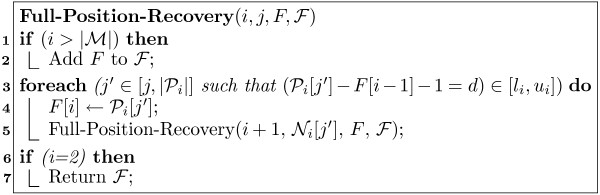Abstract
Background
Extracting motifs from sequences is a mainstay of bioinformatics. We look at the problem of mining structured motifs, which allow variable length gaps between simple motif components. We propose an efficient algorithm, called EXMOTIF, that given some sequence(s), and a structured motif template, extracts all frequent structured motifs that have quorum q. Potential applications of our method include the extraction of single/composite regulatory binding sites in DNA sequences.
Results
EXMOTIF is efficient in terms of both time and space and is shown empirically to outperform RISO, a state-of-the-art algorithm. It is also successful in finding potential single/composite transcription factor binding sites.
Conclusion
EXMOTIF is a useful and efficient tool in discovering structured motifs, especially in DNA sequences. The algorithm is available as open-source at: http://www.cs.rpi.edu/~zaki/software/exMotif/.
Introduction
Analyzing and interpreting sequence data is an important task in bioinformatics. One critical aspect of such interpretation is to extract important motifs (patterns) from sequences. The challenges for motif extraction problem are two-fold: one is to design an efficient algorithm to enumerate the frequent motifs; the other is to statistically validate the extracted motifs and report the significant ones.
Motifs can be classified into two main types. If no variable gaps are allowed in the motif, it is called a simple motif. For example, in the genome of Saccharomyces cerevisiae, the binding sites of transcription factor, GAL4, have as consensus [1], the simple motif, CGG[11,11]CCG. Here [11,11] means that there is a fixed "gap" (or don't care characters), 11 positions long. If variable gaps are allowed in a motif, it is called a structured motif. A structured motif can be regarded as an ordered collection of simple motifs with gap constraints between each pair of adjacent simple motifs. For example, many retrotransposons in the Ty1-copia group [2] have as consensus the structured motif: MT[115,136]MTNTAYGG[121,151]GTNGAYGAY. Here MT, MTNTAYGG and GTNGAYGAY are three simple motifs; [115,136] and [121,151] are variable gap constraints ([minimum gap, maximum gap]) allowed between the adjacent simple motifs. More formally, a structured motif, , is specified in the form:
M1[l1, u1]M2[l2, u2]M3 ... Mk-1[lk-1, uk-1]Mk
where Mi, 1 ≤ i ≤ k, is a simple motif component, and li and ui (for 1 ≤ i <k and where 0 ≤ li ≤ ui), are the minimum and maximum number of gaps allowed between Mi and Mi+1, respectively. Note that a gap is defined to be the number of intervening positions after Mi but before Mi+1. In other words, if si and ei represent the start and end positions of component Mi, then for i ∈ [1, k - 1], the number of gaps is given as gi = ei+1 - si - 1, and we require that gi ∈ [li, ui]. The number of simple motif components, k, is also called the length of . Let Wi, 1 ≤ i <k, denote the span of the gap range, [li, ui], which is calculated as: Wi = ui - li + 1.
In the structured motif extraction problem, the component motifs Mi are unknown before the extraction. However, we do provide some known parameters to restrict the structured motifs to be extracted, including: (i) k – the length of ; (ii) |Mi| – the length of each component Mi ∈ , for 1 ≤ i ≤ k; and (iii) [li, ui] – the gap range between Mi and Mi+1, for 1 ≤ i <k. All these parameters define a structured motif template, , for the structured motifs to be extracted from a set of sequences . A structured motif matching the template in is called an instance of . We use K to denote the number of symbols (not counting gaps) in and use [j] (with 1 ≤ j ≤ K) to denote the jth symbol of .
Let δS () denote the number of occurrences of an instance motif in a sequence S ∈ . Let dS () = 1 if δS () > 0 and dS () = 0 if δS () = 0. The support of motif in the is defined as , i.e., the number of sequences in that contain at least one occurrence of . The weighted support of is defined as , i.e., total number of occurrences of over all sequences in . We use () to denote the set of all occurrences of a structured motif . Given a user-specified quorum threshold q ≥ 1, a motif that occurs at least q times will be called frequent.
There are two main tasks in the structured motif extraction problem: a) Common Motifs – find all motifs in a set of sequences , such that the support of is at least q, b) Repeated Motifs – find all motifs in a single sequence S, such that the weighted support of is at least q. Furthermore, the structured motif extraction problem allows several variations:
• Substitutions: may consist of similar motifs, as measured by Hamming Distance [3], instead of exact matches, to the simple motifs in . We can either allow for at most εi errors for each simple motif Mi, 1 ≤ i ≤ k, or at most ε errors for the whole structured motif .
• Overlapping Components: The variable gap constraints (li and ui) can take on a limited range of negative values, allowing search for overlapping simple motifs. We allow two adjacent components Mi and Mi+1 to overlap, but we require that Mi+1 does not precede Mi. This condition can be satisfied by the following constraints on the gap range [li, ui]: -|Mi| ≤ li ≤ ui, for i ∈ [l, k). For example the search for motif template NNN[-2,2]NNN (where 'N' stands for any of the four DNA bases: A,C,G,T), may discover the pattern ACG[-2,2]CGA, representing an overlapped occurrence, ACGA, as well as a non-overlapped occurrence, ACG--CGA, at the two extremes of the gap range.
• Motif Length Ranges: Each simple motif Mi in a template can be of a range of lengths, i.e., |Mi| ∈ [la, lb], where la and lb are the lower and upper bounds on the desired length.
Table 1 shows four example DNA sequences S1, S2, S3, S4 ∈ ; a structured motif template , where M1 = NNN, M2 = NN and M3 = NNNN, and [0,3] and [1,3] are the intervening gap ranges between the components; and a quorum threshold q = 2. The length of the template is k = 3 and the number of symbols in is K = 3 + 2 + 4 = 9. The span of gap ranges are: W1 = u1 - l1 + 1 = 2 and W2 = u2 - l2 + 1 = 2. If no substitutions are allowed, there are five frequent structured motifs in matching the template , namely 1 = CCG[0,3]TA[1,3]GAAC (shown in bold) and 2 = CCG[0,3]TA[1,3]AACC which occur in S1 and S2; 3 = TAT[0,3]GG[1,3]ACCA (shown underlined), 4 = TAT[0,3]GA[1,3]CCAT and 5 = TAT[0,3] GG[1,3]CCAT which occur in S2 and S3. If substitutions are allows, say, e1 = 1 = e3, then the occurrence of 6 = TAA[0,3]GG[1,3] CCCT (shown underlined) in S4 will be considered to match motif 5.
Table 1.
Structured motif extraction.
| Sequence S1 (∈ ): | CCGTACCGAACCTCAAA |
| Sequence S2 (∈ ): | CCGTTATAGGAACCATT |
| Sequence S3 (∈ ): | TATGGAACCATCTT |
| Sequence S4 (∈ ): | TAACGGATCCCTTT |
| Structured Motif Template (): | NNN[0,3]NN[1,3]NNNN |
| Quorum (q): | 2 |
In this paper, we propose EXMOTIF, an efficient algorithm for both the structured motif extraction problems. It uses an inverted index of symbol positions, and it enumerates all structured motifs by positional joins over this index. The variable gap constraints are also considered at the same time as the joins, resulting in considerable efficiency. In order to save time and space, we only keep the start positions of each intermediate pattern during the positional join.
Related work
Many simple motif extraction algorithms have been proposed primarily for extracting the transcription factor binding sites, where each motif consists of a unique binding site [4-10] or two binding sites separated by a fixed number of gaps [11-13]. A pattern with a single component is also called a monad pattern. Structured motif extraction problems, in which variable number of gaps are allowed, have attracted much attention recently, where the structured motifs can be extracted either from multiple sequences [14-21] or from a single sequence [22,23]. In many cases, more than one transcription factor may cooperatively regulate a gene. Such patterns are called composite regulatory patterns. To detect the composite regulatory patterns, one may apply single binding site identification algorithms to detect each component separately. However, this solution may fail when some components are not very strong (significant). Thus it is necessary to detect the whole composite regulatory patterns (even with weak components) directly, whose gaps and other possibly strong components can increase its significance.
Several algorithms have been used to address the composite pattern discovery with two components, which are called dyad patterns. Helden et al. [11] propose a method for dyad analysis, which exhaustively counts the number of occurrences of each possible pair of patterns in the sequences and then assesses their statistical significance. This method can only deal with fixed number of gaps between the two components. MITRA [12] first casts the composite pattern discovery problem as a larger monad discovery problem and then applies an exhaustive monad discovery algorithm. It can handle several mismatches but can only handle sequences less than 60 kilo-bases long. Co-Bind [24] models composite transcription factors with Position Weight Matrices (PWMs) and finds PWMs that maximize the joint likelihood of occurrences of the two binding site components. Co-Bind uses Gibbs sampling to select binding sites and then refines the PWMs for a fixed number of times. Co-Bind may miss some binding sites since not all patterns in the sequences are considered. Moreover, using a fixed number of iterations for improvement may not converge to the global optimal dyad PWM.
SMILE [14] describes four variants of increasing generality for common structured motif extraction, and proposes two solutions for them. The two approaches for the first problem, in which the structured motif template consists of two components with a gap range between them, both start by building a generalized suffix tree for the input sequences and extracting the first component. Then in the first approach, the second component is extracted by simply jumping in the sequences from the end of the first one to the second within the gap range. In the second approach, the suffix tree is temporarily modified so as to extract the second component from the modified suffix tree directly. The drawback of SMILE is that its time and space complexity are exponential in the number of gaps between the two components. In order to reduce the time during the extraction of the structured motifs, [18] presents a parallel algorithm, PSmile, based on SMILE, where the search space is well-partitioned among the available processors.
RISO [15-17] improves SMILE in two aspects. First, instead of building the whole suffix tree for the input sequences, RISO builds a suffix tree only up to a certain level l, called a factor tree, which leads to a large space saving. Second, a new data structure called box-link is proposed to store the information about how to jump within the DNA sequences from one simple component (box) to the subsequent one in the structured motif. This accelerates the extraction process and avoids exponential time and space consumption (in the gaps) as in SMILE. In RISO, after the generalized factor tree is built, the box-links are constructed by exhaustively enumerating all the possible structured motifs in the sequences and are added to the leaves of the factor tree. Then the extraction process begins during which the factor tree may be temporarily and partially modified so as to extract the subsequent simple motifs. Since during the box-link construction, the structured motif occurrences are exhaustively enumerated and the frequency threshold is never used to prune the candidate structured motifs, RISO needs a lot of computation during this step.
For repeated structured motif identification problem, the frequency closure property that "all the subsequences of a frequent sequence must be frequent", doesn't hold any more since the frequency of a pattern can exceed the frequency of its sub-patterns. [22] introduces an closure-like property which can help prune the patterns without missing the frequent patterns. The two algorithms proposed in [22] can extract within one sequence all frequent patterns of length no greater than a length threshold, which can be either manually specified or automatically determined. However, this method requires that all the gap ranges [li, ui], between adjacent symbols in the structured motif be the same, i.e., [li, ui] = [l, u] for all i ∈ [1, k - 1]. Moreover, approximate matches are not allowed for the structured motif.
The EXMOTIF algorithm
We first introduce our basic approach for common structured motif extraction problem. We then successively optimize it for various practical scenarios.
The basic approach
Let's assume that we are extracting all structured motif instances from n sequence = {Si, 1 ≤ i ≤ n}, each of which satisfies the template and occurs at least in q sequences of . We assume for the moment that no substitutions are allowed in any of the simple motifs. We also assume that all Si ∈ , 1 ≤ i ≤ n and the extracted motifs are over the DNA alphabet, ΣDNA. EXMOTIF first converts each Si ∈ , 1 ≤ i ≤ n into an equivalent inverted format [25], where we associate with each symbol in the sequence Si its pos-list, a sorted list of the positions where the symbol occurs in Si. Then for each symbol we combine its pos-list in each Si to obtain its pos-list in . More formally, for a symbol X ∈ ΣDNA, its pos-list in Si is given as (X, Si) = {j | Si[j] = X, j ∈ [1, |Si|]}, where Si[j] is the symbol at position j in Si, and |Si| denotes the length of Si. Its pos-list across all sequences is obtained by grouping the pos-lists of each sequence, and is given as (X, ) = {⟨ i, | (X, Si)|, (X, Si)⟩ | Si ∈ }, where i is the sequence identifier of Si, and | (X, Si)| denotes the cardinality of the pos-list (X, Si) in sequence Si. For our example sequences in Table 1, the pos-list for each DNA base is given in Table 2. For example, A occurs in sequence S1 at the positions {5, 9, 10, 15, 16, 17}, thus the entries in A's pos-list are {1, 6, 5, 9, 10, 15, 16, 17}.
Table 2.
Pos-lists.
| X | pos-lists |
| A | {1,6,5,9,10,15,16,17, 2,5,6,8,11,12,15, 3,4,2,6,7,10, 4,3,2,3,7} |
| C | {1,7,1,2,6,7,11,12,14, 2,4,1,2,13,14, 3,3,8,9,12, 4,4,4,9,10,11} |
| G | {1,2,3,8, 2,3,3,9,10, 3,2,4,5, 4, 2,5,6} |
| T | {1,2,4,13, 2,5,4,5,7,16,17 3,5,1,3,11,13,14, 4,5,1,8,12,13,14} |
Sequence identifiers (i) and cardinality of (X, Si) are marked in bold.
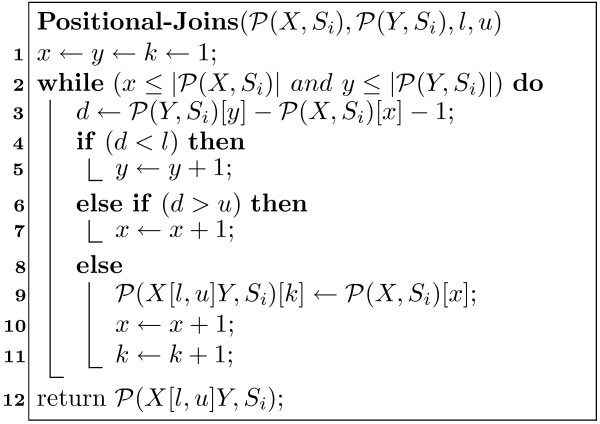
Positional joins
We first extend the notion of pos-lists to cover structured motifs. The pos-list of in Si ∈ is given as the set of start positions of all the matches of in Si. Let X, Y ∈ ΣDNA be any two symbols, and let = X[l, u]Y be a structured motif. Given the pos-lists of X and Y in Si for 1 ≤ i ≤ n, namely, (X, Si) and (Y, Si), the pos-list of in Si can be obtained by a positional join as follows: for a position x ∈ (X, Si), if there exists a position y ∈ (Y, Si), such that l ≤ y - x - 1 ≤ u, it means that Y follows X within the variable gap range [l, u] in the sequence Si, and thus we can add x to the pos-list of motif X[l, u]Y. Let d be the number of gaps between x ∈ (X, Si) and y ∈ (Y, Si), given as d = y - x - 1.
Then, in general, there are three cases to consider in the positional join algorithm:
• d <l: Advance y to the next element in (Y, Si).
• d > u: Advance x to the next element in (X, Si).
• l ≤ d ≤ u: Save this occurrence in (X[l, u]Y, Si), and then advance x to the next element in (X, Si).
The pos-list for X[l, u]Y can be computed in time linear in the lengths of (X, Si) and (Y, Si), i.e., the complexity of a positional join is O(| (X, Si)| + | (Y, Si)|). In essence, each time we advance x ∈ (X, Si), we check if there exists a y ∈ (Y, Si) that satisfies the given gap constraint. Instead of searching for the matching y from the beginning of the pos-list each time, we search from the last position used to compare with x. This results in fast positional joins. For example, during the positional join for the motif A[0,1]T in S4, with l = 0 and u = 1, we scan the pos-lists of A and T for S4 in Table 2, i.e. (X, S4) = {2, 3, 7} and (Y, S4) = {1, 8, 12, 13, 14}. Initially, x = 2 and y = 1. This gives d = 1 - 2 - 1 = - 2 <l, thus we advance y to 8. Next, d = 8 - 2 - 1 = 5 > u, thus we advance x to 3. Then, d = 8 - 3 - 1 = 4 > u, thus we advance x to 7. Next, d = 8 - 7 - 1 = 0 ∈ [l, u], so we store x = 7 in (A[0, 1]T, S4). We would advance x but since we have already reached the end of (A, S4), the positional join stops. Thus the final pos-list of A[0,1]T in S4 is: (A[0, 1]T, S4) = {7}. After we obtain the pos-list of in each Si for 1 ≤ i ≤ n, we can combine them together to obtain the pos-list of in . For example, the full pos-list of A[0,1]T for is: {2, 2, 6, 15, 3, 2, 2, 10, 4, 1, 7}. Thus the support of A[0,1]T is 3. Note here for each non-empty pos-list, we insert its sequence identifier and length before it. The pseudo-code for the positional joins for a given sequence Si ∈ is shown in Figure 1. The full pos-list is obtained by concatenating the pos-lists from each sequence Si.
Figure 1.
Positional Joins Algorithm.
Given a longer motif , the positional joins start with the last two symbols, and proceed by successively joining the pos-list of the current symbol with the intermediate pos-list of the suffix. That is, the intermediate pos-list for a (l+1)-length pattern (with l ≥ 1) is obtained by doing a positional join of the pos-list of the pattern's first symbol, called the head symbol, with the pos-list of its l-length suffix, called the tail. As the computation progresses the previous tail pos-lists are discarded. Combined with the fact that only start positions are kept in a pos-list, this saves both time and space.
In order to enumerate all frequent motifs instances in , EXMOTIF computes the pos-list for each and report only if its support is no less than the quorum (q). A straightforward approach is to directly perform positional joins on the symbols from the end to the start for each . This approach leads to much redundant computation since simple motif components may be shared among several structured motifs. EXMOTIF, in contrast, performs two steps: it first computes the pos-lists for all simple motifs in by doing positional joins on pos-lists of its symbols, and it then computes the pos-list for each structured motif by doing positional joins on pos-lists of its simple motif components. EXMOTIF handles both simple and structured motifs uniformly, by adding the gap range [0, 0] between adjacent symbols within each simple motif Mi. For our example in Table 1, the structured motif template becomes: N[0,0]N[0,0]N[0,1]N[0,0]N[2,3]N[0,0]N[0,0]N[0,0]N. Also since we only report frequent motifs, we can prune the candidate patterns during the positional joins based on the closure property of support (note however that this cannot be done for weighted support).
Extraction of the simple motifs
Given a template motif , we know the lengths of the simple motif components desired. A naive approach is to directly do positional joins on the symbols from the end to the start of each simple motif. However, since some simple motifs are of the same length and the longer simple motifs can be obtained by doing positional joins on the shorter simple motifs/symbols, we can avoid some redundant computation. Note also that the gap range inside the simple motif is always [0,0].
Let = {Li, 1 ≤ i ≤ m}, where Li is the length of each simple motif in and assume is sorted in the ascending order. For each Li, 1 ≤ i ≤ m, we need to enumerate possible simple motifs. Let be the maximum length in . We can compute the pos-lists of simple motifs sequentially from length 1 to . But this may waste time in enumerating some simple motifs of lengths that are not in . Instead, EXMOTIF first computes the pos-lists for the simple motifs of lengths that are powers of 2. Formally, let J be an integer such that 2J ≤ < 2J+1. We extract the patterns of length 2j by doing positional joins on the pos-lists of patterns of length 2j-1 for all 1 ≤ j ≤ J. For example, when = 11, EXMOTIF first computes the pos-lists for simple motifs of length 20 = 1, 21 = 2, 22 = 4 and 23 = 8.
EXMOTIF then computes the pos-lists for the simple motifs of Li ∈ , by doing positional joins on simple motifs whose pos-list(s) have already been computed and their lengths sum to Li. For example, when Li = 11, EXMOTIF has to join motifs of lengths 8, 2, and 1. It first obtains all motifs of length 8 + 2 = 10, and then joins the motifs of lengths 10 and 1, to get the pos-lists of all simple motifs of length 10 + 1 = 11. The pos-lists for the simple motifs of length Li ∈ are kept for further use in the structured motif extraction. At the end of the first phase, EXMOTIF has computed the pos-lists for all simple motif components that can satisfy the template.
Extraction of the structured motifs
We extract the structured motifs by doing positional joins on the pos-lists of the simple motifs from the end to the start in the structured motif . Formally, let H[l, u]T be an intermediate structured motif, with simple motif H as the head, and a suffix structured motif T as tail. Then (H[l, u]T) can be obtained by doing positional joins on (H) and (T). Since (H) keeps only the start positions, we need to compute the corresponding end positions for those occurrences of H, to check the gap constraints. Since only exact matches or substitutions are allowed for simple motifs, the end position is simply s + |H| - 1 for a start position s.
Full-position recovery
In our positional join approach, to save time and space we retain only the motif start positions, however, in some applications, we may need to know the full position of each occurrence, i.e., the set of matching positions for each symbol in the motif. EXMOTIF records some "indices" during the positional joins in order to facilitate full position recovery.
For each suffix of a structured motif, , starting at position i with 1 ≤ i ≤ ||, we keep its pos-list, i, and an index list, i. For each entry, say i[j], in the pos-list i, the corresponding index entry i[j], points to the first entry, say f, in i+1 that satisfies the gap range with respect to i[j], i.e., i+1[f] - i[j] - 1 ∈ [li, ui]. Note that is never used. Also note that () = 1. Let s be a start position for the structured motif in sequence S, and let s be the js-th entry in 1, i.e., s = 1[js]. Let F store a full position starting from s, and let store the set of all full positions. Figure 2 shows the pseudo-code for recovering full positions starting from s. This recursive algorithm has four parameters: i denotes a (suffix) position in , j gives the j-th entry in i, F denotes an intermediate full position, and denotes the set of all the full occurrences. The algorithm is initially called with i = 2, j = 1[js], F = {s}, and = ∅. Starting at the first index in Pi, that satisfies the gap range with respect to the last position in F, we continue to compute all such positions j' ∈ [j, |Pi|] that satisfy the gap range (line 3). That is, we find all positions j', such that Pi[j'] - F[i - 1] - 1 = d ∈ [li, ui]. For each such position j', we add it in turn to the intermediate full position, and make another recursive call (line 5), passing the first index position Ni[j'] in Pi+1 that can satisfy the gap range with respect to Pi[j']. Thus in each call we keep following the indices from one pos-list to the next, to finally obtain a full position starting from s when we reach the last pos-list, . Note that at each suffix position i, since j only marks the first position in i+1 that satisfies the gap constraints, we also need to consider all the subsequent positions j' > j that may satisfy the corresponding gap range.
Figure 2.
Indexed Full Position Recovery Algorithm.
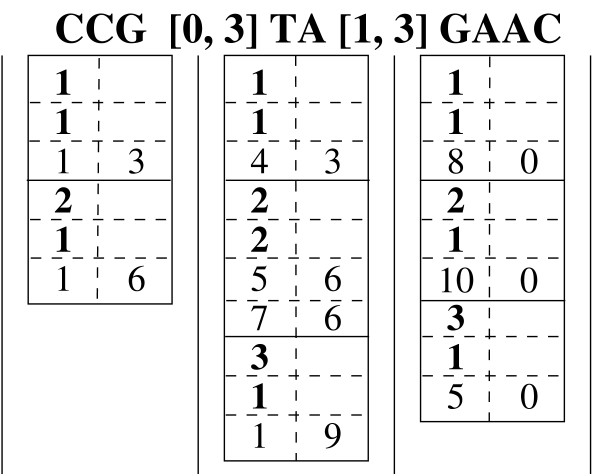
Consider the example shown in Fig. 3 to recover the full positions for = CCG[0,3]TA[1,3]GAAC. Under each symbol we show two columns. The left column corresponds to the intermediate pos-lists as we proceed from right to left, whereas the right column stores the indices into the previous pos-list. For example, the middle column gives the pos-list (TA[1,3]GAAC) = {1, 1, 4, 2, 2, 5, 7, 3, 1, 1}. For each position x ∈ (TA[l,3]GAAC) (excluding the sequence identifiers and the cardinality), the right column records an index in (GAAC) which corresponds to the first position in (GAAC) that satisfies the gap range with respect to x. For example, for position x = 5 (at index 6), the first position in (GAAC) that satisfies the gap range [1,3] is 10 (since in this case there are 3 gaps between the end of TA at position 6 and start of GAAC at position 10), and it occurs at index 6. Likewise, for each position in the current pos-list we store which positions in the previous pos-list were extended. With this indexed information, full-position recovery becomes straightforward. We begin with the start positions of the occurrences. We then keep following the indices from one pos-list to the next, until we reach the last pos-list. Since the index only marks the first position that satisfies the gap range, we still need to check if the following positions satisfy the gap range. At each stage in the full position recovery, we maintain a list of intermediate position prefixes that match up to the j-th position in . For example, to recover the full position for = CCG[0,3]TA[1,3]GAAC, considering start position 1 (with = {(1)}) in sequence 2, we follow index 6 to get position 5 in the middle pos-list, to get = {(1, 5)}. Since the next position after 5 is 7 which is also within the gap range [0,3], so we update = {(1, 5), (1, 7)}. For position 5, we follow index 6 to get position 10 in the rightmost pos-list, to get = {(1, 5, 10)}; for position 7, we follow index 6 to get position 10 in the right pos-list, to get = {(1, 7, 10)}. Likewise, we can recover the full-position in sequence 1, which is = {(1, 4, 8)}. During the full-position recovery, we can also count the number of full-positions, i.e., occurrences, of each structured motif. For example, there are 3 occurrences of CCG[0,3]TA[1,3]GAAC.
Figure 3.
Indexed Full-position Recovery Example.
Length ranges for simple motifs
EXMOTIF also allows variation in the lengths of the simple motifs to be found. For example, a motif template may be specified as M1[5,10] M2, |M1| ∈ [2,4], and |M2| ∈ [6,7], which means that we have to consider NN, NNN, and NNNN as the possible templates for M1 and similarly for M2. A straightforward way for handling length ranges is to enumerate exhaustively all the possible sub-templates of with simple motifs of fixed lengths and then to extract each sub-template separately. Instead, EXMOTIF does an optimized extraction. EXMOTIF reuses the partial pos-lists created when using a depth first search to enumerate and extract the sub-templates.
Handling substitutions
As mutations are a common phenomena in biological sequences, we allow substitutions in the extracted motifs. That is two motif instances may be considered to be the same if they are within the allowed substitution thresholds. EXMOTIF allows users to specify the number of substitutions allowed for the whole motif (ε), and also a per simple motif threshold (εi, i ∈ [1, k]). There are two types of substitutions we consider.
Position-specific substitutions
Here we allow a position (a DNA symbol) in the instance motif to be substituted with 1 or 2 other DNA symbols. All such neighbors will contribute to the frequency of . For example, for = ACG[4,6]TT, if we allow e1 = 1 substitutions in motif M1 = ACG, at position 2, then AAG[4,6]TT, ACG[4,6]TT or AGG[4,6]TT may contribute to the frequency of . Instead of enumerating all of these separately, EXMOTIF can directly mine relevant motifs using IUPAC symbols (see Table 3). EXMOTIF simply constructs the pos-lists for the relevant IUPAC symbols by scanning sequences in once. Then it mines the motif instances as in the basic approach, since all allowed substitutions have already been incorporated into the relevant IUPAC symbols. Let vi, 1 ≤ i ≤ k, to denote the set of IUPAC symbols that can appear in the motif. When vi = 1 (i.e., each position allows only 1 DNA symbol), the alphabet used is {A, C, G, T}; when vi = 2 (i.e., each position may allow up to 2 DNA symbols), the expanded alphabet is {A, C, G, T, R, Y, K, M, S, W}; and when vi = 3 (i.e., each position may allow up to 3 DNA symbols), the expanded alphabet is {A, C, G, T, R, Y, K, M, S, W, B, D, H, V}. For example, when v1 = 2, instead of reporting = ACG[4,6]TT as the mined instance, EXMOTIF may report ASG[4,6]TT as an instance, where S stands for either C or G (see Table 3). EXMOTIF also allows the user to specify the maximum number of IUPAC symbols that can appear in each simple motif, ei, 1 ≤ i ≤ k.
Table 3.
IUPAC alphabet (ΣIUPAC).
| Symbol | A | C | G | T |
| Bases | A | C | G | T |
| Symbol | U | R | Y | K |
| Bases | U | A,G | C,T | G,T |
| Symbol | M | S | W | B |
| Bases | A,C | G,C | A,T | C,G,T |
| Symbol | D | H | V | N |
| Bases | A,G,T | A,C,T | A,C,G | A,C,G,T |
Arbitrary substitutions
Here we allow a DNA symbol in to be substituted with other symbols across all positions (i.e., in a position independent manner), up to the allowed maximum errors per motif (or per component). To count the support for a motif, EXMOTIF has to consider all of its neighbors as well, which are defined as all the motifs (including itself) within Hamming distance, ε (or per motif ei). Then the support of an instance motif is calculated as the total number of sequences in which its neighbors (including itself) are present. As always, the motif is frequent if its support meets the quorum q, that is, its neighbors are present in at least q distinct sequences.
The main challenge is that when arbitrary, position independent substitutions are allowed, we cannot do support checking during each positional join, since the support of the current motif may be below quorum, but combined with its neighbors it may meet quorum. Thus EXMOTIF does support checking at two points. First, it checks for quorum after the pos-lists of all the simple motifs in have been computed, provided the per motif error thresholds ei have been specified. In this case each simple motif must be frequent to be extended to a structured motif. Second, it checks for quorum after the pos-lists of all the structured motifs that satisfy are computed.
Determining neighbors
In order to quickly find all the existing neighbors of a motif within the allowed error thresholds, EXMOTIF first computes all the exact structured motifs, and stores them into a hash table to facilitate fast lookup. Then for each extracted structured motif , EXMOTIF enumerates all its possible neighbors and checks whether they exist in the hash table. One problem is that the number of possible neighbors of can be quite large. When we allow εi substitutions for simple component Mi in , for 1 ≤ i ≤ k, the number of 's neighbors is given as . For example, for = AACGTT[1,5]AGTTCC, when we allow one substitution for each simple motif, the number of its neighbors is 361; when we allow two substitutions per component, the number of its neighbors is 23,716. Instead of enumerating the potentially large number of neighbors (many of which may not even occur in the sequence set ) for each structured motif individually, EXMOTIF utilizes the observation that many motifs have shared neighbors, and thus previously computed support information can be reused. EXMOTIF enumerates neighbors in two steps. In the first step, for each , it enumerates aggregate neighbor motifs, replacing the allowed number of errors ei with as many 'N' symbols (which stands for A,C,G, or T). The number of possible aggregate neighbors is given as . The second step, it computes the support for each aggregate neighbor by expanding each 'N' with each DNA symbol, looking up the hash table for the support of the corresponding motif, and adding the supports for all matching motifs. Since the motifs matching an aggregate are also neighbors of each other, the support of the aggregate can be re-used to compute the support of other matching motifs as well. Once the supports for all aggregate neighbors have been computed, the final support of the structured motif can be obtained. Thus for each , the number of "neighbors" to consider can be as low as !
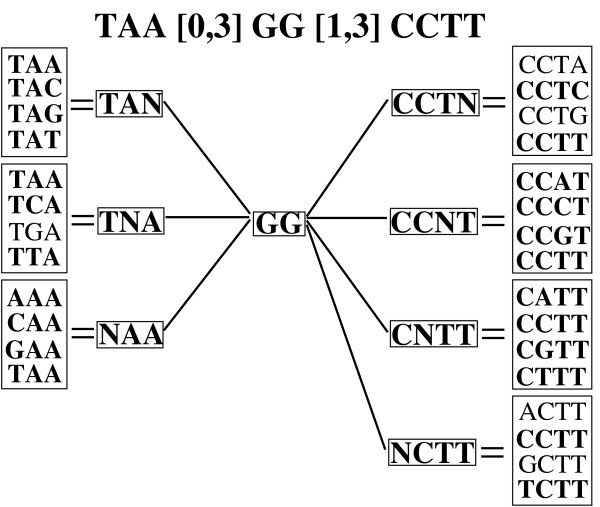
For example, consider the example shown in Figure 4. Consider the structured motif = TAA[0,3]GG[1,3]CCTT (taken from our example in Table 1); assume that ε1 = 1, ε2 = 0 and ε3 = 1. There are three possible aggregates for TAA, namely TAN, TNA, and NAA, and four aggregates for CCTT, namely CCTN, CCNT, CNTT, and NCTT, giving a total of 12 aggregate neighbors for , as illustrated in the figure. EXMOTIF processes each aggregate neighbor in turn. Using a hash-table (or direct lookup table if there are only a few neighbors), it checks if the aggregate neighbor has been processed previously. If yes, it moves on to the next aggregate. If not, it gathers the support information from all of its matching structured motifs, to compute its total support. Next, it also updates the neighbor support value for each of the matching motifs, so that once an aggregate is processed, we no longer require its information. All we need to know is whether it has been processed or not. For example, once the support of the first aggregate TAN[0,3]GG[1,3]CCTN for the example motif above is computed, EXMOTIF also updates the neighbor supports for all other matching structured motifs, such as = TAC[0,3]GG[1,3]CCTG. Later when processing , EXMOTIF can skip the above aggregate and focus on the not yet processed aggregates, e.g., NAC[0,3]GG[1,3]NCTG, and so on.
Figure 4.
Aggregate Neighbors.
The pseudo-code for arbitrary substitutions is given in Figure 5. The procedure takes as input the hash-table ℍ containing all structured motifs and their supports π(), the quorum q, and the per simple motif errors ei or the global error ε for the structured motifs. For each structured motif we also maintain its aggregate support πaggregate(), which is initially set to 0 (line 1). Initially we create all the aggregate neighbors for each extracted structured motif (lines 3–7). For each such aggregate neighbor G (line 8), if it has not been processed, we compute its support by adding the individual supports of all its matching motifs (lines 11–12). Note that these support values are found quickly via the hash-table ℍ. Once the support of an aggregate neighbor is known, we immediately update the aggregate support πaggregate) for each of its contributing matching motifs (lines 13–14). Note that since each motif has already contributed to the support of the aggregate neighbor (π (G)), we must subtract the initial support of (π()) to avoid over-counting. Finally, once all the aggregate neighbors have been processed, we output the structured motif , provided π() + πaggregate() meets the quorum requirement (line 14).
Figure 5.
Arbitrary Substitutions.
Counting support
There are two methods to record the support for each motif. In the first method, we associate each motif with a bit vector, . Each bit, i for 1 ≤ i ≤ n (where n = ||) indicates whether the motif is present in the sequence Si ∈ . The support of the motif is the number of set bits in . Thus to obtain the support for a motif, we can simply union the bit vectors of all its (aggregate) neighbors. Using one bit to represent a sequence saves space, and also saves time via the union operation. However, since we need n fixed bits for each motif to store its bit vector, this is not efficient if there are many sequences, and if a motif occurs only in a small number of sequences, which leads to a sparse bit vector. Thus in the second method, EXMOTIF associates each motif with an identifier array, , to only store the sequence identifiers in which the motif occurs. EXMOTIF can then obtain the support for a motif by scanning the identifier arrays of its neighbors in linear time. For example consider again our motif (from Table 1), TAT[0,1]GG[2,3]CCAT, which occurs in S2 and S3, Its bit vector is thus = {0110} and its identifier array = {2, 3}.
Creating positional weight matrices
For any frequent structured motif , we can summarize the information about its neighbors (including ) by computing a Positional Weight Matrix (PWM). The PWM for a structured motif gives for each non-gap position the likelihood of occurrence for each symbol in ΣDNA. The PWM for is calculated as follows:
where, fij and rij represent the observed and relative frequency of symbol i at position j, respectively, pi is the prior probability of symbol i, and ij is the weight (log-likelihood) of observing symbol i at position j. Whereas gives the likelihood of observing a given symbol in a given position in it does not account for the degree to which some symbols are conserved at some positions. We can adjust the weights ij by considering the information content at each position. The information content for a PWM is given as:
where K is the number of symbols in ; ij is the information content of symbol i at position j; j is the information content over all bases at position j; and is the information content of the entire matrix . To allow mismatches at less conserved positions to be more easily tolerated than those at highly conserved positions, we multiply each ij by j, which is larger for more conserved positions. As a result, the corrected weight of each element in the PWM becomes:
Then we can calculate the PWM score, , for a structured motif, , by summing up the positional weights for the bases in , given as . Thus for each , its PWM score and PWM information content can be further used to measure whether is a significant motif.
Solving repeated structured motif identification problem
In repeated structured motif identification problem, the frequency closure property (that all the subsequences of a frequent sequence must be frequent), does not hold any more. For example, the sequence GCTTT, has three occurrences of pattern G[1,3]T, but it sub-pattern, G, has only one occurrence. Thus we cannot apply the closure property for pruning candidates. Nevertheless, a bound on the frequency of a sub-pattern can be established, which can be used for pruning.
Theorem 1. Let = M1 ... Mk be a structured motif and = Mi ... Mk be a suffix of , for 1 ≤ i ≤ k. If the weighted support of is πw (), then , where Wm = um - lm + 1 is the span of the gap range for m ∈ [1, k - 1].
Proof. Let () be the occurrence set of and () be the occurrence set of . For each occurrence of in (), we can extend it to get occurrences of in () by adding M1 ... Mi-1 before . This leads to at most occurrences of for any occurrence of . Thus , which immediately gives . □
With Theorem 1, EXMOTIF can calculate a support bound for any suffix of , given the quorum requirement q. For example, assume that the motif template is NN[3,5]NNN[0,4]NNN and q = 100, with W1 = 5 - 3 + 1 = 3 and W2 = 4 - 0 + 1 = 5. When processing the suffix component = NNN, we require that πw() ≥ = 6; when processing = NNN[0,4]NNN, we require that πw() ≥ = 33. Thus even the weaker bounds can lead to some pruning.
The complete EXMOTIF algorithm: complexity analysis
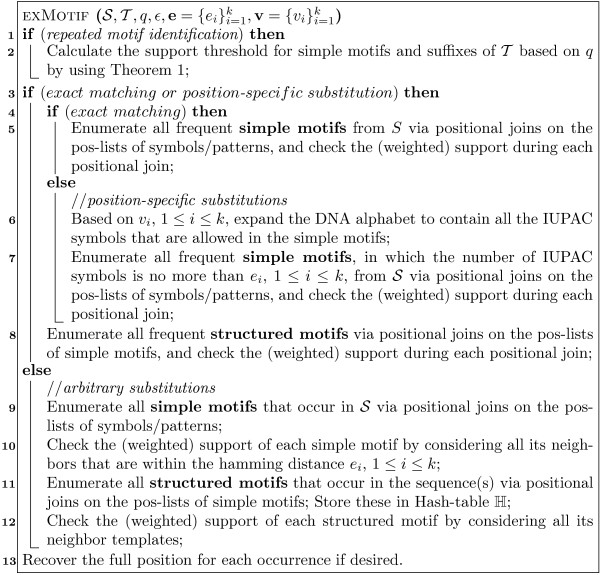
The pseudo-code for the complete EXMOTIF algorithm is shown in Figure 6. The program takes as inputs the set of sequences , the motif template = M1[l1, u1] ... [lk-1, uk-1] Mk, the quorum threshold q, the number of errors or IUPAC symbols allowed per simple motif , and the set of IUPAC symbols to use per simple motif, (only for position specific substitutions). As outlined in Figure 6 EXMOTIF allows several different variations to motif extraction, as described above. These variations include, exact matching, position-specific substitutions via use of IUPAC symbols, arbitrary substitutions, and repeated motif identification.
Figure 6.
EXMOTIF Algorithm.
EXMOTIF initially adjusts the support thresholds if the task is repeated motif identification (lines 1–2). The main approach for handling exact matches or position-specific substitutions is the same. The main difference is that while enumerating the simple motifs, EXMOTIF uses the appropriate IUPAC alphabet (specified by vi for component Mi; lines 6–7). The structured motifs are found via positional joins over the simple motifs (line 8). The positional joins are performed as described in Figure 1. For arbitrary substitutions, EXMOTIF first enumerates the simple motifs (line 9) and checks their aggregate support (i.e., including the supports of all neighbors within error εi). From these, the structured motifs are enumerated and stored in a hash-table (ℍ; line 11). Lastly, the aggregate support of all these motifs is computed as described in Figure 5 (line 12). Those that meet the quorum will be output. Finally, if desired, EXMOTIF recovers the full positions for each occurrence, via the procedure outlined in Figure 2.
In terms of the computational complexity of EXMOTIF, let's first consider the complexity of extracting the simple motifs. Assume that m is the length of the longest simple motif component in the structured template . Note that there are potentially |Σ|m frequent simple motifs at that length, but due to the quorum requirement, many of these will not be frequent. Nevertheless, in the worst case O(|Σ|m) simple components may be extracted. For a simple motif of length m, EXMOTIF uses O(log(m)) positional joins to obtain its support, and each such join takes O(N) time, where is the sum of the lengths of all the sequences Si in the database . Thus, extracting the simple motifs takes time O(N log(m)|Σ|m) in the worst case.
With |Σ|m simple motifs, there are O(|Σ|mk) potential structured motifs, though a vast majority of these will not meet the quorum requirement. Extracting the structured motifs then takes time O(kN|Σ|mk) for the exact match and position-specific substitution cases. For arbitrary substitutions there is additional cost of enumerating aggregate neighbors and computing their support. For each motif we have to consider = kme aggregate neighbors, where e = maxi{ei}. Furthermore, an aggregate neighbor can have k|Σ|e matching motifs. Thus the time complexity of extracting all the structured motifs is O(kN|Σ|mk + k2me|Σ|e) for arbitrary substitutions. Since typically mk > e and N > me, the time complexity is essentially O(kN|Σ|mk). Combined with the cost for simple motif extraction, the computational complexity of EXMOTIF is then given as O(log(m) N |Σ|m + kN|Σ|km) = O(kN|Σ|km).
Experimental results
EXMOTIF has been implemented in C++, and compiled with g++ v4.0.0 at optimization level 3 (-O3). We performed experiments on a Macintosh PowerPC G5 with dual 2.7GHz processors and 4GB memory running Mac OS X vl0.4.5. We compare our results with the latest version of RISO [15-17] (called RISOTTO [17]), the best previous algorithm for structured motif extraction problem.
EXMOTIF and RISO: comparison
For comparison, we extract structured motifs from 1,062 non-coding sequences (a total of 196,736 nucleotides) located between two divergent genes in the genome of B. subtilis [15-17]. Figure 7 and 8 compare the running time (in seconds) for EXMOTIF and RISO using exact matching and approximate matching, respectively. Experiments were done for different gap ranges, number of components, and quorum thresholds. Note that EXMOTIF has two options: one (shown as "exMOTIF" in the figures) for reporting only the number of sequences where the structured motifs occur, the other (shown as "exMOTIF(#)") for reporting both the number of sequences where the structured motifs occur and the actual occurrences. Also note that the current implementation of RISO does not report the actual occurrences; it reports only the frequency.
Figure 7.
EXMOTIF vs. RISO: Exact Matching.
Figure 8.
EXMOTIF vs. RISO: Approximate Matching.
Exact matching
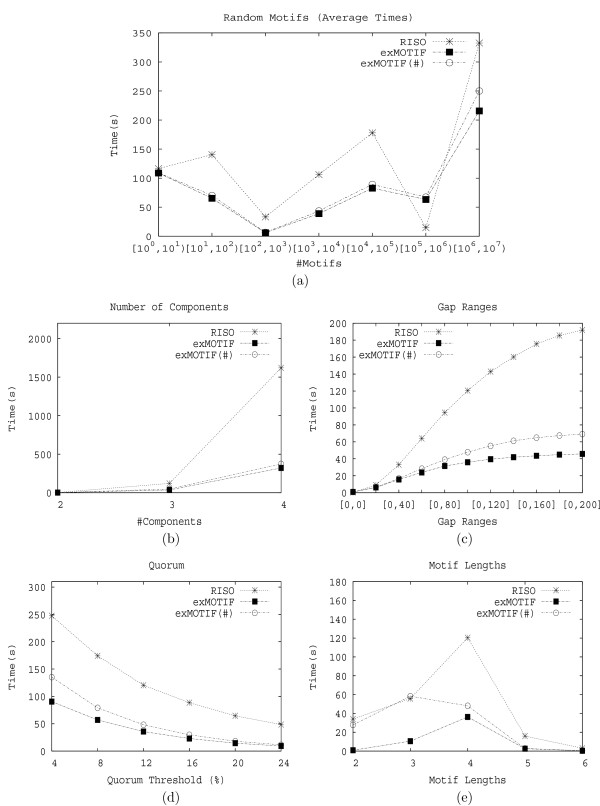
In the first experiment, shown in Figure 7(a), we randomly generated 100 structured motif templates, with k ∈ [2,4] simple motifs of length l ∈ [4,7] (k and l are selected uniformly at random within the given ranges). The gap range between each pair of simple motifs is a random sub-interval of [0, 200]. The x-axis is sorted on the number of motifs extracted. For clarity we plot average times for the methods when the number of motifs extracted fall into the given range on the x-axis. For example, the time plotted for the range [102, 103) is the average time for all the random templates that produce between 100 and 1000 motifs. We find that the average running time for RISO across all extracted motifs is 120.7s, whereas for EXMOTIF it takes 88.4s for reporting only the supports, and 91.3s for also reporting all the occurrences. The median times were 26.3s, 8.5s, and 9.2s, respectively, indicating a 3 times speed-up of EXMOTIF over RISO.
In the next set of experiments we varied one parameter while keeping the others fixed. We set the default quorum to 12% (q = 127), the default gap ranges to [0,100], the default simple motif length to l = 4 (NNNN), and the default number of components k = 3 (e.g., NNNN[0,100]NNNN[0,100]NNNN). In Figure 7(b), we plot the time as a function of the number of simple motifs k in the template. We find that as the number of components increases the time gap between EXMOTIF and RISO increases; for k = 4 simple motifs, EXMOTIF is around 5 times faster than RISO. Figure 7(c) shows the effect of increasing gap ranges, from [0,0] to [0,200]. We find that as the gap range increases the time for EXMOTIF increases at a slower rate compared to RISO. For [0,200], EXMOTIF is 3–4 times faster than RISO depending whether only frequency or full occurrences are reported. In Figure 7(d), as the quorum threshold increases, the running time goes down for both methods. For quorum 24%, EXMOTIF is 4–5 times faster than RISO. As support decreases, the gap narrows somewhat, but EXMOTIF remains 2–3 times faster. Finally, Figure 7(e) plots the effect of increasing simple motif lengths l ∈ [2,6]. We find that the time first increases and then decreases. This is because there are a large number of motif occurrences for length 3 and length 4, but relatively few occurrences for length 5 and length 6. Depending on the motif lengths, EXMOTIF can be 3–40 times faster than RISO for comparable output, i.e., reporting only the support. EXMOTIF remains up to 5 times faster when also reporting the actual occurrences.
To compare the performance for extracting structured motifs with length ranges, we used the template = M1[50, 100] M2[1,50]M3[20, 100]M4 with q = 12%, where |M1| ∈ [2,4], |M2| ∈ [3,4], |M3| ∈ [5,6], |M4| ∈ [4,5]. EXMOTIF took 78.4s, whereas RISO took 1640.9s to extract 14,174 motifs.
Approximate matching
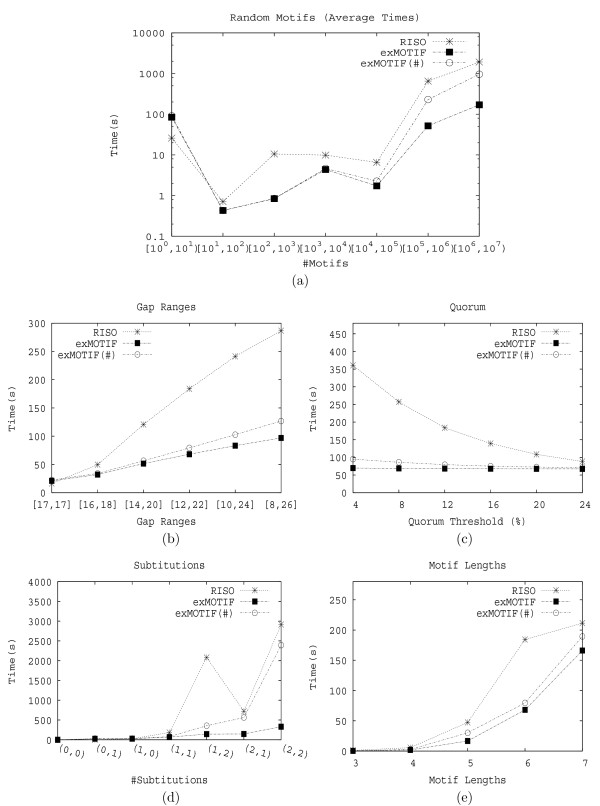
In the first experiment, shown in Figure 8(a), we randomly generated 30 structured motif templates, with k ∈ [2,3] simple motifs of length l ∈ [3,6] (k and l are selected uniformly at random within the given ranges). The gap range between each pair of simple motifs is a random sub-interval of [10, 30]. The x-axis is sorted on the number of motifs extracted, and average times are plotted for the extracted number of motifs in the given range. We find that the average running time for RISO is 334.5s, whereas for EXMOTIF it takes 59.3s seconds for reporting only the support, and 176.7s for also reporting all the occurrences. Thus EXMOTIF is on average 5 times faster than RISO, with comparable output.
Figures 8(b)–(e) plot the time for approximate matching as a function of different parameters. We set the default quorum to 12% (q = 127, out of || = 1062 sequences), the default gap ranges to [12,22], the default simple motif length to l = 6 (NNNNNN), and the default number of components k = 2 (e.g., NNNNNN[12,22]NNNNNN). Figure 8(b) shows how increasing gap ranges effect the running time; for gap range [8,26] between the two motif components, EXMOTIF is 2–3 times faster than RISO. In Figure 8(c), we increase the numbers of arbitrary substitutions allowed for each simple motif; a pair (ε1, ε2) on the x-axis denotes that ε1 substitutions are allowed for motif component M1, and ε2 for M2. We can see that EXMOTIF is always faster than RISO. It is 9 times faster when only frequencies are reported, and it can be up to 5 times faster then full occurrences are reported, though for some cases the difference is slight.
Figure 8(d) plots the effect of the quorum threshold. Compared to RISO, EXMOTIF performs much better for low quorum, e.g., for q = 4% EXMOTIF is 4–5 times faster than RISO. Finally in Figure 8(e), as the simple motif lengths increase, the time for both EXMOTIF and RISO increases, and we find that EXMOTIF can be 2–3 times faster.
We also studied the effect of quorum and allowed substitutions. Table 4 shows the comparative results for EXMOTIF and RISO. Here we used the template = NNNNNN[12, 22]NNNNNN to extract motifs from the 1062 subsequences from B. subtilis. We vary the quorum from low (5%) to high (90%), and vary the number of errors ei per simple motif (with more errors allowed for higher quorum). For a comparable output (when only the frequency is reported), EXMOTIF outperforms RISO, especially for high quorum and high number of errors. It is interesting that for this latter case, reporting all occurrences incurs significant overhead. For example for q = 90% and with (e1 = 3, e2 = 3), EXMOTIF is 20 times faster than RISO, but EXMOTIF(#) is 3 times slower!
Table 4.
Comparison of EXMOTIF and RISO for different quorums and allowed substitutions.
| Quorum | #Substitutions | RISO | EXMOTIF | EXMOTIF(#) |
| 5% | (0, 0) | 1.82s | 1.42s | 1.52s |
| 30% | (1, 1) | 63.01s | 58.91s | 64.52s |
| 60% | (2, 2) | 2763.31s | 328.43s | 2317.35s |
| 90% | (3, 3) | 13682.13s | 707.56s | 41464.93s |
The template used is = NNNNNN[12,22]NNNNNN. #Substitutions shows the number of errors (e1, e2) allowed for the two simple components.
Real applications
Discovery of single transcription factor binding sites
We evaluate our algorithm by extracting the conserved features of known transcription factor binding sites in yeast. In particular we used the binding sites for the Zinc (Zn) factors [11]. There are 11 binding sites listed for the Zn cluster, 3 of which are simple motifs. The remaining 8 are structured, as shown in Table 5. For the evaluation, we first form several structured motif templates according to the conserved features in the binding sites. Then we extract the frequent structured motifs satisfying these templates from the upstream regions of 68 genes regulated by zinc factors [11]. We used the -1000 to -1 upstream regions, truncating the region if and where it overlaps with an upstream open-reading frame (ORF). After extraction, since binding sites cannot have many occurrences in the ORF regions, we drop some motifs if they also occur frequently in the ORF regions (i.e., within the genes). Finally, we calculate the Z-scores for the remaining frequent motifs, and rank them by descending Z-scores. In our experiments, we set the minimum quorum threshold to 7% within the upstream regions and the maximum support threshold to 30% in the ORF regions. We use the shuffling program from SMILE [14] to compute the Z-scores. The shufffing program randomly shuffles the original input sequences to obtain a new shuffled set of sequences.
Table 5.
Regulons of Zn cluster proteins.
| TF Name | Known Motif | Predicted Motifs | Num-Motifs | Ranking |
| GAL4 GAL4 chips |
CGGRnnRCYnYnCnCCG | CGG[11,11]CCG | 1634(3346) | 1/1 |
| CAT8 | CGGnnnnnnGGA | CGG[6,6]GGA | 1621(3356) | 147/13 |
| HAP1 | CGGnnnTAnCGGCGGnnnTAnCGGnnnTA | CGG[6,6]CGG | 1621(3356) | 111/146 |
| LEU3 | RCCGGnnCCGGY | CCG[4,4]CGG | 1588(3366) | 2/1 |
| LYS | WWWTCCRnYGGAWWW | TCC[3,3]GGA | 1605(3360) | 33/21 |
| PPR1 | WYCGGnnWWYKCCGAW | CGG[6,6]CCG | 1621(3356) | 1/2 |
| PUT3 | YCGGnAnGCGnAnnnCCGA CGGnAnGCnAnnnCCGA |
CGG[10,11]CCG | 727(4035) | 1/1 |
TF Name stands for transcription factor name; Known Motif stands for the known binding sites corresponding to the transcription factors in TF Name column; Predicted Motifs stands for the motifs predicted by EXMOTIF; Num-Motifs gives the final (original) number of motifs extracted (final is after pruning those motifs that are also frequent in the ORF regions); Ranking stands for the Z-score ranking based on support/weighted support.
Then it computes, for each extracted frequent motif, its support (π) and weighted support (πw) in the shuffled set. For a given frequent motif , let μ and σ be the mean and standard deviation of its support across different sets (about 30) of shuffled sequences. Then the Z-score for each motif is calculated as: . Likewise we can also calculate the Z-score for each frequent motif by using the weighted support (which is also applicable for the repeated structured motif identification problem). As shown in Table 5, we can successfully predict GAL4, GAL4 chips, LEU3, PPR1 and PUT3 with the highest rank. CAT8 and LYS also have high ranks. We were thus able to extract all eight transcription factors for the Zinc factors with high confidence. As a comparison, with the same dataset RISO can only predict GAL4, LEU3 and PPR1.
Discovery of composite regulatory patterns
The complex transcriptional regulatory network in Eukaryotic organisms usually requires interactions of multiple transcription factors. A potential application of EXMOTIF is to extract such composite regulatory binding sites from DNA sequences. We took two such transcription factors, URS1H and UASH, which are involved in early meiotic expression during sporulation, and that are known to cooperatively regulate 11 yeast genes [24]. These 11 genes are also listed in SCPD [1], the promoter database of Saccharomyces cerevisiae. In 10 of those genes the URS1H binding site appears downstream from UASH; in the remaining one (HOP1) the binding sites are reversed. We took the binding sites for the 10 genes (all except HOP1), and after their multiple alignment, we obtained their consensus: taTTTtGGAGTaata[4,179]ttGGCGGCTAA (the lower case letters are less conserved, whereas uppercase letters are the most conserved). Table 6 shows the binding sites for UASH and URS1H for the 10 genes, their start positions, their alignment, and the consensus pattern. The gap between the sites are obtained after subtracting the length of UASH, 15, from the position difference (since the start position of UASH is given). The smallest gap is l = 119 - 110 - 15 = 4 and the largest is u = 288 - 94 - 15 = 179. Based on the on most conserved parts of the consensus, we formed the composite motif template: = NNN[1,1]NNNNN[10,185]NNNNNNNNN (note the 6 additional gaps added to [4,179] to account for the non-conserved positions). We then extracted the structured motifs in the upstream regions of the 10 genes. We used the -800 to -1 upstream regions, and truncated the segment if it overlaps with an upstream ORF. The numbers of substitutions for NNN, NNNNN and NNNNNNNNN were set to ε1 = 1, ε2 = 2 and ε3 = 1, respectively. The quorum thresholds was set to q = 0.7 with the upstreams, and the maximum support within genes was set to 0.1% The rank of the true motif TTT[1,1]GGAGT[10,185]GGCGGCTAA was 290 (out of 5284 final motifs) with a Z-score of 22.61.
Table 6.
UASH and URS1H binding sites.
| Genes | UASH | URS1H | Gap | ||
| Site | Pos | Site | Pos | ||
| ZIP1 | GATTCGGAAGTAAAA | -42 | ==TCGGCGGCTAAAT | -22 | 5 |
| MEI4 | TCTTTCGGAGTCATA | -121 | ==TGGGCGGCTAAAT | -98 | 8 |
| DMC1 | TTGTGTGGAGAGATA | -175 | AAATAGCCGCCCA== | -143 | 17 |
| SPO13 | TAATTAGGAGTATAT | -119 | AAATAGCCGCCGA== | -100 | 4 |
| MER1 | GGTTTTGTAGTTCTA | -152 | TTTTAGCCGCCGA== | -115 | 22 |
| SPO16 | CATTGTGATGTATTT | -201 | ==TGGGCGGCTAAAA | -90 | 96 |
| REC104 | CAATTTGGAGTAGGC | -182 | ==TTGGCGGCTATTT | -93 | 74 |
| RED1 | ATTTCTGGAGATATC | -355 | ==TCAGCGGCTAAAT | -167 | 173 |
| REC114 | GATTTTGTAGGAATA | -288 | ==TGGGCGGCTAACT | -94 | 179 |
| MEK1 | TCATTTGTAGTTTAT | -233 | ==ATGGCGGCTAAAT | -150 | 68 |
| Consensus | taTTTtGGAGTaata | ==ttGGCGGCTAA== | [4,179] | ||
Conclusion and future work
In this paper, we introduced EXMOTIF, an efficient algorithm to extract structured motifs within one or multiple biological sequences. We showed its application in discovering single/composite regulatory binding sites. In the structured motif template, we assume the gap range between each pair of simple motifs is known. In the future, we plan to solve the motif discovery problem when even the gap ranges are unknown. Another potential direction is to directly extract structured profile (or position weight matrix) patterns.
Authors' contributions
All authors contributed equally to this work.
Acknowledgments
Acknowledgements
This work was supported in part by NSF CAREER Award IIS-0092978, DOE Career Award DE-FG02-02ER25538, and NSF grants EIA-0103708 & EMT-0432098. We also thank the anonymous referees for their helpful suggestions.
Contributor Information
Yongqiang Zhang, Email: zhangy0@cs.rpi.edu.
Mohammed J Zaki, Email: zaki@cs.rpi.edu.
References
- Zhu J, Zhang M. SCPD: A Promoter Database of the Yeast Saccharomyces Cerevisiae. Bioinformatics. 1999;15:607–11. doi: 10.1093/bioinformatics/15.7.607. [DOI] [PubMed] [Google Scholar]
- Policriti A, Vitacolonna N, Morgante M, Zuccolo A. Structured Motifs Search. Symposium on Research in Computational Molecular Biology. 2004. pp. 133–139. [DOI] [PubMed]
- Michailidis P, Margaritis K. On-line Approximate String Searching Algorithms: Survey and Experimental Results. International Journal of Computer Mathematics. 2002;79:867–888. [Google Scholar]
- Sinha S, Tompa M. Discovery of Novel Transcription Factor Binding Sites by Statistical Overrepresentation. Nucleic Acids Research. 2002;30:5549–60. doi: 10.1093/nar/gkf669. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Sinha S, Tompa M. YMF: a program for discovery of novel transcription factor binding sites by statistical overrepresentation. Nucleic Acids Research. 2003;31:3586–3588. doi: 10.1093/nar/gkg618. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Pavesi G, Mauri G, Pesole G. A Consensus Based Algorithm for Finding Transcription Factor Binding Sites. Workshop on Genomes: Information Structure and Complexity. 2004.
- Pavesi G, Mauri G, Pesole G. An algorithm for finding signals of unknown length in DNA sequences. Bioinformatics. 2001;17:S207–14. doi: 10.1093/bioinformatics/17.suppl_1.s207. [DOI] [PubMed] [Google Scholar]
- Bailey TL, Elkan C. The value of prior knowledge in discovering motifs with MEME. 3rd Int'l Conference on Intelligent Systems for Molecular Biology. 1995. pp. 21–29. [PubMed]
- Sagot MF. Spelling Approximate Repeated or Common Motifs Using a Suffix Tree. 3rd Latin American Symposium on Theoretical Informatics. 1998. pp. 374–390.
- Friberg M, von Rohr P, Gonnet G. Scoring functions for transcription factor binding site prediction. BMC Bioinformatics. 2005;6:84. doi: 10.1186/1471-2105-6-84. http://www.biomedcentral.com/1471-2105/6/84 [DOI] [PMC free article] [PubMed] [Google Scholar]
- van Helden J, Rios A, Collado-Vides J. Discovering regulatory elements in non-coding sequences by analysis of spaced dyads. Nucleic Acids Res. 2000;28:1808–18. doi: 10.1093/nar/28.8.1808. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Eskin E, Pevzner P. Finding composite regulatory patterns in DNA sequences. Bioinformatics. 2002;18:S354–63. doi: 10.1093/bioinformatics/18.suppl_1.s354. [DOI] [PubMed] [Google Scholar]
- Eskin E, Keich U, Gelfand M, Pevzner P. Genome-wide analysis of bacterial promoter regions. Pac Symp Biocomput. 2003:29–40. [PubMed] [Google Scholar]
- Marsan L, Sagot M. Extracting Structured Motifs Using a suffix Tree – Algorithms and Application to Promoter Consensus Identification. Journal of Computational Biology. 2000;7:345–354. doi: 10.1089/106652700750050826. [DOI] [PubMed] [Google Scholar]
- Carvalho A, Freitas A, Oliveira A, Sagot M. Efficient Extraction of Structured Motifs Using Box-links. String Processing and Information Retrieval Conference. 2004. pp. 267–278.
- Carvalho A, Freitas A, Oliveira A, Sagot M. A highly scalable algorithm for the extraction of cis-regulatory regions. Asia-Pacific Bioinformatics Conference. 2005. pp. 273–283.
- Pisanti N, Carvalho AM, Marsan L, Sagot MF. RISOTTO: Fast extraction of motifs with mismatches. 7th Latin American Theoretical Informatics Symposium. 2006.
- Carvalho AM, Freitas AT, Oliveira AL, Sagot MF. A parallel algorithm for the extraction of structured motifs. 19th ACM Symposium on Applied Computing. 2004. pp. 147–153.
- Brazma A, Jonassen I, Vilo J, Ukkonen E. Pattern Discovery in Biosequences. International Colloquium on Grammatical Inference. 1998. pp. 257–270.
- Apostolico A, Parida L. Incremental Paradigms of Motif Discovery. Journal of Computational Biology. 2004;11:15–25. doi: 10.1089/106652704773416867. [DOI] [PubMed] [Google Scholar]
- Apostolico A, Comin M, Parida L. Conservative extraction of over-represented extensible motifs. Bioinformatics. 2005;21:i9–il8. doi: 10.1093/bioinformatics/bti1051. [DOI] [PubMed] [Google Scholar]
- Zhang M, Kao B, Cheung DWL, Yip K. Mining Periodic Patterns with Gap Requirement from Sequences. ACM Int'l Conference on Management of Data. 2005.
- Benson G. Tandem repeats finder: a program to analyze DNA sequences. Nucleic Acids Research. 1999;27:573–80. doi: 10.1093/nar/27.2.573. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Thakurta D, Stormo G. Identifying target sites for cooperatively binding factors. Bioinformatics. 2001;17:608–621. doi: 10.1093/bioinformatics/17.7.608. [DOI] [PubMed] [Google Scholar]
- Zaki MJ. SPADE: An Efficient Algorithm for Mining Frequent Sequences. Machine Learning Journal. 2001;42:1–31. [Google Scholar]