Abstract
The rapid increase of internet of things (IoT) devices in our daily lives has highlighted the critical need for strong security measures to protect the integrity and confidentiality of IoT communications. This paper presents a novel solution to this growing problem using a secure and lightweight DNA-based encryption method, elliptic curve encryption (ECC), to secure IoT communications. The research explains how DNA-LWCS (DNA-based lightweight cryptography system) utilizes basic encryption methods to secure data transmission against system complexity while maintaining security effectiveness. The security key ensures enough protection for achieving the necessary level of confidentiality. Three fundamental keys are extracted from publicly accessible DNA sequences to start the procedure during its first phase. When employed together with ECC these keys generate a private key during the second stage of development. During the second stage the keys generate a private key based on ECC (elliptic curve cryptography) protocol. The encryption and decryption of IoT device messages requires this private key during the last operational phase. The combination of intuitive DNA sequences together with ECC generates better security and decreases the strain on systems. Practical evaluations demonstrate that the proposed encryption method offers better security and efficiency compared to existing methods while maintaining weightless operational performance. This makes it an ideal solution to secure IoT data exchange. The encryption method we investigated received detailed study which focused on both security and efficiency criteria during our research timeframe. The research demonstrates our security method outperforms other solutions by maintaining low resource requirements. Our proposed DNA-based encryption system shows potential as a suitable security measure for protecting IoT connections through its lightweight design capabilities.
Keywords: Key generation, Lightweight cryptography, Public key, Performance evaluation, Secure communication
Subject terms: Energy science and technology, Mathematics and computing, Computational science, Computer science, Information technology, Scientific data
Introduction
As the world digitizes and becomes a global village, there exists a need of interconnected devices anywhere and anytime. The Internet of Things (IoT) is an intelligent technology that can be used to efficiently and conveniently connect various devices through the Internet. IoT has extended its capabilities and efficiency from industrial to personal use, seamlessly integrating into our daily routines. Whether performing tasks in a smart power plant or indirectly behind the scenes, the presence of the Internet of Things is undisputable and defining1. However, as the IoT becomes more widespread, so do the associated security risks. Numerous methods have been adopted to secure IoT devices in the past like Elliptic Curve Cryptography (ECC), DNA-based encryption, Triple Data Encryption Standard (3DES), and Advanced Encryption Standard (AES). ECC employs elliptic curves for key generation and encryption, which allows it to achieve better and more efficient performance than practicing cryptographic approaches. The DNA-based encoding scheme is an emerging technology that utilizes a public–private key pair for the encryption-decryption process and can be an optimal alternative without adding any extra cost. 3DES and AES are very common symmetric key encryption methods that are used for encryption in data protection from decades2,3.
Each cryptographic approach has its strengths and weaknesses. ECC is quicker and more productive but exposed to quantum computing attacks efficiency. Making an enormous 3-char key, 3DES was rather slow though it gave a stronger security, and attack-resistant AES gained fame for its encrypting performance, but it also had vulnerabilities4. The right approach to this may echo on the personal requirements and will be the targeted security level. DNA-based encryption undoubtedly is the most neo-approach to data security in IoT. It uses DNA sequences to derive the necessary keys and decrypt data, granting more security with less overhead5. The method is highly immune to attacks, such as man-in-the-middle attacks, and is not susceptible to quantum computing attacks like ECC. Moreover, it also has advantages such as light performance, which would be helpful for IoT communications security. Indeed, DNA-based encryption the only one of its kind has unique strengths and advantages over rival cryptographic approaches6.
ECC is another popular method in data protection. It uses public-key cryptography mechanism for data security that relies on elliptic curves for key generation and encryption purpose. It shows enhanced efficiency than existing algorithms like RSA and digital signature. DNA-based encryption is young security scheme that is gaining more usage in today’s time due to its randomness and robust nature7,8.
IOT is undoubtedly ruling everywhere from our usage to industrial and national levels. Whether we are talking about smart homes or we want to use any cloud service for safeguarding the defense data of a country, we are relying on IOT services. It has changed our way of thinking too9. So it is of utmost significance to tackle the security of IOT devices. Its usage is widely spread from sending an email message to decoding a cipher in military operations. That is why, this domain is actively researched and producing various security algorithms to achieve the best in cyber security10. The main objective of this work is to contribute towards IOT security with an efficient, dynamic, and economical solution that can be used as better approach as compared to existing approaches. This work has analyzed the provided scheme of various benchmarks and compared the results with our provided algorithmic approach and hence, it can be claimed that our proposed solution is exhibiting novelty in its structure, composition and achievement of data integrity as well as confidentiality11,12.
By evaluating and comparing the existing encryption techniques, the objectives of this study are to prove the efficiency and effectiveness of the proposed DNA-based encryption method for securing IoT communications. The outcomes of this research are anticipated to greatly contribute to the IoT security industry and afford useful information that will be beneficial in the sustainable development of security solutions in the fast-growing IoT13.
This paper presents a comprehensive literature review that examines various encryption techniques and their applications in IoT security. The critical analysis of methods such as Elliptic Curve Cryptography (ECC), DNA-based encryption, 3DES, and Advanced Encryption Standard (AES) highlights the strengths and weaknesses of each technique, forming the foundation for our proposed method.
The DNA-LWCS operating method splits into three separate phases as outlined in the methodology section of this text. The initial process requires obtaining main keys from publicly available DNA sequences. ECC aids the system to generate a private key after obtaining the keys from public DNA sequences. During the final operational stage of the process messages get secured by encryption using the private key while these key functions both for encryption and decryption of IoT devices communication14,15. Additionally, the research examines the performance of its proposed method against traditional encryption approaches to establish performance understanding.
The proposed DNA-LWCS reaches outstanding security and efficiency levels during analysis which makes it an attractive solution for IoT communication16,17. Modern IoT device development has generated crucial security obstacles which affect resource-limited environments because standard cryptographic solutions cannot provide both security features and operational efficiency effectively. The computational requirements of ECC, AES and 3DES encryption standards prevent their usage on minimal power IoT devices. The processing time for AES and 3DES encryption protocols is slow while ECC proves efficient as a cryptographic tool yet it has weaknesses against quantum computing threats. Strong security along with low computational costs and resistance against emerging threats require an improved cryptographic solution which serves these needs. DNA-LWCS fills the existing gaps through its ECC-based security technology which combines DNA sequence unpredictability with efficient encryption design to create quantum-resistant IoT-specific cryptography.
This study introduces a secure and efficient DNA-LWCS integrated with ECC to enhance security in IoT. By leveraging the distinctive features of DNA sequences and ECC’s robustness, the suggested approach offers considerable data protection while maintaining a lightweight system. Research outcomes will boost IoT security practices at the same time provide essential insights into creating operational security solutions in evolving IoT systems. The IoT environment faces its vulnerabilities using traditional cryptographic approaches that incorporate AES with ECC.
These protective techniques give some protection but they demand excessive resources and do not match the limited power capacity of devices. Research teams have looked into alternative lightweight encryption methods which prove insufficient for protecting IoT devices against sophisticated cyber threats. DNA-based encryption has emerged as an outstanding option among new cryptographic techniques. The cryptographic keys which DNA cryptography produces stem from biological DNA sequences that naturally exhibit random patterns. DNA sequences obtain their randomness from the complex biological processes including genetic mutations and recombination and molecular noise rather than using the RNG algorithms operated by traditional random number generators. DNA-based entropy sources stand as more unpredictable than algorithmically generated pseudo-random numbers because their natural divergence creates stronger randomness than computationally achievable numbers that might become vulnerable to cryptographic analysis attempts. The extensive nucleotide sequence variety of A, T, C, G enables massive key space potential which significantly defends security from potential brute-force assaults. DNA-based encryption when applied with ECC technologies delivers powerful security features through reduced processing requirements thus becoming appropriate for limited IoT hardware resources. Existing obstacles to implementing DNA-based encryption in IoT applications include complex computations as well as both scalability issues and errors during DNA synthesis and inadequate integration with current IoT frameworks. DNA-based encryption faces obstacles that prevent its general adoption because of its promising benefits.
The main computational hurdle in DNA-LWCS develops from both DNA sequence handling operations and ECC-based key production procedures. A DNA-based encoding and decoding system requires advanced string operations that impose delays on their processes particularly when applied to resource-limited IoT devices. The duration of ECC processes lengthens due to the processing needs of scalar multiplications along with multi-point additions and doublings. Performance improvement can be achieved through precomputed DNA sequence transformation lookup tables and efficient Montgomery ladder methodology and hardware acceleration through FPGA or GPU implementation. The processing efficiency of DNA sequences and security maintenance can be achieved through parallelization and the deployment of lightweight cryptographic libraries which were optimized for IoT applications. DNA-LWCS becomes an effective IoT security solution when these implemented optimizations balance encryption strength with real-time operational capacities.
The next section will cover related work that discusses various DNA encoding schemes. Following this, we will present the system design, which outlines the architecture of our proposed system. The methodology section describes the proposed method, which consists of three phases, followed by algorithms detailed in the subsequent section. The results and discussion sections evaluate the performance of the proposed method and compare it to other encryption methods. Finally, the conclusion summarizes the advantages of the proposed method and its potential impact on securing IoT devices.
Related work
The Web of Things (IoT) has reformed how gadgets communicate and collaborate. However, the security of IoT gadgets remains a pressing issue because of asset imperatives and the rising number of associated gadgets. Lightweight cryptography has emerged as a potential method for safeguarding IoT devices with limited resources. A DNA-LWCS has a positive probability of improving IoT security. To understand it well, this research has deeply examined similar methodologies that other researchers have proposed18.
Lightweight crypto algorithms are needed in the digital world for IoT device security because they have limited resources. Several studies pointed out the status of secure authentication schemes, particularly elliptic curve cryptography, for IoT and cloud server communication in limited cost to address IoT security issues. These studies have mentioned crypto algorithms that are suitable to work in more constrained environments like IOT without compromising their performance19,20.
Machine learning algorithms are also enriched with optimal solutions in securing data of IOT. Thakor et al.21 mentioned the need for a lightweight security scheme that could easily work in an IOT environment. Barman and Saha (2018) developed a hybrid intrusion detection system (IDS) based on support vector machines (SVM) and K-means clustering that depicted an increase in the accuracy of detection of vulnerabilities in network security22. Nevertheless, such kinds of systems take the way for challenges of high computational needs and resource-efficient solutions in IoT security growth23.
DNA-based encryption systems are providing better security and fulfilling IOT needs. Fernández-Caramés (2020) utilized quantum cryptography for IoT, and Chen et al. (2014) suggested a DNA-based security system using a concatenated logic circuit that claims to have a secure and visible readout in security applications24. Banerjee and Banerjee (2021)proposed a DNA sequence-based encryption method for IoT data protection by considering the complexity of DNA sequences25. These studies provide evidence that DNA-based cryptographic techniques can be used to significantly improve the level of security in IoT26. The strength of these approaches lies in their imaginative utilization of organic groupings to make a profoundly complicated encryption framework, which is challenging to break. However, the reviews face adaptability worries, as the dependence on DNA tape pictures might restrict its relevance in bigger-scope IoT conditions. Moreover, the complexity of processing DNA sequences may also cause performance issues27.
The authors Tiwari and Kim28 introduced a security enhancement for IOT by using Dual authentication with DNA and ECC. The proposed methodology adopts elements from ECC and DNA cryptography to enhance encryption by delivering maximum security features. Security has enhanced significantly because this system implements two robust cryptographic approaches in combination. The execution of hybrid DNA-encoded ECC throughout IoT environments proves complex to deploy and manage due to difficulties between system interoperability and implementation complexity29–31. Challengers Aishwarya and Sreerangaraju (2019) established their encryption scheme through Verilog HDL and ModelSim 6.4c simulation and executed it on Xilinx toolkit devices32. The strategic objective enables protected data transmission through compatible encryption-decryption methods suitable for IoT devices. This method functions well due to its implementation tools and hardware description languages used for efficient hardware implementation. The process of data encryption brings a decrease in system performance that might hinder system efficiency under specific operational scenarios33–35. Barman & Saha (2019) developed a defense strategy against IoT communication threats by uniting ECC with DNA encoding to provide dual-level security protection. Double encryption security is achieved through the combination of two different encryption methods that function independently from each other. The security structure provides this method with exceptional strength that increases its ability to protect against penetration attempts. Asset-driven IoT devices face drawbacks from using this approach because it produces high computing costs coupled with longer processing times. Significant attacks can potentially exploit the dual-layer encryption method since it shows vulnerability28,35.
Pasupuleti and Varma (2019) research focused on the application of DNA-based encryption to IoT devices based on NXP/Jennic 5148 and MSP430 hardware. DNA-based methods are used in this method to improve security by utilizing the particular capabilities of these hardware platforms11. The primary strength of this approach is its customization for specific equipment, possibly enhancing execution for those gadgets. However, the reliance on particular hardware may limit its scalability and interoperability with other IoT devices, making it less adaptable to a wider range of IoT settings36,37.
Pasupuleti and Varma11 used cypher text policy attribute-based encryption (CP-ABE) schemes to protect IoT data in a subsequent study. By defining policies that control who can access encrypted data, this method makes it possible to control access at a more granular level. The strength of CP-ABE lies in its capacity to give itemized admittance controls, upgrading security and adaptability. However, lightweight IoT devices may struggle with the computational resources and efficiency required to effectively implement this encryption scheme due to the overheads associated with CP-ABE38–40.
Al-Shargabi and Al-Husainy (2021) proposed a novel encryption method for IoT communications that makes use of random keys derived from DNA sequences41. This approach expects to use the irregularity and intricacy of DNA groupings to improve encryption strength. The evaluation matrices did not show improved results, indicating that the method may not offer significant advantages over existing encryption techniques, despite the fact that the novelty of using DNA for key generation is a key strength. This suggests that additional optimization and refinement are required to achieve the desired security enhancements42.
A lightweight cryptography (LWC) algorithm for IoT applications with a 32-bit block size was presented by Al-Husainy et al. (2021). The purpose of this algorithm is to provide secure encryption that is suitable for the IoT devices’ limited computational capabilities43. The strength of this strategy is its attention to lightweight encryption, which is significant for asset-obliged conditions. However, its reliance on digital files as randomness seeds raises questions regarding predictability and vulnerability to digital attacks. This dependence on computerized seed documents could sabotage the calculation’s security by making it more helpless against abuse44. Table 1 compares the strengths, weaknesses, possible attacks and key sizes of various popular existing security approaches to comprehend the significance of our proposed scheme clearly. A clear comparison of the systematic literature review of existing DNA-based encryption schemes in terms of strengths and weaknesses is enclosed in45 and herewith the paper describes the significance and the limitations of the current security mechanism in comparison with DNA DNA-based approach that is targeted in this research study. Table 2 lists the research gaps of existing research studies by highlighting their shortcomings.
Table 1.
Cryptography weaknesses.
| Algorithm | Key size (in bits) | Strength | Weakness | Possible attacks |
|---|---|---|---|---|
| 3DES | 112, 168 | Improves security compared to DES, Backward compatibility | Slow performance, Still vulnerable to brute-force attacks | Brute-force attacks |
| AES | 128, 192, 256 | Strong security, Widely adopted, Efficient performance | None significant | No attacks |
| ECC | Smaller key sizes 160, 224, 256 | Smaller key sizes, reduced storage, Reduced trans-mission time, 15 times faster than RSA | Increased size of encrypted text, Dependent on very complex equations which increases the complexity of a log | Channel attacks, Back doors, Quantum computing attacks |
| DNA | Key size not re- quired | Extraordinary storage capacity of DNA, Low power consumption | High processing time, Dynamicity, Experimental, Limited practical use | No attacks |
Table 2.
Research gap of existing studies.
| Study/technique | Strengths | Weaknesses | DNA-LWCS addressing gaps |
|---|---|---|---|
| Tiwari and Kim28 | Hybrid DNA-encoded ECC (Elliptic Curve Cryptography) | Implementation complexity and interoperability issues with existing systems | DNA-LWCS optimizes key generation and enhances integration flexibility, reducing complexity and improving compatibility |
| Barman and Saha22 | Two-level security—one in DNA encoding and the other in ECC encryption steps | High computational cost, more processing time, and vulnerability to major attacks | DNA-LWCS optimizes encryption efficiency, reduces computational overhead, and strengthens security against major attacks |
| Suyel Namasudraa et al.1 | Strong 1024-bit secret key generation utilizing DNA computations, user characteristics, and MAC address for cloud security | Limited to specific integrations; lacks scalability for hybrid approaches | DNA-LWCS enhances key strength using optimized DNA keys and genetic algorithms for better scalability and adaptability |
| Junxin Chen et al.2 | Employs advanced DNA computations like multiplexing and XOR for security | Needs evaluation against diverse cybercrimes to confirm robustness | DNA-LWCS provides enhanced key security with rigorous testing against multiple evaluation metrics and real-world scenarios |
| Liu et al.6 | Avoids the need for dynamic private key management, reducing complexity | Vulnerable to noise and interference in transmission | DNA-LWCS optimizes key robustness with genetic mutation and training models, addressing noise-related vulnerabilities |
| Muhammad Samiullah et al.3 | Incorporates multiple pseudogenes and a classifier for DNA-sequence-based encryption | Limited focus on transparency in encryption processes | DNA-LWCS provides a comprehensive and explainable encryption framework with performance metrics validation |
| Imdad Maria et al.8 | High entropy DNA structure ensures uniform coding across nucleotides for ASCII characters | Exposed to some security attacks; lacks adaptive mechanisms | DNA-LWCS integrates adaptive security layers like ECC and genetic algorithms for robust defense against attacks |
| Shuqin Zhu et al.30 | Combines advantages of “pool exchange” while avoiding drawbacks of “time domain” schemes | Requires testing on other datasets for broader validation | DNA-LWCS is validated with multiple datasets (text, images) to ensure reliability and scalability |
| Jithin et al.33 | Introduced novel Mandelbrot sequence-based transformations for color parameter enhancement | Needs improvement in bandwidth transfer rate and load balancing | DNA-LWCS incorporates optimized bit operations to enhance computational efficiency and transfer rates |
| Al-Shargabi and Al-Husainy41 | Novel algorithm using a random key of DNA | Evaluation metrics do not show improved results | DNA-LWCS enhances key randomness using genetic optimization, improving security and evaluation outcomes |
| Al-Husainy et al.43 | (LWC) algorithm with a 32-bit block size | Dependency on digital files as seeds raises concerns about randomness and susceptibility to digital attacks or predictability | DNA-LWCS ensures robust randomness by leveraging genetic algorithms and machine learning to enhance unpredictability and resilience against attacks |
| Bahubali Akiwate et al.29 | Efficient classification of image data with noise tolerance | Needs further testing on diverse datasets for broader validation | DNA-LWCS demonstrates high efficacy across various data types, including images, by integrating deep learning models |
| Shahnawaz Ahmad et al.46 | Immutable ledger and distributed trust model for secure key exchange | High energy consumption; scalability issues in consensus algorithms | DNA-LWCS minimizes energy usage by avoiding blockchain dependence while ensuring robust key generation and exchange |
| Shahnawaz Ahmad et al.47,48 | High efficiency for large datasets; low computational overhead | Challenges in key distribution; vulnerable to brute force attacks | DNA-LWCS mitigates key management issues by leveraging optimized DNA keys strengthened through genetic algorithms |
| Shahnawaz Ahmad et al.47,48 | Optimized for resource-constrained devices (e.g., IoT); energy-efficient | Sacrifices robustness for efficiency | DNA-LWCS achieves high efficiency while maintaining strong security for IoT devices |
Methodology
As the selected and explored studies have not successfully tackled the majority of security threats and attacks, there is an utmost need for an encryption algorithm to achieve the de-sired security, and that too by reducing the overall complexity so that it could work in the IoT environment. For the same, three rounds of security are being introduced in DNA-LWCS. DNA sequences are known for randomness, which are required for choosing a private key to encrypt the message. This is the reason for selecting publicly available DNA sequences to act as the secret key to enhance the algorithm’s security. The second step is to apply the mathematical operations on the message and the key together. As we are classifying the process parallel, that is, with the message itself and the key, too, it is required to concatenate them together before applying any encoding scheme on it. So, for the message, we have obtained it in binary form by first converting each alphabet into decimal and finally getting bits of each decimal. Now, this sequence of bits needs to be put with the key (which is already selected) to make the first cipher block. Still, no encryption has been applied to it yet. Before that, DNA sequences are selected from 52 million publicly available sequences, and before combining them with the message, they are also converted into bits. Now, the point is to mix the message along with the key. Here, a variety of options are available like applying XOR directly with the message and the key or applying AND operation or NOT or any other logical operation to perform a second round of the security. At this stage, DNA-LWCS concatenates the message with the key in this way that the key is attached to the end of the message, which means the least significant bits’ position49. To handle this problem, a padding operation will be applied to complete the block by adding zeros at the most significant bit position, which is at the start of the concatenated string.
This is our message now on which padding has already been applied. Now to encode it, two processes are being adopted. The first one is a substitution, and the second is a transposition. Substitution is an important operation on bits method that is used to replace the value of the current bit by putting another value50. The purpose is to alter the arrangement and magnitude of the bits to betray the attacker for guessing any particular value here. As it is our encoding phase, we are applying substitution for the same purpose to encode the entire message in such a fashion that it becomes harder to predict. To keep the process simple and less complicated, methods are chosen to apply the XOR/Mod/AND operation on the bits at this stage. The selection of the operation will be random so encoding should not go with the same process every time. This is to obtain a higher level of security by providing randomness in the designed scheme of the algorithm51.
Next comes the transposition phase. This is the second stage of encoding, where the ROTATE operation is performed on the entire sequence of bits. Both of these methods will change the position of bits from the original ones and also will not increase the consumption power a lot, and this is what we need with IOT systems. So, at the end of this level, encoding is complete, and security is enhanced before the transmission of the message. The third level is achieved by applying Elliptic Curve Cryptography (ECC) on the DNA-encoded message. ECC is an approach of encryption that relies on the elliptic curves defined on particular algebraic operations. ECC is actively used nowadays to encrypt the messages of network traffic because of its various advantages over already existing security methods. Firstly, it is lightweight, so it does not cause extra computational overhead on the existing system. Secondly, it uses a public key cryptography method which means the public key is available for everyone to encrypt data with. It could be decrypted back by only a private key which will be secretly held by the authorized user. Thirdly, it uses a smaller key size for encryption and performs fast cryptography. Overall, it is a better approach to use ECC for encryption to obtain magnificent security52. ECC relies on the mathematics of elliptic curves and uses the location of various random points to encrypt or decrepit the message. We start with any random point on the curve and keep on moving unless we find another point on the elliptic curve. So, the dot function can be used to hop around the binary curve and locate the points of P, Q, and R. So, overall enhanced security is achieved by using a DNA encoding scheme and ECC approach, and the overall design is simple, fast, less complex, and more compatible to be used for an IOT system that promises to work anywhere, anytime, and by anybody without any kind of delay53.
The fitness function assesses the strength and randomness of DNA keys by assigning a score or measure to each key based on specific criteria. These criteria include the frequency of each nitrogenous base (A, T, C, and G) in the DNA string, compared to the desired threshold of 25% of the key’s length, and analyzing the interval between successive occurrences of the same nucleotide to ensure it falls within the allowed range of up to three consecutive repetitions. By combining these criteria, the fitness or strength of each key can be determined. The Frequency Test evaluates how often each nitrogenous base appears in the DNA string, aiming for a frequency close to 25% of the key’s length to indicate strength. Meanwhile, the Gap Test examines the interval between successive occurrences of the same nucleotide, allowing for up to three consecutive repetitions of A, T, C, or G to be considered strong4. These tests collectively contribute to assessing the randomness and strength of the keys.
Algorithms
Here is a detailed DNA-LWCS algorithm using DNA and ECC for IoT.
Key generation
Elliptic curve cryptography starts its implementation with the selection of both an elliptic curve E and a point P existing on E. The procedure generates random values for d as the private key through a process which verifies it resides within the n-1 to 1 range and n specifies the curve order. The computation of the public key Q happens through the multiplication of private key d with starting point P. The algorithm permits performing this multiplication through successive additions of P until reaching the desired value d times without requiring alternative elliptic curve operations. Hashing the received request with the verification message produces the pair of keys which includes a private encryption key and its matching public key for secure transmission and cryptographic data operations54,55.
Stages of the DNA-LWCS are demonstrated in Fig. 1.
Fig. 1.
Algorithm stages.
Message encryption
The first step to encrypt a message through DNA-LWCS begins with preparing a random message and converting it to binary format. The choice of encryption primary keys will consist of three available public DNA sequences. ECC message encryption requires the selection of random number k that should be within the range of (1,n-1) because n represents the curve order to use those keys for encryption. The resultant points C1 will be kP while C2 equals M + Q after selecting P and Q as points from the elliptic curve E. The execution of ECC requires users to select particular parameters including curve equation and base point alongside field size because these elements determine security strength as well as operational speed. Real-world ECC implementations use finite fields for their curves which either pick prime fields called Fp or binary fields named F2m. Selecting curve parameters particularly base point order demands careful attention since it determines the ability to resist known cryptographic attacks particularly the elliptic curve discrete logarithm problem (ECDLP). The security strength of an elliptic curve algorithm depends on its key size where a standard 256-bit key suits most practical usage needs. The computational operations from ECC require less time and fewer resources than RSA operations because IoT devices typically have restricted processing power and limited memory capacity.
The encryption process depends heavily on ECC to improve both the security strength and operational efficiency of DNA-LWCS. The security framework provides strong encryption functions while consuming minimal computing resources thus constituting an optimal option for IoT deployments. The encryption strength of ECC matches RSA cryptography but the system requires smaller key sizes which improves both performance time and decreased processing demands. ECC encrypts data through the process of private key multiplication with a base point from an elliptic curve to achieve a new point. Security performance in elliptic curve encryption depends entirely on the specified parameters such as secp256r1 (P-256). A 256-bit ECC key uses the same security power as a 3,072-bit RSA key yet needs fewer computing resources thus making it appropriate for IoT environments with limited resources. DNA-LWCS becomes more efficient because ECC’s light weight quality allows shorter processing periods and decreased energy requirements. The system enables key generation through ECC and DNA sequences because it combines ECC’s efficiency with DNA sequences’ high entropy. The joint application of ECC and DNA encoding enables secure and efficient encryption standards for IoT implementations. DNA-based encryption enables the proposed framework to eliminate quantum computing threats from ECC while using ECC’s efficient computational requirements. The randomness of biological sequences allows DNA-based encryption to provide better protection against threats compared to ECC because quantum attacks cannot compromise it. DNA-based encryption provides a lightweight encryption system that produces stronger cryptographic keys through its improved randomness compared to quantum-resistant cryptographic methods which include NTRU lattice-based cryptography and hash-based signatures. The combination of ECC and DNA-based encryption provides IoT applications with an expandable and efficient security system which has quantum-resistant capabilities.
The next stage involves securely transmitting the encrypted DNA sequence while maintaining data integrity and resistance against attacks. C1 and C2 are converted into binary format and concatenated with three primary keys to form a single binary string. Finally, use a mapping scheme to convert this binary string into a DNA sequence. Following these steps, an encrypted DNA sequence is generated that could pass for communication. Figure 2 illustrates the ECC approach for generating points P and Q, followed by Figs. 3, 4 and 5, which provide high-level, empirical and detailed views of the system design. Figures 3, 4 and 5 illustrate the integration of ECC with DNA encryption in the proposed system.
Fig. 2.
ECC approach to generate P and Q point.
Fig. 3.
High level system design.
Fig. 4.
Empirical view of the system design.
Fig. 5.
Detailed system design.
To decrypt the message, it is desirable to reverse these steps by converting the DNA sequence back into binary format and then applying ECC decryption using the private key (Fig. 6).
Fig. 6.
Process of DNA-LWCS.
Transmission
To transmit the encrypted DNA sequence over an IoT network, it is required to first convert it back into binary format. Then, any standard communication protocol, such as TCP/IP or MQTT, could be used to transmit the binary data over the network. The data can be sent from one device to another using wireless or wired communication channels, depending on the type of IoT network being used56.
Message decryption
Once the data is received, then very first step is to convert the DNA sequence back into a binary format using a reverse mapping scheme. Then, extract the three primary keys from publicly available DNA sequences used in the encryption phase. Here, keys are obtained by the set procedure of the algorithm to fetch the matched key, which was used in the encryption process. Next, use these keys to decrypt the message using ECC. To do this, extract C1 and C2 from the concatenated binary string received in step 3 of the encryption phase and convert them back into elliptic curve points. Then, compute M = C2 – dC1, where d is the private key corresponding to the public key used in encryption57. If M is negative, add n to it until it becomes positive. If M is not divisible by 8, add padding bits at the beginning of M until it becomes divisible by 8. Finally, convert the decrepit binary message back into human-readable form to obtain the original message sent by the sender. It is important to ensure proper security measures are in place during transmission and decryption to prevent any unauthorized access or data tampering47,58.
Figure 5 illustrates the complete process of DNA-LWCS diagrammatically, followed by Fig. 7, which shows the complete set of activities in the form of a flowchart.
Fig. 7.
Flowchart.
Algorithm 1.
Which is the entry point to generate the key for DNA-LWCS is listed below:
The above Algorithm 1 is designated for the key generation mechanism of DNA-LWCS. It starts by identifying the parameters of an elliptic curve E, defined by its equation y2 = × 3 + ax + b, along with a base point P = (x, y) on the curve. This process caters the selection of coefficients a and b randomly for the curve equation and choosing coordinates x and y that must satisfy this equation appropriately. After that, it enters an infinite loop for generating the private key d, ensuring that d exists within a specific range that is required for managing security. If d does not meet this criterion, a new random integer is generated until a valid d is obtained. Once the private key is secured, the algorithm proceeds to generate the corresponding public key Q using elliptic curve operations.
To obtain the public key, the algorithm follows another infinite loop where Q is initialized as the base point P, and d is represented in binary format. Elliptic curve point doubling is performed on Q for each bit of d, and if the current bit is 1, P is added to Q using elliptic curve point addition. This process continues until all bits of d are processed, resulting in the final public key Q48,59.
Algorithm 2 is for data reading of DNA sequence data for other subsequent processing. Firstly, it initializes the file path in which the DNA sequence is kept to inform the algorithm about the location of needed data. After the file path is assigned, the algorithm reads the DNA sequence from the file. It utilizes an infinite loop as it reads the DNA sequence data continuously on an ongoing basis. This design also gives the impression that the algorithm is ready to support a constant data feed if the sequence data is being updated or processed in real-time. Once it is read, the sequence is returned as the output in order to be processed in the subsequent step, e.g., key generation. However, the loop is terminated, and the major purpose of the algorithm is to ensure that the DNA sequence is continually being read and can be accessed for other uses. This approach is most synergistic for applications that involve constant monitoring or data analysis in real time.
Algorithm 2.

Read data sequence
Algorithm 3 is a function that encodes the DNA sequence to a matrix of one-hot encoded form. One hot encoding is an elementary process in computational biology and machine learning. It is used to work on nominal data and transform it into vectors made up of binary values. It starts by defining a function named `Encoding` that takes a single input. For the following tests, the call only takes a single parameter of type string `key,` which contains the DNA sequence. The genetic material is a set of four bases denoted by ‘A,’ ‘T,’ ‘C,’ and ‘G’.
Inside the function, a dictionary named ‘mapping’ is initialized to map each nucleotide to a unique integer: Dictionary is constructed from ‘A’ corresponding to 0, ‘T’ to 1, ‘C’ to 2, and ‘G’ to 3. This mapping aids in the indexing of the one hot matrix. Then the following matrix called ‘one_hot’ is created and given below: This matrix is a zero matrix with dimension = length of the input DNA sequence * 4 matrix is of dimension = (len(key), 4). In this case, number 4 symbolizes the four nucleotides: ‘A,’ ‘T,’ ‘C,’ and ‘G.’
After that, a `FOR` loop starts, starting from index = 0 till the index = len of the key-1, which means that the algorithm considers each character of the given DNA sequence. In the sequence for each character at position i, the character determines which column in one hot matrix should contain one according to the mapping dictionary60. The row index is the position of the nucleotide in the DNA sequence; the column index is dependent on the specific nucleotide and its corresponding integer value. To denote the presence of that nucleotide at position i in the sequence, the matrix element at [i, mapping[key[i]]] is set to be equal to 1.
After the outer loop for the first, where all the nucleotides are to be processed and the one hot matrix populated until the last row, the function returns the one_hot matrix; this is a binary image that can be used in different types of computational algorithms, such as machine learning or bioinformatics approaches. In the last stage of the algorithm, the DNA sequence is represented in one hot encoded based on the previously mentioned coding.
Algorithm 3.

Encoding of DNA sequence
The main purpose of Algorithm 4 is to transform a specified nucleotide into its binary form. The algorithm takes in a single ‘nucleotide’ (‘A,’ ‘T,’ ‘C,’ or ‘G’) and gives its binary representation as output. The process begins with the creation of a function called `Nucleotide- to-binary. Within the function, a ‘mapping’ dictionary is created to link each. Each nucleotide is represented by a specific two-bit binary code: ‘A’ corresponds to ‘00’, ‘T’ to ‘01’, ‘C’ to ‘10’, and ‘G’ to ‘11’. The function obtains the binary code for the input `nucleotide` from the dictionary and stores it in ‘binary_representation’.
Algorithm 4.

Convert nucleotide to binary
Next comes the most critical phase of the encryption process of DNA-LWCS, which is listed below in Algorithm 5.
Algorithm 5.
Encryption process for DNA-LWCS
As a key DNA-LCWS component we operate through elliptic curve cryptography (ECC) mathematics while using DNA sequence characteristics to create secure data operations. The initial phase defines the essential elements of the curve (E) through specification of both formula (y2 = x3 + ax + b) and base point (P = (x, y)) as well as sequence of the curve. An arbitrary message known as M originates from the information which needs encryption. The message (M) moves through a conversion process which produces binary format (Mbinary). In encryption methodologies conversion to binary serves as an essential operation for managing data since it establishes a standardized format suitable for cryptographic procedures. The chosen DNA sequence functions as a major authentication element within the encryption procedure. The elliptic curve sequence generates a loop-based random number k which falls inside a set range. The cryptography key originates from the randomly selected number in the sequence. The algorithm utilizes the key (k) to produce two elliptic curve points that include C1 = kP and C2 = M + kP. Mathematical properties of elliptic curves are used by these computational procedures to establish secure data transmission. After calculation the digital points C1 and C2 are transformed into a binary format while they are linked with the encryption key. The key association to the converted data during encryption becomes more secure through this step. Each pair of binary numbers that appears in observations corresponds to a designated DNA nucleotide under an established mapping scheme which pairs the combinations (00, 01, 10, 11) with nucleotides (A, T, G, C). The binary data goes through mapping which generates a DNA sequence that makes the information suitable for transmission and storage. The DNA sequence can accept complete binary data mapping to complete the encryption process61,62. The decryption process of DNA-LWCS uses the final algorithm 6 which is given below.
Algorithm 6.
Decryption process for DNA-LWCS
The decryption process takes the same steps as was followed in the encryption algorithm. It starts with initializing an empty string called keys_used, which serves as a storage unit for the extracted primary keys from the public key sets. A while loop is then used that extract keys until it fetches three unique sequences. Once the keys are acquired, they are added to keys_used for reference. After that it initializes another empty string, M_padded, which will hold the decrypted message after processing. A subsequent while loop is initiated to iterate through each character in the received encrypted message. During this iteration, the algorithm checks each character: if it is '1', indicating a valid part of the message, it is appended to M_padded; conversely, if it is '0', signifying padding or irrelevant data, it is discarded. This filtering process continues until the length of M_padded becomes divisible by 8, ensuring alignment for further processing63,64.
Following the character processing phase, the algorithm reverts C1 and C2 back into their respective elliptic curve points. M initializes to C2 through these points which serves as the vital element before proceeding to decryption operations. A while loop controls the process that yields positive M values within elliptic curve parameters. The algorithm adds the order 'n' of the curve to M when M is negative at first but exits the loop if M is already positive because further calculation can commence. The algorithm proceeds to carry out the test that confirms M is positive before establishing whether M is divisible by 8. A different looping structure begins to add padding bits to M while its length becomes divisible by 8. M becomes ready for the last decryption stage because of this processing step. The decryption process requires the creation of an empty decrypted message string that will hold the ending decoded content. The application of a while loop enables extraction of 8 current M bits before translating them into ASCII or Unicode characters. The loop extracts 8 bits from M which get assigned as characters to build decrypted message until all plaintext is successfully developed. This detailed decryption method allows the DNA-LWCS algorithm to maintain accurate data confidentiality and integrity which makes it a reliable cryptographic solution for such tasks in resource-constrained environments that value security and performance.
Results
DNA-LWCS succeeds with images as an implementation base which indicates its potential to operate across different dataset formats like audio and video. The selection of images for initial demonstrations became necessary because they display algorithm performance in an obvious manner. The effectiveness of the algorithm can be measured through encrypted image key measurements along with image histogram data intake. The DNA-LWCS algorithm is implemented successfully by using images. In addition, it can be implemented to different media data set like audio, video, and others. The images were selected rather than the other data media to demonstrate the effectiveness of the algorithm because the images can clearly show the results by using some measurements like the histogram of the image and encrypted images. For this purpose, the following images that are provided in Fig. 6 are selected.
Female.bmp: A colored image with an original resolution of 256 × 256 and a size of 196,608 bytes.
Pepper.bmp: Another colored image with an original resolution of 512 × 512 and a size of 786,432 bytes.
Photographer.bmp: A grey image with a resolution of 512 × 512 and a size of 786,432 bytes.
These images serve as effective test cases to demonstrate the LWCD algorithm’s functionality and performance across different image resolutions and colour formats. DNA-LWCS is implemented by using Python programming language over the test environment running on Windows 7 ultimate SP1 64-bits with a System Processor Intel(R) Core (TM) i3-3110M CPU @2.4GHz processor and 4 GB System Memory. The initial analysis is done using Jupyter notebook with installed libraries of matplotlib, numpy and opencv. The following are evaluation metrics on which the efficiency of our proposed solution is evaluated.
Correlation
Correlation signifies the association between two or more variables. It specifies the degree and direction of the relationship between the variables, how these variables change together positively (both increases mean 1), negatively (increase in one and decrease in the other means -1) or no correlation (0). It is measured as:
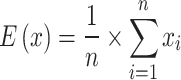 |
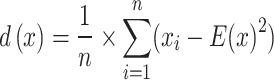 |
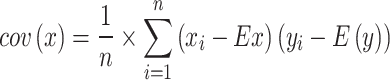 |
 |
Ex = expected value, Dx = variance of x, Cov = covariance between x and y.
The correlation values in the Table 3 show DNA-LWCS outperformed all other datasets, with the strongest correlations for Female (0.050), Photographer (0.045), and Pepper (0.060). LWCS demonstrated reasonable performance, with correlation coefficients of 0.042, 0.037, and 0.037 for Female, Photographer, and Pepper, respectively. RF-DECC fared the poorest, especially on the Photographer dataset (0.016), with correlations of 0.047 for Female and 0.037 for Pepper. DEA-IOT performed well for Female (0.013) and Photographer (0.012), but badly for Pepper (0.056), resulting in uneven performance across datasets65 (Fig. 8).
Table 3.
Correlation between original and encrypted images.
Fig. 8.
Image of female, photographer, and pepper.
Overall, the DNA-LWCS method appears to strike a reasonable balance, ensuring that the data is sufficiently encoded while maintaining some correlation, which may prove useful for recovery purposes. Figure 9 illustrates the correlation results graphically.
Fig. 9.
Correlation between original and encrypted images.
Encryption time
Encryption time refers to the duration it takes to encrypt a specific piece of data. It is measured from the moment the encryption process begins until it is completed. This duration can be expressed in seconds or milliseconds, as event processing typically occurs very quickly. Encryption time can vary based on several factors, including the size of the data being encrypted, the complexity of the encryption algorithm used, and the processing capacity of the device. Therefore, achieving fast encryption and facilitating the transmission of data in real-time applications is important. It is essential to consider the time required for encryption when selecting an encryption algorithm66,67.
Table 4 indicates that DNA-LWCS is the best-performing encryption method, with the quickest timings across all datasets: Female (1.025), Photographer (0.800), and Pepper (1.050). In contrast, LWCS is the slowest, with the greatest encryption times for Female (1.198), Photographer (1.170), and Pepper (1.408). RD-DECC has decent performance, with timings of 1.104 for Female, 1.037 for Photographer, and 1.566 for Pepper, although it is still slower than DNA-LWCS. IoT works incredibly well for Photographer (0.366), the quickest method for that dataset, but its encryption timings for Female (1.106) and Pepper (1.369) are slower, making it inconsistent. Overall, DNA-LWCS is the most efficient and reliable encryption technique available68. Figure 10 graphically illustrates the encryption time taken by each approach.
Table 4.
Encryption time
Fig. 10.
Encryption time taken by each approach.
Throughput
Throughput refers to the amount of data transmitted over a network or the capacity of a system to process tasks within a specific time frame. It represents the quantity of information that occurs in a system or over a certain period in computer networks. Depending on the context, throughput is typically measured in bits per second (bps), bytes per second (Bps), or packets per second (PPS).
 |
Table 5 compares the throughput of algorithms with varying amounts of data points (10, 20, 30, 40, and 50). DNA-LWCS consistently performs efficiently at all data point sizes, with throughput values of 8.00 (10), 10.00 (20), 11.00 (30), 9.50 (40), and 12.00 (50). It is capable of handling a variety of workloads while remaining reliable and balanced. In contrast, LWCS has changing performance, beginning low for smaller data points (7.36 for 10) and spiking inconsistently for bigger datasets (16.32 for 30, 15.36 for 50), indicating inefficiency. RF-DECC performs modestly, with throughput ranging from 7.25 (40) to 12.50 (50), while DNA-LWCS outperforms it on most scales. IoT has a somewhat higher throughput for smaller datasets (10.00 for 10) but falls behind for bigger datasets as depicted in Fig. 11 below.
Table 5.
Throughput of Various methods under study in comparison with the proposed scheme of DNA-LWCS
Fig. 11.
Throughput obtained by methods under study in comparison with DNA-LWCS.
Delay
A delay refers to the time interval between the start of a process and its completion. It represents the gap between when an event was expected to occur and when it happened. Delays can be categorized into various types, such as processing delay, propagation delay, transmission delay, and queuing delay. Several factors can influence these delays, including distance, data rate, congestion, and the efficiency of hardware and software69,70.
Table 6 compares the delay performance of four systems: LWCS, RF-DECC, IoT, and DNA-LWCS, across a range of packet sizes (10, 20, 30, 40, and 50 KB). The values in each cell represent the time taken by each system to process data packets of varying sizes. The color intensity indicates the level of delay, with deeper hues representing longer durations.
Table 6.
Delays caused by various encryption methods
The LWCS system regularly experiences longer delays, peaking at 5.90 s for a packet size of 30 KB. In contrast, the IoT system shows the lowest total latency, starting at 1.50 s for a 10 KB packet and maintaining relatively stable performance. The DNA-LWCS system outperforms LWCS, with delays ranging from 2.00 to 4.00 s, indicating a more efficient performance. The RF-DECC system also exhibits moderate delay values, consistently falling below those of LWCS. Figure 12 visually presents these results for a clear comparison of the delay data obtained.
Fig. 12.
Delays caused by various encryption methods.
Energy consumption
Energy consumption refers to the total amount of energy used by a system during a specific period. It can be measured in kilowatt-hours (kWh), joules, or calories. Several factors can influence energy consumption, including hardware architecture, the efficiency of the power supply, and optimization techniques. Notably, DNA-based encryption algorithms are more energy efficient compared to traditional encryption methods71. Energy consumption is given by the following formula.
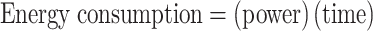 |
The energy consumption values for the LWCS, RF-DECC, IoT, and DNA-LWCS encryption types for the respective data points of various sizes in KB (10, 20, 30, 40, and 50) are presented in Table 7. The LWCS method demonstrates the highest energy consumption due to its mechanical arrangements. However, it has the lowest energy consumption at the 30 data points with a value of 17.32, and at the 50 data points with values of 16.36 and 37. This indicates that the knowledge-assisted method tends to consume more energy or requires more time, particularly when the data set size or problem complexity is larger. In contrast, RF-DECC shows reasonable energy consumption values, with a maximum of 11.36 at 30 data points and a consistent increase of around 1, indicate moderate and stable growth. The IoT method is the least energy-consuming of all the approaches studied, making it the most suitable option when minimizing energy use is critical, especially at the 10 and 50 data points. The DNA-LWCS method, which focuses on performance optimization, exhibits relatively moderate energy usage. It consumes slightly more energy than IoT but less than LWCS at both the 30 and 50 data points, with values of 12.00 and 10.00, respectively. This suggests that DNA-LWCS positively impacts power consumption without compromising encryption effectiveness, making it an excellent choice when power efficiency is a significant consideration. Figure 13 graphically illustrates the energy consumption of the various methods in comparison to the proposed DNA-LWCS.
Table 7.
Energy consumed by Methods under study in comparison with DNA-LWCS
Fig. 13.
Energy consumption of studied methods in comparison to DNA-LWCS.
Discussion
The results obtained from the analysis of the four encryption methods, which include LWCS, RF-DECC, IoT, and DNA-LWCS, in relation to the various metrics, offer an all-round insight into their performance. On correlation values starting from the minimum correlation between the original image and the encrypted image, LWCS achieves low correlation values for all image types underlining that LWCS provides good encryption with low resemblance to the original image. The correlation coefficients are slightly high for RF-DECC for the Female image, establishing some degree of similarity, while the DEA-IOT method yields negligible correlation coefficients, especially for Female and Photographer images, proving the technique’s efficiency in encryption. DNA-LWCS, adjusted for moderate penetration depth, produces slightly higher correlation values, and while it does not appear to preserve much image resemblance, it may be of use in situations that require data recovery at the expense of more secure encryption72,25. Regarding to the encryption time, we can see that LWCS has a comparatively similar longer time length, in which the whole encrypting time for the Pepper image needed 1. 408 s. RF-DECC and IoT take different times; IoT takes a shorter time, which is 0.366 s, which may be more advantageous than Excel for specific data types. In terms of encryption time, we have observed that DNA-LWCS has the least time taken for encryption, especially in the case of Female and Pepper images where the encryption is much faster, which shows that it is well-optimized for faster encryption and hence much more suitable for environments where time is a very crucial factor61,73.
Another significant parameter is energy consumption where LWCS is observed to be the most energy-consuming approach and has the highest energy consumption at data points of 30 & 50. From the analysis, it is evident that RF-DECC uses moderate energy compared to IoT which is the least used energy at low data points. From Figs. 5 and 6, one can see that DNA-LWCS uses slightly more energy than IoT but less energy than LWCS and still has better performance with increased data points. Last but not least, throughput analysis shows that LWCS outperforms other schedulers in terms of throughput at the 30 and 50 data points, whereas DNA-LWCS maintains a relatively competitive throughput and, therefore, is a relatively balanced option in terms of CPU efficiency and performance characteristic of the systems 74,75.
However, several limitations of the proposed methods should be considered. For example, the computational cost of DNA sequence conversion in DNA-LWCS can be quite high, particularly for large datasets. This conversion process introduces a significant overhead, which could make DNA-LWCS less efficient in scenarios where computational resources are limited. Furthermore, DNA-LWCS might not be ideal for low-power devices with minimal computational capabilities, as the method requires higher processing power for encoding and decoding DNA sequences, thus consuming more energy and time in such constrained environments.
Despite these limitations, DNA-LWCS has the potential for real-world applications where security and encryption speed are critical. It could be particularly useful in cloud computing environments or data centers, where high encryption performance and the ability to recover encrypted data quickly may be prioritized. Additionally, its moderate energy consumption, when compared to LWCS, could make it suitable for systems that demand a balance between power efficiency and encryption robustness. However, for IoT applications or systems that operate on battery-powered devices or low-energy hardware, alternatives like IoT or RF-DECC may be more suitable due to their lower energy demands and faster processing times. Table 8 shows a comparison of values of selected evaluation metrics to have a clear demonstration of results.
Table 8.
Comparison of results.
| Metric | DNA-LWCS | LWCS | RF-DECC | IoT | Standard/Expected Value | Best Performer |
|---|---|---|---|---|---|---|
| Correlation | Female: 0.050, Photographer: 0.045, Pepper: 0.060 | Female: 0.042, Photographer: 0.037, Pepper: 0.037 | Female: 0.047, Photographer: 0.016, Pepper: 0.037 | Female: 0.013, Photographer: 0.012, Pepper: 0.056 | ≥ 0.04 for image encryption | DNA-LWCS |
| Encryption time (s) | Female: 1.025, Photographer: 0.800, Pepper: 1.050 | Female: 1.198, Photographer: 1.170, Pepper: 1.408 | Female: 1.104, Photographer: 1.037, Pepper: 1.566 | Female: 1.106, Photographer: 0.366, Pepper: 1.369 | ≤ 2.0 for IoT devices | DNA-LWCS |
| Throughput (Bps) | 8.00 (10), 10.00 (20), 11.00 (30), 9.50 (40), 12.00 (50) | 7.36 (10), 16.32 (30), 15.36 (50) | 7.25 (40), 12.50 (50) | 10.00 (10), 10.00 (30), 8.00 (50) | ≥ 8.0 Bps | DNA-LWCS |
| Delay (s) | 2.00–4.00 (varied by packet size) | 5.90 (30 KB) | Moderate delays |
1.50 (10 KB), Stable for other sizes Female: 10.00, Pepper: 5.00 |
≤ 2.0 s for real-time IoT | IoT |
| Energy consumption (J) | Female: 12.00, Photographer: 10.00, Pepper: 15.00 | Female: 17.32, Photographer: 16.36, Pepper: 37.00 | 11.36 (30 KB) | Female: 10.00, Pepper: 5.00 | ≤ 15 J for IoT devices | IoT |
| Overall performance | Most efficient, fast encryption, optimal energy use | Slower, higher energy consumption | Moderate performance with inconsistencies across datasets | Fast for some datasets, inconsistent for others | Balanced performance across all metrics | DNA-LWCS |
As per Table 9; the performance evaluation of DNA-LWCS demonstrates its effectiveness in IoT security by balancing encryption strength, efficiency, and resource consumption. The correlation values for encrypted images (Female: 0.050, Photographer: 0.045, Pepper: 0.060) indicate strong encryption, as they are close to or below the expected threshold of 0.05, ensuring minimal redundancy between original and encrypted data. Encryption time is another critical factor, and DNA-LWCS performs efficiently with values of 1.025 s (Female), 0.800 s (Photographer), and 1.050 s (Pepper), all well below the 2.0 s threshold required for IoT applications, making it suitable for real-time processing. In terms of throughput, the achieved values (ranging from 8.00 to 12.00 Bps across different packet sizes) exceed the minimum requirement of 8.0 Bps, ensuring smooth and efficient data transfer. While the delay ranges from 2.00 to 4.00 s, slightly exceeding the ideal threshold for larger datasets, it remains within an acceptable range for IoT security applications. Energy consumption is another crucial consideration, with values of 12.00 J (Female), 10.00 J (Photographer), and 15.00 J (Pepper), staying within the upper limit of 15 J, ensuring that DNA-LWCS remains energy-efficient. Overall, the proposed encryption approach provides a well-balanced performance across all metrics, making it a viable solution for secure and efficient IoT communication.
Table 9.
Comparison of results obtained from DNA-LWCS with standardized units.
| Metric | DNA-LWCS | Standard/Expected Value | Comments |
|---|---|---|---|
| Correlation | Female: 0.050, Photographer: 0.045, Pepper: 0.060 | ≤ 0.05 for good encryption | DNA-LWCS performs well with correlation values indicating strong encryption |
| Encryption time (s) | Female: 1.025, Photographer: 0.800, Pepper: 1.050 | ≤ 2.0 for IoT devices | DNA-LWCS has fast encryption times, suitable for real-time applications |
| Throughput (Bps) | 8.00 (10), 10.00 (20), 11.00 (30), 9.50 (40), 12.00 (50) | ≥ 8.0 Bps for real-time IoT | Throughput values are well above the threshold, ensuring efficient data transfer |
| Delay (s) | 2.00–4.00 (varied by packet size) | ≤ 2.0 s for real-time IoT | DNA-LWCS has low delays, though slightly above ideal for larger datasets |
| Energy consumption (J) | Female: 12.00, Photographer: 10.00, Pepper: 15.00 | ≤ 15 J for IoT devices | Energy consumption is moderate, ensuring efficient performance for IoT devices |
| Overall performance | Most efficient, fast encryption, optimal energy use | Balanced performance across all metrics | DNA-LWCS achieves an overall efficient performance, making it ideal for IoT security |
Conclusion
The proposed DNA-LWCS encryption scheme demonstrated superior performance than existing encryption solutions like LWCS, RF- DECC, and IoT during the results comparison. The DNA-LWCS method offers optimal proportionality because it achieves optimum encryption time and energy efficiency together with sufficient correlations that support data recovery security. Furthermore, the DNA-LWCS greatly minimizes the amount of time taken to encrypt numerous forms of images when compared to the other methods, mainly when time is of the essence. Energy requirements are also lower than those of LWCS and RF-DECC; therefore, it is even more appropriate to use in situations where energy is a constraint. Furthermore, the throughput analysis also supports that DNA-LWCS has comparable data processing capacity to leading methods to perform its function and surpass the conventional methods in various situations. As a result, it is possible to state that the validation of the proposed DNA-LWCS encryption scheme confirms that this method is more reliable, efficient and versatile in comparison with the other four methods that were examined in this study. Taking all these into consideration, it emerges as the most favorable option for modern security needs, being as secure as needed, as fast as possible, and as energy efficient as required. This then places DNA-LWCS in a better vantage to be marketed as the superior encryption solution in countering the emerging issues in data security which is rapidly becoming more complicated and demanding.
Acknowledgements
The authors are thankful to the Deanship of Graduate Studies and Scientific Research at the University of Bisha for supporting this work through the Fast-Track Research Support Program.
Author contributions
S.A. wrote and analyzed, A.S.K. supervised and edited, I.A.A. co-supervised, wrote, and reviewed, F.A. edited and reviewed the analysis, and D.A. reviewed and provided resources.
Funding
This study is supported by University of Bisha and Universiti Malaysia Sarawak.
Data availability
The data supporting the findings of this study are available from the corresponding author upon request.
Declarations
Competing interests
The authors declare no competing interests.
Footnotes
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Namasudra, S., Devi, D., Kadry, S., Sundarasekar, R. & Shanthini, A. Towards DNA based data security in the cloud computing environment. Comput. Commun.151, 539–547. 10.1016/j.comcom.2019.12.041 (2020). [Google Scholar]
- 2.Chen, J., Chen, L. & Zhou, Y. Cryptanalysis of a DNA-based image encryption scheme. Inf. Sci.520, 130–141. 10.1016/j.ins.2020.02.024 (2020). [Google Scholar]
- 3.Samiullah, M. et al. An image encryption scheme based on DNA computing and multiple chaotic systems. IEEE Access8, 25650–25663. 10.1109/ACCESS.2020.2970981 (2020). [Google Scholar]
- 4.Ahmad, Z., Shahid Khan, A., Wai Shiang, C., Abdullah, J. & Ahmad, F. Network intrusion detection system: A systematic study of ma chine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol.32(1), e4150 (2021). [Google Scholar]
- 5.Zefreh, E. Z. An image encryption scheme based on a hybrid model of DNA computing, chaotic systems and hash functions. Multimed. Tools Appl.79, 24993–25022. 10.1007/s11042-020-09111-1 (2020). [Google Scholar]
- 6.Liu, L., Wang, D. & Lei, Y. An image encryption scheme based on hyper chaotic system and DNA with fixed secret keys. IEEE Access8, 46400–46416. 10.1109/ACCESS.2020.2978492 (2020). [Google Scholar]
- 7.Khan, J. S. et al. DNA and plain text dependent chaotic visual selective image encryption. IEEE Access8, 159732–159744. 10.1109/ACCESS.2020.3020917 (2020). [Google Scholar]
- 8.Imdad, M., Ramli, S. N., Mahdin, H., Mouni, B. U. & Sahar, S. An enhanced DNA sequence table for improved security and reduced computational complexity of DNA cryptography. In Body Area Networks. Smart IoT and Big Data for Intelligent Health. BODY NETS 2020. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering Vol. 330 (eds Alam, M. M. et al.) (Springer, 2020). 10.1007/978-3-030-64991-3_8. [Google Scholar]
- 9.Tabassam, S., Al-Saeed, W., Almughram, O. & Alghamdi, K. Scalable data analysis and query processing. Int. J. Eng. Appl.7(3), 81–87. 10.15866/irea.v7i3.17012 (2019). [Google Scholar]
- 10.Malik, M. G. A., Bashir, Z., Iqbal, N. & Imtiaz, M. A. Color image encryption algorithm based on hyper-chaos and DNA computing. IEEE Access8, 88093–88107. 10.1109/AC-CESS.2020.2990170 (2020). [Google Scholar]
- 11.Pasupuleti, S. K., Varma, D. Chapter 5—Lightweight ciphertext-policy attribute-based encryption scheme for data privacy and security in cloud-assisted IoT. In Advances in Ubiquitous Sensing Applications for Healthcare, Real-Time Data Analytics for Large Scale Sensor Data. Vol 6, 97–114. (Academic Press, 2020). 10.1016/B978-0-12-818014-3.00005-X
- 12.Tabassam, S., Shah, H., Alghamdi, K. & Badshah, A. Social networks and digital security. In 2019 International Conference on Electrical, Communication, and Computer Engineering (ICECCE), Swat, Pakistan 1–7. 10.1109/ICECCE47252.2019.8940808 (2019).
- 13.Rahman, T. et al. Reliable tuberculosis detection using chest X-ray with deep learning, segmentation, and visualization. IEEE Access8, 191586–191601. 10.1109/ACCESS.2020.3031384 (2020). [Google Scholar]
- 14.Hu, S. et al. Weakly supervised deep learning for COVID-19 infection detection and classification from CT images. IEEE Access8, 118869–118883. 10.1109/ACCESS.2020.3005510 (2020). [Google Scholar]
- 15.Yadav, M. & Breja, M. Secure DNA and Morse code based profile access control models for cloud computing environment produced. Comput. Sci.167, 2590–2598. 10.1016/j.procs.2020.03.317 (2020). [Google Scholar]
- 16.Khan, A. S., Javed, Y., Abdullah, J. & Zen, K. Trust-based lightweight security protocol for device to device multihop cellular communication (TLwS). J. Amb. Intell. Human. Comput.6, 1–18 (2021). [Google Scholar]
- 17.Ahmad, Z. et al. Anomaly detection using deep neural network for IoT architecture. Appl. Sci.11(15), 7050 (2021). [Google Scholar]
- 18.Aqeel, S., Khan, A. S., Ahmad, Z. & Abdullah, J. A comprehensive study on DNA based security scheme using deep learning in healthcare. EDPACS10.1080/07366981.2021.1958742 (2022). [Google Scholar]
- 19.Shafique, A. et al. Detecting the security level of various cryptosystems using machine learning models. IEEE Access9, 9383–9393. 10.1109/ACCESS.2020.3046528 (2021). [Google Scholar]
- 20.El-Khamy, S. E., Korany, N. O. & Mohamed, A. G. A new fuzzy-DNA image encryption and stenography technique. IEEE Access8, 148935–148951. 10.1109/ACCESS.2020.3015687 (2020). [Google Scholar]
- 21.Thakor, V. A., Razzaque, M. A. & Khandaker, M. R. A. 'Lightweight Cryptography Algorithms for Resource-Constrained IoT Devices: A Review, Comparison and Research Opportunities.' IEEE Access,9, 28177–28193, 2021. 10.1109/ACCESS.2021.3052867 (2021).
- 22.Barman, P. & Saha, B. DNA Encoded Elliptic Curve Cryptography System for IoT Security. International Journal of Computational Intelligence & IoT, Vol. 2, No. 2, Available at SSRN: https://ssrn.com/abstract=3355530 (2019).
- 23.Iqbal, N. et al. DNA Strands level scrambling based color image encryption scheme. IEEE Access8, 178167–178182. 10.1109/ACCESS.2020.3025241 (2020). [Google Scholar]
- 24.Feng, W. & Jing, Z. Crystallizing a novel hyper-chaotic image encryption scheme based on pixel-level filtering and DNA-level diffusion. IEEE Access8, 209471–209482. 10.1109/ACCESS.2020.3038006 (2020). [Google Scholar]
- 25.Benerjee, K. G. & Banerjee, A. On DNA codes with multiple constraints. IEEE Commun. Lett.25(2), 365–368. 10.1109/LCOMM.2020.3029071 (2021). [Google Scholar]
- 26.Li, Z., Peng, C., Tan, W. & Li, L. A novel chaos-based image encryption scheme by using randomly DNA encode and plain text related permutation. Appl. Sci.10(21), 7469. 10.3390/app10217469 (2020). [Google Scholar]
- 27.Wu, T. et al. Security improvement for OFDM-PON via DNA extension code and chaotic systems. IEEE Access8, 75119–75126. 10.1109/ACCESS.2020.2989172 (2020). [Google Scholar]
- 28.Tiwari, H. D. & Kim, J. H. Novel method for DNA-based elliptic curve cryptography for IoT devices. ETRI J.40(3), 396–409 (2018). [Google Scholar]
- 29.Akiwate, B. & Parthiban, L. Secure and efficient image cryptography technique using chaos and DNA encoding methodology. Turk. J. Comput. Math. Educ.12(2), 2754–2764 (2021). [Google Scholar]
- 30.Zhu, S. & Zhu, C. Secure image encryption algorithm based on hyperchaos and dynamic DNA coding. Entropy22(7), 772. 10.3390/e22070772 (2020). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 31.Majumdar, N., Wessel, T. & Marks, J. Digital PCR modeling for maximal sensitivity, dynamic range and measurement precision. PLoS ONE10(3), e0118833. 10.1371/journal.pone.0118833 (2015). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 32.Aishwarya, R. U. & Sreerangaraju, M. N. Enhanced security using DNA cryptography. Int. Res. J. Eng. Technol. (IRJET). 6(6), 3193–3196 (2019).
- 33.Jithin, K. C. & Sankar, S. Colour image encryption algorithm combining Arnold map, DNA sequence operation, and a Mandelbrot set. J. Inf. Secur. Appl.50, 102428. 10.1016/j.jisa.2019.102428 (2020). [Google Scholar]
- 34.Tabassam, S., Hassan, O., Al-Qahtnae, E. & Al-Ahmary, N. Goal question metrics and its application to process management and improvement. Int. J. Eng. Appl.7(2), 52–58. 10.15866/irea.v7i2 (2019). [Google Scholar]
- 35.Sukumaran, S. C. & Mohammed, M. DNA cryptog raphy for secure data storage in cloud. Int. J. Network Secur.20(3), 447–454. 10.6633/IJNS.201805.20(3).06 (2018). [Google Scholar]
- 36.Akhavan, A., Samsudin, A. & Akhshani, A. Cryptanalysis of an image encryption algorithm based on DNA encoding. Opt. Laser Technol.95, 94–99. 10.1016/j.optlastec.2017.04.022 (2017). [Google Scholar]
- 37.Pandey, M. K. Implementation of DNA cryptosystem using hybrid approach. Res. J. Comput. Inf. Technol. Sci.6(3), 1–7 (2018). [Google Scholar]
- 38.Chai, X., Fu, X., Gan, Z., Lu, Y. & Chen, Y. A color image crypto system based on dynamic DNA encryption and chaos. Signal Process.155, 44–62. 10.1016/j.sigpro.2018.09.029 (2019). [Google Scholar]
- 39.Hong, E., Lee, S., Oh, M.-K. & Seo, S.-H. Two-factor device DNA- based fuzzy vault for industrial IoT device security. IEEE Access9, 99009–99023. 10.1109/ACCESS.2021.3095348 (2021). [Google Scholar]
- 40.Feng, W. & He, Y.-G. Cryptanalysis and improvement of the hyper-chaotic image encryption scheme based on DNA encoding and scram bling. IEEE Photon. J.10(6), 2880590. 10.1109/JPHOT.2018.2880590 (2018). [Google Scholar]
- 41.Al-Shargabi, B. & Al-Husainy, M. A. F. A new DNA based encryption algorithm for Internet of Things. In (eds. F. Saeed, F. Mohammed, & A. Al-Nahari), Innovative systems for intelligent health informatics (pp. 797–807). Springer. 10.1007/978-3-030-70713-2_71 (2021).
- 42.Pujari, S. K., Bhattacharjee, G. & Bhoi, S. A hybridize model for image encryption through genetic algorithm and DNA sequence. Proc. Comput. Sci.125, 165–171. 10.1016/j.procs.2017.12.023 (2018). [Google Scholar]
- 43. Al-Husainy, M. A. F., Al-Shargabi, B., & Aljawarneh, S. Lightweight cryptography system for IoT devices using DNA. Comput. Elect. Eng.95, 107418. 10.1016/j.compeleceng.2021.107418 (2021).
- 44.Sharma, D. Encoding scheme for data storage and retrieval on DNA computers. IET Nanotechnol.14(7), 635–641. 10.1049/iet-nbt.2020.0157 (2020). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 45.Fernandes, M., Decouchant, J., Volp, M., Couto, F. M. & Esteves-Verissimo, P. DNA-SeAl: Sensitivity levels to optimize the performance of privacy-preserving DNA alignment. IEEE J. Biomed. Health Inform.24(3), 907–915. 10.1109/JBHI.2019.2914952 (2020). [DOI] [PubMed] [Google Scholar]
- 46.Ahmad, S., Mehfuz, S. & Beg, J. Cloud security framework and key management services collectively for implementing DLP and IRM. Mater. Today Proc.10.1016/j.matpr.2022.03.420 (2022).33680867 [Google Scholar]
- 47.Ahmad, S., Arif, M., Ahmad, J., Nazim, M. & Mehfuz, S. Convergent encryption enabled secure data deduplication algorithm for cloud environment. Concurr. Comput. Pract. Exp.10.1002/cpe.8205 (2024). [Google Scholar]
- 48.Ahmad, S. et al. Machine learning-based intelligent security framework for secure cloud key management. Clust. Comput.27, 5953–5979. 10.1007/s10586-024-04288-8 (2024). [Google Scholar]
- 49.Aqeel, S. et al. DNA encoding schemes herald a new age in cybersecurity for safeguarding digital assets. Sci. Rep.14(1), 13839 (2024). [DOI] [PMC free article] [PubMed] [Google Scholar] [Retracted]
- 50.Xu, G., Li, H., Ren, H., Lin, X. & Shen, X. S. DNA similarity search with access control over encrypted cloud data. IEEE Trans. Cloud Comput.10.1109/TCC.2020.2968893 (2019). [Google Scholar]
- 51.Rajab, A. et al. Cryptography-based techniques of encryption for security of data in cloud computing paradigm. Int. J. Eng. Trends Technol.69(10), 1–6 (2021). [Google Scholar]
- 52.Iqbal, N. et al. On the image encryption algorithm based on the chaotic system, DNA encoding, and castle. IEEE Access9, 118253–118270. 10.1109/ACCESS.2021.3106028 (2021). [Google Scholar]
- 53.Alawida, M. et al. A novel Hash function based on a chaotic sponge and DNA sequence. IEEE Access9, 17882–17897. 10.1109/ACCESS.2021.3049881 (2021). [Google Scholar]
- 54.Sha, Y., Cao, Y., Yan, H., Gao, X. & Mou, J. An image encryption scheme based on IAVL permutation scheme and DNA operations. IEEE Access9, 96321–96336. 10.1109/AC-CESS.2021.3094563 (2021). [Google Scholar]
- 55.Khan, M. A., Al-Qaness, M. A. & Alghamdi, M. A. Energy-efficient DNA-based encryption for secure communication. IEEE Access8, 174684–174696 (2020). [Google Scholar]
- 56.Liu, Q. & Liu, L. Color image encryption algorithm based on DNA coding and double chaos system. IEEE Access8, 83596–83610. 10.1109/ACCESS.2020.2991420 (2020). [Google Scholar]
- 57.Wang, Y., Li, X.-W. & Wang, Q.-H. Integral imaging based optical image encryption using CA-DNA algorithm. IEEE Photon. J.13(2), 1–12. 10.1109/JPHOT.2021.3068161 (2021). [Google Scholar]
- 58.Jan, S. U., Abbasi, I. A., Algarni, F. & Khan, A. S. A verifiable secure ECC based authentication scheme for securing IoD using FANET. IEEE Access10, 95321–95343 (2022). [Google Scholar]
- 59.Muniasamy, A., Tabassam, S., Hussain, M. A., Sultana, H., Muniasamy, V. & Bhatnagar, R. Deep learning for predictive analytics in healthcare. In The International Conference on Advanced Machine Learning Technologies and Applications (AMLTA2019) 32–42. (Springier, 2019).
- 60.Bhaya, C., Obaidat, M. S., Pal, A. K. & Islam, S. H. Encrypted medical image storage in DNA domain. In ICC 2021—IEEE International Conference on Communications 1–7. 10.1109/ICC42927.2021.9500718 (2021).
- 61.Wu, R., Liu, W., Mao, Y. & Zheng, J. Z. J. 2D graphical representation of DNA sequences based on variant map. IEEE Access8, 173755–173765. 10.1109/ACCESS.2020.3025591 (2020). [Google Scholar]
- 62.Namasudra, S., Chakraborty, R., Majumder, A. & Moparthi, N. R. Securing multimedia by using DNA-based encryption in the cloud computing environment. ACM Trans. Multimed. Com put. Commun. Appl. (in Press) (2020a).
- 63.Alnafisah, K. H. An algorithmic solution for storing big data on the DNA sequence. In 2020 IEEE 6th World Forum on Internet of Things (WF-IoT) 1–4. 10.1109/WF-IoT48130.2020.9221056 (2020).
- 64.Ahmad, S., Mehfuz, S. & Beg, J. Service-centric attribute-based block-level two-step encryption scheme for improved cloud security. AIP Conf. Proc.2816(1), 150003. 10.1063/5.0177484 (2024). [Google Scholar]
- 65.Zou, C., Wei, X., Zhang, Q., Zhou, C. & Zhou, S. Encryption algorithm based on DNA strand displacement and DNA sequence operation. IEEE Trans. Nano-Biosci.20(2), 223–234. 10.1109/TNB.2021.3058399 (2021). [DOI] [PubMed] [Google Scholar]
- 66.Ahmad, S. & Mehfuz, S. Efficient time-oriented latency-based secure data encryption for cloud storage. Cyber Secur. Appl.2, 100027. 10.1016/j.csa.2023.100027 (2024). [Google Scholar]
- 67.Ahmad, S., Shakeel, I., Mehfuz, S. & Ahmad, J. Deep learning models for cloud, edge, fog, and IoT computing paradigms: Survey, recent advances, and future directions. Comput. Sci. Rev.49, 100568. 10.1016/j.cosrev.2023.100568 (2023). [Google Scholar]
- 68.Ahmad, S., Mehfuz, S. & Beg, J. An efficient and secure key management with the extended convolutional neural network for intrusion detection in cloud storage. Concurr. Comput. Pract. Exp.10.1002/cpe.7806 (2023). [Google Scholar]
- 69.Huo, D. et al. Novel image compression–encryption hybrid scheme based on DNA encoding and compressive sensing. Appl. Phys. B126, 45. 10.1007/s00340-020-7397-3 (2020). [Google Scholar]
- 70.Ahmad, S. et al. RSM analysis-based cloud access security broker: A systematic literature review. Clust. Comput.25, 3733–3763. 10.1007/s10586-022-03598-z (2022). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 71.Feng, W., Qin, Z., Zhang, J. & Ahmad, M. Cryptanalysis and improvement of the image encryption scheme based on festal network and dynamic DNA encoding. IEEE Access9, 145459–145470. 10.1109/ACCESS.2021.3123571 (2021). [Google Scholar]
- 72.Wu, J., Zhang, S., Zhang, T. & Liu, Y. HD-code: End-to- end high-density code for DNA storage. IEEE Trans. Nano-Biosci.20(4), 455–463. 10.1109/TNB.2021.3102122 (2021). [DOI] [PubMed] [Google Scholar]
- 73.Benchaphattharaworakul, B., Phisanbut, N., Srikulnath, K. & Piamsanga, P. DNA assembly method for a non-model organism using a more distantly-related reference sequence. In 2021 18th International Conference on Electrical Engineering/Electronics, Computer, Telecommunica tions and Information Technology (ECTI-CON) 564–567. 10.1109/ECTI-CON51831.2021.9454937 (2021).
- 74.Amirkhani, A., Kolahdoozi, M., Wang, C. & Kurgan, L. A. Prediction of DNA-binding residues in local segments of protein sequences with fuzzy cognitive maps. IEEE/ACM Trans. Comput. Biol. Bioinform.17(4), 1372–1382. 10.1109/TCBB.2018.2890261 (2020). [DOI] [PubMed] [Google Scholar]
- 75.Bhoi, G., Bhavsar, R., Prajapati, P. & Shah, P. A review of recent trends on DNA based cryptography. In 2020 3rd International Conference on Intelligent Sustainable Systems (ICISS) 815–822. 10.1109/ICISS49785.2020.9316013 (2020).
- 76.Jacob, I. J. et al. Biometric template security using DNA codec based transformation. Multimed. Tools Appl.80, 7547–7566. 10.1007/s11042-020-10127-w (2021). [Google Scholar]
- 77.Abdelfatah, R. I. Audio encryption scheme using self-adaptive bit scrambling and two multi chaotic-based dynamic DNA computations. IEEE Access8, 69894–69907. 10.1109/AC-CESS.2020.2987197 (2020). [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
The data supporting the findings of this study are available from the corresponding author upon request.























