Abstract
Many modern cryptographic primitives for hashing and (authenticated) encryption make use of constructions that are instantiated with an iterated cryptographic permutation that operates on a fixed-width state consisting of an array of bits. Often, such permutations are the repeated application of a relatively simple round function consisting of a linear layer and a non-linear layer. These constructions do not require that the underlying function is a permutation and they can plausibly be based on a non-invertible transformation. Recently, Grassi proposed the use of non-invertible mappings operating on arrays of digits that are elements of a finite field of odd characteristic for so-called MPC-/FHE-/ZK-friendly symmetric cryptographic primitives. In this work, we consider a mapping that we call that has a simple expression and is based on squaring. We discuss, for the first time, the differential and linear propagation properties of and observe that these follow the same rules up to a relabeling of the digits. This is an intriguing property that, as far as we know, only exists for and the binary mapping that is used in the cryptographic permutation Xoodoo. Moreover, we study the implications of its non-invertibility on differentials with zero output difference and on biases at the output of the mapping and show that they are as small as they can possibly be.
Keywords: Non-linear layer, Squaring, Finite fields
Introduction
The round functions in cryptographic permutations of the type Substitution-Permutation Networks (SPN) consist of a non-linear layer and a linear layer. These layers are chosen and combined so that there is no exploitable differential propagation from input to output or exploitable correlations between input and output when used in the context of a construction like the sponge or duplex construction [1], Farfalle [2] or Even-Mansour [3]. The relevant properties of these mappings over binary fields have been studied extensively, leading to solid designs. However, in the last years there has been a growing interest in similar functions operating on arrays of digits that are elements of a field of odd characteristic. For instance, Kölbl et al. designed a ternary cryptographic hash function called Troika [4]. Other examples are the symmetric primitives defined over like MiMC [5], GMiMC [6], Poseidon [7], Ciminion [8], and many others. These are designed to be efficient in the context of Secure Multi-Party Computation (MPC), Fully Homomorphic Encryption (FHE), and Zero-Knowledge proofs (ZK).
There are interesting differences between fields of characteristic 2 and those of odd characteristic that we will denote by . For instance, addition and subtraction are the same in , but this is not the case in . In , squaring is a linear operation, whereas in squaring is a non-linear operation. In , correlations between input and output bits have values that are rational and range from to 1, but in , correlations are complex numbers inside the closed unit disk.
This work investigates a mapping over that was recently proposed by Grassi [9] and that we call . This is the mapping defined over by for and for all .
The paper is organized as follows. Section 2 deals with commonly used notation and conventions that we follow. In Section 3 we recall the basic notions from differential cryptanalysis. An overview of correlation analysis is presented in Section 4. In Section 5 we apply this existing theory to the squaring transformation and derive its DP and LP values. Based on the squaring transformation, we motivate the choice for in Section 6. The main contribution of this paper lies in Sections 7 and 8, where we study the differential and linear propagation properties of , both in the forward and backward direction. Our results are useful in determining the maximum probabilities of differentials and differential trails over transformations making use of in their round function, as in computer-assisted trail search [10]. Moreover, as the differential and linear propagation properties of follow the same rules, our results are also useful to study the correlations of linear approximations and linear trails. In Section 9 we study the collision probability and bias of linear combinations of output digits of . Finally, we conclude in Section 10.
Notation and conventions
We denote by the finite field of odd characteristic p, i.e., q is equal to for some odd prime p and positive integer . Let be the vector space of dimension n over the finite field . Given two vectors , we denote their vector subtraction by , i.e., . A vector is indexed by the set . We denote its ith coordinate by and call it a digit. The dot product between x and y is defined as . We write for the vector with all digits equal to 0, except for the digit that is indexed by i, which is equal to 1. The linear span of a set of vectors is denoted by . A digit is said to be active if it is non-zero. The Hamming weight of a vector is the number of active digits in the vector.
Let be a complex number. We denote its absolute value as |z|. We write for its complex conjugate.
Let F be a field, then we write for its multiplicative group .
Differential analysis
First published by Biham and Shamir in [11], differential cryptanalysis is a chosen-plaintext attack that exploits the non-uniformity of the distribution of differences at the output of a transformation when it is applied to pairs of inputs with a fixed difference.
Any successful theory of cryptanalysis needs to address the problem of secret key translation. Differential cryptanalysis deals with this problem by considering differences, which are invariant under translation. Let and be inputs of a transformation and let their difference be . Likewise, let and be outputs of and let their difference be . The (ordered) pair containing the input and output difference is called a differential over . The differential (0, 0) is called trivial. The differential probability (DP) of a differential (a, b) over the transformation is defined as
If , we say that a and b are compatible differences over . For compatible differences a and b, we define the weight of a differential (a, b) over as
A non-trivial differential (a, b) over can only lead to a distinguisher if differs significantly from , which is the expected DP of any non-trivial differential over a randomly selected transformation of .
Correlation analysis
Correlation analysis of cryptographic primitives effectively is Fourier analysis on finite abelian groups. As such, the theory is well-understood and this section serves as a recap. The ideas that we present here are based on the works of Daemen [12], Baignères et al. [13], and Daemen and Rijmen [14]. Many of the proofs can be found in the book by Hou [15].
Characters
Let be a finite abelian group and let e be the (finite) exponent of G, i.e., the smallest integer n such that for all .
A character of G is a homomorphism from G into the subgroup of consisting of the eth roots of unity. The set of characters of G is denoted by and it forms a group under the multiplication defined by for all and . The groups G and are isomorphic, but this isomorphism is not canonical.
For a fixed isomorphism between G and and for each , we write for the image of a under this isomorphism. In particular, the character that is defined by for all is called the trivial character and it is the identity element of the group .
Now, let be the commutative ring that is obtained by introducing a multiplicative structure on G. This is always possible by the fundamental theorem of finite abelian groups. A character is called a generating character for G if for all . If a commutative ring has a generating character for its additive group, then . In the case that G is the direct sum of n copies of a commutative ring R and if R has a generating character, say , then we obtain a generating character for G by setting . It holds that , where the multiplication in G is defined component-wise.
As an example, consider G equal to and put . Let be the absolute trace function that is defined by . This is a linear mapping. Each defines a generating character for that is defined by
As a second example, consider G equal to , which is a direct sum of n copies of . Hence, each gives a generating character for that is defined by
The Fourier transform
Consider the set of functions . Fix an ordering of the elements of G, e.g., . We write for the finite sequence of the output values of f. By identifying a function f with the vector , can be seen as a finite-dimensional complex inner product space with inner product
For any , the inner product induces a norm by setting
The standard basis of is formed by the set of Dirac delta functions , which are defined by
In the context of correlation analysis, the solution to the problem of secret key translation lies in changing the basis of to the set of characters of G. For any , the corresponding characters satisfy . By normalizing the characters, we obtain an orthonormal basis
where . By projecting f onto , we find that
The operator that is defined by for all is called the Fourier transform. By identifying a function f with , the Fourier transform is best described as assigning to f its coordinates in the normalized character basis. The Plancherel theorem asserts that the Fourier transform is unitary, i.e., we have
Let us return to the question of how to address the problem of secret key translation. Let . We define the translation operator by for all . Moreover, we define the modulation operator by for all . The big insight is that translation turns into modulation when changing from the standard basis to the normalized character basis, i.e.,
Let H be a finite abelian group and let be a mapping between G and H. We want a representation of F in . To that end, let be any character of H. We take as representation the function .
Correlation
We now specialize to the case that G and H are each equal to the vector space over the finite field .
Let be a transformation of . We consider pairs that we call linear approximations of . We refer to u as the output mask and to v as the input mask. The linear approximation (0, 0) is called trivial. The correlation of the linear approximation is defined as
We call the masks u and v compatible over if is nonzero. In general, correlations are complex numbers. The linear potential (LP) is a real number and related to a correlation by
If u and v are compatible over , then we can define the weight of the linear approximation (u, v) as
The squaring transformation
The squaring transformation is defined by for all . Because we study the case of odd characteristic, is non-linear. We show that has the property that the maximal DP over all non-trivial differentials is , which is the smallest possible value. A similar property holds for the maximal LP over all non-trivial linear approximations. In other words, we show that is a bent polynomial [16]. Note that this is an improvement from the case of characteristic 2, for which these values are both equal to and are obtained by, respectively, almost perfect nonlinear and bent functions [17].
First, by applying Theorem 5.33 from [18], we obtain that the correlation of any linear approximation with of is equal to
where if u is a square in and otherwise. It follows that for all with we have . In particular, choosing v equal to zero shows that any linear combination of output digits of is imbalanced, i.e., the distribution of this linear combination is non-uniform. If u is 0, then for all nonzero we have , and .
Second, consider the equation that relates the input , the input difference , and the output difference , i.e.,
Assuming that and because the characteristic of is odd, we can solve for x to find that . Hence, there is exactly one solution to this equation. Dividing by the domain size, q, then shows that . In particular, any nonzero input difference can propagate to a zero output difference. If a is 0, then for all nonzero , we have and .
We summarize these properties to make the symmetry between the differential and linear case apparent:
For all and , we have ;
For all , we have ;
We have .
The mapping
Some modern block cipher modes, like GCM [19], CTR and OFB [20], do not use the inverse block cipher. Similarly, constructions like sponge [21], duplex [1], and Farfalle [2], which are generally based on permutations, do not use their inverse. Therefore, in such constructions permutations can be replaced by transformations. An example is the GLUON family of lightweight hash functions [22], which makes use of the sponge construction on top of a non-invertible map.
A cryptographic transformation can be used as long as collisions and imbalances in the output cannot be exploited. This can be tackled by either ensuring that such imbalance is very small or by limiting the attacker’s access to the input and output of the transformation by construction. For instance, in the sponge and duplex constructions the attacker has control of only the outer part of the state and not of its inner part. Therefore, if a collision requires a difference in the inner part of the state at the input of the transformation, the attacker cannot inject it with input messages. Similarly, the attacker has no visibility of the inner bits or digits of any output mask. As another example, whitening keys can be added at input and output, like in Farfalle [2], Even-Mansour [3], and Elephant [23].
We consider the problem of building a non-invertible mapping based on squaring that can be used as non-linear layer in the round function of cryptographic transformations. When such transformations are used in constructions that are usually instantiated with permutations, the non-invertibility of the mapping should be difficult to exploit.
By definition, such a non-linear layer has pairs of distinct inputs that are mapped to the same output, i.e., collisions. A naive idea would be to apply to each digit of the state independently. The problem with this approach is that each collision for is trivially extended to a collision for the entire non-linear layer, giving rise to differentials with as high as . They are easy to exploit as the adversary needs access to only a single input digit to generate a local collision. Similarly, any bias in the output of is trivially present in the output of the non-linear layer, giving rise to linear approximations with as high as . They are easy to exploit as the adversary needs access to only a single output digit to exploit them. The measure of both is inversely proportional to the order of the field. Hence, unless the order of the field is very large, this leads to unacceptable weaknesses in the cryptographic transformation.
Compared to the above, the non-linear layer in the round function of a cryptographic transformation should have lower and and there should not exist local properties that can be extended to global properties. We achieve this by making the of differentials of the form (a, 0) and the of linear approximations of the form (u, 0) small, i.e., equal to the inverse of the domain size. Moreover, any differential over or linear approximation of the non-linear layer requires access to every digit of the state.
The work by Grassi [9] presents an analysis of a number of mappings based on that minimize the probability of a collision in their output. We consider one of these mappings and call it . Concretely, the mapping is defined, for all , by
The remainder of this text is concerned with an analysis of the differential and linear propagation properties of .
Differential propagation properties of
Let be a differential over and let be an input of . The equations that relate the input difference a and the output difference b are of the form
| 1 |
We consider two cases in the analysis of these equations. In the first case, we fix the input difference a and give a description of the set of compatible output differences b. From this, we are able to deduce that depends only on a and whether b is compatible with a or not.
In the second, reverse case, we fix the output difference b and present an algorithm for the computation of the set of compatible input differences a. We then derive an expression of the so-called minimum reverse weight of this set. All these results can be directly applied to perform computer-aided trail search, as described in [10], in cryptographic transformations instantiated with as the non-linear layer.
Forward propagation from a given input difference
We observe that for an input difference a, the equations of (1) are linear in the digits of x. We make this explicit by writing them as a matrix equation of the form
Hence, the set of compatible output vectors b, which we denote by , forms an affine subspace of . By affine subspace we mean the following. Let W be a linear subspace of and let . The coset is called an affine subspace of and u is called an offset. The affine subspace can be described by
Two cosets and are equal if and only if . Therefore, we may add any linear combination of the basis vectors to the offset without it changing the affine subspace that is defined. Moreover, we may scale the basis vectors by any nonzero constant. Hence, a description of in which the offset has minimal Hamming weight is given by
where
Clearly, the dimension of , which is defined as the dimension of the associated vector space, is equal to the Hamming weight of a.
We are now ready to give a complete characterization of the distribution of differentials over .
Proposition 1
Let be a differential over . Then b is compatible with a, i.e., , if and only if, for all , we have or , in which case can take on any value. Hence,
In other words, the DP of a valid differential, and thus its differential weight, is a constant that depends only on the input difference.
Backward propagation from a given output difference
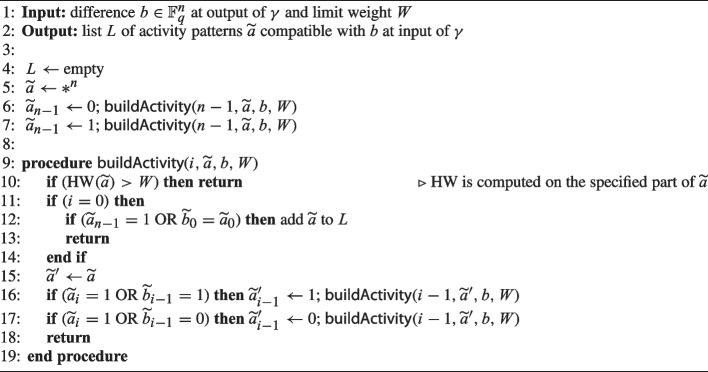
For a given output difference b, the compatible input differences do not form an affine space. However, we will show in this section how to efficiently generate all compatible input differences a with for some weight limit W. To this end, we introduce the concept of compatible activity pattern. Given a vector , its activity pattern is a vector in with equal to 1 if and 0 otherwise.
Definition 1
An activity pattern is compatible with b if there exists an input difference a that is compatible with b and for which equals this activity pattern.
The generation of all compatible input differences is done in two phases: in the first phase, we generate the set of activity patterns compatible with b, and in the second phase, we determine for each compatible activity pattern the set of compatible input differences with that pattern.
We generate the compatible activity patterns in a recursive way in Algorithm 1, making use of the following proposition.
Proposition 2
Given a differential (a, b) over , the following properties hold:
if and then ;
if and then .
Proof
The two properties immediately follow from (1). We have
and implies .
In Algorithm 1, we start with an empty list of compatible activity patterns L (line 4) and a fully unspecified activity pattern (line 6). Then we specify whether (line 6) or 1 (line 7) (and thus whether is active or not) and based on this we incrementally determine the activity of all other digits from to using the procedure . In this procedure, when we use Proposition 2 to determine whether or 0, otherwise we consider both possibilities (lines 16 and 17). When a compatible activity pattern is fully determined (i.e., when is reached) then it is added to list L (line 12).
Algorithm 1.
Generation of input activity patterns compatible with output difference b.
Given an output difference b and a compatible input activity pattern , we generate all compatible differences with activity in Algorithm 2, making use of the following proposition.
Proposition 3
Given a differential (a, b) over , the following properties hold:
if , then ;
if and , then ;
if and , then can be any value in .
Proof
The first property follows from the definition of activity pattern. The other two properties immediately follow from (1).
In Algorithm 2, we start with an empty list of compatible input differences L (line 4) and a fully unspecified difference a (line 5). We use the symbol when the activity of a digit is unspecified. Then we incrementally determine the value of all digits from to using the procedure . In this procedure, we use Proposition 3 to determine whether or 0 (lines 10-12 and 16-18). When a compatible difference is fully determined (i.e., when is reached) then it is added to list L (line 10-12).
Algorithm 2.
Generation of input differences compatible with output difference b and with activity pattern .
Computing the minimum reverse weight of an output difference
Given an output difference b, let be the set of input differences that are compatible with b. The differentials (a, b) over with can have different weights. Following [10], the minimum reverse weight of an output difference b is defined by
We notice that the minimum reverse weight of a difference b at the output of is fully determined by its activity pattern and its compatible activity patterns with minimum Hamming weight. In particular, it can be computed as in the following Proposition, which uses the notion of run.
Definition 2
Given , a run of length in x is a sequence of active digits preceded and followed by non-active digits, i.e., it satisfies and for some .
Proposition 4
Given a difference b at the output of composed by m runs of lengths , with , then
Proof
For a run starting in position i and of length in b, the digit must be 1. There can be at most a single zero digit in between two active digits in the sequence . It follows that for each run of length in b, a has at least active digits if is even and if is odd.
Linear propagation properties of
In this section we analyze the correlation properties of the mapping , starting with the correlation of linear approximations of .
Proposition 5
Let be a linear approximation of . We have
Proof
If we rewrite the correlation of a linear approximation of , we obtain
The resulting product from Proposition 5 is non-zero if each of the factors is non-zero. Note that the correlation is non-zero if is non-zero, as was discussed in Section 5. Additionally, if is non-zero, then has to be equal to zero to get a non-zero correlation. In this case it should thus hold that . From this reasoning, we can give a complete characterization of the distribution of linear approximations of .
Proposition 6
Let be a linear approximation of . Then u is compatible with v, if and only if, for all , we have or , in which case can take on any value. Hence,
Observe that Propositions 1 and 6 are very much alike. Indeed, propagation of differences and propagation of masks over follow similar rules. First, output masks play the role of input differences and input masks that of output differences. Second, indices are reversed, i.e., index i in a mask corresponds to index in a difference, to account for this change in direction. The following proposition is an immediate consequence.
Proposition 7
Let be the mapping defined by . Let (u, v) be a linear approximation of . We have
From this, it follows that we can extend the results obtained in Section 7 to masks. For a given output mask , we can build the affine subspace with dimension of compatible input masks over as in Section 7.1. Moreover, for a given input mask , the output activity patterns compatible with input masks over can be found by applying Algorithm 1. Using the resulting activity pattern and the input mask v, all compatible output masks u can be obtained as described in Algorithm 2. Note that there can be several compatible output masks u for a given input mask v. Among them, there will be one realizing the minimum value of . The minimum reverse weight of v is defined as
and is determined by the decomposition of v in a sequence of runs, as explained in Section 7.3.
On collision probability and bias
A collision in the output of occurs when maps a pair of different inputs to the same output value. Assuming randomly and uniformly selected pairs of inputs, the probability of a collision is given by
Translating this into the language of differential analysis, we find that
Proposition 8
Let . If (a, 0) is a differential with , then all digits of a are active and .
Proof
Let be such that . The input difference a is compatible with the output difference 0 if the latter is contained in the affine space A(a). This is the case if and only if for . Hence, by Proposition 1.
Clearly, there are input differences a for which this property holds. Therefore, we find that
Now, the collision probability of a function that is chosen randomly from the set of functions from to is equal to . Hence, the ratio between the collision probability of and that of a random function is equal to . If the order of the field is large, then this quantity approximates 1.
By symmetry, we obtain a similar result for the bias of any linear combination of output digits of .
Proposition 9
Let . If (u, 0) is a linear approximation with , then all digits of u are active and .
Clearly, if either q or n is large, then these quantities are very small and it becomes difficult to exploit them in practice.
Conclusion
When searching for trails over an iterated cryptographic transformation as described in [10], a number of tools are required. These include an efficient method to compute the minimum reverse weight of a given difference (resp. mask), and an efficient method to build all compatible input differences (resp. output masks) over the non-linear layer for a given output difference (resp. input mask) and vice versa. In this work we provided such tools for a mapping based on squaring that can be used as non-linear layer in the construction of cryptographic transformations of . Interestingly, it turns out that for this mapping, masks and differences follow the same propagation rules. This means that for a cryptographic transformation that uses this mapping as the non-linear layer in its round function, one would need to only perform either differential or linear trail search while obtaining insights and bounds for both.
Acknowledgements
Joan Daemen and Daniël Kuijsters are supported by the European Research Council under the ERC advanced grant agreement under grant ERC-2017-ADG Nr. 788980 ESCADA.
Silvia Mella is supported by the European Commission through the ERC Starting Grant 805031 (EPOQUE).
Footnotes
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Bertoni, G., Daemen, J., Peeters, M., Assche, G.V.: Duplexing the sponge: singlepass authenticated encryption and other applications. Cryptology ePrint archive, paper 2011/499. (2011) https://eprint.iacr.org/2011/499
- 2.Bertoni, G., Daemen, J., Hoffert, S., Peeters, M., Assche, G.V., Keer, R.V.: Farfalle: parallel permutation-based cryptography. IACR Trans. Symmetric Cryptol. 2017(4), 1–38 (2017) [Google Scholar]
- 3.Even, S., Mansour, Y.: A construction of a cipher from a single pseudorandom permutation. J. Cryptol. 10(3), 151–162 (1997). 10.1007/S001459900025 [Google Scholar]
- 4.Kölbl, S., Tischhauser, E., Derbez, P., Bogdanov, A.: Troika: a ternary cryptographic hash function. Des. Codes Crypt. 88(1), 91–117 (2019). 10.1007/s10623-019-00673-2 [Google Scholar]
- 5.Albrecht, M.R., Grassi, L., Rechberger, C., Roy, A., Tiessen, T.: MiMC: efficient encryption and cryptographic hashing with minimal multiplicative complexity. Advances in cryptology - ASIACRYPT (2016)
- 6.Albrecht, M.R., Grassi, L., Perrin, L., Ramacher, S., Rechberger, C., Rotaru, D., Roy, A., Schofnegger, M.: Feistel structures for MPC, and more. Computer security - ESORICS (2019)
- 7.Grassi, L., Khovratovich, D., Rechberger, C., Roy, A., Schofnegger, M.: Poseidon: a new hash function for zero-knowledge proof systems. 30th USENIX security symposium (2021)
- 8.Dobraunig, C., Grassi, L., Guinet, A., Kuijsters, D.: Ciminion: symmetric encryption based on toffoli-gates over large finite fields. Advances in cryptology - EUROCRYPT (2021)
- 9.Grassi, L.: Bounded surjective quadratic functions over fnp for mpc-/zk-/fhefriendly symmetric primitives. IACR Trans. Symmetric Cryptol. 2023(2), 94–131 (2023) 10.46586/TOSC.V2023.I2.94-131
- 10.Daemen, J., Assche, G.V.: Differential propagation analysis of keccak. In: Canteaut, A. (ed.) Fast Software Encryption - 19th International Workshop, FSE 2012, Washington, DC, USA, March 19-21, 2012. Revised Selected Papers. Lecture Notes in Computer Science, vol. 7549, pp. 422–441. Springer, Berlin, Heidelberg (2012). 10.1007/978-3-642-34047-5_24
- 11.Biham, E., Shamir, A.: Differential cryptanalysis of des-like cryptosystems. In: Menezes, A., Vanstone, S.A. (eds.) Advances in Cryptology - CRYPTO ’90, 10th Annual International Cryptology Conference, Santa Barbara, California, USA, august 11-15, 1990, Proceedings. Lecture Notes in Computer Science, vol. 537, pp. 2–21. Springer, Berlin, Heidelberg (1990). 10.1007/3-540-38424-3_1
- 12.Daemen, J., Govaerts, R., Vandewalle, J.: Correlation matrices. In: Preneel, B. (ed.) Fast Software Encryption: Second International Workshop. Leuven, Belgium, 14-16 December 1994, Proceedings. Lecture Notes in Computer Science, vol. 1008, pp. 275–285. Springer, Berlin, Heidelberg (1994) 10.1007/3-540-60590-8_21
- 13.Baignères, T., Stern, J., Vaudenay, S.: Linear cryptanalysis of non binary ciphers. In: Adams, C., Miri, A., Wiener, M. (eds.) Selected Areas in Cryptography, pp. 184–211. Springer, Heidelberg, Germany (2007). 10.1007/978-3-540-77360-3_13
- 14.Daemen, J., Rijmen, V.: Correlation Analysis in GF(2n). In: the design of rijndael: the advanced encryption standard (AES), pp. 181–194. Springer, Heidelberg, Germany (2020). 10.1007/978-3-662-60769-5_12
- 15.Hou, X.-d.: Lectures on Finite Fields. American Mathematical Society, Providence, Rhode Island. Series: Graduate Studies in Mathematics, vol. 190 (2018)
- 16.Coulter, R.S., Matthews, R.W.: Bent polynomials over finite fields. Bull. Aust. Math. Soc. 56(3), 429–437 (1997). 10.1017/S000497270003121X [Google Scholar]
- 17.Carlet, C. (ed.): Boolean Functions for Cryptography and Coding Theory. Cambridge University Press, UK (2020). 10.1017/9781108606806
- 18.Lidl, R., Niederreiter, H.: Finite Fields vol. 20, 2nd edn. Cambridge University Press, Cambridge, United Kingdom (1997)
- 19.Standards, N.I., Technology: NIST SP 800-38D Recommendation for Block Cipher Modes of Operation: Galois/Counter Mode (GCM) and GMAC (November 2007). https://csrc.nist.gov/pubs/sp/800/38/d/final
- 20.Standards, N.I., Technology: NIST SP 800-38A Recommendation for Block Cipher Modes of Operation: Methods and Techniques (November 2007). https://csrc.nist.gov/pubs/sp/800/38/a/final
- 21.Bertoni, G., Daemen, J., Peeters, M., Assche, G.V.: On the indifferentiability of the sponge construction. In: Smart, N.P. (ed.) Advances in Cryptology - EUROCRYPT 2008, 27th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Istanbul, Turkey, April 13- 17, 2008. Proceedings. Lecture Notes in Computer Science, vol. 4965, pp. 181–197. Springer, Berlin, Heidelberg (2008). 10.1007/978-3-540-78967-3_11
- 22.Berger, T.P., D’Hayer, J., Marquet, K., Minier, M., Thomas, G.: The GLUON family: a lightweight hash function family based on fcsrs. In: Mitrokotsa, A., Vaudenay, S. (eds.) Progress in Cryptology - AFRICACRYPT 2012 - 5th International Conference on Cryptology in Africa, Ifrance, Morocco, July 10- 12, 2012. Proceedings. Lecture Notes in Computer Science, vol. 7374, pp. 306–323. Springer, Berlin, Heidelberg (2012). 10.1007/978-3-642-31410-0_19
- 23.Beyne, T., Chen, Y.L., Dobraunig, C., Mennink, B.: Dumbo, jumbo, and delirium: parallel authenticated encryption for the lightweight circus. IACR Trans. Symmetric Cryptol. 2020(S1), 5–30 (2020) 10.13154/TOSC.V2020.IS1.5-30