Abstract
The dependability of nodes in an Industrial Wireless Sensor Network (IWSN) is vital for precise decision-making and the overall functioning of the network. Unreliable nodes have the potential to result in incorrect data, which can undermine the reliability of monitoring and control systems. Inaccurate decision-making in IWSNs can result in operational failures, safety risks, inadequate resource utilization, elevated energy consumption, and susceptibility to security vulnerabilities. Trust models tackle these challenges by recognizing and reducing the impact of unreliable nodes, improving the precision of data, and strengthening the security of the IWSNs. To overcome these challenges, this research work introduces a “Novel approach for Trust Utilization and Reliability Enhancement” (NATURE) in IWSNs. The unique approach employed in proposed NATURE model is distinguished by its multi-level clustered model, which improves attack mitigation, reduces communication overhead, and enhances overall network efficiency. This model is particularly effective in industrial environments where the network structure and the nature of data traffic are highly dynamic. The use of a multifactor trust estimation framework allows NATURE to assess the trustworthiness of SNs based on a comprehensive set of criteria, including behavior patterns, energy consumption, and communication reliability. By operating on multiple levels, NATURE can dynamically adjust trust functions to accurately distinguish between trustworthy and faulty SNs, thereby improving network reliability. Moreover, NATURE employs the temporal decay factor to prioritize recent node behaviors, ensuring that obsolete actions have minimal impact. Additionally, it uses the dynamic adjustment factor to balance the influence of negative interactions, encouraging reliable and responsive trust evaluations. Additionally, NATURE integrates a dynamically adjustable logical time window to enhance monitoring precision and adaptability, outperforming fixed-length windows in anomaly detection. NATURE integrates an Optimal Lead Node Election Algorithm (OLNEA) to improve cluster leader selection process. OLNEA considers network density, link quality, and Lead Node (LN), battery life, ensuring competent data aggregation and load balancing. By periodically selecting robust LNs and seamlessly switching to alternatives, NATURE promotes reliability and mitigates the impact of low LN battery levels. Additionally, NATURE employs a trust-based attacks detection algorithm to fortify IWSN security. This algorithm employs keen methods to verify data integrity, monitor energy levels, and ensure message authenticity, effectively safeguarding the IWSN from malevolent attacks and ensuring the safe transmission of data. Experimental results highlight NATURE’s exceptional performance across significant metrics when compared to existing trust schemes. In a WSN of 500 SNs with 30% being malicious, NATURE detects malicious behavior with a 97% accuracy, outperforming other models. Even with 50% malicious SNs, NATURE maintains a high detection accuracy of 91%, again surpassing alternative approaches. Additionally, NATURE significantly reduces energy consumption while achieving efficient throughput rates, underscoring its effectiveness in challenging network conditions.
Subject terms: Energy science and technology, Engineering, Mathematics and computing
Introduction
In the swiftly developing landscape of industrial automation and the Internet of Things (IoT), Industrial Wireless Sensor Networks (IWSNs) have emerged as a cornerstone technology1. IWSNs consist of spatially distributed sensor nodes (SNs) that monitor and collect data from industrial processes, providing real-time insights critical for decision-making2. The dependability of these nodes is paramount, as the data they gather directly influences the control and monitoring systems that ensure efficient and safe operations within industrial environments3. However, the reliability of IWSNs is frequently compromised by the presence of unreliable (malicious) SNs, which can lead to inaccurate data and, consequently, flawed decision-making4. This not only undermines the effectiveness of industrial operations but also introduces significant risks, such as operational failures, safety hazards, inefficient resource use, increased energy consumption, and exposure to security threats. These challenges highlight the need for robust trust evaluation mechanisms to ensure the trustworthiness of the data collected by IWSNs5. Trust evaluation models have been developed to address the critical need for reliable data in IWSNs by identifying and mitigating the impact of compromised SNs. These models assess the trustworthiness of each SN based on various factors, such as behavior, energy consumption, and data accuracy, enabling IWSN to mitigate the effects of untrustworthy SNs6. By improving the accuracy of the data used for decision-making, trust models enhance the overall reliability and security of industrial systems7. However, existing trust models8–23 often face significant challenges when applied to resource-constrained IWSNs. The IWSNs operate under harsh limitations in terms of power, computational resources, and communication capabilities. As a result, there is a persistent need for trust evaluation models that are not only effective in identifying unreliable SNs but also efficient in terms of resource utilization24.
The research problem addressed in this paper revolves around the need for a secure, lightweight, and efficient trust evaluation model that can enhance decision-making in resource-constrained IWSNs. Traditional trust models8–10,25–30 often fail to meet the demands of these environments due to their complexity, high computational overhead, or lack of adaptability to dynamic network conditions. These limitations can lead to excessive energy consumption, delayed response times, and reduced accuracy in trust assessments, all of which are unfavorable to the performance and reliability of IWSNs. Moreover, as industrial environments become increasingly complex and interconnected, the need for trust models that can adapt to a wide range of scenarios, including varying levels of network density, dynamic changes in node behavior, and the presence of sophisticated security threats, becomes more critical31. To address these aforesaid challenges, this research introduces a “Novel Approache for Trust Utilization and Reliability Enhancement” referred to as NATURE. NATURE is designed to address the shortcomings of current trust models8–10 by offering a multi-level, multifactor trust evaluation scheme that operates efficiently in resource-constrained environments. The key objective of NATURE is to boost the trustworthiness and security of decision-making processes in IWSNs by providing an accurate, adaptable, and energy-efficient trust evaluation framework.
One of the key innovations in NATURE is its integration of a dynamically adjustable logical time window (LTW) for trust assessments. Traditional fixed-length time windows used in trust models often fail to capture the nuances of SN behavior, either by missing critical events or generating false positives. In contrast, NATURE’s adjustable LTW enhances monitoring precision and adaptability, allowing the model to respond more effectively to changes in network conditions. This feature is particularly important in industrial environments where the timeliness and accuracy of data are crucial for maintaining operational efficiency and safety. Another significant component of NATURE is the Optimal Lead Node Election Algorithm (OLNEA), which optimizes the selection of Lead Nodes (LNs) within the IWSN. LNs play a dynamic role in data aggregation and transmission within IWSNs, and their selection has a direct impression on the IWSN’s performance and energy efficiency. OLNEA considers factors such as network density, link quality, and the battery life of potential LNs, ensuring that the most suitable SNs are chosen for this critical role. By periodically selecting robust LNs and facilitating seamless transitions to alternative LNs when necessary, OLNEA promotes reliability and mitigates the impact of low LN battery levels, thereby extending the overall lifespan of the IWSN. In addition to its advanced trust estimation and LN election mechanisms, NATURE incorporates a trust-driven attack identification algorithm to boost the security of IWSNs. This algorithm employs unique methods to verify data integrity, monitor energy levels, and ensure message authenticity, effectively safeguarding the network against a wide range of security threats. By focusing on both data and node-level security, NATURE ensures that the network remains resilient to attacks that could otherwise compromise the accuracy and reliability of the data used for decision-making. The significance of this study lies in its promising potential to transform the management of trust in resource-constrained IWSNs. NATURE addresses the dual challenges of maintaining high accuracy in trust assessments while minimizing the computational and communication overheads associated with these processes. By offering a model that is both secure and lightweight, NATURE is particularly well-suited for deployment in industrial environments where the cost of network failure is high, and the need for reliable data is paramount. The remainder of this research paper is organized into distinct sections to facilitate thorough examination. “Motivation” SubSection provides the motivation behind the proposed framework and “Key scientific innovations” SubSection provides the simplified key scientific innovations. “Related work” section provides a review of recent related studies, highlighting their advantages and shortcomings. “Problem formulation” section provides the problem statement and “List of assumptions” section provides the list of assumptions used in the proposed work during modeling and simulation. “Proposed method” section describes the proposed methodology, focusing on its novel elements. Theoretical analysis and a discussion of the results are presented in “Theoretical analysis and results discussion” section, which provides insights into the findings. “Conclusion and Future Work” section concludes the paper and suggests possible avenues for future research. This structured format ensures a clear and consistent presentation of the research methodology, analysis, and conclusions.
Motivation
The development of the NATURE method is motivated by the pressing need to address several serious challenges that existing trust evaluation models8–10,26–33 face in IWSNs. In industrial environments, the accuracy and reliability of data are supreme28,29 as they directly influence decision-making processes that ensure operational efficiency30, safety8, and security9. However, traditional trust models often struggle with several issues, including vulnerability to sophisticated attacks such as blackhole, on–off, and whitewashing attacks, which can significantly compromise the integrity of the IWSN31,32. These attacks exploit weaknesses in trust evaluation processes, leading to inaccurate trust assessments and ultimately undermining the reliability of industrial operations34. Furthermore, existing models frequently impose considerable overheads on resource-constrained IWSNs14,15. The high computational and communication costs associated with these models can lead to excessive energy consumption, reduced network lifespan, and delayed response times, all of which are detrimental to the performance of industrial systems35. In addition, many current approaches lack adaptability to dynamic network conditions, making them less effective in environments where node behavior and network topology are constantly changing36. The NATURE method is vital to overcoming these limitations by offering a secure, lightweight, and adaptive trust evaluation framework. NATURE’s multi-level clustered model enhances attack mitigation by accurately distinguishing between trustworthy and malicious SNs, even in highly dynamic and resource-constrained environments. Its efficient trust estimation and OLNEA significantly diminish communication overheads, ensuring energy-efficient operation without compromising accuracy. By addressing both security and resource utilization challenges, NATURE enhances the overall reliability and longevity of IWSNs, making it an essential solution for industrial applications where the stakes are high, and the margin for error is minimal. This method not only mitigates existing vulnerabilities but also sets a new standard for trust evaluation in industrial networks, ensuring robust and reliable decision-making processes.
Key scientific innovations
The NATURE trust model, serves as a robust defender of protection, specifically designed to strengthen IWSNs. With NATURE, significant steps are made in enhancing trust management, heralding a new era of innovation and security in these critical domains. NATURE offers several significant scientific contributions listed as following:
NATURE is a multi-tiered trust assessment framework that functions at both intracluster and intercluster levels and minimizes communication and computational overhead. It employs a dynamic, adaptive trust function that adjusts rewards and penalties according to the behavior of SNs, effectively differentiating between reliable and unreliable SNs.
NATURE incorporate Temporal Decay Factor and the Dynamic Adjustment Factor, significantly enhances trust evaluation in IWSNs. The Temporal Decay Factor exponentially reduces the influence of past interactions, ensuring that recent behaviors more accurately reflect a node’s current reliability. This factor, with its decay rate controlled by δ prevents outdated behaviors from skewing the trust score, thus maintaining its relevance to the node’s present performance. Complementing this, the Dynamic Adjustment Factor modulates the trust score based on recent failures, with η providing a baseline to balance the trust assessment. This factor adjusts the impact of negative interactions, ensuring that trust scores are not excessively penalized by a few adverse events. Together, these mechanisms enable a more responsive and accurate trust evaluation, enhancing network security and efficiency by reflecting the current and realistic behavior of nodes in dynamic environments.
NATURE employs an Optimal Lead node Election Algorithm (OLNEA) that improves lead node selection in IWSNs by considering network density, link quality, and LN battery life, ensuring efficient data aggregation and load balancing. It periodically selects robust lead SNs, promoting reliability by seamlessly switching to alternative LNs and mitigating the impact of low LN battery levels.
NATURE employs a trust-based attacks detection algorithm contributes to making IWSNs more secure by using a unique method to check if data is trustworthy, keep track of energy levels, and ensure messages are genuine. This helps protect the network from attacks, making sure data gets where it needs to go safely. NATURE’s performance is evaluated against existing schemes8–10, showcasing its efficacy in an open environment.
The suggested clustered trust model (NATURE) significantly enhances the security of IWSN data sharing by effectively tackling its distinct difficulties. The system includes both Positive and negative interactions, as well as adaptive penalty and incentive mechanisms, Primary trust (direct trust), and collective trust (feedback trust), in order to guarantee strong protection. This method enhances security by identifying and relying on SNs that consistently participate in secure connections. This limits unauthorized access and security breaches by sharing sensitive data only with reputable SNs. In addition, the proposed method proactively identifies and addresses threats by continuously monitoring unsuccessful interactions. The adaptive and dynamic feature of punishment and reward provides incentives for SNs to engage in secure manner. Individuals SN that involve in responsible information sharing are more likely to gain higher levels of trust, which in turn promotes compliance with security protocols and guarantees the honesty of the IWSN. Meanwhile, SNs that exhibit suspicious activity will be subject to repercussions such as limited access, which serves as a powerful deterrence to potential attackers. Furthermore, the model places a higher importance on interactions with reliable SNs by utilizing direct trust, which is determined by past interactions. This reduces the likelihood of interacting with unreliable SNs, hence enhancing the security of the IWSN.
Related work
This section explores the current trust management scheme (TMS) for IWSNs, providing a thorough comprehension of cutting-edge methodologies. Through an examination of existing literature, this process reveals the positive aspects, limitations, and areas that need further research. This serves as a basis for conducting a thorough comparison and validating the chosen methodology. Examining the current trust management in IWSNs offers significant insights for expanding on prior work, preventing unnecessary duplication, and identifying new research paths.
Saidi et al.8 provide a resilient strategy for selecting secure Lead nodes or cluster heads (CHs) and a technique for identifying misconduct in WSNs. Their technique utilizes a range of measures, with a primary emphasis on assessing the level of trust in SNs. Strategies are created to elect the most dependable SN as CH when dealing with compromised CHs. In addition, a monitoring technique that utilizes various forms of trust assesses the activity of SNs in order to maintain the integrity of the WSN by identifying SNs that are engaging in hostile activities. The experimental results illustrate the efficacy of the method in preventing hostile nodes from becoming lead nodes and protecting against compromised CHs. Kim et al.9 suggest a trust management methodology based on blockchain technology to improve belief and eradicate harmful SNs in WSNs. Their technique combines “behavioral-based trust and data-based trust” to calculate fused trust values of beacon nodes. These values are then transmitted to control station in order to enhance the reliability of localization in WSNs. Simulated findings demonstrate enhanced detection precision and decreased rates of both False Positive (FPR) and False Negative (FNR) compared to current techniques. Anwar et al.10 propose an effective “Belief-based Trust Evaluation Mechanism (BTEM)” for detecting rogue nodes and protecting against attacks. Their approach utilizes Bayesian estimation to collect both direct and indirect trust values of SNs, taking into account the correlation of data over time to ensure secure data transmission. BTEM exhibits higher efficacy in detecting malicious nodes, resulting in reduced latency and improved network throughput when compared to current methodologies.
Smache et al.34 specifically target the vulnerabilities present in time synchronization protocols used in IWSNs. The primary goal is to improve the identification of attacks that specifically target time synchronization, which is a crucial element for ensuring precise communication across dispersed SNs. The methodology entails a comprehensive examination of current attack strategies and the creation of novel detection factors derived from the properties of the MAC layer protocol. This technique seeks to strengthen the resilience of time synchronization by integrating innovative metrics that bolster the ability to identify and defend against advanced threats. The results indicate that the suggested metrics are superior in detecting and reducing severe and practical attacks compared to existing detection methods. Nevertheless, the study also emphasizes the shortcomings in current detection parameters, suggesting that they are inadequate for identifying sophisticated assault techniques. In summary, the study offers significant insights on enhancing time synchronization security in IWSNs by utilizing certain protocol characteristics to enhance attack detection and prevention. Nancy et al.35 presents a new intrusion detection system that is specifically built to detect known and unknown threats by utilizing sophisticated algorithms. The main breakthrough is the dynamic recursive feature selection algorithm (DRFSA), which efficiently chooses pertinent features from datasets to enhance classification accuracy. In addition, the research suggests an improved decision tree approach that incorporates fuzzy temporal constraints and convolutional neural networks (CNNs) in order to enhance detection capabilities. The efficacy of the proposed system was assessed by employing the KDD Cup and network trace datasets, revealing substantial enhancements in intrusion detection system (IDS) accuracy, packet delivery ratio (PDR), and network throughput. The system also exhibited decreases in FPRs, energy usage, and network delays. Subsequent research will prioritize the utilization of intelligent agents for decentralized communication and conducting system testing in actual network environments to further optimize performance. Kavitha et al.37 presents a novel approach called Galactic Swarm Optimization (GSO) that combines CNNs to improve energy efficiency and ensure secure routing in WSNs. The primary goal is to enhance network performance by implementing efficient node clustering and energy-conscious routing. The methodology employs swarm optimization to arrange nodes according to their energy levels and packet delivery performance. The trustworthiness of nodes is assessed in order to determine their involvement in data flows. The method utilizes recurrent convolute learning to replace nodes and initialize swarms, optimizing network operations by taking into account both energy and trust variables. The results indicate substantial enhancements: an 11.94% rise in prediction ratio, a 9.58% decrease in error rate, an 8.84% improvement in accuracy, a 6.05% gain in PDR, and an 11.53% reduction in packet loss, accompanied by an 8.01% decrease in power consumption and a 7.68% reduction in network overhead. The GSO approach is selected for its simplicity, resilience, and computing effectiveness. It employs celestial phenomena to describe node distribution and routing. Future research will prioritize the improvement of node replacements and swarm initialization processes by utilizing CNNs and energy-efficient routing algorithms. Roy et al.38 discusses the significant privacy and security issues that arise with IWSNs, which involve the deployment of nodes in hostile settings and their susceptibility to attacks. Conventional protocols are inadequate in fulfilling crucial privacy and security needs, and current network topologies face challenges in terms of performance due to the rise in traffic and the presence of various SNs. In order to address these constraints, the research suggests a pioneering authentication protocol called SDIWSN, which is based on Software-Defined Networking (SDN). SDN controllers are used to centralize network administration and control, providing a full overview of the network. The SDIWSN system fulfills important confidentiality and safety requirements such as Privacy, non-traceability, reciprocal authentication, key exchange, future confidentiality, and defense against both passive and active threats. Additionally, it presents a velocity-based approach for efficiently identifying cloning assaults. The privacy and safety aspects of the protocol are verified using both formal and informal approaches, while its efficiency is evaluated using performance-based comparisons, showing substantial enhancements compared to current alternatives. Balasundaram et al.39 investigates the use of Multimodal Internet of Things (MMIoT) devices in healthcare to improve emergency response by means of continuous monitoring and data gathering. The primary goal is to address the constraints posed by insufficient knowledge in crucial medical scenarios. In order to accomplish this, the study used MMIoT devices to collect extensive health data, which includes signals and pictures from several body areas simultaneously. The data is analyzed using U-Net and Long Short-Term Memory (LSTM) models. The analysis takes place on a server that is connected to a 5G network, ensuring efficient transmission of data. The utilization of U-Net and LSTM, with the output passed through a dense layer, greatly enhances the precision of health anomaly detection. This system offers prompt and comprehensive patient data, improving the accuracy of diagnoses and the quality of therapy. Nevertheless, the dependence on 5G connectivity and sophisticated models may pose difficulties in regions with inadequate infrastructure or limited technical accessibility.
Aruchamy et al.11 presents an innovative approach to securing IWSNs through an Artificial Intelligence-based model that integrates energy-efficient IDS with secure routing. The key objective is to enhance network security while optimizing energy consumption. The methodology involves a three-phase approach: initially deploying an IDS to identify various types of attacks, then applying a game theory-based decision mechanism to evaluate and implement necessary protection measures, and finally using an energy-aware AODV algorithm to ensure secure routing between SNs. The findings indicate that the projected model significantly improves detection accuracy to 95% and reduces energy consumption by 38% compared to existing systems. This model effectively addresses both security and energy efficiency, though it does not specify the limitations in terms of scalability or adaptability to different network sizes. Abuhasel et al.12 addresses the need for robust security and operational efficiency in Industry 5.0 by introducing a “Zero-Trust Network-based Access Control Scheme (ZTN-ACS)”. This scheme aims to enhance the resilience of industrial operations against adversarial threats through advanced access control and monitoring. The methodology involves using deep learning to manage and verify access to industrial controllers, ensuring that their outputs align with expected production standards. By dynamically adjusting access controls based on real-time verification of production outcomes, the ZTN-ACS significantly reduces controller failures and false positives. The system demonstrates a 12.55% improvement in consistency and an 11.11% reduction in access interruptions compared to existing methods. However, it currently lacks strong support for concurrency in production sequences. Future enhancements could include integrating blockchain technology to address this limitation and further optimize concurrency and storage control. Vazhuthi et al.13 presents an innovative and energy-efficient method for routing between clusters and managing faults in IWSNs. The system aims to advance the Quality of Service (QoS) in IWSNs. The primary goal is to prolong the lifespan of the IWSN while providing dependable communication. The system operates in two primary stages: first, it utilizes the Hybrid Adaptive Neuro-Fuzzy Inference System (ANFIS) Reptile Optimization Algorithm (AROA) to determine the most efficient routing path between clusters and the control station. During the second phase, a Tuned Supervision-based Fault Diagnosis (TSFD) technique is utilized to detect and resolve different types of faults, including detection errors, energy depletion issues, and transmission failures, in order to guarantee the absence of any problems in the pathways. The system underwent evaluation with a total of 1,000 nodes and two distinct sink placements. The performance results demonstrate that the suggested model successfully achieves a substantial decrease in energy usage, surpassing existing routing methods by utilizing 0.01 J less. In addition, the system exhibited enhanced routing efficiency, resulting in network lifespan enhancements of 52%, 38%, and 25% when compared to the LEACH-TM, FPTAC, and MFO-CFO schemes, respectively. The suggested system demonstrated a Detection Accuracy Rate (DAR) of 98%, indicating its potential for real-time applications in ensuring QoS in IWSNs. Nevertheless, the study fails to address the scalability or potential constraints of the approach in various settings.
Sharma et al.16 investigated Multi-Level Hierarchical Secure and Optimal Routing (ML-HSOR) protocol tackles critical issues in IoT-driven environmental monitoring utilizing WSNs. The technique consists of four stages: registration, clustering, authentication, and optimal routing. The registration phase guarantees that the SNs register with the CS, while the clustering stage employs a Markov model with adaptive weighting for optimal CH selection. The authentication phase employs a multi-tiered trust evaluation to identify fraudulent SNs, hence ensuring security. Optimal routing is attained by the Polarity Learning-Based Chimp Optimization Algorithm (PL-COA), which determines data pathways based on node fitness, taking into account energy, distance, network quality, delay, and trust. The protocol achieves a high PDR (99.8% for 500 nodes), substantial throughput (48,000 bits per second), minimal delay (0.058 s), and decreased energy consumption (0.39 Joules). Furthermore, it proficiently identifies fraudulent social networks (95%) via hierarchical trust assessments. ML-HSOR is optimal for prolonged applications in remote locations, providing extended network longevity, little energy usage, and real-time data transmission.
Saidi et al.17 suggested an adaptive trust system that dynamically modifies trust policies in WSNs according to the network’s security status and SN trust values. It implements three policies: zero tolerance for severe malicious activity, standard for moderate threats, and energy-efficient for low-risk scenarios. As attacks escalate, the system enhances trust measurements; conversely, during periods of low threat, it conserves energy by easing trust assessments. This adaptive method attains elevated detection rates—95% under zero-tolerance and 90% for standard and energy-efficient policies—while preserving sensor energy (50% to 95%, contingent on assault severity). The system is assessed against four categories of malicious SNs, surpassing existing models such as HTMS and RARTrust in detection rates while preserving similar energy efficiency. Primary limits encompass restraints on sensor resources, including restricted energy and processing capabilities.
Das et al.18 offer a large-scale energy-aware trust optimization (LS-EATO) approach to tackle the issues in hierarchical WSNs, including unreliable trust management, elevated communication overhead, and imprecise CH selection. The primary aim is to improve security and trust in hierarchical WSN by effectively selecting CHs and identifying rogue SNs. The proposed methodology employs a harmonic search genetic algorithm (HGA) to identify CHs based on criteria such as energy, trust, distance, and density. An energy-aware intra and inter-cluster trust (EAIICT) assessment model is employed for malicious SN detection, utilizing direct trust (communication and data trust) and indirect trust (feedback trust) at both intra-cluster and inter-cluster levels. The trust values are calculated both centrally and distributively, incorporating residual energy to exclude low-energy nodes from being deemed trustworthy. Simulation outcomes in MATLAB indicate that the method decreases communication overhead, enhances detection accuracy, and effectively identifies fraudulent SNs. Nonetheless, the constraint resides in possible scalability issues inside extensive networks. Future research is to investigate machine learning methodologies to provide a risk-aware trust model for intricate and diverse HWSNs and IoT systems.
Komuraiah et al.19 introduce the Multilevel Trust-Based Optimal Stochastic Data Scheduling Model (MTODS) to enhance energy efficiency, security, and network durability in heterogeneous WSNs. The model tackles two fundamental challenges: extending network lifespan and minimizing energy usage, particularly in mobile sensors. The proposed MTODS methodology incorporates a multilevel trust model that enhances energy efficiency via active clustering and beta distribution, with useful stochastic data scheduling employing hybrid particle swarm optimization (hybrid-PSO) to minimize latency. The model, simulated in NS2, was evaluated based on criteria including malicious detection rate, communication cost, data success ratio, packet loss rate, and energy efficiency. The findings indicate that MTODS surpasses prior methodologies such as CDAS-WSN, EEPC-WSN, and TCCS-WSN, attaining superior detection rates, diminished communication overhead, enhanced data success, and augmented energy efficiency. The study investigates performance discrepancies related to the number of SNs and network velocities, demonstrating significant enhancements in throughput and a reduction in packet loss.
Wang et al.20 handle the issue of safeguarding Wireless Weak-link Sensor Networks (WWSNs), which are frequently utilized in harsh situations where communication links are tenuous, rendering them more susceptible to internal attacks. The primary aim of this study is to identify malevolent SNs that could intercept or alter data during transmission between source and destination SNs. The authors offer a dynamic trust management technique that incorporates type-2 fuzzy logic to assess SN trust based on many trust parameters. The adaptive approach for updating trust values enables the system to respond to the variable conditions of WWSNs. Experimental results confirm the efficacy of the proposed strategy, demonstrating its ability to adapt dynamically to environmental changes while preserving high accuracy in detecting fraudulent SNs. The strategy effectively enhances network security by tackling trust management and the dynamic features of WWSNs, however it may be constrained by computational cost in densely populated networks.
Dinesh et al.21 propose a trust-aware neuro-fuzzy clustering and sparrow search optimization algorithm (NF-SSOA) designed to improve energy efficiency and secure data transmission in WSNs. The proposed approach incorporates a neuro-fuzzy clustering algorithm for optimal node aggregation and utilizes the sparrow search optimization method for efficient routing. The projected system incorporates an ECC-based digital signature technique to enable efficient key generation, encryption, and authentication, while ensuring anonymous communication via pseudo-random identity generation. The protocol has four essential modules: node distribution, CH selection, trust-aware routing, and security analysis. Experimental results from the NS3 simulator demonstrate that NF-SSOA markedly improves energy consumption, throughput, network delay, network longevity, and PDR relative to current protocols. Nonetheless, it encounters certain constraints in scalability and flexibility within highly dynamic network settings, potentially affecting performance under fluctuating operational conditions.
Guo et al.22 provide a trust estimation framework designed for federated learning within Dynamic Twin Models Network (DTMN), incorporating both direct trust evidence and recommended trust data. The authors construct a user behavior model that encompasses several attributes, facilitating a detailed examination of user behavior. Trust values are computed according to this concept, employing methods suggested for ascertaining both local and recommended trust levels. Essential elements, including interaction results and temporal decay, as well as behavioral attributes like as stability and reliability, are integrated into the trust computation to improve precision. A method for adaptive weight calculation is introduced to equilibrate local and recommended trust in the computation of global trust. Simulation experiments confirm the efficacy of the suggested approach, illustrating its capacity to appropriately evaluate the trust levels of individuals displaying various behavioral patterns. The approach demonstrates enhanced efficacy in detecting malicious users relative to current leading technologies. Nonetheless, constraints concerning the scalability and flexibility of the method in swiftly evolving situations may necessitate additional examination.
Guo et al.23 confronts the issue of guaranteeing the dependability of information in Vehicular Ad Hoc Networks (VANETs), where vehicles disseminate essential data for safety and improved services. The projected approach is a context-aware trust management model intended to assess the reliability of signals received by cars, thereby averting the influence of incorrect information on driving decisions. The approach evaluates trust by considering pertinent information and contextual factors, reducing the impact of contradictory evidence and differing trust levels among network components. A reinforcement learning approach is introduced, enabling vehicles to adapt their estimating tactics dynamically based on varying driving conditions. Comprehensive studies confirm that the model adapts efficiently to varied situations with no time overhead, preserving good estimation accuracy even in contexts with a significant presence of malicious SNs. This adaptive technique, unlike current trust assessment models that depend on rigid strategies and function effectively primarily in less adversarial environments, utilizes information entropy theory and learns from previous data to enhance decision-making. The findings indicate that the proposed model surpasses three leading trust models, attaining enhanced accuracy without additional overhead, even when the proportion of fraudulent SNs exceeds 50%. Nonetheless, the model’s dependence on historical data may necessitate continuous revisions to ensure precision in swiftly evolving situations.
From the above literature review it is concluded that, IWSNs require strong security measures, efficient energy usage, and dependable communication in order to function effectively, particularly in challenging conditions. Prior research offers different strategies to improve the performance of IWSN, such as implementing secure routing, trust management, fault detection, and access control. Nevertheless, these approaches frequently encounter constraints such as insufficient scalability, excessive energy consumption, subpar detection precision, and difficulties in adjusting to various network conditions. For example, although certain solutions improve trust and decrease false positives, they may not completely meet the requirements for concurrency, adaptability, or energy optimization. While AI-based models and Zero-Trust schemes enhance security measures, they lack scalability and complete fault management capabilities. The NATURE method, which is built on trust, overcomes these constraints by incorporating trust evaluation at many levels, guaranteeing flexible adjustment to network modifications, and sustaining high throughput even in the face of substantial adversarial threats. The integration of NATURE in IWSNs not only improves detection accuracy and energy efficiency, but also enables scalable, flexible, and resilient operations. This innovation is vital in meeting the core requirements of modern industrial networks.
Problem formulation
IWSNs are implemented in industrial locations to observe and gather critical data, which is then utilized for informed decision-making. In order to provide effective monitoring, it is imperative that the SNs engaged in communication with each other possess a high level of trustworthiness. Furthermore, it is crucial for the data being communicated between SNs to be dependable. Regrettably, a significant portion of the work9,10,31–33,36,40 fails to meet essential criteria and lacks the necessary flexibility that is crucial for the survival of IWSNs. The existing trust evaluation methodologies for IWSNs are unsuitable due to the ardous and unsafe environment8, centralized management structure9, and data protection concerns10. This is because the sensed data is pivotal in decision-making in a hostile industrial setting. When evaluating trust, it is important to take into account data trust, as communicating with malicious SNs might lead to data loss and impact the longevity of the sensor network. The trust model must take into account the computational overhead and different types of trust41,42. Additionally, the attention should be on the magnitude and regularity of misbehavior, the categorization of SNs into ideal clusters, and the most suitable architectural design11,39. Additionally, it should include a punitive and incentivizing component that may be adjusted to meet the needs of the system15. The suggested approach, known as NATURE, addresses all the aforementioned restrictions and satisfies all the essential requirements for enhancing both security and network availability.
List of assumptions
Our proposed schemes operate under several foundational assumptions:
Clustering: SNs in the WSN are arranged in clusters utilizing8,30, where each SN within a cluster maintains the ability to exchange information with any other SN. Algorithm 1 (OLNEA) is employed to select resourceful lead nodes (LNs) responsible for managing and coordinating cluster activities. LNs acts as cluster heads, maintain records of SN identities, locations, and updated energy levels of cluster entities (CEs). LNs play a pivotal role in trust calculation, updates, and decision-making within the cluster, forwarding gathered data to the control station (CS) for concluding decisions. The CS acts as a base station, essential, for gathering, processing and communicating data with networks. It acts as an intermediary between LNs and oversees the handling of data from different clusters, guaranteeing effective data transmission, network administration, and overall system reliability.
ID and Location: All SNs possess unique identifiers as well as spatial coordinates (X1, Y1), facilitating identification and communication among SNs.
Homogeneity: SNs are assumed to be uniform regarding their energy levels, queue capacities, processing capabilities, and interfaces. Each interaction is estimated to consume 0.01 J of energy per SN, which facilitates the calculation of residual energy and energy trust values over time.
Trust Domain: Trust values are confined within the domain [0, R], where R = 10, reducing transmission and memory overhead by employing fewer bits for trust value exchange. Using a range of 0 to 10 for trust values is widely regarded as optimal due to its simplicity, granularity, compatibility, efficiency, and ease of implementation7,29. This range provides a straightforward and intuitive scale for representing trust, with higher values indicating greater trust and lower values indicating less trust. Despite its simplicity, it offers enough granularity to capture meaningful distinctions in trust levels, making it suitable for various contexts. Moreover, the range from 0 to 10 is widely recognized and used, facilitating interoperability and communication between different systems. Its balanced approach minimizes memory and transmission overhead while simplifying computations and decision-making processes, resulting in more efficient and user-friendly systems.
Trust Threshold: The trust threshold is set at ⌈(R − 1)/2⌉, representing 50% of the maximum trust value. A SN with a trust score greater than or equal to this threshold is deemed valid.
Observing: A dynamic logical timing window (LTW) is utilized to observe positive and negative interactions within a predefined time unit, updating SN experiences accordingly. Each SN tracks the packet-forwarding activities of its direct neighbors through promiscuous learning.
Mobility: SNs are are considered motionless, non-isolated, and fixed in position.
Misconduct: Misconduct includes actions like packet dropping, data capture, and misleading information dissemination by selfish or congested SNs, aimed at disrupting network functionality and compromising integrity.
Selflessness: The source node, LNs, CS, and destination node are assumed to act altruistically without selfish motivations. Activities may be packet forwarding behaviour, processing, SN location, and SN energy. Each SN maintains a forwarding table that contains periodically updated information about the neighbour SNs. A selfish SN can drop any number of packets. Moreover, it sends false route replies to become an advisable (reasonable) SN for routing traffic. Selfish SNs try to forward data through congested and unreliable routes to increase packet loss. Due to high packet loss, the throughput of the IWSN decreases.
Proposed method
The recommended IWSN is structured into numerous groups12 to ensure the efficient management, processing, and analysis of the significant amounts of data from IWSNs devices. This organization enables dependable and scalable operations, leading to improved decision-making efficiency and effectiveness. The proposed TMS operates on two distinct levels. Level 1 denotes to the level within a cluster, while level 2 refers to the level between clusters. Trust inside a cluster is calculated by utilizing LNs and CEs. During the process of calculating direct trust inside a cluster, all SNs have the ability to communicate with one another in order to exchange data. During the process of calculating indirect trust inside a cluster, LN has the ability to connect with all CEs by transmitting a query message. Inter-cluster level trust is calculated by utilizing the CS and LNs. On each level, NATURE calculates both primary and collective trust in order to enhance the precision of threat detection systems. A LTW is employed to document the positive and negative interactions between SNs15, which includes the LN and CS. During the process of collective trust estimation, the trust of SNs will be computed by LN within clusters and by CS between the distict clusters. We utilize a trust score system to safeguard the IWSN from serious attacks, employing two distinct lists: a valid and invalid list. A valid list is a list of trusted SNs that are permitted to contribute in the IWSN for the purpose of surveillance and traffic management. The invalid list contains the identifiers of malevolent SNs that are prohibited from participating in the network’s data sensing, processing, and transmission activities with other SNs. The belief level of SNs and the entries in the valid and invalid list undergo consistent updates. NATURE incorporates the temporal decay factor to improve trust evaluation by reducing the importance of previous interactions, hence giving more weight to recent activities when judging the reliability of a SN. This modification is essential for upholding trust evaluations that precisely mirror present performance, particularly in dynamic environments such as IWSNs. In addition, NATURE utilizes the dynamic adjustment factor to ensure a fair assessment of the trustworthiness of each SN. This element acts as a moderator for the impact of recent bad interactions, ensuring that occasional failures do not result in excessive penalties, while still maintaining a consistent trust score. Collectively, these processes enhance the adaptability and precision of trust assessments, hence improving overall network security and efficiency. Figure 1 depicts the architecture of the suggested approach, which offers a well-defined and organized way to addressing the research topic. This architecture contributes to maintaining the accuracy and reliability of the research findings. Table 1 shows the list of symbols used in the research work to improve readability.
Fig. 1.
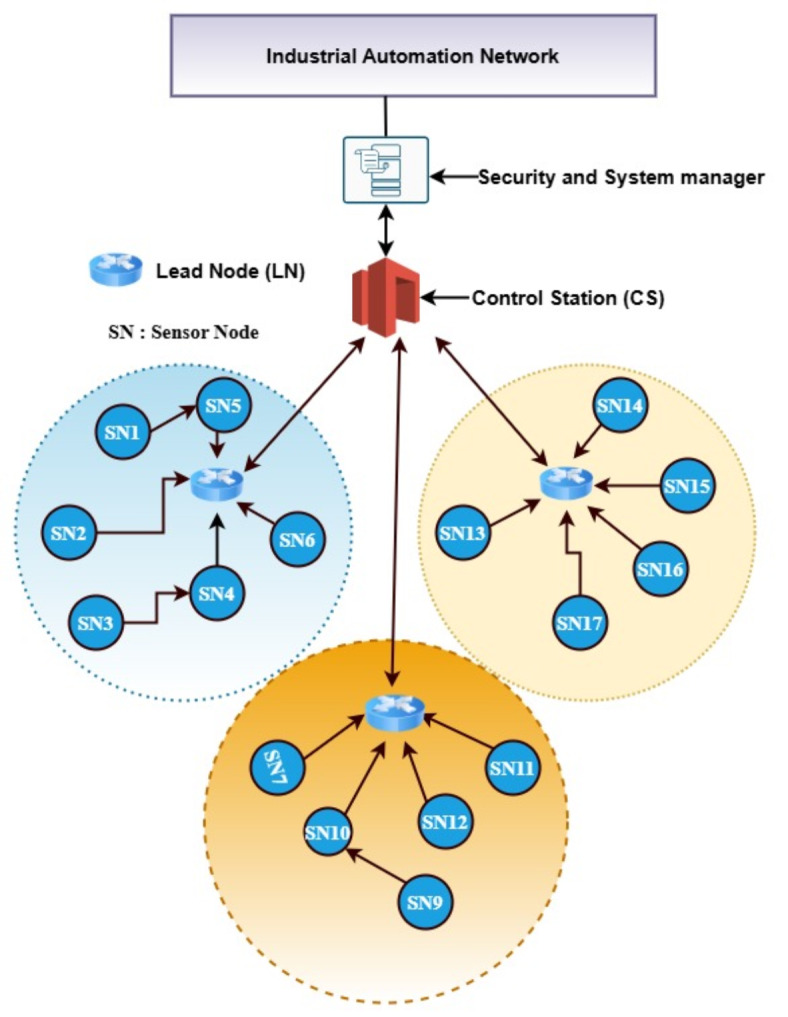
Proposed clustered architecture of IWSN.
Table 1.
Symbols and their description.
| Symbol | Description |
|---|---|
| S | Total Sensor nodes deployed in target area |
| R | Range of Trust value |
| n | Total sensor nodes within a cluster |
| m | Number of clusters |
| d | Distance |
| D | Density |
| RE | Residual energy |
| LN | Lead node or Cluster head |
| CS | Control station |
| Q | Link quality |
 |
Direct Communication trust between SN (x) and SN (y) at time 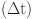
|
 |
Data trust between SN (x) and SN (y) at time 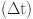
|
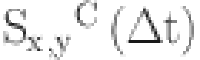 |
Positive interactions between SN(x) and SN(y) |
 |
Negative interactions between SN(x) and SN(y) |
 |
Collective (feedback) communication Trust between SN (x) and SN (y) at time 
|
| Ψ | Tunable penalty coefficient |
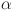 |
Tunable Reward coefficient |
 |
Path loss exponent |
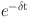 |
Temporal decay factor |
| l1 and l2 | Sliding window length |
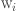 |
Weight assigned |
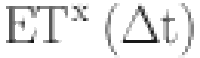 |
Energy Trust of an SN (x) at 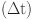 Time Time |
| CEL | Current energy level |
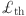 |
Energy threshold |
| P | Positive feedback |
| N | Negative feedback |
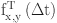 |
Final trust value |
 |
Global trust score between LNs at time 
|
| Etx | Transmission energy |
 |
Reception energy |
 |
Energy consumed per bit for electronics |
 |
Energy consumed per bit for the amplifier |
 |
Length of message (in bits) |
| k | Constant indicating how many communications occur per unit trust |
| Z | Communication rounds |
The Fig. 1 is generated by draw.io, the URL of tool is Untitled Diagram - draw.io (diagrams.net). The NATURE system enables scalability by utilizing a versatile design and implementing efficient resource allocation algorithms. NATURE can effectively handle different network sizes and adjust to environmental changes by utilizing a clustered topology as shown in Fig. 1 and distributed trust evaluation procedures. In addition, NATURE use lightweight communication protocols and improved algorithms to reduce unnecessary data and make the most efficient use of resources. This allows for smooth integration with bigger networks while maintaining high performance. Furthermore, the modular design of NATURE allows for straightforward expansion and integration of extra SNs or clusters as the IWSN expands, guaranteeing expandability while upholding strong and dependable performance in industrial environments. The proposed trust valuation framework is organized into four distinct subsections, detailed as follows.
Attack model
A SN misbehavior-based attack paradigm for internal attacks was described in this subsection. A malicious SN continuously monitors SN behaviors and messages transmitted within the IWSN in the attack model. A malicious SN deliberately manipulates the trust score of other SNs by inaccurately recording more or fewer effective interactions during the interaction. In addition, self-centered SNs attempt to squander network resources and degrade the performance of IWSNs by providing inaccurate feedback about authentic SNs. In addition, self-serving SNs alter their conduct in an attempt to deceive dependable SNs and alter sensitive data. The assault model takes into account the subsequent potential scenarios:
Scenario 1: When the SNs interact frequently and share observed information during the time window. The sender or receiver SN may be an malicious SN capable of injecting false data, dropping sensitive information, modifying the content of sensitive data, or selectively forwarding the data in this scenario. Calculating direct and indirect trust, as described in the proposed trust assessment scheme, can be used to manage this circumstance.
Scenario 2: The SNs exhibit reduced frequency of interaction while maintaining a high trust score. In order to address this circumstance, the indirect trust is computed. When SNs engage in less frequent interactions, it is common for their trust rating to be zero.
Scenario 3: A Sybil SN attempts to mislead the WSN by infiltrating the network. In order to address this circumstance, the positions and allocated IDs of the SNs that are stored in a matrix during deployment are verified. A trust estimation scheme is subsequently implemented to assess the behavior of SNs. The malicious SNs with a trust score below the trust threshold are eliminated by the CS.
Scenario 4: A malevolent SN attempts to exploit the network resources through superfluous bogus data processing or congestion. The energy trust paradigm is capable of handling this scenario. Particularly, energy trust will be crucial in identifying such egocentric SNs.
Optimal lead node election algorithm (OLNEA)
Within this subsection, we present an innovative methodology for lead node selection with the objective of enhancing the process’s efficacy. Our approach differs from current methods, which predominantly depend on distance metrics to select LNs. It considers additional critical factors, including link quality and network density, which are significant for facilitating efficient data aggregation in the direction of the drain. Moreover, whereas current approaches frequently fail to consider challenges associated with LN selfishness caused by inadequate battery capacity, OLNEA provides a comprehensive resolution to this issue. By periodically electing robust LNs, fostering load balancing among LNs, and mitigating the effects of spiteful behavior caused by low LN battery levels, OLNEA is intended to optimize IWSN performance. In light of the critical function that LNs perform in aggregating and transmitting data to the CS, OLNEA guarantees reliability and continuity by smoothly transitioning to alternative LNs in the event that the current one becomes incapable of managing sensitive data. An exhaustive description of the Lead node selection algorithm, denoted as algorithm 1, is provided below.
Algorithm 1.
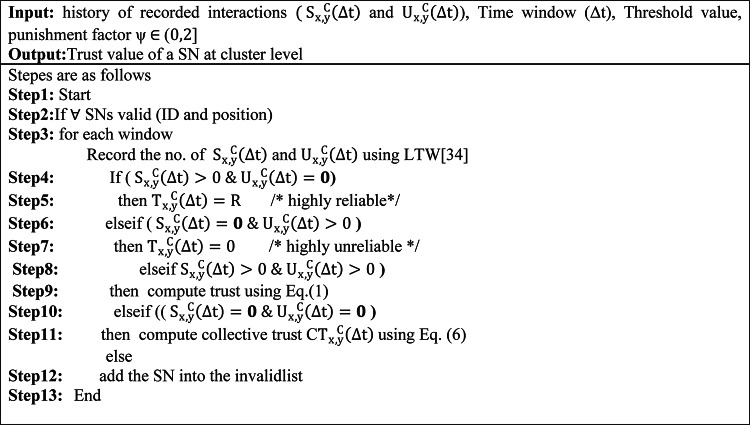
Optimal Lead Node Election Algorithm (OLNEA).
Trust assessment scheme
The trust evaluation proposal incorporates a combination of intracluster and intercluster methodologies. The purpose of intra-cluster trust assessment is to evaluate the dependability and credibility of specific SNs within each cluster, taking into account variables such as the consistency of data reporting and compliance with protocols. On the contrary, intercluster trust evaluation evaluates the reliability of clusters by analyzing their contributions to the network at large and their interactions with one another. This includes assessing the consistency of intercluster communication and the efficacy of collaboration. By integrating these evaluations, a comprehensive assessment of the trustworthiness of SNs and clusters is generated, which empowers informed decision-making with respect to network access control, resource allocation, and data forwarding. The integration of this methodology improves the dependability and protection of clustered IWSNs within industrial environments. As detailed below, the proposed trust evaluation framework is subdivided into numerous subsections. Figure 2 illustrates the flowchart of the Trust model that has been proposed.
Fig. 2.
Flow chart of NATURE.
CE to CE trust estimation
The assessment of primary trust among CE to CE is crucial in IWSNs since it offers quick understanding of the dependability of SNs by considering their previous records in LTW. Implementing this method is essential for improving security since it aids in identifying anomalies and internal attacks, such as data manipulation or unauthorized entry. Primary trust provides the immediate identification and isolation of compromised SNs, resulting in a quicker reaction to attacks and decreasing the possibility for damage. Moreover, it enhances precise decision-making by utilizing past performance data, hence enhancing network efficiency and overall performance. At the cluster level, we consider both “communication trust and data trust”. Equation (1) and Eq. (2) are used to compute communication and data trust, respectively. Computing communication and data trust in IWSNs is critical for making educated decisions. Communication trust evaluates the dependability of data transmission between SNs, assuring the accuracy and timeliness of information sharing. Meanwhile, data trust assesses the credibility and quality of sensed data, preventing malicious tampering or incorrect readings. By adding these trust measures, IWSN decision-making processes can prioritize reliable data sources, optimize resource allocation, and limit the impact of unreliable or compromised SNs, thereby improving network resilience and performance in essential industrial applications.
| 1 |
| 2 |
 denotes the positive and negative interactions between SN(x) and SN(y). Both positive and negative interactions play a crucial role in determining the level of trust among SNs in IWSNs. Positive interactions occur when SNs effectively carry out their assigned responsibilities, follow communication rules, and consistently transfer data. These interactions act as favorable indicators of a node’s dependability, proficiency, and credibility within the network. On the other hand, negative interactions point out situations where SNs vary from expected behavior, do not fulfill their tasks, or show abnormalities such packet loss or unpredictable communication patterns. Examining failed interactions is crucial for detecting internal attacks, weaknesses, or hostile behaviors within the IWSN. Trust evaluation systems can provide detailed insights into the behavior and performance of SNs by thoroughly assessing both positive and negative interactions. This enables more precise and informed trust judgments. This comprehensive method not only improves the dependability and honesty of data transmission but also fortifies the overall security and durability of IWSNs in industrial environments, protecting against possible risks and assuring strong network functionality. The multiplicative factor R is employed to ensure that the trust values remain within the specified trust range. The second term, calculated as
denotes the positive and negative interactions between SN(x) and SN(y). Both positive and negative interactions play a crucial role in determining the level of trust among SNs in IWSNs. Positive interactions occur when SNs effectively carry out their assigned responsibilities, follow communication rules, and consistently transfer data. These interactions act as favorable indicators of a node’s dependability, proficiency, and credibility within the network. On the other hand, negative interactions point out situations where SNs vary from expected behavior, do not fulfill their tasks, or show abnormalities such packet loss or unpredictable communication patterns. Examining failed interactions is crucial for detecting internal attacks, weaknesses, or hostile behaviors within the IWSN. Trust evaluation systems can provide detailed insights into the behavior and performance of SNs by thoroughly assessing both positive and negative interactions. This enables more precise and informed trust judgments. This comprehensive method not only improves the dependability and honesty of data transmission but also fortifies the overall security and durability of IWSNs in industrial environments, protecting against possible risks and assuring strong network functionality. The multiplicative factor R is employed to ensure that the trust values remain within the specified trust range. The second term, calculated as  utilizes the beta distribution function to represent the success ratio at the CE level. The third term,
utilizes the beta distribution function to represent the success ratio at the CE level. The third term, 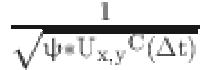 , functions as a penalty for SNs exhibiting misbehavior, with ψ being a tunable penalty coefficient tailored to system requirements. Additionally, the fourth term,
, functions as a penalty for SNs exhibiting misbehavior, with ψ being a tunable penalty coefficient tailored to system requirements. Additionally, the fourth term,  , serves as a reward mechanism, providing incremental rewards based on positive interactions. The fifth term
, serves as a reward mechanism, providing incremental rewards based on positive interactions. The fifth term  represents the Temporal Decay Factor, which exponentially decreases the influence of past interactions over time. Its primary purpose is to ensure that more recent interactions have a greater impact on the trust score than older ones. This factor adjusts the weight of historical behavior based on the elapsed time t, with δ controlling the rate of decay. By applying this decay function, the trust evaluation remains relevant to the current behavior of the SN, reflecting its most recent reliability. This is crucial in dynamic environments like IWSNs, where SN behaviors and network conditions can change rapidly. The importance of
represents the Temporal Decay Factor, which exponentially decreases the influence of past interactions over time. Its primary purpose is to ensure that more recent interactions have a greater impact on the trust score than older ones. This factor adjusts the weight of historical behavior based on the elapsed time t, with δ controlling the rate of decay. By applying this decay function, the trust evaluation remains relevant to the current behavior of the SN, reflecting its most recent reliability. This is crucial in dynamic environments like IWSNs, where SN behaviors and network conditions can change rapidly. The importance of  lies in its ability to prevent outdated or irrelevant past behaviors from disproportionately influencing the trust score, thereby ensuring that the trust assessment accurately represents the SN’s current trustworthiness. This results in a more responsive and accurate trust evaluation, enhancing overall network security and efficiency. The sixth term
lies in its ability to prevent outdated or irrelevant past behaviors from disproportionately influencing the trust score, thereby ensuring that the trust assessment accurately represents the SN’s current trustworthiness. This results in a more responsive and accurate trust evaluation, enhancing overall network security and efficiency. The sixth term 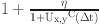 functions as a Dynamic Adjustment Factor that modulates the trust score based on the SN’s recent performance. Here, η is a constant that provides a baseline or minimum value, ensuring that the adjustment is not overly sensitive to variations in the untrusted behavior. The purpose of this factor is to balance the trust assessment by incorporating the effects of recent failures while maintaining a stable trust score. When the number of negative interactions increases, the denominator grows, reducing the impact of these negative experiences on the trust score. Conversely, when the number of negative interactions is low or zero, the adjustment is minimized, and the trust score is influenced more by positive interactions.This factor is critical for ensuring that the trust score reflects both recent negative interactions and the inherent baseline trust level. It prevents trust values from being overly penalized by a few bad interactions and ensures that a SN’s trustworthiness is evaluated in a balanced manner. This term accommodates variations in trust over time, allowing for a more adaptive and realistic assessment. It helps in maintaining trust scores that accurately reflect current network conditions and SN behavior, contributing to a more reliable and resilient network management system.
functions as a Dynamic Adjustment Factor that modulates the trust score based on the SN’s recent performance. Here, η is a constant that provides a baseline or minimum value, ensuring that the adjustment is not overly sensitive to variations in the untrusted behavior. The purpose of this factor is to balance the trust assessment by incorporating the effects of recent failures while maintaining a stable trust score. When the number of negative interactions increases, the denominator grows, reducing the impact of these negative experiences on the trust score. Conversely, when the number of negative interactions is low or zero, the adjustment is minimized, and the trust score is influenced more by positive interactions.This factor is critical for ensuring that the trust score reflects both recent negative interactions and the inherent baseline trust level. It prevents trust values from being overly penalized by a few bad interactions and ensures that a SN’s trustworthiness is evaluated in a balanced manner. This term accommodates variations in trust over time, allowing for a more adaptive and realistic assessment. It helps in maintaining trust scores that accurately reflect current network conditions and SN behavior, contributing to a more reliable and resilient network management system.
The trust evaluation process at the CE level is detailed in Algorithm 2.
Algorithm 2.
Cluster Entities (CE) Level Trust Evaluation.
The dynamically adjustable logical time window (LTW) fluctuates in accordance with the levels of trust attributed to data trust and direct communication trust, thereby indicating whether the actions of the SNs are advantageous or detrimental. The implementation of a dynamically adjustable LTW, which is dependent on the levels of trust associated with direct communication and data trust, offers a significant benefit in comparison to fixed-length windows. Through the dynamic adaptation to fluctuations in trust, the monitoring system attains improved accuracy and flexibility, surpassing the performance of static time windows. This development facilitates a more comprehensive comprehension of network dynamics, thereby enhancing the efficacy of anomaly detection and response mechanisms. In essence, it cultivates a network infrastructure that is robust and adaptable, enabling it to promptly confront emergent threats without compromising operational effectiveness. The sliding window length is determined by Eq. (3), where l1 is greater than l2.
| 3 |
The variables l1 and l2 represent the dynamic sliding lengths when the behaviors of CEs are classified as good and bad, respectively. The term Avg in Eq. (4) denotes the average of direct communication trust and data trust as follows.
| 4 |
LN to CE collective communication trust (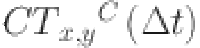 assessment
assessment
The trust estimation of collective (feedback) communication between LNs and CEs is of utmost importance in IWSNs due to following many reasons. Firstly, it improves security by guaranteeing that feedback from LNs is dependable and credible, so aiding in the identification and prevention of malicious activity. Consistent feedback promotes reliability in the network, hence decreasing the likelihood of data corruption and unwanted access. The correctness of the network’s operations plays a crucial role in maintaining its stability and efficiency. It ensures that resources are distributed in a suitable manner and that any possible dangers are swiftly dealt with. Essentially, the robust estimation of trust between LNs and CEs is crucial for ensuring the security, dependability, and operational efficiency of IWSNs.
In the process of collective trust estimation, the LN communicates with CE to collect the direct interaction trust scores of (n − 1) CEs. This is achieved by periodically sending request packets and recording the results in a (n − 1) × (n − 1) matrix, as described by Eq. (5).
 |
5 |
Based on the beta distribution function34, the collective communication trust is assessed using Eq. (6) as detailed below.
| 6 |
Where P and N represent the positive and negative feedbacks, respectively. A feedback is considered positive if the trust score  is greater than or equal to 5, indicating a reliable and favorable interaction. Conversely, if the trust score
is greater than or equal to 5, indicating a reliable and favorable interaction. Conversely, if the trust score 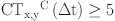 is less than 5, the feedback is deemed negative, reflecting a less reliable or unfavorable interaction. This threshold helps in categorizing feedback, allowing for a clear distinction between trustworthy and untrustworthy interactions, thereby facilitating more informed decision-making based on the quality of feedback received. A threshold value of 5 efficiently distinguishes between dependable and untrustworthy SNs while decreasing the occurrence of incorrect positive identifications. The implementation of this mid-point threshold guarantees that only SNs with a consistently positive track record of interactions are deemed trustworthy. This approach effectively minimizes the potential for malicious behavior while avoiding excessive penalties for SNs with modest changes in trustworthiness. As a result, it improves the precision and dependability of the model in identifying misconduct, while also ensuring that operational efficiency is maintained.
is less than 5, the feedback is deemed negative, reflecting a less reliable or unfavorable interaction. This threshold helps in categorizing feedback, allowing for a clear distinction between trustworthy and untrustworthy interactions, thereby facilitating more informed decision-making based on the quality of feedback received. A threshold value of 5 efficiently distinguishes between dependable and untrustworthy SNs while decreasing the occurrence of incorrect positive identifications. The implementation of this mid-point threshold guarantees that only SNs with a consistently positive track record of interactions are deemed trustworthy. This approach effectively minimizes the potential for malicious behavior while avoiding excessive penalties for SNs with modest changes in trustworthiness. As a result, it improves the precision and dependability of the model in identifying misconduct, while also ensuring that operational efficiency is maintained.
The final trust value, denoted as 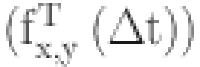 , is calculated by combining the results from Eq. (4) and Eq. (6) using Eq. (7) as follows
, is calculated by combining the results from Eq. (4) and Eq. (6) using Eq. (7) as follows
| 7 |
The energy trust of an SN (x) at  time
time  ) is computed with the help of a predefined threshold value
) is computed with the help of a predefined threshold value  which is 20% of the total energy. If the current energy level (CEL) of an SN (let’s say x) is greater than 50% of total energy, then SN(x) is highly trusted. If
which is 20% of the total energy. If the current energy level (CEL) of an SN (let’s say x) is greater than 50% of total energy, then SN(x) is highly trusted. If  then SN(x) is trusted, else it is non-trusted. In order to ascertain the status of a SN at the CM level, the
then SN(x) is trusted, else it is non-trusted. In order to ascertain the status of a SN at the CM level, the 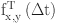 component is applied in accordance with Eq. (8).
component is applied in accordance with Eq. (8).
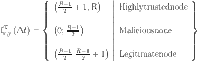 |
8 |
The value of R an be adjusted to meet the particular requirements of the system or application.
LN to LN primary communication trust assessment
In IWSNs, primary communication trust estimation between LNs is essential for maintaining network integrity and efficiency. This trust estimation ensures that interactions between LNs are reliable and secure, which is critical for preventing data tampering and unauthorized access. By evaluating trust directly, IWSNs can more accurately assess the performance and reliability of each LN, enabling timely detection of any misbehavior or malicious activities. This process enhances the overall security of the IWSN by ensuring that only trustworthy LNs participate in critical operations and decision-making. Additionally, primary communication trust estimation supports efficient resource allocation and network management by providing a clear understanding of each LNs performance. This leads to improved decision-making and operational stability, as well as fostering a more resilient and dependable network environment. The primary communication trust between LNi and LNj is defined using Eq. (9) as follows. Each term works in the same way as explain earlier in Eq. (1).
| 9 |
CS to LN collective trust calculation
The CS sends a request packet to m LNs to initiate collective trust evaluation. Upon receiving responses from LNs, the CS calculates the collective trust scores. These trust scores are then systematically organized into a matrix using the formula provided in Eq. (10). This matrix serves as a comprehensive record of the trust levels across the network, facilitating quick access to trust data for future decision-making processes. The method ensures that trust is accurately assessed and maintained throughout the network, enabling the CS to monitor the reliability and performance of each LN. By storing these trust scores in a matrix, the system can efficiently track and analyze the trustworthiness of LNs, which is critical for maintaining network security, optimizing resource allocation, and ensuring that only reliable SNs are involved in key operations.
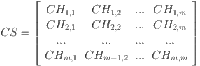 |
10 |
The beta distribution function plays a crucial role in improving the accuracy and reliability of the trust evaluation process. By leveraging this function, Eq. (11) can be effectively used to predict the trustworthiness of collective (feedback) communication. In this context, P represents positive feedback, indicating a successful interaction, while N stands for negative feedback, signaling an unreliable or unsuccessful interaction. The use of the beta distribution allows for a more truthful and nuanced assessment of trust by taking into account the quality and frequency of both positive and negative feedback. This approach ensures that trust predictions are more reflective of actual performance, leading to more reliable and secure communication within the network.
| 11 |
Global trust evaluation, represented by the global trust score  is crucial for ensuring a holistic assessment of trust within the IWSN. This evaluation provides a comprehensive view of each SN’s reliability and behavior over time. It is essential for identifying consistent patterns of trustworthy or untrustworthy behavior, which might not be apparent through local or individual trust assessments alone. This broader perspective helps in detecting potential security threats, ensuring the integrity of the network, and making informed decisions regarding SN participation in critical tasks. Ultimately, global trust evaluation strengthens the overall robustness and dependability of the network. A global trust score
is crucial for ensuring a holistic assessment of trust within the IWSN. This evaluation provides a comprehensive view of each SN’s reliability and behavior over time. It is essential for identifying consistent patterns of trustworthy or untrustworthy behavior, which might not be apparent through local or individual trust assessments alone. This broader perspective helps in detecting potential security threats, ensuring the integrity of the network, and making informed decisions regarding SN participation in critical tasks. Ultimately, global trust evaluation strengthens the overall robustness and dependability of the network. A global trust score  is computed at lead nodes using Eq. (12).
is computed at lead nodes using Eq. (12).
| 12 |
where  are respective weight-age given to primary and collective trust at LN level. Trust-based Attacks Detection Algorithm (Algorithm 3) outlines a organized approach for detecting attacks based on trust metrics.
are respective weight-age given to primary and collective trust at LN level. Trust-based Attacks Detection Algorithm (Algorithm 3) outlines a organized approach for detecting attacks based on trust metrics.
Algorithm 3.

Trust-based Attacks Detection Algorithm.
Energy consumption model
The proposed NATURE trust model employs first-order radio energy model (FOM) widely used in WSNs to analyze and predict the energy consumption of SNs during communication. Integrating the FOM into the proposed NATURE Trust Model improves the understanding of energy efficiency in the context of trust-based management. The FOM divides energy consumption during communication into two primary phases: transmission and reception. The energy consumed by a SN for transmitting and receiving messages can be defined mathematically as follows:
Transmission Energy (Etx): The energy required to transmit a L-bit message over a distance d is given by Eq. (13):
| 13 |
Reception Energy  : The energy required to receive a L-bit message is given by Eq. (14):
: The energy required to receive a L-bit message is given by Eq. (14):
| 14 |
When evaluating trust, SNs may need to transmit and receive data packets for trust assessments and updates. We can define the total energy consumption during trust evaluations by Eq. (15) as follows:
| 15 |
where  represents the energy consumed per bit for electronics, measured in joules per bit. This value reflects the energy required by the electronic components within a SN to process and transmit data. Additionally,
represents the energy consumed per bit for electronics, measured in joules per bit. This value reflects the energy required by the electronic components within a SN to process and transmit data. Additionally,  denotes the energy consumed per bit for the amplifier, which is also measured in joules per bit per meter, indicating the energy needed to amplify the signal during transmission over a distance. The distance (d) to the destination node measured in meters, which directly influences the energy expenses during communication. Lastly,
denotes the energy consumed per bit for the amplifier, which is also measured in joules per bit per meter, indicating the energy needed to amplify the signal during transmission over a distance. The distance (d) to the destination node measured in meters, which directly influences the energy expenses during communication. Lastly, 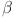 is the path loss exponent typically takes a value of 2 for free-space scenarios and 4 for indoor environments, characterizing how signal strength diminishes over distance due to environmental factors. Together, these parameters provide a comprehensive understanding of the energy dynamics involved in data transmission within WSNs. The NATURE model uses adaptive trust evaluation mechanisms, where the trust score affects the communication behavior of SNs. Nodes with higher trust scores are likely to engage in more communication, thus impacting their energy consumption. Assume that the trust score T influences the number of interactions (or communication rounds) Z: then Z = k⋅T Where k is a constant indicating how many communications occur per unit trust. Thus, the total energy consumption due to trust-based interactions can be expressed using Eq. (16):
is the path loss exponent typically takes a value of 2 for free-space scenarios and 4 for indoor environments, characterizing how signal strength diminishes over distance due to environmental factors. Together, these parameters provide a comprehensive understanding of the energy dynamics involved in data transmission within WSNs. The NATURE model uses adaptive trust evaluation mechanisms, where the trust score affects the communication behavior of SNs. Nodes with higher trust scores are likely to engage in more communication, thus impacting their energy consumption. Assume that the trust score T influences the number of interactions (or communication rounds) Z: then Z = k⋅T Where k is a constant indicating how many communications occur per unit trust. Thus, the total energy consumption due to trust-based interactions can be expressed using Eq. (16):
| 16 |
The FOM effectively models energy consumption in the NATURE Model by providing a mathematical framework to quantify the impact of trust-based interactions on energy efficiency. By systematically incorporating energy consumption metrics into trust evaluations, the model demonstrates how trust management can influence network longevity and operational effectiveness in IWSNs. This integration ensures that energy-efficient strategies are aligned with robust trust management, ultimately leading to improved network performance and security.
Theoretical analysis and results discussion
This section is organized into two key parts: theoretical investigation and assessment, and simulation results discussion. The second part focuses on discussing the results obtained from simulations, offering insights into the practical performance and effectiveness of NATURE in various scenarios. Together, these sections provide a comprehensive understanding of the protocol’s strengths, both in theory and through practical application.
Theoretical investigation and assessment
In this section, we establish the robustness of the NATURE protocol against internal threats using mathematical and analytical evidence. This entails a thorough analysis of the protocol’s architecture and functionality, emphasizing how it successfully reduces possible risks originating from within the network. Through the utilization of a comprehensive mathematical methodology, we establish a robust basis that substantiates the security assertions of NATURE.
Definition 1.
Normal node: A node is considered normal if it successfully interacts with another node for at least the threshold number of transactions and provides a genuine, unaltered recommendation.
Definition 2.
malicious node: A malicious node is one that consistently engages in unsuccessful interactions and attempts various attacks, such as badmouthing, Sybil attacks, ballot stuffing, and on–off attacks.
Meanwhile, . Let
. Let  , for simplicity
, for simplicity 
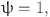

Given  and
and 
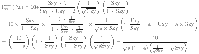 |
As  and
and  so,
so,
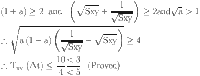 |
Theorem 1.
NATURE trust model is robust against internal atatcks i.e. no malicious node can deceive other node.
Proof.
If a malevolent SN  successfully deceive SN
successfully deceive SN  then
then  and
and 
The three different cases are as follows:
-
i.
If
 , where
, where  ,
,  has interacted with
has interacted with  within
within 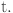
Given that
 we can derive
we can derive  . Hence given that
. Hence given that 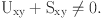
-
ii.

-
iii.If
 , we consider
, we consider  then,
then,
Other two condition of
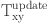 has been considered as special where
has been considered as special where  and
and  and
and  ,
, 
Thus, Theorem 1 validates that the NATURE protocol offers robust protection against malicious attacks.
Communication overhead analysis
In this scenario, we assume the worst case where the maximum number of SNs participate in communication during the trust evaluation process, as outlined in the proposed model. This includes communication between cluster entities (CEs), as well as between cluster entities and lead nodes (LNs). Let’s define the total number of SNs in the IWSN as S, and the number of clusters or LNs as m. The size n of each cluster, including its lead node, can be expressed using Eq. (17):
| 17 |
The communication overhead is divided into two parts: intra-cluster and inter-cluster communication overhead. For intra-cluster trust evaluation, a SN(x) sends and receives a single request to or from the LN to interact with another SN(y), resulting in a total of two request packets for the communication. In the worst-case scenario, where SN(x) interacts with all other (n − 2) SNs, the total communication overhead would involve 2(n − 2) request packets. If all the CEs (excluding the LN) interact with each other, the communication overhead reaches a maximum of 2(n − 2)(n − 1).
During the trust evaluation via feedback within the cluster, the LN sends r requests to its trusted members and receives r responses, where r ≤ n − 1. The resulting communication overhead, due to these feedback exchanges, is 2r request and response packets. Therefore, the total intra-cluster communication overhead is represented by the Eq. (18) as follows
| 18 |
For inter-cluster trust evaluation, the lead node LN(i) sends and receives one request to interact with another lead node LN(j), resulting in two request packets. In the worst case, if LN(i) needs to interact with all the other (g − 1) LNs, the total communication overhead becomes 2(g − 1)request packets. If all the LNs interact with each other, the overhead is maximized at 2 g(g − 1). Additionally, during the trust evaluation from the control station (CS) to the LNs, the CS sends g requests and receives g responses, leading to a total communication overhead of 2 g packets. Thus, the inter-cluster communication overhead can be described by Eq. (19) as follows
| 19 |
Therefore, In the worst-case scenario, the total communication overhead Cmax for the proposed model is given by Eq. (20) as follows
| 20 |
If we consider an average case where only 50% of the CEs are directly trusted (i.e., peer-to-peer trusted), the value of r becomes n − 1/2. Substituting this value into Eq. (20), we get the Eq. (21) for the average communication overhead as follows
| 21 |
In this study, "direct trust nodes" refer to those SNs with a trust value of 5 or higher during direct trust evaluations between CEs. In a realistic scenario, it is unlikely that all CEs would be directly trusted, just as it is unlikely for all CEs to be malicious. Therefore, the average case analysis, where 50% to 70% of SNs are directly trusted and the rest may be malicious, provides a more practical view of the suggested system.
Simulation results
To thoroughly measure the effectiveness NATURE approach, A sequence of experiments was performed utilizing MATLAB Simulink. These experiments tested different scenarios by varying parameters such as S, n, M, and m, and were repeated over 500 iterations. Misbehavior assessments were systematically performed at 100-iteration intervals. The results strongly indicate that the NATURE system is highly resilient to internal attacks, validating its robustness through simulation. A detailed comparative analysis was also undertaken, positioning NATURE against other established methods, including those by Saidi et al.8, Kim et al.9, and Anwar et al.10. This analysis focused on critical metrics such as malicious detection rates, average energy consumption, and throughput. Malicious detection rates refer to the percentage of successfully identified and mitigated malicious activities within the network, indicating the protocol’s effectiveness in recognizing and addressing security threats. This metric is typically computed by dividing the number of detected malicious SNs by the total number of malicious SNs present in the network. Average energy consumption measures the mean energy expended by SNs during network operations, reflecting the protocol’s efficiency in resource management. It is calculated by summing the energy consumed by all SNs and dividing by the total number of SNs over a specified period. Throughput represents the amount of data successfully transmitted from source to destination within a given timeframe, highlighting the network’s data handling capacity. It is usually computed by dividing the total number of successfully delivered packets by the total time taken for transmission. Together, these metrics provide a comprehensive assessment of a protocol’s security, efficiency, and overall performance in a WSN.
Compared to its counterparts, NATURE demonstrated superior performance, particularly in addressing internal challenges, reducing computational overhead, and adapting to dynamic network conditions. The trust model was tested under various scenarios, assessing both normal and malicious behaviors across the network’s lifetime. Table 2 details the simulation parameters, chosen to ensure a comprehensive performance analysis. Although the parameters were rigorously validated, they can be adjusted to meet specific application requirements. For instance, in military applications, increasing Ψ can enhance information reliability. The analysis emphasizes the impact of success rates on trust levels, with higher rates boosting trust and attacks leading to lower scores. NATURE effectively identifies and isolates non-cooperative SNs by calculating trust at both the CE and LN levels.
Table 2.
Simulation parameters.
| IWSN size | 100*100 m2 |
| IWSN topology | Random/Clustered |
| Node deployment | Fixed |
| Number of control stations | 1 |
| Range of deployed IWSN nodes (S) | 100–500 |
| Sybil ID’s | 2–7 |
| Number of rounds | 100 |
| malicious IWSN nodes (M) | 1–5 |
| No. of Lead nodes (m) | 2–7 |
| Position of the sink | (50, 50) |
| Optimal number of clusters (m) | 2–7 |
| Each simulation iteration | 100 |
| Minimum length of sliding window | (2, 5) |
| Cluster size (n) | 30 nodes |
| Initial energy of SN | 4 J |
| Packet size | 512 byte |
| Transmission range | 30 m |
| Range of trust values | [0 R] |
| Maximum trust value (R) | 10 |
| Buffer size | 30 packets |
| Weight assignment strategy | equal |
Punishment coefficient ( ) ) |
[1,2] |
Reward  ) ) |
[1,2] |
 |
160 nJ/bit |
 |
10pJ/bit/m4 |
The several internal attacks are performed during experiment as follows:
Resilience against ballot-stuffing attacks: Ballot-stuffing attacks are a potential danger as they deliberately increase the trust values of malevolent SNs, which might disrupt the network. At first, we create a network scenario by simulating it with specific characteristics, like the size of the area, its initial energy, and the number of SNs. Trust evaluation is determined through interactions between SNs, where trust values are proclaimed randomly and malicious SNs are identified. Every run record both successful and unsuccessful interactions, while also updating trust dynamics and transaction history. The detection of ballot-stuffing attacks requires a careful examination of trust values, identifying SNs that have unusually high reputations as suspicious. Simulation scenarios manipulate trust levels to detect both bad-mouthing and good-mouthing attacks, which is essential for consecutively spotting ballot-stuffing attacks.
Resilience against whitewashing attacks: Whitewashing attacks, similar to bad-mouthing attacks, occur when malevolent SNs attempt to discredit reputable SNs. Our trust approach identifies and counters such attacks by observing patterns of interaction and swiftly eliminating dishonest feedback. SNs engaging in Whitewashing assaults are promptly detected as a result of their low trust scores, hence guaranteeing the integrity of the network. Simulation configurations exclude malicious SNs and keep track of SN ratings, making it easier to identify Whitewashing attackers. Distinct SN identities facilitate effective monitoring, guaranteeing swift recognition and elimination of malevolent individuals.
Resilience against on–off attacks: In the context of network security, on–off assaults refer to a strategy employed by malicious SNs where they alternate between cooperative and disruptive activities in order to avoid being detected. NATURE’s system incorporates a policy that considers SN behavior, discouraging malicious individuals who want to undermine confidence. Simulation sets initiate settings and monitor interactions between SNs, identifying SNs that exhibit recurring adverse behavior. On–off attackers leverage the process of trust accumulation to carry out abrupt attacks, however, our system consistently imposes penalties on SNs that engage in malicious behavior, hence hindering the restoration of confidence. NATURE improves its ability to identify on–off attacks and prevent rogue SNs from evading detection by incorporating weight and penalty variables into its trust computation process.
Figure 3 shows how the level of success influences trust levels, in scenarios with and without attacks. When there are no attacks higher success rates lead to trust values because consistent positive outcomes help build faith in the SNs reliability. On the hand when attacks occur the success rate declines due to the nature of malicious activities. This leads to decreased trust values as the system adapts to the compromised reliability and performance caused by these attacks. The figure effectively illustrates how attacks erode trust and emphasizes the systems vulnerability, to behavior by showcasing the varying levels of trust under circumstances.
Fig. 3.

Effect of success rate on trust values.
Figure 4 illustrates the influence of malevolent SNs on the detection rates of different models, including those suggested by8–10 and the NATURE trust model. The image illustrates that the NATURE model outperforms the models mentioned in references8,9, and10 in terms of detecting malicious behavior, even when up to 50% of the SNs in the network are malicious. The exceptional performance of NATURE is due to its methodical documentation of both regular and harmful actions within a specific timeframe. This approach enables NATURE to enhance its ability to monitor and detect malicious activity over a period of time. Incorporating data trust into its evaluation procedure, NATURE strengthens its capability to evaluate the reliability of data transmission in Industrial IWSNs. According to the figure, when 50% of malicious SNs are present, the detection rates are 80% for8, 82% for9, 85% for10, and 90% for NATURE. This unequivocally demonstrates that NATURE not only surpasses the other models in detecting fraudulent conduct but also offers a more resilient and dependable trust evaluation framework. Figure 5 demonstrates the correlation between the accuracy of detection and the existence of malicious SNs in a network consisting of 500 SNs. The findings indicate that the NATURE model consistently attains superior detection accuracy in comparison to the approaches suggested in8,9, and10, even when the proportion of malevolent SNs escalates. When the proportion of malicious SNs is as low as 5%, all models, including8–10, and NATURE, achieve a high level of accuracy in detecting them. Specifically,8 reports 100% accuracy,9 reports 96% accuracy, and both10 and NATURE report 100% accuracy. When the percentage of malicious SNs increases to 15%, the accuracy of detection declines for all models. However, NATURE still maintains the best accuracy at 98%, compared to 97% for8, 92% for9, and 94% for10. The detection accuracy of8–10, and NATURE is 94%, 82%, 87%, and 95%, respectively, with 30% of the SNs being malicious. The pattern persists with 50% of the SNs being harmful. The accuracy of detecting these hostile networks is 90% for8, 70% for9, 80% for10, and 91% for NATURE. The results indicate that NATURE exhibits superior accuracy in detecting harmful activity and also demonstrates better adaptability to escalating levels of malicious behavior. Therefore, NATURE is a more dependable choice for ensuring network security.
Fig. 4.

Selfish nodes vs. detection rate.
Fig. 5.

Selfish nodes vs. detection accuracy.
Figure 6 exhibits the mean power usage of the NATURE model in comparison to the method suggested in9 in a network containing up to 50% of malicious SNs. It is worth mentioning that the models presented in references8 and10 do not take into consideration energy consumption in hostile circumstances. Therefore, their findings are not included in the comparison.
Fig. 6.
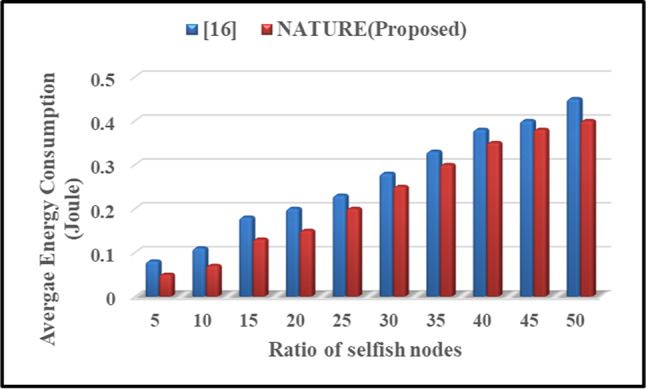
Selfish nodes vs. average energy consumption.
The results indicate that NATURE has a reduced average energy consumption compared to the model in9. The efficiency is attained by employing a clustered topology that reduces superfluous transactions and communication costs. In addition, the NATURE model guarantees that only reliable SNs process and send data, hence minimizing energy consumption caused by dealing with fraudulent packets generated by hostile SNs. Within a network with a maximum of 50% malicious SNs, the average energy usage for9 and NATURE is 0.264 J and 0.228 J, respectively. The decrease in energy consumption demonstrates the efficiency of NATURE in preserving power while ensuring network performance and security.
Figure 7 depicts the influence of malevolent SNs on the data transfer rate of IWSNs. The throughput quantifies the network’s capacity to effectively transfer data, and the findings emphasize the effectiveness of the NATURE model in comparison to the BTEM mentioned in reference10. It is important to note that the models presented in8 and10 do not contain throughput analysis, hence they are not included in this comparison. At a low concentration of 5% of malicious SN, NATURE obtains a throughput of 250 kbps, which is higher than the 200 kbps achieved by BTEM10. As the proportion of malicious SNs rises, the throughput for both models decreases. Nevertheless, NATURE constantly surpasses BTEM in terms of throughput. NATURE’s throughput is 200 kbps, which is higher than BTEM’s throughput of 170 kbps. However, NATURE has a higher percentage of malicious SNs, with 15% compared to BTEM’s SNs. This pattern persists with 30% of the social networks being malicious. In this case, NATURE maintains a throughput of 150 kbps, while BTEM declines to 140 kbps. Even with 50% of malicious SNs, NATURE still outperforms BTEM by achieving a data transfer rate of 108 kbps, whereas BTEM only achieves 100 kbps. This data highlights the ability of NATURE to sustain a greater rate of data transfer even when there are malicious SNs present. It shows that NATURE is robust and performs well under difficult network settings.
Fig. 7.
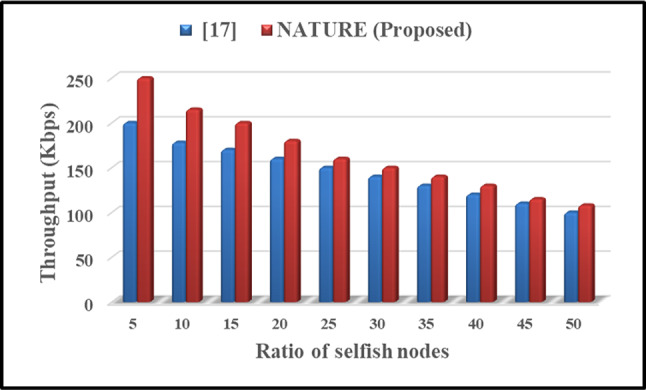
Selfish nodes vs. throughput.
Conclusion and future work
This study presents NATURE, a well-crafted trust-based method for detecting misbehavior in clustered IWSNs. NATURE utilizes two trust metrics: communication trust and confidence in data. The proposed approach evaluates communication trust by calculating measures for both primary and collective (feedback) communication trust. Trust estimation is conducted at three hierarchical levels: cluster entities, lead nodes, and control stations. This multi-tiered approach guarantees robust identification and prevention of destructive nodes by utilizing dynamic reward and punishment based on patterns of behavior. The other key innovations include the Temporal Decay Factor, which ensures that trust evaluations prioritize recent behaviors, and the Dynamic Adjustment Factor, which balances negative and positive interactions, making trust assessments more responsive and accurate. Additionally, the Optimal Lead Node Election Algorithm (OLNEA) enhances data aggregation and load balancing by selecting the most reliable lead nodes based on network density, link quality, and battery life. The suggested trust-based attack detection algorithm ensures data authenticity and integrity while minimizing energy consumption and communication overhead. Through these contributions, NATURE significantly outperforms existing trust models, providing a more secure, energy-efficient, and reliable solution for IWSNs in dynamic industrial environments.The effectiveness of the NATURE model has been confirmed thorough theoretical analysis and simulations performed using MATLAB 2019a. Assessments were conducted in settings containing a maximum of 50% malicious nodes. The results demonstrate that NATURE surpasses existing8–10 methods in terms of both detection rate and accuracy, while effectively handling memory and sustaining high throughput even in the presence of malicious nodes.
Future work could investigate several paths to further improve the performance and application of NATURE. An option worth considering is the incorporation of machine learning algorithms to assess trust levels in an adaptable manner. This would allow for real-time adjustments based on changing network conditions and potential threats. Furthermore, exploring hybrid models that integrate NATURE with other trust mechanisms could provide a more holistic approach to security in various operational situations. Another potential research focus could be the creation of scalable algorithms that can effectively handle the increasing size of networks, specifically addressing the difficulties posed by very large-scale IWSNs. Finally, conducting the model’s evaluation in real-world industrial settings could yield useful information into its practical efficacy and potential areas for enhancement.
Acknowledgements
The work is completed in Secure Computing Laboratory, SC & SS, JNU, New Delhi, India
Author contributions
V.P.: Writing—original draft, Methodology. Investigation K.S.: Methodology, Supervision, Software, Validation, Visualization, Conceptualization, Formal analysis. T.K.: Conceptualization, Writing, Editing, Methodology. M.S.: Conceptualization, Writing, Formal analysis, Investigation. S.A.C.: Formal analysis, Investigation, Editing. A.K.D.: Validation, Formal analysis, Proofreading.
Data availability
The datasets generated and/or analyzed during the current study are available from the corrresponding author on reasonable request.
Declarations
Competing interests
The authors declare no competing interests.
Footnotes
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Fang, W., Zhang, W., Chen, W., Liu, Y. & Tang, C. TMSRS: trust management-based secure routing scheme in industrial wireless sensor network with fog computing. Wirel. Netw. 26, 3169–3182 (2020). [Google Scholar]
- 2.Yang, L., Lu, Y., Yang, S. X., Guo, T. & Liang, Z. A secure clustering protocol with fuzzy trust evaluation and outlier detection for industrial wireless sensor networks. IEEE Trans. Ind. Inf. 17(7), 4837–4847 (2020). [Google Scholar]
- 3.Khan, T. & Singh, K. DTMS: A dual trust-based multi-level sybil attack detection approach in WSNs. Wirel. Pers. Commun. 1–32 (2024).
- 4.Rajasoundaran, S., SanthoshKumar, S. V. N., Selvi, M., Thangaramya, K. & Arputharaj, K. Secure and optimized intrusion detection scheme using LSTM-MAC principles for underwater wireless sensor networks. Wirel. Netw. 30(1), 209–231 (2024). [Google Scholar]
- 5.Khan, T. et al. ETERS: A comprehensive energy aware trust-based efficient routing scheme for adversarial WSNs. Fut. Gener. Comput. Syst. 125, 921–943 (2021). [Google Scholar]
- 6.Dinesh, K. & Svn, S. K. GWO-SMSLO: Grey wolf optimization based clustering with secured modified Sea Lion optimization routing algorithm in wireless sensor networks. Peer-to-Peer Netw. Appl. 1–27 (2024).
- 7.Dinesh, K. & Santhosh Kumar, S. V. N. Energy-efficient trust-aware secured neuro-fuzzy clustering with sparrow search optimization in wireless sensor network. Int. J. Inf. Secur. 1–25 (2023).
- 8.Saidi, A., Benahmed, K. & Seddiki, N. Secure cluster head election algorithm and misbehavior detection approach based on trust management technique for clustered wireless sensor networks. Ad Hoc Netw. 106, 102215 (2020). [Google Scholar]
- 9.Kim, T.-H. et al. A novel trust evaluation process for secure localization using a decentralized blockchain in wireless sensor networks. IEEE Access 7, 184133–184144 (2019). [Google Scholar]
- 10.Anwar, R. W., Zainal, A., Outay, F., Yasar, A. & Iqbal, S. BTEM: Belief based trust evaluation mechanism for Wireless Sensor Networks. Fut. Gener. Comput. Syst. 96, 605–616 (2019). [Google Scholar]
- 11.Aruchamy, P., Gnanaselvi, S., Sowndarya, D. & Naveenkumar, P. An artificial intelligence approach for energy-aware intrusion detection and secure routing in internet of things-enabled wireless sensor networks. Concurr. Comput. Pract. Exp. 35(23), e7818 (2023). [Google Scholar]
- 12.Abuhasel, K. A. A zero-trust network-based access control scheme for sustainable and resilient industry 5.0. IEEE Access (2023).
- 13.Vazhuthi, P. P. I., Prasanth, A., Manikandan, S. P. & DeviSowndarya, K. K. A hybrid ANFIS reptile optimization algorithm for energy-efficient inter-cluster routing in internet of things-enabled wireless sensor networks. Peer-to-Peer Netw. Appl. 16(2), 1049–1068 (2023). [Google Scholar]
- 14.Zhang, W., Sun, H., Fang, W., Zhu, C. & Jia, G. Trust evaluation and decision based on DS evidence theory: Early models and future perspectives. IEEE Access 11, 16032–16041 (2023). [Google Scholar]
- 15.Khan, T. & Singh, K. RTM: Realistic weight-based reliable trust model for large scale WSNs. Wirel. Pers. Commun. 129(2), 953–991 (2023). [Google Scholar]
- 16.Sharma, V., Beniwal, R. & Kumar, V. Multi-level trust-based secure and optimal IoT-WSN routing for environmental monitoring applications. J. Supercomput. 1–44 (2024).
- 17.Saidi, A. An adaptive trust system for misbehavior detection in wireless sensor networks. Wirel. Netw. 1–27 (2024).
- 18.Das, R. & Dwivedi, M. Cluster head selection and malicious node detection using large-scale energy-aware trust optimization algorithm for HWSN. J. Reliab. Intell. Environ. 10(1), 55–71 (2024). [Google Scholar]
- 19.Komuraiah, B. & Anuradha, M. S. A new trust-based optimal stochastic data scheduling for wireless sensor networks. Peer-to-Peer Netw. Appl. 17(1), 176–199 (2024). [Google Scholar]
- 20.Wang, Chenlong, Guanghua Liu, and Tao Jiang. "Malicious Node Detection in Wireless Weak-Link Sensor Networks Using Dynamic Trust Management." IEEE Transactions on Mobile Computing (2024).
- 21.Dinesh, K. & Santhosh Kumar, S. V. N. Energy-efficient trust-aware secured neuro-fuzzy clustering with sparrow search optimization in wireless sensor network. Int. J. Inf. Secur. 23(1), 199–223 (2024). [Google Scholar]
- 22.Guo, J., Liu, Z., Tian, S., Huang, F., Li, J., Li, X., Igorevich, K. K. & Ma, J. TFL-DT: A trust evaluation scheme for federated learning in digital twin for mobile networks. IEEE J. Sel. Areas Commun. (2023).
- 23.Guo, J. et al. TROVE: A context-awareness trust model for VANETs using reinforcement learning. IEEE Internet Things J. 7(7), 6647–6662 (2020). [Google Scholar]
- 24.Rathee, G., Balasaraswathi, M., Chandran, K. P., Gupta, S. D. & Boopathi, C. S. A secure WSN sensors communication in industry 4.0 using blockchain technology. J. Ambient Intell. Hum. Comput. 12(1), 533–545 (2021). [Google Scholar]
- 25.Wang, J. et al. A survey on trust evaluation based on machine learning. ACM Comput. Surv. (CSUR) 53(5), 1–36 (2020). [Google Scholar]
- 26.Ravikumar, P. & Ganesh Kumar, P. A novel energy-efficient routing protocol for industrial WSN using hybrid COOT-LS algorithm with LSTM-based DOM prediction. Int. J. Commun. Syst. 37(3), e5656 (2024). [Google Scholar]
- 27.Dinesh, K., and Santhosh Kumar Svn. "GWO-SMSLO: Grey wolf optimization based clustering with secured modified Sea Lion optimization routing algorithm in wireless sensor networks." Peer-to-Peer Networking and Applications (2024).
- 28.Anitha, S., Saravanan, S. & Chandrasekar, A. Trust management based multidimensional secure cluster with RSA cryptography algorithm in WSN for secure data transmission. Meas. Sens. 29, 100889 (2023). [Google Scholar]
- 29.Khan, T., Singh, K., Ahmad, K. & Ahmad, K. A. B. A secure and dependable trust assessment (SDTS) scheme for industrial communication networks. Sci. Rep. 13(1), 1910 (2023). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 30.Yang, L., Yang, S. X., Li, Y., Yinzhi, Lu. & Guo, T. Generative adversarial learning for trusted and secure clustering in industrial wireless sensor networks. IEEE Trans. Ind. Electron. 70(8), 8377–8387 (2022). [Google Scholar]
- 31.Talbi, S. et al. Adaptive and dual data-communication trust scheme for clustered wireless sensor networks. Telecommun. Syst. 65(4), 605–619 (2017). [Google Scholar]
- 32.Jayasinghe, U., Lee, G. M., Um, T.-W. & Shi, Qi. Machine learning based trust computational model for WSN services. IEEE Trans. Sustain. Comput. 4(1), 39–52 (2018). [Google Scholar]
- 33.Kwon, S., Jeong, J. & Shon, T. Toward security enhanced provisioning in industrial IoT systems. Sensors 18(12), 4372 (2018). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 34.Smache, M., Olivereau, A., Franco-Rondisson, T. & Tria, A. Time synchronization attack scenarios and analysis of effective self-detection parameters in a distributed industrial wireless sensor network. In 2019 17th International Conference on Privacy, Security and Trust (PST) 1–5 (IEEE, 2019).
- 35.Nancy, P. et al. Intrusion detection using dynamic feature selection and fuzzy temporal decision tree classification for wireless sensor networks. IET Commun. 14(5), 888–895 (2020). [Google Scholar]
- 36.Demertzis, K., Iliadis, L., Tziritas, N. & Kikiras, P. Anomaly detection via blockchained deep learning smart contracts in industry 4.0. Neural Comput. Appl. 32(23), 17361–17378 (2020). [Google Scholar]
- 37.Kavitha, V. & Ganapathy, K. Galactic swarm optimized convolute network and cluster head elected energy-efficient routing protocol in WSN. Sustain. Energy Technol. Assess. 52, 102154 (2022). [Google Scholar]
- 38.Roy, P. K. & Bhattacharya, A. SDIWSN: A software-defined networking-based authentication protocol for real-time data transfer in industrial wireless sensor networks. IEEE Trans. Netw. Service Manag. 19(3), 3465–3477 (2022). [Google Scholar]
- 39.Balasundaram, A., Routray, S., Prabu, A. V., Krishnan, P., Malla, P. P. & Maiti, M. Internet of things (WSN) based smart healthcare system for efficient diagnostics of health parameters of patients in emergency care. IEEE Internet Things J. (2023).
- 40.Wang, J., Jing, X., Yan, Z., Fu, Y., Pedrycz, W. & Yang, L. T. A survey on trust evaluation based on machine learning. ACM Computi. Surveys (CSUR) 53(5), 1–36 (2020).
- 41.Khan, T. et al. An efficient trust-based decision-making approach for WSNs: Machine learning oriented approach. Comput. Commun. 209, 217–229 (2023). [Google Scholar]
- 42.Alhayani, B. et al. 5G standards for the Industry 4.0 enabled communication systems using artificial intelligence: Perspective of smart healthcare system. Appl. Nanosci. 13(3), 1807–1817 (2023). [DOI] [PMC free article] [PubMed] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
The datasets generated and/or analyzed during the current study are available from the corrresponding author on reasonable request.