Abstract
Extreme events, a type of collective behavior in complex networked dynamical systems, often can have catastrophic consequences. To develop effective strategies to control extreme events is of fundamental importance and practical interest. Utilizing transportation dynamics on complex networks as a prototypical setting, we find that making the network “mobile” can effectively suppress extreme events. A striking, resonance-like phenomenon is uncovered, where an optimal degree of mobility exists for which the probability of extreme events is minimized. We derive an analytic theory to understand the mechanism of control at a detailed and quantitative level, and validate the theory numerically. Implications of our finding to current areas such as cybersecurity are discussed.
Extreme events occur on a large variety of complex networked systems, examples of which include sudden bursts of packet flows in the Internet, jamming in computer or transportation networks, abrupt rise of web requests, and power blackouts in electrical power grid, etc. The intrinsic dynamics responsible for extreme events are network traffic or flow dynamics1,2,3,4,5,6,7,8,9,10,11,12,13 and the corresponding flux-fluctuation behaviors14,15,16,17,18,19,20,21,22. Especially, abnormally large fluctuations in the flow exceeding the nodal or link capacities can lead to extreme events, which either can be triggered by external disturbances or are a type of intrinsically emergent behavior. Extreme events can have catastrophic consequences, demanding the articulation and development of effective control strategies20,23,24. This problem, despite its uttermost importance to many disciplines, has not been addressed. The purposes of this report are to present an efficient and physically implementable method and to derive an analytic theory to understand its working.
This work aims to develop a physically practical control scheme against extreme events emerged from the intrinsic dynamic factors by using a simple but extensively representative model that captures the essential mechanism of many complex networked systems with information, material, or energy transportation. Within this model, as presented in the Methods Section, the random variables essential to the emergence extreme events are sums of random variables distributed in a binomial fashion (thin-tailed) which have well-defined first and second order moments. Thus, these sums follow the Lévy-alpha-stable distribution gα(x) with α = 2 25,26, and we do not expect the model to characterize all properties observed in reality, such as the “fat-tailed” distributions corresponding to α < 2.
Our principal idea of controlling extreme events is to make the whole network system time-dependent in that every node is mobile and consequently the associated set of links is time-varying. The mobility of the nodes can be characterized by a velocity-like parameter. The system can thus be modeled as a mobile network in which agents move in random directions but with constant velocity. Between any pair of agents, a link is established to enable exchange of packets only when their physical distance is within a pre-defined communication radius. We find that, the number of extreme events depends on the velocity and, strikingly, it exhibits a bell-shape, resonant-type of functional relation, as exemplified in Fig. 1. That is, there exists an optimal velocity for which the number of extreme events can be significantly reduced as compared with that in a static network. This finding suggests a practical control scheme: the occurrence of extreme events can be suppressed by making the network mobile with proper agent velocity. To understand this striking phenomenon, we develop a detailed analytic theory. To extend the control, we find a generalized mobility capable of dramatically lowering the control cost. We also develop a low-cost “intermittent strategy” that harnesses extreme events not only in mobile networks, but also in the classical ER-random networks27. Since extreme events encompass catastrophic situations such as large-scale breakdown induced by random failures of nodes or attacks, the general principle that dynamic networks can be immune to extreme events can have significant applications in the field of security and robustness of complex systems.
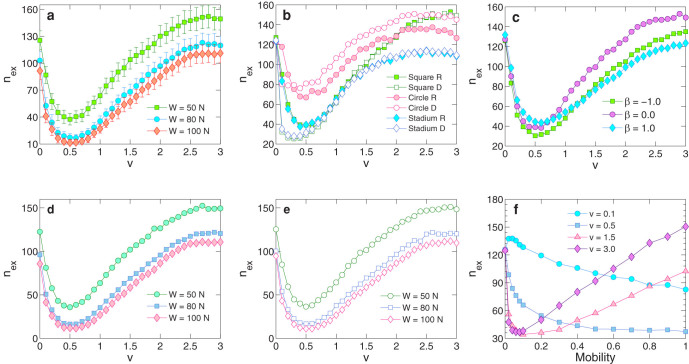
Figure 1. The number of extreme events versus velocity and mobility.
For a network of N = 1200 nodes in a square domain of size L = 10 (arbitrary unit), (a), The number of extreme events nex versus the agent velocity v for W = 50N, 80N, and 100N; (b), nex of extreme events versus velocity v when nodes execute random walk (R) or deterministic motion (D) within square, circular, and stadium-shaped domains. The areas of the circle and the stadium are chosen to be equal to the area of the square L × L. (c), Robustness of control with respect to heterogeneity in the nodal communication range: nex versus v for β = −1, 0, and 1, where β is a parameter characterizing the distribution of nodal communication range. (d) and (e), robustness of control with respect to packet-transportation protocol: nex versus velocity v when packet generation and annihilation are taken into account for two situations where (d) the total number of packets is fixed at W and (e) the number of newly generated packets at each time step is fixed to be W/N. (f), Generalization of mobility: nex versus mobility, defined as the probability that a node moves with velocity v, for a number of v values. All simulation results are obtained using 100 realizations in T = 1000 time steps. The error bars in nex from different realizations have relatively small and similar magnitude in (a–e), and it monotonously increases with velocity v, as shown in panel (a) [the error bars in (b–e) are omitted for clear visualization]. Here, the definition of an extreme event on a node is that its number of packets is at least four standard-deviations above the average.
We emphasize that our work is focused on controlling extreme events caused by the intrinsic randomness of the system, rather than external attacks. More sophisticated mechanisms such as failures and load redistribution, e.g., as triggered by external attacks, would be an interesting topic of study. Instead of analyzing the extreme value distributions above the threshold as determined by the extreme value theory28,29 under the peak-over-threshold setting, our work concentrates on calculating the total number of events that exceed a certain threshold for the purpose of control.
Results
We consider a square domain of size L × L in which N agents move at speed v but in random directions. The communication radius of each agent is 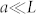 , and the total number of packets on the network at any given time is W. At time t, the number of packets carried by a node is w(t), and each packet is delivered to a randomly selected neighboring node at time t + 1. In contrast to previous works on synchronization in mobile-agent networks30,31,32 where periodic boundary conditions were often used, we use the “hard-wall” boundary condition for the consideration that a cross-boundary link connecting two nodes close to the same boundary but physically distant from each other is not physical in an actual traffic-flow network, which is discussed in a later section. We will see that boundary effect plays a crucial role in the dynamics of extreme events, a fact that will be fully exploited in our development of the analytic theory.
, and the total number of packets on the network at any given time is W. At time t, the number of packets carried by a node is w(t), and each packet is delivered to a randomly selected neighboring node at time t + 1. In contrast to previous works on synchronization in mobile-agent networks30,31,32 where periodic boundary conditions were often used, we use the “hard-wall” boundary condition for the consideration that a cross-boundary link connecting two nodes close to the same boundary but physically distant from each other is not physical in an actual traffic-flow network, which is discussed in a later section. We will see that boundary effect plays a crucial role in the dynamics of extreme events, a fact that will be fully exploited in our development of the analytic theory.
The existence of optimal mobility and its robustness
Our extensive computations indicate that the existence of an optimal moving velocity to suppress extreme events is general: it holds under a variety of boundary shapes, motion schemes, and even heterogeneously distributed communication radii, as shown in Figs. 1a,b, and c. This indicates that the characteristic, non-monotonous relation between nex and velocity v that underlies the control of extreme events is in fact robust with respect to variants in the system setting such as the geometric shape of the domain, the manner by which the individual nodes move, heterogeneity in the nodal communication range, and packet transportation protocol.
As can be seen from Fig. 1a, different W values do not affect the existence of the optimal moving velocity. Figure 1b shows, for a number of variants in the geometric shape of the domain (square, circle, and stadium), the relation between nex and v. We observe that the non-monotonous behavior holds for all geometric shapes considered. As shown, the particular manner by which nodes in the network move in the space has little effect on the non-monotonous behavior. In particular, both random walk and deterministic motion are considered, where for the latter, random moving directions are chosen initially but at time t, a node moves along the direction of the velocity at time t − 1. Figure 1b indicates that the existence of an optimal velocity to minimize the number of extreme events is highly robust regardless of the domain geometry, random or deterministic movements.
In realistic systems, mobile agents' ranges are not homogeneous. To model heterogeneity in the nodal communication range, we randomly assign each node a weight μ according to the distribution P(μ) ~ μ−3. The area of the nodal communication circle is given by 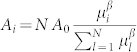 , where A0 = πa2 is the average communication area over all nodes, μi and μl are the assigned weight values corresponding to nodes i and l, and β is an adjustable parameter characterizing the heterogeneity of Ai. The distribution of Ai is thus
, where A0 = πa2 is the average communication area over all nodes, μi and μl are the assigned weight values corresponding to nodes i and l, and β is an adjustable parameter characterizing the heterogeneity of Ai. The distribution of Ai is thus 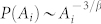 . For β > 0, majority of nodes have relatively small communication circles except for a few, and the opposite situation occurs for β < 0. For β = 0, the communication circles are all identical: namely Ai = A0 and ai = a for i ∈ [1, 2, …, N]. Since the degree of a node is proportional to its communication area, it is equivalent to a power-law degree distribution of the mobile network with the fixed average degree 〈k〉 = N/L2A0. The physical meanings of positive and negative values of β are the following. In a realistic wireless sensor network, for example, there are usually anchor nodes that have much larger communication ranges and play the role of central controllers of the whole network. This situation can be characterized by some positive value of β. There can also be a few nodes that malfunction or run low on power supply. These nodes would have nearly zero communication ranges while most nodes in the network have finite communication ranges. This corresponds to the case of a negative β value. Figure 1c shows that the non-monotonous behavior in the nex-v relation holds regardless of whether the value of β is positive or negative, indicating the robustness of mobility-based strategy to harness extreme events in the presence of nodal heterogeneity.
. For β > 0, majority of nodes have relatively small communication circles except for a few, and the opposite situation occurs for β < 0. For β = 0, the communication circles are all identical: namely Ai = A0 and ai = a for i ∈ [1, 2, …, N]. Since the degree of a node is proportional to its communication area, it is equivalent to a power-law degree distribution of the mobile network with the fixed average degree 〈k〉 = N/L2A0. The physical meanings of positive and negative values of β are the following. In a realistic wireless sensor network, for example, there are usually anchor nodes that have much larger communication ranges and play the role of central controllers of the whole network. This situation can be characterized by some positive value of β. There can also be a few nodes that malfunction or run low on power supply. These nodes would have nearly zero communication ranges while most nodes in the network have finite communication ranges. This corresponds to the case of a negative β value. Figure 1c shows that the non-monotonous behavior in the nex-v relation holds regardless of whether the value of β is positive or negative, indicating the robustness of mobility-based strategy to harness extreme events in the presence of nodal heterogeneity.
We also consider realistic variants of the packet-transportation model by randomly assigning each packet a destination node where the packet annihilates upon its arrival at the destination, and new packets are generated to balance the annihilation effect. Two packet generation schemes are studied: (1) the total amount of packets W is kept constant by generating the annihilated number of packets at randomly selected nodes; (2) W/N newly generated packets are randomly distributed to nodes to keep W statistically constant but with fluctuations (the average number of annihilated packets is W/N for high velocity). As shown in Figs. 1d and e, nearly identical behavior in the nex-v relation is observed, regardless of the specific packet-transportation protocol, providing further support for the robustness of our control method.
While so far we have focused on dynamic networks where agents move with certain velocity, the idea of making a network mobile to control extreme events can be generalized to different forms of “mobility.” Here we discuss one variant, in which the mobility is defined as the probability that any node moves with velocity v. For relatively high values of v, there exists an optimal mobility value at which the number of extreme events is minimized, as shown in Fig. 1f. Notice that the optimal mobility is near zero, indicating that only a small fraction of the nodes actually move and vast majority of the nodes remain stationary. The implication is that extreme events can be effectively mitigated by moving a few nodes, which is advantageous from the consideration of control cost.
Explanation and boundary effect
In the following, we focus on the development of analytical understanding of the phenomenon. To begin, we note that, since each node receives packets at time t from its neighbors that equally distribute all the packets obtained at t − 1 to all their neighbors, a node's flow w(t) at time t is contributed to by its neighbors' flow at time t − 1, denoted by wn(t − 1). In a static network, the ensemble averaged flow through a node at last time step is proportional to its degree 〈w(t − 1)〉 = Wk/(2E). However, in a time-varying network, this relation no longer holds. In particular, the flow would be independent of the degree under high velocity, leading to 〈w(t − 1)〉 = W/N. We thus hypothesize the following general relation between 〈w(t − 1)〉 and node degree for different regimes of the velocity v:
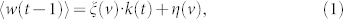 |
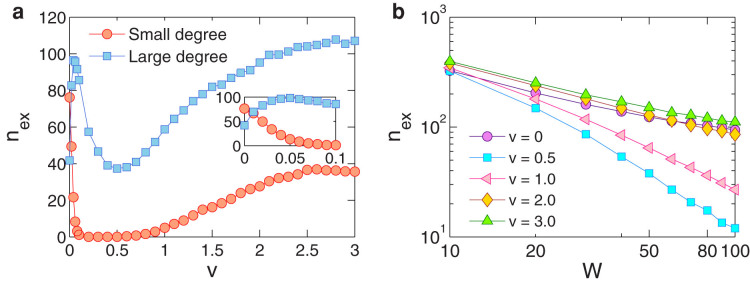
where ξ(v) and η(v) are parameters that depend on the velocity only, and the first and second terms correspond to the velocity-dependent and velocity-independent flow components, respectively. Generally, the quantity ξ(v) decreases with v, since higher mobility tends to yield a weaker flow-degree correlation. However, η(v) tends to increase with v due to the increasing degree of randomness in the dynamics. Thus, for v → 0, the steady network exhibits a high flow-degree correlation and little randomness, so we have ξ(v) = W/(2E) and η(v) = 0. For v → ∞, the correlation is lost, leading to ξ(v) = 0 and η(v) = W/N. Equation (1) thus represents a universal empirical law, which we have verified computationally through various models (see the Methods section). Conservation of the total number of data packets imposes the following constraint on the parameters ξ(v) and η(v): 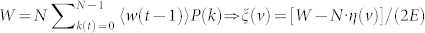 . Setting η(v) = 0 (or η(v) = W/N) yields ξ(v) = W/(2E) (or ξ(v) = 0). We see that Eq. (1) contains the results for v = 0 and v → ∞ as two limiting cases.
. Setting η(v) = 0 (or η(v) = W/N) yields ξ(v) = W/(2E) (or ξ(v) = 0). We see that Eq. (1) contains the results for v = 0 and v → ∞ as two limiting cases.
With the help of Eq. (1), the probability for the node at location b (illustrated in Fig. 2a) to carry w packet, Ψ(w(t))b, is obtained. This distribution Ψb(w(t)) serves as a centro-symmetric probability field for each dimension of the two-dimensional space. For a static node located at b0, the PDF of its flow is 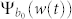 . For any moving node (v > 0) initially at b0, the PDF of its flow,
. For any moving node (v > 0) initially at b0, the PDF of its flow, 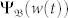 , is contributed by the Ψb(w) fields at all the locations it has visited, and thus can be expressed as an integral of Ψb(w). In turn, the total number of extreme events occurred within T time steps is obtained as an integral of
, is contributed by the Ψb(w) fields at all the locations it has visited, and thus can be expressed as an integral of Ψb(w). In turn, the total number of extreme events occurred within T time steps is obtained as an integral of 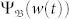 over all possible starting location,
over all possible starting location,
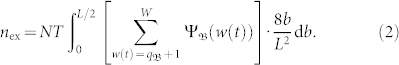 |
where 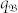 is the extreme event threshold. Since η(v) monotonously increases with v, Figure 2b shows that Eq. (2) successfully explains the numerically observed non-monotonous behavior as exemplified in Fig. 1a, providing the theoretical foundation for mobility-based control of extreme events.
is the extreme event threshold. Since η(v) monotonously increases with v, Figure 2b shows that Eq. (2) successfully explains the numerically observed non-monotonous behavior as exemplified in Fig. 1a, providing the theoretical foundation for mobility-based control of extreme events.
Figure 2. Geometrical setting and the theory result.
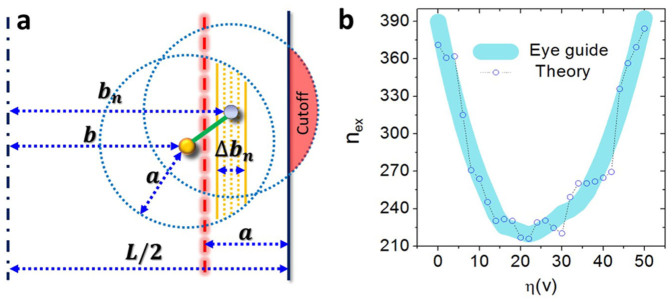
(a), Illustration of various geometrical quantities used in the analysis: communication radius a, distance b from the middle of the square to the target node, distance bn from the middle of the square to a neighbor of the target node, the width Δbn of the bar region, and the cutoff region of the communication circle. (b), Results of Eq. 2 for db = 0.01 and Δbn = 0.002 (the main features do not depend on the specific values of db and Δbn).
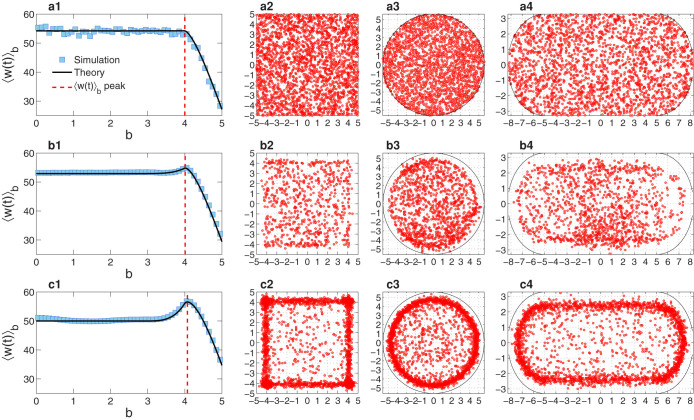
Our theory provides a detailed understanding of the effect of velocity on the occurrence of extreme events. To further demonstrate this, we exploit the effect of domain boundary on the emergence of extreme events by examining the behavior of 〈w(t)〉b versus b, as exemplified in Figs. 3a1,b1,c1, where a good agreement between our theory and simulation for various velocity values can be seen. Note that 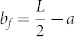 specifies the position of one communication radius away from the boundary. For v = 0, 〈w(t)〉b is constant for b ∈ [0, bf] and decreases with b in the interval
specifies the position of one communication radius away from the boundary. For v = 0, 〈w(t)〉b is constant for b ∈ [0, bf] and decreases with b in the interval 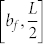 . As v is increased, a peak in 〈w(t)〉b arises for b = bf, but on the left and right sides of the peak, 〈w(t)〉b is approximately constant and a decreasing function of b, respectively. For convenience, we call
. As v is increased, a peak in 〈w(t)〉b arises for b = bf, but on the left and right sides of the peak, 〈w(t)〉b is approximately constant and a decreasing function of b, respectively. For convenience, we call 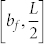 the boundary region. As a node moves closer to the boundary, more portion of its communication circle is cut off, leading to lower values of 〈k(t)〉 and 〈w(t)〉b. For v → 0,
the boundary region. As a node moves closer to the boundary, more portion of its communication circle is cut off, leading to lower values of 〈k(t)〉 and 〈w(t)〉b. For v → 0, 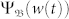 is highly localized so that
is highly localized so that 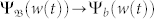 . For the static network, extreme events are approximately equally probable in the domain, except in the boundary region, as shown in Fig. 3a2. As velocity is increased from zero,
. For the static network, extreme events are approximately equally probable in the domain, except in the boundary region, as shown in Fig. 3a2. As velocity is increased from zero, 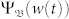 depends more strongly on Ψb(w(t))'s and the peak in 〈w(t)〉b about bf generates a higher value of
depends more strongly on Ψb(w(t))'s and the peak in 〈w(t)〉b about bf generates a higher value of 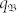 in the neighborhood region of bf, reducing the probability of extreme events. In the part of the boundary region where low values of 〈w(t)〉b meets with high value of
in the neighborhood region of bf, reducing the probability of extreme events. In the part of the boundary region where low values of 〈w(t)〉b meets with high value of 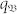 , there are no extreme events, as shown in Fig. 3b2. For high velocity, each node appears in the domain with approximately equal probability and
, there are no extreme events, as shown in Fig. 3b2. For high velocity, each node appears in the domain with approximately equal probability and 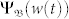 is completely delocalized, so we have
is completely delocalized, so we have  . In this case, there is little difference in the dynamical behavior of nodes. When a node is near bf, the sudden increase in the flow can cause an extreme event, which is the mechanism responsible for high concentration of extreme events about b = bf, as shown in Fig. 3 c2.
. In this case, there is little difference in the dynamical behavior of nodes. When a node is near bf, the sudden increase in the flow can cause an extreme event, which is the mechanism responsible for high concentration of extreme events about b = bf, as shown in Fig. 3 c2.
Figure 3. Boundary effect.
(a1), (b1), (c1), Behavior of 〈w(t)〉b versus b from direct simulation (blue squares) and predicted by Eq. (9) (solid black lines) for v = 0, 0.5 and 3.0, respectively. Note that v ≈ 0.5 is the optimal value of the velocity that minimizes nex in Fig. 1, and v = 3.0 represents a relatively high velocity value for the system of size L = 10 and communication radius a = 1. For (a1), we have η(v = 0) = 0. Since Eq. (9) indicates a smooth dependence of 〈w(t)〉b on b and since a detailed interdependence between η(v) and v is unknown, we find η(v) = 15 best fits the case in (b1). For (c1), we have η(v = 3.0) → η(v → ∞) = 50. The red dashed line indicates the position of the peak in the curve of 〈w(t)〉b versus b. (a2), (b2), (c2), Positions of all extreme events occurred in square domain for v = 0, 0.5, and 3.0, respectively. (a3), (b3), (c3), Positions of all extreme events occurred in circular domain for v = 0, 0.5, and 3.0, respectively. (a4), (b4), (c4), Positions of all extreme events occurred in stadium domain for v = 0, 0.5, and 3.0, respectively. All results are obtained from 20 independent statistical realizations.
Figs. 3a3, b3, c3, and a4, b4, c4 show the patterns of the locations of the extreme events occurring on nodes for v = 0, 0.5, and 3 within the circular and stadium-shaped domains, respectively, where the motions of nodes are completely random. For deterministic motions of the nodes, the patterns are similar. Regardless of the geometrical shape of the domain, a frame of extreme events (FEEs) emerges about one communication radius away from the domain boundary for high velocity, providing visual support for the basic idea underlying our theory: the boundary plays an important role in the emergence of extreme events.
To intuitively understand the non-monotonous phenomenon, we name the nodes within the boundary region (region between the boundary and the FEE) as boundary nodes (BNs), the nodes sitting on the FEE as frame nodes (FNs), and the nodes within the FEE as inside nodes (INs). Each node moves continuously in the space and acts as one of the three types of nodes from time to time. Due to the cutoff in the communication circles in the boundary region, the BNs have lower average degree than the FNs and INs, namely 〈kBN〉 < 〈kIN〉 = 〈kFN〉. At high velocity, most BNs are in fact originally INs from the inside carrying 〈wIN〉 packages, where 〈wIN〉 is the average flow of the INs. Apparently, we have 〈wIN〉/〈kIN〉 < 〈wIN〉/〈kBN〉. Thus, for BNs, each of their links delivers more packages out than the INs. As recipients, FNs and INs have the same average degree (〈kIN〉 = 〈kFN〉) while FNs have more BN neighbors than INs have. We then have 〈wFN〉 > 〈wIN〉, i.e., FNs receive more packages. In addition, the FNs have more neighbors than the BNs, and thus we have 〈wFN〉 > 〈wBN〉. This mechanism produces the FEE with higher density of extreme events due to a sudden increase in the flow when BNs and INs move into the region of FNs. However, the FEE so generated also increases the threshold 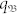 and accordingly decreases the probability of occurrence of extreme events. Consequently, the coexistence of the two competing mechanisms generates the non-monotonous behavior, leading to an optimal velocity. Our theory, albeit non-rigorous, quantifies the relative strength of the two mechanisms and determines whether extreme events are facilitated or suppressed as velocity is increased.
and accordingly decreases the probability of occurrence of extreme events. Consequently, the coexistence of the two competing mechanisms generates the non-monotonous behavior, leading to an optimal velocity. Our theory, albeit non-rigorous, quantifies the relative strength of the two mechanisms and determines whether extreme events are facilitated or suppressed as velocity is increased.
The effect of wormholes
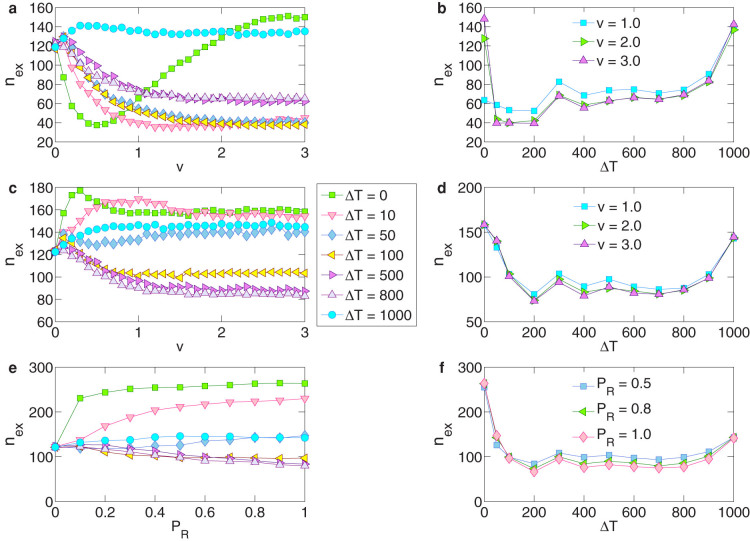
In fact, consider an artificial system in which a fraction of links can be made cross-boundary. We find that, as the number of such “periodic-boundary-condition type” of links is increased, the ability for the mobile network to suppress extreme events is degraded dramatically, as shown in Fig. 4a. This finding inspires significant applications in the emerging field of cybersecurity. Here we present one example by arguing that our control strategy can be used to detect wormhole attacks on mobile networks. In particular, a communication wormhole is a long-range link connecting two nodes beyond each's communication range, a recently developed concept in the field of network security33,34,35. Suppose any pair of nodes with distance over dwh are connected by a wormhole. A smaller value of dwh will then introduce more wormholes into the system. Let pwh be the ratio between the number of wormholes and the total number of edges E in the network. As shown in Fig. 4b, for moderate or relatively high velocity, a slight decrease in dwh can trigger an explosive increase in nex but there is only incremental change in pwh. Thus, abnormally large number of extreme events in a mobile network are strong indication that the network is under wormhole attack. Likewise, instilling a small number of wormholes into an adversary mobile network can effectively destroy its functions through the generation of a large number extreme events.
Figure 4. Effect of long range links.
(a), effect of periodic boundary condition (PBC): nex versus v when 0% (green circles, no PBC), 30% (aqua triangles), 50% (pink triangles), and 100% (purple triangles, complete PBC) randomly selected cross-boundary links are applied. (b), Effect of communication wormhole on control: nex versus v when a wormhole link is applied to any pair of nodes closer than dHW = 13.0, 12.5, 12.3, and 12.0 for pHW = 0.4%, 2%, 3%, and 5%, respectively.
Suppression of extreme events in intermittently mobile networks
A network can be made mobile but only intermittently by introducing a “frozen” time interval ΔT during which the network structure is fixed. Specifically, each time after certain nodes in the network have moved, the network structure remains invariant for ΔT time steps before the next movement. For ΔT = 0, the network structure changes at every time step. Regardless of whether nodes are moving, the packet flow on the network is not interrupted. As shown in Figs. 5a–d, the number nex of extreme events exhibits a non-monotonous behavior with velocity v (for fixed values of ΔT) or with ΔT (for fixed value of v). In particular, Figs. 5a,b show, under hard-wall boundary conditions, nex versus v for a number of fixed values of ΔT and versus ΔT for three values of the velocity, respectively. We observe that, increasing ΔT slightly above 0 leads to a sharp decrease in nex, indicating that making the network intermittently mobile can be a cost-effective strategy to suppress extreme events. This holds regardless of the boundary condition. In fact, an intermittently mobile network system under periodic boundary conditions possesses a similar ability to suppress extreme events, as shown in the corresponding plots in Figs. 5c,d. All these indicate mobility as a general and effective strategy to suppress extreme events.
Figure 5. Number of extreme events in intermittently mobile networks.
(a) and (b), For a mobile network with hard-wall boundary conditions, nex versus v and for a number of fixed values of the frozen time ΔT and versus ΔT for three values of v. (c) and (d), Corresponding results for periodic boundary conditions. (e) and (f), For a classic ER-network under intermittent random rewiring (a kind of generalized mobility), nex versus the rewiring probability PR (for a number of fixed values of ΔT) and versus ΔT (for PR = 0.5, 0.8, and 1.0), respectively.
While the concept of “mobility” can readily be generalized to static networks in which the nodes are not allowed to move physically, the existence of a physical boundary plays a critical role in controlling extreme events. For example, a network can be regarded as “mobile” insofar as its connection topology is time-varying, which can be realized, for example, by random rewiring of a subset of links from time to time in a computer network. In this case, an actual physical domain for the network cannot be properly defined. To demonstrate the importance of a physical boundary, we consider a classic ER network27 with random rewiring. Let PR be the rewiring probability, the probability that an arbitrary link in the network is removed while a new link is established between a randomly selected pair of nodes that were not previously linked. Since the ER random network has no spatial structure, it is the change of nodal degree that leads to the variation in nex as PR is increased. As shown in Fig. 5e, nex cannot be minimized by PR, indicating inability for random rewiring to suppress extreme events. Simulations also show that the number of extreme events is not affected by the detailed rewiring mechanism, insofar as the nodal degree is unchanged. However, intermittent rewiring can reduce nex to certain extent, as shown in Fig. 5f. For high value of PR in the ER random network, the number of extreme events, nex, can be solved analytically via the approach of self-consistent equation (see Methods Section).
Degree bias and scaling
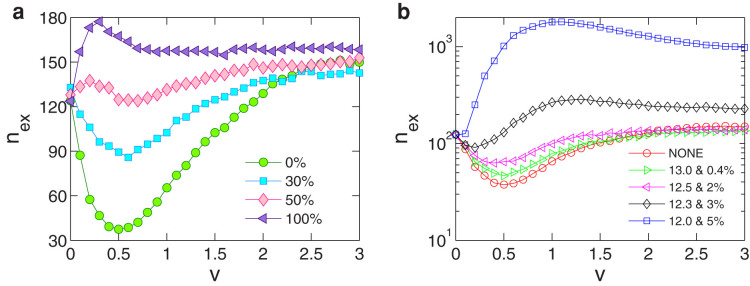
A previous result20 indicated that, in static networks, extreme events tend to occur more frequently on low-degree nodes. However, in any real-world network, certain degree of mobility is expected. Our computation indicates that, insofar as the network is mobile, extreme events tend to occur on highly connected nodes whose degrees are larger than the average degree of the network, as shown in Fig. 6a for a mobile network with hard-wall boundary conditions. Similar behaviors have been observed for mobile networks with periodic boundary conditions and for ER-random networks as well. We also find a scaling phenomenon between nex and the total number of packets W, as exemplified in Fig. 6b.
Figure 6. Degree bias and scaling.
For a mobile network in a square domain with hard-wall boundary conditions, (a), number nex of extreme events occurring on small (red circles) and large (blue squares) degree nodes versus v, and (b), nex versus the total number of packets W for various velocity values.
Discussion
To summarize, we find that extreme events in a complex network can be effectively controlled by making the network mobile, where the concept of mobility is general and can be implemented in various ways. A straightforward manifestation is that every node moves at a certain velocity but in random directions in a finite physical domain, in which case an analytic theory is developed to understand the existence of an optimal velocity to minimize the number of extreme events. Variants of the mobile schemes can also be considered, proving the generality of our control strategy. Our theory has significant applications in the field of cybersecurity, where we articulate and demonstrate, for example, that wormhole attack on a mobile network can be detected through the monitoring of extreme events. Control of extreme events is an extremely important and challenging problem in science and engineering, and our work may stimulate further efforts.
Methods
Relation between ξ(v) and η(v)
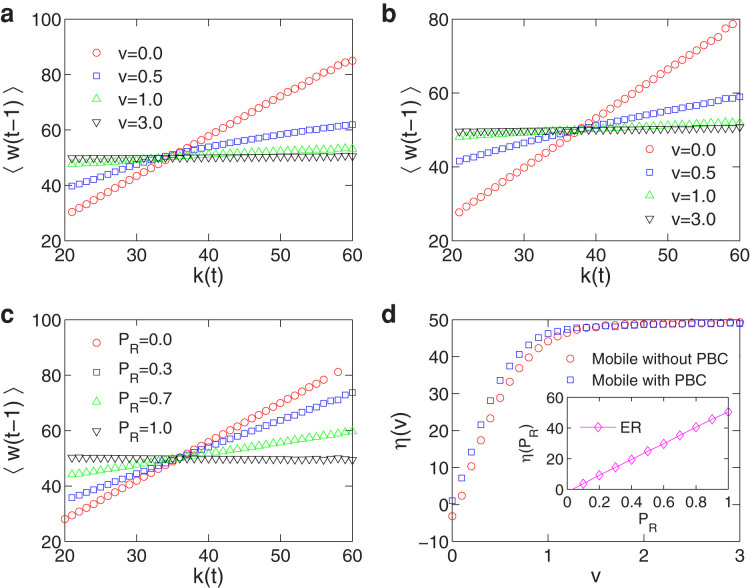
Figure 7 show the relationship between a node's flow w(t − 1) at time t − 1 and its degree k(t) at time t for different velocity values, the basic relation employed in our theoretical analysis in the main text, and the function η(v) is shown in Fig. 7d. We observe a robust linear relation for mobile networks with periodic boundary conditions and for ER-random networks27. For mobile networks with hard-wall boundary conditions, the relation is still linear, especially for low or high velocity values. For moderate velocity values, there is deviation from the linear behavior, due to the boundary effect as shown in Fig. 3. (This boundary effect does not exist in mobile networks with periodic boundary conditions and in ER-random networks.) In general, we observe an approximately linear relation between w(t − 1) and k(t), which can be taken as an empirical law for our analysis of the extreme-event dynamics in mobile networks.
Figure 7. Linear relation between 〈w(t − 1)〉 and k(t).
(a–c), Linear relation between 〈w(t − 1)〉 and k(t) for mobile networks with hard-wall and periodic boundary conditions, and for ER-random networks, respectively. (d), Dependence of η(v) on v for mobile networks with hard-wall and periodic boundary conditions (PBCs), and η(PR) versus PR for ER-random networks (inlets). All results are averaged over 20 statistical realizations.
We present a detailed derivation of the relation between ξ(v) and η(v). The starting point is the following packet conservation law:
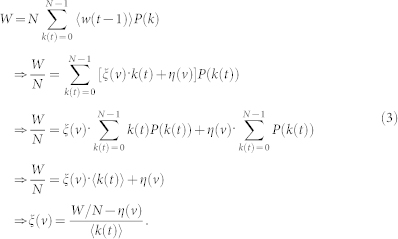 |
The average degree of the whole network is 〈k(t)〉 = 2E/N. We thus have
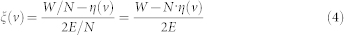 |
Detailed analytical explanation to the non-monotonous behavior
As illustrated in Fig. 2a, the probability that z packets are delivered to the focal node located at b from a neighbor of degree kn(t) located at bn and carrying wn(t − 1) packets is given by
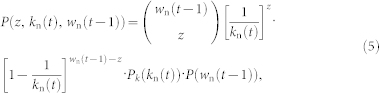 |
where Pk(kn(t)) is the degree distribution of the neighboring nodes:
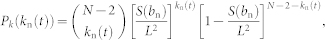 |
and S(bn) is the circular communication area of the neighbor located at bn. For bn ≤ L/2 − a, the area is a complete circle with S(bn) = πa2. However, for L/2 − a < bn ≤ L/2, a cutoff by the boundary leads to S(bn) = πa2(1 − α/π) + a sin α · (L/2 − bn), where α = arccos((L/2 − bn)/a), as shown in Fig. 2a. The quantity P(wn(t − 1)) is the probability density function (PDF) of wn(t − 1), which depends on the velocity v and further analysis is needed to determine its mathematical form.
Using Eq. (1), we can write the probability for a packet to visit a node as 〈w〉/W = (1/W)[ξ(0) · k + η(0)] for v = 0. For v ≠ 0, the probability for a node at bn to be visited is pn = 〈wn(t − 1)〉/W = [ξ(v) · kn(t) + η(v)]/W. We thus have 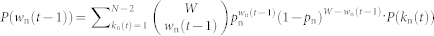 . Substituting this expression into Eq. (5), we obtain the PDF of z as
. Substituting this expression into Eq. (5), we obtain the PDF of z as 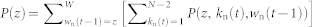 . Consider any one of the boundaries of the square domain, as shown in Fig. 2a. For the focal node located at b,
. Consider any one of the boundaries of the square domain, as shown in Fig. 2a. For the focal node located at b, 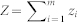 packets will be delivered to it from its m neighbors located in the bar-shaped region of width Δbn → 0 at bn. The PDF of Z associated with bn is the convolution of the m PDFs, taking into account all possible values of m:
packets will be delivered to it from its m neighbors located in the bar-shaped region of width Δbn → 0 at bn. The PDF of Z associated with bn is the convolution of the m PDFs, taking into account all possible values of m: 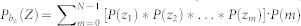 , where P(m) is the probability for m nodes to exist in the bar region:
, where P(m) is the probability for m nodes to exist in the bar region:
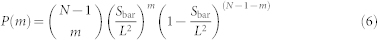 |
with area given by 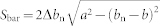 for small Δbn. The flow w(t) of the node at time t is the sum of the incoming packets from nodes in all the bar-shaped regions within its communication circle:
for small Δbn. The flow w(t) of the node at time t is the sum of the incoming packets from nodes in all the bar-shaped regions within its communication circle: 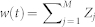 , where the contribution from each region can be treated independently and
, where the contribution from each region can be treated independently and 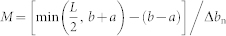 . The PDF of w(t) can then be expressed as the convolution of all
. The PDF of w(t) can then be expressed as the convolution of all 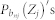 for bnj ∈ [b − a, min(L/2, b + a)], as
for bnj ∈ [b − a, min(L/2, b + a)], as 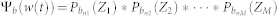 .
.
For a static node located at b0, the PDF of its flow is 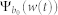 . For any moving node (v > 0) initially at b0, the PDF of its flow is contributed by the Ψb(w) fields at all the locations it has visited, i.e., the circular region centered at b0 with estimated radius R(v). The PDF of this node's flow thus contains the contributions from all Ψb(w(t))'s for b ∈ [b0 − R(v), min(b0 + R(v), L/2)]. The random walk radius R(v) increases with v, and R(v) → 0 for v → 0 and reaches L/2 (the upper bound of b) for v → ∞. Since R(v) and η(v) both increase monotonically with v, we have, approximately,
. For any moving node (v > 0) initially at b0, the PDF of its flow is contributed by the Ψb(w) fields at all the locations it has visited, i.e., the circular region centered at b0 with estimated radius R(v). The PDF of this node's flow thus contains the contributions from all Ψb(w(t))'s for b ∈ [b0 − R(v), min(b0 + R(v), L/2)]. The random walk radius R(v) increases with v, and R(v) → 0 for v → 0 and reaches L/2 (the upper bound of b) for v → ∞. Since R(v) and η(v) both increase monotonically with v, we have, approximately, 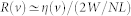 . Consequently, the flow PDF of a node initially at location b moving with velocity v can be obtained as a function of b:
. Consequently, the flow PDF of a node initially at location b moving with velocity v can be obtained as a function of b:
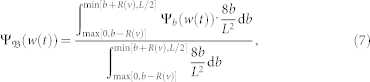 |
where 8b db/L2 is the probability that a node is in the region about the location b via random walk, and the denominator on the right side is a normalization factor. The quantity 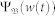 determines the threshold
determines the threshold 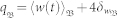 over which extreme events take place, where
over which extreme events take place, where 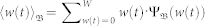 and
and 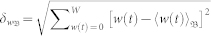 . Finally, we obtain the number of extreme events occurred within T time steps as
. Finally, we obtain the number of extreme events occurred within T time steps as
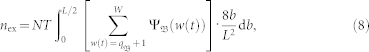 |
which is a function of η(v).
In the derivation of Eq. (2), the degrees of the neighboring nodes are treated independently in Eq. (5) and the expression of P(wn(t − 1)), which is an approximation because nodes that are spatially close tend to be degree-correlated. The spatial degree correlation represents the main discrepancy between our moving random-network model and a mobile network in the real physical space (see the following for a detailed discussion about the effect of spatial correlation). Notwithstanding, the degree correlation has no dependence on the velocity and, hence, there is little effect on extreme-event generation in the system for different values of the velocity.
The average flow 〈w(t)〉b at location b can be obtained via Ψb(w(t)) as well as the mean-field theory:
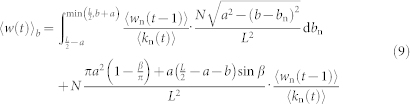 |
where β = arccos[(L/2 − a − b)/a], 〈wn(t − 1)〉 = ξ(v) · 〈kn(t)〉 + η(v), and 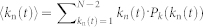 . The first term on the right side is the contribution from the neighboring nodes with their communication circles partially cutting off by the boundary, while the second term represents the contribution from neighbors with complete communication circles.
. The first term on the right side is the contribution from the neighboring nodes with their communication circles partially cutting off by the boundary, while the second term represents the contribution from neighbors with complete communication circles.
Self-consistent equation to estimate the number of extreme events in ER random networks
For high value of PR in the ER random network, the number of extreme events, nex, can be solved analytically via the approach of self-consistent equation. Regarding PR as corresponding to some kind of “velocity” v, we have that the number of extreme events nex for v = 0 is given by
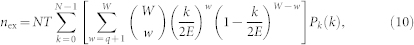 |
where q is the threshold by which extreme events are defined, and the degree distribution P(k) of the network can be written in a binomial form:
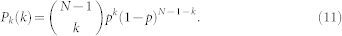 |
To map the ER random network into a two-dimensional mobile network, we set the link probability to be p = πa2/L2. Eq. (10)yields 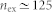 , which matches the simulation result for v = 0 well.
, which matches the simulation result for v = 0 well.
For high velocity, the PDF of flow P(w) becomes independent of k and identical for all nodes, which can be solved analytically by the self-consistent equation method. In particular, the number z of packets delivered to a node of degree k from one of its neighbors of degree kn has the following PDF
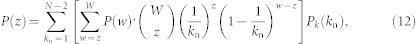 |
where Pk(kn) is the degree distribution of the neighboring node given by Eq. (11), and P(w) can be obtained via the weighted sum of the convolution of P(z):
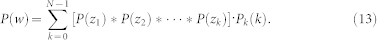 |
By substituting any form of P(w) that satisfies 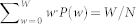 into Eq. (13), we obtain an updated form of P(w) via Eq. (12). The solution of P(w) can be obtained by iterating the self-consistent equation until the root-mean-square deviation between P(w) and its updated version falls below a small threshold
into Eq. (13), we obtain an updated form of P(w) via Eq. (12). The solution of P(w) can be obtained by iterating the self-consistent equation until the root-mean-square deviation between P(w) and its updated version falls below a small threshold  (e.g.,
(e.g., 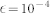 ). Figure 8a shows a good agreement between P(w) from direct simulation and from the self-consistent approach. The number of extreme events can then be estimated, yielding
). Figure 8a shows a good agreement between P(w) from direct simulation and from the self-consistent approach. The number of extreme events can then be estimated, yielding 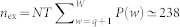 , which agrees quite well with the value from direct simulation.
, which agrees quite well with the value from direct simulation.
Figure 8. PDF of flow P(w) in simulation and in different theory assumptions.
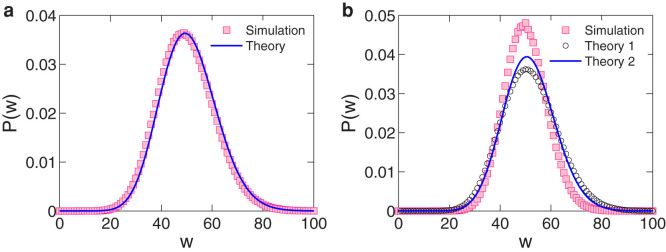
(a), For the classic ER random networks with rewiring probability PR = 1, PDF of flow P(w) obtained from direct simulation (red squares) and self-consistent equation (solid blue line). (b), PDF of flow P(w) from direct simulation (red squares), from theory without taking into account spatial degree correlation (black circles), and from theory with degree-degree correlation (solid blue line).
Effect of degree-degree correlation
The probability pΔ that a given node i and one of its neighbors j share a neighbor in the ER-random network of link probability p is p2. For a mobile network in a two-dimensional domain, this probability is given by
 |
where r denotes the distance between node i and its neighboring node j, and Sij (r) is the overlapping area of i and j's communication circles, which is given by
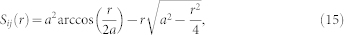 |
Numerical calculation reveals that 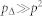 , indicating that a node's degree is much more likely to have a value similar to that of its neighbor, giving rise to a strong correlation between the degrees of neighboring nodes, or the phenomenon of degree-degree correlation. Namely, node i's degree k is correlated with its neighbor's degree kn, the so-called k-kn correlation. In addition, the degrees of the neighboring nodes of i are also correlated, leading to the so-called kn-kn correlation. Since the effect of cutoff of the communication circle by a boundary makes the analysis on spatial degree correlation extraordinarily complicated, here we neglect the effect of the boundary or, equivalently, we focus on mobile networks with periodic boundary conditions.
, indicating that a node's degree is much more likely to have a value similar to that of its neighbor, giving rise to a strong correlation between the degrees of neighboring nodes, or the phenomenon of degree-degree correlation. Namely, node i's degree k is correlated with its neighbor's degree kn, the so-called k-kn correlation. In addition, the degrees of the neighboring nodes of i are also correlated, leading to the so-called kn-kn correlation. Since the effect of cutoff of the communication circle by a boundary makes the analysis on spatial degree correlation extraordinarily complicated, here we neglect the effect of the boundary or, equivalently, we focus on mobile networks with periodic boundary conditions.
For convenience, we classify the neighbors of node j into two classes with respect to the focal node i: nj1 neighbors in the overlapping area Sij(r) (i.e., the regions shared by these nodes and i) and the remaining nj2 = kj − nj1 neighbors in the non-overlapping area. The PDF of nj1 is
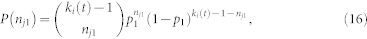 |
where p1 = Sij (r)/(πa2). The number nj2 of neighbors in the non-overlapping area has the PDF as
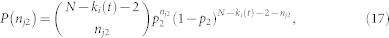 |
where p2 = (πa2 − Sij(r))/L2. The degree distribution of node j is given by
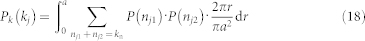 |
where kj = nj1 + nj2. In the high-velocity regime, the self-consistent equation method can be adopted to solving P(w) by substituting Pk(kn) from Eq. (12) into Eq. (18), while the quantity Pk(k) in Eq. (13) can still be determined by Eq. (11). Figure 8b shows the flow distribution P(w) obtained from direct simulation and from self-consistent theory with or without the k-kn correlation. We observe a better agreement between simulation and theory when the k-kn correlation is taken into account.
It is mathematically difficult to consider both the k-kn and kn-kn correlations. Nonetheless, since the spatial degree correlation depends solely on the spatial distribution of the nodes, which is completely random regardless of the velocity, the combined effect of the two kinds of correlations on nex has little dependence on the actual value of the velocity. Consequently, the non-monotonous behavior of extreme events caused by the boundary effect should persist even in realistic situations where both types of degree-degree correlations are present, and we expect the theory of mobility-based control developed in the main text to be generally valid.
Author Contributions
Y.C.L. devised the research project. Y.Z.C. performed numerical simulations. Y.Z.C., Z.G.H. and Y.C.L. analyzed the results. Y.Z.C. and Y.C.L. wrote the paper.
Acknowledgments
We thank Prof. W.-X. Wang and Prof. L. Huang for helpful discussions. This work was partially supported by AFOSR under Grant No. FA9550-10-1-0083, by NSF under Grant No. CDI-1026710 and by ARO under Grant No. W911NF-14-1-0504.
References
- Noh J. D. & Rieger H. Random walks on complex networks. Phys. Rev. Lett. 92, 118701 (2004). [DOI] [PubMed] [Google Scholar]
- Tejedor V., Bénichou O. & Voituriez R. Global mean first-passage times of random walks on complex networks. Phys. Rev. E 80, 065104(R) (2009). [DOI] [PubMed] [Google Scholar]
- Nicolaides C., Cueto-Felgueroso L. & Juanes R. Anomalous physical transport in complex networks. Phys. Rev. E 82, 055101(R) (2010). [DOI] [PubMed] [Google Scholar]
- Zhao L., Lai Y.-C., Park K., & Ye N. Onset of traffic congestion in complex networks. Phys. Rev. E 71, 026125 (2005). [DOI] [PubMed] [Google Scholar]
- Wang W.-X., Wang B.-H., Hu B., Yan G. & Ou Q. General dynamics of topology and traffic on weighted technological networks. Phys. Rev. Lett. 94, 188702 (2005). [DOI] [PubMed] [Google Scholar]
- Yang H.-X., Wang W.-X., Xie Y.-B., Lai Y.-C. & Wang B.-W. Transportation dynamics on networks of mobile agents. Phys. Rev. E 83, 016102 (2011). [DOI] [PubMed] [Google Scholar]
- Goh K.-I., Kahng B. & Kim D. Universal behavior of load distribution in scale-free networks. Phys. Rev. Lett. 87, 278701 (2001). [DOI] [PubMed] [Google Scholar]
- Holme P. & Kim B. J. Vertex overload breakdown in evolving networks. Phys. Rev. E 65, 066109 (2002). [DOI] [PubMed] [Google Scholar]
- Guimerà R., Díaz-Guilera A., Vega-Redondo F., Cabrales A. & Arenas A. Optimal network topologies for local search with congestion. Phys. Rev. Lett. 89, 248701 (2002). [DOI] [PubMed] [Google Scholar]
- Sun J.-T., Wang S.-J., Huang Z.-G. & Wang Y.-H. Effect of degree correlations on networked traffic dynamics. Physica A 388, 3244–3248 (2009). [Google Scholar]
- Dong J.-Q. et al. Enhancing transport efficiency by hybrid routing strategy. Europhys. Lett. 99, 20007 (2012). [Google Scholar]
- Echenique P., Gómez-Gardeńes J. & Moreno Y. Improved routing strategies for internet traffic delivery. Phys. Rev. E 70, 056105 (2004). [DOI] [PubMed] [Google Scholar]
- Echenique P., Gómez-Gardeńes J. & Moreno Y. Dynamics of jamming transitions in complex networks. Europhys. Lett. 71, 325–331 (2005). [Google Scholar]
- deMenezes M. A. & Barabási A. L. Fluctuations in network dynamics. Phys. Rev. Lett. 92, 028701 (2004). [DOI] [PubMed] [Google Scholar]
- Duch J. & Arenas A. Scaling of fluctuations in traffic on complex networks. Phys. Rev. Lett. 96, 218702 (2006). [DOI] [PubMed] [Google Scholar]
- Meloni S., Gómez-Gardeńes J., Latora V. & Moreno Y. Scaling breakdown in flow fluctuations on complex networks. Phys. Rev. Lett. 100, 208701 (2008). [DOI] [PubMed] [Google Scholar]
- Eisler Z. & Kertesz J. Random walks on complex networks with inhomogeneous impact. Phys. Rev. E 71, 057104 (2005). [DOI] [PubMed] [Google Scholar]
- Yoon S., Yook S.-H. & Kim Y. Scaling property of flux fluctuations from random walks. Phys. Rev. E 76, 056104 (2007). [DOI] [PubMed] [Google Scholar]
- He S., Li S. & Ma H. R. Integrating fluctuations into distribution of resources in transportation networks. Eur. Phys. J. B 76, 31–36 (2010). [Google Scholar]
- Kishore V., Santhanam M. S. & Amritkar R. E. Extreme events on complex networks. Phys. Rev. Lett. 106, 188701 (2011). [DOI] [PubMed] [Google Scholar]
- Kujawski B., Tadić B. & Rodgers G. J. Preferential behaviour and scaling in diffusive dynamics on networks. New. J. Phys. 9, 154 (2007). [Google Scholar]
- Zhou Z. et al. Universality of flux-fluctuation law in complex dynamical systems. Phys. Rev. E 87, 012808 (2013). [DOI] [PubMed] [Google Scholar]
- Kishore V., Santhanam M. S. & Amritkar R. E. Extreme events and event size fluctuations in biased random walks on networks. Phys. Rev. E 85, 056120 (2012). [DOI] [PubMed] [Google Scholar]
- Kishore V., Sonawane A. R. & Santhanam M. S. Manipulation of extreme events on scale-free networks. Phys. Rev. E 88, 014801 (2013). [DOI] [PubMed] [Google Scholar]
- Shlesinger, M. F., Zaslavsky, G. M. & Frisch, U. (eds.). Lévy Flights and Related Topics in Physics, vol. 450 of Lecture Notes in Physics (Springer Verlag, Berlin, 1995). [Google Scholar]
- Penson K. A. & Górska K. Exact and explicit probability densities for one-sided lévy stable distributions. Phys. Rev. Lett. 105, 210604 (2010). [DOI] [PubMed] [Google Scholar]
- Erdös P. & Rényi A. On random graphs i. Publ. Math. Debrecen 6, 290–291 (1959). [Google Scholar]
- Gumbel E. J. Statistics of Extremes (Cambridge University, New York, 1958), first edn. [Google Scholar]
- Sabhapandit S. & Majumdar S. N. Density of near-extreme events. Phys. Rev. Lett. 98, 140201 (2007). [DOI] [PubMed] [Google Scholar]
- Skufca J. & Bollt E. Communication and synchronization in disconnected networks with dynamic topology: moving neighborhood networks. Math. Biosci. Eng. 1, 347–359 (2004). [DOI] [PubMed] [Google Scholar]
- Stilwell D. J., Bollt E. M. & Roberson D. G. Sufficient conditions for fast switching synchronization in time varying network topologies. SIAM J. Dyn. Sys. 5, 140–156 (2006). [Google Scholar]
- Kim B. S., Do Y. & Lai Y.-C. Emergence and scaling of synchronization in moving-agent networks with restrictive interactions. Phys. Rev. E 88, 042818 (2013). [DOI] [PubMed] [Google Scholar]
- Papadimitratos P. & Haas Z. J. Secure routing for mobile ad hoc networks. In: Proceedings of the SCS Commnication Networks and Distributed Systems Modeling and Simulation Conference (CNDS), vol. 625, 193–204 (KTH, 2007, Jul. 30-Aug. 1). [Google Scholar]
- Hu Y. C., Perrig A. & Johnson D. Packet leashes: a defense against wormhole attacks in wireless networks. In: INFOCOM 2003 - Twenty-Second Annual Joint Conference of the IEEE Computer and Communications. IEEE Societies, vol. 3, 1977–1986 (IEEE, 2003, Mar. 30-Apr. 3). [Google Scholar]
- Maheshwari R., Gao J. & Das S. R. Detecting wormhole attacks in wireless networks using connectivity information. In: INFOCOM 2007 - 26th IEEE International Conference on Computer Communications, 107–115 (IEEE, May6–122007). [Google Scholar]