Abstract
With global data expected to reach 175 zettabytes by 2025, traditional storage methods face unprecedented challenges, including security risks, limited durability, and high maintenance costs associated with centralized infrastructure. While DNA-based storage systems have demonstrated high density and chemical stability, most existing methods focus primarily on static storage, lacking effective strategies for secure and controllable information transmission. Coli Bond offers a revolutionary approach by combining the molecular precision of DNA storage with the controllable dynamics of synthetic biology, providing an innovative platform for data encryption and storage. In this system, controllable dynamics refer to information transfer regulated by caffeine concentration and temperature. The system leverages synthetic biology to engineer an auxotrophic Escherichia coli strain with a caffeine degradation pathway, enabling precise control of information transfer through conditional growth. A temperature-sensitive self-destruction mechanism ensures irreversible destruction of stored information under specific conditions, preventing unauthorized access and enhancing data security. Experimental validation demonstrated the system’s stability and reliability under various real-world conditions, including survival and function in commercial beverages, during transmission cycles, and under temperature variation. The results confirmed high transmission efficiency during initial contact and a rapid decline in strain viability after multiple transfers, providing an inherent layer of security. By integrating the high density of DNA storage with the dynamic control capabilities of synthetic biology, “Coli Bond” offers a secure and adaptable platform for the storage and transmission of DNA-encoded information, paving the way for future advancements in information storage and transmission technologies.
Introduction
With the rapid global growth of data, information storage and transmission technologies are facing unprecedented challenges. In the field of informatics, existing technologies such as Cloud Storage, Network-Attached Storage (NAS), and Storage Area Networks (SANs) have played significant roles in data management and sharing [1–3]. However, these technologies exhibit notable limitations in terms of security, durability, and sustainability [4,5]. For example, Cloud storage relies on stable network connections and the continuous maintenance of data centers, making it vulnerable to threats such as cyberattacks and data breaches [6,7]. While NAS and SAN have shown improvements in transmission efficiency, their limitations in scalability, cost-effectiveness, and system design restrict their applicability [8]. Furthermore, the risk of data breaches in distributed learning systems has raised widespread concern in recent years [9]. Research has demonstrated that private training data can be maliciously recovered through gradient-sharing mechanisms. In the field of supply chain management, although blockchain technology has enhanced the transparency of data sharing, the risk of information leakage persists [10]. In scenarios requiring strict data confidentiality, such as sensitive commercial information storage, these limitations are particularly pronounced, as traditional technologies struggle to provide robust security. [7,11].
In recent years, DNA-based storage and transmission technologies have rapidly emerged as a research focus in the field of informatics owing to their exceptional molecular properties and information-carrying capacity [12–14]. The high storage density of DNA enables the storage of vast amounts of information in extremely small volumes. Theoretically, one gram of DNA can store approximately 215 petabytes (PBs) of data, and its chemical stability ensures data integrity for decades, even under extreme conditions [15,16]. Moreover, compared with traditional storage media, DNA does not rely on electronic devices, which results in lower energy consumption and longer preservation periods, making it highly significant for long-term archiving and rare data storage [17–19]. In terms of encoding strategies, innovations in DNA storage technology continue to drive improvements in performance. Research has shown that by introducing degenerate bases and optimizing the encoding character set, the information capacity of DNA can be increased to 3.37 bits per character while simultaneously reducing both synthesis and reading costs [20]. Along with the optimization of encoding strategies, advancements in de novo DNA synthesis technology have not only increased storage efficiency but also significantly lowered cost barriers, opening new possibilities for large-scale applications [21].
Sensitive commercial data, such as intellectual property and financial records, depend heavily on cloud storage and encrypted databases. However, these methods remain vulnerable to cyberattacks, insider threats, and long-term degradation [22]. Additionally, advances in quantum computing pose a future risk to encryption security, whereas centralized data centers introduce concerns about physical damage and high maintenance costs [23]. DNA storage offers a durable, secure, and high-density alternative [24]. DNA retains chemical stability for thousands of years within biological environments and is inherently immune to hardware-related degradation. Unlike traditional digital storage, DNA enables biologically secure and decentralized data preservation, making unauthorized access significantly harder [14,25]. With these advantages, DNA storage provides a future-proof solution for businesses requiring long-term, highly secure data protection.
However, DNA storage and transmission technologies still face numerous challenges, including issues related to the reliability and environmental robustness of information transfer, the lack of dynamic system control capabilities, and the limited adaptability of existing technologies in complex scenarios [26]. First, the majority of current research focuses on the synthesis, storage, and reading capabilities of DNA, with relatively limited exploration into its potential for secure information transmission [27–30]. In practical applications, the information transfer process is susceptible to environmental factors, posing risks of data loss or leakage [15,17]. Moreover, even during storage, DNA molecules are prone to degradation through mechanisms such as strand breakage, particularly at room temperature, which may cause irreversible information loss. Moreover, there is currently a lack of effective methods to ensure the precision and confidentiality of information transmission. Existing approaches struggle to achieve high-precision dynamic control during the information storage and transmission process. This is particularly challenging in complex environments, where achieving reliable and controllable information transfer remains an unresolved technical problem. DNA storage technology has demonstrated unique advantages in long-term data archiving because of its high confidentiality and storage density. In previous studies [17–19], existing solutions lack real-time control over the storage and transmission processes. This limitation undermines its performance in terms of both security and efficiency, thereby restricting its widespread application in dynamic scenarios.
Current information storage and transmission systems face a range of limitations across digital and molecular platforms. Cloud-based and centralized systems such as NAS and SAN offer scalable data access but rely heavily on stable networks and data centers, making them prone to cyberattacks, high energy consumption, and limited sustainability. Distributed frameworks, including federated learning and blockchain storage, improve data transparency but still face privacy challenges such as gradient leakage and information reconstruction. DNA-based systems, while promising ultra-high storage density and long-term chemical stability, are mostly implemented in vitro and suffer from strand breakage, lack of dynamic access control, and poor environmental robustness. These limitations highlight the need for a new biological approach that combines secure data retention with externally controllable information transmission (Table 1).
Table 1. Comparison of mainstream information storage and transmission systems. This table summarizes the key characteristics, advantages, and limitations of three representative categories: centralized digital storage (Cloud/ NAS/ SAN), distributed data systems (e.g., federated learning and blockchain), and in vitro DNA-based storage.
| System Type | Cloud/ NAS/ SAN | Distributed Data Systems | In vitro DNA Storage |
|---|---|---|---|
| Technology & Features | Centralized storage with network access | Federated learning, blockchain, shared ledger storage | Synthetic oligos stored in solution or dried formats |
| Advantages | Fast access, scalable, widely adopted | Improved transparency and decentralization | Ultra-high density, chemical stability |
| Limitations | Vulnerable to cyberattacks, energy-intensive, high maintenance | Risk of gradient leakage, partial anonymity, lacks full privacy guarantees | No access control, environmentally fragile, prone to strand breakage |
To address these challenges, we developed Coli Bond, a system that integrates DNA storage with synthetic biology to achieve externally regulated access and reliable information transmission. By embedding data in metabolically engineered E. coli, Coli Bond supports caffeine-dependent decoding and temperature-triggered self-destruction, enabling precise control over data flow and lifespan.
Its key features include:
Metabolism-dependent controlled transfer: Enables real-time, selective propagation via caffeine-dependent growth [31,32].
Temperature-triggered self-destruction: Irreversibly destroys stored information upon thermal activation [33].
Dual-layer security: Combines metabolic and temperature control to safeguard access.
Environmental robustness: Maintains function across real-world conditions such as beverage exposure and sequential transfers.
Programmable storage lifespan: Leverages the long-term stability of living cells while enabling controlled erasure when needed.
Combining DNA’s storage potential with dynamic biological control, Coli Bond provides a secure, adaptable platform for next-generation data transmission, with promising applications in complex and decentralized environments (Fig 1).
Fig 1. Conceptual diagram of the Coli Bond system.
This diagram illustrates the process of data encryption, storage, transmission, and decryption using the Coli Bond system. Data are first encoded into DNA, utilizing existing or future DNA-based storage methods. The Coli Bond system then encrypts and stores this information, enabling controlled transmission through a caffeine-dependent mechanism and a temperature-sensitive self-destruction feature. Finally, the stored DNA reaches the recipient, where it is decrypted to recover the original data, completing the secure transfer process.
Materials and methods
Chemical reagents and medium preparation
In this study, 7-MX (purity 97%) was purchased from Aladdin Biotech Co., Ltd. (Shanghai, China), and xanthine (purity 99%) was purchased from McLean Biochemical Technology Co., Ltd. (Shanghai, China). Caffeine was sourced from guarana extract (containing approximately 22% caffeine). The standard curve for caffeine was constructed using an indirect method involving 7-MX and theobromine. All other chemical reagents used in the experiments were routine molecular biology reagents of analytical grade and were purchased from reputable suppliers.
Strain construction
The bacterial strains used in this study included Escherichia coli (E. coli) DH5α and BW25113, purchased from Weidi Biotechnology Co., Ltd. (Shanghai, China). The gene knockout strain BW-ΔguaB was constructed by using the RED recombination method [34–36] to knock out the guaB gene and replace it with a kanamycin resistance gene. (S1 Fig) The competent cells were prepared in the laboratory, while the other strains were purchased from Weidi Biotechnology Co., Ltd. (Shanghai, China).
Plasmid construction and optimization
The plasmid construction in this study combined the Gibson assembly method and Golden Gate ligation method. The Gibson assembly method was used for seamless connection of larger fragments, ensuring efficient and seamless ligation, whereas the Golden Gate method utilized BsaI restriction enzyme digestion and T4 DNA ligase for directional insertion of fragments, which is particularly useful for multifragment constructions. After construction, the plasmids were transformed into competent E. coli DH5α cells, which were subsequently plated on LB agar plates containing 50 mg/L antibiotics. The plates were incubated at 37 °C for 12 hours.
Subsequently, positive clones were selected by colony PCR, and the plasmids were extracted and verified by sequencing. The successfully verified plasmid was then transformed into E. coli BW25113, resulting in the final engineered strains required for this study.
Protein expression and screening
Protein expression in engineered strains was performed using the standardized ZYM5052 media. The expression was induced in medium containing arabinose (0.2%) and isopropyl-β-D-thiogalactopyranoside (IPTG). The cultures were incubated at 37 °C with shaking at 200 rpm for 12–16 hours. Protein expression levels were verified by SDS‒PAGE, and functional screening was conducted on the expressed products.
Construction of the coli bond system
The Coli Bond system was constructed by modularly engineering Escherichia coli BW25113 to incorporate caffeine-dependent growth control and a conditional self-destruction mechanism. To establish an auxotrophic background, the guaB gene was knocked out via λ-Red recombination and replaced with a kanamycin resistance cassette, yielding strain BW-ΔguaB (S1 Fig). Growth assays in M9 minimal medium verified the strain’s dependence on exogenous purines, as it exhibited no growth without xanthine supplementation (S2 Fig).
To convert this dependency from xanthine to caffeine, a caffeine demethylation pathway derived from Pseudomonas putida CBB5 was introduced. Genes encoding the N-demethylases (ndmA, ndmB, ndmC) and associated redox partners (ndmD) were assembled into a plasmid using Gibson and Golden Gate cloning strategies and placed under constitutive or inducible promoters. The functionality of the Decaf pathway was confirmed by the restored growth of BW-ΔguaB in M9 medium supplemented with caffeine as the sole purine source (S3 Fig).
For the self-destruction module, the dpnI restriction endonuclease gene was cloned under the control of an inducible promoter. Upon activation, DpnI expression led to methylated DNA degradation, resulting in irreversible loss of genomic integrity and cell death.
All plasmids were constructed and verified in E. coli DH5α via colony PCR and Sanger sequencing, then transformed into BW-ΔguaB. Engineered strains were cultured in ZYM5052 auto-induction medium supplemented with 0.2% arabinose and 0.1 mM IPTG at 37 °C with shaking at 200 rpm. Target protein expression was confirmed by SDS–PAGE, and functional validation was conducted through caffeine-responsiveness assays and temperature-induced viability tests.
Results
Construction of auxotrophic E. coli and the decaf pathway
In this study, we constructed an auxotrophic E. coli strain and introduced a caffeine degradation pathway (Decaf pathway) [37,38] to develop a conditional growth system that enhances the security and practicality of information transmission.
By knocking out the guaB gene, we successfully created the auxotrophic strain BW-ΔguaB, which depends on exogenous xanthine or its derivatives for growth. The guaB gene encodes a key enzyme in the de novo guanine biosynthesis pathway, and its deletion disrupts the production of xanthine-5’-phosphate, a crucial intermediate [39] (Fig 2A). As a result, the BW-ΔguaB strain is unable to grow under conditions lacking xanthine (S2 Fig). However, the growth of BW-ΔguaB could be restored by supplementing the medium with 0.5 mM xanthine, confirming its dependency on exogenous xanthine and validating the successful construction of the auxotrophic host (Fig 2B).
Fig 2. Construction and validation of the Decaf pathway and auxotrophic E. coli system.
(A) Schematic of the purine biosynthesis pathway and the integration of the Decaf pathway. The auxotrophic strain BW-ΔguaB/Decaf was engineered to metabolize caffeine into xanthine by deleting the guaB gene and introducing the Decaf pathway. (B-C) Growth curves demonstrating system functionality: growth restoration of BW-ΔguaB in LB medium supplemented with xanthine (B) and caffeine utilization by BW-ΔguaB/Decaf in LB medium (C). (D) Verification of caffeine conversion to xanthine via the Decaf pathway. The figure shows three HPLC chromatograms, with the signals from top to bottom corresponding to xanthine, caffeine, and the results following Decaf pathway treatment (DeCaf), respectively. These results demonstrate that the Decaf pathway effectively converts caffeine into xanthine. (E) Growth of BW-ΔguaB/Decaf in commercially available caffeine-containing beverages, illustrating its potential for real-world applications.
In the context of information decoding, caffeine is more readily available and cost-effective than xanthine. Thus, the use of caffeine enhances the security and practicality of the system. To enable the strain to utilize caffeine as a precursor for xanthine, we integrated the key caffeine degradation genes from Pseudomonas putida CBB5 into the BW-ΔguaB strain, constructing the engineered strain BW-ΔguaB/Decaf, thereby allowing the strain to rely on caffeine rather than exogenous xanthine (Fig 2A and S3 Fig). Next, to verify whether the Decaf pathway could successfully convert caffeine to xanthine, we performed HPLC analysis. The HPLC chromatograms show signals corresponding to xanthine, caffeine, and Decaf pathway-treated samples (DeCaf) from top to bottom. These results indicate that the Decaf pathway effectively converts caffeine into xanthine (Fig 2D). Functional analysis further confirmed that the engineered strain BW-ΔguaB/Decaf could grow normally in caffeine-containing media, demonstrating that the Decaf pathway successfully enabled the strain to metabolize caffeine into xanthine, thereby supporting guanine synthesis (Fig 2C).
Further experiments verified that BW-ΔguaB/Decaf could grow stably in various commercially available caffeinated beverages, such as energy drinks, coffee, and preworkout mixtures (Fig 2E) [40].
Self-destruction mechanism verification
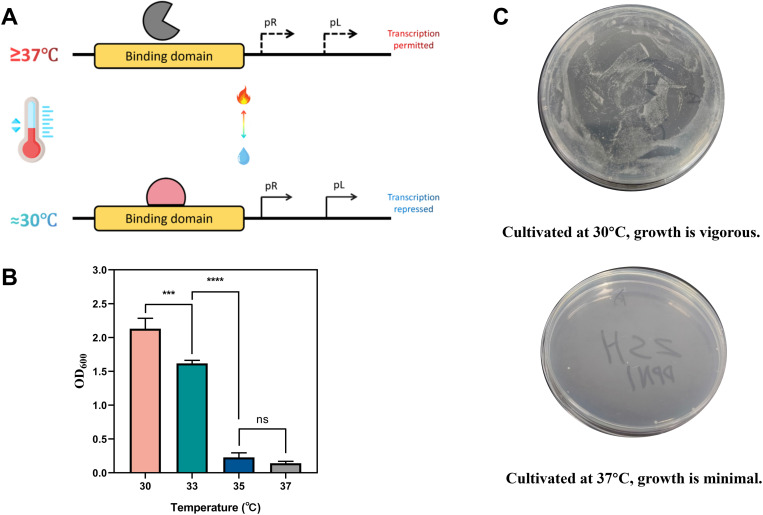
To ensure the security of encoded information and prevent unauthorized access, we designed a temperature-controlled self-destruction system. This system triggers the degradation of genomic DNA carrying information and induces cell death, thereby resulting in irreversible data destruction. The core of the system is the temperature-sensitive Y38 promoter, which regulates the expression of the DpnI gene. DpnI encodes a DNA endonuclease that specifically cleaves GATC sequences, which are abundant in the E. coli genome. At the commonly used cultivation temperature of 37 °C, the Y38 promoter is activated, inducing DpnI expression, which leads to genome fragmentation and self-destruction of the cell. We exploited this temperature, which is typically considered optimal for bacterial growth, to enable the encrypted strain to destroy the information under standard conditions, thus realizing a unique strategy for confidentiality and destruction.
During the construction process, we assembled the Y38 promoter (1488 bp), the DpnI gene (805 bp), and the TrrnB terminator into the PY38a plasmid via the Gibson assembly method, generating the composite part Y38-DpnI-TrrnB (BBa_K5480009). At low temperatures (30 °C), the lambda repressor (cI dimer) binds to and inhibits the promoter, preventing DpnI expression and maintaining genomic stability. Upon temperature elevation to 37 °C, the cI dimer dissociates, activating the promoter and driving DpnI expression, thus initiating the self-destruction process (Fig 3A).
Fig 3. Validation of the temperature-sensitive self-destruction mechanism.
(A) Schematic representation of the temperature-sensitive self-destruction system. At 30 °C, the repressor binds to the promoter region, preventing DpnI gene expression. At 37 °C, the repressor dissociates from the promoter, activating DpnI expression, leading to DNA degradation and cell death. (B) Growth analysis of the BW-ΔguaB/Decaf/Y38-DpnI-TrrnB strain at different temperatures. OD600 measurements indicate robust growth at 30 °C, which is slightly reduced at 33 °C (***p < 0.001). Growth is almost entirely inhibited at 35 °C (****p < 0.0001), with no significant difference (ns) between 35 °C and 37 °C, confirming effective self-destruction at higher temperatures. (C) Plate cultivation experiments confirming the temperature-sensitive effect. At 30 °C, the strain grows vigorously, whereas at 37 °C, growth is markedly reduced, further demonstrating the efficacy of the self-destruction mechanism.
The temperature sensitivity of this system was first validated in E. coli BW25113 cells. At 30 °C, the cells harboring the Y38-DpnI-TrrnB construct grew normally, whereas at 37 °C, growth was almost completely inhibited (Fig 3C). The OD600 values further validated the temperature-sensitive characteristics of the system. The results revealed that the strain exhibited robust growth at 30 °C, significantly reduced growth at 33 °C (***p < 0.001), and was nearly completely inhibited at 35 °C (****p < 0.0001), with no significant difference (ns) between 35 °C and 37 °C (Fig 3B). These results demonstrate that the self-destructive mechanism can be effectively triggered at the set temperature threshold, enabling the controllable destruction of engineered strains. Moreover, this design prevents strain leakage and misuse after information transmission is completed, further enhancing the security of data storage and transmission.
Transmission
After validating the conditional growth mechanism and the temperature-controlled self-destruction system, we further investigated the efficacy and limitations of the engineered strain in information transmission. To assess the practical application value of this system in information storage and transfer, we designed a “handshake” experiment to simulate the transmission process and evaluate the survival capacity of the strain after multiple contacts.
In the experiment, five glove-wearing volunteers participated sequentially. The first volunteer applied a bacterial suspension containing the BW-ΔguaB/Decaf/Y38-DpnI-TrrnB strain onto their hands, which was then transferred to the next volunteer’s hands, and so on. By measuring the colony count after each transmission, we observed a gradual decline in the strain’s survival rate. In the first and second transfers, the colony counts were relatively high, whereas in the third, fourth, and fifth transfers, the survival rate significantly decreased (Fig 4). This transmission decay phenomenon highlights the unique advantages of biological carriers in terms of information security—an entropy-driven security mechanism.
Fig 4. Viability assessment of information carriers during physical contact transmission.
The left panel shows plate cultivation results from sequential hand-to-hand transmissions, reflecting changes in strain viability. The right panel shows a marked decline in colony numbers after the third transmission, culminating in complete loss of viability. These findings confirm the system’s reliability in initial transmissions and enhanced security in preventing unauthorized multiple transfers.
These results indicate that although the engineered strain can effectively facilitate secure information transfer during initial contact, its survival capacity rapidly decreases after multiple transfers. This phenomenon highlights two key features of the dual-functional system: first, the strain’s high efficiency in the initial transmission ensures the reliability and security of information transfer; second, the rapid decline in survival during subsequent transfers provides a natural protective layer to the system, making unauthorized or repeated transmissions to restore the information difficult, thereby enhancing the system’s security and covert nature.
Discussion
Key features and implications
The “Coli Bond” system created in this study is an innovative approach that combines synthetic biology with data security. This provides an effective method for secure information storage and sharing using microorganisms. This design incorporates special growth conditions and a temperature-controlled self-destruction mechanism to construct a complex system for protecting stored information.
“Coli Bond” offers an additional solution to biosafety concerns by utilizing the DeCaf pathway, which allows bacterial growth only in the presence of caffeine or its derivatives. This approach not only enhances biosafety but also aligns with the international trend in bioengineering, which involves the design of environmentally dependent mechanisms to control the behavior of organisms. By replacing hypoxanthine with caffeine as a metabolic product, the system’s practicality can be further improved, as caffeine is widely found in everyday consumer products. This finding is consistent with previous research in microbial engineering, where caffeine was converted into valuable metabolites [41,42]. The core advantage of the system lies in its dual-composite mechanism: first, caffeine, a compound widely found in everyday consumer products, enables seamless integration of the decryption key into existing supply chains without the need for specialized chemical distribution channels [43,44]; second, the auxotrophic strain enhances resistance to unauthorized access by strictly controlling its metabolic pathways, limiting its growth to specific conditions, and significantly increasing the difficulty of brute-force cracking. Experimental validation further confirmed the strain’s stable growth in commercial beverages, demonstrating the system’s practical potential: the decryption process requires both specialized biological knowledge, such as the revival of the strain, and precise chemical control, including the regulation of caffeine concentration. This dual-authentication mechanism, by introducing “biochemical uncertainty,” surpasses traditional digital encryption systems in terms of security, providing a more robust safeguard for data storage and transmission.
The temperature-sensitive self-destruction system serves as a backup mechanism to protect sensitive data. Under regular E. coli cultivation conditions, the DpnI gene is activated, leading to the degradation of DNA containing the information, rendering it inaccessible or preventing unauthorized use. This concept is similar to the widely accepted gene kill switches, which play a significant role in enhancing the biosafety and controllability of synthetic microbial systems [45]. Moreover, this strategy effectively addresses biosafety concerns related to the deployment of genetically modified organisms (GMOs) in uncontrolled environments [46]. The design of the self-destruction mechanism offers unprecedented security for data storage and transmission, particularly when sensitive data are handled, effectively preventing data theft or tampering. As biological data storage technologies continue to evolve, ensuring absolute confidentiality and the complete destruction of data in the case of unauthorized access has become a critical issue [47]. Our temperature-controlled self-destruction system provides an innovative solution to this challenge and is applicable to future high-security storage fields, ensuring that once information is decrypted or accessed without authorization, it is immediately destroyed, thus preventing data leakage or misuse.
The experimental results show that while the engineered strain effectively facilitates information transfer upon initial contact, its survival capacity rapidly declines after multiple transfers, highlighting two key features of the dual-functional system: first, the strain’s high efficiency ensures the reliability and security of the initial transmission; second, the rapid decline in survival during subsequent transfers provides a natural protective barrier, preventing unauthorized or repeated transmissions from restoring information, further enhancing the system’s security and covert nature. This transmission decay phenomenon reveals the unique advantages of biological carriers in terms of information security—an entropy-driven security mechanism. The entropy-driven security mechanism is based on the randomness and irreversibility of biological systems, making unauthorized access more difficult to achieve. Each physical contact induces mechanical damage and nutrient depletion, creating a natural “biological one-time password (OTP)” system, turning biological limitations into security advantages [48]. In practical applications, unauthorized intermediaries need laboratory-level environmental control capabilities and real-time monitoring technologies to exceed the limits of three effective transfers, thus creating an insurmountable technical barrier.
Challenges and future directions
However, the system also has inherent limitations. The use of antibiotic resistance genes as selection markers may pose potential biosafety risks, including the horizontal transfer of resistance traits to native microbial populations [49]. How to ensure the isolation of genetically modified organisms in the natural environment and how to effectively avoid their potential harm to local ecosystems will be issues that cannot be ignored in future research [50–52]. The literature has proposed antibiotic-free metabolic complementation screening methods [53], which should be considered in future iterations of this system. For example, the use of caffeine toxicity as a screening tool for target strains could provide an effective alternative.
Although the “Coli Bond” system enhances data security through the “biological one-time password” mechanism, once the information is successfully destroyed, the recovery of the data becomes extremely difficult. This irrecoverability may present challenges for privacy protection in some scenarios. For example, in the case of misoperation or accidental damage, the data may never be restored, causing irrevocable losses to users. Therefore, how to provide a certain data recovery capability while ensuring data security to address unexpected situations is also one of the directions of future improvement [54].
DNA holds significant potential for information storage, and improvements in DNA synthesis and reading technologies have enabled the long-term, large-scale storage of information. Tools such as portable sequencers (e.g., nanopore technology) are continuously being developed to address real-world challenges in DNA synthesis and reading. These advancements are crucial to enhancing the practicality and scalability of DNA-based data storage systems [55–57].
To further improve the practicality and scalability of the “Coli Bond” system, interdisciplinary collaboration and technical integration play crucial roles. In addition to the basic research of synthetic biology, the research and development of data storage systems also needs to be closely coordinated with computer science, information technology, materials science and other fields [58,59]. For example, artificial intelligence can be used for data encryption and decoding, while nanotechnology may optimize the physical storage media. [60–62] Moreover, incorporating mathematical modeling and system-level simulation could enhance the quantitative understanding of signal-controlled growth and improve the fidelity of data transmission. These interdisciplinary approaches are expected to unlock more innovative applications and technological breakthroughs for the Coli Bond platform.
Conclusion
In this study, we aimed to develop a secure information storage and transmission platform by integrating synthetic biology with DNA-based technologies. To achieve this, we developed Coli Bond, a dual-function encryption system based on synthetic biology for secure information storage and transmission. This system integrates metabolism-dependent growth control and a temperature-sensitive self-destruction mechanism. By knocking out the guaB gene and introducing the Decaf (caffeine degradation) pathway, we engineered an E. coli strain that requires exogenous caffeine for growth, thereby enabling information decoding control. Additionally, a temperature-sensitive DpnI restriction enzyme system was designed to trigger irreversible DNA degradation at 37 °C, ensuring data security. The experimental results demonstrated that the system reliably preserves information integrity and ensures security during storage and transmission. The engineered strain showed high survival rates during initial transmission but experienced a rapid decline after multiple transfers, enhancing data security. Furthermore, the temperature-controlled self-destruction mechanism effectively triggered cell lysis, preventing unauthorized access. In addition, the Coli Bond system holds significant potential for applications in commercial confidential data storage and transmission, steganographic communication, personal privacy protection, and DNA-based information computing. Although the Coli Bond system demonstrates strong potential as a biological encryption strategy, several limitations remain. First, the current reliance on antibiotic resistance markers poses potential biosafety risks due to the possibility of horizontal gene transfer in environmental settings. Second, the methods for encoding information into bacteria and retrieving information from bacteria require further improvement. Future enhancements could include adopting antibiotic-free selection strategies, integrating CRISPR-based control systems such as CRISPR-Cas9 for targeted data insertion, CRISPRa/i for programmable regulation of information accessibility, and CRISPR-Cas3 for controlled sequence deletion, and incorporating nanopore sequencing technologies to enhance overall biosafety and operational efficiency [63–66].This study presents a novel approach to bioencryption and secure data transmission, with potential applications in confidential information storage, steganography, and DNA-based computation. In conclusion, Coli Bond not only advances the frontier of DNA-based storage but also opens new possibilities for secure communication in an era where data privacy is paramount.
Supporting information
This figure illustrates the process of gene knockout using the RED (Recombination Engineering) system, a highly efficient genomic editing technology based on the λ phage Red system. The system includes three key enzymes: Exo (5’ → 3’ exonuclease), Beta (single-stranded DNA binding protein), and Gam (antinuclease protein), which facilitate homologous integration or replacement of foreign DNA into the host genome [35,36,67,68]. In this study, the upstream and downstream fragments of the guaB gene were amplified by PCR, along with the kanamycin resistance gene. These fragments were assembled into the linearized pccdK2 vector using the Gibson assembly method to generate a targeting fragment, which was then transformed into competent E. coli DH5α cells. Positive clones were selected by colony PCR and verified by sequencing. The verified plasmid was transformed into E. coli BW25113 [69], resulting in the successful construction of the gene knockout strain BW-ΔguaB (S2 Fig).
(TIF)
(A) Growth of the auxotrophic E. coli strain BW-ΔguaB in M9 medium supplemented with 0.5 mM xanthine. (B) Growth of the strain in M9 medium without any added xanthine. The strain shows a clear dependency on the supplementation of xanthine for growth, as evidenced by the lack of growth in the medium without xanthine.
(TIF)
This figure illustrates the plasmid constructed by incorporating caffeine demethylation genes derived from Pseudomonas putida CBB5. The positions of promoters, ribosome binding sites, and terminators are indicated. The purpose of this pathway is to convert caffeine into xanthine, thereby supplementing the xanthine required by the BW-ΔguaB strain and shifting its dependence from xanthine to caffeine.
(TIF)
This zip file contains the raw data sets supporting the findings of this study.
(ZIP)
Acknowledgments
We sincerely thank the faculty members and research teams at the College of Life Science, NEFU, for their technical assistance and valuable discussions throughout this study.
Data Availability
All relevant data are within the manuscript and its Supporting information files.
Funding Statement
The author(s) received no specific funding for this work.
References
- 1.Feng F-J, Li X-S, Yao J-P. Research on virtual storage system in cloud computing. dtcse. 2017;(aice-ncs). doi: 10.12783/dtcse/aice-ncs2016/5711 [DOI] [Google Scholar]
- 2.Singh S, Anand S. Implementing storage as a service in cloud using network attached storage. IJCA. 2014;108(13):6–9. doi: 10.5120/18969-7701 [DOI] [Google Scholar]
- 3.Peng Y, Zhu Y, Luo J. A network storage framework based on SAN. In: 2012 7th International Conference on Computer Science & Education (ICCSE), 2012. 818–21. doi: 10.1109/iccse.2012.6295196 [DOI] [Google Scholar]
- 4.Pawar CS, Patil PR, Chaudhari SV. Providing security and integrity for data stored in cloud storage. In: International Conference on Information Communication and Embedded Systems (ICICES2014), 2014. 1–5. doi: 10.1109/icices.2014.7033968 [DOI] [Google Scholar]
- 5.Li P, Yang X. On dynamic recovery of cloud storage system under advanced persistent threats. IEEE Access. 2019;7:103556–69. doi: 10.1109/access.2019.2932020 [DOI] [Google Scholar]
- 6.Wang C, Wang Q, Ren K, Lou W. Privacy-Preserving Public Auditing for Data Storage Security in Cloud Computing. In: 2010 Proceedings IEEE INFOCOM, 2010. 1–9. doi: 10.1109/infcom.2010.5462173 [DOI] [Google Scholar]
- 7.Alneyadi S, Sithirasenan E, Muthukkumarasamy V. A survey on data leakage prevention systems. J Net Comp Appl. 2016;62:137–52. doi: 10.1016/j.jnca.2016.01.008 [DOI] [Google Scholar]
- 8.Deng Y. Deconstructing network attached storage systems. J Net Comp Appl. 2009;32(5):1064–72. doi: 10.1016/j.jnca.2009.02.006 [DOI] [Google Scholar]
- 9.Jin X, Chen P, Hsu C, Yu C, Chen T. (2021). CAFE: Catastrophic data leakage in vertical federated learning. arXiv (Cornell University). doi: 10.48550/arxiv.2110.15122 [DOI] [Google Scholar]
- 10.Li Q, Ji H, Huang Y. The information leakage strategies of the supply chain under the block chain technology introduction. Omega. 2022;110:102616. doi: 10.1016/j.omega.2022.102616 [DOI] [Google Scholar]
- 11.Chukry S, Sbeyti H. Security Enhancement in Storage Area Network. In: 2019 7th International Symposium on Digital Forensics and Security (ISDFS), 2019. 1–5. doi: 10.1109/isdfs.2019.8757492 [DOI] [Google Scholar]
- 12.Cao B, Wang B, Zhang Q. GCNSA: DNA storage encoding with a graph convolutional network and self-attention. iScience. 2023;26(3):106231. doi: 10.1016/j.isci.2023.106231 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 13.Wang S, Mao X, Wang F, Zuo X, Fan C. Data storage using DNA. Adv Mater. 2024;36(6):e2307499. doi: 10.1002/adma.202307499 [DOI] [PubMed] [Google Scholar]
- 14.Doricchi A, Platnich CM, Gimpel A, Horn F, Earle M, Lanzavecchia G, et al. Emerging approaches to DNA data storage: challenges and prospects. ACS Nano. 2022;16(11):17552–71. doi: 10.1021/acsnano.2c06748 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 15.Goldman N, Bertone P, Chen S, Dessimoz C, LeProust EM, Sipos B, et al. Towards practical, high-capacity, low-maintenance information storage in synthesized DNA. Nature. 2013;494(7435):77–80. doi: 10.1038/nature11875 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 16.Service R. DNA could store all of the world’s data in one room. Science. 2017. doi: 10.1126/science.aal0852 [DOI] [Google Scholar]
- 17.Gupta T, Khandelwal R, Sharma R, Verma M. DNA: the ultimate data-storage solution. JAC. 2024;XVIII(1):272–80. doi: 10.30696/jac.xviii.1.2024.272-280 [DOI] [Google Scholar]
- 18.Xie X, Wang S, Chen Z, Yu Y, Hu X, Ma N, et al. Exploring DNA computers: advances in storage, cryptography and logic circuits. Chembiochem. 2025;26(1):e202400670. doi: 10.1002/cbic.202400670 [DOI] [PubMed] [Google Scholar]
- 19.Piao Y, Fang Y, Li B, Man T, Chen J, Zhu F, et al. Bead-based DNA synthesis and sequencing for integrated data storage using digital microfluidics. Angew Chem Int Ed Engl. 2025;64(4):e202416004. doi: 10.1002/anie.202416004 [DOI] [PubMed] [Google Scholar]
- 20.Choi Y, Ryu T, Lee AC, Choi H, Lee H, Park J, et al. High information capacity DNA-based data storage with augmented encoding characters using degenerate bases. Sci Rep. 2019;9(1):6582. doi: 10.1038/s41598-019-43105-w [DOI] [PMC free article] [PubMed] [Google Scholar]
- 21.Kosuri S, Church GM. Large-scale de novo DNA synthesis: technologies and applications. Nat Methods. 2014;11(5):499–507. doi: 10.1038/nmeth.2918 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 22.Chen L, Aziz MM, Mohammed N, Jiang X. Secure large-scale genome data storage and query. Comput Methods Programs Biomed. 2018;165:129–37. doi: 10.1016/j.cmpb.2018.08.007 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 23.Liu A, Chen X-B, Xu S, Wang Z, Li Z, Xu L, et al. A secure scheme based on a hybrid of classical-quantum communications protocols for managing classical blockchains. Entropy (Basel). 2023;25(5):811. doi: 10.3390/e25050811 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 24.Li K, Chen H, Li D, Yang C, Zhang H, Zhu Z. Empowering DNA-based information processing: computation and data storage. ACS Appl Mater Interfaces. 2024;16(50):68749–71. doi: 10.1021/acsami.4c13948 [DOI] [PubMed] [Google Scholar]
- 25.Wang S, Mao X, Wang F, Zuo X, Fan C. Data storage using DNA. Adv Mater. 2024;36(6):e2307499. doi: 10.1002/adma.202307499 [DOI] [PubMed] [Google Scholar]
- 26.Li S-Y, Liu J-K, Zhao G-P, Wang J. CADS: CRISPR/Cas12a-assisted DNA steganography for securing the storage and transfer of DNA-encoded information. ACS Synth Biol. 2018;7(4):1174–8. doi: 10.1021/acssynbio.8b00074 [DOI] [PubMed] [Google Scholar]
- 27.Hoose A, Vellacott R, Storch M, Freemont PS, Ryadnov MG. DNA synthesis technologies to close the gene writing gap. Nat Rev Chem. 2023;7(3):144–61. doi: 10.1038/s41570-022-00456-9 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 28.Eisenstein M. Enzymatic DNA synthesis enters new phase. Nat Biotechnol. 2020;38(10):1113–5. doi: 10.1038/s41587-020-0695-9 [DOI] [PubMed] [Google Scholar]
- 29.Arredondo-Alonso S, Pöntinen AK, Cléon F, Gladstone RA, Schürch AC, Johnsen PJ, et al. A high-throughput multiplexing and selection strategy to complete bacterial genomes. Gigascience. 2021;10(12):giab079. doi: 10.1093/gigascience/giab079 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 30.Gervasio JHDB, da Costa Oliveira H, da Costa Martins AG, Pesquero JB, Verona BM, Cerize NNP. How close are we to storing data in DNA? Trends Biotechnol. 2024;42(2):156–67. doi: 10.1016/j.tibtech.2023.08.001 [DOI] [PubMed] [Google Scholar]
- 31.Quandt EM, Hammerling MJ, Summers RM, Otoupal PB, Slater B, Alnahhas RN, et al. Decaffeination and measurement of caffeine content by addicted Escherichia coli with a refactored N-demethylation operon from Pseudomonas putida CBB5. ACS Synth Biol. 2013;2(6):301–7. doi: 10.1021/sb4000146 [DOI] [PubMed] [Google Scholar]
- 32.Summers RM, Louie TM, Yu CL, Subramanian M. Characterization of a broad-specificity non-haem iron N-demethylase from Pseudomonas putida CBB5 capable of utilizing several purine alkaloids as sole carbon and nitrogen source. Microbiology (Reading). 2011;157(Pt 2):583–92. doi: 10.1099/mic.0.043612-0 [DOI] [PubMed] [Google Scholar]
- 33.Yang J, Wang C, Lu Y. A temperature-controlled cell-free expression system by dynamic repressor. ACS Synth Biol. 2022;11(4):1408–16. doi: 10.1021/acssynbio.1c00641 [DOI] [PubMed] [Google Scholar]
- 34.Miller EM, Nickoloff JA. Escherichia coli Electro-transformation. Humana Press. 2003. p. 105–14. [Google Scholar]
- 35.Stahl FW, Kobayashi I, Stahl MM. In phage lambda, cos is a recombinator in the red pathway. J Mol Biol. 1985;181(2):199–209. doi: 10.1016/0022-2836(85)90085-3 [DOI] [PubMed] [Google Scholar]
- 36.Thaler DS, Stahl MM, Stahl FW. Tests of the double-strand-break repair model for red-mediated recombination of phage lambda and plasmid lambda dv. Genetics. 1987;116(4):501–11. doi: 10.1093/genetics/116.4.501 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 37.Liu C, Wu Y, Zhao H, Gu X, Gu J, Zhao M, et al. Highly efficient whole-cell biocatalysis for the biosynthesis of 7-methylxanthine and other xanthine derivatives. ACS Sustainable Chem Eng. 2024;12(26):9716–26. doi: 10.1021/acssuschemeng.4c01165 [DOI] [Google Scholar]
- 38.Ogita S, Uefuji H, Morimoto M, Sano H. Metabolic engineering of caffeine production. Plant Biotechnology. 2005;22(5):461–8. doi: 10.5511/plantbiotechnology.22.461 [DOI] [Google Scholar]
- 39.Peng Y, Moffat JG, DuPai C, Kofoed EM, Skippington E, Modrusan Z, et al. Differential effects of inosine monophosphate dehydrogenase (IMPDH/GuaB) inhibition in Acinetobacter baumannii and Escherichia coli. J Bacteriol. 2024;206(10):e0010224. doi: 10.1128/jb.00102-24 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 40.da Costa BRB, El Haddad LP, Freitas BT, Marinho PA, De Martinis BS. Pre-workout supplements marketed in Brazil: Caffeine quantification and caffeine daily intake assessment. Drug Test Anal. 2022;14(3):567–77. doi: 10.1002/dta.3043 [DOI] [PubMed] [Google Scholar]
- 41.Mizuno K, Kato M, Irino F, Yoneyama N, Fujimura T, Ashihara H. The first committed step reaction of caffeine biosynthesis: 7-methylxanthosine synthase is closely homologous to caffeine synthases in coffee (Coffea arabica L.). FEBS Lett. 2003;547(1–3):56–60. doi: 10.1016/s0014-5793(03)00670-7 [DOI] [PubMed] [Google Scholar]
- 42.Li M, Sun Y, Pan S, Deng W, Yu O, Zhang Z. Engineering a novel biosynthetic pathway in Escherichia coli for the production of caffeine. RSC Adv. 2017;7(89):56382–9. doi: 10.1039/c7ra10986e [DOI] [Google Scholar]
- 43.Heckman MA, Weil J, Gonzalez de Mejia E. Caffeine (1, 3, 7-trimethylxanthine) in foods: a comprehensive review on consumption, functionality, safety, and regulatory matters. J Food Sci. 2010;75(3):R77-87. doi: 10.1111/j.1750-3841.2010.01561.x [DOI] [PubMed] [Google Scholar]
- 44.Reyes CM, Cornelis MC. Caffeine in the diet: country-level consumption and guidelines. Nutrients. 2018;10(11):1772. doi: 10.3390/nu10111772 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 45.Stirling F, Bitzan L, O’Keefe S, Redfield E, Oliver JWK, Way J, et al. Rational design of evolutionarily stable microbial kill switches. Mol Cell. 2017;68(4):686–697.e3. doi: 10.1016/j.molcel.2017.10.033 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 46.Chan CTY, Lee JW, Cameron DE, Bashor CJ, Collins JJ. “Deadman” and “Passcode” microbial kill switches for bacterial containment. Nat Chem Biol. 2016;12(2):82–6. doi: 10.1038/nchembio.1979 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 47.Chaudhari JK, Pant S, Jha R, Pathak RK, Singh DB. Biological big-data sources, problems of storage, computational issues, and applications: a comprehensive review. Knowl Inf Syst. 2024;66(6):3159–209. doi: 10.1007/s10115-023-02049-4 [DOI] [Google Scholar]
- 48.Yamato I, Murata T, Khrennikov A. Energy and information flows in biological systems: Bioenergy transduction of V1-ATPase rotary motor and dynamics of thermodynamic entropy in information flows. Prog Biophys Mol Biol. 2017;130(Pt A):33–8. doi: 10.1016/j.pbiomolbio.2017.04.004 [DOI] [PubMed] [Google Scholar]
- 49.McInnes RS, McCallum GE, Lamberte LE, van Schaik W. Horizontal transfer of antibiotic resistance genes in the human gut microbiome. Curr Opin Microbiol. 2020;53:35–43. doi: 10.1016/j.mib.2020.02.002 [DOI] [PubMed] [Google Scholar]
- 50.Kuvshinov V V, Koivu K, Kanerva A, Pehu E. Molecular control of transgene escape from genetically modified plants. Plant Sci. 2001;160(3):517–22. doi: 10.1016/s0168-9452(00)00414-3 [DOI] [PubMed] [Google Scholar]
- 51.Peng H, Bilal M, Iqbal HMN. Improved biosafety and biosecurity measures and/or strategies to tackle laboratory-acquired infections and related risks. Int J Environ Res Public Health. 2018;15(12):2697. doi: 10.3390/ijerph15122697 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 52.Trump BD, Galaitsi SE, Appleton E, Bleijs DA, Florin M-V, Gollihar JD, et al. Building biosecurity for synthetic biology. Mol Syst Biol. 2020;16(7):e9723. doi: 10.15252/msb.20209723 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 53.Dong W-R, Xiang L-X, Shao J-Z. Novel antibiotic-free plasmid selection system based on complementation of host auxotrophy in the NAD de novo synthesis pathway. Appl Environ Microbiol. 2010;76(7):2295–303. doi: 10.1128/AEM.02462-09 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 54.Sharma RK, Issac B, Xin Q, Gadekallu TR, Nath K. Plant and salamander inspired network attack detection and data recovery model. Sensors (Basel). 2023;23(12):5562. doi: 10.3390/s23125562 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 55.Peter S, Bosio M, Gross C, Bezdan D, Gutierrez J, Oberhettinger P, et al. Tracking of antibiotic resistance transfer and rapid plasmid evolution in a hospital setting by nanopore sequencing. mSphere. 2020;5(4):e00525–20. doi: 10.1128/mSphere.00525-20 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 56.Pomerantz A, Peñafiel N, Arteaga A, Bustamante L, Pichardo F, Coloma LA, et al. Real-time DNA barcoding in a rainforest using nanopore sequencing: opportunities for rapid biodiversity assessments and local capacity building. Gigascience. 2018;7(4):giy033. doi: 10.1093/gigascience/giy033 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 57.Zhou Y, Long X, Zhang Y, Zheng D, Jiang Y, Hu Y. Advances and challenges in solid-state nanopores for DNA sequencing. Langmuir. 2025;41(9):5736–61. doi: 10.1021/acs.langmuir.4c04961 [DOI] [PubMed] [Google Scholar]
- 58.Mısırlı G, Hallinan J, Pocock M, Lord P, McLaughlin JA, Sauro H, et al. Data integration and mining for synthetic biology design. ACS Synth Biol. 2016;5(10):1086–97. doi: 10.1021/acssynbio.5b00295 [DOI] [PubMed] [Google Scholar]
- 59.Wong S. T. C., Patwardhan A. (2001). Storage, data management, and retrieval in bioinformatics. Proceedings of SPIE, the International Society for Optical Engineering/Proceedings of SPIE, 4676, 248–263. doi: 10.1117/12.451113 [DOI] [Google Scholar]
- 60.tahmasebi T, Piramanayagam SN. Nanoscience and nanotechnology for memory and data storage. COSMOS. 2011;07(01):25–30. doi: 10.1142/s0219607711000705 [DOI] [Google Scholar]
- 61.Grosges T, Barchiesi D. Toward nanoworld-based secure encryption for enduring data storage. Opt Lett. 2010;35(14):2421–3. doi: 10.1364/OL.35.002421 [DOI] [PubMed] [Google Scholar]
- 62.Zafar S, Rana N. The convergence of nanotechnology and artificial intelligence: unlocking future innovations. RICE. 2025;18. doi: 10.2174/0124055204359215250127071256 [DOI] [Google Scholar]
- 63.Cottingham H, Judd LM, Wisniewski JA, Wick RR, Stanton TD, Vezina B, et al. Targeted sequencing of Enterobacterales bacteria using CRISPR-Cas9 enrichment and Oxford Nanopore Technologies. mSystems. 2025;10(2):e0141324. doi: 10.1128/msystems.01413-24 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 64.Kim MB, Lee YJ. Characterisation of the CRISPR-Cas systems in Enterococcus faecalis from commercial broiler farm environments and its association with antimicrobial resistance. Br Poult Sci. 2025;:1–8. doi: 10.1080/00071668.2025.2451268 [DOI] [PubMed] [Google Scholar]
- 65.Pacalin NM, Steinhart Z, Shi Q, Belk JA, Dorovskyi D, Kraft K, et al. Bidirectional epigenetic editing reveals hierarchies in gene regulation. Nat Biotechnol. 2025;43(3):355–68. doi: 10.1038/s41587-024-02213-3 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 66.Xu X, Lv X, Liu Y, Li J, Du G, Chen J, et al. CRISPR/Cas13X-assisted programmable and multiplexed translation regulation for controlled biosynthesis. Nucleic Acids Res. 2025;53(1):gkae1293. doi: 10.1093/nar/gkae1293 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 67.Thomason LC, Sawitzke JA, Li X, Costantino N, Court DL. Recombineering: genetic engineering in bacteria using homologous recombination. Curr Protoc Mol Biol. 2014;106:1.16.1–1.16.39. doi: 10.1002/0471142727.mb0116s106 [DOI] [PubMed] [Google Scholar]
- 68.Caldwell BJ, Bell CE. Structure and mechanism of the Red recombination system of bacteriophage λ. Prog Biophys Mol Biol. 2019;147:33–46. doi: 10.1016/j.pbiomolbio.2019.03.005 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 69.Woodall CA. Electroporation of E. coli. Methods Mol Biol. 2003;235:55–69. doi: 10.1385/1-59259-409-3:55 [DOI] [PubMed] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Supplementary Materials
This figure illustrates the process of gene knockout using the RED (Recombination Engineering) system, a highly efficient genomic editing technology based on the λ phage Red system. The system includes three key enzymes: Exo (5’ → 3’ exonuclease), Beta (single-stranded DNA binding protein), and Gam (antinuclease protein), which facilitate homologous integration or replacement of foreign DNA into the host genome [35,36,67,68]. In this study, the upstream and downstream fragments of the guaB gene were amplified by PCR, along with the kanamycin resistance gene. These fragments were assembled into the linearized pccdK2 vector using the Gibson assembly method to generate a targeting fragment, which was then transformed into competent E. coli DH5α cells. Positive clones were selected by colony PCR and verified by sequencing. The verified plasmid was transformed into E. coli BW25113 [69], resulting in the successful construction of the gene knockout strain BW-ΔguaB (S2 Fig).
(TIF)
(A) Growth of the auxotrophic E. coli strain BW-ΔguaB in M9 medium supplemented with 0.5 mM xanthine. (B) Growth of the strain in M9 medium without any added xanthine. The strain shows a clear dependency on the supplementation of xanthine for growth, as evidenced by the lack of growth in the medium without xanthine.
(TIF)
This figure illustrates the plasmid constructed by incorporating caffeine demethylation genes derived from Pseudomonas putida CBB5. The positions of promoters, ribosome binding sites, and terminators are indicated. The purpose of this pathway is to convert caffeine into xanthine, thereby supplementing the xanthine required by the BW-ΔguaB strain and shifting its dependence from xanthine to caffeine.
(TIF)
This zip file contains the raw data sets supporting the findings of this study.
(ZIP)
Data Availability Statement
All relevant data are within the manuscript and its Supporting information files.