Abstract
In the digital era, data has become a core resource driving the development of the global sports industry. With the increasing awareness of athlete data protection, ensuring the security of this sensitive information worldwide has become a significant issue. This study employs configurational theory and Fuzzy-set Qualitative Comparative Analysis to investigate the various factors affecting athlete data protection. The research reveals three key configurational pathways: “Single Organization Support Type,” “Organization-Environment Support Type,” and “Organizational Support Absent Type.” The “Single Organization Support Type” pathway emphasizes the role of a single organizational condition in athlete data protection, while the “Organization-Environment Support Type” considers the interaction between organizational and external environmental factors. In contrast, the “Organizational Support Absent Type” pathway reveals viable paths for data protection in the absence of effective organizational support. These findings not only provide valuable insights for policymakers to construct a more comprehensive framework for athlete data protection but also offer strategic support for the sustainable development of the global sports industry. They promote the safe use of sports data and the overall progress of the industry. Moreover, with the worldwide focus on sustainable development goals, the sports industry, as an essential component, plays an increasingly prominent role in promoting coordinated development of society, economy, and environment. The rational protection and utilization of sports data will contribute to achieving this global goal, especially in promoting healthy lifestyles, gender equality, and inclusive social construction. Therefore, the conclusions of this study are not only instructive for data governance within the sports domain but also provide practical contributions to global sustainable development.
Subject terms: Environmental sciences, Environmental social sciences
Introduction
In the era of big data, the massive collection, storage, transfer, and use of athlete data have become an irreversible trend. This also further increases the risk of athlete data infringement. The particularity of the sports industry in the practical field makes the processing and protection of athlete data different from general personal data protection. This has led to a large number of scholars discussing athlete data protection. However, at present, the lag in legal constraints, the neglect of organizational management, and the lack of corporate protection efforts make athlete data protection still an unresolved issue. Therefore, the study attempts to analyze the diversified paths to achieve athlete data protection from a management perspective using configurational theory.
What is athlete data? In terms of data content, athlete data can be divided into two main categories: personal information and sports performance data. Personal information includes basic identity details and health physiology provided by athletes throughout their sports event participation, as well as sensitive information required for doping tests, such as genetics, accommodation, travel trajectory, etc. Sports performance data refers to the statistical results of athletes’ tactics, techniques, and physical indicators during competitions, including biometric and technical movement data. This data is often central to the commercial development of sports events, as examplified by SAP’s Tennis Analytics for Coaches, which offers real-time data analysis to inform strategic decisions during competitions1.
The protection of athlete data faces three main challenges: (1) Multiple Entities and Data Ownership: The vast majority of sports event data originates athletes, and the extraction of value from this data often involves sports event organizers or authorized data service companies, leading to disputes over data rights ownership. (2) Cost of Claiming Rights vs. Privacy Protection: Athletes must authorize the use of their personal data to gain competition qualifications. Retaining personal data rights could result in exclusion from competitions, forcing athletes to weigh the costs of claiming rights against privacy protection. (3) Legal Framework Inadequacy: Existing laws struggle to protect athletes’ rights effectively. Once athletes sign up for events, they often authorize the analysis and use of their data by organizers or data service companies, without full knowledge of its specific use or commercial value, leading to a state of “data out of control”. The legal framework is ill-equipped to address illegal data acquisition or distribution effectively.
In conclusion, athlete data protection is a complex, systematic project that requires attention at both the legislative/judical and organizational management levels. When the legal framework falls short, exploring management perspectives for achieving athlete data protection becomes crucial.. The configurational perspective and the QCA method, which are often used to analyze the complexity of causality in multiple factors, can provide an effective explanation for this multi-factorial dynamic2. In athlete data protection, athletes, event organizers (including data service companies), government departments, and other stakeholders must choose to carry out joint protection strategies to achieve their common goal, that is, to protect their rights and interests. However, the premise of this strategy is not determined by a single factor. Just as user data security is affected by users’ and platforms’ willingness to invest, investment costs, benefits, and government incentives3. Since athlete data protection depends on the matching of multiple factors, the perspective of configuration and the QCA method can provide an effective explanation. However, for the same multi-factor coupling theory and ecological theory, the advantage of configuration theory lies in its concurrent causality, equivalence, and asymmetry. Compared with coupling and ecological theory, the perspective of configuration is based on causal complexity, which can more clearly distinguish between necessary and sufficient causal relationships4. This will help to have a more detailed and in-depth understanding of the causal mechanism of athlete data protection.
Literature review
Current research mainly focus on the privacy protection of athletes’ personal data5. On the one hand, the development of big data technology enables the real-time capture and cloud storage of athletes’ biometric and technical-tactical movement data, forming personal data sets. These data, after analysis by algorithms, can assess athletes’ performance, such as passing routes, passing frequency, and physical condition, and make improvements accordingly. However, the widespread application of big data monitoring also brings risks of privacy leakage and data misuse, which poses a potential threat to athletes’ personal privacy6. In response, athletes face choices between privacy protection and data utilization, and collective bargaining becomes a potential way to resolve this contradiction and promote the protection of athletes’ data7. On the other hand, the protection of athletes’ biometric data (ABD) has also become a focus of scholars in various countries in recent years. Especially for professional sports leagues such as the NBA, NFL, MLB, NHL, and MLS, which use wearable devices in training to generate biometric data. Some scholars have conducted research on the protection issues of ABD, deeply discussing the applicability of federal and state laws, as well as the differences in protection of ABD by event organizers8. Research has found that although ABD collection devices bring many benefits to athletes, athlete data still faces many risks, even affecting the order of athletes’ appearance and draft position9. How to solve the challenges faced by the protection of athletes’ data? Some scholars believe that the use of ABD collection devices should be resisted until effective policies are formulated to avoid risks, while institutions involved in collection and use fully understand the risks of data collection, storage, and use, and take necessary protective measures. Some Chinese scholars propose strategies for the protection of athletes’ data from a legal perspective, such as trying to introduce data property theory and granting athletes data property rights. In specific practice, a “data trust” model is proposed to strengthen the protection of athletes’ data. Overall, current research on the protection of athletes’ data is still in the exploratory stage, with existing research mainly focusing on the identification and avoidance of risks in the protection of athletes’ data, and mostly relying on legal protection measures. In addition to the further improvement of legal provisions for protection regulations, policy regulation also plays an important role in the protection of athletes’ data. Therefore, this study will focus on the diverse paths affecting the protection of athletes’ data and use it as a theoretical reference for policy formulation. The contribution of this study to the existing research field is mainly reflected in the analysis of the diverse paths affecting the protection of athletes’ data through configurational theory, providing a theoretical reference for policy formulation. Compared with existing research, the innovation of this study lies in the expansion of the research paradigm. This study introduces configurational theory to analyze the protection of athletes’ data, which has not been fully explored in previous studies. At the same time, it provides new perspectives and solutions for actual policy formulation and the practice of athletes’ data protection.
Theoretical background and conceptual framework
Configurational theory
Configurational theory and Qualitative Comparative Analysis (QCA) is a paradigm for analyzing the configurational effects of multiple factors. It was first developed by sociologist Ragin (1987) based on set theory and provides a new method for solving complex causal relationships10. The expression of any function is not the result of a single factor, but the result of the combination of various factors. Different factor combinations can express the same function, but they can also express different functions, and there is no symmetric relationship between the function and a single factor. These causal complexities are exactly what this theory and method try to solve11. At the end of the 1980s and the beginning of the 1990s, the QCA method was mostly applied in the fields of political science and sociology, and research was carried out using macro comparison methods. In recent years, the QCA method has attracted the attention of management scholars in dealing with large samples and complex configuration issues and has been widely used in the fields of digital transformation and information systems, strategic management, marketing management, corporate governance, public management, etc.12. On the other hand, scholars have also begun to use the QCA method to solve some “meso” and “micro” level management issues.
There are three common technologies in the QCA method: crisp set Qualitative There are three common technologies in the QCA method: crisp set Qualitative Comparative Analysis (csQCA), multi-value set Qualitative Comparative Analysis (mvQCA), and fuzzy set Qualitative Comparative Analysis (fsQCA). Among them, csQCA is the mainstream application of QCA, but it can only handle binary variables. This limitation leads to the loss of variable information, which further increases the difficulty and challenge of analysis11. mvQCA uses multi-value classification, which is more suitable for dealing with multi-category phenomena than csQCA. However, csQCA and mvQCA are only suitable for dealing with category problems, that is, cases can only be assigned to a certain category of categorical variables. The emergence of fsQCA has expanded the application range of QCA technology. In addition to dealing with category problems, fsQCA can also deal with problems of degree changes and partial membership. At this time, fsQCA has the dual attributes of qualitative and quantitative analysis11. Therefore, many scholars have used fsQCA to solve organizational management issues in digital transformation13. This study attempts to seek multiple configurational pathways for sports event data protection through configurational analysis, that is, to answer questions like “Which configurations of conditions may lead to the expected result (improving the effectiveness of sports event data protection)?” Considering the limitations of existing csQCA and mvQCA in the application, the study will use fsQCA for in-depth analysis and discussion of diversified configurational pathways for athlete data protection.
At present, the QCA method has been widely used in questionnaire design, secondary data, and case studies14. Usually, when using the QCA method for analysis, the first task is to select conditional variables. How to identify the conditions of the configuration has become a difficult point of this method. Currently, there are two main methods for identifying conditions: induction and deduction15. Induction is mainly exploratory, mainly relying on the induction and summary of past research and experience, and then incorporating variables that play a role alone into the configurational conditional variables. Deduction is based on a certain theoretical framework to propose conditional variables. There are already studies that have proposed conditional variables for data protection based on the TOE theoretical framework, which provides a reference for this study. Therefore, the study will use the deductive method, based on the TOE theoretical framework, to propose conditional variables for athlete data protection (this part will be detailed in 4). In the QCA method, the selection of conditions and cases needs to be controlled within a certain range. No matter which configuration analysis method is used, the number of conditional variables selected should not be too many, generally between 4 and 716. At the same time, the increase in the number of conditions will lead to an exponential increase in the number of combinations17. Therefore, the number of cases and the number of conditions need to be maintained in a certain proportion. Generally speaking, the number of cases corresponding to 4–7 conditional variables is 10–40, which belongs to the medium sample. At present, the number of cases in existing studies is usually between 10 and 50, and some are between 50 and 80. However, there is still a certain gap in the sample size required for most quantitative (statistical) analyses.
TOE framework
The occurrence of the issue of athlete data protection stems from the rapid development of digital technology. The intervention of digital technology has not only greatly improved the level of sports competition and fairness, but also enhanced the watchability of the event, which has also led to increased data risks and frequent infringements. For example, some infringers carry out continuous event infringements by changing domain names and website names. In response, sports event parties or data service parties can only work hard in all aspects of data collection, use, and storage to enhance the protection of athlete data. Therefore, the TOE framework, which is a comprehensive analysis framework for technology application scenarios, provides more effective support for explaining and analyzing the influencing factors of organizational adoption and implementation of innovation.
The TOE (Technology-Organization-Environment) framework was proposed by Tornatizky and Fleischer (1990). The framework emphasizes dividing the conditions affecting technology application into three categories: technological, organizational, and environmental conditions. Among them, technological conditions refer to the characteristics of the technology itself and its relationship with the organization. This condition focuses on whether the technology matches the organizational structure characteristics and application capabilities, and whether it can bring potential benefits to the organization, including technological management capabilities, technological infrastructure, etc.18; organizational conditions mainly include many aspects such as organizational size, business scope, institutional arrangements, communication mechanisms, etc.19; environmental conditions mainly include the market structure in which the organization is located, external government regulatory policies, and other aspects20.
This study employs the TOE framework to construct the antecedents of athlete data protection for two main reasons. First, according to the existing literature, the environmental level (such as the government’s legal and policy environment) determines the enforcement and implementation effectiveness of athlete data protection policies. Many studies have emphasized the need to improve the protection system for athletes’ personal information through legal means, such as perfecting the protection system through international regulations21. Or by combining the particularities of the sports industry to further improve relevant legislation, detailing “Professional Sports Regulations,” “Sports Event Activity Management Regulations,” and “Sports Club Regulations.” However, some scholars have attempted to promote the protection of sports event data rights and interests by improving technological and organizational factors, such as proposing the use of big data encryption technology to protect user privacy data; or by improving organizational institutional arrangements and communication mechanisms to protect sports event data22. Second, some Chinese research based on the TOE framework analyzes the manifestation of data silos in national fitness, pointing out that technology, organization, and environment will jointly affect data sharing and data governance. And some research points out that when the sports governance structure is not well-fitted, technology is merely an external tool and cannot exert real effectiveness. Effective data governance will enhance data protection capabilities. Therefore, although the aforementioned studies do not directly point to data protection or use the TOE framework, they all ultimately point to the impact of the interaction of technology, organization, and environmental factors on data protection. This indicates that it is appropriate and necessary to discuss athlete data protection issues based on the TOE framework.
Conceptual framework and research hypothesis
Based on the TOE framework proposed by Tornatsky and Fleischer (1990), and referring to existing studies that apply the TOE framework to data analysis and data protection23,24, as well as the utilization scenarios of athlete data, this study constructs a fine-tuned and expanded TOE framework from a configurational perspective24. Based on this foundation, research hypotheses are proposed. From a configurational perspective, various conditions do not exist independently but work together synergistically through reinforcement or offset matching. Therefore, the study will use Partial Least Squares Structural Equation Modeling (PLS-SEM), a multivariate statistical analysis method based on the method of partial least squares, to verify whether various conditions significantly impact the athlete data protection effectiveness (APE).
Technological Aspects. Referring to the TOE framework in Li24, the technological conditions specifically includes two second-level conditions: the event organizer’s technological processing capability (OTI) and the event organizer’s technological management capability (OTM). The event organizer’s technological processing capability refers to the information technology capabilities mastered by the event organizer, which is also the foundation of athlete data security. With the empowerment of digital technology in sports events, it has become a routine operation in professional events to use data visualization content to assess one’s status and the situation of opponents. Event organizers have also begun to strengthen their information technology capabilities to provide a richer range of operations, such as the “Tennis IQ” sports performance analysis platform released by Tennis Data Innovations, which can use the virtual stadium, real-time data display, and other visual content to let players better understand their strengths and weaknesses in the game, and view detailed information about opponents25. Therefore, the event organizer’s technological processing capability mainly emphasizes the event organizer’s information technology level in the collection, processing, application, and protection of athlete data. However, merely having technological processing capabilities without effective data management cannot move the risk of athlete data leakage forward. Therefore, in the technological aspects, the event organizer’s technological management capability will also affect the protection effectiveness of athlete data. The event organizer’s technological management capability mainly refers to the management capability of the event data organizer to integrate various athlete data and respond quickly to external changes, thereby serving the interests of various stakeholders in the sports event26. Protecting athlete data requires not only hardware facilities but also professional management to form effective protection at the source of data. At this stage, most event organizers are limited by the lack of professional technology and personnel and often seek external technical support, such as cooperating with data service companies. However, the initial management and protection of athlete data still depend on the information technology level and professional management of the event organizer.
H1: OTI has a positive impact on APE.
H2: OTM has a positive impact on APE.
Organizational Aspects. Referring to the TOE framework in Li24, the organizational conditions specifically includes two second-level conditions: the event organizer’s readiness (OAD) and the event organizer’s data management system (OMS). The development of information technology can “recreate the organization,” but it is also subject to the backlash of organizational conditions27. Organizational conditions usually include organizational size, business scope, institutional arrangements, communication mechanisms, and so on28. In the protection of athlete data, the technical processing and management level of the event organizer determines whether effective advance prevention and post-event control can be achieved. The readiness of the event organizer, as a structural safeguard for technological development, will have a significant impact on the effectiveness of athlete data protection. The readiness of the event organizer can also be understood as the “attention” of the event organizer to data protection, which will directly determine the priority order of the event organizer for a series of matters and resources, thereby forming strong protection externally. The event organizer’s data management system mainly emphasizes the definition and specification of data quality, data standards, data update speed, and the degree of openness of the data itself. In the protection of athlete data, the event organizer needs to reach an agreement with the athlete on the content, scope, and use of data collection, thereby strictly controlling the athlete’s data and forming constraints throughout the process from data production to data utilization to ensure the confidentiality of the data.
H3: OAD has a positive impact on APE.
H4: OMS has a positive impact on APE.
Environmental Aspects. Referring to the TOE framework in Li24, the environmental conditions mainly refers to the government’s legal policy environment (GR). Government regulation usually affects the implementation and effectiveness of athlete data protection policies. Compared with the event data management system and organizational policy system formulated by the event organizer, government regulation emphasizes the clarification of the ownership issues of athlete data through legal policies and effective sanctions when third-party competitors infringe. For example, Garlewicz believes that athlete biometric data is a matter of public rights, and when an athlete’s ABD is collected or used improperly, the athlete has the right to claim damages29. Clarifying the government’s relevant responsibilities and judicial remedies in the protection of athlete data can determine whether the external policy environment is safe and reliable, thereby achieving effective protection of athlete data.
H5: GR has a positive impact on APE.
In summary, this study refers to the TOE framework, combined with the practical scenario of athlete data protection, and deduces five second-level conditions from the three dimensions of technological aspects, organizational aspects, and environmental aspects, constructing a multi-level analysis framework and conceptual model for the impact on athlete data protection (Figs. 1, 2). From a configurational perspective, various conditions do not exist independently but work together synergistically through reinforcement or offset matching. Therefore, this study will further explore how each antecedent condition configuration affects the realization of athlete data protection from a configurational perspective.
Fig. 1.
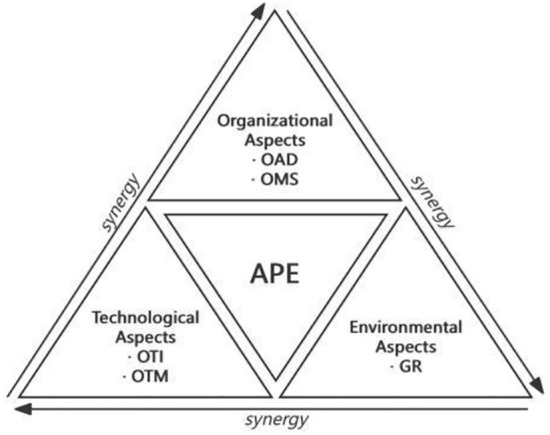
Conceptual framework.
Fig. 2.
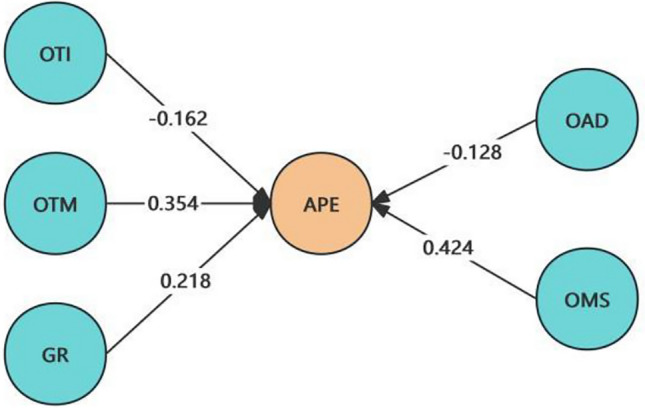
Conceptual model.
Methodology
Variable specification
This study involves a total of six variables. To ensure the effectiveness and reliability of the study, all measurement variables for the antecedent variables are derived from established scales, and adjustments are made accordingly based on Li24 and the specific context of this study. Among them, the measurement of the event organizer’s technological processing capability (OTI) and the event organizer’s technological management capability (OTM) refers to the research of Lu and Ramamurthy (2011), including a total of six measurement items. The measurement of event organizer’s readiness (OAD) and event organizer’s data management system (OMS) is adapted from the research of Wang et al. (2019) and Lu and Ramamurthy (2011), including a total of six measurement items. The measurement items for government regulation (GR) are adapted from the research of Wirtz et al. (2007), including a total of three items. The measurement items for athlete data protection effectiveness (APE) refer to the research of Krasnova et al. (2010), including a total of three items. Finally, a questionnaire including 18 measurement items is formed. All measurement items are set using a 5-point Likert scale, with 1–5 representing an increasing level of agreement (1 = Strongly Disagree, 5 = Strongly Agree) (Table 1).
Table 1.
Research variables.
| Antecedent variables | Coding | Supporting literature | |
|---|---|---|---|
| Technological aspects | Event organizer’s technological processing capability | OTI | Lu and Ramamurthy30 |
| Event organizer’s technological management capability | OTM | ||
| Organizational aspects | Event organizer’s readiness | OAD | Wang et al.31 |
| Event organizer’s data management system | OMS | Lu and Ramamurthy30 | |
| Environmental aspects | Government regulation | GR | Wirtz et al.32 |
| Result variable | Athlete data protection effectiveness | APE | Krasnova et al.33 |
Data collection
The study employs a questionnaire survey to collect relevant data. It adheres to all applicable ethical guidelines and regulations, ensuring compliance with both institutional and legal standards. The study strictly follows data protection and privacy regulations to safeguard the confidentiality and integrity of the information gathered. The study protocol has been meticulously reviewed and approved by the School of Economics and Management at Chengdu Sports University, further validating the research methodology and its alignment with ethical research practices. All questionnaire items (18 in total) and corresponding responses (mainly in the form of Likert scales) are listed in the Supplementary Information. The questionnaire is sent through online platforms (including WeChat and Questionnaire Star) or offline (face-to-face), and respondents voluntarily (click on the link/fill in manually) complete the questionnaire. In this process, respondents have been informed that “submitting answers” is considered informed consent, and the data they provide will be used only for this study, and anonymity is guaranteed. And all participants gave informed consent for use of their data for research purposes. The sample selection follows the case selection principles of the QCA method, that is, the homogeneity of the overall cases and the heterogeneity between cases. First, the sample group is defined as athletes participating in large-scale sports events (such as CBA professional leagues, single championship events, etc.) [the classification of events refers to the classification method of Chinese scholar Ye Qinghui (2003)]. Large-scale events refer to sports events that have a significant impact on the hosting location and can generate good economic benefits. Secondly, considering the impact of different sports on the survey results, this study mainly selects sports with more data services applied in China, such as basketball, football, e-sports, etc. Finally, the respondents are determined to be athletes who have participated in the above-mentioned large-scale sports events. This survey obtains the contact information of the research subjects through various single-sport associations and collects data through telephone, WeChat, and face-to-face filling methods. From July to September 2023, a total of 60 questionnaires were issued. Data cleaning was carried out by checking duplicate IDs and setting questionnaire answers. At the same time, after excluding invalid questionnaires with incomplete items, most items as extreme values, and all items the same, 56 valid questionnaires were obtained, with an effective recovery rate of 93.33%. In addition, the fsQCA method is more suitable for small and medium-sized sample studies. According to the case number requirements of Rihoux and Ragin (2008), the number of cases in this study has exceeded the minimum case standard and belongs to a medium sample study11.
Statistical analysis
First, SmartPLS4.0 statistical software is used to test the measurement properties of the model, and Bootstrapping converges after the 5th iteration. The results show that in terms of model reliability, the α coefficients of each potential factor are all greater than 0.7 (the minimum value is 0.766, and the maximum value is 0.892), and the CR values of the composition reliability indicators are all greater than 0.7 (the minimum value is 0.865, and the maximum value is 0.993), showing that the model has good internal consistency and composition reliability. In terms of the convergent validity of the model, the AVE values of each potential factor are all greater than 0.5 (the minimum value is 0.681, and the maximum value is 0.823), showing that the measurement model has good convergent validity (Table 2). In terms of the discriminant validity of the model, according to the Fornell-Larcker Criterion, since the square root of the AVE value of each potential factor is all greater than the correlation coefficient of that factor with any other potential factor (Table 3), it is determined that the measurement model has good discriminant validity.
Table 2.
Reliability test.
| Variable | 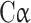 |
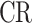 |
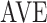 |
Minimum factor loading | |
|---|---|---|---|---|---|
| Technological aspects | OTI | 0.784 | 0.870 | 0.692 | 0.750 |
| OTM | 0.766 | 0.865 | 0.681 | 0.788 | |
| Organizational aspects | OAD | 0.833 | 0.894 | 0.739 | 0.743 |
| OMS | 0.841 | 0.898 | 0.747 | 0.814 | |
| Environmental aspects | GR | 0.812 | 0.888 | 0.726 | 0.817 |
| Result variable | APE | 0.892 | 0.933 | 0.823 | 0.885 |
Table 3.
The square root of AVE value of potential factors and the correlation coefficient between factors.
| APE | GR | OAD | OMS | OTI | OTM | |
|---|---|---|---|---|---|---|
| APE | 0.907 | |||||
| GR | 0.332 | 0.852 | ||||
| OAD | 0.325 | 0.345 | 0.860 | |||
| OMS | 0.416 | 0.233 | 0.850 | 0.864 | ||
| OTI | 0.251 | 0.149 | 0.402 | 0.459 | 0.832 | |
| OTM | 0.416 | 0.236 | 0.234 | 0.352 | 0.672 | 0.825 |
Secondly, it is necessary to analyze whether there is a problem of collinearity between the potential factors in the model. In PLS-SEM, collinearity between potential factors is usually judged by the variance inflation factor (VIF). In the model, there are 5 predictive variables for the dependent variable of athlete data protection effectiveness, and the VIF is below the critical value of 5. Therefore, it can be determined that there is no collinearity problem between the predictive variables in the model. The significance test of the path relationship in the structural equation model uses Bias-Corrected and Accelerated (BCa) Bootstrap and a two-tailed test (the significance level is set at 0.05), and the calculation results are shown in Fig. 2 and Table 4.
Table 4.
Model path coefficient and significance level.
| Path relationship | Path coefficient | 97.5% Confidence interval | Significance | Hypothesis test |
|---|---|---|---|---|
| OTI—> APE | − 0.162 | [− 0.439, 0.237] | Not significant | H1Not established |
| OTM—> APE | 0.354* | [0.003, 0.631] | Significant | H2 established |
| OAD—> APE | − 0.128 | [− 0.623, 0.314] | Not significant | H3Not established |
| OMS—> APE | 0.424 | [− 0.008, 0.892] | Not significant | H4Not established |
| GR—> APE | 0.218 | [− 0.042, 0.486] | Not significant | H5Not established |
*Indicates that the path coefficient difference reaches the significance level (P < 0.05).
The results show that the event organizer’s technological management capability has a significant positive impact on the athlete data protect effectiveness, with a path coefficient of 0.354 (P < 0.05), and hypothesis H2 is established; other predictive variables have no significant positive impact on the effectiveness of athlete data protection, and hypotheses H1, H3, H4, and H5 are not established. On the other hand, it is found that the f2 values of OTM, OMS, and GR are 0.090, 0.064, and 0.056, respectively. According to J. COHEN’s determination standard (an f2 value of about 0.02 is a weak impact, about 0.15 is a moderate impact, and about 0.35 is a high impact), it can be seen that the event organizer’s technological management capability, the event organizer’s data management system, and government regulation have a weak impact on the effectiveness of athlete data protection34. This indicates that each single factor has a certain influence on the protection of athlete data, but the influence is weak. Therefore, the study will further explore how each factor can enhance data protection effectiveness through a synergistic or offsetting linkage.
Data analysis and empirical results
Variable calibration
The study obtained data on each variable based on the questionnaire survey. Each variable includes 3 measurement items. The study uses the average score of each variable as the final score for that variable and refers to the research of Fiss35 and Greckhamer36 to construct calibration anchors. The upper quartile (75%), median (50%), and lower quartile (25%) of the sample descriptive statistics are selected as the full membership threshold, crossover point, and non-membership threshold, respectively. The percentile function is used to calculate the anchors for each variable (Table 5), and the calibration function in fsQCA 4.1 software is used to calibrate the integrated data.
Table 5.
Variable calibration anchor point.
| Variable | Anchor point | |||
|---|---|---|---|---|
| Full affiliation value | Junction | Totally unaffiliated values | ||
| Technological aspects | OTI | 4.001 | 3.334 | 2.668 |
| OTM | 4.001 | 3.334 | 2.668 | |
| Organizational aspects | OAD | 4.001 | 3.334 | 2.334 |
| OMS | 4.001 | 3.001 | 2.334 | |
| Environmental aspects | GR | 3.668 | 3.334 | 2.668 |
| Result variable | APE | 4.001 | 3.301 | 2.301 |
Necessity analysis
Necessary conditions are the conditions that must exist for the result to occur and are the basis for fuzzy set truth table analysis. Since the truth table analysis is essentially a sufficiency analysis, detecting whether there is a single necessary condition is a prerequisite for the next analysis. Generally, a condition with a consistency greater than 0.9 is considered a necessary condition, indicating that the antecedent condition is a necessary condition for athlete data protection. A condition with less than 0.9 is not a necessary condition, indicating that the explanatory power of the antecedent condition is weak37. According to the analysis results, none of the antecedent conditions can constitute a necessary condition for athlete data protection when considered alone, indicating that athlete data protection is influenced by a variety of conditions and requires further analysis of the configuration of antecedent conditions (Table 6).
Table 6.
Necessity test of antecedent conditions.
| Antecedent conditions | APE | ~ APE | ||
|---|---|---|---|---|
| Consistency | Coverage | Consistency | Coverage | |
| OTI | 0.614855 | 0.591465 | 0.530802 | 0.490242 |
| ~ OTI | 0.470083 | 0.510646 | 0.557665 | 0.581621 |
| OTM | 0.648212 | 0.626246 | 0.477436 | 0.442857 |
| ~ OTM | 0.423315 | 0.457621 | 0.597063 | 0.619703 |
| OAD | 0.607290 | 0.657728 | 0.431232 | 0.448417 |
| ~ OAD | 0.490715 | 0.473300 | 0.670845 | 0.621227 |
| OMS | 0.634800 | 0.654842 | 0.472779 | 0.468251 |
| ~ OMS | 0.484525 | 0.489066 | 0.651504 | 0.631378 |
| GR | 0.539546 | 0.617960 | 0.446275 | 0.490744 |
| ~ GR | 0.555365 | 0.510914 | 0.652579 | 0.576400 |
The configuration analysis of different conditions mainly aims to answer the question, “Which configurations of conditions can lead to the desired result?” Therefore, based on the analysis of single necessary conditions, the study uses fsQCA4.1 software to analyze the configuration of conditions that achieve high effectiveness of athlete data protection. Each condition configuration represents a different path to achieve the same result. First, the study conducts a fuzzy set truth table analysis on the integrated data, selecting a case frequency threshold of 1 and a consistency threshold greater than or equal to 0.8. In QCA analysis, the case frequency threshold is usually chosen as 1 or 2 as the critical value to distinguish between relevant configurations and “logical remainders.” A larger threshold should be chosen when the sample is large enough; on the contrary, considering that the case sample of this study is small to medium-sized, a case frequency threshold of 1 is chosen. In addition, the consistency threshold measures the consistency relationship between each configuration and the result set. Usually, the consistency threshold should not be lower than 0.75. If it is lower than 0.75, it means there is substantial inconsistency, so the consistency threshold is set to be greater than or equal to 0.811. To avoid the problem of “subset relations” and reduce contradictory configuration issues, the study also takes into account the PRI consistency (proportional reduction in inconsistency). For the selection of the PRI consistency threshold, the study refers to Greckhamer’s (2020) research and maintains the PRI value above 0.6512. Through standard analysis, complex solutions (excluding logical remainders), parsimonious solutions (including logical remainders but not evaluating their rationality), and intermediate solutions (using logical remainders but only those with a rational basis) are obtained. Usually, the conditions appearing in the parsimonious solution are called core conditions, and the remaining conditions appearing in the intermediate solution but not in the parsimonious solution are called peripheral conditions, that is, the causal relationship with the result is weaker. Finally, three condition configurations for athlete data protection are derived (Table 7).
Table 7.
Configurational pathways of antecedent conditions for athlete data protection.
| Antecedent conditions | APE | ||
|---|---|---|---|
| T1 | T2 | T3 | |
| OTI | 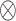 |
● | |
| OTM | ● | ● | ● |
| OAD | ● | ● | ● |
| OMS | ● | ● | 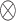 |
| GR | ● | ● | |
| Consistency | 0.843 | 0.906 | 0.841 |
| Raw coverage | 0.173 | 0.251 | 0.108 |
| Unique coverage | 0.042 | 0.129 | 0.043 |
| Overall solution consistency | 0.848 | ||
| Overall solution coverage | 0.355 | ||
Black circle (●) indicate the presence of a condition, and circles with “x” (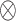 ) indicate its absence. Large circle; core condition. Small circle; peripheral condition. Blank space; “don’t care” condition38.
) indicate its absence. Large circle; core condition. Small circle; peripheral condition. Blank space; “don’t care” condition38.
As can be seen from Table 7, the three condition configurations for athlete data protection have an overall consistency of 0.848 and an overall solution coverage of 35.3%. The consistency values for the individual solutions are 0.843, 0.906, and 0.841, all of which exceed the minimum threshold of 0.75, indicating that the three condition configurations are sufficient conditions for athlete data protection38. They have good reliability and strong explanatory power for the result variable.
To better identify the differences between different pathways, the study summarizes the three condition configurations as Single Organization Support Type (T1), Organization-Environment Support Type (T2), and Organizational Support Absent Type (T3) based on the logical characteristics they exhibit. Further explanations are as follows (“*” indicates the simultaneous presence of all antecedent conditions; “~” indicates the absence of the antecedent condition).
Configuration T1: ~OTI*OTM*OAD*OMS indicates that regardless of whether the government regulatory environment is good or not, as long as the event organizer has a sound event organization structure and event organization management system, it can enhance the effectiveness of athlete data protection and achieve athlete data protection. For example, FIFA has created a unified standard for “Global Football Wearable Technology” and introduced the “FIFA Quality Programme for Wearable Electronic Performance and Tracking Systems,” which provides a unified quality standard for the application of wearable technology in sports events, thereby enhancing the security of athlete data after collection39. In this configuration, government regulation is blank, indicating that the condition of government regulation can be present or absent. Assuming that government regulation is absent, this configuration can be called the “Single Organization Support Type,” which emphasizes the importance of the event organizer’s organizational capabilities.
Configuration T2: OTM*OAD*OMS*GR indicates that regardless of whether the event organizer has the corresponding technical capabilities, as long as there is a good policy regulatory environment and a sound event organization structure and management system, it can also enhance the effectiveness of athlete data protection. For example, by enacting legislation to determine the property rights of athletes’ data and implementing a licensing system; formulating data protection manuals in the form of rules and regulations, and improving the channels for athletes to appeal and complain. In this configuration, the technical processing capability of the event organizer can be present or absent. To better analyze the next step, it is assumed that the technical processing capability of the event organizer is absent, so this configuration is called the “Organization-Environment Support Type,” which mainly emphasizes the importance of the event organizer’s organizational capabilities and the regulatory strength of government departments.
Configuration T3: OTI*OTM*OAD ~ OMS*GR indicates that in a sound government regulatory environment, with good technical processing and management capabilities, even if the event organizer’s data management system is not sound or absent, effective regulation and preemptive measures can be formed to actively protect athlete data. For example, in response to the protection of athletes’ biometric information, the United States has four states, including Illinois, Texas, Washington, and California, that have officially introduced relevant legislation, forming a special regulatory model for the protection of athletes’ biometric information8. The ATP has set up Tennis Data Innovations (TDI) to be responsible for the collection, management, and development of match statistics data. TDI has reached an agreement with Sportrader, which provides advanced analysis, data visualization, and data protection technology40. This configuration can be called the “Organizational Support Absent Type,” which mainly emphasizes the importance of the event organizer’s technical capabilities and the regulatory strength of the government.
Robustness testing
To ensure the robustness of the research results, this study conducted two robustness tests. The first test adjusted the consistency threshold from the original 0.8 to 0.85. The second test raised the PRI consistency from 0.65 to 0.7. The results of the two tests were consistent with the original configuration paths. The overall consistency increased from 0.848 to 0.875, and the overall coverage decreased from 0.355 to 0.312. It can be seen that the research results are stable.
Discussion
The study employs fsQCA to analyze the antecedent conditions for athlete data protection, resulting in three condition configurations, including: “Single Organization Support Type” “Organization-Environment Support Type” and “Organizational Support Absent Type” (1) The “Single Organization Support Type” reflects the impact of organizational-level factors on the effectiveness of athlete data protection. This condition configuration demands a high level of organizational management capability from event organizers, who need to have a well-established organizational management system to provide effective protection for athletes’ data, but this inevitably faces the issue of high organizational costs. (2) The “Organization-Environment Support Type” is influenced by both organizational and environmental factors in the effectiveness of athlete data protection, indicating that event organizers have a relatively comprehensive organizational management system, coupled with strong government support and strict regulation, which can also enhance the effectiveness of athlete data protection to a certain extent. At this point, the organizational costs for event organizers are controlled, and the government can also use administrative measures for macro control. (3) The “Organizational Support Absent Type” is to strengthen the effectiveness of athlete data protection through technical and environmental factors. This configuration shows that event organizers have good technical conditions, can respond quickly to external changes, and serve event decision-making, and with strong government support and strict regulation, it can also enhance the effectiveness of athlete data protection to a certain extent.
Conclusions and limitations
Conclusions
In practice, the factors affecting the protection of athletes’ data are not independent or singular but interact with each other. Existing research, limited by methodological constraints, does not clearly define the causal relationships between various influencing factors and the protection of athletes’ data. Therefore, this study, based on configurational theory and employing fsQCA methodology, analyzes the configurations of antecedent conditions affecting the protection of athletes’ data and arrives at the following findings.
The study initially identified three distinct configurations for athlete data protection: “Single Organization Support Type” “Organization-Environment Support Type” and “Organizational Support Absent Type” The “Single Organization Support Type” enhances the effectiveness of athlete data protection solely through organizational-level factors; the “Organization-Environment Support Type” strengthens protection by combining organizational and environmental factors; the “Organizational Support Absent Type” enhances the protection through technological and environmental factors despite a lack of robust organizational support. These findings provide a reference for the strategic formulation of athlete data protection.
The “Single Organization Support Type” configuration emphasizes the role of litigation costs and organizational management costs. However, under this configuration, government regulatory intensity is a missing condition, relying on the organizational management system to function effectively. In this regard, government departments could attempt to guide the marketization of sports events and establish a standardized system for sports event data, thereby forming a guide for the application of athlete data and promoting the maximization of benefits in the management of athlete data by event organizers. At this time, the role of event organizers is more critical, and it is essential to focus on improving the organizational management system of sports events and clarifying the standardized processes for the collection, processing, utilization, and development of athlete data.
The “Organization-Environment Support Type” configuration not only emphasizes the role of litigation costs and organizational management costs but also the government’s punitive measures. Under this configuration, there is an emphasis on the joint protection of data security by the government and event organizers. The government establishes a data compliance review mechanism, increases the investigation and handling of the behavior of various data entities, raises the cost of illegal activities, and thus deters third-party violations; event organizers need to work with government departments to establish a data breach notification system, jointly forming a standardized review and regulatory mechanism. This not only enhances the protection of athlete data rights and interests but also allows for the sharing of regulatory costs, reducing the regulatory costs for government departments and event organizers, and improving regulatory efficiency.
In the “Organization Support Absent Type” configuration, due to the absence of organizational conditions, technical levels and government support become crucial. At this time, event organizers need to enhance their technical capabilities to compensate for deficiencies in organizational management. Given the limitations of technical processing costs, strong government support is required, such as establishing special funds for sports events to support event organizers in improving data security technology.
Recommendations
Establishing a legal framework to regulate the rights and interests of all parties
Regarding the protection of athletes’ data, China’s “Civil Code” preliminarily confirms general principles for the protection of personal information. The “Personal Information Protection Law” stipulates the rights of individuals in personal information processing activities, including the right to be informed, the right to decide, the right to restrict processing, the right to refuse processing, the right to access and copy, the right to ensure the accuracy and completeness of information, the right to delete, and the right to request explanations. These provisions form a strong protection for the personal data of the general public but are significantly insufficient for the protection of athletes’ data. In professional sports events, the requirements for athletes’ informed consent are almost always problematic, such as the deprivation of informed consent rights, the suppression of informed consent rights by reality, and the increased cost of informed consent. At present, China’s “Sports Law” only responds to the protection of property rights related to sports events and does not clearly address the allocation of rights to sports event data, the circulation and use of event data, and the security and supervision of event data. In this regard, the study suggests that reference can be made to the EU’s legislative framework for personal data protection. Firstly, the property rights of athletes to their personal data in sports events should be determined and written into the “Sports Law”; secondly, corresponding local regulations and administrative rules should be formed; finally, social sports organizations should form suggestions and opinions around the authorization and use range of athletes’ data, the notification of athletes’ data leaks, etc., thereby forming a comprehensive and multi-level legal protection framework.
Ensuring the rights and interests of all parties through the regulatory function of public power
"The true content of all epoch-making systems is formed due to the needs of the period in which these systems arise.” All of this is inseparable from the leading role of the government as an absolute leader. Compared with legislation, the government’s flexible and efficient policy tools are highly favored. From the perspective of policy science, “policy is the prototype of law, and law is the standardized and regularized policy.” Therefore, the introduction of a series of policies will help promote the development of relevant legislation for sports data protection. In the previous text, the study proposes government strategies under the “Single Organization Support Type,” “Organization-Environment Support Type,” and “Organizational Support Absent Type” configurations, with the core being to give necessary support to the protection of athletes’ data through further improvement of the system and mechanism. In current practice, it can be seen that some Chinese government departments are continuously improving policies for the development of digital sports, such as the “Zhejiang Province Sports Reform 'Fourteenth Five-Year Plan’” and the “Zhejiang Province Digital Sports Fitness 'Fourteenth Five-Year Plan’.” However, existing policies have defects such as abstraction vagueness, and lack of rigidity. In this regard, government departments first need to clarify the content, scope, and usage boundaries of athletes’ data collection, and then clarify the scope of rights holders of sports event data. On this basis, form rules for the grading and classification of sports data, and continuously improve the standardization system of event data. Secondly, the government needs to further increase the compliance review of athletes’ data during the hosting of sports events, clearly include data security and protection content in the rules and regulations of sports event activity safety supervision services, and supervise the circulation and use of data in various sports events throughout the process. Finally, the government can take certain incentive measures to encourage event organizers to upgrade digital technology and strengthen the protection of athletes’ data at the technical level. For example, improve the incentive mechanism and provide special financial support for event data to promote event organizers and data service companies to take the initiative to participate in data security governance.
Improving the implementation details of events to clarify the rights and interests of all parties
Legislation is not the only means of protecting athletes’ data. In the digital age, technical issues need to be answered by technology. Faced with the increasingly severe problem of athletes’ data security, on the one hand, it is necessary to clarify the rights and interests of relevant rights holders through relevant legislation and policies. On the other hand, it is also necessary to form private protection of data through organizational management and technical measures.
In terms of organizational management, event organizers can try to establish a data leak notification system centered on data protection with all stakeholders to further strengthen the monitoring of data risks; in addition, event organizers also need to further improve the implementation details of sports events. Given the current situation of domestic sports events, most sports events have not clarified the rights and interests of various data subjects in the implementation details, which leads to difficulties in determination in the event of data infringement disputes. In this regard, event organizers need to further clarify the collection range and usage methods of athletes’ data; clarify the development and use range of data by data service companies, as well as the rights and interests of data service companies in event commercial data and extended data products.
In terms of technical measures, event organizers and data service companies can solve the problem of athletes’ data protection through technical solutions, such as establishing a “trusted data space.” At present, 16 companies in China have tried to explore the establishment of a trusted industrial data space, and pilot projects have been carried out in Guangdong, Jiangsu, Chongqing, and other places. The trusted data space is based on the distributed control of all parties, providing a safe and trustworthy public space for data circulation, in which network security, evidence tracing, data control, and other technologies are mainly used to ensure the control of the entire process of data transactions. So, for athletes’ data, event organizers, governments, and data service companies can try to establish a similar “data space,” thus shifting from post-event law enforcement to pre-event prevention, and providing strong protection for athletes’ data through front-end and back-end joint technical encryption means.
Main contributions and future research
The main contribution of this study is the use of configurational theory and fsQCA methodology to deeply analyze various factors affecting the protection of athletes’ data and to reveal three key configurational pathways: “Single Organization Support Type,” “Organization-Environment Support Type,” and “Organizational Support Absent Type,” providing policymakers with insights for constructing a framework for the protection of athletes’ data, while also providing strategic support for the sustainable development of the global sports industry. In addition, the study also explores the role of sports data protection in promoting the coordinated development of society, economy, and environment, contributing to the practice of achieving global sustainable development goals. However, the study also has limitations, such as a relatively small sample size, which may affect the universality of the results, and it mainly focuses on the context of Chinese sports events, which may limit the international applicability of the research results. Future research can expand the sample size, consider sports events in different countries and regions, and further explore the long-term impact of technological development on the protection of athletes’ data, providing a more comprehensive and in-depth understanding of global sports data governance.
Supplementary Information
Author contributions
Funding acquisition: X.Y.G. Project administration: X.Y.G. Resources: X.Y.G. Supervision: X.Y.G. Validation: X.Y.G. Writing—original draft: X.Y.L. Writing—review & editing: X.Y.L. & M.Q.G.
Funding
Funding was provided by National Social Science Fund of China (Grant Number 23BTY012).
Data availability
All relevant data are within the paper and its Supporting Information files.
Declarations
Competing interests
The authors declare no competing interests.
Footnotes
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
The online version contains supplementary material available at 10.1038/s41598-024-83792-8.
References
- 1.Tennis Team Packages, Tennis Analytics. https://www.tennisanalytics.net/services/teams/ (2021).
- 2.Dos-Santos, M. A., Alguacil, M., Pérez-Campos, C. & Velasco-Vizcaíno, F. How to improve sports fans’ attitudes toward the sponsor through brand management? A PLS and QCA approach. Phys. Cult. Sport Stud. Res.100(1), 61–74 (2023). [Google Scholar]
- 3.Li, X. & Guo, X. Factors affecting the protection of data rights in sports events: A configurational analysis. Sci. Rep.14, 1 (2024). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 4.Beekun, R. I. & Glick, W. H. Organization structure from a loose coupling perspective: A multidimensional approach. Decis. Sci.32(2), 227–250 (2001). [Google Scholar]
- 5.Baerg, A. Big data, sport, and the digital divide: Theorizing how athletes might respond to big data monitoring. J. Sport Soc. Issues41(1), 3–20 (2017). [Google Scholar]
- 6.Bialik, C. The people tracking every touch, pass and tackle in the world cup; http://fivethirtyeight.com/features/the-people-tracking-every-touch-pass-and-tackle-in-the-world-cup/ (2014).
- 7.Kennedy, H. & Moss, G. Known or knowing publics? Social media data mining and the question of public agency. Big Data Soc.2, 2 (2015). [Google Scholar]
- 8.Brown, S. M. & Brison, N. T. Big data, big problems: Analysis of professional sports leagues’ CBAs and their handling of athlete biometric data. J. Legal Asp. Sport30(1), 63–81 (2020). [Google Scholar]
- 9.Jessop, A. & Baker, T. A. III. Big data bust: Evaluating the risks of tracking NCAA athletes’ biometric data. Texas Rev. Entertain. Sports Law20(1), 81–112 (2019). [Google Scholar]
- 10.Ragin, C. C. The Comparative Method (University of California Press, 1987). [Google Scholar]
- 11.Rihoux, B. & Ragin, C. C. Configurational Comparative Methods: Qualitative Comparative Analysis (SAGE Publications, 2008). [Google Scholar]
- 12.Greckhamer, T., Furnari, S., Fiss, P. C. & Aguilera, R. V. Studying configurations with qualitative comparative analysis: Best practices in strategy and organization research. Strateg. Organ.16(4), 482–495 (2018). [Google Scholar]
- 13.Park, Y. K. & Mithas, S. Organized complexity of digital business strategy: A configurational perspective. MIS Q.44(1), 85–127 (2020). [Google Scholar]
- 14.Misangyi, V. F. & Acharya, A. G. Substitutes or complements? A configurational examination of corporate governance mechanisms. Acad. Manag. J.57(6), 1681–1705 (2014). [Google Scholar]
- 15.Ketchen, J. D. J., Thomas, J. B. & Snow, C. C. Organizational configurations and performance: A comparison of theoretical approaches. Acad. Manag. J.36(6), 1278–1313 (1993). [Google Scholar]
- 16.Berg-Schlosser, D. & De Meur, G. Comparative research design: Case and variable selection. In Configurational Comparative Methods: Qualitative Comparative Analysis (QCA) and Related Techniques (eds Rihoux, B. & Ragin, C. C.) 19–32 (Sage Publications, 2009). [Google Scholar]
- 17.Ragin, C. C. The Comparative Method: Moving Beyond Qualitative and Quantitative Strategies (University of California Press, 1987). [Google Scholar]
- 18.Chau, K. & Tam, Y. Factors affecting the adoption of open systems: An exploratory study. MIS Q.21(1), 1–24 (1997). [Google Scholar]
- 19.Walker, R. M. Internal and External Antecedents of Process Innovation: A Review and Extension. Public Manag. Rev.16(1), 21–44 (2014). [Google Scholar]
- 20.Oliveir, T. & Martins, M. F. Literature review of information technology adoption models at firm level. Electron. J. Inf. Syst. Eval.14(2), 312–323 (2011). [Google Scholar]
- 21.Ghibellini, N. Some aspects of the EU’s new framework for personal data privacy protection. Bus. Lawyer73(1), 207–213 (2018). [Google Scholar]
- 22.Mitropoulos, D. et al. PDGuard: An architecture for the control and secure processing of personal data. Int. J. Inf. Secur.19(4), 479–498 (2020). [Google Scholar]
- 23.Ghaleb, E. A. A. et al. The assessment of big data adoption readiness with a technology–organization–environment framework: A perspective towards healthcare employees. Sustainability13, 8379 (2021). [Google Scholar]
- 24.Li, X. & Guo, X. Factors affecting the protection of data rights in sports events: A confgurational analysis. Sci. Rep.14(1), 5353 (2024). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 25.Elevating Tennis Performance: ATP & TDI Unveil Tennis IQ Analytics Platform. https://www.atptour.com/en/news/atp-tdi-unveil-tennis-iq-analytics-platform (2023).
- 26.Wiesböck, F., Hess, T. & Spanjol, J. The dual role of IT capabilities in the development of digital products and services. Inf. Manag.57(8), 103389 (2020). [Google Scholar]
- 27.Mergel, I. & Desouza, K. C. Implementing open innovation in the public sector: The case of Challenge. gov. Public Manag. Rev.73(6), 882–290 (2013). [Google Scholar]
- 28.Grimmelikhuijsen, S. G. & Feeney, M. K. Developing and testing an integrative framework for open government adoption in local governments. Public Adm. Rev.77(4), 579–590 (2017). [Google Scholar]
- 29.Garlewicz, A. Athlete biometric data in soccer: Athlete protection or athlete athlete biometric data in soccer: Athlete protection or athlete exploitation?. DePaul J. Sports Law16(1), 1–34 (2020). [Google Scholar]
- 30.Lu, Y. & Ramamurthy, K. R. Understanding the link between information technology capability and organizational agility: An empirical examination. MIS Q.35(4), 931–954 (2022). [Google Scholar]
- 31.Wang, N., Xue, Y., Liang, H., Wang, Z. & Ge, S. T. The dual roles of the government in cloud computing assimilation: an empirical study in China. Inf. Technol. People32(1), 147–170 (2019). [Google Scholar]
- 32.Wirtz, J., Lwin, M. O., Lwin Jerome D. Williams. Causes and consequences of consumer online privacy concern. International Journal of Service Industry Management.18(4), 326–348 (2007).
- 33.Krasnova, H., Spiekermann, S., Koroleva, K. & Hildebrand, T. Online social networks: Why we disclose. J. Inf. Technol.25, 109–125 (2010). [Google Scholar]
- 34.Cohen, J. Statistical Power Analysis for the Behavioral Sciences (Lawrence Erlbaum, 1988). [Google Scholar]
- 35.Fiss, P. C. Building better causal theories: A fuzzy set approach to typologies in organization research. Acad. Manag. J.54(2), 393–420 (2011). [Google Scholar]
- 36.Greckhamer, T. CEO compensation in relation to worker compensation across countries: The configurational impact of country-level institutions. Strat. Manag. J.37(4), 793–815 (2016). [Google Scholar]
- 37.Ragin, C. C. & Fiss, P. C. Net Effects Analysis Versus Configurational Analysis: An Empirical Demonstration (University of Chicago Press, 2008). [Google Scholar]
- 38.Morgan, R. Redesigning social inquiry: Fuzzy sets and beyond by Charles C. Ragin. Soc. Forces88(4), 1934–1936 (2010). [Google Scholar]
- 39.Electronic Performance and Tracking Systems (EPTS). https://inside.fifa.com/technical/football-technology/standards/epts (2016). [DOI] [PMC free article] [PubMed]
- 40.SportsRadar Wins Major Bid For ATP Rights. https://www.atptour.com/en/media/media-releases (2023).
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Supplementary Materials
Data Availability Statement
All relevant data are within the paper and its Supporting Information files.


