Abstract
Authentication is considered one of the most critical technologies for the next generation of the Internet of Medical Things (IoMT) due to its ability to significantly improve the security of sensors. However, higher frequency cyber-attacks and more intrusion methods significantly increase the security risks of IoMT sensor devices, resulting in more and more patients’ privacy being threatened. Different from traditional IoT devices, sensors are generally considered to be based on low-cost hardware designs with limited storage resources; thus, authentication techniques for IoMT scenarios might not be applicable anymore. In this paper, we propose an efficient three-factor cluster-based user authentication protocol (3ECAP). Specifically, we establish the security association between the user and the sensor cluster through fine-grained access control based on Merkle, which perfectly achieves the segmentation of permission. We then demonstrate that 3ECAP can address the privilege escalation attack caused by permission segmentation. Moreover, we further analyze the security performance and communication cost using formal and non-formal security analysis, Proverif, and NS3. Simulation results demonstrated the robustness of 3ECAP against various cyber-attacks and its applicability in an IoMT environment with limited storage resources.
Keywords: Internet of Medical Things, mutual authentication, fine-grained access control, security
1. Introduction
The number of connected devices has grown exponentially due to advances in communications technology, resulting in what is known as the Internet of Things (IoT) [1,2,3]. IOT technology has continued to develop and innovate, profoundly changing traditional industrial models and people’s lifestyles, such as smart agriculture, smart healthcare, smart homes, and self-driving cars [4]. And healthcare is rapidly evolving, driven by an aging population, consumer demand for better services in more affordable prices, and a growing global focus on preventative health [5,6]. In recent years, IoMT has been recognized as one of the most important technologies in healthcare, which is used for systematic monitoring of patient status, enabling doctors to provide timely and appropriate treatment [7]. Specifically, IoMT sensors such as defibrillators, sphygmomanometers, and oximeters provide real-time monitoring and observation for patients’ temperature, pulse, blood pressure, respiration, and more [8]. Typically, sensors in IoMT are widely accessible and can be installed across geographies as the focus has been on making them multifunctional, low-cost, and available on hardware platforms when coordinated with back-end processing systems. With these new technologies, the prospect of IoMT sensors in healthcare is extremely promising.
Despite the convenience that IoMT brings to patients in terms of treating, diagnosing, and maintaining their health, once the information carried by these sensors is accessed by attackers, it can be a great threat to patient privacy and security [9]. One of the crucial factors to ensure the security of IoMT is node authentication. Usually, the generic architecture of IoMT consists of three node participants, i.e., user, gateway, and sensor. The sensor is placed in a designated area to collect environmental parameters and then transmits these parameters to the gateway through a wireless channel [10]. The user must be authenticated to access these data as the patient data provided by sensors are analyzed and collated to make appropriate and feasible decisions for the timely treatment of the patient.
Specifically, the IoMT system can be simplified into three dimensions, i.e., perception layer, network layer, and application layer [11]. (1) Perception layer: each patient is equipped with a variety of medical sensors used to sense and monitor vital statistics. In this layer, the attacker usually utilizes a device capture attack to obtain patient information inside sensors. (2) Network layer: similar to the OSI network and transport layer, it is responsible for authentication, communication and data transfer between sensors and users via an open channel/private network. However, it is vulnerable to man-in-the-middle attacks, impersonation attacks, replay attacks and so on. (3) Application layer: in this layer, legitimate users/medical staff can realize access to patient information through authentication with the sensors, and it is the top layer of the three-layer IoMT system architecture. However, the application layer is also vulnerable to many attacks such as insider privilege attacks, privilege escalation attacks, etc. Therefore, it is necessary to ensure the privacy and security of patient information in the multilayer architecture of an IoMT system.
Once the information is compromised, the corresponding patient information (including history of illness) may also be exposed to the attacker [12]. Worse, the attacker can even illegally sell this information, thus seriously compromising the patient’s personal privacy. In addition, insider attackers (i.e., medical staff) also pose a potential risk of IoMT information leakage. It is extremely necessary to implement permission segmentation according to access levels due to the differences in sensor data accessible to medical staff in different departments (e.g., neurology, gastroenterology, cardiovascular, etc.). Moreover, IoMT is susceptible to various types of attacks, including replay attacks, user privilege escalation attacks, smart card theft attacks, etc., which further compromise the security of the system. Therefore, it is urgent to design a new authentication protocol to ensure the security and privacy of IoMT.
Considering the security, low complexity, and low cost requirements of IoMT, we propose a new efficient cluster-based lightweight secure authentication protocol (3ECAP), with the ultimate goal of establishing a secure session key before participants transmit data. The specific contributions of this paper are as follows.
(1) 3ECAP implements IoMT user permission segmentation using fine-grained access control to establish a security association between the user and the sensor cluster, which reduces subsequent database access costs. Then, the user’s password, biometrics and smart card are used as the three factors for authentication, where biometrics are collected through a fuzzy extractor. In addition, the communication cost and computation cost of 3ECAP are further reduced by only performing hash and dissimilarity operations.
(2) The formal security analysis of 3ECAP is demonstrated through the widely used Real or Random (RoR) model and the formal automated verification tool Proverif. In addition, 3ECAP informal security analysis is also provided, which indicates that 3ECAP is not only resistant to most known attacks but also to privilege elevation attacks from insiders (see Section 6.2).
(3) Considering the limited resources of IoMT devices, compared to other schemes, our proposed authentication protocol is not only lightweight and efficient but also resistant to a variety of complex typical attacks.
The rest of this paper is structured as follows: Section 2 presents the literature survey. Some necessary mathematical background is provided in Section 3. The system model utilized in 3ECAP is given in Section 4. Section 5 describes the phases of the designed protocol (3ECAP). In Section 6, the security of 3ECAP is ensured by using formal and informal security analysis. Section 7 presents a comparative analysis of 3ECAP and other related protocols with respect to computational cost, latency, and security characteristics. Section 8 presents a simulation analysis of 3ECAP using a network simulation tool. The last section concludes the paper and gives some future research directions.
2. Related Work
In this section, research advances in the relevant areas are provided, including the methods used and advantages and limitations.
Wang et al. [13] proposed a cloud-assisted secure user authentication scheme with various attributes such as forward secrecy and multi-factor security. However, the scheme requires high computational costs and does not ensure user privacy. Masud et al. [14] proposed a lightweight anonymous user authentication protocol for IoT, which only uses lightweight cryptographic primitives (hash). The scheme establishes a secure session for legitimate users and prohibits unauthorized user access to IoT sensor nodes. Although the protocol has low computational and communication costs, it proved to be vulnerable to attacks such as impersonation and replay. In addition, relevant existing protocols [15,16,17] are designed for various IoT scenarios, e.g., IoMT, smart firefighting, smart transportation, etc., with provably secure protocols that provide mutual authentication for involved nodes. However, according to recent studies [18,19,20], the mentioned schemes are susceptible to attacks such as man-in-the-middle, denial-of-service, and internal privilege.
Zhang et al. [21] propose a password-based lightweight security authentication scheme that can flexibly achieve mutual authentication between the user and sensor. Unfortunately, studies have demonstrated that this authentication scheme based on only a single factor can be easily compromised and therefore cannot withstand attacks such as password guessing. To address these problems, Nandy et al. [22] and Singh et al. [23] have proposed security schemes based on multifactor privacy protection. However, Chaudhry et al. [24] point out that the public key of the sensor in the scheme of Nandy et al. [22] is invalid, due to the inability of the device to generate its own private key, and susceptible to clogging attacks. Moreover, the above schemes also require high communication costs.
Nyangaresi et al. [25] propose a lightweight key management and mutual authentication protocol based on Elliptic Curve Cryptography (ECC) for smart home environments. Li et al. [26] design a robust two-factor user authentication protocol based on ECC and prove that the construction of the proposed scheme can achieve user anonymity, forward secrecy of the session key, etc. However, since the above schemes use the ECC algorithm, this significantly increases the communication and computational costs to verify the protocol. Furthermore, Xie et al. [27] proposed a blockchain-based vehicle-to-infrastructure (V2I) authentication protocol using lightweight cryptographic primitives that guarantee sensor anonymity and untraceability. Son et al. [28] design a lightweight mutual authentication protocol for IoT sensors, in which the node performs cryptographic computation only when switching in order to improve the network transmission efficiency. Yang et al. [29] propose a mutual authentication scheme based on decentralized edge collaboration to provide continuous protection for zero-trust IoT and enable flexible updating for the sensor.
By reading and summarizing the above existing studies, we found that existing authentication protocols have low utility in IoMT, e.g., susceptibility to various attacks, high overhead algorithmic application, access control of user authority, high maintenance cost of protocol, and so on. Therefore, we intended to design a lightweight secure and reliable authentication protocol for IoMT to solve the above problems, and some of these research results have been published in the form of a conference [30]. Please note that 3ECAP is an extended version of the published conference paper. Compared to the previous version, 3ECAP contains more comprehensive authentication schemes, security analyses, simulations, graphs, results and utilities. The relevant changes are indicated in the text. Table 1 summarizes the relevant work described above.
Table 1.
Related works.
| Reference | Method | Advantage (+) | Limitation (−) |
|---|---|---|---|
| Wang et al. [13] | ECC, hash, fuzzy extractor | +three-factor authentication +forward secrecy |
−high computational cost −user privacy −lack of access control |
| Masud et al. [14] | hash, password | +lightweight authentication +node anonymity |
−impersonation attack −replay attack −lack of access control |
| Sutrala et al. [15] | ECC, hash | +impersonation attack protection +MITM attack protection |
−privilege-insider attack −high computational cost −lack of access control |
| Iqbal et al. [16] | hash, symmetric encryption | +privacy-preserving +node anonymous |
−impersonation attack −replay attack −lack of access control |
| Wei et al. [17] | ECC, hash, pseudo random function | +privacy-preserving +system secret key update |
−impersonation attack −lack of access control |
| Zhang et al. [21] | hash, password, homomorphic encryption | +key leakage protection +anonymity and untraceability |
−password guessing attack −lack of access control −high resource cost |
| Nandy et al. [22] | hash, ECC, RSA or DSA | +privacy-preserving +forward secrecy −insider attack protection |
−clogging attack −high resource cost −lack of access control |
| Singh et al. [23] | hash, fuzzy extractor, PUF | +two-factor authentication +physical layer security |
−MITM attack −replay attack −high resource cost −privilege escalation attack |
| Nyangaresi et al. [25] | hash, ECC, password | +replay attack protection +impersonation attack protection +MITM attack protection |
−anonymity and untraceability −device capture attack −high resource cost −lack of access control |
| Li et al. [26] | hash, ECC | +three-factor authentication +forward secrecy +device capture attack protection +impersonation attack protection |
−high resource cost −untraceability −lack of access control |
| Xie et al. [27] | hash, ECC, PUF | +device capture attack protection +MITM attack protection +impersonation attack protection |
−privilege-insider attack −forward secrecy −lack of access control |
| Son et al. [28] | hash, ECC, password | +anonymity and untraceability +ephemeral key leakage protection |
−device capture attack −high calculation cost −lack of access control |
| Yang et al. [29] | hash, ECC, bilinear pairing | +device update +token forgery attack protection |
−device capture attack −privacy disclosure −high resource cost −lack of access control |
3. Preliminaries
3.1. One-Way Hash Function
A one-way hash function can transform an input message string of arbitrary length into a fixed-length output. It is widely used in areas such as the generation of message digests and message authentication codes, key encryption, and data integrity tests. Collision resistance is the main property and is defined as follows.
Definition 1.
Suppose a one-way hash function can be expressed as . Specifically, the hash function outputs a fixed-length binary string for an arbitrary-length input binary string . Assume is defined as the probability of an adversary obtaining a hash collision in execution time t, then , where refers to the probability of a random event X occurring, and means that both input strings m and n are randomly selected by . If an -adversary attempts to attack the collision resistance of , it means that the maximum execution time of is t and that .
3.2. Fuzzy Extractor for Biometric Verification
The secret value in an encryption mechanism is a random string that requires uniform distribution and can be copied exactly. However, in the real world, it is difficult for the secret value to satisfy this. For example, biometric features, such as fingerprints, brain prints, etc., cannot be accurately copied due to a non-uniform distribution of random values. Thus, we select the fuzzy extraction method for the collection of biometric features [31].
Recently, the fuzzy extractor method has been widely used to extract biometric keys from user biometric input. This method can allow the input to have a certain amount of noise (or error), and as long as the input is similar, the same uniform random string can be extracted. The general structure is as follows.
(1) Gen: Given that the user inputs biometrics , the gen process will generate a biometric key of l bits and the corresponding auxiliary public parameter ; that is, .
(2) Rep: Given a noisy user input biometric , will return the original biometric key with the help of the auxiliary public data when the Hamming distance between the current biometric input and the original biometric input is less than a specific error tolerance threshold t; that is, . Thus, .
Considering the false-positive and false-negative events of biometric authentication, we make a note of and . If both and originate from the same person, then the Hamming distance between the two will converge to 0. We assume that , where means the false negative probability. If and originate from different people, then the Hamming distance between the two may be significant. We assume that , , where means the false positive probability.
4. System Model
4.1. Authentication Model
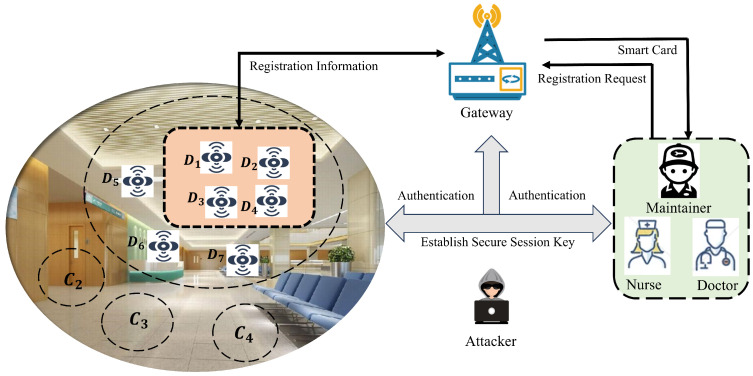
The IoMT-based authentication model is shown in Figure 1. In this model, patients suffering from different diseases are being treated in the hospital. Each hospital bed is equipped with a number of sensors to monitor and sense the real-time status of the patient (e.g., blood pressure, heart rate, etc.). Since the hospital contains different departments, such as brain, orthopedics, etc., as well as different types of medical staff in each department, such as doctors and nurses, they are all concerned with monitoring the patient’s physical condition. Specifically, only the nurse is required to handle a patient who needs a medication change, while the doctor is required to take quick emergency measures when the patient is in a life-threatening situation. Therefore, it is necessary to set the corresponding accessible sensor cluster for different user levels.
Figure 1.
Authentication model for IoMT.
Four different departments , , , and exist in the hospital, as shown on the left side of Figure 1, and some sensor devices are deployed in them. For example, in , seven sensors are deployed to detect real-time data of patients, where represents the accessible sensor cluster by a particular member of the medical staff . Before authentication, both and need to complete registration with the help of , where also sends a sensor cluster to . Then, can authenticate with through . Once authenticated, can securely access the real-time data from . Specifically, first sends a login request to . Then, validates the login request and sends the access request to the accessible . Finally, once the authentication is complete, sends a reply message to and generates a session key shared between the two. It is worth noting that the registration phase of 3ECAP is performed in a secure environment, whereas information is transmitted via a public channel in the authentication phase, which makes it vulnerable to anonymous attackers.
4.2. Threat Model
The protocol we designed uses the Dolev–Yao [32] threat model (DY model) for security analysis, where an adversary can not only intercept messages transmitted between participants but also perform deletion and modification operations. In addition, we consider the widely accepted RoR model [33], which is used to secure the session key generated by medical staff and sensors. Note that in the authentication model, suppose that the is fully trusted and is deployed in a fixed location that is physically protected so that the likelihood of the being captured is extremely low compared to that of the sensor device. In contrast, for some physically captured sensor devices, the corresponding secret information stored in these devices can be extracted by the adversary using power analysis attacks.
5. Proposed Scheme
In this section, we elaborate on a new protocol called 3ECAP for IoMT deployments. The protocol requires the following phases: (1) setup; (2) medical staff registration; (3) sensor registration; (4) login and authentication; (5) password and biometric update; and (6) new smart-device addition phase. In the setup phase, the public parameters of the protocol are selected by the fully trusted . Once the setup is complete, the medical staff and the sensor need to complete the registration in the system. In the login and authentication phase, a user (i.e., legal medical staff) and a sensor device , with the help of the , establish a shared key between and for future communication. The proposed protocol also enables to change the password and biometric information without the need for . In addition, the protocol can support the addition of new sensor devices. The notations and their abbreviations are presented in Table 2 [30] for the analysis of 3ECAP.
Table 2.
Notations and abbreviations.
| Noation | Description |
|---|---|
| , , | user, sensor and gateway |
| , , | Identities of , and |
| , , | Pseudo-identities of , , and |
| , | Smart card and biometrics of user |
| User’s access list | |
| , | Functions of the fuzzy extractor |
| , | Secret parameter and public parameter of |
| Hamming distance between and | |
| t | Fault tolerance threshold applied in |
| , | False negative probability and false positive probability |
| One-way collision-resistant hash function | |
| ⊕, | Bitwise XOR and concatenation operations |
| , , | Current timestamps |
| Maximum transmission delay | |
| , | Random numbers applied in the registration phase |
| a, b, c | Random numbers applied in the login and authentication phase |
| x | Master key for |
| , | Shared keys for and |
| Adversary | |
| P sends the message M to Q |
5.1. Setup Phase
During the system setup phase, some public parameters are initialized by . Specifically, chooses a one-way hash function , a biometric key generation function and a biometric key replication function , where and are used for bio-information extraction and recovery of medical staff, respectively. Then, generates a unique master key x, an identity , and also calculates the corresponding pseudo-identity .
5.2. Sensor Addition Phase
During the sensor addition phase, generates a unique for the medical sensor , a random number , and then calculates the pseudo-identity . In addition, a secret pairwise key is established between and by means of the master key x of , where , which will be used for mutual authentication and message encryption between nodes in the subsequent login phase. Finally, stores into the database. Meanwhile, also saves into the memory.
5.3. Medical Staff Registration Phase
In general, there are many disease departments in the medical system, such as neurology, orthopedics, brain and cardiovascular, etc. Each department is composed of many medical sensor devices that contain sensitive patient information. Therefore, in order to protect patient privacy, medical staff can only access patient information based on access permission for a specific cluster of sensor devices. The registration process for medical staff can also be divided into two phases, as follows.
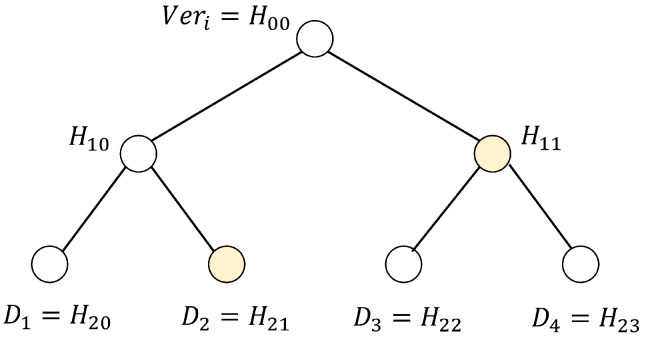
(1) Fine-Grained Access Control: The purpose of fine-grained access control [30] is to restrict the access permission of the medical staff. For example, medical staff in a neurology department can only access information from sensors relevant to their department, where these sensors are connected to the patient to monitor individual status.
Our sensor cluster model can be simplified to a merkle tree, which consists of multiple leaf nodes and a single root node , where represents the sensor device nodes accessible to a particular medical staff. Assume that the number of leaf nodes for , can be computed as follows.
Procedure 1: Denote the leaf nodes as , respectively.
Procedure 2: , where for and .
can also be calculated using auxiliary and leaf nodes, which can effectively reduce the computational complexity. As shown in Figure 2 [30], , utilizing auxiliary nodes and , instead of and .
Figure 2.
Merkle tree-based access list.
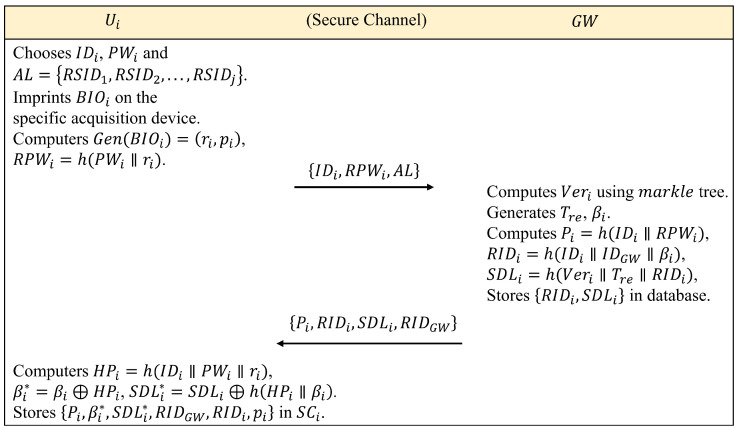
(2) Personal Information Registration
Step 1: chooses his or her identity , password , access list (generated from the cluster of accessible sensors) and imprints biological information on the specific acquisition device. The device then extracts the secret parameter and the public parameter with the help of the generating function , namely . Next, computes and sends to via a secure channel.
Step 2: After receiving the message , computes using the above tree and auxiliary nodes and also computes the personal information . Moreover, generates the current registration timestamp , a random number , and computes the pseudo-identity and the sensor device list . Next, stores in its memory. also returns the message to via a secure channel.
Step 3: Once the message is received from , calculates , , . Finally, stores the verifiable information into its own smart card ; note that represents the cluster of sensor devices accessible to the particular user. Figure 3 illustrates the complete process of 3ECAP registration.
Figure 3.
Summary of medical staff registration phase.
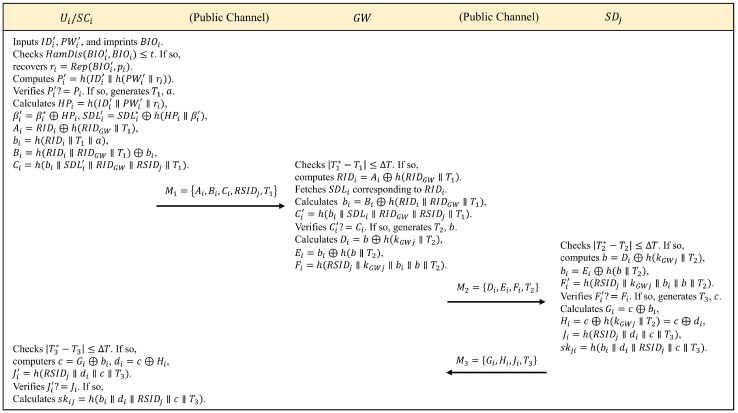
5.4. Login and Authentication Phase
When wants to access the data of , he/she needs to login and authenticate to the first. After the authentication process is complete, a secure session key is established between and for subsequent communication. The following steps are essential under the proposed protocol.
Step 1:
Step 1.1: inputs , , and imprints at a biometric acquisition device. then extracts the public parameter and recovers if is satisfied. Next, computes and verifies . The login request is terminated if .
Step 1.2: then generates the current timestamp , a random number a, and calculates , , , , , , . Finally, sends the message to via a common channel, where contains the information wants to obtain.
Step 2:
Step 2.1: Once is received from , first verifies the validity of under the condition of , where is the receive timestamp, and is the maximum time delay. The entire session is aborted if the condition is not met. Otherwise, computes and finds the corresponding from the memory. Meanwhile, also calculates , and verifies . If , it indicates two possibilities, case 1: is an external attacker who does not have the key for the registration phase of the personnel information, and case 2: is an internal attacker who wants to access sensors beyond his/her own permission, i.e., the sensor cluster .
Step 2.2: If , it indicates that the identity of is confirmed. Then, generates the current timestamp , a random number b and computes , , , where is the symmetric key for and is stored in the memory of . At last, sends the message publicly to .
Step 3:
Step 3.1: Once receives message from , verifies that timestamp matches condition . If the condition does not match, it indicates that the timeliness of is not guaranteed and the session will be closed. Otherwise, calculates , and using the stored symmetric key . then verifies that .
Step 3.2: If , the access request from is terminated. Otherwise, authenticates successfully. Then, generates the current timestamp , a random number c and calculates , , . Meanwhile, also computes the secure session key . Finally, sends the message to via a public channel.
Step 4: Once is received at time by , verifies the validity of in this message with the condition of . If the condition fails, the session is immediately terminated by . Otherwise, calculates , and and verifies . If , it means that the identity of is confirmed. Eventually, computes the session key shared with , which will be used to encrypt the data transmitted between and . Figure 4 illustrates the complete process of 3ECAP login and authentication.
Figure 4.
Summary of login and authentication phase.
5.5. Password and Bio-Information Update Phase
Usually, human biological characteristics change over time, for example, the characteristics of brain waves are completely different at different ages. Therefore, 3ECAP supports the modification of biological information for medical staff. In addition, we recommend that medical staff change their passwords regularly to ensure the security of their privacy (this part was not considered in the previous conference). The specific steps for password and bio-information modification are as follows.
Step 1: input and and imprint the old bio-information on the specific collection device. Meanwhile, inserts its smart card in the system terminal. Then, computes with the condition , where is the biological information previously registered by . Next, computes and verifies . If , authenticates successfully. Otherwise, password and bio-information change requests are terminated by .
Step 2: After successful authentication, enters a new password and imprints the new bio-information at the acquisition device. The device then extracts the corresponding secret parameter and public parameter using . Next, calculates the old secret information , and . also calculates the new secret information , , , . finally replaces with in its memory.
5.6. New Smart Device Addition Phase
Usually, a sensor is installed in each sickbed to capture the real-time status of the patient (e.g., blood pressure, temperature, heartbeat, etc.). Hence, the number of sensors is generally fixed. However, when emergencies arise (for example, the outbreak of COVID-19), the original number of beds cannot meet the demand of patients. Therefore, 3ECAP can support the bulk addition of new sensors with the following steps (this part was not considered in the previous conference).
Step 1: Before new sensors are deployed, they need to register with the gateway. Specifically, selects an identity and a random number for and computes the pseudo-identity . Meanwhile, computes . Then, and store and into their own databases, respectively. Furthermore, after the registration of the sensor is complete, needs to broadcast the addition regarding so that can access the data therein.
Step 2: needs to update sensor device list with the help of before accessing the bulk-added . first inputs , , and inserts . Then, calculates if condition is satisfied. Next, computes and verifies . If , sends to via a secure channel, where consists of the old devices and the newly added devices .
Step 3: Once the message is received from , generates a new current registration timestamp and computes , where is calculated based on using the tree. Then, sends to via a secure channel.
Step 4: When is received from , computes , , . Finally, replaces with in its memory.
6. Security Analysis
In this section, we verify the security reliability of 3ECAP using both formal and informal security analysis. Specifically, we first prove the security of session keys in the proposed protocol based on the ROR model. Then, we use informal security analysis to demonstrate that 3ECAP is secure in the face of access privilege escalation as well as other known attacks. In addition, we perform formal security verification using the popular automated verification tool Proverif.
6.1. ROR Model-Based Formal Security Analysis
We consider random oracles under the formal security model, where the adversary/attacker can make multiple oracle queries (this part was not considered in the previous conference).
(1) ROR model:
In the login and authentication phase of 3ECAP, three participants , and are involved in this process. The model considers the following.
Participants: The instances i, k, and j corresponding to the participants , , and can be denoted as , , and , respectively, which are called oracles.
Accepted state: An instance is in the accept state, indicating that it has received the last message. Once the messages sent and received by are sequentially ordered, it forms the session identifier side of for the running session.
Partnering: Two instances, called and , are partners if the following conditions are met: (1) and are in the accepted state; (2) and have the same session identification (sid), i.e., ; and (3) ’s partner identification (pid) is and vice versa.
Freshness: Two instances, called and , are fresh if the key () established between and is not disclosed by adversary through reveal query.
Adversary: Since the ROR model is based on the DY threat model, adversary can fully control all messages transmitted in the network, which means that can eavesdrop, modify, delete, forge, or inject messages between two entities.
Execute (,,): The passive attack is modeled under this query, which allows to intercept all communication records between participants , , and .
Send (,m): This query is considered an active attack, where can send a message m to an instance and also receive a response message.
Reveal (): When this query is executed, the session key (=) established between and its partner is leaked to .
CorruptSC (): Once such a query is executed, the information stored in the smart card of is disclosed to .
CorruptSD (): Under this query, can extract all the sensitive information stored in a sensor by a power analysis attack. Therefore, this query is modeled as an active attack. In addition, we also assume that both and provide a weak corruption model where the temporary keys and internal data of the instance are not corrupted.
Test (): The semantic security of the session key (i.e., or ) established between instances can be modeled with this query. Once this query is executed, a coin c is tossed and the result is returned to . If , the instance returns or a random number of the same length as if ; otherwise, it returns a null value.
It is worth noting that, according to [34], we perform a limit on the number of queries for and queries. However, is allowed to execute multiple queries. Furthermore, since is absolutely secure in the network, cannot obtain any information from by query. All participants and have access to a one-way collision-resistant hash function , which is modeled as a random oracle.
(2) Security Proof: The semantic security (or AKE security) of the session key in 3ECAP is given in Theorem 1. Furthermore, similar proofs [35] and [34] follow Theorem 1.
Theorem 1.
If is the adversary in polynomial time against 3ECAP in the RoR model, and , , and denote the number of Hash queries, Send queries, and Execute queries, respectively, then
where , , and refer to the length of the hash output, the length of the random number, and the length of the user bio-secret parameter , respectively. is denoted as the password space and obeys the Zipf distribution, and and are the parameters of Zipf.
Proof.
The security proof of the proposed protocol (3ECAP) is composed of a series of games: , , , . Suppose () represents an event in which successfully guesses the random bit c of a tossed coin in the game and the corresponding probability of occurrence is denoted as . □
Game : This is the initial game where performs a real attack simulation on 3ECAP in the ROR model. Thus, according to the definition of semantic security, we have
| (1) |
Game : It corresponds to a passive attack implemented by , where can perform an query and intercept all messages , and transmitted in the public channel during the login and authentication phases of . Once the game is over, executes a query and discriminates the genuine from a random number based on the results returned by the query, where , and . Therefore, needs the secret information , and a to calculate the session key . However, this secret information cannot be obtained by by eavesdropping on messages , and . Therefore, the probability of adversary winning the game does not increase. Due to the indistinguishability of games and , we have
| (2) |
Game : Game is modeled as an active attack where the primary goal of is to attempt to convince participating nodes that the forged message is legitimate. Suppose that performs number of Hash queries with the help of number of the queries. Based on the results of the birthday paradox, the collision probability of the Hash query is at most . Since the random numbers a, b and c exist in messages , and , respectively, the collision probability of the random numbers is at most . Hence, we obtain
| (3) |
Game : This is the last game, where executes and queries. Specifically, the information stored in and the information stored in are obtained by using and , respectively. Note that the pseudo-identity and of all sensors are different from each other. In 3ECAP, uses both password and bio-information for authentication, which can be divided into two cases.
Case 1: Suppose that attempts to guess the low entropy password using number of the send queries. Since the user’s password follows Zipf’s law [36,37], the probability of this case is .
Case 2: Assume that tries to extract the biological key of from the obtained information. Since 3ECAP adopts the fuzzy extractor technique, can only extract at most random bits, and the corresponding probability of guessing is approximately . In addition, we consider the probability of false positive that occurs for biometric feature extraction. In general, for fingerprints, [34].
Therefore, based on case 1 and case 2, it follows that
| (4) |
Since all queries are executed, can only win the game by guessing bit c. This means that
| (5) |
From (1) and (2), it is given that
| (6) |
From (5) and (6), we have
| (7) |
Using the trigonometric inequality, we can obtain
| (8) |
Finally, from (3), (4), (7) and (8), we have
6.2. Informal Security Analysis
(1) Medical Staff Impersonation Attack: The adversary/attacker who attempts to impersonate a legitimate medical staff needs to create a valid message , where , , . Even if can generate the timestamp and the random number , cannot recover due to the lack of the key secret information , , and . This indicates that 3ECAP is secure against a user impersonation attack.
(2) Gateway Impersonation Attack: In order to become a legitimate node by impersonating , adversary needs to create a message to send to , where , , . Even if can generate the timestamp and the random number , will be unable to recover as the calculations of need the secret information , and . Thus, 3ECAP is protected in a gateway impersonation attack.
(3) Sensor Impersonation Attack: Suppose that attempts to generate a message on behalf of to become a legitimate device node, where , , . Although can generate timestamp and random number due to the absence of secret information and , also cannot recover .
(4) Stolen Verifier Attack: Assume that has stolen the medical staff’s smart card and obtains the secret information stored in using the power analysis attack, where , , , , . Suppose guesses a password and attempts to verify its authenticity using known information. However, verifying requires guessing both the identity and the secret information of , which is computationally difficult to achieve due to the collision-resistant property of (see Definition 1). Similarly, A cannot guess the bio-information correctly without and . Moreover, it is not possible for to compute other information, such as and , in the absence of . Hence, 3ECAP is secure against a stolen smart card attack.
(5) Replay Attack: Suppose that adversary intercepts messages , and in a session and replays them after some time. The replay attack makes the participating nodes unable to recognize the authenticity of the messages and may lead to system breakdown as the number of replayed messages increases. However, due to the presence of timestamp T in , and , when a node receives a message, the first task for it is to verify the validity of T under the condition , where represents the reception timestamp. Therefore, 3ECAP is secure against a replay attack.
(6) Denial-of-Service Attack: In the login and authentication phase of medical staff , first inserts the smart card and imprints his or her bio-information on the acquisition device, and also enters the corresponding identity and password . If the condition is not satisfied, the whole session is terminated. Otherwise, computes , , and verifies . The session is also aborted if the equation does not hold. Therefore, it is clear that 3ECAP is capable of dealing with denial-of-service attacks.
(7) Sensor Device Capture Attack: Assume that has captured and obtained information from it and attempts to compute the session key between and other uncaptured sensors based on , where , . However, it is difficult for to accomplish this task as these calculations require and , which are randomly generated by . Hence, 3ECAP is secure in the face of a sensor device capture attack.
(8) Man-in-the-Middle Attack: In this attack, adversary intercepts the messages , and in a particular session and attempts to modify them into another form, which can make it impossible for participating nodes, such as , , and , to determine whether they are communicating with a legitimate node. Suppose intercepts message and forges a new message using the information in it, where , , . Even if has the ability to generate timestamp and random number , cannot forge message , which can be recognized by participating nodes, due to the fact that these calculations require secret information , , and . Similarly, adversary cannot forge and . Therefore, 3ECAP is safe in responding to a man-in-the-middle attack.
(9) Insider Privilege Attack: There may be a scenario in which a privileged internal personnel of the trusted serves as an internal attacker . This attack can be divided into two cases as follows.
Case 1: Assume that obtains of during the medical staff registration phase, where . Without knowing the identity of and the random number , it is difficult for A to guess one of them correctly from due to the collision resistance property of .
Case 2: Suppose that intercepts message at the time of medical staff registration, which is initially sent by to via a secure channel, where , , . However, cannot obtain any information from the message, due to the lack of , , , , , x and the collision resistance property of . Hence, 3ECAP has the capability to cope with a privileged-insider attack.
(10) Privilege Escalation Attack: In this attack, medical staff , authorized by , wants to gain data from other devices, which are out of ’s access list, by upgrading his/her access privilege. For this purpose, the access list for needs to be changed from to , such that and , when ’s sensor device list is . Although gains , he or she cannot upgrade while keeping unchanged, as explained below.
Note: Let be a function for the calculation of the root hash of a tree consisting of j leaf nodes. Also let be denoted as . Then, we prove that has the property of collision resistance by mathematical induction, same as . In order not to lose generality, assume that for . Given for , we have
| (9) |
where and . It is obvious that is a collision-resistant function, same as . Suppose the same is true when , that is, there is no
| (10) |
where . Then, when , we have
| (11) |
| (12) |
| (13) |
Therefore, it follows from (9), (10), (11), (12) and (13) that is as collision resistant as . Let and , where for and . Next, and . Due to the collision-resistant nature of , it is not feasible to find , where , such that is satisfied.
Suppose obtains the registration timestamp and extracts the pseudo-identity by power analysis attack, which is stored in . Then, expands the permissions to and computes and . However, in step 2.1 of the authentication phase, uses stored in the database to compute and verify , where belongs to and is sent by to . It is clear that because of the collision-resistant property of and such that the whole session is terminated. Thus, 3ECAP is protected against a privilege escalation attack.
(11) Anonymity and Untraceability: In 3ECAP, all messages , and of a particular session are set with timestamps , and , respectively, and also with random numbers a, b and c, which ensure that the participants , and in the session are not tracked by the adversary. Furthermore, 3ECAP uses pseudo-identities , and to transmit information in the public channel instead of the original identities , and , respectively, of the participating nodes in the session. Therefore, the anonymity of all participants in 3ECAP can be guaranteed.
6.3. Formal Verification with Proverif
Proverif is a formal automatic verification cryptographic protocol tool based on the Dolev–Yao model developed by Bruno Blanchet, which is able to describe various cryptographic primitives such as shared key cryptography and public key cryptography (encryption and digital signatures), Hash functions and Diffie–Hellman key exchange protocols. In addition, Proverif can handle an infinite session concurrent protocol and infinite message space, which overcomes the problem of state space explosion. When applying the Proverif tool to verify a cryptographic protocol, the tool gives a sequence of attacks if the protocol is vulnerable. All details about the usage of Proverif are in [38].
Four different channels, , , and , are defined in Proverif, where and are secure channels for node registration and and are public channels for medical staff login and authentication. In addition, we define three processes for , , and , respectively, and use to implement the parallel operation of the three entities.
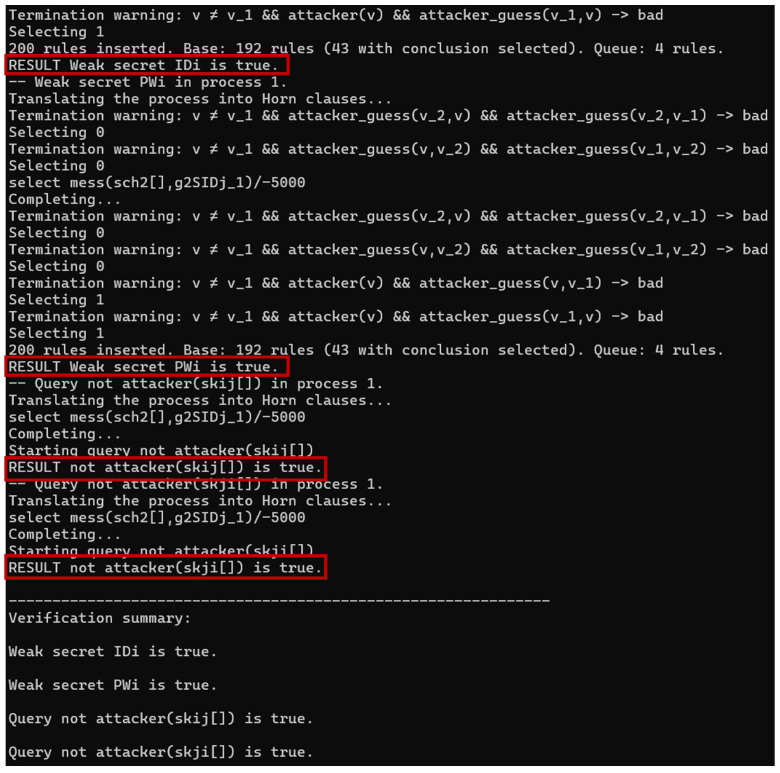
The results of the Proverif execution are shown in Table 3 [30] and Figure 5. The first two rows demonstrate that both weak and can cope with guessing attacks. The last two rows imply that the generated session keys between and are robust against common attacks. Therefore, 3ECAP is secure under formal verification.
Table 3.
Results for code.
| Secure channel | , |
| Public channel | , |
| Process | , , |
| RESULT Weak secret IDi is true (bad not derivable). | |
| RESULT Weak secret PWi is true (bad not derivable). | |
| RESULT not attacker(skij[]) is true. | |
| RESULT not attacker(skji[]) is true. | |
Figure 5.
Results of executing Proverif.
7. Comparative Analysis
In this section, a comparative analysis of the calculation cost, communication and security features of 3ECAP and related protocols for Li et al. [26], Xie et al. [27], Son et al. [28] and Yang et al. [29] is shown.
7.1. Calculation Costs Comparison
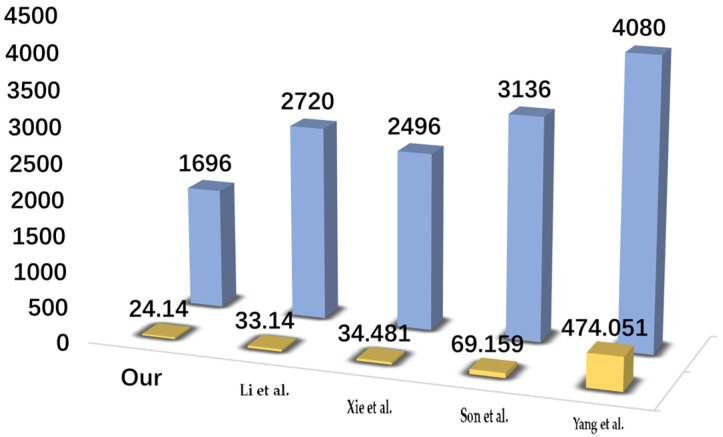
The calculation costs required for 3ECAP and other protocols in the login and authentication phases are provided in this section. Assume that , , , and represent the time required for the hash function (SHA-256), asymmetric encryption/decryption (RSA-1024), bilinear pairing, ECC point multiplication and fuzzy extractor, respectively. Based on the available experimental results of Challa et al. [39], the time required to use these functions are ms, ms, ms, ms and ms. Specifically, the various calculation costs required for the user, gateway, and sensor in each protocol are shown in Table 4 and Figure 6. The calculation cost of 3ECAP for the , , and are, respectively, , and . The total calculation cost of 3ECAP is only ms compared to other protocols, which is especially suitable for the communication requirements for IoMT.
Table 4.
Calculation costs comparison.
Figure 6.
Comparison of calculation and communication cost [26,27,28,29].
7.2. Communication Costs Comparison
To measure the communication cost of the login and authentication phase, we assume that the identity, hash digest, random nonce, ECC point multiplication, asymmetric encryption/decryption (RSA-1024), and timestamp are 160 bits, 160 bits, 128 bits, 320 bits, 512 bits and 32 bits, respectively. Therefore, the total communication cost in 3ECAP is 1696 bits. The protocols of Li et al. [26], Xie et al. [27], Son et al. [28] and Yang et al. [29] require 2720, 2496, 3136, and 4080 bits (b) of communication cost, respectively. The details are shown in Table 5.
Table 5.
Communication costs comparison.
7.3. Security Features Comparison
The comparative analysis of thesecurity and functional features of 3ECAP and other related protocols is presented in Table 5. It can be observed that 3ECAP provides improved security and more functional features compared to the other four protocols. For example, the protocol by Li et al. [26] directly uses the identity of the participating nodes for information transmission, which can be easily tracked by the adversary. Moreover, in IoMT, the permission of different levels of users should be divided, which is not involved in the four other protocols. In contrast, 3ECAP divides several sensors into corresponding clusters based on the user’s access list and stores in a smart card and gateway, which not only achieves permission segmentation but also eliminates part of the subsequent database validation. Therefore, 3ECAP clearly outperforms other related protocols according to the comparison of all the features in Table 6.
Table 6.
Security features comparison.
| Feature | 3ECAP | [26] | [27] | [28] | [29] |
|---|---|---|---|---|---|
| User impersonation attack | ✔ | ✔ | ✔ | × | ✔ |
| Gateway impersonation attack | ✔ | ✔ | ✔ | × | ✔ |
| Sensor device impersonation attack | ✔ | ✔ | ✔ | × | ✔ |
| Stolen verifier attack | ✔ | — | ✔ | × | ✔ |
| Replay attack | ✔ | ✔ | ✔ | ✔ | ✔ |
| Denial-of-service attack | ✔ | ✔ | × | × | × |
| Sensor device capture attack | ✔ | × | ✔ | × | × |
| Man-in-the-middle attack | ✔ | × | ✔ | ✔ | ✔ |
| Insider privilege attack | ✔ | × | ✔ | × | ✔ |
| Privilege escalation attack | ✔ | × | × | × | × |
| Anonymity | ✔ | — | × | ✔ | × |
| Untraceability | ✔ | ✔ | × | × | × |
| Forward secrecy | ✔ | ✔ | ✔ | ✔ | × |
| Mutual authentication | ✔ | ✔ | ✔ | ✔ | × |
| Session key agreement | ✔ | × | ✔ | ✔ | ✔ |
| Biometric update | ✔ | ✔ | × | × | × |
| Password change | ✔ | ✔ | ✔ | × | × |
| Sensor device addition | ✔ | — | — | — | — |
| Two/three factor authentication | 3 | 3 | 3 | 2 | 2 |
| Fine-grained access control | ✔ | × | × | × | × |
| Formal analysis | ✔ | ✔ | ✔ | × | ✔ |
| Authentication based on Proverif/AVISPA tool | ✔ | ✔ | ✔ | × | × |
✔: The protocol securely resists a particular attack or supports a particular feature; ×: the protocol is insecure against a particular attack or does not support a particular feature; —: not applied in the protocol.
8. NS3 Simulation
In this section, we attempt to measure the performance of 3ECAP in terms of network throughput (in bytes/second) and end-to-end delay (EED, in seconds) using the widely accepted NS3 tool (this part was not considered in the previous conference).
8.1. Simulation Parameters and Scenario
Table 7 [30] lists the basic network parameters used in the NS3 simulation. We used the Ubuntu 18.04.4 LTS platform. The simulation of the user, gateway, and sensor was executed on 2.4GHz Wi-Fi media. The gateway was set at the origin. The users were permitted to move randomly in any direction at a speed of 3 m within a 150 m2 area centered at the origin. Sensors were randomly distributed on an 80-m ring and centered on the gateway. We then set the size of the messages transmitted between the nodes, i.e., bytes, bytes, and bytes.
Table 7.
Simulation parameters.
| Parameter | Description | |
|---|---|---|
| Platform | NS3 3.27/Ubuntu 18.04.4 LTS | |
| Mobility | random (3 m/s) | |
| Simulation time | 1200 s | |
| Scenarios | No. of users | No. of devices |
| 1 | 10 | 5 |
| 2 | 5 | 10 |
| 3 | 8 | 10 |
| 4 | 5 | 15 |
| 5 | 5 | 20 |
| 6 | 8 | 50 |
In this scenario, a complete message transfer consists of (the NS3 simulation does not involve specific cryptographic operations) (1) the user first sends an authentication request to a gateway in order to access the device; (2) the gateway receives the request and then forwards to the device; and (3) once it receives the message from gateway, the device sends the message to the user. Through 1, 2 and 3, the information interaction between a user and a device can be accomplished. Meanwhile, since there is more than one user and device in the scenario, they can all authenticate each other through the gateway. Therefore, it can be assumed that there are multiple message transfers at a given moment. And the main purpose of using NS3 is to show how the total throughput and delay change with the number of participating nodes.
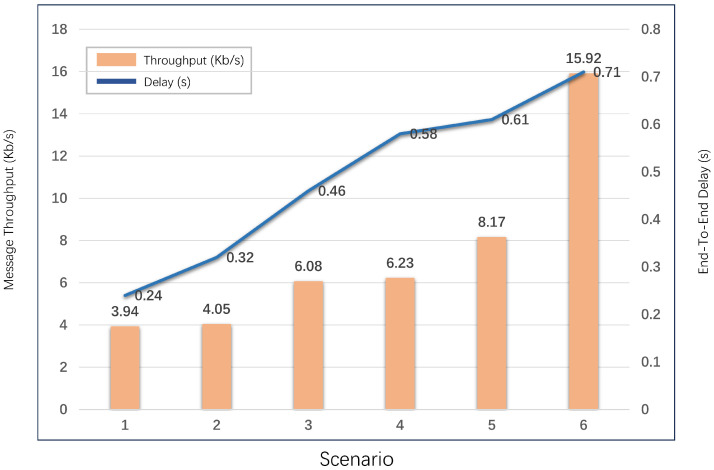
We also set the simulation time for this scenario to 1200 s, which is a relatively appropriate setting that is sufficient to reflect the simulation results of 3ECAP. Finally, we configure a different number of users and devices, and the simulation parameters and results are shown in Table 7 [30] and Figure 7.
Figure 7.
NS3-based 3ECAP simulation results.
8.2. Discussion of Simulation Results
(1) Impact on Network Throughput: The total throughput of 3ECAP in the six scenarios is represented by bar charts in Figure 7. The throughput is calculated as , where the total amount of data received in the simulated environment is , the time to send the first packet is , and the time to receive the last packet is . It is observed that as the number of participating nodes, including users and sensors, increases, the network throughput in the network also increases accordingly.
(2) Impact on End-to-End Delay: The total delay of 3ECAP in the six scenarios is represented by the discounted graph in Figure 7. EED delay can be expressed as , where and represent the sending time and receiving time, respectively, when the ith packet is transmitted, and the total number of packets transmitted during the simulation is . It follows from the figure that when the number of participating nodes increases, the number of messages transmitted will increase, which may cause network congestion to the extent that the EED delay increases.
9. Conclusions
Considering the aspects of security, low cost, and access control for IoMT sensors, in this paper, we propose a new efficient cluster-based user authentication protocol (3ECAP). In 3ECAP, three factors, i.e., password, biometric and smart card, are employed to resist a single-factor incidental guessing attack. In addition, 3ECAP enables user-specific privilege segmentation through fine-grained access control and can address the resulting privilege escalation attack. Furthermore, provable security based on the ROR model, formal verification based on the Proverif tool, as well as non-formal analysis are provided in this paper, and the results demonstrate the robustness of 3ECAP in the face of most attacks. Finally, the comparison and analysis with the latest related protocols indicate that 3ECAP provides higher security and lower computation and communication costs; therefore, it is very suitable for the practical deployment of the IoMT.
Future research directions related to this paper are as follows: (1) implementing and evaluating 3ECAP in real IoMT environments, (2) providing a flexible on-line sensor device addition phase, and (3) supporting dynamic updating of user-accessible lists based on sensor clusters in order to maintain forward and backward secrecy.
Acknowledgments
The authors would like to thank the reviewers for their valuable feedback and suggestions on this paper, which helped to improve the quality of the paper.
Author Contributions
Conceptualization, X.S. and Y.X.; methodology, X.S.; software, X.S.; validation, X.S. and Y.X.; formal analysis, X.S.; investigation, X.S.; resources, X.S. and Y.X.; data curation, X.S.; writing—original draft preparation, X.S.; writing—review and editing, X.S. and Y.X.; visualization, X.S.; supervision, X.S. and Y.X.; project administration, X.S. and Y.X.; funding acquisition, X.S. All authors have read and agreed to the published version of the manuscript.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
Funding Statement
The work of this paper was funded by the National Natural Science Foundation of China No. 62371246 and the Practice Innovation Program of Jiangsu Province No. KYCX22_0936.
Footnotes
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
References
- 1.Laghari A.A., Wu K., Laghari R.A., Ali M., Khan A.A. A review and state of art of Internet of Things (IoT) Arch. Comput. Methods Eng. 2021;29:1–19. [Google Scholar]
- 2.Soori M., Arezoo B., Dastres R. Internet of things for smart factories in industry 4.0, a review. Internet Things Cyber-Phys. Syst. 2023;3:192–204. doi: 10.1016/j.iotcps.2023.04.006. [DOI] [Google Scholar]
- 3.Sadhu P.K., Yanambaka V.P., Abdelgawad A. Internet of things: Security and solutions survey. Sensors. 2022;22:7433. doi: 10.3390/s22197433. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 4.Zhang L., Lin Y., Yang X., Chen T., Cheng X., Cheng W. From Sample Poverty to Rich Feature Learning: A New Metric Learning Method for Few-Shot Classification. IEEE Access. 2024;2024:124990–125002. doi: 10.1109/ACCESS.2024.3444483. [DOI] [Google Scholar]
- 5.Mahmoud H.H.H., Amer A.A., Ismail T. 6G: A comprehensive survey on technologies, applications, challenges, and research problems. Trans. Emerg. Telecommun. Technol. 2021;32:e4233. doi: 10.1002/ett.4233. [DOI] [Google Scholar]
- 6.Tataria H., Shafi M., Molisch A.F., Dohler M., Sjöland H., Tufvesson F. 6G wireless systems: Vision, requirements, challenges, insights, and opportunities. Proc. IEEE. 2021;109:1166–1199. doi: 10.1109/JPROC.2021.3061701. [DOI] [Google Scholar]
- 7.Razdan S., Sharma S. Internet of medical things (IoMT): Overview, emerging technologies, and case studies. IETE Tech. Rev. 2022;39:775–788. doi: 10.1080/02564602.2021.1927863. [DOI] [Google Scholar]
- 8.Hernandez-Jaimes M.L., Martinez-Cruz A., Ramírez-Gutiérrez K.A., Feregrino-Uribe C. Artificial intelligence for IoMT security: A review of intrusion detection systems, attacks, datasets and Cloud-Fog-Edge architectures. Internet Things. 2023;23:100887. doi: 10.1016/j.iot.2023.100887. [DOI] [Google Scholar]
- 9.Garg N., Wazid M., Singh J., Singh D.P., Das A.K. Security in IoMT-driven smart healthcare: A comprehensive review and open challenges. Secur. Priv. 2022;5:e235. doi: 10.1002/spy2.235. [DOI] [Google Scholar]
- 10.Hireche R., Mansouri H., Pathan A.S.K. Security and privacy management in Internet of Medical Things (IoMT): A synthesis. J. Cybersecur. Priv. 2022;2:640–661. doi: 10.3390/jcp2030033. [DOI] [Google Scholar]
- 11.Koutras D., Stergiopoulos G., Dasaklis T., Kotzanikolaou P., Glynos D., Douligeris C. Security in IoMT communications: A survey. Sensors. 2020;20:4828. doi: 10.3390/s20174828. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 12.Mishra N., Pandya S. Internet of things applications, security challenges, attacks, intrusion detection, and future visions: A systematic review. IEEE Access. 2021;9:59353–59377. doi: 10.1109/ACCESS.2021.3073408. [DOI] [Google Scholar]
- 13.Wang C., Wang D., Duan Y., Tao X. Secure and Lightweight User Authentication Scheme for Cloud-Assisted Internet of Things. IEEE Trans. Inf. Forensics Secur. 2023;18:2961–2976. doi: 10.1109/TIFS.2023.3272772. [DOI] [Google Scholar]
- 14.Masud M., Gaba G.S., Choudhary K., Hossain M.S., Alhamid M.F., Muhammad G. Lightweight and Anonymity-Preserving User Authentication Scheme for IoT-Based Healthcare. IEEE Internet Things J. 2022;9:2649–2656. doi: 10.1109/JIOT.2021.3080461. [DOI] [Google Scholar]
- 15.Sutrala A.K., Bagga P., Das A.K., Kumar N., Rodrigues J.J., Lorenz P. On the design of conditional privacy preserving batch verification-based authentication scheme for internet of vehicles deployment. IEEE Trans. Veh. Technol. 2020;69:5535–5548. doi: 10.1109/TVT.2020.2981934. [DOI] [Google Scholar]
- 16.Iqbal W., Abbas H., Deng P., Wan J., Rauf B., Abbas Y., Rashid I. ALAM: Anonymous lightweight authentication mechanism for SDN-enabled smart homes. IEEE Internet Things J. 2020;8:9622–9633. doi: 10.1109/JIOT.2020.3024058. [DOI] [Google Scholar]
- 17.Wei L., Cui J., Xu Y., Cheng J., Zhong H. Secure and lightweight conditional privacy-preserving authentication for securing traffic emergency messages in VANETs. IEEE Trans. Inf. Forensics Secur. 2020;16:1681–1695. doi: 10.1109/TIFS.2020.3040876. [DOI] [Google Scholar]
- 18.Yang Y., Huang X. Comments on “On the Design of Conditional Privacy Preserving Batch Verification-Based Authentication Scheme for Internet of Vehicles Deployment”. [(accessed on 1 November 2024)];Cryptol. ePrint Arch. 2021 018 Available online: https://eprint.iacr.org/2021/018. [Google Scholar]
- 19.Yu S., Das A.K., Park Y. Comments on “ALAM: Anonymous lightweight authentication mechanism for SDN enabled smart homes”. IEEE Access. 2021;9:49154–49159. doi: 10.1109/ACCESS.2021.3068723. [DOI] [Google Scholar]
- 20.Zhang J., Zhang Q. Comment on “Secure and Lightweight Conditional Privacy-Preserving Authentication for Securing Traffic Emergency Messages in VANETs”. IEEE Trans. Inf. Forensics Secur. 2021;18:1037–1038. doi: 10.1109/TIFS.2021.3066277. [DOI] [Google Scholar]
- 21.Zhang S., Liu Y., Gao T., Xie Y., Zhou C. Practical and Secure Password Authentication and Key Agreement Scheme Based Dual-Server for IoT Devices in 5G Network. IEEE Internet Things J. 2024;2024:34639–34651. doi: 10.1109/JIOT.2024.3407714. [DOI] [Google Scholar]
- 22.Nandy T., Idris M.Y.I., Noor R.M., Wahab A.W.A., Bhattacharyya S., Kolandaisamy R., Yahuza M. A Secure, Privacy-Preserving, and Lightweight Authentication Scheme for VANETs. IEEE Sens. J. 2021;21:20998–21011. doi: 10.1109/JSEN.2021.3097172. [DOI] [Google Scholar]
- 23.Singh N., Das A.K. TFAS: Two factor authentication scheme for blockchain enabled IoMT using PUF and fuzzy extractor. J. Supercomput. 2024;80:865–914. doi: 10.1007/s11227-023-05507-6. [DOI] [Google Scholar]
- 24.Chaudhry S.A. Comments on “A Secure, Privacy-Preserving, and Lightweight Authentication Scheme for VANETs”. IEEE Sens. J. 2022;22:13763–13766. doi: 10.1109/JSEN.2022.3168512. [DOI] [Google Scholar]
- 25.Nyangaresi V.O. ECC Based Authentication Scheme for Smart Homes; Proceedings of the 2021 International Symposium ELMAR; Zagreb, Croatia. 13–15 September 2021; pp. 5–10. [DOI] [Google Scholar]
- 26.Li X., Peng J., Obaidat M.S., Wu F., Khan M.K., Chen C. A secure three-factor user authentication protocol with forward secrecy for wireless medical sensor network systems. IEEE Syst. J. 2019;14:39–50. doi: 10.1109/JSYST.2019.2899580. [DOI] [Google Scholar]
- 27.Xie Q., Ding Z., Tang W., He D., Tan X. Provable Secure and Lightweight Blockchain-Based V2I Handover Authentication and V2V Broadcast Protocol for VANETs. IEEE Trans. Veh. Technol. 2023;72:15200–15212. doi: 10.1109/TVT.2023.3289175. [DOI] [Google Scholar]
- 28.Son S., Lee J., Park Y., Park Y., Das A.K. Design of Blockchain-Based Lightweight V2I Handover Authentication Protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022;9:1346–1358. doi: 10.1109/TNSE.2022.3142287. [DOI] [Google Scholar]
- 29.Yang A., Weng J., Yang K., Huang C., Shen X. Delegating Authentication to Edge: A Decentralized Authentication Architecture for Vehicular Networks. IEEE Trans. Intell. Transp. Syst. 2022;23:1284–1298. doi: 10.1109/TITS.2020.3024000. [DOI] [Google Scholar]
- 30.Su X., Xu Y., Tong H., Li T. A Cluster-based User Authentication Protocol for Internet of Medical Things Deployment; Proceedings of the 2023 International Conference on Wireless Communications and Signal Processing (WCSP); Hangzhou, China. 2–4 November 2023; pp. 517–522. [Google Scholar]
- 31.Ebrahimi S., Bayat-Sarmadi S. Lightweight fuzzy extractor based on LPN for device and biometric authentication in IoT. IEEE Internet Things J. 2021;8:10706–10713. doi: 10.1109/JIOT.2021.3050555. [DOI] [Google Scholar]
- 32.Dolev D., Yao A. On the security of public key protocols. IEEE Trans. Inf. Theory. 1983;29:198–208. doi: 10.1109/TIT.1983.1056650. [DOI] [Google Scholar]
- 33.Abdalla M., Fouque P.A., Pointcheval D. Password-based authenticated key exchange in the three-party setting; Proceedings of the International Workshop on Public Key Cryptography; Les Diablerets, Switzerland. 23–26 January 2005; Berlin/Heidelberg, Germany: Springer; 2005. pp. 65–84. [Google Scholar]
- 34.Banerjee S., Odelu V., Das A.K., Srinivas J., Kumar N., Chattopadhyay S., Choo K.K.R. A provably secure and lightweight anonymous user authenticated session key exchange scheme for internet of things deployment. IEEE Internet Things J. 2019;6:8739–8752. doi: 10.1109/JIOT.2019.2923373. [DOI] [Google Scholar]
- 35.Das A.K., Wazid M., Kumar N., Vasilakos A.V., Rodrigues J.J. Biometrics-based privacy-preserving user authentication scheme for cloud-based industrial Internet of Things deployment. IEEE Internet Things J. 2018;5:4900–4913. doi: 10.1109/JIOT.2018.2877690. [DOI] [Google Scholar]
- 36.Roy S., Das A.K., Chatterjee S., Kumar N., Chattopadhyay S., Rodrigues J.J. Provably secure fine-grained data access control over multiple cloud servers in mobile cloud computing based healthcare applications. IEEE Trans. Ind. Inform. 2018;15:457–468. doi: 10.1109/TII.2018.2824815. [DOI] [Google Scholar]
- 37.Wang D., Cheng H., Wang P., Huang X., Jian G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017;12:2776–2791. doi: 10.1109/TIFS.2017.2721359. [DOI] [Google Scholar]
- 38.Blanchet B., Smyth B., Cheval V., Sylvestre M. ProVerif 2.00: Automatic cryptographic protocol verifier, user manual and tutorial. [(accessed on 1 November 2024)];Version. 2018 16:5–16. Available online: https://bblanche.gitlabpages.inria.fr/proverif/manual.pdf. [Google Scholar]
- 39.Challa S., Wazid M., Das A.K., Kumar N., Reddy A.G., Yoon E.J., Yoo K.Y. Secure signature-based authenticated key establishment scheme for future IoT applications. IEEE Access. 2017;5:3028–3043. doi: 10.1109/ACCESS.2017.2676119. [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Data are contained within the article.