Abstract
An anonymous user authentication scheme allows a user, who wants to access a remote application server, to achieve mutual authentication and session key establishment with the server in an anonymous manner. To enhance the security of such authentication schemes, recent researches combined user's biometrics with a password. However, these authentication schemes are designed for single server environment. So when a user wants to access different application servers, the user has to register many times. To solve this problem, Chuang and Chen proposed an anonymous multiserver authenticated key agreement scheme using smart cards together with passwords and biometrics. Chuang and Chen claimed that their scheme not only supports multiple servers but also achieves various security requirements. However, we show that this scheme is vulnerable to a masquerade attack, a smart card attack, a user impersonation attack, and a DoS attack and does not achieve perfect forward secrecy. We also propose a security enhanced anonymous multiserver authenticated key agreement scheme which addresses all the weaknesses identified in Chuang and Chen's scheme.
1. Introduction
With the rapid growth of internet technology, a system providing various services using the network often consists of many different servers around the world. The distribution of the remote system hardware allows its users to access resources efficiently and conveniently. In multiple server environments, an authentication mechanism is required to achieve a high level of security [1]. Lamport [2] first proposed a password authentication scheme for communication through an insecure channel. However, Lamport's scheme requires the server to manage a password table and is, thus, vulnerable to stolen-verifier attacks. To resist this attack, several researchers proposed improved password-based authentication schemes using smart cards. But, these schemes are still easily broken by simple dictionary attacks due to the low entropy of passwords and because the information stored in smart cards could be extracted by physically monitoring power consumption [3, 4]. Therefore, many other researchers have combined users' biometrics and passwords to enhance the security of their user authentication schemes for multiserver environments; see, for example, references [5–7] for earlier work in this domain. Every human being has a different biometrics, and thus, it is difficult for the adversary to compute the biometric information [8, 9].
Relatively recently, D. Yang and B. Yang [10] and Yoon and Yoo [11] independently introduced a biometric-based multiserver authentication scheme. But, these schemes still do not consider user anonymity which has been identified as a major security property for privacy protection in many applications, including location-based services, anonymous web browsing, e-voting, and mobile roaming services. Moreover, D. Yang and B. Yang's scheme requires users to perform expensive exponentiation operations, while Yoon and Yoo's scheme, as demonstrated by He [12], is vulnerable to a privileged insider attack, a masquerade attack, and a stolen smart card attack.
Recently, Chuang and Chen [13] proposed an anonymous multiserver authenticated key agreement scheme to address the weaknesses in the D. Yang and B. Yang's scheme [10] and the Yoon-Yoo scheme [11]. This scheme is based on nonces and is very efficient in that it only requires users to perform hash function evaluations. Chuang and Chen claimed that their scheme satisfies all the desired security-related properties: anonymity, absence of verification tables, mutual authentication, resistance to forgery attack, resistance to modification attacks, resistance to replay attacks, fast error detection, resistance to off-line guessing attacks, resistance to insider attacks, simple and secure password choice and modification, biometric template protection, and session key agreement. However, we found that Chuang and Chen's scheme has various security problems. According to our analysis given in this paper, Chuang and Chen's scheme is vulnerable to a masquerade attack, a smart card attack, a user impersonation attack, and a denial-of-service (DoS) attack and does not achieve perfect forward secrecy. To solve these security problems with Chuang and Chen's scheme, we propose an improved anonymous multiserver authenticated key agreement scheme using a smart card together with biometrics and passwords.
The remainder of this paper is organized as follows. Section 2 describes security and efficiency requirements for anonymous user authentication schemes in multiserver environments. Section 3 briefly reviews Chuang and Chen's authentication scheme, while Section 4 provides a detailed security analysis on the scheme. Section 5 presents our security-enhanced authentication scheme and shows how the security weaknesses of Chuang and Chen's scheme are addressed in our scheme. Section 6 analyzes our scheme in terms of both security and efficiency. Section 7 concludes the paper.
2. Requirements for Multiserver Authentication Schemes
Most conventional password authentication methods, when they are deployed in a multiple server environment, require each network user not only to log into various remote servers repetitively but also to remember many sets of identities and passwords. Such inefficiency and complexity easily lead to the exposure of users' identities and passwords and necessarily make it difficult to manage the shared secret keys among the involved participants. Moreover, those conventional authentication methods usually do not provide user anonymity. In contrast, an anonymous multiserver authentication scheme is designed to allow users to be authenticated by multiple servers via only one registration with the registration center [1]. Figure 1 shows a framework of an anonymous user authentication system in a multiserver environment.
Figure 1.
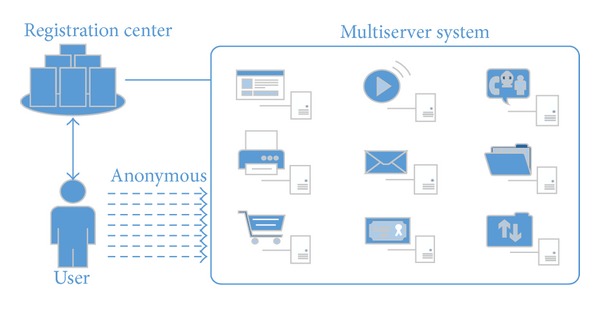
Framework of a multiserver authentication system.
2.1. Security Properties
Various security requirements for a multiserver authentication scheme have been suggested in the previous studies [1, 7, 10, 13–24]. The most essential security properties include the following.
-
(S1)
Anonymity: anonymity is of increasing importance and is achieved when the user's identity is not disclosed to an unauthorized party.
-
(S2)
Mutual authentication: mutual authentication means that the two parties, user and server, authenticate each other. That is, both user and server are assured of each other's identity.
-
(S3)
Session key agreement: the user and server securely agree on a session key to be used for protecting their subsequent communications.
-
(S4)
Perfect forward secrecy: perfect forward secrecy means that a session key derived from a set of long-term keys will not be compromised if one of the long-term keys is compromised in the future.
2.2. Attack Resistance
To achieve these security properties, a multiserver authentication scheme has to resist various kinds of attacks. The most typical attacks include the following
-
(A1)
Replay attack: an adversary intercepts data transmissions for the purpose of making use of that data in some manner. Typically, this type of attack involves copying and possibly altering the data in various ways before releasing it for delivery to the intended recipient.
-
(A2)
Modification attack: an adversary intercepts the authentication message and attempts to modify it for illegal authentication.
-
(A3)
Stolen-verifier attack: an adversary steals the password-verifier from the server and directly uses it to masquerade as a legitimate user.
-
(A4)
Off-line guessing attack: an adversary guesses a password and verifies it in an off-line environment. The information stored in the smart card is often used in such an attack.
-
(A5)
Forgery attack: a malicious yet legitimate user attempts to forge an authentication message of another legitimate user.
-
(A6)
Insider attack: an insider attack literally means an attack mounted by a malicious insider. Malicious insiders have a distinct advantage over external adversaries because they have an authorized system access and also may be familiar with the network architecture and system policies/procedures. Typically, malicious insiders want to acquire users' private information such as their password and biometrics.
-
(A7)
Masquerade attack: an adversary is authenticated by the server using a fake user ID.
-
(A8)
Smart card attack: an adversary is authenticated by the server by using only the information obtained from a user's smart card but without the password or biometrics of the user.
-
(A9)
User impersonation attack: an adversary impersonates a legitimate user using only the user's smart card but without the password or biometric of the user.
-
(A10)
DoS attack: a DoS attack is any event that diminishes or eliminates a network's capability of performing its expected function. In other words, an adversary mounts a DoS attack to make the server unavailable.
2.3. Efficiency Measures
Efficiency is an important consideration in evaluating any schemes or protocols. The efficiency of a multiserver authentication scheme can be measured by the following metrics.
-
(E1)
Single registration: a single point of registration ought to allow users to gain access to all the servers in the system.
-
(E2)
Simple and secure password modification: the system should allow users to choose and change their passwords easily and securely. In other words, each user should be able to change their passwords without the help of any third trusted party once the authenticity of the user is verified by its smart card.
-
(E3)
Fast error detection: the smart card needs to check the user's incorrect password or any other discrepancy quickly.
-
(E4)
Low computational cost: the computational cost incurred by the scheme should be minimized for the participants.
3. A Review of Chuang and Chen's Scheme
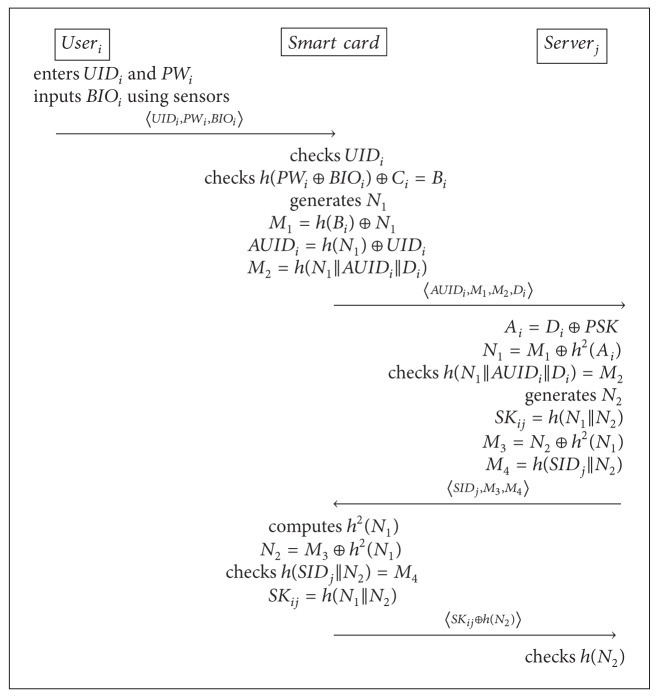
This section describes Chuang and Chen's anonymous multiserver authenticated key agreement scheme which involves four phases: server registration, user registration, login and authentication, and password change. For convenience, the notations used throughout this paper are summarized in Notation Section.
3.1. The Server Registration Phase
The application server sends the RC a join message if it would like to become an authorized server. Then, the RC replies with the key (PSK) to the server through a secure channel. And then, the authorized server uses the PSK to check the user's authentication message. If the server needs to obtain the PSK from the RC to perform the authentication phase every session, authentication delay and the communication cost between the RC and the servers will increase substantially, but this scheme and proposed scheme register only once so they are efficient.
3.2. The User Registration Phase
For a user useri, this phase is performed only once when useri registers itself with the registration center RC.
useri chooses his identity UIDi and password PWi freely and inputs his biometrics BIOi and sends the identity useri and h(PWi ⊕ BIOi) to RC via a secure channel.
RC computes A i = h(UIDi||x) and B i = h 2(UIDi||x) = h(A i) and C i = h(PWi||BIOi) ⊕ B i and D i = PSK ⊕ A i and issues useri a smart card loaded with 〈UIDi, h(), B i, C i, D i〉.
3.3. The Login and Authentication Phase
In this phase, useri logs in to the smart card and is authenticated by serverj. In login phase, is executed to check the user's legality. The smart card can detects an error event immediately using the user's identification, password, and biometrics information. And then, the smart card computes 〈AUIDi, M 1, M 2, D i〉 for the authentication. In authentication phase, the smart card sends authentication messages to the serverj after the useri finishes the login phase successfully. The smart card never send user's real identity to execute the authentication phase for providing the user's anonymity. During the phase, the session-key establishment is conducted between useri and serverj. Algorithm 1 depicts how the login and authentication phase works.
Algorithm 1.
Login and authentication phase of Chuang and Chen's scheme.
3.4. The Password Change Phase
One of the general guidelines to get better password security is to ensure that passwords are changed at regular intervals. Chuang and Chen's scheme allows legitimate users to freely change their passwords:
useri inserts his smart card into a card reader and enters both the current password PWi and the new password PWi*.
The smart card checks UIDi and h(PWi ⊕ BIOi) ⊕ C i = B i.
The smart card computes C i* = C i ⊕ h(PWi ⊕ BIOi) ⊕ h(PWi* ⊕ BIOi) and replaces C i with C i*.
4. Security Vulnerabilities in Chuang and Chen's Scheme
We analyze Chuang and Chen's scheme and figure out some security vulnerabilities. Their scheme is vulnerable to the masquerade attack, smart card attack, user impersonation attack, and DoS attack and does not achieve perfect forward secrecy.
4.1. A Masquerade Attack
Chuang and Chen's scheme is vulnerable to user masquerade attack. An adversary can be authenticated to another serverk using the messages that useri sends to serverj for authentication. Figure 2 describes the masquerade attack on Chuang and Chen's scheme. When the useri wants to be authenticate with serverj, the useri logs on the smart card and then sends a message (1) to the serverj. After an adversary intercepts the message (1), the adversary will send it to another server serverk. This is because that message (1) does not include about the serverj as follows:
| (1) |
Figure 2.
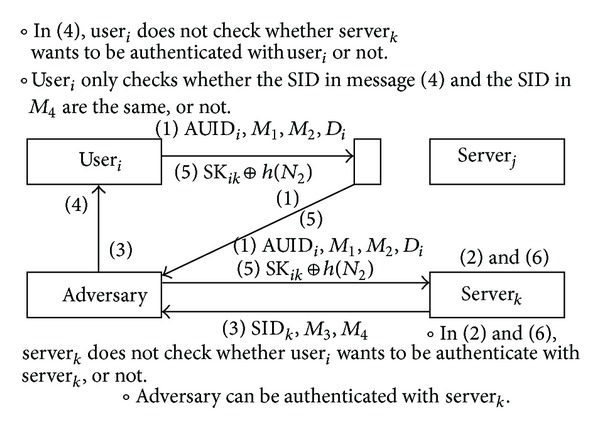
Masquerade attack on Chuang and Chen's scheme.
So the serverk executes operation (2) and sends the message (3) to the adversary without any suspicion of the attack. The adversary forwards the message (3) to the useri. The useri does not check the SIDj of the serverj. It only checks the sameness with the SID of M 4 and the SID of the message (3) as follows:
| (2) |
So the useri executes operation (4) and sends message (5) to serverj without any suspicion of the attack. Then, an adversary intercepts the message (5) and sends it to another serverk. Finally, the adversary can be authenticated with serverk. Therefore, the adversary can masquerade as a legitimate user to serverk. In this way, the scheme becomes vulnerable to the masquerade attack.
The serverk cannot check whether useri wants to be authenticated by serverk or not. Thus serverk authenticates all legitimate messages though these message are not sent to serverk. And useri does not check whether serverj wants to be authenticated with useri. Thus useri authenticates all legitimate messages though these message are sent by serverk. The useri only checks whether SID in message (3) and SID in M 4 are the same or not. To solve this problem, the destination of message is added to authentication messages. So the information about SID of serverj has to be added to the message (1), and this means that useri want to be authenticated with serverj, not serverk. And the information about AUID of useri has to be added to message (3); it means that the serverj wants to be authenticated with anonymous useri.
4.2. A Smart Card Attack
When an adversary gets or steals the user's smart card, the adversary can compute the session key between the useri and serverj without the user's password or biometric information. So the adversary can decrypt the all encrypted communications between the useri and serverj because the adversary can compute all previous session keys. Algorithm 2 describes the smart card attack on Chuang and Chen's scheme.
Algorithm 2.
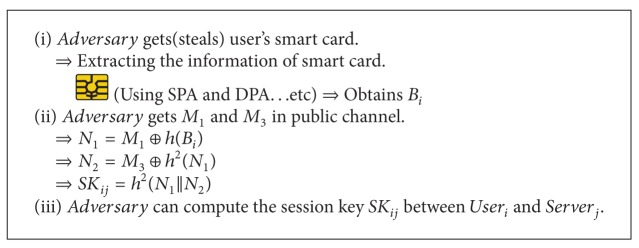
Smart card attack on Chuang and Chen's scheme.
When the adversary obtains the user's smart card, the adversary can extract information about the smart card using a side-channel attack such as SPA (simple power analysis) or DPA (differential power analysis). The adversary can obtain B i in the user's smart card and M 1, M 3 in the public communication channel. Then, the adversary can compute N 1 using M 1 and h(B i) and N 2 using M 3 and h 2(N 1). Finally, the adversary can determine the session key user and server using N 1 and N 2. This scheme uses the combination values with a password and biometrics, so the adversary cannot compute the user's password. However, using the smart card attack, the adversary can compute the session key between the useri and the serverj without the information about user's password or biometrics.
Kocher et al. and Messerges et al. pointed out that confidential information stored in all existent smart cards could be extracted by physically monitoring power consumption [3, 4]. If a user loses his smart card, all secrets in the smart card may be revealed to the adversary. Using this information, the adversary can determine the session key between the useri and serverj. To solve this problem, it is necessary to add authentication value that adversary cannot reveal using the side-channel attack. In other words, it is necessary to add the value that only legitimate user and server can compute using the secret information, which the adversary cannot know or compute.
4.3. A User Impersonation Attack
In Chuang and Chen's scheme, an adversary can be authenticated with the server using user's smart card without user's password or biometrics, so the adversary can impersonate the legitimate user. It is critical problem that the adversary can be authenticated with the server using user's smart card only. Figure 3 describes the user impersonation attack on Chuang and Chen's scheme. As described above, the adversary can illegally extract the secret values including B i from the user's smart card by some means. And he can intercept the message (1) = 〈AUIDi, M 1, M 2, D i〉 and acquire the AUIDi, M 1, and D i.
Figure 3.
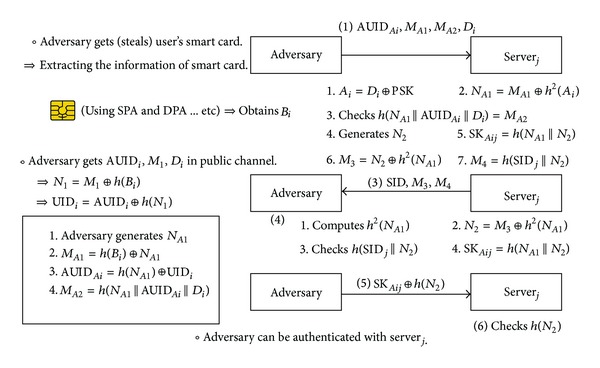
User impersonation attack on Chuang and Chen's scheme.
Next procedure for user impersonation attack occurs in the following steps. The adversary computes the N 1 using M 1 and h(B i). And then, he can figure out the UIDi using AUIDi and h(N 1). Next, the adversary generates another random nonce N A1 and computes M A1, AUIDAi, and M A2. Next, the adversary sends AUIDAi, M A1, M A2, and D i to serverj. The adversary can be authenticate to serverj because he knows B i, N A1, and UIDi and the serverj cannot figure out the difference between the adversary and legitimate user. The user's password and biometric information are not used in authentication phase, so serverj authenticates the adversary without doubt. serverj does not store user's password or biometric information because Chuang and Chen's scheme is designed for anonymous user. Therefore, server cannot check the password or biometric information for authentication. To solve this problem, it is necessary to add the shared value between the user and servers. The share value can be computed by only the legitimate user using user's password and biometircs in login and authentication phase, and never be stored in the smart card.
4.4. A DoS Attack
The DoS attack is an attempt to make a machine or network resource unavailable to its intended users. Although the means to carry out motives for and targets of the DoS attack may vary, it generally consists of efforts to temporarily or indefinitely interrupt or suspend services of a host connected to the networks. In Chuang and Chen's scheme, an adversary can implement the DoS attack without difficulty. Figure 4 describes DoS attack on Chuang and Chen's scheme. The adversary gets the previous message (1) from a legitimate user and sends it to the serverj. Then, the serverj executes operation (2) and sends message (3) to the useri. The processes of operation (2) include executing the hash function 7 times, calculating the exclusive-or operation 3 times, and generating a random nonce once. The adversary can attempt to make the server or network resource unavailable if he uses a lot of intercepted authentication messages.
Figure 4.

DoS attack on Chuang and Chen's scheme.
In Chuang and Chen's scheme, serverj does not check the freshness of authentication message from useri. Thus, when an adversary sends the intercepted authentication messages to serverj, the serverj cannot know whether the message is current or outdated. So, serverj executes a lot of operations. To resist the DoS attack, the serverj has to check the freshness of messages using the timestamp or other means.
4.5. No Perfect Forward Secrecy
Perfect forward secrecy means that a session key derived from a set of long-term keys will not be compromised if one of the long-term keys is compromised in the future. Chuang and Chen's scheme does not achieve perfect forward secrecy. So the adversary can compute the all session key between the useri and serverj if the adversary knows the one of long-term keys A i in future. Algorithm 3 describes why Chuang and Chen's scheme does not achieve perfect forward secrecy. First, the adversary got M P1 and M P3 in previous communication between useri and serverj. Next, the adversary knows one of user's long-term secrets A i. So the adversary can calculate N P1 from N P1 = M P1 ⊕ h 2(A i) and N P2 from N P2 = M P3 ⊕ h 2(N P1). Finally, the adversary can compute the previous session key SKPij using N P1 and N P2 Therefore, this scheme does not achieve perfect forward secrecy.
Algorithm 3.

No perfect forward secrecy on Chuang and Chen's scheme.
In Chuang and Chen's scheme, A i is a secure shared key among RC and authenticated useri. The RC computes A i using UIDi and secret value x. And then, The RC sends the h(A i) to useri within user's smart card. The h(A i) is unchanged even if useri changes his password. So A i is one of the long-term keys. If an adversary got the M P1 and M P3 in previous public channel and knows A i at present, the adversary can compute the previous session key between the useri and serverj. To solve this problem, it is needed that the adversary cannot compute the N 1 and N 2 using only A i. By adding another secret information, it is necessary that the adversary cannot compromise the session key between useri and serverj.
5. Our Proposed Scheme
Our proposed scheme improves Chuang and Chen's scheme in various aspects: (1) it checks the destination of messages and so it prevents the masquerade attack, (2) it withstands the smart card attack and the user impersonation attack even when the information in the smart card is disclosed, (3) it resists DoS attacks by checking the freshness of messages, and (4) it protects the security of previously-established session keys even when the adversary knows the long-term key A i, thereby achieving perfect forward secrecy.
5.1. Countermeasures
The vulnerability of Chuang and Chen's scheme to the masquerade attack is due to the fact that
there is no way for serverj to check whether the user wants to be authenticated with it or with another server, serverk;
useri cannot check whether the server wants to be authenticated with him or with another user, userj.
This design flaw allows the adversary to be authenticated with serverk using useri's message directed to serverj. Therefore, to prevent the masquerade attack, we suggest to modify the computations of M 2 and M 4 from M 2 = h(N 1||AUIDi||D i) and M 4 = h(SIDj||N 2) to
| (3) |
The server ID, SIDj, and the anonymous user ID, AUIDi, are now included as part of the inputs of the hash function. The inclusion of SIDj and AUIDi allows serverj and useri to confirm the destination of the messages M 2 and M 4, respectively, and therefore effectively prevents the masquerade attack.
The Dos attack is possible because serverj performs all its operations without checking the freshness of incoming messages, and thus it can be prevented by modifying the computation of M 2 to
| (4) |
where T i is the timestamp retrieved by useri and sent to serverj. The inclusion of the timestamp T i to the computation of M 2 enables serverj to check and confirm the freshness of the user's authentication message and prevents the DoS attack. Due to this modification, the authentication message of useri should be also modified as follows:
| (5) |
We next present a possible way of eliminating the vulnerability of Chuang and Chen's scheme to the smart card attack. Recall that this vulnerability is due to that the value B i stored in the smart card together with M 1 and M 3 exchanged between useri and serverj enables the adversary to compute N 1 and N 2 and thereby to derive the session key SKij = h 2(N 1||N 2). Therefore, to prevent the smart card attack, we suggest to modify the computations of M 1 and M 3 from M 1 = h(B i) ⊕ N 1 and M 3 = N 2 ⊕ h 2(N 1) to
| (6) |
With this modification, the adversary now cannot compute N 1 and N 2 without the hash value h(PSK). To make this countermeasure work, we add a new value E i = h(PSK) ⊕ h(PWi ⊕ BIOi) to useri's smart card so that only useri can extract h(PSK) from its password and biometrics.
However, with the modifications described above, Chuang and Chen's scheme is still vulnerable to the user impersonation attack as the adversary can obtain h(PWi ⊕ BIOi) from B i and C i = h(PWi ⊕ BIOi) ⊕ B i which are stored in the smart card. To prevent the user impersonation attack, we modify the computation of C i to
| (7) |
The adversary now cannot calculate h(PWi ⊕ BIOi) as it does not know h(PSK).
Finally, to provide the perfect forward secrecy in our proposed scheme, we modify the computation of D i from D i = PSK ⊕ A i to
| (8) |
With this modification, the adversary cannot derive PSK from the long-term key A i and, thus, cannot compute N 1, N 2, and the previous session key SKij = h(N 1||N 2).
The password update phase should be also modified for consistency purpose (see Section 5.5 for details). Combining all the modifications above together yields an improved authentication scheme described in the following subsections.
5.2. The Server Registration Phase
The application server sends a message for join to the RC when they want to become an authorized server. Then, the RC sends the key(PSK) to the server using secure communication. And then, the server is ready to compute h(PSK) for user authentication. Next, the authorized server uses the shared information like PSK and h(PSK) to check the user's legitimacy in authentication phase.
5.3. The User Registration Phase
The registration phase of proposed scheme is described in Algorithm 4. useri needs to perform the user registration phase with the registration center using a secure channel. In this phase, RC sends to useri the information about PSK and h(PSK). PSK is included in D i = PSK ⊕ A i ⊕ h(PSK). useri can be authenticated with serverj using D i but cannot compute the PSK and A i even if he knows the D i and h(PSK). And useri can calculate the h(PSK) using user's password and biometrics from E i = h(PSK) ⊕ h(PWi ⊕ BIOi). In other words, the useri receives the hidden PSK and h(PSK) in D i and E i, respectively, included in smart card for user's login and authentication. Detailed steps are explained as follows.
-
(1)
The useri sends UIDi and h(PWi ⊕ BIOi) to the RC through a secure channel.
-
(2)After receiving the useri's information, the RC computes the authentication parameters for the useri as follows:
(9) -
(3)
The RC stores these authentication parameters 〈UIDi, h(), B i, C i, D i, E i〉 in a smart card and sends the smart card to useri via a secure channel.
Algorithm 4.
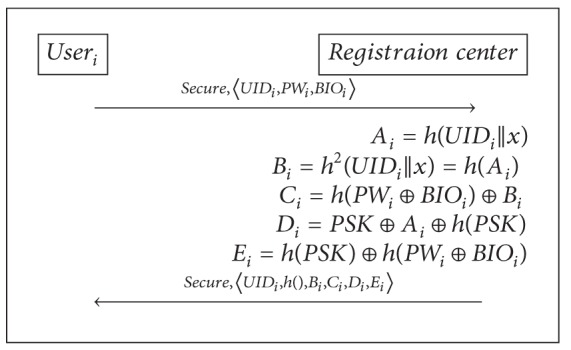
Our registration phase.
The RC does not store the user's password or biometrics information. Therefore, our proposed scheme is secure against a stolen-verifier attack. The registered user cannot fake another legitimate user successfully though the user obtains these parameters 〈UIDi, h(), B i, C i, D i, E i〉. This is because that the user does not know the secret value x and PSK. The authenticated user can only compute h(PSK) using his password and biometrics.
5.4. The Login and Authentication Phases
The login and authentication phases for the proposed scheme are described in Algorithm 5. In the login phase, the smart card checks the legitimacy of the user. The smart card checks an error event immediately using identification, password, and biometric information. Detailed steps of the login phase are explained as follows.
-
(1)
The useri inserts his smart card into a card reader and enters his UIDi and PWi. Then, the useri inputs his biometric information BIOi using the sensor.
-
(2)The smart card checks the UIDi and confirms that B i in smart card is same to h(PWi ⊕ BIOi) ⊕ C i. If all information is accurate, then the smart card generates a random nonce N 1 and a timestamp T i and computes the h(PSK) using E i and h(PWi ⊕ BIOi). Next the smart card computes the following:
(10)
Algorithm 5.
Our login and authentication phase.
In the authentication phase, the smart card sends an authentication message to the server after the useri finishes the login phase successfully. The proposed scheme only uses the anonymous identity AUIDi to perform the authentication phase. The detailed steps of the authentication phase are explained as follows.
-
(3)
The smart card sends the message 〈AUIDi, M 1, M 2, D i, T i〉 to the serverj for the useri's authentication.
-
(4)The serverj confirms the legality of the useri and the freshness of authentication message. First, the serverj checks the freshness of T i. If T i is not fresh, the serverj rejects the useri's request. The serverj uses PSK and h(PSK) to obtain A i from the D i. The serverj computes the value of N 1 (N 1 = M 1 ⊕ h 2(A i) ⊕ h(PSK)) and then confirms whether h(N 1||AUIDi||D i||SIDj||T i) is same to M 2. If the result of M 2 is not same, the serverj terminates this session. Then, the serverj computes UIDi using h(N 1) and checks the legitimacy of UIDi. Next, the serverj generates a random nonce N 2 and computes the following:
(11) -
(5)
The serverj sends back the authentication message 〈SIDj, M 3, M 4〉 to the smart card.
-
(6)The smart card confirms the legality of the serverj. It computes h 2(N 1) and then calculates N 2 using M 3, h 2(N 1), and h(PSK). Next, the smart card checks whether
Next, the smart card computes the session key SKij as h(N 1||N 2). Finally, the smart card computes SKij ⊕ h(N 2).(12) -
(7)
The smart card sends the message 〈SKij ⊕ h(N 2)〉 to the serverj.
-
(8)
The serverj uses the session key SKij for checking SKij ⊕ h(N 2), anf if h(N 2) is correct, the serverj authenticates the useri. From now on, the serverj can communicate securely with useri using the SKij
5.5. The Password Change Phase
The password change phase for the proposed scheme is described in Algorithm 6. The proposed password change phase is executed when the useri wants to update his password. In this phase, the useri can easily change his password without any assistance from the registration center. Detailed processes are as follows.
-
(1)
The useri inserts his smart card into a card reader and enters both the current password PWi and the new password PWi* with UIDi and BIOi.
-
(2)The smart card checks UIDi and computes h(PSK) = E i ⊕ h(PWi ⊕ BIOi) and then checks whether
(13) -
(3)
The smart card computes C i* = C i ⊕ h(PWi ⊕ BIOi) ⊕ h(PWi* ⊕ BIOi) and then replaces C i with C i*.
Algorithm 6.
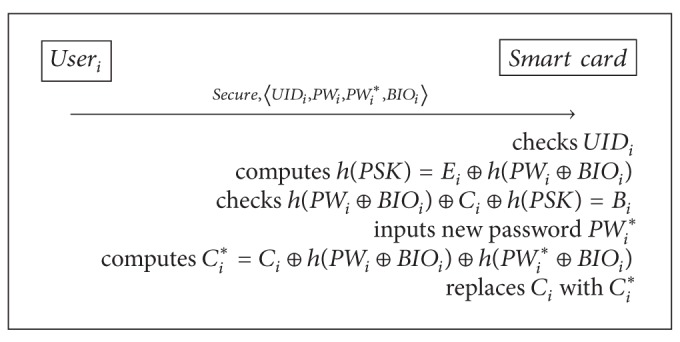
Our password change phase.
6. Analysis of Our Scheme
An anonymous multiserver authenticated key agreement scheme has three important requirements: the security properties, the attack resistance, and the efficiency, so it needs to analyze the proposed scheme using them. In this section, we explain how the proposed scheme is satisfied with the requirements and compare the proposed scheme with other authentication schemes.
6.1. Security Properties
-
(S1)
Anonymity: in the proposed scheme, an adversary cannot compute the user's real identity UIDi without h(N 1) because the real identity of user is always converted using AUIDi = h(N 1) ⊕ UIDi. Only legitimate server can compute and check the user's real identity, because the server has the PSK and can compute the N 1 from N 1 = M 1 ⊕ h 2(A i) ⊕ h(PSK) using the PSK, M 1, and A i. Thus, only authorized server confirms the UID of user. As a result, the adversary cannot obtain the user's real identity, but legitimate useri can anonymously be authenticated with serverj.
-
(S2)Mutual authentication: the mutual authentication means that two parties authenticate each other. In proposed scheme, the user and server authenticated each other using N 1, N 2, h(PSK), and D i. In the authentication phase, the server authenticates the user if the M 2 is correct as follows:
And the user authenticates the server using M 4 and N 2; it checks whetherthe M 4 is correct as follows:(14)
Though an adversary intercepts the messages and wants to fake a legitimate user/server, the adversary cannot compute the accurate values, so it cannot send valid reply message to the user/server. This is because that the adversary does not know the secret key PSK, h(PSK) and random nonce N 1 and N 2.(15) -
(S3)
Session key agreement: in the proposed scheme, the user and server can share the session key after the authentication phase. Then, they can communicate securely using the shared session key, which encrypts the communication packets. The session key is generated using h(N 1||N 2). N 1 and N 2 change in every session, so session key is different in each session. Therefore, it is difficult for the adversary to compute the session key from the intercepted messages.
-
(S4)Perfect forward secrecy: the proposed scheme computes the session key between the useri and serverj as follows:
Though the user's long-term key A i is compromised, the adversary cannot compute N 1 or N 2 because the adversary cannot calculate the h(PSK) and PSK, so it cannot generate session key between useri and serverj. Therefore, the proposed scheme achieves perfect forward secrecy. Table 1 shows the analysis on the security properties of various multisever authenticated key agreement schemes.(16)
Table 1.
Comparison of security properties.
6.2. Attack Resistance
-
(A1)Replay attack resistance: the proposed scheme is secure against replay attack by adding the random nonce N 1 and the timestamp T i into the message. Though an adversary intercepts the previous authentication message 〈AUIDi, M 1, M 2, D i, T i〉 and sends it to the server, the server can check the illegality of the request using checking N 1 and T i as follows:
So the proposed scheme can prevent the replay attack using N 1 and T i because the adversary cannot compute another M 2 in T i(17) -
(A2)
Modification attack resistance: the adversary can intercept the authentication message and attempt to modify it for illegal authentication. Using a one-way hash function, the proposed scheme checks whether authentication information is modified or not. The adversary cannot obtain the random nonce N i or h(PSK), so the adversary cannot compute a legitimate authentication message. Therefore, the server and user can check whether the authentication message is modified by the adversary or not. Therefore, the proposed scheme is secure against modification attack.
-
(A3)
Stolen-verifier attack resistanc: the registration center and application servers do not have the user's ID/password table or the biometrics. The application server serverj authenticates the legitimate user using h(PSK) and D i. Therefore, the adversary cannot obtain the authentication information about legitimate users even if the adversary gets the authority to access the database of the RC or application servers. Thus, proposed scheme is secure against stolen-verifier attack.
-
(A4)
Off-line guessing attack resistance: an adversary can extract the information stored in smart card using a side-channel attack such as SPA or DPA. So the adversary can know UIDi, B i, C i, D i, and E i, but he cannot figure out a user's password because h(PSK), PSK, BIOi, and x are unknown to the adversary. In proposed scheme, the user's password is always used with the biometrics of the user; h(PWi ⊕ BIOi), which are protected by the one-way hash function. Therefore, the adversary cannot calculate the user's password because biometric information has high entropy. Moreover, the adversary cannot figure out the biometrics because it is impossible for any two people to have the same biometrics template. Therefore, the proposed scheme is secure on off-line guessing attack.
-
(A5)
Forgery attack resistance: a legitimate user cannot attempt to forge another legitimate user. The legitimate useri can know his parameters 〈UIDi, B i, C i, D i, E i, PWi and BIOi〉. However the useri cannot calculate another user's real identity because another user's anonymous identity AUIDi changes in every session and is protected using a random nonce; AUIDi = h(N 1) ⊕ UIDi. Therefore, the proposed scheme is secure against the forgery attack.
-
(A6)
Insider attack resistance: in the proposed scheme, the useri never send plain PWi and BIOi to the registration center RC. The useri sends only h(PWi ⊕ BIOi), so the RC cannot obtain the user's password or biometrics. And the RC cannot compute the PWi using h(PWi ⊕ BIOi) because the biometric information has high entropy. Moreover, h(PWi ⊕ BIOi) is sent through a secure channel and needs not store in the database of RC. So, it is difficult for even insider adversary to figure out user's PWi and BIOi. Therefore, the proposed scheme is secure against the insider attack.
-
(A7)Masquerade attack resistance: the masquerade attack means that an adversary is authenticated with the legitimate server using a fake or real authentication information such as the authentication messages. In Chuang and Chen's scheme, the adversary uses the authentication message between useri and serverj to gain unauthorized access of serverk. This problem occurred because useri and serverj cannot check the destination of authentication message. To solve this problem, the proposed scheme uses AUIDi and SIDj including M 2 as follows:
AUIDi includes UIDi. So the serverj can check whether useri wants to be authenticated with serverj or not. And also M 4 include AUIDi and SIDj as follows:(18)
So the useri can check whether serverj wants to be authenticated with useri or not. The adversary cannot compute M 2 and M 4 because the adversary cannot compute N 1 and N 2. Therefore the proposed scheme is resistant to the masquerade attack.(19) -
(A8)Smart card attack resistance: in the proposed scheme, the smart card stores various information such as 〈UIDi, B i, C i, D i, E i, h()〉. An adversary can obtain all information stored in user's smart card using SPA or DPA. But the adversary cannot compute the session key between useri and serverj using M 1 and M 3 because the adversary cannot compute h(PSK) using obtained information as follows:
Though the adversary obtains B i and M 1, the adversary cannot compute N 1 because of the ignorance about h(PSK). Thus the adversary cannot compute N 2 and SKij. Therefore the proposed scheme is secure against smart card attack.(20) -
(A9)
User impersonation attack resistance: in Chuang and Chen's scheme, an adversary can impersonate the legitimate user using only user's smart card because the adversary can be authenticated to the serverj using user's smart card without user's password or biometrics. However, the proposed scheme uses h(PSK) for protecting D i, N 1, N 2, M 1, and M 3. For example, even though the adversary knows M 1 and B i in M 1 = N 1 ⊕ h(B i) ⊕ h(PSK), the adversary cannot compute N 1 without h(PSK), so he cannot generate the SKij. The adversary cannot know h(PSK) without user's password or biometric. So the adversary cannot impersonate a legal user. Therefore the proposed scheme is secure against the user impersonation attack.
-
(A10)
DoS attack resistance: the proposed scheme checks the freshness of message using timestamp, so it is useless that an adversary sends the previous message to the server. Moreover, the proposed scheme uses M 2 = h(N 1||AUIDi||D i||SIDj||T i) that includes timestamp T i. The server can check the freshness and legality of M 2 because M 2 and the timestamp do not match even though the adversary sends the previous M 2 with the current timestamp. Therefore the proposed scheme is more secure against the DoS attack than Chuang and Chen's scheme.
The proposed scheme is more secure than Chuang and Chen's scheme against the masquerade attack, smart card attack, user impersonation attack, and DoS attack, and also it achieves perfect forward secrecy. Moreover, the proposed scheme is also satisfactory with regard to the anonymity, mutual authentication, session key agreement, replay attack resistance, modification attack resistance, stolen-verifier attack resistance, off-line guessing attack resistance, forgery attack resistance, and insider attack resistance. Table 2 shows the analysis on attack resistance of various multisever authenticated key agreement schemes.
Table 2.
Comparison of attack resistance.
| Attack resistance | D. Yang and B. Yang scheme [10] | Yoon and Yoo scheme [11] | Chuang and Chen scheme [13] | Our scheme |
|---|---|---|---|---|
| (A1) Replay attack | ◯ | × | ◯ | ◯ |
| (A2) Modification attack | ◯ | ◯ | ◯ | ◯ |
| (A3) Stolen-verifier attack | ◯ | ◯ | ◯ | ◯ |
| (A4) Off-line guessing attack | ◯ | × | ◯ | ◯ |
| (A5) Forgery attack | ◯ | × | ◯ | ◯ |
| (A6) Insider attack | × | × | ◯ | ◯ |
| (A7) Masquerade attack | × | × | × | ◯ |
| (A8) Smart card attack | ◯ | × | × | ◯ |
| (A9) User impersonation attack | ◯ | ◯ | × | ◯ |
| (A10) DoS attack | × | × | × | ◯ |
6.3. Efficiency
The efficiency measures include single registration, simple and secure password modification, fast error detection, and low computational cost. In performance, the proposed scheme has similar computational with Chuang and Chen's scheme. Chuang and Chen's scheme has slightly lower computational cost than the proposed scheme, but it is vulnerable to various attacks. The proposed scheme has a little higher computational cost, but it is more secure than Chuang and Chen's scheme. In other words, the proposed scheme solves security problems using similar computational cost as compared with Chuang and Chen's scheme.
-
(E1)
Single registration: in the proposed scheme, a user can be authenticated with various servers. However, the user does not need to register with every servers. To use the server's services, the user registers only one time with the registration center. The proposed scheme provides single registration so the user can anonymously use multiserver system using one registration.
-
(E2)Simple and secure password modification: in the proposed scheme, the user can change the user's password conveniently so that it is easy for the user to change the password anytime. And, the password change phase does not need any communication with the RC. Moreover, an adversary cannot change the password even though the adversary can obtain the smart card and the user's password. This is because that the smart card can check the incorrect biometric information using PWi, BIOi, C i, and B i. The smart card verifies whether h(PWi ⊕ BIOi) ⊕ C i is the same to B i as follows:
(21) -
(E3)
Fast error detection: during the login and password change phases, the smart card detects the error or mistake immediately when the adversary inputs the wrong identification, password, and biometrics information. The smart card can check the error or mistake without the RC's assistance. Therefore the proposed scheme provides fast error detection.
In Table 3, we use the following notations: “·”: that there is no computational cost in that phase, n: the number of users, m: the number of application servers, C h: executing time of one-way hash function, C F: executing time of the fuzzy extractor, C ECC: executing time of the elliptic curve encryption or decryption operation, and C EXP: executing time of the exponential operation. C EXP is higher than C ECC. And C EXP and C ECC are considerably higher than C h. Therefore, the comparison of computational cost on above-mentioned operations is as follows:
| (22) |
And the hash function is generally executed quickly, so it is about 1000 times faster than asymmetric encryption. In D. Yang and B. Yang's scheme, the exponential operation is executed. In Yoon and Yoo's scheme, the elliptic curve encryption or decryption operation is executed. But in Chuang and Chen's scheme and proposed scheme, they use only one-way hash function. Therefore, Chuang and Chen's scheme and proposed scheme are faster than both D. Yang and B. Yang's scheme and Yoon and Yoo's scheme. And our proposed scheme adds only one C h on RC's operation in the registration phase and also adds only one C h on server's operation in authentication phase in comparison with Chuang and Chen's scheme. C h has a little computational cost. Therefore, our proposed scheme has similar computational cost as compared with Chuang and Chen's scheme, but Chuang and Chen's scheme has security vulnerabilities on the masquerade attack, smart card attack, user impersonation attack, and DoS attack as well as no perfect forward secrecy. Our proposed scheme similarly maintains the computational performance and solves the security problems of Chuang and Chen's scheme. Therefore, the proposed scheme is the security enhanced anonymous multiserver authenticated key agreement scheme using the smart card and biometrics.
Table 3.
Comparison of efficiency measures.
| Efficiency measures | D. Yang and B. Yang scheme [10] | Yoon and Yoo scheme [11] | Chuang and Chen scheme [13] | Our scheme |
|---|---|---|---|---|
| (E1) Single registration | ◯ | ◯ | ◯ | ◯ |
| (E2) S/S PW modification | ◯ | ◯ | ◯ | ◯ |
| (E3) Fast error detection | ◯ | ◯ | ◯ | ◯ |
|
| ||||
| (E4) Low computational cost | ||||
| Registration user | · | C h | C h | C h |
| Registration server | · | · | · | · |
| Registration RC | n(3C h + C EXP + C F) | (n + m)C h | n(2C h) | n(2C h) + C h |
| Login user | 4C h + C EXP + C F | 2C h + C ECC | 4C h | 4C h |
| Login server | · | · | · | · |
| Authentication user | C h + C EXP | 3C h + C ECC | 5C h | 5C h |
| Authentication server | 3C h + 2C EXP | 5C h + 2C ECC | 8C h | 9C h |
| Authentication RC | · | 7C h | · | · |
| PW change user | 3C h + C F | 2C h | 3C h | 3C h |
| PW change RC | · | · | · | · |
7. Conclusion
Chuang and Chen proposed an anonymous multiserver authenticated key agreement scheme. This scheme is efficient in that it only requires users to perform hash function evaluations but has various security vulnerabilities. So, we show that this scheme is vulnerable to a masquerade attack, a smart card attack, a user impersonation attack, and a DoS attack and does not achieve perfect forward secrecy. To solve the security problems of Chuang and Chen's scheme, we propose a security enhanced anonymous multiserver authenticated key agreement scheme using smart cards and biometrics. And also, we show how the security weaknesses of Chuang and Chen's scheme are addressed in our scheme and lastly analyze our scheme in terms of both security and efficiency.
Acknowledgments
This research was supported by the Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Science, ICT, and Future Planning (2014R1A1A2002775).
Notations
- x:
A secret value of the registration center
- RC:
The registration center
- UIDi:
The identification of useri
- SIDj:
The identification of serverj
- AUIDi:
The anonymous identification of useri
- PWi:
The password of useri
- BIOi:
The biometrics information of useri
- h():
A secure one-way hash function
- Mi:
ith authenticator exchanged between useri and serverj
- Ni:
A random nonce
- PSK:
A secure pre-shared key among RC and servers
- ||:
A string concatenation operation
- ⊕:
A string XOR operation
- ↔:
Communication through a public channel
- ↔ Secure:
Communication through a secure channel.
Conflict of Interests
The authors do not have a direct financial relation with any institution or organization mentioned in the paper that might lead to a conflict of interests for any of them.
References
- 1.Liao YP, Wang SS. A secure dynamic ID based remote user authentication scheme for multi-server environment. Computer Standards and Interfaces. 2009;31(1):24–29. [Google Scholar]
- 2.Lamport L. Password authentication with insecure communication. Communications of the ACM. 1981;24(11):770–772. [Google Scholar]
- 3.Kocher P, Jaffe J, Jun B. Advances in Cryptology—CRYPTO '99. Berlin, Germany: Springer; 1999. Differential power analysis; pp. 388–397. (Lecture Notes in Computer Science). [Google Scholar]
- 4.Messerges TS, Dabbish EA, Sloan R. Examining smart-card security under the threat of power analysis attacks. IEEE Transactions on Computers. 2002;51(5):541–552. [Google Scholar]
- 5.Chang CC, Lee JS. An efficient and secure multi-server password authentication scheme using smart cards. Computer Communications. 2009;32(4):611–618. [Google Scholar]
- 6.Khan MK, Zhang J. Information Security Practice and Experience 2006. Berlin, Germany: Springer; 2006. An efficient and practical fingerprint-based remote user authentication scheme with smart cards; pp. 260–268. [Google Scholar]
- 7.Ku WC, Chang ST, Chiang MH. Further cryptanalysis of fingerprint-based remote user authentication scheme using smartcards. Electronics Letters. 2005;41(5):240–241. [Google Scholar]
- 8.Li C-T, Hwang M-S. An efficient biometrics-based remote user authentication scheme using smart cards. Journal of Network and Computer Applications. 2010;33(1):1–5. [Google Scholar]
- 9.Li X, Niu JW, Ma J, Wang WD, Liu CL. Cryptanalysis and improvement of a biometrics-based remote user authentication scheme using smart cards. Journal of Network and Computer Applications. 2011;34(1):73–79. [Google Scholar]
- 10.Yang D, Yang B. A biometric password-based multi-server authentication scheme with smart card. Proceedings of the International Conference on Computer Design and Applications (ICCDA '10); June 2010; Qinhuangdao, China. pp. 554–559. [Google Scholar]
- 11.Yoon E-J, Yoo K-Y. Robust biometrics-based multi-server authentication with key agreement scheme for smart cards on elliptic curve cryptosystem. The Journal of Supercomputing. 2013;63(1):235–255. [Google Scholar]
- 12.He D. Security flaws in a biometrics-based multi-server authentication with key agreement scheme. IACR Cryptology ePrint Archive. 2011;365 [Google Scholar]
- 13.Chuang MC, Chen MC. An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Expert Systems with Applications. 2014;41(4):1411–1418. [Google Scholar]
- 14.Tsaur WJ. Networking—ICN 2001. Berlin, Germany: Springer; 2001. A flexible user authentication scheme for multi-server internet services; pp. 174–183. [Google Scholar]
- 15.Li L, Lin I, Hwang M. A remote password authentication scheme for multiserver architecture using neural networks. IEEE Transactions on Neural Networks. 2001;12(6):1498–1504. doi: 10.1109/72.963786. [DOI] [PubMed] [Google Scholar]
- 16.Lin IC, Hwang MS, Li LH. A new remote user authentication scheme for multi-server architecture. Future Generation Computer Systems. 2003;19(1):13–22. [Google Scholar]
- 17.Kim J, Lee D, Jeon W, Lee Y, Won D. Security analysis and improvements of two-factor mutual authentication with key agreement in wireless sensor networks. Sensors. 2014;14:6443–6462. doi: 10.3390/s140406443. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 18.Nam J, Paik J, Won D. Security improvement on Wu and Zhu's protocol for password-authenticated group key exchange. IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences. 2011;E94-A(2):865–868. [Google Scholar]
- 19.Tsaur W, Wu C, Lee W. An enhanced user authentication scheme for multi-server internet services. Applied Mathematics and Computation. 2005;170(1):258–266. [Google Scholar]
- 20.Wu T, Hsu C. Efficient user identification scheme with key distribution preserving anonymity for distributed computer networks. Computers and Security. 2004;23(2):120–125. [Google Scholar]
- 21.Juang WS. Efficient multi-server password authenticated key agreement using smart cards. IEEE Transactions on Consumer Electronics. 2004;50(1):251–255. [Google Scholar]
- 22.Nam J, Choo KKR, Kim J, Kang HK, Paik J, Won D. Password-only authenticated three-party key exchange with provable security in the standard model. The Scientific World Journal. 2014;2014:11 pages. doi: 10.1155/2014/825072.825072 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 23.Choi Y, Lee D, Kim J, Jung J, Nam J, Won D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors. 2014;14:10081–10106. doi: 10.3390/s140610081. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 24.Jeon W, Kim J, Nam J, Lee Y, Won D. An enhanced secure authentication scheme with anonymity for wireless environments. IEICE Transactions on Communications. 2012;95(7):2505–2508. [Google Scholar]