Abstract
Driven by the demand for cost-effective vehicle access, enhanced flexibility, and sustainable transportation practices, smart car-sharing has emerged as a prominent alternative to traditional vehicle rental systems. Leveraging the Internet of Vehicles (IoV) and wireless communication, these systems feature dynamic renter-vehicle mappings, enabling users to access any available vehicle rather than being restricted to a specific one pre-assigned by the service provider. However, many existing schemes in the IoV field conflate users and vehicles, complicating the identification and tracking of the vehicle’s actual driver. Moreover, most current authentication protocols rely on a strict, initial binding between a user and a vehicle, rendering them unsuitable for the dynamic nature of car-sharing environments. To address these challenges, we propose an enhanced certificateless signature scheme tailored for smart car-sharing. By employing a biometric fuzzy extractor and the Chinese Remainder Theorem, our scheme provides a fine-grained authentication mechanism that eliminates the need for local computations on the user’s side, meaning users do not require a smartphone or other digital device. Furthermore, our scheme introduces category identifiers to facilitate vehicle selection based on specific classes within car-sharing contexts. A formal security analysis demonstrates that our scheme is existentially unforgeable against adversaries under the random oracle model. Finally, a comprehensive evaluation shows that our proposed scheme achieves competitive performance in terms of computational and communication overhead while offering enhanced practical functionalities.
Keywords: car-sharing, certificateless signature, internet of vehicles, authentication
1. Introduction
The widespread adoption of digital technologies and the development of the Internet of Vehicles (IoV) are driving the transformation of the automotive sector toward intelligent systems [1]. For instance, connected vehicles exchange real-time traffic information through vehicle-to-vehicle communication, while smart parking systems leverage positional data to optimize space allocation. Furthermore, within the framework of intelligent transportation systems, all automotive entities can contribute to optimizing traffic flow and enhancing overall transportation efficiency through global monitoring and data analytics [2,3]. In recent years, driven by the growing demand for cost-effective mobility, smart car-sharing has gained significant traction as an alternative to traditional vehicle rental services [4]. According to a report by Statista Market Insights, global car-sharing revenue is projected to reach approximately USD 13.89 billion in 2025 and is forecast to grow at a compound annual growth rate (CAGR) of 3.23% over the subsequent five-year period [5].
Traditional car rental services require users to book a specific vehicle in advance and retrieve it from a designated depot, a process that is often time-consuming and inconvenient. In contrast, smart car-sharing providers (e.g., Zipcar, Car2Go) offer a more flexible alternative. As illustrated in Figure 1, a typical smart car-sharing workflow begins with vehicles being classified into categories based on their characteristics (e.g., model, capacity) and registered with the service center. After completing registration and payment, users can select any available vehicle within a category that meets their requirements. This model allows individuals to use vehicles on demand, thereby avoiding the costs and responsibilities associated with private car ownership, such as maintenance expenses [6]. Furthermore, compared with public transportation and conventional car rentals, smart car-sharing provides greater flexibility in travel time and destination, as well as more convenient vehicle access [7].
Figure 1.
A general scenario of smart car-sharing.
Despite these benefits, communication in IoV environments relies on wireless channels, which are inherently insecure and susceptible to malicious attacks. Consequently, various authentication schemes [8,9,10] have been proposed for the IoV domain to safeguard against threats such as replay [11] and forgery attacks [12]. However, a prevalent limitation of these protocols is their static binding of users to vehicles, which effectively treats the pair as an inseparable entity. This approach is ill-suited for dynamic car-sharing environments. For instance, when malicious behavior occurs, traditional schemes can typically only identify the specific vehicle involved, not the driver. As a result, preventing the malicious user from accessing other vehicles is a challenging and delayed process, as existing authentication protocols incorporate vehicle-specific, rather than user-specific, information in their computations. In a system characterized by rapid user turnover, this oversight creates a significant security vulnerability.
Furthermore, the high turnover of renters for a single vehicle necessitates schemes with dynamic membership management capabilities. Various approaches have been proposed to achieve this functionality, including the use of area keys [13] and Merkle Hash Trees (MHTs) [14]. However, the former approach is computationally expensive due to the need for individual calculations per user, while the latter incurs significant storage overhead because of the hierarchical structure of hash trees. In contrast, the Chinese Remainder Theorem (CRT) enables efficient and lightweight membership management by maintaining and distributing a global shared secret value through broadcasting, demonstrating advantages in both computational efficiency and storage overhead [15]. Nevertheless, current applications of CRT in the IoV field primarily focus on vehicle-side applications. These implementations often require users to perform computations on their personal digital devices, such as smartphones, which can be impractical or inconvenient for renters in real-world scenarios.
In response to the aforementioned challenges, we propose an enhanced CLS scheme that introduces a fine-grained and user-vehicle decoupled authentication mechanism for smart car-sharing scenarios. Specifically, our scheme employs the fuzzy extractor to securely incorporate user biometric information into the authentication process while eliminating the need for user-side computation. Once a user completes the login procedure, the corresponding vehicle generates a signature embedded with a biometric-derived secret, thereby enhancing authenticity by jointly verifying both the user and the vehicle. Additionally, vehicles within the system are classified into categories, with each assigned a unique identifier. This process enables legitimate users to select and access any available vehicle within their chosen category. Furthermore, we integrate the CRT with user-extracted biometric secrets and facilitate the dynamic revocation of renters in cases of service expiration or malicious behavior. The key contributions of the article are outlined as follows:
-
(1)
We propose an efficient CLS authentication scheme for smart car-sharing scenarios, built upon the fuzzy extractor and the CRT. Compared with existing authentication schemes, our scheme provides decoupled, fine-grained authentication, supports dynamic user revocation, and eliminates computation on the user side.
-
(2)
We introduce a novel category-range authentication framework where vehicles are organized into distinct categories with unique identifiers. This enables users to access any vehicle within an authorized category, instead of a single specific one in most IoV frameworks, thereby enhancing the flexibility and efficiency of the rental process.
-
(3)
We conduct a comprehensive security analysis of our scheme and benchmark its performance against related works. The results demonstrate that our proposal achieves provable security and exhibits competitive overhead in terms of computation, communication, and dynamic membership management.
The remainder of this article is structured as follows: Section 2 reviews the existing related works relevant to our proposed scheme. Section 3 introduces the preliminaries, as well as our system and security models. Section 4 elaborates on the details of our proposed scheme. Subsequently, Section 5 presents the formal security analysis and discusses the security properties of our scheme. In Section 6, we evaluate the performance of our proposed scheme and compare it with other existing schemes. Finally, Section 7 concludes the article.
2. Related Works
Digital signature schemes have been widely adopted in the IoV to secure communication processes. In early approaches based on Public Key Infrastructure (PKI) [16,17], certificates and the corresponding public–private key pairs of the vehicles are issued by a trusted certificate authority (CA). Although the implementation of PKI systems enhances the security level of these schemes, the resource-intensive certificate management process remains a significant concern. To mitigate this issue, subsequent protocols leveraged Identity-Based Cryptography (IBC), which eliminates certificate management overhead by employing a trusted Private Key Generator (PKG) to derive public keys directly from identities [18,19,20]. However, the implementation of PKG also introduces the key escrow problem, which can lead to sensitive information exposure and faulty authentication if the PKG in the scheme is compromised and no longer trusted.
To address the key escrow problem, Al-Riyami and Paterson proposed the concept of certificateless public key cryptography (CL-PKC) [21]. By replacing PKG with a semi-trusted key generation center (KGC) and incorporating random numbers selected by users themselves in the key generation process, certificateless signature (CLS) schemes achieve private key confidentiality, as KGC cannot acquire the complete private key of the participants [22].
Built on the framework of CL-PKC, numerous CLS schemes with varying characteristics have been proposed. For instance, Malip et al. [23] proposed a certificateless anonymous authentication scheme designed to facilitate secure message transmission. Zhong et al. [24] introduced a certificateless aggregate signature scheme (CLAS) incorporating pseudonyms to achieve message authentication and conditional privacy preservation. Wang et al. [25] proposed a novel certificateless authentication scheme and demonstrated its security within the standard model. However, the scheme proposed by Wang et al. was subsequently proven to be insecure [26]. Furthermore, the aforementioned schemes are all based on bilinear mapping, which is computationally intensive, raising significant concerns regarding their efficiency.
To reduce the computational overhead associated with bilinear pairings, schemes based on elliptic curve cryptography (ECC) have been widely proposed [27,28,29,30,31,32]. Ali et al. [33] proposed a certificateless authentication scheme utilizing map-to-point hash functions and short signatures. However, Li et al. [34] later identified that the scheme proposed in [33] is vulnerable against Type-II adversaries and subsequently contributed a new reliable CLAS scheme for VANET. Aiming to solve the weakness of the potential side channel attacks against tamper-proof devices, Xiong et al. [35] proposed a double insurance CLS scheme. Unfortunately, Shim [26] later demonstrated that Xiong’s scheme is susceptible to forgery attacks. Following this, Gong et al. [36] introduced a certificateless authentication protocol, asserting its robustness against both Type-I and Type-II adversaries while claiming superiority over prior schemes in [35,37]. Nevertheless, Wu et al. [38] recently concluded that the scheme by Gong et al. [36] also fails to achieve the claimed resistance against forgery attacks by Type-I adversaries. Crucially, in IoV-based car-sharing scenarios, these schemes focus solely on inter-vehicle authentication while neglecting the essential granular authentications required between users and vehicles, thereby rendering them impractical for dynamic car-sharing applications.
In recent years, numerous schemes have sought to enhance the flexibility of users in IoV by incorporating techniques such as passwords and biometric information [39,40]. Islam et al. [41] proposed a password-based authentication protocol for VANETs that supports the dynamic changes in vehicle membership. Later, Cui et al. [42] introduced an authentication scheme based on the Chebyshev chaotic map, incorporating fuzzy verification and honeywords for rescue scenarios. Regarding the application of biometric information, Azees et al. [43] proposed a hybrid CMOS memristor-based authentication scheme employing bilinear operations, ensuring that only registered users can interact with the vehicle. Wang et al. [44] integrated distance calculation into the biometric authentication process and proposed a fuzzy CLS scheme. Despite these advancements, existing approaches maintain a rigid binding between users and vehicles, preventing users from accessing vehicles beyond their specifically assigned ones. Meanwhile, in smart car-sharing scenarios, it is crucial for service providers to allow renters to access vehicles at their convenience.
A comparative summary of existing schemes is presented in Table 1. The limitations identified therein highlight the need for a practical authentication scheme that decouples users from specific vehicles, thereby better addressing the operational requirements of real-world car-sharing services.
Table 1.
Comparative summary of the existing schemes.
| Scheme | Technologies | Unforgeability | GA a | DB b |
|---|---|---|---|---|
| [33] | ECC, Short signature | Type II weak | ✕ | ✕ |
| [34] | ECC, Registration-based encryption | ✔ | ✕ | ✕ |
| [35] | ECC, Private key double insurance | Type I weak | ✕ | ✕ |
| [36] | ECC, Pseudonym mechanism, Low resource consumption | Type I weak | ✕ | ✕ |
| [41] | ECC, Password-based auth., Vehicle membership alteration | ✔ | ✔ | ✕ |
| [42] | Chebyshev chaotic map, Fuzzy verification, Honeywords | ✔ | ✔ | ✕ |
| [43] | Bilinear mapping, CMOS memristor-based auth. | ✔ | ✔ | ✕ |
| [44] | ECC, Fuzzy extractor, Biometric-based auth. | ✔ | ✔ | ✕ |
✔: The scheme satisfies the feature. ✕: The scheme does not satisfy the feature. a GA: Granular authentication. b DB: Dynamic binding.
3. Preliminaries
In this section, we first provide a concise background explanation of elliptic curve cryptography and the Chinese Remainder Theorem. Then, we introduce the system and security models of our proposed authentication scheme. The symbols used in our scheme are described in Table 2.
Table 2.
Symbols and definitions.
| Symbol | Definition |
|---|---|
| Security parameter | |
| TA | Trust Authority |
| KGC | Key generation center |
| Sharing vehicle | |
| User | |
| s | Secret key of KGC |
| t | Secret key of TA |
| System parameters | |
| Identity of the vehicle | |
| Pseudonym of the vehicle | |
| Identity of the user | |
| Pseudonym of the user | |
| Public key of the vehicle | |
| Private key of the vehicle | |
| Private key of the user | |
| Category identifier | |
| z | Group identifier |
| Signature | |
| Identifier update secret | |
| Timestamp |
3.1. Elliptic Curve Cryptography
In the ECC system, an elliptic curve E is defined by the equation over , where is a finite field defined on a large prime number p. Here, , satisfying the condition . Furthermore, let O represent a point at infinity; then an additive elliptic curve group with order q and the generator P can be defined with O and the points on E.
Elliptic Curve Discrete Logarithm Problem (ECDLP): Given the instance , where and , it is computationally infeasible to obtain a from in probabilistic polynomial time.
3.2. Chinese Remainder Theorem
Let be pairwise coprime positive integers, and let denote arbitrary integers. Then, the system
has a unique solution modulo . Specifically, the solution can be expressed as , where and .
3.3. System Model
In our proposed scheme, four main participants are involved, namely the TA (trust authority), the KGC (key generation center), the SV (sharing vehicle), and the users.
TA: It represents the service center in smart car-sharing, which is a fully trusted authority that generates the system parameters and manages the service membership of users within the system by distributing and updating the group identifier. Moreover, it is also responsible for generating pseudonyms for users and can track and reveal their real identities when malicious behaviors occur.
KGC: It represents a key generation center that generates the partial private keys for vehicles and the private keys for users and is considered to be a semi-trusted third party.
SV: It represents a vehicle in the car-sharing service. In our scheme, SVs are classified into individual categories based on their characteristics (e.g., model and capacity). After an SV is logged in by a legitimate renter via biometric information, it can authenticate with other verified SVs by generating signatures utilizing the derived group identifier.
User: It represents the actual user of the car-sharing service. Additionally, it is important to emphasize that no local computational abilities are required for users in our proposed scheme.
The system model of our proposed scheme is demonstrated in Figure 2. Initially, SVs register with KGC to obtain their partial private keys and category identifiers. Subsequently, users complete the registration process by submitting biometric information to TA. When a legitimate user requires access to a vehicle, they may access any vehicle that shares the same category identifier selected during user registration. Upon successful user login, the vehicle can generate signatures to enable secure authentication with other accessed vehicles. In the event that a malicious user is detected, TA will update the group identifier and broadcast the auxiliary information to process revocation, and legitimate vehicles can obtain the updated group identifier using their identifier update secrets derived from the users.
Figure 2.
The system model of the proposed scheme.
3.4. Security Model
In the field of CLS schemes, two types of attacks are often considered, namely Type-I attacks launched by external adversaries and Type-II attacks launched by internal adversaries [45]. In a Type-I attack, an adversary is able to launch public key replacement attacks but cannot gain access to the master secret key. In contrast, in a Type-II attack, an adversary can acquire the system’s master secret key but cannot replace the public key of any entity.
To demonstrate the security of our proposed scheme, we will prove its existential unforgeability against chosen-message attacks (EUF-CMA). This proof is based on two challenge-response games, each formalizing one of the aforementioned attack scenarios.
Game I: This game is performed by a Type-I adversary and the challenger . The details are as follows:
Setup: runs Setup to generate its master secret key s and the system parameters . Then it sends to and keeps s secret.
Queries: In this phase, can adaptively access the following queries.
-
(1)
Vehicle Registration Query: When receiving this query from with as input, generates the related information for the corresponding vehicle.
-
(2)
User Registration Query: When receiving this query from with as input, generates the related information for the corresponding user.
-
(3)
Reveal Vehicle Partial Key Query: When receiving this query from with as input, returns the corresponding .
-
(4)
Reveal User Private Key Query: When receiving this query from with as input, returns the corresponding .
-
(5)
Reveal Vehicle Secret Query: When receiving this query from with as input, returns the corresponding .
-
(6)
Reveal Vehicle Public Key Query: When receiving this query from with as input, returns the corresponding .
-
(7)
Reveal User Public Key Query: When receiving this query from with as input, returns the corresponding .
-
(8)
Replace Vehicle Public Key Query: When receiving this query from with as input, replaces the public key of the corresponding vehicle with .
-
(9)
Replace User Public Key Query: When receiving this query from with as input, replaces the public key of the corresponding user with .
-
(10)
Sign Query: When receiving this query from with as input, outputs a legitimate signature .
Forgery: In this phase, outputs a signature for the tuple , and wins in this game if the following conditions are satisfied.
Sign Query has never been queried with the submitted tuple.
Reveal User Private Key Query and Replace User Public Key Query have never been queried with the pseudonym by .
is a valid signature for the submitted tuple.
Game II: This game is performed by a Type-II adversary and the challenger . The details are as follows:
Setup: runs Setup to generate its master secret key s and the system parameters . Then it sends and s to .
Queries: In this phase, can adaptively access the following queries.
-
(1)
Vehicle Registration Query: When receiving this query from with as input, generates the related information for the corresponding vehicle.
-
(2)
User Registration Query: When receiving this query from with as input, generates the related information for the corresponding user.
-
(3)
Reveal User Private Key Query: When receiving this query from with as input, returns the corresponding .
-
(4)
Reveal Vehicle Secret Query: When receiving this query from with as input, returns the corresponding .
-
(5)
Reveal Vehicle Public Key Query: When receiving this query from with as input, returns the corresponding .
-
(6)
Reveal User Public Key Query: When receiving this query from with as input, returns the corresponding .
-
(7)
Sign Query: When receiving this query from with as input, outputs a legitimate signature .
Forgery: In this phase, outputs a signature for the tuple , and wins in this game if the following conditions are satisfied.
Sign Query has never been queried with the submitted tuple.
Reveal Vehicle Secret Query has never been queried with the pseudonym by .
is a valid signature for the submitted tuple.
4. Proposed Scheme
In this section, we describe our proposed scheme in detail.
4.1. Setup
First, TA and KGC will initialize the system by generating public and secret parameters.
-
(1)
Given as the security parameter, TA chooses a cyclic group of order q with P as its generator. Then, TA randomly selects and calculates .
-
(2)
Then, TA selects five secure hash functions: , , , , .
-
(3)
KGC randomly selects and calculates .
-
(4)
TA selects n unique prime numbers and calculates . Then, for each , TA calculates , , individually.
-
(5)
Finally, TA calculates and publishes the system parameters, which are denoted as .
4.2. Registration
Every entity, both the SVs and the users, will first complete the registration after system initialization. The registration process includes vehicle registration, user registration, and group identifier distribution.
4.2.1. Vehicle Registration
As demonstrated in Figure 3, when an SV proceeds with registration, it first generates its partial key and transmits its unique identity to KGC. Upon receiving the request, KGC generates the corresponding partial private key and assigns a category identifier to the SV. Later, according to the received information from KGC, SV can complete its public–private key pair.
Figure 3.
The vehicle registration phase of the proposed scheme.
-
(1)
A vehicle first randomly selects and calculates . Then, it sends to TA through a secure channel, where denotes the unique identifier of .
-
(2)
Upon receiving the request from , TA randomly selects and calculates , where is the current timestamp. Consequently, TA transmits to KGC through a secure channel.
-
(3)
After receiving information from TA, KGC randomly selects and calculates , , . Then, based on the characteristics of the vehicle (e.g., model, capacity), KGC assigns an existing or creates a new class identifier to and transmits to through a secure channel. Note that every time after a new class identifier is created and assigned, KGC calculates and discloses it to all the entities within the system.
-
(4)
After obtaining the message from KGC, sets its public key as and its private key as .
4.2.2. User Registration
As presented in Figure 4, when registering, users are required to provide their biometric information. Then, based on the pre-selected category identifier and the pseudonym generated, KGC generates the corresponding credentials, which are consequently encrypted and broadcast to all SVs within the system by TA.
Figure 4.
The user registration phase of the proposed scheme.
-
(1)
With the real user identity , the target category identifier , and the biometric information acquired from , TA first utilizes the fuzzy extractor to calculate . Then, TA randomly selects and calculates , where is the current timestamp. Consequently, TA transmits to KGC through a secure channel.
-
(2)
Upon receiving the data of TA, KGC randomly selects and calculates . Then, KGC calculates the credential for and transmits it to TA via a secure channel, where .
-
(3)
Next, TA randomly selects and an identifier update secret . Then, TA calculates and .
-
(4)
TA calculates , and records the parameters in a list L.
-
(5)
Finally, TA updates with , with and broadcasts through a public channel.
4.2.3. Group Identifier Distribution
To transmit the latest group identifier to all SVs, TA first randomly selects and calculates , , and , where denotes the current timestamp. Later, TA broadcasts to all vehicles within the system.
Upon receiving the message from TA, SVs will first check the freshness of the message. Then, they will verify the authenticity of by checking whether the equation holds. If not, the message will be rejected. Otherwise, SVs will accept the broadcast message and store locally for the subsequent derivation of the group identifier.
4.3. Authentication
By providing the biometric information, registered users can log into any SV within the same pre-selected target category. Subsequently, the authenticated SVs can establish communications with signature generation and verification. The detailed process of the authentication phase is illustrated in Figure 5.
Figure 5.
The authentication process of the proposed scheme.
4.3.1. User Login
Suppose that is requesting to log in to , where the target identifier .
-
(1)
Upon receiving the biometric data from , utilizes the fuzzy extractor to obtain .
-
(2)
Next, calculates , and checks whether the equation holds. If not, rejects the request. Otherwise, succeeds in the login process.
4.3.2. Signing
Prior to generating the signature for message , extracts the group identifier from the locally stored by calculating . Subsequently, proceeds with the signing process, which is detailed as follows:
-
(1)
randomly selects and calculates .
-
(2)
then acquires the hash values by calculating and , where denotes the current timestamp and .
-
(3)
calculates , where denotes the multiplicative inverse of z on .
-
(4)
Finally, constructs the signature and sends the tuple to the receiver.
4.3.3. Verification
Upon receiving the tuple from the sender, , a logged-in SV can verify the signature and proceed with authentication.
-
(1)
Upon receiving the message, vehicle will first check its freshness and will abort it if the timestamp is considered invalid. Then, as mentioned in the signing process, will extract z from stored locally by calculating , where denotes the identifier update secret obtained during the user login phase.
-
(2)
With the received parameters, calculates and .
-
(3)
Finally, checks whether the equation holds. If not, the authentication process fails. Otherwise, accepts as a valid signature from .
4.4. User Logout
When the service of terminates, erases the credentials and sends a logout notification containing ’s information to TA and KGC. Upon receiving the logout message, TA and KGC generate the new credential and identifier update secret for to enable future vehicle usage.
Upon service termination of , randomly selects and calculates and , where denotes the current timestamp. Then, transmits to TA and KGC. When receiving the message, TA and KGC can verify its authenticity by checking whether the equation holds.
After successful verification, based on the received , KGC randomly selects and generates the corresponding credential for with operations described in the User registration section, which are then transmitted to TA.
According to the received information, TA retrieves the relevant parameters from the list L, selects a new identifier update secret , and calculates , where is the current timestamp.
TA then updates the recorded parameters in list L with , which is calculated based on the newly generated .
Finally, TA updates and with , , and broadcasts via a public channel. Additionally, TA performs the operations described in the Group identifier distribution section to prevent potential illegal access with the outdated group identifier.
4.5. Revocation
Upon the detection of irregular behaviors, TA is responsible for revealing the real identity of the malicious user and revoking the corresponding user from the system by generating a new group identifier. Suppose the user to be revoked is .
TA first acquires the corresponding by searching the maintained list L and updates by calculating .
Next, TA randomly selects and calculates , , and , where denotes the current timestamp.
TA then broadcasts to all SVs within the system.
Upon receiving the update message from TA, each SV first checks the timestamp of the message. If the message is fresh, then vehicles will continue to check whether the equation holds. If not, then the update process is aborted. Otherwise, a new group identifier can be calculated with , where denotes the individual identifier update secret held by each SV within the system.
5. Security Analysis
In this section, we first prove the existential unforgeability of our scheme under the random oracle model. Then, we analyze the security features of our scheme utilizing the defined security model.
5.1. Security Proof
The proofs of Theorem 1 and Theorem 2 are based on a security reduction from the ECDLP, as illustrated in Figure 6. Specifically, we design simulators and to interact with two distinct types of adversaries, and , respectively. Given an ECDLP instance provided by the challenger , the simulator engages with the adversary in a simulated environment to produce a forged signature. Subsequently, by applying the Forking Lemma [46,47] is able to obtain a second forgery corresponding to a different random oracle query made by . From these two distinct forgeries, the simulator can extract and output the solution to the given ECDLP instance, thus completing the reduction.
Figure 6.
The construction of the security reduction process.
Theorem 1.
With the hardness assumption of the ECDLP, our proposed ECACS scheme realizes EUF-CMA security against Type-I adversaries under the random oracle model.
The following Lemma 1 concludes the proof of Theorem 1.
Lemma 1.
If there exists a Type-I adversary who can successfully forge a valid signature with obvious advantage , then a simulator can be constructed to solve the ECDLP with non-negligible advantage , where , , and denote the times of User Registration Query, Sign Query, and Query, respectively.
Proof.
For the proof of Lemma 1, the challenger will first set up an ECDLP instance and send it to . Then, will play the following game with in order to acquire the solution to the ECDLP instance. The detailed process is as follows:
Setup: sets and sends the system parameters to . Meanwhile, maintains six lists to record the query results, namely .
Query Stage: In this stage, will adaptively submit the following queries.
- (1)
Hash Query: will respond to the hash queries from as follows:
- (a)
Query: When receiving an hash query with , if , returns . Otherwise, selects , adds the tuple to , and then returns . Note that the and here generally represent a random string and a point on the defined elliptic curve.- (b)
Query: When receiving an hash query with , if , returns . Otherwise, selects , adds the tuple to , and then returns .- (c)
Query: When receiving an hash query with , if the corresponding tuple , then returns . Otherwise, selects , adds to , and then returns .- (d)
Query: When receiving an hash query with , if the corresponding tuple , then returns . Otherwise, selects , adds to , and then returns .- (2)
Vehicle Registration Query: When receives a Vehicle Registration Query from with as input, if exists in , returns ⊥. Otherwise, selects and calculates , and . Then, adds to and to .
- (3)
User Registration Query: When receives a User Registration Query from with as input, if exists in , returns ⊥. Otherwise, continues the game as follows:
- (4)
Reveal Vehicle Partial Key Query: When receives a Reveal Vehicle Partial Key Query from with as input, if the tuple , returns the corresponding . Otherwise, first executes the Vehicle Registration Query with as input and then returns the corresponding .
- (5)
Reveal User Private Key Query: When receives a Reveal User Private Key Query from with as input, if , aborts the game. Otherwise, continues the game as follows:
- (6)
Reveal Vehicle Secret Query: When receives a Reveal Vehicle Secret Query from with as input, returns if . Otherwise, first executes the Vehicle Registration Query with as input and then returns the corresponding .
- (7)
Reveal Vehicle Public Key Query: When receives a Reveal Public Key Query from with as input, if , returns the corresponding . Otherwise, first executes the Vehicle Registration Query with as input and then returns the corresponding .
- (8)
Reveal User Public Key Query: When receives a Reveal User Public Key Query from with as input, if , returns the corresponding . Otherwise, first executes the User Registration Query with as input and then returns the corresponding .
- (9)
Replace Vehicle Public Key Query: When receives a Replace Vehicle Public Key Query from with as input, sets as s new public key and updates the record in .
- (10)
Replace User Public Key Query: When receives a Replace User Public Key Query from with as input, sets as ’s new public key and updates the record in .
- (11)
Sign Query: When receives a Sign Query from with as input, first checks whether and exist in and . If not, first executes the Vehicle Registration Query and User Registration Query with the input identities. Then, after acquiring the corresponding records, continues the game as follows:
Forgery Stage: After all the queries have been made and replied to, outputs a forged signature for the identity-message pair . If , outputs ⊥ and aborts the game. Otherwise, according to the Forking Lemma, can rewind the game process and make output another forged signature by changing the output of . Hence, we have
From the above equations, outputs as the solution to the ECDLP instance.
Let denote the event that the game does not abort in the Query Stage, denote the event that the game does not abort in the Forge Stage, and denote the event that successfully outputs two valid forged signatures in the game. Then the advantage of solving the ECDLP instance can be presented with . Furthermore, we have , , where denotes the times of User Registration Query, denotes the times of Reveal User Private Key Query, and denotes the times of Sign Query.
According to the Forking Lemma, we have , where represents the advantage that can successfully forge a signature, and represents the times of Query.
Therefore, ’s advantage of solving the ECDLP instance is
Thus, if there exists an adversary who can successfully forge a signature with advantage , then can output the solution to the ECDLP instance with probability . □
Theorem 2.
With the hardness assumption of the ECDLP, our proposed ECACS scheme realizes EUF-CMA security against Type-II adversaries under the random oracle model.
The following Lemma 2 concludes the proof of Theorem 2.
Lemma 2.
If there exists a Type-II adversary who can successfully forge a valid signature with obvious advantage , then a simulator can be constructed to solve the ECDLP with non-negligible advantage , where and denote the times of Vehicle Registration Query and Query, respectively.
Proof.
For the proof of Lemma 2, the challenger will set up an ECDLP instance and send it to . Then, will play the following game with in order to acquire the solution to the ECDLP instance. The detailed process is as follows:
Setup: sets and sends s and the parameters to . Meanwhile, maintains six lists to record the query results, namely .
Query Stage: In this stage, will adaptively submit the following queries.
- (1)
Hash Query: answers the Hash Query the same as in Game I.
- (2)
Vehicle Registration Query: When receives a Vehicle Registration Query from with as input, if exists in , returns ⊥. Otherwise, continue the game as follows.
- (3)
User Registration Query: When receives a User Registration Query from with as input, if exists in , returns ⊥. Otherwise, selects and calculates . Then, adds the tuple to and the tuple to , where is selected from the existing records in .
- (4)
Reveal User Private Key Query: When receives a Reveal User Private Key Query from with as input, if the tuple , returns the corresponding . Otherwise, first executes the User Registration Query with as input and then returns the corresponding .
- (5)
Reveal Vehicle Secret Query: When receives a Reveal Vehicle Secret Query from with as input, if , aborts the game. Otherwise, continues the game as follows:
- (6)
Reveal Vehicle Public Key Query: When receives a Reveal Public Key Query from with as input, if , returns the corresponding . Otherwise, first executes the Vehicle Registration Query with as input and then returns the corresponding .
- (7)
Reveal User Public Key Query: When receives a Reveal User Public Key Query from with as input, if , returns the corresponding . Otherwise, first executes the User Registration Query with as input and then returns the corresponding .
- (8)
Sign Query: When receives a Sign Query from with as input, first checks whether and exist in and . If not, first executes the Vehicle Registration Query and User Registration Query with the input identities. Then, after acquiring the corresponding records, continues the game as follows:
Forgery Stage: After all the queries have been made and replied to, outputs a forged signature for the identity-message pair . If , outputs ⊥ and aborts the game. Otherwise, according to the Forking Lemma, can rewind the game process and make output another forged signature by changing the output of . Hence, we have
From the above equations, outputs as the solution to the ECDLP instance.
Let denote the event that the game does not abort in Query Stage, denote the event that the game does not abort in Forge Stage, and denote the event that successfully outputs two valid forged signatures in the game. Then the advantage of solving the ECDLP instance can be presented with . Furthermore, we have , , where denotes the times of Vehicle Registration Query, denotes the times of Reveal Vehicle Secret Query, and denotes the times of Sign Query.
According to the Forking Lemma, we have , where represents the advantage that can successfully forge a signature and represents the times of Query.
Therefore, ’s advantage of solving the ECDLP instance is
Thus, if there exists an adversary who can successfully forge a signature with advantage , then can output the solution to the ECDLP instance with probability . □
5.2. Security Features
In particular, our CLS scheme satisfies the following security objectives: message authenticity and integrity, anonymity, traceability, revocability, and resistance against replay and MITM attacks.
5.2.1. Message Authenticity and Integrity
Based on the existential unforgeability proof presented above, it is computationally infeasible for either Type-I or Type-II adversaries to forge a valid signature. Furthermore, since the corresponding identifier update secrets of revoked users are no longer included in , no revoked user can generate a valid signature with any SV due to the inability to extract the latest group identifier z. Consequently, our proposed scheme ensures both the authenticity and integrity of the transmitted message.
5.2.2. Anonymity
In our proposed scheme, the identities utilized by vehicles and users in the authentication process are pseudonyms generated based on their real identities and TA’s secret key t. Consequently, no adversary can obtain the real identity of any entity without access to TA’s secret key. Hence, our proposed scheme achieves anonymity.
5.2.3. Traceability
When emergencies occur, TA can reveal the real identity of any entity by calculating or . Thus, our proposed scheme meets the requirement of traceability.
5.2.4. Revocability
In the event of a user with unusual behaviors, it is imperative for TA to promptly revoke the user’s ability to process authentication within the system. By updating the group identifier z and distributing it through the application of the Chinese Remainder Theorem, only vehicles authenticated with the current legitimate users can generate valid signatures and perform the verification process. Thus, our proposed scheme effectively supports the revocation feature.
5.2.5. Resistance Against Replay Attacks
In our scheme, the messages transmitted during the signing and verification processes all contain timestamps. Any message that fails to meet the freshness requirements will be rejected. Therefore, our scheme is capable of resisting replay attacks.
5.2.6. Resistance Against MITM Attacks
To launch a man-in-the-middle (MITM) attack, an adversary would first need to forge a valid signature; otherwise, it would not be able to modify the signature it captures. Moreover, based on the existential unforgeability proof provided above, neither Type-I nor Type-II adversaries can forge a valid signature. Therefore, our proposed scheme is resistant to MITM attacks.
6. Performance Evaluation
In this section, we provide the performance comparison between our proposed scheme and the related schemes [48,49,50,51,52,53,54]. Given that practical communications among entities are established over wireless channels, necessitating timely and lightweight information transmission, our evaluation primarily focuses on the calculation time cost and information payload size. Specifically, our evaluation encompasses four key aspects: functional properties, computational overhead, communication overhead, and the revocation feature.
6.1. Experiment Environment
Our experiments are conducted on a Lenovo personal computer (Lenovo Group Ltd., Beijing, China) equipped with an Intel Core i5-9500T 2.20 GHz CPU and 8 GB of RAM. The standard open-source MIRACL Crypto SDK is employed on the Ubuntu 22.04 operating system to implement the cryptographic operations, with the security parameter set to 128 bits to meet the required security standards. The bilinear pairing operations for pairing-based schemes are performed over a Tate pairing-based curve with an embedding degree of 2, while the scalar operations for ECC-based schemes are executed over the secp256r1 curve. The measured results of the operation time cost are presented in Table 3.
Table 3.
Execution time of cryptographic operations.
| Symbol | Meaning | Time (ms) |
|---|---|---|
| Bilinear Pairing | 27.844 | |
| Pairing-based Scalar Multiplication | 9.027 | |
| Pairing-based Point Addition | 0.055 | |
| Scalar Multiplication | 2.632 | |
| Point Addition | 0.018 | |
| Hash to Point Operation | 5.433 | |
| General Secure Hash | 0.001 |
6.2. Functional Properties
The comparison results of the functionalities of our proposed scheme with other state-of-the-art relatives are illustrated in Table 4. While the scheme proposed in [48] achieves unforgeability, its reliance on bilinear pairings incurs substantial computational overhead. Regarding ECC-based schemes, though the schemes proposed in [49,50] support revocation, they overlook the need for a decoupled user authentication phase. The scheme proposed in [54] utilizes passwords and biometric data to realize the authentication processes for users, but it is based on individual relationships between users and vehicles, which lacks the flexibility required in rental scenarios. In contrast, our scheme utilizes the Chinese Remainder Theorem to achieve user revocation. Furthermore, the fuzzy extractor and category identifier mechanism allow our scheme to support both user decoupling and category-range selective authentication. Hence, our scheme demonstrates superior performance under the smart car-sharing situations.
Table 4.
Properties of the related schemes.
| Scheme | Pairing-Free | Unforgeability | Revocation | User Decoupling | Category Range Selection |
|---|---|---|---|---|---|
| [48] | ✕ | ✔ | ✕ | ✕ | ✕ |
| [49] | ✔ | ✔ | ✔ | ✕ | ✕ |
| [50] | ✔ | ✔ | ✔ | ✕ | ✕ |
| [51] | ✔ | ✔ | ✕ | ✕ | ✕ |
| [52] | ✔ | ✕ | ✕ | ✕ | ✕ |
| [53] | ✔ | ✕ | ✕ | ✕ | ✕ |
| [54] | ✔ | ✔ | ✕ | ✔ | ✕ |
| Our scheme | ✔ | ✔ | ✔ | ✔ | ✔ |
✔: The scheme satisfies the feature. ✕: The scheme does not satisfy the feature.
6.3. Computational Overhead
To conduct a comprehensive evaluation, we assess the computational overhead of the schemes by analyzing the time cost associated with signature generation and verification, with the results detailed in Table 5 and Figure 7.
Table 5.
Comprehensive overhead comparison with the related schemes.
Figure 7.
Comparison of the computational overhead of our proposed scheme with related works [48,49,50,51,52,53,54]: (a) signature generation phase; (b) signature verification phase.
For our scheme, the signature generation process involves one scalar multiplication operation and two general secure hash operations, and the computational cost is ms. As for signature verification, our proposed scheme requires four ECC scalar multiplication operations, four ECC point addition operations, and four general secure hash operations, which cost ms. Based on the evaluation, our scheme demonstrates competitive computational efficiency compared with other related schemes. Moreover, our scheme offers additional functionalities, including category-range selection when performing authentication between vehicles and users, as well as the feature of revocation. Therefore, it is reasonable to conclude that our scheme demonstrates outstanding performance in terms of computational overhead.
6.4. Communication Overhead
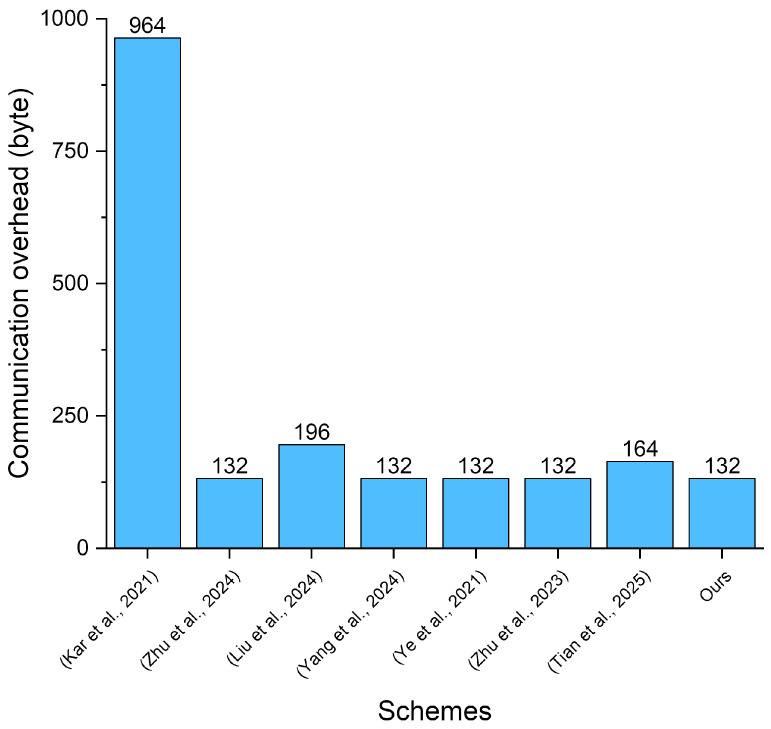
In our evaluation, we measure the communication overhead of the related schemes based on the length of the transmitted signature tuples. To meet the requirements of the security parameter, we set the size of elements in to 384 bytes, the size of elements in to 64 bytes, and the size of elements in to 32 bytes. Considering schemes implying timestamps to resist replay attacks, we set the size of the timestamps to 4 bytes. The comparison results are presented in Table 5 and Figure 8.
Figure 8.
Comparison of the communication overhead of our proposed scheme with related works [48,49,50,51,52,53,54].
In our proposed scheme, the communication overhead for a signature is bytes. As demonstrated in Table 5 and Figure 4, our scheme is superior to the schemes in [48,54] and is at the same low overhead level as the schemes in [49,51,52,53]. Moreover, while maintaining communication efficiency, our proposed scheme realizes enhanced functionality that increases its practicality in real-world scenarios. Therefore, our scheme outperforms the related scheme in the field of communication overhead.
6.5. Revocation Feature
Table 6 presents a comparative analysis of the revocation feature of our proposed scheme against related schemes. Specifically, the schemes in [48,51,53,54] lack the functionality of revocation. Meanwhile, the schemes in [8,52] implement revocation through the use of revocation lists. However, this approach inherently incurs a linear increase in overhead as the system scales and the number of entities grows. Likewise, the revocation mechanism in [50] requires synchronization with the blockchain database, introducing additional latency while still exhibiting linear growth in resource consumption.
Table 6.
Comparison of the revocation feature.
| Scheme | Support Revocation | Method | Overhead Complexity |
|---|---|---|---|
| [48] | ✕ | N/A | N/A |
| [49] | ✔ | Revocation list | Linear |
| [50] | ✔ | Blockchain database | Linear |
| [51] | ✕ | N/A | N/A |
| [52] | ✔ | Revocation list | Linear |
| [53] | ✕ | N/A | N/A |
| [54] | ✕ | N/A | N/A |
| Our scheme | ✔ | CRT | Constant |
✔: The scheme satisfies the feature. ✕: The scheme does not satisfy the feature.
In contrast, our proposed scheme leverages the CRT and achieves revocation by broadcasting the group identifier through public channels, thereby ensuring that revocation efficiency remains independent of system scale. This inherent scalability makes our scheme particularly suitable for large-scale applications.
7. Conclusions
In this paper, we introduced an enhanced certificateless authentication scheme tailored for smart car-sharing environments. By incorporating biometric information and leveraging the Chinese Remainder Theorem for user membership management, our scheme provides a lightweight, decoupled, and fine-grained authentication mechanism between users and vehicles, eliminating the need for user-side computation. The implementation of category identifiers further enhances flexibility, allowing users to access any vehicle within a designated class, which is a feature essential for the dynamic nature of practical car-sharing. A formal security analysis proves our scheme is secure against both Type-I and Type-II adversaries under the random oracle model. Furthermore, performance evaluations demonstrate that our scheme achieves competitive efficiency while delivering significant practical functionalities. Future work will focus on extending this framework to multi-domain environments and developing practical cross-domain authentication protocols.
Author Contributions
Conceptualization, Z.S. and X.K.; methodology, X.K.; validation, X.K. and T.Y.; formal analysis, X.K.; writing—original draft preparation, X.K.; writing—review and editing, Z.S., X.K. and T.Y.; visualization, X.K.; supervision, Z.S.; project administration, Z.S.; funding acquisition, Z.S. All authors have read and agreed to the published version of the manuscript.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
Funding Statement
This research was funded by the National Key R&D Program of China (Grant. 2022YFB3104602).
Footnotes
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
References
- 1.Rajkumar Y., Santhosh Kumar S. A comprehensive survey on communication techniques for the realization of intelligent transportation systems in IoT based smart cities. Peer-Peer Netw. Appl. 2024;17:1263–1308. doi: 10.1007/s12083-024-01627-9. [DOI] [Google Scholar]
- 2.Ji B., Zhang X., Mumtaz S., Han C., Li C., Wen H., Wang D. Survey on the internet of vehicles: Network architectures and applications. IEEE Commun. Stand. Mag. 2020;4:34–41. doi: 10.1109/MCOMSTD.001.1900053. [DOI] [Google Scholar]
- 3.Karabulut M.A., Shah A.S., Ilhan H., Pathan A.S.K., Atiquzzaman M. Inspecting VANET with various critical aspects—A systematic review. Ad Hoc Netw. 2023;150:103281. doi: 10.1016/j.adhoc.2023.103281. [DOI] [Google Scholar]
- 4.Vélez A.M.A. Economic impacts, carbon footprint and rebound effects of car sharing: Scenario analysis assessing business-to-consumer and peer-to-peer car sharing. Sustain. Prod. Consum. 2023;35:238–249. doi: 10.1016/j.spc.2022.11.004. [DOI] [Google Scholar]
- 5.Statista Market Insights Car-Sharing–Worldwide. [(accessed on 26 May 2025)]. Available online: https://www.statista.com/outlook/mmo/shared-mobility/car-sharing/worldwide.
- 6.Huang C., Lu R., Ni J., Shen X. DAPA: A decentralized, accountable, and privacy-preserving architecture for car sharing services. IEEE Trans. Veh. Technol. 2020;69:4869–4882. doi: 10.1109/TVT.2020.2980777. [DOI] [Google Scholar]
- 7.Liu Y., He D., Bao Z., Luo M., Peng C. PEACS: A Privacy-Enhancing and Accountable Car Sharing System. IEEE Internet Things J. 2024;11:16422–16435. doi: 10.1109/JIOT.2024.3353458. [DOI] [Google Scholar]
- 8.Zhu D., Guan Y. Secure and Lightweight Conditional Privacy-Preserving Identity Authentication Scheme for VANET. IEEE Sens. J. 2024;24:35743–35756. doi: 10.1109/JSEN.2024.3431557. [DOI] [Google Scholar]
- 9.Yue Q., Jiang W., Lei H. A lightweight certificateless aggregate signature scheme without pairing for VANETs. Sci. Rep. 2025;15:23663. doi: 10.1038/s41598-025-08656-1. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 10.Rajkumar Y., Kumar S.S. An elliptic curve cryptography based certificate-less signature aggregation scheme for efficient authentication in vehicular ad hoc networks. Wirel. Netw. 2024;30:335–362. doi: 10.1007/s11276-023-03473-8. [DOI] [Google Scholar]
- 11.Mundhe P., Verma S., Venkatesan S. A comprehensive survey on authentication and privacy-preserving schemes in VANETs. Comput. Sci. Rev. 2021;41:100411. doi: 10.1016/j.cosrev.2021.100411. [DOI] [Google Scholar]
- 12.AlMarshoud M., Sabir Kiraz M., Al-Bayatti A.H. Security, privacy, and decentralized trust management in VANETs: A review of current research and future directions. ACM Comput. Surv. 2024;56:1–39. doi: 10.1145/3656166. [DOI] [Google Scholar]
- 13.Wang Y., Liu Y., Tian Y. ISC-CPPA: Improverd-security certificateless conditional privacy-preserving authentication scheme with revocation. IEEE Trans. Veh. Technol. 2022;71:12304–12314. doi: 10.1109/TVT.2022.3194060. [DOI] [Google Scholar]
- 14.Al-Mekhlafi Z.G., Al-Janabi H.D.K., Al-Shareeda M.A., Mohammed B.A., Alshudukhi J.S., Al-Dhlan K.A. Fog computing and blockchain technology based certificateless authentication scheme in 5G-assisted vehicular communication. Peer-Peer Netw. Appl. 2024;17:3703–3721. doi: 10.1007/s12083-024-01778-9. [DOI] [Google Scholar]
- 15.Hou Y., Cao Y., Xiong H., Sun Z., Mumtaz S., Tian D. CASKA-CRT: Chinese remainder theorem empowered certificateless aggregate signcryption scheme with key agreement in IoVs. IEEE Trans. Intell. Veh. 2024;9:6814–6829. doi: 10.1109/TIV.2024.3388724. [DOI] [Google Scholar]
- 16.Raya M., Hubaux J.P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007;15:39–68. doi: 10.3233/JCS-2007-15103. [DOI] [Google Scholar]
- 17.Sun Y., Lu R., Lin X., Shen X., Su J. An efficient pseudonymous authentication scheme with strong privacy preservation for vehicular communications. IEEE Trans. Veh. Technol. 2010;59:3589–3603. doi: 10.1109/TVT.2010.2051468. [DOI] [Google Scholar]
- 18.Di C., Wu W. A Novel Identity-Based Mutual Authentication Scheme for Vehicle Ad Hoc Networks. Wirel. Commun. Mob. Comput. 2022;2022:7881079. doi: 10.1155/2022/7881079. [DOI] [Google Scholar]
- 19.Umar M., Islam S.H., Mahmood K., Ahmed S., Ghaffar Z., Saleem M.A. Provable secure identity-based anonymous and privacy-preserving inter-vehicular authentication protocol for VANETS using PUF. IEEE Trans. Veh. Technol. 2021;70:12158–12167. doi: 10.1109/TVT.2021.3118892. [DOI] [Google Scholar]
- 20.Li Q., Hsu C.F., Raymond Choo K.K., He D. A Provably Secure and Lightweight Identity-Based Two-Party Authenticated Key Agreement Protocol for Vehicular Ad Hoc Networks. Secur. Commun. Netw. 2019;2019:7871067. doi: 10.1155/2019/7871067. [DOI] [Google Scholar]
- 21.Al-Riyami S.S., Paterson K.G. Certificateless public key cryptography; Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security; Taipei, Taiwan. 30 November–4 December 2003; Berlin/Heidelberg, Germany: Springer; 2003. pp. 452–473. [Google Scholar]
- 22.Ma K., Zhou Y., Wang Y., Dong C., Xia Z., Yang B., Zhang M. An efficient certificateless signature scheme with provably security and its applications. IEEE Syst. J. 2023;17:5636–5647. doi: 10.1109/JSYST.2023.3269597. [DOI] [Google Scholar]
- 23.Malip A., Ng S.L., Li Q. A certificateless anonymous authenticated announcement scheme in vehicular ad hoc networks. Secur. Commun. Netw. 2014;7:588–601. doi: 10.1002/sec.760. [DOI] [Google Scholar]
- 24.Zhong H., Han S., Cui J., Zhang J., Xu Y. Privacy-preserving authentication scheme with full aggregation in VANET. Inf. Sci. 2019;476:211–221. doi: 10.1016/j.ins.2018.10.021. [DOI] [Google Scholar]
- 25.Wang H., Wang L., Zhang K., Li J., Luo Y. A conditional privacy-preserving certificateless aggregate signature scheme in the standard model for VANETs. IEEE Access. 2022;10:15605–15618. doi: 10.1109/ACCESS.2022.3147595. [DOI] [Google Scholar]
- 26.Shim K.A. Security analysis of conditional privacy-preserving authentication schemes for VANETs. IEEE Access. 2023;11:33956–33963. doi: 10.1109/ACCESS.2023.3263738. [DOI] [Google Scholar]
- 27.Zheng H., Luo M., Zhang Y., Peng C., Feng Q. A security-enhanced pairing-free certificateless aggregate signature for vehicular Ad-Hoc networks. IEEE Syst. J. 2022;17:3822–3833. doi: 10.1109/JSYST.2022.3220869. [DOI] [Google Scholar]
- 28.Cheng G., Huang J., Wang Y., Zhao J., Kong L., Deng S., Yan X. Conditional privacy-preserving multi-domain authentication and pseudonym management for 6G-enabled IoV. IEEE Trans. Inf. Forensics Secur. 2023;19:10206–10220. doi: 10.1109/TIFS.2023.3314211. [DOI] [Google Scholar]
- 29.Yin D., Gong B. A Lightweight Certificateless Mutual Authentication Scheme Based on Signatures for IIoT. IEEE Internet Things J. 2024;11:26852–26865. doi: 10.1109/JIOT.2024.3389018. [DOI] [Google Scholar]
- 30.Lin H.T., Jhuang W.L. Blockchain-Based Lightweight Certificateless Authenticated Key Agreement Protocol for V2V Communications in IoV. IEEE Internet Things J. 2024;11:27744–27759. doi: 10.1109/JIOT.2024.3400320. [DOI] [Google Scholar]
- 31.Gu Y., Shen L., Gao C., Zhu T. Efficient and Secure Certificateless Aggregate Signature Scheme in Vehicle Networks. Netinfo Secur. 2024;24:188–202. [Google Scholar]
- 32.Genc Y., Aytas N., Akkoc A., Afacan E., Yazgan E. ELCPAS: A new efficient lightweight certificateless conditional privacy preserving authentication scheme for IoV. Veh. Commun. 2023;39:100549. doi: 10.1016/j.vehcom.2022.100549. [DOI] [Google Scholar]
- 33.Ali I., Chen Y., Ullah N., Kumar R., He W. An efficient and provably secure ECC-based conditional privacy-preserving authentication for vehicle-to-vehicle communication in VANETs. IEEE Trans. Veh. Technol. 2021;70:1278–1291. doi: 10.1109/TVT.2021.3050399. [DOI] [Google Scholar]
- 34.Li X., Yin X., Ning J. RelCLAS: A Reliable Malicious KGC-Resistant Certificateless Aggregate Signature Protocol for Vehicular Ad Hoc Networks. IEEE Internet Things J. 2023;10:21100–21114. doi: 10.1109/JIOT.2023.3285402. [DOI] [Google Scholar]
- 35.Xiong W., Wang R., Wang Y., Zhou F., Luo X. CPPA-D: Efficient conditional privacy-preserving authentication scheme with double-insurance in VANETs. IEEE Trans. Veh. Technol. 2021;70:3456–3468. doi: 10.1109/TVT.2021.3064337. [DOI] [Google Scholar]
- 36.Gong Z., Gao T., Guo N. PCAS: Cryptanalysis and improvement of pairing-free certificateless aggregate signature scheme with conditional privacy-preserving for VANETs. Ad Hoc Netw. 2023;144:103134. doi: 10.1016/j.adhoc.2023.103134. [DOI] [Google Scholar]
- 37.Ali I., Hassan A., Li F. Authentication and privacy schemes for vehicular ad hoc networks (VANETs): A survey. Veh. Commun. 2019;16:45–61. doi: 10.1016/j.vehcom.2019.02.002. [DOI] [Google Scholar]
- 38.Wu W., Ye F. IPCAS: An improved conditional privacy-preserving certificateless aggregate signature scheme without bilinear pairing for VANETs. J. Syst. Archit. 2024;152:103175. doi: 10.1016/j.sysarc.2024.103175. [DOI] [Google Scholar]
- 39.Paliwal S., Cherukuri A.K., Gao X.Z. Dynamic private Modulus based password conditional privacy preserving authentication and key-agreement protocol for VANET. Wirel. Pers. Commun. 2022;123:2061–2088. doi: 10.1007/s11277-021-09228-y. [DOI] [Google Scholar]
- 40.Roeschlin M., Vaas C., Rasmussen K.B., Martinovic I. Bionyms: Driver-centric message authentication using biometric measurements; Proceedings of the 2018 IEEE Vehicular Networking Conference (VNC); Taipei, Taiwan. 5–7 December 2018; pp. 1–8. [Google Scholar]
- 41.Islam S.H., Obaidat M.S., Vijayakumar P., Abdulhay E., Li F., Reddy M.K.C. A robust and efficient password-based conditional privacy preserving authentication and group-key agreement protocol for VANETs. Future Gener. Comput. Syst. 2018;84:216–227. doi: 10.1016/j.future.2017.07.002. [DOI] [Google Scholar]
- 42.Cui J., Liu X., Zhong H., Zhang J., Wei L., Bolodurina I., He D. A Practical and Provably Secure Authentication and Key Agreement Scheme for UAV-Assisted VANETs for Emergency Rescue. IEEE Trans. Netw. Sci. Eng. 2024;11:1454–1468. doi: 10.1109/TNSE.2023.3323972. [DOI] [Google Scholar]
- 43.Azees M., Rajasekaran A.S., Vijayakumar P., Karuppiah M. Hybrid CMOS Memristor Based Biometric OBU Authentication and Anonymous Mutual Authentication for Secure Communication in Fog-Based VANETs. IEEE Trans. Intell. Transp. Syst. 2024;25:11117–11129. doi: 10.1109/TITS.2024.3378724. [DOI] [Google Scholar]
- 44.Wang L., Xu J., Qin B., Wen M., Chen K. An Efficient Fuzzy Certificateless Signature-Based Authentication Scheme Using Anonymous Biometric Identities for VANETs. IEEE Trans. Dependable Secur. Comput. 2025;22:292–307. doi: 10.1109/TDSC.2024.3392470. [DOI] [Google Scholar]
- 45.Huang X., Mu Y., Susilo W., Wong D.S., Wu W. Certificateless signatures: New schemes and security models. Comput. J. 2012;55:457–474. doi: 10.1093/comjnl/bxr097. [DOI] [Google Scholar]
- 46.Pointcheval D., Stern J. Security arguments for digital signatures and blind signatures. J. Cryptol. 2000;13:361–396. doi: 10.1007/s001450010003. [DOI] [Google Scholar]
- 47.Bellare M., Neven G. Multi-signatures in the plain public-key model and a general forking lemma; Proceedings of the 13th ACM Conference on Computer and Communications Security; Alexandria, VA, USA. 30 October–3 November 2006; pp. 390–399. [Google Scholar]
- 48.Kar J., Liu X., Li F. CL-ASS: An efficient and low-cost certificateless aggregate signature scheme for wireless sensor networks. J. Inf. Secur. Appl. 2021;61:102905. doi: 10.1016/j.jisa.2021.102905. [DOI] [Google Scholar]
- 49.Zhu Y., Zhou Y., Wang J., Yang B., Zhang M. A Lightweight Cross-Domain Direct Identity Authentication Protocol for VANETs. IEEE Internet Things J. 2024;11:37741–37757. doi: 10.1109/JIOT.2024.3438257. [DOI] [Google Scholar]
- 50.Liu X., Wang L., Li L., Zhang X., Niu S. A Certificateless Anonymous Cross-Domain Authentication Scheme Assisted by Blockchain for Internet of Vehicles. Wirel. Commun. Mob. Comput. 2022;2022:3488977. doi: 10.1155/2022/3488977. [DOI] [Google Scholar]
- 51.Yang X., Li S., Yang L., Du X., Wang C. Efficient and Security-Enhanced Certificateless Aggregate Signature-Based Authentication Scheme With Conditional Privacy Preservation for VANETs. IEEE Trans. Intell. Transp. Syst. 2024;25:12256–12268. doi: 10.1109/TITS.2024.3367925. [DOI] [Google Scholar]
- 52.Ye X., Xu G., Cheng X., Li Y., Qin Z. Certificateless-Based Anonymous Authentication and Aggregate Signature Scheme for Vehicular Ad Hoc Networks. Wirel. Commun. Mob. Comput. 2021;2021:6677137. doi: 10.1155/2021/6677137. [DOI] [Google Scholar]
- 53.Zhu F., Yi X., Abuadbba A., Khalil I., Huang X., Xu F. A security-enhanced certificateless conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2023;24:10456–10466. doi: 10.1109/TITS.2023.3275077. [DOI] [Google Scholar]
- 54.Tian J., Wang Y., Shen Y. A Security-Enhanced Certificateless Anonymous Authentication Scheme with High Computational Efficiency for Mobile Edge Computing. IEEE Trans. Netw. Serv. Manag. 2025;22:3555–3572. doi: 10.1109/TNSM.2025.3563637. [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Data are contained within the article.