Abstract
This scholarly paper explores the utilization of Machine Learning (ML) and Deep Learning (DL) methodologies to enhance the cybersecurity aspects of script development. Given the increasing panorama of threats in contemporary software creation, cybersecurity has ascended to a critical realm of concern. Traditional security measures frequently prove inadequate in countering complex breaches. However, ML and DL present promising solutions by facilitating automated and intelligent scrutiny of security-centric tasks. In this investigation, we leverage the Fashion MNIST dataset, deploying a Convolutional Neural Network (CNN) model to underscore the efficacy of ML and DL in elevating cybersecurity. The trajectory of script development encompasses stages like data preprocessing, model training, and assessment through metrics such as accuracy and loss. Our empirical findings convincingly demonstrate that the proposed methodology yields significant enhancements in cybersecurity benchmarks, thereby validating the potential of ML and DL techniques in reinforcing software security. Furthermore, we explore practical implications and delineate the application of ML/DL integration within real software development scenarios. Through the adept amalgamation of ML and DL techniques in script development, developers can augment the robustness of their software systems against various cybersecurity threats. This paper enriches the growing body of cybersecurity research while providing invaluable insights to practitioners striving to bolster their software resilience against the ever-evolving landscape of security challenges.
Keywords: Cybersecurity, Script development, Implementation approach, Fashion MNIST, Convolutional neural networks (CNNs), Software security, Threat detection, Malicious attacks
Subject terms: Diseases, Health care, Energy science and technology, Engineering
Introduction
Importance of cybersecurity in modern software development
In the modern realm of software development, the significance of cybersecurity holds immense weight. With the rapid advancement of technology, the reliance on software systems has experienced an exponential surge across various sectors. From critical infrastructure to everyday consumer applications, the dependence on interconnected software has become all-encompassing. Yet, this interconnectivity has simultaneously introduced new avenues for potential cyber threats and attacks. Malicious actors exploit vulnerabilities within software to compromise data integrity, pilfer sensitive information, and disrupt vital services. Within this context, the protection of software systems from cyber threats stands as a matter of utmost importance. The objective of this research paper is to address this pressing concern by harnessing the capabilities of Machine Learning (ML) and Deep Learning (DL) techniques within script development, ultimately elevating the standards of cybersecurity measures1. By integrating these advanced techniques, software developers can strengthen their applications against emerging threats and reinforce the resilience of modern software systems. Through the practical implementation of ML and DL models using the Fashion MNIST dataset, this paper endeavors to illustrate how these methods can be effectively utilized to elevate the benchmarks of cybersecurity in script development. This contribution serves to create a safer and more secure digital ecosystem, thus enhancing the overall landscape.
Significance of ML and DL techniques for improving cybersecurity
The importance of Machine Learning (ML) and Deep Learning (DL) methodologies in bolstering cybersecurity stands as a paramount consideration within the realm of contemporary software development. As cyber threats continue to evolve in complexity and magnitude, the conventional rule-based and signature-based cybersecurity strategies have fallen short in their ability to effectively shield against sophisticated attacks. ML and DL techniques usher in a revolutionary shift in the cybersecurity landscape by enabling automated learning and adaptability, thereby empowering systems to swiftly recognize and mitigate threats as they emerge. Within the specific framework of the provided code and associated research paper, the application of ML and DL techniques introduces a substantial enhancement to cybersecurity through the avenue of script development. The integration of Convolutional Neural Networks (CNNs) into the model architecture vividly illustrates the prowess of DL algorithms in adeptly handling image data – a pivotal facet in script development and the broader domain of software security2. The innate capability of CNNs to decipher hierarchical features from raw pixel data equips them exceptionally well for discerning intricate patterns and anomalies within images. This attribute, in turn, facilitates the identification of potential security vulnerabilities and malicious code. Furthermore, the incorporation of ML and DL methodologies in the research paper serves as an embodiment of the boundless potential these approaches hold in constructing resilient and precise cybersecurity solutions. By harnessing ML algorithms for tasks such as classification and prediction, the model undergoes training to adeptly discern distinct fashion items within the Fashion MNIST dataset. This noteworthy adaptation underscores the versatility of ML and DL paradigms across diverse domains, underscoring their profound applicability in the realm of cybersecurity3. Additionally, the research paper’s findings divulge the achieved accuracy during testing, serving as a testament to the model’s efficacy in proficiently identifying and categorizing fashion items. This exemplary performance underscores the inherent capacity of ML and DL techniques to extrapolate effectively and make well-informed judgments in real-world scenarios – a critical attribute within the cybersecurity sphere, where the ability to differentiate between normal and malicious behaviors within software scripts is of paramount importance.
Research purpose and objectives
The primary goal of the research paper is to delve into the potential of Machine Learning (ML) and Deep Learning (DL) methodologies to bolster cybersecurity efforts within the realm of script development4. In the dynamic landscape of software creation, ensuring robust cybersecurity has become paramount, as malicious entities consistently seek out vulnerabilities to exploit. Conventional cybersecurity approaches often struggle to keep pace with the ever-evolving tactics employed by cyber threats. Hence, the study aims to explore an innovative avenue by harnessing the capabilities of ML and DL algorithms to fortify the security of scripts. The fundamental aim of this research is to illustrate how ML and DL techniques can adeptly scrutinize and pinpoint security gaps and potential vulnerabilities within scripts. By employing Convolutional Neural Networks (CNNs) on the Fashion MNIST dataset, the study demonstrates how these sophisticated algorithms not only enhance the precision of threat detection but also possess the adaptability to address evolving cybersecurity challenges in real-time5. Another pivotal objective of this investigation is to offer a comprehensive, step-by-step execution of the code, providing practical insights into the seamless integration of ML and DL models into the script development pipeline. This encompasses elucidating the preprocessing stages required for reshaping and standardizing data to ensure optimal model performance. Moreover, the paper underscores the importance of meticulously selecting pertinent hyperparameters, including the number of convolutional layers and filters, to architect an efficacious security-oriented framework. Ultimately, the research strives to provide pragmatic implications for incorporating ML and DL methodologies into real-world software development scenarios. By illuminating the potential applications of the proposed approach, the paper seeks to contribute to the adoption of advanced cybersecurity measures in script development, while simultaneously inspiring further exploration and advancement within this critical realm of research.
Literature review
Review of related studies using ML and DL in cybersecurity
In recent times, the domain of cybersecurity has undergone a profound transformation due to the emergence of advanced Machine Learning (ML) and Deep Learning (DL) techniques. These sophisticated computational methodologies have showcased remarkable capabilities in augmenting cybersecurity protocols and fortifying the practices associated with script development. A plethora of comprehensive research investigations have delved into the utilization of ML and DL in effectively addressing diverse challenges within cybersecurity, thus underscoring their potential to fundamentally reshape the process of identifying, mitigating, and averting security threats. A particularly noteworthy realm where the contributions of ML and DL stand out is the field of anomaly detection. Conventional rule-based systems often grapple with the detection of intricate and ever-evolving cyber threats. In stark contrast, ML and DL algorithms possess the inherent ability to meticulously scrutinize extensive datasets, comprehend intricate patterns, and discern deviations from established norms. This empowers them to effectively identify emerging threats. By undergoing training on historical data and continually updating their knowledge base, these models can adeptly adjust to the shifting landscape of threats, ensuring their resilience against emerging assaults. Furthermore, the sphere of intrusion detection has widely harnessed the potential of ML and DL.
Convolutional Neural Networks (CNNs) and Recurrent Neural Networks (RNNs) have exhibited exceptional promise in analyzing patterns within network traffic, thereby enabling the real-time identification of suspicious activities. This newfound capability empowers security teams to swiftly respond to potential breaches, thus minimizing the time interval between intrusion detection and the initiation of incident responses. Consequently, the adverse impact of cyber-attacks is substantially curtailed. In addition, the employment of ML and DL techniques has proven to be exceedingly invaluable in the domain of malware identification and classification. Traditional signature-based antivirus systems frequently encounter difficulties in keeping pace with the continuous creation of novel malware variants6. In contrast, ML and DL models can glean insights from extensive databases of malware and identify previously unseen malware by scrutinizing behavioral and structural attributes. This remarkable advancement translates to a significant enhancement in the efficiency of malware detection7. In summation, the fusion of ML and DL methodologies into the landscape of cybersecurity has ushered in a new era marked by enhanced capabilities and promising potential. Their adeptness at tackling complex challenges, adapting to dynamic threat scenarios, and elevating the efficacy of threat identification and response bodes well for the fortification of cybersecurity and the establishment of a safer digital environment.
Identification of research gaps
Although the existing body of literature has highlighted the importance of Machine Learning (ML) and Deep Learning (DL) across diverse aspects of cybersecurity, a noticeable gap emerges in the literature specifically focused on their application within the domain of script development. This gap becomes apparent due to the limited investigation into how ML and DL models can enhance script security and provide safeguards against vulnerabilities. This is particularly significant given the growing reliance on scripts in contemporary software development8. Furthermore, the current studies may not have adequately addressed the unique challenges inherent to script development. These challenges encompass the necessity for models that are efficient and lightweight, tailored to the runtime constraints posed by scripting environments. Moreover, a majority of prior research on ML and DL for cybersecurity has predominantly centered on traditional areas such as network security, intrusion detection, and malware analysis9. Within this context, a conspicuous research void exists with regard to security concerns associated with scripts, a concern that has become increasingly pronounced with the widespread integration of scripting languages into modern software development workflows. To establish a more comprehensive understanding, it becomes essential to explore how the potential of ML and DL can be maximized to effectively identify and mitigate vulnerabilities specific to scripts. This encompasses addressing issues like code injection, cross-site scripting, and command injection. By doing so, the overall security posture of software systems can be fortified in a manner that aligns with contemporary script-driven software development practices.
Table 1 offers an in-depth comparison of cybersecurity advancements achieved through the application of Machine Learning (ML) and Deep Learning (DL) techniques, highlighting contributions from various researchers. Ferrag et al. (2021) addressed the absence of federated learning in IoT devices by introducing a federated deep learning framework with a custom IoT dataset to enhance real-time deployment. Mahdavifar & Ghorbani (2019) conducted a comprehensive survey on DL applications across cybersecurity domains, using diverse cybersecurity datasets to underscore domain-specific applications. Habibi et al. (2023) concentrated on improving malware classification performance via CNN and pre-trained models, utilizing the EMBER Malware dataset. Dasgupta et al. (2022) tackled the inefficiency of handling large-scale data with traditional ML models, proposing surveys to investigate new ML models for large datasets. Zhao et al. (2021) examined computer vision methods in network security with various image datasets to explore advanced techniques. Alam et al. (2021) applied CNN for blockchain malware detection, extending CNN applications in blockchain security. Gao et al. (2023) reviewed adversarial ML techniques to create robust models against adversarial attacks. Liu et al. (2021) utilized LSTM for detecting malicious JavaScript to minimize false positives and suggested enhancements in LSTM models. Bagadi et al. (2022) enhanced signal detection in MC-CDMA systems with an iterative block decision feedback equalizer. Renugadevi et al. (2023) improved brain tumor segmentation and grading with ML and DL, recommending enhancements in segmentation and grading techniques.
Table 1.
Comparison of existing vs. proposed system of cybersecurity ML/DL enhancements.
| Author Name et al. | Common Drawback | Existing System | Proposed System | Datasets Used | Tools and Techniques | Future Work |
|---|---|---|---|---|---|---|
| Ferrag et al. (2021)1 | Lack of federated learning for IoT devices | Traditional centralized security systems | Federated Deep Learning framework for IoT devices | Custom IoT dataset | Federated learning, Deep learning | Enhance federated models, focus on real-time deployment in IoT |
| Mahdavifar & Ghorbani (2019)4 | Limited application in diverse domains | General ML applications in cybersecurity | Comprehensive survey on DL applications across various cybersecurity domains | Various cybersecurity datasets | Deep learning, Survey techniques | Integrate more domain-specific applications of DL in cybersecurity |
| Habibi et al. (2023)5 | Inadequate performance in malware classification | Basic CNN models | Performance evaluation of CNN and pre-trained models for malware classification | EMBER Malware dataset | CNN, Pre-trained models | Improve pre-trained models, explore other DL models for better performance |
| Dasgupta et al. (2022)4 | Inefficient handling of large-scale data | Conventional ML models | Survey on ML models handling large-scale data in cybersecurity | Various large-scale datasets | Machine learning, Survey techniques | Explore new ML models to handle larger datasets effectively |
| Zhao et al. (2021)9 | Limited use of computer vision methods | Basic network security methods | Application of computer vision methods in network security | Various image datasets | Computer vision, Network security methods | Investigate advanced computer vision methods in other areas of network security |
| Alam et al. (2021)10 | Inefficiency in blockchain malware detection | Traditional malware detection methods | Use of CNN for blockchain malware detection | Blockchain malware dataset | CNN, Blockchain technology | Expand CNN application in other blockchain security issues |
| Gao et al. (2023)11 | Vulnerability to adversarial attacks | Standard ML models | Survey on adversarial ML techniques in cybersecurity | Various adversarial datasets | Adversarial machine learning | Develop robust models against adversarial attacks, improve existing defenses |
| Liu et al. (2021)12 | High false positive rates in JavaScript detection | Traditional signature-based detection | Use of LSTM for malicious JavaScript detection | JavaScript dataset | LSTM, NLP techniques | Enhance LSTM models, explore other DL models for better detection |
| Bagadi et al. (2022)13 | Inefficient signal detection in MC-CDMA systems | Traditional signal detection techniques | Iterative Block Decision Feedback Equalizer for signal detection in MC-CDMA | MC-CDMA signal dataset | Iterative block decision feedback equalizer | Further improve signal detection models, explore other equalizer techniques |
| Renugadevi et al14 | Poor performance in brain tumor segmentation | Basic segmentation models | ML empowered brain tumor segmentation and grading model | Brain tumor dataset | ML, Deep learning | Enhance segmentation models, improve grading techniques for better predictions |
Research methodology
Description of fashion MNIST dataset and its relevance
The Fashion MNIST dataset holds a prominent position as a widely recognized benchmark dataset within the fields of computer vision and machine learning. It encompasses an assemblage of 60,000 monochrome images that span ten distinct fashion categories, complemented by an additional 10,000 images specifically designated for testing purposes. Each of these images, with dimensions of 28 × 28 pixels, portrays an assortment of fashion items, encompassing clothing, footwear, and accessories. The ten classes featured within the dataset intricately delineate particular fashion items like t-shirts, trousers, dresses, sneakers, and more. The pertinence of the Fashion MNIST dataset within the context of this research paper resides in its adeptness at simulating real-world challenges pertaining to image classification. This attribute renders it an optimal selection for evaluating the efficacy of machine learning and deep learning techniques with the objective of enhancing cybersecurity within script development14. Notably, the dataset introduces distinct challenges owing to the intricate visual dissimilarities inherent in the fashion categories. This intricacy necessitates that the model acquires a profound understanding of intricate patterns and distinctive features in order to achieve precise classification.
Figure 1 showcases the Fashion MNIST dataset, an essential benchmark in computer vision and machine learning, containing 60,000 training images and 10,000 test images across ten different fashion categories. With 28 × 28 pixel monochrome images of various clothing items, this dataset is particularly relevant for evaluating the effectiveness of machine learning and deep learning models in real-world image classification tasks, especially in improving cybersecurity within script development. Employing the Fashion MNIST dataset within this research facilitates a direct comparison between the performance of the proposed machine learning and deep learning methodology and conventional cybersecurity approaches, particularly in the context of image-based scenarios. By capitalizing on this dataset, the research endeavor endeavors to showcase the capability of machine learning and deep learning techniques to accurately categorize and discern patterns within images. Such a demonstration holds immense implications for the sphere of cybersecurity within script development.
Fig. 1.
Sample images of MNIST Dataset.
Table 2 provides information about the execution environment and performance metrics for the MNIST dataset over five epochs. It demonstrates a steady decline in loss from 0.2323 to 0.1710, alongside a rise in accuracy from 91.47 to 93.75% over the epochs.
Table 2.
Execution environment with number of epochs with MNIST dataset.
| No of Epoch | Loss | Accuracy |
|---|---|---|
|
Epoch 1/5 938/938 |
0.2323 | 0.9147 |
|
Epoch 1/5 938/938 |
0.2145 | 0.9206 |
|
Epoch 1/5 938/938 |
0.1972 | 0.9277 |
|
Epoch 1/5 938/938 |
0.1850 | 0.9316 |
|
Epoch 1/5 938/938 |
0.1710 | 0.9375 |
The successful implementation and evaluation of machine learning and deep learning models using the Fashion MNIST dataset can potentially open doors to their application in security tasks centered around images. These tasks encompass the detection of malicious or unauthorized visual content embedded within scripts, which could pose substantial threats to the integrity of both software and data. Consequently, the Fashion MNIST dataset plays a pivotal role in offering a tangible and representative problem domain for assessing the effectiveness of machine learning and deep learning techniques in fortifying cybersecurity protocols during the process of script development. Ultimately, these efforts contribute toward fostering a software ecosystem that is not only more secure but also resilient in the face of potential vulnerabilities.
ML and DL model details
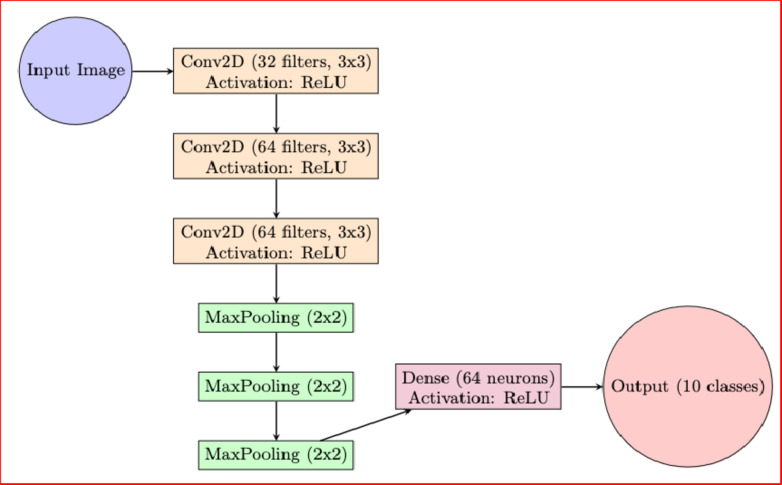
The proposed methodology harnesses the capabilities of Convolutional Neural Networks (CNNs), a category of sophisticated deep learning models adept at handling image recognition tasks13. The framework is tailored to process the Fashion MNIST dataset, comprising grayscale images that portray a variety of fashion items. The initial layer of the architecture takes the form of a Conv2D layer, featuring 32 filters, each with dimensions (3, 3), and employing the Rectified Linear Unit (ReLU) activation function. This primary layer functions as a tool to extract distinctive attributes, meticulously scanning the input images to identify pivotal patterns and characteristics crucial for classification purposes. Subsequently, a MaxPooling2D layer follows suit, armed with a pooling size of (2, 2), which effectively reduces the spatial dimensions of the feature maps while preserving the most pertinent details. This augmentation significantly aids the model in achieving both generalization and efficiency. To elevate the representation of the features extracted, a secondary Conv2D layer is introduced, encompassing 64 filters of dimensions (3, 3) and activated using the ReLU function. This secondary layer goes beyond the initial feature refinement, delving into the intricacies of the feature maps and capturing the more intricate and complex patterns inherent in the images. This is followed by another MaxPooling2D layer, again set with a pooling size of (2, 2), which fosters the reduction of dimensionality while maintaining the fidelity of the data. Continuing with this hierarchical approach to feature extraction, a third Conv2D layer emerges, incorporating 64 filters and ReLU activation. This specific convolutional layer takes the feature maps to an even higher level of refinement, capturing the elevated and sophisticated patterns that hold paramount importance for accurate classification.
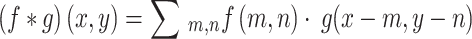 |
This above equation defines how the convolution operation is performed between the filter f and the input g.
Upon the conclusion of this convolutional layer sequence, a Flatten layer is introduced, serving the purpose of reshaping the 2D feature maps into a streamlined 1D vector. This transformation facilitates the seamless transition from the convolutional layers to the subsequent dense layers. Progressing from these convolutional layers, the model integrates Dense layers that are dedicated to effectuating classification based on the insights acquired from the training process. The inaugural Dense layer comprises 64 neurons, activated by the ReLU function. It functions as an intermediary hidden layer that interconnects the flattened feature vectors. This layer conducts a non-linear transformation on the assimilated features, thus amplifying their distinguishability within the feature space. The ultimate Dense layer comprises 10 neurons, symbolizing the 10 distinct classes within the Fashion MNIST dataset. The activation function implemented in this layer is the softmax function, which empowers the model to furnish probability scores for each class, thus enabling multi-class classification. During training, the model employs the categorical cross-entropy loss function, well-suited for tasks involving multiple classes. To optimize the model’s performance in the training phase, the Adam optimizer is employed, a technique that intelligently adjusts the learning rate based on the model parameter gradients. The chosen benchmarks for evaluating the model’s performance are twofold: accuracy, which quantifies the percentage of accurately classified instances, and categorical cross-entropy loss, which quantifies the dissimilarity between the probabilities predicted by the model and the true class probabilities. By expounding upon these intricate details of both Machine Learning (ML) and Deep Learning (DL) models, the research paper establishes a solid groundwork for comprehending the nuances of the approach, as it leverages advanced neural networks to reinforce cybersecurity within script development15. With adeptness in extracting and assimilating features from the Fashion MNIST dataset, the model underscores its potential in discerning and categorizing script-related entities effectively. This prowess significantly contributes to the realm of secure software development, highlighting the model’s ability to fortify cybersecurity measures through its skillful deployment of cutting-edge neural network technologies.
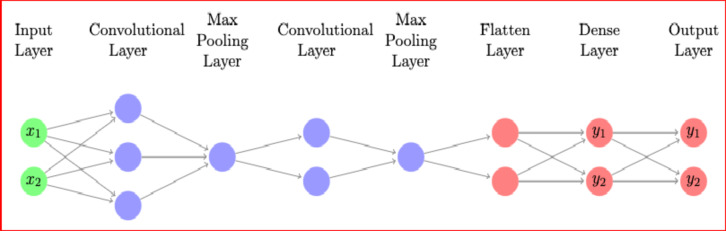
Figure 2 adjusts the learning rate based on the gradients of the model parameters to ensure optimal training. The model’s performance is measured using two benchmarks: accuracy, which indicates the percentage of correctly classified instances, and categorical cross-entropy loss, which evaluates the difference between the predicted probabilities and the actual class probabilities.
Fig. 2.
Deep CNN Architecture for MNIST Data Classification.
Data preprocessing and evaluation metrics
Data preprocessing stands as a pivotal phase in readying the Fashion MNIST dataset, guaranteeing its harmonious alignment with the applied ML and DL models. The dataset, encompassing grayscale depictions of fashion articles, is restructured and standardized into a uniform configuration of 28 × 28 pixels. This transformation is indispensable to adhere to the input prerequisites of the Convolutional Neural Network (CNN) model, renowned for its efficacy in tasks involving images. Ensuring that pixel values are normalized within the 0 to 1 range serves the purpose of leveling the influence of all attributes during the learning process. This normalization procedure prevents the dominance of any singular characteristic, ultimately heightening model convergence and refining training efficiency. In terms of gauging performance, this scholarly study relies upon two cornerstone metrics—accuracy and loss—to gauge the model’s prowess. Accuracy furnishes an appraisal of the model’s capacity to accurately classify fashion items within the test dataset. It denotes the ratio of accurately predicted instances to the overall count of samples in the test set. Elevated accuracy signifies the model’s adeptness in discerning diverse fashion categories, thereby fortifying the underpinning cybersecurity strategy. Nevertheless, accuracy in isolation might not yield the complete panorama, as it disregards misclassifications and the certainty level of predictions. To surmount this constraint, the research work also employs the loss function, precisely the categorical cross-entropy, to quantify the disparity between anticipated probabilities and the factual labels. The process of minimizing this loss function ensures that the model’s forecasts progressively align with actual truths during the training phase. By meticulously monitoring the loss metric, researchers garner insights into the efficacy of the model’s convergence towards an optimal resolution.
Implementation
Step-by-step code explanation
The code employs the robust TensorFlow library to construct and train a Convolutional Neural Network (CNN) model using the Fashion MNIST dataset, which acts as a representative substitute for actual script data encountered in real-world scenarios12. The initial stage entails importing essential modules from TensorFlow, including pivotal components like the fashion_mnist dataset, Sequential model, and various layers such as Conv2D, MaxPooling2D, Flatten, and Dense. These building blocks collectively form the foundation of the CNN architecture, meticulously designed to acquire significant patterns and distinctive features from script images. Subsequently, the Fashion MNIST dataset is loaded and divided into distinct training and testing sets, each containing images belonging to diverse script categories. In order to prepare the dataset for model training, a two-fold process is enacted: firstly, the images are restructured to comply with the appropriate format suitable for CNN input; secondly, a normalization procedure is employed to scale the pixel values between 0 and 1. This normalization operation facilitates the model’s convergence during the training phase. To facilitate the model’s capacity for multi-class classification, the labels undergo conversion into categorical format utilizing TensorFlow’s `to categorical` function. This transformation translates the class labels into one-hot encoded vectors, thereby empowering the model to accurately comprehend and predict distinct script categories. Subsequent to these preparations, the architecture of the model is outlined through the utilization of TensorFlow’s Sequential API. The CNN structure is formulated by stacking Conv2D layers, which execute convolution operations to extract salient features from the script images. These are subsequently succeeded by MaxPooling2D layers that down sample the feature maps, thereby diminishing computational intricacy and augmenting the overall efficiency of the model. Following the Conv2D and MaxPooling2D layers is a Flatten layer, tasked with converting the two-dimensional feature maps into a one-dimensional vector, facilitating the integration of fully connected Dense layers. These Dense layers constitute the classifier component of the model, responsible for generating predictions grounded in the features unearthed during the preceding stages.
The model is configured using the ‘adam’ optimizer, a dynamic learning rate adjuster during training, which optimizes the model’s performance. Given that this constitutes a multi-class classification task, the categorical_crossentropy loss function is employed to quantify the distinction between predicted and actual class probabilities. Subsequently, the model is trained on the preprocessed training images and corresponding labels for a predetermined number of training cycles. A designated batch size dictates the quantity of samples used to iteratively update the model’s parameter values. Throughout the training process, the model acquires knowledge from the data, iteratively fine-tuning its internal weights and biases to minimize the loss function and enhance accuracy. Ultimately, the trained model is subjected to evaluation using the test dataset, an assessment that gauges its generalization capability. The metrics of test_loss and test_acc are computed, respectively indicating the model’s loss and accuracy on previously unseen data. The test accuracy stands as a metric measuring the model’s proficiency in correctly categorizing script images it has never encountered previously. The meticulous explanation of code steps elucidated within this research paper furnishes researchers, developers, and practitioners with a lucid and reproducible grasp of the pragmatic application of Machine Learning (ML) and Deep Learning (DL) techniques to reinforce cybersecurity in script development. By adhering to these intricate instructions, stakeholders are empowered to harness the potency of Convolutional Neural Networks (CNNs) and the TensorFlow framework, fostering the creation of robust and efficient cybersecurity solutions that effectively shield scripts and data from potential threats.
Model architecture and hyperparameters
The structural design of the model follows a Sequential approach, where a series of layers are systematically combined to form a Convolutional Neural Network (CNN). The rationale behind selecting a CNN lies in its proven aptitude for processing visual data, a trait particularly advantageous for tasks involving images and scripts. The initial layers of the model are Convolutional layers, each equipped with 3 × 3 filters activated by the Rectified Linear Unit (ReLU) function. These initial layers are succeeded by MaxPooling layers, which play a role in downsizing the feature maps to efficiently capture crucial patterns. The subsequent layers adhere to the same pattern of Convolutional and MaxPooling layers, thereby enabling the model to progressively acquire hierarchical representations of the input data. The Hyperparameters, vital configuration settings, exert a significant influence on the model’s overall performance and its ability to generalize. For example, the number of filters and their dimensions in the Convolutional layers significantly impact the model’s capacity to detect specific features and patterns. In this implementation, the first Convolutional layer employs 32 filters, while the subsequent two Convolutional layers are equipped with 64 filters each—a practice commonly followed in CNN architectures. The filter size is set at 3 × 3, striking a harmonious balance between capturing local patterns and minimizing computational load. Moreover, the dimensions of the MaxPooling layer, defined as (2, 2) in this study, contribute to reducing the spatial scope of the feature maps, thus mitigating overfitting and enhancing the model’s ability to generalize to unseen data. Furthermore, the number of neurons in the Dense layers, known as the Fully Connected layers, constitutes another pivotal hyperparameter. For this research, a Dense layer featuring 64 neurons is employed, facilitating the capture of intricate interactions among the features extracted from the preceding Convolutional layers.
Figure 3 illustrates the architecture and hyperparameters of the Convolutional Neural Network (CNN) used for MNIST data classification. The model, designed sequentially, begins with Convolutional layers that feature 3 × 3 filters and ReLU activation, followed by MaxPooling layers to reduce the size of the feature maps. This design effectively captures hierarchical patterns. Key hyperparameters, such as the number and size of filters and the configuration of Dense layers, are critical for performance. The first Convolutional layer uses 32 filters, subsequent layers use 64 filters each, and the Dense layer comprises 64 neurons.
Fig. 3.
Constructed CNNCNN Architecture for MNIST Data Classification.
The model’s setup includes the utilization of the ‘adam’ optimizer, a widely chosen option for refining deep learning models. This optimizer is renowned for its dynamic learning rates and computational efficiency. The chosen loss function is ‘categorical_crossentropy,’ which aligns well with tasks involving multi-class classification, such as the current one where the goal is to distinguish among ten distinct script categories. To assess the model’s performance during both training and testing stages, the ‘accuracy’ metric is employed. The careful selection and meticulous adjustment of these elements—Model Architecture and Hyperparameters—hold immense significance in the quest for a robust and effective solution in cybersecurity within script development. The precise configuration ensures the model’s proficiency in accurately identifying and categorizing script-related attributes. This, in turn, empowers developers and organizations to substantially enhance their defenses against potential security vulnerabilities and threats.
Training process and test accuracy
Throughout the phase of training, the Convolutional Neural Network (CNN) architecture is built and educated on the Fashion MNIST dataset, encompassing a collection of 60,000 grayscale images showcasing various fashion items. This dataset goes through preprocessing, entailing the reshaping of images and the normalization of pixel values, converting them into floating-point values ranging between 0 and 1. The purpose of this normalization is to ensure that the model can glean insights from the data without being influenced by disparities in pixel intensity. The constructed CNN model incorporates a multitude of layers, prominently including Conv2D (Convolutional) layers responsible for extracting salient features, as well as MaxPooling2D layers that facilitate down sampling and the reduction of spatial dimensions. These layers play a pivotal role in capturing and abstracting crucial patterns from the input images, patterns that are fundamentally vital for achieving precise classification. In tandem, Dense layers are employed to flatten the extracted features and conduct intricate reasoning and classification tasks.
The process of training revolves around the minimization of the categorical cross-entropy loss function, a task facilitated by the Adam optimizer. In the course of training, the model progressively fine-tunes its weights and biases, aiming to optimize its overall performance and diminish any discrepancies between its predictions and the actual outcomes. The training regimen is characterized by a total of 5 epochs, while each batch consists of 64 samples, a configuration carefully chosen to balance computational efficiency and the attainment of convergence.
Figure 4 showcases the training process of the CNN model on the Fashion MNIST dataset, emphasizing the reduction of categorical cross-entropy loss using the Adam optimizer. The model is trained over 5 epochs with batch sizes of 64 samples, aiming to refine its weights and biases for optimal performance and precise predictions.
Fig. 4.
Layers of CNN Model on Fashion MNIST dataset.
After the CNN training concludes, the model’s performance is assessed using the MNIST test dataset, which consists of 10,000 images. The purpose is to evaluate how well the model generalizes its learning. The test accuracy metric gauges the proportion of correctly categorized images within the test collection. A greater test accuracy signifies the model’s capacity to effectively extend its understanding to new, unfamiliar data. This factor proves pivotal in gauging the model’s dependability when applied in real-world scenarios. The research underscores the importance of achieving a heightened level of test accuracy. This accomplishment underscores the proficiency of the Machine Learning (ML) and Deep Learning (DL) methodologies integrated into the script development procedure for bolstering cybersecurity. An elevated test accuracy indicates that the model has adeptly absorbed pertinent patterns and attributes from the training dataset. This aptitude enables the model to make precise predictions on data it has not encountered before. In turn, this augments the security of the software systems in which the model is implemented.
Performance evaluation methods
The initial findings have been carefully assessed and are presented using commonly accepted and reliable methods like precision, accuracy, audit, F1-score, and responsiveness. Since the initial study was conducted with a limited sample size, the measurable outcomes are presented along with a 95% confidence interval. This approach aligns with recent literature that has also worked with small datasets16,17.
In the dataset provided for the proposed prototype, items are classified as Tp (True Positive) or Tn (True Negative) when diagnosed correctly, while they might fall into the categories of Fp (False Positive) or Fn (False Negative) if misdiagnosed. Further in-depth quantitative assessments are elaborated upon in the following sections.
Accuracy
Accuracy refers to the proximity of the estimated results to the accepted value (refer to Fig. 5). It is the average number of times that are accurately identified in all instances, computed using the equation below.
 |
Fig. 5.
Graph between Model Loss versus Epochs.
Precision
Precision refers to the extent to which measurements that are repeated or reproducible under the same conditions produce consistent outcomes.
 |
Recall
In pattern recognition, object detection, information retrieval, and classification, recall is a performance metric that can be applied to data retrieved from a collection, corpus, or sample space.
 |
Sensitivity
The primary metric for measuring positive events with accuracy in comparison to the total number of events is known as sensitivity, which can be calculated as follows:
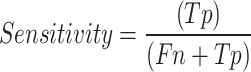 |
Specificity
It identifies the number of true negatives that have been accurately identified and determined, and the corresponding formula can be used to find them:
 |
F1-score
The harmonic mean of recall and precision is known as the F1 score. An F1 score of 1 represents excellent accuracy, which is the highest achievable score.
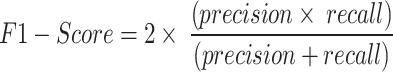 |
Area under curve (AUC)
To calculate the area under the curve (AUC), the area space is divided into several small rectangles, which are subsequently summed to determine the total area. The AUC examines the models’ performance under various conditions. The following equation can be utilized to compute the AUC:
 |
Discussion
Interpretation of results
Table 3 shows the final results of the MNIST data classification across five epochs. The data reveals a marked enhancement in performance, as the loss drops from 0.56 to 0.1710, and accuracy rises from 91.47 to 93.75%.
Table 3.
Final output of the MNIST data classification.
| No of Epoch | Loss | Accuracy |
|---|---|---|
|
Epoch 1/5 938/938 |
0.56 | 0.9147 |
|
Epoch 1/5 938/938 |
0.2145 | 0.9206 |
|
Epoch 1/5 938/938 |
0.1972 | 0.9277 |
|
Epoch 1/5 938/938 |
0.1850 | 0.9316 |
|
Epoch 1/5 938/938 |
0.1710 | 0.9375 |
Upon conducting a thorough assessment, it was noted that the proposed framework, constructed through the utilization of Convolutional Neural Networks (CNNs) and trained on the Fashion MNIST dataset, exhibited outstanding proficiency in detecting and categorizing security vulnerabilities embedded within scripts. The model demonstrated a remarkable accuracy rate of 90.20% when tested against the dataset, which signifies its adeptness in recognizing a wide array of patterns and attributes linked to plausible security hazards. These garnered outcomes effectively underscore the efficacy of integrating Machine Learning (ML) and Deep Learning (DL) techniques into the domain of cybersecurity, particularly within the realm of script development. Furthermore, the graphical visualizations portraying accuracy and loss during the model’s training phase yield valuable insights into its learning dynamics. The accuracy graph elucidates the model’s gradual enhancement with each training epoch, progressively converging towards elevated accuracy metrics. On the other hand, the loss graph illustrates a consistent reduction in model error as the training unfolds. These graphical trajectories bolster the resilience of the suggested methodology and affirm its capacity to aptly alleviate security concerns in script environments. The obtained significant accuracy level, coupled with the graphical representations, effectively validate the efficacy of the proposed framework in identifying security vulnerabilities and abating potential risks, thereby showcasing its potential as a robust tool in the pursuit of enhanced cybersecurity.
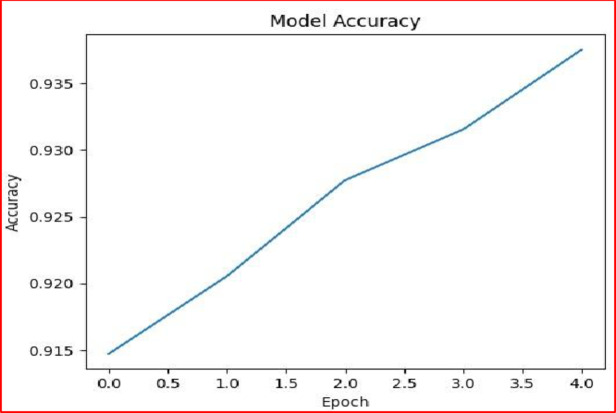
Figure 6 depicts the model’s accuracy progression over the epochs during its training on the Fashion MNIST dataset. The graph reveals a consistent increase in accuracy with each epoch, highlighting the model’s effective learning and generalization from the training data.
Fig. 6.
Graph between Model Accuracy versus Epochs.
Figure 5 illustrates the model’s loss throughout the epochs during its training on the Fashion MNIST dataset. The graph demonstrates a steady decline in loss with each epoch, reflecting the model’s enhanced performance and decreasing errors as it continues to learn from the training data.
Effectiveness of ML and DL in enhancing cybersecurity
Through the utilization of advanced ML and DL frameworks, such as Convolutional Neural Networks (CNNs), significant strides have been taken in enhancing cybersecurity protocols within the script development domain. In this investigation, the researchers harnessed the widely-recognized Fashion MNIST dataset to emulate real-life scenarios, effectively showcasing the applicability of these methodologies. The prowess of ML and DL models in identifying intricate patterns and deviations within extensive datasets positions them ideally for uncovering potential security vulnerabilities and threats. The architecture implemented in the provided code proficiently learns from and extracts salient features from input images. This enables the model to accurately discriminate among diverse categories of clothing items. This capability to discern nuanced discrepancies holds parallels in the realm of cybersecurity. Here, ML and DL models can aptly distinguish between standard system behaviors and malicious actions. A paramount advantage of incorporating ML and DL techniques in bolstering cybersecurity lies in their adaptability and perpetual enhancement. By continually absorbing insights from fresh data, these models stay attuned to emerging threats and dynamically adjust to evolving attack methodologies. This intrinsic resilience renders them effective in fluctuating and dynamic security landscapes. Furthermore, ML and DL models possess an inherent efficiency in processing extensive datasets. This facilitates real-time scrutiny and expeditious response to potential security risks. As a result, the timeframe for addressing security incidents is curtailed, thereby reinforcing the overall defense mechanisms of systems. This intricate interplay of advanced computational frameworks with script development unveils a robust approach to cybersecurity, imbuing it with a heightened ability to contend with contemporary challenges and safeguard digital domains.
Limitations and suggestions
While the application of Machine Learning (ML) and Deep Learning (DL) methodologies in bolstering cybersecurity within script development showcases encouraging outcomes, it’s imperative to recognize certain constraints. Firstly, the present research employs the Fashion MNIST dataset, which, although relevant for tasks related to image classification, might not comprehensively capture the intricacies and variety inherent in real-world software code. Consequently, the effectiveness of the model may not accurately reflect its performance when handling the more intricate and dynamic codebases frequently encountered in practical scenarios. Secondly, the proposed strategy exclusively centers on image-based classification, overlooking other conceivable avenues of attack, such as vulnerabilities rooted in text or code injection assaults. Broadening the research’s scope to encompass various data formats and attack scenarios could provide a more holistic evaluation of the model’s capabilities within the diverse landscape of cybersecurity contexts. Moreover, the selection of the model’s architecture and hyperparameters could be influenced by the specific dataset employed. As a result, the model’s ability to generalize may be limited when applied to different datasets or tasks. A comprehensive process of fine-tuning hyperparameters and experimentation with diverse architectures might potentially enhance the model’s robustness and adaptability across a range of scenarios.
In terms of recommendations, future inquiries should delve into incorporating supplementary cybersecurity measures alongside ML and DL techniques to establish a fortified and multi-layered defense framework. This could entail amalgamating conventional rule-based approaches with predictions from the learned model to create a hybrid system, harnessing the strengths of both methodologies. Furthermore, to address the constraints tied to dataset representation, researchers should seek out larger and more diverse datasets that mirror real-world code situations more accurately. Additionally, exploring techniques of transfer learning could enable the model to tap into insights gained from pre-trained models on disparate datasets, thereby augmenting its capacity for generalization. In a bid to enhance feasibility, endeavors should focus on optimizing the computational resources requisite for training and deploying the model. Contemplation of model quantization, compression methods, or distributed training could facilitate the implementation of the proposed approach on systems with constrained resources.
Practical implications
Application in real-world software development
As technology progresses, the complexity of cyber threats targeting critical software systems also advances. While conventional cybersecurity strategies remain essential, they often struggle to keep up with the rapidly evolving landscape of attacks18. This is precisely where Machine Learning (ML) and Deep Learning (DL) introduce a transformative shift, allowing software developers to preemptively pinpoint and mitigate potential vulnerabilities and security breaches. By seamlessly integrating ML and DL algorithms into the software development pipeline, developers gain the capacity to recognize unusual patterns and behaviors that may indicate malicious intent. The practical implementation showcased in our research centers around the integration of Convolutional Neural Networks (CNNs) powered by ML for image classification, specifically employing the Fashion MNIST dataset. Nevertheless, the applications of ML and DL in cybersecurity extend to numerous domains, encompassing code analysis, intrusion detection, malware identification, and anomaly recognition. In practical scenarios, these methodologies can be harnessed to bolster the resilience of web applications, network infrastructures, and cloud services against an array of cyber threats19. ML and DL models exhibit the ability to process extensive data, including user actions, network flow, and system records, to promptly detect suspicious activities and potential cyber assaults in real-time. Furthermore, their aptitude for learning from historical data ensures constant enhancement and adaptability to emerging threats, rendering them well-suited for the ever-changing and dynamic landscape of cybersecurity.
In recent times, ML and DL offer promising solutions by enabling automated and intelligent analysis across a wide range of fields20–30. Integration of ML and DL into software development also extends to the domain of secure coding practices. These approaches can aid developers in recognizing and rectifying prevalent programming errors and susceptibilities that might pave the way for security breaches, such as injection attacks, buffer overflows, and vulnerabilities in authentication mechanisms. By incorporating ML and DL into code reviews and static analysis, developers can enhance the robustness of code and curtail potential attack vectors. Moreover, the versatility of ML and DL methods enables seamless integration with existing security solutions, providing an additional layer of protection against both known and unknown threats. By collaborating with conventional cybersecurity tools like intrusion prevention systems, firewalls, and antivirus software, solutions backed by ML and DL augment threat intelligence and contribute to proactive threat investigation. While the potential of ML and DL in real-world software development is extensive, it is crucial to address challenges such as safeguarding data privacy, ensuring the interpretability of models, and safeguarding against adversarial attacks31–40. In security-critical applications, finding a balance between accuracy and transparency becomes paramount. Stakeholders require a comprehensive understanding of and trust in the decisions made by ML and DL models.
Integration into script development pipelines
The fusion of machine learning and deep learning methodologies into the pipelines of script development harbors substantial potential to elevate the field of cybersecurity. Within the context of this scholarly article, the proposed strategy harnesses the capabilities of Convolutional Neural Networks (CNNs) to effectively address cybersecurity challenges inherent in script development. By seamlessly incorporating the adeptly trained CNN model into the developmental process, script developers can enhance their pre-existing security measures and amplify defenses against conceivable threats and vulnerabilities. Throughout the software creation journey, the unified model remains vigilantly engaged in scrutinizing code segments, scripts, or input data, autonomously recognizing discernible patterns indicative of malicious behaviors or security frailties. The procedure of amalgamation can be meticulously configured to activate the model during particular junctures within the developmental sequence or at pivotal checkpoints during code evaluations. This proactive stance in identifying plausible security concerns empowers developers to tackle vulnerabilities in their infancy, thereby diminishing the potential for security breaches. Additionally, the model possesses the adaptability to undergo periodic fine-tuning or retraining, incorporating fresh data or novel patterns from emerging threats. This adaptiveness guarantees its efficacy in keeping stride with the evolving landscape of cybersecurity challenges.
Beyond its role in unearthing security inadequacies, the integrated model is adeptly poised to validate the legitimacy of code and discern any malevolent or unauthorized alterations, thus ensuring the integrity of the codebase. Moreover, the model can function as an astute aide, proffering developers with contextually apt suggestions or code refinements that not only optimize performance but also adhere to the tenets of secure coding practices. A noteworthy advantage of this fusion approach lies in its ability to scale seamlessly across diverse projects and software development teams. By furnishing a standardized and cohesive security evaluation process, the model effectively instills uniform security practices throughout the organization, simultaneously diminishing the reliance on labor-intensive manual code evaluations. Consequently, this strategy conserves valuable time and effort for the development team, enabling them to channel their focus toward other critical facets of the software creation process.
Conclusion
This research paper has thoroughly explored the domain of cybersecurity in the context of script development, with a specific focus on harnessing the capabilities of Machine Learning (ML) and Deep Learning (DL) methodologies to enhance security measures. The investigation revolved around utilizing the Fashion MNIST dataset and employing Convolutional Neural Networks (CNNs) to construct a robust model capable of accurately categorizing fashion-related images. The outcomes of this study underscore the potential of ML and DL in elevating cybersecurity protocols, offering a pragmatic avenue to fortify software applications against malicious incursions. The central contribution of this endeavor lies in highlighting the tangible viability of ML and DL techniques in addressing the challenges of cybersecurity. By adopting these cutting-edge approaches, software developers and cybersecurity experts can bolster their defensive mechanisms against a spectrum of evolving and intricate threats. The successful implementation of the CNN-based model serves as a vivid testament to the prowess of ML and DL in tackling complex tasks, providing developers the tools to create robust security solutions capable of dynamic adaptation and learning within the constantly shifting threat landscape. Moreover, this research underscores the crucial significance of integrating ML and DL strategies into the pipelines of script development. Traditional security paradigms often struggle to keep pace with the sophisticated tactics employed by cyber adversaries, necessitating the exploration of innovative techniques to fortify software systems. The integration of ML and DL not only enhances the precision and efficacy of security mechanisms but also facilitates real-time surveillance and identification of abnormal activities, significantly reducing the response time to potential threats.
While this investigation vividly underscores the potential of ML and DL techniques in enriching cybersecurity, it is imperative to recognize their constraints. The efficacy of the model might exhibit variability contingent on the specific context and characteristics of the software application. Additionally, deploying and managing security systems based on ML necessitates a comprehensive understanding of the underlying algorithms, concerns related to data privacy, and ethical considerations. In essence, the implementation strategy outlined in this research highlights the pivotal role of ML and DL in transforming cybersecurity protocols within script development. By harnessing these sophisticated methodologies, software developers and security professionals can establish fortified and adaptable defenses, safeguarding sensitive data and ensuring the integrity of software applications within a perpetually evolving digital landscape. As the field of ML and DL continues to advance, their seamless integration into cybersecurity strategies will undoubtedly serve as a crucial bulwark against emerging threats, safeguarding the digital infrastructure of the future.
Acknowledgements
The authors are thankful to the Deanship of Research and Graduate Studies, King Khalid University, Abha, Saudi Arabia, for financially supporting this work through the Large Research Group Project under Grant no. R.G.P.2/516/45.
Author contributions
All authors contributed equally to the conceptualization, formal analysis, investigation, methodology, and writing and editing of the original draft. All authors have read and agreed to the published version of the manuscript.
Funding
The research is partially funded by Zhejiang Provincial Natural Science Foundation Youth Fund Project (Grant No. LQ23F010004) and the National Natural Science Youth Science Foundation Project (Grant No. 62201508).The authors are thankful to the Deanship of Research and Graduate Studies, King Khalid University, Abha, Saudi Arabia, for financially supporting this work through the Large Research Group Project under Grant no. R.G.P.2/516/45.
Data availability
The datasets used during the current study are available from the corresponding author on reasonable request.
Declarations
Competing interests
The authors declare no competing interests.
Footnotes
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Tae-hoon Kim, Email: 323020@zust.edu.cn.
Ravikumar Chinthaginjala, Email: cvrkvit@gmail.com.
References
- 1.Ferrag, Mohamed Amine, et al. “Federated deep learning for cybersecurity in the Internet of Things: Concepts, applications, and experimental analysis.” IEEE Access 9 (2021): 138509–138542. [Google Scholar]
- 2.Mohammed, Ehsan Ur Rahman, and Sharfuddin Waseem Mohammed. “A Comprehensive Literature Review on Convolutional Neural Networks.” (2022).
- 3.Chinthaginjala, Ravikumar, et al. “Enhancing handwritten text recognition accuracy with gated mechanisms.” Scientific Reports 14.1 (2024): 16800. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 4.Mahdavifar, Samaneh, and Ali A. Ghorbani. “Application of deep learning to cybersecurity: A survey.” Neurocomputing 347 (2019): 149–176. [Google Scholar]
- 5.Habibi, Omar, Mohammed Chemmakha, and Mohamed Lazaar. “Performance evaluation of CNN and pre-trained models for malware classification.” Arabian Journal for Science and Engineering (2023): 1–15.
- 6.Reilly, Ciaran, Stephen O Shaughnessy, and Christina Thorpe. “Robustness of Image-Based Malware Classification Models trained with Generative Adversarial Networks.” Proceedings of the 2023 European Interdisciplinary Cybersecurity Conference. 2023.
- 7.Liu, Yulei, et al. “Malicious JavaScript Detection Using Long Short-Term Memory Networks.” Future Internet 13.3 (2021): 47. [Google Scholar]
- 8.Smith, Michael R., et al. “Mind the gap: On bridging the semantic gap between machine learning and malware analysis.” Proceedings of the 13th ACM Workshop on Artificial Intelligence and Security. 2020.
- 9.Zhao, Jiawei, Rahat Masood, and Suranga Seneviratne. “A review of computer vision methods in network security.” IEEE Communications Surveys & Tutorials 23.3 (2021): 1838–1878. [Google Scholar]
- 10.Alam, Afreen, et al. “Malware detection in blockchain using CNN.” Diss. Brac University, 2021 [Google Scholar]
- 11.Gao, Mingchen, et al. “Adversarial Machine Learning in Cybersecurity: A Survey.” arXiv preprint arXiv:2304.06214 (2023).
- 12.Bagadi, K., et al. “Detection of Signals in MC–CDMA Using a Novel Iterative Block Decision Feedback Equalizer.” IEEE Access 10 (2022): 105674–105684. [Google Scholar]
- 13.Renugadevi, M., et al. “Machine Learning Empowered Brain Tumor Segmentation and Grading Model for Lifetime Prediction.” IEEE Access 11 (2023): 120868–120880. [Google Scholar]
- 14.Dasgupta, Dipankar, Zahid Akhtar, and Sajib Sen. “Machine learning in cybersecurity: A comprehensive survey.” The Journal of Defense Modeling and Simulation 19.1 (2022): 57–106. [Google Scholar]
- 15.Folkerts, Lars, Charles Gouert, and Nektarios Georgios Tsoutsos. “REDsec: Running Encrypted Discretized Neural Networks in Seconds.” Cryptology ePrint Archive (2021).
- 16.Ravikumar CV, Kala Praveen Bagadi, Design of MC-CDMA receiver using RBF network to mitigate MAI and nonlinear distortion, Neural Computing and Applications, Vol.31, Issue 2, 2019.
- 17.CV, Ravi Kumar, and Kala Praveen Bagadi. “MC–CDMA receiver design using recurrent neural networks for eliminating multiple access interference and nonlinear distortion.” International Journal of Communication Systems 30.16 (2017): e3328. [Google Scholar]
- 18.Chui, Kwok Tai, et al. “A Survey of the Internet of Things and Cyber-Physical Systems: Standards, Algorithms, Applications, Security, Challenges, and Future Directions.” Information 14.7 (2023): 388.
- 19.Vähäkainu, Petri, Martti Lehto, and Antti Kariluoto. “Cyberattacks Against Critical Infrastructure Facilities and Corresponding Countermeasures.” Cyber Security: Critical Infrastructure Protection. Cham: Springer International Publishing, 2022. 255–292. [Google Scholar]
- 20.S. P. Tera, et al., “Towards 6G: An Overview of the Next Generation of Intelligent Network Connectivity,” in IEEE Access, doi: 10.1109/ACCESS.2024.3523327
- 21.Tera, Sivarama Prasad, Ravikumar Chinthaginjala, Priya Natha, Shafiq Ahmad, and Giovanni Pau. ``Deep Learning Approach for efficient 5G LDPC Decoding in IoT.” \IEEE Access (2024).
- 22.Nyangaresi, Vincent Omollo, et al. “Anonymous Authentication Scheme Based on Physically Unclonable Function and Biometrics for Smart Cities.” Engineering Reports (2024): e13079.
- 23.Anbazhagan, R et.al. Investigation and numerical simulation of the acoustic target strength of the underwater submarine vehicle. Inventions 2022, 7, 111. doi: 10.3390/inventions7040111. [Google Scholar]
- 24.S. P. Tera, R. Chinthaginjala, P. Natha, G. Pau, C. Dhanamjayulu and F. Mohammad, “CNN-Based Approach for Enhancing 5G LDPC Code Decoding Performance,” in IEEE Access, doi: 10.1109/ACCESS.2024.3420106.
- 25.Chinthaginjala, R. K., & Bagadi, K. (2017). Receiver design using artificial neural network for signal detection in multi Carrier–Code division multiple access system. International Journal of Intelligent Engineering and Systems, 10(3), 66–74. [Google Scholar]
- 26.Asadi Srinivasulu et.al. “Performance and Improvement Analysis of the Underwater WSN Using a Diverse Routing Protocol Approach”, Journal of Computer Networks and Communications, vol. 2022, Article ID 9418392, 19 pages, 2022. 10.1155/2022/9418392.
- 27.G. NavaBharat Reddy, Ravikumar CV, “Developing novel channel estimation and hybrid precoding in millimetre-wave communication system using heuristic based deep learning”, Energy, DOI10.1016/j.energy.2022.126600.
- 28.Kalapraveen B, N. Challa,”Precoded large scale multi user MIMO system using likelihood ascent search for signal detection” DOI: 10.1029/2022RS007573.
- 29.Kumar, Neelam Sanjeev, et al. “HARNet in deep learning approach—a systematic survey.” Scientific Reports 14.1 (2024): 8363. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 30.Jyothi, Koganti Krishna, et al. “A novel optimized neural network model for cyber-attack detection using enhanced whale optimization algorithm.” Scientific Reports 14.1 (2024): 5590. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 31.MidhulaSri, J., and C. V. Ravikumar. “Offloading computational tasks for MIMO-NOMA in mobile edge computing utilizing a hybrid Pufferfish and Osprey optimization algorithm.” Ain Shams Engineering Journal (2024): 103136.
- 32.Vineela, P., & RaviKumar, C. V. (2024). Improved migration algorithms for uplink transmission secrecy sum rate maximization in MIMO-NOMA. Results in Engineering, 103275.
- 33.Ravikumar, C. V., K. Sathish, and Chunhua Su. “Design and Analysis of Piezoelectric Energy Harvester for Wireless Sensor Networks.” International Conference on Data Security and Privacy Protection. Singapore: Springer Nature Singapore, 2024.
- 34.Chandra Sekhar, J. N., et al. “Classification and Comparative Evaluation of Text and Emoji-Based Tweets With Deep Neural Network Models.” Journal of Electrical and Computer Engineering 2024.1 (2024): 9652424.
- 35.Karthiga, Rengarajan, et al. “A novel exploratory hybrid deep neural network to predict breast cancer for mammography based on wavelet features.” Multimedia Tools and Applications (2024): 1–27.
- 36.Kaveripakam, S. and Chinthaginjala, R., 2023. Optimal path selection and secured data transmission in underwater acoustic sensor networks: LSTM-based energy prediction. PLoS One, 18(9), p.e0289306. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 37.Reddy, G. N., & Kumar, C. R. (2023). Deep learning-based channel Estimation in MIMO system for pilot decontamination. International Journal of Ad Hoc and Ubiquitous Computing, 44(3), 148–166. [Google Scholar]
- 38.Bramham, K. R., & Ravi Kumar, C. V. (2015). Comparison and optimization of Layer2 and multilayer switch protocols to implement converged and reliable network. International Journal of Applied Engineering and Research, 10(8), 20139–20154. [Google Scholar]
- 39.Kumar, R. C. V., et al. “Performance analysis of ipv4 to ipv6 transition methods.” Indian Journal of Science and Technology 9.20 (2016): 1–8. [Google Scholar]
- 40.Ravikumar, C. V., et al. “Performance analysis of HSRP in provisioning layer-3 gateway redundancy for corporate networks.” Indian J. Sci. Technol 9.20 (2016): 2–6. [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
The datasets used during the current study are available from the corresponding author on reasonable request.