Abstract
The evolution of aposematism is considered to be a major evolutionary problem because if new aposematic forms emerged in defended cryptic populations, they would face the dual problems of rarity and conspicuousness. We argue that this commonly assumed starting point might not have wide validity. We describe a novel evolutionary computer model in which prey evolve secondary defences and become conspicuous by moving widely over a visually heterogeneous habitat. Unless crypsis imposes high opportunity costs (for instance, preventing prey from efficient foraging, thermoregulation and communication), costly secondary defences are not predicted to evolve at all. However, when crypsis imposes opportunity costs, prey evolve secondary defences that facilitate raised behavioural conspicuousness as prey exploit opportunities within their environment. Optimal levels of secondary defence and of behavioural conspicuousness increase with population sizes and the costs imposed by crypsis. When prey are already conspicuous by virtue of their behaviours, the evolution of aposematic appearances (bright coloration, etc.) is much easier to explain because aposematic traits add little further costs of conspicuousness, but can bring large benefits.
Keywords: aposematism, crypsis, predator, frequency-dependent selection, secondary defence
1. Introduction
A. R. Wallace originally invented the concept now known as aposematism to describe prey that combine warning displays with secondary defences (Wallace 1867, 1889). More than a century later, the evolution of aposematism remains a remarkably fertile and controversial area of research (Ruxton et al. 2004). Warning displays are still of interest to researchers, in part, because the proximate mechanisms by which they operate tell us much about predator behaviour and predator–prey coevolution. As originally envisaged by Wallace (1867) and Poulton (1890), warning displays function to enhance discrimination, to accelerate learning and perhaps slow down forgetting.
However, aposematic displays remain the focus of considerable attention because, for many researchers, their initial origins contain at least two important evolutionary paradoxes. First, it is generally assumed that before the first aposematic traits evolved, prey were both highly cryptic and had effective secondary defences. If secondary defences are costly (and they often are—see Ruxton et al. (2004)), then their presence in prey already highly protected by crypsis is paradoxical: why pay for repellent secondary defences if your enemy rarely finds you (Speed & Ruxton 2002)? Second, there is a better-known paradox of warning signals, which also emerges from commonly held assumptions about initial conditions. Ever since the seminal theoretical model of Harvey et al. (1982), it is widely taken that aposematic mutants must emerge from defended cryptic species (Sillén-Tullberg & Bryant 1983; Sundberg 1987; Alatalo & Mappes 1996; Yachi & Higashi 1998; Lindström et al. 1999; Servedio 2000; Brodie & Agrawal 2001; Speed 2001; Sherratt 2002; Sherratt & Beatty 2003; Thomas et al. 2003; Franks & Noble 2004). When this is the case, new aposematic forms suffer combined and highly effective barriers to survival because of their rarity and their conspicuousness.
This second problem can be easily illustrated with a simple example. In a scenario in which a prey passes a predator during a specified period, a new rare aposematic mutant has a high chance of being detected (e.g. 0.5). Because the aposematic form is rare and unfamiliar, it may also have a high probability of attack given detection (say p=1), giving a high overall chance that the prey does not survive the period (0.5×1=0.5). By contrast, the much more numerous cryptic conspecific has a lower probability of detection (e.g. 0.15), and probability of an attack given detection is also lower (e.g. 0.6), because the prey is relatively familiar. Hence, for the common and familiar cryptic conspecific the probability of death during the period is much smaller (0.6×0.15=0.09) than for a rare, conspicuous conspecific.
Given such strong frequency-dependent selection against a new aposematic form, it seems remarkable that such prey could evolve at all. However, aposematism patently exists and is common in the natural world. In addition, the benefits of aposematic display to very common aposemes may be very large. Imagine, for example, that the probability of detection remains at 0.5, but that because of accurate discrimination, fast learning, etc. attack given detection is only 0.01, now the aposematic prey has a greater likelihood of survival (i.e. probability of death is now 0.005, less than for its cryptic conspecifics).
Hence, the initial evolution of aposematism provides an important evolutionary challenge that has been taken up by several researchers who have used laboratory and theoretical simulations to explain the evolution of conspicuousness via the ‘rarity and conspicuousness’ scenario (reviewed in Speed 2003). Most explanations use a combination of predator psychology (wariness of novel foods, learning, memorability and biased generalization) and prey population structures (especially spatial clumping and structures conducive to random drift). Nonetheless, several authors from Poulton (1890) onwards have suggested alternative routes, which may be more feasible. These include sexual selection (and other forms of pre-adaptation, in which existing traits are turned into aposematic traits when a secondary defence arises; Mallet & Singer 1987) and facultative aposematism (in which aposematic displays are only manifest at high densities; Sword 2002).
In this paper, however, we focus on the validity of the commonly used ‘cryptic and defended’ starting point. We argue that if defences are costly and crypsis is already highly effective, secondary defences are unlikely to exist, except by pre-adaptation. Alternatively, defences may evolve because they facilitate environmental exploitation, allowing prey to use important opportunities in their environments, often in direct view of predators. In the main part of this paper, we evaluate how defences and a form of ‘behavioural conspicuousness’ may evolve when crypsis imposes opportunity costs. To do this we present a novel stochastic evolutionary model. Subsequently, we argue that if prey without evolved aposematic displays are quite conspicuous anyway, the subsequent evolution of aposematic traits are then quite easy to explain.
1.1 Costs of crypsis and the evolution of secondary defence
We assume that the conspicuousness of a prey (and also the effectiveness of its crypsis) has two components that we treat as independent: external appearance and behaviour. Both components may incur costs. Thus, to match a particular background (or otherwise generate a cryptic appearance) a prey may have to forgo external characteristics that could, for example, enhance thermoregulatory efficiency (e.g. dark, black patches), and facilitate social/sexual signalling and aposematic display. Similarly, crypsis may incur opportunity costs by constraining the full range of an animal’s behaviour (see the excellent discussion in Stamp & Wilkens (1993)). Crypsis may be incompatible with movement across microhabitats from which significant benefits can be obtained (here termed ‘environmental exploitation benefits’). Hiding under a rock may provide excellent protection from predation, but can prevent essential behaviours such as effective foraging, thermoregulation, mating, communication and parasite avoidance (Dunham & Tierney 1983; Stamp & Wilkens 1993; Lindquist & Hay 1996; Moses & Sih 1998; Carrascal et al. 2001). Hence, to greater or lesser extents, crypsis is costly because of the constraints it places both on appearance and on behaviour (and see related discussion in Wiklund & Sillén-Tullberg (1985); Merilaita & Tullberg (2005)).
The trade-off between behaviour and environmental exploitation is well known in parts of the literature on foraging and it is not our intention here to repeat detailed modelling of spatial distribution of animals (Abrams 1991; Sih 1992; Grand 2002). Instead, we first describe a model that evaluates the importance of determinants of variation in ‘behavioural conspicuousness’ and then, in our discussion, apply the predictions of the model to the problem of aposematic evolution.
1.2 A model
We consider a prey population with a very simple life-history strategy: asexual reproduction occurring in discrete generations. The generation time T is fixed, taking a value of 100 unless otherwise stated. After this time, all survivors reproduce (clonally) then die, their progeny beginning a new generation.
Individual prey items all have the same appearance but can potentially differ in two heritable characteristics: their ‘behavioural conspicuousness’ to predators (C) and their level of defence (D), such that the genotype of individual i is fully specified by the pair {Ci,Di}.
Ci can be interpreted as the rate at which individual i encounters the predator. For simplicity, we assume that the locality within which predators and prey exist varies continuously along a single visual dimension (see illustration in figure 1) and hence, other things being equal, the value of Ci is set by the average degree of contrast between the prey and its chosen backgrounds within the habitat. The background is assumed to be sufficiently heterogeneous that for prey of fixed appearance crypsis is not compatible with comprehensive use of the habitat (cf. Merilaita et al. 1999). We run the model with a single predator, but our results are not sensitive to this assumption.
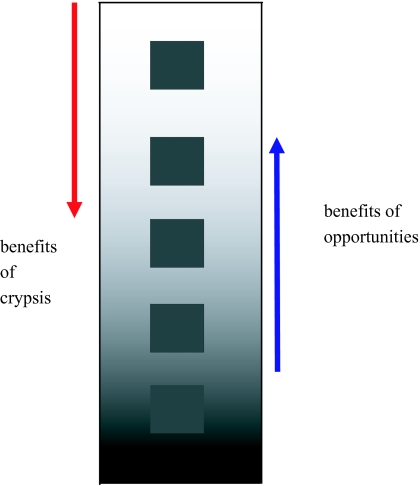
Figure 1.
Illustration of the prey’s conspicuousness against a background. We assume that the habitat’s background varies continuously along a single dimension, so that as the prey moves over more backgrounds it becomes more conspicuous. Benefits to a prey increase to a maximum gained if it divides its time evenly across the whole range of backgrounds. In this illustration we arbitrarily choose an initially dark prey (squares) that matches dark areas of the habitat. However, the assumption is that the costs of conspicuousness are similar regardless of the initial coloration of the prey along this stimulus dimension.
We assume a non-zero lower bound to Ci, such that even maximally cryptic prey (those that stay in one locality of the habitat in which they match the background very closely) can be detected by the predator, albeit at a low rate. As a default, we set this minimum (Cmin) to 0.0005, so that the expected time for the predator to find an individual, maximally cryptic prey item is 20 times the generation time T. We begin each generation at time t=0, with a fixed initial number of individual prey items N1. We first calculate the time (t1) until the predator first encounters a prey item. This is simply a random number drawn from a negative exponential distribution with mean value equal to the inverse of the total encounter rate with all prey alive at that time:
We then move forward to time t=t1, and stochastically select the prey individual that the predator encounters. The probability that individual i is the one encountered is based on the relative conspicuousness of that individual: specifically this probability (Pi) is given by
When the predator encounters individual i, the outcome is dependent on the defence level of that individual, Di, in two ways. First, the time taken in the encounter increases with defence level. For simplicity we define defence in this manner: if the predator encounters an individual with defence level Di, then it takes a time Di for the interaction with that prey item to be concluded. During this time, no encounters with other prey items can occur. This can be interpreted in several ways. For example, Di can be the time needed to overcome a physical defence such as spines or a tough integument. Alternatively, Di can be interpreted as the time needed to recover physiologically from ingested toxins during which searching for prey is curtailed. If the value of Di increases then the probability that a focal individual will be attacked over the season declines. This provides the kind of selective environment we need to simulate prey evolution, so that poor secondary defences make a species vulnerable to predation after detection. However it is interpreted, if the first prey encountered (after time t1) is individual i, then that encounter takes a further time Di, so the predator begins looking for further prey at time t=t1+Di.
A second outcome of variation in prey defence is variation in the probability of prey survival. In some simulations we assume that any attack leads to death of the prey. However, in others Di determines whether individual i survives the encounter with the predator (cf. Wiklund & Järvi 1982). We expect that probability of surviving an encounter Si should increase with Di, and assume the functional form
for some positive constant s. The survivorship of a given encounter is determined stochastically. However, increasing values of the survivorship constant s are associated with improved survival. Unless otherwise specified, we assume that s=0.5. This means that if there is no investment in defence, then the probability of surviving an attack is zero, rising to 5% if Di=0.1, 22% if Di=0.5 and 40% if Di=1.
If the first prey item encountered in a given generation survives, then the number of prey items from which the second encountered individual will be randomly drawn remains unchanged (N2=N1), otherwise the first encountered individual will be removed from the population and N2=N1−1 remain. We then proceed to calculate the further time until the predator encounters a second prey item, drawn stochastically from the appropriate negative exponential distribution:
The identity of that individual is also obtained stochastically as before, using the probabilities
The duration and outcome of this second interaction is determined stochastically, exactly as for the first interaction. We continue in this fashion until the end of the generation (i.e. when time t>T). At this point there will be some number of individuals surviving, Ni. We will select N1 progeny from these, to begin the next generation (resetting t to zero again). We assume that the reproductive ability of individual i (Ri) decreases with its level of defence (representing the idea that defences are costly), and may increase with conspicuousness (representing opportunity costs). We will define the exact functional form of Ri later. The probability that individual i is the parent of the jth offspring is simply
An individual is selected randomly (with replacement) independently to be a parent for each of the N1 offspring. The genotype of offspring j {Cj,Dj} will be determined in part stochastically and in part by the genotype of its parent {Ci,Di}. If we assume that the values C and D can take are continuous, then we assume that individuals inherit their parent’s value of a given characteristic plus a small perturbation drawn from the uniform distributions [−εc,εc] and [−εd,εd], subject to resampling to ensure that C and D values remain above their minimum values. For C we assume a non-zero Cmin (see above) and εc=0.0001; For D we assume that all non-negative values are possible and εc=0.01.
To run a simulation, the number of individuals at the start of a generation N1 must be specified, and {Ci, Di} values given to all these individuals. We assume N1=300 as a default, and that the population starts with C values distributed evenly between Cmin and 1.1Cmin. D values are initially distributed uniformly between 0 and 0.01. That is, the population begins with individuals that are close to maximally cryptic and do not invest substantially in defence. Simulations generally run for 104 generations over which we expect the distribution of C and D values to settle down to equilibrium values (regardless of the starting values); periodic checks have shown that for the parameter values used this is the case.
We assume that the costs of defence and release from the opportunity costs of crypsis act independently on reproductive ability so that Ri(Di,Ci) can be decomposed into a product of two functions f(Di) and g(Ci). An appropriate form for f might be a simple negative exponential
for some positive constant CD. Increased costs of defence are represented by increasing CD. This clearly has the property that increasing investment in defence (increasing Di) reduces reproductive ability Ri. As a default, we give DC a value of 0.1, such that f is 1 when Di=0, dropping to 0.9 when Di=1 and 0.37 when Di=10.
The function g could also have an exponential form:
where α and β are positive constants. The constant α lies between zero and one and can be seen as describing maximum contribution that saving opportunity costs of crypsis can make to reproductive ability. For example, if α=0.2 then the benefits of giving up crypsis contribute 20% of the reproductive ability of a (highly conspicuous) maximally reproductive individual. The other parameter β controls how quickly this benefit from saving the opportunity costs of crypsis is felt with increasing conspicuousness levels. We set β=400; thus when C=10Cmin=0.005, then 83% of the benefits of increased conspicuousness can be collected.
2. Results
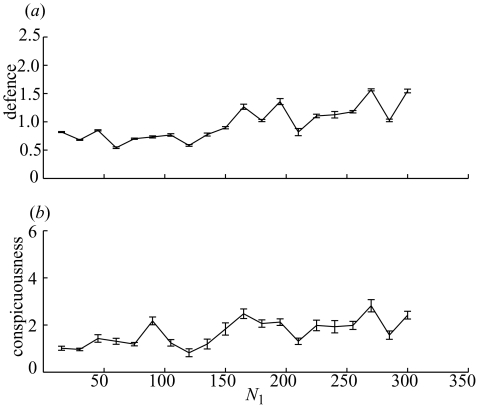
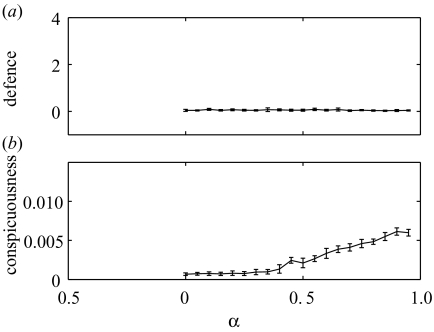
To explore the effects of opportunity costs on the evolution of conspicuousness and defence, we hold all other parameters at their default values and vary the benefit of giving up crypsis (α). The model predictions can be seen in figure 2 for situations in which survival after an attack (Si) is related to the level of prey defence Di. When α=0, and there are no opportunity costs of crypsis, then the evolutionarily stable strategy is to be maximally cryptic and invest little in defence. This remains generally true for low values of opportunity costs (α values less than 0.4 in figure 2). However, for substantial opportunity costs, the population evolves to levels of conspicuousness significantly higher than those associated with maximal crypsis (Cmin=0.0005). This occurs because although increasing conspicuousness increases an individual’s risk of being attacked by the predator, this becomes a price worth paying when there are substantial opportunity costs to crypsis. If the more conspicuous individual survives, then it has a reproductive advantage over less conspicuous survivors. However, because the risk of being attacked increases linearly with increasing conspicuousness and the benefits of crypsis saturate, the population does not evolve ever higher levels of conspicuousness, but rather settles to an equilibrium where the costs and benefits of conspicuousness are most advantageously traded off. This equilibrium value increases as α (and so the opportunity costs of crypsis) increase.
Figure 2.
The mean and standard deviation (across the population) of the (a) defensive investment (Di) and (b) conspicuousness (Ci) of individual in the population at the 104 generation, as a function of the parameter controlling the benefits of conspicuousness (α).
When α is 0.5, and so a maximally cryptic individual that survives has only 50% of the reproductive capability of a maximally conspicuous individual, then the population average value of conspicuousness is over five times that of a maximally cryptic individual. However, interestingly, the increase in conspicuousness is mirrored by an increase in investment in defence as α increases. This occurs because investment in defence is more attractive for individuals that are more conspicuous and so more likely to encounter the predator. The more conspicuous an individual is, the more attractive investment in defence becomes. The reproductive cost of investment in defence means that there is not continual evolution towards ever-higher levels of defence. Investment is relatively modest in figure 2, with average values of D rising to approximately 3 when opportunity costs of crypsis are very high. A value of 3 for Di gives a 78% chance of surviving an attack at a cost of a 26% reduction in reproductive ability (in the order of costs shown by Hetz & Slobodchikoff (1990)). These results are qualitatively unchanged by changes to the exact values given to various model parameters.
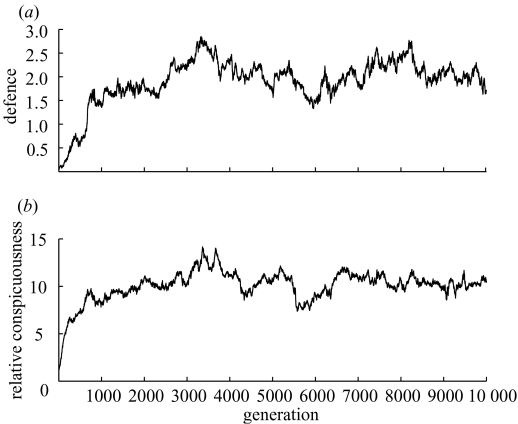
We can see a general trend of increasing conspicuousness and defence with increasing opportunity costs of crypsis, and this leads to a strong positive correlation between conspicuousness and defence. Note that although the overall trend of increasing defence with increasing opportunity costs of crypsis is clear from figure 2, the rise appears not to be monotonic. For example, there is a slight decrease in defence as α rises from 0.5 to 0.55. This is an artefact of figure 2, showing a snapshot of the state of the population at generation 104. The small population size and stochastic nature of the model means that the population levels of both defence and conspicuousness do fluctuate a little over time, although figure 3 illustrates that this fluctuation is relatively minor, and after an initial phase of rapid evolution in the first 1000 generations, the system remains relatively settled.
Figure 3.
The mean levels of (a) defence (Di) and (b) relative conspicuousness (Ci/Cmin) for each generation for a realization of the model with α=0.55.
Reduction in the population size (from N1=300) has the effect of lowering optimal levels of defence and conspicuousness (figure 4). This result is perhaps predictable, because the level of inhibition of predator attacks is reduced as the size of the prey population decreases; hence conspicuousness becomes more costly in smaller populations.
Figure 4.
As figure 2 except that α is fixed at 0.5 and the maximum population size (N1) is varied between simulations.
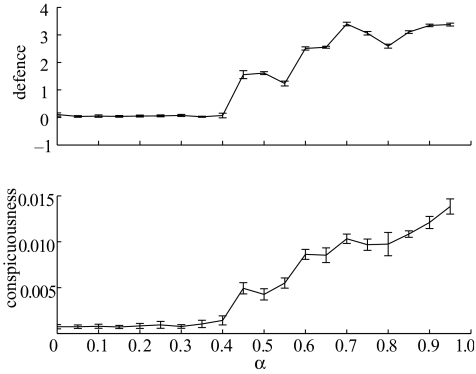
If defences confer no survival advantage to an individual when attacked by a predator (Si=0), then we anticipate that they will not evolve, because, as Fisher originally pointed out, kin selection would be necessary for such defences to evolve as adaptations (Fisher 1930). Our model confirms Fisher’s argument. Without kin-structuring secondary defences that provide no direct individual protection only exist in the population as a result of random drift in a small population and high levels of mutation. Such secondary defences do not therefore evolve adaptively in response to increases or decreases in the opportunity costs of crypsis (i.e. variation in α; figure 5). Nonetheless, even without selection for secondary defence prey do vary their optimal rates of conspicuousness, especially for values of α greater than 0.4, albeit to lowered maximum levels (figures 2 and 5). Comparison of figures 2 and 5 shows that although evolved defences are not necessary for prey to raise their optimal level of behavioural conspicuousness, they are necessary for behavioural conspicuousness to reach high optimal levels.
Figure 5.
Identical simulations to those of figure 2 except that we assume that all attacked prey (regardless of their level of defence) are killed by the predator (Si=0).
3. Discussion
We consider first the evolution of secondary defences and then the evolution of conspicuousness and aposematic signalling.
3.1 Evolution of secondary defences
Because both behavioural conspicuousness and levels of secondary defence are allowed to evolve in this system, we can see that both traits are optimized in relation to, and vary with, the benefits that can be gained by forgoing high levels of crypsis (defined by α and β in the model). In our simulations, costly secondary defences evolved primarily because they facilitated exploitation of opportunities within a visually heterogeneous habitat (Bakus 1981). Within the parameters of our model, optimal investment in defences generally increased with the value of environmental benefits (or, alternatively, increased with the opportunity costs of crypsis) and with the size of the prey population, provided they conferred a survival benefit to individuals during an attack. Hence the presence of a costly secondary defence in highly cryptic prey, as so often assumed in theoretical models of aposematism (reviewed in Ruxton et al. (2004)), is unstable within the parameters of our system.
In the only other published model that, to our knowledge, considers the combined evolution of secondary defences and conspicuousness (the seminal Evolutionary Stable Strategy model described by Leimar et al. (1986)), a similar conclusion about the instability of costly secondary defences in highly cryptic prey was drawn. In the model described by Leimar et al. (1986), it becomes optimal for prey to invest in secondary defences when crypsis is degraded because the number of predators and/or the duration of exposure to predators increases. Though they did not include opportunity costs of crypsis in their model, Leimar et al. (1986) suggested that ‘when a species shifts from profitable to unprofitable, some major change in conditions should have preceded the shift’ (p. 481). In our evolutionary simulations this would be consistent with increases in the opportunity costs of crypsis, giving prey ecological reason to invest in secondary defences (cf. Guilford 1988). Leimar et al. (1986) further suggest that a switch from nocturnal to diurnal activity might provide sufficient cause for unprofitability to evolve. Even within daylight conditions in aquatic and terrestrial environments there may still be many opportunities lost to prey without suitable secondary defences (Schmidt 1990; Lindquist & Hay 1996).
Another important possibility is that highly cryptic prey are pre-adapted to the generation of secondary defences, for instance because they happen to produce chemicals repellent to predators. Potential examples include chemicals used in sexual communication mechanisms, in the subjugation of prey, anti-parasite/parasitoid defences, antimicrobial properties, wetting or waterproofing agents and intraspecific conflict (Whitman et al. 1990; Weller et al. 1999). Similarly, certain morphological traits such as spines or tough skins may have primary functions other than predator deterrence (such as interspecific aggression, protection from abrasion, etc.), but may also aid in survival from predation, in which case a prototype secondary defence exists without additional costs. The possibility of pre-adaptation may explain several instances of the initial evolution of chemical secondary defences. However, we note that pre-adaptation to generation of secondary defence is compatible with the expansion of habitat to use environmental opportunities (cf. discussion in Guilford (1988)). Furthermore, if prototype secondary defences that exist because of pre-adaptation require investment to maximize their effectiveness as defences, then optimization of the effectiveness of the defence will occur in a manner similar to that simulated here.
3.2 Behavioural conspicuousness and the evolution of aposematic displays
The central aim of our paper is to demonstrate that the common assumption that aposematic displays evolved in initially cryptic populations is unlikely; hence explaining the initial evolution of aposematism is not a major evolutionary problem. Species that are behaviourally conspicuous are good candidates for the evolution of novel aposematic displays. Consider an extreme case in which individuals with secondary defences in an ancestral population are already very highly conspicuous by virtue of their behaviours; changes in their appearance can now have little further effect on their risk of detection and in these circumstances aposematic displays can add few extra costs of conspicuousness.
Suppose that we measure both behavioural conspicuousness (cb) and conspicuousness by individual appearance (ca) on a scale between zero and one, such that overall conspicuousness ct is, for simplicity, defined in a linear fashion, e.g. ct=cb+ca(1−cb); then if cb is high, 0.9, the effect of wide variation in ca on the value of overall conspicuousness is necessarily small. By contrast, if the prey were initially highly cryptic (e.g. ca=0.01), the costs from increased conspicuousness of even modestly conspicuous aposematic displays (e.g. ca=0.04) would be relatively great. This suggests that there may be some relationship between the level of behavioural conspicuousness that a prey manifests and the conspicuousness of the aposematic signal that it can sustain. The remarkable finding by Summers & Clough (2001) that conspicuousness of dendrobatid coloration is correlated with the level of a prey’s defence may be thus explained if there is also a correlation between behavioural conspicuousness and defence levels in these animals. Clearly, there is scope for phylogenetically controlled investigations of the relationship between the level of a secondary defence and the behavioural conspicuousness of prey.
If we accept that full-blown aposematic displays are more likely to evolve in behaviourally conspicuous prey than in behaviourally cryptic ones, we still need to be able to explain why such traits evolve at all. Over the years, many explanations have been put forward including combinations of receiver psychology effects (of accelerated learning, memory and wariness), stochastic population effects and characteristics of prey distribution (reviewed in Ruxton et al. 2004). Each of these explanations remains valid but should in our view be re-evaluated, relaxing the narrow assumption that prey were initially cryptic before the evolution of aposematic displays.
Furthermore, as Wallace originally envisaged, warning displays might be conspicuous so as to be ‘very distinct from the protective tints of the defenceless animals allied to them’ (Wallace 1889, p. 232). Hence, a good reason that aposematism may evolve initially is to prevent confusion with undefended prey (Guilford 1990; Sherratt & Beatty 2003). On its own, behavioural conspicuousness itself may not be a sufficiently reliable signal of non-profitability to function as an aposematic display. As we found in figure 5, prey can evolve some heightened levels of behavioural conspicuousness even when they do not evolve adaptive secondary defences. Hence, some additional discriminative cue may be necessary for defended prey to minimize erroneous attacks by educated predators.
Such cues may initially be traits beneficial to individuals in their own right, that in addition function as discriminative cues. Probable examples include: conspicuous stimuli that direct predator attacks toward dispensable organs, perhaps those in which secondary defences are localized; and traits that enhance, for example, thermoregulatory efficiency, parasite resistance and sexual signalling (see Poulton 1890; Mallet & Singer 1987; Sword 1999). Again, if prey are already behaviourally conspicuous, such traits can add relatively small increases in overall conspicuousness while in each case bringing direct benefits. When such traits are beneficial in themselves, they can evolve from a point of rarity and take on qualities of aposematic display (sensu Wallace) as they become common. Furthermore, as Sherratt (2002) recently argued, predators may often select conspicuous traits to use as discriminative aposematic cues (rather than less conspicuous but similarly discriminative traits), because they are likely to function as reliable indicators of defence: the costs of conspicuous aposematic displays are borne much more easily by individuals with effective secondary defences than those with poor defences (see also Sherratt & Beatty 2003). In summary, we suggest that one plausible route to aposematism (but by no means the only plausible route) is roughly: behavioural conspicuousness plus secondary defence; acquisition of traits that can borne by behaviourally conspicuous prey and are beneficial in themselves; use by predators of a conspicuous subset of these traits as reliable cues aiding in the discrimination of defended from edible prey; coevolution of conspicuous traits and predator preferences towards highly evolved warning displays (cf. Turner 1984; Mallet & Singer 1987).
4. Conclusions
Most theoretical models of aposematism focus on the evolution of a conspicuous component of an animal’s appearance, and ignore the evolution of secondary defences (though see the important exception in Leimar et al. (1986)) and of behavioural conspicuousness. These models almost deliberately use the most difficult scenario to explain the starting point of aposematism: that of rarity and conspicuousness. However, the model outlined here indicates that when crypsis imposes strong opportunity costs and when habitats are visually heterogeneous, we may expect that secondary defences evolve to facilitate the behavioural conspicuousness necessary for optimal exploitation of a habitat. When these conditions pertain, aposematism is relatively easy to explain and is not a major evolutionary problem.
Acknowledgments
The authors are grateful to two anonymous referees for their comments, and to Tom Sherratt for numerous discussions.
References
- Abrams P.A. Life-history and the relationship between food availability and foraging effort. Ecology. 1991;72:1242–1252. [Google Scholar]
- Alatalo R.V., Mappes J. Tracking the evolution of warning signals. Nature. 1996;382:708–710. [Google Scholar]
- Bakus G.J. Chemical defence mechanisms on the Great Barrier Reef, Australia. Science. 1981;211:497–498. doi: 10.1126/science.7455691. [DOI] [PubMed] [Google Scholar]
- Brodie E.D., Agrawal A.F. Maternal effects and the evolution of aposematic signals. Proc. Natl Acad. Sci. USA. 2001;98:7884–7887. doi: 10.1073/pnas.141075998. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Carrascal L.M., Diaz J.A., Huertas D.L., Mozetich I. Behavioral thermoregulation by treecreepers: trade-off between saving energy and reducing crypsis. Ecology. 2001;82:1642–1654. [Google Scholar]
- Dunham D.W., Tierney A.J. The communicative cost of crypsis in a hermit crab Pagurus marshi. Anim. Behav. 1983;31:783–785. [Google Scholar]
- Fisher R.A. The genetical theory of natural selection. Clarendon Press; Oxford: 1930. [Google Scholar]
- Franks D.W., Noble J. Warning signals and predator-prey coevolution. Proc. R. Soc. B. 2004;271:1859–1865. doi: 10.1098/rspb.2004.2795. doi:10.1098/rspb.2004.2795 [DOI] [PMC free article] [PubMed] [Google Scholar]
- Grand T.C. Foraging-predation risk trade-offs, habitat selection, and the coexistence of competitors. Am. Nat. 2002;159:106–112. doi: 10.1086/324124. [DOI] [PubMed] [Google Scholar]
- Guilford T. The evolution of conspicuous coloration. Am. Nat. 1988;131:S7–S21. [Google Scholar]
- Guilford T. The evolution of aposematism. In: Schmidt J.O., Evans D.L., editors. Insect defenses: apative mechanisms and strategies of prey and predators. State University of New York Press; New York: 1990. pp. 23–61. [Google Scholar]
- Harvey P.H., Bull J.J., Pemberton M., Paxton R.J. The evolution of aposematic coloration in distasteful prey—a family model. Am. Nat. 1982;119:710–719. [Google Scholar]
- Hetz M., Slobodchikoff C.N. Reproduction and the energy-cost of defense in a Batesian mimicry complex. Oecologia. 1990;84:69–73. doi: 10.1007/BF00665597. [DOI] [PubMed] [Google Scholar]
- Leimar O., Enquist M., Sillèn-Tullberg B. Evolutionary stability of aposematic coloration and prey unprofitability—a theoretical-analysis. Am. Nat. 1986;128:469–490. [Google Scholar]
- Lindquist N., Hay M.E. Palatability and chemical defense of marine invertebrate larvae. Ecol. Monogr. 1996;66:431–450. [Google Scholar]
- Lindström L., Alatalo R.V., Mappes J., Riipi M., Vertainen L. Can aposematic signals evolve by gradual change? Nature. 1999;397:249–251. [Google Scholar]
- Mallet J., Singer M.C. Individual selection, kin selection, and the shifting balance in the evolution of warning colors—the evidence from butterflies. Biol. J. Linn. Soc. 1987;32:337–350. [Google Scholar]
- Merilaita, S. & Tullberg, B. S. 2005 Warning colouration and constrained crypsis. Evolution (In the press.) [PubMed]
- Merilaita S., Tuomi J., Jormalainen V. Optimization of cryptic coloration in heterogeneous habitats. Biol. J. Linn. Soc. 1999;67:151–161. [Google Scholar]
- Moses J.L., Sih A. Effects of predation risk and food availability on the activity, habitat use, feeding behavior and mating behavior of a pond water strider, Gerris marginatus (Hemiptera) Ethology. 1998;104:661–669. [Google Scholar]
- Poulton E.B. The colours of animals: their meaning and use especially considered in the case of insects. Kegan Paul, Trench, Trubner & Co; London: 1890. [Google Scholar]
- Ruxton G.D., Sherratt T.N., Speed M.P. Avoiding attack: the evolutionary ecology of crypsis, aposematism and mimicry. Oxford University Press; 2004. [Google Scholar]
- Schmidt J.O. Hymenopteran venoms: striving toward the ultimate defense against vertebrates. In: Evans D.L., Schmid J.O., editors. Insect defenses: adaptive mechanisms and strategies of prey and predators. State of New York University Press; New York: 1990. pp. 387–420. [Google Scholar]
- Servedio M.R. The effects of predator learning, forgetting, and recognition errors on the evolution of warning coloration. Evolution. 2000;54:751–763. doi: 10.1111/j.0014-3820.2000.tb00077.x. [DOI] [PubMed] [Google Scholar]
- Sherratt T.N. The coevolution of warning signals. Proc. R. Soc. B. 2002;269:741–746. doi: 10.1098/rspb.2001.1944. doi:10.1098/rspb.2001.1944 [DOI] [PMC free article] [PubMed] [Google Scholar]
- Sherratt T.N., Beatty C.D. The evolution of warning signals as reliable indicators of prey defense. Am. Nat. 2003;162:377–389. doi: 10.1086/378047. [DOI] [PubMed] [Google Scholar]
- Sih A. Prey uncertainty and the balancing of antipredator and feeding needs. Am. Nat. 1992;139:1052–1069. [Google Scholar]
- Sillèn-Tullberg B., Bryant E.H. The evolution of aposematic coloration in distasteful prey—an individual selection model. Evolution. 1983;37:993–1000. doi: 10.1111/j.1558-5646.1983.tb05627.x. [DOI] [PubMed] [Google Scholar]
- Speed M., Ruxton G.D. Animal behaviour: evolution of suicidal signals. Nature. 2002;416:375–375. doi: 10.1038/416375a. [DOI] [PubMed] [Google Scholar]
- Speed M.P. Can receiver psychology explain the evolution of aposematism? Anim. Behav. 2001;61:205–216. doi: 10.1006/anbe.2000.1558. [DOI] [PubMed] [Google Scholar]
- Speed M.P. Theoretical developments in the understanding of warning signals. Comments Theor. Biol. 2003;8:207–224. [Google Scholar]
- Stamp N.E., Wilkens R.T. On the cryptic side of life: being unapparent to enemies and the consequences for foraging and growth in caterpillars. In: Stamp N.E., Casey T.M., editors. Caterpillars: ecological and evolutionary constraints on foraging. Chapman & Hall; New York: 1993. pp. 283–330. [Google Scholar]
- Summers K., Clough M.E. The evolution of coloration and toxicity in the poison frog family (Dendrobatidae) Proc. Natl Acad. Sci. USA. 2001;98:6227–6232. doi: 10.1073/pnas.101134898. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Sundberg P. A possible mechanism for the evolution of aposematic coloration in solitary nemerteans (phylum—Nemertea) Oikos. 1987;48:289–296. [Google Scholar]
- Sword G.A. Density-dependent warning coloration. Nature. 1999;397:217–217. [Google Scholar]
- Sword G.A. A role for phenotypic plasticity in the evolution of aposematism. Proc. R. Soc. B. 2002;269:1639–1644. doi: 10.1098/rspb.2002.2060. doi:10.1098/rspb.2002.2060 [DOI] [PMC free article] [PubMed] [Google Scholar]
- Thomas R.J., Marples N.M., Cuthill I.C., Takahashi M., Gibson E.A. Dietary conservatism may facilitate the initial evolution of aposematism. Oikos. 2003;101:458–466. [Google Scholar]
- Turner J.R.G. The palatability spectrum and its consequences. In: Vane-Wright R.I., Ackery P., editors. The biology of butterflies. Princeton University Press; 1984. pp. 141–161. [Google Scholar]
- Wallace, A. R. 1867 Proceedings of the Entomological Society of London, 4 March, pp. IXXX–IXXXi.
- Wallace A.R. Darwinism—an exposition of the theory of natural selection with some of its applications. Macmillan; London: 1889. [Google Scholar]
- Weller S.J., Jacobson N.L., Conner W.E. The evolution of chemical defences and mating systems in tiger moths (Lepidoptera: Arctiidae) Biol. J. Linn. Soc. 1999;68:557–578. [Google Scholar]
- Whitman D.W., Blum M.S., Alsop D.W. Allomones: chemicals for defense. In: Evans D.L., Schmidt J.O., editors. Insect defenses: adaptive mechanisms and strategies of prey and predators. State University of New York Press; New York: 1990. pp. 229–251. [Google Scholar]
- Wiklund C., Järvi T. Survival of distasteful insects after being attacked by naive birds—a reappraisal of the theory of aposematic coloration evolving through individual selection. Evolution. 1982;36:998–1002. doi: 10.1111/j.1558-5646.1982.tb05468.x. [DOI] [PubMed] [Google Scholar]
- Wiklund C., Sillèn-Tullberg B. Why distasteful butterflies have aposematic larvae and adults, but cryptic pupae—evidence from predation experiments on the monarch and the European swallowtail. Evolution. 1985;39:1155–1158. doi: 10.1111/j.1558-5646.1985.tb00456.x. [DOI] [PubMed] [Google Scholar]
- Yachi S., Higashi M. The evolution of warning signals. Nature. 1998;394:882–884. [Google Scholar]