Abstract
We evaluated the effects of three different methods of denying access to requested high-preference activities on escalating problem behavior. Functional analysis and response class hierarchy (RCH) assessment results indicated that 4 topographies of problem behaviors displayed by a 13-year-old boy with high-functioning autism constituted an RCH maintained by positive (tangible) reinforcement. Identification of the RCH comprised the baseline phase, during which computer access was denied by saying “no” and providing an explanation for the restriction. Two alternative methods of saying “no” were then evaluated. These methods included (a) denying computer access while providing an opportunity to engage in an alternative preferred activity and (b) denying immediate computer access by arranging a contingency between completion of a low-preference task and subsequent computer access. Results indicated that a hierarchy of problem behavior may be identified in the context of denying access to a preferred activity and that it may be possible to prevent occurrences of escalating problem behavior by either presenting alternative options or arranging contingencies when saying “no” to a child's requests.
Keywords: response class hierarchy; saying “no,” autism
Children with behavioral difficulties often pose requests or demands that cannot be honored. This situation often arises in two forms: (a) A child may request a reinforcer that cannot be delivered immediately, or (b) a child may request a reinforcer that cannot be delivered due to its unavailability or unsuitability to the child or situation. Because denial of access to requested reinforcers often evokes problem behavior, operations that abate the likelihood of problem behavior in response to imposed limits are important components of any behavior management program. Limited behavior-analytic research has examined effective methods of saying “no” to children with behavioral difficulties despite the prevalence of problem behavior evoked by denied access to preferred items or activities. Related research, though, has demonstrated that (a) problem behavior may be evoked by restricted access to preferred objects or activities and maintained by positive (tangible) reinforcement (e.g., Mueller, Wilczynski, Moore, Fusilier, & Trahant, 2001), (b) “do” requests are more effective than “don't” requests in preventing problem behavior and promoting compliance (e.g., Adelinis & Hagopian, 1999; Mace et al., 1988), and (c) the escalation of problem behavior that comprises a response class hierarchy (RCH) may be prevented through behavior-management procedures (e.g., Lalli, Mace, Wohn, & Livezey, 1995).
Functional communication training (FCT) is one of the most common function-based interventions indicated for individuals who engage in problem behavior that is maintained by access to tangible items. For example, Hagopian, Wilson, and Wilder (2001) implemented an intervention that consisted of FCT with response-independent reinforcer deliveries after functional analysis results revealed that the problem behaviors of a child with developmental disabilities were maintained, in part, by positive reinforcement in the form of access to preferred tangible items. This procedure resulted in a substantial reduction in problem behavior, and a delay-to-reinforcement procedure increased the generality of the results by extending the participant's tolerance for delayed reinforcement for a duration of 10 s. In a previous study with 12 participants, Hagopian, Fisher, Sullivan, Acquisto, and LeBlanc (1998) also employed delay-to-reinforcement fading procedures to increase participants' tolerance for delays between the emission of a communication response and the delivery of the requested reinforcer. In this investigation, delays to reinforcement were faded to an interval of 3.5 min, but reductions in problem behavior were maintained successfully for only 42% of the sample.
The difficulty of maintaining reductions in problem behavior when delays to reinforcement are increased may be viewed in the context of matching theory. As Hagopian et al. (1998) and Hagopian, Kuhn, Long, and Rush (2005) noted, FCT teaches individuals to emit a communication response to obtain the reinforcer that maintains problem behavior. Thus, FCT weakens problem behavior by training individuals to emit a low-effort communication response that produces immediate high-quality reinforcement that effectively competes with the reinforcement produced by problem behavior and results in the allocation of proportionally more responses to the positive alternative. Delay-to-reinforcement fading, however, reduces the immediacy of reinforcement contingent on the communication response; therefore, response allocation tends to shift such that the positive alternative becomes less likely than problem behavior.
Fisher, Kuhn, and Thompson (1998) attempted to mitigate the limitations associated with schedule thinning during FCT by training participants to emit two different communication responses in the presence of respective discriminative stimuli (SDs): mands for the functional reinforcer for problem behaviors and mands for an alternative reinforcer. Fisher et al. then demonstrated that reductions in problem behavior could be maintained when the functional reinforcer was unavailable by presenting participants with an opportunity to request and receive an alternative reinforcer. Hagopian et al. (2005) applied the same principle when they presented participants with response-independent reinforcers during schedule-thinning components of an FCT intervention. Results from this study suggest that the delivery of competing stimuli when requested reinforcers are temporarily unavailable may enhance the effectiveness of FCT. Nonetheless, the authors demonstrated the feasibility of terminal delay-to-reinforcement intervals only up to 9 min. Furthermore, individuals' tolerance for delayed reinforcement varies, and occasions inevitably arise in which requested reinforcers are permanently unavailable (Hagopian et al., 1998). Given these findings, alternative behavior-management strategies warrant consideration.
The literature on compliance to requests provides some direction for the development of such alternative interventions. Specifically, two studies demonstrated lower rates of problem behavior and higher rates of compliance to “do” requests compared to “don't” requests. Adelinis and Hagopian (1999) evaluated the relative effects of symmetrical “do” and “don't” requests on aggression occasioned by the interruption of a putatively preferred activity. “Don't” requests specified that the ongoing activity should cease, whereas symmetrical “do” requests prompted the participant to engage in an activity incompatible with the ongoing activity. Results showed that substantially higher rates of aggression were occasioned by the presentation of “don't” requests than by the presentation of symmetrical “do” requests. Mace et al. (1988) found similarly positive effects for the use of “do” requests on compliance rates. One participant in their study complied with “do” requests 27% more often than he complied with “don't” requests. Together, these studies suggest that modifications to the stimulus properties of requests may effect changes in rates of problem behaviors and compliance. This finding is conceptually relevant to the present investigation because symmetrical “do” and “don't” requests are functionally equivalent to methods for denying access to presumably preferred objects and activities.
The last line of research pertinent to the present investigation into effective methods for denying access to tangible reinforcers involves studies on RCHs. RCHs are defined by topographically distinct responses that produce common effects on the environment but have different probabilities of occurrence. Lalli et al. (1995) presented a methodology for identifying RCHs. After a functional analysis suggested that the participant engaged in escape-maintained screams, aggression, and self-injury in a stable, escalating sequence, Lalli et al. arranged negative reinforcement contingencies for one response topography at a time while extinction operations remained in effect for the other response topographies. Data on the resulting patterns of response latencies supported the hypothesis that all three response topographies comprised an RCH. Subsequent research has replicated the finding that escalation to severe forms of problem behavior may occur when more probable (and less problematic) members of an RCH are ineffective at producing reinforcement (Harding et al., 2001; Magee & Ellis, 2000; Richman, Wacker, Asmus, Casey, & Andelman, 1999).
Lalli et al. (1995) hypothesized that the hierarchical sequencing of members of a response class may be a function of reinforcement rate, delay to reinforcement, response effort, and punishment history. Because they hypothesized that the probability of any given member of an RCH may be altered by operations involving these variables, Lalli et al. attempted to reduce occurrences of problem behavior by training their participant to emit a low-effort communication response that was functionally equivalent to other response class members and resulted in immediate high-rate reinforcement. Results showed that (a) topographically dissimilar responses may be maintained by the same reinforcer; (b) members of a response class may occur in a predictable, escalating sequence; and (c) positive alternative behaviors may be introduced into the response class to prevent escalation through the entire RCH. As discussed by Bowman, Fisher, Thompson, and Piazza (1997) in the case of tangible-maintained problem behavior, the response class may be expanded by the presentation of a discriminative stimulus for positive social behavior at the same time access to preferred activities is denied.
In sum, the existing literature indicates that (a) escalating problem behavior may be evoked by restricted access to preferred activities and maintained by positive reinforcement in the form of access to those activities, (b) the stimulus properties of requests to disengage from preferred activities may alter the probability of problem behavior and compliance, and (c) interventions implemented early in an RCH, prior to the occurrence of severe problem behavior, may prevent behavioral escalation. However, no research has explicitly examined the effects of different methods of denying access to requested activities on RCHs maintained by positive reinforcement. Therefore, the purpose of the present study was to evaluate the relative effects of three different methods of saying “no” to requests to engage in a preferred activity on the occurrence and escalation of oppositional, disruptive, and aggressive behavior.
METHOD
Participants and Setting
Philip was a 13-year-old boy who had been diagnosed with Waardenburg syndrome (Type 1) and high-functioning autism. Formal cognitive assessment had not been done; however, Philip spoke in multiple complete sentences using grade-level vocabulary and performed near grade-level academic work in most subjects. Severe hearing impairment is a characteristic feature of Waardenburg syndrome. Philip had been fitted with a cochlear implant at the age of 4 years, which resulted in him being able to hear most vocalizations of others. His hearing impairment did result in moderate articulation difficulties.
Philip lived in a residential school for children with behavior disorders secondary to developmental disabilities. All sessions were conducted in his classroom (3.5 m square) that contained two tables and chairs, cabinets, and a desk with a Dell PC computer. The walls of the classroom were decorated with several posters. The experimenter and one or two data collectors were present for all sessions.
Target Behaviors, Data Collection, and Interobserver Agreement
Philip's target behaviors were (a) oppositional vocalizations, defined as saying “no” or verbally protesting the therapist's decision to deny computer access; (b) loud vocalizations, defined as screaming or yelling at a volume above normal conversational level (excluding oppositional vocalizations); (c) disruption, defined as climbing on furniture, overturning furniture, or ripping papers off walls; and (d) aggression or threat of aggression, defined as hitting, kicking, or a verbal or gestural threat to physically harm another person.
Target behaviors were measured in two ways. Latency to the first occurrence was defined as the number of seconds from the offset of the therapist's verbal denial of access to the computer to the onset of the first occurrence of each target behavior. Latency was measured with a stopwatch, and these measures were used to establish the temporal sequence of the target behaviors that constituted an RCH (Lalli et al., 1995). Target behaviors were also measured using 10-s partial-interval recording to estimate the duration of target behaviors and thereby to evaluate the relative effectiveness of the three methods of denying computer access. The participant requested access to the computer game in all trials.
A second observer concurrently and independently collected latency and partial-interval data on Philip's target behaviors during 53% of functional analysis sessions and 28% of the sessions across all conditions of the treatment evaluation that compared methods of saying “no.” During the RCH analysis, interobserver agreement was calculated by dividing the shorter latency by the longer latency and multiplying this ratio by 100%. For partial-interval recording, interobserver agreement was calculated on an interval-by-interval basis by dividing the number of intervals with agreements by the number of intervals with agreements plus those with disagreements and multiplying by 100%. Mean agreement for the functional analysis was 100%. Mean agreement during treatment evaluation sessions was 96% for latency measures and 97% for the partial-interval data. Agreement on the temporal order of the target behaviors during the evaluation of the RCH was 100%.
Functional Analysis
A functional analysis was conducted according to the methods described by Iwata, Dorsey, Slifer, Bauman, and Richman (1982/1994) using 5-min sessions. Consequences were arranged on intermittent ratio schedules and applied to the four target behaviors in a quasirandom order to avoid the possibility that all target behaviors in the response class would not be observed. In the attention condition, Philip and a therapist conversed about a preferred topic for 2 min, after which time the session time began and the therapist said, “I have to do some work now, you can have some free time.” The therapist did paperwork and said nothing to Philip. Contingent on one of the target behaviors, the therapist provided a disapproving comment. The demand condition consisted of the therapist presenting Philip with a math worksheet that was at his grade level. Vocal prompts to continue with the assignment were provided after 5 s of Philip being off task. Occurrences of any target behavior resulted in removal of the worksheet for 15 s. There were two tangible conditions. During Tangible 1, the therapist was seated at the computer playing one of Philip's most preferred computer games. One of the data collectors vocally prompted Philip to enter the classroom and ask the therapist if he could play the game. The therapist replied, “Not now, Philip, I'm playing.” During this condition, Philip accepted this limitation and stood behind the therapist to watch the game. Given the ineffectiveness of this condition for evoking the target problem behaviors, a modified Tangible 2 condition also was implemented. The Tangible 2 condition was identical to Tangible 1 except that the therapist turned the computer screen away from Philip after delivering the statement about its unavailability. Occurrences of any of the target behaviors resulted in giving Philip 30-s access to the computer game. After this 30-s access period, the therapist said, “It's my turn to play now.” and took control of the keyboard. The control condition consisted of the therapist and Philip conversing about a topic of Philip's choice without the presence of task demands or restrictions on his access to tangible reinforcers; the computer game was not available.
Identification of Response Class Hierarchy
To demonstrate empirically that Philip's target behaviors constituted an RCH, positive reinforcement contingencies were arranged sequentially across sessions for one target behavior at a time. Thus in each session, one target topography was reinforced while the other three target topographies were placed on extinction. Session duration was 15 min.
Sessions were initiated when one therapist verbally prompted Philip to approach a second therapist to request access to the preferred computer game. The second therapist responded to the participant's request by saying, “I'm sorry, you can't play now. Professor Mace is doing his work on the computer.” This condition was similar to how Philip's school staff responded to his requests for objects or activities that were not appropriate to honor. The computer game was not visible to Philip as in the Tangible 2 condition of the functional analysis. In the first session, access to the computer was provided contingent on loud vocalizations. This positive reinforcement contingency was arranged for disruption and aggression or threats of aggression in the second and third sessions, respectively. No contingencies were applied to oppositional vocalizations because they were not considered serious enough to warrant intervention; however, they reliably began the escalation process. In Sessions 1, 2 and 3, Philip retained access to the computer for the duration of the 15-min session once it was provided. All target responses were placed on extinction during the fourth session, and access to the computer was restricted for the 15-min session duration. This four-session sequence was conducted over the course of 1 day and then replicated on a 2nd day.
Evaluation of Methods of Saying “No”
“No” with explanation (A)
The four-session RCH assessment described above served as the initial baseline (A) condition and a four-session RCH replication functioned as the second baseline. Thus, during baseline, the therapist responded to each request for computer access by denying the request and then offering the same brief explanation for the unavailability of the computer as described above. Reinforcement contingencies and extinction schedules were arranged for different target topographies across sessions in the manner described above for the RCH assessment.
“No” with explanation plus alternative (B)
This condition was identical to Condition A except that the therapist responded to Philip's request for the computer by suggesting an alternative preferred activity. Specifically, the therapist issued the following statement in response to Philip's request: “I'm sorry, you can't play now. Professor Mace is doing his work on the computer. But I would be happy to play football with you outside.” When he accepted the offer, the therapist engaged him in a game of football for approximately 5 min or until he lost interest in the activity. He never refused to engage in football play, and the session terminated after football play. None of the problem behaviors resulted in access to the computer game. In other words, whereas extinction was arranged sequentially for different topographies of problem behavior during Condition A, extinction was arranged for all topographies of problem behavior during Condition B.
“Yes” with contingency (C)
The same procedures employed in Condition B were repeated; however, the participant was granted 5-min access to the computer contingent on the completion of a nonpreferred academic assignment (i.e., a grade-level math worksheet with approximately 10 problems). The therapist responded to the participant's request for the computer by saying, “Sure you can play the computer game, just as soon as you finish this school work.” The therapist then prompted Philip to sit at a table to complete the assignment and provided assistance if he requested it. The therapist reviewed the worksheet for completion and accuracy and provided access to the computer game contingent on all of the problems being completed with 100% accuracy. Philip completed the worksheet in 7 to 10 min and never refused to do the assignment. Thus, session duration was between 12 and 15 min. None of the problem behaviors resulted in access to the computer game or any response from the therapist. Extinction was arranged for all topographies of problem behavior as in Condition B.
Design
Four consecutive baseline (A) sessions were followed by a counterbalanced alternation of Conditions B and C. This sequence was replicated according to an ABAB design.
RESULTS
Functional Analysis
Target behaviors were observed only during the Tangible 2 condition. During this condition loud or oppositional vocalizations occurred during 60% of the sessions (three of five sessions) and averaged 8% of the intervals (range, 0% to 24%). Disruption occurred during 20% of the sessions (one of five) and averaged 4% of the intervals (range, 0% to 20%). Aggression or threats occurred during 40% of the sessions (two of five) and averaged 7% of the intervals (range, 0% to 28%). These results confirmed that Philip's target behaviors were maintained by positive (tangible) reinforcement (data from the functional analysis are available from the first author).
Identification of Response Class Hierarchy
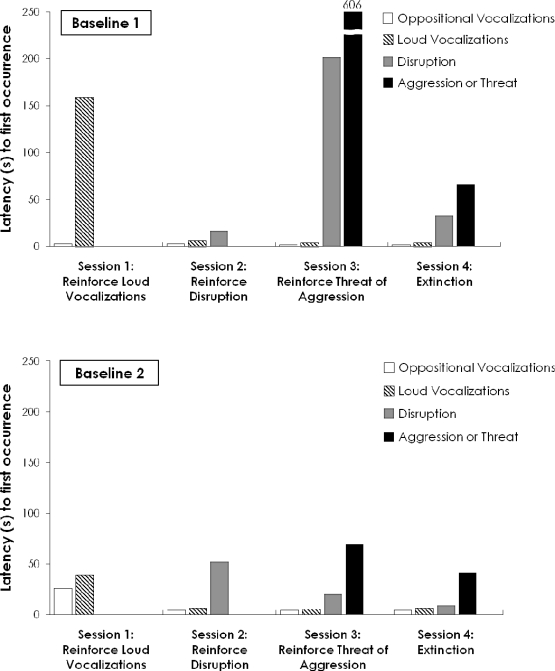
Figure 1 presents the latency in seconds to the first occurrence of each target behavior after access to the requested activity was denied. Results revealed a consistent escalating sequence of target topographies that was interrupted when reinforcement contingencies were arranged for more probable members of the response class. Thus, when computer access was provided contingent on loud vocalizations, the participant did not engage in disruption, aggression, or threats of aggression. When computer access was provided contingent on disruption, the participant did not engage in aggression or threats of aggression. When access to the computer was provided contingent on aggression or threats of aggression or denied altogether (i.e., target responses were placed on extinction), the participant emitted the full response class in the following sequence: oppositional vocalizations, loud vocalizations, disruption, and then aggression or threats of aggression.
Figure 1.
Identification of the RCH: latency to the first occurrence of target behaviors across four sessions in the first baseline phase (top) and four sessions in the second baseline phase (bottom).
Evaluation of Methods of Saying “No”
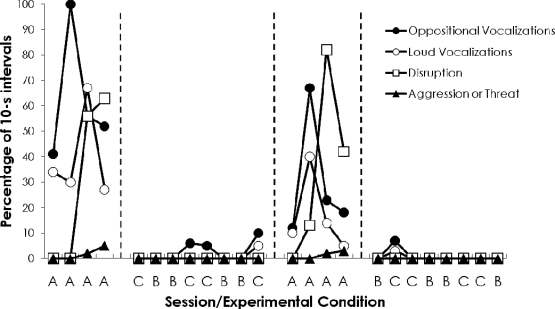
Figure 2 shows the results of the evaluation of the two alternatives methods of saying “no” compared to baseline. Data are expressed as the percentage of 10-s intervals per session during which the participant engaged in each of the four target behaviors. Because problem behaviors did occur during reinforcer access, data reflect Philip's behavior during the entire session duration. Baseline (A), which represented the therapist's typical approach to denying access to preferred activities by saying “no” and providing an explanation for his decision, was associated with consistently high levels of target behaviors. In contrast, the alternative methods of denying computer access (Conditions B and C) rarely evoked target behaviors. The participant did not display any target behaviors during Condition B, which evaluated the effects of denying access to the requested activity while providing an option to engage in an alternative preferred activity (i.e., playing football). In Condition C, which evaluated the effects of allowing access to the requested activity contingent on compliance with a therapist-issued demand, the participant engaged only in less severe members of the RCH (i.e., oppositional and loud vocalizations). These responses occurred during 5% to 10% of 10-s intervals during 50% of the sessions; no target behaviors occurred in the remaining 50% of the sessions. Thus, Condition C prevented escalation of the RCH to disruptive behavior and aggression or threats of aggression even after early members of the class had already occurred.
Figure 2.
Percentage of 10-s intervals with target behaviors across three conditions and four phases.
DISCUSSION
The present study demonstrated that a hierarchy of disruptive and destructive behaviors may be identified in the context of denying access to a requested activity by saying “no” and then offering an explanation for the refusal. The study further suggested that it may be possible to prevent occurrences of escalating behaviors maintained by positive (tangible) reinforcement by either (a) denying access to the requested activity but offering an opportunity to engage in a preferred alternative activity or (b) denying immediate access to the requested activity but permitting delayed access contingent on the completion of a low-preference demand. The latter intervention was effective even after less severe members of the RCH had occurred, demonstrating the importance of intervention to limit escalation to more severe topographies of problem behavior.
The effectiveness of the two alternative methods of saying “no” relative to the baseline approach may be interpreted in light of basic behavioral principles. The statement denying computer access in the baseline condition (i.e., saying “no” and providing an explanation for the refusal) likely functioned as a change in the discriminative stimulus (SΔ) by indicating the unavailability of reinforcement. In the participant's learning history, the statement “no” may have been correlated with extinction. Accordingly, the elevated levels of problem behavior emitted during the baseline condition may reflect the undesirable side effects associated with extinction, such as increases in the intensity (i.e., frequency, magnitude, or duration) of responding, increases in response variability, and induced aggression (Lerman, Iwata, & Wallace, 1999).
In Condition B, the therapist presented the same SΔ (i.e., “no”) but immediately introduced an SD correlated with the availability of an alternative form of reinforcement (Bowman et al., 1997). This method of saying “no” thus involved the establishment of a concurrent schedule that provided the participant with a choice to escalate disruptive behavior or to engage in the alternative. Matching theory, which provides a mathematical account of choice behavior, predicts that relative response rates distributed across concurrently available alternatives will match the relative rates of reinforcement obtained on those alternatives (Herrnstein, 1961, 1970). Accordingly, the reduction in problem behaviors as a function of Condition B may be attributable to the participant's allocation of behavior to the positive alternative; this result is predictable given the higher rate of reinforcement arranged for that alternative.
The therapist in Condition C avoided the presentation of an SΔ by saying “yes” rather than “no” and then invoked the Premack principle by making the opportunity to engage in the requested activity contingent on completion of a less probable activity (i.e., math work). However, this condition represented a functional means of saying “no.” According to this interpretive framework, Philip responded positively to the altered stimulus properties of the statement that denied access to the preferred activity, and his compliance with the demand task was reinforced by the opportunity to engage in the initially requested activity.
The effectiveness of Conditions B and C may also be attributed to alterations in the motivating conditions for problem behavior. In Condition B, the provision of access to an alternative form of reinforcement that competed with the unavailable maintaining reinforcer may be conceptualized as an abolishing operation (Laraway, Snycerski, Michael, & Poling, 2003). The therapist's offer to engage the participant in a game of football may have abolished the value of computer access as an effective form of reinforcement and abated the likelihood that he would emit disruptive or destructive behaviors that historically resulted in the therapist's compliance with his initial mand. Condition C likewise may have altered motivation to engage in problem behavior by replacing “no” with “yes” coupled with an alternative response to produce the desired computer game.
Changing the stimulus properties of the reinforcer denial statement also provided the opportunity to expand the RCH to include a positive alternative response that obtained tangible reinforcement. The changed denial statements set the occasion for agreeing to engage in an alternative to computer games (Condition B) and agreeing to complete a nonpreferred demand prior to access to the computer game (Condition C). These changed denial statements apparently functioned as SDs for positive social behavior because these responses reliably resulted in access to the requested tangible reinforcer or a substitutable one. This outcome is predicted by matching theory because, compared to the disruptive or destructive members of the RCH, the positive social alternative resulted in a comparatively high rate of high-quality reinforcement that required low to moderate response effort in the Conditions B and C, respectively. At the same time, contingencies for problem behavior were suspended, which contributed to the reallocation of behavior toward positive social forms.
The implications of these findings regarding the differential effectiveness of three methods for denying access to a requested high-preference activity are significant to clinical practice. As noted previously, a substantial portion of individuals with behavioral difficulties engage in behaviors maintained by access to positive reinforcement in the form of preferred objects or activities (Hanley, Iwata, & McCord, 2003). When these individuals mand for a reinforcer that is unavailable, their communication responses functionally are placed on extinction. Because evidence indicates that extinction operations may produce undesirable side effects, including the escalation of responses that form an RCH, interventions to reduce the likelihood of escalating behaviors warrant investigation (Lalli et al., 1995; Lerman et al., 1999). Although delay-to-reinforcement fading procedures may maintain low rates of problem behaviors when mands cannot be reinforced immediately, research indicates variable degrees of effectiveness across participants and relatively temporary meliorative effects (i.e., tolerance for delays ranging only from 10 s to 210 s; Hagopian et al., 1998, 2001). In contrast, the present results provide preliminary support for the effectiveness of a simple intervention (i.e., manipulation of the stimulus properties of the therapist's statement) for preventing escalating problem behaviors when access to a preferred activity must be denied for indefinite periods of time.
In addition to providing evidence of a functional relation between the stimulus properties of “no” statements and problem behaviors maintained by positive reinforcement, the present investigation also extends the literature on RCHs. Specifically, this represents the first study to identify an RCH of escalating behaviors during the baseline phase of the design and thus presents a potential methodological advance. This approach to assessment may prove to be advantageous to applied behavior analysts for two reasons. First, as noted by Lalli et al. (1995), methods for empirically identifying RCHs are clinically important because they provide practitioners with data needed to implement interventions early in the hierarchy and thereby to prevent occurrences of more severe members of the response class. Second, the superimposition of an RCH analysis on the baseline phase of a single-subject research study results in cost savings during the pretreatment assessment phase, which translates into shorter delays to the implementation of effective treatments.
Nonetheless, several limitations render these results preliminary in nature. First, only one individual with high-functioning autism participated. Therefore, replications with additional participants who have a variety of disabilities (e.g., emotional and behavioral disorders) are needed to establish the generality of these findings. Second, although the participant's response to both alternative methods for denying computer access was immediate and pronounced, these procedures may not be equally effective for all individuals who engage in problem behaviors maintained by positive reinforcement. Therefore, research examining additional alternative methods for denying access to preferred objects or activities is recommended. For instance, a future study may incorporate a condition in which access to the requested reinforcer is denied, but the participant is presented with a choice between two or more alternative putative reinforcers. Third, the present study did not incorporate a formal preference assessment to confirm that playing computer games and football were highly preferred activities and likely to function as reinforcers. The possibility thus remains that the pronounced reduction in problem behaviors was related, in part, to the procedural reliance on prompted mands for a presumably high-preference activity. To rule out this interpretation and to ensure approximate equivalence between the participants' preferences for the requested activities and any suggested alternative activities, future replications should include a preference or reinforcer assessment in the pretreatment phase. Finally, the present investigation demonstrated that the presentation of alternative methods of saying “no” immediately after the participant's mand effectively prevented the escalation of problem behaviors. It remains unknown, however, whether or not these alternative methods of denying access to preferred activities would effectively halt escalation when presented subsequent to the emission of one or more disruptive topographies in the RCH. In conclusion, the present study presents significant preliminary findings about three alternative methods of saying “no” that may avoid an RCH, but future studies are needed to establish the generality of these results across participants and methods.
REFERENCES
- Adelinis J.D, Hagopian L.P. The use of symmetrical “do” and “don't” requests to interrupt ongoing activities. Journal of Applied Behavior Analysis. 1999;32:519–523. doi: 10.1901/jaba.1999.32-519. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Bowman L.G, Fisher W.W, Thompson R.H, Piazza C.C. On the relation of mands and the function of destructive behavior. Journal of Applied Behavior Analysis. 1997;30:251–265. doi: 10.1901/jaba.1997.30-251. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Fisher W.W, Kuhn D.E, Thompson R.H. Establishing discriminative control of responding using functional and alternative reinforcers during functional communication training. Journal of Applied Behavior Analysis. 1998;31:543–560. doi: 10.1901/jaba.1998.31-543. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Hagopian L.P, Fisher W.W, Sullivan M.T, Acquisto J, LeBlanc L.A. Effectiveness of functional communication training with and without extinction and punishment: A summary of 21 inpatient cases. Journal of Applied Behavior Analysis. 1998;31:211–235. doi: 10.1901/jaba.1998.31-211. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Hagopian L.P, Kuhn S.A.C, Long E.S, Rush K.S. Schedule thinning following communication training: Using competing stimuli to enhance tolerance to decrements in reinforcer density. Journal of Applied Behavior Analysis. 2005;38:177–193. doi: 10.1901/jaba.2005.43-04. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Hagopian L.P, Wilson D.M, Wilder D.A. Assessment and treatment of problem behavior maintained by escape from attention and access to tangible items. Journal of Applied Behavior Analysis. 2001;34:229–232. doi: 10.1901/jaba.2001.34-229. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Hanley G.P, Iwata B.A, McCord B.E. Functional analysis of problem behavior: A review. Journal of Applied Behavior Analysis. 2003;36:147–185. doi: 10.1901/jaba.2003.36-147. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Harding J.W, Wacker D.P, Berg W.K, Barretto A, Winborn L, Gardner A. Analysis of response class hierarchies with attention-maintained problem behaviors. Journal of Applied Behavior Analysis. 2001;34:61–64. doi: 10.1901/jaba.2001.34-61. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Herrnstein R.J. Relative and absolute strength of response as a function of frequency of reinforcement. Journal of the Experimental Analysis of Behavior. 1961;4:267–272. doi: 10.1901/jeab.1961.4-267. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Herrnstein R.J. On the law of effect. Journal of the Experimental Analysis of Behavior. 1970;13:243–266. doi: 10.1901/jeab.1970.13-243. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Iwata B.A, Dorsey M.F, Slifer K.J, Bauman K.E, Richman G.S. Toward a functional analysis of self-injury. Journal of Applied Behavior Analysis. 1994;27:197–209. doi: 10.1901/jaba.1994.27-197. (Reprinted from Analysis and Intervention in Developmental Disabilities, 2, 3–20, 1982) [DOI] [PMC free article] [PubMed] [Google Scholar]
- Lalli J.S, Mace F.C, Wohn T, Livezey K. Identification and modification of a response class hierarchy. Journal of Applied Behavior Analysis. 1995;28:551–559. doi: 10.1901/jaba.1995.28-551. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Laraway S, Snycerski S, Michael J, Poling A. Motivating operations and terms to describe them: Some further refinements. Journal of Applied Behavior Analysis. 2003;36:407–414. doi: 10.1901/jaba.2003.36-407. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Lerman D.C, Iwata B.A, Wallace M.D. Side effects of extinction: Prevalence of bursting and aggression during the treatment of self-injurious behavior. Journal of Applied Behavior Analysis. 1999;32:1–8. doi: 10.1901/jaba.1999.32-1. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Mace F.C, Hock M.L, Lalli J.S, West B.J, Belfiore P, Pinter E, et al. Behavioral momentum in the treatment of noncompliance. Journal of Applied Behavior Analysis. 1988;21:123–141. doi: 10.1901/jaba.1988.21-123. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Magee S.K, Ellis J. Extinction effects during the assessment of multiple problem behaviors. Journal of Applied Behavior Analysis. 2000;33:313–316. doi: 10.1901/jaba.2000.33-313. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Mueller M.M, Wilczynski S.M, Moore J.W, Fusilier I, Trahant D. Antecedent manipulations in a tangible condition: Effects of stimulus preference on aggression. Journal of Applied Behavior Analysis. 2001;34:237–240. doi: 10.1901/jaba.2001.34-237. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Richman D.M, Wacker D.P, Asmus J.M, Casey S.D, Andelman M. Further analysis of problem behavior in response class hierarchies. Journal of Applied Behavior Analysis. 1999;32:269–283. doi: 10.1901/jaba.1999.32-269. [DOI] [PMC free article] [PubMed] [Google Scholar]