Abstract
Social transmission of acquired foraging techniques is rarely considered outside of a vertebrate context. Here, however, we show that nectar robbing by bumble-bees (Bombus terrestris)—an invertebrate behaviour of considerable ecological significance—has the potential to spread through a population at the accelerated rates typical of social transmission. Nectar robbing occurs when individuals either bite through the base of a flower to ‘steal’ nectar (primary robbing) or use robbing holes that others have made (secondary robbing). We found that experience of foraging from robbed flowers significantly promoted the development of primary robbing in previously legitimate foragers, thus implying that the acquisition of nectar robbing by one individual will facilitate its adoption in others. Our findings suggest that the positive feedback effects of social transmission may potentially play an ecologically important role in the relationship between plants and pollinators.
Keywords: social transmission, social information, nectar robbing
1. Introduction
Instances where the adoption of a behaviour pattern by one individual directly promotes its adoption and continued exhibition by another, termed social transmission (Galef 1988), can have profound implications for a species' ecology because behaviour initiated by a few individuals may quickly spread at an accelerating rate (Cavalli-Sforza & Feldman 1981; Pulliam 1983; Boyd & Richerson 1985; Reader & Laland 2000, 2003). Novel foraging techniques can spread through a group in this way (e.g. Kawai 1965; Lefebvre 1995; Whiten et al. 2005), and yet transmission from one animal to the next can be mechanistically very simple. For example, black rats (Rattus rattus) in Israeli forests survive entirely on a diet of pine seeds, but juvenile rats do not learn how to extract the seeds unless they are allowed to hone their skills on pine cones that have been partially stripped by older conspecifics (Aisner & Terkel 1992; Terkel 1996). Social transmission therefore plays a direct role in niche construction, but observational social learning is not involved; instead, the behaviour spreads because individuals interact with the products of their conspecifics' behaviour.
Until recently, social transmission through the coincidental products of others' behaviour, rather than through direct signalling, was typically investigated only in a vertebrate context. However, a growing number of studies now show that invertebrates can also learn through inadvertently provided social information (Coolen et al. 2005; Worden & Papaj 2005; Leadbeater & Chittka 2007a, reviewed in Leadbeater & Chittka 2007b). Nonetheless, the possibility that such learning might stretch to procedural knowledge (skills), in addition to simple declarative knowledge (facts), remains untested in an invertebrate context. In this study, we explore the role of social transmission in the spread of a foraging technique employed by bumble-bees (Bombus terrestris), and other pollinators, to obtain nectar without entering a flower's corolla. ‘Nectar robbing’ occurs when bees create or reuse holes bitten through the base of a flower, or a nectar spur, to extract nectar, and thus do not pollinate the flower in the ‘legitimate’ manner (Inouye 1983).
Almost all plant species with tubular flowers or nectar spurs are likely to experience some form of nectar robbing (Irwin & Maloof 2002). Bees sometimes rob flowers from which they cannot extract nectar, which are morphologically matched to longer-tongued pollinators, but they also rob species that they could pollinate legitimately, perhaps because using robbing holes may require less handling effort or provide greater nectar rewards than legitimate visitation (Dedej & Delaplane 2005). As yet, little is known about the factors that lead individual bees to rob, but the available evidence suggests that foragers learn the technique through trial and error, initially perforating flowers at random, and subsequently learning to create holes in the locations where nectar can be accessed (Olesen 1996). The question of whether nectar robbing might spread quickly through a group of bees, at the accelerated rate typical of social transmission, is evolutionarily interesting because robbers exert selection on the mutualistic relationship between flowering plants and pollinators through their effects on plant fitness (Irwin 2006). Such effects vary from strongly negative to positive, depending upon whether robbing precludes pollination, how robbing influences the behaviour or other pollinators and whether robbers also make legitimate flower visits (Maloof & Inouye 2000).
We focus here on the adoption of robbing behaviour by naive bumble-bees that have never previously robbed flowers or encountered robbing. Our subjects foraged on broad bean (Vicia faba) flowers and artificial flower models. In both systems, individuals can extract nectar either legitimately, or by using robbing holes that others have created (secondary robbing), or by creating holes themselves (primary robbing; Kendall & Smith 1975). Firstly, we investigated whether bees that have been exposed to flowers that others have robbed are more likely to begin creating robbing holes for themselves. In other words, secondary robbing may facilitate primary robbing, creating a positive feedback loop. Secondly, we examined whether interaction with other bees that act as secondary robbers can lead a legitimate forager to become a secondary robber itself. Our findings provide the first evidence that social transmission may facilitate the spread of nectar robbing through a group of foraging bumble-bees, and thus increase the frequency of a behaviour which exerts natural selection on the plant/pollinator mutualism.
2. Material and methods
(a) Experiment 1: does secondary robbing lead to primary robbing?
In this experiment, individual bees were initially allowed to forage either on flowers with pre-cut robbing holes or on intact flowers, and then subsequently tested for their propensity to create robbing holes.
(i) Pretesting period
Subjects were workers from a commercially obtained B. terrestris colony, housed in two-chamber wooden nest-boxes (28×16×11 cm) that were connected via a Plexiglas tube to a large flight arena (105×70×30 cm). This colony was replaced twice over the course of testing, to ensure a constant supply of motivated foragers. During the week prior to testing, and between tests, bees had constant access to a transparent feeder placed within the arena, which dispensed 50% (v/v) sucrose solution ad libitum. Before each test, one motivated forager (as determined by a minimum of two visits to the feeder in the 20 min prior to selection) was chosen from those visiting the feeder and individually tagged. Bees to be tested were allocated to the ‘robbing’ or ‘legitimate foraging’ groups in alternate order.
(ii) Phase 1
For the first phase of each test, the arena was cleared of bees and the feeder replaced by three broad bean flowers, cut from the plant immediately prior to use. Plants had been stored in the laboratory for at least a day before testing, to prevent bee visitation. The flowers were mounted on syringe needles protruding through the rear wall of the arena, through which sucrose solution was pumped continuously at 0.19 ml h−1 by an external set of continuous nectar pumps (see the electronic supplementary material). The tubular base of each flower's corolla was wrapped with clear tape, to prevent subjects from creating robbing holes during the training period, and glued to the syringe at the joint to prevent leakage. Flowers available to bees in the robbing group had a 2 mm diameter circular robbing hole cut through the taped area. Each subject was permitted 30 min of individual foraging on the flowers, excluding return visits to the colony to offload sucrose.
(iii) Phase 2
After the training period, the subject was returned to the nest, and the flowers and syringe needles were exchanged for fresh untaped replacements. When it returned, the test bee was released into the arena and allowed to visit the flowers. Each visit to either the legitimate entrance of the flower or to the tubular base of the flower was recorded, along with the time of any biting and the part of the flower bitten. Again, subjects were allowed to return to the nest between foraging bouts if required. Tests ended after 30 min (not including time that the subject spent in the nest-box offloading sucrose). Bees that stopped foraging during testing were removed from the experiment (n=6). Testing continued daily until 30 individuals had completed both training and testing (n=15 in each treatment group).
(iv) Analysis
Every individual that bit the flowers during phase 2, from either treatment group, was classified as either a ‘robber’ or a ‘non-robber’ according to the location of the majority of its bites. ‘Robbers’ were bees that directed more than 50% of their bites to the base of the flower, thereby successfully creating robbing holes, while ‘non-robbers’ bit the petals on the majority of occasions. In practice, this division reflected two distinct, easily observable behavioural categories, since robbers directed 91.7±2.4% (mean ±s.e.) of their bites to the base of the flower, and non-robbers only 3.6±0.8%. We then compared the distribution of robbers and non-robbers between the two treatment groups using a non-parametric (Fisher's exact probability) test, expecting that if previous exposure to robbed flowers promotes primary robbing behaviour, then robbers should be more common in the robbing group. All analyses were carried out using R statistical software (v. 2.6.1).
(b) Experiment 2: does foraging with secondary robbers promote secondary robbing?
In this experiment, all test bees (termed ‘observers’) visited artificial flowers with pre-cut robbing holes, accompanied either by demonstrators that foraged legitimately or that foraged only from the robbing holes.
(i) Set-up
Robber and legitimate demonstrator bees originated from a divided colony of commercially obtained bumble-bees. On arrival in the laboratory, the brood of this colony was distributed between two nest-boxes, the queen removed and workers randomly allocated to each box. These boxes were glued together allowing airflow between the nest chambers through ventilation holes (3 cm in diameter, covered by metallic mesh with holes of width 2 mm). Thus, the two demonstrator groups experienced similar nest conditions, but could not mix with each other during training and testing. ‘Observer’ bees were housed as a single colony in a similar wooden nest-box. Throughout the course of training and testing, both observer and demonstrator colonies were replaced once to ensure a constant supply of motivated foragers.
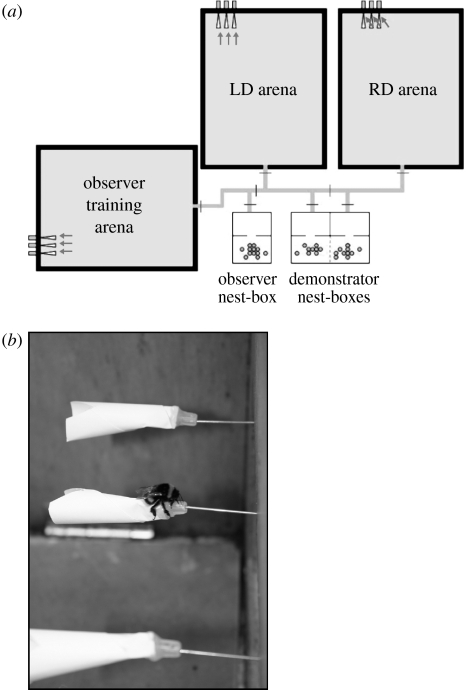
Each nest-box was connected to one of the three flight arenas (referred to as the legitimate demonstrators', robbing demonstrators' or observers' arena) via a system of interconnected transparent tubing (figure 1a). Every arena contained a set of three removable white paper flowers, protruding from the rear wall, which were refilled with 50% (v/v) sucrose solution at a rate of 0.19 ml h−1 by an external set of continuous syringe pumps, as described above.
Figure 1.
Artificial flower and colony arrangement. (a) Each demonstrator group had constant access to one of the three flight arenas. Observer bees were tested in either the robber demonstrators' (RD) or the legitimate demonstrators' (LD) arena. (b) Flowers used during testing (and for training robber demonstrators) had pre-cut robbing holes at the base.
Artificial flowers were used because we found in pilot studies that real inflorescences quickly degraded under high levels of visitation by demonstrators. The artificial flowers were conical in shape and 25 mm long, with an additional 10 mm tubular plastic base through which a syringe needle delivered sucrose. Bees could access the sucrose solution either by crawling through the large entrance hole and into the flower, reaching the reward with the tip of their extended proboscis, or by robbing the flower through small holes previously drilled into the base of the corolla (figure 1b).
(ii) Pretesting period
Prior to testing, and in between tests, both demonstrator groups were allowed constant access to their flight arena and flowers were modified to ensure that bees learnt to forage consistently in the designated manner. For the robber demonstrators, the legitimate entrance to each flower was blocked using moulded glue, and a drop of aversive quinine hemisulphate solution (0.12%) was regularly placed on the edge of the petals, to encourage bees to visit only the pre-cut robbing hole. For the legitimate demonstrators, flowers with no robbing holes were used and the drop of quinine solution was placed on the plastic tubular base of the flower, where robbing would normally take place.
To train sufficient demonstrators to begin testing required between 4 and 8 days in each case. During this period, observer bees were allowed to forage in their own arena under the same conditions as the legitimate demonstrators, but without quinine. Thus, prior to testing, observers were used to visiting the flowers legitimately, but had no previous experience of nectar robbing. All foragers in the observer group that began to make repeated visits to the flowers (more than two visits during one 30 min period) were marked for individual identification.
(iii) Testing
Trials were carried out within either the legitimate demonstrators' arena or the robber demonstrators' arena, in alternate order where possible. An individual trial could take place when at least three bees from the respective demonstrator group (i.e. the group trained to forage in that arena), and one individually marked observer bee, were motivated to forage (more than two visits to the flowers, interspersed with return visits to the nest, during the period immediately prior to testing). Before a trial began, the appropriate demonstrator arena was cleared of bees and the floor and walls cleaned. Syringe needles were replaced and new white inflorescences, where the reward could be accessed either legitimately or through the drilled robbing holes, were fixed to them. Thus, observers were tested in identical arenas and with identical flowers, but the behaviour of the demonstrators differed between treatments.
At the start of a trial, the selected test bee was held in the access tubing leading to the appropriate demonstrator arena, together with three motivated demonstrators from the correct group. The trial started when all four bees were released to forage from the flowers. During the test, demonstrators were permitted to return to the nest if required, although it was ensured that there was never less than one foraging demonstrator in the arena. If a demonstrator ceased foraging or did not return from the nest, she was replaced by another where possible. Demonstrators that began to forage in the opposite way to which they had been trained during trials (n=4) were removed and replaced where possible, to ensure that all demonstrators behaved in a consistent manner.
For each observer bee, every visit to either the entrance hole or the robbing hole of a flower was recorded, along with the time taken to use the robbing hole for the first time. Again, trials continued for 30 min. Those subjects (n=12) that did not begin foraging within 20 min were removed from the arena and did not participate further in the experiment. A total of 30 bees completed testing, 15 from each treatment group.
(iv) Analysis
For each subject, we calculated an index of robbing behaviour based on the proportion of visits in which the robbing hole was visited, relative to the total number of flower visits during the test period, and compared these values between the two treatment groups using a two-sample t-test. If interaction with demonstrators that use robbing holes promotes secondary robbing, we expected that observers that were accompanied by robber demonstrators should direct their foraging behaviour towards the robbing hole more often than those accompanied by legitimate demonstrators. In addition, we used a non-parametric (Wilcoxon signed-rank) test to compare the number of times each subject visited the flower before the robbing hole was first probed, and another two-sample t-test to compare the time taken to first rob the flower for bees in each group.
3. Results
(a) Experiment 1: does secondary robbing lead to primary robbing?
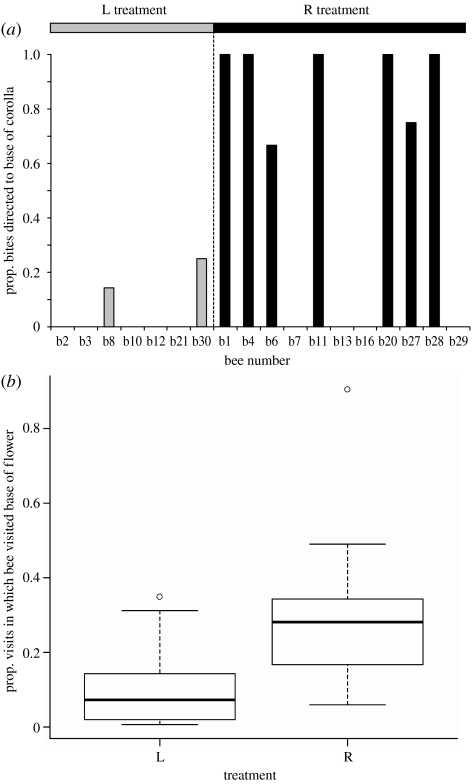
In total, 18 of the 30 bees that completed training and testing showed biting behaviour during the test period (7 that had previously foraged on unrobbed flowers (legitimate group) and 11 that had visited robbed flowers (robbing group)). Of these, all of the individuals in the legitimate group directed the majority of their bites towards the petals, and were thus designated non-robbers, while 7 of the 11 bees from the robbing group were classified as robbers because they showed a preference for biting the base of the flower as is required to ‘steal’ nectar (figure 2a). Thus, bees that had previous experience of using robbing holes were more likely to successfully create such holes themselves than those who had never acted as secondary robbers (Fisher's exact probability test, p=0.013).
Figure 2.
(a) Biting preferences. The proportion of bites directed to the base of the flower for each individual bee that exhibited any biting behaviour is represented in groups R (black bars) and L (grey bars). (b) Visitation preferences. Box plots represent the proportion of flower visits in which the base of the flower was visited, for only those bees that never created robbing holes for themselves. Boxes represent median and interquartile range and narrow lines within the boxes depict the full range of the data, but exclude outliers indicated as open circles. Data are presented prior to log transformation.
Analysis of bees' behaviour during flower visits suggests that this difference reflects a tendency to direct foraging behaviour towards areas where nectar has previously been available, irrespective of whether rewards are currently available there. Even when only bees that never created robbing holes, and were thus never rewarded for visiting the base of the flower during the test period, are considered (13 and 9 bees in the legitimate and the robbing groups, respectively), individuals in the robbing group showed a significantly greater tendency to visit the base of the flower than those in the legitimate group (log transformation, t19.5=−3.45, p<0.01; figure 2b). Given that there were no significant differences in the propensity to perform biting behaviour between the groups (Fisher's exact probability test, p=0.26); this suggests that the occurrence of biting behaviour itself does not depend upon previous experience, but previous experience of attaining nectar through robbing holes leads bees to bite in the appropriate area, i.e. at the base of the flower.
No differences in motivation to forage, as indicated by initial latency to visit flowers during the test period (t27.9=1.2, p=0.24) and by the total number of flower visits during the test period (t27.7=−0.68, p=0.50), could be found between the two treatment groups.
(b) Experiment 2: does foraging with robbing conspecifics promote secondary robbing?
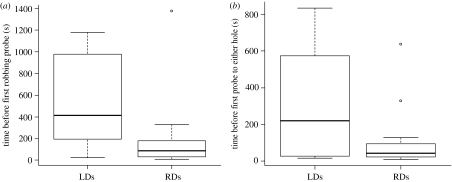
Almost every bee tested (13 of 15 and 14 of 15 observers accompanied by legitimate and robber demonstrators, respectively) probed the robbing holes at some point during the test period. We found no differences in either the number of visits to the legitimate hole before first probing the robbing hole (Wilcoxon signed-rank test, W=131.5, p=0.43) or the overall proportion of visits in which the robbing hole was visited (arcsine transformation, t25.85=1.2293, p=0.23), between the two treatments. Although bees accompanied by robber demonstrators showed a slightly increased tendency to visit the robbing hole on their first flower visit than those accompanied by legitimate demonstrators (7 of 15 and 4 of 15, respectively; Fisher's exact test, p=0.45), this difference was not significant at the 5% level.
Nonetheless, bees that were accompanied by robber demonstrators took significantly less time to first probe the robbing holes than those accompanied by legitimate demonstrators that could only observe demonstrators foraging legitimately (log transformation, t25.0=2.5916, p=0.01572; figure 3a). However, latency to probe the flowers in general (through either hole) was also reduced in the robbing group (figure 3b), and this difference bordered on significance (log transformation, t26.055=2.0389, p=0.0517). This strongly suggests that bees accompanied by robber demonstrators were quicker to probe the robbing holes because they were quicker to visit the flowers in general, rather than because they specifically directed their behaviour towards the robbing holes.
Figure 3.
Latency to (a) become a secondary robber and (b) first probe either hole. Box plots depict data from subjects that interacted with secondary robbers (RDs) and those that interacted only with legitimate foragers (LDs), before transformation. Boxes represent median and interquartile range and narrow lines within the boxes depict the full range of the data, but exclude outliers indicated as open circles.
4. Discussion
Bees were significantly more likely to become primary robbers if they had previously been exposed to robbed flowers than if they had visited only intact flowers. In this study, successful creation and continued visitation of robbing holes by bees that had never acted as secondary robbers was rare. Thus, nectar robbing can be transmitted socially because exposure to the products of primary nectar robbing promotes the development of primary robbing in others.
By contrast, we found no evidence to suggest that visual or olfactory cues provided by the physical presence of foraging robbers promoted secondary robbing. Bees that foraged alongside secondary robbers did not significantly differ from those accompanied by legitimate foragers in their overall tendency to use pre-cut robbing holes, or in the number of flower visits performed before probing pre-cut robbing holes for the first time. Although subjects were quicker to switch from legitimate foraging to using pre-cut robbing holes if accompanied by secondary robbers, these bees were also quicker to approach the flowers overall. Thus, this finding can be explained by the enhanced visibility of robbers relative to legitimate foragers, who can be obscured by floral parts when visiting flower types of a similar morphology to the artificial flower used in this study (e.g. snapdragons Antirrhinum majus or foxgloves Digitalis purpurea). A number of studies have found that bumble-bees are attracted to visibly occupied flowers (Brian 1957; Leadbeater & Chittka 2005; Kawaguchi et al. 2006).
Why does using others' robbing holes lead bees to bite the correct part of flowers? Analysis of individual behaviour revealed a simple underlying mechanism. Overall, bees in the two groups showed similar levels of biting, but bit different parts of the flower. Given that bees in the robbing group had previously received rewards at the base of the flower, while those in the legitimate group had found nectar at the legitimate entrance only, we hypothesized that differences in the location of biting might simply reflect differential amounts of time spent at the base of the flower by bees in the two groups. Accordingly, when we considered the behaviour of only those bees that never created robbing holes (to ensure that preferences for visiting the base of the flower did not reflect the rewards currently available there), we found that, during the test period, bees in the robbing group visited the tubular base of the flower significantly more often than those in the legitimate group. Thus, our data suggest that bees that had previously acted as secondary robbers were more likely to bite the base of the flower, and hence become primary robbers, because they spent more time there than their legitimately foraging counterparts. It is unlikely that any learning about where to direct biting behaviour took place away from the flower, in the nest, because bumble-bees do not communicate even the general direction of food to their nest-mates (Dornhaus & Chittka 1999), and thus communication about small-scale locations seems implausible.
What are the implications of the main finding of this study—that exposure to robbed flowers facilitates adoption of robbing behaviour—at the group level? The incidence of nectar robbing is not entirely dependent on social transmission—indeed, two of the bees in our study learnt to rob flowers despite having no previous experience as a secondary robber—but our findings provide strong evidence that primary robbing in one individual will facilitate its occurrence in others. Mathematical models predict that, once initiated by one or a few individuals, socially transmitted traits will spread via positive feedback, accelerating through a group relative to the linear increases usually predicted for behaviour that is not influenced by conspecifics (Giraldeau et al. 1994; Laland et al. 1996; Giraldeau & Caraco 2000). Accordingly, our findings suggest that as more individuals become primary robbers, and more holes are created, the incidence of primary robbing may increase at an accelerating rate.
Whether these predictions hold up to empirical testing will depend upon the relative rewards of robbing and legitimate foraging, and the available data suggest that the ecological and social factors influencing the occurrence of nectar robbing may be complex (Irwin & Maloof 2002). Nonetheless, observations of natural plant populations indeed suggest that robbing may sometimes undergo a sudden rapid increase, with the proportion of robbed flowers at a site rising exponentially over just a few days (fig. 2 in Irwin & Maloof 2002). Based on our findings, it is highly plausible that social transmission may play a significant role in such sudden transitions. Furthermore, given that other insect species may also produce robbing holes, it seems unlikely that social transmission should be limited to conspecifics in this context. Several recent studies illustrate that adaptive behaviour can be socially transmitted between heterospecifics (Seppänen et al. 2007), and the occurrence of nectar robbing by bumble-bees might equally promote its occurrence in other species (including honeybees; Darwin 1841; Romanes 1844). Further theoretical and empirical work investigating the diffusion curves of nectar robbing both between and within species is warranted.
Although we found no evidence that bees learn how to rob through an observation of others, the finding that individuals were quicker to approach flowers where robbers were foraging raises an interesting possibility. If, as these results suggest, the presence of highly visible robbers attracts other foragers to robbed inflorescences through local enhancement, then the presence of robbers might attract foragers to robbed flowers of species that they would not normally visit. This effect might be particularly important in systems where bees rob flower species from which they cannot extract nectar legitimately—a possibility that is open to empirical testing.
Nectar robbing is of ecological importance because it represents ‘cheating’ and thus may impose selection on the mutualistic relationship between plants and pollinators (Maloof & Inouye 2000; Irwin 2006). Taken together, the results of these experiments demonstrate that the adoption of nectar robbing by bees is facilitated by the same behaviour in others, through a simple and ecologically realistic transmission process. Our findings not only add to the growing body of evidence that insects are capable of using social information, but also provide grounds to suggest that the positive feedback effects of social transmission may play an ecologically significant role in the relationship between plants and pollinators.
Supplementary Material
Diagram of automatic nectar pumps which provided sucrose solution to flowers
References
- Aisner R, Terkel J. Ontogeny of pine cone opening behaviour in the black rat, Rattus rattus. Anim. Behav. 1992;44:327–336. doi:10.1016/0003-3472(92)90038-B [Google Scholar]
- Boyd R, Richerson P. University of Chicago Press; Chicago, IL: 1985. Culture and the evolutionary process. [Google Scholar]
- Brian A.D. Differences in the flowers visited by four species of bumble-bees and their causes. J. Anim. Ecol. 1957;26:71–98. doi:10.2307/1782 [Google Scholar]
- Cavalli-Sforza L, Feldman M.W. Princeton University Press; Princeton, NJ: 1981. Cultural transmission and evolution: a quantitative approach. [PubMed] [Google Scholar]
- Coolen I, Dangles O, Casas J. Social learning in noncolonial insects? Curr. Biol. 2005;21:1931–1935. doi: 10.1016/j.cub.2005.09.015. doi:10.1016/j.cub.2005.09.015 [DOI] [PubMed] [Google Scholar]
- Darwin, C. R. 1841 Letter no. 607, from Charles Darwin to The Gardener's Chronicle, published 21st August 1841. In The correspondence of Charles Darwin 2, pp. 1837–1843. Cambridge, UK: Cambridge University Press.
- Dedej S, Delaplane K. Net energetic advantage drives honey bees (Apis mellifera L.) to nectar larceny in Vaccinium ashei Reade. Behav. Ecol. Sociobiol. 2005;57:398–403. doi:10.1007/s00265-004-0852-z [Google Scholar]
- Dornhaus A, Chittka L. Evolutionary origins of bee dances. Nature. 1999;401:38. doi:10.1038/43372 [Google Scholar]
- Galef, B. G. 1988 Imitation in animals: history, definition, and interpretation of data from the psychological laboratory. In Social learning: psychological and biological perspectives Hillsdale, NJ: Lawrence Erlbaum Associates.
- Giraldeau L.A, Caraco T. Princeton University Press; Princeton, NJ: 2000. Social foraging theory. [Google Scholar]
- Giraldeau L.A, Caraco T, Valone T.J. Social foraging—individual learning and cultural transmission of innovations. Behav. Ecol. 1994;5:35–43. doi:10.1093/beheco/5.1.35 [Google Scholar]
- Inouye D.W. The terminology of floral larceny. Ecology. 1983;61:1251–1252. doi:10.2307/1936841 [Google Scholar]
- Irwin R.E. The consequences of direct versus indirect species interactions to selection on traits: pollination and nectar robbing in Ipomopsis aggregata. Am. Nat. 2006;167:315–328. doi: 10.1086/499377. doi:10.1086/499377 [DOI] [PubMed] [Google Scholar]
- Irwin R.E, Maloof J.E. Variation in nectar robbing over time, space, and species. Oecologia. 2002;133:525–533. doi: 10.1007/s00442-002-1060-z. doi:10.1007/s00442-002-1060-z [DOI] [PubMed] [Google Scholar]
- Kawaguchi L.G, Ohashi K, Toquenaga Y. Do bumble bees save time when choosing novel flowers by following conspecifics? Funct. Ecol. 2006;20:239–244. doi:10.1111/j.1365-2435.2006.01086.x [Google Scholar]
- Kawai M. Newly-acquired pre-cultural behavior of the natural troop of Japanese monkeys on Koshima Islet. Primates. 1965;6:1–30. doi:10.1007/BF01794457 [Google Scholar]
- Kendall D.A, Smith B.D. The pollinating efficiency of honeybee and bumblebee visits to field bean flowers (Vicia faba L.) J. Appl. Ecol. 1975;12:709–717. doi:10.2307/2402083 [Google Scholar]
- Laland K.N, Richerson P, Boyd R. Developing a theory of animal social learning. In: Heyes C.M, Galef B.G, editors. Social learning in animals: the roots of culture. Academic Press, Inc; San Diego, CA: 1996. pp. 129–154. [Google Scholar]
- Leadbeater E, Chittka L. A new mode of information transfer in foraging bumblebees? Curr. Biol. 2005;15:R447–R448. doi: 10.1016/j.cub.2005.06.011. doi:10.1016/j.cub.2005.06.011 [DOI] [PubMed] [Google Scholar]
- Leadbeater E, Chittka L. The dynamics of social learning in an insect model, the bumblebee Bombus terrestris. Behav. Ecol. Sociobiol. 2007a;61:1789–1796. doi:10.1007/s00265-007-0412-4 [Google Scholar]
- Leadbeater E, Chittka L. Social learning in insects—from miniature brains to consensus building. Curr. Biol. 2007b;17:R703–R713. doi: 10.1016/j.cub.2007.06.012. doi:10.1016/j.cub.2007.06.012 [DOI] [PubMed] [Google Scholar]
- Lefebvre L. Culturally-transmitted feeding-behavior in primates—evidence for accelerating learning rates. Primates. 1995;36:227–239. doi:10.1007/BF02381348 [Google Scholar]
- Maloof J.E, Inouye D.W. Are nectar robbers cheaters or mutualists? Ecology. 2000;81:2651–2661. doi:10.2307/177331 [Google Scholar]
- Olesen J.M. From naivete to experience: bumblebee queens (Bombus terrestris) foraging on Corydalis cava (Fumariaceae) J. Kans. Entomol. Soc. 1996;69:274–286. [Google Scholar]
- Pulliam H.R. On the theory of gene–culture co-evolution in a variable environment. In: Melgren R, editor. Animal cognition and behavior. North-Holland; Amsterdam, The Netherlands: 1983. pp. 427–443. [Google Scholar]
- Reader S.M, Laland K.N. Diffusion of foraging innovations in the guppy. Anim. Behav. 2000;60:175–180. doi: 10.1006/anbe.2000.1450. doi:10.1006/anbe.2000.1450 [DOI] [PubMed] [Google Scholar]
- Reader S.M, Laland K.N, editors. Animal innovation. Oxford University Press; Oxford, UK: 2003. [Google Scholar]
- Romanes G.J. AMS Press; New York, NY: 1884. Mental evolution in animals. [Google Scholar]
- Seppänen J.T, Forsman J.T, Mönkönen M, Thomson R.L. Social information use is a process across time, space and ecology, reaching heterospecifics. Ecology. 2007;88:1622–1633. doi: 10.1890/06-1757.1. doi:10.1890/06-1757.1 [DOI] [PubMed] [Google Scholar]
- Terkel J. Cultural transmission of feeding behaviour in the black rat (Rattus rattus) In: Heyes C.M, Galef B.G, editors. Social learning in animals: the roots of culture. Academic Press, Inc; San Diego, CA: 1996. pp. 17–47. [Google Scholar]
- Whiten A, Horner V, de Waal F.B.M. Conformity to cultural norms of tool use in chimpanzees. Nature. 2005;437:737–740. doi: 10.1038/nature04047. doi:10.1038/nature04047 [DOI] [PubMed] [Google Scholar]
- Worden B.D, Papaj D.R. Flower choice copying in bumblebees. Biol. Lett. 2005;1:504–507. doi: 10.1098/rsbl.2005.0368. doi:10.1098/rsbl.2005.0368 [DOI] [PMC free article] [PubMed] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Supplementary Materials
Diagram of automatic nectar pumps which provided sucrose solution to flowers