Abstract
Background
cis-Regulatory modules (CRMs) of eukaryotic genes often contain multiple binding sites for transcription factors. The phenomenon that binding sites form clusters in CRMs is exploited in many algorithms to locate CRMs in a genome. This gives rise to the problem of calculating the statistical significance of the event that multiple sites, recognized by different factors, would be found simultaneously in a text of a fixed length. The main difficulty comes from overlapping occurrences of motifs. So far, no tools have been developed allowing the computation of p-values for simultaneous occurrences of different motifs which can overlap.
Results
We developed and implemented an algorithm computing the p-value that s different motifs occur respectively k1, ..., ks or more times, possibly overlapping, in a random text. Motifs can be represented with a majority of popular motif models, but in all cases, without indels. Zero or first order Markov chains can be adopted as a model for the random text. The computational tool was tested on the set of cis-regulatory modules involved in D. melanogaster early development, for which there exists an annotation of binding sites for transcription factors. Our test allowed us to correctly identify transcription factors cooperatively/competitively binding to DNA.
Method
The algorithm that precisely computes the probability of simultaneous motif occurrences is inspired by the Aho-Corasick automaton and employs a prefix tree together with a transition function. The algorithm runs with the O(n|Σ|(m|| + K|σ|K) ∏i ki) time complexity, where n is the length of the text, |Σ| is the alphabet size, m is the maximal motif length, || is the total number of words in motifs, K is the order of Markov model, and ki is the number of occurrences of the ith motif.
Conclusion
The primary objective of the program is to assess the likelihood that a given DNA segment is CRM regulated with a known set of regulatory factors. In addition, the program can also be used to select the appropriate threshold for PWM scanning. Another application is assessing similarity of different motifs.
Availability
Project web page, stand-alone version and documentation can be found at http://bioinform.genetika.ru/AhoPro/
Background
During the past few years, a number of computational tools have been designed [1-3] for locating potential transcription factor binding sites (TFBSs) in nucleotide sequences, e.g., in compilations of sequences upstream of putative co-regulated genes. In parallel, experimental approaches were developed [4], which allowed identification of binding motifs for many different transcription factors. Experimental [5] and bioinformatical [6] studies demonstrated that sequences of regulatory DNA that bind transcription factors can exhibit many different types of architecture. In eukaryotes TFBSs found in DNA sequences often form rather dense clusters: this was demonstrated both by experimental [5,7] and computational [8,9] methods. Such clusters can contain sites binding the same factor or several different factors [10]. The cis-regulatory module (CRM) in this case contains respectively homotypic or heterotypic clusters of motifs specifically recognized by binding proteins [11].
The particular arrangement of motifs in a homotypic or heterotypic cluster is not random, and it is commonly accepted, that the motif arrangement within a CRM is important for its functionality [12-20]. Bioinformatics studies indicate that antagonistic factors often bind to overlapping sites [21] whereas synergetic factors are often positioned within a fixed distance [20], often close to the multiple of 10.2 bp, the DNA double-helix pitch value [21].
Non-random arrangements of TFBSs within regulatory segments of DNA sequences are exploited in several TFBS identification tools, and it was observed that cooperativity-based discrimination of TFBSs surpasses the performance of models for individual TFBSs [22].
On observing a cluster of TFBSs in some genome segment one can calculate the probability of observing similar site arrangements in a random sequence. This idea of evaluating the statistical significance of heterotypic clusters of sites was implemented in many programs including ClusterDraw [23], ModuleSearcher [24], MCAST [25], eCIS-ANALYST [26], Cister [27], Cluster-Buster [28] and TargetExplorer [29]. At the moment, such programs use empirical procedures like motif counting in biological and simulated sequences to assess the significance of observed site clustering. But it is highly desirable to have a good statistical measure of site clustering, and we believe that the best measure is the p-value of obtaining the observed cluster by chance in a random sequence of a Markov or Bernoulli (common name for Markov chain of order 0) type. In the case of heterotypic clusters one needs to take into account possible overlapping occurrences of different motifs, a problem that was considered difficult until now [30]. In the case of homotypic clusters, an approximate statistical scoring function was constructed [8,31]; this approach has been implemented in algorithms like FLYENHANCER [32], SCORE [33], and CLUSTER [34]. However, this approximation performs poorly for highly overlapping TFBSs. One cannot ignore site overlapping if the motifs are fuzzy (highly degenerate), which is often the case for so-called "shadow sites" [31]. In the case of heterotypic clusters, competing factors can bind even to very well determined motifs that overlap.
Representation of protein binding motifs in nucleotide sequences
Experimental methods on protein binding to DNA usually locate some DNA segment, or word in DNA text, as a probable binding target. Proteins can bind to similar DNA words [4], the whole assembly of which can be called a motif. The simplest motif representation is the enumeration of sequences that can be bound by a transcription factor (TF) [35]. Sometimes, information about binding sites can be found in SELEX [36,37] or Protein Binding Microarray (PBM) experiments [38]. However, it is possible that such experiments do not give the exhaustive list of sequences of binding sites, so one needs to expand the list of putative binding sites using an appropriate criterion, which brings about the problem of the generalization of several known examples.
For instance, several words aligned with mismatches, can be generalized to IUPAC string (like RSTGACTNMNW for AP-1 binding sites [39]) by disregarding correlated substitutions in different motif positions [40]. Another example of generalization is the set of words that can deviate from a consensus word for less than a given number of mismatches.
The most popular way to represent binding sites is a Position Weight Matrix (PWM), which is also called position-specific weight matrix (PSWM) or position-specific scoring matrix (PSSM) [41]. For a text with length D over an alphabet Σ with |Σ| symbols, a PWM is a |Σ| × D matrix: each row corresponding to a symbol of the alphabet Σ, and each column to a position in the motif. For DNA texts, one has Σ = {A, C, G, T}. The PWM score is defined as , where i represents a position in the D-substring, ω(i) the symbol at position i in the substring, and mα, i the score in row α, column i of the matrix. So, given a cutoff value, one gets a list of D-sequences that score higher than this cutoff; thus representing possible DNA binding sites for the protein.
Any of the three motif representations above can be converted to a list of words. The same is true for many other representations of motifs. In this study, we consider only the motifs that can be represented as a set of words.
P-value for clusters of motif occurrences, problem formulation
The objective of this work is to develop a statistical criterion to assess clustering of TFBS. Intuitively, a TFBS cluster is a DNA segment simultaneously containing "too many" TFBSs for given factor proteins; such a segment can often operate as a CRM regulated by these TFs. From a formal point of view, the problem we address here is as follows. Let s sets of words be given. Typically, each set i is associated to a TF motif. Given a s-tuple of integers (k1, ..., ks), we compute the corresponding p-value, that is the probability to find at least ki occurrences of words from each set i in a random text of size n. We assume that the texts where motifs are searched are randomly generated by a Bernoulli process or a Markov model of order K. If (k1, ..., ks) occurrences of motifs are found in a DNA segment, the p-value can be used to infer if such numbers of occurrences could be found by chance.
Related work
Most previous works address counting problems for one set of several words . In contrast, in this paper we deal with a separate counting for several sets of several words , each set j represents one TFBS motif.
All methods of solving the problem of p-value calculations for multiple occurrences of words from a set study some basic languages. Let Ln (; k) be the set of texts of length n containing at least k occurrences of . The desired p-value would therefore be the probability P (Ln (; k)). Let be the set of texts of all lengths that contain exactly k words of , the last one occurring as a suffix [42]. For any Hj in , let be the subset of where Hj is a suffix. One observes that a text contains at least k occurrences if and only if it admits a prefix in . One defines (p) as the probability that a text of size p be in set . If no word in is a subword of another word in , the probability P (Ln (; k)) to find at least k occurrences of words from in a random text of length n satisfies
Therefore, one tries to compute the sequence of ( (p)) values.
Linear induction
In the first class of methods [43-46], one computes, implicitly or explicitly, probabilities P (Ln (; k)) up to a given text length n. Such methods are intrinsically linear in n. In [43-46] one relies on a recurrence relation on (n) that extends the one originally given in [47]. Typically, one step will cost O (||m), where is a set of words of length m and || is its cardinality. Time complexity is O (n||m) and, relying on a combinatorial property, [44] achieves optimal space complexity O (|| log ||m). However the authors of [44] do not consider several motifs occurrences and restrict themselves to the Bernoulli model. The authors of [43] consider the Markov model, still using one motif for TFBS.
Algebraic Formulae
In a second class of methods [47-52], a preprocessing computes generating functions
In a second step, probabilities P (Ln (; k)) are either extracted from the generating function or approximated.
In [49,53], (z) are the solutions of a system of equations. To derive these equations, the authors build an automaton that recognizes these languages (one can prove that they are regular).
A language approach [50] or an induction [48] leads to a formal expression that depends on the words overlaps. The main drawback is that these methods need to compute the determinant of a matrix of polynomials with a huge dimension, e.g. O (||). This O (||2) symbolic computation may be more expensive than the extraction step or the linear computation above, that involve arithmetic operations on real numbers.
When the preprocessing step is achievable, the extraction step is amenable to the solution of a linear recurrence of degree m||; therefore, its complexity is O (m||n) and a classical optimization yields O (m|| log n). There exists some good implementations that are numerically stable. One may cite the REGEXPCOUNT [54] or EXCEP [55] programs that rely on Fast Fourier Transform.
Finally, approximations are available, the computation of which is constant with respect to n, but not to . One approach is the compound Poisson approximation [56], but this approximation is not precise enough [57]. Asymptotic results can also be derived from the algebraic formulae above [44,58], not needing an explicit expression for (z), and therefore avoiding the expensive determinant computation. Time complexity, typically, is the one for computing all possible overlaps, that is approximately O (||2). This yields extremely precise results when the expectation of the number of occurrences, nP (H) is very small [59] or close to 1 [51] (the case studied the most often). Case nP (H) ~2 is achieved in [60]. Nevertheless, extension to larger values of k or multioccurrences and multisets is still open.
Methods
Here we consider in detail the approach we suggest.
A motif assigned to a TF is a finite set of words = (H1, ..., Hr) where each word represents one putative TF binding site in DNA. Note that words in motif can generally be of different lengths. However, no word from can contain another word from as a substring. We consider, as an occurrence of motif in text T, any occurrence of any word j ∈ in T. Below all texts and words in motifs are sequences on a given alphabet Σ.
Let () be s different motifs. Our objective is to calculate the probability (p-value) that motifs () have respectively at least (k1, ..., ks) possibly overlapping occurrences in a random text Tn.
To be more precise, there is a probability distribution defined on the set Σn of all texts of length n in the alphabet Σ; the most widely used models are random Bernoulli trials and a Markov model of order K. Denote as Ln (; k1, ..., ks) the set of all texts of length n containing at least ki possibly overlapping occurrences of each motif i; i = 1, ..., s. Then the desired p-value is the probability P (Ln (; k1, ..., ks)) of the set Ln (; k1, ..., ks) with respect to the given probability distribution on Σn.
Our approach to the calculation of this p-value is similar to that published in [61], which was used there to calculate seed sensitivity in local alignment search. The approach exploits the fact that the algorithm of Aho and Corasick [62] can be modified to efficiently determine whether a given text belongs to the set Ln (; k1, ..., ks) or not. Ideas published in [61] and [62] can be adopted to compute the probability P (Ln (; k1, ..., ks)) that the random text Tn ∈ Σn belongs to the set Ln (; k1, ..., ks).
We start from the simplest case of one motif for which we calculate the probability P (Ln (; 1)) that text Tn contains at least one occurrence of the motif with respect to a Bernoulli probability distribution. More complicated cases (arbitrary number of occurrences; arbitrary number of motifs; Markov distribution) will be discussed in the following sections.
Construction of Aho-Corasick traversal
Aho and Corasick [62] have proposed the algorithm determining if a given text T contains an occurrence of a word from a given set . The basic data structure is a prefix tree which is a variant of the classical trie [42] that may be built on the set of words . Let denote the set of prefixes of these words. In the following, we identify a word q ∈ with node Node (q) at the end of the branch labeled by q. In particular, the root is identified with the empty string ε. The length of a prefix is the depth of Node (q).
The classic Aho-Corasick algorithm is a tree traversal determined by a transition function defined as follows. For any pair (p, a) in × Σ, δ (p, a) is the largest suffix of concatenation pa that belongs to . Remark that δ (p, a) = pa iff pa ∈ .
Given a text T read from left to right, let T [i] denote the letter of T at position i. Let qi be the largest suffix in text T[1] ⋯ T [i] that belongs to . The sequence of nodes visited during the traversal are defined by words qi that satisfy the inductive relationship
| ∀i ≥ 0, qi+1 = δ (qi, T [i + 1]), |
with the initial condition q0 = ε.
Example: Let be the set {AAA, AAC, ACA, ACA, CCT}. The corresponding tree is depicted in Figure 1. Values of δ function are given in Table 1. Aho-Corasick traversal of tree according to text T = 'ATGCCAACCTT' produces the following sequence of nodes {qi}i ≥ 1 in (the numbers of corresponding nodes in Figure 1 are shown in square brackets): A[1], ε[0], ε[0], C[2], CC[5], A[1], AA[3], AAC[7], ACC[9], CCT[10], ε[0].
Figure 1.
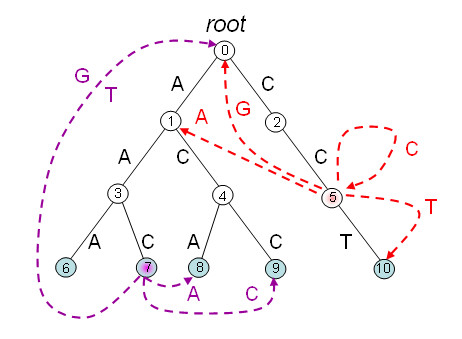
Tree for the set = {aaa, aac, aca, acc, cct} with dashed links for δ function. Tree for the set = {AAA, AAC, ACA, ACC, CCT}. Dashed colored links represent δ function for internal node (5) – in red, and for marked node (7) corresponding to the word AAC ∈ – in purple.
Table 1.
Values of δ function for the set = {aaa, aac, aca, acc, cct}.
| q\α | A | C | G | T |
| 0 | 1 | 2 | 0 | 0 |
| 1 | 3 | 4 | 0 | 0 |
| 2 | 1 | 5 | 0 | 0 |
| 3 | 6 | 7 | 0 | 0 |
| 4 | 8 | 9 | 0 | 0 |
| 5 | 1 | 5 | 0 | 10 |
| 6 | 6 | 7 | 0 | 0 |
| 7 | 8 | 9 | 0 | 0 |
| 8 | 3 | 4 | 0 | 0 |
| 9 | 1 | 5 | 0 | 10 |
| 10 | 1 | 2 | 0 | 0 |
Values of δ (q, α) function for q ∈ Q and α = A, C, G, T constructed for the set = {AAA, AAC, ACA, ACC, CCT}.
and transition function δ can be efficiently constructed with an algorithm proposed by Aho and Corasick [62]. Both time and space of the algorithm is proportional to the sum of lengths of all words from .
The combination of tree and transition function δ allows solving numerous pattern matching problems: search of the first occurrence of a word from a given set, search of all occurrences, word counting, etc.
Bernoulli text model. Probability to find at least one occurrence of a single motif
In this section we consider the simplest case. One computes the p-value for a single motif in a text Tn of length n, assuming that Tn is generated by independent Bernoulli random trials over alphabet Σ. The algorithm computes probabilities P (Ln (; 1)) by induction on n.
To describe the algorithm we divide the set Σi of all texts Ti of length i into classes that do and do not contain occurrences of .
Definition 1 A text Ti belongs to class Ci (0; q) iff
1. Length of Ti is i,
2. Ti does not contain words from ,
3. A traversal AC (, Ti) ends at node q.
A text Ti belongs to class Gi (1) iff
(i) Length of Ti is i,
(ii) Ti does contain at least one occurrence of a word from .
For a given number i larger than m, the union for classes Ci (0; q), where q is in and the class Gi (1) form a partition of the set Σi of all texts of length i, i.e., any texts of length i belongs either to a class Ci (0; q) for some q in , or to a class Gi (1). Indeed, condition 3. means that the largest suffix of Ti in is q. It follows from condition 2. that classes Ci (q; 0) are empty if q is in . A text Ti of length i is in Gi (1) if and only if a node of was visited during the traversal.
Let P (Cn (0; q)) and P (Gn (1)) denote probabilities that a text Tn belongs to class Cn (0; q) and Gn (1), respectively. Then, Ln (; 1) = Gn (1); therefore the desired p-value P (Ln (; 1)) is equal to P (Gn (1)).
The algorithm calculates probabilities P (Ci (0; q)) and P (Gi (1)) using induction on length i. For i = 0, these probabilities obviously comply with: P (C0 (0; ε)) = 1; P (C0 (0; q)) = 0, for any q ≠ ε; P (G0 (1)) = 0.
The values of P (Ci+1 (0; q)) and P (Gi+1 (1)) are calculated using values of P (Ci (0; q)) and P (Gi (1)). Therefore, the needed space is proportional to the size of (see section Extensions and complexity below).
Calculation of values P (Ci+1 (0; q)) and P (Gi+1 (1)) is based on the following observations. Let U be a set of texts of the same length over the alphabet Σ, P (U) the probability of U in the Bernoulli model and a a character in Σ. Let U·a be the set of all possible concatenations, i.e., U·a = {xa|x ∈ U}. And in the case of the Bernoulli model
| P (U·a) = P (U) P (a). |
Then the following relations hold for any i ∈ {1, ..., n - 1} and Σ:
(i) if the text Ti contains a word from then all its concatenations with characters from Σ would contain a word from ; i.e.,
| Gi (1)·a ⊂ Gi+1 (1). |
(ii) if the text Ti does not contain a word from and belongs to Ci+1 (0; q), i.e., ends with q ∈ , then its concatenation Ti·a belongs to the class determined by the result of the Aho-Corasick transition function δ (q, a); i.e.,
| if δ (q, a) ∈ , then Ci (0; q)·a ⊂ Ci+1 (0; δ (q, a)) |
| otherwise Ci (0; q) ⊂ Gi+1 (1). |
Remembering that classes Ci (0; q) for different q and Gi (1) form a partition of Σi, we obtain the following relation for the texts containing words from :
Similarly, classes of texts that do not contain words from satisfy
Classes Ci (0; q) for different q in and Gi (1) form a partition of Σi; classes Ci (0; q) are empty if q is in . Relations (5) and (6) with the help of (1) yield the recursive expressions for probabilities P (Ci+i (0; q)) and P (Gi+1 (1)) in the Bernoulli case:
The run-time for each step of the computation of Ci+1 (0; q) and Gi+1 (1) is O (||·|Σ|); therefore the total time of all n stages of p-value computation is O (||·|Σ|·n).
The approach described in this section can be readily extended to the case of multiple occurrences of motif . The detailed procedure can be found in Additional file 1.
Bernoulli text model. Probability to find multiple occurrences of multiple motifs
DNA transcription is usually regulated with several factors simultaneously interacting with DNA and specifically recognizing different DNA sites. Individual regulatory segment of DNA can contain many binding sites for several factors, often substantially overlapping with each other [5]. This brings about a problem of studying of co-occurring motifs.
Let () be s different motifs. Our objective is to calculate the probability that motifs () have respectively at least (k1, ..., ks) possibly overlapping occurrences in the random text Tn of the length n. This p-value is the probability P (Ln (; k1, ..., ks)) to obtain text Tn belonging to the set of texts Ln (; k1, ..., ks). In this section, we will suppose that the probability of each text is given by Bernoulli model. The Markov case will be considered in the next subsection. The recursion for multiple occurrences of multiple motifs obtained here is rather tricky. Therefore we suggest the reader to see Additional file 1 where we describe the recursion for the simpler case of multiple occurrences of a single motif
Let us consider the union of individual motifs . It contains all words that belong to any of motifs i. The tree is constructed for the overall set , its nodes contain all possible prefixes of all motifs from (). A node of the tree q ∈ can belong to some motif k or simultaneously to several different motifs from {j}1≤j≤s. Let each node q ∈ be marked with numbers j of motifs j to which it belongs. Nodes, corresponding to proper prefixes of , remain unmarked. The transition function is defined as it was defined in the case of a single motif for the unified motif .
All texts Tn of length n are classified into classes depending on occurrences of different j. In this case it is difficult to introduce the target class G, since when the target number of occurrences ki is attained for some motif i, the corresponding value kj may not yet be attained for another motif j. Therefore we need to introduce the occurrence index of a set of motifs.
Definition 2 Let the target number of occurrences of motif i be ki. Then, the occurrence index (l1, ..., ls) of a set of motifs () in the text Tn containing li possibly overlapping occurrences of each i is an s-vector the ith component of which can be calculated as follows:
Definition 3 A text Ti belongs to class Ci (λ1, ..., λs; q), 0 ≤ λi ≤ ki iff
1. Length of Ti equals i,
2. The occurrence index of motifs () in text Ti is equal to (λ1, ..., λs),
3. A traversal AC (, Ti) ends in node q.
A text Ti belongs to class Gi (k1, ..., ks) if it belongs to the union of classes
The desired p-value P (Ln (; k1, ..., ks)) is equal to P (Gn (k1, ..., ks)). The value is calculated iteratively. Again, we have a sum over all possible tree nodes q and symbols a. Now, q', the image of the transition function δ (q, a) can belong simultaneously to several motifs {j}1≤j≤s. Thus, the resulting probability P (Ci+1 (λ1, ..., λs; q')) that text Ti+1 belongs to class Ci+1 (λ1, ..., λs; q') calculates as
where the summation in the second sum is performed over all allowed s-tuples of indexes (r1, ..., rs) which together make the set of s-tuples J. A s-tuple of indexes (r1, ..., rs) belongs to J if it complies with the following conditions:
1. if q' ∉ j then rj = λj,
2. if q' j and λj <kj then rj = λj - 1,
3. if q' ∈ j and λj = kj then rj = kj or rj = kj - 1.
Implementation details
Our basic data structure is the prefix tree; we use its standard representation [42] [see also Additional files 2 and 3 for Tree construction from PWM motif representation]. Each tree node q ∈ is supplied with several additional variables.
At stage (i + 1) of probability computation the values P (Ci+1 (λ1, ..., λs; q)) become computed from the values P (Ci (λ1, ..., λs; q)) obtained at the previous stage of induction. Therefore, at stage (i + 1), one no longer needs the values calculated at stage (i - 1). Thus, each node is supplied with two k1 × ⋯ × ks-arrays of real values C0 and C1 for storing P (Ci (λ1, ..., λs; q)) and P (Ci+1 (λ1, ..., λs; q)) for different λj. C0 is used to store probabilities for even text lengths while C1 for odd.
In implementation the calculation of values P (Ci+1 (λ1, ..., λs; q')) from P (Ci (λ1, ..., λs; q)) for all q', q ∈ and (λ1, ..., λs): 0 ≤ λj ≤ kj, 1 ≤ j ≤ s, is performed in the parallel way. Initially we set all the values P (Ci+1 (λ1, ..., λs; q')) to 0. Then we look over all tuples (r1, ..., rs; q), where q ∈ and (r1, ..., rs): 0 ≤ rj ≤ kj, 1 ≤ j ≤ s. For each tuple (r1, ..., rs; q) and all letters a ∈ Σ we find the prefix q' = δ (q, a) and the value P (Ci (r1, ..., rs; q))·p(a). Then we add P (Ci (r1, ..., rs; q))·p(a) to the value P (Ci+1 (λ1, ..., λs; q')) where (λ1, ..., λs; q') meet the conditions inverse to those of formula (11):
1. if q' ∉ j then λj = rj,
2. if q' ∈ j and rj <kj then λj = rj + 1,
3. if q' ∈ j and rj = kj then λj = rj.
At the stage i = n the desired p-value is the sum
Markov text model
Tree approach and the recursion (11) can be readily extended to calculate p-values of motif occurrences in random texts generated by the Markov model of order K. Given the order K of the Markov model, the probability p(a) in (11) depends on K previous letters. Thus, if the length |q| of the prefix q is less than K, one cannot calculate p(a) knowing only the prefix q. To overcome this we divide each class Ci (r1, ..., rs; q), where |q| = d <min (K, i) into subclasses Ci (r1, ..., rs; q, w); each subclass corresponds to a word w of length min (K, i) - d. Then, a text Ti of length i belongs to class Ci (r1, ..., rs; q, w) if the suffix of Ti of length min (K, i) equals to w·q.
Figure 2 gives an example for Markov model of order K = 1. The tree is constructed for the set = {AAA, AAC, ACA, ACC, CCT}. The text T = ATGCCAACCTT produces the following sequence of nodes {qi}i≥1 (the numbers of the corresponding nodes in Figure 2 are shown in square brackets): A[4], (ε, T)[3], (ε, G)[2], C[5], CC[8], A[4], AA[6], AAC[10], ACC[12], CCT[13], (ε, T)[3].
Figure 2.
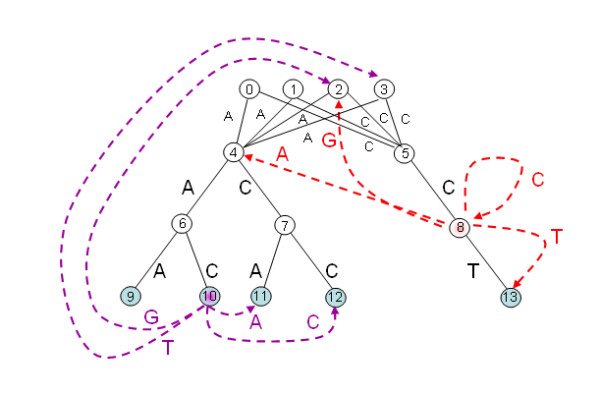
Tree for the set = {aaa, aac, aca, acc, cct} with dashed links for δ function under Markov(1) model. Tree for the set = {AAA, AAC, ACA, ACC, CCT} under Markov model of order 1. Dashed colored links represent δ function for internal node (8) – in red, and for marked node (10) corresponding to the word AAC ∈ – in purple.
The recursive equations for probabilities P (Ln (; 1)), P (Ln (; k)), and P (Ln (; k1, ..., ks)) can be obtained from the corresponding formulae (7-8), (11–13) and (16) by substituting probabilities p(a) with p(a|t[1] ⋯ t [K]), where
The Markov extension is currently implemented for K = 1.
Complexity
To resume, the computation of P (Ln (; k)) for one set requires a computation of for i ≤ n. For each iteration, the time complexity is O (k|| |Σ|), where |Σ| is the size of the alphabet. One traverses the tree n times. As || is upper bounded by (m||), where m is the maximal length of word in , this yields the overall O (nkm|||Σ|) time complexity and a O (km||) space complexity.
When several sets are involved, the number of nodes in the tree becomes O (m||) with m equal to the maximal length of word in . Additional memory in each node is ∏i ki. Therefore, the time complexity is O (nm|Σ|∏i ki||) and the space complexity is O (m ∏i ki ||). In the Markov model of order K, one memorizes |Σ|K - d predecessors for each node at depth d, 0 = d <K. In other words, the number of classes becomes (m|| + K|Σ|K). Therefore, the space memory is O ((m|| + K |Σ|K) ∏i ki) and the running time is O (n|Σ|(m|| + K |Σ|K )∏i ki). This additive increment compares favorably to simple induction methods [45,53] that introduce a multiplicative O (K|Σ|K) factor in time and space complexity for the Markov(K) model.
Results and discussion
We developed an algorithm for precise calculation of the p-value for multiple occurrences of multiple motifs with possible overlaps. The running time is linear in the text length and depends on the alphabet size, the maximal motif length, the number of words in the motifs, and the number of occurrences of each motif. The algorithm was implemented in the AHOPRO software. Below we give examples of how p-values can be used for studying gene regulation in silico, particularly for selecting optimal cutoff values for motifs represented by PWMs. In the subsection 'Comparison with simulation and approximation methods' we compare our p-value computations with the result of Monte Carlo simulations and the Poisson approximation. Our results confirm the accuracy of our algorithm and show in what cases the Poisson approximation [8,11] cannot be employed. In the subsection 'Optimal cutoffs', we apply AHOPRO to choose an appropriate cutoff score for Position Weights Matrices. In the subsection 'Assessment of gene regulation', we show how AHOPRO can be used for studying regulatory regions containing heterotypic clusters of TFBSs to distinguish genes that are regulated by given transcription factors from those that are not.
As a model example, we use in this section data published in [34] on regulatory clusters in D. melanogaster. This compilation includes information on
(i) known binding motifs for transcription factors,
(ii) known CRM regions, and
(iii) known regulatory interactions.
Comparison with simulation and approximation methods
In our first example we use the even-skipped stripe 2 enhancer (eve2) [63] of length 728 bp that is known to contain binding sites for TFs bicoid, kruppel and hunchback. Below we compare p-values calculated by the AHOPRO program and those calculated using compound Poisson approximation with p-values computed through Monte Carlo simulations.
AhoPro and Monte Carlo comparisons
Table 2 displays results of comparison of p-values calculated with AHOPRO and with Monte Carlo simulation assuming the Bernoulli model M0. The corresponding results for the first order Markov model M1 are displayed in Table 3. Letters probabilities for M0 and the transition matrix for M1 were evaluated from eve2 sequence. We used the PWM cutoff values taken from [34], i.e., 5.3, 5.0, and 6.2 for bicoid, kruppel, and hunchback respectively. With these threshold values in sequence eve2 we have found 3, 4, and 2 occurrences of motifs of each type respectively. In Tables 2 and 3 we listed the p-values, i.e, the probabilities to find no less than the observed number of occurrences of motifs in a random text of length L, where L is the length of eve2 enhancer. The number of Monte Carlo simulations was set to 106 everywhere, except for the triplet (bcd&kr&hb), where we did 107 simulations. The probability to find the observed number of occurrences of (bcd&kr&hb) simultaneously in the same simulated sequence is extremely low; thus we increased the number of simulations so that the product of the probability by the number of simulations be greater than 1.
Table 2.
Comparison of p-values calculated by the AHOPRO program, by Monte Carlo simulations and by compound Poisson distribution formula under the M0 model
| MOTIF, CUTOFF | OCC. | AHOPRO | MONTE CARLO | POISSON | AHOPRO/MC | AHOPRO/POISSON |
| bcd, 5.3 | 3 | 0.012 | 0.012 | 0.010 | 1.00 | 1.10 |
| kr, 5.0 | 4 | 0.0044 | 0.0044 | 0.0033 | 1.01 | 1.34 |
| hb, 6.2 | 2 | 0.013 | 0.013 | 0.012 | 0.99 | 1.04 |
| bcd & kr | 3&4 | 0.00025 | 0.00026 | 3.6E-05 | 0.99 | 7.10 |
| bcd & kr & hb | 3&4&2 | 6.54E-06 | 5.8E-06 | 4.34E-07 | 1.13 | 7.13 |
Comparison of p-values calculated for the Markov(0) model by the AHOPRO program with p-values calculated by Monte Carlo simulations and by Poisson formula for motifs of D. melanogaster developmental transcription factors bicoid, kruppel and hunchback.
Table 3.
Comparison of p-values calculated by the AHOPRO program, by Monte Carlo simulation and by compound Poisson distribution formula under the M1 model
| MOTIF, CUTOFF | OCC. | AHOPRO | MONTE CARLO | POISSON | AHOPRO/MC | AHOPRO/POISSON |
| bcd, 5.3 | 3 | 0.013 | 0.014 | 0.012 | 0.998 | 1.11 |
| kr, 5.0 | 4 | 0.011 | 0.011 | 0.008 | 1.01 | 1.43 |
| hb, 6.2 | 2 | 0.14 | 0.14 | 0.11 | 0.9987 | 1.25 |
| bcd & kr | 3&4 | 0.00051 | 0.00051 | 9.62E-05 | 0.9991 | 5.34 |
| bcd & kr & hb | 3&4&2 | 6.9E-05 | 6.97E-05 | 1.08E-05 | 0.9889 | 6.36 |
Comparison of p-values calculated by the AHOPRO program for the Markov(1) model with those calculated by Monte Carlo simulations and by Poisson formula for motifs of D. melanogaster developmental transcription factors bicoid, kruppel, and hunchback.
The results of comparison of the AHOPRO computation with those obtained from simulated random sequences presented in Tables 2 and 3 confirm the accuracy of our algorithm.
Poisson approximation
In practical application, compound Poisson distribution [64] is widely used to assess p-values of multiple motif occurrences [2,8,34,65]. Here we apply it to compute the probability to observe the given number of motif occurrences when the probabilities of individual words are calculated adopting the M0 or M1 models described above. The results of the comparison given in corresponding columns in Tables 2 and 3 show that the p-value calculated using Poisson approximation can be significantly underestimated. This happens most probably because the Poisson approximation does not take into account possible overlaps between motif occurrences and considers motif occurrences as independent. The error increases when the p-value is calculated for simultaneous occurrences of several factors, as it is done in the last two rows. In this case, the Poisson approximation p-value for a combination of several TFs is calculated as a product of p-values calculated independently for each TF. Actually, the motif occurrences can overlap especially when the motifs resemble each other, thus there is no independence, which brings about the error.
Optimal cutoffs
Below, we use AHOPRO to determine the optimal cutoff values for PWMs of regulatory factors, given the sequences of regulatory region assumedly interacting with the factors. The distribution of occurrences of TF binding sites in corresponding experimentally confirmed regulatory regions is strongly biased [34]. In CRMs binding sites often tend to occur in clusters, which is not the case for random sequences.
Different cutoff values correspond to different numbers of putative binding sites of different quality. The higher the cutoff value, the closer the motif occurrences are to the consensus and the smaller the number of motif occurrences. Therefore, for a given factor it is reasonable to select a cutoff value that minimizes the probability of finding in the random sequence the number of motif occurrences observed in the sequence of the regulatory region.
As an example, we considered again transcription factors bicoid, kruppel, which are known to regulate the even-skipped stripe 2 (eve2) enhancer. To select the optimal cutoff value we used the following procedure: first, in the sequence of eve2 we counted occurrences of motifs with a score greater than the cutoff with cutoff values varied from 3 to 8.5. Therefore, each pair of cutoff values (S1, S2) corresponded to (k1, k2) occurrences for motifs of bicoid and kruppel respectively. For each pair (k1, k2), we computed p-value Pn (k1 (S1), k2 (S2)), which is denoted below as P (S1, S2). That is the probability to obtain at least k1 occurrences of bicoid, with scores greater than S1, and at least k2 occurrences of kruppel, with scores greater than S2. In Figure 3, a 3D-surface is shown, where (x, y, z) corresponds to (S1, S2, - log10 P (S1, S2)), the cutoff value for bicoid motif, the cutoff value for kruppel motif and -logarithm of the corresponding p-value calculated for the M1 model respectively. The view to the surface from the above is shown in Figure 3C. The maximal value for – log10 P (S1, S2), 6.3044, is attained when the bicoid cutoff is equal to S1 = 5.1 and the kruppel cutoff is equal to S2 = 5.6. With such cutoff values in the sequence of the eve2 enhancer there are k1 = 6 and k2 = 4 occurrences of bicoid and kruppel motifs defined by corresponding PWMs. We believe that the sites that are found with this optimal p-value are the best candidates for functional TF binding sites.
Figure 3.
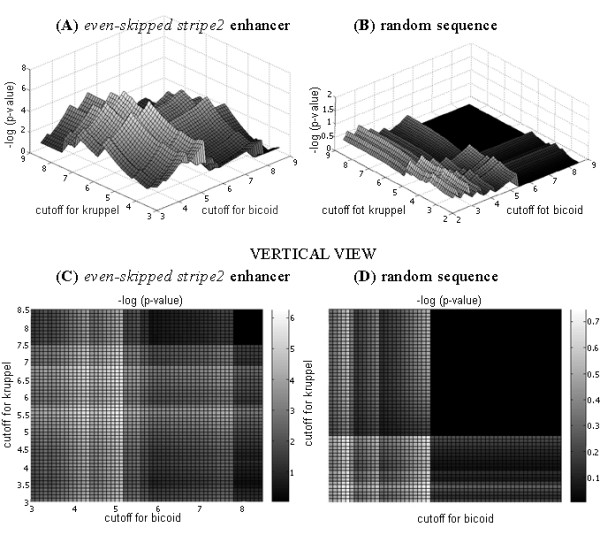
P-value distribution for eve2 and random sequences. Distribution of log10 (Pvalue) calculated for the M1 model as a function of cutoff values for PWMs for BICOID and KRUPPEL in the even-skipped stripe 2 enhancer (A), in a random sequence (B). View from above: eve2 sequence (C), random sequence (D).
For comparison, we simulated random sequences with the same length as the eve2 enhancer and the same dinucleotide probabilities. In most of simulated sequences, for the cutoff values for bicoid and kruppel equal to (S1, S2) = (5.1, 5.6) we found no more than one occurrence of each motif. The average number of occurrences is 0.54 for bicoid and 0.31 for kruppel. The average p-value is 0.633. We took one of the random sequences and compared p-values calculated for various cutoff values in this random sequence (Figures 3B, 3D) and in the real biological sequence of the eve2 enhancer (Figures 3A, 3C). One can see that there are two major differences between p-value distributions in really regulated sequences and in the random sequence. First, p-values in the random sequence are much greater than those in the enhancer sequence. In particular, maximal – log(pvalue) for this random sequence is about 1.02 which is 6.17 times smaller than maximal – log(pvalue) for the enhancer sequence (see also Table 4). Second, the shapes of p-value distributions are different. For the enhancer sequence, there are only few distinct peaks (4.3, 5.6),(4.3, 6.8), (5.1, 5.6), (5.1, 6.8) whereas for the random sequence we see ridges between (2.2, 2.0) and (2.2, 4.8), and (2.8, 2.0) and (2.8, 4.8). As we expected, it is impossible to choose the appropriate cutoff for PWMs of factors from the random sequence data (Figures 3B and 3D).
Table 4.
Comparison of p-values and cutoff for different sets of DNA sequences
| regulatory regions bicoid regulated | minimal pvalue | Cut-off | regulatory regions not regulated by bicoid | minimal pvalue | Cut-off | random seq. | minimal pvalue | Cut-off |
| Btd crm | 3.24E-05 | 3.4 | Gt p. enh. | 0.023 | 2.7 | seq. 1 | 0.16 | 2.6 |
| Hb P2 | 4.13E-05 | 3.7 | Hb upstream enh. | 0.053 | 4.4 | seq. 2 | 0.12 | 1.7 |
| Kni cis element | 0.01 | 5.3 | Eve stripe 4+6 enh. | 0.41 | 3.6 | seq. 3 | 0.25 | 1.2 |
| Kr CD-1 enh. | 0.0001 | 5.1 | Eve stripe 3+7 enh. | 0.58 | 2.5 | seq. 4 | 0.065 | 1.6 |
| Otd early enh. | 0.024 | 5 | Ftz upstream enh. | 0.037 | 5.8 | seq. 5 | 0.11 | 1 |
| Sal blastoder. enh. | 8.62E-04 | 6.5 | Ftz | 0.28 | 3.3 | seq. 6 | 0.0087 | 3.8 |
| Tll PD enh. | 0.26 | 4.2 | Ubx PBX enh. | 0.196 | 6.7 | seq. 7 | 0.024 | 2.9 |
| Tll AD+PD enh. | 0.025 | 8.1 | Ubx BXD enh. | 0.698 | 4.6 | seq. 8 | 0.17 | 3.4 |
| Eve stripe 2 enh. | 4.04E-05 | 5.1 | Ubx BX enh. (BRE) | 0.05 | 7.5 | seq. 9 | 0.092 | 2.8 |
| Eve stripe 1 enh. | 8.09E-06 | 5.2 | Ems upstream enh. | 0.276 | 4.4 | seq. 10 | 0.052 | 3.6 |
| Eve stripe 5 enh. | 0.27 | 3.8 | En stripe enh. (intr. 1) | 0.049 | 5 | seq. 11 | 0.13 | 1.7 |
| Median | 8.62E-04 | 5.1 | Median | 0.196 | 4.4 | Median | 0.1128 | 2.6 |
Comparison of minimal p-values and best found cutoffs for bicoid PWM calculated (i) in regulatory regions which are regulated by bicoid, (ii) in regulatory regions which are not regulated by bicoid, and (iii) in random sequences of the same length and with the same dinucleotide distribution as in the even-skipped stripe 2 enhancer.
We also would like to address the choice between the M0 and M1 models. We observed, that in almost all cases the p-value calculated for the M0 model is smaller than the p-value calculated for the M1 model. This can probably be explained by the fact that using the M1 model we take into account more information about the real sequence than in the M0 model. Nevertheless, the difference is not crucial; for instance, the greatest value of the ratio between p-values calculated adopting the M0 and M1 for bicoid and kruppel is about 3.62 for the eve2 enhancer. So, the M0 model can be equally used in practical applications.
Assessment of gene regulation
Enhancers may contain clusters of TF binding sites for gene regulators. In such cases, p-value computation can be used to distinguish genes that are regulated by a given transcription factor from those that are not. To illustrate this, we took PWM for TF bicoid and calculated p-values for different cutoff values in various sets of sequences:
- regulatory regions which are regulated by bicoid, the positive set;
- regulatory regions which are not regulated by bicoid, the negative set;
- random sequences of the same length as eve2 enhancer and with the same dinucleotide distribution, the random set.
Minimal p-value and the corresponding cutoff value for 11 sequences in each set are presented in Table 4. Comparing the p-values we observed that p-values calculated for the positive set generally were significantly smaller than those, calculated for the negative and for the random sets.
The median for the p-value in the positive set is equal to 8.62E-04. But there are some exceptions, for instance, the tailless PD enhancer with a minimal p-value that is equal to 0.26 and the even-skipped stripe 5 enhancer with the minimal p-value that is equal to 0.27. Despite the fact that these genes are reported to be regulated by bicoid and that there are experimentally confirmed individual bicoid binding sites in these sequences, these sequences do not contain clusters of bicoid binding sites.
Most p-values calculated for the negative set, (second set in Table 4), are significantly higher than p-values calculated for the positive set. But we observed rather small p-values for sequences of the giant posterior enhancer (0.023), the hunchback upstream enhancer (0.053), the fushi tarazu upstream enhancer (0.037), the ultrabithorax BX enhancer (0.05), and the engrailed stripe enhancer (0.049). We believe that this can be explained by the fact that these regions contain clusters of binding sites of regulatory factors with motifs that are similar to the bicoid motif. Indeed, it was experimentally shown that TF kruppel regulates the giant posterior enhancer, TF tailless regulates the hunchback upstream enhancer and the ultrabithorax BX enhancer, and TF fushi tarazu regulates the fushi tarazu upstream enhancer, the ultrabithorax BX enhancer and the engrailed stripe enhancer. All these motifs of kruppel, tailless and fushi tarazu exhibit some similarity to the bicoid motif. This observation shows the necessity to use some sort of conditional p-values in order to distinguish between the true bicoid clusters and the clusters of weak bicoid sites induced by presence of the clusters of other TF sites [67]. Moreover, the apparent false positive hit (p-value = 0.05, cutoff = 7.5) in a region that was not reported to be regulated by bicoid seems to be related to the real bicoid binding, although not necessarily functional.
For the random set, i.e., sequences simulated with the same dinucleotide probabilities as in the even-skipped stripe 2 enhancer, we observe a rather broad range of minimal p-values, from 0.0087 for the 6th sample to 0.25 for the 3rd sample. It shows that the predictive power of this approach is limited to the case of regulatory sequences containing clusters of motifs.
Conclusion
In this work we have developed an algorithm inspired by the Aho-Corasick pattern matching algorithm that allows precise calculation of the probability to find given motif conformation in a random text. It was implemented in the AHOPRO software for the Bernoulli model and the Markov model of order 1 of random sequences. There would be no difficulty in extending our approach for Markov models of order k, k > 1. We compared probabilities computed with AHOPRO with those computed by compound Poisson distribution and showed that in the case of multiple occurrences of multiple motifs the Poisson approximation often substantially underestimate the p-value.
As we have demonstrated, the statistical significance of multiple motif occurrence in the text can be efficiently calculated with a simple algorithm. This can give an independent criteria to improve the results of site extraction algorithms, which still performs rather poorly. P-values or E-values are used in such programs as BLAST and make quantities to which practicing biologists are used to. Thus, adopting this measure to motif extraction (for a single or multiple motif occurrences) would greatly help the users who use motif extraction analysis as a preliminary stage for experiments in the lab. On the other hand, our algorithm is not connected with a particular motif extraction program, and uses a most general motif representation, the list of the allowed words [35], as input. Thus, it can be used when the results of several motif extraction algorithms are compared, for instance in the interpretation of ChIP-chip experiments [5]. In addition, our algorithm AHOPRO can easily be extended to amino acid sequences and applied in identification of protein domain signatures.
Authors' contributions
VM initiated the study by pointing at the biological problem. JC suggested the initial idea of using Aho-Corasick structure. The final version of the algorithm was developed in discussions between JC, VB, MR and MAR. JC and VB developed the implementation. VB obtained results on simulated and biological sequences. VB designed the web site. MR, MAR, VB and VM participated in manuscript writing. MR and VM coordinated the study. All authors read and approved the final manuscript.
Supplementary Material
Bernoulli text model. Probability to find multiple occurrences of a single motif. The detailed description of the algorithm for the p-value calculation in the case of multiple occurrences of a single motif.
Tree construction from PWM motif representation. The brief description of the procedure of the prefix tree construction from PWM motif representation.
Tree construction from PWM motif representation. Steps of the prefix tree construction for a PWM and a given cut-off.
Acknowledgments
Acknowledgements
Thanks to Andrey Mironov, Stephen Small, Dmitri Papatsenko, Bruno Salvy and Philippe Flajolet for helpful comments and suggestions. Thanks to Alexander Favorov for help with the programming. Thanks to Tim Barker for correcting the English in the manuscript. This research was partially supported by INTAS #04-83-3994 and #05-1000008-8028, French Program EcoNet-12635WG, the RFBR grants 07-04-01584 and 06-04-49249, and by Russian Federation Agency in Science and Innovation State Contract 02.531.11.9003.
Contributor Information
Valentina Boeva, Email: valeyo@yandex.ru.
Julien Clément, Email: Julien.Clement@info.unicaen.fr.
Mireille Régnier, Email: Mireille.Regnier@inria.fr.
Mikhail A Roytberg, Email: mroytberg@impb.psn.ru.
Vsevolod J Makeev, Email: makeev@genetika.ru.
References
- MacIsaac KD, Fraenkel E. Practical strategies for discovering regulatory DNA sequence motifs. PloS Comput Biol. 2006;2:e36. doi: 10.1371/journal.pcbi.0020036. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Sandve GK, Drablos F. A survey of motif discovery methods in an integrated framework. Biol Direct. 2006;1:11. doi: 10.1186/1745-6150-1-11. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Rombauts S, Florquin K, Lescot M, Marchal K, Rouze P, van de Peer Y. Computational approaches to identify promoters and cis-regulatory elements in plant genomes. Plant Physiol. 2003;132:1162–1176. doi: 10.1104/pp.102.017715. Review. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Bulyk ML. DNA microarray technologies for measuring protein-DNA interactions. Curr Opin Biotechnol. 2006;17:422–30. doi: 10.1016/j.copbio.2006.06.015. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Harbison CT, Gordon B, Lee TI, Rinaldi NJ, Macisaac KD, Danford T, Hannett NM, Tagne JB, Reynolds DB, Yoo J, Jennings EG, Zeitlinger J, Pokholok DK, Kellis M, Rolfe PA, Takusagawa KT, Lander ES, Gifford DK, Fraenkel E, Young RA. Transcriptional regulatory code of a eukaryotic genome. Nature. 2004;431:99–104. doi: 10.1038/nature02800. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Zhu Z, Shendure J, Church GM. Discovering functional transcription-factor combinations in the human cell cycle. Genome Res. 2005;15:848–55. doi: 10.1101/gr.3394405. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Clyde DE, Corado MS, Wu X, Pare A, Papatsenko D, Small S. A self-organizing system of repressor gradients establishes segmental complexity in Drosophila. Nature. 2003;426:849–53. doi: 10.1038/nature02189. [DOI] [PubMed] [Google Scholar]
- Wagner A. Genes regulated cooperatively by one or more transcription factors and their identification in whole eukaryotic genomes. Bioinformatics. 1999;15:776–784. doi: 10.1093/bioinformatics/15.10.776. [DOI] [PubMed] [Google Scholar]
- Lifanov AP, Makeev VJ, Nazina AG, Papatsenko DA. Homotypic regulatory clusters in Drosophila. Genome Res. 2003;13:579–88. doi: 10.1101/gr.668403. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Brown CT, Rust AG, Clarke PJ, Pan Z, Schilstra MJ, De Buysscher T, Griffin G, Wold BJ, Cameron RA, Davidson EH, Bolouri H. New computational approaches for analysis of cis-regulatory networks. Dev Biol. 2002;246:86–102. doi: 10.1006/dbio.2002.0619. [DOI] [PubMed] [Google Scholar]
- Wagner A. A computational genomics approach to the identification of gene networks. Nucleic Acids Res. 1997;25:3594–3604. doi: 10.1093/nar/25.18.3594. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Liaw GJ, Lengyel JA. Control of tailless expression by bicoid, dorsal and synergistically interacting terminal system regulatory elements. Mech Dev. 1993;40:47–61. doi: 10.1016/0925-4773(93)90087-E. [DOI] [PubMed] [Google Scholar]
- Jun S, Desplan C. Cooperative interactions between paired domain and homeodomain. Development. 1996;122:2639–50. doi: 10.1242/dev.122.9.2639. [DOI] [PubMed] [Google Scholar]
- Mitashev VI, Koussoulakos S, Zinov'eva RD, Ozerniuk ND, Mikaelian AS, Shmukler E, Smirnova Iu A. [Constructive synergism of regulatory genes expressed in the course of the eye and muscle development and regeneration] Izv Akad Nauk Ser Biol. 2001:261–75. [PubMed] [Google Scholar]
- Klingenhoff A, Frech K, Werner T. Regulatory modules shared within gene classes as well as across gene classes can be detected by the same in silico approach. In Silico Biol. 2002;2:S17–26. [PubMed] [Google Scholar]
- Kato M, Hata N, Banerjee N, Futcher B, Zhang MQ. Identifying combinatorial regulation of transcription factors and binding motifs. Genome Biol. 2004;5:R56. doi: 10.1186/gb-2004-5-8-r56. Epub 2004 Jul 28. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Hu YJ, Sandmeyer S, McLaughlin C, Kibler D. Combinatorial motif analysis and hypothesis generation on a genomic scale. Bioinformatics. 2000;16:222–32. doi: 10.1093/bioinformatics/16.3.222. [DOI] [PubMed] [Google Scholar]
- Jegga AG, Sherwood SP, Carman JW, Pinski AT, Phillips JL, Pestian JP, Aronow BJ. Detection and visualization of compositionally similar cis-regulatory element clusters in orthologous and coordinately controlled genes. Genome Res. 2002;12:1408–17. doi: 10.1101/gr.255002. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Li H, Rhodius V, Gross C, Siggia ED. Identification of the binding sites of regulatory proteins in bacterial genomes. Proc Natl Acad Sci USA. 2002;99:11772–7. doi: 10.1073/pnas.112341999. Epub 2002 Aug 14. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Markstein M, Zinzen R, Markstein P, Yee KP, Erives A, Stathopoulos A, Levine M. A regulatory code for neurogenic gene expression in the Drosophila embryo. Development. 2004;131:2387–94. doi: 10.1242/dev.01124. [DOI] [PubMed] [Google Scholar]
- Makeev V, Lifanov A, Nazina A, Papatsenko D. Distance preferences in distribution of binding motifs and hierarchical levels in organization of transcription regulatory information. Nucleic Acids Res. 2003;31:6016–26. doi: 10.1093/nar/gkg799. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Halfon MS, Michelson AM. Exploring genetic regulatory networks in metazoan development: methods and models. Physiol Genomics. 2002;10:131–43. doi: 10.1152/physiolgenomics.00072.2002. [DOI] [PubMed] [Google Scholar]
- Papatsenko D. ClusterDraw web server: a tool to identify and visualize clusters of binding motifs for transcription factors. Bioinformatics. 2007;23:1032–1034. doi: 10.1093/bioinformatics/btm047. [DOI] [PubMed] [Google Scholar]
- Aerts S, Loo PV, Thijs G, Moreau Y, Moor BD. Computational detection of cis -regulatory modules. Bioinformatics. 2003;19:II5–II14. doi: 10.1093/bioinformatics/btg1052. [DOI] [PubMed] [Google Scholar]
- Bailey T, Noble W. Searching for statistically significant regulatory modules. Bioinformatics. 2003;19:II16–II25. doi: 10.1093/bioinformatics/btg1054. [DOI] [PubMed] [Google Scholar]
- Berman B, Pfeiffer B, Laverty T, Salzberg S, Rubin G, Eisen M, Celniker S. Computational identification of developmental enhancers: conservation and function of transcription factor binding-site clusters in Drosophila melanogaster and Drosophila pseudoobscura. Genome Biol. 2004;5:R61. doi: 10.1186/gb-2004-5-9-r61. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Frith M, Hansen U, Weng Z. Detection of cis-element clusters in higher eukaryotic DNA. Bioinformatics. 2001;17:878–889. doi: 10.1093/bioinformatics/17.10.878. [DOI] [PubMed] [Google Scholar]
- Frith MC, Li MC, Weng Z. Cluster-Buster: Finding dense clusters of motifs in DNA sequences. Nucleic Acids Res. 2003;31:3666–3668. doi: 10.1093/nar/gkg540. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Sosinsky A, Bonin C, Mann R, Honig B. Target Explorer: an automated tool for the identification of new target genes for a specified set of transcription factors. Nucleic Acids Research. 2003;31:3589–3592. doi: 10.1093/nar/gkg544. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Krivan W. Searching for transcription factor binding site clusters: how true are true positives? J Bioinform Comput Biol. 2004;2:413–6. doi: 10.1142/S021972000400065X. [DOI] [PubMed] [Google Scholar]
- Papatsenko D, Makeev V, Lifanov A, Régnier M, Nazina A, Desplan C. Extraction of Functional Binding Sites from Unique Regulatory Regions: The Drosophila Early Developmental Enhancers. Genome Research. 2002;12:470–481. doi: 10.1101/gr.212502. [Preliminary version in Drosophila Workshop, Washington 2001]. 10.1101/gr.212502. Article published online before print in February 2002. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Markstein M, Markstein P, Markstein V, Levine M. Genome-wide Analysis of Clustered Dorsal Binding Sites Identifies Putative Target Genes in the Drosophila Embryo. PNAS. 2002;99:763–768. doi: 10.1073/pnas.012591199. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Rebeiz M, Reeves NL, Posakony JW. SCORE: a computational approach to the identification of cis-regulatory modules and target genes in whole-genome sequence data. Site clustering over random expectation. Proc Natl Acad Sci USA. 2002;99:9888–93. doi: 10.1073/pnas.152320899. Epub 2002 Jul 09. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Lifanov A, Makeev V, Nazina A, Papatsenko D. Uniform clusters in Drosophila. Genome Res. 2003;13:579–588. doi: 10.1101/gr.668403. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Staden R. Methods for calculating the probabilities of finding patterns in sequences. Comput Appl Biosci. 1989;5:89–96. doi: 10.1093/bioinformatics/5.2.89. [DOI] [PubMed] [Google Scholar]
- Ellington A, Szostak J. In vitro selection of RNA molecules that bind specific ligands. Nature. 1990;346:818–822. doi: 10.1038/346818a0. [DOI] [PubMed] [Google Scholar]
- Tuerk C, Gold L. Systematic evolution of ligands by exponential enrichment: RNA ligands to bacteriophage T4 DNA polymerase. Science. 1990;249:505–510. doi: 10.1126/science.2200121. [DOI] [PubMed] [Google Scholar]
- Berger MF, Philippakis AA, Qureshi AM, He FS, Estep PW, Bulyk ML. Compact, universal DNA microarrays to comprehensively determine transcription-factor binding site specificities. Nat Biotechnol. 2006;24:1429–1435. doi: 10.1038/nbt1246. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Liu Y, Yokota H. Modeling Transcriptional Regulation in Chondrogenesis Using Particle Swarm Optimization. IEEE Symposium on Computational Intelligence in Bioinformatics and Computational Biology, CIBCB2005. 2005. pp. 311–317.
- IUPAC codes http://bioinformatics.org/sms2/iupac.html
- Berg OG. Selection of DNA binding sites by regulatory proteins. Functional specificity and pseudosite competition. J Biomol Struct Dyn. 1988;6:275–297. doi: 10.1080/07391102.1988.10507713. [DOI] [PubMed] [Google Scholar]
- Knuth DE. The Art of Computer Programming, Sorting and Searching. Vol. 3. Addison-Wesley; 1973. [Google Scholar]
- Zhang J, Jiang B, Li M, Tromp J, Zhang X, Zhang M. Computing exact P-values for DNA motifs. Bioinformatics. 2007;23:531–537. doi: 10.1093/bioinformatics/btl662. [DOI] [PubMed] [Google Scholar]
- Hertzberg L, Zuk O, Getz G, Domany E. Finding Motifs in Promoter Regions. Journal of Computational Biology. 2005;12:314–330. doi: 10.1089/cmb.2005.12.314. [DOI] [PubMed] [Google Scholar]
- Robin S, Daudin JJ. Exact distribution of word occurrences in a random sequence of letters. J Appl Prob. 1999;36:179–193. doi: 10.1239/jap/1032374240. [DOI] [Google Scholar]
- Chrysaphinou C, Papastavridis S. The Occurrence of Sequence of Patterns in Repeated Dependent Experiments. Theory of Probability and Applications. 1990;79:167–173. [Google Scholar]
- Guibas L, Odlyzko A. String Overlaps, Pattern Matching and Nontransitive Games. Journal of Combinatorial Theory, Series A. 1981;30:183–208. doi: 10.1016/0097-3165(81)90005-4. [DOI] [Google Scholar]
- Tanushev M, Arratia R. Central Limit Theorem for Renewal Theory for Several Patterns. Journal of Computational Biology. 1997;4:35–44. doi: 10.1089/cmb.1997.4.35. [DOI] [PubMed] [Google Scholar]
- Nicodème P, Salvy B, Flajolet P. Motif Statistics. Theoretical Computer Science. 2002;287:593–618. doi: 10.1016/S0304-3975(01)00264-X. [Preliminary version at ESA'99]. [DOI] [Google Scholar]
- Régnier M. A Unified Approach to Word Occurrences Probabilities. Discrete Applied Mathematics. 2000;104:259–280. doi: 10.1016/S0166-218X(00)00195-5. [Special issue on Computational Biology;preliminary version at RECOMB'98]. [DOI] [Google Scholar]
- Szpankowski W. Average Case Analysis of Algorithms on Sequences. New York: John Wiley and Sons; 2001. [Google Scholar]
- Bassino F, Clément J, Fayolle J, Nicodème P. Counting occurrences for a finite set of words: an inclusion-exclusion approach. 2007 International Conference on Analysis of Algorithms (AofA'07), Discrete Mathematics and Theoretical Computer Science. 2007. p. 12.
- Park Y, Spouge J. Searching for Multiple Words inMarkov Sequences. INFORMS journal of Computing. 2004;16:341–347. doi: 10.1287/ijoc.1040.0095. [DOI] [Google Scholar]
- Nicodème P. Regexpcount, a symbolic package for counting problems on regular expressions and words. Fundamenta Informaticae. 2003;56:71–88. [Google Scholar]
- Klaerr-Blanchard M, Chiapello H, Coward E. Detecting localized repeats in genomic sequences: A new strategy and its application to B. subtilis and A. thaliana sequences. Comput Chem. 2000;24:57–70. doi: 10.1016/S0097-8485(99)00047-9. [DOI] [PubMed] [Google Scholar]
- Reinert G, Schbath S. Compound Poisson Approximation for Occurrences of Multiple Words in Markov Chains. Journal of Computational Biology. 1998;5:223–253. doi: 10.1089/cmb.1998.5.223. [DOI] [PubMed] [Google Scholar]
- Régnier M, Vandenbogaert M. Comparison of statistical significance criteria. J Bioinform Comput Biol. 2006;4:537–551. doi: 10.1142/S0219720006002028. [DOI] [PubMed] [Google Scholar]
- Régnier M. Mathematical Tools for Regulatory Signals Extraction. In: Kolchanov N, Hofestaedt R, editor. Bioinformatics of Genome Regulation and Structure. Kluwer Academic Publisher; 2004. pp. 61–70. [Preliminary version at BGRS'02]. [Google Scholar]
- Régnier M, Denise A. Rare events and Conditional Events on random strings. DMTCS. 2004;6:191–214. [Google Scholar]
- Boeva V, Clément J, Régnier M, Vandenbogaert M. CPM'05, of Lecture Notes in Computer Science. Vol. 3537. Springer-Verlag; 2005. Assessing the significance of Sets of Words; pp. 358–370. [Proc. CPM'05, Jeju Island, Korea]. [Google Scholar]
- Kucherov G, Noé L, Roytberg M. Multi-seed lossless filtration. In: Sahinalp S, Muthukrishnan S, Dogrusoz U, editor. Proceedings of the 15th Annual Combinatorial Pattern Matching Symposium (CPM), Istanbul (Turkey), of Lecture Notes in Computer Science. Vol. 3109. Springer Verlag; 2004. pp. 297–310. [Google Scholar]
- Aho A, Corasick M. Efficient String Matching. CACM. 1975;18:333–340. [Google Scholar]
- Small S, Blair A, Levine M. Regulation of even-skipped stripe 2 in the Drosophila embryo. Embo Journal. 1992;11:4047–4057. doi: 10.1002/j.1460-2075.1992.tb05498.x. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Reinert G, Schbath S. Compound Poisson and Poisson process approximations for occurrences of multiple words in Markov chains. J Comput Biol. 1998;5:223–53. doi: 10.1089/cmb.1998.5.223. [DOI] [PubMed] [Google Scholar]
- Wasserman W, Fickett J. Identification of regulatory regions which confer muscle-specific gene expression. J Mol Biol. 1998;278:167–81. doi: 10.1006/jmbi.1998.1700. [DOI] [PubMed] [Google Scholar]
- Tompa M, Li N, Bailey T, Church G, De Moor B, Eskin E, Favorov A, Frith M, Fu Y, Kent J, Makeev V, Mironov A, Noble W, Pavesi G, Pesole G, Régnier M, Simonis N, Sinha S, Thijs G, van Helden J, Vandenbogaert M, Weng Z, Workman C, Ye C, Zhu Z. An Assessment of Computational Tools for the Discovery of Transcription Factor Binding Sites. Nature Biotechnology. 2005;23:137–144. doi: 10.1038/nbt1053. [DOI] [PubMed] [Google Scholar]
- Blanchette M, Sinha S. Separating real motifs from their artifacts. Bioinformatics. 2001;17:S30–8. doi: 10.1093/bioinformatics/17.suppl_1.s30. [DOI] [PubMed] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Supplementary Materials
Bernoulli text model. Probability to find multiple occurrences of a single motif. The detailed description of the algorithm for the p-value calculation in the case of multiple occurrences of a single motif.
Tree construction from PWM motif representation. The brief description of the procedure of the prefix tree construction from PWM motif representation.
Tree construction from PWM motif representation. Steps of the prefix tree construction for a PWM and a given cut-off.


