimator under stealthy attacks. Automatica. 2021;133:109869. doi: 10.1016/j.automatica.2021.109869. [DOI] [Google Scholar]
- 27.Zhou Q., Ren Q., Ma H., Chen G., Li H. Model-free adaptive control for nonlinear systems under dynamic sparse attacks and measurement disturbances. IEEE Trans. Circuits Syst. I Regul. Pap. 2024;71:4731–4741. doi: 10.1109/TCSI.2024.3434607. [DOI] [Google Scholar]
- 28.Zhao R., Zuo Z., Shi Y., Wang Y., Zhang W. DoS and stealthy deception attacks for switched systems: A cooperative approach. IEEE Trans. Autom. Control. 2024;69:4396–4410. doi: 10.1109/TAC.2023.3321248. [DOI] [Google Scholar]
- 29.Zhang T.Y., Ye D. False data injection attacks with complete stealthiness in cyber–physical systems: A self-generated approach. Automatica. 2020;120:109117. doi: 10.1016/j.automatica.2020.109117. [DOI] [Google Scholar]
- 30.An D., Zhang F., Yang Q., Zhang C. Data integrity attack in dynamic state estimation of smart grid: Attack model and countermeasures. IEEE Trans. Autom. Sci. Eng. 2022;19:1631–1644. doi: 10.1109/TASE.2022.3149764. [DOI] [Google Scholar]
- 31.Li X., Jiang C., Du D., Li W., Fei M., Wu L. A novel state estimation method for smart grid under consecutive denial of service attacks. IEEE Syst. J. 2023;17:513–524. doi: 10.1109/JSYST.2022.3171751. [DOI] [Google Scholar]
- 32.Hu S., Ge X., Li Y., Chen X., Xie X., Yue D. Resilient load frequency control of multi-area power systems under DoS attacks. IEEE Trans. Inf. Forensics Secur. 2023;18:936–947. doi: 10.1109/TIFS.2022.3232961. [DOI] [Google Scholar]
- 33.Zhou J., Yang W., Zhang H., Zheng W.X., Xu Y., Tang Y. Security analysis and defense strategy of distributed filtering under false data injection attacks. Automatica. 2022;138:110151. doi: 10.1016/j.automatica.2021.110151. [DOI] [Google Scholar]
- 34.Sun Y.C., Yang G.H. Event-triggered distributed state estimation for multiagent systems under DoS attacks. IEEE Trans. Cybern. 2022;52:6901–6910. doi: 10.1109/TCYB.2020.3034456. [DOI] [PubMed] [Google Scholar]
- 35.Hu L., Wang Z., Rahman I., Liu X. A constrained optimization approach to dynamic state estimation for power systems including PMU and missing measurements. IEEE Trans. Control Syst. Technol. 2016;24:703–710. doi: 10.1109/TCST.2015.2445852. [DOI] [Google Scholar]
- 36.Cheng Z., Ren H., Zhang B., Lu R. Distributed Kalman filter for large-scale power systems with state inequality constraints. IEEE Trans. Ind. Electron. 2021;68:6238–6247. doi: 10.1109/TIE.2020.2994874. [DOI] [Google Scholar]
- 37.Ren H., Cheng Z., Qin J., Lu R. Deception attacks on event-triggered distributed consensus estimation for nonlinear systems. Automatica. 2023;154:111100. doi: 10.1016/j.automatica.2023.111100. [DOI] [Google Scholar]
- 38.Basit A., Tufail M., Rehan M., Ahmed W., Radwan A., Ahmed I. Event-based secure filtering under two-channel stochastic attacks and switching topologies over wireless sensor networks. IEEE Trans. Netw. Sci. Eng. 2024;11:3704–3717. doi: 10.1109/TNSE.2024.3383280. [DOI] [Google Scholar]
- 39.Cheng Z., Ren H., Qin J., Lu R. Security analysis for dynamic state estimation of power systems with measurement delays. IEEE Trans. Cybern. 2023;53:2087–2096. doi: 10.1109/TCYB.2021.3108884. [DOI] [PubMed] [Google Scholar]
- 40.Hashemipour H.R., Roy S., Laub A.J. Decentralized structures for parallel Kalman filtering. IEEE Trans. Autom. Control. 1988;33:88–94. doi: 10.1109/9.364. [DOI] [Google Scholar]
- 41.Cheng Z., Yang L., Yuan Q., Long Y., Ren H. Distributed Consensus Estimation for Networked Multi-Sensor Systems under Hybrid Attacks and Missing Measurements. Sensors. 2024;24:4071. doi: 10.3390/s24134071. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 42.Battistelli G., Chisci L. Kullback–Leibler average, consensus on probability densities, and distributed state estimation with guaranteed stability. Automatica. 2014;50:707–718. doi: 10.1016/j.automatica.2013.11.042. [DOI] [Google Scholar]
- 43.Liang Y., Li Y., Chen S., Qi G., Sheng A. Event-triggered Kalman consensus filter for sensor networks with intermittent observations. Int. J. Adapt. Control Signal Process. 2021;35:1478–1497. doi: 10.1002/acs.3254. [DOI] [Google Scholar]
- 44.Reif K., Gunther S., Yaz E., Unbehauen R. Stochastic stability of the discrete-time extended Kalman filter. IEEE Trans. Autom. Control. 1999;44:714–728. doi: 10.1109/9.754809. [DOI] [Google Scholar]
- 45.Korres G.N., Manousakis N.M. State estimation and bad data processing for systems including PMU and SCADA measurements. Electr. Power Syst. Res. 2011;81:1514–1524. doi: 10.1016/j.epsr.2011.03.013. [DOI] [Google Scholar]
- 46.An L., Yang G.H. Distributed secure state estimation for cyber–physical systems under sensor attacks. Automatica. 2019;107:526–538. doi: 10.1016/j.automatica.2019.06.019. [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.