Abstract
Wireless sensor networks (WSNs) can be quickly and randomly deployed in any harsh and unattended environment and only authorized users are allowed to access reliable sensor nodes in WSNs with the aid of gateways (GWNs). Secure authentication models among the users, the sensor nodes and GWN are important research issues for ensuring communication security and data privacy in WSNs. In 2013, Xue et al. proposed a temporal-credential-based mutual authentication and key agreement scheme for WSNs. However, in this paper, we point out that Xue et al.'s scheme cannot resist stolen-verifier, insider, off-line password guessing, smart card lost problem and many logged-in users' attacks and these security weaknesses make the scheme inapplicable to practical WSN applications. To tackle these problems, we suggest a simple countermeasure to prevent proposed attacks while the other merits of Xue et al.'s authentication scheme are left unchanged.
Keywords: cryptanalysis, key agreement, mutual authentication, temporal credential, wireless sensor network
1. Introduction
Wireless sensor networks are innovative ad hoc networks that include a large number of sensor nodes with resource-constrained characteristics such as limited power, communication and computational capabilities [1–4]. As soon as sensor nodes are massively and randomly deployed in a target field, the basic functions of the gateway node are to collect sensitive data for authorized users [5,6]. In many cases, a WSN may be deployed in hostile environments and malicious intruders may launch possible attacks for disrupting the normal operations (such as impersonating a legal user to abuse the network resources, inject false messages or invalid sensors into the WSN, launch security attacks and so on) of a WSN. Therefore, entity authentication [7–16] plays an important role in WSNs and logging-in users and deployed sensors should be authenticated to be the admissible participants by the GWN.
In the recent literature, there are a few works that detail a complete secure user authentication schemes for wireless sensor networks with all their different features. In [17] Das proposed an efficient two-factor scheme of user authentication, which is based on easy-to-remember passwords and smart cards. In Das' scheme, it only needs XOR and hashing computations and this reduces the computational complexity, which is suitable for resource-constrained WSNs. Although Das' scheme enhances system performance, it did not make up for the security weaknesses [18–20]. Das' scheme has later attracted a lot of attention and several two-factor user authentication schemes with mutual authentication and key agreement have been proposed in Li et al. [20], Yeh et al. [21], Das et al. [22], Li et al. [23], and Xue et al. [24]. In [20], Li et al. proposed a secure billing service based on the framework of Das' scheme. In [21], Yeh et al. introduced an ECC-based user authentication scheme for preventing all the security flaws of the previous scheme [25]. However, in [23], Li et al. showed that Yeh et al.'s scheme is insecure against several security attacks and further proposed an improved version of Yeh et al.'s scheme, which covers all the identified weaknesses and is more efficient for practical WSN environments. In [24], Xue et al. suggest a lightweight temporal-credential-based mutual authentication and key agreement scheme that not only provides more functionality features with higher security, but also ensures low costs of computation, communication and storage.
1.1. Our Contributions
Contributions made in this work can be summarized as follows
We analyze the security weaknesses of one of the most recent temporal-credential-based authentication schemes for WSNs proposed by Xue et al. [24]. Xue et al. claimed that their authentication scheme is secure against various known attacks with mutual authentication and key agreement and is suitable for resource-constrained WSNs. However, we find that Xue et al.'s authentication scheme still has other security weaknesses such as disclosure of the password and failing to prevent the lost smart card problem and many logged-in users' attacks.
We propose an advanced scheme to prevent the security threats of Xue et al.'s authentication scheme and the phases in our scheme are shown to be efficient in terms of computational complexity and communication overhead.
Our advanced scheme provides both mutual authentication and key agreement among the user, GWN and the sensor node in wireless sensor networks.
Our three-party authentication scheme can be used to verify users and sensor nodes without revealing their passwords whenever it is deemed to be necessary.
A service period feature can be used to revoke users or sensor nodes in a controlled manner and prevent abuse by an authority node GWN.
Status-bit and login recording features are efficiently implemented and assist in catching misbehaving attackers trying to abuse network resources. The above-mentioned features are especially useful when non-registered attackers attempt illegal activities such as many logged-in user attacks.
1.2. Organization of the Paper
The remainder of the paper is organized as follows: Section 2 reviews Xue et al.'s authentication scheme [24], whose security weaknesses are shown in Section 3. We propose an advanced authentication scheme with higher security in Section 4, whose security and comparisons of related schemes are analyzed in Section 5 and Section 6, respectively. Section 7 concludes the paper.
2. A Review of Xue et al.'s Temporal-Credential-Based Authentication Scheme
In this section, we review Xue et al.'s temporal-credential-based mutual authentication scheme [24]. This scheme is mainly composed of three phases: registration, login, authentication and key agreement. Moreover, their scheme is composed of three roles: gateway node (GWN), sensor node (Sj) and user (Ui). For convenience of description, we summarize the notations used throughout this paper in Table 1.
Table 1.
Notations used throughout this paper.
| Symbol | Description |
|---|---|
| Ui | User |
| Sj | Sensor node |
| GWN | Gateway node |
| IDi/PWi | Identity/Password of the user Ui |
| SIDj/PWj | Pre-configured identity/password of the sensor node Sj |
| KGWN_U/KGWN_S | Two private system parameters only know to GWN |
| TCi/TCj | A temporal credential issued by GWN to Ui/Sj |
| TS | The timestamp value |
| KEYij | The shared session key between Ui and Sj |
| TEi | The expiration time of Ui's temporal credential |
| ⊕ | The bitwise exclusive-OR operation |
| H(•) | The one-way hashing function |
| ‖ | The bitwise concatenation operation |
2.1. Registration Phase
Before registration of the user Ui and the sensor node Sj, each Ui has a secure password pre-shared with GWN and Ui's identity IDi and hash value of Ui's password H(PWi) are stored in GWN's side. Moreover, each Sj has a pre-configured password PWi and hash value of Sj's password H(PWi) is stored in GWN's side. This phase has two parts for Ui and Sj and we review them as follows:
(U-1) Ui selects IDi and computes VIi = H(TS1‖ H(PWi)) and sends {IDi, TS1, VIi} to GWN via an open and public channel, where TS1 is current timestamp value of Ui.
(U-2) After receiving the registration request from Ui, GWN checks if |TS1–T*GWN| < ΔT, where T*GWN is the current system timestamp of GWN and ΔT is the expected time interval for the transmission delay. If it does not hold, GWN sends REJ message back to Ui. Otherwise, GWN retrieves its own copy of H(PWi) by using the key “IDi”, computes VIi* = H(TS1‖ H(PWi)) and checks if VIi* = VIi. If not, GWN terminates it; otherwise, GWN computes Pi = H(IDi‖TEi), TCi = H(KGWN_U‖Pi‖TEi) and PTCi = TCi⊕H(PWi) and personalizes the smart card for Ui with the parameters:{H(•), IDi, H(H(PWi)), TEi, PTCi}.
Before deployment of sensor nodes in a target field, each Sj performs the following steps for registration:
(S-1) Sj computes VIj = H(TS2‖H(PWj)) and sends {SIDj, TS2} to GWN via an open and public channel, where TS2 is current timestamp value of Sj.
(S-2) After receiving the message from Sj, GWN checks if |TS2–T*GWN | < ΔT, where T*GWN is the current system timestamp of GWN and ΔT is the expected time interval for the transmission delay. If it does not hold, GWN sends REJ message back to Sj. Otherwise, GWN retrieves its own copy of H(PWj) by using the key “SIDj”, computes VIj* = H(TS2‖H(PWj)) and check if VIj* = VIj. If not, GWN terminates it; otherwise, GWN computes TCj = H(KGWN_S‖ SIDj) and REGj = H(H(PWj)‖TS3)⊕TCj and sends {TS3, REGj} to Sj.
(S-3) After receiving the message from GWN, Sj checks if |TS3 – Tj*| < ΔT, where Tj* is the current timestamp value of Sj. If not, Sj terminates it; otherwise, Sj computes its temporal credential TCj = REGj⊕H(H(PWj)‖TS3) and stores it.
2.2. Login Phase
If the user Ui wants to access sensor data from the wireless sensor network, Ui inserts a smart card into a terminal and enters IDi and PWi. The terminal computes H(H(PWi)) and checks the validity of IDi and PWi with the stored IDi and H(H(PWi)). If not, the smart card terminates this login request. Otherwise, Ui passes the verification and he/she can read the information stored in the smart card. Ui computes TCi = PTCi⊕H(PWi).
2.3. Authentication and Key Agreement Phase
(A-1) Ui computes DIDi = IDi⊕H(TCi‖TS4), Ci = H(H(IDi‖TS4)⊕TCi) and PKSi = Ki⊕H(TCi‖TS4‖“000”) and sends the mutual authentication message {DIDi, Ci, PKSi, TS4, TEi, Pi} to GWN, where TS4 is current timestamp value of Ui, Ki is a random key only known to Ui and the binary number “000” is used for distinguishing H(TCi‖TS4‖“000”) and H(TCi‖TS4).
(A-2) After receiving the message from Ui, GWN checks the validity of TS4. If TS4 is valid for the transmission delay, GWN computes IDi = DIDi⊕H(H(KGWN_U‖Pi‖TEi)‖TS4), Pi* = H(IDi‖TEi), TCi = H(KGWN_U‖Pi‖TEi) and Ci* = H(H(IDi*‖TS4)⊕TCi) and verifies whether Ci* ≠ Ci or Pi* ≠ Pi. If it holds, GWN rejects Ui's login request; otherwise, GWN computes Ki = PKSi⊕H(TCi‖TS4‖“000”) and chooses a nearby suitable sensor node Sj as the accessed sensor node. GWN further computes Sj's temporal credential TCj = H(KGWN_S‖SIDj), DIDGWN = IDi⊕H(DIDi‖TCj‖TS5), CGWN = H(IDi‖TCj‖TS5) and PKSGWN = Ki⊕H(TCj‖TS5) and sends {TS5, DIDi, DIDGWN, CGWN, PKSGWN} to Sj, where TS5 is current timestamp value of GWN.
(A-3) After receiving the message from GWN, Sj checks the validity of TS5. If TS5 is valid for the transmission delay, Sj computes IDi = DIDGWN⊕H(DIDi‖TCj‖TS5) and and checks if . If not, Sj terminates this session. Else, Sj convinces that the received message is from a legitimate GWN. Moreover, Sj computes Ki = PKSGWN⊕H(TCj‖TS5), Cj = H(Kj‖IDj‖SIDj‖TS6) and PKSj = Kj⊕H(Ki‖TS6) and sends {SIDj, TS6, Cj, PKSj} to Ui and GWN, where Kj is a random key chosen by Sj.
(A-4) After receiving the message from Sj, Ui and GWN separately computes Kj=PKSj⊕H(Ki‖TS6) and Cj* = H(Kj‖IDi‖SIDj‖TS6). For GWN, if Cj* = Cj, Sj is authenticated by GWN. For the user Ui, if Cj* = Cj, Sj and GWN are authenticated by Ui. Finally, Ui and Sj can separately compute a common session key KEYij = H(Ki⊕Kj) and Ui and Sj will use KEYij for securing communications in future.
3. Security Analysis on Xue et al.'s Scheme
Xue et al. claimed that their authentication scheme is robust and secure against insider, password guessing and stolen smart card attacks. In fact, based on our security analysis, we observe that Xue et al.'s temporal-credential based scheme is insecure against these security requirements. The details of our attacks are as follows.
3.1. Stolen Verifier and Insider Attack
In Xue et al.'s scheme, GWN needs to maintain the verifier table and it stores each Ui's identity IDi and hash value to Ui's password H(PWi) in GWN's side. In a practical environment, the PWi chosen by Ui could be short and easily human memorizable, which might be convenient for Ui to remember easily and in practice many users use same identities and passwords to access various online applications or remote servers for their convenience. Thus, we assume that an attacker UA may steal the password-verifier from GWN's database and launches off-line guessing attacks on it to obtain Ui's real password PWi. The details of stolen verifier attack are as follows.
-
Step 1:
UA steals verifier table from GWN's database and retrieves the hash value of Ui's password H(PWi).
-
Step 2:
UA guesses a password PWi* and computes H(PWi*).
-
Step 3:
UA compares the result of H(PWi*) with stolen H(PWi).
A match in Step 3 above indicates the correct guessing of Ui's easy-to-remember password and Xue et al.'s authentication scheme then cannot resist the stolen verifier attack. Moreover, if a privileged insider of GWN knows Ui's password PWi, he/she may try to use the knowledge of Ui's PWi and IDi to access other applications or servers.
3.2. Off-Line Password Guessing Attack
In step (U-1) of registration phase of Xue et al.'s scheme, Ui sends{IDi, TS1, VIi} to GWN via an open and public environment, where TS1 is current timestamp value of Ui and VIi = H(TS1‖H(PWi)). If an attacker UA eavesdrops Ui's registration message {IDi, TS1, VIi}, UA can launch the off-line password guessing attack by performing the following step:
-
Step 1:
UA guesses a password PWi* and computes VIi* = H(TS1‖H(PWi*)).
-
Step 2:
UA compares the result of VIi* with eavesdropped VIi.
A match in Step 2 above indicates the correct guessing of Ui's easy-to-remember password and Xue et al.'s authentication scheme suffers from off-line password guessing attack in user side. On the other hand, in step (S-1) of registration phase, Sj sends {SIDj, TS2, VIi} to GWN via an open and public environment, where TS2 is the current timestamp value of Sj and VIj = H(TS2‖H(PWj)). If an attacker UA eavesdrops Sj's registration message {SIDj, TS2, VIj}, UA can launch an off-line password guessing attack by performing the following steps:
-
Step 1:
UA guesses a password PWj* and computes VIj* = H(TS2‖H(PWj*)).
-
Step2:
UA compares the result of VIj* with eavesdropped VIj.
A match in Step 2 above indicates the correct guessing of Sj's password and Xue et al.'s authentication scheme is then open to an off-line password guessing attack on the sensor side. Moreover, once UA has successfully guessed Sj's random password, UA can use PWj* and the eavesdropped message in step (S-2) of the registration phase to derive Sj's temporal credential TCj by computing TCj=REGj⊕H(H(PWj*)‖TS3) = H(KGWN_S‖SIDj). Finally, Xue et al.'s scheme may suffer from masquerading attacks and an attacker UA who knows TCj can easily impersonate the sensor node Sj.
3.3. Lost Smart Card Problem
Let us consider the scenario of a lost smart card problem. In the case where Ui's smart card is lost and it is picked up by an attacker UA, the stored parameters can be extracted by launching a power analysis attack [22]. As we know, the content of Ui's smart card is {H(•), IDi, H(H(PWi)), TEi, PTCi}. With this information, UA can launch another off-line password guessing attack by performing the following steps:
-
Step 1:
UA guesses a password PWi* and computes H(H(PWi*)).
-
Step 2:
UA compares the result of H(H(PWi*)) with extracted H(H(PWi*)).
If Step 2 holds, the guessed password PWi* is the same as Ui's real password PWi. Otherwise, UA tries another password. Once UA successfully guesses Ui's real password, UA can use PWi* and the content of Ui's smart card to derive Ui's temporal credential TCi by computing TCi = PTCi⊕H(PWi*) = H(KGWN_U‖Pi‖TEi). Thus, Xue et al.'s scheme may suffer from masquerading attacks and an attacker UA who knows TCi can easily impersonate a legal user Ui to log in to the gateway node and GWN is not aware of having caused any problem.
3.4. Many Logged-in Users' Problem
The many logged-in users attack [26,27] means that if a registered user Ui's smart card is massively duplicated and his/her identity IDi and password PWi are exposed to m non-registered users Ua, where a = 1, 2, …, m. Each one who has a smart card and knows IDi and PWi can log in to GWN at the same time and GWN is not aware of having caused any problem. In Xue et al.'s scheme, each non-registered user Ua generates his/her timestamp TSa and random key Ka and sends a legal login message {DIDa, Ca, PKSa, TSa, TEi, Pi} to GWN, where DIDa = IDi⊕H(TCi‖TSa), Ca = H(H(IDi‖TSa)⊕TCi) and PKSa = Ka⊕H(TCi‖TSa‖“000”). After receiving all the login requests from Ua, GWN gets the same identity IDi with different timestamps TSa and random keys Ka and GWN allows them to log in and access Ui's account simultaneously.
4. Advanced Authentication Scheme
In this section, we propose an advanced scheme with strong security. Our advanced scheme consists of four phases, namely pre-registration phase, registration phase, login phase, authentication and key agreement phase. The details of each of these phases are as follows.
4.1. Pre-Registration Phase
Before registration of the user Ui and the sensor node Sj, each Ui has a pre-configured pair of identity and password with GWN and the unique parameter and are kept by GWN to check the validity of registration user. Moreover, each Sj has a pre-configured identity SIDj and a 160-bits random number rj and the hash value of Sj's pre-configured identity and random number H(SIDj‖rj) and SIDj are stored on the GWN's side.
4.2. Registration Phase
This phase has two parts for Ui and Sj and the details will be described as follows:
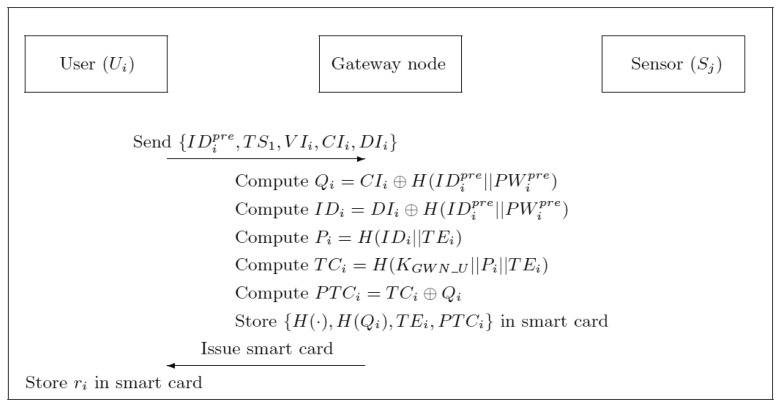
(U-1) Ui selects his/her own IDi and password PWi. Then Ui computes , , and sends { , TS1, VIi, CIi, DIi} to GWN via an open and public channel, where TS1 is current timestamp value of Ui and ri is a random number generated by Ui.
(U-2) After receiving the registration request from Ui, GWN checks if |TS1–T*GWN | < ΔT, where T*GWN is the current system timestamp of GWN and ΔT is the expected time interval for the transmission delay. If it does not hold, GWN sends REJ message back to Ui. Otherwise, GWN retrieves its own copy of by using the parameter “ ”, computes and checks if VIi* = VIi. If not, GWN terminates it; otherwise, GWN computes Qi=CIi⊕H(IDipre‖PWipre) = H(IDi‖PWi‖ri), IDi = DIi⊕H(IDipre‖PWipre), Pi = H(IDi‖TEi), TCi = H(KGWN_U‖Pi‖TEi) and PTCi = TCi⊕Qi and personalizes the smart card for Ui with the parameters:{H(•), H(Qi), TEi, PTCi}. Note that GWN maintains a write protected file as depicted in Table 2, where the Status-bit indicates the status of the user, i.e., when Ui is logged-in to GWN, the status-bit is set to one, otherwise it is set to zero. Finally, GWN sends H(Qi) and smart card to Ui via an public and open environment.
(U-3) After receiving H(Qi) and smart card from GWN, Ui checks whether the computed H(H(IDi‖PWi‖ri)) is equal to H(Qi). If they are not equal, Ui aborts this session and the smart card. Otherwise, GWN is authenticated by Ui. Ui enters ri into his/her smart card and Ui's smart card contains {H(•), H(Qi), TEi, PTCi, ri}. Note that Ui does not need to remember ri after finishing this phase. The communication handshakes of the registration phase of the user Ui are depicted in Figure 1.
Table 2.
The identity table of GWN after finishing the registration phase.
| User Identity | Password-Verifier | Status-Bit | Last Login | Service Period |
|---|---|---|---|---|
| … | … | … | … | … |
| IDi | Qi | 0/1 | N/A | TEi |
| … | … | … | … | … |
Figure 1.
Communication handshakes of the registration phase of the user Ui.
Before deployment of sensor nodes in a target field, each Sj performs the following steps for registration.
(S-1) Sj computes VIj = H(TS2‖H(SIDj‖rj)) and sends {SIDj, TS2, VIj} to GWN via an open and public channel, where TS2 is current timestamp value of Sj.
(S-2) After receiving the message from Sj, GWN checks if |TS2–T*GWN | < ΔT, where T*GWN is the current system timestamp of GWN and ΔT is the expected time interval for the transmission delay. If it does not hold, GWN sends REJ message back to Sj. Otherwise, GWN retrieves its own copy of H(SIDj‖rj) by using the key “SIDj”, computes VIj* = H(TS2‖H(SIDj‖rj)) and checks if VIj* = VIj. If not, GWN terminates it; otherwise, GWN computes TCj = H(KGWN_S‖SIDj), Qj = H(TS3‖H(SIDj‖rj)) and REGj = H(H(SIDj ‖rj) ‖TS3)⊕TCj and sends {TS3, Qj, REGj} to Sj.
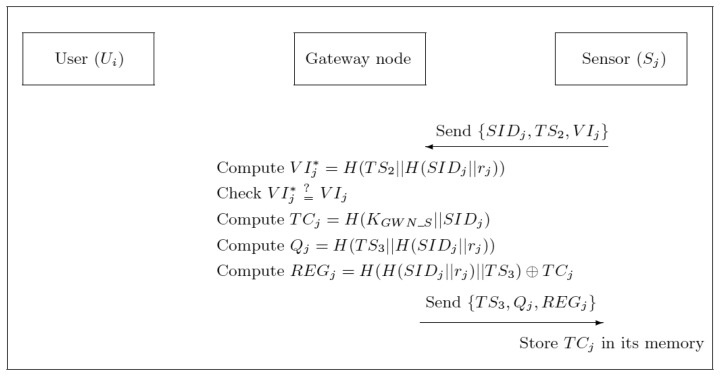
(S-3) After receiving the message from GWN, Sj checks if |TS3–Tj*| < ΔT, where Tj* is the current timestamp value of Sj. If not, Sj terminates it. Otherwise, Sj checks whether the computed H(TS3‖H(SIDj‖rj) is equal to Qj. If they are equal, Sj computes its temporal credential TCj = REGj⊕H(H(SIDj)‖rj‖TS3) and stores it. Note that Sj does not need to store rj after finishing the phase. The communication handshakes of the registration phase of sensor node Sj are depicted in Figure 2.
Figure 2.
Communication handshakes of the registration phase of sensor node Sj.
4.3. Login Phase
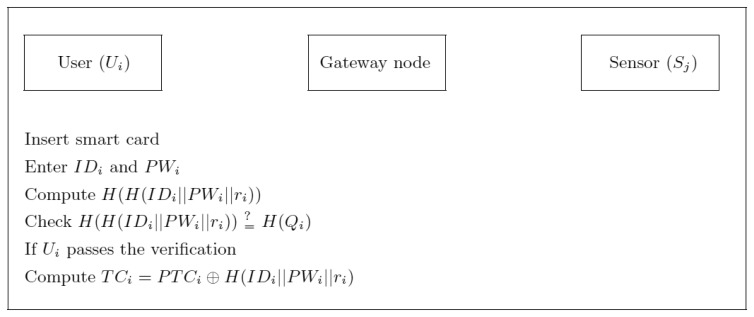
If the user Ui wants to access sensor data from the wireless sensor network, Ui inserts a smart card into a card reader and enters IDi and PWi. The smart card retrieves ri, computes H(H(IDi‖PWi‖ri)) ≠ H(Qi), and the smart card terminates this login request. Otherwise, Ui passes the verification and he/she can read the information stored in the smart card. Ui computes TCi = PTCi⊕H(IDi‖PWi‖ri). The details of the login phase are shown in Figure 3.
Figure 3.
Illustration of the login phase of our advanced scheme.
4.4. Authentication and Key Agreement Phase
(A-1) Ui computes DIDi = IDi⊕H(TCi‖TS4), Ci = H(H(IDi‖PWi‖ri)‖TS4)⊕TCi) and PKSi = Ki⊕H(TCi‖TS4‖“000”) and H(TCi‖TS4).
(A-2) After receiving the message from Ui, GWN checks the validity of TS4. If TS4 is valid for the transmission delay, GWN computes TCi* = H(KGWN_U‖Pi‖TEi) and IDi = DIDi⊕H(TCi*‖TS4) and retrieves Ui's password-verifier of Qi = H(IDi‖PWi‖ri) by using the parameter “IDi”. Then, GWN further computes Ci* = H(H(Qi‖TS4)⊕TCi) and verifies whether Ci* = Ci. If it does not hold, GWN rejects Ui's login request; otherwise, the status-bit is set to one and TS4 is recorded in the 4th field of the identity table to demonstrate Ui's last login. GWN computes Ki = PKSi⊕H(TCi‖TS4‖“000”) and chooses a nearby suitable sensor node Sj as the accessed sensor node. GWN further computes Sj's temporal credential TCj = H(KGWN_S‖SIDj), DIDGWN = IDi⊕H(DIDi‖TCj‖TS5), CGWN = H(IDi‖TCi‖TS5) and PKSGWN = Ki⊕H(TCj‖TS5) and sends {TS5, DIDi, DIDGWN, CGWN, PKSGWN} to Sj, where TS5 is current timestamp value of GWN.
(A-3) After receiving the message from GWN, Sj checks the validity of TS5. If TS5 is valid for the transmission delay, Sj computes IDi = DIDGWN⊕H(DIDi‖TCj‖TS5) and C*GWN = H(IDi‖TCj‖TS5) and check if C*GWN = CGWN. If not, Sj terminates this session. Else, Sj convinces that the received message is from a legitimate GWN. Moreover, Sj computes Ki = PKSGWN⊕H(TCj‖TS5), Cj = H(Kj‖IDi‖SIDi‖TS6) and PKSj = Kj⊕H(Ki‖TS6) and sends{SIDj, TS6, Cj, PKSj} to Ui and GWN.
(A-4) After receiving the message from Sj, Ui and GWN separately computes Kj = PKSj⊕H(Ki‖TS6) and Cj* = H(Kj‖IDi‖SIDj‖TS6). For GWN, if Cj* = Cj, Sj is authenticated by GWN. For the user Ui, if Cj* = Cj, Sj and GWN are authenticated by Ui. Finally, Ui and Sj can separately compute a common session key KEYij = H(Ki⊕Kj) and Ui and Sj will use KEYij for securing communications in future.
After finishing the authentication and key agreement phase, the identity table is updated and the content of the identity table is shown in Table 3. The detailed steps of the authentication and key agreement phase are shown in Figure 4.
Table 3.
The identity table of GWN after finishing the authentication and key agreement phase.
| User Identity | Password-Verifier | Status-Bit | Last Login | Service Period |
|---|---|---|---|---|
| … | … | … | … | … |
| IDi | Qi | 0/1 | TS4 | TEi |
| … | … | … | … | … |
Figure 4.
Illustration of the authentication and key agreement phase of our advanced scheme.
5. Security Analysis on Our Advanced Authentication Scheme
In this section, for security analysis on our advanced authentication scheme, we use the threat model described in Section 3 and show that our proposed scheme can withstand the following security attacks. Let us consider the following threat scenarios.
-
–Scenario 1
We assume that a privileged-insider of GWN can steal Ui's identity and password verifier from the GWN's identity table.
-
– Scenario 2
We assume that an attacker can eavesdrop Ui's registration message.
-
– Scenario 3
We assume that a legal user's smart card has been stolen or lost and the attacker can extract the secret parameters stored in the smart card.
-
– Scenario 4
We assume that Ui's identity IDi, password PWi and login parameters {H(•), H(Qi), TEi, PTCi, ri} are leaked to more than one non-registered users.
5.1. Resistance to Stolen Verifier and Insider Attacks
In registration phase of our advanced authentication scheme, Ui registers to GWN by presenting Qi = H(IDi‖PWi‖ri) instead of PWi and H(PWi). For the threat model in Scenario 1, we assume that a privileged-insider of GWN can steal Ui's identity and password-verifier from GWN's identity table. Note that the value of ri is not revealed to GWN and the bit length of |ri| is large enough. If SHA-256 is used in our advanced scheme, the attacker may attempt to derive PWi and ri from password-verifier Qi = H(IDi‖PWi‖ri). Due to the intractability under the assumption of a secure one-way hashing function and the bit-length of ri is 160 bits. Thus, the probability to guess correct ri is 1/2160. Moreover, the attacker must guess a correct password PWi and the probability to guess a correct p character PWi approximated to 1/26p. Therefore, it is computationally infeasible for the attacker to derive Ui's password PWi and random number ri at the same time because the probability approximated to 1/2(6p+160). As a result, a privileged-insider still cannot derive Ui's real password PWi by performing off-line password guessing attacks on H(IDi‖PWi‖ri) and our advanced authentication scheme is secure against stolen verifier and insider attacks.
5.2. Resistance to Off-Line Password Guessing Attacks
In step (U-1) of registration phase of our scheme, Ui sends { , TS1, VIi, CIi, DIi} to GWN via an open and public environment. For the threat model in Scenario 2, if an attacker UA eavesdrops Ui's registration message { , TS1, VIi, CIi, DIi}. First, UA cannot derive Ui's password-verifier H(IDi‖PWi‖ri) from because UA does not know Ui's unique parameter . Second, Ui's password-verifier H(IDi‖PWi‖ri) is under protection of a one-way hashing function and it is computationally infeasible without knowing Ui's identity IDi, password PWi and the random number ri. We assume the bit-length of IDi is q characters and the probability to guess a correct m character IDi approximated to 1/26q. Therefore, it is computationally infeasible for the attacker to derive Ui's identity IDi, password PWi and random number ri at the same time because the probability approximated to 1/2(6p+6q+160). On the other hand, in step (S-1) of registration phase of our scheme, Sj registers to GWN by presenting {SIDj, TS2, VIj = H(TS2‖H(SIDj‖rj))} instead of PWj and H(PWj). Therefore the attacker cannot launch an off-line guessing attack unless he/she knows the random number rj. In this case, a possible off-line password guessing attack on user or sensor side is not working in our advanced scheme.
5.3. Resistance to Smart Card Lost Problem
The smart card lost problem is an inherent limitation of remote user authentication schemes. For the threat model in Scenario 3, we assume that Ui's smart card has been stolen or lost and the attacker UA can extract the secret parameters {H(•), H(Qi), TEi, PTCi, ri} stored in the smart card. However, in order to log in to GWN by using Ui's lost or stolen smart card, UA needs to guess real identity IDi and password PWi correctly at the same time. In fact, it is computationally infeasible to guess these two parameters correctly at the same time in polynomial time since IDi and PWi are well-protected by a one-way hashing function. Therefore, our proposed scheme can withstand this type of attack too.
5.4. Resistance to the Many Logged-in Users Problem
For the threat model in Scenario 4, we assume that Ui's identity IDi, password PWi and parameters {H(•), H(Qi), TEi, PTCi, ri} are leaked to more than one non-registered users. However, the gateway node GWN maintained a status-bit field and a last login field in its identity table. Therefore, no one is allowed to login GWN at the same time out of all who know IDi, PWi and valid parameters {H(•), H(Qi), TEi, PTCi, ri}. Based on the protection of GWN's identity table, the advanced scheme is secure against many logged-in users attacks.
6. Comparisons of Related Schemes
In this section, we will analyse the functionality and performance of our advanced scheme and compare it with Xue et al.'s scheme [24] and other related schemes [17,21]. Functionality and performance comparisons of our scheme and other related schemes [17,21,24] are shown in Table 4 and Table 5, respectively. In Table 4, we can see that our advanced scheme not only provides proper password protection and secure service billing, but also prevents many logged-in users attack and other attacks. According to the analysis results reported in [10,24], the time complexity of various operations in terms of TH and TECC are listed in Table 5. We have compared the computational complexity using both formulated results and rough quantitative analysis in Table 5 for different phases: the registration, login and authentication phases of [17,21,24], and our scheme. For example in the test environment (CPU: 2.4 GHz, RAM: 4.0 G), we have run it 100 times to get the average result. TH is about 3,000 times faster than TECC (TH is nearly 0.0002 second on average when using SHA-256 and TECC is nearly 0.6 second on average when using ECC-160). Our advanced scheme, Yeh et al. [21] and Xue et al. [24] all provide the functions of session key agreement and mutual authentication between each two of the user, GWN and the sensor node.
Table 4.
Functionality comparisons of our advanced scheme and related schemes.
| Items/Schemes | Das [17] (2009) | Yeh et al.[21] (2011) | Xue et al.[24] (2013) | Our Advanced Scheme |
|---|---|---|---|---|
| Mutual authentication | No | Yes | Yes | Yes |
| Key agreement | No | Yes | Yes | Yes |
| Password protection | No | No | No | Yes |
| Provision of service billing | No | No | Yes | Yes |
| Resistant to stolen verifier attack | Yes | Yes | No | Yes |
| Resistant to insider attack | No | Yes | No | Yes |
| Resistant to lost smart card attack | No | No | No | Yes |
| Resistant to many logged-in users' attack | No | No | No | Yes |
Table 5.
Performance comparisons of our advanced scheme and related schemes.
| Participant/Computations | Das [17] (2009) | Yeh et al.[21] (2011) | Xue et al.[24] (2013) | Our Advanced Scheme |
|---|---|---|---|---|
| User (Ui) | 4 TH | 1 TH + 2 TECC | 7 TH | 9 TH |
| Sensor (Sj) | 1 TH | 3 TH + 2 TECC | 5 TH | 6 TH |
| Gateway node (GWN) | 7 TH | 4 TH + 4 TECC | 10 TH | 11 TH |
| Computation costs | 12 TH | 8 TH + 8 TECC | 22 TH | 26 TH |
| Computation time | 0.0024 s | 4.8016 s | 0.0044 s | 0.0052 s |
TH: Time for SHA-256 one-way hashing computation; TECC: Time for ECC-160 encryption/decryption computation; s: Second.
Moreover, our scheme and Xue et al. [24] both provide the service billing function. Our advanced scheme requires 9TH for the user, 6TH for the sensor node and 11TH for GWN. Assume TH = 0.0002 second and TECC = 0.6 second according to our simulation.
Compared with other three schemes which cannot ensure password protection, all participants in three phases of our advanced scheme require about 0.0052 seconds, which can be almost ignored, so our advanced scheme does not increase too much computational complexity while providing more function requirements and preventing more security attacks.
7. Conclusions
In this paper, we have analyzed the vulnerability and security attacks existing in Xue et al.'s temporal-credential-based mutual authentication scheme and proposed an advanced secure authentication scheme which can satisfy mutual authentication and key agreement between the user, the gateway node and the sensor node. Compared to the existing schemes, our advanced scheme supports extra functionalities such as user password protection and login recording strategy for enhancing the system security. In addition, through the use of lightweight one-way hashing computation, our authentication scheme significantly reduces the implementation cost. Through informal security analysis, we have shown that our proposed scheme has the ability to resist various known attacks, including stolen verifier attacks, insider attacks, lost smart card problems and many logged-in users attack, etc. As a result, extra functionalities are added and its higher security along with low computational cost make our advanced scheme very appropriate for securing wireless sensor networks in practice.
Acknowledgments
This research was partially supported by the National Science Council, Taiwan, R.O.C., under contract No.: NSC 101-2221-E-165-002 and NSC 102-2221-E-030-003.
Conflict of Interest
The authors declare no conflict of interest.
References
- 1.Asadi M., Zimmerman C., Agah A. A game-theoretic approach to security and power conservation in wireless sensor networks. Int. J. Netw. Secur. 2013;15:50–58. [Google Scholar]
- 2.Das A.K. Improving Identity-based Random Key Establishment Scheme for Large-scale hierarchical wireless sensor networks. Int. J. Netw. Secur. 2012;14:1–21. [Google Scholar]
- 3.Li C.T. Secure smart card based password authentication scheme with user anonymity. Inform. Technol. Contr. 2011;40:157–162. [Google Scholar]
- 4.Mi Q., Stankovic J.A., Stoleru R. Practical and secure localization and key distribution for wireless sensor networks. Ad Hoc Netw. 2012;10:946–961. [Google Scholar]
- 5.Jie H., Guohua O. A public key polynomial-based key pre-distribution scheme for large-scale wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2012;16:45–64. [Google Scholar]
- 6.Poornima A.S., Amberker B.B. Secure end-to-end data aggregation (seeda) protocols for wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2013;17:193–219. [Google Scholar]
- 7.Delgado-Mohatar O., Fuster-Sabater A., Sierra J.M. A light-weight authentication scheme for wireless sensor networks. Ad Hoc Netw. 2011;9:727–735. [Google Scholar]
- 8.Han K., Kim K., Choi W., Choi H.H., Seo J., Shon T. Efficient authenticated key agreement protocols for dynamic wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2012;14:251–269. [Google Scholar]
- 9.Li C.T., Hwang M.S. An efficient biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 2010;33:1–5. [Google Scholar]
- 10.Li C.T., Hwang M.S. A lightweight anonymous routing protocol without public key en/decryptions for wireless ad hoc networks. Inform. Sci. 2011;181:5333–5347. [Google Scholar]
- 11.Li Z., Gong G. Computationally efficient mutual entity authentication in wireless sensor networks. Ad Hoc Netw. 2011;9:204–215. [Google Scholar]
- 12.Li C.T., Lee C.C. A novel user authentication and privacy preserving scheme with smart cards for wireless communications. Math. Comput. Model. 2012;55:35–44. [Google Scholar]
- 13.Li C.T. A more secure and efficient authentication scheme with roaming service and user anonymity for mobile communications. Inform. Technol. Contr. 2012;41:69–76. [Google Scholar]
- 14.Ramasamy R., Muniyandi A.P. An efficient password authentication scheme for smart card. Int. J. Netw. Secur. 2012;14:180–186. [Google Scholar]
- 15.Barsocchi P., Chessa S., Martinovic I., Oligeri G. A cyber-physical approach to secret key generation in smart environments. J. Amb. Intell. Human. Comput. 2013;4:1–16. [Google Scholar]
- 16.Barsocchi P., Chessa S., Martinovic I., Oligeri G. AmbiSec: Securing smart spaces using entropy harvesting. Lect. Notes Comput. Sci. 2010;6439:73–85. [Google Scholar]
- 17.Das M.L. Two-factor user authentication scheme in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009;8:1086–1090. [Google Scholar]
- 18.Han K., Kim K., Choi W. An enhanced two-factor user authentication scheme in wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2010;10:361–371. [Google Scholar]
- 19.Khan M.K., Alghathbar K. Cryptanalysis and security improvements of two-factor user authentication in wireless sensor networks. Sensors. 2010;10:2450–2459. doi: 10.3390/s100302450. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 20.Li C.T., Lee C.C., Wang L.J., Liu C.J. A secure billing service with two-factor user authentication in wireless sensor networks. Int. J. Innov. Comput. Inform. Contr. 2011;7:4821–4831. [Google Scholar]
- 21.Yeh H.L., Chen T.H., Liu P.C., Kim T.H., Wei H.W. A secure authentication protocol for wireless sensor networks using elliptic curves cryptography. Sens. J. 2011;11:4767–4779. doi: 10.3390/s110504767. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 22.Das A.K., Sharma P., Chatterjee S., Sing J.K. A dynamic password-based user authentication scheme for hierarchical wireless sensor networks. J. Netw. Comput. Appl. 2012;35:1646–1656. [Google Scholar]
- 23.Li C.T., Lee C.C., Lee C.W. An improved two-factor user authentication protocol for wireless sensor networks using elliptic curve cryptography. Sens. Lett. 2013 in press. [Google Scholar]
- 24.Xue K., Ma C., Hong P., Ding R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013;36:316–323. [Google Scholar]
- 25.Chen T.H., Shih W.K. A robust mutual authentication protocol for wireless sensor networks. ETRI J. 2010;32:704–712. [Google Scholar]
- 26.Li C.T., Lee C.C., Weng C.Y., Fan C.I. An extended multi-server-based user authentication and key agreement scheme with user anonymity. KSII Trans. Int. Inform. Syst. 2013;7:119–131. [Google Scholar]
- 27.Li C.T. A new password authentication and user anonymity scheme based on elliptic curve cryptography and smart card. IET Inform. Secur. 2013;7:3–10. [Google Scholar]