Abstract
The asymmetric Hopfield model is used to simulate signaling dynamics in gene regulatory networks. The model allows for a direct mapping of a gene expression pattern into attractor states. We analyze different control strategies aimed at disrupting attractor patterns using selective local fields representing therapeutic interventions. The control strategies are based on the identification of signaling bottlenecks, which are single nodes or strongly connected clusters of nodes that have a large impact on the signaling. We provide a theorem with bounds on the minimum number of nodes that guarantee control of bottlenecks consisting of strongly connected components. The control strategies are applied to the identification of sets of proteins that, when inhibited, selectively disrupt the signaling of cancer cells while preserving the signaling of normal cells. We use an experimentally validated non-specific and an algorithmically-assembled specific B cell gene regulatory network reconstructed from gene expression data to model cancer signaling in lung and B cells, respectively. Among the potential targets identified here are TP53, FOXM1, BCL6 and SRC. This model could help in the rational design of novel robust therapeutic interventions based on our increasing knowledge of complex gene signaling networks.
Introduction
The vision behind systems biology is that complex interactions and emergent properties determine the behavior of biological systems. Many theoretical tools developed in the framework of spin glass models are well suited to describe emergent properties, and their application to large biological networks represents an approach that goes beyond pinpointing the behavior of a few genes or metabolites in a pathway. The Hopfield model [1] is a spin glass model that was introduced to describe neural networks, and that is solvable using mean field theory [2]. The asymmetric case, in which the interaction between the spins can be seen as directed, can also be exacty solved in some limits [3]. The model belongs to the class of attractor neural networks, in which the spins evolve towards stored attractor patterns, and it has been used to model biological processes of high current interest, such as the reprogramming of pluripotent stem cells [4]. Moreover, it has been suggested that a biological system in a chronic or therapy-resistant disease state can be seen as a network that has become trapped in a pathological Hopfield attractor [5]. A similar class of models is represented by Random Boolean Networks [6], which were proposed by Kauffman to describe gene regulation and expression states in cells [7]. Differences and similarities between the Kauffman-type and Hopfield-type random networks have been studied for many years [8]–[11].
In this paper, we consider an asymmetric Hopfield model built from real (even if incomplete [12], [13]) cellular networks, and we map the spin attractor states to gene expression data from normal and cancer cells. We will focus on the question of controling of a network's final state (after a transient period) using external local fields representing therapeutic interventions. To a major extent, the final determinant of cellular phenotype is the expression and activity pattern of all proteins within the cell, which is related to levels of mRNA transcripts. Microarrays measure genome-wide levels of mRNA expression that therefore can be considered a rough snapshot of the state of the cell. This state is relatively stable, reproducible, unique to cell types, and can differentiate cancer cells from normal cells, as well as differentiate between different types of cancer [14], [15]. In fact, there is evidence that attractors exist in gene expression states, and that these attractors can be reached by different trajectories rather than only by a single transcriptional program [16]. While the dynamical attractors paradigm has been originally proposed in the context of cellular developement, the similarity between cellular ontogenesis, i.e. the developement of different cell types, and oncogenesis, i.e. the process under which normal cells are transformed into cancer cells, has been recently emphasized [17]. The main hypothesis of this paper is that cancer robustness is rooted in the dynamical robustness of signaling in an underlying cellular network. If the cancerous state of rapid, uncontrolled growth is an attractor state of the system [18], a goal of modeling therapeutic control could be to design complex therapeutic interventions based on drug combinations [19] that push the cell out of the cancer attractor basin [20].
Many authors have discussed the control of biological signaling networks using complex external perturbations. Calzolari and coworkers considered the effect of complex external signals on apoptosis signaling [21]. Agoston and coworkers [22] suggested that perturbing a complex biological network with partial inhibition of many targets could be more effective than the complete inhibition of a single target, and explicitly discussed the implications for multi-drug therapies [23]. In the traditional approach to control theory [24], the control of a dynamical system consists in finding the specific input temporal sequence required to drive the system to a desired output. This approach has been discussed in the context of Kauffmann Boolean networks [25] and their attractor states [26]. Several studies have focused on the intrinsic global properties of control and hierarchical organization in biological networks [27], [28]. A recent study has focused on the minimum number of nodes that needs to be addressed to achieve the complete control of a network [29]. This study used a linear control framework, a matching algorithm [30] to find the minimum number of controllers, and a replica method to provide an analytic formulation consistent with the numerical study. Finally, Cornelius et al. [31] discussed how nonlinearity in network signaling allows reprogrammig a system to a desired attractor state even in the presence of contraints in the nodes that can be accessed by external control. This novel concept was explicitly applied to a T-cell survival signaling network to identify potential drug targets in T-LGL leukemia. The approach in the present paper is based on nonlinear signaling rules and takes advantage of some useful properties of the Hopfield formulation. In particular, by considering two attractor states we will show that the network separates into two types of domains which do not interact with each other. Moreover, the Hopfield framework allows for a direct mapping of a gene expression pattern into an attractor state of the signaling dynamics, facilitating the integration of genomic data in the modeling.
The paper is structured as follows. In Mathematical Model we summarize the model and review some of its key properties. Control Strategies describes general strategies aiming at selectively disrupting the signaling only in cells that are near a cancer attractor state. The strategies we have investigated use the concept of bottlenecks, which identify single nodes or strongly connected clusters of nodes that have a large impact on the signaling. In this section we also provide a theorem with bounds on the minimum number of nodes that guarantee control of a bottleneck consisting of a strongly connected component. This theorem is useful for practical applications since it helps to establish whether an exhaustive search for such minimal set of nodes is practical. In Cancer Signaling we apply the methods from Control Strategies to lung and B cell cancers. We use two different networks for this analysis. The first is an experimentally validated and non-specific network (that is, the observed interactions are compiled from many experiments conducted on heterogeneous cell types) obtained from a kinase interactome and phospho-protein database [32] combined with a database of interactions between transcription factors and their target genes [33]. The second network is cell-specific and was obtained using network reconstruction algorithms and transcriptional and post-translational data from mature human B cells [34]. The algorithmically reconstructed network is significantly more dense than the experimental one, and the same control strategies produce different results in the two cases. Finally, we close with Conclusions.
Methods
Mathematical Model
We define the adjacency matrix of a network  composed of
composed of  nodes as
nodes as
| (1) |
where  denotes a directed edge from node
denotes a directed edge from node 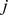 to node
to node  . The set of nodes in the network
. The set of nodes in the network 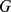 is indicated by
is indicated by 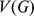 and the set of directed edges is indicated by
and the set of directed edges is indicated by 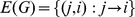 . (See Table 1 for a list of mathematical symbols used in the text.) The spin of node
. (See Table 1 for a list of mathematical symbols used in the text.) The spin of node  at time
at time  is
is 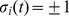 , and indicates an expresssed
, and indicates an expresssed 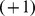 or not expressed
or not expressed 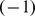 gene. We encode an arbitrary attractor state
gene. We encode an arbitrary attractor state 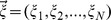 with
with 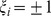 by defining the coupling matrix [1]
by defining the coupling matrix [1]
Table 1. Reference table for symbols.
| Symbol | Explanation |
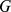
|
Set of nodes and directed edges (network) |
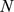
|
Number of nodes |
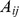
|
Adjacency matrix |
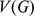
|
Set of nodes in 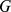
|
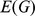
|
Set of edges in 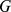
|
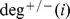
|
Outdegree/indegree of node 
|
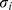
|
Spin of node  , , 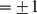
|
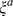
|
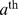 attractor attractor |
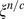
|
Normal/cancer attractor |
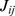
|
Coupling matrix |
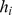
|
Total field at node 
|
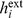
|
External field applied to node 
|
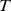
|
Temperature |
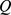
|
Set of source and effective source nodes |
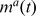
|
Magnetization along attractor  at time at time 
|
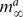
|
Steady-state magnetization along attractor 
|
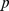
|
Number of attractors in coupling matrix |
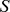
|
Set of similarity nodes |
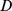
|
Set of differential nodes |
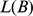
|
Control set of bottleneck 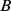
|
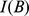
|
Impact of bottleneck 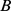
|

|
Cycle cluster |
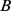
|
Size  bottleneck, where bottleneck, where 
|
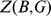
|
Set of critical nodes for bottleneck 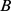 in network in network 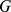
|
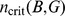
|
Critical number of nodes in bottleneck 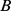 in network in network 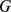
|
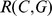
|
Set of externally influenced nodes |
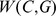
|
Set of intruder connections |
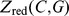
|
Reduced set of critical nodes |
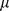
|
Minimum indegree of all nodes in a cycle cluster |
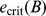
|
Critical efficiency of bottleneck 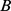
|
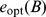
|
Optimal efficiency of bottleneck 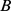
|
This table lists all important symbols introduced in the article with a brief explanation of its purpose.
| (2) |
The total field at node  is then
is then 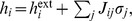 where
where 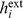 is the external field applied to node
is the external field applied to node  , which will be discussed below. The discrete-time update scheme is defined as
, which will be discussed below. The discrete-time update scheme is defined as
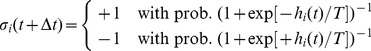 |
(3) |
where 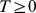 is an effective temperature. For the remainder of the paper, we consider the case of
is an effective temperature. For the remainder of the paper, we consider the case of 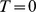 so that
so that 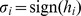 , and the spin is chosen randomly from
, and the spin is chosen randomly from 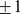 if
if 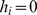 . For convenience, we take
. For convenience, we take 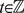 and
and 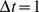 . Nodes can be updated synchronously, and synchronous updating can lead to limit cycles [9]. Nodes can also be updated separately and in random order (anynchronous updating), which does not result in limit cycles. All results presented in this paper use the synchronous update scheme.
. Nodes can be updated synchronously, and synchronous updating can lead to limit cycles [9]. Nodes can also be updated separately and in random order (anynchronous updating), which does not result in limit cycles. All results presented in this paper use the synchronous update scheme.
Source nodes (nodes with zero indegree) are fixed to their initial states by a small external field so that 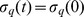 for all
for all 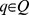 , where
, where 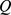 is the set of source nodes. However, the source nodes flip if directly targeted by an external field. Biologically, genes at the “top” of a network are assumed to be controlled by elements outside of the network.
is the set of source nodes. However, the source nodes flip if directly targeted by an external field. Biologically, genes at the “top” of a network are assumed to be controlled by elements outside of the network.
In application, two attractors are needed. Define these states as 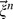 and
and 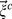 , the normal state and cancer state, respectively. The magnetization along attractor state
, the normal state and cancer state, respectively. The magnetization along attractor state  is
is
| (4) |
Note that if 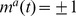 ,
, 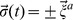 . We also define the steady state magnetization along state
. We also define the steady state magnetization along state  as
as
| (5) |
There are two ways to model normal and cancer cells. One way is to simply define a different coupling matrix for each attractor state  ,
,
| (6) |
Alternatively, both attractor states can be encoded in the same coupling matrix,
| (7) |
Systems using Eqs. 6 and 7 will be referred to as the one attractor state (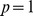 ) and two attractor state (
) and two attractor state (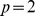 ) systems, respectively. Eqs. 6 and 7 are particular cases of the general Hopfield form [1]
) systems, respectively. Eqs. 6 and 7 are particular cases of the general Hopfield form [1]
| (8) |
where 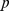 is the number of attractor states, often taken to be large. An interesting property emerges when
is the number of attractor states, often taken to be large. An interesting property emerges when 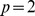 , however. Consider a simple network composed of two nodes, with only one edge
, however. Consider a simple network composed of two nodes, with only one edge 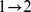 with attractor states
with attractor states 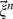 and
and 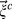 , and
, and 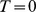 . The only nonzero entry of the matrix
. The only nonzero entry of the matrix 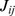 is
is
| (9) |
Note that if 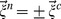 ,
, 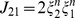 . In either case, by Eq. 3 we have
. In either case, by Eq. 3 we have
| (10) |
that is, the spin of node 2 at a given time step will be driven to match the attractor state of node 1 at the previous time step. However, if 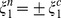 and
and 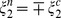 ,
, 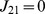 . This gives
. This gives
 |
(11) |
In this case, node 2 receives no input from node 1. Nodes 1 and 2 have become effectively disconnected.
This motivates new designations for node types. We define similarity nodes as nodes with 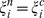 , and differential nodes as nodes with
, and differential nodes as nodes with 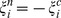 . We also define the set of similarity nodes
. We also define the set of similarity nodes 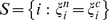 and the set of differential nodes
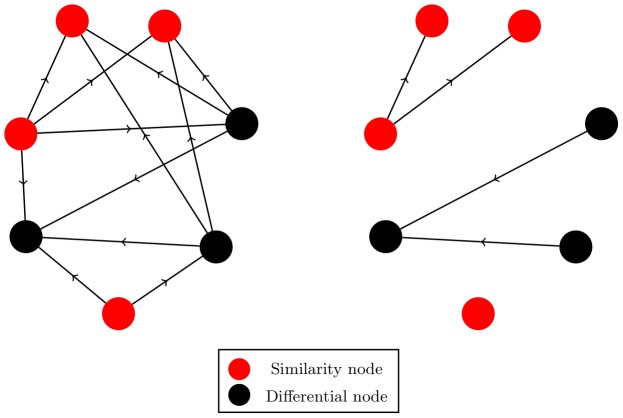
and the set of differential nodes 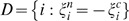 . Connections between two similarity nodes or two differential nodes remain in the network, whereas connections that link nodes of different types transmit no signals. The effective deletion of edges between nodes means that the original network fully separates into two subnetworks: one composed entirely of similarity nodes (the similarity network) and another composed entirely of differential nodes (the differential network), each of which can be composed of one or more separate weakly connected components (see Fig. 1). With this separation, new source nodes (effective sources) can be exposed in both the similarity and differential networks. For the remainder of this article,
. Connections between two similarity nodes or two differential nodes remain in the network, whereas connections that link nodes of different types transmit no signals. The effective deletion of edges between nodes means that the original network fully separates into two subnetworks: one composed entirely of similarity nodes (the similarity network) and another composed entirely of differential nodes (the differential network), each of which can be composed of one or more separate weakly connected components (see Fig. 1). With this separation, new source nodes (effective sources) can be exposed in both the similarity and differential networks. For the remainder of this article, 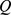 is the set of both source and effective source nodes in a given network.
is the set of both source and effective source nodes in a given network.
Figure 1. Network segregation for two attractor states (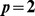 ).
).
Every edge that connects a similarity node to a differential node or a differential node to a similarity node transmits no signal. This means that the signaling in the right network shown above is identical to that of the left network. Because the goal is to leave normal cells unaltered while damaging cancer cells as much as possible, all similarity nodes can be safely ignored, and searches and simulations only need to be done on the differential subnetwork.
Control Strategies
The strategies presented below focus on selecting the best single nodes or small clusters of nodes to control, ranked by how much they individually change 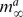 . In application, however, controlling many nodes is necessary to achieve a sufficiently changed
. In application, however, controlling many nodes is necessary to achieve a sufficiently changed 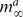 . The effects of controlling a set of nodes can be more than the sum of the effects of controlling individual nodes, and predicting the truly optimal set of nodes to target is computationally difficult. Here, we discuss heuristic strategies for controlling large networks where the combinatorial approach is impractical.
. The effects of controlling a set of nodes can be more than the sum of the effects of controlling individual nodes, and predicting the truly optimal set of nodes to target is computationally difficult. Here, we discuss heuristic strategies for controlling large networks where the combinatorial approach is impractical.
For both 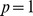 and
and 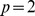 , simulating a cancer cell means that
, simulating a cancer cell means that 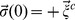 , and likewise for normal cells. Although the normal and cancer states are mathematically interchangeable, biologically we seek to decrease
, and likewise for normal cells. Although the normal and cancer states are mathematically interchangeable, biologically we seek to decrease 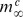 as much as possible while leaving
as much as possible while leaving 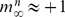 . By “network control” we thus mean driving the system away from its initial state of
. By “network control” we thus mean driving the system away from its initial state of 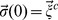 with
with 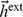 . Controlling individual nodes is achieved by applying a strong field (stronger than the magnitude of the field due to the node's upstream neighbors) to a set of targeted nodes
. Controlling individual nodes is achieved by applying a strong field (stronger than the magnitude of the field due to the node's upstream neighbors) to a set of targeted nodes 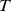 so that
so that
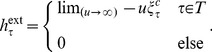 |
(12) |
This ensures that the drug field can always overcome the field from neighboring nodes.
In application, similarity nodes are never deliberately directly targeted, since changing their state would adversely affect both normal and cancer cells. Roughly 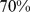 of the nodes in the networks surveyed are similarity nodes, so the search space is reduced. For
of the nodes in the networks surveyed are similarity nodes, so the search space is reduced. For 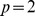 , the effective edge deletion means that only the differential network in cancer cells needs to be simulated to determine the effectiveness of
, the effective edge deletion means that only the differential network in cancer cells needs to be simulated to determine the effectiveness of 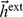 . For
. For 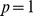 , however, there may be some similarity nodes that receive signals from upstream differential nodes. In this case, the full effect of
, however, there may be some similarity nodes that receive signals from upstream differential nodes. In this case, the full effect of 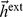 can be determined only by simulating all differential nodes as well as any similarity nodes downstream of differential nodes. All following discussion assumes that all nodes examined are differential, and therefore targetable, for both
can be determined only by simulating all differential nodes as well as any similarity nodes downstream of differential nodes. All following discussion assumes that all nodes examined are differential, and therefore targetable, for both 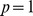 and
and 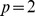 . The existence of similarity nodes for
. The existence of similarity nodes for 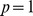 only limits the set of targetable nodes.
only limits the set of targetable nodes.
Directed acyclic networks
Full control of a directed acyclic network is achieved by forcing 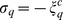 for all
for all 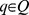 . This guarantees
. This guarantees  . Suppose that nodes
. Suppose that nodes  in an acyclic network have always been fixed away from the cancer state, that is,
in an acyclic network have always been fixed away from the cancer state, that is,  . For any node
. For any node  to have
to have 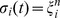 , it is sufficient to have either
, it is sufficient to have either 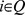 or
or 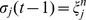 for all
for all 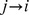 ,
, 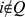 . Because there are no cycles present, all upstream paths of sufficent length terminate at a source. Because the spin of all nodes
. Because there are no cycles present, all upstream paths of sufficent length terminate at a source. Because the spin of all nodes 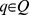 point away from the cancer attractor state, all nodes downstream must also point away from the cancer attractor state. Thus, for acyclic networks, forcing
point away from the cancer attractor state, all nodes downstream must also point away from the cancer attractor state. Thus, for acyclic networks, forcing 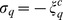 guarantees
guarantees 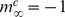 . The complications that arise from cycles are discussed in the next subsubsection. However, controlling nodes in
. The complications that arise from cycles are discussed in the next subsubsection. However, controlling nodes in 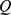 may not be the most efficient way to push the system away from the cancer basin of attraction and, depending on the control limitations, it may not be possible. If minimizing the number of controllers is required, searching for the most important bottlenecks is a better strategy.
may not be the most efficient way to push the system away from the cancer basin of attraction and, depending on the control limitations, it may not be possible. If minimizing the number of controllers is required, searching for the most important bottlenecks is a better strategy.
Consider a directed network 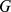 and an initially identical copy,
and an initially identical copy, 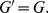 If removing node
If removing node  (and all connections to and from
(and all connections to and from  ) from
) from 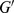 decreases the indegree of at least one node
decreases the indegree of at least one node 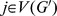 ,
, 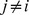 , to less than half of its indegree in network
, to less than half of its indegree in network 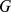 ,
, 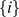 is a size 1 bottleneck. The bottleneck control set of bottleneck
is a size 1 bottleneck. The bottleneck control set of bottleneck 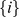 ,
, 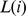 , is defined algorithmically as follows: (1) Begin a set
, is defined algorithmically as follows: (1) Begin a set 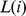 with the current bottleneck
with the current bottleneck  so that
so that 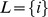 ; (2) Remove bottleneck
; (2) Remove bottleneck 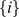 from network
from network 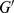 ; (3) Append
; (3) Append 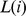 with all nodes
with all nodes 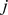 with current indegree that is less than half of that from the original network
with current indegree that is less than half of that from the original network 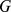 ; (4) Remove all nodes
; (4) Remove all nodes 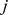 from the network
from the network 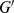 . If additional nodes in
. If additional nodes in 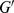 have their indegree reduced to below half of their indegree in
have their indegree reduced to below half of their indegree in 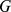 , go to step 3. Otherwise, stop. The impact of the bottleneck i,
, go to step 3. Otherwise, stop. The impact of the bottleneck i, 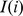 , is defined as
, is defined as
| (13) |
where 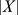 is the cardinality of the set
is the cardinality of the set 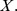 The impact of a bottleneck is the minimum number of nodes that are guaranteed to switch away from the cancer state when the bottleneck is forced away from the cancer state.
The impact of a bottleneck is the minimum number of nodes that are guaranteed to switch away from the cancer state when the bottleneck is forced away from the cancer state.
The impact is used to rank the size 1 bottlenecks by importance, with the most important as those with the largest impact. In application, when searching for nodes to control, any size 1 bottleneck 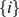 that appears in the bottleneck control set of a different size 1 bottleneck
that appears in the bottleneck control set of a different size 1 bottleneck 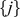 can be ignored, since fixing
can be ignored, since fixing 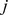 to the normal state fixes
to the normal state fixes  to the normal state as well. Note that the definition given above in terms of
to the normal state as well. Note that the definition given above in terms of 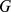 and
and  avoids miscounting in the impact of a bottleneck.
avoids miscounting in the impact of a bottleneck.
The network in Fig. 2, for example, has three sources (nodes 1, 2 and 3), but one important bottleneck (node 6). If full damage, i.e. 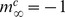 , is required, then control of all source nodes is necessary. If minimizing the number of directly targeted nodes is important and
, is required, then control of all source nodes is necessary. If minimizing the number of directly targeted nodes is important and 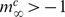 can be tolerated, then control of the bottleneck node 6 is a better choice.
can be tolerated, then control of the bottleneck node 6 is a better choice.
Figure 2. A directed acyclic network.
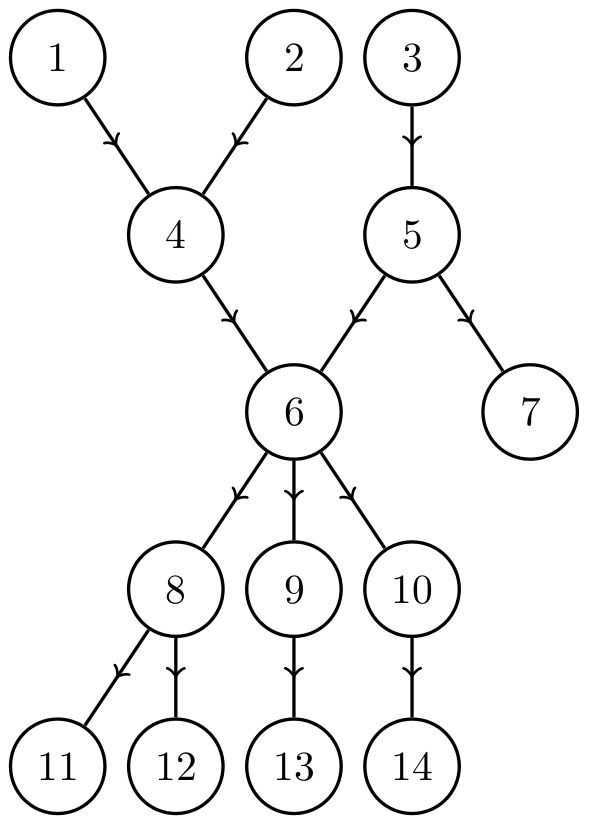
Controlling all three source nodes (nodes 1, 2 and 3) guarantees full control of the network, but are ineffective when targeted individually. The best single node to control in this network is node 6 because it directly controls all downstream nodes.
Directed cycle-rich networks
Not all networks can be fully controlled at 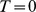 by controlling the source nodes, however. If there is a cycle present, paths of infinite length exist and the final state of the system may depend on the initial state, causing parts of the network to be hysteretic. Controlling only sources in a general directed network thus does not guarantee
by controlling the source nodes, however. If there is a cycle present, paths of infinite length exist and the final state of the system may depend on the initial state, causing parts of the network to be hysteretic. Controlling only sources in a general directed network thus does not guarantee 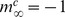 unless the system begins with
unless the system begins with 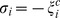 .
.
Define a cycle cluster,  , as a strongly connected subnetwork of a network
, as a strongly connected subnetwork of a network 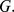 The network in Fig. 3, for example, has one cycle cluster with nodes
The network in Fig. 3, for example, has one cycle cluster with nodes 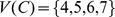 . If the network begins with
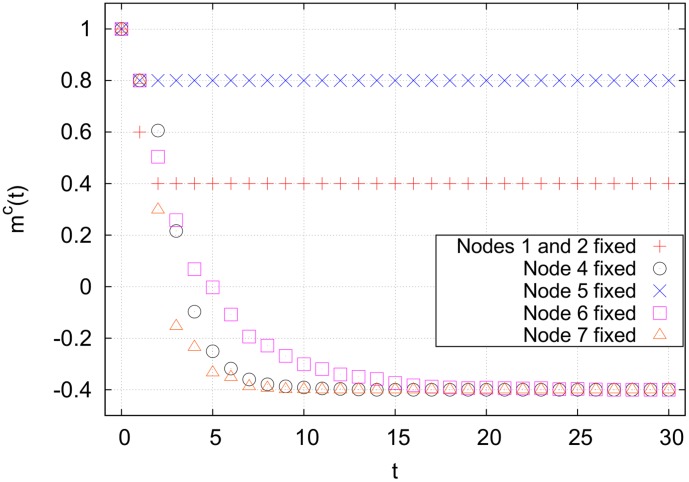
. If the network begins with 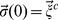 , forcing both source nodes away from the cancer state does nothing to the nodes downsteam of node 3 (see Fig. 4). This is because the indegree
, forcing both source nodes away from the cancer state does nothing to the nodes downsteam of node 3 (see Fig. 4). This is because the indegree 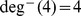 , and a majority of the nodes connecting to node 4 are in the cancer attractor state. At
, and a majority of the nodes connecting to node 4 are in the cancer attractor state. At 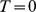 , cycle clusters with high connectivity tend to block incoming signals from outside of the cluster, resulting in an insurmountable activation barrier.
, cycle clusters with high connectivity tend to block incoming signals from outside of the cluster, resulting in an insurmountable activation barrier.
Figure 3. A network in which nodes 4, 5, 6 and 7 compose a single cycle cluster.
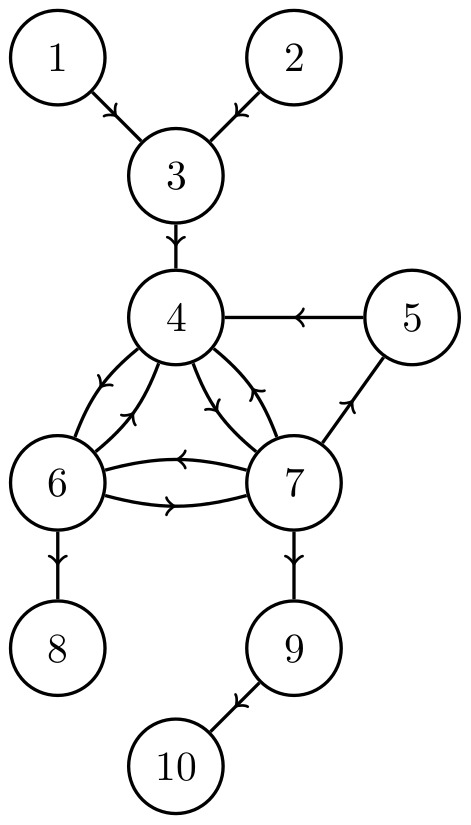
The high connectivity of node 4 prevents any changes made to the spin of nodes 1–3 from propagating downstream. The only way to indirectly control nodes 8–10 is to target nodes inside of the cycle cluster. Targeting node 4, 6 or 7 will cause the entire cycle cluster to flip away from its initial state, guaranteeing control of nodes 4–10 (see Fig. 4).
Figure 4. Cancer magnetization from targeting various nodes in the network shown in Fig. 3, averaged over 10,000 runs.
The averaging removes fluctuations due to the random flipping of nodes with  Targeting node 7 results in the quickest stabilization, but targeting any one of nodes 4, 6 or 7 results in the same final magnetization.
Targeting node 7 results in the quickest stabilization, but targeting any one of nodes 4, 6 or 7 results in the same final magnetization.
The most effective single node to control in this network is any one of nodes 4, 6 or 7. Forcing any of these away from the cancer attractor state will eventually cause the entire cycle cluster to flip away from the cancer state, and all nodes downstream will flip as well, as shown in Fig. 4. The cycle cluster here acts as a sort of large, hysteretic bottleneck. We now generalize the concept of bottlenecks.
Define a size
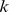 bottleneck in a network
bottleneck in a network 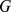 to be a cycle cluster
to be a cycle cluster 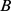 with
with 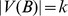 which, when removed from
which, when removed from 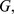 reduces the indegree of at least one node
reduces the indegree of at least one node 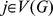 ,
, 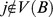 to less than half of its original indegree. Other than now using the set of nodes
to less than half of its original indegree. Other than now using the set of nodes 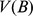 rather than a single node set, the above algorithm for finding the bottleneck control set remains unchanged. In Fig. 3, for instance,
rather than a single node set, the above algorithm for finding the bottleneck control set remains unchanged. In Fig. 3, for instance, 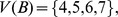
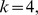
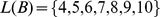 , and
, and 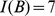 . With this more general definition, we note that controlling any size
. With this more general definition, we note that controlling any size 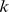 bottleneck
bottleneck 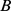 guarantees control of all size 1 bottlenecks
guarantees control of all size 1 bottlenecks 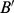 in the control set of
in the control set of 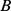 for all
for all 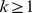 .
.
For any bottleneck 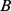 of size
of size 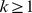 in a network
in a network 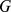 , define the set of critical nodes,
, define the set of critical nodes, 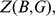 as the set of nodes
as the set of nodes 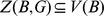 of minimum cardinality that, when controlled, guarantees full control of all nodes
of minimum cardinality that, when controlled, guarantees full control of all nodes 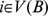 after a transient period. Also define the critical number of nodes as
after a transient period. Also define the critical number of nodes as 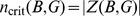 . Thus, for the network in Fig. 3,
. Thus, for the network in Fig. 3, 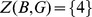 ,
, 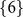 , or
, or  , and
, and 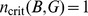 .
.
In general, however, more than one node in a cycle cluster may need to be targeted to control the entire cycle cluster. Fig. 5 shows a cycle cluster (composed of nodes 2–10) that cannot be controlled by targeting any single node. The precise value of 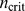 for a given cycle cluster
for a given cycle cluster  depends on its topology as well as the edges connecting nodes from outside of
depends on its topology as well as the edges connecting nodes from outside of  to the nodes inside of
to the nodes inside of 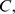 and finding
and finding 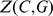 can be difficult. We present a theorem that puts bounds on
can be difficult. We present a theorem that puts bounds on 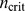 to help determine whether a search for
to help determine whether a search for 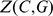 is practical.
is practical.
Figure 5. A network with a cycle cluster  , composed of nodes 2–10, that cannot be controlled at
, composed of nodes 2–10, that cannot be controlled at  by controlling any single node.
by controlling any single node.
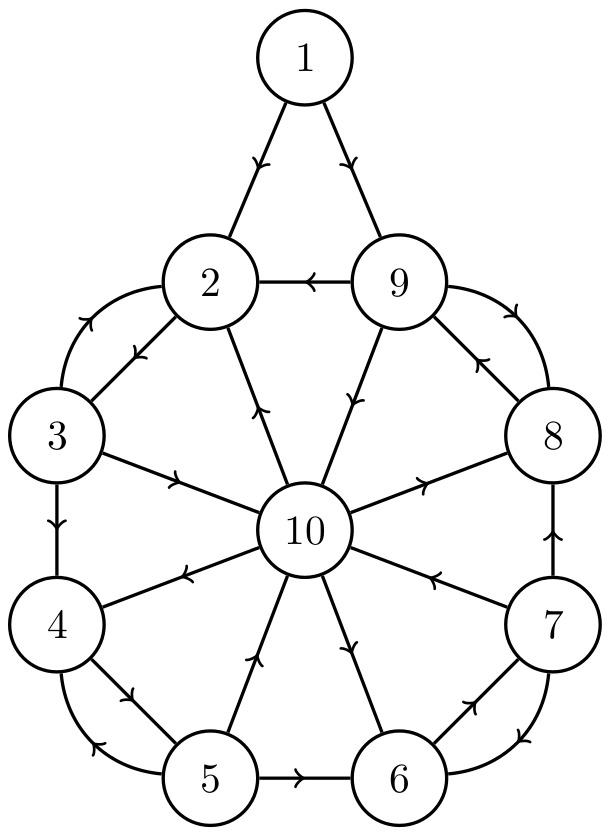
Here, the set of externally influenced nodes is 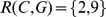 , the set of intruder connections is
, the set of intruder connections is 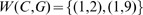 , the reduced set of critical nodes is
, the reduced set of critical nodes is 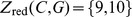 , the minimum indegree is
, the minimum indegree is 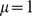 and the number of nodes in the cycle cluster is
and the number of nodes in the cycle cluster is 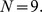 By Eq. 18, this gives the bounds of the critical number of nodes to be
By Eq. 18, this gives the bounds of the critical number of nodes to be 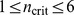 .
.
Theorem: Suppose a network 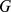 contains a cycle cluster
contains a cycle cluster 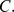 Define the set of externally influenced nodes
Define the set of externally influenced nodes
| (14) |
the set of intruder connections
| (15) |
and the reduced set of critical nodes
| (16) |
If 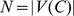 and
and
| (17) |
where 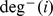 is computed ignoring intruder connections, then
is computed ignoring intruder connections, then
| (18) |
where
| (19) |
Proof: First, prove the lower limit of Eq. 18. Let  be a cycle cluster in a network
be a cycle cluster in a network 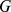 with
with 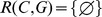 . (A cycle cluster in a network with
. (A cycle cluster in a network with 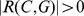 will have the same or higher activation barrier for any node in the cluster than the same cycle cluster in a network with
will have the same or higher activation barrier for any node in the cluster than the same cycle cluster in a network with 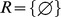 . Since we are examining the lower limit of Eq. 18, we consider the case with the lowest activation barrier. Any externally influenced nodes cause
. Since we are examining the lower limit of Eq. 18, we consider the case with the lowest activation barrier. Any externally influenced nodes cause 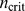 to either increase or remain the same.) For any node
to either increase or remain the same.) For any node  to be able to flip away from the cancer state (although not necessarily remain there), we must have that
to be able to flip away from the cancer state (although not necessarily remain there), we must have that 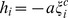 for
for 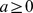 , meaning that at least half of the nodes upstream of
, meaning that at least half of the nodes upstream of  must point away from the cancer state. The node
must point away from the cancer state. The node  requiring the smallest number of upstream nodes to be in the normal state is the node that satisfies
requiring the smallest number of upstream nodes to be in the normal state is the node that satisfies 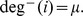 Controlling less than
Controlling less than 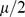 nodes will leave all uncontrolled nodes with a field in the cancer direction, and no more flips will occur. Thus,
nodes will leave all uncontrolled nodes with a field in the cancer direction, and no more flips will occur. Thus,
| (20) |
For the upper limit of Eq. 18, consider a complete clique on 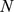 nodes,
nodes, 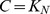 (that is,
(that is, 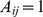 for all
for all 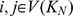 , including self loops) in a network
, including self loops) in a network 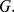 First, let there be no connections to any nodes in
First, let there be no connections to any nodes in  from outside of
from outside of  so that
so that 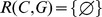 . For odd
. For odd 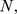 forcing
forcing 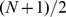 nodes away from the cancer state will result in the field
nodes away from the cancer state will result in the field
| (21) |
for all nodes 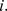 After one time step, all nodes will flip away from the cancer state. For even
After one time step, all nodes will flip away from the cancer state. For even 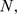 forcing
forcing 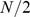 nodes away from the cancer state will result in the field
nodes away from the cancer state will result in the field
| (22) |
for all nodes 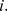 At the next time step, the unfixed nodes will pick randomly between the normal and cancer state. If at least one of these nodes makes the transition away from the cancer state, the field at all other nodes will point away from the cancer direction. The system will then require one more time step to completely settle to
At the next time step, the unfixed nodes will pick randomly between the normal and cancer state. If at least one of these nodes makes the transition away from the cancer state, the field at all other nodes will point away from the cancer direction. The system will then require one more time step to completely settle to 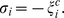 . Thus, we have that for
. Thus, we have that for 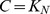 in a network
in a network 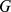 with
with  ,
,
| (23) |
 with
with 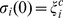 gives the largest activation barrier for any cycle cluster on
gives the largest activation barrier for any cycle cluster on 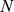 nodes with
nodes with 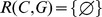 to switch away from the cancer attractor state. A general cycle cluster
to switch away from the cancer attractor state. A general cycle cluster  with any topology on
with any topology on 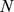 nodes with
nodes with 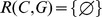 in a network
in a network 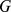 will have
will have 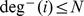 for all nodes
for all nodes  , and so we have the upper bound
, and so we have the upper bound
| (24) |
thus proving Eq. 18 for the special case of 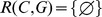 .
.
Now consider a cycle cluster  on
on 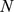 nodes in a network
nodes in a network 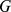 with
with 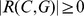 . Suppose all nodes in
. Suppose all nodes in 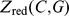 are fixed away from the cancer state. By Eq. 24,
are fixed away from the cancer state. By Eq. 24, 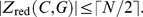 For any node
For any node 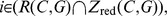
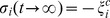 is guaranteed because it has already been directly controlled. Any node
is guaranteed because it has already been directly controlled. Any node 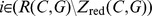 has some incoming connections from nodes
has some incoming connections from nodes 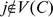 , and these connections could increase the activation barrier enough such that fixing
, and these connections could increase the activation barrier enough such that fixing 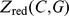 is not enough to guarantee
is not enough to guarantee 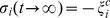 . To ensure that any node
. To ensure that any node 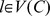 points away from the cancer state, it is sufficient to fix all nodes
points away from the cancer state, it is sufficient to fix all nodes 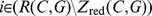 as well as
as well as 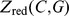 away from the cancer state. This increases
away from the cancer state. This increases 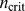 by at most
by at most 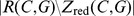 , leaving
, leaving
| (25) |
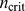 can never exceed
can never exceed 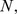 however, because directly controlling every node results in controlling
however, because directly controlling every node results in controlling 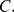 We can thus say that
We can thus say that
| (26) |
Finally, combining the upper limit in Eq. 26 with the lower limit from Eq. 20 gives Eq. 18. ▪
There can be more than one 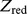 for a given cycle cluster. Note that the tightest constraints on
for a given cycle cluster. Note that the tightest constraints on 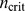 in Eq. 18 come from using the
in Eq. 18 come from using the 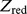 with the largest overlap with
with the largest overlap with 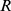 . If finding
. If finding 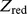 is too difficult, an overestimate for the upper limit of
is too difficult, an overestimate for the upper limit of 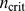 can be made by assuming that
can be made by assuming that 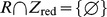 so that
so that
| (27) |
The cycle cluster in Fig. 5 has 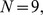
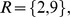
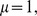 and one of the reduced sets of critical nodes is
and one of the reduced sets of critical nodes is 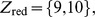 so
so 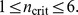 It can be shown through an exhaustive search that for this network
It can be shown through an exhaustive search that for this network 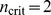 , and the set of critical nodes is
, and the set of critical nodes is 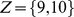 (see Fig. 6). Here,
(see Fig. 6). Here, 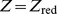 , although this is not always the case. Because the cycle cluster has 9 nodes and
, although this is not always the case. Because the cycle cluster has 9 nodes and 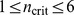 , at most
, at most 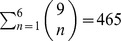 simulations are needed to find at least one solution for
simulations are needed to find at least one solution for 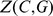 . However, the maximum number of simulations required to find
. However, the maximum number of simulations required to find 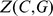 increases exponentially and for larger networks the problem quickly becomes intractable.
increases exponentially and for larger networks the problem quickly becomes intractable.
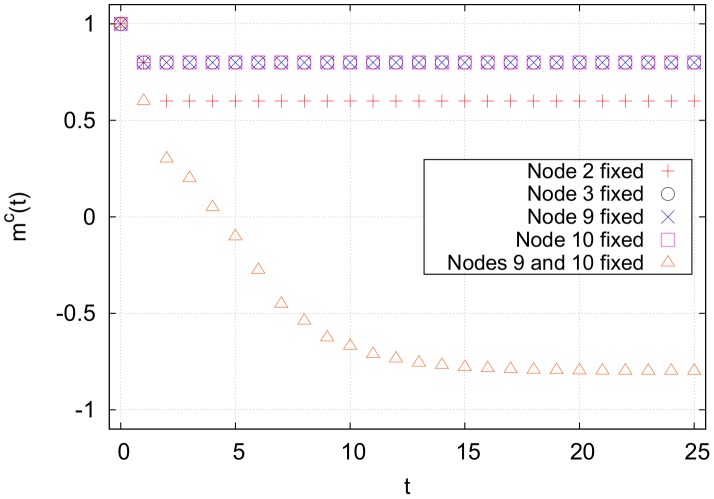
Figure 6. Magnetization for network from Fig. 5, averaged over 10,000 runs.
There is no single node to target that will control the cycle cluster, but fixing nodes 9 and 10 results in full control of the cycle cluster, leaving only node 1 in the cancer state. This means 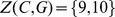 and
and 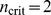 .
.
One heuristic strategy for controlling cycle clusters is to look for size 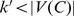 bottlenecks inside of
bottlenecks inside of 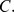 Bottlenecks of size
Bottlenecks of size 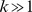 and average indegree
and average indegree 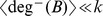 can contain high impact size
can contain high impact size 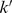 bottlenecks, where
bottlenecks, where 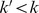 . Size
. Size 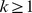 bottlenecks need to be compared to find the best set of nodes to target to reduce
bottlenecks need to be compared to find the best set of nodes to target to reduce 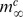 . Simply comparing the impact is insufficent because a cycle cluster with a large impact could also have a large
. Simply comparing the impact is insufficent because a cycle cluster with a large impact could also have a large 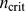 , requiring much more effort than its impact merits. Define the critical efficiency of a bottleneck
, requiring much more effort than its impact merits. Define the critical efficiency of a bottleneck 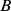 as
as
| (28) |
If the critical efficiency of a cycle cluster is much smaller than the impacts of size 1 bottlenecks from outside of the cycle cluster, the the cycle cluster can be safely ignored.
For some cycle clusters, however, not all of the nodes need to be controlled in order for a large portion of the nodes in the cycle cluster's control set to flip. Define the optimal efficiency of a bottleneck 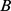 as
as
| (29) |
where 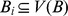 are size 1 bottlenecks and
are size 1 bottlenecks and 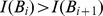 for all
for all 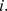 Note that for any size 1 bottleneck
Note that for any size 1 bottleneck 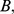
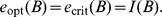 This quantity thus allows bottlenecks with very different properties (
This quantity thus allows bottlenecks with very different properties (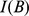 ,
, 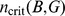 , or
, or 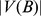 ) to be ranked against each other.
) to be ranked against each other.
All strategies presented above are designed to select the best individual or small group of nodes to target. Significant changes in the biological networks' magnetization require targeting many nodes, however. Brute force searches on the effect of larger combinations of nodes are typically impossible because the required number of simulations scales exponentially with the number of nodes. A crude Monte Carlo search is also numerically expensive, since it is difficult to sample an appreciable portion of the available space. One alternative is to take advantage of the bottlenecks that can be easily found, and rank all size 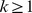 bottlenecks
bottlenecks 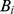 in an ordered list
in an ordered list 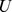 such that
such that
| (30) |
where
| (31) |
for all 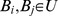 and fix the bottlenecks in the list in order. This is called the efficiency-ranked strategy. If all size
and fix the bottlenecks in the list in order. This is called the efficiency-ranked strategy. If all size 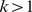 bottlenecks are ignored, it is called the pure efficiency-ranked strategy, and if size
bottlenecks are ignored, it is called the pure efficiency-ranked strategy, and if size 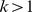 bottlenecks are included it is called the mixed efficiency-ranked strategy.
bottlenecks are included it is called the mixed efficiency-ranked strategy.
An effective polynomial-time algorithm for finding the top  nodes to fix, which we call the best+1 strategy (equivalent to a greedy algorithm), works as follows: (1) Begin with a seed set of nodes to fix,
nodes to fix, which we call the best+1 strategy (equivalent to a greedy algorithm), works as follows: (1) Begin with a seed set of nodes to fix, 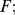 (2) Test the effect of fixing
(2) Test the effect of fixing 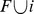 for all allowed nodes
for all allowed nodes 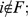 (3)
(3) 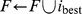 , where
, where 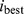 is the best node from all
is the best node from all  sampled; (4) If
sampled; (4) If 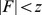 , go to step (2). Otherwise, stop. The seed set of nodes could be the single highest impact size 1 bottleneck in the network, or it could be the best set of
, go to step (2). Otherwise, stop. The seed set of nodes could be the single highest impact size 1 bottleneck in the network, or it could be the best set of  nodes (where
nodes (where 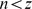 ) found from a brute force search.
) found from a brute force search.
Cancer Signaling
In application to biological systems, we assume that the magnetization of cell type  is related to the viability of cell type
is related to the viability of cell type 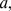 that is, the fraction of cells of type
that is, the fraction of cells of type  that survives a drug treatment. It is reasonable to assume that the viability of cell type
that survives a drug treatment. It is reasonable to assume that the viability of cell type  ,
, 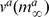 , is a monotonically increasing function of
, is a monotonically increasing function of 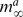 . Because the exact relationship is not known, we analyze the effect of external perturbations in terms of the final magnetizations.
. Because the exact relationship is not known, we analyze the effect of external perturbations in terms of the final magnetizations.
We need to use as few controllers as possible to sufficiently reduce 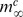 while leaving
while leaving 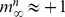 . In practical applications, however, one is limited in the set of druggable targets. All classes of drugs are constrained to act only on a specific set of biological components. For example, one class of drugs that is currently under intense research is protein kinase inhibitors [35]. In this case one has two constraints: the only nodes that can be targeted are those that correspond to kinases, and they can only be inhibited, i.e. turned off. We will use the example of kinase inhibitors to show how control is affected by such types of constraints. In the real systems studied, many differential nodes have only similarity nodes upstream and downstream of them, while the remaining differential nodes form one large cluster. This is not important for
. In practical applications, however, one is limited in the set of druggable targets. All classes of drugs are constrained to act only on a specific set of biological components. For example, one class of drugs that is currently under intense research is protein kinase inhibitors [35]. In this case one has two constraints: the only nodes that can be targeted are those that correspond to kinases, and they can only be inhibited, i.e. turned off. We will use the example of kinase inhibitors to show how control is affected by such types of constraints. In the real systems studied, many differential nodes have only similarity nodes upstream and downstream of them, while the remaining differential nodes form one large cluster. This is not important for 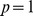 , but the effective edge deletion for
, but the effective edge deletion for 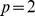 results in many islets, which are nodes
results in many islets, which are nodes  with
with 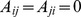 for all
for all 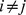 (self-loops allowed). Controlling islets requires targeting each islet individually. For
(self-loops allowed). Controlling islets requires targeting each islet individually. For 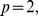 we concentrate on controlling only the largest weakly connected differential subnetwork. All final magnetizations are normalized by the total number of nodes in the full network, even if the simulations are only conducted on small portion of the network.
we concentrate on controlling only the largest weakly connected differential subnetwork. All final magnetizations are normalized by the total number of nodes in the full network, even if the simulations are only conducted on small portion of the network.
The data files for all networks and attractors analyzed below can be found in Supporting Information.
Lung Cell Network
The network used to simulate lung cells was built by combining the kinase interactome from PhosphoPOINT [32] with the transcription factor interactome from TRANSFAC [33]. Both of these are general networks that were constructed by compiling many observed pairwise interactions between components, meaning that if 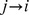 , at least one of the proteins encoded by gene
, at least one of the proteins encoded by gene 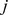 has been directly observed interacting with gene
has been directly observed interacting with gene  in experiments. This bottom-up approach means that some edges may be missing, but those present are reliable. Because of this, the network is sparse (
in experiments. This bottom-up approach means that some edges may be missing, but those present are reliable. Because of this, the network is sparse (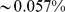 complete, see Table 2), resulting in the formation of many islets for
complete, see Table 2), resulting in the formation of many islets for 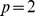 . Note also that this network presents a clear hierarchical structure, characteristic of biological networks [36], [37], with many “sink” nodes [38] that are targets of transcription factors and a relatively large cycle cluster originating from the kinase interactome.
. Note also that this network presents a clear hierarchical structure, characteristic of biological networks [36], [37], with many “sink” nodes [38] that are targets of transcription factors and a relatively large cycle cluster originating from the kinase interactome.
Table 2. General properties of the full networks.
| Properties | Lung | B cell |
| Nodes | 9073 | 4364 |
| Edges | 45635 | 55144 |
| Sources | 129 | 8 |
| Sinks | 8443 | 1418 |
| Av. outdegree | 5.03 | 12.64 |
| Max outdegree | 240 | 2372 |
| Max indegree | 68 | 196 |
| Self-loops | 238 | 0 |
| Undirected edges | 350 | 23386 |
| Diameter | 11 | 11 |
| Max cycle cluster | 401 | 2886 |
| Av. clustering coeff. [73] | 0.0544 | 0.2315 |
It is important to note that this is a non-specific network, whereas real gene regulatory networks can experience a sort of “rewiring” for a single cell type under various internal conditions [39]. In this analysis, we assume that the difference in topology between a normal and a cancer cell's regulatory network is negligible. The methods described here can be applied to more specialized networks for specific cell types and cancer types as these networks become more widely avaliable.
In our signaling model, the IMR-90 cell line [40], [41] was used for the normal attractor state, and the two cancer attractor states examined were from the A549 (adenocarcinoma) [42]–[46] and NCI-H358 (bronchioalveolar carcinoma) [42], [43] cell lines. Gene expression measurements from all referenced studies for a given cell line were averaged together to create a single attractor. The resulting magnetization curves for A549 and NCI-H358 are very similar, so the following analysis addresses only A549. The full network contains 9073 nodes, but only 1175 of them are differential nodes in the IMR-90/A549 model. In the unconstrained 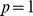 case, all 1175 differential nodes are candidates for targeting. Exhaustively searching for the best pair of nodes to control requires investigating 689725 combinations simulated on the full network of 9073 nodes. However, 1094 of the 1175 nodes are sinks (i.e. nodes
case, all 1175 differential nodes are candidates for targeting. Exhaustively searching for the best pair of nodes to control requires investigating 689725 combinations simulated on the full network of 9073 nodes. However, 1094 of the 1175 nodes are sinks (i.e. nodes  with outdegree
with outdegree 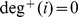 , ignoring self loops) and therefore have
, ignoring self loops) and therefore have 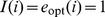 , which can be safely ignored. The search space is thus reduced to 81 nodes, and finding even the best triplet of nodes exhaustively is possible. Including constraints, only 31 nodes are differential kinases with
, which can be safely ignored. The search space is thus reduced to 81 nodes, and finding even the best triplet of nodes exhaustively is possible. Including constraints, only 31 nodes are differential kinases with 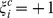 . This reduces the search space at the cost of increasing the minimum achievable
. This reduces the search space at the cost of increasing the minimum achievable 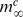 .
.
There is one important cycle cluster in the full network, and it is composed of 401 nodes. This cycle cluster has an impact of 7948 for 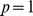 , giving a critical efficiency of at least
, giving a critical efficiency of at least 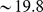 , and
, and 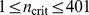 by Eq. 27. The optimal efficiency for this cycle cluster is
by Eq. 27. The optimal efficiency for this cycle cluster is 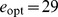 , but this is achieved for fixing the first bottleneck in the cluster. Additionally, this node is the highest impact size 1 bottleneck in the full network, and so the mixed efficiency-ranked results are identical to the pure efficiency-ranked results for the unconstrained
, but this is achieved for fixing the first bottleneck in the cluster. Additionally, this node is the highest impact size 1 bottleneck in the full network, and so the mixed efficiency-ranked results are identical to the pure efficiency-ranked results for the unconstrained 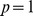 lung network. The mixed efficiency-ranked strategy was thus ignored in this case.
lung network. The mixed efficiency-ranked strategy was thus ignored in this case.
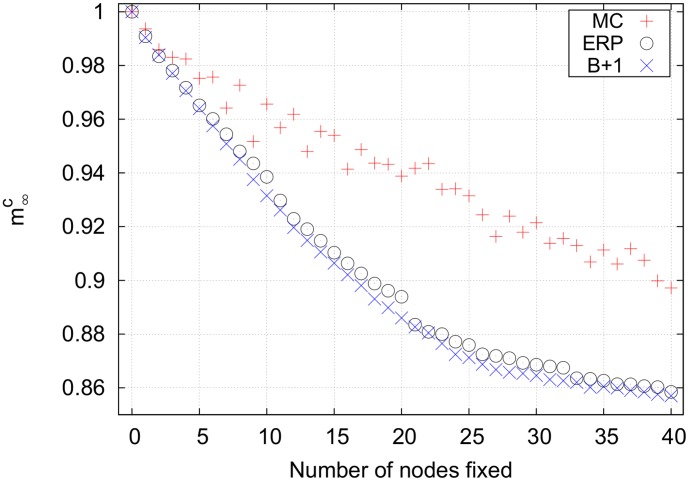
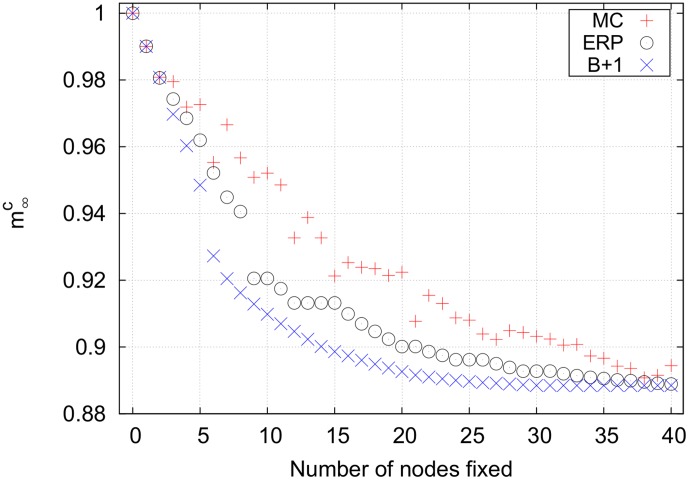
Fig. 7 shows the results for the unconstrained 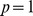 model of the IMR-90/A549 lung cell network. (All simulations were performed using MATLAB on a desktop computer. Running the simulations to make all curves shown below required approximately 12 hours.) The unconstrained
model of the IMR-90/A549 lung cell network. (All simulations were performed using MATLAB on a desktop computer. Running the simulations to make all curves shown below required approximately 12 hours.) The unconstrained 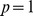 system has the largest search space, so the Monte Carlo strategy performs poorly. The best+1 strategy is the most effective strategy for controlling this network. The seed set of nodes used here was simply the size 1 bottleneck with the largest impact. Note that best+1 works better than effeciency-ranked. This is because best+1 includes the synergistic effects of fixing multiple nodes, while efficiency-ranked assumes that there is no overlap between the set of nodes downstream from multiple bottlenecks. Importantly, however, the efficiency-ranked method works nearly as well as best+1 and much better than Monte Carlo, both of which are more computationally expensive than the efficiency-ranked strategy.
system has the largest search space, so the Monte Carlo strategy performs poorly. The best+1 strategy is the most effective strategy for controlling this network. The seed set of nodes used here was simply the size 1 bottleneck with the largest impact. Note that best+1 works better than effeciency-ranked. This is because best+1 includes the synergistic effects of fixing multiple nodes, while efficiency-ranked assumes that there is no overlap between the set of nodes downstream from multiple bottlenecks. Importantly, however, the efficiency-ranked method works nearly as well as best+1 and much better than Monte Carlo, both of which are more computationally expensive than the efficiency-ranked strategy.
Figure 7. Final cancer magnetizations for an unconstrained search on the lung cell network using p = 1.
The efficiency-ranked strategy outperforms the relatively expensive Monte Carlo strategy. The best+1 strategy works best, although it requires the largest computational time. Note that the mixed efficiency-ranked curve is not shown because it is identical to the pure efficiency-ranked curve. Key for magnetization curves: MC = Monte Carlo, B+1 = best+1, ERP = pure efficiency-ranked, ERM = mixed efficiency-ranked, EX = exhausive search.
Fig. 8 shows the results for the unconstrained 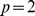 model of the IMR-90/A549 lung cell network. The search space for
model of the IMR-90/A549 lung cell network. The search space for 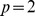 is much smaller than that for
is much smaller than that for 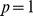 . The largest weakly connected differential subnetwork contains only 506 nodes (see Table 3), and the remaining differential nodes are islets or are in subnetworks composed of two nodes and are therefore unnecessary to consider. Of these 506 nodes, 450 are sinks. Fig. 9 shows the largest weakly connected component of the differential subnetwork, and the top five bottlenecks in the unconstrained case are shown in red. If limiting the search to differential kinases with
. The largest weakly connected differential subnetwork contains only 506 nodes (see Table 3), and the remaining differential nodes are islets or are in subnetworks composed of two nodes and are therefore unnecessary to consider. Of these 506 nodes, 450 are sinks. Fig. 9 shows the largest weakly connected component of the differential subnetwork, and the top five bottlenecks in the unconstrained case are shown in red. If limiting the search to differential kinases with 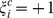 and ignoring all sinks,
and ignoring all sinks, 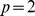 has 19 possible targets. There is only one cycle cluster in the largest differential subnetwork, containing 6 nodes. Like the
has 19 possible targets. There is only one cycle cluster in the largest differential subnetwork, containing 6 nodes. Like the 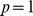 case, the optimal efficiency occurs when targeting the first node, which is the highest impact size 1 bottleneck. Because the mixed efficiency-ranked strategy gives the same results as the pure efficiency-ranked strategy, only the pure strategy was examined. The Monte Carlo strategy fares better in the unconstrained
case, the optimal efficiency occurs when targeting the first node, which is the highest impact size 1 bottleneck. Because the mixed efficiency-ranked strategy gives the same results as the pure efficiency-ranked strategy, only the pure strategy was examined. The Monte Carlo strategy fares better in the unconstrained 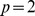 case because the search space is smaller. Additionally, the efficiency-ranked strategy does worse against the best+1 strategy for
case because the search space is smaller. Additionally, the efficiency-ranked strategy does worse against the best+1 strategy for 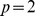 than it did for
than it did for 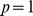 . This is because the effective edge deletion decreases the average indegree of the network and makes nodes easier to control indirectly. When many upstream bottlenecks are controlled, some of the downstream bottlenecks in the efficiency-ranked list can be indirectly controlled. Thus, controlling these nodes directly results in no change in the magnetization. This gives the plateaus shown for fixing nodes 9-10 and 12–15, for example.
. This is because the effective edge deletion decreases the average indegree of the network and makes nodes easier to control indirectly. When many upstream bottlenecks are controlled, some of the downstream bottlenecks in the efficiency-ranked list can be indirectly controlled. Thus, controlling these nodes directly results in no change in the magnetization. This gives the plateaus shown for fixing nodes 9-10 and 12–15, for example.
Figure 8. Final cancer magnetizations for an unconstrained search on the lung cell network using p = 2.
As in the p = 1 case, the efficiency-ranked strategy outperforms the expensive Monte Carlo search. The plateaus in the efficiency-ranked strategy when fixing 9–10, 12–15, 20–21, etc. nodes are a result of targeting bottlenecks that are already indirectly controlled.
Table 3. Properties of the largest weakly connected differential subnetworks for all cell types.
| Lung | B | |||||||
| Properties | I/A | I/H | N/D | N/F | N/L | M/D | M/F | M/L |
| Nodes | 506 | 667 | 684 | 511 | 841 | 621 | 457 | 742 |
| Edges | 846 | 1227 | 2855 | 1717 | 3962 | 2525 | 1501 | 3401 |
| Sources and effective sources | 30 | 34 | 12 | 11 | 9 | 9 | 9 | 12 |
| Sinks and effective sinks | 450 | 598 | 286 | 198 | 369 | 275 | 204 | 333 |
| Av. outdegree | 1.67 | 1.84 | 4.17 | 3.36 | 4.71 | 4.07 | 3.28 | 4.58 |
| Max outdegree | 52 | 51 | 155 | 143 | 336 | 138 | 132 | 292 |
| Max indegree | 8 | 10 | 40 | 29 | 49 | 35 | 27 | 44 |
| Self-loops | 27 | 31 | 0 | 0 | 0 | 0 | 0 | 0 |
| Undirected edges | 0 | 4 | 1238 | 738 | 1468 | 1000 | 596 | 1214 |
| Diameter | 9 | 9 | 12 | 15 | 12 | 13 | 14 | 12 |
| Max cycle cluster size | 6 | 3 | 351 | 280 | 397 | 305 | 199 | 337 |
| Av. clustering coeff | 0.0348 | 0.0421 | 0.1878 | 0.1973 | 0.2446 | 0.1751 | 0.1935 | 0.2389 |
I = IMR-90 (normal), A = A549 (cancer), H = NCI-H358 (cancer), N = Naïve (normal), M = Memory (normal), D = DLBCL (cancer), F = Follicular lymphoma (cancer), L = EBV-immortalized lymphoblastoma (cancer).
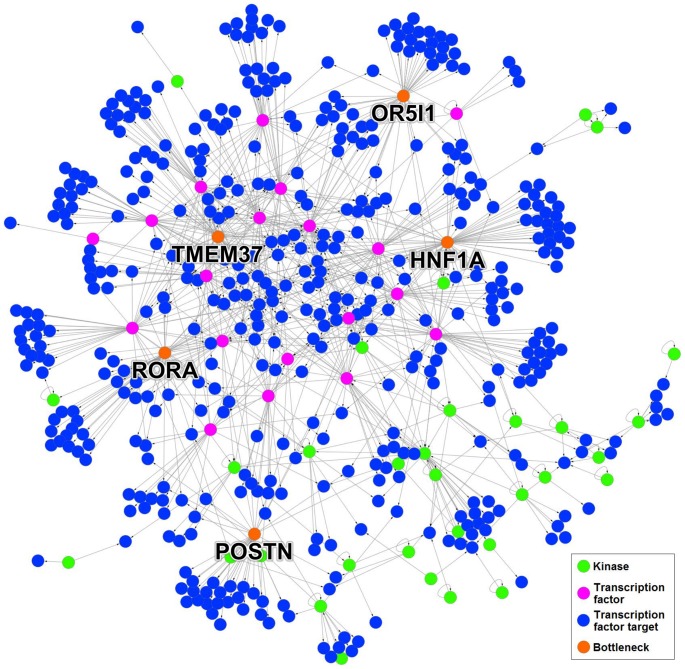
Figure 9. Largest weakly connected differential subnetwork for IMR-90/A549 and p = 2.
Out of the 506 pictured nodes, 450 are sinks and therefore have an impact equal to one. The top five bottlenecks are labeled with their gene names and colored orange.
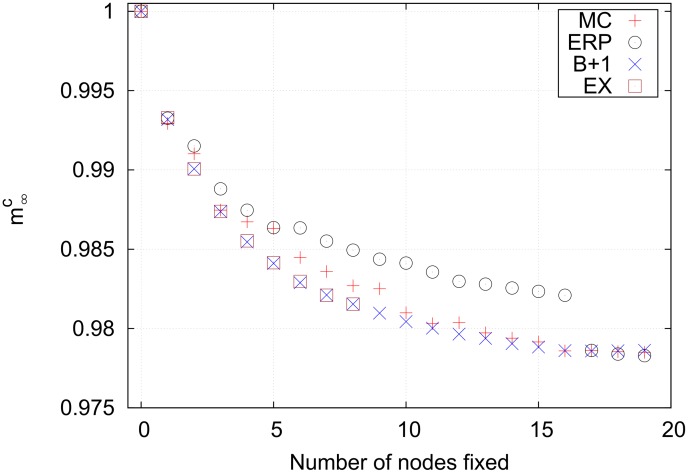
The only case in which an exhaustive search is possible is for 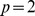 with constraints, which is shown in Fig. 10. Note that the polynomial-time best+1 strategy identifies the same set of nodes as the exponential-time exhaustive search. This is not surprising, however, since the constraints limit the available search space. This means that the Monte Carlo also does well. The efficiency-ranked method performs worst. The efficiency-ranked strategy is designed to be a heuristic strategy that scales gently, however, and is not expected to work well in such a small space when compared with more computationally expensive methods.
with constraints, which is shown in Fig. 10. Note that the polynomial-time best+1 strategy identifies the same set of nodes as the exponential-time exhaustive search. This is not surprising, however, since the constraints limit the available search space. This means that the Monte Carlo also does well. The efficiency-ranked method performs worst. The efficiency-ranked strategy is designed to be a heuristic strategy that scales gently, however, and is not expected to work well in such a small space when compared with more computationally expensive methods.
Figure 10. Final cancer magnetizations for a constrained search on the lung cell network using p = 2.
This is the only case in which a limited exhaustive search is possible. Interestingly, the exhaustive search locates the same nodes as the best+1 strategy for fixing up to eight nodes. The efficiency-ranked strategy performs poorly compared to the Monte Carlo strategy because the search space is small and a large portion of the available space is sampled by the Monte Carlo search.
B Cell Network
The B cell network was derived from the B cell interactome of Ref. [34]. The reconstruction method used in Ref. [34] removes edges from an initially complete network depending on pairwise gene expression correlation. Additionally, the original B cell network contains many protein-protein interactions (PPIs) as well as transcription factor-gene interactions (TFGIs). TFGIs have definite directionality: a transcription factor encoded by one gene affects the expression level of its target gene(s). PPIs, however, do not have obvious directionality. We first filtered these PPIs by checking if the genes encoding these proteins interacted according to the PhosphoPOINT/TRANSFAC network of the previous section, and if so, kept the edge as directed. If the remaining PPIs are ignored, the results for the B cell are similar to those of the lung cell network. We found more interesting results when keeping the remaining PPIs as undirected, as is discussed below.
Because of the network construction algorithm and the inclusion of many undirected edges, the B cell network is more dense ( 0.290% complete, see Table 2) than the lung cell network. This higher density leads to many more cycles than the lung cell network, and many of these cycles overlap to form one very large cycle cluster containing
0.290% complete, see Table 2) than the lung cell network. This higher density leads to many more cycles than the lung cell network, and many of these cycles overlap to form one very large cycle cluster containing  66% of nodes in the full network. All gene expression data used for B cell attractors was taken from Ref. [47]. We analyzed two types of normal B cells (naïve and memory) and three types of B cell cancers (diffuse large B-cell lymphoma (DLBCL), follicular lymphoma, and EBV-immortalized lymphoblastoma), giving six combinations in total. We present results for only the naïve/DLBCL combination below, but Tables 3 and 4 list the properties of all normal/cancer combinations. Again, all gene expression measurements for a given cell type were averaged together to produce a single attractor. The full B cell network is composed of 4364 nodes. For
66% of nodes in the full network. All gene expression data used for B cell attractors was taken from Ref. [47]. We analyzed two types of normal B cells (naïve and memory) and three types of B cell cancers (diffuse large B-cell lymphoma (DLBCL), follicular lymphoma, and EBV-immortalized lymphoblastoma), giving six combinations in total. We present results for only the naïve/DLBCL combination below, but Tables 3 and 4 list the properties of all normal/cancer combinations. Again, all gene expression measurements for a given cell type were averaged together to produce a single attractor. The full B cell network is composed of 4364 nodes. For 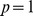 , there is one cycle cluster
, there is one cycle cluster  composed of 2886 nodes. This cycle cluster has
composed of 2886 nodes. This cycle cluster has 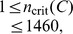
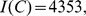 and
and 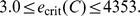 Finding
Finding 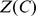 was deemed too difficult.
was deemed too difficult.
Table 4. Best single genes and their impacts for the 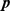 = 1 and
= 1 and 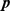 = 2 models.
= 2 models.
|
|
|
|
|
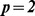
|
|||||||
| Gene |
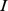
|
Gene |
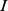
|
Gene |
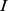
|
Gene |
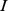
|
Gene |
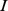
|
Gene |
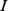
|
|
| I/A | I/H | |||||||||||
| UNC | HNF1A | 29 | OR5I1 | 35 | HNF1A | 29 | HMX1 | 41 | ||||
| TMEM37 | 22 | TMEM37 | 25 | MAP3K3 | 18 | PBX1 | 38 | |||||
| OR5I1 | 20 | HNF1A | 23 | TP53 | 18 | MYB | 25 | |||||
| MAP3K14 | 19 | POSTN | 21 | RUNX1 | 17 | ITGB2 | 20 | |||||
| MAP3K3 | 18 | RORA | 18 | RORA | 16 | TNFRSF10A | 18 | |||||
| CON | MAP3K14 | 19 | SRC | 15 | TTN | 16 | BMPR1B | 18 | ||||
| SRC | 14 | BMPR1B | 7 | RIPK3 | 6 | LCK | 8 | |||||
| N/D | N/F | N/L | ||||||||||
| UNC | BCL6 | 12 | NFIC | 22 | BCL6 | 12 | NCOA1 | 20 | RBL2 | 11 | RBL2 | 22 |
| MEF2A | 5 | TGIF1 | 19 | MEF2A | 5 | NFATC3 | 15 | FOXM1 | 8 | ATF2 | 12 | |
| NCOA1 | 5 | BCL6 | 14 | NCOA1 | 5 | BCL6 | 11 | ATF2 | 7 | NFATC3 | 11 | |
| TGIF1 | 4 | FOXJ2 | 12 | TGIF1 | 4 | CEBPD | 8 | RXRA | 5 | RXRA | 9 | |
| NFATC3 | 4 | NFATC3 | 12 | NFATC3 | 4 | RELA | 8 | NFATC3 | 4 | PATZ1 | 8 | |
| CON | BUB1B | 2 | CSNK2A2 | 2 | BUB1B | 2 | WEE1 | 2 | BUB1B | 2 | PRKCD | 2 |
| AAK1 | 1 | AKT1 | 2 | AAK1 | 1 | CSNK2A2 | 2 | AAK1 | 1 | AURKB | 2 | |
| M/D | M/F | M/L | ||||||||||
| UNC | BCL6 | 12 | FOXJ2 | 12 | BCL6 | 12 | NCOA1 | 18 | RBL2 | 11 | RBL2 | 16 |
| MEF2A | 5 | NFIC | 12 | MEF2A | 5 | BCL6 | 13 | FOXM1 | 8 | ATF2 | 10 | |
| NCOA1 | 5 | BCL6 | 11 | NCOA1 | 5 | E2F3 | 9 | ATF2 | 7 | ZNF91 | 8 | |
| NFATC3 | 4 | NCOA1 | 9 | NFATC3 | 4 | RUNX1 | 9 | RXRA | 5 | STAT6 | 8 | |
| SMAD4 | 4 | MEF2A | 8 | RELA | 4 | TFE3 | 7 | TGIF1 | 4 | FOXM1 | 8 | |
| CON | AAK1 | 1 | RIPK2 | 1 | AAK1 | 1 | ROCK2 | 2 | AAK1 | 1 | AURKB | 2 |
| RIPK2 | 1 | MAST2 | 1 | RIPK2 | 1 | RIPK2 | 1 | SCYL3 | 1 | RIPK2 | 1 | |
The unconstrained (UNC) and constrained (CON) case are shown. The constrained case refer to target that are kinases and are expressed in the cancer case. I = IMR-90 (normal), A = A549 (cancer), H = NCI-H358 (cancer), N = Naïve (normal), M = Memory (normal), D = DLBCL (cancer), F = Follicular lymphoma (cancer), L = EBV-immortalized lymphoblastoma (cancer).
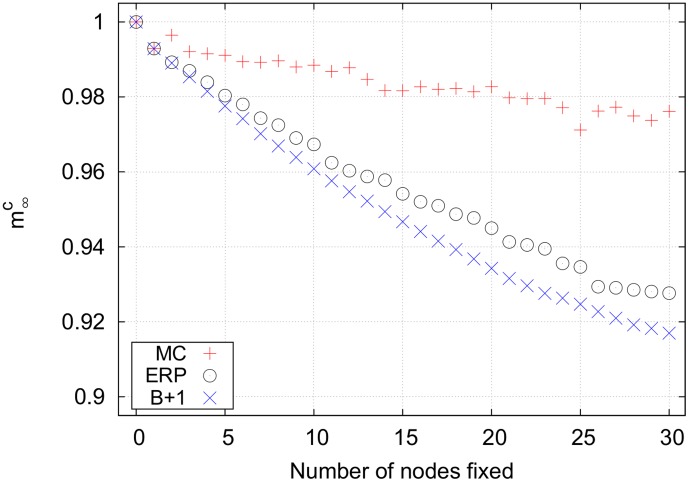
Fig.11 shows the results for the unconstrained 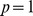 case. Again, the pure efficiency-ranked strategy gave the same results as the mixed efficiency-ranked strategy, so only the pure strategy was analyzed. As shown in Fig. 11, the Monte Carlo strategy is out-performed by both the efficiency-ranked and best+1 strategies. The synergistic effects of fixing multiple bottlenecks slowly becomes apparent as the best+1 and efficiency-ranked curves separate.
case. Again, the pure efficiency-ranked strategy gave the same results as the mixed efficiency-ranked strategy, so only the pure strategy was analyzed. As shown in Fig. 11, the Monte Carlo strategy is out-performed by both the efficiency-ranked and best+1 strategies. The synergistic effects of fixing multiple bottlenecks slowly becomes apparent as the best+1 and efficiency-ranked curves separate.
Figure 11. Final cancer magnetizations for an unconstrained search on the B cell network using p = 1.
The Monte Carlo strategy is ineffective for fixing any number of nodes. The efficiency-ranked and best+1 curves slowly separate because synergistic effects accumulate faster for best+1.
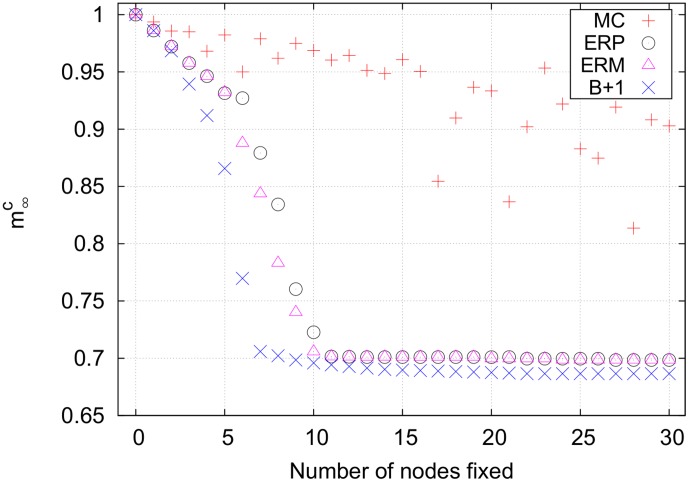
Fig. 12 shows the results for the unconstrained 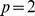 case. The largest weakly connected subnetwork contains one cycle cluster with 351 nodes, with
case. The largest weakly connected subnetwork contains one cycle cluster with 351 nodes, with 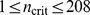 . Although finding a set of critical nodes is difficult, the optimal efficiency for this cycle cluster is 62.2 for fixing 10 bottlenecks in the cycle cluster. This makes targeting the cycle cluster worthwhile. The efficiency of this set of 10 nodes is larger than the efficiencies of the first 10 nodes from the pure efficiency-ranked strategy, so the
. Although finding a set of critical nodes is difficult, the optimal efficiency for this cycle cluster is 62.2 for fixing 10 bottlenecks in the cycle cluster. This makes targeting the cycle cluster worthwhile. The efficiency of this set of 10 nodes is larger than the efficiencies of the first 10 nodes from the pure efficiency-ranked strategy, so the 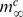 from the mixed strategy drops earlier than the pure strategy. Both strategies quickly identify a small set of nodes capable of controlling a significant portion of the differential network, however, and the same result is obtained for fixing more than 10 nodes. The best+1 strategy finds a smaller set of nodes that controls a similar fraction of the cycle cluster, and fixing more than 7 nodes results in only incremental decreases in
from the mixed strategy drops earlier than the pure strategy. Both strategies quickly identify a small set of nodes capable of controlling a significant portion of the differential network, however, and the same result is obtained for fixing more than 10 nodes. The best+1 strategy finds a smaller set of nodes that controls a similar fraction of the cycle cluster, and fixing more than 7 nodes results in only incremental decreases in 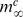 . The Monte Carlo strategy performs poorly, never finding a set of nodes adequate to control a significant fraction of the nodes in the cycle cluster.
. The Monte Carlo strategy performs poorly, never finding a set of nodes adequate to control a significant fraction of the nodes in the cycle cluster.
Figure 12. Final cancer magnetizations for an unconstrained search on the B cell network using p = 2.
The rather sudden drop in the magnetization between controlling 5 and 10 nodes in the efficiency-ranked strategies comes from flipping a significant portion of a cycle cluster. This is the only network examined in which the mixed efficiency-ranked strategy produces results different from the pure efficiency-ranked strategy.
Conclusions
Signaling models for large and complex biological networks are becoming important tools for designing new therapeutic methods for complex diseases such as cancer. Even if our knowledge of biological networks is incomplete, rapid progress is currently being made using reconstruction methods that use large amounts of publicly available omic data [12], [13]. The Hopfield model we use in our approach allows mapping of gene expression patterns of normal and cancer cells into stored attractor states of the signaling dynamics in directed networks. The role of each node in disrupting the network signaling can therefore be explicitly analyzed to identify isolated genes or sets of strongly connected genes that are selective in their action. We have introduced the concept of size
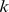 bottlnecks to identify such genes. This concept led to the formulation of several heuristic strategies, such as the efficiency-ranked and best+1 strategy to find nodes that reduce the overlap of the cell network with a cancer attractor. Using this approach, we have located small sets of nodes in lung and B cancer cells which, when forced away from their initial states with local magnetic fields (representing targeted drugs), disrupt the signaling of the cancer cells while leaving normal cells in their original state. For networks with few targetable nodes, exhaustive searches or Monte Carlo searches can locate effective sets of nodes. For larger networks, however, these strategies become too cumbersome and our heuristic strategies represent a feasible alternative. For tree-like networks, the pure efficiency-ranked strategy works well, whereas the mixed efficiency-ranked strategy could be a better choice for networks with high-impact cycle clusters.
bottlnecks to identify such genes. This concept led to the formulation of several heuristic strategies, such as the efficiency-ranked and best+1 strategy to find nodes that reduce the overlap of the cell network with a cancer attractor. Using this approach, we have located small sets of nodes in lung and B cancer cells which, when forced away from their initial states with local magnetic fields (representing targeted drugs), disrupt the signaling of the cancer cells while leaving normal cells in their original state. For networks with few targetable nodes, exhaustive searches or Monte Carlo searches can locate effective sets of nodes. For larger networks, however, these strategies become too cumbersome and our heuristic strategies represent a feasible alternative. For tree-like networks, the pure efficiency-ranked strategy works well, whereas the mixed efficiency-ranked strategy could be a better choice for networks with high-impact cycle clusters.
We make two important assumptions in applying this analysis to real biological systems. First, we assume that genes are either fully off or fully on, with no intermediate state. Modelling the state of a neuron as “all-or-none” has long been accepted as a reasonable assumption [48], which provided the spin glass framework for the Hopfield model. While similar switch-like behavior in gene regulatory networks has been proposed as an explanation of, for example, segmentation in Drosophila embryos [49], assigning a Boolean value to gene expression may be overly simplistic in many cases. A model which uses spins with more than two projections could prove to be more realistic and predictive. Second, we assume that all nodes update their status with a single timescale and with a single interaction strength. If the signaling timescale 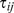 for each edge in the biological network is known, simulations could be conducted in which a signal traveling along an edge
for each edge in the biological network is known, simulations could be conducted in which a signal traveling along an edge 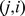 reaches its target after
reaches its target after 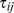 time steps. This would amount to a synchronous update schedule with a “queue” of signals moving between nodes. Likewise, our model gives equal weight to all edges (aside from edges that are effectively deleted in the
time steps. This would amount to a synchronous update schedule with a “queue” of signals moving between nodes. Likewise, our model gives equal weight to all edges (aside from edges that are effectively deleted in the 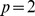 case), whereas real gene regulatory networks exhibit a spectrum of interaction strengths. This can easily be integrated with our model by using a weighted, directed adjacency matrix. However, doing this would surely require a change in control strategy.
case), whereas real gene regulatory networks exhibit a spectrum of interaction strengths. This can easily be integrated with our model by using a weighted, directed adjacency matrix. However, doing this would surely require a change in control strategy.
Despite these issues, our model shows promise. Some of the genes identified in Table 4 are consistent with current clinical and cancer biology knowledge. For instance, in the lung cancer list we found a well known tumor suppressor gene (TP53) [50] that is frequently mutated in many cancer types including lung cancer [51]. Mutations in PBX1 have recently been detected in non-small-cell lung cancer and this gene is now being considered as a target for therapy and prognosis [52]. MAP3K3 and MAP3K14 are in the MAPK/ERK pathway which is a target of many novel therapeutic agents [53], and SRC is a well known oncogene and a candidate target in lung cancer [54]. BCL6 (B-cell lymphoma 6) is the most common oncogene in DLBCL, and it is known that its expression can predict prognosis and response to drug therapy [55]–[57]. BCL6 is also frequently mutated in follicular lymphoma [58], [59]. Our analysis identified BCL6 as an important drug target for both DLBCL and follicular lymphoma using either naive or memory B-cells as a control for both 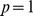 and
and 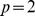 . RBL2 disregulation has been recently associated with many types of lymphoma [60]–[62]. FOXM1 is a potential therapeutic target in mature B cell tumors [63] and ATF2 has been recently found to be highly disregulated in lymphoma [64], [65]. Besides BCL6 discussed above, the N/D list for DLBCL contains genes (MEF2A [66], NCOA1 [67], [68], TGIF1 [69]–[71], NFATC3 [72]) that are all known to have a functional role in cancer, even if they have not been associated to the specific B-cell cancer types we have considered. Our predictions are for the immortalized cell lines we have selected, some of which are commonly used for in-vitro testing in many laboratories. RNAi and targeted drugs could then be used in these cell lines against the top scoring genes in Table 4 to test the disruption of survival or proliferative capacity. If experimentally validated, our analysis based on attractor states and bottlenecks could be applied to patient-derived cancer cells by integrating in the model patient gene expression data to identify patient-specific targets.
. RBL2 disregulation has been recently associated with many types of lymphoma [60]–[62]. FOXM1 is a potential therapeutic target in mature B cell tumors [63] and ATF2 has been recently found to be highly disregulated in lymphoma [64], [65]. Besides BCL6 discussed above, the N/D list for DLBCL contains genes (MEF2A [66], NCOA1 [67], [68], TGIF1 [69]–[71], NFATC3 [72]) that are all known to have a functional role in cancer, even if they have not been associated to the specific B-cell cancer types we have considered. Our predictions are for the immortalized cell lines we have selected, some of which are commonly used for in-vitro testing in many laboratories. RNAi and targeted drugs could then be used in these cell lines against the top scoring genes in Table 4 to test the disruption of survival or proliferative capacity. If experimentally validated, our analysis based on attractor states and bottlenecks could be applied to patient-derived cancer cells by integrating in the model patient gene expression data to identify patient-specific targets.
The above unconstrained searches assume that there exists some set of “miracle drugs” which can turn any gene “on” and “off” at will. This limitation can be patially taken into account by using constrained searches that limit the nodes that can be addressed. However, even the constrained search results are unrealistic, since most drugs directly target more than one gene. Inhibitors, for example, could target differential nodes with 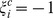 and
and 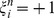 , which would damage only normal cells. Additionally, drugs would not be restricted to target only differential nodes, and certain combinations could be toxic to both normal and cancer cells. Few cancer treatments involve the use of a single drug, and the synergistic effects of combining multiple drugs adds yet another level of complication to finding an effective treatment [27]. On the other hand, the intrinsic nonlinearity of a cellular signaling network, with its inherent structure of attractor states, enhances control [31] so that a properly selected set of druggable targets might be sufficient for robust control.
, which would damage only normal cells. Additionally, drugs would not be restricted to target only differential nodes, and certain combinations could be toxic to both normal and cancer cells. Few cancer treatments involve the use of a single drug, and the synergistic effects of combining multiple drugs adds yet another level of complication to finding an effective treatment [27]. On the other hand, the intrinsic nonlinearity of a cellular signaling network, with its inherent structure of attractor states, enhances control [31] so that a properly selected set of druggable targets might be sufficient for robust control.
Supporting Information
Lung cell network. The column labeled “Source EzID” contains the Entrez IDs of transcription factors and kinases, and “Target EzID” contains the Entrez IDs of the genes targeted by the transcription factor or kinase to its left.
(TXT)
IMR-90/A549 attractors for lung cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
IMR-90/NCI-H358 attractors for lung cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
B cell network. The column labeled “Source EzID” contains the Entrez IDs of transcription factors and kinases, and “Target EzID” contains the Entrez IDs of the genes targeted by the transcription factor or kinase to its left.
(TXT)
Memory/DLBCL attractors for B cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
Memory/EBV-immortalized lymphoblastoma attractors for B cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
Memory/follicular lymphoma attractors for B cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
Naïve/DLBCL attractors for B cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
Naïve/EBV-immortalized lymphoblastoma attractors for B cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
Naïve/follicular lymphoma attractors for B cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
Acknowledgments
We thank Andrew Hodges and Jacob Feala for help with biological datasets. Correspondence and requests for materials should be addressed to carlo@pa.msu.edu or szedlak1@msu.edu.
Data Availability
The authors confirm that all data underlying the findings are fully available without restriction. All relevant data are within the paper and its Supporting Information files.
Funding Statement
The authors acknowledge support from the Congressionally Directed Medical Research Program (DOD, http://cdmrp.army.mil) Lung Cancer Research (W81XWH-12-1-0233) and NIH/NCI (Grant 1R41CA174059-01). Salgomed Inc., provided support in the form of salaries for authors G.P. and C.P., but did not have any additional role in the study design, data collection and analysis, decision to publish, or preparation of the manuscript. The specific roles of these authors are articulated in the ‘author contributions’ section.
References
- 1. Hopfield J (1982) Neural networks and physical systems with emergent collective computational abilities. Proc Nat Acad Sci USA 79: 2554–2558. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2. Amit D, Gutfreund H, Sompolinsky H (1985) Spin-glass models of neural networks. Phys Rev A 32: 1007. [DOI] [PubMed] [Google Scholar]
- 3. Derrida B, Gardner E, Zippelius A (1987) An exactly solvable asymmetric neural network model. Europhys Lett) 4: 167. [Google Scholar]
- 4.Lang AH, Li H, Collins JJ, Mehta P (2012) Epigenetic landscapes explain partially reprogrammed cells and identify key reprogramming genes. ArXiv e-prints: arXiv: 1211.3133v3. [DOI] [PMC free article] [PubMed]
- 5. Anafi RC, Bates JHT (2010) Balancing robustness against the dangers of multiple attractors in a hopfield-type model of biological attractors. PLoS ONE 5: e14413. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 6. Aldana M, Coppersmith S, Kadanoff L (2003) Boolean dynamics with random couplings. In: Perspectives and Problems in Nonlinear Sciences, Springer pp. 23–89. [Google Scholar]
- 7. Kauffman S (1969) Metabolic stability and epigenesis in randomly constructed genetic nets. J Theor Biol 22: 437–467. [DOI] [PubMed] [Google Scholar]
- 8. Amari S, Ando H, Toyoizumi T, Masuda N (2013) State concentration exponent as a measure of quickness in kauffman-type networks. Phys Rev E 87: 022814. [DOI] [PubMed] [Google Scholar]
- 9. Rohlf T, Bornholdt S (2009) Self-organized criticality and adaptation in discrete dynamical networks. In: Adaptive Networks, Springer pp. 73–106. [Google Scholar]
- 10. Kürten K (1988) Correspondence between neural threshold networks and kauffman boolean cellular automata. J Phys A 21: L615. [Google Scholar]
- 11. Kürten K (1988) Critical phenomena in model neural networks. Phys Lett A 129: 157–160. [Google Scholar]
- 12. De Smet R, Marchal K (2010) Advantages and limitations of current network inference methods. Nature Rev Microbiol 8: 717–729. [DOI] [PubMed] [Google Scholar]
- 13. Hartemink A (2005) Reverse engineering gene regulatory networks. Nature Biotechnol 23: 554–555. [DOI] [PubMed] [Google Scholar]
- 14. Bullinger L, Döhner K, Bair E, Fröhling S, Schlenk R, et al. (2004) Use of gene-expression profiling to identify prognostic subclasses in adult acute myeloid leukemia. New Engl J Med 350: 1605–1616. [DOI] [PubMed] [Google Scholar]
- 15. Eppert K, Takenaka K, Lechman E, Waldron L, Nilsson B, et al. (2011) Stem cell gene expression programs influence clinical outcome in human leukemia. Nature Med 17: 1086–1093. [DOI] [PubMed] [Google Scholar]
- 16. Huang S, Eichler G, Bar-Yam Y, Ingber D (2005) Cell fates as high-dimensional attractor states of a complex gene regulatory network. Phys Rev Lett 94: 128701. [DOI] [PubMed] [Google Scholar]
- 17. Sui H, Ernberg I, Kauffman S (2009) Cancer attractors: A systems view of tumors from a gene network dynamics and developmental perspective. Sem Cell Dev Biol 20: 869–876. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 18. Ao P, Galas D, Hood L, Zhu X (2008) Cancer as robust intrinsic state of endogenous molecular-cellular network shaped by evolution. Med Hypotheses 70: 678–684. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 19. Feala J, Cortes J, Duxbury P, Piermarocchi C, McCulloch A, et al. (2010) Systems approaches and algorithms for discovery of combinatorial therapies. Wiley Interdisciplinary Reviews: Systems Biology and Medicine 2: 181–193. [DOI] [PubMed] [Google Scholar]
- 20. Creixell P, Schoof EM, Erler J, Linding R (2012) Navigating cancer network attractors for tumor-specific therapy. Nature Biotechnol 30: 842–848. [DOI] [PubMed] [Google Scholar]
- 21. Calzolari D, Paternostro G, Harrington P Jr, Piermarocchi C, Duxbury P (2007) Selective control of the apoptosis signaling network in heterogeneous cell populations. PLoS ONE 2: e547. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 22. Ágoston V, Csermely P, Pongor S (2005) Multiple weak hits confuse complex systems: a transcriptional regulatory network as an example. Phys Rev E 71: 051909. [DOI] [PubMed] [Google Scholar]
- 23. Csermely P, Ágoston V, Pongor S (2005) The effciency of multi-target drugs: the network approach might help drug design. Trends in Pharmacological Sciences 26: 178–182. [DOI] [PubMed] [Google Scholar]
- 24.Sontag E (1998) Mathematical control theory: deterministic finite dimensional systems, volume 6. Springer.
- 25. Akutsu T, Hayashida M, Ching W, Ng M (2007) Control of boolean networks: hardness results and algorithms for tree structured networks. J Theor Biol 244: 670–679. [DOI] [PubMed] [Google Scholar]
- 26. Choudhary A, Datta A, Bittner M, Dougherty E (2006) Intervention in a family of boolean networks. Bioinformatics 22: 226–232. [DOI] [PubMed] [Google Scholar]
- 27. Feala J, Cortes J, Duxbury P, McCulloch A, Piermarocchi C, et al. (2012) Statistical properties and robustness of biological controller-target networks. PLoS ONE 7: e29374. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 28. Bhardwaj N, Carson M, Abyzov A, Yan KK, Lu H, et al. (2010) Analysis of combinatorial regulation: scaling of partnerships between regulators with the number of governed targets. PLoS Comp Biol 6: e1000755. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 29. Liu YY, Slotine JJ, Barabási AL (2011) Controllability of complex networks. Nature 473: 167–173. [DOI] [PubMed] [Google Scholar]
- 30.Plummer MD, Lovász L (1986) Matching theory. Elsevier.
- 31. Cornelius S, Kath W, Motter A (2013) Realistic control of network dynamics. Nature Commun 4: 1–9. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 32. Yang CY, Chang CH, Yu YL, Lin TCE, Lee SA, et al. (2008) Phosphopoint: a comprehensive human kinase interactome and phospho-protein database. Bioinformatics 24: i14–i20. [DOI] [PubMed] [Google Scholar]
- 33. Matys V, Fricke E, Geffers R, Gössling E, Haubrock M, et al. (2003) Transfac: transcriptional regulation, from patterns to profiles. Nucleic Acids Res 31: 374–378. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 34. Lefebvre C, Rajbhandari P, Alvarez M, Bandaru P, Lim W, et al. (2010) A human b-cell interactome identifies myb and foxm1 as master regulators of proliferation in germinal centers. Mol Syst Biol 6. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 35. Cohen P (2002) Protein kinases - the major drug targets of the twenty-first century? Nature Rev Drug Discov 1: 309–315. [DOI] [PubMed] [Google Scholar]
- 36. Ravasz E, Somera A, Mongru D, Oltvai Z, Barabási AL (2002) Hierarchical organization of modularity in metabolic networks. Science 297: 1551–1555. [DOI] [PubMed] [Google Scholar]
- 37. Girvan M, Newman MEJ (2002) Community structure in social and biological networks. Proc Nat Acad Sci USA 99: 7821–7826. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 38. Shen-Orr S, Milo R, Mangan S, Alon U (2002) Network motifs in the transcriptional regulation network of escherichia coli. Nature Genet 31: 64–68. [DOI] [PubMed] [Google Scholar]
- 39. Luscombe N, Babu M, Yu H, Snyder M, Teichmann S, et al. (2004) Genomic analysis of regulatory network dynamics reveals large topological changes. Nature 431: 308–312. [DOI] [PubMed] [Google Scholar]
- 40.Munoz J, Low TY, Kok YJ, Chin A, Frese CK, et al.. (2011) The quantitative proteomes of human-induced pluripotent stem cells and embryonic stem cells. Molecular systems biology 7. [DOI] [PMC free article] [PubMed]
- 41. Muggerud AA, Edgren H, Wolf M, Kleivi K, Dejeux E, et al. (2009) Data integration from two microarray platforms identifies bi-allelic genetic inactivation of ric8a in a breast cancer cell line. BMC medical genomics 2: 26. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 42. Wagner KW, Punnoose EA, Januario T, Lawrence DA, Pitti RM, et al. (2007) Death-receptor o-glycosylation controls tumor-cell sensitivity to the proapoptotic ligand apo2l/trail. Nature medicine 13: 1070–1077. [DOI] [PubMed] [Google Scholar]
- 43. Stinson S, Lackner MR, Adai AT, Yu N, Kim HJ, et al. (2011) Trps1 targeting by mir-221/222 promotes the epithelial-to-mesenchymal transition in breast cancer. Science Signaling 4: ra41. [DOI] [PubMed] [Google Scholar]
- 44. Hussain M, Rao M, Humphries AE, Hong JA, Liu F, et al. (2009) Tobacco smoke induces polycomb-mediated repression of dickkopf-1 in lung cancer cells. Cancer research 69: 3570–3578. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 45. Muzikar KA, Nickols NG, Dervan PB (2009) Repression of dna-binding dependent glucocorticoid receptor-mediated gene expression. Proceedings of the National Academy of Sciences 106: 16598–16603. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 46. Sartor MA, Mahavisno V, Keshamouni VG, Cavalcoli J, Wright Z, et al. (2010) Conceptgen: a gene set enrichment and gene set relation mapping tool. Bioinformatics 26: 456–463. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 47. Compagno M, Lim WK, Grunn A, Nandula SV, Brahmachary M, et al. (2009) Mutations of multiple genes cause deregulation of nf-κb in diffuse large b-cell lymphoma. Nature 459: 717–721. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 48. McCulloch W, Pitts W (1943) A logical calculus of the ideas immanent in nervous activity. The bulletin of mathematical biophysics 5: 115–133. [PubMed] [Google Scholar]
- 49.Krotov D, Dubuis JO, Gregor T, Bialek W (2014) Morphogenesis at criticality. Proceedings of the National Academy of Sciences. [DOI] [PMC free article] [PubMed]
- 50. Baker S, Fearon E, Nigro JM, Preisinger A, Jessup J, et al. (1989) Chromosome 17 deletions and p53 gene mutations in colorectal carcinomas. Science 244: 217–221. [DOI] [PubMed] [Google Scholar]
- 51. Takahashi T, Nau M, Chiba I, Birrer M, Rosenberg R, et al. (1989) p53: a frequent target for genetic abnormalities in lung cancer. Science 246: 491–494. [DOI] [PubMed] [Google Scholar]
- 52. Mo ML, Chen Z, Zhou HM, Li H, Hirata T, et al. (2013) Detection of e2a-pbx1 fusion transcripts in human non-small-cell lung cancer. J Exp Clin Canc Res 32: 29. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 53. Montagut C, Settleman J (2009) Targeting the raf-mek-erk pathway in cancer therapy. Canc Lett 283: 125–134. [DOI] [PubMed] [Google Scholar]
- 54. Rothschild S, Gautschi O, Haura E, Johnson F (2010) Src inhibitors in lung cancer: current status and future directions. Clin Lung Canc 11: 238–242. [DOI] [PubMed] [Google Scholar]
- 55. Hans C, Weisenburger D, Greiner T, Gascoyne R, Delabie J, et al. (2004) Confirmation of the molecular classification of diffuse large b-cell lymphoma by immunohistochemistry using a tissue microarray. Blood 103: 275–282. [DOI] [PubMed] [Google Scholar]
- 56. Rosenwald A, Wright G, Chan W, Connors JM, Campo E, et al. (2002) The use of molecular profiling to predict survival after chemotherapy for diffuse large-b-cell lymphoma. New Engl J Med 346: 1937–1947. [DOI] [PubMed] [Google Scholar]
- 57. Winter J, Weller E, Horning S, Krajewska M, Variakojis D, et al. (2006) Prognostic significance of bcl-6 protein expression in dlbcl treated with chop or r-chop: a prospective correlative study. Blood 107: 4207–4213. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 58. Diaz-Alderete A, Doval A, Camacho F, Verde L, Sabin P, et al. (2008) Frequency of bcl2 and bcl6 translocations in follicular lymphoma: relation with histological and clinical features. Leukemia Lymphoma 49: 95–101. [DOI] [PubMed] [Google Scholar]
- 59. Akasaka T, Lossos I, Levy R (2003) Bcl6 gene translocation in follicular lymphoma: a harbinger of eventual transformation to diffuse aggressive lymphoma. Blood 102: 1443–1448. [DOI] [PubMed] [Google Scholar]
- 60. Wang L, Pal S, Sif S (2008) Protein arginine methyltransferase 5 suppresses the transcription of the rb family of tumor suppressors in leukemia and lymphoma cells. Mol Cell Biol 28: 6262–6277. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 61. De Falco G, Leucci E, Lenze D, Piccaluga P, Claudio P, et al. (2007) Gene-expression analysis identifies novel rbl2/p130 target genes in endemic burkitt lymphoma cell lines and primary tumors. Blood 110: 1301–1307. [DOI] [PubMed] [Google Scholar]
- 62. Piccaluga P, De Falco G, Kustagi M, Gazzola A, Agostinelli C, et al. (2011) Gene expression analysis uncovers similarity and differences among burkitt lymphoma subtypes. Blood 117: 3596–3608. [DOI] [PubMed] [Google Scholar]
- 63. Tompkins V, Han SS, Olivier A, Syrbu S, Bair T, et al. (2013) Identification of candidate b-lymphoma genes by cross-species gene expression profiling. PLoS ONE 8: e76889. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 64. Valdez B, Zander A, Song G, Murray D, Nieto Y, et al. (2014) Synergistic cytotoxicity of gemcitabine, clofarabine and edelfosine in lymphoma cell lines. Blood Canc J 4: e171. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 65. Walczynski J, Lyons S, Jones N, Breitwieser W (2013) Sensitisation of c-myc-induced b-lymphoma cells to apoptosis by atf2. Oncogene 33: 1027–1036. [DOI] [PubMed] [Google Scholar]
- 66. Bai X, Wu L, Liang T, Liu Z, Li J, et al. (2008) Overexpression of myocyte enhancer factor 2 and histone hyperacetylation in hepatocellular carcinoma. J Canc Res Clinic Oncol 134: 83–91. [DOI] [PubMed] [Google Scholar]
- 67. Fabris S, Mosca L, Cutrona G, Lionetti M, Agnelli L, et al. (2013) Chromosome 2p gain in monoclonal b-cell lymphocytosis and in early stage chronic lymphocytic leukemia. Am J Hemat 88: 24–31. [DOI] [PubMed] [Google Scholar]
- 68. Zhang Y, Duan C, Bian C, Xiong Y, Zhang J (2013) Steroid receptor coactivator-1: A versatile regulator and promising therapeutic target for breast cancer. J Steroid Biochem 138: 17. [DOI] [PubMed] [Google Scholar]
- 69. Hamid R, Brandt S (2009) Transforming growth-interacting factor tgif regulates proliferation and differentiation of human myeloid leukemia cells. Mol Oncol 3: 451–463. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 70. Libório T, Ferreira EN, Aquino Xavier FC, Carraro DM, Kowalski LP, et al. (2013) Tgif1 splicing variant 8 is overexpressed in oral squamous cell carcinoma and is related to pathologic and clinical behavior. Oral Surg Oral Med 116: 614–625. [DOI] [PubMed] [Google Scholar]
- 71. Bengoechea-Alonso M, Ericsson J (2010) Tumor suppressor fbxw7 regulates tgifβ signaling by targeting tgif1 for degradation. Oncogene 29: 5322–5328. [DOI] [PubMed] [Google Scholar]
- 72. Glud SZ, Sörensen AB, Andrulis M, Wang B, Kondo E, et al. (2005) A tumor-suppressor function for nfatc3 in t-cell lymphomagenesis by murine leukemia virus. Blood 106: 3546–3552. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 73. Fagiolo G (2007) Clustering in complex directed networks. Phys Rev E 76: 026107. [DOI] [PubMed] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Supplementary Materials
Lung cell network. The column labeled “Source EzID” contains the Entrez IDs of transcription factors and kinases, and “Target EzID” contains the Entrez IDs of the genes targeted by the transcription factor or kinase to its left.
(TXT)
IMR-90/A549 attractors for lung cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
IMR-90/NCI-H358 attractors for lung cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
B cell network. The column labeled “Source EzID” contains the Entrez IDs of transcription factors and kinases, and “Target EzID” contains the Entrez IDs of the genes targeted by the transcription factor or kinase to its left.
(TXT)
Memory/DLBCL attractors for B cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
Memory/EBV-immortalized lymphoblastoma attractors for B cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
Memory/follicular lymphoma attractors for B cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
Naïve/DLBCL attractors for B cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
Naïve/EBV-immortalized lymphoblastoma attractors for B cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
Naïve/follicular lymphoma attractors for B cell network. The column labeled “EzID” contains the Entrez ID of the genes. The second and third columns are the normal and cancer attractor, respectively.
(TXT)
Data Availability Statement
The authors confirm that all data underlying the findings are fully available without restriction. All relevant data are within the paper and its Supporting Information files.