Abstract
Wireless sensor networks (WSNs) consist of sensors, gateways and users. Sensors are widely distributed to monitor various conditions, such as temperature, sound, speed and pressure but they have limited computational ability and energy. To reduce the resource use of sensors and enhance the security of WSNs, various user authentication protocols have been proposed. In 2011, Yeh et al. first proposed a user authentication protocol based on elliptic curve cryptography (ECC) for WSNs. However, it turned out that Yeh et al.'s protocol does not provide mutual authentication, perfect forward secrecy, and key agreement between the user and sensor. Later in 2013, Shi et al. proposed a new user authentication protocol that improves both security and efficiency of Yeh et al.'s protocol. However, Shi et al.'s improvement introduces other security weaknesses. In this paper, we show that Shi et al.'s improved protocol is vulnerable to session key attack, stolen smart card attack, and sensor energy exhausting attack. In addition, we propose a new, security-enhanced user authentication protocol using ECC for WSNs.
Keywords: authentication protocol, elliptic curves cryptography, wireless sensor network
1. Introduction
Wireless sensor networks (WSNs) provide a feasible real-time monitoring system. Wireless sensors can be easily deployed in various environments such as military surveillance, forest fire detection, health care and wildlife monitoring. WSNs basically consist of users, sensors and gateways whose communication security is a significant concern in real-world applications [1]. Users and gateways have sufficient resources to be used in the system, but sensors are different. Sensors have limited computational ability, low battery, low bandwidth, and a small amount of memory. Therefore, in WSNs, it is important to reduce the use of sensors to extend their lifespans [2–4].
Various user authentication protocols have been proposed for securing WSNs while minimizing the use of sensors. In 2004, Watro et al. proposed a user authentication protocol employing the RSA and Diffie-Hellman algorithms [5]. In 2006, Wong et al. proposed an efficient dynamic user authentication protocol using a hash function [6]. However, Tseng et al. demonstrated that Wong et al.'s authentication protocol is vulnerable to stolen-verifier attack, replay attack and forgery attack [7,8]. Later in 2009, Das proposed a two-factor user authentication protocol using smart cards. Das showed how to design an authentication protocol where only the user who is in possession of both the smart card and the password can pass the verification of the gateway [8]. However, several security-related flaws in Das's protocol have been disclosed by later studies as summarized below:
He et al. demonstrated that Das's protocol is vulnerable to insider attacks and impersonation attacks, and that it does not allow users to change their passwords freely. He et al. proposed an improved two-factor protocol [9] which can resist insider and impersonation attacks.
Khan and Alghathbar showed that Das's protocol fails to provide mutual authentication between the gateway and the sensor, and due to this failure, it is not secure against a gateway bypassing attack and a privileged-insider attack [10].
Chen et al. also pointed out that Das's protocol does not achieve mutual authentication between the gateway and the sensor, and proposed a robust authentication protocol that provides the property of mutual authentication [11].
In 2011, Yeh et al. [2] revealed that Chen et al.'s protocol has difficulty in updating users' passwords and is vulnerable to an insider attack. As an improvement of Chen et al.'s protocol, Yeh et al. presented the first user authentication protocol that uses elliptic curve cryptography (ECC) in WSN environments. However, Han [12] showed that Yeh et al.'s protocol has still some security weaknesses: it does not provide perfect forward secrecy and fails to achieve mutual authentication and key agreement between the user and the sensor. To address these problems with Yeh et al.'s protocol, Shi et al. [3] have recently proposed a new smart-card-based user authentication protocol using ECC for WSNs. Shi et al.'s protocol performs more efficiently, both in terms of computation and communication costs, and provides better security than Yeh et al.'s protocol. However, we found that Shi et al.'s improvement is not secure enough yet and their protocol is susceptible to session key attacks, stolen smart card attacks, and sensor energy exhausting attacks. In addition to reporting the security weaknesses, we also show how to enhance the security of Shi et al.'s protocol with no significant increase in communication and computation costs. We analyze and verify the security of the proposed protocol using non-monotonic cryptographic logic (Rubin logic).
Throughout the paper, we make the following assumptions on the capabilities of the probabilistic polynomial-time adversary
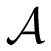 in order to properly capture security requirements of two-factor authentication protocols using smart cards in wireless sensor networks.
in order to properly capture security requirements of two-factor authentication protocols using smart cards in wireless sensor networks.
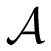 has the complete control of all message exchanges between the protocol participants: a user, a sensor and the gateway. That is,
has the complete control of all message exchanges between the protocol participants: a user, a sensor and the gateway. That is,
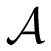 can eavesdrop, insert, modify, intercept, and delete messages exchanged among the three parties at will.
can eavesdrop, insert, modify, intercept, and delete messages exchanged among the three parties at will.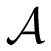 is able to (1) extract the sensitive information on the smart card of a user through a power analysis attack [13,14] or (2) find out the user's password possibly via shoulder-surfing or by employing a malicious card reader. However, it is assumed that
is able to (1) extract the sensitive information on the smart card of a user through a power analysis attack [13,14] or (2) find out the user's password possibly via shoulder-surfing or by employing a malicious card reader. However, it is assumed that
 is unable to compromise both the two factors: the information on the smart card and the password of the user; it is clear that there is no way to prevent
is unable to compromise both the two factors: the information on the smart card and the password of the user; it is clear that there is no way to prevent
 from impersonating the user if both factors are compromised.
from impersonating the user if both factors are compromised.
2. Overview of Elliptic Curves Cryptography
In 1985, Neal Koblitz and Victor S. Miller proposed the use of elliptic curves in cryptography. After various studies on ECC, it has been widely used since the early 21st century. ECC is a type of public-key cryptography and based on the algebraic structure of elliptic curves over finite fields. Elliptic curves are also used in several integer factorization algorithms. ECC provides the important benefit of a smaller key size, despite which it is able to maintain the same degree of security as other types of public-key cryptography, such as RSA, DH and DSA. Therefore, ECC is especially useful for wireless devices, which typically have limited CPU capacity, power and network connectivity. Table 1 shows the NIST guidelines on choosing key sizes in ECC and other public key cryptography [15].
Table 1.
ECC key sizes compared with other PKC schemes.
| Security (bits) | ECC | RSA/DH/DSA | MIPS-Years to Attack | Protection Lifetime |
|---|---|---|---|---|
| 80 | 160 | 1,024 | 1012 | until 2010 |
| 112 | 224 | 2,048 | 1024 | until 2030 |
| 128 | 256 | 3,072 | 1028 | beyond 2031 |
| 192 | 384 | 7,680 | 1047 | beyond 2031 |
| 256 | 512 | 15,360 | 1066 | beyond 2031 |
ECC has three related mathematical problems: the Elliptic Curve Discrete Logarithm Problem (ECDLP), Elliptic Curve Computational Diffie-Hellman Problem (ECCDHP), and Elliptic Curve Decisional Diffie-Hellman Problem (ECDDHP). No polynomial time algorithm can solve the ECDLP, ECCDHP and ECDDHP with non-negligible probability.
Let p > 3 be a large prime and choose two field elements a, b ∈ Fp satisfying 4a3 + 27b2 ≠ 0 mod p to define the equation of a non-supersingular elliptic curve E: y2 = x3 + ax + b mod p over Fp. Choose a generator point P = (xP, yP) whose order is a large prime number q over E(Fp). In the same way, a subgroup G of the elliptic curve group E(Fp) with order q is constructed. Then, the three mathematical problems in ECC are defined at various study [16–18] as follows.
ECDLP: Given a point element Q in G, find an integer x ∈ such that Q = xP, where xP indicates that the point P is added to itself x times by the elliptic curves operation.
ECCDHP: For a, b ∈ , given two point elements aP, bP in G, compute abP in G.
ECDDHP: For a, b, c ∈ , given three point elements aP, bP and cP in G, decide whether cP = abP.
3. Review of Shi et al.'s Protocol
In Shi et al.'s protocol [3], the gateway is a trusted node that holds two sufficiently large master keys, x and y. Before starting the system, the gateway and the sensors share a long-term secret key SKGS = h(IDSn‖y). Shi et al.'s protocol consists of four phases; user registration phase, login phase, authentication phase, and password update phase. For convenience, the notations used throughout this paper are summarized in Table 2.
Table 2.
Notations.
| Symbol | Description |
|---|---|
| p, q | Two large prime numbers |
| FP | A finite field |
| E | An elliptic curve defined on finite field FP with large order |
| G | The group of elliptic curve points on E |
| IDU | The identity of user U |
| IDSn | The identity of sensor Sn |
| pwU | The user U's password |
| GW | The gateway of WSN |
| x, y | The master keys of GW |
| h(·) | A secure one-way hash function |
| ‖ | A string concatenation operation |
| ⊕ | A bitwise XOR operation |
3.1. Registration Phase
In this phase, the user U securely submits its identity IDU and password pwU to the gateway GW. Then, GW issues U a smart card containing the user authentication information, as shown in Figure 1.
Figure 1.

The registration phase of Shi et al.'s protocol.
3.2. Login and Authentication Phases
In the login and authentication phases, when U enters IDU and pwU into a smart card terminal, the smart card must validate the legitimacy of U. Then, U, Sn and GW authenticate with each other. This protocol uses 4 messages (M1, M2, M3, M4) for mutual authentication, as described in Figure 2. Lastly, U and Sn share the session key sk. After the authentication phase, U and Sn communicate with each other using the session key sk.
Figure 2.
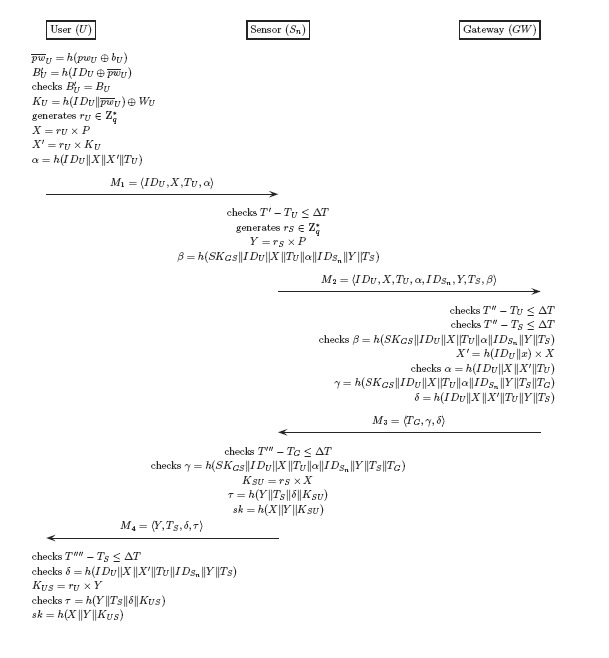
The login and authentication phases of Shi et al.'s protocol.
3.3. Password Update Phase
In the password update phase, U enters the identity IDU, the old password pwU, and the new password . Then, the smart card updates the password after first checking the correctness of the old password, as shown in Figure 3.
Figure 3.

The password update phase of Shi et al.'s protocol.
4. Security Weaknesses in Shi et al.'s Protocol
This section shows that Shi et al.'s protocol is vulnerable to a session key attack, a stolen smart card attack, and a sensor energy exhausting attack.
4.1. Session Key Attack
In Shi et al.'s protocol, the user U and the sensor Sn have to perform the login and authentication phases when they want to share a session key which will be used for protecting their subsequent communication. A problem occurs if U shares its session key with an attacker, not with the intended sensor Sn. In the protocol, the gateway GW and the user U check each other's legitimacy using the authenticators α and δ, respectively. However, α and δ do not include information about the sensor Sn with which U intends to establish a session key. The attacker exploits this design flaw in mounting a session key attack. The attack is depicted in Figure 4 and its description follows.
Figure 4.
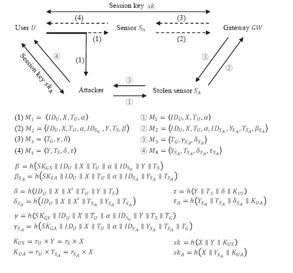
A session key attack on Shi et al.'s protocol.
When U inputs IDU and pwU, and sends M1 to sensor Sn, the attacker intercepts M1 and sends it to sensor Sa which was previously stolen by the attacker. Upon receiving M1, the stolen sensor Sa will generate the message A2 and send it to the gateway GW. However, the attacker replaces IDSn contained in A2 with IDa to make GW believe that IDU wants to communicate with sensor Sa, not with Sn. After receiving A2, the gateway GW generates A3 without noticing any discrepancy and sends it to sensor Sa. Lastly, the attacker sends the user U the message A4 generated by Sa using the message A3 from GW. Because there is no information about the sensor Sn in A4 and M4, the user U undoubtedly shares the session key with the attacker while thinking that it has shared the key with the sensor Sn.
4.2. Stolen Smart Card Attack
Kocher et al. and Messerges et al. pointed out that the confidential information stored in smart cards could be extracted by physically monitoring its power consumption [13,14]. Therefore, it is fair to say that if a user loses his or her smart card, all information in the smart card may be revealed to the attacker.
In Shi et al.'s protocol, the smart card stores various information for user login and authentication. The smart card for the user IDU includes bU, BU, WU and h(·). Using these information and IDU, an attacker can guess U's password pwU. If IDU is used in public communication, the attacker can obtain or steal it without difficulty. Figure 5 describes a stolen smart card attack against Shi et al.'s protocol.
Figure 5.
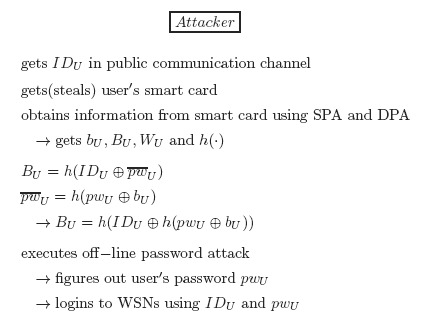
A stolen smart card attack on Shi et al.'s protocol.
The attacker can obtain information from the smart card using attacks such as simple power analysis (SPA) and differential power analysis (DPA). This information includes bU, BU, WU and h(·). Recall that BU = h(IDU ⊕ h(pwU ⊕ bU)). Using BU as a password verifier, the attacker can easily find out the password pwU by mounting an offline password guessing attack (also known as an offline dictionary attack) [19–22] if the password pwU is not long enough. After successfully mounting the password guessing attack, the attacker can login and authenticate with the sensor Sn and the gateway GW using the identity IDU and the password pwU.
4.3. Sensor Energy Exhausting Attack
The computational cost of a sensor is a critical consideration in the design of WSNs as it increases the consumption of the battery power of the sensor. Often it is economically advantageous to discard a sensor rather than recharge it. For this reason, the battery power of a sensor is usually important in wireless devices, with its lifetime determining the sensor lifetime. Previous work have suggested several types of energy exhausting attacks. Buttyan et al. [23] investigated the reliability of transport protocols for WSNs. Brownfield et al. [24] researched the battery depletion effect through the reduction of sleep cycles. Khouzani et al. [25,26] investigated malware attacks in battery-constrained wireless networks. As shown by the previous researches, WSNs need to eliminate unnecessary computational costs of sensors so that the effects of an energy exhausting attack on sensors can be minimized.
In Shi et al.'s protocol, the sensor performs various cryptographic operations such as one-way hash function evaluations, scalar-point multiplications, random number generations, and map-to-point hash function evaluations. Scalar-point multiplications are much more expensive than hash function evaluations. The computational costs of generating a random number and evaluating a map-to-point hash function are about half the cost of performing a scalar-point multiplication. A sensor consumes a large amount of energy to perform a scalar-point multiplication and very little to perform a hash function evaluation [27–29].
Figure 6 shows the possibility of a sensor energy exhaustion attack. The attacker can keep sending malicious messages, A1, A2, A3, generated to consume the battery power of the sensor. The attacker can do so because the sensor only checks the freshness of the timestamp in M1. For each of these fake messages, the sensor checks the freshness of the timestamp and proceeds to perform the subsequent cryptographic operations, thereby consuming large amounts of energy. Accordingly, it is necessary to modify the protocol so that the sensor can check if the message M1 is from a legitimate user, not from an imposter.
Figure 6.
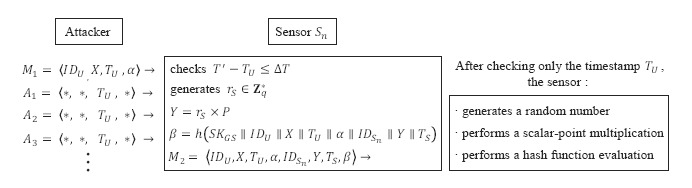
A sensor energy exhausting attack on Shi et al.'s protocol.
5. The Proposed Protocol
Like Shi et al.'s protocol, our proposed protocol is divided into three phases: the user registration phase, login and authentication phase, and password update phase. Before the protocol is ever executed, the gateway generates two master keys, x and y, and shares a long-term secret key SKGS = h(IDSn ‖ y) with the sensor Sn. In describing the protocol, we use the same notations as in Table 2 unless stated otherwise.
5.1. Registration Phase
For a user U, this phase is performed only once when U registers itself with the gateway GW. Figure 7 illustrates how the phase works, and its description follows:
-
(1)
The user U chooses its identity IDU and password pwU freely, generates a random number bU, and computes . U sends IDU and to GW via a secure channel.
-
(2)The gateway GW computes:
Then, GW issues U a smart card loaded with {AU, BU, WU, h(·)}. -
(3)
Lastly, U inputs the random number bU into the smart card.
Figure 7.
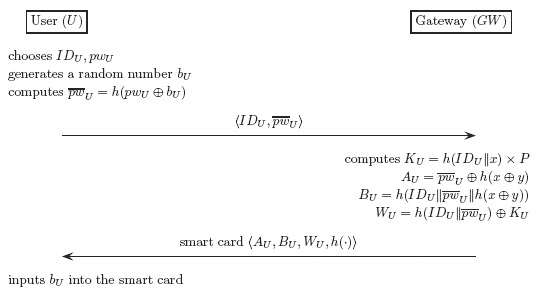
The registration phase.
5.2. Login and Authentication Phase
This phase is carried out whenever U wants to gain access to the WSN. During the phase, U establishes a session key with the sensor Sn while being authenticated by the gateway GW. The phase proceeds as follows (see also Figure 8):
-
Step 1.U inserts its smart card into the card reader and inputs its identity IDU and password pwU. Then, the smart card computes:
and checks if BU is equal to . If not equal, the smart card aborts the protocol. Otherwise, it retrieves the current timestamp TU, chooses a random number rU ∈ , and computes:
After the computations, the smart card sends the message M1 = 〈IDU, IDSn, X, TU, α, ω〉 to the sensor Sn. -
Step 2.Upon receiving M1 from U, the sensor Sn retrieves the current timestamp T′ and verifies the freshness of U's timestamp TU by checking that:
where ΔT is the maximum allowed time difference between TU and T′. If TU is not fresh, Sn rejects U's request and aborts the protocol. Otherwise, Sn checks if ω is equal to the hash value h(IDU‖h(IDsn‖h(x ⊕ y)) ‖ TU). If they are not equal, Sn aborts the protocol. Otherwise, Sn generates a random number rS ∈ retrieves the current timestamp TS, and computes:
Then, Sn sends the message M2 = 〈IDU, X, TU, α, ω, IDSn, Y, TS, β〉 to the gateway GW. -
Step 3.After receiving M2, GW retrieves the current timestamp T″ and verifies the freshness of the timestamp TS by checking that T″ − TS ≤ ΔT. If TS is not fresh, GW aborts the protocol. Otherwise, GW computes X′ = h(IDU‖x) × X and checks if α equals h(IDU‖IDSn‖X‖X′‖TU‖ω) and β equals h(SKGS‖IDU‖X‖TU‖α‖ω‖IDSn‖Y‖TS). If either of the checks fails, GW aborts the protocol. Otherwise, GW retrieves the current timestamp TG and computes:
Then, GW sends M3 = 〈TG, γ, δ〉 to the sensor Sn. -
Step 4.Having received M3, Sn retrieves the current timestamp T‴ and checks if T‴ − TG ≤ ΔT and γ = h(SKGS‖IDU‖X‖TU‖α‖IDSn‖Y‖TS‖TG) Only if both the checks hold, Sn retrieves the new timestamp and computes:
Then, Sn sends M4 = 〈Y, TS, , δ, τ〉 to the user U. -
Step 5.With M4 in hand, U retrieves the current timestamp T⁗, computes KUS = rU × Y, and checks if (1) T⁗− T′S ≤ ΔT; (2) δ = h(IDU‖X‖X′ ‖TU‖IDSn‖Y‖TS); and (3) . If any of the checks fail, U aborts the protocol. Otherwise, U computes:
Figure 8.

The login and authentication phase.
5.3. Password Update Phase
Our protocol allows users to freely update their passwords. The password update phase works as follows (see also Figure 9):
The user U inserts its smart card into a smart card reader and enters the identity IDU, the old password pwU, and the new password pw′U.
- The smart card computes , , and and checks if B′ is equal to B. If they are not the same, the password update phase stops. Otherwise, the smart card computes:
and replaces AU, BU and WU with A′U, B′U and W′U, respectively.
Figure 9.
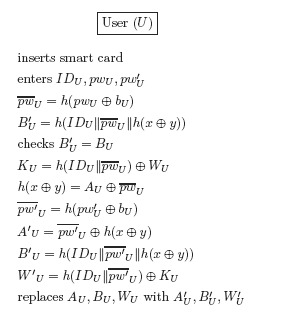
The password update phase.
6. Performance Comparison
Table 3 compares our improved protocol with Yeh et al.'s protocol [2] and Shi et al.'s protocol [3] in terms of the computational costs required by the protocols. The efficiency comparison is based on theoretical analysis and experimental results [3,27–29].
Table 3.
Efficiency comparison.
| Protocol | Computational Cost | ||
|---|---|---|---|
|
| |||
| User | Sensor | Gateway | |
| Yeh et al.'s protocol | 2M +1R+1A+4H | 2M +1R +1A+ 1P +1H | 3M +1R+1P + 1H |
| Shi et al.'s protocol | 3M +5H | 2M +3H | 1M +4H |
| Our protocol | 3M +7H | 2M +4H | 1M +4H |
Notations used in Table 3 are described as follows:
| M | scalar-point multiplication |
| R | random point generation |
| A | point addition |
| P | map-to-point hash function evaluation |
| H | hash function evaluation |
The computational costs of generating a random point and evaluating a map-to-point hash function are about half the cost of performing a scalar-point multiplication. Hash function evaluations and point addition operations are often ignored in cost estimates since they are much faster than scalar-point multiplications. If we ignore hash function evaluations, the computational costs described in Table 3 can be estimated as in Table 4.
Table 4.
Estimated efficiency comparison.
| Protocol | Computational Cost | ||
|---|---|---|---|
|
| |||
| User | Sensor | Gateway | |
| Yeh et al.'s protocol | 2.5M | 3M | 3M |
| Shi et al.'s protocol | 3M | 2M | 1M |
| Our protocol | 3M | 2M | 1M |
As shown in Tables 3 and 4, our proposed protocol and Shi et al.'s protocol are more efficient than Yeh et al.'s protocol, in terms of the computational costs of the sensor and the gateway. In WSNs, it is important to minimize the energy consumption of the sensor node. In this sense, it is fair to say that our protocol and Shi et al.'s protocol are better suited for WSNs than Yeh et al.'s protocol. The performance of our proposed protocol is similar to that of Shi et al.'s protocol. But, as we demonstrated in Section 4, Shi et al.'s protocol is vulnerable to a session key attack, a stolen smart card attack, and a sensor energy exhausting attack. Consequently, we can say that our protocol enhances the security of Shi et al.'s protocol while maintaining the efficiency of the protocol.
7. Security Analysis and Verification
In this section, we first provide a heuristic security analysis for the proposed protocol and then formally verify the security analysis by using Rubin logic.
7.1. Heuristic Security Analysis
7.1.1. Stolen-Verifier Attack
In WSNs, an attacker may attempt to mount a stolen-verifier attack if the gateway stores a password verifier [30] and then, impersonate a legal user using the verifier stolen from the gateway. However, in our protocol, the gateway does not store a password verifier of any kind but stores only the master secret keys x and y which are used in computing:
7.1.2. Insider Attack
An insider attack occurs when the gateway manager or system administrator can access a user's secret (e.g., user password) and then impersonate the user. However, in our protocol, the user U does not send a plain password to the gateway, but sends only the password-derived hash value . Since bU is a sufficiently high-entropy random number, the gateway cannot learn the password pwU from the hash value . In addition, the gateway does not manage any table for storing user passwords or their verifiers (e.g., an ID/password table) Therefore, an insider attack is not possible against our protocol.
7.1.3. Replay Attack
In our protocol, each of the protocol messages (M1, M2, M3 and M4) accompanies at least one of the authenticators (α, β, γ, δ, τ and ω) which are generated using a timestamp (TU, TS, T′S or TG) as part of the hash input. The protocol participants (U, Sn and GW) verify the authenticity of incoming messages by checking the freshness of the timestamps and the legitimacy of the authenticators. But, an attacker cannot compute any of the authenticators for a fresh timestamp without knowing an appropriate secret. Therefore, our proposed protocol is secure against replay attacks.
7.1.4. Man-in-the-Middle Attack
It is impossible for an attacker to mount a man-in-the-middle attack against our proposed protocol. In a typical man-in-the-middle attack, an attacker intercepts the messages being exchanged between the communicating parties and instead, sends arbitrary messages for its own benefit impersonating one of them to the other. But, our protocol allow the parties to authenticate all the protocol messages with the authenticators α, β, γ, δ, τ and ω, and therefore, is secure against man-in-the-middle attacks.
7.1.5. Gateway Impersonation Attack
An attacker cannot impersonate the gateway because it cannot forge the message:
To generate γ or δ, one needs to know either SKGS or h(IDU‖x). However, h(IDU‖x) is the secret shared only between the user and the gateway while SKGS is the secret shared between the sensor and the gateway. Therefore, it is impossible for an attacker to mount a gateway impersonation attack.
7.1.6. User Impersonation Attack
It is impossible for an attacker to impersonate the user as it cannot forge the message:
The attacker should know X′ to compute α and should know h(x ⊕ y) to compute ω. But, the attacker knows neither X′ nor h(x ⊕ y) and therefore, cannot mount a user impersonation attack.
7.1.7. Sensor Impersonation Attack
An attacker cannot impersonate the sensor because it can forge the messages M2 = 〈IDU, X, TU, α, ω, IDSn, Y, TS, β〉 and M4 = 〈Y, TS,T′S, δ, τ〉. The attacker cannot compute β without knowing SKGS and cannot compute δ without knowing the secret h(IDU‖x). But, the attacker knows neither SKGS nor x and therefore, cannot mount a sensor impersonation attack.
7.1.8. Mutual Authentication
Mutual authentication is an important security property that an authentication protocol should achieve [31,32]. Our proposed protocol provides mutual authentication among the three parties: the user, the sensor and the gateway.
The gateway authenticates the user using α in M2.
The gateway authenticates the sensor using β in M2.
The sensor authenticates the gateway using γ in M3.
The user authenticates the gateway using δ in M4.
The user and the sensor authenticate each other via δ from the gateway.
This means that our protocol achieves mutual authentication.
7.1.9. Perfect Forward Secrecy
Perfect forward secrecy means that a session key derived from a set of long-term keys will not be compromised even if one of the long-term keys is compromised in the future. The proposed protocol uses the session key sk = h(X‖Y‖rS × X) for the sensor and sk = h(X‖Y‖rU × Y) for the user. Even though h(IDU‖x) and x are compromised, an attacker cannot know rU or rS. Under the assumption that the ECCDHP problem is hard, the attacker cannot compute rS from rS × X and rU from rU × Y. Therefore, our protocol provides perfect forward secrecy.
7.1.10. Key Agreement
The proposed protocol provides key agreement between the user and the sensor. To the session-key computation, the user contributes its random number rU while the sensor contributes its random number rS. It is straightforward to verify that KSU and KUS are equal:
Since KSU = KUS, it is clear that the user and the sensor compute session keys of the same value:
7.1.11. Session Key Attack
In our protocol:
α is combined with two identities IDU and IDSn, which indicates that the user U wants to communicate with the sensor Sn,
δ is also combined with IDU and IDSn, which indicates that the gateway has authenticated both the user IDU and the sensor IDSn.
But, no attacker can compute α and δ, and therefore, can share a session key with the user.
7.1.12. Stolen Smart Card Attack
In Shi et al.'s protocol, the attacker can obtain bU and BU from the smart card and thus can use BU = h(IDU ⊕ h(pwU ⊕ bU)) as the password verifier in its offline dictionary attack. However, in our protocol, BU is computed as . Even if the attacker obtains bU and BU from the smart card, it cannot use BU as a password verifier since it does not know the hash value h(x ⊕ y). Therefore, no attacker can mount an offline dictionary attack against our protocol.
7.1.13. Sensor Energy Exhausting Attack
In Shi et al.'s protocol, the sensor has to generate a random number and execute a scalar-point multiplication whenever it receives the message M1 from the user. Random number generations and scalar-point multiplications are expensive and exhaust a large amount of the sensor's energy. This makes Shi et al.'s protocol vulnerable to a sensor energy exhausting attack. However, in our protocol, the sensor first checks the validity of ω = h(IDU‖h(IDSn‖h(x ⊕ y))‖TU) before generating a random number and performing a scalar-point multiplication. Checking the validity of ω only requires one hash function evaluation. Therefore, our proposed protocol is secure against a sensor energy exhausting attack.
Table 5 summarizes and compares the security of our protocol, Yeh et al.'s protocol, and Shi et al.'s protocol.
Table 5.
Security comparison.
| Attack and Security Property | Yeh et al.'s Protocol | Shi et al.'s Protocol | Our Protocol |
|---|---|---|---|
| Stolen-verifier attack | Secure | Secure | Secure |
| Insider attack | Secure | Secure | Secure |
| Replay attack | Secure | Secure | Secure |
| Man-in-the-middle attack | Secure | Secure | Secure |
| Gateway impersonation attack | Secure | Secure | Secure |
| User impersonation attack | Secure | Secure | Secure |
| Sensor impersonation attack | Insecure | Secure | Secure |
| Mutual authentication | No | Yes | Yes |
| Perfect forward secrecy | No | Yes | Yes |
| Key agreement between user and sensor | No | Yes | Yes |
| Session key attack | Insecure | Insecure | Secure |
| Stolen smart card attack | Insecure | Insecure | Secure |
| Sensor energy exhausting attack | Insecure | Insecure | Secure |
7.2. Rubin Logic Verification
We analyze the proposed protocol using Rubin logic which can be applicable in analyzing an authentication protocol. Rubin logic integrates protocol analysis with specification and uses the notions of global sets, local sets, and actions. As the protocol run is progressed, the possession and belief sets (specified by local sets) are modified for each principal by inference rules (specified by global sets) and actions [33,34]. As the possession and belief sets are modified, secret set and observers sets (specified by global sets) are modified as well.
Global Sets
The first step of the specification of any protocol using Rubin logic is to instantiate the global sets with values. Global sets are public to each principal in a protocol specification.
Principal Set: This set contains the principals who participate in a protocol.
Rule Set: This set contains inference rules for deriving new statements from existing assertions.
Secret Set: This set contains all of the secrets that exist at any given time in the system.
Observers Sets: For each secret, its set contains all the principals who could possibly know the secret by listening to network traffic or generating it themselves.
Local Sets
Local sets are private to each principal in a protocol specification [35]. For each principal, Pi, Rubin logic defines the following sets:
Possession Set(Pi): This set contains all the data relevant to security that this principal knows or possesses. We denote this set by POSS(Pi) = (poss1, poss2, ⋯, possn).
Belief Set(Pi): This set contains all the beliefs hold by a principal. For example, the keys it holds between itself and other principals, beliefs about jurisdiction, beliefs about freshness, and beliefs about the possessions of other principals. We denote this set by BEL(Pi) = (bel1, bel2, ⋯, beln).
Behavior List(Pi): This item is a list rather than a set because the elements are ordered. BL(Pi) = Behavior List of Pi.
Actions
Rubin logic defines actions for dealing with the knowledge in a protocol [36]. The action lists that precede and follow message operations in a principal's behavior list determine a sequence of events performed by the principal during a protocol run. We use the following actions:
Generate-nonce(N)
Send(Pi, X)
Receive(Pi, X)
Update(X)
Forget(X)
Concat(X1, X2, ⋯,Xn)
XOR(X1, X2, ⋯,Xn)
Check(X1, X2, ⋯, Xn)
Scalar-multiplication(X1, X2, ⋯, Xn)
Hash(h(·); X1, X2, ⋯, Xn)
Check-freshness(T)
Here, Concat(X1, X2, ⋯, Xn) is the action that concatenates the submessages X1, X2, ⋯, Xn.
7.2.1. Protocol Specification
Notations used for the protocol specification is the same as those in Table 2. Phases 1, 2 and 3 represent the registration phase, the login and authentication phase, and the password updated phase. The global and local sets for the protocol are specified as follows:
Global Sets
The global sets are specified as follows:
Principal set: A principal is one of U, Sn and GW. U is the protocol initiator.
- Rule set:
-
–X contains Y: Y appears as a submessage of X.
-
–S ≔← f(S): S is replaced by the value f(S).
-
–X from E: X is received from E.
-
–LINK(N): LINK is used to link responses to challenges. When a principal generates a nonce, N, the formula LINK(N) is added to the belief set of the principal.
-
–
Secret Set: {pwU, bU, x, y, h(x ⊕ y), SKGS}
- Observers Sets:
-
–Observers(pwU): {U}
-
–Observers(bU): {U}
-
–Observers(x): {GW}
-
–Observers (y): {GW}
-
–Observers(h(x ⊕ y)): {Sn,GW}
-
–Observers(SKGS): {Sn,GW}
-
–
Local Sets
The local sets are defined for each U, Sn and GW. Tables 67 and 8 show the specification of the local sets for U, Sn and GW, respectively.
Table 6.
Local sets specification for principal U.
| Principal U | |
|---|---|
| POSS(U) = {pwU, bU, {IDU}} | (U16) Update(IDU, IDSn, X, TU, α, ω) |
| BEL(U) = {#(pwU), #(bU)} | (U17) Receive(Sn, {Y, TS, δ, τ}) |
| BL(U) | (U18) Check-freshness(T′S) |
| Phase 1 | (U19) Check (δ, Hash(h(·); Contat(IDU, X, X′,TU, IDSn, Y, TS))) |
| (U1) | |
| (U2) Send (GW,{IDU, }) | (U20) KUS ← Scalar-multiplication(rU, Y) |
| (U3) Update(IDU, ) | (U21) Check(τ, Hash(h(·); Contat(Y, T′S, δ, KUS))) |
| (U4) Receive(GW, {AU, BU, WU, h(·)}) | (U22) sk ← Hash(h(·); Contat(X, Y, KUS)) |
| Phase 2 | Phase 3 |
| (U5) | (U23) |
| (U6) h(x⊕y) ← XOR( , AU) | (U24) B′U ← Hash(h(·); Concat (IDU, , h(x(⊕ y)) |
| (U7) B′U ← Hash(h(·);Concat (IDU, , h(x⊕y))) | (U25) Check(B′U, BU) |
| (U8) Check(B′U, BU) | (U26) KU ← XOR(Hash(h(·); Concat(IDU, )), WU) |
| (U9) KU ← XOR(Hash(h(·); Concat(IDU, )),WU) | (U27) h(x(⊕ y) ← XOR( , AU) |
| (U10) Generate-nonce(rU) | (U28) |
| (U11) X ← Scalar-multiplication(rU, P) | (U29) A′U ← XOR ( , h(x ⊕ y)) |
| (U12) X′ ← Scalar-multiplication(rU, KU) | (U30) B′U ← Hash(h(·); Concat(IDU, , h(x(⊕ y))) |
| (U13) ω ← Hash(h(·); Concat(IDU, Hash(h(·);IDSn, h(x ⊕ y)), TU)) | (U31) W′U ← XOR(Hash(h(·); Concat(IDU, )), KU) |
| (U32) AU ← A′U | |
| (U14) α ← Hash(h(·); Concat(IDU, IDSn, X, X′, TU,ω)) | (U33) BU ← B′U |
| (U15) Send(Sn, {IDU, IDSn, X, TU, α, ω}) | (U34) WU ← W′U |
Table 7.
Local sets specification for principal Sn.
| Principal Sn | |
|---|---|
| POSS(Sn) = {SKGS, h(x ⊕ y), {IDSn}} | (SN7) |
| BEL(Sn) = {#(SKGS), #(h(x ⊕ y))} | Send(GW, {IDU, X, TU, α, ω, IDSn, Y, TS, β}) |
| BL(Sn) | (SN8) Update(IDU, X, TU, α, ω, IDSn, Y, TS, β) |
| Phase 2 | (SN9) Receive(GW, {TG, γ, δ}) |
| (SN1) Receive(U, {IDU, IDSn, X, TU, α, ω}) | (SN10) Check-freshness(TG) |
| (SN2) Check-freshness(TU) | (SN11) Check |
| (SN3) Check | (γ,Hash(h(·); Concat(SKGS,IDU,X,TU,α,IDSn,Y,TS,TG))) |
| (ω, Hash(h(·);Concat(IDU,Hash(h(·);IDSn,h(x ⊕ y)),TU))) | (SN12) KSU ← Scalar-multiplication(rS, X) |
| (SN4) Generate-nonce(rS) | (SN13) τ ← Hash(h(·); Concat(Y, T′S, δ, KSU)) |
| (SN5) Y ← Scalar-multiplication(rS, P) | (SN14) sk ← Hash(h(·); Contat(X, Y, KSU)) |
| (SN6) β ← Hash | (SN15) Send(U, {Y, TS, T′S, δ, τ}) |
| (h(·); Concat (SKGS, IDU, X, TU, α, ω, IDSn, Y, TS)) | (SN16) Update(Y, TS,T′S,δ, τ) |
Table 8.
Local sets specification for principal GW.
| Principal GW | |
|---|---|
| POSS(GW) = {x, y, h(x ⊕ y), SKGS} | Phase 2 |
| BEL(GW) = {#(x), #(y), #(h(x ⊕ y)), #(SKGS)} | (GW9) Receive(Sn, {IDU, X, TU, α, ω, IDSn, Y, TS, β}) |
| BL(GW) | (GW10) Check-freshness(TS) |
| Phase 1 | (GW11) Check (β, Hash(h(·); Concat(SKGS, IDU, X, TU, α, ω, IDSn, Y, TS))) |
| (GW1) Received(U, {IDU, ) | |
| (GW2) KU ← Scalar-multiplication(Hash(h(·); Concat(IDU, x)), P) | (GW12) X′ ← Scalar-multiplication(Hash(h(·); Concat(IDU, x)), X) |
| (GW3) AU ← XOR ( , h(x ⊕ y)) | (GW13) |
| (GW4) BU ← Hash(h(·); Concat(IDU, , h(x ⊕ y))) | Check(α, Hash(h(·); Concat(IDU, IDSn, X, X′, TU, ω))) |
| (GW5) | (GW14) γ ← |
| WU ← XOR(Hash(h(·); Concat(IDU, )), KU) | Hash(h(·); Concat(SKGS, IDU,X,TU,α,IDSn,Y,Ts,TG)) |
| (GW6) Send(U, {AU, BU, WU, h(·)}) | (GW15) δ ← Hash(h(·);Contat(IDU, X, X′, TU, IDSn, Y, TS)) |
| (GW7) Update(AU, BU, WU, h(·)) | (GW16) Send(Sn, {TG, γ, δ}) |
| (GW8) Forget(IDU, , AU, BU, KU, WU) | (GW17) Update(TG, γ, δ) |
7.2.2. Analysis and Verification
In phase 1, U initiates the protocol, and then the actions in BL(U) are performed. Firstly, (U1)–(U3) actions in BL(U) are performed, which represent that U sends IDU and to GW for registration. Next, (GW1)–(GW8) actions in BL(GW) are performed to generate AU, BU, KU and WU, and to send them to U. By (GW8), GW deletes IDU, , AU, BU, KU and WU from POSS(GW) and BEL(GW). Lastly, the (U4) action in BL(U) is executed, then phase 1 is finished. Due to the (GW8) forget action, the local sets of GW are not changed. However, the local sets of principal U are changed as described below.
POSS(U) = {pwU, bU, , {IDU}, {AU, BU, WU, h(·)} from GW}
BEL(U) = {#(pwU), #(bU), #( )}
Accordingly, the global sets are modified as follows:
Secret set: {pwU, bU, , x, y, SKGS, h(x ⊕ y)}
- Observers sets:
-
–Observers ( ): {U}
-
–
In the (U5)–(U8) actions in BL(U) of phase 2, the smart card authenticates U, who inputs IDU and pwU, by checking whether BU and are same or not. Next, the (U9)–(U15) actions are executed to generate the protocol values X, X′, h(x ⊕ y), ω, α and rU. After the (U16) update action, the local sets of U are changed as follows:
POSS(U) = {IDSn, pwU, bU, , X, X′, h(x ⊕ y), TU, α, ω, rU, {IDU}}
BEL(U) = {#(pwU), #(bU), #(rU), #( ), #(X′), #(h(x ⊕ y)), #(TU), LINK(rU)}
Then, the global sets are modified as follows:
Secret set: {pwU, bU, , x, y, X′, SKGS, h(x ⊕ y)}
- Observers sets:
-
–Observers(X′): {U}
-
–Observers(h(x ⊕ y)): {U}
-
–
After the (U5)–(U16) actions are finished, Sn starts the actions in BL(Sn) with the incoming message M1 from U. The (SN1)–(SN3) actions in BL(Sn) are performed to verify the correctness of message M1. If the check succeeds, the (SN4)–(SN8) actions are performed to make the values Y, β and rS, and to send the message M2. The local sets of Sn are changed as follows.
POSS(Sn) = {Y, TS, rS, β, SKGS, h(x ⊕ y), {IDSn}, {IDU, X, TU, α, ω} from U}
BEL(Sn) = {#(rS), #(SKGS), #(h(x ⊕ y)), #(TS), LINK(rS)}
In this case, the global sets remain unchanged and thus, the secret set is the same as above:
Secret set: {pwU, bU, , x, y, X′, SKGS, h(x ⊕ y)}
After (SN1)–(SN8) actions of BL(Sn) are finished, (GW9)–(GW17) actions of BL(GW) are executed. (GW9)–(GW13) actions check the timestamp of Sn, and then verify the legitimacy of U and Sn. If they are correct, (GW14)–(GW17) actions of BL(Sn) are executed to make values(γ, δ) for authentication and send message. γ is used for authentication with Sn and δ is used for authentication with U.
After the (SN1)–(SN8) actions are done, the (GW9)–(GW13) actions in BL(GW) are performed to check the legitimacy of U and Sn. If the verification succeeds, the (GW14)–(GW17) actions are performed to generate γ and δ and to send the message M3 to Sn. The local sets of GW are modified as shown below.
POSS(GW) = {TG, γ, δ,x, y, X′, SKGS, h(x ⊕ y), {IDU, X, TU, α, ω, IDSn, Y, TS, β} from Sn}
BEL(GW) = {(#(x), #(y), #(X′), #(SKGS), #(h(x ⊕ y)), #(TG)}
The global sets are updated as follows:
Secret set: {pwU, bU, , x, y, X′, SKGS, h(x ⊕ y)}
- Observers sets:
-
–Observers(X′) = {GW}
-
–
After the (GW9)–(GW17) actions are finished, the (SN9)-(SN11) actions in BL(Sn) are conducted to verify the legitimacy of GW and U via the authenticator γ. If the verification process is completed, the (SN12)–(SN16) actions are performed to generate τ and sk from rS, KSU, X and Y, and to send the message M4 to U. The local sets of Sn is updated as follows:
POSS(Sn) = {Y, , KSU, rS, τ, sk, SKGS, {IDSn},{TG, γ, δ} from GW}
BEL(Sn) = {#(KSU), #(sk), #(SKGS), #( ), LINK (rS)}
Accordingly, the global sets are modified as follows:
Secret set: {pwU, bU, , x, y, KSU, sk, X′, SKGS, h(x ⊕ y)}
- Observers sets:
-
–Observers (KSU) = {Sn}
-
–Observers(sk) = {Sn}
-
–
The (U17)–(U19) actions in BL(U) are to check the legitimacy of GW and Sn while the (U20)–(U22) actions are to generate the session key sk from rU, KUS, X and Y. So, the conditions for the linkage rule are satisfied.
POSS(U) = {KUS, sk, {IDU}, {Y, , δ, τ} from Sn}
BEL(U) = {#(KUS), #(X′), #(sk), #(h(x ⊕ y)}
Secret set: {pwU, bU, , x, y, KSU, KUS, sk, X′, SKGS, (x ⊕ y)}
- Observers sets:
-
–Observers (KUS) = {U}
-
–Observers(sk) = {U}
-
–
In phase 3, U changes its password and updates AU, BU and WU stored in the smart card. In this phase, the local sets of U and the global sets remain unchanged.
The following shows the final version of the global sets.
Secret set: {pwU, bU, , x, y, KSU, KUS, sk, X′, SKGS, h(x ⊕ y)}
- Observers sets:
-
–Observers (pwU): {U}
-
–Observers (bU): {U}
-
–Observers( ): {U}
-
–Observers(x): {GW}
-
–Observers(y): {GW}
-
–Observers (KSU): {Sn}
-
–Observers (KUS): {U}
-
–Observers(sk): {U, Sn}
-
–Observers(X′): {U,GW}
-
–Observers(SKGS): {Sn, GW}
-
–Observers(h(x ⊕ y)): {U, Sn, GW}
-
–
This result implies that:
pwU, bU and are known only to the user U.
x and y are known only to the gateway GW.
The long-term key SKGS shared between Sn and GW is not exposed.
X′ is only known to U and GW.
KUS and KSU are only available to U and Sn.
The session key sk is securely shared between U and Sn.
h(x ⊕ y) is only known to the authorized principals: U, Sn and GW.
U, Sn and GW are mutually authenticated during the protocol execution.
This verifies the security claims we made in the previous subsection.
8. Conclusions
In this paper, we have identified that Shi et al.'s ECC-based authentication protocol designed for wireless sensor networks (WSNs) is vulnerable to: a session key attack, a stolen smart card attack, and a sensor energy exhausting attack. We have also proposed a new authentication protocol that addresses the identified security weaknesses. Our proposed protocol is as efficient as Shi et al.'s protocol and is better suited for WSNs than Yeh et al.'s protocol, the predecessor of Shi et al.'s protocol. As for the security of the proposed protocol, we have provided a heuristic analysis and formally verified the analysis using Rubin logic.
Acknowledgments
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Science, ICT&Future Planning (2014R1A1A2002775).
Author Contributions
Younsung Choi, Donghoon Lee, Jiye Kim, Jaewook Jung, Junghyun Nam and Dongho Won have contributed to security analysis, design of the proposed scheme, and manuscript preparation.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Dressler F. Authenticated reliable and semi-reliable communication in wireless sensor networks. Int. J. Netw. Secur. 2008;7:61–68. [Google Scholar]
- 2.Yeh H.L., Chen T.H., Liu P.C., Kim T.H., Wei H.W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors. 2011;11:4767–4779. doi: 10.3390/s110504767. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 3.Shi W., Gong P. A new user authentication protocol for wireless sensor networks using elliptic curves cryptography. Int. J. Distrib. Sens. Netw. 2013;2013:730831. [Google Scholar]
- 4.Satpute R.S., Thakare A.N. Survey on Security in Wireless Sensor Networks Using Elliptical Curves Cryptography. [(accessed on 6 June 2014)]. Available online: http://www.ijert.org/view.php?id=5878&title=survey-on-security-in-wireless-sensor-networks-using-elliptical-curves-cryptography.
- 5.Watro R., Kong D., Cuti S.F., Gardiner C., Lynn C., Kruus P. ACM Workshop on Security of Ad Hoc and Sensor Networks. ACM Press; Washington, DC, USA: 2004. TinyPK: Securing Sensor Networks with Public Key Technology; pp. 59–64. [Google Scholar]
- 6.Wong K.H., Zheng Y., Cao J., Wang S. A dynamic user authentication scheme for wireless sensor networks. Proceedings of 2006 IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing; Taichung, Taiwan. 5–7 June 2006; pp. 1–9. [Google Scholar]
- 7.Tseng H.R., Jan R.H., Yang W. An improved dynamic user authentication scheme for wireless sensor networks. Proceedings of IEEE Global Telecommunications Conference (GLOBECOM '07); Washington, DC, USA. 26–30 November 2007; pp. 986–990. [Google Scholar]
- 8.Das M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009;8:1086–1090. [Google Scholar]
- 9.He D., Gao Y., Chan S., Chen C., Bu J. An enhanced two-factor user authentication scheme in wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2010;10:361–371. [Google Scholar]
- 10.Khan M.K., Alghathbar K. Cryptanalysis and security improvements of “two-factor user authentication in wireless sensor networks”. Sensors. 2010;10:2450–2459. doi: 10.3390/s100302450. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 11.Chen T.H., Shih W.K. A robust mutual authentication protocol for wireless sensor networks. ETRI J. 2010;32:704–712. [Google Scholar]
- 12.Han W. Weakness of a Secured Authentication Protocol for Wireless Sensor Networks Using Elliptic Curves Cryptography. [(accessed on 27 June 2011)]. Available online: http://eprint.iacr.org/2011/293. [DOI] [PMC free article] [PubMed]
- 13.Kocher P., Jaffe J., Jun B. Differential power analysis. Proceedings of the 19th Annual International Cryptology Conference on Advances in Cryptology; Santa Barbara, CA, USA. 15–19 August 1999; pp. 388–397. [Google Scholar]
- 14.Messerges T.S., Dabbish E.A., Sloan R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002;51:541–552. [Google Scholar]
- 15.Muthukuru J., Sathyanarayana B. A Survey of Elliptic Curve Cryptography Implementation Approaches for Efficient Smart Card Processing. Glob. J. Comput. Sci. Technol. 2012;12:7–12. [Google Scholar]
- 16.Kar J., Majhi B. An efficient password security of multiparty key exchange protocol based on ECDLP. Proceedings of 2010 2nd International Conference on Computer Engineering and Technology (ICCET); Chengdu, China. 16–18 April 2010; pp. 405–413. [Google Scholar]
- 17.Venkata C., Saikat C., Mukesh S. A distributed multi-party key agreement protocol for dynamic collaborative groups using ECC. J. Parall. Distrib. Comput. 2006;66:959–970. [Google Scholar]
- 18.Lu R., Cao Z., Chai Z., Liang X. A simple user authentication scheme for grid computing. Int. J. Netw. Secur. 2008;7:202–206. [Google Scholar]
- 19.Nam J., Paik J., Kang H.K., Kim U.M., Won D. An off-line dictionary attack on a simple three-party key exchange protocol. IEEE Commun. Lett. 2009;13:205–207. [Google Scholar]
- 20.Lee Y., Kim S., Won D. Enhancement of two-factor authenticated key exchange protocols in public wireless LANs. Comput. Electr. Eng. 2010;36:213–223. [Google Scholar]
- 21.Nam J., Choo K.K.R., Kim M., Paik J., Won D. Dictionary attacks against password-based authenticated three-party key exchange protocols. KSII Trans. Internet Inf. Syst. 2013;7:3244–3260. [Google Scholar]
- 22.Jeon W., Kim J., Nam J., Lee Y., Won W. An enhanced secure authentication scheme with anonymity for wireless environments. IEICE Trans. Commun. 2012;E95.B:2505–2508. [Google Scholar]
- 23.Buttyan L., Csik L. Security analysis of reliable transport layer protocols for wireless sensor networks. Proceedings of 2010 8th IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOM Workshops); Mannheim, Germany. 29 March– 2 April 2010; pp. 419–424. [Google Scholar]
- 24.Brownfield M., Gupta Y., Davis N. Wireless sensor network denial of sleep attack. Proceedings of 2005 the Sixth Annual IEEE SMC Information Assurance Workshop (IAW '05); West Point, NY, USA. 15–17 June 2005; pp. 356–364. [Google Scholar]
- 25.Khouzani M.H.R., Sarkar S. Maximum damage battery depletion attack in mobile sensor networks. IEEE Trans. Autom. Control. 2011;56:2358–2368. [Google Scholar]
- 26.Khouzani M.H.R., Sarkar S., Altman E. Maximum damage malware attack in mobile wireless networks. ACM Trans. Netw. 2012;20:1347–1360. [Google Scholar]
- 27.Chen L., Cheng Z., Smart N.P. Identity-based key agreement protocols from pairings. Int. J. Inf. Secur. 2007;6:213–241. [Google Scholar]
- 28.Cao X., Zeng X., Kou W., Hu L. Identity-based anonymous remote authentication for value-added services in mobile networks. IEEE Trans. Veh. Technol. 2009;58:3508–3517. [Google Scholar]
- 29.He D., Chen J., Hu J. An ID-based client authentication with key agreement protocol for mobile client-server environment on ECC with provable security. Inf. Fusion. 2012;13:223–230. [Google Scholar]
- 30.Jeong H., Won D., Kim S. Weaknesses and improvement of secure hash-based strong-password authentication protocol. J. Inf. Sci. Eng. 2010;26:1845–1858. [Google Scholar]
- 31.Lee C.C., Hwang M.S., Liao I.E. Security enhancement on a new authentication scheme with anonymity for wireless environments. IEEE Trans. Ind. Electron. 2006;53:1683–1687. [Google Scholar]
- 32.Nam J., Kim S., Park S., Won D. Security analysis of a nonce-based user authentication scheme using smart cards. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2007;E90-A:299–302. [Google Scholar]
- 33.Rubin A.D., Honeyman P. Nonmonotonic cryptographic protocols. Proceedings of the Computer Security Foundations Workshop VII 1994 (CSFW 7); Franconia, NH, USA. 14–16 June 1994; pp. 100–116. [Google Scholar]
- 34.Das M.L., Narasimhan V.L. Towards a formal verification of an authentication protocol using non-monotonic logic. Proceedings of the IEEE Fifth International Conference on Information Technology: New Generations; Las Vegas, NV, USA. 7–9 April 2008; pp. 545–550. [Google Scholar]
- 35.Xu Y., Xie X. Analysis of authentication protocols based on Rubin logic. Proceedings of the 4th IEEE International Conference on Wireless Communications, Networking and Mobile Computing; Dalian, China. 12–14 October 2008; pp. 1–5. [Google Scholar]
- 36.Vaidya B., Makrakis D., Mouftah H. Two-factor mutual authentication with key agreement in wireless sensor networks. Secur. Commun. Netw. 2012 doi: 10.1002/sec.517. [DOI] [Google Scholar]


