Abstract
A smart-card-based user authentication scheme for wireless sensor networks (hereafter referred to as a SCA-WSN scheme) is designed to ensure that only users who possess both a smart card and the corresponding password are allowed to gain access to sensor data and their transmissions. Despite many research efforts in recent years, it remains a challenging task to design an efficient SCA-WSN scheme that achieves user anonymity. The majority of published SCA-WSN schemes use only lightweight cryptographic techniques (rather than public-key cryptographic techniques) for the sake of efficiency, and have been demonstrated to suffer from the inability to provide user anonymity. Some schemes employ elliptic curve cryptography for better security but require sensors with strict resource constraints to perform computationally expensive scalar-point multiplications; despite the increased computational requirements, these schemes do not provide user anonymity. In this paper, we present a new SCA-WSN scheme that not only achieves user anonymity but also is efficient in terms of the computation loads for sensors. Our scheme employs elliptic curve cryptography but restricts its use only to anonymous user-to-gateway authentication, thereby allowing sensors to perform only lightweight cryptographic operations. Our scheme also enjoys provable security in a formal model extended from the widely accepted Bellare-Pointcheval-Rogaway (2000) model to capture the user anonymity property and various SCA-WSN specific attacks (e.g., stolen smart card attacks, node capture attacks, privileged insider attacks, and stolen verifier attacks).
Introduction
The quest to understand real-world phenomena at a fine spatial-temporal resolution has led to a great increase in the interest in wireless sensor networks (WSNs). Where not already in place, a WSN is now being planned and deployed in various application settings such as wildlife monitoring, military surveillance, healthcare diagnostics, and vehicular tracking [1]. Providing an application service in a WSN environment introduces significant security challenges for the involved parties: sensors, users and gateways. One fundamental challenge is to establish a shared session key between a sensor and a user in an authenticated manner (known as authenticated key exchange) via a gateway, and thereby to prevent unauthorized access to sensitive sensor data and their transmissions. Since sensors have severe resource constraints and due to network characteristics such as unattended operation and unreliable communication channel, authenticated key exchange in WSNs is generally regarded as more challenging to achieve than in traditional networks with sufficient computing resources and pre-existing infrastructures. Achieving authenticated key exchange becomes even more difficult when user anonymity is desired. As the concern for privacy increases in our lives, user anonymity has become a vital security property in various WSN applications as well as in many other applications like location-based services, e-voting, mobile roaming services, and anonymous web browsing.
A smart-card-based user authentication scheme for WSNs (in short, a sca-wsn scheme) allows a user holding its smart card issued by the gateway to achieve authenticated key exchange with a sensor, preferably in a way that its anonymity is preserved. Since the early work of Das [2], He et al. [3], Khan and Alghathbar [4] and Chen and Shih [5], all of which provide no key-exchange functionality, the design of sca-wsn schemes has attracted much attention from researchers due to their potential to be widely deployed, and a number of proposals offering various levels of security and efficiency have been presented [6–20]. Some schemes consider only authenticated key exchange [6, 8, 9, 12, 20] while others attempt to additionally provide user anonymity [7, 10, 11, 13–19]. Schemes such as the ones in [6, 12, 20] employ elliptic curve cryptography to provide perfect forward secrecy while most schemes [7–11, 13–19] use only lightweight cryptographic techniques, such as symmetric encryptions, message authentication codes and hash functions, to focus on improving the efficiency.
One common security requirement for sca-wsn schemes is to ensure that:
only a user who is in possession of both a smart card and the corresponding password can be successfully authenticated (by the gateway) and access the sensor data.
This requirement is commonly referred to as two-factor security [21–25] and is modelled via an adversary who is able to either extract all the information inside the smart card of a user or learn the password of the user, but not both. (Clearly, there is no means to prevent the adversary from impersonating a user if both the information in the smart card and the password of the user are disclosed.) The former requires physical access to the smart card and then mounting a side-channel attack [26, 27] on the (lost, misplaced or stolen) card, while the latter can be achieved with shoulder-surfing or by using a malicious card reader. Any attack exploiting the former ability is commonly called a stolen smart card attack and is considered practical under the assumption that users’ smart cards are non-tamper-resistant. Accordingly, sca-wsn schemes should be designed to achieve their intended security properties, such as authenticated key exchange and user anonymity, against stolen smart card attacks.
Despite the many research efforts to date, it remains a challenging task to design an efficient sca-wsn scheme that provides user anonymity. The recent work of Wang and Wang [28, 29] shows that, under the non-tamper-resistance assumption of smart cards, no sca-wsn scheme can provide user anonymity without recourse to public key cryptography. This result is somewhat surprising because it implies that all existing anonymous schemes using only lightweight cryptographic techniques [7, 10, 11, 13–19] fail to achieve user anonymity in the presence of an adversary who can mount a stolen smart card attack. As an example of such a failure, we here take the recent sca-wsn scheme of Jiang et al. [19] which has been presented with a claim of user anonymity. To illustrate the failure, we only need to examine the user registration and login request phases of the scheme. Let MK be the master key of the gateway GW, and H be a cryptographic hash function. Then, the two phases proceed as follow:
- User Registration. A user U registers with GW as follows:
- U chooses its identity ID U and password PW U, generates a random number r, computes RPW U = H(r‖PW U), and submits ID U and RPW U to GW via a secure channel.
- If ID U is valid, GW generates a temporary identity for U, TID U, and computes TC U = H(MK‖ID U‖TE U) and PTC U = TC U⊕RPW U, where TE U is the expiration time of TID U. GW then stores (TID U, ID U, TE U) in its verification table, and issues U a smart card containing {H(⋅), TID U, TE U, PTC U}.
- U stores the random number r into the smart card, which then holds {H(⋅), TID U, TE U, PTC U, r}.
Login Request. U inserts its smart card into a card reader, and inputs ID U and PW U. The smart card retrieves the current timestamp T U, selects a random key K U, and computes TC U = PTC U⊕H(r‖PW U), PKS U = K U⊕H(TC U‖T U) and C U = H(ID U‖K U‖TC U‖T U). Then, U sends the login request message M U = ⟨TID U, C U, PKS U, T U⟩ to GW.
Assume an attacker A who has obtained the information {H(⋅), TID U, TE U, PTC U, r} stored on the smart card of user U. A eavesdrops and obtains the login request message M U = ⟨TID U, C U, PKS U, T U⟩, and mounts the following offline dictionary attack.
Step 1. A makes a guess on the password PW U and computes and .
Step 2. For each possible identity , A computes and verifies the correctness of and by checking that is equal to C U. Note that, with an overwhelming probability, if and only if and .
Step 3. A repeats Steps 1 and 2 until the correct password and identity are found.
This dictionary attack works because the identity space is very limited in practice, being usually even smaller than the password space [28, 29]. All other schemes using only lightweight cryptographic techniques are also vulnerable to similar dictionary attacks, as shown in [28, 29]. Note that simply using a symmetric encryption scheme cannot overcome the inherent failure. Although there are some published schemes that employ elliptic curve cryptography [6, 12, 20], these schemes were designed with no user anonymity in the first place and moreover, are not efficient in the sense that they impose expensive scalar-point multiplications on resource-constrained sensors.
In this paper, we present an efficient and provably-anonymous sca-wsn scheme that requires sensors to perform only lightweight cryptographic operations. Our scheme employs elliptic curve cryptography but restricts its use to anonymous user-to-gateway authentication in order not to impose any (expensive) public-key operations, such as scalar-point multiplications and map-to-point operations, on sensors. We formally prove that our scheme achieves user anonymity as well as authenticated key exchange in an extension of the widely accepted model of Bellare et al. [30]. In proving the security properties, we assume that the cryptographic hash functions used are random oracles and the elliptic curve computational Diffie-Hellman problem is computationally hard. The extended model captures not only the notion of two-factor security but also standard attacks against sca-wsn schemes like node capture attacks, privileged insider attacks, and stolen verifier attacks.
The remainder of this paper is structured as follows. Section 2 describes an extended security model for the analysis of anonymous sca-wsn schemes. Section 3 presents our proposed sca-wsn scheme along with cryptographic primitives on which the security of the scheme relies. Section 4 provides proofs for the security properties of our proposed scheme in the extended security model. Section 5 concludes the paper with a comparative efficiency and security of our scheme and other sca-wsn schemes.
A Security Model for Anonymous sca-wsn Schemes
This section describes a security model extended from the Bellare et al.’s model [30] to analyze authentication and key exchange protocols of anonymous sca-wsn schemes. Our security model captures the notion of two-factor security as well as the resistance to node capture attacks, privileged insider attacks, stolen verifier attacks, and other common attacks. We provide two security definitions associated with the model, one for authenticated key exchange and one for user anonymity, which collectively define a secure, anonymous sca-wsn scheme.
Participants
Let 𝓢𝓝 and 𝓤 be the sets of all sensors and users, respectively, registered with the gateway GW. Let 𝓔 = 𝓤∪𝒮𝓝∪{GW}. We identify each entity E ∈ 𝓔 by a string, and interchangeably use E and ID E to refer to this identifier string. To formally capture the user anonymity property, we assume that: (1) each user U ∈ 𝓤 has its pseudo identity PID U in addition to the true identity ID U and (2) the adversary 𝓐 is given only PID U but not ID U.
Protocol Executions
A user U ∈ may run multiple sessions of the authentication and key exchange protocol of a sca-wsn scheme, either serially or concurrently, to establish a session key with a sensor SN ∈ 𝒮𝓝 via assistance of the gateway GW. Therefore, at any given time, there could be multiple instances of the entities U, SN and GW. We use to denote instance i of entity E ∈ 𝓔. Instances of U and SN are said to accept when they compute a session key in an execution of the protocol. We denote the session key of by .
Long-Lived Keys
During the initialization of the protocol,
each U ∈ 𝓤 chooses its password PW U from a fixed dictionary 𝒟, and
GW generates its master secret(s), issues a smart card to each U ∈ 𝓤, and shares a cryptographic key with each SN ∈ 𝒮𝓝.
Partnering
Informally, two instances are said to be partners of each other if they participate together in the same protocol session and as a result, compute the same session key. Formally, partnering between instances is defined in terms of the notion of session identifier. A session identifier (sid) is an identifier of a protocol session and is typically defined as a function of the messages exchanged in the session. Let denote the sid of instance . We say that two instances, and , are partners if (1) both the instances have accepted and (2) .
Adversary Capabilities
We assume there exists an adversary 𝓐 running in a probabilistic polynomial time (ppt) in the security parameter κ, which represents the bit-length of session keys. We note that the size of the dictionary 𝒟 is a fixed constant that is independent of the security parameter κ. The ppt adversary 𝓐 has complete control of all communications between entities, can request for access to session keys and long-term keys, and can extract user’s information stored on the smart card. These capabilities of 𝓐 are modeled via the following oracle queries which are allowed for 𝓐 to make.
(, , ): This query models passive attacks against the protocol. It prompts an execution of the protocol between the instances , and , and outputs the transcript of the protocol execution to 𝓐.
(): This query sends a message m to an instance , modelling active attacks against the protocol. Upon receiving m, the instance proceeds according to the protocol specification. The message output by , if any, is returned to 𝓐. A query of the form (, start:⟨SN, GW⟩) prompts to initiate a protocol session with instances of SN and GW.
(): This query captures the notion of known key security. The instance , upon receiving the query and if it has accepted, returns the session key, , back to 𝓐.
: These queries together capture the notion of two-factor security. The former returns the password of U while the latter returns the information stored in the smart card of U.
(SN): This query returns the long-lived secret(s) of the sensor SN, modelling node capture attacks.
(GW), modelling privileged insider attacks.
(GW): This query returns the password verifiers stored by GW, modelling stolen verifier attacks.
(): This query is used for determining whether the protocol achieves authenticated key exchange or not. If has accepted, then depending on a random bit b chosen by the oracle, 𝓐 is given either the real session key if b = 1 or a random key drawn from the session-key space if b = 0.
(U): This query is used for determining whether the protocol provides user anonymity or not. Depending on a randomly chosen bit b, 𝓐 is given either the identity actually used for U in the protocol sessions (when b = 1) or a random identity drawn from the identity space (when b = 0).
queries all together also capture the notion of perfect forward secrecy. SN and GW are said to be corrupted when they are asked a query while U is considered as corrupted if it has been asked both and queries.
Authenticated Key Exchange (AKE)
The AKE security of an authentication and key exchange protocol P is defined via the notion of freshness. Intuitively, a fresh instance is one that holds a session key which should not be known to the adversary 𝓐, and an unfresh instance is one whose session key (or some information about the key) can be known by trivial means. A formal definition of freshness follows:
Definition 1 (Freshness). An instance is fresh if none of the following occurs:
𝓐 queries or , where is the partner of .
𝓐 queries both and when U is E itself or the peer entity of E.
𝓐 queries when SN is E itself or the peer entity of E.
𝓐 queries .
Note that this definition of freshness is unable to capture the notion of perfect forward secrecy. (As explained in the next section, the authentication and key exchange protocol of our scheme does not provide perfect forward secrecy.) The AKE security of protocol P is defined in the context of the following two-stage experiment:
Experiment ExpAKE 0:
- Stage 1. 𝓐 makes any oracle queries at will, except that:
- 𝓐 is not allowed to make the () query if the instance is not fresh.
- 𝓐 is not allowed to make the () query if it has already made a query to or its partner instance.
- 𝓐 is not allowed to access to the oracle.
Stage 2. Once 𝓐 decides that Stage 1 is over, it outputs a bit b ′ as a guess on the hidden bit b chosen by the oracle. 𝓐 is said to succeed if b = b ′.
Let be the event that 𝓐 succeeds in the experiment ExpAKE 0, and denote the advantage of 𝓐 in breaking the AKE security of protocol P. Then, we define .
Definition 2 (AKE Security). An authentication and key exchange protocol P is AKE-secure if is negligible for any ppt adversary 𝓐.
User Anonymity
An authentication and key exchange protocol that does not provide user anonymity may still be rendered AKE-secure. That is, the AKE security does not imply user anonymity. Therefore, a new, separate definition is necessary to capture the user anonymity property. Our definition of user anonymity is based on the notion of cleanness.
Definition 3 (Cleanness). A user U ∈ 𝓤 is clean if none of the following occurs:
𝓐 queries both and .
𝓐 queries .
Note that the definition of cleanness does not impose any restriction on making queries to sensors. This reflects our objective to achieve user anonymity even against sensors.
User anonymity is formalized in the context of the following two-stage experiment:
Experiment ExpUA 0:
- Stage 1. 𝓐 makes any oracle queries at will, except that:
- 𝓐 is not allowed to make the (U) query if the user U is not clean.
- 𝓐 is not allowed to corrupt GW and U if it has already made the query.
- 𝓐 is not allowed to access to the oracle.
Stage 2. Once 𝓐 decides that Stage 1 is over, it outputs a bit b ′ as a guess on the hidden bit b chosen by the oracle. 𝓐 is said to succeed if b = b ′.
Let be the event that 𝓐 succeeds in the experiment ExpUA 0, and denote the advantage of 𝓐 in attacking the user anonymity of protocol P. Then, we define .
Definition 4 (User Anonymity). An authentication and key exchange protocol P provides user anonymity if is negligible for any ppt adversary 𝓐.
Our Proposed Scheme
Our sca-wsn scheme restricts the use of elliptic curve cryptography to anonymous user-to-gateway authentication and thereby allows sensor nodes to perform only lightweight cryptographic operations such as symmetric encryption/decryption, MAC generation/verification, and hash function evaluation. We begin by describing the cryptographic building blocks on which the security of our scheme depends.
Building Blocks
Elliptic curve computational Diffie-Hellman (ECCDH) problem
Let 𝔾 be an elliptic curve group of prime order q. Typically, 𝔾 will be a subgroup of the group of points on an elliptic curve over a finite field. Any elliptic curve and finite field recommended by NIST [31] can be used to instantiate the group 𝔾. The recent work of Choi et al. [20], for example, describes a typical elliptic curve group of a prime order. Let P be a generator of 𝔾. The ECCDH problem for 𝔾 is to compute xyP ∈ 𝔾 when given two elements (xP,yP) ∈ 𝔾2, where . We say that the ECCDH assumption holds for 𝔾 if it is computationally infeasible to solve the ECCDH problem for 𝔾. Let be the advantage of an algorithm 𝓐 in solving the ECCDH problem for 𝔾 and be defined as . We assume that is negligible for all ppt algorithms 𝓐 (i.e., the ECCDH assumption holds in 𝔾). We denote by the maximum value of over all algorithms 𝓐 running in time at most t.
Message authentication code schemes
A message authentication code (MAC) scheme Σ is a pair of efficient algorithms (, ) where: (1) the MAC generation algorithm takes as input an ℓ-bit key k and a message m, and outputs a MAC σ; and (2) the MAC verification algorithm takes as input a key k, a message m, and a MAC σ, and outputs 1 if σ is valid for message m under the key k or outputs 0 if σ is invalid. We require that Σ should achieve the strong existential unforgeability against chosen message attacks. To formally define this requirement, let be the probability that an adversary 𝓐, who mounts an adaptive chosen message attack against Σ with oracle access to and , outputs a message/tag pair (m, σ) such that: (1) and (2) σ has not been output by the oracle as a MAC on the message m. The, we say that the MAC scheme Σ is secure if is negligible for every ppt adversary 𝓐. We use to denote the maximum value of over all adversaries 𝓐 running in time at most t.
Cryptographic hash functions
Let κ be the bit-length of session keys, ℓ be as defined for Σ, and ω be the bit-length of EID U (see the registration phase of our scheme described in the next section). Then, our scheme uses three cryptographic hash functions H:{0, 1}* → {0, 1}κ, J:{0, 1}* → {0, 1}ℓ, and I:{0, 1}* → {0, 1}ω. These hash functions are modelled as random oracles in our security proofs.
Symmetric encryption schemes
A symmetric encryption scheme Δ is a pair of efficient algorithms (, ) where: (1) the encryption algorithm takes as input an ℓ-bit key k and a plaintext message m, and outputs a ciphertext c; and (2) the decryption algorithm takes as input a key k and a ciphertext c, and outputs a message m. For an eavesdropping adversary 𝓐 against Δ, and for an integer n ≥ 1 and a random bit b ∈ R{0, 1}, consider the following indistinguishability experiment where only a single encryption key is used:
Experiment
k ∈R {0, 1}ℓ
for i = 1 to n
(m i, 0, m i,1) ← 𝓐(Δ)
𝓐(ci)
b ′ ← 𝓐, where b ′ ∈ {0, 1}
return b ′
We use to denote the advantage of 𝓐 in violating the indistinguishability of Δ in experiment , and define it as
We say that the symmetric encryption scheme Δ is secure if is negligible for every ppt eavesdropper 𝓐. Let be the maximum value of over all 𝓐 running in time at most t.
We now claim that if a symmetric encryption scheme is secure with respect to a single encryption key, then it is also secure with respect to multiple encryption keys. Now consider the following indistinguishability experiment where d encryption keys are used:
Experiment
for i = 1 to d
ki ∈R {0, 1}ℓ
for j = 1 to n
(m i,j,0, m i,j,1) ← 𝓐(Δ)
c i,j ← Enc ki(m i,j,b)
𝓐(c i,j)
b ′ ← 𝓐, where b ′ ∈ {0, 1}
return b ′
We define and respectively as
and
where the maximum is over all 𝓐 running in time at most t.
Lemma 1. For any symmetric encryption scheme Δ,
where d is as defined for experiment .
Proof. Assume an adversary 𝓐 who attacks the indistinguishability of Δ in with time complexity t. The proof proceeds with a standard hybrid argument [32]. Consider a sequence of d + 1 hybrid experiments , 0 ≤ ξ ≤ d, where each , n, d, b) is different from only in that each c i,j is set as follows:
The experiments and at the extremes of the sequence are identical to the experiments and , respectively. As we move from to in the sequence, we change the n ciphertexts c ξ,1, …, c ξ,n from encryptions of the first plaintexts to encryptions of the second plaintexts. Since there are d such moves from to , the inequality of the lemma follows immediately if we prove that the difference between the probabilities that 𝓐 outputs 1 in any two neighboring experiments and is at most . That is, to complete the proof, it suffices to show that for any 1 ≤ ξ ≤ d,
| (1) |
Let . Then, to prove Equation 1, we will construct, from 𝓐, an adversary 𝓐ξ who attacks the indistinguishability of Δ in with advantage ɛ.
𝓐ξ begins by invoking adversary 𝓐, then proceeds to simulate the indistinguishability experiment for 𝓐, and finally ends by outputting whatever bit 𝓐 eventually outputs. In the simulated experiment, 𝓐ξ generates the ciphertexts exactly as in the hybrid experiment except that it generates c ξ,1, …, c ξ,n as follows:
When 𝓐 outputs the n plaintext pairs (m ξ,1,0,m ξ,1,1), …, (m ξ,n,0,m ξ,n,1), 𝓐ξ outputs them as its own plaintext pairs in experiment , receives in return the ciphertexts c 1, …, c n, and sets c ξ,1 = c 1, …, c ξ,n = c n.
Then, it follows that:
the probability that 𝓐ξ outputs 1 when the given ciphertexts are the encryptions of the first plaintexts is equal to the probability that 𝓐 outputs 1 in the experiment , and
the probability that 𝓐ξ outputs 1 when the given ciphertexts are the encryptions of the second plaintexts is equal to the probability that 𝓐 outputs 1 in the experiment .
That is:
Since 𝓐ξ has time complexity t, it follows that by definition. This completes the proof of Equation 1 and hence the proof of Lemma 1.
Description of the Scheme
The scheme consists of three phases: the registration phase, the authentication and key exchange phase, and the password update phase. During the system initialization, the gateway GW determines the following public parameters: (1) an elliptic curve group 𝔾 with a generator P of prime order q, (2) a MAC scheme , (3) a symmetric encryption scheme , and (4) three hash functions H, J and I. We assume that these parameters are known to all parties in the network including the adversary 𝓐. As part of the system initialization, GW chooses two master secrets and z ∈ {0, 1}ℓ, computes its public key Y = yP, and shares a secret key k GS = J(ID SN‖z) with each sensor SN.
Registration phase
A user U should register itself with the gateway GW before it can ever gain access to the sensor network and data. The registration proceeds as follows:
U chooses its identity ID U and password PW U at will, and submits the identity ID U to GW via a secure channel.
GW computes and issues U a smart card loaded with {EID U, Y, ID GW, 𝔾, P, Σ, Δ, H, J, I}. (We assume that q is implicit in 𝔾.)
U replaces EID U with XEID U = EID U⊕I(ID U‖PW U).
Authentication and key exchange phase
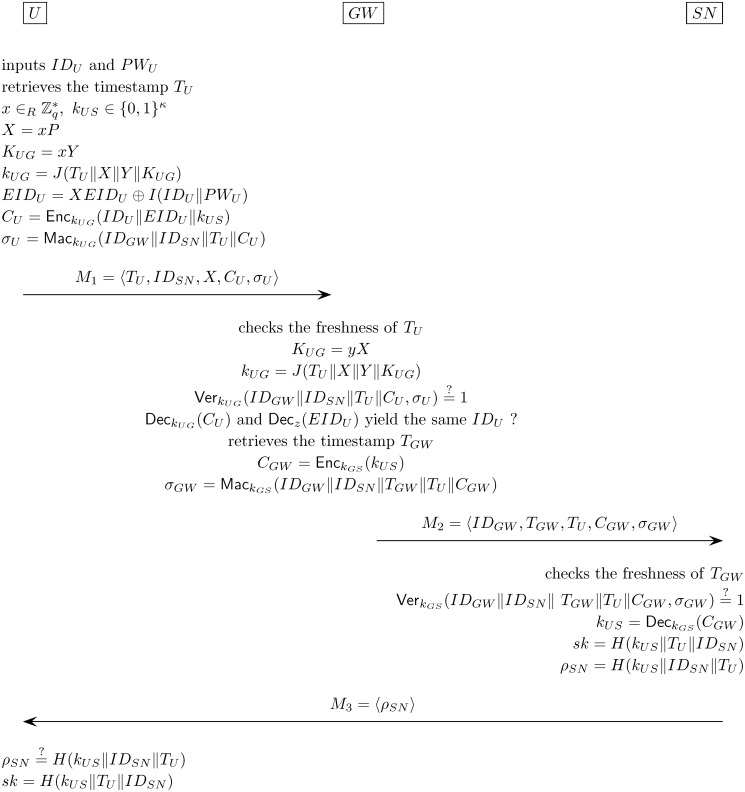
U needs to perform this phase with SN and GW whenever it wishes to access to the sensor network and data. The steps of the phase are depicted in Fig. 1 and are described as follows:
- Step 1. U inserts its smart card into a card reader and inputs its identity ID U and password PW U. Then, the smart card retrieves the current timestamp T U, selects two random and k US ∈ {0, 1}κ, and computes
After the computations, the smart card sends the message M 1 = ⟨T U,ID SN,X,C U,σ U⟩ to the gateway GW. - Step 2. GW rejects the message M 1 (and aborts the session) if T U is not fresh. Otherwise, GW computes K UG = yX and k UG = J(T U‖X‖Y‖K UG), and checks if T U‖C U,σ U) = 1. If the check fails, GW aborts the session. Otherwise, GW decrypts C U with key k UG and then EID U with key z, and checks if the decryption of EID U yields the same ID U as produced through the decryption of C U. If only the two IDs match, GW retrieves the current timestamp T GW, computes
and sends the message M 2 = ⟨ID GW,T GW,T U,C GW,σ GW⟩ to the sensor SN. - Step 3. Upon receiving M 2, SN verifies that (1) T GW is fresh and (2) T U‖C GW,σ GW) = 1. If any of the verifications fails, SN aborts the session. Otherwise, SN decrypts C GW to obtain k US and computes the session key sk and the authenticator ρ SN as follows:
Then, SN sends the message M 3 = ⟨ρ SN⟩ to the user U. Step 4. With M 3 in hand, U checks if ρ SN is equal to H(k US‖ID SN‖T U). U aborts the session if the check fails or otherwise computes the session key sk = H(k US‖T U‖ID SN).
Fig 1. Our proposed authentication and key exchange protocol for wireless sensor networks.
Password update phase
One of the recommended guidelines for achieving better password security is to enforce regular password updates. In our scheme, users can change their passwords either non-interactively or interactively. The non-interactive password change procedure proceeds as follows:
U inserts his smart card into a card reader and enters the identity ID U, the current password PW U, and the new password .
The smart card computes and replaces XEID U with .
Although this procedure is simple and non-interactive, it may render the smart card unusable if the user enters a wrong password by mistake or an adversary intentionally inputs an arbitrary password after gaining temporary access to the smart card. When an invalid password is entered, subsequent login requests of the user will be rejected unless it reregisters with the gateway. This problem can be addressed by storing a password verifier on the smart card, which is used to check the correctness of the user-given password. However, as soon as the smart card contains a password verifier, the scheme becomes vulnerable to an offline dictionary attack under the non-tamper-resistance assumption of smart cards and, consequently, fails to achieve two-factor security. This is clearly unacceptable and, therefore, we suggest the following interactive password change procedure.
U inserts his smart card into a card reader and enters the identity ID U, the current password PW U, and the new password .
- The smart card retrieves the current timestamp T U, selects a random , and computes
The smart card sends a password update request ⟨T U,X,C U⟩ to the gateway GW. GW rejects the request if T U is not fresh. Otherwise, GW computes K UG = yX and k UG = J(T U‖X‖Y‖K UG), decrypts C U with key k UG and then EID U with key z, and checks whether the two decryptions return the same ID U. If the check succeeds, GW computes ρ GW = H(ID GW‖ID U‖X‖k UG) and sends it to the smart card. Otherwise, GW sends a failure message to the smart card.
The smart card aborts the password change procedure if it receives a failure message or ρ GW is not equal to H(ID GW‖ID U‖X‖k UG). Otherwise, it sets .
This interactive password change procedure provides a secure yet practical way of updating user password, though it is more expensive than the non-interactive one.
Performance and Security Comparison
In Table 1, we provide a comparative summary between our scheme and other sca-wsn schemes both in terms of computation and security. As shown in the table, our scheme requires the sensor SN to perform only lightweight cryptographic operations while enjoying provable anonymity in an extension of the widely accepted model of Bellare et al. [30]. While the recent schemes of Shi & Gong [12] and Choi et al. [20] provide forward secrecy, they impose 2 scalar-point multiplications on the resource-constrained sensor SN. Note that scalar-point multiplication is much more expensive than the lightweight cryptographic operations considered in the table, such as symmetric encryption/decryption, MAC generation/verification, and hash function evaluation. Moreover, these two schemes fail to achieve user anonymity despite their use of elliptic curve cryptography. The schemes presented in [10, 11, 13–19] are computationally efficient, but suffer from the inherent failure of user anonymity. To the best of our knowledge, all existing sca-wsn schemes fall into one of the two classes.
Table 1. A comparative summary of smart-card-based user authentication schemes for wireless sensor networks.
| Scheme | Computation | Security | |||||
|---|---|---|---|---|---|---|---|
| SN | U+SN+GW | SKS | UA | FS | RSSC | RNC | |
| Jiang et al. [19] | 5H | 22H | Yes | No | No | No | Yes |
| Khan & Kumari [18] | 7H | 3E+20H | Yes | No | No | No | Yes |
| Kim et al. [17] | 2H | 18H | Yes | No | No | No | Yes |
| Chi et al. [16] | 2E+1A+1H | 4E+1A+5H | Yes | No | No | No | Yes |
| He et al. [15] | 2E+1H | 10E+7H | Yes | No | No | No | Yes |
| Kumar et al. [14] | 2E+1H | 7E+8H | Yes | No | No | No | Yes |
| Li et al. [13] | 6H | 26H | Yes | No | No | No | Yes |
| Xue et al. [11] | 6H | 22H | Yes | No | No | No | Yes |
| Vaidya et al. [10] | 2H | 15H | Yes | No | No | No | No [17] |
| Our scheme | 1E+1A+2H | 3M+5E+4A+7H | Yes | Proven | No | Yes | Yes |
| Choi et al. [20] | 2M+5H | 6M+18H | Yes | No | Yes | No | Yes |
| Shi & Gong [12] | 2M+4H | 6M+15H | No [20] | No | Yes | No | Yes |
| Yeh et al. [6] | 2M+1P+2H | 8M+2P+9H | No [33] | No | No [33] | No | Yes |
SKS: session key security; UA: user anonymity; FS: forward secrecy; RSSC: resistance to stolen smart card attacks; RNC: resistance to node capture attacks.
M: scalar-point multiplication; P: map-to-point operation; E: symmetric encryption/decryption; A: MAC generation/verification; H: hash function evaluation.
According to Crypto++ 5.6.0 benchmarks that ran on an Intel Core 2 1.83 GHz processor under Windows Vista in 32-bit mode, SHA-1 and HMAC take 11.4 and 11.9 cycles per byte respectively; while AES (with 128-bit key) takes 12.6 to 16.9 cycles per byte, depending on the operation mode used—see Table 2 and we refer interested readers to http://www.cryptopp.com/benchmarks.html for Crypto++ benchmarks for commonly used cryptographic algorithms.
Table 2. Crypto++ 5.6.0 benchmarks for SHA-1, HMAC and AES.
| Algorithm | SHA-1 | HMAC (SHA-1) | AES (with 128-bit key) | ||||
|---|---|---|---|---|---|---|---|
| CTR | CBC | OFB | CFB | ECB | |||
| Cycles Per Byte | 11.4 | 11.9 | 12.6 | 16.0 | 16.9 | 16.1 | 16.0 |
Our scheme requires the sensor SN to perform 1E+1A+2H operations which amount to about 4.5H operations. Therefore, in terms of computational requirements for SN, our scheme is comparable with other sca-wsn schemes [11, 13–16, 18, 19] using only lightweight cryptographic techniques. Although the schemes of Vaidya et al. [10] and Kim et al. [17] require SN to perform only 2 hash function evaluations, these schemes do not achieve user anonymity and are vulnerable to a stolen smart card attack. Under the non-tamper-resistance assumption of smart cards, our scheme is the only one that provides user anonymity and resists stolen smart card attacks.
Security Proofs
We now prove that the authentication and key exchange protocol of our scheme is AKE-secure (in the sense of Definition 2) and provides user anonymity (in the sense of Definition 4). Recall that the security model described in Section 2 captures various sca-wsn specific attacks (such as stolen smart card attacks, node capture attacks, privileged insider attacks, and stolen verifier attacks) as well as other common attacks (like impersonation attacks, man-in-the-middle attacks, replay attacks, and known key attacks) [21, 23, 25, 34]. Before providing formal security proofs in the model, we briefly discuss the security of our scheme against sca-wsn specific attacks.
Stolen smart card attacks. Our scheme does not require a password verifier to be stored on the smart card of user U. Moreover, even if an adversary managed to obtain the ciphertext , the adversary would be unable to exploit C U as a password verifier since, under the ECCDH assumption, it is infeasible to compute k UG = J(T U‖X‖Y‖K UG) from X and Y. Thus, our scheme is resistant against stolen smart card attacks.
Node capture attacks. In our scheme, each sensor node SN holds its individual secret key k GS = J(ID SN‖z) which is shared only with the gateway GW. In other words, different sensor nodes have different secret keys (with an overwhelming probability). Thus, the secret key k GS obtained by capturing a sensor node SN will be of no use in impersonating another sensor node SN ′ who holds a secret key other than k GS. Therefore, node capture attacks are not possible against our scheme.
Privileged insider attacks. A privileged insider attack occurs when the gateway administrator can access a user’s password to impersonate the user. In our scheme, the gateway GW receives no password-related information from the user U and does not manage any table for storing such information. It is thus clear that privileged insider attacks cannot be mounted against our scheme.
Stolen verifier attacks. In a stolen verifier attack, the adversary attempts to impersonate a legitimate user by stealing the user’s password verifier stored on the gateway GW. However, in our scheme, GW does not store a password verifier of any kind but stores only two master secrets y and z which are selected independently of user passwords. Hence, our scheme is secure against stolen verifier attacks.
User Anonymity
Theorem 1. Our authentication and key exchange protocol, P, provides user anonymity in the random oracle model under the ECCDH assumption in 𝔾 and the security of the symmetric encryption scheme Δ.
Proof. Let 𝓐 be a ppt adversary against the user anonymity property of protocol P. We prove the theorem by making a series of modifications to the original experiment ExpUA 0, bounding the difference in the success probability of 𝓐 between two consecutive experiments, and ending up with an experiment where 𝓐 has a success probability of 1/2 (i.e., 𝓐 has no advantage). Let denote the event that 𝓐 correctly guesses the hidden bit b chosen by the oracle in experiment ExpUA i. Let be the maximum time required to perform the experiment ExpUA i involving the adversary 𝓐.
Experiment ExpUA 1. In this experiment, we simulate the random oracle J as follows:
Simulation of the J oracle: For each J query on a string str, the simulator first checks if an entry of the form (str,j) is in a list called JList which contains all the input-output pairs of J. If such an entry exists in JList, the simulator returns j as the output of the J query. Otherwise, the simulator chooses a random ℓ-bit string j ′, returns j ′ in response to the query, and adds the entry (str,j ′) to JList.
For all other oracle queries of 𝓐, the simulator answers them as in the original experiment ExpUA 0. Then, ExpUA 1 is perfectly indistinguishable from ExpUA 0 and therefore, Claim 1 holds.
Claim 1. .
Experiment ExpUA 2. Here, we modify the experiment so that X is computed as follows:
The ExpUA 2 modification:
The simulator chooses a random exponent and computes A = aP.
For each user instance, the simulator chooses a random and sets X = rA.
As a result of the modification, each K UG is set to rayP for some random . Since the view of 𝓐 is identical between ExpUA 2 and ExpUA 1, it follows that:
Claim 2. .
Experiment ExpUA 3. We next modify the computations of X and Y as follows:
The ExpUA 3 modification:
The simulator chooses two random elements A, B ∈ 𝔾 and sets Y = B.
For each instance of clean users, the simulator chooses a random and sets X = rA. For other instances, the simulator computes X as in experiment ExpUA 2.
For each instance of clean users, the simulator sets each k UG to a random ℓ-bit string. For other instances, the simulator computes k UG as in experiment ExpUA 2.
Since k UG is set to a random ℓ-bit string (for instances of clean users), the success probability of 𝓐 may be different between ExpUA 3 and ExpUA 2 if it makes an J(T U‖X‖Y‖K UG) query. However, this difference is bounded by Claim 3.
Claim 3. , where qJ is the number of queries made to the J oracle.
Proof. We prove the claim via a reduction from the ECCDH problem which is believed to be hard. Assume that the success probability of 𝓐 is non-negligibly different between ExpUA 3 and ExpUA 2. Then we construct an algorithm 𝓐ECCDH that solves the ECCDH problem in 𝔾 with a non-negligible advantage. The objective of 𝓐ECCDH is to compute and output the value W = uvP ∈ 𝔾 when given an ECCDH-problem instance (U = uP, V = vP) ∈ 𝔾2. 𝓐ECCDH runs 𝓐 as a subroutine while simulating all the oracles on its own.
𝓐ECCDH handles all the oracle queries of 𝓐 as specified in experiment ExpUA 3 but using U and V in place of X and Y. When 𝓐 outputs its guess b ′, 𝓐ECCDH chooses an entry of the form (T U‖X‖Y‖K,j) at random from JList and terminates outputting K/r. From the simulation, it is clear that 𝓐ECCDH outputs the desired result W = uvP with probability at least 1/q J if 𝓐 makes a J(T U‖X‖Y‖K UG) query for some instance of a clean user U ∈ 𝓤. This completes the proof of Claim 3.
Experiment ExpUA 4. We finally modify the experiment so that, for each clean user U ∈ 𝓤, a random identity drawn from the identity space is used in place of the true identity ID U in generating C U.
Claim 4. .
Proof. We prove the claim by constructing an eavesdropping adversary 𝓐IND-MEK who attacks the indistinguishability of Δ in with advantage equal to (see Section 1 for details of experiment ).
𝓐IND-MEK begins by choosing a random bit b ∈ {0, 1}. Then, 𝓐IND-MEK invokes the adversary 𝓐 and answers all the oracle queries of 𝓐 as in experiment ExpUA 3 except that, for each clean user U ∈ 𝓤, it generates C U by accessing its own encryption oracle as follows:
𝓐IND-MEK outputs as the first plaintext-pair in the indistinguishability experiment . Let c 1 be the ciphertext received in return for the first pair. 𝓐IND-MEK sets C U equal to the ciphertext c 1.
That is, 𝓐IND-MEK sets C U to the encryption of either ID U‖EID U‖k US or . Now when 𝓐 terminates and outputs its guess b ′, 𝓐IND-MEK outputs 1 if b = b ′, and 0 otherwise. Then, it is clear that:
the probability that 𝓐IND-MEK outputs 1 when the first plaintexts are encrypted in the experiment is equal to the probability that 𝓐 succeeds in the experiment ExpUA 3, and
the probability that 𝓐IND-MEK outputs 1 when the second plaintexts are encrypted in the experiment is equal to the probability that 𝓐 succeeds in the experiment ExpUA 4.
That is, . Note that in the simulation, 𝓐IND-MEK eavesdrops at most q send encryptions which is polynomial in the security parameter ℓ. This completes the proof of Claim 4.
In the experiment ExpUA 4, the adversary 𝓐 gains no information on the hidden bit b chosen by the oracle because the identities of all clean users are chosen uniformly at random from the identity space. It, therefore, follows that . This result combined with Claims 1–4 yields the statement of Theorem 1.
AKE Security
Theorem 2. As long as the MAC scheme Σ and the symmetric encryption scheme Δ are both secure, our authentication and key exchange protocol P is secure in the random oracle model under the ECCDH assumption in 𝔾.
Proof. Fix a ppt adversary 𝓐 against the security of the protocol P. To prove the theorem, we make a series of modifications to the original experiment ExpAKE 0, bounding the effect of each change in the experiment on the success probability of 𝓐 and ending up with an experiment where 𝓐 has a success probability of 1/2. We use to denote the event that 𝓐 correctly guesses the hidden bit b chosen by the oracle in experiment ExpAKE i. Let be the maximum time required to perform the experiment ExpAKE i involving the adversary 𝓐.
Experiment ExpAKE 1. This experiment is different from ExpAKE 0 in that the random oracle J is simulated as follows:
Simulation of the J oracle: For each J query on a string str, the simulator first checks if an entry of the form (str,j) is in a list called JList which contains all the input-output pairs of J. If such an entry exists in JList, the simulator returns j as the output of the J query. Otherwise, the simulator chooses a random ℓ-bit string j ′, returns j ′ in response to the query, and adds the entry (str,j ′) to JList.
The other oracle queries of 𝓐 are answered as in the original experiment ExpAKE 0. Then, since J is a random oracle, ExpAKE 1 is perfectly indistinguishable from ExpAKE 0, and Claim 5 immediately follows.
Claim 5. .
Experiment ExpAKE 2. Here, we modify the experiment so that X is computed as follows:
The ExpAKE 2 modification:
The simulator chooses a random exponent and computes A = aP.
For each instance of users, the simulator chooses a random and sets X = rA.
As a result, each K UG is set to rayP for some random . Since the view of 𝓐 is identical between ExpAKE 2 and ExpAKE 1, it follows that:
Claim 6. .
Experiment ExpAKE 3. We further modify the experiment as follows:
The ExpAKE 3 modification:
The simulator chooses two random elements A,B ∈ 𝔾 and sets Y = B.
For each fresh instance, the simulator chooses a random and sets X = rA. For other instances, the simulator computes X as in experiment ExpAKE 2.
For each fresh instance, the simulator sets each k UG to a random ℓ-bit string. For other instances, the simulator computes k UG as in experiment ExpAKE 2.
Since k UG is set to a random ℓ-bit string (for fresh instances), the success probability of 𝓐 may be different between ExpAKE 2 and ExpAKE 3 if it makes an J(T U‖X‖Y‖K UG) query. This difference is bounded by Claim 7.
Claim 7 , where qJ is the number of queries made to the J oracle.
Proof. We prove the claim via a reduction from the ECCDH problem which is believed to be hard. Assume that the success probability of 𝓐 is non-negligibly different between ExpAKE 2 and ExpAKE 3. Then we construct an algorithm 𝓐ECCDH that solves the ECCDH problem in 𝔾 with a non-negligible advantage. The objective of 𝓐ECCDH is to compute and output the value W = uvP ∈ 𝔾 when given an ECCDH-problem instance (U = uP,V = vP) ∈ 𝔾2. 𝓐ECCDH runs 𝓐 as a subroutine while simulating all the oracles on its own.
𝓐ECCDH handles all the oracle queries of 𝓐 as specified in experiment ExpAKE 3 but using U and V in place of X and Y. When 𝓐 outputs its guess b ′, 𝓐ECCDH chooses an entry of the form (T U‖X‖Y‖K,j) at random from JList and terminates outputting K/r. From the simulation, it is clear that 𝓐ECCDH outputs the desired result W = uvP with probability at least 1/q J if 𝓐 makes a J(T U‖X‖Y‖K UG) query for some fresh instance of any U ∈ 𝓤. This completes the proof of Claim 7.
Experiment ExpAKE 4. This experiment is different from ExpAKE 3 in that it is aborted if the following event occurs.
: The event that the adversary 𝓐 makes a query that contains a MAC forgery.
Then we claim that:
Claim 8 , where q send is the number of queries made to the oracle.
Proof. Assume that the event occurs with a non-negligible probability. Then, we construct an algorithm who generates, with a non-negligible probability, a forgery against the MAC scheme Σ. The algorithm is is given access to the and oracles. The goal of is to produce a message/MAC pair (m,σ) such that: (1) and (2) σ has not been output by the oracle on input m.
Let n be the total number of MAC keys used in the sessions initiated via a query. begins by choosing a random i ∈ {1, …, n}. Let k i denote the i th key among all the n MAC keys, and be any query that is expected to be answered and/or verified using k i. runs 𝓐 as a subroutine and answers the oracle queries of 𝓐 as in experiment ExpAKE 3 except that: it answers all queries by accessing its and oracles. As a result, the i th MAC key k i is not used during the simulation. If occurs against an instance who holds halts and outputs the message/MAC pair generated by 𝓐 as its forgery. Otherwise, terminates with a failure indication.
If the guess i is correct, then the simulation is perfect and achieves its goal. Namely, . Since n ≤ q send and runs in time at most , we get
This completes the proof of Claim 8.
Experiment ExpAKE 5. We next modify the way of answering queries to the H oracle as follows: Simulation of the H oracle: For each H query on a string str, the simulator first checks if an entry of the form (str,h) is in a list called HList which is maintained to store input-output pairs of H. If it is, h is the answer to the hash query. Otherwise, the simulator chooses a random κ-bit string h ′, answers the query with h ′, and adds the entry (str,h ′) to HList.
The other oracle queries of 𝓐 are handled as in experiment ExpAKE 4. Since ExpAKE 5 is perfectly indistinguishable from ExpAKE 4, it is clear that:
Claim 9.
Experiment ExpAKE 6. We finally modify the experiment so that the session key sk is set to a random κ-bit string for each fresh instance and its partner. Accordingly, the success probability of 𝓐 may be different between ExpAKE 6 and ExpAKE 5 if it asks an H query of the form H(k US‖T U‖ID SN) for some uncorrupted U ∈ 𝓤 and SN ∈ 𝒮𝓝. But the difference is bounded by:
Claim 10 , where qH is the number of queries made to the H oracle.
Proof. We prove the claim by constructing an eavesdropper 𝓐IND-MEK who attacks the indistinguishability of Δ in experiment . 𝓐IND-MEK invokes the adversary 𝓐 and answers all the oracle queries of 𝓐 as in experiment ExpAKE 5 except that it generates each C GW to be sent to a fresh sensor instance by accessing its own encryption oracle as follows:
Let be a random string chosen from {0, 1}κ. 𝓐IND-MEK outputs as a plaintext pair in the indistinguishability experiment . Let c be the ciphertext received in return for the plaintext pair. 𝓐IND-MEK sets C GW equal to the ciphertext c.
That is, each C GW is set to the encryption of either k US or . Now when 𝓐 terminates and outputs its guess b ′, 𝓐IND-MEK selects an entry of the form (k US‖T U‖ID SN,h) at random from HList and outputs 0 if k = k US, and 1 otherwise. If 𝓐 asks an H query of the form H(k US‖T U‖ID SN) for some uncorrupted U ∈ 𝓤 and SN ∈ 𝒮𝓝, 𝓐IND-MEK correctly guesses the bit b in its indistinguishability experiment with probability at least and therefore, Claim 10 follows.
In experiment ExpAKE 6, the adversary 𝓐 obtains no information on the hidden bit b chosen by the oracle since the session keys of all fresh instances are selected uniformly at random from {0, 1}κ. Therefore, it follows that . This result combined with Claims 5–10 completes the proof of Theorem 2.
Concluding Remarks
With the continuing advancements in sensor technologies, WSNs will play an increasingly important role in commercial, government and military settings. A number of recent high profiles such as the revelations by Edward Snowden that the US National Security Agency has been conducting massive online surveillance of both US and non-US citizens highlighted the potential of ensuring user privacy and anonymity. In WSNs, for example, designing a secure and efficient user authentication scheme without compromising user anonymity remains an area of active research.
In this work, we have presented a sca-wsn scheme, a smart-card-based user authentication scheme for wireless sensor networks, which achieves user anonymity without imposing (expensive) public key operations on sensors. Our result in this paper does not contradict the result of Wang and Wang [28, 29] but rather supports and clarifies it: in order for a sca-wsn scheme to achieve user anonymity, the use of public key cryptography is inevitable but, if forward secrecy is not desired, can be avoided at least on the sensor side. Extending our result to the case of three-factor authentication [34] would be an interesting future work.
Acknowledgments
All authors, especially the corresponding author Sangchul Han, would like to thank the anonymous reviewers for their time and invaluable comments and suggestions on this paper.
Data Availability
All relevant data are within the paper and its Supporting Information files.
Funding Statement
This work was supported by Konkuk University. The funders had no role in study design, data collection and analysis, decision to publish, or preparation of the manuscript.
References
- 1. Rawat P, Singh K, Chaouchi H, Bonnin J (2014) Wireless sensor networks: a survey on recent developments and potential synergies. The Journal of Supercomputing 68: 1–48. [Google Scholar]
- 2. Das M (2009) Two-factor user authentication in wireless sensor networks. IEEE Transactions on Wirelelss Communications 8: 1086–1090. 10.1109/TWC.2008.080128 [DOI] [Google Scholar]
- 3. He D, Gao Y, Chan S, Chen C, Bu J (2010) An enhanced two-factor user authentication scheme in wireless sensor networks. Ad Hoc & Sensor Wireless Networks 10: 361–371. [Google Scholar]
- 4. Khan M, Alghathbar K (2010) Cryptanalysis and security improvements of “two-factor user authentication in wireless sensor networks”. Sensors 10: 2450–2459. 10.3390/s100302450 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 5. Chen T, Shih W (2010) A robust mutual authentication protocol for wireless sensor networks. ETRI Journal 32: 704–712. 10.4218/etrij.10.1510.0134 [DOI] [Google Scholar]
- 6. Yeh H, Chen T, Liu P, Kim T, Wei H (2011) A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 11: 4767–4779. 10.3390/s110504767 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 7. Kumar P, Choudhury A, Sain M, Lee S, Lee H (2011) RUASN: a robust user authentication framework for wireless sensor networks. Sensors 11: 5020–5046. 10.3390/s110505020 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 8. Kumar P, Lee S, Lee H (2012) E-SAP: efficient-strong authentication protocol for healthcare applications using wireless medical sensor networks. Sensors 12: 1625–1647. 10.3390/s120201625 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 9.Yoo S, Park K, Kim J (2012) A security-performance-balanced user authentication scheme for wireless sensor networks. International Journal of Distributed Sensor Networks 2012: Article ID 382810.
- 10.Vaidya B, Makrakis D, Mouftah H (2012) Two-factor mutual authentication with key agreement in wireless sensor networks. Security and Communication Networks.
- 11. Xue K, Ma C, Hong P, Ding R (2013) A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. Journal of Network and Computer Applications 36: 316–323. 10.1016/j.jnca.2012.05.010 [DOI] [Google Scholar]
- 12.Shi W, Gong P (2013) A new user authentication protocol for wireless sensor networks using elliptic curves cryptography. Internation Journal of Distributed Sensor Networks 2013: Article ID 730831.
- 13. Li C, Weng C, Lee C (2013) An advanced temporal credential-based security scheme with mutual authentication and key agreement for wireless sensor networks. Sensors 13: 9589–9603. 10.3390/s130809589 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 14. Kumar P, Gurtov A, Ylianttila M, Lee S, Lee H (2013) A strong authentication scheme with user privacy for wireless sensor networks. ETRI Journal 35: 889–899. 10.4218/etrij.13.0113.0103 [DOI] [Google Scholar]
- 15.He D, Kumar N, Chen J, Lee C, Chilamkurti N, Yeo S (2013) Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimedia Systems.
- 16.Chi L, Hu L, Li H, Chu J (2014) Analysis and improvement of a robust user authentication framework for ubiquitous sensor networks. International Journal of Distributed Sensor Networks 2014: Article ID 637684.
- 17. Kim J, Lee D, Jeon W, Lee Y, Won D (2014) Security analysis and improvements of two-factor mutual authentication with key agreement in wireless sensor networks. Sensors 14: 6443–6462. 10.3390/s140406443 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 18.Khan M, Kumari S (2014) An improved user authentication protocol for healthcare services via wireless medical sensor networks. Internation Journal of Distributed Sensor Networks 2014: Article ID 347169.
- 19.Jiang Q, Ma J, Lu X, Tian Y (2014) An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-to-Peer Networking and Applications.
- 20. Choi Y, Lee D, Kim J, Jung J, Nam J, Won D (2014) Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 14: 10081–10106. 10.3390/s140610081 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 21. Khan M, He D (2012) A new dynamic identity-based authentication protocol for multi-server environment using elliptic curve cryptography. Security and Communication Networks 5: 1260– 1266. [Google Scholar]
- 22. Khan M, Kumari S, Singh P (2013) Cryptanalysis of an ‘efficient-strong authentiction protocol (E-SAP) for healthcare applications using wireless medical sensor networks’. KSII Transactions on Internet & Information Systems 7: 967–979. 10.3837/tiis.2013.05.002 [DOI] [Google Scholar]
- 23. He D, Kumar N, Khan M, Lee J (2013) Anonymous two-factor authentication for consumer roaming service in global mobility networks. IEEE Transactions on Consumer Electronics 59: 811–817. 10.1109/TCE.2013.6689693 [DOI] [Google Scholar]
- 24. Xie Q, Hu B, Tan X, Bao M, Yu X (2014) Robust anonymous two-factor authentication scheme for roaming service in global mobility network. Wireless Personal Communications 74: 601–614. 10.1007/s11277-013-1309-3 [DOI] [Google Scholar]
- 25. He D, Zhang Y, Chen J (2014) Cryptanalysis and improvement of an anonymous authentication protocol for wireless access networks. Wireless Personal Communications 74: 229–243. 10.1007/s11277-013-1282-x [DOI] [Google Scholar]
- 26. Kocher P, Jaffe J, Jun B (1999) Differential power analysis Proceedings of CRYPTO 1999, Santa Barbara, California, USA, pp. 388–397. [Google Scholar]
- 27. Messerges T, Dabbish E, Sloan R (2002) Examining smart-card security under the threat of power analysis attacks. IEEE Transactions on Computers 51: 541–552. 10.1109/TC.2002.1004593 [DOI] [Google Scholar]
- 28. Wang D, Wang P (2014) Understanding security failures of two-factor authentication schemes for real-time applications in hierarchical wireless sensor networks. Ad Hoc Networks 20: 1–15. 10.1016/j.adhoc.2014.03.003 [DOI] [Google Scholar]
- 29. Wang D, Wang P (2014) On the anonymity of two-factor authentication schemes for wireless sensor networks: Attacks, principle and solutions. Computer Networks 73: 41–57. 10.1016/j.comnet.2014.07.010 [DOI] [Google Scholar]
- 30. Bellare M, Pointcheval D, Rogaway P (2000) Authenticated key exchange secure against dictionary attacks Proceedings of EUROCRYPT 2000, Bruges, Belgium, pp. 139–155. [Google Scholar]
- 31.NIST (1999) Recommended elliptic curves for federal government use. Avaliable: http://csrc.nist.gov/groups/ST/toolkit/documents/dss/NISTReCur.pdf.
- 32. Goldwasser S, Micali S (1984) Probabilistic encryption. Journal of Computer and System Sciences 28: 270–299. 10.1016/0022-0000(84)90070-9 [DOI] [Google Scholar]
- 33.Han W (2011) Weakness of a secured authentication protocol for wireless sensor networks using elliptic curves cryptography. IACR Cryptology ePrint Archive. Available: http://eprint.iacr.org/2011/293. [DOI] [PMC free article] [PubMed]
- 34. He D, Kumar N, Lee J, Sherratt R (2014) Enhanced three-factor security protocol for USB mass storage devices. IEEE Transactions on Consumer Electronics 60: 30–37. 10.1109/TCE.2014.6780922 [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
All relevant data are within the paper and its Supporting Information files.