Abstract
Wi-Fi sensing is an innovative technology that enables numerous human-related applications. Among these, Wi-Fi based person re-identification (Re-ID) is an emerging research topic aiming to address well-known challenges related to traditional vision-based methods, such as occlusions or illumination changes. This approach can serve as either an alternative or a supplementary solution to those conventional techniques. However, public datasets and benchmarks for Wi-Fi based person Re-ID are still missing, posing constraints on future investigations. Towards filling this gap, this paper presents Wi-PER81, a pioneering dataset comprising measurements of 162,000 wireless packets captured at two different times, associated with 81 distinct identities. Furthermore, it introduces a baseline Siamese neural network architecture used to analyze person-related signal magnitude heatmaps and the results of a comparative study against well-known neural network models, serving as backbones in the proposed approach, that provides a comprehensive benchmark for person Re-ID using radio-based visual features.
Subject terms: Computer science, Scientific data
Background & Summary
Wi-Fi sensing has recently gained significant attention as an innovative technology that leverages the pervasive nature of Wi-Fi signals to sense both private and public environments, enabling a wide range of human-related sensing applications such as vital sign monitoring1,2, gesture3,4 and activity recognition5,6, event detection7,8, or person re-identification (Re-ID)9,10. These are possible by exploiting the intrinsic properties of Wi-Fi signals, e.g., amplitude and phase, encoding and transmitting information over a wireless network. When traveling between the transmitting (TX) and receiving (RX) antennas of two connected wireless devices, signals are affected by the presence of objects and people along their propagation path, resulting in variations in the signal characteristics that can be caught through the channel state information (CSI) measurement11. The CSI, a PHY layer measure obtained employing orthogonal frequency-division multiplexing (OFDM) technology12, incorporates fine-grained signal information at the subcarrier level and enables the extraction of radio-based features that are subsequently used in deep learning models tailored to a specific sensing task13. The advent of deep learning has significantly enhanced the field of Wi-Fi sensing, especially in interpreting subtle signal variations, surpassing traditional model-based approaches14. However, the effectiveness of deep learning methods significantly depends on the availability of relevant human-related sensing and modeling datasets that fit this technology15,16. Among various Wi-Fi sensing applications, person Re-ID via Wi-Fi signals is still an emerging research topic that remains underexplored due to the lack of publicly available datasets, which hampers progress in this area9. Traditionally, person Re-ID involves recognizing individuals across different time instants and locations using non-overlapping camera views17. This is done by matching a probe image against a gallery of identities, using visual features extracted from images to retrieve the most probable match18,19. Despite the remarkable results achieved by visual-based methods, they still face challenges such as occlusions20, illumination changes21, varying viewing angles22, background clutter23, and long-term Re-ID24. In contrast, Wi-Fi sensing technology offers a new alternative or complementary solution that inherently avoids these visual issues. Furthermore, Wi-Fi signals mitigate human privacy concerns because the radio-based medium does not collect sensitive data like facial features14,25, thus providing more privacy-preserving methods for re-identifying people. Despite these, and to the best of our knowledge, public datasets and benchmarks similar to the ones available for visual recognition have not yet been established for Wi-Fi person Re-ID, limiting the evidence and resources available for future research. Therefore, this paper introduces Wi-PER81, a new benchmark dataset specifically designed for person re-identification through radio-based visual information. This dataset includes Wi-Fi signal captures from 81 distinct individuals, each recorded in two separate sessions, resulting in a total of 162 signal captures. Each session comprises 1,000 data packets per individual, thus collecting 162,000 wireless packets across the entire collection. For each identity, the dataset provides CSI measurements, raw and sanitized amplitude values, and corresponding signal magnitude heatmaps. The Wi-PER81 dataset is intended to be a foundation for developing and benchmarking person Re-ID systems using radio-based visual features. To demonstrate its potential, we propose a baseline neural network architecture employing a Siamese-like pipeline to analyze person-related signal amplitude heatmaps. Based on convolutional neural networks (CNNs), this architecture is designed to learn fine-grained differences among individuals by comparing pairs of signal magnitude heatmaps26,27, which proved practical in previous person Re-ID studies9. Using common Re-ID metrics, the baseline model’s performance is compared against several well-known neural network architectures, serving as backbones in the presented approach, to establish a comprehensive benchmark encouraging the exploration of radio-based person Re-ID. Most recent Wi-Fi sensing research has focused on gesture4,28,29 and human activity recognition (HAR)6,30,31, resulting in limited datasets for human movement analysis via Wi-Fi. Notable datasets include UT-HAR32, Widar3.03, and OPERAnet16, each providing CSI data for various activities but in controlled scenarios and limited in scale or diversity. Wi-PER81 differentiates itself by offering data over 52 OFDM subcarriers from 81 individuals in real-world settings. Recently, Yang et al.14 introduced a benchmark for radio-based HAR in literature, but a benchmark encouraging future investigation of integrating radio signals for person Re-ID is still missing. However, novel pioneering studies9,10,33 have explored Wi-Fi person Re-ID, demonstrating the potential of using Wi-Fi signals for capturing unique human features and indicating that further studies should be performed.
In summary, the main contributions of this paper are:
the introduction of Wi-PER81, a pioneering benchmark dataset containing Wi-Fi CSI data, amplitude values, and signal heatmaps to support radio-based visual person Re-ID under realistic, noisy conditions;
a thorough data analysis exploration to understand inherent signal properties, focusing on both intra- and inter-personal signal variations by applying multiple sanitization techniques to extract person-specific radio biometrics;
an extensive benchmarking by comparing several CNN-based backbones, each operating within a Siamese architecture proven effective for processing distinctive radio-based visual characteristics.
Methods
Data Collection
Wi-Fi sensing system setup
The Wi-Fi sensing system, depicted in Fig. 1(a), consists of two communicating ESP32 - low-cost, low-power microcontrollers with integrated Wi-Fi and Bluetooth capabilities - each connected to different laptops and acting as TX and RX antennas, respectively, using the IEEE 802.11n protocol and 2.4 GHz frequency band.
Fig. 1.
In (a) the Wi-Fi Sensing System experimental setup; in (b) the indoor stand configuration.
This setup enables the CSI collection of Wi-Fi signals, effectively measuring the fine-grained signal propagation characteristics. Specifically, for the acquisition of the Wi-PER81 dataset, the ESP32 CSI toolkit34 was used. The latter uses the OFDM technology to transmit shared pilot symbols interleaved within the data frame, which are predefined signal patterns used for essential purposes, including CSI estimation. Precisely, for each wireless data packet, the CSI vector contains 64 subcarriers, where 52 correspond to data subcarriers and the remaining ones are zero subcarriers35, i.e. guard-bands and Direct Current (DC) component. Formally, given a pair of devices, the CSI complex vector H, denoting the characteristics of the received signal, is modeled using the following relation:
| 1 |
where s ∈ [0, 63] is the s-th subcarrier, y(s) indicates the received signal, x(s) is the transmitted signal (i.e., the shared pilot), η(s) is the noise vector, and H(s) is the CSI complex value. Such CSI value consists of a real component and an imaginary component , which can be used to compute signal attributes like the amplitude value for each subcarrier, as follows:
| 2 |
Design criteria
Wi-PER81 was acquired at a stand of a public convention while showing the potential of human-related Wi-Fi sensing. Therefore, unlike other datasets, it was collected in a real-world application setting, characterized by unconstrained environmental properties, e.g., crowded areas, and no shielding mechanism against interference from other radio signals, which is inevitable in our highly connected world. For these reasons, Wi-PER81 emphasizes its relevance in demonstrating the capabilities of Wi-Fi person Re-ID in a practical context. Specifically, as depicted in Fig. 1(b), the stand had a size of 400 × 200 cm in width and length, respectively, and was located in an indoor environment. Moreover, it accommodated two desks with chairs, each of 120 × 70 cm in size. The TX and RX devices were placed towards the rear of the right-hand desk, mounted on two plastic poles anchored in wooden bases, and spaced 1.75 meters apart. Additionally, each ESP32 device was elevated to 131.5 cm from the ground and 130 cm from the wooden support, aligning approximately with the average adult chest height. In this experimental setting, the CSI of the received Wi-Fi signals was collected within a LoS configuration, where the human subject was positioned at the central point between the TX and RX devices. This arrangement was chosen to understand the human body’s effect on Wi-Fi signal propagation and simulate real-world conditions in a surveillance scenario, e.g., security screening. Furthermore, for each individual, the influenced signal was captured twice at two distinct times to evaluate the signal’s integrity over multiple sessions. This study was approved by the Institutional Review Board (IRB-’DMIF) of the Department of Mathematics, Computer Science and Physics (DMIF) at the University of Udine. Informed consent for participation and data sharing was obtained directly from all participants involved.
Wi-PER81 dataset description
The Wi-PER81 dataset consists of Wi-Fi signal acquisitions influenced by 81 distinct volunteers, categorized into 59 males and 22 females, with ages estimated to range from 18 to 65 years and heterogeneous body types. Each participant contributed to two separate acquisition sessions, resulting in a collective total of 162 signals. Apart from Wi-Fi signals, no additional personal information was requested to preserve the volunteers’ privacy. Specifically, 1,000 data packets describing the influenced Wi-Fi signal were collected within each session, totaling 162,000 wireless packets for the entire collection. The dataset contains the CSI measurements, extracted raw and sanitized amplitude values for the 52 data subcarriers, and corresponding signal magnitude heatmaps for each acquisition. The RSSI values are not included because they do not provide fine-grained radio-based features except for the relative signal quality. To the best of our knowledge, the Wi-PER81 dataset provides more participants and higher-resolution CSI data than most publicly available human-related Wi-Fi sensing datasets.
Data Analysis
Wi-Fi signal amplitude sanitization
The extraction of amplitude from the CSI measurement of a Wi-Fi signal is the most common starting point to understand the inherent signal properties required for various sensing applications2,6,13. However, the wireless channel is not a noise-free communication medium and abnormal values can appear among CSI values, affecting the extraction of human-related radio-based features. Thus, the obtained amplitude values require a sanitization procedure to alleviate the possible noise from protocol specifications, external interferences, and ambient noise while maintaining relevant information. To this end, we tested various sanitization techniques over subcarriers to filter amplitude values, i.e., Hampel filter9, Z-score36, and Interquartile Range (IQR)37, discovering each person’s amplitude radio biometric. Figure 2(a) shows the raw amplitude values and the results of each sanitization procedure. The IQR strategy resulted in the best solution for capturing the relevant signal information and filtering out outlier values. Figure 2(b) confirms this finding; indeed, the IQR-derived signal magnitude heatmap best highlights the person’s influence on the Wi-Fi signal. In particular, given the raw amplitude values sorted in ascending order, the outlier detection process for each data subcarrier s ∈ [0, 51] can be modeled as:
| 3 |
where Q1s and Q3s are the first and third quartiles of the specific subcarrier, respectively, while LBs and UBs are the lower and upper bounds used for outlier detection. Therefore, for each amplitude value x in subcarrier s, if x < LBs or x > UBs, x is identified as an outlier and replaced with the nearest previous non-outlier value.
Fig. 2.
In (a) the raw amplitude values and the related different sanitization results; in (b) the corresponding signal magnitude heatmaps.
Intra-person comparisons
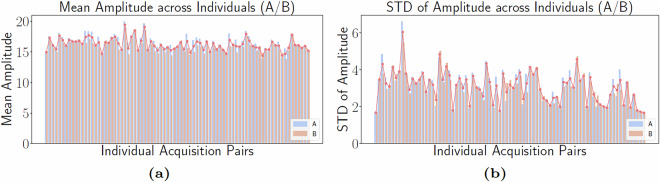
This analysis aims to investigate the impact of the same individual on Wi-Fi signals across two acquisition sessions, denoted as A and B, providing insights into the variability and stability of signal behavior in the presence of the same person. As shown in Fig. 3, comparing amplitude values and signal magnitude between sessions A and B for the same identity highlights consistent patterns and moderate value changes between the two acquisitions. These variations could be influenced by factors such as the slight difference in the person’s positioning or tiny movement. Figure 4 confirms such findings by comparing the mean and standard deviation of amplitude values across two acquisitions for different persons. The standard deviation for each person confirms the moderate amplitude fluctuation and consistent patterns. Concurrently, the mean – indicating the average signal strength over subcarriers – further demonstrates the observation of consistent patterns and signal magnitude values.
Fig. 3.
In (a) the sanitized amplitude values from the same-person acquisition sessions (A and B); in (b) the corresponding signal magnitude heatmaps.
Fig. 4.
Comparisons of mean (a) and standard deviation (b) of sanitized amplitude values within acquisition pairs (A vs B) for different persons.
Inter-person comparisons
This analysis explores how distinct persons influence Wi-Fi signals differently, enabling and supporting the use of such signals to discriminate among individuals for their re-identification. Expanding upon the previous analysis, Fig. 5 depicts mean and standard deviations across different person acquisition pairs (i.e., A and B), where the red dot denotes the mean value for each pair. The standard deviation measure indicates a significant variation in amplitude values among different individuals. Similarly, the mean indicates a noticeable difference in signal patterns and, consequently, in magnitude. To further confirm these observations, the Manhattan distance was used to measure and compare the signal strength variations across acquisition sessions for the same individual and acquisition pairs for different persons. Figure 6 depicts such metric and comparison via the box plot. The lower median of intra-personal distances indicates that variations within acquisitions for the same identity tend to be smaller than variations between distinct individuals. Moreover, the wider IQR for inter-personal distances indicates more variability in acquisition pairs between identities than within acquisitions for the same person. Finally, the large number of outliers in the inter-personal distribution indicates that signals associated with distinct persons significantly differ from one another due to unique individual characteristics such as body height. In conclusion, both intra-personal and inter-personal distances confirm the consistency of signal measurements among single individuals versus those from different persons.
Fig. 5.
Comparison of mean (a) and standard deviation (b) across different person acquisition pairs (A and B), with the mean of each pair indicated by the red dot.
Fig. 6.
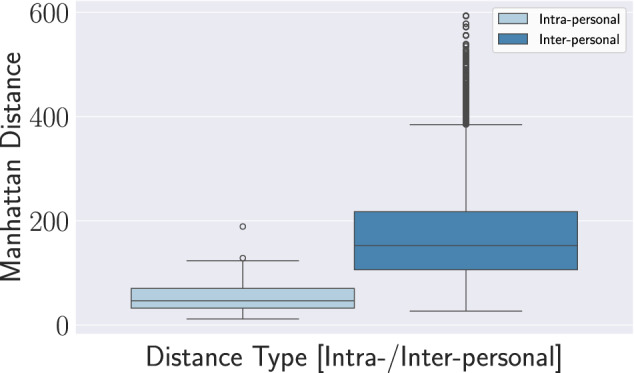
Comparison between intra-personal and inter-personal Manhattan distances, indicating the signal strength variations over subcarriers across acquisition sessions for the same person and acquisition pairs for different persons, respectively.
Data Records
Data annotation and structure
The dataset is available at Figshare38. The Wi-PER81 dataset contains anonymous data, encoding some non-sensitive relevant information within a systematic naming convention. For each filename, the 0000N number is the unique person identity, the subsequent letter [m/f] indicates the individual gender, and the final letter [A/B] denotes the data acquisition session. The CSI data and amplitude values are stored in the CSV file format. Each CSV file contains 1000 rows (i.e., wireless data packets) over 52 indexed columns (i.e., data subcarriers), and the packet Unix timestamps in the last column to eventually enable analyses that require time sequencing or event timing. The IQR-derived signal magnitude heatmap, depicted in Figs. 2(b) and 3(b), is stored as a PNG image. Such visualization can be crucial for quickly assessing signal characteristics. Visually encapsulating the variations in signal strength over subcarriers offers a more accessible and interpretable method than numerical values alone. Both CSV and PNG files follow the specified naming convention, ensuring numerical or visual data are associated with the corresponding identity and acquisition session.
Concerning the signal magnitude heatmaps, the image data was divided into two non-overlapping subsets, D1 and D2, each containing 81,000 processed wireless packets. The first subset, D1, is intended to train neural models and includes acquisitions associated with all 81 identities in session A. The second subset, D2, is intended for evaluation purposes and consists of all acquisitions in session B. For each identity in either dataset, the corresponding 1,000 packets were divided into 10 groups to create 10 distinct identity-related Wi-Fi signal magnitude heatmaps, each derived from 100 wireless data packets and identified by an index gidx integrating the filename convention. Regarding the training process, the 10 identity-related heatmaps were further divided into two subsets, using five heatmaps as probes and the remaining five as a gallery, generating 164,025 input pairs. For the validation and testing phases, two distinct subsets were produced from D2, named and . The former contained four heatmaps, divided into two probes and two gallery items per identity, while the latter comprised the remaining six heatmaps, split into three probes and three gallery items per identity. Consequently, the resulting validation and test sets contained 162 and 243 probes, totaling 26,244 and 59,049 validation and test pairs, respectively. The Wi-PER81 data structure is summarized in Table 1.
Table 1.
Wi-PER81 data structure.
| CSV File - Field(s) | Description |
|---|---|
| CSV/csi_matrices | Folder containing CSI data files |
| 0000N[m/f][A/B]. csv | Filename encoding unique person identifier (0000N), gender (m or f), and acquisition session (A or B). |
| 6,7,8,...,58,timestamp | Data subcarrier indexes and packet Unix timestamp. |
| (7 + 16j), (6 + 14j), . . . , ( − 11 + 20j), 1697788582.0932152 | Packet CSI and timestamp values. |
| CSV/raw_amplitudes | Folder containing raw amplitude data files |
| 0000N[m/f][A/B]. csv | Filename encoding unique person identifier (0000N), gender (m or f), and acquisition session (A or B). |
| 6,7,8,...,58,timestamp | Data subcarrier indexes and packet Unix timestamp. |
| 17.4642, 15.2315, . . . , 22.8254, 1697788582.0932152 | Packet raw amplitude and timestamp values. |
| CSV/IQR_amplitudes | Folder containing sanitized amplitude data files |
| 0000N[m/f][A/B]. csv | Filename encoding unique person identifier (0000N), gender (m or f), and acquisition session (A or B). |
| 6,7,8,...,58,timestamp | Data subcarrier indexes and packet Unix timestamp. |
| 11.6619, 15.2315, . . . , 17.4642, 1697788582.0932152 | Packet IQR amplitude and timestamp values. |
| PNG File - Field(s) | Description |
| ImageData/D1/Gallery | Folder containing gallery images for training |
| 0000N[m/f]A_gidx. png | Filename encoding unique person identifier (0000N), gender (m or f), acquisition session (A), and packets group index (gidx). |
| ImageData/D1/Probe | Folder containing probe images for training |
| 0000N[m/f]A_gidx. png | Filename encoding unique person identifier (0000N), gender (m or f), acquisition session (A), and packets group index (gidx). |
| ImageData/D2v/Gallery | Folder containing gallery images for validation |
| 0000N[m/f]B_gidx. png | Filename encoding unique person identifier (0000N), gender (m or f), acquisition session (B), and packets group index (gidx). |
| ImageData/D2v/Probe | Folder containing probe images for validation |
| 0000N[m/f]B_gidx. png | Filename encoding unique person identifier (0000N), gender (m or f), acquisition session (B), and packets group index (gidx). |
| ImageData/D2t/Gallery | Folder containing gallery images for testing |
| 0000N[m/f]B_gidx. png | Filename encoding unique person identifier (0000N), gender (m or f), acquisition session (B), and packets group index (gidx). |
| ImageData/D2t/Probe | Folder containing probe images for testing |
| 0000N[m/f]B_gidx. png | Filename encoding unique person identifier (0000N), gender (m or f), acquisition session (B), and packets group index (gidx). |
Technical Validation
Wi-Fi Signal Image-based Person Re-ID Baseline
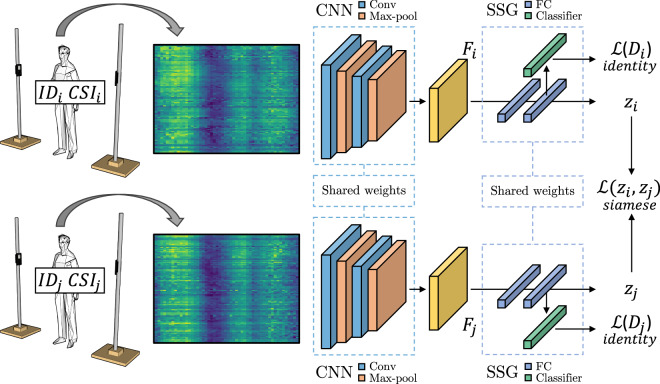
For technical validation, a baseline neural network architecture is proposed for person Re-ID by analyzing sanitized Wi-Fi signal magnitude heatmaps, further validating the already explored hypothesis that such graphical signal representations can serve as indicators for person re-identification9. The proposed network, shown in Fig. 7, works in a Siamese-like fashion and is implemented via two parallel CNN branches to correctly analyze the pre-processed signal heatmaps, which represent the person’s radio-based information derived from amplitude values. Each CNN-based module is trained as a feature extractor (i.e., backbone) and learns invariant mappings from the extracted radio-based representations39, resulting in a suitable option for the re-identification task. Precisely, each branch consists of two convolutional layers, interleaved by two max-pooling operations, followed by two fully connected (FC) layers. Convolutions are responsible for feature extraction from the input images, employing a 3 × 3 filter matrix alongside a padding set to 1. This configuration allows careful analysis of the inputs, producing feature maps F that summarize the features detected within the signal representations without losing significant information. Following the convolutional layers, the max-pooling operations utilize a 2 × 2 window and stride of 2 to downsample the input while preserving the most important features. Finally, the FC layers form the Signal-based Signature Generator (SSG), which is crucial for synthesizing the features extracted by convolutional layers into a latent representation z that captures the unique aspects of an individual’s radio-based information. Concerning the model training, the proposed architecture receives as input image pairs representing signal magnitude heatmaps associated with the same or different persons. Afterward, while each branch learns the discriminant features, the cosine similarity is applied across the CNNs output via a Siamese loss function. This strategy allows maximizing or minimizing the distance among features extracted from signal heatmaps for dissimilar or similar inputs, respectively. Formally, given a pair of Wi-Fi signal magnitude heatmaps (Mi, Mj), the two parallel CNNs extract the corresponding feature maps, Fi and Fj, later used by the SSG component to produce their latent representations, zi and zj. Thus, the Siamese loss function can be defined as:
| 4 |
where m is a margin encouraging the separation of dissimilar pairs that are too close in the feature space during optimization. Even if the Siamese loss is crucial to the signatures generation, the training loss was extended with a joint identification and verification process that can improve the quality of signatures. Specifically, at training time, each branch predicts the person’s identity while equation (4) is globally satisfied. Formally, the person’s signature z generated by each SSG is given as input to a classification layer with dimension D, i.e., the number of identities, and is classified by exploiting a cross-entropy loss function as follows:
| 5 |
where d and yd are the ground truth and predicted person identity, respectively. Therefore, the overall objective training function is defined as:
| 6 |
where and are the identification losses computed by the two model branches. Note that while equation (6) is used to train the neural network in extracting high-quality features from the input signal magnitude heatmaps, at test time, only the Siamese-like architecture is used as a signature extractor. In particular, the losses defined in equation (5) are not computed, while the Siamese loss is replaced by a cosine similarity to perform the person Re-ID on previously unseen data, where higher scores between two signatures indicate likely matching identities.
Fig. 7.
Proposed baseline for Wi-Fi signal image-based person Re-ID. Starting from a wireless transmission, the CSI is used for signal magnitude heatmap generation. Afterward, CNN and SSG are exploited to build relevant signatures for person re-identification.
Implementation details
Regarding the experimental settings, the Wi-Fi signals were collected and preprocessed as described in the Methods section to obtain the signal magnitude heatmaps, and the proposed baseline and alternative backbones, replacing the CNN feature extractor, were tested to establish a benchmark against which new methods can be evaluated to quantify future progress. The assessed models adhered to the same protocol for all tests. Each model was trained for 50 epochs using the Adam optimizer with a learning rate lr set to 5e-4 and a batch size ranging from 32 to 128, depending on the backbone complexity. Dropout was employed across all networks during the training phase, except for the proposed baseline, which was evaluated with and without the application of dropout to assess its impact on generalization. All experiments were evaluated using standard person re-identification (Re-ID) metrics17, i.e., the mean average precision (mAP) and the cumulative matching characteristic (CMC), to represent up to Rank #10 re-identification accuracy. Finally, all networks were implemented using the PyTorch framework and its TorchVision library, while tests were performed on a single GPU, i.e., a GeForce GTX 1070 with 8GB of RAM.
Wi-PER81 benchmark
As described above, the two parallel CNNs act as backbone feature extractors in the proposed baseline architecture. To create a benchmark on the Wi-PER81 dataset, the CNNs were replaced with parallel architectures based on VGG1640, VGG1940, DenseNet12141, EfficientNetB042, and MobileNetV343. All the designed models were trained on set D1 and evaluated on sets and presented in the Data Reports section. Figure 8(a) depicts losses at training time. As can be observed, all models report downward trends, indicative of learning, except for the Baseline network, which flattens out as epochs increase, suggesting that it possibly overfits by rapidly adapting to patterns in the training data. Figure 8(b),(d) show ranks #1, #5, and #10, achieved on the validation set . These ranks represent the likelihood that the correct re-identification happens within the top 1, 5, or 10 predictions, i.e., the accuracy of a model at a given rank. Although the Baseline model learns quickly, it demonstrates limitations in its generalization capabilities by showing relatively low performance when exposed to previously unseen data. However, when applying a dropout strategy, the Baselinew/dropout model displays a remarkable improvement on all ranks, highlighting the value of dropout to effectively regularize and enhance a model in addressing the Wi-Fi signal image-based person Re-ID task. Note that while Baselinew/dropout obtains significant performances, the DenseNet121 backbone outperforms all other models on all ranks on the validation set , appearing to have the highest discrimination power, an aspect that is upheld by its steady and rapid decrease in loss, which suggests robust feature learning capabilities.
Fig. 8.
Training loss (a) and ranks #1, #5, and #10 accuracies on set (b)–(d).
Regarding experiments on the test set , quantitative comparisons in terms of rank accuracies, mAP metric, testing time, and model size are reported in Table 2. As expected, the DenseNet121 backbone is confirmed to be the most effective architecture on the Wi-PER81 dataset, achieving a remarkable rank #1 accuracy of 83%, even though there are models with a higher number of trainable parameters. This outcome indicates, on the one hand, that the DenseNet121 backbone extracts high-quality and unique identity-related features that carry enough radio-based information to correctly describe identities from heatmaps associated with signals acquired at different times. On the other hand, it shows that the internal configuration of an architecture can be more useful than the sheer number of trainable parameters when addressing the person Re-ID task. This aspect is also corroborated by the significant results obtained by Baselinew/dropout at all ranks with respect to the Baseline model, confirming the higher generalization capability of the dropout technique.
Table 2.
Wi-Fi person Re-ID quantitative comparisons on set .
| Model | Rank #1 | Rank #5 | Rank #10 | mAP | Test Time* | Params |
|---|---|---|---|---|---|---|
| VGG1640 | 55.967% | 76.955% | 83.951% | 76.680% | 9’06” | 17.4M |
| VGG1940 | 48.971% | 75.309% | 85.597% | 79.595% | 9’55” | 22.7M |
| DenseNet12141 | 83.128% | 95.473% | 96.708% | 65.364% | 6’57” | 12.3M |
| EfficientNetB042 | 63.786% | 83.951% | 92.181% | 73.442% | 5’09” | 11.9M |
| MobileNetV343 | 41.564% | 67.078% | 75.720% | 82.682% | 4’14” | 4.5M |
| Baseline | 45.679% | 73.663% | 82.716% | 80.967% | 4’21” | 22.6M |
| Baselinew/dropout | 75.720% | 93.004% | 94.650% | 68.450% | 4’31” | 22.6M |
*Time required to evaluate the entire test set .
The internal structure and the number of trainable parameters also affect the inference speed. Naturally, models with fewer parameters tend to be faster even if they can show a trade-off between speed and accuracy (e.g., MobileNetV3). However, a good design can balance this aspect out. For instance, the proposed Baselinew/dropout is almost as fast as the smallest architecture (i.e., MobileNetV3), contains roughly the same number of parameters of the biggest model (i.e., VGG19), and achieves comparable performances with the best backbone (i.e., DenseNet121).
On a different note, while the DenseNet121 backbone and Baselinew/dropout models demonstrate the highest performance at all ranks on the Wi-Fi signal image-based person Re-ID, they exhibit the lowest mAP scores. This indicates that, despite their high accuracy in correctly re-identifying heatmaps, they tend to retrieve wrong identities at higher ranks, resulting in lower accuracy gains.
Conversely, the regular baseline and MobileNetV3 backbone networks show good overall precision, indicating that they can consistently retrieve the correct identities when considering high Re-ID rankings but can still suffer from poor performance at lower ranks, which is not ideal for potential security applications.
Finally, Fig. 9 depicts the CMC curve up to rank #10. As expected, the graph shows an increasing trend across ranks for all the tested models, with the DenseNet121 and Baselinew/dropout consistently outperforming the others. More interestingly, the former backbone achieved significant accuracy even at lower ranks, highlighting the effectiveness of Wi-Fi signal image-based person Re-ID approaches.
Fig. 9.

CMC curve up to rank #10 computed on set .
Conclusion and Future Work
This work introduces Wi-PER81, the first publicly available benchmark dataset explicitly designed for radio signal image-based person re-identification. Wi-PER81 represents a substantial step forward in the field by offering a comprehensive collection of Wi-Fi CSI data, including raw and sanitized amplitude values and visual signal heatmaps. Its real-world acquisition setting, diverse participant pool, and multiple acquisition sessions provide a robust foundation for studying person Re-ID under realistic and noisy conditions. A key contribution of this study is the in-depth analysis of Wi-Fi signal characteristics, where we explored intra- and inter-personal signal variability through multiple statistical sanitization techniques. By applying the Hampel filter, Z-score normalization, and IQR filtering, we examined their effectiveness in isolating person-specific radio biometrics. Among these, the IQR method demonstrated superior performance in capturing discriminative amplitude features while effectively mitigating outlier effects. Furthermore, we conducted comprehensive benchmarking of several CNN-based architectures embedded in a Siamese learning framework, validating their performance in extracting and comparing radio-based visual features. The DenseNet121 backbone emerged as the top performer across standard Re-ID evaluation metrics, while a simple baseline backbone offered an excellent trade-off between computational efficiency and performance.
In summary, Wi-PER81 lays the groundwork for advancing research in privacy-preserving, radio signal image-based Re-ID. As future work, we plan to expand the dataset and explore additional sanitization strategies, particularly those leveraging temporal modeling or adaptive noise estimation, while also incorporating more advanced or hybrid methods to assess whether they offer meaningful performance improvements over the current approach.
Usage Notes
The Wi-PER81 collection can be used to develop radio-based person Re-ID systems using Wi-Fi signal data. The dataset is structured in CSV format for CSI measurements and amplitude values, as well as PNG files for signal magnitude heatmaps. These can be analyzed using common data processing libraries such as Pandas and NumPy for Python. Visualization and analysis of the signal magnitude heatmaps, instead, can be conducted using image processing libraries like Seaborn or Matplotlib. For deep learning model implementation, the PyTorch framework is recommended, especially for training and evaluating neural networks on the signal magnitude heatmaps. The Wi-PER81 dataset is fully anonymized, containing no personal identifiers beyond the numerical labels for each participant. As such, there are no additional privacy or safety controls required for public access. The data is freely accessible, and there are no restrictions on its use. Researchers can download the dataset from the provided repository and use it under the terms of the associated license provided proper citation is given.
Acknowledgements
This paper was partially supported by the FVG Project “Supporting the diagnosis of rare diseases (MR) through artificial intelligence” (2023-26) (CUP: F53C22001770002); by University of Udine project on “Piano Stretegico Dipartimentale on Artificial Intelligence” (PSD-AI) (2022-25) project at the University of Udine, and by the Project “Ecosistema dell’innovazione - Rome Technopole” financed by EU in NextGenerationEU plan through MUR Decree n. 1051 23-06-2022 - CUP B83C22002820006 (generale H33C22000420001).
Author contributions
M.C. and A.F. led the project, devised the dataset, conceived and conducted the experiments, and analyzed the results. All authors wrote and reviewed the manuscript.
Code availability
Custom code for data processing, the neural model implementation, training, and evaluation is provided alongside the dataset and is available at Figshare44. These scripts include functions for loading the CSV files, computing and sanitizing amplitude values, analyzing data, generating signal magnitude heatmaps, and setting up the proposed neural architectures. Furthermore, trained models will be released to ensure the reproducibility of results. Researchers are encouraged to extend these scripts or integrate them into their data processing pipelines to facilitate the adaptation of Wi-PER81 to person Re-ID systems.
Competing interests
The authors declare no competing interests.
Footnotes
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Liu, J. et al. Monitoring vital signs and postures during sleep using wifi signals. IEEE Internet Things J.5, 2071–2084, 10.1109/JIOT.2018.2822818 (2018). [Google Scholar]
- 2.Yu, B. et al. Wifi-sleep: Sleep stage monitoring using commodity wi-fi devices. IEEE Internet Things J.8, 13900–13913, 10.1109/JIOT.2021.3068798 (2021). [Google Scholar]
- 3.Zhang, Y. et al. Widar3.0: Zero-effort cross-domain gesture recognition with wi-fi. IEEE TPAMI44, 8671–8688, 10.1109/TPAMI.2021.3105387 (2022). [DOI] [PubMed] [Google Scholar]
- 4.Wang, D., Yang, J., Cui, W., Xie, L. & Sun, S. Airfi: Empowering wifi-based passive human gesture recognition to unseen environment via domain generalization. IEEE Trans. Mob. Comput.23, 1156–1168, 10.1109/TMC.2022.3230665 (2024). [Google Scholar]
- 5.Wei, B., Hu, W., Yang, M. & Chou, C. T. From real to complex: Enhancing radio-based activity recognition using complex-valued csi. ACM Trans. Sen. Netw.15, 1–32, 10.1145/3338026 (2019). [Google Scholar]
- 6.Yang, J., Chen, X., Zou, H., Wang, D. & Xie, L. Autofi: Toward automatic wi-fi human sensing via geometric self-supervised learning. IEEE Internet Things J.10, 7416–7425, 10.1109/JIOT.2022.3228820 (2023). [Google Scholar]
- 7.Ding, J. & Wang, Y. A wifi-based smart home fall detection system using recurrent neural network. IEEE Trans. Consum. Electron.66, 308–317, 10.1109/TCE.2020.3021398 (2020). [Google Scholar]
- 8.Ribeiro, M., Teixeira, D., Barbosa, P. & Nunes, N. J. Using passive wi-fi for community crowd sensing during the covid-19 pandemic. J. Big Data10, 10.1186/s40537-022-00675-3 (2023). [DOI] [PMC free article] [PubMed]
- 9.Avola, D., Cascio, M., Cinque, L., Fagioli, A. & Petrioli, C. Person re-identification through wi-fi extracted radio biometric signatures. IEEE Trans. Inf. Forensics Secur.17, 1145–1158, 10.1109/TIFS.2022.3158058 (2022). [Google Scholar]
- 10.Ren, Y., Wang, Y., Tan, S., Chen, Y. & Yang, J. Person re-identification using wifi signals. In MOBICOM, 829-831, 10.1145/3495243.3558252 (Association for Computing Machinery, 2022).
- 11.Halperin, D., Hu, W., Sheth, A. & Wetherall, D. Tool release: gathering 802.11n traces with channel state information. SIGCOMM Comput. Commun. Rev.41, 1, 10.1145/1925861.1925870 (2011). [Google Scholar]
- 12.Yang, Z., Zhou, Z. & Liu, Y. From rssi to csi: Indoor localization via channel response. ACM Comput. Surv.46, 1–32, 10.1145/2543581.2543592 (2013). [Google Scholar]
- 13.Avola, D., Cascio, M., Cinque, L., Fagioli, A. & Foresti, G. L. Human silhouette and skeleton video synthesis through wi-fi signals. Int. J. Neural Syst.32, 1–20, 10.1142/S0129065722500150 (2022). [DOI] [PubMed] [Google Scholar]
- 14.Yang, J. et al. Sensefi: A library and benchmark on deep-learning-empowered wifi human sensing. Patterns4, 1–23, 10.1016/j.patter.2023.100703 (2023). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 15.Guo, L. et al. Wiar: A public dataset for wifi-based activity recognition. IEEE Access7, 154935–154945, 10.1109/ACCESS.2019.2947024 (2019). [Google Scholar]
- 16.Bocus, M. J. et al. Operanet, a multimodal activity recognition dataset acquired from radio frequency and vision-based sensors. Sci. Data9, 1–18, 10.1038/s41597-022-01573-2 (2022). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 17.Luo, C., Song, C. & Zhang, Z. Generalizing person re-identification camera-aware invariance learning and cross-domain mixup. In ECCV, 224—241, 10.1007/978-3-030-58555-6_14 (Springer International Publishing, 2020).
- 18.Ye, M. et al. Deep learning for person re-identification: A survey and outlook. IEEE TPAMI44, 2872–2893, 10.1109/TPAMI.2021.3054775 (2022). [DOI] [PubMed] [Google Scholar]
- 19.Zhu, K. et al. Pass: Part-aware self-supervised pre-training for person re-identification. In ECCV, 198–214, 10.1007/978-3-031-19781-9_12 (Springer International Publishing, 2022).
- 20.Zhu, K., Guo, H., Liu, Z., Tang, M. & Wang, J. Identity-guided human semantic parsing for person re-identification. In ECCV, 346–363, 10.1007/978-3-030-58580-8_21 (Springer International Publishing, 2020).
- 21.Li, X. et al. Counterfactual intervention feature transfer for visible-infrared person re-identification. In ECCV, 381–398, 10.1007/978-3-031-19809-0_22 (Springer International Publishing, 2022).
- 22.Sun, X. & Zheng, L. Dissecting person re-identification from the viewpoint of viewpoint. In CVPR, 608–617, 10.1109/CVPR.2019.00070 (IEEE, 2019).
- 23.Shim, M., Ho, H.-I., Kim, J. & Wee, D. Read: Reciprocal attention discriminator for image-to-video re-identification. In ECCV, 335—350, 10.1007/978-3-030-58568-6_20 (Springer International Publishing, 2020).
- 24.Huang, Y. et al. Beyond scalar neuron: Adopting vector-neuron capsules for long-term person re-identification. IEEE TCSVT30, 3459–3471, 10.1109/TCSVT.2019.2948093 (2020).
- 25.Fan, L. et al. Learning longterm representations for person re-identification using radio signals. In CVPR, 10696–10706, 10.1109/CVPR42600.2020.01071 (IEEE, 2020).
- 26.Zhang, Y., Shi, W., Liu, S., Bao, J. & Wei, Y. Scale-invariant siamese network for person re-identification. In ICIP, 2436–2440, 10.1109/ICIP40778.2020.9191079 (IEEE, 2020).
- 27.Xiang, J., Huang, Z., Jiang, X. & Hou, J. Similarity learning with deep crf for person re-identification. Pattern Recognit.135, 109151, 10.1016/j.patcog.2022.109151 (2023). [Google Scholar]
- 28.Li, C., Liu, M. & Cao, Z. Wihf: Enable user identified gesture recognition with wifi. In IEEE INFOCOM, 586–595, 10.1109/INFOCOM41043.2020.9155539 (IEEE, 2020).
- 29.Zhang, X., Tang, C., Yin, K. & Ni, Q. Wifi-based cross-domain gesture recognition via modified prototypical networks. IEEE Internet Things J.9, 8584–8596, 10.1109/JIOT.2021.3114309 (2022). [Google Scholar]
- 30.Li, B. et al. Two-stream convolution augmented transformer for human activity recognition. AAAI Conf. Artif. Intell.35, 286–293, 10.1609/aaai.v35i1.16103 (2021). [Google Scholar]
- 31.Yang, J., Zou, H. & Xie, L. Securesense: Defending adversarial attack for secure device-free human activity recognition. IEEE Trans. Mob. Comput.23, 823–834, 10.1109/TMC.2022.3226742 (2024). [Google Scholar]
- 32.Yousefi, S., Narui, H., Dayal, S., Ermon, S. & Valaee, S. A survey on behavior recognition using wifi channel state information. IEEE Commun. Mag.55, 98–104, 10.1109/MCOM.2017.1700082 (2017). [Google Scholar]
- 33.Ren, Y., Wang, Y., Tan, S., Chen, Y. & Yang, J. Person re-identification in 3d space: a wifi vision-based approach. In Proc. of USENIX Security, 10.5555/3620237.3620529 (USENIX Association, 2023).
- 34.Hernandez, S. M. & Bulut, E. Lightweight and standalone IoT based WiFi sensing for active repositioning and mobility. In WoWMoM, 277–286, 10.1109/WoWMoM49955.2020.00056 (IEEE, 2020).
- 35.Hernandez, S. M. & Bulut, E. Scheduled spatial sensing against adversarial wifi sensing. In PerCom, 91–100, 10.1109/PERCOM56429.2023.10099079 (IEEE, 2023).
- 36.Barnett, V. & Lewis, T.Outliers in Statistical Data (Wiley, 1994).
- 37.Moore, D. S., McCabe, G. P. & Craig, B. A.Introduction to the Practice of Statistics (W. H. Freeman, 2021).
- 38.Marco, C., Luigi, C., Damiano, D., Gian Luca, F. & Alessio, F. Wi-per81: A benchmark dataset for radio signal image-based person re-identification. figshare10.6084/m9.figshare.26984497 (2025).
- 39.Hadsell, R., Chopra, S. & LeCun, Y. Dimensionality reduction by learning an invariant mapping. In CVPR, vol. 2, 1735–1742, 10.1109/CVPR.2006.100 (IEEE, 2006).
- 40.Simonyan, K. & Zisserman, A. Very deep convolutional networks for large-scale image recognition. In ICLR, 1–14 (ICLR, 2015).
- 41.Huang, G., Liu, Z., Van Der Maaten, L. & Weinberger, K. Q. Densely connected convolutional networks. In CVPR, 2261–2269, 10.1109/CVPR.2017.243 (IEEE, 2017).
- 42.Tan, M. & Le, Q. V. Efficientnet: Rethinking model scaling for convolutional neural networks. In ICML, 6105–6114 (Proceedings of Machine Learning Research, 2019).
- 43.Howard, A. et al. Searching for mobilenetv3. In ICCV, 1314–1324, 10.1109/ICCV.2019.00140 (IEEE, 2019).
- 44.Marco, C., Luigi, C., Damiano, D., Gian Luca, F. & Alessio, F. Wi-per81: A benchmark dataset for radio signal image-based person re-identification. figshare10.6084/m9.figshare.29477087 (2025).
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Custom code for data processing, the neural model implementation, training, and evaluation is provided alongside the dataset and is available at Figshare44. These scripts include functions for loading the CSV files, computing and sanitizing amplitude values, analyzing data, generating signal magnitude heatmaps, and setting up the proposed neural architectures. Furthermore, trained models will be released to ensure the reproducibility of results. Researchers are encouraged to extend these scripts or integrate them into their data processing pipelines to facilitate the adaptation of Wi-PER81 to person Re-ID systems.