Abstract
Despite the prevalence of vocal mimicry in animals, few functions for this behaviour have been shown. I propose a novel hypothesis that false mimicked alarm calls could be used deceptively to scare other species and steal their food. Studies have previously suggested that animals use their own species-specific alarm calls to steal food. However none have shown conclusively that these false alarms are deceptive, or that mimicked alarm calls are used in this manner. Here, I show that wild fork-tailed drongos (Dicrurus adsimilis) make both drongo-specific and mimicked false alarm calls when watching target species handling food, in response to which targets flee to cover abandoning their food. The drongo-specific and mimicked calls made in false alarms were structurally indistinguishable from calls made during true alarms at predators by drongos and other species. Furthermore, I demonstrate by playback experiments that two of these species, meerkats (Suricata suricatta) and pied babblers (Turdoides bicolor), are deceived by both drongo-specific and mimicked false alarm calls. These results provide the first conclusive evidence that false alarm calls are deceptive and demonstrate a novel function for vocal mimicry. This work also provides valuable insight into the benefits of deploying variable mimetic signals in deceptive communication.
Keywords: mimicry, deception, alarm call, drongo, kleptoparasitism
1. Introduction
Many animals mimic the vocalizations of other species [1,2], yet there is little evidence of a function for this behaviour [3,4]. Hypotheses suggest that vocal mimicry may be used in interspecific communication to manipulate the behaviour of other species to the advantage of the vocal mimic (reviewed by [4]). In support of this, studies have found that phainopeplas (Phainopepla nitens) recruit other bird species to mob predators by mimicking calls [5], and that racket-tailed drongos (Dicrurus paradiseus) form foraging partnerships with species attracted by their mimetic vocalizations [6]. Perhaps the best evidence of a function for vocal mimicry indicates that it is used deceptively by cuckoos whose chicks mimic the begging calls of host species, thus allowing them to evade rejection by host parents [7]. One novel possibility is that false mimicked alarm calls may be used deceptively as part of a repertoire of alarm calls to scare and then steal food from (or kleptoparasitize) other species. Mimicry could be particularly advantageous in this system, since deceptive signals typically become ineffective when made too frequently relative to honest signals [8] and by changing their false alarm calls, a species could maintain deception.
Several studies have suggested that species use their own species-specific false alarm calls to steal food [9–12]. However, none have conclusively demonstrated that the calls are deceptive, or that mimicked calls are used. In a classic study, Munn [9] suggested that false alarm calls were used deceptively by two kleptoparasitic bird species, white-winged shrike tanagers (Lanio versicolor) and bluish-slate antshrikes (Thamnomanes scistogynus), when attacking individuals to steal their food. However, it was recently suggested that calls given during these attacks could be interpreted as aggressive signals rather than alarm signals [12]. Wheeler [11] suggested that alarm calls were used deceptively by tufted capuchins (Cebus apella nigritus) to steal food, but the proposed alarm call type made in false alarms was also a call type made in social dominance interactions, while other alarm-specific vocalizations were not made in false contexts. Furthermore, this study did not test whether the intended targets showed a similar alarm response to true and false calls, which would indicate that the alarms were deceptive [13]. It therefore remains to be shown that false alarms are used deceptively or that mimicked alarm calls are deployed in this context.
To conclusively demonstrate that false alarm calls (both species-specific and mimicked) are deceptive, it must be shown that: (i) false alarms are specific to deceptive contexts and are rarely if ever made in direct physical attacks on targets; (ii) the type of calls made in true alarms at predators are the same as the types of calls made in false alarms to scare target species and steal their food; and (iii) that the target species react with a similar alarm response to playbacks of alarm calls originally recorded in a true or false context.
Fork-tailed drongos are medium-small passerines (50 g) that principally forage alone, hawking insects from a perch or flying to the ground to catch larger food such as lizards and crickets [14,15]. However, they also follow other species, including pied babblers and meerkats, catching food that the species flush as they forage, and occasionally kleptoparasitize food directly from them [14,16]. Previous studies of interactions between pied babblers and fork-tailed drongos have also suggested that drongos make alarm calls during kleptoparasitism [17]. Drongo species, including fork-tailed drongos, are renowned vocal mimics and the racket-tailed drongo is known to mimic alarm calls [18,19], a behaviour which has also been anecdotally reported for the fork-tailed drongo [18]. In this study, I therefore investigate whether fork-tailed drongos employ their own and mimicked false alarm calls in kleptoparasitism and test the three predictions outlined above to determine whether these false alarm calls are deceptive.
2. Methods
(a). Study site and population
I collected data during two field seasons from March 2008 to July 2008, and April 2009 to September 2009 on a wild population of fork-tailed drongos located in an area of xeric savannah in the South African Kalahari Desert (26°58′ S, 21°49′ E). Details of the habitat and climate have been published elsewhere [20]. The study population consisted of 50 drongos habituated to close observation (less than 5 m), that had been captured and given individually unique colour rings. The drongo study populations' range overlapped with the territories of 11 meerkat and 10 pied babbler groups, with which the drongos associated during the study period. Meerkat groups ranged in size from 5 to 27 individuals and pied babbler groups from 3 to 14 individuals. The meerkats and babblers at the study site are both the subject of ongoing scientific studies. Consequently, they were habituated to close observation (less than 2 m) and were individually recognizable by unique dye marks on their fur or unique colour rings, respectively. Drongos were also observed interacting with 18 other bird species. To avoid disturbing behavioural interactions with these unhabituated species, observations were made at a distance of approximately 30 m with binoculars. The species drongos targeted foraged in the open on the ground and it was therefore possible to see the behaviour of both the drongo under observation and the species that they interacted with at all times.
(b). Drongo kleptoparasitic foraging strategies
To determine what strategies drongos used in kleptoparasitism and what proportion of their food they obtained from kleptoparasitism, I conducted 294 approximately 1 h focal observations (55 ± 1 min; mean ± 1 s.e.) on 25 specific drongo individuals. A minimum of six focals were collected per drongo (mean total observation time per drongo: 10.47 h, range: 4.02–20.10) between March 2008 and July 2008. During focal observations I recorded the time drongos spent foraging when alone and when following target species, defined as watching the species at a distance of less than 20 m. I also recorded all foraging attempts; whether the drongo was foraging alone or attempting to kleptoparasitize a food item found by a target individual of another species; and what strategy drongos employed in kleptoparasitism. Drongos used two strategies to kleptoparasitize food: (i) attack, the drongo flew directly at a target that was handling a food item and chased or attacked it; and (ii) call from perch, the drongo called from a perch while watching a target that was handling a food item, in response to which the target commonly fled to cover abandoning the food. In all cases, I recorded whether the foraging attempt was successful. Food items were categorized by size relative to drongo bill length; the corresponding wet mass of items of these sizes has been previously established [21] which enabled the calculation of food mass intake per hour for each focal observation.
(c). Defining true and false alarms
During focal observations I recorded all calls made by the focal drongos, other ringed drongos associating with them, and the species that focal drongos were following, from a distance of 2–30 m using a Sennheiser ME67 shotgun microphone coupled to a Marantz PMD660 digital recorder (sampling rate of 44.1 kHz and 16 bit resolution). When a drongo or other species made a call I recorded its behaviour. On 190 occasions drongos fled to cover in a tree or to a high perch while calling. When they did so, I interpreted these calls as true alarms, and observed an approaching predator (raptors, owls, foxes and mongoose species) on 98/190 occasions. On 258 occasions drongos made calls in ‘call from perch’ type kleptoparasitism; the drongos never fled to cover or to a high perch, and I never saw a predator, I interpreted these calls as false alarms. On 128 occasions an individual of another species (17 species) made a call when a known predatory species came into view, and the alarming species additionally fled to cover and/or watched the predator from a high perch. I interpreted these as true alarms by these species. When drongos made true and false alarm calls while following target species I recorded whether the majority (more than 50%) of individuals of the target species fled to cover while the drongo was making alarm calls. I measured the duration of all drongo alarms from the first to the last call given by the alarming individual from recordings displayed in Cool Edit Pro (v. 2.0). Finally, I calculated the frequency of true alarm calls given per focal individual when foraging alone and the frequency of both true and false alarms given when following other species.
(d). Comparison of true and false alarm calls
(i). Drongo-specific alarm calls
Direct attacks during kleptoparasitism were typically accompanied by ‘kerrr’ mob calls (95 ± 2% of attacks per drongo, n = 23 drongos). Kerrr mob calls were also made in 27 ± 6% of ‘call from perch’ kleptoparasitism attempts per drongo (n = 27), but since this call type is given frequently during attacks it could be interpreted as an aggressive signal rather than an alarm signal, consequently these were not considered to be false alarms and were excluded from analyses (see electronic supplementary material, S1 for sonograms of kerrr mob calls). All other alarm call types were very rarely made in kleptoparasitism involving direct attacks (mean 4 ± 1%, range 0–12% attacks per drongo, n = 17). Drongos made a wide variety of alarm call types during both true and false alarms [22]. Of these, six were considered drongo-specific alarm calls since they were recorded from at least 20 of 25 focal drongos, were the call types most likely to be made in both true and false alarms, and were never recorded from other species.
To determine whether drongo-specific alarm calls were the same when made in true and false alarms, I compared structural components of one of the drongo-specific alarm calls, the ‘chink’ call, when made by the same drongo in true and false alarms (figure 1a–c). The chink alarm call type was chosen because sufficient recordings were available for this call when made in both a true and false alarm by the same drongo. It is also one of the most commonly made calls in both true (25 ± 5%, n = 26 drongos) and false alarms (11 ± 3%, n = 27 drongos); and is rarely made in attacks (4 ± 2%, n = 23 drongos). All true chink alarm calls were made in response to flying raptors (pale chanting goshawk (Melierax canurus), gabar goshawk (Melierax gabar) and black shouldered kite (Elanus axillaris)), and all false chink alarm calls were made in ‘call from perch’ kleptoparasitism attempts. Only high quality calls were used, defined as having high amplitude relative to background noise and no overlap with other sounds. True and false chink calls were available for 12 individual drongos. Calls were displayed in spectrograms using the program Avisoft SASLab Pro (v. 4.53) (see electronic supplementary material, S1 for details). Measurements were made on five parameters: (i) duration (ms); (ii) call frequency range, calculated as the maximum peak frequency measurement from the entire call minus the minimum peak frequency measurement (Hz); (iii) peak frequency (Hz); (iv) Wiener entropy (at peak frequency), which is a measure of the randomness of sounds where 1 = random noise and 0 = pure tone; and (v) frequency change, calculated as peak frequency at the end of a call minus peak frequency at the start of the call (Hz). Chink calls were composed of two syllables and measurements were taken from both. The first syllable was harmonic and measurements were made on the fifth harmonic since this was the location of the peak frequency in all calls. Data were analysed in a paired MANOVA.
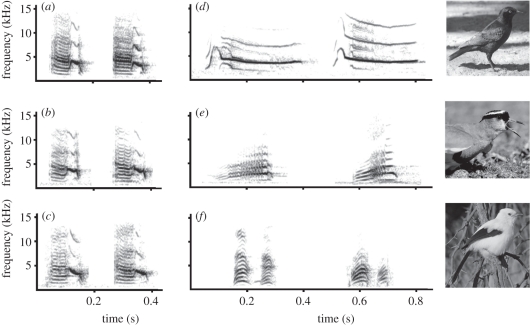
Figure 1.
(a,b,c) Sonograms from recordings; of drongo-specific chink alarm calls made in true and false contexts by three drongos; of true alarm calls made by model species in response to predators, and mimics of these calls made by drongos in false alarms: (d) glossy starling, (e) crowned plover, and (f) pied babbler. Photo credits: T. Flower, M. Boerner.
(ii). Mimicked alarm calls
In addition to drongo-specific alarm calls, drongos made a number of alarm calls that appeared to be mimicry of true alarm calls made in response to predators by other species, including glossy starlings (Lamprotornis nitens), crowned plovers (Vanellus coronatus) and pied babblers (figure 1d–f). To determine whether drongos made mimicked alarm calls in false contexts, I compared the structural components of one of the suspected false mimic alarm calls made by drongos with true alarm calls of that model species. The mimicked alarm calls of glossy starlings were selected because sufficient high quality recordings of true alarms by glossy starlings were available. They are also the most frequently mimicked call per drongo in false alarms (9 ± 4%, n = 27); and are rarely made in attacks per drongo (1 ± 1%, n = 23). The 10 highest quality false mimicked alarm calls of glossy starlings made by different drongos were selected for comparison with 10 true alarm calls made by glossy starlings in response to raptor species. To reduce the likelihood that the glossy starling true alarm calls were from the same individual, recordings were made at locations at least 800 m apart (location was recorded using a Garmin Etrex GPS). Calls were displayed in spectrograms and measurements were taken from them for the same five parameters previously defined in the drongo-specific call analysis. Data were analysed in a MANOVA.
(e). Experimental playback of true and false alarm calls
(i). Drongo-specific alarm calls
Playback experiments were undertaken to determine whether the species that drongos steal food from respond to drongo-specific alarm calls, and whether they distinguish between drongo-specific true and false alarms. I created 11 exemplars each comprising three different calls made by the same drongo to avoid pseudoreplication of my playback stimulus [23]. Details of how exemplars were made can be found in the electronic supplementary material, S1. The three calls were: (i) a true chink alarm call, (ii) a false chink alarm call, and (iii) a non-alarm call, and the order in which these were played was randomized in a block structure. The non-alarm calls were made in the absence of predators and appeared to function as territorial calls, since the same call was repeatedly made at approximately 20 s intervals from a perch and drongos on neighbouring territories typically responded by matching these calls (see electronic supplementary material, S1 for sonograms of non-alarm calls). I played each call, with a 20 minute interval between calls, to a specific meerkat or pied babbler that I had provisioned with a food item and recorded its response. Meerkats were provisioned with a live scorpion (of genus Opistophthalamus) collected at the field site and handled with tongs; meerkats commonly eat scorpions. Pied babblers were presented with three mealworms impaled on a thorn to increase handling time since the babbler had to remove them before eating. When the individual meerkat or pied babbler contacted the food item, the playback of a call was begun using a Marantz PMD 660 solid state recorder coupled to a Pignose 7–100 speaker placed on a tripod (1.2 m high), and concealed by a tree or bush 5 m from the meerkat or pied babbler. Playback amplitude was standardized at 80.3 db at 3 m, which was the mean amplitude of alarm calls given in response to a hawk glider model (see electronic supplementary material, S1 for details). Playbacks were undertaken only when group members were engaged in foraging, and at least 5 min after any natural alarm or group disturbance. The duration of the alarm response (seconds), timed from when the meerkat or pied babbler stopped handling the food item (scanned area or fled to cover) to when it resumed foraging, was recorded using a stopwatch. I also recorded whether the meerkat or pied babbler abandoned the food item, defined as dropping the food and moving greater than 1 m towards cover (a bolt hole, or thick vegetation, respectively). Drongos are able to steal food even if it is dropped only for an instant and directly next to the target individual (T. Flower 2008, personal observations), so these are conservative conditions that would enable them to steal a food item from a target. Playbacks were made to 22 meerkats in 11 groups, and 20 pied babblers in 10 groups (two individuals per group) and there was a two-week break between experimentation on the first and second individual at a group. Each exemplar was used twice, but never at the same group and no call type was played in the same order position twice at the same group.
(ii). Mimicked alarm calls
Playback experiments were undertaken to determine whether the species targeted by drongos respond to false mimicked alarm calls made by drongos and whether they differentiate between the drongos' false mimicked alarm calls and the true alarm calls of the species mimicked. I created 10 exemplars comprising four different calls: (i) a drongo false mimicked alarm call of a glossy starling, (ii) a true alarm call of a glossy starling, (iii) a drongo non-alarm call, and (iv) a glossy starling non-alarm call. Drongo non-alarm calls were recorded in the same context as for the drongo-specific alarm call playbacks; glossy non-alarm calls were recorded from individual glossy starlings in the absence of predators as they foraged, at locations at least 800 m apart (see electronic supplementary material, S1 for sonograms of non-alarm calls). The four calls were played at 20 min intervals to a meerkat or pied babbler that had been provisioned with a food item and the duration of alarm response and whether the food item was abandoned were recorded. Experimental playback techniques were identical to those outlined in the drongo-specific alarm call playback experiment with the exception of the preparation of the exemplars used in playbacks (see electronic supplementary material, S1 for details). Playbacks were undertaken to 20 meerkats in 10 groups and 20 pied babblers in 10 groups.
(f). Statistical analyses
Multifactorial analyses involved repeated sampling of individuals or exemplars. Therefore, to determine what factors affect the response time of meerkats and pied babblers to calls and whether or not a target individual abandoned a food item, linear mixed models (LMMs) and generalized linear mixed models (GLMMs) were undertaken, respectively (see electronic supplementary material, S1 for further details). Shapiro–Wilk tests were used to determine if data were distributed normally and Levene's tests were used to ensure the homogeneity of variances of the data. When appropriate, non-parametric statistics were used. For Fisher's tests, Wilcoxon signed rank tests and t-tests, two-tailed p-values are quoted. All analyses were undertaken using Genstat 10.0 (Lawes Agricultural Trust, Rothamsted, Harpenden, UK), except Levene's tests which were undertaken in Minitab 15.0 (Minitab Ltd. Coventry, UK).
3. Results
(a). False alarm call use in kleptoparasitism and the response of target species
Drongos (n = 25) spent 27 ± 3% of their foraging time following target species including pied babblers (mean 15% following time, range 0–68%) and less frequently, meerkats (mean 1% following time, range 0–7%). When following target species, drongos kleptoparasitized food items from them including insect larvae, reptiles, scorpions and crickets, contributing an average 22 ± 4% to biomass intake per focal drongo. Sometimes drongos stole food by attacking targets (52 ± 8% of kleptoparasitisms). However, in 48 ± 8% of kleptoparasitisms drongos made false alarm calls from a perch when a target was handling a food item. In 31 ± 5% of these false alarms drongos exclusively made drongo-specific alarm calls; in 42 ± 6% drongos exclusively made suspected mimicked alarm calls; and in 27 ± 6% drongos made a combination of both drongo-specific and suspected mimicked alarm calls. Target individuals fled to cover in response to false alarm calls in 211/258 (82%) cases, leaving their food behind on 140/258 (54%) occasions, enabling the drongo to fly down and steal it. These false alarms not only influenced the target, but also other group members, which also fled to cover in 110/183 (60%) cases where their response was recorded. This was similar to their response to true alarms made by drongos when following target species (79/104 cases, 75%). Although group members were less likely to respond to drongo false alarms than drongo true alarms (Fisher's test: p = 0.005), there are several probable explanations for this. Firstly, some target individuals may only respond to sustained alarms and the mean duration of false alarms (4.12 ± 1.33 s) was shorter than true alarms (27.09 ± 5.34 s) (Wilcoxon test: W21 = 26, p < 0.001, n = 22), since drongos ceased calling when food was obtained; and secondly, target species sometimes scan the area in response to alarm calls [15] and may only continue to flee to cover if a predator is seen.
False alarm calls were unlikely to be accidental alarm calls given coincidentally when target species found food, since drongos gave more alarms when following target species than when they foraged alone (paired t-test: T24 = −10.16, p < 0.001, n = 25 drongos). This was a consequence of the false alarms made in kleptoparasitism; more false alarms (3.48 ± 0.28 alarms per hour) were made than true alarms by drongos (1.04 ± 0.14 alarms per hour) when following target species (paired t-test: T24 = 5.77, p < 0.001, n = 25 drongos), while there was no change in the frequency of true alarms made when following compared with when foraging alone (1.31 ± 0.11 alarms per hour) (paired t-test: T24 = 1.79, p = 0.086, n = 25 drongos).
(b). Structural comparison of true and false alarm calls
Structural comparison of drongo-specific chink alarm calls revealed that they were not significantly different when recorded in true and false alarms made by the same individual (paired MANOVA: F2,10 = 0.92, p = 0.627, n = 12). Furthermore, the structure of mimicked glossy starling alarm calls made by drongos in false alarms was not significantly different from that of true alarm calls made by glossy starlings in response to predators (MANOVA: F5,14 = 2.01, p = 0.140, n = 20). Drongos therefore appear to make both drongo-specific and mimicked alarm calls in false alarms.
(c). Experimental playback of true and false alarm calls
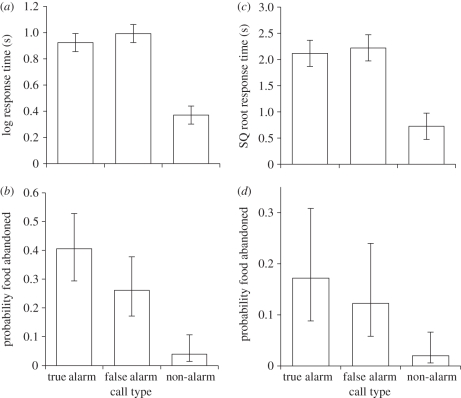
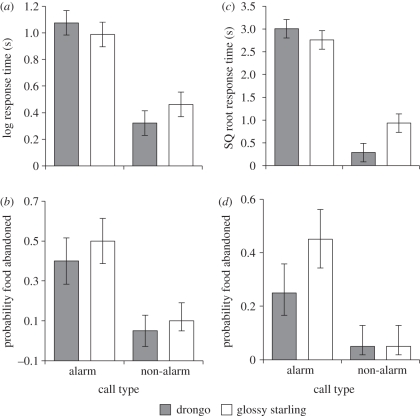
In the drongo-specific alarm call playback experiment, the response time of meerkats and pied babblers to true or false alarm calls did not significantly differ, but were significantly longer than to non-alarm calls (figure 2a,c); further statistics for analyses of playback experiments are located in figures 1 and 2, and see electronic supplementary material, S2. Meerkats were not more likely to abandon food in response to either true or false alarm calls, but were more likely to do so than in response to non-alarm calls (figure 2b). A similar pattern was observed for pied babblers, but there were no significant differences in the likelihood that food was abandoned between calls (figure 2d). In the mimicked alarm call playback experiment the response time of meerkats and pied babblers to either true glossy starling or false drongo-mimic alarm calls did not differ, but both were significantly longer than in response to non-alarm calls (figure 3a,c). Furthermore, meerkats and pied babblers did not differ in the likelihood they abandoned food in response to the true glossy starling and false drongo-mimic alarm calls, but were more likely to do so in response to these calls than to non-alarm calls (figure 3b,d). It therefore appears that both meerkats and pied babblers are deceived by drongo-specific and mimicked false alarm calls.
Figure 2.
(a) Meerkats (n = 22) responded for longer and (b) were more likely to abandon food in response to playback of true and false chink alarm calls than to non-alarm calls, but did not differ in their response to the true or false chink alarm calls (LMM response time: χ22=48.29, p < 0.001; GLMM abandon food: χ22 = 6.25, p = 0.044 (see electronic supplementary material S2, table S1)). (c) Pied babblers (n = 20) responded for longer to playback of true and false chink alarm calls than to non-alarm calls, but did not differ in their response to the true or false chink alarm calls (LMM: χ22 = 41.25, p < 0.001 (see electronic supplementary material S2, table S2)). (d) Call type did not significantly affect the likelihood that pied babblers abandoned food (GLMM: χ22 = 3.34, p = 0.188 (see electronic supplementary material S2, table S2)). Predicted mean values ± 1 s.e. calculated from models are shown.
Figure 3.
(a) Meerkats (n = 20) responded for longer and (b) were more likely to abandon food, in response to playback of false (drongo-mimicked) and true glossy starling alarm calls than to non-alarm calls of these species, but did not differ in their response to the false (drongo-mimicked) and true glossy starling alarm calls (LMM response time: χ23 = 50.44, p < 0.001; GLMM abandon food: χ23 = 11.72, p = 0.008 (see electronic supplementary material S2, table S3)). (c) Pied babblers (n = 20) responded for longer to false (drongo-mimicked) and true glossy starling alarm calls than to non-alarm calls, but did not differ in their response to the false (drongo-mimicked) and true glossy starling alarm calls though glossy starling non-alarm calls elicited a longer response than the drongo non-alarm calls (LMM: χ23 = 119.57, p < 0.001 (see electronic supplementary material S2, table S4)). (d) Pied babblers were more likely to abandon food in response to false (drongo-mimicked) and true glossy starling alarm calls than to non-alarm calls, but did not differ in their response to the false (drongo-mimicked) and true glossy starling alarm calls (GLMM: χ23 = 8.50, p = 0.005 (see electronic supplementary material S2, table S4)). Predicted mean values ± 1 s.e. calculated from models are shown.
4. Discussion
These results support the three criteria outlined in this study; firstly, drongo false alarm calls were specifically made in kleptoparasitism and rarely made in non-alarm contexts; secondly, the drongo-specific and mimicked calls made by drongos in false alarms were the same as those made in true alarms by drongos and other species; thirdly, target species alarmed in response to both true and false drongo-specific and mimicked alarm calls, which caused them to abandon their food. Previous studies have indicated that false alarm calls are used to steal food, but have not disentangled the function of the supposed false alarm calls made in kleptoparasitism or demonstrated that targets respond similarly to true and false alarm calls [11,12]. Consequently, this is the first study to show that false alarms are functionally deceptive and also demonstrates a novel function for vocal mimicry.
Animals commonly eavesdrop on the alarm calls of other species in their environment [6,24,25] and drongos appear to exploit this behaviour by using deceptive alarm calls to steal food from target species [16]. These deceptive alarm calls are likely to work because the cost to target species of ignoring drongo true alarms is greater than the cost of responding to false alarms [9,26]. However, deceptive signals typically become ineffective when made too frequently relative to their honest counterpart [8,27]. This could explain why pied babblers did not abandon their food in response to playbacks of drongo-specific chink alarms, one of the most frequently made false alarm calls. Conversely, they did abandon food in response to playback of mimicked glossy starling alarms. Vocal mimicry could therefore have large adaptive benefits in this system as drongos could change their alarm call type when their own drongo-specific calls become ineffective.
A fascinating study by Sheppard [28] revealed that frequencies of visually mimetic butterfly species in the natural environment correlated with those of distasteful model species. By analogy, we may expect drongos to reach an equilibrium point where the frequency with which they vocally mimic the alarm calls of other species reflects the natural occurrence of the model alarm call. However, alarms may vary in their reliability, drongos are likely to differ in their call repertoires and individuals may strategically adjust their alarms to match target species, or even make some call types infrequently to maintain their efficacy. Further investigation of drongo call use could therefore provide valuable insights into the strategies employed by signallers in deceptive communication.
Fork-tailed drongos appear to use a comparatively sophisticated deceptive trick, since they strategically make alarms in both honest and dishonest contexts. However, while drongo false alarms are functionally deceptive [29,30] this behaviour is likely to result from trial and error or social learning mechanisms, rather than from an understanding of how to manipulate the mental states of others, termed tactical deception [31,32]. Juvenile drongos commonly accompanied adults that were stealing food using false alarms and subsequently made false alarms themselves. Furthermore, the racket-tailed drongo is known to learn the alarm calls of other species, employing these in true alarm contexts [19], and fork-tailed drongos also appear to do this (Flower in preparation). Further investigation of deceptive signal use by animals could improve our understanding of the evolution of cognitive processes that underlie such apparently complex behaviour.
Acknowledgements
Access to the study site and meerkats was kindly provided by the Kalahari Research Trust, T. Clutton-Brock and M. Manser. A. Ridley greatly helped in the establishment of the drongo study population and provided access to the pied babblers. The Department of Environment and Conservation for Northern Province, SA provided authorization for my work (FAUNA 270/2008) and the Percy Fitzpatrick Institute, University of Cape Town provided ethical permission (2010/V20/TF). I thank N. Davies for supervision and M. Nelson-Flower, E. Goodale, M. Bell, A. Thornton, M. Gribble and A. Radford for their help and advice. R. Magrath kindly provided experimental glider designs and I am very grateful to two anonymous referees for their comments. My work was funded by the Natural Environment Research Council.
References
- 1.Baylis J. R. 1982. Avian vocal mimicry: its function and evolution. In Acoustic communication in birds (eds Kroodsma D. E., Miller E. H.), pp. 51–80 New York, NY: Academic Press [Google Scholar]
- 2.Janik V. M., Slater P. J. B. 1997. Vocal learning in mammals. Adv. Stud. Behav. 26, 59–99 10.1016/S0065-3454(08)60377-0 (doi:10.1016/S0065-3454(08)60377-0) [DOI] [Google Scholar]
- 3.Garamszegi L. Z., Eens M., Pavlova D. Z., Aviles J. M., Møller A. P. 2007. A comparative study of the function of heterospecific vocal mimicry in European passerines. Behav. Ecol. 18, 1001–1009 10.1093/beheco/arm069 (doi:10.1093/beheco/arm069) [DOI] [Google Scholar]
- 4.Kelley L. A., Coe R. L., Madden J. R., Healy S. D. 2008. Vocal mimicry in songbirds. Anim. Behav. 76, 521–528 10.1016/j.anbehav.2008.04.012 (doi:10.1016/j.anbehav.2008.04.012) [DOI] [Google Scholar]
- 5.Chu M. 2001. Heterospecific responses to scream calls and vocal mimicry by phainopeplas (Phainopepla nitens) in distress. Behaviour 138, 775–787 10.1163/156853901752233406 (doi:10.1163/156853901752233406) [DOI] [Google Scholar]
- 6.Goodale E., Kotagama S. W. 2008. Response to conspecific and heterospecific alarm calls in mixed-species bird flocks of a Sri Lankan rainforest. Behav. Ecol. 19, 887–894 10.1093/beheco/arn045 (doi:10.1093/beheco/arn045) [DOI] [Google Scholar]
- 7.Langmore N. E., Hunt S., Kilner R. M. 2003. Escalation of a co-evolutionary arms race through host rejection of brood parasitic young. Nature 422, 157–160 10.1038/nature01460 (doi:10.1038/nature01460) [DOI] [PubMed] [Google Scholar]
- 8.Pfennig D. W., Harcombe W. R., Pfennig K. S. 2001. Frequency-dependent batesian mimicry. Nature 410, 323. 10.1038/35066628 (doi:10.1038/35066628) [DOI] [PubMed] [Google Scholar]
- 9.Munn C. A. 1986. Birds that cry wolf. Nature 319, 143–145 10.1038/319143a0 (doi:10.1038/319143a0) [DOI] [Google Scholar]
- 10.Moller A. P. 1988. False alarm calls as a means of resource usurpation in the great tit, Parus major. Ethology 79, 25–30 10.1111/j.1439-0310.1988.tb00697.x (doi:10.1111/j.1439-0310.1988.tb00697.x) [DOI] [Google Scholar]
- 11.Wheeler B. C. 2009. Monkeys crying wolf? Tufted capuchin monkeys use anti-predator calls to usurp resources from conspecifics. Proc. R. Soc. B 276, 3013–3018 10.1098/rspb.2009.0544 (doi:10.1098/rspb.2009.0544) [DOI] [PMC free article] [PubMed] [Google Scholar]
- 12.Satischandra S. H. K., Kodituwakku P., Kotagama S. W., Goodale E. 2010. Assessing ‘false’ alarm calls by a drongo (Dicruris paradiseus) in mixed-species bird flocks. Behav. Ecol. 21, 396–403 10.1093/beheco/arp203 (doi:10.1093/beheco/arp203) [DOI] [Google Scholar]
- 13.Owen-Ashley N. T., Schoech S. J., Mumme R. L. 2002. Context-specific response of Florida scrub-jay pairs to Northern mockingbird vocal mimicry. The Condor 104, 858–865 10.1650/0010-5422(2002)104[0858:CSROFS]2.0.CO;2 (doi:10.1650/0010-5422(2002)104[0858:CSROFS]2.0.CO;2) [DOI] [Google Scholar]
- 14.Herremans M., Herremans-Tonnoeyr D. 1997. Social foraging of the Forktailed Drongo Dicrurus adsimilis: beater effect or kleptoparasitism? Bird Behav. 12, 41–45 [Google Scholar]
- 15.Ridley A. R., Child M. F. 2009. Specific targeting of host individuals by a kleptoparasitic bird. Behav. Ecol. Sociobiol. 63, 1119–1126 10.1007/S00265-009-0766-x (doi:10.1007/S00265-009-0766-x) [DOI] [Google Scholar]
- 16.Ridley A. R., Raihani N. J. 2007. Facultative response to a kleptoparasite by the cooperatively breeding pied babbler. Behav. Ecol. 18, 324–330 10.1093/beheco/arl092 (doi:10.1093/beheco/arl092) [DOI] [Google Scholar]
- 17.Ridley A. R., Child M. F., Bell M. B. V. 2007. Interspecific audience effects on the alarm-calling behaviour of a kleptoparasitic bird. Biol. Lett. 3, 589–591 10.1098/rsbl.2007.0325 (doi:10.1098/rsbl.2007.0325) [DOI] [PMC free article] [PubMed] [Google Scholar]
- 18.Vernon C. J. 1973. Vocal imitation by southern African birds. Ostrich 44, 23–30 [Google Scholar]
- 19.Goodale E., Kotagama S. W. 2006. Context-dependent vocal mimicry in a passerine bird. Proc. R. Soc. B 273, 875–880 10.1098/rspb.2005.3392 (doi:10.1098/rspb.2005.3392) [DOI] [PMC free article] [PubMed] [Google Scholar]
- 20.Russell A. F., Clutton-Brock T. H., Brotherton P. N. M., Sharpe L. L., McIlrath G. M., Dalerum F. D., Cameron E. Z., Barnard J. A. 2002. Factors affecting pup growth and survival in co-operatively breeding meerkats. Suricata suricatta. J. Anim. Ecol. 71, 700–709 10.1046/j.1365-2656.2002.00636.x (doi:10.1046/j.1365-2656.2002.00636.x) [DOI] [Google Scholar]
- 21.Raihani N. J., Ridley A. R. 2007. Adult vocalizations during provisioning: offspring response and postfledging benefits in wild pied babblers. Anim. Behav. 74, 1303–1309 10.1016/j.anbehav.2007.02.025 (doi:10.1016/j.anbehav.2007.02.025) [DOI] [Google Scholar]
- 22.Flower T. P., Gribble M. In preparation Fork-tailed drongos account for heterospecific referential alarm calls systems when mimicking alarm calls. [Google Scholar]
- 23.Kroodsma D. E. 1989. Suggested experimental designs for song playbacks. Anim. Behav. 37, 600–609 10.1016/0003-3472(89)90039-0 (doi:10.1016/0003-3472(89)90039-0) [DOI] [Google Scholar]
- 24.Magrath R. D., Pitcher B. J., Gardner J. L. 2007. A mutual understanding? Interspecific responses by birds to each other's alarm calls. Behav. Ecol. 18, 944–951 10.1093/beheco/arm063 (doi:10.1093/beheco/arm063) [DOI] [Google Scholar]
- 25.Bell M. B. V., Radford A. N., Rose R., Wade H. M., Ridley A. R. 2009. The value of constant surveillance in a risky environment. Proc. R. Soc. B 276, 2997–3005 10.1098/rspb.2009.0276 (doi:10.1098/rspb.2009.0276) [DOI] [PMC free article] [PubMed] [Google Scholar]
- 26.Johnstone R. A., Grafen A. 1993. Dishonesty and the handicap principle. Anim. Behav. 46, 759–764 10.1006/anbe.1993.1253 (doi:10.1006/anbe.1993.1253) [DOI] [Google Scholar]
- 27.Lindström L., Alatalo R. V., Mappes J. 1997. Imperfect Batesian mimicry: the effects of the frequency and the distastefulness of the model. Proc. R. Soc. Lond. B 264, 149–153 10.1098/rspb.1997.0022 (doi:10.1098/rspb.1997.0022) [DOI] [Google Scholar]
- 28.Sheppard P. M. 1959. The evolution of mimicry; a problem in ecology and genetics. Cold Spring Harbor. Symp. Quant. Biol. 24, 131–140 [DOI] [PubMed] [Google Scholar]
- 29.Cheney D. L., Seyfarth R. M. 1991. Truth and deception in animal communication. In Cognitive ethology: the minds of other animals (eds Ristau C. A., Griffin D. R.), pp. 127–151 Hillsdale, NJ: Lea Lawrence Erlbaum Associates [Google Scholar]
- 30.Hauser M. D. 1997. Minding the behaviour of deception. In Machiavellian intelligence II: extensions and evaluations (eds Whiten A., Byrne R.), pp. 112–143 Oxford, UK: Oxford University Press [Google Scholar]
- 31.Byrne R. A., Whiten A. 1985. Tactical deception of familiar individuals in baboons (Papio ursinus). Anim. Behav. 33, 669–673 10.1016/S0003-3472(85)80093-2 (doi:10.1016/S0003-3472(85)80093-2) [DOI] [Google Scholar]
- 32.Semple S., McComb K. 1996. Behavioural deception. Trends Ecol. Evol. 11, 434–437 10.1016/0169-5347(96)20068-0 (doi:10.1016/0169-5347(96)20068-0) [DOI] [PubMed] [Google Scholar]