1 Introduction
The electronic medical record (EMR) system is a critical component of a modern health information architecture. EMRs are increasingly connected to a diverse array of systems that support healthcare business operations, such as clinical documentation, laboratory reporting, radiology services, pharmaceutical dispensing, and billing. The complexity of this domain creates challenges for ensuring patient data security and compliance with regulations (e.g., HIPPA). Certain challenges are common across domains and have thus been addressed through traditional solutions. For instance, exploits against the external perimeter of EMR systems are mitigated by network-based intrusion detection systems (IDS), hardening operating systems, and updating security patches. Additionally, access control mechanisms have been adopted by EMRs to enforce users' privileges with respect to patient records. Beyond access control, the notion of experience based access management (EBAM) has been proposed to refine access control assignments via documented user behavior [4].
Other challenges are unique to the clinical domain. First, EMR systems are connected to web portals and exposed to the Internet for a wide range of users; e.g., patients, providers. The vulnerabilities within web-based systems attract various attacks, which are difficult to detect because they exploit the semantics of clinical operations. Second, healthcare organizations use a coarsegrained implementation of access control. This is because access control mechanisms do not scale to manage the large number of clinical functions that can be invoked (e.g., medication ordering, laboratory report editing, consult requests). Third, clinical treatment guidelines are usually too complex to be modeled and explicitly enforced, which may lead to guideline violation by insiders.
Our objective is to build a context-aware anomaly detection system that is customized to the needs of the clinical domain and EMR systems. Our detection system will model the characteristics of EMR systems, monitor the system usage, and detect anomalous user behaviors. This system can help realize the user behavior monitoring component of an EBAM framework.
2 System Framework
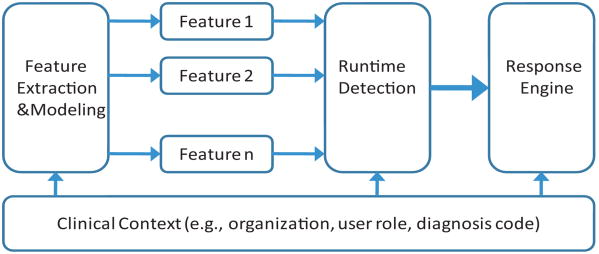
Our anomaly detection system mainly consists of three components, as shown in Fig. 1. (1) The feature extraction and modeling component is responsible for analyzing collected user sessions and establishing normal profiles for EMR users based on extracted features. (2) The runtime detection component aims to evaluate the incoming user session, synthesize its deviations from normal profiles and determine its normality. If the user session is determined abnormal, an alert is generated. (3) The response engine is designed to respond to different alerts with respective actions. Due to coarse access policies and guideline definitions, exceptions are common in the clinical domain, so an anomalous user session may not necessarily imply an intrusion, for instance, when the caregiver is processing a medical emergency. Our system should be able to handle the outliers in training data and respond in a flexible manner by taking into account other context information and security policies. Notably, all components are built on and leverage the context information from the clinical domain, such as the healthcare organization, user roles and patient diagnosis codes.
Figure 1. System framework.
3 Three-tier Workflow Model
The key issue is to discover differentiating features that can accurately characterize the unique behaviors of EMR users. Our preliminary study has been conducted on server traces collected from StarChart [3], an integrated EMR system in operation at Vanderbilt University Medical Center. Our study considers several perspectives, including system-wide usage patterns [7], user EMR access session pattern [6] and dynamic social networks of users [1]. Existing research has shown that behavior-based anomaly detection systems can only achieve limited performances [8]. Directly applying statistical models into user sessions would introduce an overwhelming number of false alerts for the highly interactive EMR system. Therefore, to differentiate normal from anomalous user sessions more precisely, we leverage the clinical workflow, which is one of the unique features associated with the EMR system.
A clinical workflow is the process during which the patient receives healthcare services. An instance of a clinical workflow relates to the role of the user, who initiates such an instance, the diagnosis of the patient and an applicable treatment guideline. In an EMR system, the sequence of operations performed over patient records during the user session is the manifestation of several interleaving workflow instances. Although there are existing techniques for formalizing treatment workflows (e.g., [2, 5]), they are challenging to specialize to enforce more general clinical processes facing the dynamics of a clinical environment (e.g., user role change and emergent scenarios) and overly time-consuming to be developed and deployed. Rather, we extract statistical profiles for clinical workflows from a corpus of observed user sessions.
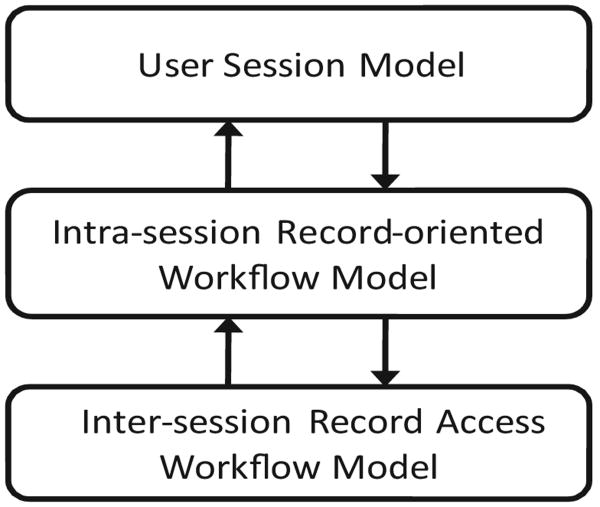
We propose a three-tier workflow model, as illustrated in Fig. 2. The first tier corresponds to the sequence of operations performed by the user during the session (i.e., from login to session termination). The user session model is aimed at profiling user behaviors in general and the basis for evaluating incoming user sessions. The second tier corresponds to the intra-session record-oriented workflow. A user session is possibly embedded with several workflows oriented at different patients. The decomposition of a session into a set of record-specific workflows reveals the clinical workflow between one caregiver and one patient. The third tier corresponds to the inter-session record access workflow. Intra-session workflows are integrated to reflect the treatment procedures that the patient has received, which involve multiple users (or roles). Based on the three-tier workflow model, we can determine the extent to which the incoming user session deviates from the normal profiles.
Figure 2. Three-tier workflow model.
We wish to highlight that several challenges need to be addressed before such an approach is sufficient for application in the clinical domain. First, the workflow patterns for a patient's record may evolve over time due to a number of reasons, for instance, a treatment plan. Second, a patient may be complicated by multiple disorders, which makes it difficult to utilize diagnosis codes directly. Moreover, the granularity of modeling user sessions (i.e., action set or sequence) needs further refinement.
4 Conclusions
In this position paper, we sketched a context-aware anomaly detection framework for clinical environments. The framework uses a three-tier workflow model. In the future, we plan to implement our framework in an EBAM toolkit and evaluate it with several EMR systems.
References
- 1.Chen Y, Malin B. Detection of anomalous insiders in collaborative environments via relational analysis of access logs. ACM CODASPY. 2011:63–74. doi: 10.1145/1943513.1943524. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2.Christov Stefan, et al. Rigorously Defining and Analyzing Medical Processes: An Experience Report. Models in software engineering. 2008:118–131. ch. [Google Scholar]
- 3.Giuse D. Supporting communication in an integrated patient record system. AMIA Annu Symp Proc. 2003:1065. [PMC free article] [PubMed] [Google Scholar]
- 4.Gunter CA, Liebovitz D, Malin B. Experience-based access management: A lifecycle framework to evolve identity and access management systems. IEEE Security and Privacy Magazine. doi: 10.1109/MSP.2011.72. to appear. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 5.Mathe Janos L, et al. A model-integrated, guideline-driven, clinical decision-support system. IEEE Software. 2009;26(4):54–61. [Google Scholar]
- 6.Li X, Xue Y, Malin B. Towards understanding the usage pattern of web-based electronic medical record systems. IEEE IREHSS Workshop. 2011 doi: 10.1109/WoWMoM.2011.5986195. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 7.Malin B, Nyemba S, Paulett J. Learning relational policies from electronic health record access logs. Journal of Biomedical Informatics. 2011;44:333–342. doi: 10.1016/j.jbi.2011.01.007. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 8.Salem MB, Stolfo SJ. Detecting masqueraders: A comparison of one-class bag-of-words user behavior modeling techniques. The 2nd International Workshop on Managing Insider Security Threats (MIST 2010) 2010 [Google Scholar]