Abstract
Biometrics authenticated schemes using smart cards have attracted much attention in multi-server environments. Several schemes of this type where proposed in the past. However, many of them were found to have some design flaws. This paper concentrates on the security weaknesses of the three-factor authentication scheme by Mishra et al. After careful analysis, we find their scheme does not really resist replay attack while failing to provide an efficient password change phase. We further propose an improvement of Mishra et al.’s scheme with the purpose of preventing the security threats of their scheme. We demonstrate the proposed scheme is given to strong authentication against several attacks including attacks shown in the original scheme. In addition, we compare the performance and functionality with other multi-server authenticated key schemes.
Introduction
With the swift development of wireless communications and network technologies, more and more people use wireless handheld devices (e.g.PDA, notebook and mobile phone, etc) to enjoy mobile services almost anytime and anywhere. However, open nature of networks demands for security concern of paid and protected resources available over the network [1–5]. Authentication mechanism becomes an essential need before a remote user can access the services. Since then Lamport [6] proposed the first authentication scheme, a number of authentication schemes have been put forward for different applications [7–13].
However, most of the existing password authentication schemes are based on a single-server environment which are unfit for the multi-server environments. Recently, a large number of smart cards based remote user authentication schemes for multi-server environments have been proposed. In addition, compared with other authentication schemes, schemes that only use random numbers and a hash function were getting much more attention because of their low computation costs. In 2008, Tsai [14] proposed an efficient multi-server authentication scheme using the random number and one-way hash function. After that, numerous authenticated key agreement schemes were presented for multi-server environments one after another [15–17]. In 2012, Li et al. [18] proposed a novel authenticated key exchange scheme for multi-server environments. Unfortunately, Xue et al.[19] showed that Li et al.’s scheme did not resist some types of known attacks, such as vulnerability to verifier stolen, off-line password guess, replay, denial of service and forgery attacks. Then, Xue et al. proposed an improved scheme to remedy the weaknesses of Li et al.’s scheme. Nevertheless, Lu et al.[20] observed that Xue et al.’s scheme was not only really insecure against masquerade and insider attacks but also was vulnerable to off-line password guessing attack. To improve the shortcomings of Xue et al.’s scheme, Lu et al. proposed a slight modified authentication scheme for multi-server environments.
All above mentioned authentication schemes are based on password and smart cards. Note that the password cannot be considered as a unique identity identifier and it’s needed to be remembered. Moreover, possibility of password guessing attack is also a concern. Compared with cryptographic keys and passwords, biometric keys (e.g.fingerprint, face, iris, hand geometry and palm-print, etc.) have many advantages [21], for example, they are difficult to lose or forget; they are difficult to copy or share; they are difficult to forge or distribute biometrics; they are difficult to guess; they are more difficult to break biometric keys. Recently, Chuang et al.[22] presented an efficient biometrics based authentication scheme using smart cards for multi-server environments, which was previously considered to be have more security properties. However, Mishra et al. [23] showed that Chuang et al.’s scheme was vulnerable to stolen smart card attack, server spoofing attack and impersonation attack. In addition, they proposed an improved biometrics-based multi-server authenticated key agreement scheme using smart cards and they claimed that their scheme satisfied all desirable security requirements. Unfortunately, this paper will demonstrate that the scheme cannot really resist replay attack and cannot provide an efficient password change phase.
In this paper, we concentrate on the security weaknesses of the three-factor authentication scheme by Mishra et al. After carefully analysis, we find their scheme does not really resist replay attack while fails to provide an efficient password change phase. We further propose an improvement of Mishra et al.’s scheme with the purpose of preventing the security threats of their scheme. We demonstrate the proposed scheme is given to strong authentication against several attacks including attacks showed in the original scheme. In addition, we compare the performance and functionality with other related schemes.
The rest of paper is organized as follows: In Section 2 and Section 3, we review and analyze the Mishra et al.’s scheme. In Section 4, we propose an enhancement authentication scheme for multi-sever environments. In Section 5, we present a security analysis of our scheme. Section 6 shows security and performance analyses by comparing our scheme with previous schemes. We conclude in Section 7.
Review of Mishra et al.’s scheme
There are three phases relating to Mishra et al.’s scheme which consists of the registration, login and authentication and password updating. Table 1 lists the notations used in this paper.
Table 1. Notations.
| U i, S j | User, server |
| RC | The registration center |
| ID i, SID j | Identity of U i, S j |
| PW i, BIO i | Password and biometrics of U i |
| x, y | Master secret key of U i and RC |
| PSK | Secure key shared by RC and S j |
| h(⋅) | Hash function |
| H(⋅) | Biohash function |
| ⊕, ∣∣ | Exclusive-or operation and concatenation operation |
Registration
Suppose RC is the trusted third party responsible for registration of U i and S j.
Server registration
S j sends the registration request to RC;
After receiving the request, RC sends the key PSK to S j through a secure channel;
Upon receiving the secret key PSK, S j stores it with aim to authorize a legitimate user.
User registration
U i selects his identity ID i, password PW i and keys his biometrics BIO i. Then, U i generates a random number N i, computes W 1 = h(PW i∣∣N i), W 2 = h(ID i⊕N i) and sends the registration message {ID i, W 1, W 2} to RC via a secure channel.
RC computes A i = h(ID i∣∣x∣∣T r), B i = h(A i), X i = W i⊕B i, Y i = h(PSK)⊕W 2 and Z i = PSK⊕A i, where T r is the registration time. Then, RC issues the smart card SC i to U i which contains {X i, Y i, Z i, h(⋅)} over a secure channel.
Upon receiving SC i, U i enters his personal biometric BIO i at the sensor and computes N = N i⊕H(BIO i), V = h(ID i∣∣N i∣∣PW i). Finally, U i stores {X i, Y i, Z i, N, V, h(⋅)} into SC i.
Login and authentication
U i inserts SC i into the terminal and inputs his identity ID i, password PW i and imprints his biometrics BIO i at the sensor.
SC i computes N i = N⊕h(BIO i) and checks . If it holds, SC i continues to compute W 1 = h(PW i∣∣N i), W 2 = h(ID i⊕N i), B i = X i⊕W i and h(PSK) = Y i⊕W 2. Then, SC i generates a random number n 1 and computes M 1 = h(PSK)⊕n 1, M 2 = ID i⊕h(n 1∣∣B i) and M 3 = h(ID i∣∣n 1∣∣B i). Finally, U i sends {Z i, M 1, M 2, M 3} to S j.
When receiving the message from SC i, S j immediately computes A i = Z i⊕PSK, n 1 = M 1⊕h(PSK), ID i = M 2⊕h(n 1∣∣h(A i)) and checks whether . If it is equal, S j generates a random number n 2 and computes SK ji = h(ID i∣∣SID j∣∣B i∣∣n 1∣∣n 2), M 4 = n 2⊕h(ID i∣∣n 1), M 5 = h(SK ji∣∣n 1∣∣n 2). Then, S j sends {SID j, M 4, M 5} to SC i.
SC i first computes n 2 = M 4⊕h(ID i∣∣n 1), SK ij = h(ID i∣∣SID j∣∣B i∣∣n 1∣∣n 2) and then checks whether h(SK ij∣∣n 1∣∣n 2) is consistent with M 5. If it is true, SC i computes M 6 = h(SK ij∣∣n 1∣∣n 2) and delivers it to S j.
S j verifies the verification condition . If this verification holds, S j can now use the keys SK ji to communicate with U i securely.
Password updating
U i inputs his ID i, PW i and imprints his biometrics BIO i at the sensor. SC i computes N i = N⊕h(BIO i) and checks . If SC i determines that they are equal, then U i can key the new password . Subsequently, SC i computes and replaces X i and V i with and , respectively.
Security analysis of Mishra et al.’s scheme
This section presents a cryptanalysis of a recently scheme proposed by Mishra et al. We show their scheme does not satisfy the key security attribute such as vulnerability to replay attack and incorrect password change phase. We assume that a malicious adversary 𝓐 has totally supervised the communication channel in login and session key establishment phases. In other words, 𝓐 has the capacity to intercept, insert, delete, refresh or update any information delivered between U i and S j [6].
Not withstanding the replay attack
Suppose an adversary 𝓐 has intercepted a past login message {Z i, M 1, M 2, M 3}. He is able to launch a replay attack and login to the server by resending the eavesdropped message {Z i, M 1, M 2, M 3} to S j. In other words, the adversary without running the “Login phase”, sends the eavesdropped message {Z i, M 1, M 2, M 3} to S j. In the “Login and authentication”, upon receiving the message {Z i, M 1, M 2, M 3}, S j computes A i = Z i⊕PSK, n 1 = M 1⊕h(PSK), ID i = M 2⊕h(n 1∣∣h(A i)), and checks whether is equal to the received M 3 or not. Since M 3 and are equal, S j will authenticate 𝓐 and 𝓐 will be able to login to S j. Thus, 𝓐 can easily login to S j by re-sending an old login message. Since S j does not check the freshness of the received login message {Z i, M 1, M 2, M 3} and authenticate U i in (3) of the “Login and authentication”, S j will not be able to discover replay attack.
Incorrect password change phase
The user U i inserts his smart card into a card reader and enters his identity ID i, password PW i and imprints his personal biometric BIO i at the sensor corresponding to his smart card. Then smart card computes N i = N⊕h(BIO i), and compares with the stored value of V in its memory to verify the legitimacy of U i. Once the authenticity of cardholder is verified then U i can instruct smart card to change his password. Afterwards, smart card asks the cardholder to resubmit a new password , then X i = B i⊕h(PW i∣∣N i) and V = h(ID i∣∣N i∣∣PW i) stored in the smart card can be updated with and , where . The value contains older password PW i in h(PW i∣∣N i). Therefore, the modified is not correct.
The proposed scheme
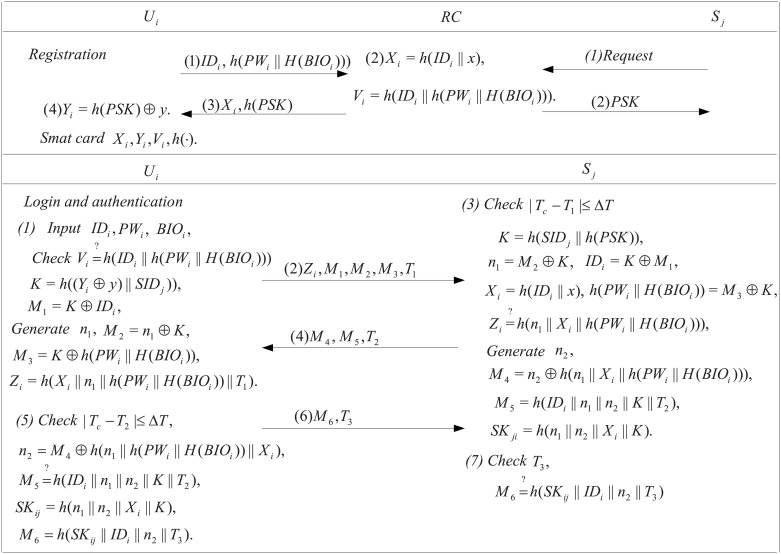
In this section, we will present our robust biometrics based authentication scheme using smart cards for multi-sever environments. In our scheme, there are also three participants, the user U i, the server S j and the registration center RC. RC chooses the secret key PSK and a secret number x and shares them with S j via a secure channel. We will describe all the phases relating to our scheme in the subsections, i.e. registration, login and authentication, and password update, where registration and login and authentication phases are shown in Fig 1.
Fig 1. Registration and authentication phases.
Registration
U i keys his biometrics BIO i, identity ID i and password PW i. Then, U i sends {ID i, h(PW i∣∣H(BIO i))} to RC.
Upon receiving the message from U i, RC computes X i = h(ID i∣∣x), V = h(ID i∣∣h(PW i∣∣H(BIO i))). Then, RC stores {X i, V i, h(PSK)} into a smart card and submits them to U i.
U i computes Y i = h(PSK)⊕y, and replaces h(PSK) with Y i. Finally, the smart card stores the values of {X i, Y i, V i, h(⋅)}.
Login and authentication
U i inserts his smart card into device and enters his identity ID i, password PW i and biometrics BIO i. Then, the smart card validates whether V i = h(ID i∣∣h(PW i∣∣H(BIO i))) is equal to the stored V. If it holds, the smart card generates a random number n 1 and computes K = h((y⊕Y i)∣∣SID j), M 1 = K⊕ID i, M 2 = n 1⊕K, M 3 = h(PW i∣∣H(BIO i))⊕K, Z i = h(B i∣∣n 1∣∣h(PW i∣∣H(BIO i))∣∣T 1). Finally, U i submits {Z i, M 1, M 2, M 3, T 1} to S j, where T 1 is the current timestamp.
Upon receiving the message from U i, S j first checks whether T c−T 1 ≤ ΔT and then computes K = h(SID j∣∣h(PSK)) by using a secure pre-shared key PSK. Then, S j retrieves ID i = M 1⊕K, n 1 = M 2⊕K, h(PW i∣∣BIO i) = M 3⊕K. Now, S j computes X i = h(ID i∣∣x) and verifies whether . If it holds, S j generates a random number n 2 and computes SK ji = h(n 1∣∣n 2∣∣K∣∣X i), M 4 = n 2⊕h(n 1∣∣h(PW i∣∣H(BIO i))∣∣X i), M 5 = h(ID i∣∣n 1∣∣n 2∣∣K∣∣T 2). Then, S j sends back authentication message {M 4, M 5, T 2} to U i, where T 2 is the current timestamp.
After checking the freshness of T 2, U i first computes n 2 = M 4⊕h(n 1∣∣h(PW i∣∣H(BIO i))∣∣X i) and then verifies whether h(ID i∣∣n 1∣∣n 2∣∣K) is equal to the received M 5. If they are equal, U i computes the common session key SK ij = h(n 1∣∣n 2∣∣K∣∣X i) and sends {M 6 = h(SK ij∣∣ID i∣∣n 2∣∣T 3), T 3} to S j, where T 3 is the current timestamp.
S j verifies the freshness T 3 and the correctness of M 6 by using SK ji. If they do not hold, S j stops the execution; Otherwise, S j confirms the common session key SK ji with U i.
Password updating
U i first inputs his smart card into the device and provides his identity ID i, password PW i and biometrics BIO i. Then, the smart card validates whether V i = h(ID i∣∣h(PW i∣∣H(BIO i))) is equal to the stored V i. If they are not equal, the smart card refuses the request; Otherwise, U i keys in the new password . Finally, the smart card computes and replaces V i by .
Security analysis of the proposed scheme
In this section, we first adopt Burrows-Abadi-Needham (BAN)Logic [24] to demonstrate the completeness of the proposed scheme. Then, we conduct discussion and a cryptanalysis of the proposed scheme through both the informal and formal analyses.
Verifying the proposed scheme with BAN logic
BAN logic [24] is a set of rules for defining and analyzing information exchange schemes. It helps its users determine whether exchanged information is trustworthy, secured against eavesdropping, or both. It has been highly successful in analyzing the security of authentication schemes. First, we introduce some notations and logical postulates of BAN logic in Table 2.
- BAN logical postulates
- Message-meaning rule: : if A believes that the key K is shared by A and B, and sees X encrypted with K, then A believes that B once said X.
- Fresh conjuncatenation rule: : if A believes freshness of X, then A believes freshness of the (X, Y).
- Belief rule: : if A believes X and Y, then A believes (X, Y).
- Nonce-verification rule: : if A believes that X could have been uttered only recently and that B once said X, then A believes that B believes X.
- Jurisdiction rule: : if A believes that B has jurisdiction over X and A trusts B on the truth of X, then A believes X.
-
Establishment of security goals
-
Idealized scheme
S j: < n 1, X i, h(PW i∣∣H(BIO i)) > n 2, (ID i, n 1, n 2, T 2)K
-
Initiative premises
p 1. U i∣ ≡ #n 1 p 2. U i∣ ≡ S j ⇒ #n 2 p 3. S j∣ ≡ #n 1 p 4. S j∣ ≡ #n 2
p 7. U i∣ ≡ ID i p 8. S j∣ ≡ U i ⇒ h(PW i∣∣BIO i)
p 9. S j∣ ≡ U i ⇒ ID i p 10. U i∣ ≡ S j ⇒ X i
p 11. .
-
Scheme analysis
a 1. By p 5 and S j⊲ < n 1, ID i, h(PW i∣∣BIO i) > K, we apply the message-meaning rule to derive: S j∣ ≡ U i∣ ∼ (n 1, ID i, h(PW i∣∣H(BIO i)))
a 2. By a 1 and p 3, we apply the fresh conjuncatenation rule and the nonce-verification rule to derive: S j∣ ≡ U i∣ ≡ (n 1, ID i, h(PW i∣∣H(BIO i)))
a 3. By a 2, p 3 and p 8, we apply the belief rule and the jurisdiction rule to derive: S j∣ ≡ ID i
a 4. By a 3 and , we apply the message-meaning rule to derive:
a 5. By p 4 and a 4, we apply the fresh conjuncatennation rule and the nonce-verification rule to derive:
g 1. By a 5, we apply the belief rule to derive:
g 2. By g 1 and p 11, we apply the jurisdiction rule to derive:
a 6. By p 6 and U i⊲(ID i, n 1, n 2, T 2)K, we apply the message-meaning rule to derive: U i∣ ≡ S j∣ ∼ (ID i, n 1, n 2, T 2)
a 7. By p 2 and a 9, we apply the fresh conjuncatenation rule and the nonce-verification rule to derive: U i∣ ≡ S j∣ ≡ (ID i, n 1, n 2, T 2)
a 8. By a 7, we apply the belief rule to derive: U i∣ ≡ S j∣ ≡ n 2
a 9. By p 2 and a 8, we apply the jurisdiction rule to derive: U i∣ ≡ n 2
a 10. By a 9 and U i⊲ < n 1, X i, h(PW i∣∣BIO i) > n 2, we apply the message-meaning rule to derive: U i∣ ≡ S j∣ ∼ (n 1, X i, h(PW i∣∣BIO i))
a 11. By a 10 and p 1, we apply the fresh conjuncatennation rule and the nonce-verification rule to derive: U i∣ ≡ S j∣ ≡ (n 1, X i, h(PW i∣∣BIO i))
g 3. By p 1, p 3, p 4, p 6, a 11 and SK ji = h(n 1∣∣n 2∣∣K∣∣X i), we apply the fresh conjuncatennation rule and the nonce-verification rule to derive:
g 4. By g 3 and p 12, we apply the jurisdiction rule to derive:
Table 2. BAN logic notations.
| A∣ ≡ X | A believes a statement X |
| Share a key K between A and B | |
| #X | X is fresh |
| A⊲X | A sees X |
| A ⇒ X | A controls X |
| A∣ ∼ X | A said X |
| (X)K | The formula X is hashed by K |
| < X, Y > K | X and Y are encrypted with the key K |
| (X, Y) | The formula X or Y is one part of the formula (X, Y) |
Informal security analysis
This subsection verifies whether the proposed scheme is secure against various kinds of known attacks. We assume that a malicious adversary 𝓐 has totally supervised the communication channel in login and session key establishment phases. In other words, 𝓐 has the capacity to intercept, insert, delete, refresh or update any information delivered between U i and S j [6].
Anonymity
U i’s identity ID i is well protected by the shared secret parameter K as a substitute for real ones, 𝓐 can not get users’ real identities. In addition, the unauthorized server cannot get ID i without knowing K since K is protected by the secret key PSK only known by the authorized server and is not exposed in the open channel. Thus, our scheme provides user anonymity, which can prevent the leakage of private user identities to malicious attackers.
Mutual authentication
In order to authenticate U i, S j has to verify validity of the evidence Z i = h(X i∣∣n 1∣∣h(PW i∣∣H(BIO i))). The evidence is computed with the common secret parameter K only known U i and S j. In other words, (n 1, ID i, h(PW i∣∣H(BIO i))) are derived from the valid login message {Z i, M 1, M 2, M 3, T 1} through K, no one can counterfeit the evidence. In addition, to compute X i, secret key x is needed but only known by S j. Moreover, checking h(SK ij∣∣ID i∣∣n 2) to further assist S j in authenticating U i because the session key is only known by U i and S j. To authenticate S j, U i needs to verify whether . Because ID i and K are only known by U i and S j, no one can forge a valid {M 4, M 5, T 2} without them. Hence, mutual authentication between U i and S j is achieved.
Resist stolen smart card attack
Even if 𝓐 has gathered [25] the information {X i, Y i, V i, h(⋅)} stored in the smart card, 𝓐 cannot figure out the login request message {Z i, M 1, M 2, M 3, T 1} without the secret key y. Moreover, 𝓐 cannot get the identity ID i and PW i since they are protected by hash functions with the U i’s biometrics BIO i. Hence, 𝓐 still cannot succeed if he steals the smart card.
Session key agreement
We provide the session key SK = h(n 1∣∣n 2∣∣K∣∣X i) to protect the message communication between U i and S j, where (n 1, n 2, K, X i) are known to anybody but U i and S j. In addition, SK is different in each session, 𝓐 has obtained a known session key cannot be used to calculate the value of the next session key.
Resist replay attack
Assume 𝓐 has intercepted all the communication message {Z i, M 1, M 2, M 3, T 1, M 4, M 5, T 2, M 6, T 3,} and tried to replay them to U i or S j to obtain authentication. However, it is impossible to come true since all the authenticated messages imply the timesstamp which is also exposed in public channel. If 𝓐 resends the transmitted messages, the receiver will immediately detect the attack through the authenticated message. Hence, our scheme can withstand replay attack.
Resist stolen verifier and insider attacks
In the registration phase, RC does not directly get the U i’s password PW i and biometrics information BIO i. Hence, 𝓐 performs a stolen verifier attack or insider attack will be hard.
Resist off-line guessing attack
In our proposed scheme, trying to launch an off-line passsword guessing attack with the information stored in the smart card and the eavesdropped messages is trying to solve the input from the given hash value. Since the identity ID i and the random number N i are required with the purposed of knowing PW i, both the secrets are protected by the hash function and known by the user himself.
Formal security analysis of the proposed scheme
This subsection presents the formal security analysis of our scheme and shows that it is secure. For this, we first define the following hash function [26].
Definition 1. A secure one-way hash function h:{0, 1}* → {0, 1}n, which takes an input as an arbitrary length binary string x ∈ {0,1}* and outputs a binary string h(x) ∈ {0,1}n and satisfies the following requirements: a. Given y ∈ Y, it is computationally infeasible to find an x ∈ X such that y = h(x); b. Given x ∈ X, it is computationally infeasible to find another x′ ≠ x ∈ X, such that h(x′) = h(x); c. It is computationally infeasible to find a pair (x′, x) ∈ X′ × X, with x′ ≠ x, such that h(x′) = h(x).
Theorem 1. Under the assumption that the one-way hash function h(⋅) closely behaves like an oracle, then our scheme is provably secure against an attacker 𝓐 for protecting user’s personal information including identity ID i, password PW i and biometrics BIO i, sever’s private key x and PSK.
Proof. The formal security proof of our scheme is similar to that as in [27–28]. Using the following oracle to construct 𝓐 who will have the ability to derive the user’s ID i, password PW i, biometrics BIO i, sever’s private key x and PSK.
Reveal: This random oracle will unconditionally output the input x from the given hash value y = h(x).
𝓐 runs the experimental algorithm showed in Table 3, for our biometrics based authentication and key agreement scheme using smart cards for multi-server environments, say BAKASSCMSE.
Table 3. Algorithm 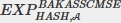 .
.
| 1. | Eavesdrop login message {Z i, M 1, M 2, M 3, T 1} |
| 2. | Call the Reveal oracle. Let |
| 3. | Eavesdrop authentication message {M 4, M 5, T 2} |
| 4. | Call the Reveal oracle. Let |
| 5. | if then |
| 6. | Call the Reveal oracle. Let |
| 7. | Call the Reveal oracle. Let |
| 8. | Compute |
| 9. | if (K′ = K′′) then |
| 10. | Call the Reveal oracle. Let (q′, SID j) ← Reveal(K) |
| 11. | Compute |
| 12. | if then |
| 13. | Call the Reveal oracle. Let (PSK′) ← Reveal(q′) |
| 14. | Accept as the correct ID i, PW i and BIO i of U i x′ and PSK′ as the correct private key of S j |
| 15. | return 1 |
| 16. | else |
| 17. | return 0 |
| 18. | end if |
| 19. | else |
| 20. | return 0 |
| 21. | end if |
| 22. | else |
| 23. | return 0 |
| 24. | end if |
Define the success probability for is and the advantage function for this experiment then becomes , where the maximum is taken over all 𝓐 with execution time t and the number of queries q R made to the Reveal oracle. Consider the experiment showed in Table 3 for 𝓐. If 𝓐 has the ability to solve the hash function problem provided in Definition 1, then he can directly derive U i’s identity ID i, password PW i, biometrics BIO i, and S j’s private key x and PSK. In this case, 𝓐 will discover the complete connections between U i and S j. However, it is a computationally infeasible problem to invert the input from a given hash value, i.e., , ∀ϵ > 0. Hence, we have , since depends on . As a result, there is no way for 𝓐 to discover the complete connections between U i and S j and our scheme is provably secure against an adversary for deriving (ID i, PW i, BIO i, x, PSK).
Performance and functionality analysis
In this section, we compare our scheme with other existing multi-server authenticated schemes ([18–20], [22–23]) regarding security and performance. Table 4 lists the functionality comparisons of our proposed scheme with other related schemes. It can be seen that the proposed scheme achieves all security and functionality requirements and is more secure than other related schemes.
Table 4. Functionality comparison.
| Ours | Mishra et al. [23] | Chuang et al. [22] | Lu et al. [20] | Xue et al. [19] | Li et al. [18] | |
|---|---|---|---|---|---|---|
| Provide mutual authentication | Yes | Yes | No | Yes | Yes | Yes |
| User anonymity | Yes | Yes | Yes | Yes | Yes | Yes |
| Resist insider attack | Yes | Yes | Yes | Yes | No | Yes |
| Resist off-line guessing attack | Yes | Yes | Yes | Yes | No | No |
| Resist stolen smart card attack | Yes | Yes | No | - | Yes | Yes |
| Resist replay attack | Yes | No | No | No | No | No |
| Resist verifier attack | Yes | Yes | Yes | - | No | Yes |
| Session key agreement | Yes | Yes | Yes | Yes | Yes | Yes |
| Efficient password change phase | Yes | No | No | Yes | No | No |
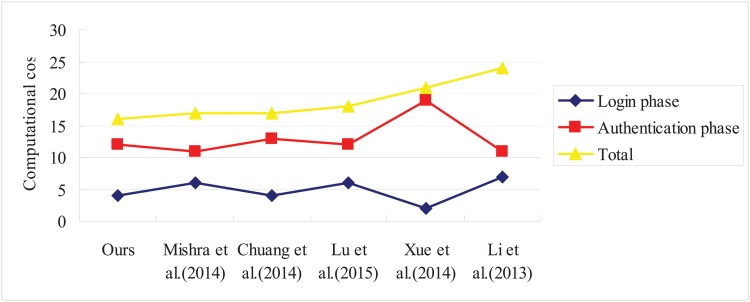
For performance analysis, we compare the computational primitives involved in login and authentication phases of our scheme and other related schemes. To analyze the computational complexity of the schemes, we use hashing operation as the time complexity since XOR operations require very little computations. Fig 2 shows comparison regarding the performance. From this comparison, we can see that our proposed scheme has better efficiency in comparison with other schemes.
Fig 2. Performance comparison.
Conclusion and future work
In this paper, we presented a cryptanalysis of a recently proposed Mishra et al.’scheme and showed that their scheme was susceptible to replay attack while failed to provide an efficient password change phase. An improved scheme is proposed that inherits the merits of Mishra et al.’s scheme and resists different possible attacks. The proposed scheme is practical and efficient compared with other related schemes. Comprehensive security analysis proves that the robustness of our scheme is more secure than other related schemes. Among the open problems to be faced in the near future we can mention the study of specific applications and practical limitations of our scheme for mutual authentication using smart cards based on biometrics and their large-scale implementation in real multi-sever environments.
Data Availability
All relevant data are within the paper.
Funding Statement
This work was supported by National Natural Science Foundation of China (grant no. 61121061), the Beijing Natural Science Foundation (grant no. 4142016), and the Asia Foresight Program under NSFC Grant (grant no. 61411146001). The funders had no role in study design, data collection and analysis, decision to publish, or preparation of the manuscript.
References
- 1. Liu C, Du WB, Wang WX. Particle Swarm Optimization with Scale-Free Interactions. PLoS One 9(5). 2014. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2. Du WB, Wu ZX, Cai KQ. Effective usage of shortest paths promotes transportation efficiency on scale-free networks. Physica A. 2013; 392(17): 3505–3512. 10.1016/j.physa.2013.03.032 [DOI] [Google Scholar]
- 3. Wang Z, Perc M. Aspiring to the fittest and promotion of cooperation in the prisoner’s dilemma game. Physical Review E. 2010; 82(2), 021115 10.1103/PhysRevE.82.021115 [DOI] [PubMed] [Google Scholar]
- 4. Boccaletti S, Bianconi G, Criado R, del Genio CI, Gómez-Gardeñes J, Romance M, et al. The structure and dynamics of multilayer networks. Physics Reports. 2014; 544(1): 1–122. 10.1016/j.physrep.2014.07.001 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 5.Zhao DW, Peng HP, Li LX, Yang YX, Li SD. An efficient patch dissemination strategy for mobile networks. Mathematical Problems in Engineering. 2013; Article ID 896187, 13 pages., 2013.
- 6. Lamport L. Password authentication with insecure communication. ACM Communication. 1981; 24(11): 770–772. 10.1145/358790.358797 [DOI] [Google Scholar]
- 7. Sun DZ, Huai JP, Sun JZ, Li JX, Zhang JW, Feng ZY. Improvements of Juang’s password authenticated key agreement scheme using smart cards. IEEE Transactions on Industrial Electronics. 2009; 56(6): 2284–2291. 10.1109/TIE.2009.2016508 [DOI] [Google Scholar]
- 8. Lu RX, Lin XD, Liang XH, Shen XM A dynamic privacy-preserving key management scheme for location-based services in vanets. IEEE Transactions on Intelligent Transportation Systems. 2012; 13(1): 127–139. 10.1109/TITS.2011.2164068 [DOI] [Google Scholar]
- 9. Zhao DW, Peng HP, Li LX, Yang YX. A secure and effective anonymous authentication scheme for roaming service in global mobility networks. Wireless Personal Communications. 2013; 78: 247–269. 10.1007/s11277-014-1750-y [DOI] [Google Scholar]
- 10.Lu, YR, Li, LX, Yang, YX. Robust and efficient authentication scheme for session initiation protocol. Mathematical Problems in Engineering. 2015; 2015, Article ID 894549, 9 pages.
- 11. Lu YR, Li LX, Peng HP, Yang YX. An enhanced biometric-based authentication scheme for telecare medicine information systems using elliptic curve cryptosystem. Journal of Medical Systems. 2015; 39(3): 1–8. 10.1007/s10916-015-0221-7 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 12. Lu YR, Li LX, Peng HP, Yang YX. Robust and efficient biometrics based password authentication scheme for telecare medicine information systems using extended chaotic maps. Journal of Medical Systems. 2015. 10.1007/s10916-015-0221-7 [DOI] [PubMed] [Google Scholar]
- 13.Lu, YR, Li, LX, Peng, HP, Yang, YX. A biometrics and smart cards based authentication scheme for multi-server environments. Security and Communication Networks. 2015;
- 14. Tsai JL. Efficient multi-server authentication scheme based on one-way hash function without verification table. Computers & Security. 2008; 27(3–4): 115–121. 10.1016/j.cose.2008.04.001 [DOI] [Google Scholar]
- 15. Lu RX, Lin XD, Zhu HJ, Liang XH, Shen XM. BECAN: a bandwidth-efficient cooperative authentication scheme for filtering injected false data in wireless sensor networks. IEEE Transactions on Parallel and Distributed Systems. 2012; 23(1): 32–43. 10.1109/TPDS.2011.95 [DOI] [Google Scholar]
- 16. Liao YP, Wang SS. A secure dynamic ID based remote user authentication scheme for multi-server environment. Computer Standards & Interfaces. 2009; 31(1): 24–29. 10.1016/j.csi.2007.10.007 [DOI] [Google Scholar]
- 17. Lee CC, Lin TH, Chang RX. A secure dynamic ID based remote user authentication scheme for multi-server environment using smart cards. Expert Systems with Applications. 2011; 38(11): 13863–13870 [Google Scholar]
- 18. Li X, Ma J, Wang WD, Liu CL. A novel smart card and dynamic ID based remote user authentication scheme for multi-server environments. Mathematical and Computer Modelling. 2013; 58: 85–95. 10.1016/j.mcm.2012.06.033 [DOI] [Google Scholar]
- 19. Xue KP, Hong PL, Ma CS. A lightweight dynamic pseudonym identity based authentication and key agreement protocol without verification tables for multi-server architecture. Journal of Computer and System Sciences. 2014; 80: 195–206. 10.1016/j.jcss.2013.07.004 [DOI] [Google Scholar]
- 20. Lu YR, Li LX, Peng HP, Yang X, Yang YX. A lightweight ID based authentication and key agreement protocol for multi-server architecture. International Journal of Distributed Sensor Network. 2015, Article ID 635890, 9 pages. [Google Scholar]
- 21. Li CT, Hwang MS. An efficient biometrics-based remote user authentication scheme using smart cards. Journal of Network and Computer Applications. 2010; 33(1): 1–5. 10.1016/j.jnca.2009.08.001 [DOI] [Google Scholar]
- 22. Chuang MC, Chen MC. An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Expert Systems with Applications. 2014; 41: 1411–1418. 10.1016/j.eswa.2013.08.040 [DOI] [Google Scholar]
- 23. Mishra D, Das AK, Mukhopadhyay S. A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Systems with Applications. 2014; 41(18): 8129–8143. 10.1016/j.eswa.2014.07.004 [DOI] [Google Scholar]
- 24. Burrow M, Abadi M, Needham R. A logic of authentication, ACM Transactions on Computer System. 1990; 8(1): 18–36. 10.1145/77648.77649 [DOI] [Google Scholar]
- 25. Messerges TS, Dabbish EA, Sloan RH. Examining smart-card security under the threat of power analysis attacks. IEEE Transactions on Computers. 2002; 51(5): 541–552. 10.1109/TC.2002.1004593 [DOI] [Google Scholar]
- 26. Stallings W. Cryptography and Network Security: Principles and Practices, third ed Prentice Hall; 2003. [Google Scholar]
- 27. Das AK. A secure and effective user authentication and privacy preserving protocol with smart cards for wireless communications. Networking Science. 2013; 2(1–2): 12–27. 10.1007/s13119-012-0009-8 [DOI] [Google Scholar]
- 28. Das AK, Paul NR, Tripathy L. Cryptanalysis and improvement of an access control in user hierarchy based on elliptic curve cryptosystem. Information Sciences. 2012; 209: 80–92. 10.1016/j.ins.2012.04.036 [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
All relevant data are within the paper.