Abstract
Telemedicine is a technology-based alternative to traditional health care delivery. However, poor security measures in telemedicine services can have an adverse impact on the quality of care provided, regardless of the chronic condition being studied. We undertook a systematic review of 58 journal articles pertaining to telemedicine security. These articles were selected based on a keyword search on 14 relevant journals. The articles were coded to evaluate the methodology and to identify the key areas of research in security that are being reviewed. Seventy-six percent of the articles defined the security problem they were addressing, and only 47% formulated a research question pertaining to security. Sixty-one percent proposed a solution, and 20% of these tested the security solutions that they proposed. Prior research indicates inadequate reporting of methodology in telemedicine research. We found that to be true for security research as well. We also identified other issues such as using outdated security standards.
Keywords: diabetes, privacy, safety, security, telecare, telemedicine
Introduction
Traditional health care services for the treatment of chronic conditions are expensive.1 The cost of diabetes care alone is estimated at $132 billion annually, $92 billion of this in the United States.2 Telemedicine services for diabetes are an effort to lower cost and improve quality of care.
Telemedicine, though promising in trial stages, has been less successful in real life.3,4 Reporting of research methodology used in the trials has been inadequate,5 which makes it difficult to analyze the gap between real life and trial stages.6 Security has also been identified as a determinant for successful telemedicine implementations.7 Thus, in this article, we look at the research done in the field of telemedicine security. In particular, we address the reporting of methodology in telemedicine security research. The articles reviewed include several different chronic diseases, including diabetes. The research does not break out diabetes separately, as the issues in security discovered apply across all studies.
Telemedicine security includes problems such as authorization, authentication, and accounting8 that are common with other information technology applications such as banking and manufacturing support. There are, however, many new challenges as well. Telemedicine requires information security and privacy as well as physical safety. Physical safety, for example, detection of falls in older adults, has to be evaluated remotely. The patient should be able to trust the system and not feel that human contact in terms of an onsite caregiver is needed. Thus reliability is an important concern. Fischhoff and colleagues9 noted, “Acceptable risk for a new technology is defined as that level of safety associated with ongoing activities having similar benefits to society.” Thus telemedicine systems should also be evaluated for perceptions of both patients and caregivers since they may be perceived as intrusive and ineffective.10
According to Broens and associates,7 both patient physical safety and patient information security are crucial to support the trust relationship between health care providers and patients and for acceptance of telemedicine implementations. Savastano and coworkers10 note that lack of patient trust means that patients would not reveal accurate and complete information, which lowers the quality of care. This is a critical consideration because a big part of the treatment of diabetes patients is in the accurate self-reporting of blood glucose levels. Poor quality of care would further reduce the confidence of both providers and consumers of telemedicine services. Lack of confidence would make it less likely for these services to be deployed widely.
Earlier research11 suggests that security is not the primary focus of the telemedicine research community. But this needs to change if telemedicine is to become widely acceptable.7 Several articles10,12 have suggested that poor security may lead to lesser quality of care and lack of confidence in the services for both providers and consumers and cause legal liability. These are unique challenges, separate from other forms of health-care-technology-related initiatives such as electronic medical record systems that need to be identified. Not addressing these issues in telemedicine services not only lowers the quality of care but may also have fatal consequences.13
Thus, in this review, we consider the following research questions:
What methodological details are commonly reported in telemedicine research?
What security problems are specifically targeted?
What security problems have not been adequately addressed in the literature?
What are the criteria for reliability, or how accurately and widely are the proposed solutions tested?
Methods
The framing of this research is based on Whitten and colleagues5 who conducted a systematic review of methodology in telemedicine research. We modified their approach to incorporate the research questions outlined earlier as pertaining to security. A keyword search was done on 14 journals. These journals were selected because they were focused primarily on telemedicine research from a caregiver's perspective. All 14 journals were searched through PubMed. In all, 66 articles were found. Eight articles, found with the search phrase “telemedicine and safety,” were excluded because they dealt with nontechnology-based safety issues. The dates of publication were between 1994 and 2009.
We did a keyword search on the following journals:
Journal of Telemedicine and Telecare
Journal of the American Medical Informatics Association
Journal of Nursing Management
International Journal of Medical Informatics
International Journal of Telemedicine and Applications
Health and Social Care in Community
Computer Methods in Biomedicine
Quality Assurance and Devices in Telemedicine
Medical Journal of Australia
EBMS Annual International Conference
Informatics for Health and Social Care
Telemedicine Journal and e-Health
Telemedicine Today
Studies in Health Technology and Informatics
The following keywords were used:
Telemedicine and security
Telemedicine and safety
Telemedicine and privacy
Telecare and security
Telecare and safety
Telecare and privacy
We modified the coding scheme used by Whitten and colleagues5 to answer the specific research questions pertaining to telemedicine security. The modified coding scheme is given here:
Research questions
Security questions
Type of security questions, e.g., privacy, physical safety
Threat model
Metrics (yes/no). If yes, what metrics?
Significance of problem
Solution proposed
Solution tested (yes/no). If yes, what were the results?
Limitation of the solution
Results
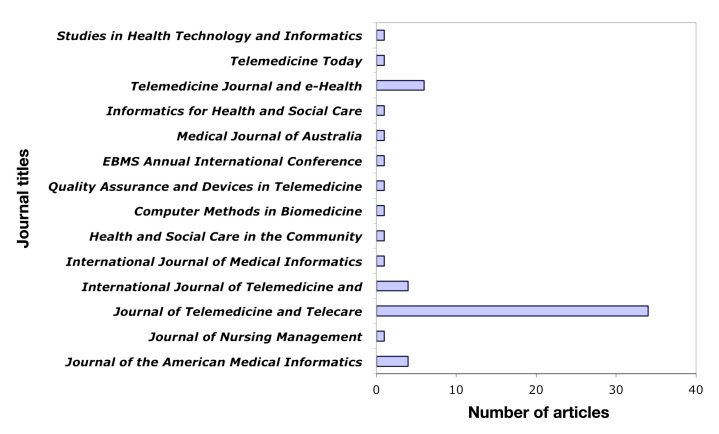
We found 58 articles in 14 journals (see Appendix; assuming no constraint on the date of publication). These articles were coded according to the scheme given in the previous section. On average, these journals publish less than 1 article per year on security. Figure 1 gives a distribution of the number of articles for each journal.
Figure 1.
Distribution of articles over journals.
Six of the articles were quantitative, 13 were qualitative, and the remaining articles were theoretical. Reporting of methodology in quantitative and qualitative articles was inadequate. Fifteen percent of the articles did not report population size. Fifty percent of the articles did not report age range. Eighty percent of the articles did not represent the age mean or median.
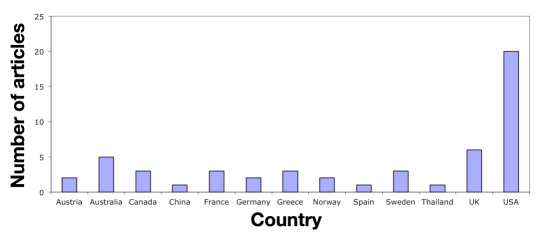
Figure 2 gives a distribution of articles by country. Europe accounts for almost half of the security research. While 20 of the articles were based in the United States, only 6 mentioned the Health Insurance Portability and Accountability Act (HIPAA).
Figure 2.
Distribution of articles across countries.
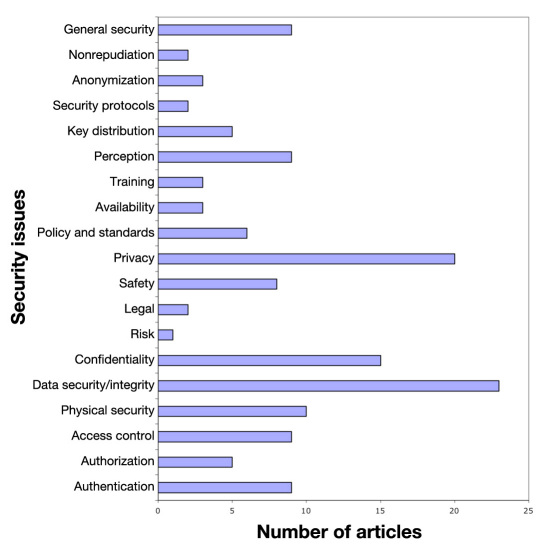
Seventy-six percent of the articles defined a security problem, and only 47% formulated a research question specific to security. Of these, 61% proposed a solution. Only 20% of these tested their solutions. None of the articles specifically tested for security. Ninety-three percent of the articles did not have a threat model. Different articles dealt with different security issues. Figure 3 shows a distribution of articles by security topics. Privacy and data integrity were most represented, but privacy is hard to maintain without addressing authentication and authorization (represented by merely nine and five articles, respectively).
Figure 3.
Distribution across security issues.
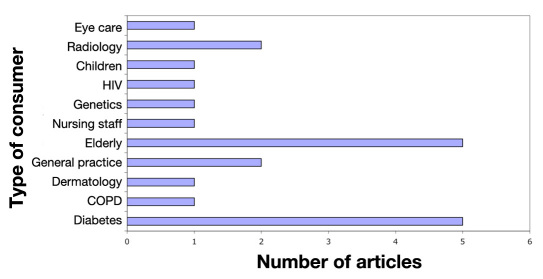
Figure 4 shows the distribution of articles over the types of consumers. Most papers addressed older adults and diabetes patients. For both these groups, security can be very important. For example, in the cases of the elderly, timely intervention in the event of a fall is important14. Older adults also suffer from an increasing occurrence of Alzheimer disease.15 Thus they should not be made to wear devices that make them stand out, or they might become targets of crime (see http://www.quackwatch.org/01quackeryrelatedtopics/hearing/fbi.html).
Figure 4.
Distribution across consumers.
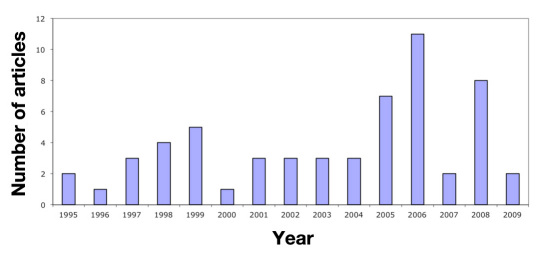
The number of publications pertaining to security in telemedicine is very low compared to the overall number of publications in telemedicine. Figure 5 shows the distribution of articles over years. The graph is left skewed, which suggests that the number of security-related publications has increased, but that might be due to an increase in the overall number of telemedicine publications.
Figure 5.
Distribution of articles across years.
Discussion
Missing Subject Data
Many qualitative and quantitative papers did not report population characteristics such as age range and average. This seems to be an important oversight because age is an important factor in the adoption of telemedicine services, as older adults are less likely to accept new technology than their younger cohorts.16
Many articles did not report the kind of users that they were catering to. This is important because security solutions cannot always be generalized. Different systems will have a different threat model. For example, physical safety is important for the elderly, but for individuals suffering from HIV/AIDS, privacy may be a bigger concern. No security solution can be all-encompassing, protecting the system against everything. The articles need to report a threat model so that the reader would know what the solution is going to protect against (see http://insecure.org/stf/whycrypto.html).
Merely three articles address training of personnel. This is an important area that needs to be addressed. One of the drawbacks of traditional care is negligence by caregivers; it is bound to happen in telemedicine as well unless the caregivers are trained well. Not only the caregivers need to be trained, but also the patients and other personnel who interact with the system directly or indirectly. Most systems are vulnerable because the users do not use them correctly. Training also prevents other attacks like social engineering.17
Legalities, Policies, and Standards
Only two articles addressed the legal issues, and five articles addressed policies and standards. Legislation and policy has been identified as one of the five determinants for successful telemedicine implementation.7 Legal issues in telemedicine are very different from legal issues in traditional caregiving, especially when it comes to legal liability. Disclosure of sensitive data can be a big problem for caregivers. Stanberry18 notes that, other than information leakage, interception and modification of telemedicine transmissions leading to inaccurate or incomplete data can have catastrophic consequences for patient care. Network-related issues such as packet dropping and jitter could also lower the quality of medical data being transmitted, leading to further liability. The only two papers18,19 that discuss legal liability were published in 1998 and 1999 and were conducted in United Kingdom. This needs to be addressed further because legal liability can often be a big hurdle in the adoption of a new technology.
Legal liability can be avoided by providing policies and standards for health care providers to observe. However, only five articles addressed policy and standards. Most articles did not talk about HIPAA or Health Level Seven (HL7) compliance. Policy and standards help in building confidence among the consumers and providers regarding the reliability and safety of the service. Savastano and coworkers10 note that certain biometric sensors might be seen to cause infections, in the case of touch-based sensors, or can be seen to cause safety concerns when the biometric technology requires the emission of infrared light as is the case with iris recognition. Standardization would reduce the fear of using these technologies. Certain other technologies like radio-frequency identification might raise privacy concerns. If a well-established standard is used, it may alleviate worries. Standardization also implies that device developers would repeatedly implement the same framework. This allows researchers to borrow from previous implementations and improve on them. Yellowlees and Harry20 also talk about standards, but their focus is on how standardization helps in quicker dissemination of technology. Alexander21 talks about developing a nationwide privacy policy for health care data in Australia. None of the papers talks about HL7, even though three of the studies have been conducted in the United States and the United Kingdom, where HL7 is the standard for storing medical data.
However, no standards are better than bad standards. Makris and associates22 use Data Encryption Standard for encryption. This paper was published in 1997. However, the algorithm was already broken in 1993.22 Makris and associates22 also describe two authentication protocols. They do not provide a proof of security for either of the protocols. Neither of the protocols is referenced, so it can be assumed that the authors constructed both protocols themselves. However, designing security protocols can be a tricky task. While protocols can be checked for attacks, using either logic-based proofs or automated modeling tools, security is not guaranteed. For example, the Needham–Schroeder protocol was proven insecure more than a decade after its publication even though the protocol had been proven secure using Burrows–Abadi–Needham logic.23,24 The researchers used an insecure algorithm for encryption and unproven security protocols for communication. This would be a concern because an insecure system can reveal private data and lead to various attacks, some even fatal.13
Another area that seems to be neglected is research on availability. Only three papers discuss availability.10,25,26 None of the papers discuss the importance of availability, the implications, or lack of it. They do not mention any measures that can be used to ensure availability. This is an important issue because it is a necessary condition for reliability of the service, especially for patients with type 1 diabetes who need to frequently monitor and report glucose levels for proper insulin therapy and lifestyle changes.
Another important property is nonrepudiation. It implies that a person cannot deny responsibility for a certain transaction. This is important to maintain audit trails because a person implicated by an audit should not be able to repudiate responsibility. Only two papers mention this property.22,27 Ferrante27 states that nonrepudiation is necessary to comply with HIPAA and thus needs to be addressed by all telemedicine systems targeted toward the United States.
Conclusion
There is a dearth of standardization in telemedicine security across all chronic illnesses under study. It also appears that many telemedicine researchers are unfamiliar with the field of security in general. There were instances of use of poor encryption standards. In some articles, authors designed their own protocols for communication without giving any proof of security, formal or otherwise. Many of these systems would have to comply with HIPAA and HL7. However, there is no discussion of how those requirements are being met. There is also insufficient reporting of methodological details that severely limits the inferences one can draw from the articles. The same system may provide good results for older adults but fail for cognitively challenged adults. Most of the articles did not try to solve the security problems they faced. The few articles that provided solutions neither formally proved them nor tested them. Most articles failed to mention the security guarantees their system would provide and did not present a threat model.
While several security challenges in telemedicine are common to all information-technology-based systems, there are unique questions that need further attention. Reliability and availability is a key issue, as many of these systems might be critical life-supporting systems. It is also important to maintain the usability of these systems without compromising the security. Usability among other factors would drive adoption. This means that these systems cannot be developed in isolation and must be developed in conjunction with the organizations they target to ensure success.28
Challenges in diabetes technology are similar to other telemedicine services. There is a need for data confidentiality during both transmission and retention. Data integrity is also a key concern to ensure correct diagnosis and quality of care. There is a need to define standards for minimum requirements. Researchers need to address these security concerns in order to increase the dissemination of telemedicine services and to improve the quality of care provided. Also, both in terms of reporting and design, the quality of security research should be improved. One recommendation would be for researchers to collaborate with researchers in security and associated fields who may have a better understanding of technology. It is also recommended to review literature in information security, especially network security and cryptography.
Acknowledgments
We thank Prof. Eugene Spafford, Prof. Victor Raskin, and Prof. Teresa Doughty who helped with the Master's thesis on which this article is based. We also thank Prof. Sheba M. George who took time to provide valuable insights.
Abbreviations
- (HIPAA)
Health Insurance Portability and Accountability Act
- (HL7)
Health Level Seven
Appendix
List of 58 Articles Reviewed
| 1. | Starren J, Hripcsak G, Sengupta S, Abbruscato CR, Knudson PE, Weinstock RS, Shea S. Columbia University's Informatics for Diabetes Education and Telemedicine (IDEATel) project: technical implementation. J Am Med Inform Assoc. 2002;9(1):25–36. |
| 2. | Lindberg DA, Humphreys BL. High-Performance Computing and Communications program, the national information infrastructure and health care. J Am Med Inform Assoc. 1995;2(3):156–9. |
| 3. | Horton K. The use of telecare for people with chronic obstructive pulmonary disease: implications for management. J Nurs Manag. 2008;16(2):173–80. |
| 4. | Wallace S, Sibson L, Stanberry B, Waters D, Goodall P, Jones R, Evans J, Dunn R. The legal and risk management conundrum of telemedicine. J Telemed Telecare. 1999;5 Suppl 1:S8–9. |
| 5. | Mao Y, Zhang Y, Zhai S. Mobile phone text messaging for pharmaceutical care in a hospital in China. J Telemed Telecare. 2008;14(8):410–4. |
| 6. | Arsand E, Tufano JT, Ralston JD, Hjortdahl P. Designing mobile dietary management support technologies for people with diabetes. J Telemed Telecare. 2008;14(7):329–32. |
| 7. | Botsis T, Demiris G, Pedersen S, Hartvigsen G. Home telecare technologies for the elderly. J Telemed Telecare. 2008;14(7):333–7. |
| 8. | Savastano M, Hovsto A, Pharow P, Blobel B. Identity-management factors in e-health and telemedicine applications. J Telemed Telecare. 2008;14(7):386–8. |
| 9. | Armstrong N, Powell J, Hearnshaw H, Dale J. Design of a trial of Internet-based self-management for diabetes. J Telemed Telecare. 2007;13 Suppl 1:1–2. |
| 10. | Barlow J, Singh D, Bayer S, Curry R. A systematic review of the benefits of home telecare for frail elderly people and those with long-term conditions. J Telemed Telecare. 2007;13(4):172–9. |
| 11. | Yellowlees PW, Harry D. Standards for data collection and monitoring in a telemedicine research network. J Telemed Telecare. 2006;12 Suppl 2:S72–6. |
| 12. | Pappa D, Telonis P, Stergioulas LK. Management of medicines information for patient safety. J Telemed Telecare. 2006;12 Suppl 1:34–6. |
| 13. | Nilsson C, Ohman M, Söderberg S. Information and communication technology in supporting people with serious chronic illness living at home-an intervention study. J Telemed Telecare. 2006;12(4):198–202. |
| 14. | Harnett B. Telemedicine systems and telecommunications. J Telemed Telecare. 2006;12(1):4–15. |
| 15. | Huston JL. Information governance standards for managing e-health information. J Telemed Telecare. 2005;11 Suppl 2:S56–8. |
| 16. | Gururajan R, Moloney C, Soar J. Challenges for implementing wireless hand-held technology in health care: views from selected Queensland nurses. J Telemed Telecare. 2005;11 Suppl 2:S37–8. |
| 17. | Lee T, Mihailidis A. An intelligent emergency response system: preliminary development and testing of automated fall detection. J Telemed Telecare. 2005;11(4):194–8. |
| 18. | Gemmill J. Network basics for telemedicine. J Telemed Telecare. 2005;11(2):71–6. |
| 19. | Strauss JS, Felten CL, Okada DH, Marchevsky AM. Virtual microscopy and public-key cryptography for Internet telepathology. J Telemed Telecare. 1999;5(2):105–10. |
| 20. | Giacomuzzi SM, Springer P, Stöger A, Dessl A, Buchberger W, Bodner G, Bale R, Schreder JG, Gell G, Jaschke W. The Austrian Academic Computer Network and its usefulness for teleradiology. J Telemed Telecare. 1998;4 Suppl 1:41–2. |
| 21. | Crowe BL, McDonald IG. Telemedicine in Australia. Recent developments. J Telemed Telecare. 1997;3(4):188–93. |
| 22. | Stalker HJ, Wilson R, McCune H, Gonzalez J, Moffett M, Zori RT. Telegenetic medicine: improved access to services in an underserved area. J Telemed Telecare. 2006;12(4):182–5. |
| 23. | Malasanos TH, Burlingame JB, Youngblade L, Patel BD, Muir AB. Improved access to subspecialist diabetes care by telemedicine: cost savings and care measures in the first two years of the FITE diabetes project. J Telemed Telecare. 2005;11 Suppl 1:74–6. |
| 24. | Cavallerano J, Aiello LM. Emerging trends in ocular telemedicine: the diabetic retinopathy model. J Telemed Telecare. 2005;11(4):163–6. |
| 25. | Alexander M. Telemedicine in Australia. 2: The Health Communication Network. J Telemed Telecare. 1996;2(1):1–6. |
| 26. | Erkert T. High-quality television links for home-based support for the elderly. J Telemed Telecare. 1997;3 Suppl 1:26–8. |
| 27. | D. Shwartz. TECHTALK: Security of internet-based telemedicine systems. Telemedicine Today. January 1998. http://www2.telemedtoday.com/articles/techtalk.shtml. Accessed November 3, 2010. |
| 28. | Fragopoulos A, Gialelis J, Serpanos D. Security framework for pervasive healthcare architectures utilizing MPEG-21 IPMP components. Int J Telemed Appl. 2009;2009:461560. |
| 29. | Data S, Pekhteryev G, Sahinolu Z, Cam H, Challa N. Real-time and secure wireless health monitoring. Int J Telemed Appl. 2008:135808. |
| 30. | Quantin C, Allaert FA, Avillach P, Fassa M, Riandey B, Trouessin G, Cohen O. Building application-related patient identifiers: what solution for a European country? Int J Telemed Appl. 2008:678302. |
| 31. | Anciaux N, Berthelot M, Braconnier L, Bouganim L, De la Blache M, Gardarin G, Kesmarszky P, Lartigue S, Navarre JF, Pucheral P, Vandewalle JJ, Zeitouni K. A tamper-resistant and portable healthcare folder. Int J Telemed Appl. 2008:763534. |
| 32. | Caceres C, Gomez EJ, Garcia F, Gatell JM, del Pozo F. An integral care telemedicine system for HIV/AIDS patients. Int J Med Inform. 2006;75(9):638–42. |
| 33. | Young NL, Barden W, McKeever P, Dick PT; Tele-HomeCare Team. Taking the call-bell home: a qualitative evaluation of Tele-HomeCare for children. Health Soc Care Community. 2006;14(3):231–41. |
| 34. | Rialle V, Lamy JB, Noury N, Bajolle L. Telemonitoring of patients at home: a software agent approach. Comput Methods Programs Biomed. 2003;72(3):257–68. |
| 35. | Xiao Y, Shen X, Sun BO, Cai L. Security and privacy in RFID and applications in telemedicine. Commun Mag IEEE. 2006;44(4):64–72. |
| 36. | Giakoumaki AL, Perakis K, Tagaris A, Koutsouris D. Digital watermarking in telemedicine applications–towards enhanced data security and accessibility. Conf Proc IEEE Eng Med Biol Soc. 2006;1:6328–31. |
| 37. | Pettersen S, Uldal SB, Baardsgard A, Amundsen M, Myrvang R, Nordvåg D, Stenmarkl H. The North Norwegian Health Net. J Telemed Telecare. 1999;5 Suppl 1:S34–6. |
| 38. | Aas IH. Changes in the job situation due to telemedicine. J Telemed Telecare. 2002;8(1):41–7. |
| 39. | Vincent DS, Berg BW, Hudson DA, Chitpatima ST. International medical education between Hawaii and Thailand over Internet2. J Telemed Telecare. 2003;9 Suppl 2:S71–2. |
| 40. | Von Tigerstrom B. Current developments in Canadian privacy and information law: implications for telehealth. J Telemed Telecare. 2000;6 Suppl 2:S83–5. |
| 41. | Sixsmith AJ. An evaluation of an intelligent home monitoring system. J Telemed Telecare. 2000;6(2):63–72. |
| 42. | Wahlberg AC, Wredling R. Telephone advice nursing–callers' experiences. J Telemed Telecare. 2001;7(5):272–6. |
| 43. | Soegner P, Rettenbacher T, Smekal A, Zur Nedden D. Guidelines for teleradiology practice: results of the Tyrolean teleradiology pilot project. J Telemed Telecare. 2003;9 Suppl 1:S48–50. |
| 44. | Celler BG, Lovell NH, Chan DK. The potential impact of home telecare on clinical practice. Med J Aust. 1999;171(10):518–21. |
| 45. | Makris L, Argiriou N, Strintzis MG. Network and data security design for telemedicine applications. Med Inform (Lond). 1997;22(2):133–42. |
| 46. | Demiris G, Edison K, Schopp LH. Shaping the future: needs and expectations of telehealth professionals. Telemed J E Health. 2004;10 Suppl 2:S60–3. |
| 47. | Starren J, Sengupta S, Hripcsak G, Ring G, Klerer R, Shea S. Making grandma's data secure: a security architecture for home telemedicine. Proc AMIA Symp. 2001:657–61. |
| 48. | Sanders JH, Bashshur RL. Challenges to the implementation of telemedicine. Telemed J. 1995 Summer;1(2):115–23. |
| 49. | Harris G. Home telecare and its discontents. Telemed Today. 1999;7(4):27–35. |
| 50. | Ferrante FE. Evolving telemedicine/ehealth techonology. Telemed J E Health. 2005;11(3):370–83. |
| 51. | Collmann J, Coleman J, Sostrom K, Wright W. Organizing safety: conditions for successful information assurance programs. Telemed J E Health. 2004;10(3):311–20. |
| 52. | Wei JC, Valentino DJ, Bell DS, Baker RS. A Web-based telemedicine system for diabetic retinopathy screening using digital fundus photography. Telemed J E Health. 2006;12(1):50–7. |
| 53. | Jones PC, Silverman BG, Athanasoulis M, Drucker D, Goldberg H, Marsh J, Nguyen C, Ravichandar D, Reis L, Rind D, Safran C. Nationwide telecare for diabetics: a pilot implementation of the HOLON architecture. Proc AMIA Symp. 1998:346–50. |
| 54. | Yogesan K, Henderson C, Barry CJ, Constable IJ. Online eye care in prisons in Western Australia. J Telemed Telecare. 2001;7 Suppl 2:63–4. |
| 55. | Bolte R, Walz M, Lehmann KJ, Hothorn T, Brill C, Hothorn L, Georgi M. Teleradiology: results of a questionnaire of German radiologists. J Telemed Telecare. 1998;4 Suppl 1:69–71. |
| 56. | Stanberry B. The legal and ethical aspects of telemedicine. 2: Data protection, security and European law. J Telemed Telecare. 1998;4(1):18–24. |
| 57. | Larsen D, Hudnall Stamm B, Davis K, Magaletta PR. Prison telemedicine and telehealth utilization in the United States: State and federal perceptions of benefits and barriers. Telemed J E Health. 2004;10 Suppl 2:S81–90. |
| 58. | Koch S. Meeting the challenges–the role of medical informatics in an ageing society. Stud Health Technol Inform. 2006;124:25–31. |
References:
- 1.Huang ES, Basu A, O'Grady M, Capretta JC. Projecting the future diabetes population size and related costs for the US. Diabetes Care. 2009;32(12):2225–2229. doi: 10.2337/dc09-0459. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2.Hogan P, Dall T, Nikolov P, American Diabetes Association Economic costs of diabetes in the US in 2002. Diabetes Care. 2003;26(3):917–932. doi: 10.2337/diacare.26.3.917. [DOI] [PubMed] [Google Scholar]
- 3.Berg M. Patient care information systems and health care work: a sociotechnical approach. Int J Med Inform. 1999;55(2):87–101. doi: 10.1016/s1386-5056(99)00011-8. [DOI] [PubMed] [Google Scholar]
- 4.Tanriverdi H, Iacono CS. Diffusion of telemedicine: a knowledge barrier perspective. Telemed J. 1999;5(3):223–244. doi: 10.1089/107830299311989. [DOI] [PubMed] [Google Scholar]
- 5.Whitten P, Johannessen LK, Soerensen T, Gammon D, Mackert M. A systematic review of research methodology in telemedicine studies. J Telemed Telecare. 2007;13(5):230–235. doi: 10.1258/135763307781458976. [DOI] [PubMed] [Google Scholar]
- 6.Whetton S. Success and failures: what are we measuring? J Telemed Telecare. 2005;11(Suppl 2):S98–S100. doi: 10.1258/135763305775124678. [DOI] [PubMed] [Google Scholar]
- 7.Broens TH, Huis in't Veld RM, Vollenbroek-Hutten MM, Hermens HJ, van Halteren AT, Nieuwenhuis LJ. Determinants of successful telemedicine implementations: a literature study. J Telemed Telecare. 2007;13(6):303–309. doi: 10.1258/135763307781644951. [DOI] [PubMed] [Google Scholar]
- 8.Stell A, Sinnott R, Ajayi O. Secure federated data retrieval in clinical trials. Proceedings of the 2nd IASTED International Conference on Telehealth; Anaheim. ACTA; 2006. [Google Scholar]
- 9.Fischhoff B, Slovic P, Lichtenstein S, Read S, Combs B. How safe is safe enough? A psychometric study of attitudes towards technological risks and benefits. Policy Sci. 1978;9(2):127–152. [Google Scholar]
- 10.Savastano M, Hovsto A, Pharow P, Blobel B. Identity-management factors in e-health and telemedicine applications. J Telemed Telecare. 2008;14(7):386–388. doi: 10.1258/jtt.2008.007014. [DOI] [PubMed] [Google Scholar]
- 11.Huston JL. Telemedical record documentation: a preliminary survey. J Telemed Telecare. 1999;5(Suppl 1):S6–S8. doi: 10.1258/1357633991932630. [DOI] [PubMed] [Google Scholar]
- 12.Huston JL. Information governance standards for managing e-health information. J Telemed Telecare. 2005;11(Suppl 2):S56–S58. doi: 10.1258/135763305775124614. [DOI] [PubMed] [Google Scholar]
- 13.Traynor P. Privacy and security concerns for personal and mobile health devices. Proceedings of the Workshop to Set A Research Agenda for Privacy and Security of Healthcare Technologies; 2009. pp. 34–48. [Google Scholar]
- 14.Lee T, Mihailidis A. An intelligent emergency response system: preliminary development and testing of automated fall detection. J Telemed Telecare. 2005;11(4):194–198. doi: 10.1258/1357633054068946. [DOI] [PubMed] [Google Scholar]
- 15.Whitehouse P, Marling C, Harvey R. Can a computer be a caregiver?. Proceedings of the AAAI-02 Workshop: Automation as Caregiver; Menlo Park. AAAI Press; 2002. pp. 103–107. [Google Scholar]
- 16.Czaja SJ, Charness N, Fisk AD, Hertzog C, Nair SN, Rogers WA, Sharit J. Factors predicting the use of technology: findings from the Center for Research and Education on Aging and Technology Enhancement (CREATE) Psychol Aging. 2006;21(2):333–352. doi: 10.1037/0882-7974.21.2.333. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 17.Mitnick K, Simon W. New York: Jon Wiley & Sons; 2003. The art of deception: controlling the human element of security. [Google Scholar]
- 18.Stanberry B. The legal and ethical aspects of telemedicine. 2: Data protection, security and European law. J Telemed Telecare. 1998;4(1):18–24. doi: 10.1258/1357633981931236. [DOI] [PubMed] [Google Scholar]
- 19.Wallace S, Sibson L, Stanberry B, Waters D, Goodall P, Jones R, Evans J, Dunn R. The legal and risk management conundrum of telemedicine. J Telemed Telecare. 1999;5(Suppl 1):S8–S9. doi: 10.1258/1357633991932748. [DOI] [PubMed] [Google Scholar]
- 20.Yellowlees PW, Harry D. Standards for data collection and monitoring in a telemedicine research network. J Telemed Telecare. 2006;12(Suppl 2):S72–S76. doi: 10.1258/135763306778393153. [DOI] [PubMed] [Google Scholar]
- 21.Alexander M. Telemedicine in Australia. 2: The Health Communication Network. J Telemed Telecare. 1996;2(1):1–6. doi: 10.1258/1357633961929079. [DOI] [PubMed] [Google Scholar]
- 22.Makris L, Argiriou N, Strintzis MG. Network access and data security design for telemedicine applications. Presented at: 2nd IEEE Symposium on Computers and Communications; 1997. [DOI] [PubMed] [Google Scholar]
- 23.Needham RM, Schroeder MD. Using encryption for authentication in large networks of computers. Comm ACM. 1978;21(12):993–999. [Google Scholar]
- 24.Lowe G. An attack on the Needham-Schroeder Public Key Authentication Protocol. Inform Process Lett. 1995;56(3):131–136. [Google Scholar]
- 25.Collmann J, Coleman J, Sostrom K, Wright W. Organizing safety: conditions for successful information assurance programs. Telemed J E Health. 2004;10(3):311–320. doi: 10.1089/tmj.2004.10.311. [DOI] [PubMed] [Google Scholar]
- 26.Koch S. Meeting the challenges–the role of medical informatics in an ageing society. Stud Health Technol Inform. 2006;124:25–31. [PubMed] [Google Scholar]
- 27.Ferrante FE. Evolving telemedicine/ehealth technology. Telemed J E Health. 2005;11(3):370–383. doi: 10.1089/tmj.2005.11.370. [DOI] [PubMed] [Google Scholar]
- 28.Whitten P, Adams I. Success and failure: a case study of two rural telemedicine projects. J Telemed Telecare. 2003;9(3):125–129. doi: 10.1258/135763303767149906. [DOI] [PubMed] [Google Scholar]