Abstract
Security is one of the increasingly significant issues given advancements in technology that harness data from multiple devices such as the internet of medical devices. While protecting data from unauthorized user access, several techniques are used including fingerprints, passwords, and others. One of the techniques that has attracted much attention is the use of human features, which has proven to be most effective because of the difficulties in impersonating human-related features. An example of a human-related attribute includes the electrical signal generated from the heart, mostly referred to as an Electrocardiogram (ECG) signal. The methods to extract features from ECG signals are time domain-based; however, the challenge with relying only on the time-domain or frequency-domain method is the inability to capture the intra-leading relationship of Variational Mode Decomposition signals. In this research, fusing multiple domains ECG feature and adaptive Variational Mode Decomposition approaches are utilized to mitigate the challenge of losing the intra-leading correlations of mode decompositions, which might reduce the robustness of encryption algorithms. The features extracted using the reconstructed signal have a mean (0.0004), standard deviation (0.0391), skewness (0.1562), and kurtosis (1.2205). Among the lightweight encryption methods considered, Chacha20 has a total execution time of 27µs. The study proposes a lightweight encryption technique based on the fused vector representation of extracted features to provide an encryption scheme in addition to a bio-inspired key generation technique for data encryption.
Keywords: time-domain feature extraction, lightweight encryption, adaptive variational mode decomposition, ECG feature extraction, bio-inspired key generation
1. Introduction
Feature extraction is one of the topical issues in medical diagnosing. In order to have a proper diagnosis, one needs to understand the nature of feature extraction and its role in determining a diagnosis. The typical features used in a medical diagnosis include an Electroencephalogram or Electrocardiogram; while many techniques have been applied to feature extraction in the context of an Electrocardiogram (ECG), the effectiveness of these techniques has constantly been enhanced. Research has proven that using human features to create an encryption algorithm provides a much stronger approach notwithstanding the anticipated challenge it may have. Nonetheless, human biometric information are a promising alternative for cryptographic key generation to the traditional use of passwords as cryptographic keys. Cryptographic keys generated from biometrics are difficult to forge and thus expand the frontiers of research into the use of different biometric key generation approaches. Keys can be extracted from biometric features, in raw ECG signals, which can be reliable despite the noise in ECG signals or abnormalities [1]. ECG-based biometric systems are much more reliable than other present biometric systems, e.g., fingerprints [2]. Furthermore, the widespread adoption of ECG technology in some clinical or hospital facilities and the ease of deploying ECG sensors in consumer settings in wearable devices [3] makes ECG signal encryption more imperative. Security-related application domains, when equipped with ECG signal encryption, provide many strong features to secure data on devices.
Currently, most Internet of Things (IoT) devices are championing the use of human features in encrypting data from medical devices. These IoT devices used in the context of medical diagnosing are so small that using traditional encryption algorithms on these devices may require more energy for computation [4]. Though most consider the use of a cloud computing framework to provide the needed encryption, it also requires that devices are constantly connected to the internet for data encryption [5]. The efficiency and security for privacy are often very distinct leading to the proposition of an image privacy protection scheme that ensures high-quality reconstruction using the discrete cosine transform compression and nonlinear dynamics [6]. When IoT devices use ECG signals for feature extraction, then the amplitude and intervals are used, which are further processed [7]. Here, it is the case that IoT devices are used to capture and monitor ECG features. It is very common these days to have wearable ECG devices attached to the human skin to continuously monitor ECG signals. This development demonstrates how IoT devices have evolved. Again, it is common to have IoT devices and smart watches equipped with ECG sensors to monitor a person’s heartbeat. The integration of IoT in these areas suggests easy-to-collect ECG features; however, the challenge is the computation algorithm to ensure encryption using ECG features. Therefore, crafting any algorithm based on an ECG signal should be very lightweight. One of the key phases in the integration of IoT with ECG is the security of data being transmitted.
Feature extraction in the context of an ECG requires the identification and analysis of features in ECG data. When dealing with ECG feature extraction, the amplitude and intervals are very time-dependent. Thus, time-domain feature extraction may have to deal with the intra-leading relationship within the sequence of multiple ECG signals from the same person. Mostly, statistical and machine learning techniques play a leading role in analyzing these intra-leading correlations and thus model accuracy in analyzing these is imperative. Again, these intra-leading relationships are key for a comprehensive understanding of the heart’s electrical activity and for making accurate diagnoses based on ECG data. One will expect that while these electrical activities are happening, the approach to encrypting these data should be robust, taking into account the intra-leading correlations. This research seeks to develop a lightweight encryption algorithm that considers these intra-leading relationships using a time-domain feature, frequency-time domain, and adaptive variational model decomposition-based technique. Existing cryptographic schemes are complex, such that the key generation consumes a large computation time and a large amount of energy [8]; thus, encryption schemes need a suitable lightweight approach to encryption. Thus, this study contributes to the introduction bio-inspired algorithm based on the Kestrel-based search algorithm as it randomizes searching with its half-life component, which adds layers of randomization for a more secure key generation for encryption. The advantage of the Kestrel-based approach is the ease of formulation, which does not add more computational cost in the search for an optimal key.
The remainder section is organized as follows: Section 2 (literature review), Section 3 (methods and materials), Section 4 (results), Section 5 (discussion), and the conclusion in Section 6.
2. Literature Review
This section focused on reviewing articles on multiple domain feature extraction techniques and also lightweight encryption mechanisms. The review is necessary to know what has been performed and the gap that needs to be filled through our research. These sections are aligned with the research topic, thus helping the crystallization of articles along the thematic domains.
2.1. Model-Based and Multi-Fusion Domain Bio-Signals Techniques
ECG signals are electrical impulses generated by the heart’s activity, and these signals are recorded in series of waves (P, Q, R, S, T), representing the varied phases of the electrical activities of the heart’s cycle from its starts (P wave) to the end of the sequence (T wave). The intermediate waves are the time to transition from one wave to another wave. Thus, the regular and timing features are very relevant in diagnosing any heart-related condition. In this regard, the ECG is very crucial in diagnosing heart-related issues. To capture these electrical activities, electrodes are placed on the skin of an individual and then the waves are monitored, which helps to differentiate people based on these waves [2].
The time-domain approach quantifies changes in ECG signal over time. Among the time domain features include average heart rate variations, R-R intervals, and Shannon entropy [9,10].
Zhao, Li [11] segmented and extracted ECG features into a time-domain matrix. Then, the periodic signal was transformed into a wavelet to output the frequency domain features in the matrix structure. Furthermore, a nature-inspired algorithm such as particle swarm optimization (PSO) was utilized to fine-tune parameters to optimize the extraction of ECG features. To address the accuracy of ECG feature identification from different domains, such as time, frequency, or time–frequency; the multi-feature fusion method was proposed, which combined Variational Mode Decomposition (VMD) and the Convolutional Neural Network (CNN) [12]. On one hand, the VMD technique was used for feature decomposition while the CNN was used to extract feature information from the ECG signal. Furthermore, the features extracted were weighted and fused for ECG signal recognition. Machine learning models have been leveraged for ECG feature extraction to help in cardiac evaluation and treatment decisions [13]. It has been indicated that ECG signals are time domain-reliant, leading to the conversion to spectrogram signals using a Short-Time Fourier Transform (STFT) [14]. Thus, different signals of heartbeat were segregated into a deep learning model for training. While using an open dataset, the six best P-QRS-T fragments were extracted based on priority and the normalization of positions using the non-fiducial symlets and non-fiducial daubechies [15]. Unfortunately, the accurate identification of fiducial points is a very challenging task in ECG signals if not well addressed: it can degrade the performance of the ECG-based biometrics [16]. This leads to the proposition of a framework based on ECG signal for user authentication, which does not need the detection of fiducial points. This framework utilized data-adaptive Variational Model Decomposition for noise removal and feature extraction from the ECG signal. Pradhan, Neelappu [17] suggested that mode decomposition approaches (e.g., empirical mode decomposition) are effective in signal analysis.
Physiological signals can be linked to emotions because both provide unconscious responses, suggesting that ECG features can help recognize people’s emotions, which can influence their physiological responses at any given time [18]. The ubiquity of wearable ECG devices helps to recognize people’s emotions; however, there are high chances of ECG signal contamination, which is caused by motion artifacts, thus leading to a decline in distinguishing ECG features [19]. The feature extraction algorithm for coronary heart disease detection using photoplethysmography used three algorithms that are respiratory rate (RR) interval, HRV Features, and Time Domain Features [20]. A photoplethysmograph (PPG) is a biomedical signal capable of detecting blood volume changes in the microvascular bed of tissues [21]. Myocardial infarction, also known as heart attack, was detected using 21 time-domain features that are extracted from 12-lead ECG signals [22]. Gender classification based on ECG signals has also been proposed using time and frequency domain features [23]. The Time Multiplexed Fast Fourier Transform (TMFFT) approach was used to extract features for categorization into the frequency domain for Arrhythmia classification [24]. An Electrocardiogram (ECG) is broadly utilized for monitoring and diagnosing cardiac arrhythmia, which is an irregularity of the heartbeat that can potentially cause difficulties that create an instantaneous life risk [25]. In this regard, the Selective Opposition (SO)-based Artificial Rabbits Optimization (SOARO) strategy was applied to extract different features on time, time–frequency, entropy, and nonlinearity features of ECG [25]. In the context of the Autism Spectrum Disorders screening method, an acoustic method was employed in speech processing, where the acoustic features are constructed based on time–frequency domain independent component analysis (TF-ICA). In this approach, three methods used are, firstly extracting and combining the rows of the unmixing matrix of each frequency point to build the feature vector; secondly, entailing the separation of results on each frequency point as a time–frequency feature; and lastly, entailing the extraction of time-domain features from the outputs of TF-ICA [26]. When time-domain (TD) and frequency–time-domain (TFD) features are used together in a movement classification, it improves efficiency [27]. The Singh and Krishnan [28] approach leads to the extraction of the time domain, frequency domain, and time–frequency domain features in addition to the use of decomposition and sparse domain for ECG signal processing.
In the context of person identification, different EEG features like time domain, frequency domain, and time–frequency domain features were extracted and fused, in which a supervised learning approach was applied and evaluated in terms of accuracy rate, specificity, sensitivity, and F-score, and it was determined that the fusing method is efficient for user authentication [29].
Deep learning models such as the spatiotemporal deep learning technique have been applied to learn time-domain features, which are extracted into a matrix structure [30]. Furthermore, Khushaba, Phinyomark [31] proposed a simple time-domain feature extraction technique that leverages the capability of waveform length, zero crossings, and root mean squared to capture the relation between any number of channels.
In some instances, multiple domain feature extraction approaches were used combined with ensemble machine learning methods for classification and prediction [32]. Wavelet packet transform (WPT) and Short-Timed Fourier Transform (STFT) approaches were used to extract features from EEG signals. It has been indicated that using a single feature does not yield better performance compared to the fusion of multiple features [33]. In these regards, model-based approaches have been applied for both ECG and EEG feature extraction, and examples of such models include CNN and supervised learning. Again, fusing multiple different ECG features can provide an effective way to develop an encryption algorithm for the Internet of Medical Things. The feature normalization approach proposed used a binary classifier based on a support vector machine to classify features for high classification accuracy [34].
2.2. Lightweight Encryption Mechanisms
The unique properties of ECGs described in the previous section demonstrate the reason why it is preferred for user identification rather than the use of more traditional methods, such as passwords, etc. [35]. This section mainly focuses on the encryption mechanism.
Hash function and DNA cryptography were used to implement the Triple Data Encryption Standard (Triple-DES) that combines Hash function and DNA cryptography to encrypt different bio-signals into the DNA format. Mathivanan, Ganesh [36] proposed a system to convert ECG signals into QR codes. Additionally, Karthikeyan and Martin Leo Manickam [37] introduced a secret key generation algorithm extracted from the parameters of the ECG signal to allow device authentication. A reversible bio-signal steganography method was applied using the Extended Binary Golay Code based on the error correction method [38].
A wavelet-based 128-bit key generator using the uniqueness and quasi-stationary biometric behavior of ECG signals of individuals was proposed: there were two stages: key generator on enroll and verify and another on key determination with an algorithm [39]. Many encryption algorithms that rely on the key size of the 256-bit key have also been proposed, which include the Chacha20 encryption scheme [40]. This scheme encrypts data a byte at a time leading to the generation of stream cipher for data encryption [41].
Heartbeat-based Random Binary Sequences (RBSs) that generate 128-bit RBSs using inter-pulse intervals (IPIs) of heartbeats incorporate a finite monotonic increasing sequence generation mechanism of IPIs and a cyclic block encoding procedure that extracts a high number of entropic bits from each IPI [42].
The generation of a security key using the R-R interval feature of ECG signals as an input for verification and identification occurs by generating a security key corresponding to an individual. The system comprises two independent stages: registration and authentication. The biometric security key, created in the registration stage, was generated using Hamming Distance and the extended version of the triple DES algorithm. Biometric security key generation, verification, authentication, and performance of the biometric security key have been assessed using the R-R interval of ECG signals taken from the standard MIT-BIH database [43]. The simulation results for 64-bit, 128-bit, and 256-bit biometric security keys indicate that the performance of the proposed biometric security key is reasonably good for a security system.
An energy-efficient and computationally less complex authentication technique for BSN, which is a biometric-based algorithm, is proposed, which utilizes Heart Rate Variability (HRV) for a simple key generation process. The proposed algorithm is compared with three data authentication techniques, namely Physiological Signal Key Agreement (PSKA), Data Encryption Standard (DES), and Rivest Shamir Adleman (RSA). The results suggest that the proposed algorithm is quite efficient in terms of transmission time utilization, average remaining energy, and total power consumption [8]. The RSA encryption algorithm is utilized to encrypt an ECG signal; however, the RSA algorithm only performs one operation on encrypted data, which can either be addition or multiplication [44].
Generation of the fly without requiring the key pre-distribution solutions approach was proposed involving two different Interpulse Interval (IPI) features of ECG-based cryptographic key generation. The first approach is realized by using a pseudo-random number and consecutive IPI sequences. The second approach is realized by utilizing the Advanced Encryption Standard (AES) algorithm and IPI as the seed generator for the AES algorithm [45].
Due to intra-individual variability, bio-crypto keys (bio-keys), in the context of wearable devices, based on Electrocardiograms (ECGs), were proposed for flexibility and convenience to use bio-key using ECGs. This approach minimizes biosignal variability using normalization, clustering-based binarization, and the fuzzy extractor, enabling the generation of personalized seeds and offering ease of use with the accuracy of authentication [46].
Moosavi, Nigussie [45] combined two different bio-signals, such as ECG and EMG, to generate keys in cryptographic systems by initially using a “pseudo-random number” and consecutive IPI sequences, then followed by the use of an “Advanced Encryption Standard” (AES) algorithm and IPI as a seed generator for the AES algorithm. The advantage of this approach is that it avoids pre-key distribution and ensures ease of key generation. Karthikeyan and Manickam [47] proposed an authentication model for a low resource-constrained architecture where a secret key is generated from the ECG signal parameter and combined with the Secure Force (SF) algorithm in a wireless network.
The generation of a persistent key from an ECG signal to ensure symmetric encryption of data in a time-invariant key has been considered in [48]. Similarly, a time-invariant cryptographic key generation mechanism based on electroencephalogram (EEG) signals has also been proposed [49]. A key generation approach that uses a wavelet-based 128-bit key generator from ECG signals was proposed, which comprises two independent steps, that is, enrollment and verification generation [39].
The ECG signal is distinct to an individual such that it is very difficult to emulate; therefore, securing these features of ECG so that only an authenticated person can assess these signals for diagnosis purposes is imperative [50]. Furthermore, the processing of the ECG signal was achieved with the QRS complex method, which shows the heart rates (HR) that can be visually seen and traced; thus, it is easy to encrypt the visual part of ECG tracing.
ECG signals are used for identification because it varies between individuals [51]. From a diagnostic perspective, individuals who have a background of heart-related issues and have a long record of ECG require a large amount of storage space [52]. Pan and Tompkin’s algorithm helps in the detection of ECG signal [52]. In these regards, selecting the optimal key parameter is significant for an encryption algorithm and this optimization was achieved using the glow-worm swarm optimization method for encryption [5]. Thus, this suggests that a nature-inspired optimization algorithm can play a role in key generation for an encryption algorithm. ECG encryption technique relies on DNA layers and AES to reduce the encryption execution time and improve security for IoT health applications [53]. Methods to extract ECG features include the Lyapunov exponent‘s spectrum in which the extracted features are used as a secret key to encrypt pictures and text messages [54].
3. Materials and Methods
The method and material section outlines the stages to preprocess ECG signals, extract features, normalize features, generate the feature vector, conduct a statistical analysis on the feature vector including zero crossing, and then save the final feature vector. Developing an encryption algorithm using ECG (Electrocardiogram) signals is an intriguing idea that combines elements of biometric security with cryptography. ECG signals are unique to individuals, which means they can serve as a basis for personalized encryption. The following sub-sections detail how the study approaches this.
3.1. Loading of the ECG Signal Dataset
The ECG signal is loaded from a file or data source. Each recording has a 20-s single-lead ECG signal from LIMB II, with a sampling rate of 500 Hz. The dataset contains 89 ECG recordings, including 25 from healthy individuals in a lab setting, 20 from the MIT-BIH Arrhythmia Database (MITDB), and 44 from cardiac patients in a clinical environment. These data are stored in the “data. mat” file and can be read using Python 3.13 with the Scipy package. The package is organized as a dictionary, with corresponding labels and original signal data, each containing 10,000 data points. The input to the model is the BIH Arrhythmia Database (MITDB).
3.2. Preprocess ECG Signal
The raw ECG signal is cleaned from noise and normalized for further processing. The band-pass filter approach is used to remove noise, which is expressed as a frequency response H(f) (see Equation (1)). The band-pass filter allows only a specific range of frequencies to pass while attenuating frequencies outside this range [0, 1].
| (1) |
where f is frequency, fL is the lower cutoff frequency, and the upper cutoff frequency is fH; therefore, Equation (2) is as follows:
| (2) |
where and represent the impulse responses of the low-pass and high-pass filters, respectively. To improve the model’s ability to generalize, the recordings were normalized and scaled to a common range (e.g., 0 to 1) using min–max scaling expressed in Equation (3), as follows:
| (3) |
where and are the min and max feature normalization in the range [0, 1].
3.3. ECG Extract Features
The adaptive variational model decomposition (adaptive VMD) approach is used to decompose the ECG signal and further remove noise. Thus, given the ECG signal x(t), the decomposition is expressed in Equation (4), as follows:
| (4) |
where x(t) is the observed signal, is ith signal, n(t) is residual noise, and M is the total number of signals. Residual noise in the ECG signal and noise after ECG signal reconstruction can impact the feature extraction with the adaptive VMD; thus, functions expressed in Equations (5)–(8) were employed to address these noises.
The variational mode defines the likelihood function Fn, which is expressed in Equation (5), as follows:
| (5) |
where the prior distribution probability p(s, n) represents the likelihood of any other noise in the ECG signal. Thus, the objective function of the variational mode is expressed in Equation (6) as follows:
| (6) |
where Rerror is the reconstruction error and R is the regularization, which is the smoothness of the sparsity of noise. Thus, in Equations (7) and (8),
| (7) |
| (8) |
where and are the regularization parameters and and are the norms. The model parameters are adjusted based on the input signal at the decomposition stage at a learning rate based on the observed data; thus, si(t) and n(t) parameters are iteratively updated to reduce any possible impact of noise and the parameters were achieved using Equations (9) and (10).
| (9) |
| (10) |
where and k are the learning rate and iteration, respectively.
Though mode decomposition aids in feature extraction, the study went a step further to extract features using the R-peak, which aids in computing the Heart Rate Variability (HRV), RR interval (Time between successive R-wave peaks), and wave characteristics Q, S, and T in terms of amplitude and duration. The approach to compute the HRV is based on the standard deviation of the R-R intervals, which is measured using the Standard Deviation of NN intervals-SDNN). Also, by using the Root Mean Square of Successive Differences (RMSSD), the continual differences in the interval are computed. HRV metrics capture the SDNN and RMSSD of the extracted features, which are expressed using Equations (11) and (12):
| (11) |
| (12) |
Three types of features are imperative in feature extraction, namely, time-domain, frequency-domain, and time–frequency domain. The time-domain feature like the mean, standard deviation, root mean square (RMS), skewness, and kurtosis from each segment were computed.
The discrete Fourier transform (DFT) signal is used to compute the spectrum of finite duration signal expressed in Equation (13) by
| (13) |
where X[k] and N are the DFT coefficient at index k and total number of samples, respectively. x[n] is the discrete time-domain signal. Then, to recover the original discrete signal, the Inverse Discrete Fourier Transform is expressed in Equation (14) by
| (14) |
where x[n] and X[k] are the n-th time domain in a sample and the k-th frequency domain components, respectively. N represents the number of points in the sequence and j is the imaginary units.
Furthermore, the time–frequency domain features , which addresses the changes in frequency over time, was computed using a Short-Time Fourier Transform (STFT) that maps subsequent segments of ECG signal into dimensions of time and frequency expressed in Equation (15), as follows:
| (15) |
where is the window function positioned at t.
Finally, the fusion of multiple domains is expressed to concatenate all the different domain features into a single vector representation that can be expressed in Equation (16) as:
| (16) |
where is the fused vector, is the vector of the time-domain feature, is the frequency-domain feature, and is the vector of time–frequency domain features.
3.4. Statistical Analysis
Zero-crossing rate (ZCR) calculates the number of times the preprocessed signal crosses zero within a time t window. ZCR for the continuous-time signal is expressed in Equation (17) as
| (17) |
where Sf represents the sign function of x(t) between (+1, 0, −1) in Equation (18), as follows:
| (18) |
3.5. Bio-Inspired Key Generation
The bio-inspired method was inspired by the concept of the half-life of a radioactive substance, which was considered in the formulation of the kestrel-based search algorithm [55]. The half-life was expressed as having N unstable substances that decay at time t is expressed in Equation (19):
| (19) |
Which can be simplified in Equations (20)–(22), as follows:
| (20) |
| (21) |
| (22) |
where φ is the decay constant and t½ is the period of half-life representing the required time for to become half of . is the light intensity variation generated at random intervals between [0, 1]. The bio-inspired method has been applied in several problem domains and the selection of the parameters in the method was demonstrated through an experiment with promising performance results [55,56,57]. Among the parameters include the flight (0.8) and perch (0.2) modes. The initial population in the bio-inspired algorithm is generated using Equation (23), as follows:
| (23) |
Randbit() represents a random bit generator to ensure randomization and reduce the chance of unauthorized breaking of the encryption key. A unique key is generated from the vectorized fused feature and hashed. Afterward, the bio-inspired algorithm final key is generated using the following Equation (24):
| (24) |
| (25) |
where is the fused multi-domain vectorized ECG feature. The randomness of the generated key with Shannon entropy and Min-entropy for the bio-key generated on the ECG signal of the subject were evaluated to assess randomness through entropy in Equation (26):
| (26) |
| (27) |
The final key Fkey is used with Chacha20 for encrypting ECG bio-signals. The encryption scheme is mathematically modeled such that it takes the plaintext Pi and applies the XOR on the keystream k to output the cypher text Ci at each position i as expressed by Equation (28):
| (28) |
Furthermore, the decryption scheme is then expressed by Equation (29), as follows:
| (29) |
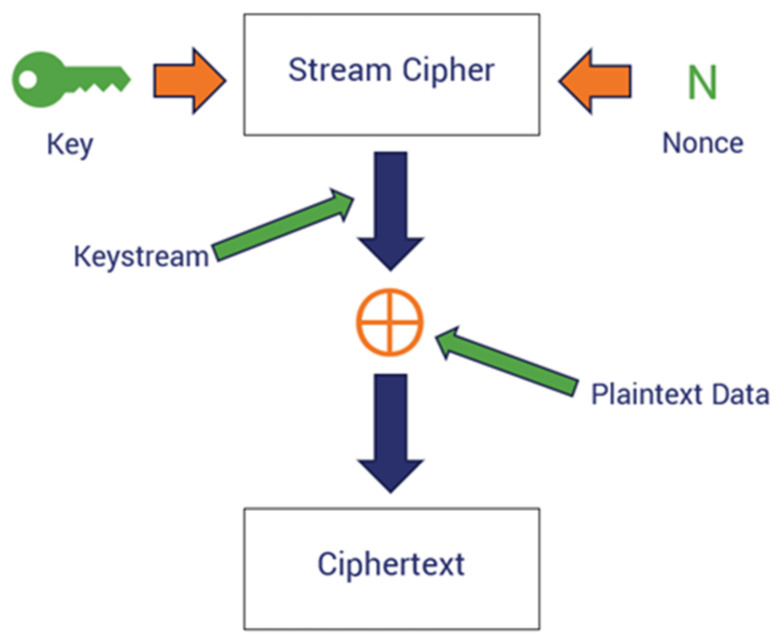
where represents the plaintext and is the cipher text at the ith position. The keystreams k are extracted from the fused vector representation. Figure 1 below illustrates the encryption scheme.
Figure 1.
Diagram of the encryption scheme.
3.6. Algorithm to Implement Lightweight Encryption
The algorithm to implement the lightweight encryption steps is expressed with Algorithms 1–3. Algorithm 1 indicates the steps in ECG signal processing. In this algorithm, raw ECG signal is inputted, and then different mathematical computations are performed to output the pre-processed ECG signal.
| Algorithm 1: ECG signal Preprocessing | |
| 1. | Input: raw ECG signal, , , |
| 2. | Compute: using Equation (1) |
| 3. | Compute: using Equation (2) |
| 4. | Compute: using Equation (3) |
| 5. | Output: Preprocessed ECG signal |
Algorithm 2 presents the steps to implement the feature extraction.
| Algorithm 2: Feature Extraction | |
| //data-adaptive variational model decomposition | |
| 1. | Compute: x(t) using Equation (4) |
| 2. | Compute: using Equation (6) to compute the objective function and likelihood of error in mode reconstruction |
| 3. | Compute: , |
| 4. | Compute: discrete Fourier transform (DFT) signal using Equation (11) |
| 5. | Compute: using Equation (15) |
| 6. | Compute: using Equation (16) |
| 7. | Compute: ZCR using Equation (17) |
| 8. | Output: fused feature vector |
Algorithm 3 presents a fused feature vector and the bio-inspired key generation steps.
| Algorithm 3: Fused feature vector and bio-inspired key generation | |
| 1. | Initialize population: |
| 2. | Generate Unique key for the feature vector in the string representation |
| 3. | Generate: random key using Half-life |
| 4. | Generate: Fkey |
| 5. | Output: Fkey |
| 6. | Apply: Fkey with the Chacha20 encryption scheme as expressed by Equations (28) and (29). |
4. Results
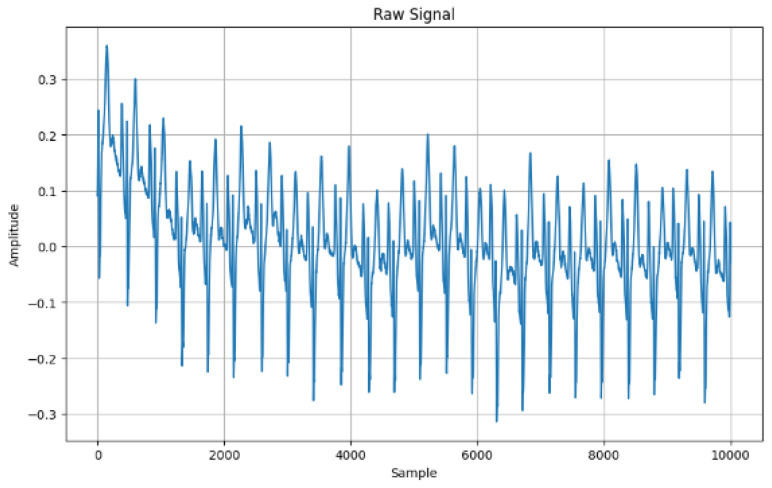
This section presents the experimental results. Figure 2 shows the frequency of the original ECG data. The highest amplitude is a little above 0.3 and the lowest is below the −0.3 amplitude.
Figure 2.
Raw signal.
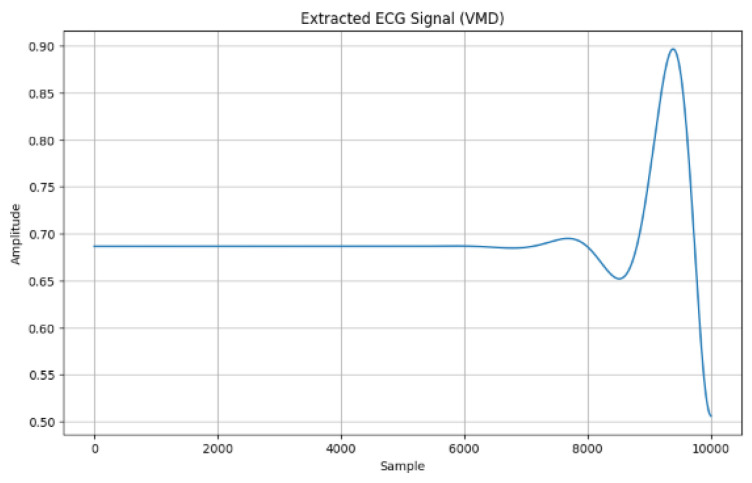
Figure 3 shows the extracted ECG signal using the adaptive VMD method in which the amplitude signal was 0.90, such as the peak for the 10,000 samples.
Figure 3.
ECG signal extraction using adaptive VMD.
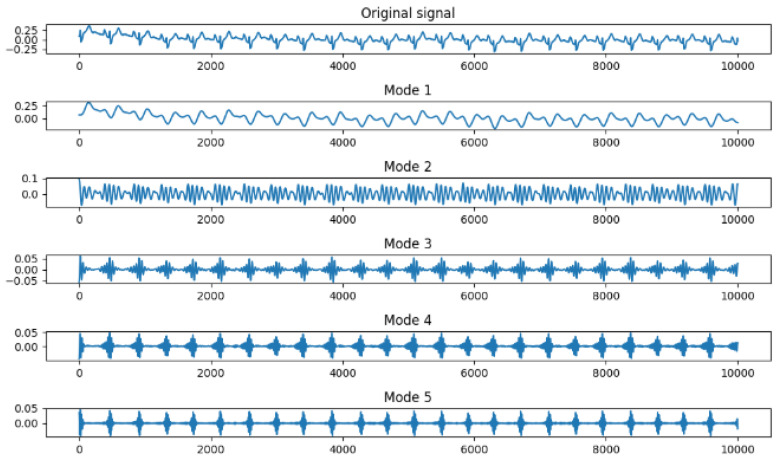
Figure 4 shows the adaptive VMD consisting of three stages. The first phase of the decomposition initialized the noise tolerance value (0.0), in which the mode five decomposition is created to enable a view of the behavior of the frequencies. The bandwidth constraint of 2000 was set within a tolerant convergence criterion of 1 × 10−7. The second stage is the visualization of the mode decomposition in terms of the original signal and the five-mode decomposition as shown in Figure 4.
Figure 4.
Five adaptive Variational Mode Decomposition (VMD).
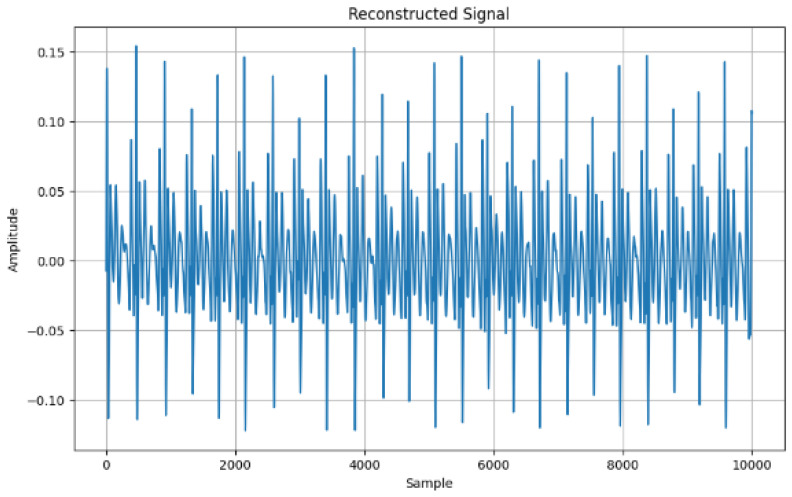
Finally, Figure 5 shows the mode reconstruction where all noise has been removed from the signal in preparation for feature extraction. The highest amplitude was a little above the 0.15 amplitude and the lowest amplitude was below −0.10.
Figure 5.
Signal reconstruction with adaptive VMD.
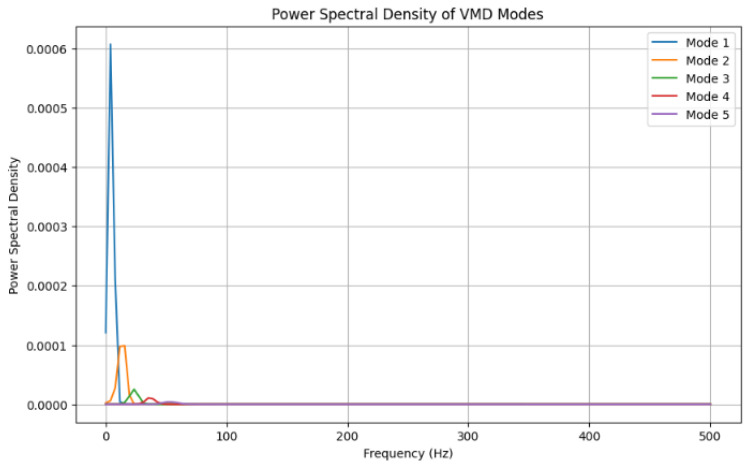
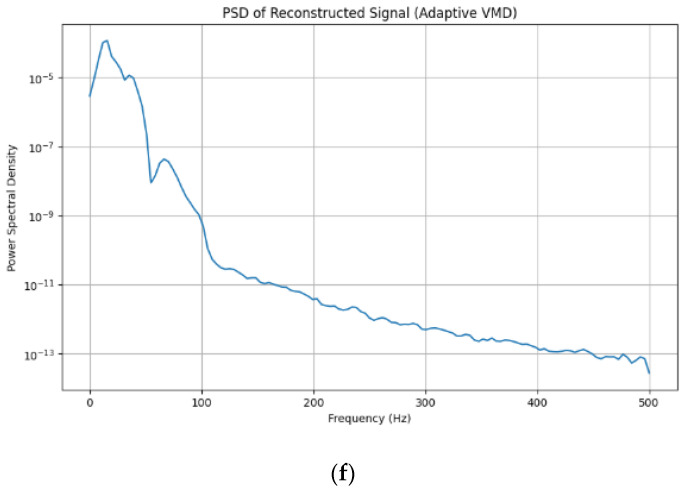
Figure 6 depicts the power spectral density of the adaptive VMD models where mode 1 (in Figure 5) happens to have the highest peak of (0.0006) and mode 2 (0.0001).
Figure 6.
Power spectral density of adaptive Variational Mode Decomposition (VMD).
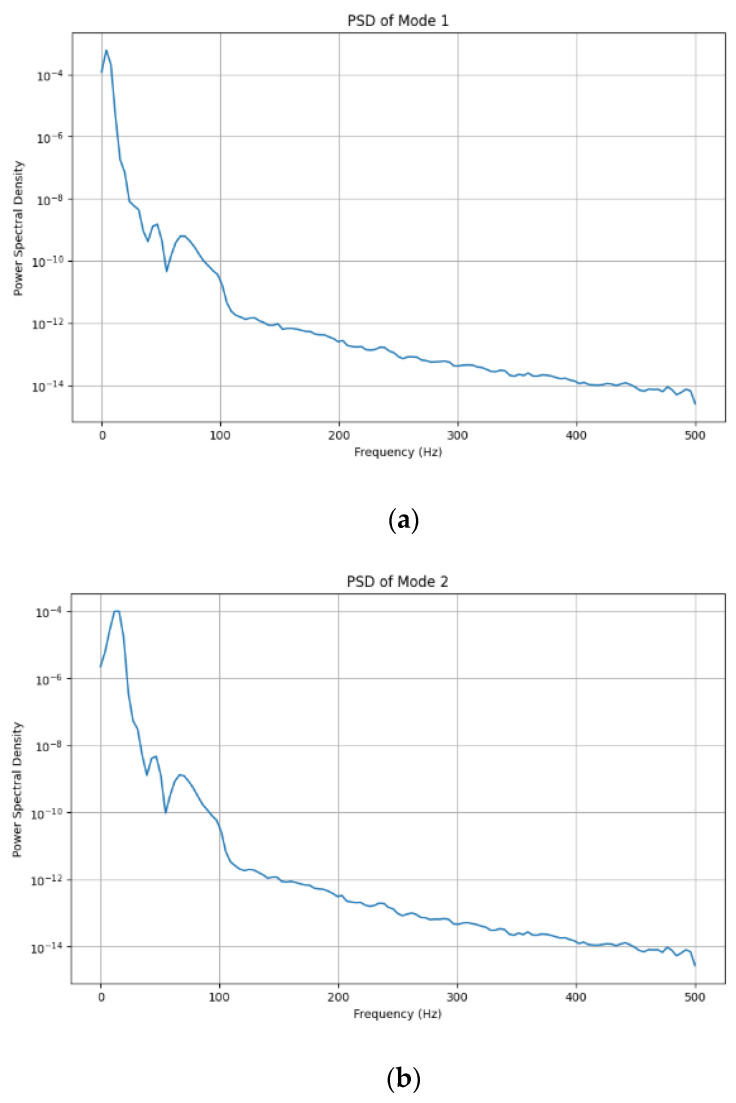
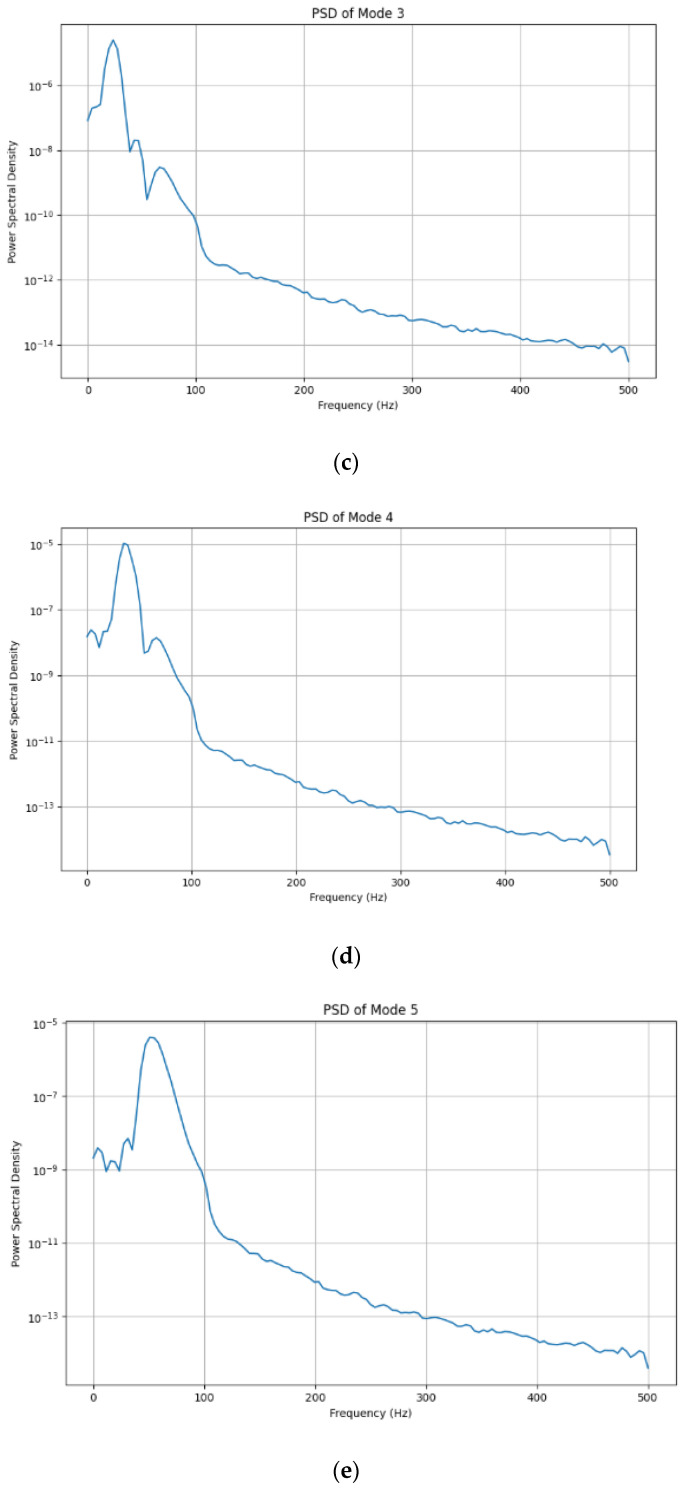
Figure 7 shows each adaptive VMD mode for the reconstructed signal. The mode shows the decomposition of the ECG signal to help understand the frequencies in each segment of the mode.
Figure 7.
Power spectral density of the adaptive VMD with five modes.
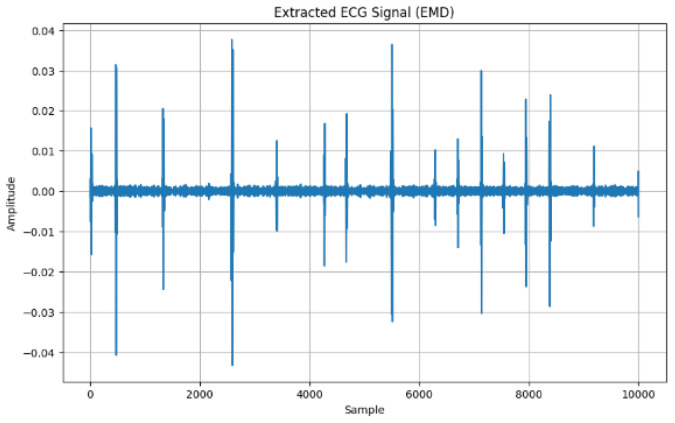
Figure 8 shows the Empirical Mode Decomposition method (EMD) as another approach to recovering the ECG signal in which the first Intrinsic Mode Function (IMF) of the ECG signal is identified as it recognizes the highest frequency. IMF varies in amplitude and frequency, where the high amplitude is approximating to 0.04.
Figure 8.
Extracted ECG signal with EMD.
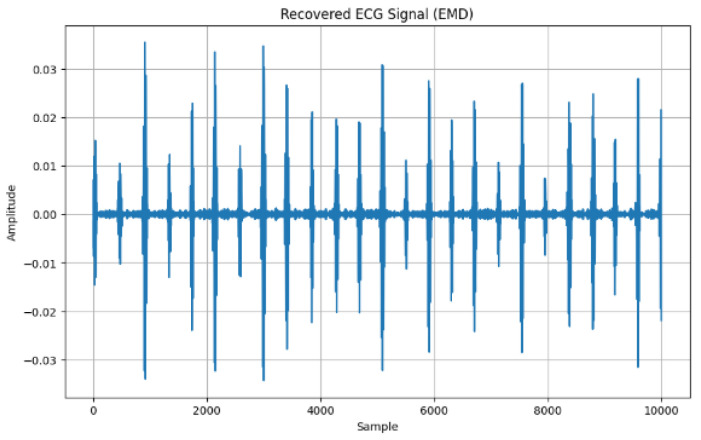
Using the EMD approach, the first IMF becomes the recovered signal, which is depicted in Figure 9.
Figure 9.
Recovered ECG signal (EMD).
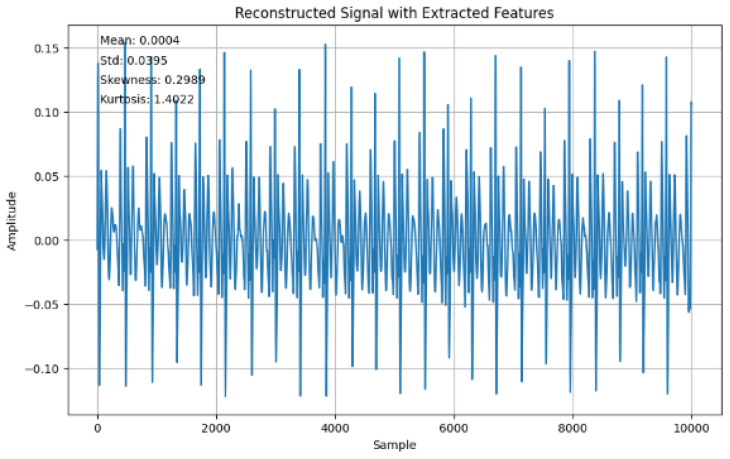
Figure 10 shows the reconstructed signal with the time-domain features extracted showing the mean (0.0004), standard deviation (0.0395), skewness (0.2989), and kurtosis (1.4022).
Figure 10.
Reconstructed signal with extracted features.
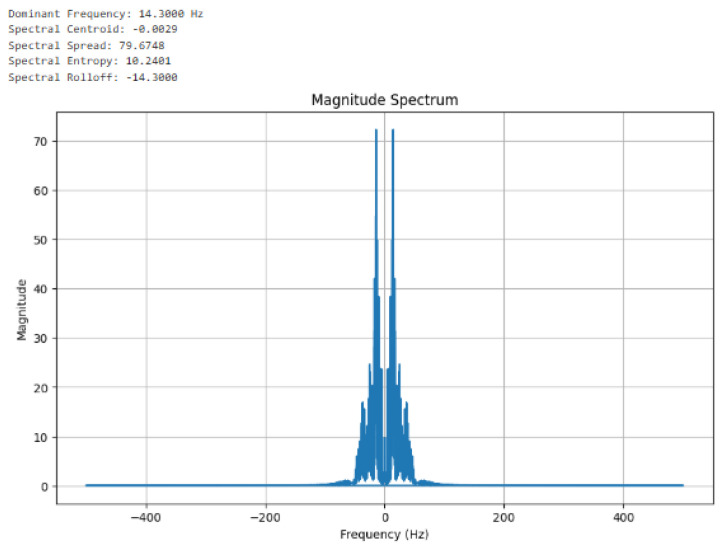
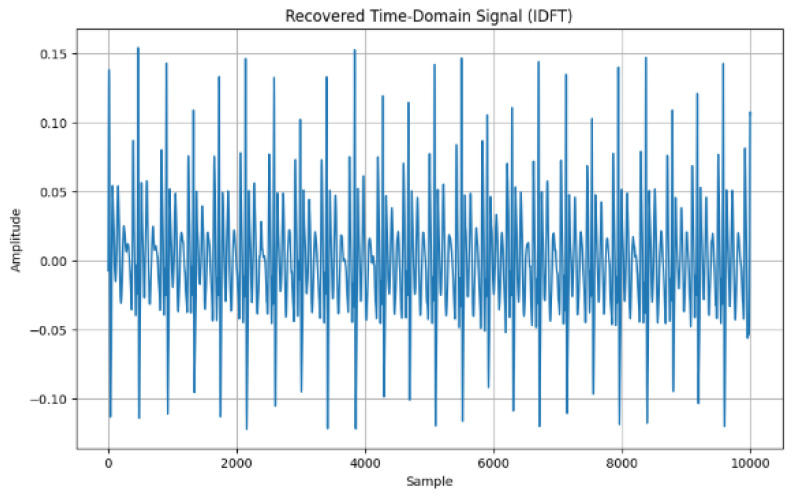
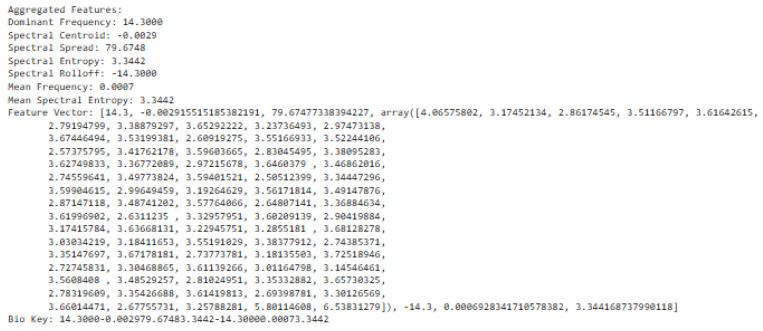
Figure 11 shows the frequency domain feature extractions using the continuous Fourier transform. The magnitude spectrum was computed and the features captured are the dominant frequency (14.3000 Hz), spectral centroid (−0.0030), spectral spread (80.3951), spectral entropy (10.1530), and spectral Rolloff (−14.0000). In Figure 12, the Inverse Discrete Fourier Transform (IDFT) is presented as it converts the frequency-domain features back to the corresponding time domain; such conversion confirms Figure 10 and Figure 11.
Figure 11.
Frequency domain features extracted from the reconstructed signal using a continuous Fourier transform.
Figure 12.
Time domain signal.
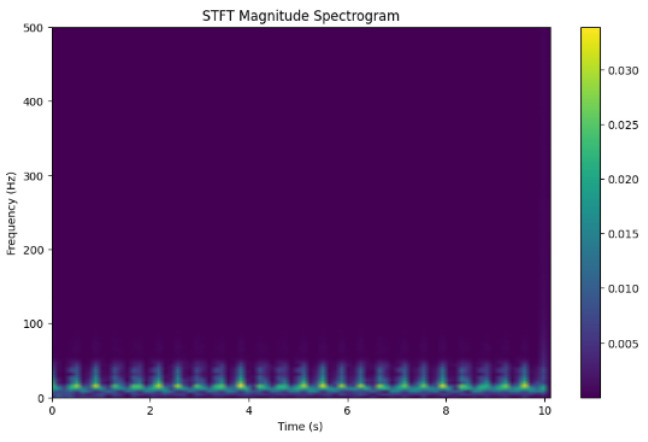
Figure 13 shows the STFT magnitude spectrogram showing the actual signals. It highlights the time–frequency property for an accurate representation of the signal. Colors represent the amplitude frequency at each point in time. Dark portions are regions with one signal. Through the distribution, the patterns can be visualized and timed in seconds (s) displayed.
Figure 13.
STFT Magnitude spectrogram visualization.
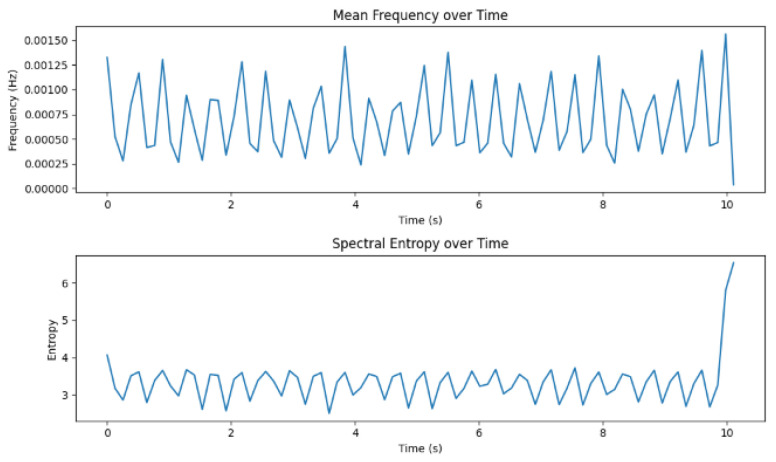
Figure 14 shows the frequency domain in terms of the mean and spectral entropy over time. The mean frequency describes the central frequency of the power spectrum concentration.
Figure 14.
Frequency domain.
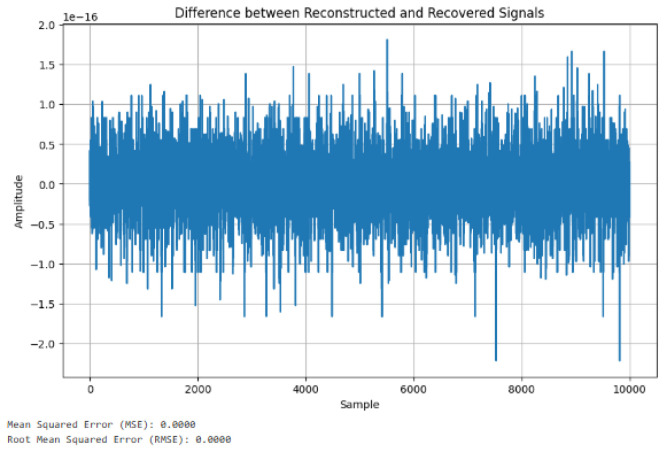
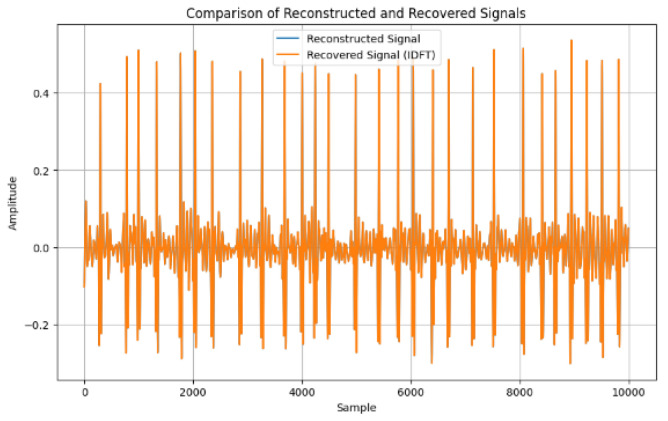
Figure 15 shows the difference between reconstructed and recovered signals. The MSE and RMSE are the statistical methods used to find the differences, which demonstrates that the means were both 0.00, suggesting that there is no variation between the reconstructed and the recovered signals. Figure 16 shows further analysis of the reconstructed and recovered signal, which further demonstrates no variation.
Figure 15.
Differences between reconstructed and recovered signal.
Figure 16.
Comparison of reconstructed and recovered signal.
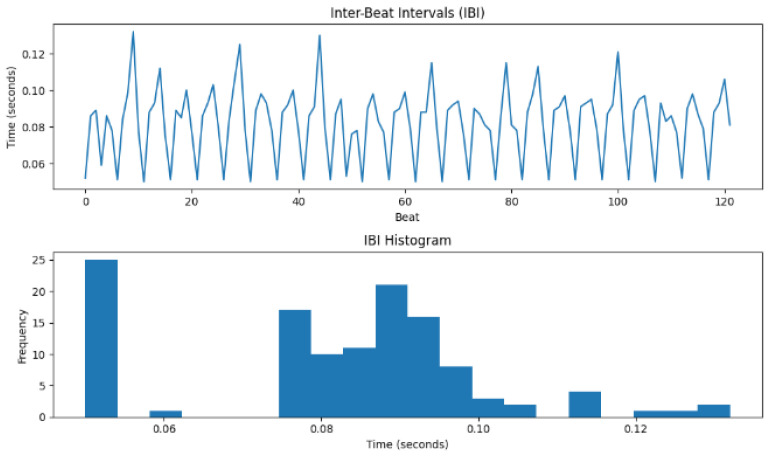
Figure 17 displays both the IBI and its histogram. The fluctuation in the heartbeat varies with time indicates a functioning nervous system of the individual. Again, the histogram demonstrates the time interval of successive heartbeats over some time. These features of the heartbeat are imperative in creating an effective encryption scheme from the human features.
Figure 17.
Inter-beat interval (IBI) and IBI histogram.
The HRV computation utilized standard deviation among others to calculate, in beats per minute (BPM), the heart rate, which was recorded as 738.00 (BPM), RMSSD (0.0840 s), SDNN (0.0191 s), NN50 (0), and pNN50 (0.00%). Also, the zero-crossing rate was 0.0245. Table 1 shows the aggregated domain features in terms of the time domain and frequency domains.
Table 1.
Domain features.
| Aggregated Features | Value | Type of Feature Domain |
|---|---|---|
| Dominant Frequency: | 14.3000 | Frequency domain |
| Spectral Centroid: | −0.0029 | Frequency domain |
| Spectral Spread: | 79.6748 | Frequency domain |
| Spectral Entropy: | 10.2401 | Frequency domain |
| Spectral Rolloff: | −14.3000 | Frequency domain |
| Mean Frequency: | 0.0007 | Time–frequency |
| Mean Spectral Entropy: | 3.3442 | Time–frequency |
| Mean | 0.0004 | Time domain |
| standard deviation | 0.0395 | Time domain |
| Skewness | 0.2989 | Time domain |
| Kurtosis | 1.4022 | Time domain |
The fusing approach is an aggregation of time–frequency domain features, frequency domain features, time-domain features, EMD, and adaptive VMD features, which were vectorized. Having extracted these features as shown in a vector representation, the bio-inspired algorithm was utilized to generate a random key. Before this, the extracted feature vector is converted to string representation and the bio-key was applied to finally generate the encryption key. The encryption scheme was evaluated by loading different ECG signals to extract the features in vector format and applied for ECG signal encryption. The resultant feature extracted is shown in Figure 18 as
Figure 18.
Fused feature vector with adaptive VMD.
Figure 19 depicts the bio-key, random bio key, and encryption key obtained from the feature vector.
Figure 19.
Key generation.
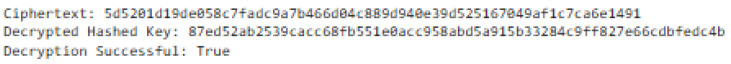
Figure 20 shows the cipher and decrypted text. It also indicated the status of decryption.
Figure 20.
Cipher and decrypted text.
A large population of kestrels can cover a broader search area, which increases the chances of finding a global optimum key but requires more computational resources. In this study, the population size was 200, to limit the computational cost of devices. However, a small population might fail to explore enough of the solution space, leading to a less secure key. Table 2 provides a comparison of the execution time of the encryption algorithms.
Table 2.
Comparison of execution time.
| Encryption Scheme | Encryption Time | Decryption Time | Key Generation Time | Total Time |
|---|---|---|---|---|
| ChaCha20 | 9.40 µs | 9.75 µs | 7.85 µs | 27 µs |
| ChaCha | 10.80 µs | 10.98 µs | 7.85 µs | 29.63 µs |
| Salsa20 | 11.45 µs | 11.60 µs | 7.85 µs | 30.90 µs |
The computing time (execution time) was considered in terms of time of encryption, time of decryption, and time for key generation. In this instance, the same population size in the bio-inspired search method was maintained and the efficiency was recorded in terms of execution time. The speed of encryption and decryption were measured (in microseconds (µs)) by executing the algorithm and recording the time taken. From Table 2, it can be observed that Chacha20 has a total execution time of 27 µs, Chacha (29.63 µs), and Salsa20 (30.90 µs). Thus, Chacha20 was efficient and suitable for resource-constrained devices.
The potential vulnerability of the proposed encryption scheme was the noise removal from the raw signal, which may impact the encryption key generation. Thus, the signal reconstruction approach was introduced to further remove noise, thus providing the surety and robustness of the encryption scheme.
5. Discussion
This study focused on extracting features from ECG signals to create an encryption scheme. The results demonstrated the capability to extract features into vector forms using time domain, frequency domain, and time–frequency domains. The advantage of time-domain approaches is their simplicity, which is based on statistical measures such as mean and variance. Again, this suggests less computation in signal analysis. Furthermore, it is effective for stationary signal analysis due to the statistical properties that do not change over time [58]. The advantage of the frequency domain is that it is more applicable for non-stationary signals due to the changing frequency over time. Again, it is more useful for processing more compact signals. Furthermore, it helps to identify noise signals and filter the signal to identify the most relevant signals [59]. Whereas, the advantage of time–frequency domain is that it provides a more comprehensive analysis of the signal, in both time and frequency domain features, over time. Again, it shows more patterns and insight into the signal. Bao, Yan [12] provided fusing mechanisms that leverage Variational Mode Decomposition (VMD) and Convolutional Neural Networks (CNNs) for feature extraction toward user identification system development. The VMD model can decompose features and remove noise that may affect the ECG signal quality. Modes from these decomposed features were derived (Figure 5) after all residual noise had been removed to enable feature extraction. In furtherance to this, the Empirical Mode Decomposition method (EMD) is an approach to enable the ECG signal to be recovered using the IMF to find the highest frequency. The EMD technique is used to assist in understanding the frequency oscillations of heartbeats.
In terms of the time domain, by using the reconstructed signal features, the mean (0.0004), standard deviation (0.0391), skewness (0.1562), and kurtosis (1.2205) were all extracted (Figure 10) from the ECG data. The use of IDFT and DFT further validated the consistency of the conversion as captured in Figure 10 and Figure 11, such that the frequency-domain features are correlated with the back with the time-domain representation features.
With respect to the frequency domain, the mean and spectral entropy were also displayed in Figure 14. The spectral entropy helps quantify the uncertainty that might occur in the power distribution of the signal from different frequency points of view. While high spectral entropy signifies the complexity of frequency distribution, the contrary suggests a more predictable distribution. Moreover, the power distribution is indicative of how power can be dispersed over frequencies [28].
Using metrics of MSE and RMSE to measure variation, Figure 15 shows that there was no deviation between the reconstructed and the recovered signals. Hence, the viability of our methods is demonstrated.
The features of the heartbeat are critical in the process of developing unique bio-keys for encryption; these features are indicated in the inter-beat interval and histogram as illustrated in Figure 17. Metrics about the time and frequency domain were extracted through HRV computation as outlined in Table 1 from these HRV-related features.
In the final analysis, the study utilized the feature extraction methods in this paper to aggregate these metrics into feature vectors to enable the encryption scheme development. Notably, HRV was employed as a simple key-generation approach [8]. Moreover, our approach provides a more robust key generation approach because it leverages the capabilities of more feature extraction approaches to create a more complex feature vector.
Bio-inspired algorithms, which by their nature provide randomness, increase the robustness of the encryption key. The bio-inspired algorithm Kestrel’s initial population is randomly generated as potential solutions to be found. This randomized searching enables bits of the fused feature vector to be chosen at random. The concept of half-life, introduced in the Kestrel algorithm, provides an additional layer of randomization, via the light intensity variation in the half-life component, in the formulation of the encryption key.
The selection of parameters in bio-inspired algorithms is crucial for the efficiency and security of the encryption key generation. Tuning the population size of the bio-inspired algorithm optimizes the generation of robust unpredictable keys that enhance the security of encryption systems. Moreover, an improper parameter selection may result in weak keys or longer computation times, which could undermine the effectiveness of an encryption system. Setting an optimal population size can provide an efficient key generation for an encryption algorithm and also ensure security. The trade-off between security and efficiency depends on the computing limitations and the strength of the encryption key [40]. Thus, while a smaller population size may guarantee faster results, it may compromise the security of the generated key. On the other hand, a larger population size provides a more secure encryption key at a high computational cost. Thus, while Table 2 provides the trade-offs on executing time as the measure of efficiency, Chacha20 was efficient.
This simplified encryption key is provided as a parameter for use in the ChaCha20 encryption algorithm while The ChaCha20 algorithm is a symmetric-key algorithm as it ensures that the same key is both used for encryption and decryption in applications that require high speed and security [41]. Our study has provided an encryption scheme that is suitable for high-speed environments and for IoMT devices that can process data quickly but also ensure the security transmission of data using extracted human features. Our study extracts human features from the bio-signals of these IOMT devices to ensure that these bio-signals can be securely encrypted and transmitted. From a theoretical perspective, this study contributes to the introduction of the unique bio-inspired Kestrel algorithm with its randomized searching and its half-life component, both of which add layers of randomization for a more secure key for ECG signals. In this research, the impact of noise on generated encryption keys and the impact of bio-inspired search parameters on key generation were, respectively, addressed with signal reconstruction and the use of population tuning of the bio-inspired search method.
6. Conclusions
The paper sought to extract features from ECG signals to create an encryption scheme that does not only rely the on time domain, frequency domain, or time–frequency domains. Instead, through the use of the mode decomposition approach, features of an intra-relationship were extracted and statistically validated to help create a fusion feature vector. Through leveraging this vector with the unique features of the bio-inspired Kestrel algorithm, a more robust encryption scheme is provided. Thus, by leveraging the chacha20 encryption algorithm with our feature extraction and key generation approach, we provide an encryption scheme that might be suitable for lightweight devices like IoMT. Future work includes further evaluation of this proposed encryption scheme within the context of IOMT devices in the real-world environment.
Author Contributions
Conceptualization, methodology, writing—original draft preparation, writing—review and editing, I.E.A.; writing—review and editing, supervision, analysis, R.C.M.; writing—review and editing, E.F.; writing—review and editing, W.W.; writing—review and editing, X.Z. All authors have read and agreed to the published version of the manuscript.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are available upon request.
Conflicts of Interest
The authors declare no conflicts of interest.
Funding Statement
This work was funded in part by the National Key R&D Program of China (Grant number: 2023YFE0110200), in part by the National Research Foundation of South Africa (Grant number 151178).
Footnotes
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
References
- 1.Karimian N., Guo Z., Tehranipoor M., Forte D. Highly reliable key generation from electrocardiogram (ECG) IEEE Trans. Biomed. Eng. 2016;64:1400–1411. doi: 10.1109/TBME.2016.2607020. [DOI] [PubMed] [Google Scholar]
- 2.Aziz S., Hayat M.M., Naqvi S.Z.H., Furqan M., Khan M.U., Zahid M.Z. Electrocardiography based Biometric Verification System; Proceedings of the 2020 International Conference on Electrical, Communication, and Computer Engineering (ICECCE); Istanbul, Turkey. 12–13 June 2020. [Google Scholar]
- 3.Neri L., Oberdier M., van Abeelen K., Menghini L., Tumarkin E., Tripathi H., Jaipalli S., Orro A., Paolocci N., Gallelli I., et al. Electrocardiogram Monitoring Wearable Devices and Artificial-Intelligence-Enabled Diagnostic Capabilities: A Review. Sensors. 2023;23:4805. doi: 10.3390/s23104805. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 4.Asim M., Akhtar M., Faraz M., Khan M.U., Aziz S., Montes G.A. Pattern Analysis for Biometric Authentication using Electrocardiogram Signal; Proceedings of the 2023 2nd International Conference on Emerging Trends in Electrical, Control, and Telecommunication Engineering (ETECTE); Lahore, Pakistan. 27–29 November 2023. [Google Scholar]
- 5.Shuma M., Madhumathy P. Brakerski-Gentry-Vaikuntanathan fully homomorphic encryption cryptography for privacy preserved data access in cloud assisted internet of things services using glow-worm swarm. Trans. Emerg. Telecommun. Technol. 2022;33:e4641. doi: 10.1002/ett.4641. [DOI] [Google Scholar]
- 6.Lin Y., Xie Z., Chen T., Chen X., Wen H. Image privacy protection scheme based on high-quality reconstruction DCT compression and nonlinear dynamics. Expert Syst. Appl. 2024;257:124891. doi: 10.1016/j.eswa.2024.124891. [DOI] [Google Scholar]
- 7.Karpagachelvi S., Arthanari M., Sivakumar M. ECG Feature Extraction Techniques—A Survey Approach. (IJCSIS) Int. J. Comput. Sci. Inf. Secur. 2010;8:1–5. [Google Scholar]
- 8.Pirbhulal S., Zhang H., Mukhopadhyay S.C., Li C., Wang Y., Li G., Wu W., Zhang Y.-T. An Efficient Biometric-Based Algorithm Using Heart Rate Variability for Securing Body Sensor Networks. Sensors. 2015;15:15067–15089. doi: 10.3390/s150715067. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 9.Kumar S., Vaishali K., Maiya G., Shivashankar K.N., Shashikiran U. Analysis of time-domain indices, frequency domain measures of heart rate variability derived from ECG waveform and pulse-wave-related HRV among overweight individuals: An observational study. F1000Research. 2023;12:1229. doi: 10.12688/f1000research.139283.1. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 10.Escribano P., Ródenas J., García M., Arias M.A., Hidalgo V.M., Calero S., Rieta J.J., Alcaraz R. Combination of frequency-and time-domain characteristics of the fibrillatory waves for enhanced prediction of persistent atrial fibrillation recurrence after catheter ablation. Heliyon. 2024;10:e25295. doi: 10.1016/j.heliyon.2024.e25295. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 11.Zhao L., Li J., Ren H. Multi domain fusion feature extraction and classification of ECG based on PCA-ICA; Proceedings of the 2020 IEEE 4th Information Technology, Networking, Electronic and Automation Control Conference (ITNEC); Chongqing, China. 12–14 June 2020. [Google Scholar]
- 12.Bao Z., Yan L., Wang M. Multi-feature Fusion ECG Signal Recognition Algorithm Based on VMD; Proceedings of the 2022 4th International Conference on Natural Language Processing (ICNLP); Xi’an, China. 25–27 March 2022. [Google Scholar]
- 13.Bazhutina A., Khamzin S., Sinitca A., Chmelevsky M., Zubarev S., Budanova M., Rainer W. An Ensemble of Machine Learning Models for Multilabel Classification of Cardiovascular Diseases by ECGs; Proceedings of the 2023 Computing in Cardiology (CinC); Atlanta, GA, USA. 1–4 October 2023. [Google Scholar]
- 14.Buyya A., Ogeti T., Suhas G., Kashapogula P., Panigrahy A.K. Arrhythmias Classification by using STFT-based Spectrograms, Transfer Learning and Concatenation of features; Proceedings of the 2023 4th International Conference for Emerging Technology (INCET); Belgaum, India. 26–28 May 2023. [Google Scholar]
- 15.Choudhary S.K., Sandee B. Real Time Biometric Authentication System Using ECG; Proceedings of the 2023 14th International Conference on Computing Communication and Networking Technologies (ICCCNT); Delhi, India. 6–8 July 2023. [Google Scholar]
- 16.Choudhary T., Das M., Sharma L.N., Bhuyan M.K. A Non-Fiducial Noise Robust VMD-based Framework for ECG-based Biometric Recognition; Proceedings of the 2021 IEEE 18th India Council International Conference (INDICON); Guwahati, India. 19–21 December 2021. [Google Scholar]
- 17.Pradhan B.K., Neelappu B.C., Sivaraman J., Kim D., Pal K. A Review on the Applications of Time-Frequency Methods in ECG Analysis. J. Healthc. Eng. 2023;34:3145483. doi: 10.1155/2023/3145483. [DOI] [Google Scholar]
- 18.Anjitha P., Dhanya K.R., Sindhu N., Jerritta S. The Untapped Potential of Feature Selection for Emotion Recognition: Literature Review; Proceedings of the 2020 International Conference on Power, Instrumentation, Control and Computing (PICC); Thrissur, India. 17–19 December 2020. [Google Scholar]
- 19.He W., Ye Y., Pan T., Meng Q., Li Y. Emotion Recognition from ECG Signals Contaminated by Motion Artifacts; Proceedings of the 2021 International Conference on Intelligent Technology and Embedded Systems (ICITES); Chengdu, China. 31 October 2021–2 November 2021. [Google Scholar]
- 20.Ihsan M.F., Mandala S., Pramudyo M. Study of Feature Extraction Algorithms on Photoplethysmography (PPG) Signals to Detect Coronary Heart Disease; Proceedings of the 2022 International Conference on Data Science and Its Applications (ICoDSA); Bandung, Indonesia. 6–7 July 2022. [Google Scholar]
- 21.Khan M.U., Aziz S., Naqvi S.Z.H., Zaib A., Maqsood A. Pattern Analysis Towards Human Verification using Photoplethysmograph Signals; Proceedings of the 2020 International Conference on Emerging Trends in Smart Technologies (ICETST); Karachi, Pakistan. 26–27 March 2020. [Google Scholar]
- 22.Omar N., Dey M., Ullah M.A. Detection of Myocardial Infarction from ECG Signal Through Combining CNN and Bi-LSTM; Proceedings of the 2020 11th International Conference on Electrical and Computer Engineering (ICECE); Dhaka, Bangladesh. 17–19 December 2020. [Google Scholar]
- 23.Khan M.U., Saad M., Aziz S., Ch J.M., Naqvi S.Z.H., Qasim M.A. Electrocardiogram based Gender Classification; Proceedings of the 2020 International Conference on Electrical, Communication, and Computer Engineering (ICECCE); Istanbul, Turkey. 12–13 June 2020. [Google Scholar]
- 24.Mahmud M.S., Nayan M.M.R., Hasan S., Taj M.N.A. A Deep Ensemble Model with an Efficient Feature for Multi-class Arrhythmia Classification Utilizing 12-Lead ECG Signal; Proceedings of the 2022 12th International Conference on Electrical and Computer Engineering (ICECE); Dhaka, Bangladesh. 21–23 December 2022. [Google Scholar]
- 25.Nijaguna G.S., Lal N.D., Divakarachari P.B., Prado R.P.d., Woźniak M., Patra R.K. Feature Selection Using Selective Opposition Based Artificial Rabbits Optimization for Arrhythmia Classification on Internet of Medical Things Environment. IEEE Access. 2023;11:100052–100069. doi: 10.1109/ACCESS.2023.3312537. [DOI] [Google Scholar]
- 26.Chen L., Zhang C., Gao X. Speech Signal Analysis of Autistic Children Based on Time-Frequency Domain Distinguishing Feature Extraction; Proceedings of the 2022 IEEE 34th International Conference on Tools with Artificial Intelligence (ICTAI); Macao, China. 31 October 2022–2 November 2022. [Google Scholar]
- 27.Kuznetsov I.V. Movements Classification Based on Surface Electromyography Using Time-frequency Domain Features; Proceedings of the 2024 XXVII International Conference on Soft Computing and Measurements (SCM); Saint Petersburg, Russian. 22–24 May 2024. [Google Scholar]
- 28.Singh A.K., Krishnan S. ECG signal feature extraction trends in methods and applications. BioMed. Eng. OnLine. 2023;22:22. doi: 10.1186/s12938-023-01075-1. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 29.Alyasseri Z.A.A., Al-Betar M.A., Awadallah M.A., Makhadmeh S.N., Alomari O.A., Abasi A.K., Doush I.A. EEG Feature Fusion for Person Identification Using Efficient Machine Learning Approach; Proceedings of the 2021 Palestinian International Conference on Information and Communication Technology (PICICT); Gaza, Palestine. 28–29 September 2021. [Google Scholar]
- 30.Khushaba R.N., Al-Timemy A.H., Samuel O.W., Scheme E.J. Myoelectric Control with Fixed Convolution-Based Time-Domain Feature Extraction: Exploring the Spatio–Temporal Interaction. IEEE Trans. Hum. Mach. Syst. 2022;52:1247–1257. doi: 10.1109/THMS.2022.3146053. [DOI] [Google Scholar]
- 31.Khushaba R.N., Phinyomark A., Al-Timemy A.H., Scheme E. Recursive Multi-Signal Temporal Fusions With Attention Mechanism Improves EMG Feature Extraction. IEEE Trans. Artif. Intell. 2020;1:139–150. doi: 10.1109/TAI.2020.3046160. [DOI] [Google Scholar]
- 32.Jiang K., Wang Z., Shen R., Wang S., Liu Y., Feng Y., Lisun X., Li Z. A Neurological Recovery Prediction Algorithm Based on Multi-Feature Extraction and Bagging Aggregation; Proceedings of the 2023 Computing in Cardiology (CinC); Atlanta, GA, USA. 1–4 October 2023. [Google Scholar]
- 33.Kherdekar V.A., Naik S.A. Feature Fusion Extraction Method for Improvement of Recognition of Continuous Speech: A Feature Fusion Method for Recognition of Continuous Speech; Proceedings of the 2024 Fourth International Conference on Advances in Electrical, Computing, Communication and Sustainable Technologies (ICAECT); Bhilai, India. 11–12 January 2024. [Google Scholar]
- 34.Jain R., Garg V.K. An Efficient Feature Extraction Technique and Novel Normalization Method to Improve EMG Signal Classification; Proceedings of the 2022 3rd International Conference on Intelligent Engineering and Management (ICIEM); London, UK. 27–29 April 2022. [Google Scholar]
- 35.Premkumar S., Mohana J. International Journal of Innovative Technology and Exploring Engineering (IJITEE) Blue Eyes Intelligence Engineering & Sciences Publication; Bhopal, India: 2019. An efficient method for Secure ECG Feature Based Cryptographic Key Generation. [Google Scholar]
- 36.Mathivanan P., Ganesh A.B., Venkatesan R. QR code–based ECG signal encryption/decryption algorithm. Cryptologia. 2019;43:233–253. doi: 10.1080/01611194.2018.1549122. [DOI] [Google Scholar]
- 37.Karthikeyan M.J., Martin Leo Manickam A. 128-Bit secret key generation using unique ECG Bio-signal for medical data cryptography in lightweight wireless body area networks. J. Biotechnol. 2017;14:257–264. [Google Scholar]
- 38.Rahman M.S., Khalil I., Yi X. Reversible Biosignal Steganography Approach for Authenticating Biosignals using Extended Binary Golay code. IEEE J. Biomed. Health Inform. 2020;25:35–46. doi: 10.1109/JBHI.2020.2988449. [DOI] [PubMed] [Google Scholar]
- 39.Garcia-Baleon H.A., Alarcon-Aquino V., Starostenko O. 2009 52nd IEEE International Midwest Symposium on Circuits and Systems. IEEE; Piscataway, NJ, USA: A Wavelet-Based 128-bit Key Generator Using Electrocardiogram Signals; pp. 644–647. [Google Scholar]
- 40.Radhakrishnan I., Jadon S., Honnavalli P.B. Efficiency and Security Evaluation of Lightweight Cryptographic Algorithms for Resource-Constrained IoT Devices. Sensors. 2024;24:4008. doi: 10.3390/s24124008. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 41.Kebande V.R. Extended-Chacha20 Stream Cipher with Enhanced Quarter Round Function. IEEE Access. 2023;18:114220–114237. doi: 10.1109/ACCESS.2023.3324612. [DOI] [Google Scholar]
- 42.Pirbhulal S., Zhang H., Wu W., Mukhopadhyay S.C., Zhang Y.-T. Heart-Beats Based Biometric Random Binary Sequences Generation to Secure Wireless Body Sensor Networks. IEEE Trans. Biomed. Eng. 2018;65:2751–2759. doi: 10.1109/TBME.2018.2815155. [DOI] [PubMed] [Google Scholar]
- 43.Khokher R., Singh R.C. Generation of Security Key using ECG Signal; Proceedings of the International Conference on Computing, Communication and Automation (ICCCA2015); Greater Noida, India. 15–16 May 2015; pp. 1–6. [Google Scholar]
- 44.Viand A., Jattke P., Hithnawi A. SoK: Fully Homomorphic Encryption Compilers; Proceedings of the 2021 IEEE Symposium Conf. on Security and Privacy (SP), IEEE Computer Society; San Francisco, CA, USA. 24–27 May 2021; pp. 1092–1108. [Google Scholar]
- 45.Moosavi S.R., Nigussie E., Virtanen S., Isoaho J. Cryptographic Key Generation Using ECG Signal; Proceedings of the 2017 14th IEEE Annual Consumer Communications & Networking Conference (CCNC); Las Vegas, NV, USA. 8–11 January 2017; pp. 1–8. [Google Scholar]
- 46.Hwang H.B., Lee J., Kwon H., Chung B., Lee J., Kim Y. Preliminary Study of Novel Bio-Crypto Key Generation Using Clustering-Based Binarization of ECG Features. Sensors. 2024;24:1556. doi: 10.3390/s24051556. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 47.Karthikeyan M., Manickam J.M.L. ECG-signal based secret key generation (ESKG) scheme for WBAN and hardware implementation. Wirel. Pers. Commun. 2019;106:2037–2052. doi: 10.1007/s11277-018-5924-x. [DOI] [Google Scholar]
- 48.Gonzalez-Manizano L., Fuentes J.M.D., Peris-Lopez P., Camara C. Encryption by Heart (EbH)-using ECG for time-invariant symmetric key generation. Future Gener. Comput. Syst. 2017;77:136–148. doi: 10.1016/j.future.2017.07.018. [DOI] [Google Scholar]
- 49.Hernández-Álvarez L., Barbierato E., Caputo S., Fuentes J.M.d., González-Manzano L., Encinas L.H., Mucchi L. KeyEncoder: A secure and usable EEG-based cryptographic key generation mechanism. Pattern Recognit. Lett. 2023;173:1–9. doi: 10.1016/j.patrec.2023.07.008. [DOI] [Google Scholar]
- 50.Shaikh M.U., Adnan W.A.W., Ahmad S.A. Secured electrocardiograph (ECG) signal using partially homomorphic encryption technique-RSA algorithm. Pertanika J. Sci. Technol. 2020;28:231–242. doi: 10.47836/pjst.28.s2.18. [DOI] [Google Scholar]
- 51.Ahmed A.A.A., Madboly M.M., Guirguis S.K. Securing data transmission and privacy perserving using fully homomorphic encryption. Int. J. Intell. Eng. Syst. 2023;16:2023. [Google Scholar]
- 52.Shaikh M.U., Adnan W.A.W., Ahmad S.A. Sensitivity and positive prediction of secured electrocardiograph (ECG) transmission using fully homomorphic encryption technique (FHE); Proceedings of the 2020 IEEE-EMBS Conference of Biomedical Engineering and Sciences (IECBES); Langkawi Island, Malaysia. 1–3 March 2021; pp. 292–297. [Google Scholar]
- 53.Madhloom J.K., Ghani M.K.A., Baharon M.R. ECG encryption enhancement technique with multiple layers of AES and DNA computing. Intell. Autom. Soft Comput. 2021;28:493–512. doi: 10.32604/iasc.2021.015129. [DOI] [Google Scholar]
- 54.Premkumar S., Mohana J. A novel ECG based encryption algorithm for securing patient confidential information. Int. J. Electr. Eng. Technol. (IJEET) 2020;11:35–43. [Google Scholar]
- 55.Agbehadji I.E., Abayomi A., Bui K.-H.N., Millham R.C., Freeman E. Kestrel-based Search Algorithm (KSA) for parameter tuning unto Long Short Term Memory (LSTM) Network for feature selection in classification of high-dimensional bioinformatics datasets; Proceedings of the Federated Conference on Computer Science and Information Systems; Poznan, Poland. 9–12 September 2018; pp. 15–20. [Google Scholar]
- 56.Agbehadji I.E., Millham R., Fong S.J., Hong H.-J. Nature-Inspired Search Method and Custom Waste Object Detection and Classification Model for Smart Waste Bin. Sensors. 2022;22:6176. doi: 10.3390/s22166176. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 57.Agbehadji I.E., Millham R., Fong S.J., Hong H.-J. Integration of Kestrel-based search algorithm with artificial neural network for feature subset selection. Int. J. Bio-Inspired Comput. 2019;13:222–233. doi: 10.1504/IJBIC.2019.100151. [DOI] [Google Scholar]
- 58.Wang W.-K., Wan M., Zhang W.-H., Yang Y. Chatter detection methods in the machining processes: A review. J. Manuf. Process. 2022;77:240–259. doi: 10.1016/j.jmapro.2022.03.018. [DOI] [Google Scholar]
- 59.Jardine A.K.S., Lin D., Banjevic D. A review on machinery diagnostics and prognostics implementing condition-based maintenance. Mech. Syst. Signal Process. 2006;20:1483–1510. doi: 10.1016/j.ymssp.2005.09.012. [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Data are available upon request.