Abstract
We consider the Galerkin boundary element method (BEM) for weakly-singular integral equations of the first-kind in 2D. We analyze some residual-type a posteriori error estimator which provides a lower as well as an upper bound for the unknown Galerkin BEM error. The required assumptions are weak and allow for piecewise smooth parametrizations of the boundary, local mesh-refinement, and related standard piecewise polynomials as well as NURBS. In particular, our analysis gives a first contribution to adaptive BEM in the frame of isogeometric analysis (IGABEM), for which we formulate an adaptive algorithm which steers the local mesh-refinement and the multiplicity of the knots. Numerical experiments underline the theoretical findings and show that the proposed adaptive strategy leads to optimal convergence.
Keywords: Isogeometric analysis, Boundary element method, A posteriori error estimate, Adaptive mesh-refinement
1. Introduction
Isogeometric analysis. The central idea of isogeometric analysis is to use the same ansatz functions for the discretization of the partial differential equation at hand, as are used for the representation of the problem geometry. Usually, the problem geometry is represented in computer aided design (CAD) by means of NURBS or T-splines. This concept, originally invented in [1] for finite element methods (IGAFEM) has proved very fruitful in applications [1,2]; see also the monograph [3]. Since CAD directly provides a parametrization of the boundary , this makes the boundary element method (BEM) the most attractive numerical scheme, if applicable (i.e., provided that the fundamental solution of the differential operator is explicitly known). Isogeometric BEM (IGABEM) has first been considered for 2D BEM in [4] and for 3D BEM in [5]. Unlike standard BEM with piecewise polynomials which is well-studied in the literature, cf. the monographs [6,7] and the references therein, the numerical analysis of IGABEM is essentially open. We only refer to [2,8–10] for numerical experiments and to [11] for some quadrature analysis. In particular, a posteriori error estimation has been well-studied for standard BEM, e.g., [12–18] as well as the recent overview article [19], but has not been treated for IGABEM so far. The purpose of the present work is to shed some first light on a posteriori error analysis for IGABEM which provides some mathematical foundation of a corresponding adaptive algorithm.
Main result. Let be a Lipschitz domain and be a compact, piecewise smooth part of the boundary with finitely many connected components (see Sections 2.2 and 2.3). Given a right-hand side , we consider boundary integral equations in the abstract form
| (1.1) |
where is an elliptic isomorphism. Here is a fractional-order Sobolev space, and is its dual (see Section 2). Given , the Lax–Milgram lemma provides existence and uniqueness of the solution of the variational formulation of (1.1)
| (1.2) |
In the Galerkin boundary element method (BEM), the test space is replaced by some discrete subspace . Again, the Lax–Milgram lemma guarantees existence and uniqueness of the solution of the discrete variational formulation
| (1.3) |
and can in fact be computed by solving a linear system of equations.
We assume that is linked with a partition of into a set of connected segments. For each vertex of , let denote the node patch. If is sufficiently rich (e.g., contains certain splines or NURBS; see Section 4), we prove that
| (1.4) |
with some -independent constants , i.e., the unknown BEM error is controlled by some computable a posteriori error estimator . Here, denotes the residual and
| (1.5) |
is the Sobolev–Slobodeckij seminorm.
Estimate (1.4) has first been proved by Faermann [17] for closed and standard spline spaces based on the arclength parametrization . In isogeometric analysis, is not the arclength parametrization. In our contribution, we generalize and refine the original analysis of Faermann [17]: Our analysis allows, first, closed as well as open parts of the boundary, second, general piecewise smooth parametrizations and, third, covers standard piecewise polynomials as well as NURBS spaces .
Outline. Section 2 recalls the functional analytic framework, provides the assumptions on and its parametrization , and fixes the necessary notation. The proof of (1.4) is given in Section 3 for sufficiently rich spaces (Theorem 3.1). In Section 4, we recall the NURBS spaces for IGABEM and prove that these spaces satisfy the assumptions (Assumptions (A1)–(A2) in Section 3.1) of the a posteriori error estimate (1.4). Based on knot insertion, we formulate an adaptive algorithm which is capable to control and adapt the multiplicity of the nodes as well as the local mesh-size (Algorithm 4.5). Section 5 gives some brief comments on the stable implementation of adaptive IGABEM for Symm’s integral equation and provides the numerical evidence for the superiority of the proposed adaptive IGABEM over IGABEM with uniform mesh-refinement. In the final Section 6, some conclusions are drawn and some comments on future work and open questions are reported.
2. Preliminaries
The purpose of this section is to collect the main assumptions on the boundary and its discretization as well as to fix the notation. For more details on Sobolev spaces and the functional analytic setting of weakly-singular integral equations, we refer to the literature, e.g., the monographs [20,21,6] and the references therein.
Throughout, denotes the absolute value of scalars, the Euclidean norm of vectors in , the measure of a set in , e.g. the length of an interval, or the arclength of a curve in . The respective meaning will be clear from the context.
2.1. Sobolev spaces
For any measurable subset , let denote the Lebesgue space of all square integrable functions which is associated with the norm . We define the Hilbert space
| (2.1) |
associated with the Sobolev–Slobodeckij norm
| (2.2) |
For finite intervals we use analogous definitions. By , we denote the dual space of , where duality is understood with respect to the -scalar product, i.e.,
| (2.3) |
We note that form a Gelfand triple and all inclusions are dense and compact. Amongst other equivalent definitions of are the characterization as trace space of functions in as well as equivalent interpolation techniques. All these definitions provide the same space of functions but different norms, where norm equivalence constants depend only on ; see, e.g., the monograph [21] and references therein. Throughout, we shall use the Sobolev–Slobodeckij norm (2.2), since it is numerically computable.
2.2. Connectedness of
Let the part of the boundary be decomposed into its finitely many connected components . The are compact and piecewise smooth as well. Note that this yields existence of some constant such that for all , , and . Together with , this provides the estimate
and results in norm equivalence
The usual piecewise polynomial and NURBS basis functions have connected support and are hence supported by some single each. Without loss of generality and for the ease of presentation, we may therefore from now on assume that is connected. All results of this work remain valid for non-connected .
2.3. Boundary parametrization
We assume that either is parametrized by a closed continuous and piecewise two times continuously differentiable path such that the restriction is even bijective, or that is parametrized by a bijective continuous and piecewise two times continuously differentiable path . In the first case, we speak of closed , whereas the second case is referred to as open . For closed , we denote the -periodic extension to also by . For the left and right derivative of , we assume that for and for . Moreover we assume that for all and resp. . Finally, let denote the arclength parametrization, i.e., , and its periodic extension. Then, elementary differential geometry yields bi-Lipschitz continuity
| (2.4) |
A proof is given in [22, Lemma 2.1] for closed . For open , the proof is even simpler. If is closed and resp. if is open and , we see from (2.4) that
| (2.5) |
2.4. Boundary discretization
The part of the boundary is split into a set of compact and connected segments . The endpoints of the elements of form the set of nodes for closed and for open . The arclength of each element is denoted by , where . Moreover, we define the shape regularity constant
For closed , we extend the nodes, elements and their length periodically. We suppose
| (2.6) |
if is closed.
2.5. Parameter domain discretization
Given the parametrization , the discretization induces a discretization on the parameter domain . Let be the endpoints of the elements of . We assume , and . We define for closed , and for open . The length of each element is denoted by . Moreover, we define the shape regularity constant on as
3. A posteriori error estimate
3.1. Main theorem
For , we inductively define the patch of order by
| (3.1) |
The main result of Theorem 3.1 requires the following two assumptions on and for some fixed integer :
-
(A1)For each , there exists some fixed function with connected support such that
(3.2) -
(A2)There exists some constant such that
(3.3)
With these assumptions, we can formulate the following theorem which states validity of (1.4). For standard BEM and piecewise polynomials based on the arclength parametrization of some closed boundary , the analogous result is first proved in [17, Theorem 3.1]
Theorem 3.1
The residual satisfies the efficiency estimate
(3.4) If the mesh and the discrete space satisfy assumptions (A1)–(A2) , also the reliability estimate
(3.5) holds. The constant depends only on , while depends additionally on , , , and .
Remark 3.2
The proof reveals that the efficiency estimate (3.4) is valid for any approximation of , while the upper reliability estimate (3.5) requires some Galerkin orthogonality.
Sketch of the proof of Theorem 3.1
Since is an isomorphism, the residual satisfies , where the hidden constant depends only on . Therefore, it suffices to prove (3.4)–(3.5) with replaced by . For , Proposition 3.3 proves , and hence results in (3.4). For , Lemma 3.4 shows that it suffices to verify to conclude reliability (3.5). This is done via a generalized Poincaré inequality, which involves the abstract assumptions (A1)–(A2) and requires that the residual is -orthogonal to the functions ; see Lemma 3.6 which is proved by induction on . Combining Lemmas 3.4 and 3.6, Proposition 3.7 concludes that and hence results in reliability (3.5). □
3.2. Proof of efficiency estimate (3.4)
The elementary proof of the following proposition is already found in [17, page 208], but we include the proof for closed to stress the explicit constant. For open , the proof works analogously.
Proposition 3.3
For arbitrary , it holds
(3.6)
Proof for closed
For we abbreviate . For with some , we set . There holds
The last term is just , which concludes the proof. □
Proof of Theorem 3.1, eq. (3.4)
Recall that , where the hidden constants depend only on . Together with (3.6), this proves (3.4). □
3.3. Proof of reliability estimate (3.5)
We start with the following lemma. For the elementary (but long) proof, we refer to [17, Lemma 2.3]. A detailed proof is also found in [22, Proposition 2.13].
Lemma 3.4
There exists a constant such that for all
The constant depends only on and .
Our next goal is to bound . To this end, we need the following Poincaré-type inequality from [17, Lemma 2.5].
Lemma 3.5
Let be a finite interval with length . Then, there holds
Lemma 3.6
Suppose the assumptions (A1)–(A2) . Let satisfy
(3.7) Then, there exists a constant which depends only on , , , and such that for all
(3.8)
Proof of Lemma 3.6 for closed
The assertion is formulated on the boundary itself. Without loss of generality, we may therefore assume that . Since is connected, there is an interval of length with . We use Lemma 3.5 and get
With the orthogonality (3.7) and Assumption (A2), we see
Using the last two inequalities, we therefore get
Together with , this implies
(3.9) For , (A1) with , (2.5) (applicable because of (2.6)), and (3.9) conclude the proof with . To estimate for , we use induction on to prove the following assertion for all :
(3.10) For , (3.10) even holds with equality. The induction hypothesis for is
(3.11) For , let
For , the definition of the Sobolev–Slobodeckij seminorm (2.2) shows
(3.12) For , we have
With the abbreviate notation , it hence follows
There holds
This implies
Inserting this into (3.12) and using
as well as the induction hypothesis (3.11), we obtain
This concludes the induction step and thus proves (3.10). Since is closed, the patch consists either of elements or coincides with , wherefore there is an index with
(3.13) Because of Assumption (A1), one can choose such that . We use (3.9) and (3.10) for to see
Finally, we use (2.5) and
which follows immediately from (3.13), to get
which concludes the proof. □
Proof of Lemma 3.6 for open
The proof works essentially as before, where (3.10) now becomes
Details are found in [22, Lemma 2.15]. □
Proposition 3.7
Suppose the assumptions (A1)–(A2) and let satisfy (3.7). Then, there exists a constant which depends only on , , , and such that
(3.14)
Proof of Proposition 3.7 for closed
Without loss of generality, we may assume that . Due to Lemma 3.4, it remains to estimate the term . For , we see
For , Assumption (A1) and Lemma 3.6 give
(3.15) Let with . We extend the mesh data periodically. With the abbreviate notation , we see
(3.16) Combining (3.15) and (3.16), we obtain with
(3.17) This concludes the proof. □
Proof of Proposition 3.7 for open
The proof works essentially as for . For details we refer to [22, Proposition 2.16]. □
Proof of Theorem 3.1, eq. (3.5)
Galerkin BEM ensures the Galerkin orthogonality
and hence guarantees (3.7) for the residual . Since is an isomorphism, together with (3.14) proves (3.5). □
4. Adaptive IGABEM
4.1. B-splines and NURBS
Throughout this subsection, we consider knots on with for and . For the multiplicity of any knot , we write . We denote the corresponding set of nodes with for . For , the th B-Spline of degree is defined inductively by
| (4.1) |
where, for ,
We also use the notations and to stress the dependence on the knots . The proof of the following theorem is found in [23, Theorem 6].
Theorem 4.1
Let be a finite interval and . Then
(4.2) is a basis for the space of all right-continuous piecewise polynomials of degree lower or equal on and which are, at each knot , times continuously differentiable if .
In addition to the knots , we consider positive weights with . For and , we define the th non-uniform rational B-Spline of degree or shortly NURBS as
| (4.3) |
We also use the notation . Note that the denominator is locally finite and never zero as shown in the following lemma.
Lemma 4.2
For and , the following assertions hold:
- (i)
is a rational function with nonzero denominator, which can be extended continuously at .
- (ii)
vanishes outside the interval . It is positive on the open interval .
- (iii)
It holds if and only if .
- (iv)
is completely determined by the knots . is completely determined by the knots and the weights . Therefore, we will also use the notation
(4.4) - (v)
The NURBS functions of degree form a partition of unity, i.e.
(4.5) - (vi)
If all weights are equal, then . Hence, B-splines are just special NURBS functions.
- (vii)
Each NURBS function is at least times continuously differentiable at if .
- (viii)
For and , we haveas well as
(4.6)
(4.7) - (ix)
Let be a sequence of knots such that for all and, a sequence of positive weights. If converges pointwise to and converges pointwise to , then converges almost everywhere to for all .
Proof
The proof for (i)–(v) can be found in [23, Section 2, page 9–10] for B-splines. The generalization to NURBS is trivial. (vi) is an immediate consequence of (v). (vii) follows from Theorem 4.1. To prove (viii), we note that for all and it holds
as well as
Hence, the assertion is an immediate consequence of the definition of B-splines. For B-splines, (ix) is proved by induction, noting that for all and , we have
This easily implies the convergence of . □
For any , we define the vector spaces
| (4.8) |
as well as
| (4.9) |
Note that the sums are locally finite.
An analogous version of the following result is already found in [17] for the special case of B-splines of degrees and knot multiplicity for all and weight function . The following generalization to arbitrary NURBS, however, requires a completely new idea.
Lemma 4.3
Let be a compact interval with nonempty interior, , real numbers, , and a piecewise continuously differentiable function with positive infimum. Then there exists a constant
such that for arbitrary knots and corresponding nodes with
(4.10) weights and all ,
(4.11) Note that there holds
Proof
We prove the lemma in five steps.
Step 1: We give an abstract formulation of the problem. For , we define the bounded set
Note that already implies . For a vector of multiplicities with we introduce the function
Moreover, we define for the function
where . Our aim is to show that for arbitrary there holds . Then, we define the constant as the maximum of all these suprema. Note that the maximum is taken over a finite set, since , and . Before we proceed, we show that really has the desired properties. Without loss of generality, we can assume that not all considered knots are equal. The corresponding nodes and weights are in . If is the corresponding multiplicity vector, (4.11) can indeed be equivalently written as
Step 2: We fix . Without loss of generality, we assume that there exists such that . This just means that the appearing integrals have nonempty integration domains , since in this case is already bounded. Using Lemma 4.2 (ii) and (v), we see that for , the function attains only values in and is positive on the interval . This implies
(4.12) Because of Lemma 4.2 (ix), we can apply Lebesgue’s dominated convergence theorem to see that is continuous. If was compact, we would be done. Unfortunately it is not.
Step 3: Now, we prove the lemma for . In the definition of we replace the interval by to define a superset of
We extend the function to
We define a closed and bounded and hence compact subset of
If , then and due to the substitution rule and Lemma 4.2 (viii), there holds with the notation
Hence we have
As in Step 2 one sees that only attains values in and is continuous. Since is compact we get
This proves the lemma for .
Step 4: We prove the lemma for with and . Again, we extend the function to
For the proof of the lemma, it is sufficient to show . Due to the substitution rule and Lemma 4.2 (viii), we can assume without loss of generality that . Because of Step 3 it only remains to show that
As in Step 2, one verifies that only attains values in and is continuous. Moreover, due to the substitution rule and Lemma 4.2 (viii), we have for any element of
and hence
The second set is compact, since it is the image of a closed and bounded set under a continuous mapping. Therefore it attains a maximum smaller than one. This concludes the proof for .
Step 5: Finally, we are in the position to prove the assertion of the lemma for arbitrary functions with the desired properties. Let be a sequence in such that the -values converge to . Because of the boundedness of , we can assume convergence of the sequence, where the limit is in , i.e. or with . In the first case, we are done because of (4.12) and the continuity of . For the second case, we define
Note that , and that the sequences and converge to the limit
We consider two cases.
Case 1: If is continuous at the limit , it is absolutely continuous on the interval for sufficiently large . Hence we have for sufficiently large
The second summand converges to zero. We consider the first one. For any , there holds for sufficiently large
Since was arbitrary, this implies
Case 2: If is not continuous at the limit we proceed as follows. For sufficiently large , is absolutely continuous on and on . By considering suitable subsequences, we can assume that , or , each for all . In the first two cases, we can proceed as in Case 1. In the third case, we argue similarly as in Case 1 to see, with the left-handed limit and the right-handed limit for large enough
Again, the second summand converges to zero, wherefore it remains to consider the first one. For any , there holds for sufficiently large
Since was arbitrary, this implies
which concludes the proof. □
We return to our problem (1.1). If is closed, each node may be assigned with a multiplicity . This induces a sequence of non decreasing knots on . Let be a sequence of weights on these knots. We extend the knot sequence -periodically to and the weight sequence to by for . For the extended sequences we also write and . We set
| (4.13) |
If is open, we assign to each node a corresponding multiplicity such that . This induces a sequence of non decreasing knots on . Let be a sequence of weights. To keep the notation simple, we extend the sequences arbitrarily to with for , for and for , and with . This allows to define
| (4.14) |
Due to Lemma 4.2 (ii) and (iv), this definition does not depend on how the sequences are extended.
With the following theorem, we conclude that Theorem 3.1 holds for the span of transformed NURBS functions.
Theorem 4.4
Let and . Then, the space is a subspace of which satisfies the assumptions (A1)–(A2) from Section 3.1 with the constant of Lemma 4.3
where with resp. .
Proof of Theorem 4.4 for closed
Lemma 4.2 (i) and (ii), implies . This shows .
Let be an element of the mesh , with , and with and . We define for and extend it continuously at . We set . Because of Lemma 4.2 (ii), there holds
(4.15) Since and are homeomorphisms, there holds
(4.16) wherefore is connected. With (4.15), this shows
and hence implies Assumption (A1).
To verify Assumption (A2), we apply Lemma 4.3. Note that is completely determined by the knots in and their weights. This is due to and Lemma 4.2 (iv). The regularity constant of these knots from (4.10) is obviously smaller or equal than . Since is piecewise two times continuously differentiable and its left and right derivative vanishes nowhere, is piecewise continuously differentiable and is bounded from above by some positive constant. With Lemma 4.3 and (4.16), we hence get
Consequently, Assumption (A2) is also fulfilled. This concludes the proof. □
Proof of Theorem 4.4 for open
The proof works analogously as before. Details are found in [22, Theorem 4.14]. □
4.2. Knot insertion
Before we formulate an adaptive algorithm based on NURBS, we recall refinement by knot-insertion, see e.g. [23, Section 11]. For general knots as in the previous subsection, a polynomial degree , and a refined sequence (i.e., is a subsequence of ) Theorem 4.1 implies nestedness
| (4.17) |
We assume that the multiplicities of the knots in are lower or equal . Because of Lemma 4.2 (ii), and Theorem 4.1 each element admits some unique coefficient vector with
| (4.18) |
If contains only one additional knot (possibly already contained in ), the coefficients can be calculated explicitly. We assume for all with . Then, [23, Algorithm 11] shows
| (4.19) |
For closed , we consider again knots and weights as in the previous subsection. We additionally assume . Now we insert an additional knot to the knots such that the multiplicities of the new knots are still smaller or equal than . The new knots are extended -periodically. We want to find the unique weights which fulfill
| (4.20) |
With (4.9) and (4.17), this already implies nestedness
| (4.21) |
The sought weights are obviously -periodic. We cannot immediately apply (4.19), since infinitely many knots are added to . First, we add to and obtain with and . There exist unique weights with
With , Lemma 4.2 (ii) and (iv), and our assumption imply
With , it is easy to check that for . Hence, Theorem 4.1 implies for . It just remains to add the knots , and . To this end, we can repetitively apply (4.19) to obtain the weights . Note that this only involves the weights are needed. Moreover, the new weights are just convex combinations of the old ones .
For open , a knot can analogously be inserted to the knots .
4.3. Adaptive algorithm
In this section, we introduce an adaptive algorithm, which uses the local contributions of to steer the -refinement of the mesh as well as the increase of the multiplicity of the nodes . To respect the iterative character of this procedure, all discrete quantities (as, e.g., , , etc.) are indexed by the level of the adaptive process instead of the mesh-size . Let be an adaptivity parameter and a polynomial degree. We start with some nodes . Each node has a multiplicity lower or equal , where for open we assume . This induces knots . Let be some initial positive weights. We assume and for closed , for all . As the initial trial space, we consider
| (4.22) |
The adaptive algorithm with Dörfler marking reads as follows:
Algorithm 4.5
Input: Adaptivity parameter , polynomial order , initial mesh with knots , initial weights .
Adaptive loop: Iterate the following steps, until is sufficiently small:
- (i)
Compute discrete solution .
- (ii)
Compute indicators for all nodes .
- (iii)
Determine a minimal set of nodes such that
(4.23) - (iv)
If both nodes of an element belong to , will be marked.
- (v)
For all other nodes in , the multiplicity will be increased if it is smaller than , otherwise the elements which contain one of these nodes , will be marked.
- (vi)
Refine all marked elements by bisection of the corresponding . Use further bisections to guarantee that the new mesh satisfiesUpdate counter .
(4.24) Output: Approximate solutions and error estimators for all .
An optimal 1D bisection algorithm which ensures (4.24), is discussed and analyzed in [24]. Note that boundedness of implies as well boundedness of . Moreover, there holds
| (4.25) |
since the new weights are convex combinations of the old weights. Hence, Theorems 3.1 and 4.4 apply and show efficiency and reliability of the estimator
| (4.26) |
5. Numerical experiments
In this section, we empirically investigate the performance of Algorithm 4.5 in three typical situations: In Sections 5.2 and 5.3, we consider a closed boundary , where the solution is smooth resp. exhibits a generic (i.e., geometry induced) singularity. In Section 5.4, we consider a slit problem. In either example, the exact solution is known and allows us to compute the Galerkin error to underline reliability and efficiency of the proposed estimator.
In each example, the parametrization of the part of the boundary is a NURBS curve and thus has the special form
| (5.1) |
for all . Here, is the polynomial degree, and are knots and weights as in Section 4.3 and are control points in which are periodic for closed .
We choose the same polynomial degree for our approximation spaces . Since for the refinement strategy only knot insertion is used, we can apply (4.17) and (4.20) to see for the first and second component of
| (5.2) |
Hence, this approach reflects the main idea of isogeometric analysis, where the same space is used for the geometry and for the approximation. We compare uniform refinement, where and hence all elements are refined, and adaptive refinement with .
5.1. Stable implementation of adaptive IGABEM
To compute the approximation of one step of the adaptive algorithm, we first note that Theorem 4.1 implies that
| (5.3) |
resp.
| (5.4) |
forms a basis of . We abbreviate the elements of this basis with and its index set with . Then, there holds the unique basis representation . The coefficient vector is the unique solution of
| (5.5) |
with the symmetric positive definite matrix
| (5.6) |
and the right-hand side vector
| (5.7) |
The energy norm then reads
| (5.8) |
To calculate , and the -seminorms of the residual , singular integrals and double integrals have to be evaluated. Since this is hardly possible analytically, we approximate the appearing integrals. To this end, we first write them as sum of integrals over the elements of the mesh . In the spirit of [6, Section 5.3], the local integrals which contain singularities, are transformed by Duffy transformations such that either the singularity vanishes or a pure logarithmic singularity of the form on remains. Finally, the integrals are evaluated over the domain or using tensor-Gauss quadrature with weight function 1 resp. . Since the integrands are smooth up to logarithmic terms, this yields exponential convergence of adapted Gauss quadrature and hence provides accurate approximations. For closed and arbitrary parametrization as in Section 2.3, all details are elaborated in [22, Section 5].
5.2. Adaptive IGABEM for problem with smooth solution
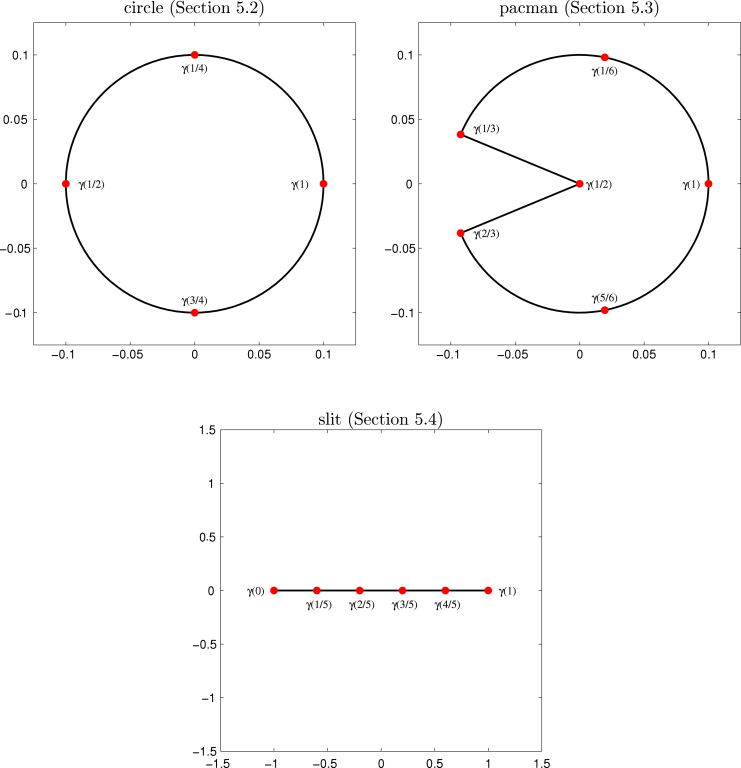
Let be the circle with midpoint and radius . We consider the Laplace–Dirichlet problem on
| (5.9) |
for given Dirichlet data and closed boundary . The problem is equivalent to Symm’s integral equation (1.1) with the single-layer integral operator
| (5.10) |
and the right-hand side , where
| (5.11) |
denotes the double-layer integral operator. The unique solution of (1.1) is the normal derivative of the weak solution of (5.9).
We prescribe the exact solution and solve Symm’s integral equation (1.1) on the closed boundary . The normal derivative reads
The geometry is parametrized on by the NURBS curve induced by
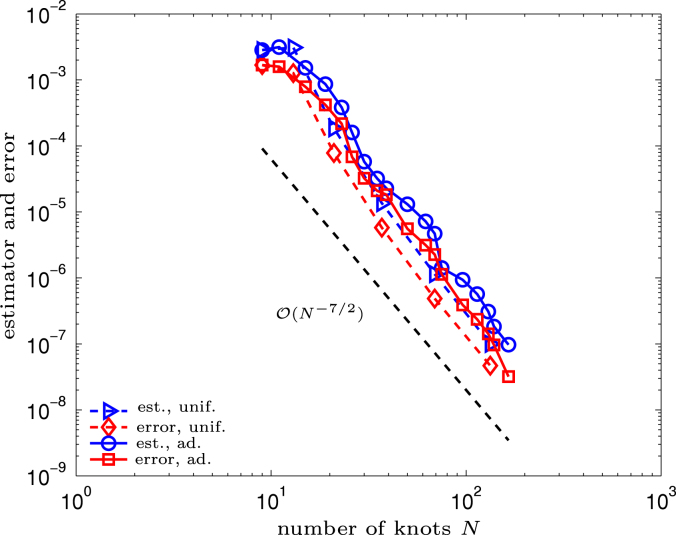
Note that this parametrization does not coincide with the natural parametrization . Fig. 5.1 visualizes the geometry and the -values of the initial nodes. Fig. 5.2 shows error and error estimator for the uniform and the adaptive approach. All values are plotted in a log–log scale such that the experimental convergence rates are visible as the slope of the corresponding curves. The Galerkin orthogonality allows to compute the energy error by
| (5.12) |
With respect to the number of knots , both approaches lead to the rate . If discontinuous piecewise polynomials of order 2 were used as ansatz space, this is the optimal convergence rate. In each case, the curves for the error and the corresponding estimator are parallel. This empirically confirms the proven efficiency and reliability of the Faermann estimator .
Fig. 5.1.
Geometries and initial nodes for the experiments from Sections 5.2–5.4.
Fig. 5.2.
Experiment with smooth solution on circle geometry from Section 5.2. Error and estimator are plotted versus the number of knots .
5.3. Adaptive IGABEM for problem with generic singularity
As second example, we consider the Laplace–Dirichlet problem (5.9) on the pacman geometry
with ; see Fig. 5.1. We prescribe the exact solution
The normal derivative of reads
and has a generic singularity at the origin. With , the geometry is parametrized on by the NURBS curve induced by
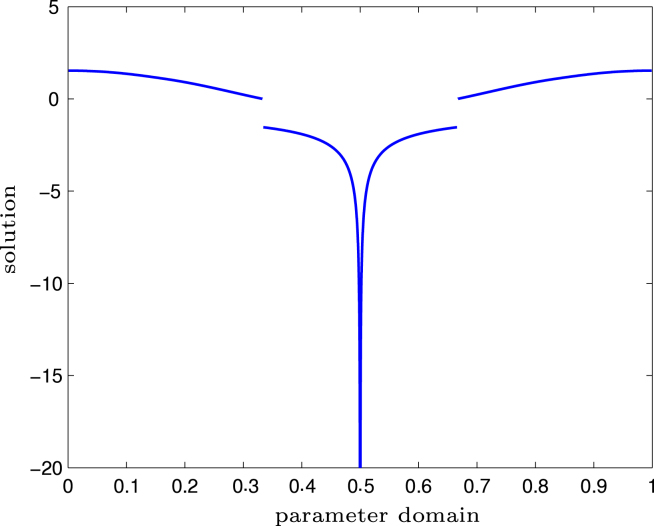
In Fig. 5.3, the solution is plotted over the parameter domain. We can see that has a singularity at as well as two jumps at resp. .
Fig. 5.3.
Experiment with singular solution on pacman geometry from Section 5.3. The singular solution is plotted on the parameter interval, where 0.5 corresponds to the origin, where is singular.
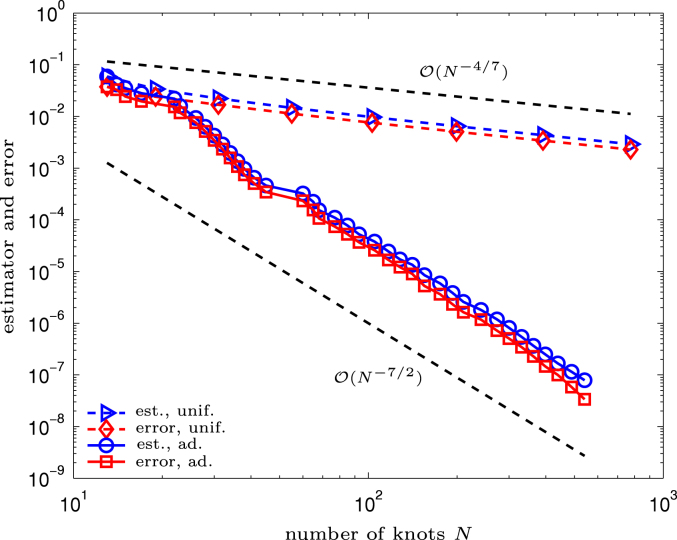
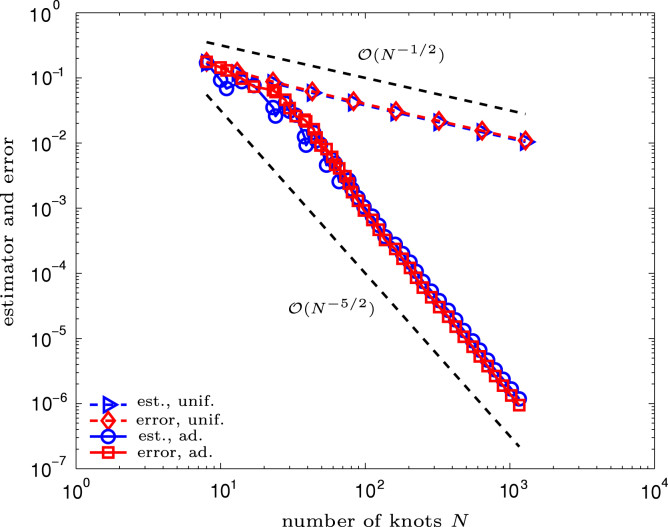
In Fig. 5.4, error and error estimator are plotted. As the respective curves are parallel, we empirically confirm efficiency and reliability of the Faermann estimator. For the calculation of the error, we used in (5.12) which is obtained by Aitken’s -extrapolation. Since the solution lacks regularity, uniform refinement leads to the suboptimal rate , whereas adaptive refinement leads to the optimal rate .
Fig. 5.4.
Experiment with singular solution on pacman geometry from Section 5.3. Error and estimator are plotted versus the number of knots .
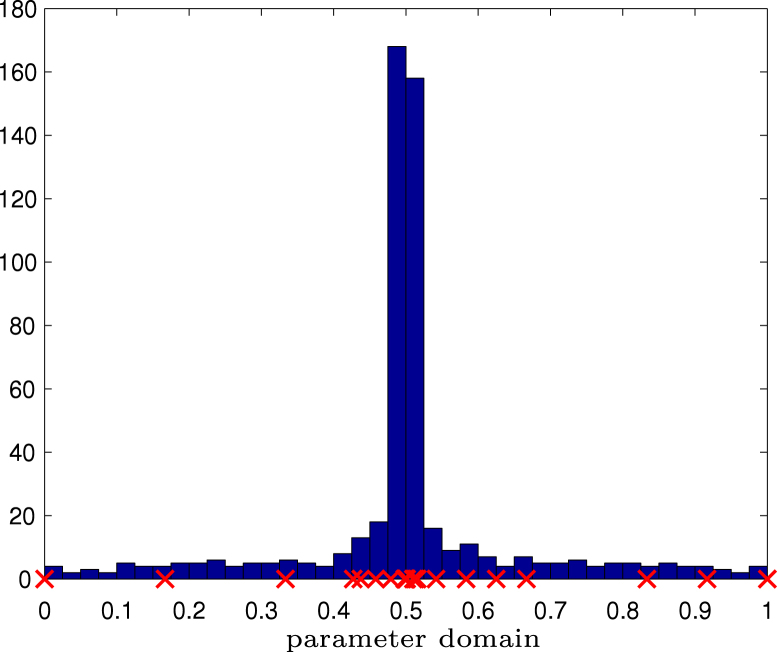
For adaptive refinement, Fig. 5.5 provides a histogram of the knots in of the last refinement step. We see that the algorithm mainly refines the mesh around the singularity at . Moreover, the multiplicity at the jump points and appears to be maximal so that the discrete solution also mimics the discontinuities of the exact solution . Hence the functions of the considered ansatz space do not need to be continuous there, see Theorem 4.1.
Fig. 5.5.
Experiment with singular solution on pacman geometry from Section 5.3. Histogram of number of knots over the parameter domain. Knots with maximal multiplicity are marked.
5.4. Adaptive IGABEM for slit problem
As last example, we consider a crack problem on the slit . For and the single-layer operator from (5.10), the exact solution of (1.1) reads
Note that for all and that has singularities at the tips . We parametrize by the NURBS curve induced by
In Fig. 5.6, error and error estimator for the uniform and for the adaptive approach are plotted. The error is obtained via (5.12), where is computed analytically. Since the solution lacks regularity, uniform refinement leads to the suboptimal rate , whereas adaptive refinement leads to the optimal rate .
Fig. 5.6.
Experiment with singular solution on slit from Section 5.4. Error and estimator are plotted versus the number of knots .
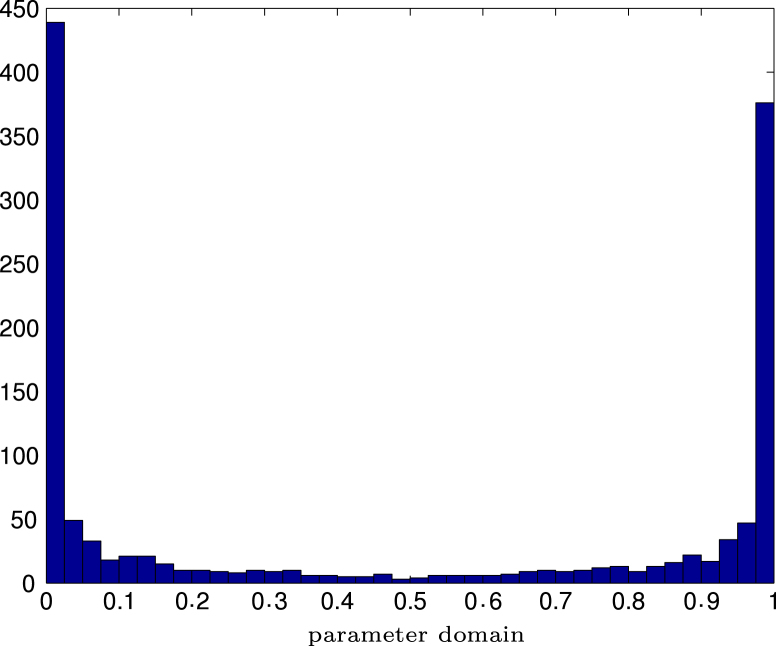
For adaptive refinement, we plot in Fig. 5.7 a histogram of the knots in of the last refinement step. As expected, the algorithm mainly refines the mesh at the tips and .
Fig. 5.7.
Experiment with singular solution on slit from Section 5.4. Histogram of number of knots over the parameter domain.
6. Conclusion
In this paper, we studied the residual-based a posteriori error estimator proposed by Faermann [17] for the Galerkin boundary element method (BEM) in 2D. We proved reliability as well as efficiency of this estimator, where reliability requires that the ansatz space is sufficiently rich. This property is in particular satisfied for NURBS (see Theorem 4.4), and thus our result provides a first a posteriori error estimator for isogeometric BEM (IGABEM). Based on this error estimator, we formulated an adaptive algorithm for IGABEM, which uses -refinement as well as multiplicity increase of the knots for refinement.
6.1. Analytical results
The numerical analysis of the pioneering work [17] is restricted to the case of transformed spline ansatz spaces, where the arclength parametrization is used to define polynomial ansatz spaces on the boundary. It is our contribution, first, to work out the essential properties of the BEM spaces, which are needed to prove reliability and efficiency (see (A1)–(A2)), and, second, to show their validity in the case of IGABEM. Additionally, we propose a mesh-refining adaptive algorithm, which, in contrast to the one proposed in [17] and the state-of-the-art concepts [25], also steers the continuity properties of the discrete solution at the knots.
6.2. Numerical results
We considered the weakly-singular integral equation associated to the 2D Laplace problem. The conclusions of the three examples in Sections 5.2–5.4 are analogous and can be described as follows: Compared to uniform refinement, we always observed a superior convergence rate (or at least an equal one in the case of a smooth solution) of our proposed adaptive strategy. Indeed, the convergence rates of adaptive refinement are optimal with respect to the number of knots. Our algorithm is capable to detect the singularities of the (in general unknown) solution and to mainly perform refinement at these points. Moreover, jumps of the solution are automatically detected and the discontinuity is adaptively included in the ansatz spaces.
6.3. Open questions and future work
As already mentioned, all considered numerical experiments show optimal convergence of the estimator and the error. Thus, it is a goal of our future research to understand this observation mathematically in the spirit of [25]. However, it is questionable if an analogous version of the reduction property on refined element domains [25, (A2)], can be proved for the Faermann estimator . Indeed, this is yet an open problem even for standard BEM with piecewise polynomials; see [26], where at least convergence of an -adaptive algorithm is analyzed. For the weighted-residual error estimator proposed in [16], the axioms of [25] are satisfied for standard BEM with piecewise polynomials, see [25, Section 5.4]. In [22, Section 3.2], we show that the Faermann estimator can always be bounded from above by , i.e., , where depends only on . This especially implies reliability of for Galerkin IGABEM. Therefore, a natural goal is to prove optimal convergence of our adaptive algorithm for the estimator .
Finally, the ultimate goal is of course to apply the estimators and in 3D Galerkin IGABEM. One then has to consider, e.g., T-splines [5] or hierarchical B-splines [27], since, in contrast to multivariate NURBS, they naturally allow for local mesh refinement. For standard BEM with piecewise polynomials, [18] shows reliability and efficiency for , whereas [16] proves reliability. [25, Section 5.4] proves optimal convergence of adaptive -refinement for , while the estimate as well as plain convergence for -based adaptivity is analyzed in [26]. The transfer of the mentioned results from standard BEM to adaptive IGABEM leaves interesting and challenging questions for future research.
Acknowledgments
The authors acknowledge support through the Austrian Science Fund (FWF) under grant P21732Adaptive Boundary Element Method as well as P27005 Optimal adaptivity for BEM and FEM–BEM coupling. In addition, DP and MF are supported through the FWF doctoral school Nonlinear PDEs funded under grant W1245, and GG through FWF under grant P26252Infinite elements for exterior Maxwell problems.
Contributor Information
Michael Feischl, Email: Michael.Feischl@tuwien.ac.at.
Gregor Gantner, Email: Gregor.Gantner@tuwien.ac.at.
Dirk Praetorius, Email: Dirk.Praetorius@tuwien.ac.at.
References
- 1.Hughes Thomas J.~R., Cottrell J.~Austin, Bazilevs Yuri. Isogeometric analysis: CAD, finite elements, NURBS, exact geometry and mesh refinement. Comput. Methods Appl. Mech. Engrg. 2005;194(39–41):4135–4195. [Google Scholar]
- 2.Simpson Robert~N., Bordas Stéphane P.~A., Trevelyan Jon, Rabczuk Timon. A two-dimensional isogeometric boundary element method for elastostatic analysis. Comput. Methods Appl. Mech. Engrg. 2012;209/212:87–100. [Google Scholar]
- 3.Cottrell J.~Austin, Hughes Thomas~J.R., Bazilevs Yuri. John Wiley & Sons; 2009. Isogeometric Analysis: Toward Integration of CAD and FEA. [Google Scholar]
- 4.Politis Costas, Ginnis Alexandros~I, Kaklis Panagiotis~D, Belibassakis Kostas, Feurer Christian. 2009 SIAM/ACM Joint Conference on Geometric and Physical Modeling. ACM; 2009. An isogeometric BEM for exterior potential-flow problems in the plane; pp. 349–354. [Google Scholar]
- 5.Scott M.A., Simpson Robert~Napier, Evans J.A., Lipton S., Pierre~Alain Bordas Stephane, Hughes T.J.R., Sederberg T.W. Isogeometric boundary element analysis using unstructured T-splines. Comput. Methods Appl. Mech. Engrg. 2013;254:197–221. [Google Scholar]
- 6.Sauter Stefan~A., Schwab Christoph. vol. 39. Springer-Verlag; Berlin: 2011. Boundary element methods. (Springer Series in Computational Mathematics). [Google Scholar]
- 7.Steinbach Olaf. Springer; New York: 2008. Numerical Approximation Methods for Elliptic Boundary Value Problems. [Google Scholar]
- 8.Takahashi Toru, Matsumoto Toshiro. An application of fast multipole method to isogeometric boundary element method for Laplace equation in two dimensions. Eng. Anal. Bound. Elem. 2012;36(12):1766–1775. [Google Scholar]
- 9.Peake Michael~J., Trevelyan Jon, Coates Graham. Extended isogeometric boundary element method (XIBEM) for two-dimensional Helmholtz problems. Comput. Methods Appl. Mech. Engrg. 2013;259:93–102. [Google Scholar]
- 10.Simpson Robert N., Scott Michael A., Taus Matthias, Thomas Derek C., Lian Haojie. Acoustic isogeometric boundary element analysis. Comput. Methods Appl. Mech. Engrg. 2014;269:265–290. [Google Scholar]
- 11.Heltai Luca, Arroyo Marino, DeSimone Antonio. Nonsingular isogeometric boundary element method for Stokes flows in 3D. Comput. Methods Appl. Mech. Engrg. 2014;268:514–539. [Google Scholar]
- 12.Carstensen Carsten, Stephan Ernst~P. A posteriori error estimates for boundary element methods. Math. Comp. 1995;64(210):483–500. [Google Scholar]
- 13.Carstensen Carsten, Stephan Ernst~P. Adaptive boundary element methods for some first kind integral equations. SIAM J. Numer. Anal. 1996;33(6):2166–2183. [Google Scholar]
- 14.Carstensen Carsten. An a posteriori error estimate for a first-kind integral equation. Math. Comp. 1997;66(217):139–155. [Google Scholar]
- 15.Carstensen Carsten, Maischak Matthias, Praetorius Dirk, Stephan Ernst~P. Residual-based a posteriori error estimate for hypersingular equation on surfaces. Numer. Math. 2004;97(3):397–425. [Google Scholar]
- 16.Carstensen Carsten, Maischak Matthias, Stephan Ernst~P. A posteriori error estimate and -adaptive algorithm on surfaces for Symm’s integral equation. Numer. Math. 2001;90(2):197–213. [Google Scholar]
- 17.Faermann Birgit. Localization of the Aronszajn-Slobodeckij norm and application to adaptive boundary element methods. I. The two-dimensional case. IMA J. Numer. Anal. 2000;20(2):203–234. [Google Scholar]
- 18.Faermann Birgit. Localization of the Aronszajn-Slobodeckij norm and application to adaptive boundary element methods. II. The three-dimensional case. Numer. Math. 2002;92(3):467–499. [Google Scholar]
- 19.Feischl Michael, Führer Thomas, Heuer Norbert, Karkulik Michael, Praetorius Dirk. Adaptive boundary element methods: A posteriori error estimators, adaptivity, convergence, and implementation. Arch. Comput. Methods Eng. 2014 doi: 10.1016/j.enganabound.2013.10.008. in print. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 20.Hsiao George~C., Wendland Wolfgang~L. Springer; Berlin: 2008. Boundary Integral Equations. [Google Scholar]
- 21.McLean William. Cambridge University Press; Cambridge: 2000. Strongly Elliptic Systems and Boundary Integral Equations. [Google Scholar]
- 22.Gantner Gregor. Vienna University of Technology; 2014. Isogeometric Adaptive BEM. (Master’s thesis) [Google Scholar]
- 23.de~Boor Carl. Mathematics Research Center, University of Wisconsin-Madison; 1986. B (asic)-Spline Basics. [Google Scholar]
- 24.Aurada Markus, Feischl Michael, Führer Thomas, Karkulik Michael, Praetorius Dirk. Efficiency and optimality of some weighted-residual error estimator for adaptive 2D boundary element methods. Comput. Methods Appl. Math. 2013;13(3):305–332. [Google Scholar]
- 25.Carstensen Carsten, Feischl Michael, Page Marcus, Praetorius Dirk. Axioms of adaptivity. Comput. Math. Appl. 2014;67(6):1195–1253. doi: 10.1016/j.camwa.2013.12.003. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 26.Feischl Michael, Führer Thomas, Mitscha-Eibl Gregor, Praetorius Dirk, Stephan Ernst~P. Convergence of adaptive BEM and adaptive FEM-BEM coupling for estimators without -weighting factor. Comput. Methods Appl. Math. 2014;14(4):485–508. [Google Scholar]
- 27.Annalisa Buffa, Carlotta Giannelli, Adaptive isogeometric methods with hierarchical splines: error estimator and convergence, 2015 ArXiv preprint arXiv:1502.00565.