Abstract
Energy consumption in Wireless Sensor Networks (WSNs) has become a critical concern due to the proliferation of sensors in internet-connected devices. Existing solutions often address energy efficiency in isolation, failing to consider the complex interplay of factors affecting WSN performance. In this context, this study proposes an integrated approach, Vigorous Technique for Augmented Lifetime (ViTAL), which holistically addresses the challenges of node positioning, network topology, radio conditions, and node mobility to optimize energy efficiency in WSNs. The proposed approach consists of three phases: minimizing the number of nodes to cover a specific area, constructing a Connected Dominating Set (CDS) for packet routing, and integrating the 4-factor Cluster Head (CH) selection model in the WSNs. This multi-faceted approach is necessary to overcome the limitations of existing methods that often focus on single aspects of WSN optimization, leading to suboptimal overall performance. The results demonstrate that ViTAL’s integrated approach, which combines optimized deployment through HSA and efficient routing using CDS, significantly outperforms traditional protocols in both static and mobile scenarios. In static environments, ViTAL achieves average improvements of 80.9%, 62%, and 58% in network lifetime compared to LEACH, EE-LEACH, and I-LEACH respectively, when using optimized deployment. The overall throughput experiences average increases of 83%, 59%, and 52%, while the average residual energy is enhanced by 68%, 58%, and 41%, respectively. In mobile scenarios, ViTAL extends the lifespan of the first node by 68.2%, 49%, and 42%, and increases the number of rounds before the last node becomes inactive by 74%, 52%, and 36% compared to LEACH, EE-LEACH, and I-LEACH. The throughput in mobile environments improves by 57%, 50%, and 37%, respectively, showcasing ViTAL’s adaptability to node mobility.
Subject terms: Computer science, Information technology
Introduction
WSNs have become indispensable across diverse domains, transforming environmental monitoring, healthcare, industrial automation, and smart city applications by transforming data collection and enabling real-time decision-making. The WSN market is expected to experience further growth, with a projected market size of about USD 426.2 billion by 20301, reflecting a compound annual growth rate of 18.3% from 2018 to 20262. As WSNs continue to evolve and expand, the issue of energy efficiency takes center stage. Although technological advancements have reduced energy consumption per individual device, the exponential increase in the number of deployed sensors necessitates the optimization of energy utilization to ensure sustainable operation. Addressing energy efficiency holistically requires optimizing multiple factors, such as deployment strategies, topology control, and adaptive routing protocols, to prolong the network lifespan and reduce operational costs. The deployment and routing strategies in these networks are vital for energy efficiency. Deployment strategies, covering node placement and coverage , help minimize redundancy and maximize the effectiveness of sensor nodes, conserving energy. Efficient routing protocols, based on remaining energy, hop count, and path quality, reduce transmission energy3. By addressing these all together, WSNs operate optimally, consequently enhancing lifetime4,5.
Numerous research studies have been conducted to boost the efficiency of large-scale networks. In the domain of communications in brain networks, an intriguing insight sheds light on the concept of navigation routing6. Their research demonstrates that navigation routing in the brain can demonstrate comparable efficiency to the traditional shortest-path routing, effectively distribute the load across different paths, and mitigates the risks of node failures. Researchers have explored several promising dimensions that aim to maximize the performance of the WSN in different aspects. These include the development of energy-efficient routing protocols7, adaptive power management techniques8, duty cycling mechanisms9, data aggregation and compression algorithms10, sleep scheduling strategies11, the use of renewable energy sources12, energy harvesting techniques13, cooperative communication schemes14, machine learning-based energy optimization15, and cross-layer optimization approaches16. While these approaches address specific facets of energy optimization, their effectiveness often hinges on foundational deployment parameters. However, existing works often fail to provide an in-depth study that combines deployment strategies with routing protocols. Most approaches focus on either deployment or routing in isolation, neglecting the interplay between the two. This limits their effectiveness in real-world scenarios, where both aspects must work together to optimize network performance.
This paper proposes a three-phase approach named ViTAL to investigate the importance of deployments and radio conditions, as well as to enhance energy efficiency and maximize the network’s lifetime. It is not a standalone protocol but rather a comprehensive approach that incorporates various techniques and considerations to enhance energy efficiency and maximize network lifetime. Firstly, the sensor nodes are deployed randomly within the network area. Subsequently, optimal node locations are determined to maintain a coverage ratio of 90%. This ensures efficient coverage across the network. In the next phase, the nodes utilize a approach, which limits the number of broadcast transmissions by utilizing unicast or multicast communication. This reduces unnecessary energy consumption. Finally, a modified version of the selection in the Low-Energy Adaptive Clustering Hierarchy (LEACH) routing model is leveraged. This selection process takes into account four crucial parameters: node residual energy, neighbor ratio, distance to the BS, and the radio condition of the node. By incorporating these factors into the CH selection process, the overall network lifetime can be improved. Our proposed strategy addresses the limitations of deployments and radio conditions while leveraging the strengths of existing protocols to optimize energy efficiency in WSNs. ViTAL has been evaluated in static and mobile scenarios where it showed substantial improvements. It achieved an average increase of 75% and 74% in network lifetime, extended the first node’s lifetime by 80.9% and 68.2%, increased residual energy by 68% and 54.5%, and improved packet transmission to the BS by 83% and 57% in both scenarios, respectively. The key contributions of our work are summarized as follows.
Our proposed approach ViTAL swiftly integrates the Harmony Search Algorithm (HSA)-based optimized deployment fused with connecting dominating set to further limit the number of sensors required for coverage area. This allows WSNs to enhance energy efficiency and maximize their lifetime.
Our customized approach provides applications to adjust the routing tailored to the specific requirements of WSNs. These protocols optimize data transmission, minimize energy consumption, and strengthen network scalability, leading to enhanced performance and prolonged network lifetime.
ViTAL has been tested in multiple network scenarios where it outperformed state-of-the-art for deployment and routing approaches. This validation demonstrates the effectiveness of ViTAL in optimizing energy consumption and improving the lifetime of sensor networks in real-world scenarios.
The rest of this paper is organized as follows. Section “Related work” presents the fundamental terminologies and reviews various related works concerning node deployment and the existing research on LEACH and its subsequent protocols proposed for optimization purposes. Section “ViTAL” introduces our proposed approach, ViTAL. Next, in section “Experiments and results”, the experimental setup, results, and corresponding analyses are presented, highlighting notable landmarks. Finally, in section “Conclusion and future works”, the paper is concluded and future directions for research are outlined.
Related work
Deployment in WSN
The architecture of WSNs is composed of sensor nodes and a Base Station (BS) or sink deployed over a geographical area or Region of Interest (ROI) to monitor any physical phenomena as shown in Fig. 1. These networks aim to achieve effective coverage and a sense of ROI and send the data to the internet through the sink. Various sensing models, such as Boolean, multi-layer, Elfes, Li, and shadow-fading, have already been discussed in detail17. When deploying a WSN, the first step is to determine the monitoring objectives, which can involve full area coverage, target coverage, or barrier coverage. Full coverage ensures that every point within the field of interest is within the sensing range of at least one sensor node, while target coverage focuses on observing specific targets18,19. Different approaches have been proposed, such as the concept of an “r-strip” for node placement to achieve full coverage20. However, this solution may face practical challenges in deployment. Maintaining target coverage while conserving energy has also been addressed in the work21. Additionally, barrier coverage, which involves detecting movement across a barrier of sensors, has been studied to quantify the coverage improvement with the addition of more sensors. Barrier coverage plays a critical role in intrusion detection and perimeter defense applications, further underscoring its importance in security-sensitive deployments. These considerations play a significant role in optimizing WSN deployments and achieving efficient monitoring in various applications.
Fig. 1.

Model of WSN.
Several deployment algorithms have been proposed to optimize the coverage of a WSN while minimizing the number of nodes utilized. One such algorithm in the literature is HSA-based deployment22, which focuses on deterministic deployment to achieve maximum network coverage. However, this algorithm does not consider network connectivity and energy consumption of the nodes. A differential evolution-based regional coverage-enhancing algorithm is introduced for directional 3D WSNs23. This algorithm aims to maximize coverage while minimizing the number of sensors employed. Additionally, the area coverage problem has been addressed by strategically relocating a specific number of sensors to ensure that every point in the sensing terrain is monitored by at least k sensors24. The area coverage problem is further tackled where researchers map it as the Maximum Coverage Sensor Deployment Problem (MCSDP)25. A genetic algorithm is utilized to solve MCSDP for a WSN with homogeneous sensors in a 2D Euclidean area. These approaches highlight the trade-off between computational complexity and coverage quality, with heuristic solutions providing a balance for real-time applications. These innovative deployment algorithms lay the foundation for efficient coverage and resource utilization in WSNs, setting the stage for further advancements in this field. However, even the best deployment strategy cannot yield optimal results without a decent routing strategy.
Routing
Introduced as a pioneering clustering routing protocol for WSNs, LEACH26 focuses on maximizing energy efficiency through the selection of CHs based on a rotation-based approach that utilizes random numbers. LEACH operates in multiple rounds, each consisting of two phases: the set-up phase and the steady-state phase. In the set-up phase, clusters are formed, and CHs allocate (TDMA) schedules to neighboring member nodes. To determine the CHs, each node generates a random priority value within the range of 0 to 1 and compares it to a threshold value, T(n), calculated using Eq. 1. If the generated random number of a sensor node is less than T(n), that node becomes a CH.
 |
1 |
where  represents the desired percentage of sensor nodes to become CHs among all sensor nodes.
represents the desired percentage of sensor nodes to become CHs among all sensor nodes.  is the set of nodes that have not been selected as CHs in the last
is the set of nodes that have not been selected as CHs in the last  rounds. Each node randomly selects a value between 0 and 1, and if the selected value is less than the threshold
rounds. Each node randomly selects a value between 0 and 1, and if the selected value is less than the threshold  , the node becomes a CH for the current round. This probabilistic mechanism ensures that nodes take turns being the CH, helping to distribute energy consumption across the network. While LEACH successfully reduces energy consumption to a significant extent through its CH selection strategy, there still is a limitation to be taken care of. In some cases, a node that previously served as a CH and currently has low energy levels can be selected as a CH again. This situation increases the likelihood of network failure earlier than expected. This indicates that further improvements are necessary to ensure the reliability and stability of the network. While LEACH is foundational, its randomized approach may lead to uneven energy distribution and early node failure. This has driven extensive research into enhancing clustering protocols to improve network longevity and load balancing.
, the node becomes a CH for the current round. This probabilistic mechanism ensures that nodes take turns being the CH, helping to distribute energy consumption across the network. While LEACH successfully reduces energy consumption to a significant extent through its CH selection strategy, there still is a limitation to be taken care of. In some cases, a node that previously served as a CH and currently has low energy levels can be selected as a CH again. This situation increases the likelihood of network failure earlier than expected. This indicates that further improvements are necessary to ensure the reliability and stability of the network. While LEACH is foundational, its randomized approach may lead to uneven energy distribution and early node failure. This has driven extensive research into enhancing clustering protocols to improve network longevity and load balancing.
Researchers continue to actively explore variations and alternatives of the LEACH protocol to better address its limitations and meet the evolving needs of WSNs3. A thorough comparison of LEACH successors is discussed in another study27,28, which covers key research domains including energy efficiency, security, data aggregation, and mobility. In the context of energy consumption and network lifetime, the random selection of CH and single-hop communication from CH to BS are the two main limitations of LEACH. To counter that, the Energy-Efficient Multi-hop LEACH (EEM-LEACH)29 is proposed to select the CH based on residual energy, average energy consumption of the nodes, and multi-hop paths to the BS. EEM-LEACH augments energy efficiency by 42%, but leads to increased control packets and packet delay due to complex computations for relay node selection. Enhanced Centralized-LEACH30 improves network lifetime by efficiently distributing CHs . This centralized distribution results in better energy utilization. Similarly, I-LEACH31 employs distributed clustering, and the CH is selected by considering residual energy, the number of neighboring nodes, and the distance to the BS. Although it achieves a 55% augmented lifetime of the network, sudden CH failure remains a concern. Energy Efficient-LEACH32 uses Gaussian distribution of node deployment, conditional probability for data aggregation, and residual energy for CH selection. However, it faces complexity and risks to data integrity. Apart from the above-mentioned successors, research has been conducted for energy harvesting techniques in protocols like EH-WSN-based LEACH33, while optimization methods are employed in protocols such as LEACH-SAGA34 and LEACH-GA35. In order to better summarize, Table 1 shows a list of some popular variations along with their improvement compared to basic LEACH.
Table 1.
LEACH variations and their improvement.
| Name | Improvement (%) w.r.t LEACH | Year |
|---|---|---|
| LEACH-C36 | 30 | 2002 |
| MELEACH-L37 | 60 | 2008 |
| LEACH-DCHS38 | 30 | 2008 |
| LEACH-B39 | 20 | 2010 |
| LEACH-GA35 | 50 | 2011 |
| LEACH-SWDN40 | 24 | 2012 |
| Q-LEACH41 | 41 | 2013 |
| LEACH-SAGA34 | 10 | 2014 |
| LEACH-MAC42 | 24 | 2016 |
| EHA-LEACH43 | 29 | 2016 |
| O-LEACH44 | 30 | 2016 |
| IMHT-LEACH45 | 55 | 2017 |
| IoT-LEACH46 | 52 | 2018 |
| MG-LEACH47 | 24 | 2019 |
| BRE-LEACH48 | 24 | 2019 |
| Enhanced LEACH49 | 4 | 2019 |
| MW-LEACH50 | 20 | 2020 |
| LEACH-K51 | 54 | 2020 |
| NOVEL-LEACH-POS52 | 41 | 2020 |
| ESO-LEACH53 | 50 | 2021 |
| ETH-LEACH54 | 54 | 2021 |
| EACR-LEACH55 | 4 | 2022 |
| S-LEACH56 | 36 | 2022 |
| LEACH-DSA57 | 62 | 2022 |
Besides, threshold sensitive energy efficient sensor network58 offers improved energy efficiency by dynamically adjusting the duty cycle of each node, but it may suffer from higher latency due to its hybrid communication approach. Stable election protocol59 focuses on stability and energy balancing, addressing some of the limitations of LEACH in terms of network lifetime. However, it introduces additional overhead due to the need for stability calculations. Power-efficient gathering in sensor information system60 provides energy-efficient data transmission and avoids the energy-hungry clustering process of LEACH, but it requires precise location information and coordination among nodes. In summary, these protocols offer distinct approaches to energy optimization and network performance in WSNs, providing alternative options to LEACH depending on the specific requirements and constraints of the application.
The selection of the LEACH base model over other alternatives in this work is justified based on its unique strengths that align directly with our research objectives. LEACH has garnered significant recognition and popularity as a pioneering clustering routing protocol for WSNs. Its primary focus on maximizing energy efficiency is particularly crucial in the context of our work, where we aim to assess the influence of sensor nodes’ position and mobility on energy consumption. LEACH’s utilization of a rotation-based CH selection mechanism, complemented by its well-established clustering and TDMA scheduling techniques, provides a solid framework for investigating the intricate impact of topology and radio conditions on energy efficiency. Moreover, the simplicity and wide acceptance of LEACH within the research community ensure easy comparability with existing studies, allowing us to build upon a robust foundation of prior knowledge. By leveraging LEACH in our study, we can gain valuable insights into optimizing energy consumption in WSNs, ultimately enhancing network lifetime and strengthening resilience in static and mobile scenarios.
ViTAL
The proposed work is inspired by a research, where it is suggested that comparable performance can be achieved by employing navigation instead of strictly following the shortest path4. This insight is particularly valuable as it helps alleviate the operational burden on specific nodes that are situated in favorable topological conditions. By adopting navigation-based routing, the strain on these nodes can be mitigated, as they would otherwise experience more significant stress compared to other nodes. A comprehensive approach ViTAL is proposed that addresses the challenges of sensor nodes’ deployment, coverage maintenance, energy consumption, and efficient communication in WSNs. ViTAL consists of three key phases designed to optimize the network’s energy efficiency and maximize its lifetime. In the first phase, sensor nodes are randomly deployed across the network area, establishing an initial configuration. Then the number of nodes are minimized by taking it as an optimization problem by taking the coverage ratio as a constraint. The second phase involves the utilization of a CDS approach, where nodes employ unicast or multicast communication to limit unnecessary broadcast transmissions, reducing energy consumption. Additionally, the CDS approach ensures efficient network connectivity and reliability. In the final phase, ViTAL incorporates a modified approach for CH selection in LEACH. This selection process considers crucial parameters such as node’s residual energy, neighbor count, distance to the BS, and radio conditions, enabling effective routing decisions and further extending the network’s lifetime. By integrating these phases, ViTAL provides a comprehensive solution that addresses the challenges of sensor node deployment, coverage maintenance, energy consumption, and efficient communication in WSNs, ultimately enhancing energy efficiency and maximizing the network’s lifetime.
Deployment
In the initial phase of our approach, sensor nodes are randomly deployed within a specified area . Subsequently, a relocation process is carried out based on the number of nodes and a predetermined coverage threshold, with the objective of identifying optimal positions for the deployed nodes. To achieve this, an existing model22 has been employed. This involves utilizing the HSA, a meta-heuristic optimization algorithm inspired by the harmonious behavior of musicians tuning their instruments to achieve balance. HSA has demonstrated success in solving various NP-hard optimization problems61. The purpose for the use of HSA is to refine the placement of the randomly deployed nodes and provide the minimum number of nodes and their position to meet the coverage criteria. Thus, enhancing the overall coverage and effectiveness of the WSN. This relocation process contributes to the network’s ability to efficiently monitor the designated area of interest.
Network model and formulation
Within a monitored network area A, characterized by parameters of width and height, comprising  cells, the center of each cell represents a point of demand denoted as P(x, y). In WSNs, the selection of an appropriate sensing model plays a crucial role. Two commonly used sensing models in WSNs are the binary (disk) model and the probabilistic model. In the binary model, the sensor node, referred to as
cells, the center of each cell represents a point of demand denoted as P(x, y). In WSNs, the selection of an appropriate sensing model plays a crucial role. Two commonly used sensing models in WSNs are the binary (disk) model and the probabilistic model. In the binary model, the sensor node, referred to as  , is defined by its coordinates
, is defined by its coordinates  . This model allows for determining the probability of sensor
. This model allows for determining the probability of sensor  covering a specific point of interest
covering a specific point of interest  using Eq. (2). The sensing range of the sensor node is represented by
using Eq. (2). The sensing range of the sensor node is represented by  , which is the maximum distance within which it can detect a target or event. The Euclidean distance from the sensor hub to the point of interest
, which is the maximum distance within which it can detect a target or event. The Euclidean distance from the sensor hub to the point of interest  is measured by using Eq. (3). The coverage probability,
is measured by using Eq. (3). The coverage probability,  of a sensor
of a sensor  at a specific point P is based on the distance
at a specific point P is based on the distance  between the sensor node and the point. It is mathematically represented by (4). Table 2 shows the notation and their description.
between the sensor node and the point. It is mathematically represented by (4). Table 2 shows the notation and their description.
 |
2 |
 |
3 |
 |
4 |
where:
 : Sensing range of the sensor.
: Sensing range of the sensor. : Uncertainty margin of the sensor’s range.
: Uncertainty margin of the sensor’s range. : Scaling factors to adjust the drop-off in the transition zone.
: Scaling factors to adjust the drop-off in the transition zone. : Functions of distance and uncertainty.
: Functions of distance and uncertainty. : Exponents that control the steepness of the decay in the coverage probability.
: Exponents that control the steepness of the decay in the coverage probability.
The parametric variables  ,
,  ,
,  ,
,  ,
,  , and
, and  are related to the sensor nodes and
are related to the sensor nodes and  is the factor of uncertainty for detecting the coverage area of sensors. where
is the factor of uncertainty for detecting the coverage area of sensors. where  and
and  are computed by Eq. (5) and Eq. (6) respectively.
are computed by Eq. (5) and Eq. (6) respectively.
 |
5 |
 |
6 |
When a point j is located in an area covered by multiple sensors ( ), its coverage probability P(j) is calculated by combining the coverage probabilities of all overlapping sensors. The coverage probability
), its coverage probability P(j) is calculated by combining the coverage probabilities of all overlapping sensors. The coverage probability  is defined by Eq. 7:
is defined by Eq. 7:
 |
7 |
Here,  is the coverage threshold required by the application to maintain
is the coverage threshold required by the application to maintain  with 1 representing 100% coverage requirement. If
with 1 representing 100% coverage requirement. If  , then the point of demand P covered effectively. The value of
, then the point of demand P covered effectively. The value of  depends on application32. The coverage ratio is calculated by using Eq. (8).
depends on application32. The coverage ratio is calculated by using Eq. (8).
 |
8 |
In above equation,  represents the overall area of the location whereas
represents the overall area of the location whereas  represents only the effective coverage area.
represents only the effective coverage area.
Table 2.
Notation and their description.
| Notation | Description |
|---|---|
| G | Set of all sensor nodes |
 |
Sensor node |
| W | Width of the network |
| H | Height of the network |
 |
Coverage threshold |
 |
Distance between sensor  and point P and point P
|
 |
Coverage probability of P by 
|
 |
Sensing range of sensor |
 |
Uncertainity margin in 
|
 |
Coverage ratio |
 |
Minimum distance between the sensors |
 |
Coverage probability when P is covered by multiple sensors |
The coverage probability for each demand point j is classified into following four distinct categories, demonstrated in the following Fig. 2. These probabilities are determined by the value of the overlap coverage probability  calculated through Eq. 7. These categories help quantify the level of sensor coverage for each point in the network.
calculated through Eq. 7. These categories help quantify the level of sensor coverage for each point in the network.
Fig. 2.

Target point coverage classification.
If
 , the target point is fully covered
, the target point is fully coveredIf
 , the target point is partially covered, but considered as acceptable)
, the target point is partially covered, but considered as acceptable)If
 , the target point is partially covered - but considered as unacceptable)
, the target point is partially covered - but considered as unacceptable)If
 , it is no coverage point
, it is no coverage point
HS begins with the Harmony memory that is used to represent the quantity of sensor hub location, starting with the random deployment of initial nodes as per lines 1-2 in algorithm 1. Initial random deployment ensures wide area coverage, but may lead to sensor redundancy or coverage gaps. HSA iteratively optimizes placement to minimize node count while maintaining effective coverage.
Objective function
The definition of objective function is the key factor when solving an optimization problem. Objective functions defined in Eq. (9) and equations till Eq. (20), used in our simulations, are already presented22 , as in line 3 of the algorithm 1.
 |
9 |
here, s is the number of sensor nodes,  is the coverage ratio, minimum distance between sensor nodes is represented by
is the coverage ratio, minimum distance between sensor nodes is represented by  . .
. .  is measured by Eq. (9a). The objective function seeks to minimize the number of sensor nodes while ensuring coverage efficiency by maintaining a balance between node count and their spatial distribution.
is measured by Eq. (9a). The objective function seeks to minimize the number of sensor nodes while ensuring coverage efficiency by maintaining a balance between node count and their spatial distribution.
 |
9a |
This equation calculates a ratio between the minimum distance between sensor nodes and the maximum possible distance in the field. The numerator finds the shortest Euclidean distance between any two sensors. The denominator represents the longest possible distance, which is the diagonal of the monitored area. The monitored field’s dimensions are adjusted to prevent sensors from detecting areas outside the intended region. This is done by subtracting the difference between the sensing range ( ) and uncertainty value (
) and uncertainty value ( ) from the original width (W) and height (H). The resulting modified dimensions (
) from the original width (W) and height (H). The resulting modified dimensions ( and
and  ) ensure that sensors stay within the field’s boundaries and do not sense beyond them.
) ensure that sensors stay within the field’s boundaries and do not sense beyond them.
K, in the Eq. 9, is the constant for WSN that scales coverage efficiency by balancing the trade-offs between minimizing the number of sensor nodes and maintaining effective network coverage. It is calculated as the ratio of the total initial energy of the network ( ) to the desired coverage ratio (
) to the desired coverage ratio ( ). For example, with 100 nodes each having an initial energy of 0.5 J, and a desired coverage ratio of 90%,
). For example, with 100 nodes each having an initial energy of 0.5 J, and a desired coverage ratio of 90%,  is computed as follows:
is computed as follows:
 |
9b |
Here,  J and
J and  . During the optimization process,
. During the optimization process,  remains constant. Harmony Memory Size (HMS), Harmony Memory Considering Rate (HMCR), Pitch Adjusting Rate (PAR), Bandwidth (BW) and stopping criteria are the HS parameters, as shown in line 4 of the algorithm 1. Lines 5 to 18 of the HSA follows the iterations steps until the nodes are at their optimal positions. Following are the steps the algorithm follows.
remains constant. Harmony Memory Size (HMS), Harmony Memory Considering Rate (HMCR), Pitch Adjusting Rate (PAR), Bandwidth (BW) and stopping criteria are the HS parameters, as shown in line 4 of the algorithm 1. Lines 5 to 18 of the HSA follows the iterations steps until the nodes are at their optimal positions. Following are the steps the algorithm follows.
Step 1: Sensors Deployment For every choice of variable all conceivable scope of qualities is generated from solution vector,  , in this
, in this  is known as the lower bound and
is known as the lower bound and  is known as the upper bound of
is known as the upper bound of  . These lower limits of x and y-axis can be estimated by the use of Eq. (10) and Eq. (11).
. These lower limits of x and y-axis can be estimated by the use of Eq. (10) and Eq. (11).
 |
10 |
 |
11 |
 represents uncertainty parameters and
represents uncertainty parameters and  is the sensing limit.
is the sensing limit.
In a case where the given networks have a non-zero origin value, Eq. (11) is updated by adding a new origin value. The width W and height H of the provided network limited all the sensor hubs on the upper boundary of the x-axis and y-axis respectively. The upper limits can be determined by Eq. (12) and Eq. (13).
 |
12 |
 |
13 |
The random locations of the sensor nodes are generated as in the equations (14) and (15).
 |
14 |
 |
15 |
Step 2: Determining the desired number of Sensors To find the minimum and maximum number of sensors, Eq. (16) and Eq. (17) can be used respectively. This is used in line 9 of the Algorithm 1. These bounds ensure that the sensing range  and uncertainty
and uncertainty  define the minimum and maximum required sensor density to maintain desired coverage levels in a grid of width W and height H.
define the minimum and maximum required sensor density to maintain desired coverage levels in a grid of width W and height H.
 |
16 |
 |
17 |
 is used to define the length of HMV with the help of two parameters namely
is used to define the length of HMV with the help of two parameters namely  and
and  .
.  is calculated by Eq. (18).
is calculated by Eq. (18).
 |
18 |
Algorithm 1.
HSA assisted deployment22
Step 3: Improvise a New Harmony Vector The goal is to adjust sensor positions iteratively to reduce overlap while maintaining optimal coverage. In this step, a new candidate sensor node configuration is generated by modifying the existing sensor node positions within the search space. The new harmony vector is defined as  , representing the updated positions of sensor nodes in the network. From the harmony memory vectors stored in HM, Harmony vector
, representing the updated positions of sensor nodes in the network. From the harmony memory vectors stored in HM, Harmony vector  inherits the values of its components with the possibility of HMCR. A new random value of (
inherits the values of its components with the possibility of HMCR. A new random value of ( ) is chosen from the list of available positions, as in line 11. If the generated number lies in the probability of 1- HMCR, the new vector components are selected from the given range of upper and lower boundaries of
) is chosen from the list of available positions, as in line 11. If the generated number lies in the probability of 1- HMCR, the new vector components are selected from the given range of upper and lower boundaries of  and
and  . This ensures the node remains within the coverage area while avoiding redundant placement. Moreover, if the random number is within the probability of PAR, the candidate node position will be adjusted, as per lines 11 to 14. For example, if
. This ensures the node remains within the coverage area while avoiding redundant placement. Moreover, if the random number is within the probability of PAR, the candidate node position will be adjusted, as per lines 11 to 14. For example, if  ,
,  , and
, and  , the updated
, the updated  becomes
becomes  , demonstrating how small variations refine the node position without drastic shifts. This update is accomplished using the following equation.
, demonstrating how small variations refine the node position without drastic shifts. This update is accomplished using the following equation.
 |
19 |
BW, representing bandwidth, is a parameter that controls the local search in HS. It is used to slightly adjust the new node position, improving the algorithm’s performance. The iterative nature of this adjustment ensures that each sensor gradually converges to an optimal position, contributing to minimal node deployment while maximizing coverage efficiency.
Step 4: Update the Harmony Vector Using Eq. 9, a newly generated vector quality is measured and analyze the results with the worst HM solution in the objective function. The worst harmony is excluded if the result is better and new vectors added HM, as per line 16. Solution vectors stored in HM can improve the HS algorithm iteratively.
Step 5: Check the Stopping Criterion The solution vector with the highest target work value is selected as the best solution vector, representing the optimal number and placement of sensor hubs. The algorithm halts when either the coverage ratio meets or exceeds the threshold (typically 90%) or further iterations no longer yield improvements in coverage or node efficiency. This ensures that sensor deployment is both cost-effective and energy-efficient. By terminating at this point, the algorithm prevents unnecessary computations, conserving resources while guaranteeing adequate coverage. This algorithm is summarized in the pseudocode in algorithm 1.
Building connected dominating set
Each node in the network constructs its own CDS, which is a set of nodes that connects the individual node to the entire network, excluding the node itself. The CDS consists of distinct nodes and plays a crucial role in network connectivity. For instance, if we consider node 1, its CDS would be { 3, 4, 5, 9} as depicted in Fig. 3. In our approach, the first CDS generated in this step is utilized for the selection of the first CH. Subsequently, this step is integrated with the baseline LEACH protocol after completing 10% of the average total rounds. CDS is discussed in detail in62. It enables efficient clustering and management of the network to enhance energy efficiency and extend the network’s lifetime.
Fig. 3.

CDS for Node 1.
4-factor (4F) based CH selection
In the selection of CH for WSNs, a hierarchical approach consisting of four levels is proposed. This approach takes into consideration various constraints, including the remaining energy of the node, the total number of neighbors directly connected to the node, the distance between the node and the BS, and the radio conditions, specifically the SNR. These factors play a crucial role in ensuring efficient network operation and energy conservation. To determine whether a specific node qualifies as a CH, Eq. (20) is employed, which assigns weights to each factor based on the specific requirements of the application. By incorporating these constraints into the CH selection process, the proposed approach aims to enhance the overall performance and effectiveness of WSNs.
 |
20 |
Algorithm 2.
Proposed 4F-CH selection
where NV represents normalization vector.  is the instantaneous residual energy of the node at a specific round r,
is the instantaneous residual energy of the node at a specific round r,  represents the total remaining amount of energy of all the nodes in the network.
represents the total remaining amount of energy of all the nodes in the network.  represent the number of neighbors of the current node. The distance of the current node with the BS is represented by
represent the number of neighbors of the current node. The distance of the current node with the BS is represented by  whereas the average distance of all the nodes with the BS is represented by
whereas the average distance of all the nodes with the BS is represented by  .
.  is the signal to noise ratio of the current node whereas
is the signal to noise ratio of the current node whereas  is the average SNR of all nodes. Similarly,
is the average SNR of all nodes. Similarly,  and
and  are the normalization parameters and are adjusted to satisfy the below Eq. (21).
are the normalization parameters and are adjusted to satisfy the below Eq. (21).
 |
21 |
All the other default settings are the same as described in61 except for the CH selection. Lines 1 to 8 of algorithm 2 describes the ground assumptions taken for the proposed 4F-CH selection. Lines 10 to 15 iterative loop selects the CH based on Eq. (22), where the NV and CH selection criteria are combined together. The name ViTAL incorporates the fact that the nodes are deployed using Phase 1. The algorithm exits once the maximum number of deep nodes are exceeded than a provided threshold. The flow of the 4F-CH selection is also illustrated in Fig. 4.
 |
22 |
Fig. 4.

4F-CH selection flowchart.
Experiments and results
To evaluate the performance of ViTAL, it is implemented using MATLAB 2019a on a virtual machine VMware running with a graphical tool for MATLAB. The simulation is conducted on an Intel Core i5 processor operating at 2.25 GHz. The technique is validated using various numbers of nodes and traffic scenarios, carefully selecting simulation parameters to align with the analytical model outlined in section “ViTAL”. Initially, a random topology with N nodes is employed, assuming all sensor nodes operate in the 2.4 GHz frequency band, with a maximum bit rate of 250 kbps. During the initial simulation setup, the selection of CHs is performed. The transmission range for all nodes is set to 15 meters, while the  is assumed to be 5 meters. The network is designed such that all nodes have knowledge of each other’s existence through the CDS approach and have sufficient energy reserves. Default parameters specified in Table 3 are used, and the remaining parameters are derived from22. To capture real-world scenarios, the number of nodes is varied in the experiments, ranging from 100 to 500 nodes. The simulation area is set to 100m
is assumed to be 5 meters. The network is designed such that all nodes have knowledge of each other’s existence through the CDS approach and have sufficient energy reserves. Default parameters specified in Table 3 are used, and the remaining parameters are derived from22. To capture real-world scenarios, the number of nodes is varied in the experiments, ranging from 100 to 500 nodes. The simulation area is set to 100m  100m, and each simulation run lasts for 1000 seconds. A log-normal shadowing model is used for signal propagation and an IEEE 802.15.4 MAC layer is implemented. The initial energy of each node is set to 0.5 J, and the energy consumption model considers both transmission and reception costs. The detailed Simulation parameters and their initial values are provided in Table 3.
100m, and each simulation run lasts for 1000 seconds. A log-normal shadowing model is used for signal propagation and an IEEE 802.15.4 MAC layer is implemented. The initial energy of each node is set to 0.5 J, and the energy consumption model considers both transmission and reception costs. The detailed Simulation parameters and their initial values are provided in Table 3.
Table 3.
Simulation parameters and their initial values.
| Parameter | Value |
|---|---|
| Coverage area | 100  100 100 
|
| Density of sensor node | 100-500 nodes |
| Sink location | (5,5) |
| Energy receive in free space | 10 pJ/bit |
| Energy receive in multipath | 0.0013 pJ/bit |
| Size of the data packets | 800 bits |
| Energy per sensor node | 0.5 J |
| Transmission range | 15 m |
Two distinct scenarios are considered for evaluation of the proposed approach: static and mobile. In the former, the sensor nodes and the sink remain fixed throughout the simulation. This configuration emulates scenarios where the deployment of sensor nodes and the location of the sink are predetermined and do not change over time. This scenario allows to evaluate the performance of the network under stable conditions, where the connectivity and communication patterns remain consistent. In the mobile scenario, the sink exhibits random waypoint mobility. This allows the sink to move randomly within the network area. This simulates dynamic environments where the sink is mounted on a mobile entity with the velocity ranging from 1 m/s to 10 m/s. By using this model, the effects of node mobility on different network metrics such as energy consumption, connectivity, and data transmission efficiency can be evaluated. For each scenario, 30 independent simulation runs are conducted to ensure statistical significance. Key performance metrics including network lifetime, packet delivery ratio, end-to-end delay, and energy consumption are measured. The static scenario uses a grid-based node deployment, while the mobile scenario employs a uniform random distribution of nodes. In the mobile scenario, a pause time of 10 seconds between movements is implemented to simulate realistic mobility patterns. By examining both scenarios, the behavior and performance of the network under different operational conditions can be analyzed, facilitating a comprehensive evaluation of the proposed approach. The simulation results are averaged across all runs, and 95% confidence intervals are calculated to ensure the reliability of the findings.
In the evaluation process, several metrics are employed to assess the performance of the system. Firstly, the first node dead metric is considered, which measures the time it takes for the first node in the network to become non-functional. This metric helps to understand the robustness and longevity of the system. Secondly, the number of rounds for all nodes to be dead is examined, which determines the duration until all nodes in the network cease to operate. This metric provides insights into the overall system reliability and potential failure scenarios. Additionally, the packets transmitted to the BS are analyzed, which quantifies the rate of successful packet transmission within the network from nodes to BS, allowing for the evaluation of its efficiency and capacity. Lastly, the average residual energy is assessed, which calculates the remaining energy levels across all nodes, providing valuable information about energy consumption and resource management. These metrics collectively enable a comprehensive evaluation of the performance and effectiveness of the system. The sensor node deployment in both random and HSA-based configurations is depicted in Fig. 5. Notably, the adoption of the HSA significantly reduces the number of sensors required for adequate area coverage.
Fig. 5.
Comparison of node deployments (a) Random deployments of nodes (b) HSA deployment with a minimized number of nodes.
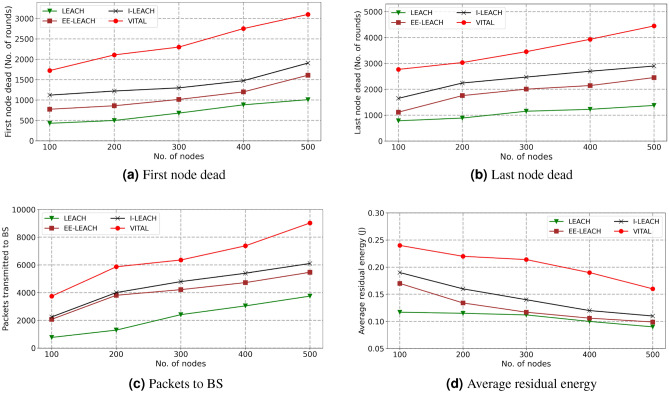
To ensure a fair comparison between different configurations, the performance of ViTAL is evaluated alongside LEACH, I-LEACH, and EE-LEACH on optimally deployed nodes. These approaches are selected because they serve as well-established benchmarks in the field of WSNs. Moreover, the existence of other latest protocols is also acknowledged, but it is crucial to understand that most of those approaches are also considering the similar benchmark for their evaluation. By conducting rigorous number of experiments, a fair and controlled comparison , enabling the demonstration of the advantages offered by ViTAL in terms of energy efficiency, network lifetime, and other relevant metrics. The results for the static scenario are presented in Fig. 6, while Fig. 7 illustrates various performance metrics for the mobile scenario.
Fig. 6.
Performance under static nodes with random and optimal deployment.
Fig. 7.
Performance under mobile sink with optimal deployment.
In the static scenario, ViTAL showcases superior performance compared to previous techniques, particularly in terms of network lifetime. It demonstrates substantial increases in the number of rounds before the first node’s demise and overall network lifespan. To gain a deeper understanding, ViTAL is compared with several existing schemes, including LEACH, I-LEACH, and EE-LEACH. Additionally, random deployment and deployment through HSA are examined. When nodes are randomly deployed, using only the proposed 4F-LEACH, an average increase of 77.5%, 48%, and 54% in the number of rounds before the first node ceases functioning , as compared to LEACH, EE-LEACH, and I-LEACH, respectively. The notable performance gap reflects the enhanced efficiency of ViTAL’s deployment optimization through HSA, which minimizes node overlap and reduces energy dissipation during initial rounds. This strategic node placement contrasts with the less efficient random deployment seen in conventional approaches, where clustering is suboptimal.
However, once ViTAL is deployed, the performance further improve to 80.9%, 62%, and 58% compared to the case of randomly deployed nodes. This additional improvement can be attributed to the combination of optimized deployment and robust routing using the CDS, which reduces redundant transmissions and enhances communication reliability. Moreover, when considering the number of rounds before the last node stops operating, ViTAL demonstrates increases of 75%, 69%, and 62% compared to randomly deployed nodes using conventional LEACH, EE-LEACH, and I-LEACH, respectively. The overall throughput, measured in terms of packets transmitted to the BS, experiences average increases of 83%, 59%, and 52% compared to the three mentioned approaches with random deployment. Additionally, ViTAL significantly enhances the average residual energy across nodes, with improvements of 68%, 58%, and 41%, respectively. These results highlight the network’s enhanced energy efficiency, resulting in improved reliability throughout the entire system.
In the mobile scenario, ViTAL demonstrates remarkable improvements in network performance. As shown in Fig. 7, compared to LEACH, EE-LEACH, and I-LEACH, ViTAL extends the lifespan of the first node by 68.27%, 49%, and 42%, respectively. Additionally, the number of rounds before the last node became inactive also increases by 74%, 52%, and 36%. This is largely attributed to the adaptability of ViTAL’s routing process, which dynamically adjusts to node mobility, mitigating disconnections that often disrupt conventional schemes. Moreover, ViTAL has achieved significant enhancements in average residual energy, with improvements of 54.5%, 49.95%, and 41.36%, respectively. The CDS mechanism ensures that even as nodes move, minimal energy is expended in rerouting, preserving overall network longevity. The throughput, measured by the number of packets transmitted to the BS, also experiences notable improvements of 57%, 50.04%, and 37%. ViTAL’s ability to maintain stable communication in mobile environments ensures data delivery remains consistent, reducing packet drops that often plague less adaptive protocols. These findings emphasize the superior performance of ViTAL in optimizing energy efficiency and packet delivery in diverse mobile scenarios.
The substantial performance improvements observed in both static and mobile scenarios can be attributed to the synergistic operation of ViTAL’s three core components: deployment efficiency through HSA, routing optimization via CDS, and robust CH selection through the proposed 4F-LEACH. The iterative deployment process of HSA minimizes node redundancy, ensuring optimal sensor placement that maximizes coverage while reducing unnecessary node activation. Routing efficiency is enhanced by the CDS mechanism, which reduces energy consumption by limiting multi-hop transmissions to essential nodes, effectively extending the lifespan of non-cluster head nodes. Additionally, the 4F CH selection prioritizes nodes with higher residual energy, better positioning, and stronger communication links, preventing premature CH depletion and promoting load balancing. These integrated strategies directly contribute to the observed increases in network lifetime, throughput, and residual energy, reinforcing ViTAL’s capability to outperform traditional approaches across varying scenarios.
To further examine the adaptability of ViTAL, an additional simulation scenario is introduced, focusing and mimicking an IoT-based in-home health monitoring system. The simulation models a healthcare monitoring setup where various sensors, including temperature and humidity sensors, light sensors, pulse sensors, fire and smoke detectors, and gyroscopes, generate and transmit simulated readings to a base station (BS). The data is then relayed over a virtual network for further analysis. Sensor placement within the simulated home environment is optimized to maintain a nearly constant SNR, disregarding minor variations. The simulation enforces an average distance of 3 meters between devices, with data transmission occurring at 5-minute intervals. The impact of sensor positioning is evaluated, demonstrating how the proposed model optimally deploys sensors within the simulation environment. The remote interface, represented as a mobile application, is illustrated in Fig. 8.
Fig. 8.

Readings received on Android-based remote user.
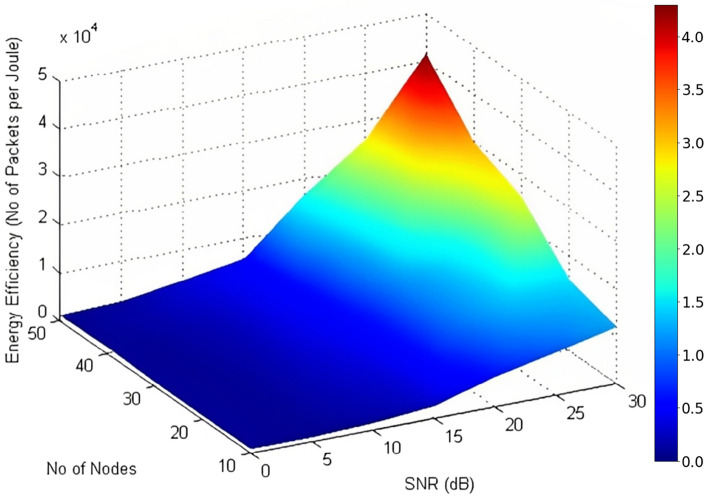
Results from this simulation indicate that the proposed model enhances network longevity and increases packet transmission efficiency. Figure 9 visually represents the effects of node density and radio conditions on energy efficiency, showing that poor radio conditions contribute to energy loss due to retransmissions and reduced packet delivery rates, whereas higher SNR conditions improve efficiency. Continuous data analysis is conducted using MATLAB, focusing on sensor accuracy, network efficiency, and system adaptability within the simulated environment. The findings validate the proposed model’s ability to improve network performance and ensure continuous monitoring capabilities. These initial simulation results provide insights into the system’s potential for future real-world applications.
Fig. 9.
Energy efficiency vs SNR vs No. of nodes.
Conclusion and future works
This study highlights the crucial role of the deployment of nodes, network topology, node energy, and radio conditions in the energy efficiency and lifetime of sensor networks. Recognizing the significance of these factors, we have developed an integrated approach called ViTAL, which comprehensively addresses these challenges to ensure the maximum lifetime of a WSN. In this work, initially, the nodes are deployed in a way such that the number of nodes to cover an ROI is reduced to maintain a certain coverage ratio. In the next phase, each node develops its CDS which is then used in the last phase of 4F CH selection. All four parameters are considered during the process of selection procedure. ViTAL is evaluated against existing solutions under various conditions. Results demonstrate that ViTAL outperforms previous schemes by considering multiple factors simultaneously, leading to significant improvements in network lifetime and energy efficiency. In the static scenario, ViTAL achieves remarkable outcomes, increasing the overall network lifetime by an average of 75%. Moreover, it extends the lifespan of the first node by 80.9%, increases the average residual energy by 68%, and increases the number of packets transmitted to the BS by 83%. In the scenario with mobility, ViTAL continues to exhibit outstanding performance. It enhances the network lifetime by 74% and extends the first node’s lifespan by 74%. Additionally, ViTAL improves the average residual energy by 54.5% and increases the packets transmitted to the BS by 57%. The success of ViTAL can be attributed to its deployment strategy, providing nodes with comprehensive topological information. It also effectively utilizes four parameters to select CHs from the CDS which significantly contributes to its overall performance.
In the future, we aim to explore the potential of dynamic weight assignment for further analysis in the normalization vector, particularly for mobile applications like outdoor IoT. We also are in the process of integrating deep learning for node placement based on environmental conditions and application requirements. This work will be further used for improving energy harvesting and scheduling in future networks. By continuously refining and enhancing such comprehensive approaches, we can continue to optimize energy efficiency and improve the lifetime of WSNs, enabling their effective deployment in a wide range of real-world scenarios.
Author contributions
Conceptualization and implementation: Sardar Jaffar Ali; validation and supervision: Javed Iqbal; writing-original draft preparation: Sardar Jaffar Ali; writing- formatting and visualizations: Javed Iqbal; writing- review and editing: Faheem Khan and Yeon-Kug Moon. All authors have read and approved the final manuscript.
Funding
This work was supported by the Technology Innovation Program(RS-2024-00487049, Development and demonstration of complex emotion recognition on-device AI technology for in-vehicle driver emotional services ) funded By the Ministry of Trade Industry & Energy(MOTIE, Korea, Contribution Rate: 100%)
Data availability
The datasets used and /or analyzed during the current study are available from the corresponding author on reasonable request.
Declarations
Competing interest
The authors declare no competing interests.
Ethical approval
This research involved entirely computational simulations, with no human or animal subjects used in the experiments. As such, no ethical review board approval was required.
Footnotes
The original online version of this Article was revised: The original version of this Article contained an error in the Introduction. Full information regarding the corrections made can be found in the correction for this Article.
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Change history
7/7/2025
A Correction to this paper has been published: 10.1038/s41598-025-08058-3
Contributor Information
Faheem Khan, Email: faheem@gachon.ac.kr.
Yeon-Kug Moon, Email: ykmoon@sejong.ac.kr.
References
- 1.Luxton, R. Challenges and future aspects of sensor technology 853–877 (Elsevier, Amsterdam, 2023). [Google Scholar]
- 2.Fortune Business Insights. Wireless sensor network market size, share & covid-19 impact analysis (2023).
- 3.Kumar, N., Rani, P., Kumar, V., Athawale, S. V. & Koundal, D. Thwsn: Enhanced energy-efficient clustering approach for three-tier heterogeneous wireless sensor networks. IEEE Sens. J.22, 20053–20062 (2022). [Google Scholar]
- 4.Khan, F. et al. An efficient and reliable algorithm for wireless sensor network. Sensors21(24), 8355 (2021). [DOI] [PMC free article] [PubMed]
- 5.Rashid, A. et al. Improving energy conservation in wireless sensor networks using energy harvesting system. Int. J. Adv. Comput. Sci. Appl.9(1), 354–361 (2018).
- 6.Seguin, C., Van Den Heuvel, M. P. & Zalesky, A. Navigation of brain networks. Proc. Natl. Acad. Sci.115, 6297–6302 (2018). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 7.Ullah, F. et al. Traffic priority based delay-aware and energy efficient path allocation routing protocol for wireless body area network. J. Ambient. Intell. Humaniz. Comput.10, 3775–3794 (2019). [Google Scholar]
- 8.Vázquez-Castillo, J. et al. Energy-saving techniques for urban noise wsn with kalman-based state estimation and green facade energy harvester. IEEE Trans. Instrum. Meas.71, 1–10 (2022). [Google Scholar]
- 9.Ahmed, Z., Rehan, M. M., Chughtai, O. & Rehan, M. W. Ad-rdc: A novel adaptive dynamic radio duty cycle mechanism for low-power iot devices. IEEE Internet Things J.9, 13376–13389 (2022). [Google Scholar]
- 10.Iqbal, J., Giaccone, P. & Rossi, C. Local cooperative caching policies in multi-hop d2d networks. In 2014 IEEE 10th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), 245–250 (2014).
- 11.Abdulzahra, A. M. K., Al-Qurabat, A. K. M. & Abdulzahra, S. A. Optimizing energy consumption in WSN-based IOT using unequal clustering and sleep scheduling methods. Intern. Things22, 100765 (2023). [Google Scholar]
- 12.Gupta, P., Tripathi, S., Singh, S. & Gupta, V. Mppt-epo optimized solar energy harvesting for maximizing the wsn lifetime. Peer-to-Peer Network. Appl.16, 347–357 (2023). [Google Scholar]
- 13.Oukas, N., Boulif, M., Hadiouche, H. & Bengharabi, C. A new petri nets for wsns to model the behaviour of solar-energy harvesting sensors with double sleeping strategy. In 2022 2nd International Conference on Computing and Information Technology (ICCIT), 237–242 (IEEE, 2022).
- 14.Gujral, S. & Sarma, S. Wireless powered backscatter-aided cooperative communication scheme for iot. Wireless Netw.28, 1771–1784 (2022). [Google Scholar]
- 15.Abadi, A. F. E. et al. Rlbeep: Reinforcement-learning-based energy efficient control and routing protocol for wireless sensor networks. IEEE Access10, 44123–44135 (2022). [Google Scholar]
- 16.Rao, K. R., Rahman, M. Z. U., Satamraju, K. P. & Reddy, B. N. K. Genetic algorithm for cross-layer-based energy hole minimization in wireless sensor networks. IEEE Sens. Lett.6, 1–4 (2022). [Google Scholar]
- 17.Cao, B. et al. Deployment optimization for 3d industrial wireless sensor networks based on particle swarm optimizers with distributed parallelism. J. Netw. Comput. Appl.103, 225–238 (2018). [Google Scholar]
- 18.Jaradat, Y., Masoud, M. & Jannoud, I. A mathematical framework of optimal number of clusters in 3d noise-prone wsn environment. IEEE Sens. J.19, 2378–2388 (2018). [Google Scholar]
- 19.Jain, N., Bohara, V. A. & Gupta, A. ideg: Integrated data and energy gathering framework for practical wireless sensor networks using compressive sensing. IEEE Sens. J.19, 1040–1051 (2018). [Google Scholar]
- 20.Kar, K. & Banerjee, S. Node placement for connected coverage in sensor networks. In WiOpt’03: Modeling and Optimization in Mobile, Ad Hoc and Wireless Networks, 2 (2003).
- 21.Zorlu, O. & Sahingoz, O. K. Increasing the coverage of homogeneous wireless sensor network by genetic algorithm based deployment. In 2016 Sixth International Conference on Digital Information and Communication Technology and its Applications (DICTAP), 109–114 (IEEE, 2016).
- 22.Moh’d Alia, O. & Al-Ajouri, A. Maximizing wireless sensor network coverage with minimum cost using harmony search algorithm. IEEE Sens. J.17, 882–896 (2016).
- 23.Zhang, L. et al. Differential evolution based regional coverage-enhancing algorithm for directional 3d wireless sensor networks. IEEE Access7, 93690–93700 (2019). [Google Scholar]
-
24.Li, F., Luo, J., Wang, W. & He, Y. Autonomous deployment for load balancing
 -surface coverage in sensor networks. IEEE Trans. Wireless Commun.14, 279–293 (2014). [Google Scholar]
-surface coverage in sensor networks. IEEE Trans. Wireless Commun.14, 279–293 (2014). [Google Scholar] - 25.Wang, K., Wu, Q., Peng, Y., Hu, C. & Chen, N. A collaborative planning method of space-ground sensor network coverage optimization for multiparameter observation tasks. IEEE Sens. J.21, 8384–8399 (2020). [Google Scholar]
- 26.Heinzelman, W. R., Chandrakasan, A. & Balakrishnan, H. Energy-efficient communication protocol for wireless microsensor networks. In Proceedings of the 33rd annual Hawaii international conference on system sciences, 10 (IEEE, 2000).
- 27.Daanoune, I., Abdennaceur, B. & Ballouk, A. A comprehensive survey on leach-based clustering routing protocols in wireless sensor networks. Ad Hoc Netw.114, 102409 (2021). [Google Scholar]
- 28.Singh, S. K., Kumar, P. & Singh, J. P. A survey on successors of leach protocol. IEEE Access5, 4298–4328 (2017). [Google Scholar]
- 29.Antoo, A. & Mohammed, A. R. Eem-leach: Energy efficient multi-hop leach routing protocol for clustered wsns. In 2014 international conference on control, instrumentation, communication and computational technologies (ICCICCT), 812–818 (IEEE, 2014).
- 30.Bsoul, M., Al-Khasawneh, A., Abdallah, A. E., Abdallah, E. E. & Obeidat, I. An energy-efficient threshold-based clustering protocol for wireless sensor networks. Wireless Pers. Commun.70, 99–112 (2013). [Google Scholar]
- 31.Beiranvand, Z., Patooghy, A. & Fazeli, M. I-leach: An efficient routing algorithm to improve performance & to reduce energy consumption in wireless sensor networks. In The 5th Conference on Information and Knowledge Technology, 13–18 (IEEE, 2013).
- 32.Arumugam, G. S. & Ponnuchamy, T. Ee-leach: development of energy-efficient leach protocol for data gathering in wsn. EURASIP J. Wirel. Commun. Netw.2015, 1–9 (2015). [Google Scholar]
- 33.Xiao, M., Zhang, X. & Dong, Y. An effective routing protocol for energy harvesting wireless sensor networks. In 2013 IEEE wireless communications and networking conference (WCNC), 2080–2084 (IEEE, 2013).
- 34.Zhang, H., Zhang, S. & Bu, W. A clustering routing protocol for energy balance of wireless sensor network based on simulated annealing and genetic algorithm. Int. J. Hybrid Inf. Technol.7, 71–82 (2014). [Google Scholar]
- 35.Liu, J.-L. & Ravishankar, C. V. Leach-ga: Genetic algorithm-based energy-efficient adaptive clustering protocol for wireless sensor networks. Int. J. Mach. Learn. Comput.1, 79 (2011). [Google Scholar]
- 36.Heinzelman, W. B., Chandrakasan, A. P. & Balakrishnan, H. An application-specific protocol architecture for wireless microsensor networks. IEEE Trans. Wireless Commun.1, 660–670 (2002). [Google Scholar]
- 37.Chen, J. & Shen, H. Meleach-l: More energy-efficient leach for large-scale wsns. In 2008 4th International Conference on Wireless Communications, Networking and Mobile Computing, 1–4 (IEEE, 2008).
- 38.Liu, Y., Gao, J., Jia, Y. & Zhu, L. A cluster maintenance algorithm based on leach-dchs protoclol. In 2008 International Conference on Networking, Architecture, and Storage, 165–166 (IEEE, 2008).
- 39.Tong, M. & Tang, M. Leach-b: an improved leach protocol for wireless sensor network. In 2010 6th international conference on wireless communications networking and mobile computing (WiCOM), 1–4 (IEEE, 2010).
- 40.Wang, A., Yang, D. & Sun, D. A clustering algorithm based on energy information and cluster heads expectation for wireless sensor networks. Comput. Electr. Eng.38, 662–671 (2012). [Google Scholar]
- 41.Gnanambigai, J., Rengarajan, N. & Anbukkarasi, K. Q-leach: An energy efficient cluster based routing protocol for wireless sensor networks. In 2013 7th international conference on intelligent systems and control (ISCO), 359–362 (IEEE, 2013).
- 42.Batra, P. K. & Kant, K. Leach-mac: a new cluster head selection algorithm for wireless sensor networks. Wireless Netw.22, 49–60 (2016). [Google Scholar]
- 43.Tang, C. et al. An energy harvesting aware routing algorithm for hierarchical clustering wireless sensor networks. KSII Trans. Internet Inf. Syst.10 (2016).
- 44.Jerbi, W., Guermazi, A. & Trabelsi, H. O-leach of routing protocol for wireless sensor networks. In 2016 13th international conference on computer graphics, imaging and visualization (CGiV), 399–404 (IEEE, 2016).
- 45.Alnawafa, E. & Marghescu, I. Imht: Improved mht-leach protocol for wireless sensor networks. In 2017 8th international conference on information and communication systems (ICICS), 246–251 (IEEE, 2017).
- 46.Behera, T. M., Samal, U. C. & Mohapatra, S. K. Energy-efficient modified leach protocol for iot application. IET Wirel. Sens. Syst.8, 223–228 (2018). [Google Scholar]
- 47.Ouldzira, H., Lagraini, H., Mouhsen, A., Chhiba, M. & Tabyaoui, A. Mg-leach: an enhanced leach protocol for wireless sensor network. Int. J. Electr. Comput. Eng. (2088-8708)9 (2019).
- 48.Daanoune, I., Baghdad, A. & Balllouk, A. Bre-leach: A new approach to extend the lifetime of wireless sensor network. In 2019 Third International Conference on Intelligent Computing in Data Sciences (ICDS), 1–6 (IEEE, 2019).
- 49.Abu Salem, A. O. & Shudifat, N. Enhanced leach protocol for increasing a lifetime of wsns. Pers. Ubiquitous Comput.23, 901–907 (2019).
- 50.El Khediri, S., Khan, R. U., Nasri, N. & Kachouri, A. Mw-leach: Low energy adaptive clustering hierarchy approach for wsn. IET Wirel. Sens. Syst.10, 126–129 (2020). [Google Scholar]
- 51.Gantassi, R., Gouissem, B. B. & Othmen, J. B. Routing protocol leach-k using k-means algorithm in wireless sensor network. In Web, Artificial Intelligence and Network Applications: Proceedings of the Workshops of the 34th International Conference on Advanced Information Networking and Applications (WAINA-2020), 299–309 (Springer, 2020).
- 52.Thiagarajan, R. et al. Energy consumption and network connectivity based on novel-leach-pos protocol networks. Comput. Commun.149, 90–98 (2020). [Google Scholar]
- 53.Nigam, G. K. & Dabas, C. Eso-leach: Pso based energy efficient clustering in leach. J. King Saud Univ. Comput. Inf. Sci.33, 947–954 (2021). [Google Scholar]
- 54.Chithaluru, P. K., Khan, M. S., Kumar, M. & Stephan, T. Eth-leach: An energy enhanced threshold routing protocol for wsns. Int. J. Commun Syst34, e4881 (2021). [Google Scholar]
- 55.Sennan, S., Alotaibi, Y., Pandey, D., Alghamdi, S. et al. Eacr-leach: Energy-aware cluster-based routing protocol for wsn based iot. Comput. Mater. Continua72 (2022).
- 56.Mohammed, F. A., Mekky, N., Suleiman, H. H. & Hikal, N. A. Sectored leach (s-leach): An enhanced leach for wireless sensor network. IET Wirel. Sens. Syst.12, 56–66 (2022). [Google Scholar]
- 57.Pamungkas, K. N. P., Djanali, S., Anggoro, R., Burhan, P. et al. Dual cluster head selection based on leach and differential search algorithm to extend network lifetime in wireless sensor network. In 2022 Seventh International Conference on Informatics and Computing (ICIC), 1–7 (IEEE, 2022).
- 58.Manjeshwar, A. & Agrawal, D. P. Teen: Arouting protocol for enhanced efficiency in wireless sensor networks. In ipdps, vol. 1, 189 (2001).
- 59.Pothalaiah, S. & Rao, D. S. New hierarchical stable election protocol for wireless sensor networks. In 2015 International Conference on Innovations in Information, Embedded and Communication Systems (ICIIECS), 1–5 (IEEE, 2015).
- 60.Wang, J., Gao, Y., Yin, X., Li, F. & Kim, H.-J. An enhanced pegasis algorithm with mobile sink support for wireless sensor networks. Wirel. Commun. Mob. Comput.2018, 1–9 (2018). [Google Scholar]
- 61.Ala’a, A., Alsewari, A. A., Alamri, H. S. & Zamli, K. Z. Comprehensive review of the development of the harmony search algorithm and its applications. IEEE Access7, 14233–14245 (2019). [Google Scholar]
- 62.Ali, J. et al. Wireless sensor network design for smart grids and internet of things for ambient living using cross-layer techniques. Int. J. Distrib. Sens. Netw.15, 1550147719862208 (2019). [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
The datasets used and /or analyzed during the current study are available from the corresponding author on reasonable request.