Abstract
In the current study, the audiotapes from three hostage-taking situations were analyzed. Hostage negotiator requests to the hostage taker were characterized as either high or low probability. The results suggested that hostage-taker compliance to a hostage negotiator's low-probability request was more likely when a series of complied-with high-probability requests preceded the low-probability request. However, two of the three hostage-taking situations ended violently; therefore, the implications of the high-probability request sequence for hostage-taking situations should be assessed in future research.
Keywords: high-probability request sequence, hostage negotiation
A hostage negotiation can be defined as a negotiation conducted between law enforcement agencies or diplomatic representatives for the release of persons held hostage against their will by criminal, terrorist, or other elements (“Hostage Negotiation.” Retrieved November 20, 2007, from http://www.negotiations.com/definition/hostage-negotiation). Hostage negotiation is estimated to be unsuccessful in 18% of the over 10,000 estimated hostage-taking incidents annually in the United States (Van Hasselt et al., 2006). Unsuccessful hostage negotiations can result in loss of life and can have significant negative impact on economies and community relations in instances of politically motivated hostage takings. The hostage taking of 11 Israeli athletes at the 1972 Olympic Games in Munich marked a starting point for escalating interest by psychologists in hostage negotiating (Webster, 2004). Despite the absence of any data to suggest why some hostage negotiations fail, law enforcement has appealed to psychology to provide specific strategies for handling hostage-taking situations (Fuselier, 1988; Wardlaw, 1984). Psychology has responded to this request with extensive training of negotiators in traditional counseling skills such as empathic and active listening (Van Hasselt et al.). This training has developed negotiators' skills in responding to demands made by a hostage taker. However, a critical component of a successfully resolved hostage-taking situation is compliance by a hostage taker to requests made by a hostage negotiator. Often the key requests are ones with which the hostage taker has demonstrated a reluctance or refusal to comply. The critical aspects of making such requests of a hostage taker have not been examined to date.
The current study examined the extent to which the behavior-analytic high-probability request sequence might have relevance to hostage negotiation, because hostage negotiators ultimately work toward hostage takers complying with a low-probability request (e.g., releasing hostages). Research on the high-probability request sequence has demonstrated that compliance can be enhanced by preceding a low-probability request with a series of high-probability requests (Belfiore, Lee, Vargas, & Skinner, 1997). This high-probability request sequence has shown to be effective in enhancing compliance across a wide variety of target behaviors, individual characteristics, and applied settings. The current study hypothesized that a series of hostage taker/hostage negotiator interactions might represent high-probability and low-probability requests and that a descriptive analysis (Thompson & Iwata, 2007) could reveal whether hostage-taker compliance to low-probability requests was enhanced in situations that involved sequences adventitiously arranged according to a high-probability request sequence.
METHOD
Administrative staff from a community-based hospital created written transcripts from the audiotapes of three actual hostage-taking events. These events will be referred to as Brooklyn (a robbery attempt in 1972), Sacramento (a robbery attempt in 1991), and Atlanta (an invasion of Federal Bureau of Investigation offices in 1981). These hostage situations are included in the current study based on the availability of audiotapes of the events. (“Negotiation Audio.” Retrieved June 14, 2006, from http://www.hostagenegotiation.com/Audio.asp). The three events involved 3, 41, and 9 hostages respectively, and 2, 4, and 1 armed hostage takers, respectively.
A trained observer read the transcripts and used paper and pencil to identify requests made by the hostage negotiator and compliance by the hostage taker to those requests. A request was defined as any demand to perform a behavior (e.g., “Put Carol on the phone, let me talk to her”), to provide information (e.g., “How many people do you have with you?”), to cease performing a behavior (e.g., “Don't put the phone down”), or to refrain from commencing to perform a behavior (e.g., “Don't shoot anybody in the leg”). Compliance was identified by information contained in the transcripts subsequent to the request being issued (e.g., Carol was put on phone, the presence of nine hostages was reported, the hostage taker remained on the phone, and no hostage was shot in the leg).
There were a total of 617 requests made by a hostage negotiator to a hostage taker across the three hostage-taking situations. Each of these 617 requests made by a hostage negotiator to a hostage taker was separated into one of four categories. Category 1 consisted solely of requests to provide nonpersonal information, answers to clarification questions, and situational information regarding happenings in the immediate environment (e.g., “Please spell that name for me,” and “You mean you have people calling the employees?”). Category 2 consisted solely of requests to provide personal information including thoughts and feelings (e.g., “How can we contact your wife?” and “Are you hungry?”). Category 3 consisted solely of requests to perform a behavior with the exception of behaviors in Category 4 (e.g., “Why don't you go ahead and send Sam out to pick up the food?”). Category 4 consisted solely of requests to forfeit a negotiating item (e.g., release of a hostage, surrender of a weapon, surrender of the hostage taker).
The initial rater was a behavior analyst in a community-based hospital. A second observer independently read and scored 100% of the transcripts. This second rater was a police constable with 7 years of experience and formal training in crisis resolution. For each of the hostage-taking situations, the point-by-point agreement method was used to calculate interrater agreement by dividing the number of agreements regarding the categorization of requests by the number of agreements plus disagreements regarding the categorization of requests; this ratio was converted to a percentage. There was an interrater agreement of 98% for the categorization of all requests across the four categories. Due to the critical nature of requests in Category 4 and their impact on the potential resolution of a hostage-taking situation, interrater agreement was calculated for all requests in Category 4 across the three events. The interrater agreement for Category-4 requests was 100%.
For each of the hostage-taking situations, the point-by-point agreement method was used to calculate interrater agreement by dividing the number of agreements regarding the occurrence of compliance to a request by the number of agreements plus disagreements regarding the occurrence of compliance to a request; this ratio was converted to a percentage. Mean interrater agreement was 98% for the occurrence of compliance to all requests and 100% for the occurrence of compliance to Category 4 requests.
The probability of compliance within each of the request categories for each hostage-taking situation was calculated by dividing the number of requests to which there was compliance by the total number of requests within that category. For each of the three hostage-taking situations, Category 4 requests had the lowest probability of compliance. The probabilities of compliance for Category 4 requests were 9%, 2%, and 14% for Brooklyn, Sacramento, and Atlanta, respectively. The probabilities of compliance for Brooklyn, Sacramento, and Atlanta, respectively, were 77%, 58%, and 93% for Category 1 requests; 47%, 53%, and 62% for Category 2 requests; and 33%, 43%, and 90% for Category 3 requests.
For each hostage-taking situation, all requests within the category with the lowest probability of compliance (Category 4) were identified as low-probability requests. For each hostage-taking situation, all requests within the categories with the two highest probabilities of compliance (Categories 1 and 2 for Brooklyn and Sacramento and Categories 1 and 3 for Atlanta) were identified as high-probability requests. All requests for each situation were chronologically arranged in table format. Low-probability requests were highlighted, and the number of high-probability requests immediately preceding each low-probability request was determined and recorded. The presence or absence of compliance to every request in the table was also recorded. The interrater agreement for the number of high-probability requests that preceded each low-probability request was 100%. The interrater agreement for the presence or absence of compliance to the high-probability requests preceding the low-probability request was 100%. The number of instances in which a low-probability request immediately preceded a low-probability request was also determined for each of the three situations.
RESULTS AND DISCUSSION
The current study examined a total of 617 requests made of hostage takers by hostage negotiators. This consisted of 273, 205, and 139 total requests for Brooklyn, Sacramento, and Atlanta, respectively. There were 22, 41, and 7 low-probability requests for Brooklyn, Sacramento, and Atlanta, respectively, for a total of 70 low-probability requests. Of these 70 low-probability requests, there were four episodes of compliance, two for Brooklyn and one each for Sacramento and Atlanta. Figure 1 depicts the percentage of compliance to low-probability requests when the low-probability request was not preceded by any high-probability requests or when the low-probability request was not preceded by any high-probability requests to which the hostage taker was compliant (n = 49). Figure 1 also depicts the percentage of compliance to low-probability requests when the low-probability request was preceded by 1 (n = 11), 2 (n = 5), 3 (n = 1), 4 (n = 0), 5 (n = 1), 6 (n = 0), 7 (n = 1), 8 (n = 0), or 9 (n = 2) high-probability requests to which the hostage taker was compliant. The probability of compliance to the low-probability request generally increased as the number of preceding high-probability requests to which the hostage taker was compliant increased. That is, hostage-taker compliance with the low-probability request was 100% when the hostage negotiator issued three, five, or nine high-probability requests that resulted in compliance prior to the low-probability request.
Figure 1.
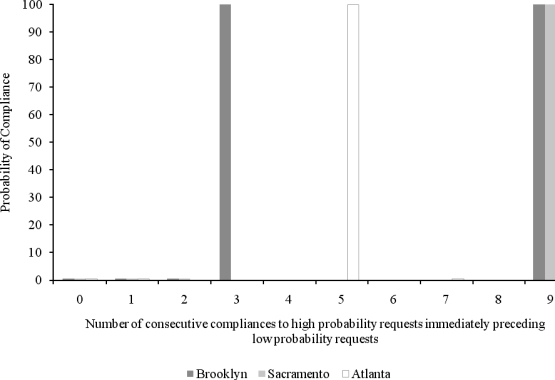
Probability of compliance to low-probability requests following high-probability requests.
Brooklyn
The first instance of compliance to a low-probability request, which resulted in the release of one of the three hostages, followed a sequence of three high-probability requests with which the hostage taker complied. The second compliance to a low-probability request (“Go right to the door … with your hands up”) followed a sequence of nine high-probability requests with which the hostage taker complied. This was the last of the low-probability requests in this negotiation and culminated with the surrender of the hostage takers without casualties to the remaining hostages. The hostage negotiator issued a total of 20 low-probability requests without a minimum of three preceding high-probability requests with which the hostage taker complied. Compliance to the low-probability requests did not occur in any of these instances. On seven occasions the hostage negotiator issued low-probability requests consecutively, and the hostage taker was not compliant with any of these low-probability requests.
Sacramento
The only compliance to a low-probability request, which resulted in the release of one hostage, followed a sequence of nine high-probability requests with which the hostage taker was compliant. The hostage negotiator issued a total of 40 low-probability requests that were not preceded by three high-probability requests with which the hostage taker was compliant. The hostage taker was not compliant with any of these low-probability requests. The hostage negotiator issued 16 low-probability requests consecutively, and the hostage taker was not compliant with any of these low-probability requests. The hostage negotiator also issued seven consecutive low-probability requests with which the hostage taker was not compliant. The Sacramento situation was ultimately resolved in a violent manner: Fourteen hostages were injured, and three hostages and three of the four hostage takers died.
Atlanta
The hostage taker was compliant with one low-probability request (which resulted in the release of three hostages) that followed a sequence of five high-probability requests with which the hostage taker was compliant. The hostage negotiator issued a total of five low-probability requests that were not preceded by three high-probability requests with which the hostage taker was compliant. The hostage taker was not compliant with any of these low-probability requests. The hostage negotiator made low-probability requests consecutively on two occasions, and the hostage taker was not compliant with these two low-probability requests. The situation culminated in the shooting and killing of the hostage taker. At the time of the shooting, the hostage taker had complied with 15 consecutive high-probability requests.
These data suggest that instances of the high-probability request sequence naturally occur during some hostage negotiations. There were 70 low-probability requests delivered across the three situations; of these, compliance occurred four times, for an overall probability of compliance of .057. However, all four instances of compliance with a low-probability request followed a high-probability sequence in which three or more high-probability requests produced compliance. In addition, there was only one instance in which noncompliance with a low-probability request followed a sequence in which three or more high-probability requests produced compliance. Thus, the conditional probability of compliance with a low-probability request given prior compliance with a series of at least three high-probability requests was .8 (i.e., four of five). This difference between the conditional probability of compliance with low-probability requests (.8) and the overall probability of compliance with low-probability requests (.057) is statistically significant (Z = 7.16, p < .001).
There are several acknowledged limitations in interpreting the present data. First, scoring of data could not be achieved in a few brief instances due to the poor quality of the audiotape of the hostage-taking situation. Second, the transcription of the audiotape to written transcripts for analysis did not permit a consideration of the amount of time that passed between verbal exchanges. The analysis of data directly from the audio format and the calculation of high- and low-probability requests within specific time frames may represent an area for future research. Third, only three hostage-taking situations were analyzed with compliance to a total of four low-probability requests. Two of the three situations were ultimately resolved by violent means; thus, replications of this analysis might assist in the determination of the reliability of the current findings and their potential practical significance.
In conclusion, the data from the current analysis suggest that hostage negotiators issue many requests in hostage-taking situations. Based on the current data, these requests can be categorized as high and low probability, and high- and low-probability request sequences occur infrequently during hostage negotiations. Despite the infrequency with which these sequences occur, there was a significantly greater likelihood that hostage takers would comply with low-probability requests that were preceded by high-probability requests with which they were compliant. Therefore, even though these results are preliminary, given the potential negative consequences of hostage-taking situations, even such preliminary results require further analysis if they suggest a potential means for improving the outcomes of hostage negotiations.
Acknowledgments
I thank James Carr for his generous guidance, feedback, and encouragement; Maurice Feldman for his thoughtful review of the original manuscript; and Lauri Angus for her careful and diligent review of the data.
REFERENCES
- Belfiore P.J, Lee D.L, Vargas A.U, Skinner C.H. Effects of high-preference single-digit mathematics problem completion on multiple-digit mathematics problem performance. Journal of Applied Behavior Analysis. 1997;30:327–330. doi: 10.1901/jaba.1997.30-327. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Fuselier G.D. Hostage negotiation consultant: Emerging role for the clinical psychologist. Professional Psychology. 1988;19:175–179. [Google Scholar]
- Thompson R.H, Iwata B.A. A comparison of outcomes from descriptive and functional analyses of problem behavior. Journal of Applied Behavior Analysis. 2007;40:333–338. doi: 10.1901/jaba.2007.56-06. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Van Hasselt V.B, Baker M.T, Romano S.J, Schlessinger K.M, Zucker M, Dragone R, et al. Crisis (hostage) negotiation training. Criminal Justice and Behavior. 2006;33:56–69. [Google Scholar]
- Wardlaw G. The psychologist's role in hostage negotiations. The Police Chief. 1984;51((5)):56–58. [Google Scholar]
- Webster M. Do crisis negotiators practice what they preach. The Canadian Review of Policing Research. 2004;1:1–8. [Google Scholar]