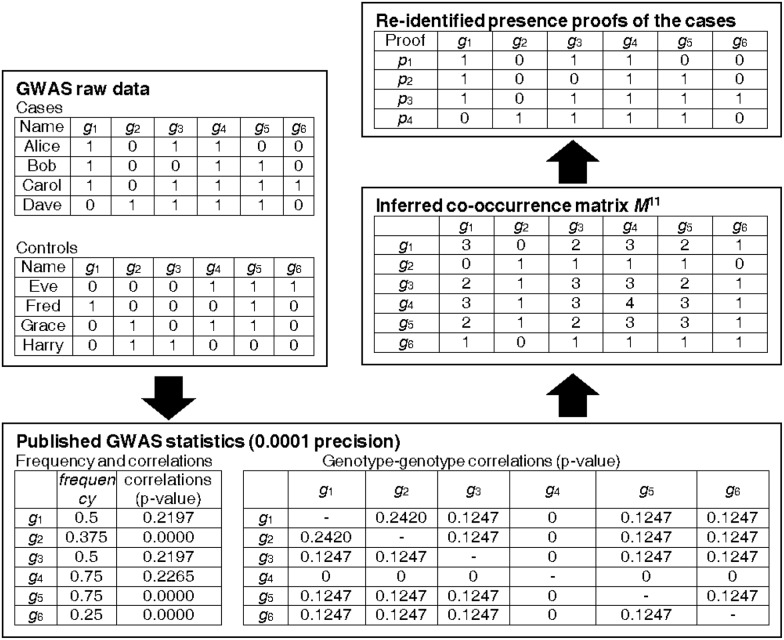
Fig. 1.
Example of GWAS result publication and the privacy attack. Top left: part of the raw data of the GWAS, which contains genome sequences for study participants. Bottom: published results of the GWAS, which lists the genotypes of interest, their frequencies and correlation with the disease, as well as the correction between each pair of these genotypes. Right column: the proposed privacy attack, which first recovers a co-occurrence matrix from the published statistics (only M11 is given for space limitation) and uses this matrix to build presence proofs, i.e. sets of genotypes that must be present among the cases