Abstract
The rise of Non-Fungible Tokens (NFTs) and Internet of Things (IoT) devices created new demands for secure data management. To address these needs, we propose LIBLO, a lightweight blockchain-based smart NFT architecture designed for decentralized environments with limited resources. Traditional models mostly depend on heavy computation techniques to ensure the data security. To avoid this, LIBLO introduces a compressed blockchain layer combined with lightweight encryption techniques. This allows secure storage, verification, and controlled access to IoT-generated data without overloading devices. In this architecture, LIBLO acts as a trusted digital framework that securely encapsulates metadata, ownership identity, and access control policies. Each transaction is verified through digital signatures and efficiently recorded on a compressed blockchain ledger. This design ensures privacy, traceability, and integrity and also contributes to energy-efficient implementation in real-time IoT scenarios. Experimental results demonstrate that the suggested LIBLO achieves high encryption strength and strong decryption accuracy of 0.96%, and low error rates of (1.1%). By simplifying cryptographic operations and reducing blockchain complexities, LIBLO presents a practical and adaptable solution for securing digital assets and IoT interactions in smart environments.
Keywords: Lightweight blockchain, Internet of things (IoT), Smart Non-Fungible tokens (NFTs), Secure data management, Digital signatures, Decentralized architecture, Metadata protection, Compressed ledger
Subject terms: Computational science, Computer science
Introduction
Non-fungible tokens (NFTs) have emerged as a revolutionary concept in the digital realm, fundamentally altering how we perceive and represent digital assets1–3. Unlike traditional cryptocurrencies like Bitcoin or Ethereum, NFTs are indivisible and unique, making them ideal for representing digital assets with distinct value. For example, NFTs can represent digital art, collectables, virtual real estate, and more, providing a new way for creators and collectors to engage with digital content4–6. However, as NFTs gained prominence, they also brought forth critical challenges that must be addressed. These challenges span various domains, with data privacy and security being paramount concerns. NFTs often involve the transfer of valuable digital assets, and ensuring the privacy and security of these transactions is crucial7. Additionally, as the NFT ecosystem grew more complex, managing these digital assets intelligently became increasingly challenging. Traditional NFT systems, initially designed for simpler use cases, struggled to keep pace with the evolving demands of the digital asset landscape8–10.
Recognizing these challenges, a pressing need emerged for innovative solutions that could re-envision NFT management11,12. This is where the Lightweight Blockchain-based (LIBLO) Smart and Secure NFT Architecture comes into play. LIBLO represents a paradigm shift in how NFTs are handled and secured. It draws on cutting-edge technologies and integrates various crucial domains, effectively reshaping how NFTs are managed and utilized. Instead of depending on computationally intensive mechanisms, LIBLO involves lightweight cryptographic techniques and decentralized trust mechanisms tailored for IoT environments. LIBLO involves IoT-driven data intelligence, lightweight symmetric encryption (SIT cipher), ECC-based digital signatures, compressed blockchain ledgers, and smart contract-driven access control to achieve privacy, efficiency, and traceability. These elements specifically strengthen the foundation of LIBLO, by restricting the performance risks found commonly in traditional blockchain-NFT models13–15.
The advantages of the proposed LIBLO architecture are multifaceted. It transforms NFTs into lightweight, intelligent containers that support encrypted metadata, automated verification, and traceable interactions16,17. By compressing blockchain records and enabling policy-based access through smart contracts, LIBLO provides a scalable solution for secure NFT management. It is specifically designed for IoT settings, ensuring low power consumption and reduced bandwidth needs that perform without centralised intermediaries18,19. Also, Smart NFTs in LIBLO integrate encrypted metadata and digital ownership signatures, which helps to allow secure asset tracking by maintaining user privacy. In the upcoming sections, we discuss in depth the LIBLO and its contributions that highlight its ability to reshape the NFT landscape and provide users with enhanced security, trust, and user experiences in the world of digital assets.
The main contributions of the paper are as follows.
This paper presents Lightweight BLOckchain (LIBLO), a Smart and Secure NFT architecture that integrates IoT-driven data collection, lightweight encryption, ECC-based signatures, compressed blockchain storage, and smart contracts.
LIBLO ignores the dependence on heavy learning-based encryption methods; instead of that it focused on lightweight cryptography to reduce computational burden by preserving data security and access control.
LIBLO transforms NFT management by converting NFTs into lightweight digital wrappers which help to encapsulate encrypted metadata and signatures for secure verification and traceability.
The paper presents evidence through simulations, showcasing the effectiveness of LIBLO in revolutionizing the NFT landscape.
Literature review
Existing encryption techniques
The proliferation of IoT technology20 has introduced advancements and security challenges, particularly in interconnected networks susceptible to IoT attacks. Protecting sensitive data collected by numerous Internet of Things (IoT) devices in smart cities is crucial to prevent privacy violations and data abuse. To address these concerns, the study proposes an innovative solution combining Federated Learning (FL) and Fully Homomorphic Encryption (FHE). FL facilitates collaborative data analysis without data sharing, while FHE enables secure computations on encrypted data, bolstering data privacy and security. The evaluation of four FL-based FHE approaches demonstrates their efficacy in enhancing data accuracy, privacy, and security while reducing communication overhead and latency. This paper21 addresses security and privacy concerns in mobile services and networks, particularly in federated learning and the Internet of Things (IoT). The proposed solution, xMK-CKKS, enhances privacy preservation in federated learning by encrypting model updates with an aggregated public key before sharing them with a server. Collaboration among participating devices is necessary for decryption, ensuring privacy protection. The paper aims to prevent privacy leakage, resist collaboration between devices and servers, and maintain model accuracy while optimising communication and computational efficiency.
The article22 addresses the challenges organizations face, particularly in finance and healthcare, when collaboratively training machine learning models without sharing sensitive data in cross-silo federated learning (FL). The primary goal is to reduce the computational and communication costs associated with homomorphic encryption (HE), which is currently a dominant and resource-intensive approach in federated learning (FL) frameworks. The proposed solution, BatchCrypt, encodes batches of quantized gradients into a single ciphertext, optimizing gradient-wise aggregation and significantly reducing encryption and communication overhead. The implementation is integrated into the FATE framework, contributing to more efficient cross-silo FL.
The paper’s23 motivation is to address the efficiency challenges in federated learning (FL), where statistical heterogeneity among client data distributions and global distribution skewness can degrade performance. The primary aim is to improve the FL process by introducing a client selection method called Dubhe. This method enables clients to actively participate in training while maintaining data privacy through homomorphic encryption (HE), ultimately enhancing the efficiency and effectiveness of FL across various datasets.
Lightweight blockchain models
This study24 introduces a blockchain architecture that operates over a Distributed Hash Table (DHT), allowing for efficient storage and retrieval of blocks and transactions. This design is handy for environments with limited resources. In study25, SeF is proposed as a blockchain storage solution that utilizes fountain codes to reduce storage requirements. This architecture allows full nodes to store encoded versions of the blockchain and provides lightweight operations without compromising security benefits for NFT platforms. This study26 presents a privacy-preserving system for managing self-sovereign identities using NFTs on the Dusk Network. By applying zero-knowledge proofs, it ensures that user identities and associated NFTs remain confidential. This research27, which introduces SB, a blockchain framework designed for IoT environments, highlights lightweight consensus mechanisms and scalable architecture. Its design reduces computational overhead and makes it suitable for NFT applications where devices have limited processing capabilities.
NFT encryption
The primary motivation28 behind this project is to address privacy concerns in the rapidly growing Non-Fungible Token (NFT) market. Current NFT marketplaces lack privacy tools, making NFTs easily visible to everyone and leading to issues like theft and shill trading. The project aims to create Paras, a blockchain-agnostic protocol, to enhance NFT privacy. Paras allows users to hide real NFTs, seller and bidder identities, bid values, and wallet balances using cryptographic techniques such as threshold encryption and robust secret sharing, without relying on trusted execution environments for security. This initiative seeks to provide a more secure and private environment for NFT transactions. The purpose of this research study29 is to address the shortcomings in the existing medical data management system by creating a user-friendly mobile application. This application uses blockchain technology to centralize and secure users’ medical information. It provides a secure and easily accessible platform for storing, sharing, and tracking medical records, ensuring data integrity and privacy. Users can monitor who accesses their data, and hospitals can efficiently input and manage patient information, including various medical data formats like images and PDFs. This initiative aims to enhance the overall efficiency and security of medical data management. The integration of artificial intelligence (AI) and digital technologies in the financial sector has garnered significant attention in recent years30. According to31,32, the authors highlight how AI-driven solutions are transforming various aspects of financial operations, from risk assessment to customer service. They emphasize that AI technologies enhance decision-making processes, improve operational efficiencies, and enable more robust security measures.
This study33 addresses challenges in the gaming industry, particularly in the context of NFT-based In-App Purchases (IAPs) and player preferences. The gaming industry’s significant market value and the widespread use of IAPs have created a situation where players have many choices but may find it overwhelming. Additionally, concerns about the security of digital assets in games due to hacking incidents are prevalent. The proposed solution is a recommendation system that leverages a multi-criteria recommender system (MCRS) method. It uses eight criteria to provide players with more accurate and tailored item recommendations, improving their gaming experience and asset security.
Research gap
By thoroughly examining the above encryption techniques, most solutions remain computationally intensive. Lightweight blockchain models are already implemented in the existing NFT domain, but they lack unified frameworks that integrate efficient encryption, identity protection, and decentralised control in low-resource settings. Additionally, current privacy solutions primarily rely on complex cryptographic protocols, often overlooking device-level constraints. To address these restrictions, we develop our suggested LIBLO framework, which helps to balance privacy, security and computational efficiency in IoT-driven NFT platforms.
Methodology
System overview
The LIBLO architecture is designed to enable secure and efficient management of smart NFTs using lightweight blockchain and encryption methods. Initially, the process begins with data collection, where IoT devices gather real-time data, including sensor outputs, environmental readings, and transaction logs. This raw data is encrypted locally using lightweight symmetric algorithms and processed through Elliptic Curve Cryptography (ECC)-based digital signatures to ensure confidentiality. Instead of using an existing blockchain mechanism, LIBLO utilizes a novel compressed blockchain ledger, which stores only essential hashes and references to reduce memory and bandwidth requirements. Transactions and Smart NFTs are processed using lightweight consensus mechanisms, such as Proof of Authority (PoA), to validate and record updates with minimum energy consumption. A smart contract layer involves handling data verification, enforcing access policies, and managing NFT ownership. This decentralized structure ensures that all operations are performed without overburdening the IoT devices. The schematic illustration of the suggested LIBLO is depicted in Fig. 1.
Fig. 1.
Proposed LIBLO model for smart and secure NFT.
System initialization
The initial phase of the LIBLO framework focused on creating cryptographic identities and securing the communication throughout the participating nodes. Each IoT device 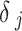 is installed with a lightweight cryptographic identity, based on elliptic curve operations that allows signed and verifiable interactions. Here, each device generates a key pair using a compact elliptic curve signature algorithm, this can be expressed as
is installed with a lightweight cryptographic identity, based on elliptic curve operations that allows signed and verifiable interactions. Here, each device generates a key pair using a compact elliptic curve signature algorithm, this can be expressed as
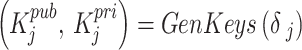 |
1 |
where, 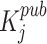 is the public key of
is the public key of  ,
, 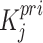 is a private key and
is a private key and 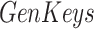 denotes the lightweight ECC key generation function. To uniquely denotes the device within a blockchain, hashed token is created by binding the public key with the device-specific ID, which is expressed as
denotes the lightweight ECC key generation function. To uniquely denotes the device within a blockchain, hashed token is created by binding the public key with the device-specific ID, which is expressed as
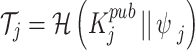 |
2 |
Here, 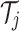 is the identity token of device
is the identity token of device 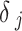 ,
, 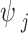 is the device assigned identifier, and
is the device assigned identifier, and 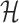 is the Hash function. This token is registered on the compressed blockchain ledger through a smart contract. It allows decentralized identity verification, which prevents impersonation, and supports trust bootstrapping for secure smart NFT interactions.
is the Hash function. This token is registered on the compressed blockchain ledger through a smart contract. It allows decentralized identity verification, which prevents impersonation, and supports trust bootstrapping for secure smart NFT interactions.
Secure data acquisition and lightweight encryption
As we discussed earlier, each IoT device is denoted as 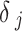 , which continuously collects the data at specific time intervals. The raw data is collected at time
, which continuously collects the data at specific time intervals. The raw data is collected at time 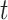 which is expressed as
which is expressed as
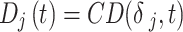 |
3 |
Here, 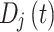 is collected by device at time
is collected by device at time 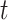 , and
, and 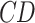 denotes the data acquisition process.
denotes the data acquisition process.
Lightweight symmetric encryption using SIT cipher
In the LIBLO framework, Secure IoT (SIT) cipher is applied by considering its efficiency and low computational overhead. SIT is a 64-bit block cipher that utilizes a hybrid structure combining Feistel networks and substitution-permutation (SP) networks, that achieves high level security in just five encryption rounds. Where, 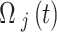 denotes the raw data collected from the IoT device of
denotes the raw data collected from the IoT device of 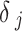 at time
at time 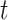 ,
, 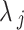 is the 64-bit symmetric key and
is the 64-bit symmetric key and 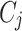 is the encrypted data output for device
is the encrypted data output for device 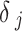 at time
at time 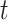 .
.
Here, the structure of SIT is adapted from34. The 64 bit  is expanded to 5 unique round keys of
is expanded to 5 unique round keys of 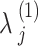 to
to 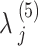 using a key expansion function. For initial data preparation, the plain text data
using a key expansion function. For initial data preparation, the plain text data 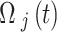 is classified into four 16-bit blocks, which are denoted as
is classified into four 16-bit blocks, which are denoted as 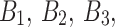 and
and 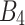 . For each five rounds
. For each five rounds 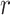 , each block of
, each block of 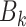 undergoes substitution using predefined
undergoes substitution using predefined  boxes to produce
boxes to produce  . Then the substituted blocks
. Then the substituted blocks 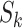 are arranged to enhance distribution. Then apply the Feistal operation.
are arranged to enhance distribution. Then apply the Feistal operation.
Update each block using XOR and round function 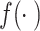 .
.
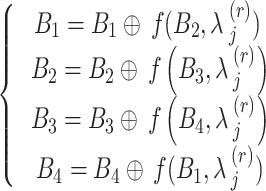 |
4 |
where, 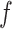 is a round function to ensure non-linearity. Therefore, the final output is expressed as
is a round function to ensure non-linearity. Therefore, the final output is expressed as
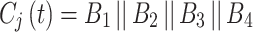 |
5 |
Decryption process.
The decryption follows the reverse of the encryption steps. Using the same symmetric key 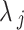 , the round keys are applied in reverse order. The encrypted data
, the round keys are applied in reverse order. The encrypted data 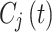 is first split into four blocks, and the reverse operation are performed per round.
is first split into four blocks, and the reverse operation are performed per round.
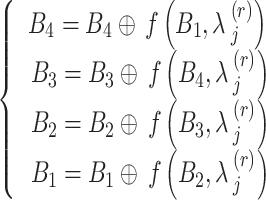 |
6 |
This process is repeated for r = 5 down to 1 and reassembled to recover the original plaintext was shown as
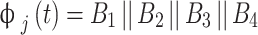 |
7 |
Algorithm 1: Lightweight encryption using SIT cipher
Digital signature using ECC
In this section we generate the digital signature using Elliptic Curve Cryptography (ECC)35. It is a lightweight and secure public-key cryptographic mechanism that is highly suitable for IoT environments due to its ability to provide strong encryption and digital signing abilities using small key sizes. In the LIBLO framework, ECC is used to digitally sign encrypted NFT data to ensure authenticity. This process is defined as
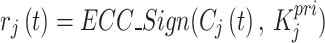 |
8 |
where, 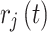 is the signature attached to the encrypted NFT,
is the signature attached to the encrypted NFT, 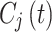 is the encrypted data and
is the encrypted data and 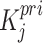 is the private key.
is the private key.
ECC is based on the mathematics of elliptic curves over finite fields. According to the concept of [], elliptic curve E of a prime field 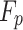 is defined as
is defined as
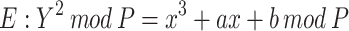 |
9 |
Here, the security of ECC depends on the difficulty of Elliptic Curve Discrete Logarithm Problem (ECDLP). According to our suggested LIBLO, each device 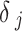 has a private signing key of
has a private signing key of 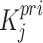 and a corresponding public key of
and a corresponding public key of 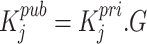 .
.
Where, 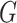 is the base point on the elliptic curve. To sign the encrypted data
is the base point on the elliptic curve. To sign the encrypted data 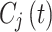 . LIBLO performs a cryptographic Hash function which is expressed as
. LIBLO performs a cryptographic Hash function which is expressed as
 |
10 |
Then, the random number of 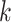 is generated. Here,
is generated. Here, 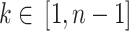 . Where,
. Where, 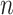 is the order of the base point
is the order of the base point 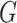 . Using the random number
. Using the random number 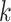 , we calculate a new elliptic curve point
, we calculate a new elliptic curve point  by performing scalar multiplication,
by performing scalar multiplication,  . Here
. Here 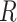 is a new point on the curve and it has two coordinates
is a new point on the curve and it has two coordinates 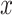 and
and 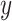 . Now we consider the
. Now we consider the 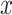 coordinate of
coordinate of 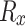 to reduce it module
to reduce it module 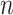 to get the value
to get the value 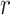 . This will become the first part of the signature, which is defined as
. This will become the first part of the signature, which is defined as
 |
11 |
This value  serves as a compressed representation of the elliptic curve point and contributes to the security and uniqueness of the final ECC signature.
serves as a compressed representation of the elliptic curve point and contributes to the security and uniqueness of the final ECC signature.
Algorithm 2: ECC based digital signature generation
Smart NFT construction and metadata binding
Once the NFT data from IoT devices is encrypted and digitally signed, LIBLO moves to the next phase of Smart NFT construction. In this step, all essential features such as the encrypted content, the signature, and additional metadata are grouped into a Smart NFT. The encrypted data  and its digital signature
and its digital signature 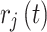 and also the descriptive metadata
and also the descriptive metadata 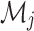 is involved in smart NFT. This smart NFT is specifically defined as
is involved in smart NFT. This smart NFT is specifically defined as
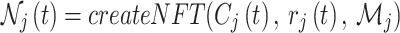 |
12 |
Equation (9) combines encrypted data, digital signature and metadata in unique traceable NFT. The metadata 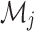 acts as a digital identity and decide who is the authorized user based on the rule.
acts as a digital identity and decide who is the authorized user based on the rule.
Compressed blockchain storage and smart Contract-Based access control
Traditional blockchain systems store complete transaction records in every block, which leads to high storage costs, particularly in managing large-scale NFT metadata and transactions. To overcome this limitation, LIBLO uses a novel compressed blockchain ledger, also referred as a squeezed ledger, which is used to notably reduces on-chain storage by preserving data integrity.
Consider that 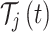 be the full NFT transaction bundle at time
be the full NFT transaction bundle at time 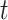 , consisting encrypted data
, consisting encrypted data 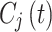 , digital signature
, digital signature 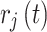 and metadata
and metadata 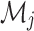 . This is defined as
. This is defined as
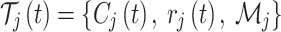 |
13 |
Here, instead of recording all the transactions  directly on the blockchain, LIBLO calculates Merkle Root Hash
directly on the blockchain, LIBLO calculates Merkle Root Hash 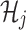 over multiple transaction bundles, defined as
over multiple transaction bundles, defined as
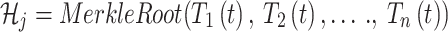 |
14 |
This root hash 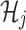 becomes a compressed representation of an entire batch of transactions. The blockchain replaces the original old blocks with a new block that contains only
becomes a compressed representation of an entire batch of transactions. The blockchain replaces the original old blocks with a new block that contains only 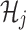 and a pointer to the corresponding off-chain storage location
and a pointer to the corresponding off-chain storage location 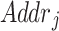 . Then, the updated compressed block is defined as
. Then, the updated compressed block is defined as
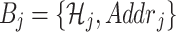 |
15 |
Here, 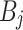 denotes the compressed blockchain block for device
denotes the compressed blockchain block for device  and
and  is a secure off chain database reference for raw transaction data.
is a secure off chain database reference for raw transaction data.
Once a user 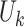 request access to NFT data, the LIBLO smart contract evaluate this request
request access to NFT data, the LIBLO smart contract evaluate this request 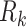 against predefined access control rules
against predefined access control rules 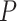 , this include role based, attribute-based ownership policies, which means the decision is based on the access evaluation, expressed as
, this include role based, attribute-based ownership policies, which means the decision is based on the access evaluation, expressed as
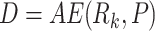 |
16 |
Here, 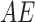 is the access evaluation about request
is the access evaluation about request 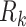 and predefined access control rules
and predefined access control rules 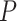 .
.
If the access policy conditions are met, the access is granted
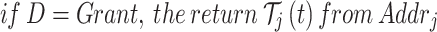 |
17 |
Algorithm 3: Compressed ledger storage and access control
Results and experiments
Dataset description
The dataset features selected to evaluate the proposed LIBLO comprise critical information essential for assessing LIBLO’s performance in managing and securing NFTs. These features include NFT transaction data from prominent NFT markets, encompassing 6.1 million transactions involving 4.7 million NFTs distributed across more than 4000 collections, further categorised into six main categories (Art, Collectable, Games, Metaverse, Utility, and Other). Each NFT within the dataset is associated with image data, textual descriptions, and selling prices, facilitating comprehensive evaluations of LIBLO’s capabilities in handling diverse NFTs. To demonstrate the real-world applicability, LIBLO is simulated in an IoT environment using a Raspberry Pi 4 Model B, configured to perform in lightweight models. This setup confirms LIBLO ability in resource-constrained settings. The dataset’s focus on transaction history, categorisation, and pricing ensures a strong foundation for evaluating NFT data tracking, integrity preservation, and decentralised access. The dataset features are adapted from the study36. Table 1 shows the hyperparameters of the model.
Table 1.
Hyperparameters of the model.
| Parameter | Value |
|---|---|
| Dataset source | NFT market transactions |
| Total transactions | 6.1 million |
| Total NFTs | 4.7 million |
| NFT categories | Art, collectable, games, metaverse, utility, other |
| Encryption cipher | SIT (64-bit) |
SIT rounds (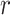 ) ) |
5 |
| ECC curve | secp256r1 |
| ECC key size | 256 bits |
| Data block size | 64 bits (4 × 16-bit blocks) |
| Merkle batch size | 128 transactions per block |
| Smart contract policy | Role-based access control (RBAC) |
Sampling interval 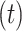
|
10 s |
| Token generation hash | SHA-256 |
| Number of IoT devices | 50 |
| Signature scheme | ECC digital signature (ECDSA) |
| Avg CPU usage | 23–28% |
| Avg RAM usage | 32–40 MB per operation |
Evaluation criteria
In this study, we conduct a comparative analysis of our novel LIBLO system against established privacy-preserving techniques, including Blockchain-based Zero-Knowledge Proofs37 and traditional Homomorphic Encryption methods like Partially Homomorphic Encryption (PHE)38 and Somewhat Homomorphic Encryption (SHE)39. LIBLO integrates the robustness of Federated Learning-based Homomorphic Encryption with several advanced techniques, as previously discussed. Therefore, we embark on a comprehensive evaluation through simulated comparisons and practical experiments to gauge the effectiveness of LIBLO in safeguarding sensitive data in various scenarios.
Encryption strength
The robustness of LIBLO’s encryption strength becomes evident through an extensive comparative analysis with existing models, like BL-ZK, PHE, and SHE, was shown in Fig. 2. These evaluations are structured throughout varying encryption rounds (from 1 to 5). By assigning encryption strength values to each model across these encryption stages, the consistent dominance of LIBLO in terms of cryptographic security becomes evident. As depicted in Fig. 2, where each curve corresponds to a model (LIBLO, BL-ZK, PHE, SHE), the x-axis now represents the number of encryption rounds, and the y-axis signifies encryption strength (in bits). Notably, LIBLO consistently outperforms BL-ZK, PHE, and SHE, and proves its provision of more effective encryption.
Fig. 2.
Encryption strength.
Decryption accuracy
Figure 3 demonstrates the computational efficiency and cryptographic stability achieved by the proposed LIBLO framework based on increasing encryption rounds, which ranges from 1 to 5. Within this illustrative visual, we accurately outline the decryption accuracy values attributed to LIBLO, as well as other prominent models, including BL-ZK, PHE, and SHE. The figure’s significance unfolds through several critical facets: Initially, it provides a direct evidence of LIBLO’s decryption accuracy against its competitive models, enabling a precise evaluation of LIBLO’s performance with 5 simulation rounds. Next, the figure proves the LIBLO’s consistent efficiency over BL-ZK, PHE, and SHE through each encryption round. This consistent dominance highlights the LIBLO’s decryption accuracy. Also, the controlled and stable reduction pattern observed in LIBLO’s decryption curve highlights its efficient inverse in cryptographic processing, particularly in resource-constrained IoT scenarios.
Fig. 3.
Decryption accuracy.
Data integrity
The effectiveness of the proposed LIBLO model in ensuring data integrity is prominently illustrated in Fig. 4. This visual representation distinctly highlights LIBLO’s consistent superiority over other models, including BL-ZK, PHE, and SHE. Throughout all the encryption rounds considered, LIBLO consistently maintains a position above these models, firmly establishing its robustness in safeguarding data integrity. This noteworthy trend underscores LIBLO’s unwavering commitment to upholding data accuracy and reliability. LIBLO’s remarkable consistency in maintaining data integrity serves as a testament to its resilience and adaptability. It vividly showcases the model’s capacity to ensure the precision and trustworthiness of data, even when confronted with complex computational challenges.
Fig. 4.
Data integrity.
Error handling
Figure 5 offers a concise and visually informative comparison of LIBLO’s error handling performance against other models, namely BL-ZK, PHE, and SHE. The x-axis identifies each model, while the corresponding error rate percentages are displayed on the y-axis. LIBLO emerges as the standout performer with the lowest error rate, underscoring its exceptional error management capabilities. Its minimal error rate underscores LIBLO’s proficiency in handling errors during data processing, ensuring the highest level of data accuracy and integrity. In contrast, BL-ZK exhibits a slightly higher error rate in comparison to LIBLO, suggesting a somewhat lower degree of effectiveness in error handling. While BL-ZK maintains reasonable performance, it may have a marginally increased likelihood of encountering errors during data operations. PHE, on the other hand, demonstrates a significantly higher error rate when compared to both LIBLO and BL-ZK. This notable increase in error rate suggests potential challenges in error management, which could compromise the overall integrity of processed data. Lastly, SHE exhibits the highest error rate among the models, indicating potential struggles in effective error handling. This higher error rate highlights the increased likelihood of SHE encountering errors during data processing tasks. Finally, the overall comparison analysis is shown in Table 2.
Fig. 5.
Error handling.
Table 2.
Overall comparison of the models.
| Features | LIBLO | BL-ZK | PHE | SHE |
|---|---|---|---|---|
| Encryption type | Lightweight SIT | Zero-knowledge proofs | Partial homomorphic encryption | Somewhat homomorphic encryption |
| Decryption accuracy | High (95–98%) | Moderate (88–91%) | Moderate (84–89%) | Low (76–82%) |
| Encryption strength (bits) (5 Rounds) | 256 | 192 | 160 | 128 |
| Error rate (%) | 1.1 | 3.5 | 6.8 | 9.3 |
| Avg. CPU usage | 23–28% | 40–50% | 58–65% | 60–70% |
| Avg. RAM usage | 32–40 MB | 60–75 MB | 80–100 MB | 90–120 MB |
| Blockchain storage | Compressed (Merkle-based) | Standard | Standard | Standard |
| Suitability for IoT | High | Low | Low | Low |
User experience
The efficacy of the proposed LIBLO, as observed through user experience was shown in Fig. 6, is a critical aspect that reflects its performance and impact on end-users. In the context of user experience, LIBLO aims to provide a seamless and satisfactory interaction for individuals interacting with the system.
Excellent: LIBLO strives to deliver an exceptional user experience, which is represented by the highest percentage of users who rate their experience as “Excellent.” This category signifies that a significant portion of users finds LIBLO to be highly effective, user-friendly, and reliable. An excellent user experience suggests that LIBLO successfully meets user expectations and offers a smooth, hassle-free experience.
Good: The “Good” category in the user experience evaluation indicates that a substantial number of users have a positive perception of LIBLO. They may encounter minor issues or challenges occasionally, but overall, their experience is satisfactory. LIBLO ensures that a considerable proportion of users fall into this category, demonstrating its ability to provide a generally positive user interaction.
Average: Some users may find their experience with LIBLO to be “Average.” This category suggests that while LIBLO offers functionality and utility, there might be room for improvement in certain aspects. These users might encounter occasional usability issues or limitations, which LIBLO should consider addressing to enhance the user experience further.
Poor: The “Poor” user experience category represents the smallest percentage of users who find their interaction with LIBLO to be unsatisfactory. This category indicates that there are specific areas where LIBLO may need improvement to meet user expectations and resolve usability or performance issues.
LIBLO’s efficacy depends on its ability to maintain a high percentage of users within the “Excellent” and “Good” categories while minimizing the proportion of users in the “Average” and “Poor” categories. A higher percentage of satisfied users in the top categories demonstrates LIBLO’s effectiveness in delivering a superior user experience. It showcases LIBLO’s commitment to user-centric design, usability, and overall performance, making it a preferred choice for secure digital asset management and NFT applications where user trust and satisfaction are paramount.
Fig. 6.
User experience rating comparison.
Conclusion
In this paper, we have addressed the critical challenges facing Non-Fungible Tokens (NFTs), including data privacy, security, and intelligent management. Traditional NFT systems often struggle to provide robust solutions to these challenges. In response, we have introduced the innovative Lightweight Blockchain-based (LIBLO) Smart and Secure NFT Architecture, which represents an efficient approach to NFT management. LIBLO takes on these challenges head-on by leveraging IoT-driven data intelligence, lightweight symmetric encryption (SIT cipher), and elliptic curve digital signatures (ECC). Also, LIBLO maintains its cryptographic strength and acts as an effective contribution for resource-constrained IoT environments. This combination transforms NFTs from simple tokens into repositories of intelligence. With LIBLO, NFT data tracking, management, and analysis become automated, resulting in enhanced performance, security, and valuable insights. Our lightweight framework offers a holistic approach to digital asset management. Through the integration of smart contracts and digital wallets, NFT transactions gain trust and automation, while advanced analytics enable real-time tracking and comprehensive behavior analysis. LIBLO’s design is tailored for the IoT, effectively addressing the complexities of the IoT ecosystem, such as security, trust, and seamless connectivity. At the heart of LIBLO are Smart NFTs, fortified with lightweight encryption and ECC based digital signatures with a compressed blockchain ledger. These Smart NFTs ensure data integrity, enable verifiable ownership, and enforce decentralized access policies through smart contracts. Each secure operation is subject to meticulous authentication through Smart NFTs, instilling the highest level of trust in the NFT ecosystem. In conclusion, our simulations have validated the effectiveness of LIBLO, showcasing its potential to practical NFT landscape. By addressing the challenges of data privacy, security, and intelligent management, LIBLO offers a robust and comprehensive solution that can elevate the NFT industry to new heights, providing users with enhanced security, trust, and user experiences in the rapidly evolving world of digital assets. Apart from advantages some restrictions should be considered. LIBLO uses lightweight encryption and ECC-based digital signatures to secure data and verify identities, therefore full security analysis of possible threats is not fully analyzed. Some risks like key leakage, replay attacks, and misuse of smart contracts are observed but not deeply analysed in this version. In future work, we plan to explore these vulnerabilities more thoroughly using standard threat modeling approaches like STRIDE. Also, future versions should focus to incorporate direct inputs from environmental or visual sensors depending on the NFT domain.
Acknowledgements
This work is supported by Xinjiang University Post-Funding Special Project "Research on Enterprise Digital Transformation and Financing Efficiency" (No.:22FPY006).
Author contributions
L.W.: Conceptualization, methodology, software , editing-original draft preparation, supervision. Z.L.: Data curation, editing-original draft preparation.
Funding
This work is supported by Xinjiang University Post-Funding Special Project "Research on Enterprise Digital Transformation and Financing Efficiency" (No.:22FPY006).
Data availability
The datasets used and/or analyzed during the current study are available from the corresponding author upon reasonable request.
Declarations
Competing interests
The authors declare no competing interests.
Footnotes
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Arcenegui, J., Arjona, R., Román, R. & Baturone, I. Secure combination of IoT and blockchain by physically binding IoT devices to smart non-fungible tokens using PUFs. Sensors. 21(9), 3119 (2021). [DOI] [PMC free article] [PubMed]
- 2.Sun, G., Li, Y., Liao, D. & Chang, V. Service function chain orchestration across multiple domains: A full mesh aggregation approach. IEEE Trans. Netw. Serv. Manag.15(3), 1175–1191 (2018).
- 3.Pandey, S. S., Dash, T., Panigrahi, P. K. & Farouk, A. Efficient quantum non-fungible tokens for blockchain. arXiv preprint arXiv:2209.02449. (2022).
- 4.Luo, H., Zhang, Q., Sun, G., Yu, H. & Niyato, D. Symbiotic blockchain consensus: cognitive backscatter communications-enabled wireless blockchain consensus. IEEE/ACM Trans. Netw. 32 (6), 5372–5387 (2024). [Google Scholar]
- 5.Luo, H., Sun, G., Chi, C., Yu, H. & Guizani, M. Convergence of symbiotic communications and blockchain for sustainable and trustworthy 6G wireless networks. IEEE Wirel. Commun.32(2), 18–25 (2025).
- 6.Wang, P., Song, W., Qi, H., Zhou, C., Li, F., Wang, Y., et al. Server-initiated federated unlearning to eliminate impacts of low-quality data. IEEE Trans. Serv. Comput.17(3), 1196–1211 (2024).
- 7.Zou, X., Yuan, J., Shilane, P., Xia, W., Zhang, H., et al. From hyper-dimensional structures to linear structures: maintaining deduplicated data’s locality. ACM Trans. Storage. 18(3), 1–28 (2022).
- 8.Xia, W., Pu, L., Zou, X., Shilane, P., Li, S., Zhang, H., et al. The design of fast and lightweight resemblance detection for efficient post-deduplication delta compression. ACM Trans. Storage. 19(3), 1–30 (2023).
- 9.Sestino, A., Guido, G. & Peluso, A. M. Non-Fungible Tokens (NFTs). In Examining the Impact on Consumers and Marketing Strategies. (2022).
- 10.Xu, F., Yang, H. & Alouini, M. Energy consumption minimization for data collection from wirelessly-powered IoT sensors: Session-specific optimal design with DRL. IEEE Sens. J.22(20), 19886–19896 (2022).
- 11.Siddique, H. M. A., Yaqub, R. M. S., Akram, H. M. Z. & Khurshid, R. Determinants of AI non-fungible tokens gaming and blockchain based digital marketing: A revolution of metaverse in Asia Pacific region. Pakistan J. Humanit. Social Sci.11 (2), 1909–1931 (2023). [Google Scholar]
- 12.Huang, S., Sun, C. & Pompili, D. Meta-ETI: Meta-reinforcement learning with explicit task inference for UAV-IoT coverage. IEEE Internet Things J. (2025).
- 13.Huang, F., Bei, Y., Yang, Z., Jiang, J., Chen, H., Shen, Q., et al. Large language model simulator for cold-start recommendation. In Paper Presented at the WSDM ‘25, New York (2025).
- 14.Rasheed, A. M. & Kumar, R. M. S. Efficient lightweight cryptographic solutions for enhancing data security in healthcare systems based on IoT. Front. Comput. Sci.7, 1522184 (2025).
- 15.Liu, Y., Huo, M., Li, M., He, L. & Qi, N. Establishing a digital twin diagnostic model based on Cross-Device transfer learning. IEEE Trans. Instrum. Meas.74, 1–10 (2025). [Google Scholar]
- 16.Yang, J., Yang, K., Xiao, Z., Jiang, H., Xu, S., et al. Improving commute experience for private car users via blockchain-enabled multitask learning. IEEE Internet Things J.10(24), 21656–21669 (2023).
- 17.Punia, A. et al. A systematic review on blockchain-based access control systems in cloud environment. J. Cloud Comput.13(1), 146 (2024).
- 18.Polenakis, I., Vouronikos, V., Kiafa, E., Chroni, M. & Nikolopoulos, S. D. June. ProtAIN: Protecting the authenticity and integrity properties of NFT images. In Proceedings of the International Conference on Computer Systems and Technologies 2024, 16–23 (2024).
- 19.Jiang, H., Ji, P., Zhang, T., Cao, H. & Liu, D. Two-factor authentication for keyless entry system via finger-induced vibrations. IEEE Trans. Mob. Comput.23 (10), 9708–9720 (2024). [Google Scholar]
- 20.Hijazi, N. M., Aloqaily, M., Guizani, M., Ouni, B. & Karray, F. Secure federated learning with fully homomorphic encryption for IoT communications. IEEE Internet Things J. (2023).
- 21.Ma, J., Naas, S. A., Sigg, S. & Lyu, X. Privacy-preserving federated learning based on multi‐key homomorphic encryption. Int. J. Intell. Syst.37 (9), 5880–5901 (2022). [Google Scholar]
- 22.Zhang, C. et al. {BatchCrypt}: Efficient homomorphic encryption for {Cross-Silo} federated learning. In 2020 USENIX Annual Technical Conference (USENIX ATC 20), 493–506 (2020).
- 23.Zhang, S. et al. August. Dubhe: Towards data unbiasedness with homomorphic encryption in federated learning client selection. In Proceedings of the 50th International Conference on Parallel Processing, 1–10 (2021).
- 24.Xu, Y., Ding, L., He, P., Lu, Z. & Zhang, J. Meta: A memory-efficient tri-stage polynomial multiplication accelerator using 2D Coupled-BFUs. IEEE Trans. Circuits Syst. I Regul. Pap.72 (2), 647–660 (2025). [Google Scholar]
- 25.Gong, Y., Yao, H., Liu, X., Bennis, M., Nallanathan, A., et al., Computation and privacy protection for satellite-ground digital twin networks. IEEE Trans. Commun.72(9), 5532–5546 (2024).
- 26.Salleras, X. Citadel: Self-Sovereign Identities on Dusk Network. arXiv preprint arXiv:2301.09378. (2023).
- 27.Guruprakash, J. & Koppu, S. EC-ElGamal and genetic algorithm-based enhancement for lightweight scalable blockchain in IoT domain. IEEE Access.8, 141269–141281 (2020). [Google Scholar]
- 28.Rao, V. Paras-A Private NFT Protocol. Cryptology ePrint Archive. (2022).
- 29.Zhang, Y., Zhao, M., Chen, Y., Lu, Y. & Cheung, Y. Learning unified distance metric for heterogeneous attribute data clustering. Expert Syst. Appl.273, 126738 (2025). [Google Scholar]
- 30.Ahmadirad, Z. Evaluating the influence of AI on market values in finance: distinguishing between authentic growth and speculative hype. Int. J. Adv. Res. Humanit. Law. 1 (2), 50–57 (2024). [Google Scholar]
- 31.Pazouki, S., Jamshidi, M. B., Jalali, M. & Tafreshi, A. Transformative impact of AI and digital technologies on the fintech industry: a comprehensive review. Int. J. Adv. Res. Humanit. Law. 2 (2), 1–27 (2025). [Google Scholar]
- 32.Pazouki, S., Jamshidi, M. B., Jalali, M. & Tafreshi, A. Artificial intelligence and digital technologies in finance: a comprehensive review. J. Econ. Finance Acc. Stud.7 (2), 54–69 (2025). [Google Scholar]
- 33.Pradana, R. P., Hariadi, M., Rachmadi, R. F. & Arif, Y. M. July. A multi-criteria recommender system for NFT based IAP in RPG game. In 2022 International Seminar on Intelligent Technology and its Applications (ISITIA), 214–219 (IEEE, 2022).
- 34.Zhang, J., Sui, H., Sun, X., Ge, C., Zhou, L., et al. GrabPhisher: Phishing scams detection in ethereum via temporally evolving GNNs. IEEE Trans. Serv. Comput.17(6), 3727–3741 (2024).
- 35.Adhikari, S., Ray, S., Obaidat, M. S. & Biswas, G. P. ECC-based efficient and secure access control scheme for content centric Network-A next generation internet. Wirel. Pers. Commun.132 (1), 571–607 (2023). [Google Scholar]
- 36.Costa, D., La Cava, L. & Tagarelli, A. April. Show me your NFT and I tell you how it will perform: Multimodal representation learning for NFT selling price prediction. In Proceedings of the ACM Web Conference 2023, 1875–1885 (2023).
- 37.Li, T., Kouyoumdjieva, S. T., Karlsson, G. & Hui, P. Data collection and node counting by opportunistic communication. In Paper Presented at the 2019 IFIP Networking Conference (IFIP Networking, 2019).
- 38.Li, T., Xiao, Z., Georges, H., Luo, Z. & Wang, D. Performance analysis of co- and cross-tier device-to-device communication underlaying macro-small cell wireless networks. KSII Trans. Internet Inf. Syst.10 (4), 1481–1500 (2016). [Google Scholar]
- 39.Wibawa, F., Catak, F. O., Kuzlu, M., Sarp, S. & Cali, U. June. Homomorphic encryption and federated learning based privacy-preserving cnn training: Covid-19 detection use-case. In Proceedings of the 2022 European Interdisciplinary Cybersecurity Conference, 85–90 (2022).
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
The datasets used and/or analyzed during the current study are available from the corresponding author upon reasonable request.











