Abstract
Key agreements that use only password authentication are convenient in communication networks, but these key agreement schemes often fail to resist possible attacks, and therefore provide poor security compared with some other authentication schemes. To increase security, many authentication and key agreement schemes use smartcard authentication in addition to passwords. Thus, two-factor authentication and key agreement schemes using smartcards and passwords are widely adopted in many applications. Vaidya et al. recently presented a two-factor authentication and key agreement scheme for wireless sensor networks (WSNs). Kim et al. observed that the Vaidya et al. scheme fails to resist gateway node bypassing and user impersonation attacks, and then proposed an improved scheme for WSNs. This study analyzes the weaknesses of the two-factor authentication and key agreement scheme of Kim et al., which include vulnerability to impersonation attacks, lost smartcard attacks and man-in-the-middle attacks, violation of session key security, and failure to protect user privacy. An efficient and secure authentication and key agreement scheme for WSNs based on the scheme of Kim et al. is then proposed. The proposed scheme not only solves the weaknesses of previous approaches, but also increases security requirements while maintaining low computational cost.
Keywords: authentication, key agreement, dynamic identity, wireless sensor networks, password, smartcard
1. Introduction
1.1. Authentication and Key Agreement for WSNs
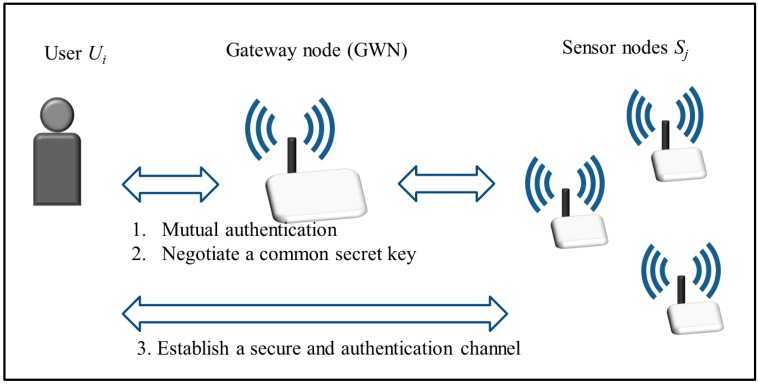
An authentication and key agreement scheme for WSNs comprises users, sensor nodes and a gateway node (GWN), and enables a user and sensor nodes to realize mutual authentication and to negotiate a common secret key via the help of the GWN. The legitimate user and sensor nodes then establish a secure and authentication channel [1,2,3,4,5,6,7,8,9], as shown in Figure 1. A password-based authentication and key agreement scheme only uses a weak password for user authentication, and is the most convenient authentication method. However, these schemes tend to suffer from some possible attacks, and thus have poor security. To improve security, many authentication and key agreement schemes supplement password authentication with long-term secret keys stored in RFID tags or smartcards [1,8,9,10,11,12]. Since long-term secret keys are not easy to guess and break, two-factor authentication schemes that realize identification using passwords and smartcards may increase security, and thus are suitable for WSNs.
Figure 1.
An authentication and key agreement scheme for WSNs.
Several efficient two-factor authentication and key agreement schemes for WSNs have been presented recently. For example, in 2009 Das proposed a two-factor authentication and key agreement scheme using passwords and smartcards [1]. The scheme of Das has low computational cost, and is suitable for resource-constrained WSNs. Many improved authentication and key agreement schemes [9,10,11,12,13] were proposed later to solve the security weaknesses in the Das scheme. Yeh et al. Chen and Shih [11] in 2010 provided an improved scheme based on the Das scheme to ensure that a legal user can use a WSN in a public environment. Yeh et al. [14] in 2011 presented a user authentication scheme based on Elliptic Curves Cryptography (ECC) to overcome the perceived security weaknesses of the scheme of Chen and Shih [11]. However, the scheme of Yeh et al. [14] requires time-consuming scalar multiplications on an elliptic curve, and is still insecure against several possible types of attack, and thus fails to provide a secure and efficient solution for WSNs. Vaidya et al. [15] in 2012 showed that the Das scheme and its derivatives not only have security flaws, but also do not provide key agreement. Additionally, Kim et al. [16] pointed out in 2014 that the scheme of Vaidya et al. fails to resist gateway node bypassing and user impersonation attacks, and also proposed an improved scheme that eliminates such security weaknesses and is efficient in term of computational and communication cost. However, their scheme still fails to withstand some possible attacks, as any legitimate user can obtain the secret keys of sensor nodes such that an adversary can perform impersonation, lost smartcard and man-in-the-middle attacks. Moreover, their scheme violates session key security, and fails to provide user privacy protection.
1.2. Our Contributions
This investigation presents an efficient and secure authentication and key agreement scheme for WSNs to address the weaknesses of the two-factor scheme of Kim et al. [16]. The proposed scheme protects user privacy by using dynamic identities, and by eliminating constant parameters in request messages. Our scheme also encrypts the communicating messages with temporary secret keys rather than constant secret keys of users and sensor nodes, and diminishes redundant variables to ensure session key security. It overcomes the weaknesses in previous schemes, increases security requirements and maintains low computational cost.
1.3. Organization of the Paper
The remainder of this investigation is organized as follows: Section 2 lists the notations and definitions adopted in this investigation, reviews the two-factor authentication and key agreement scheme for WSNs of Kim et al. [16], and analyzes its weaknesses. Section 3 presents the proposed authentication and key agreement scheme using dynamic identities for WSNs. Section 4 and Section 5 present the results of the security and performance evaluation, respectively. Finally, Section 6 draws the conclusions.
2. Preliminaries
This section lists the notations adopted in this paper, describes the underlying primitives used in this investigation, briefly reviews the two-factor authentication and key agreement scheme for WSNs of Kim et al. [16], and then addresses the weaknesses of the their scheme.
Assume that Ui denotes the ith user; Sj denotes the jth sensor node, and GWN denotes the gateway node in which Ui and Sj are registered. Table 1 lists the notations used throughout this paper.
Table 1.
Notation.
| IDi, pwi | Identity and password pair of user Ui |
| SIDj | Identity of sensor node Sj |
| IDs | Identity of smart card |
| K | Secret key only know to GWN |
| xs | Secret value of GWN and Sj |
| KS | Session key |
| RNi, RNj, RNG | Random numbers selected by Ui, Sj and GWN, respectively |
| Ti, Ti′, Tj, TG, TG′ | The timestamp values |
| h(·) | A collision free one-way hash function |
| f(x, k) | Pseudo-random function of variable x with key k |
| A →B:M | A sends message M to B through a common channel. |
| A ⇒ B:M | A sends message M to B through a secure channel |
| ⊕ | The exclusive-or (XOR) operation. |
| M1||M2 | Message M1 concatenates to message M2. |
2.1. Review of the Authentication and Key Agreement Scheme of Kim et al.
Kim et al. [16] in 2014 proposed an improved two-factor authentication and key agreement scheme for WSNs. Their improved scheme comprises registration, login, authentication and key agreement, and password change phases, which are described as follows:
2.1.1. Registration Phase
In the registration phase, Ui registers his/her identity and password to GWN. Then, GWN personalizes a smartcard for Ui. Meanwhile, Sj keeps (SIDj, XSj*) in its storage before being deployed, where XSj* = h(SIDj||xs):
-
Step 1:
Ui GWN:{IDi, HPWi}
Ui selects IDi, password pwi, a random number RNr, computes HPWi = h(pwi||RNr) and sends {IDi, HPWi} to GWN via a secure channel.
-
Step 2:
GWN Ui: Ui′s smartcard
GWN computes HIDi = h(IDi||K), XSi = h(HIDi||xs), Ai = h(HPWi||XSi) h(HIDi||K), Bi = h(HPWi* XSi), Ci = XSi h(IDs||HPWi) and personalizes the smart card for Ui with the parameters: (IDs, HIDi, h(·), Ai, Bi, Ci). Then, GWN sends the smartcard to Ui via a secure channel.
-
Step 3:
Ui computes XPWi = h(pwi) RNr and inserts XPWi into his/her smart card.
2.1.2. Login Phase
-
Step 1:
Ui inserts his/her smart card into a terminal and enters IDi* and PWi*.
-
Step 2:
The smart card computes RNr* = h(pwi) XPWi, HPWi* = h(pwi*||RNr*), XSi* = Ci h(IDs||HPWi*), Bi* = h(HPWi* XSi*) and verifies Bi* = ? Bi. If unsuccessful, the smart card aborts this request; otherwise, the smartcard computes DIDi = Bi* h(XSi*||RNi||Ti), MUi,G = h(Ai||XSi*||RNi||Ti) and vi = RNi XSi*, where RNi is a nonce and Ti is the current timestamp. Then the smartcard sends the authentication request {DIDi, MUi,G, vi, Ti, HIDi} to GWN.
2.1.3. Authentication and Key Agreement Phase
This phase enables Ui and Sj to authenticate each other and to negotiate a secret key, and functions as follows:
-
Step 1:
GWN → Sj: {DIDi, MG,Sj, TG}
GWN checks the validity of Ti, computes XSi = h(HIDi||xs), RNi = vi XSi, X* = DIDi h(XSi||RNi||Ti), MUi,G* = h((X* h(HIDi||K)||XSi||RNi||Ti) and checks MUi,G* = ? MUi,G. If successful, GWN computes XSj = h(SIDj||xs), MG,Sj = h(DIDi||SIDj||XSj||TG) and sends {DIDi, MG,Sj, TG} to Sj, where Sj is the nearest sensor node for Ui and TG is current timestamp.
-
Step 2:
Sj → GWN: {yj, MSj,G, Tj}
Sj checks the validity of TG, computes MG,Sj* = h(DIDi||SIDj||XSj*||TG) and checks MG,Sj* = ? MG,Sj. If successful, Sj computes yj = RNj XSj*, zi = MG,Sj* RNj and MSj,G = h(zi||XSj*||Tj), KS = f((DIDi||RNj), XSj*), and sends {yj, MSj,G, Tj} to GWN, where RNj is a nonce and Tj is current timestamp.
-
Step 3:
GWN → Ui: {yi, wi, MG,Ui, qj, TG′}
GWN checks the validity of Tj, computes RNj = yj XSj, zi* = MG,Sj* RNj, MSj,G* = h(zi*||XSj||Tj), and checks MSj,G* = ? MSj,G. If successful, GWN computes MG,Ui = h(DIDi||MSj,G|| MUi,G||XSj||TG′), wi = zi* XSi, yj = RNj XSj, qj = XSj RNj and sends {yi, wi, MG,Ui, qj, TG′} to Ui, where TG′ is current timestamp.
-
Step 4:
The smart card checks the validity of TG′ and computes RNj = yj XSj, zi* = wi XSi, MG,Sj = zi* RNj, MG,Ui* = h(DIDi||MSj,G*|| MUi,G||XSj||TG′), and checks MG,Ui* = ? MG,Ui. If successful, Ui computes XSj = qj RNj and the session key KS = f((DIDi||RNj), XSj). Then, Ui and Sj successfully realize mutual authentication and have a common session key KS.
2.1.4. Password Change Phase
This phase provides user Ui to change his/her password by performing the following steps:
-
Step 1:
Ui inserts his smartcard and inputs his/her identity IDi*, old password pwi*, and a new password pwni.
-
Step 2:
The smart card computes RNr* = h(pwi*) XPWi, HPWi* = h(pwi*||RNr*), XSi* = Ci h(IDs||HPWi*), Bi* = h(HPWi* XSi*), and checks Bi* = ? Bi. If successful, the smart card computes HPWni = h(pwni||RNr*), Ani = Ai h(HPWi*||XSi*) h(HPWni||XSi*), Bni = h(HPWni XSi*), Cni = XSi* h(IDs||HPWni), and replaces (Ai, Bi, Ci) with (Ani, Bni, Cni).
2.2. Limitations of the Authentication and Key Agreement Scheme of Kim et al.
This subsection addresses the weaknesses of the authentication and key agreement scheme of Kim et al. [16], which include: vulnerability to impersonation, lost smartcard and man-in-the-middle attacks; violation of session key security, and failure to protect user privacy.
2.2.1. Security Against Impersonation Attacks
In the scheme of Kim et al., any legitimate user can obtain the sensor node Sj’s secret XSj* after performing the login phase followed by the authentication and key agreement phase. Malicious user 𝒜 can then easily impersonate Sj to communicate with GWN and any user Ui by using the following steps:
-
Step 1:
On receiving the message {DIDi, MG,Sj, TG} from GWN, 𝒜 computes yj′ = RNj′ XSj*, zi′ = MG,Sj* RNj′ and MSj,G′ = h(zi′||XSj*||Tj), where RNj′ is a nonce selected by 𝒜 and Tj is the timestamp. Then 𝒜 sends back {yj′, MSj,G′, Tj} to GWN
-
Step 2:
Next, 𝒜 is authenticated by GWN since GWN successfully checks and MSj,G′ = ? MSj,G, where RNj′ = yj′ XSj, zi′* = MG,Sj* RNj′, MSj,G′* = h(zi′*||XSj||Tj).
-
Step 3:
Then, 𝒜 computes the session key KS = f((DIDi||RNj′), XSj) shared with Ui. Thus, 𝒜 successfully impersonates Sj to communicate with GWN and Ui.
2.2.2. Security against Lost Smart Card Attacks
The malicious user 𝒜 gets (IDs, HIDi, h(·), Ai, Bi, Ci, XPWi) from Ui’s smartcard. Then 𝒜 can impersonate Ui to communicate with GWN and any sensor node Sj by using the following steps:
-
Step 1:
𝒜 collects previous messages between Ui, GWN and Sj0, which include (DIDi0, vi0, Ti0, HIDi, yj0, yi0, wi0, qj0), and has Sj0’s secret XSj0.
-
Step 2:
𝒜 computes RNj0 = yj0 XSj0, XSi = yi0 RNj0, RNi0 = vi0 XSi, DIDi′ = DIDi0 h(XSi||RNi0||Ti0) h(XSi||RNi′||Ti′), MUi,G′ = h(Ai||XSi||RNi′||Ti′) and vi′ = RNi′ XSi, where RNi′ is a nonce selected by 𝒜 and Ti′ is the current timestamp. Then 𝒜 impersonates Ui and sends the authentication request {DIDi′, MUi,G′, vi′, Ti′, HIDi} to GWN.
-
Step 3:
GWN successfully authenticates 𝒜 by checking and MUi,G* = ? MUi,G′. Next, GWN and Sj realize mutual authentication by validating timestamps TG, Tj and checking MG,Sj* = ? MG,Sj, MSj,G* = ? MSj,G. Then GWN sends back {yi, wi, MG,Ui, qj, TG′} to 𝒜, where MG,Ui = h(DIDi′||MSj,G|| MUi,G||XSj||TG′), wi = zi* XSi, yj = RNj XSj, qj = XSj RNj, and is the current timestamp.
-
Step 4:
The adversary 𝒜 computes RNj = yj XSj and XSj = qj RNj. Then, 𝒜 successfully has the session key KS = f((DIDi′||RNj), XSj) shared with Sj.
2.2.3. Security against Man-in-the-Middle Attacks
Additionally, a legitimate user 𝒜 has Sj’s secret XSj* and can successfully perform the man-in-the-middle attack by using the following steps:
-
Step 1:
User 𝒜 intercepts the communications between GWN and Sj. After receiving the message {DIDi, MG,Sj, TG} from GWN, 𝒜 forwards it to Sj.
-
Step 2:
On receiving the message {yj, MSj,G, Tj} from Sj, 𝒜 computes RNj = yj XSj*, yj′ = RNj′ XSj*, zi′ = MG,Sj* RNj′ and MSj,G′ = h(zi′||XSj*||Tj), and sends {yj′, MSj,G′, Tj} to GWN, where RNj is a nonce selected by Sj and RNj′ is a nonce selected by 𝒜, respectively
-
Step 3:
GWN successfully checks Tj, computes RNj′ = yj′ XSj, zi′* = MG,Sj* RNj′, MSj,G′* = h(zi′*||XSj||Tj), and checks MSj,G′* = ? MSj,G′. Then, GWN computes MG,Ui′ = h(DIDi||MSj,G′|| MUi,G||XSj||TG′), wi′ = zi′* XSi, yj′ = RNj′ XSj, qj′ = XSj RNj′ sends {yi′, wi′, MG,Ui′, qj′, TG′} to Ui.
-
Step 4:
The smart card successfully checks TG′ and computes RNj′ = yj′ XSj, zi′* = wi′ XSi, MG,Sj′ = zi′* RNj′, MG,Ui′* = h(DIDi||MSj,G′*|| MUi,G||XSj||TG′), and checks MG,Ui′* = ? MG,Ui′. Then Ui computes XSj = qj′ RNj′ and the session key KS′ = f((DIDi||RNj′), XSj) shared with 𝒜. Sj computes the session key KS" = f((DIDi||RNj), XSj) shared with 𝒜.
2.2.4. Violation of Session Key Security
Moreover, the legitimate 𝒜 can derive each RNj by computing yj XSj* and calculate all used session keys KS = f((DIDi||RNj), XSj) of Ui and Sj since 𝒜 has XSj* and DIDi. Then, 𝒜 derives all transmitted secrets between Ui and Sj. Therefore, the scheme of Kim et al. violates session key security.
2.2.5. Failure to Privacy Protection of Users
In the scheme of Kim et al., Ui’s identity IDi is protected with GWN’s secret key K and hash function h(·), and is not revealed. However, the parameter HIDi = h(IDi||K) in the request message {DIDi, MUi,G, vi, Ti, HIDi} from Ui relies on Ui’s IDi and is constant. An adversary can then easily distinguish whether any two request messages are from the same user using HIDi. Thus, the scheme of Kim et al. fails to exhibit data unlinkability, and cannot realize privacy protection of users [17].
3. Proposed Authentication and Key Agreement Scheme Using Dynamic Identities for WSNs
This section presents a secure authentication and key agreement scheme based on the scheme of Kim et al. [16] for WSNs. The proposed scheme appends a dynamic identity for the user and eliminates constant parameters from the user’s request messages such that any two request messages are independent and indistinguishable. It also encrypts the communicating messages with the temporary secret keys rather than the constant secret keys of users and sensor nodes, and diminishes redundant variables. Additionally, the proposed scheme modifies sensor nodes’ secret keys such that a sensor node cannot derive other sensor nodes’ secret keys. Consequently, an adversary cannot discover the secret keys of users and sensor nodes, and thus used session keys and transmitted secrets. The proposed scheme also has registration, login, authentication & key agreement and password change phases. The password change phase is the same as that of the scheme of Kim et al., and therefore is not presented here.
3.1. Registration Phase
In the registration phase, Ui registers his/her identity and password to GWN. Then, GWN personalizes a smart card for Ui. Meanwhile, Sj keeps (SIDj, XSj*) in its storage before being deployed, where XSj* = h(SIDj||K):
-
Step 1:
Ui GWN: {IDi, HPWi}
Ui selects IDi, password pwi, a random number RNr, computes HPWi = h(pwi||RNr) and sends {IDi, HPWi} to GWN via a secure channel.
-
Step 2:
GWN Ui: Ui′s smartcard
GWN computes HIDi = h(IDi||K), XSi = h(HIDi||K), Ai = h(HPWi||XSi) HIDi, Bi = h(HPWi XSi), Ci = XSi h(IDs||HPWi) and personalizes the smartcard for Ui with the parameters: (IDs, h(·), Ai, Bi, Ci, TIDi). Then, GWN sends the smartcard to Ui via a secure channel. GWN also stores parameters (TIDi, TIDi°, HIDi) in its storage for Ui, where TIDi is the temporal identity for Ui’s next login and TIDi = RNG, RNG is a nonce, and TIDi°= "".
-
Step 3:
Ui computes XPWi = h(pwi) RNr and inserts XPWi into his/her smartcard.
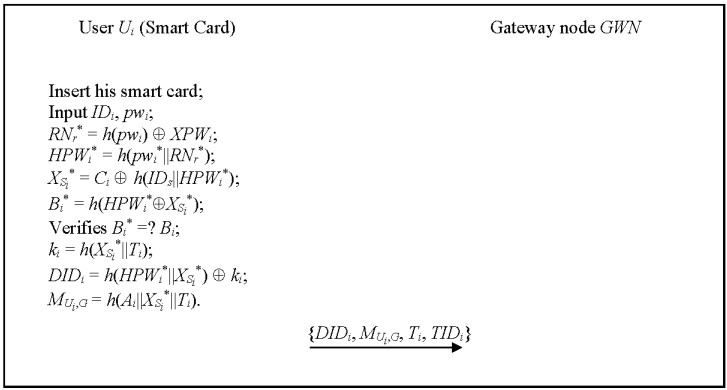
3.2. Login Phase
In this phase, user Ui inserts his/her smart card, inputs his/her identity and password, and sends the service request to GWN. Figure 2 illustrates the login phase, which works as follows.
-
Step 1:
inserts his/her smart card into a terminal and enters IDi* and pwi*.
-
Step 2:
The smartcard computes RNr* = h(pwi) XPWi, HPWi* = h(pwi*||RNr*), XSi* = Ci h(IDs||HPWi*), Bi* = h(HPWi* XSi*) and verifies Bi* = ? Bi. If unsuccessful, the smartcard aborts this request; otherwise, the smart card computes a temporary secret key ki = h(XSi*||Ti), DIDi = h(HPWi*||XSi*) ki, MUi,G = h(Ai||XSi*||Ti), where Ti is the current timestamp. Then the smartcard sends the authentication request {DIDi, MUi,G, Ti, TIDi} to GWN.
Figure 2.
The login phase of the proposed scheme for WSNs.
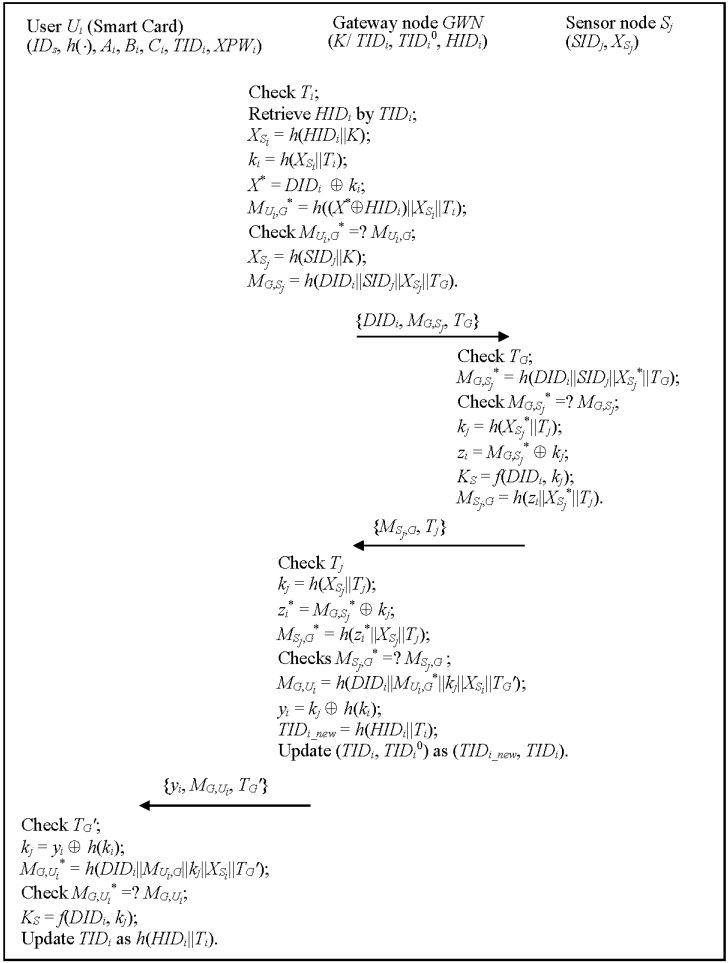
3.3. Authentication and Key Agreement Phase
This phase enables Ui, GWN and Sj to authenticate each other, and to establish a common session key of Ui and Sj. Figure 3 illustrates the authentication and key agreement phase, which works as follows:
Figure 3.
The authentication and key agreement phase of the proposed scheme for WSNs.
-
Step 1:
GWN → Sj: {DIDi, MG,Sj, TG}
GWN checks the validity of Ti, retrieves Ui,’s information HIDi by using TIDi. If TIDi is not found, then GWN retrieves HIDi by using TIDi°. If unsuccessful, GWN rejects this service request; otherwise, GWN computes XSi = h(HIDi||K), ki = h(XSi||Ti), X* = DIDi ki, MUi,G* = h((X* HIDi)||XSi||Ti) and checks MUi,G* = ? MUi,G. If successful, GWN computes XSj = h(SIDj||K), MG,Sj = h(DIDi||SIDj||XSj||TG) and sends {DIDi, MG,Sj, TG} to Sj, where Sj is the nearest sensor node for Ui and TG is current timestamp.
-
Step 2:
Sj → GWN: {MSj,G, Tj}
Sj checks the validity of TG, computes MG,Sj* = h(DIDi||SIDj||XSj*||TG) and checks MG,Sj* = ? MG,Sj. If successful, Sj computes a temporary secret key kj = h(XSj*||Tj), zi = MG,Sj* kj, KS = f(DIDi, kj) and MSj,G = h(zi||XSj*||Tj), and sends {MSj,G, Tj} to GWN, where Tj is current timestamp.
-
Step 3:
GWN → Ui: {yi, MG,Ui, TG′}
GWN checks the validity of Tj, computes kj = h(XSj||Tj), zi* = MG,Sj* kj, MSj,G* = h(zi*||XSj||Tj), and checks MSj,G* = ? MSj,G. If successful, GWN computes MG,Ui = h(DIDi||MUi,G*||kj||XSi||TG′), yi = kj h(ki), TIDi_new = h(HIDi||Ti), and sends{yi, MG,Ui, TG′} to Ui, where TG′ is current timestamp. At this time, GWN updates (TIDi, TIDi°) as (TIDi_new, TIDi).
-
Step 4:
The smartcard checks the validity of TG′, and computes kj = yi h(ki), MG,Ui* = h(DIDi||MUi,G||kj||XSi||TG′), and checks MG,Ui* = ? MG,Ui. If successful, Ui computes the session key KS = f(DIDi, kj). Then, Ui and Sj successfully realize mutual authentication and have a common session key KS. Similarly, Ui also updates TIDi as h(HIDi||Ti).
4. Security Analyses
This section analyzes the security of the proposed authentication and key agreement scheme. The benefits of the proposed scheme provide mutual authentication, session key security, user privacy protection, known-key security and resistance to privileged insider, impersonation and stolen verifier attacks. Since the proposed scheme is based on the scheme of Kim et al. [16], the analyses of the resistance to possible attacks, including replay attacks, parallel session attacks, privileged insider attacks and password guessing attacks, closely resemble those for the scheme of Kim et al., and so are not presented here.
The following descriptions show that the proposed scheme provides the indistinguishability in the Real-or-Random model [17,18,19].
4.1. Security Definitions
4.1.1. AKE Security (Session Key Security)
This definition defines that an adversary cannot effectively distinguish between two messages from a challenger. One message is computed by the real session key and the other one is computed by a random string via an unbiased coin c. The adversary selects one message and sends to the challenger. The challenger then decides to return the message computed by the real session key if c = 1 or computed by a random string if c = 0 by flipping an unbiased coin c. The adversary aims to correctly guess the value of the hidden bit c. The advantage that an adversary violates the indistinguishability of a scheme is denoted as Advake(𝒜), and is defined as:
| Advake(𝒜) = | 2Pr[E] − 1 | |
where E denotes the event that the adversary wins this game. The scheme is AKE-secure if Advake(𝒜) is negligible [17,18,19].
4.1.2. Mutual Authentication (MA) Security
In executing a scheme, the adversary 𝒜 violates mutual authentication if 𝒜 can successfully fake the authenticator MUi,G, MG,Sj, MSj,G or MG,Ui. The probability of this event is denoted by Advma(𝒜). The scheme is MA-secure if Advma(𝒜) is negligible [17,18,19].
The Difference Lemma [20] is made used within our sequence of games (SOG), which is described as follows:
Lemma 1.
(Difference Lemma). Let A, B and F be events defined in some probability distribution, and suppose that . Then
| Pr[A] − Pr[B] | ≤ Pr[F]
4.2. Session Key Security
Theorem 1.
The advantage that an adversary breaks the AKE security of the proposed scheme:
Advake ≤ 3/2l−1+ 4·Advsk where Advsk denotes the advantage that an adversary breaks the long-term secret key and l is a security parameter.
Proof:
The proof consists of a sequence of games starting at the game G0. Each game Gi defines the probability of the event Ei that the adversary wins this game. The first game is the real attack against the protocol and the terminal game G2 concludes that the adversary has a negligible advantage to break the AKE security of the proposed scheme. Assume that the challenger 𝒜1 attempts to breaks long-term secret keys (XSi and XSj), and the adversary 𝒜ake is constructed to break the session key security. Then 𝒜ake tries to distinguish the real session key from the random string. The challenger 𝒜1 sets up the used parameters, starts simulating the scheme and returns the real session key or a random string to 𝒜ake by flipping an unbiased coin . The adversary 𝒜ake outputs its guess bit c′ and wins if c′ = c.
Game G0: This game corresponds to the real attack. By definition, we have:
| Advake (𝒜ake) = |2Pr[E0]−1| | (1) |
Game G1: This game transforms game G0 into game G1 by replacing the long-term secret keys, XSi and XSj, with two random numbers. Thus, by using Lemma 1, we have:
| | Pr[E0] − Pr[E1] | ≤ 2·Advsk (𝒜1) | (2) |
Game G2: This game transforms game G1 into game G2 by replacing ki (= h(=XSi||Ti)) and kj (= h(XSj||Tj)) with two random numbers. Then, games G1 and G2 are indistinguishable except collisions of a hash function in G2. Thus, by using the birthday paradox and Lemma 1, we have:
| | Pr[E1] − Pr[E2] | ≤ 2×(1/2l) | (3) |
Game G3: This game transforms previous game except for replacing KS with a random number. Similarly, games G2 and G3 are indistinguishable except collisions of a hash function in G3, and thus we have:
| | Pr[E2] − Pr[E3] | ≤ 1/2l | (4) |
Therefore, the probability of the event that 𝒜1 outputs 1 when the response message is obtained by using the real session key is equal to the probability of the event that 𝒜ake correctly guesses the hidden bit c in game G2. Similarly, the probability of the event that 𝒜1 outputs 1 when the response message obtained by a random string is equal to the probability of the event that 𝒜ake correctly guesses the hidden bit c in game G3. All session keys are random and independent, and no information about c is revealed. Thus, we have:
| Pr[E3] = 1/2 | (5) |
Combining Equations (1)–(5), we have:
| Advake(𝒜ake) ≤ 3/2l−1 + 4·Advsk (𝒜1) |
Then the proof is concluded.
4.3. Mutual Authentication
Theorem 2.
Let Advma be the advantage in violating the mutual authentication of the proposed scheme. Then, Advma is negligible, and thus the proposed scheme provides mutual authentication.
Proof:
The proof also consists of a sequence of games. The first game G0 is the real attack against the proposed protocol and the terminal game G3 concludes that the adversary has a negligible advantage to break mutual authentication of the proposed protocol. Assume that Advsk denotes the advantage that an adversary breaks the long-term secret keys and l is a security parameter. The challenger 𝒜2 attempts to break long-term secret keys of the proposed scheme, and the adversary 𝒜ma is constructed to break mutual authentication security for the scheme. The adversary 𝒜ma wins this game if he/she successfully fakes the authenticator MUi,G, MG,Sj, MSj,G or MG,Ui.
Game G0: This game corresponds to the real attack. By definition, we have:
| Advma (𝒜ma)=| 2Pr[E0] – 1 | | (6) |
Game G1: This game transforms game G0 into game G1 by replacing XSi and XSj with two random numbers. Thus, by using Lemma 1, we have:
| | Pr[E0] − Pr[E1] | ≤ 2·Advsk (𝒜2) | (7) |
Game G2: This game transforms game G1 into game G2 by replacing ki and kj with two random numbers. Thus, by using the birthday paradox and Lemma 1, we have:
| | Pr[E1] − Pr[E2] | ≤ 2×(1/2l) | (8) |
Game G3: This game transforms previous game by replacing the authenticators with random numbers. Similarly, games G2 and G3 are indistinguishable except collisions of a hash function in G3, and thus we have:
| | Pr[E2] − Pr[E3] | ≤ 4×(1/2l) | (9) |
Therefore, the probability of the event that 𝒜2 outputs 1 when the authenticator is computed by using the real secret key is equal to the probability of the event that 𝒜ma correctly guesses the hidden bit c in game G2. Similarly, the probability of the event that 𝒜2 outputs 1 when the authenticator obtained by a random string is equal to the probability of the event that 𝒜ma correctly guesses the hidden bit c in game G3. Since no information on the authenticator is leaked to the adversary, we have:
| Pr[E3] = 1/2 | (10) |
Combining Equations (6)–(10), we have the advantage that the adversary violates the mutual authentication of the proposed scheme is:
| Advma(𝒜ma)≤ 4·Advsk(𝒜2)+ 3/2l−2 | (11) |
and thus is negligible.
4.4. Privacy Protection of Users
Theorem 3.
The proposed scheme provides privacy protection of users.
Proof:
The proposed scheme does not reveal the user’s real identity IDi; it replaces the constant temporal identity HIDi with a dynamic user identity TIDi, and eliminates constant parameters from the user’s request messages. Consequently, any two request messages are independent and indistinguishable. The proposed scheme thus exhibits user anonymity, unlinkability and data untrackability [21]. Accordingly, the proposed scheme provides users with privacy protection.
4.5. Known-Key Security
Theorem 4.
The proposed scheme provides privacy known-key security.
Proof:
Since the parameters DIDi and kj are independent among scheme executions, the session keys KS = f(DIDi, kj) generated in different runs are independent where DIDi = h(HPWi||XSi) h(XSi||Ti) and kj = h(XSj||Ti). Accordingly, the proposed scheme provides known-key security.
4.6. Resistance to Impersonation Attacks
Theorem 5.
The proposed scheme provides privacy known-key security.
Proof:
An adversary who tries to impersonate Ui fails to compute ki = h(XSi||Ti), DIDi = h(HPWi||XSi) ki, MUi,G = h(Ai||XSi||Ti), and fails to send out the correct request messages {DIDi, MUi,G, Ti, TIDi} in the login phase without correct IDi, pwi, XSi and (IDs, h(·), Ai, Bi, Ci, HPWi, TIDi) in Ui’s smart card, where RNr = h(pwi) XPWi, HPWi = h(pwi||RNr), and Ti is the current timestamp. A failed login is detected by GWN in the authentication and key agreement phase, and thus the proposed scheme withstands impersonation attacks.
4.7. Resistance to Stolen Verifier Attacks
Theorem 6.
The proposed scheme withstands stolen verifier attacks.
Proof:
In the proposed scheme, the GWN maintains (TIDi, TIDi0, HIDi) in the verifier table for each user Ui. An adversary who steals a GWN’s verifier table and copies (TIDi, TIDi0, HIDi) still fails to compute RNr = h(pwi) XPWi, HPWi = h(pwi||RNr), XSi = Ci h(IDs||HPWi), ki = h(XSi||Ti), DIDi = h(HPWi||XSi) ki and MUi,G = h(Ai||XSi||Ti) without the knowledge of user Ui’s (IDi, pwi) and (IDs, h(·), Ai, Bi, Ci, XPWi, TIDi) in the smartcard. The adversary fails to send the authentication request {DIDi, MUi,G, Ti, TIDi} to GWN, and a failure login is detected by GWN. Therefore, the enhanced scheme withstands stolen verifier attacks.
4.8. Resistance to Lost Smartcard Attacks
Theorem 7.
The proposed scheme withstands lost smart card attacks.
Proof:
An adversary who steals user Ui’s smartcard and copies the message (IDs, h(·), Ai, Bi, Ci, XPWi, TIDi) still fails to compute RNr = h(pwi) XPWi, HPWi = h(pwi||RNr), XSi = Ci h(IDs||HPWi), ki = h(XSi||Ti), DIDi = h(HPWi||XSi) ki and MUi,G = h(Ai||XSi||Ti), and fails to send out the correct authentication request {DIDi, MUi,G, Ti, TIDi} without the correct IDi and pwi. Consequently, a failed login is detected by GWN in the authentication and key agreement phase, and thus the enhanced scheme withstands lost smartcard attacks.
4.9. Resistance to Sensor Node Capture Attacks
Theorem 8.
The proposed scheme withstands sensor node capture attacks.
Proof:
The enhanced scheme eliminates the shared secret key xs of all sensor nodes and GWN in the WSN, and modifies the sensor node Sj’s secret key as XSj = h(SIDj||K). That is, each Sj does not require maintaining xs. Thus, an attacker 𝒜 who has captured Sj′ and obtained (SIDj′, XSj′) cannot derive other Sj’s secret key, and also cannot impersonate Ui, GWN or other Sj.
5. Performance Analyses and Functionality Comparisons
5.1. Performance Analyses
Table 2 and Table 3 compare the performance and the simulation time of the proposed scheme with Vaidya et al.’s scheme [15], Li et al.’s scheme [9] and Kim et al.’s scheme [16], where H denotes the execution time for a one-way hash function operation, and X denotes the execution time for an exclusive-or operation. Table 4 lists our simulation environment, including hardware/software specifications and used algorithms. The proposed scheme involves a user Ui, a sensor node Sj, and a gateway node GWN. The user Ui is simulated by using a personal computer, the sensor node Sj is simulated by using a mobile device and the gateway node GWN is simulated by using a powerful server, respectively.
Table 2.
The comparisons of related schemes and the proposed scheme.
Table 3.
The simulation comparisons of related schemes and the proposed scheme.
Table 4.
Simulation environment.
| Hardware/Software Specification | ||
|---|---|---|
| User Ui | Mainboard | ASUSTeK Computer INC. CM5571 |
| CPU | Intel Core 2 Quad Q8300 @ 2.50 GHz 2.50 GHz | |
| Memory | 4.00 GB Dual-Channel DDR3 @ 533 MHz | |
| OS | Windows 7 64-bit SP1 | |
| Sensor Node Sj | Mainboard | ASUSTeK Computer INC. UX303LN |
| CPU | Intel Core i3/i5/i7 4xxx @ 1.70 GHz | |
| Memory | 4.00 GB Single-Channel DDR3 @ 798 MHz | |
| OS | Windows 8.1 64-bit | |
| Gateway Node GWN | Mainboard | IBM 46W9191 |
| CPU | Intel Xeon E3 1231 v3 @ 3.40 GHz 3.40 GHz | |
| Memory | 8.00 GB Dual-Channel DDR3 @ 800 MHz | |
| OS | Windows Server 2008 R2 Standard 64-bit SP1 | |
| Used Programming Language and Algorithms | ||
| C/C++ | ||
| Hash function: SHA-1 | ||
The first comparison item in Table 2 lists the computational cost used in login and authentication-key agreement phases. Vaidya et al. [15] requires 15 hash function and 13 exclusive-or operations; Li et al. [9] requires 11 hash function and 5 exclusive-or operations; Kim et al. [16] requires 11 hash function and 5 exclusive-or operations, and the proposed scheme requires 25 hash function and 10 exclusive-or operations, respectively. The subsequent comparison item is uses random numbers. The proposed scheme requires three random numbers, which is less than that required by related schemes. The comparison item in Table 3 lists the simulation time used in login and authentication-key agreement phases. Although the proposed scheme requires more computations and spends much time in simulation than related schemes, it is still computationally simple and retains low energy consumption.
5.2. Functionality Comparisons
Table 5 compares the functionality of the proposed scheme with that of comparable schemes. The comparison items include resisting possible attacks and providing security requirements. Kim et al.’s improved scheme [16] is based on Vaidya et al.’s scheme [15], and therefore has the similar security problems. Accordingly, both Vaidya et al. [15] and Kim et al. schemes [16] fail to withstand possible attacks, including impersonation, lost smartcard and man-in-the-middle attacks. They never provide session key security and protect user privacy. Additionally, Li et al.’s scheme [9] fails to withstand impersonation and stolen-verifier attacks, and fail to provide privacy protection. The proposed scheme appends a dynamic identity, eliminates redundant parameters, encrypts the communicating messages with the temporary secret keys, and modifies sensor nodes’ secret keys such that a sensor node cannot derive other sensor nodes’ secret keys, and thus withstands possible attacks and provides privacy protection. Therefore, the proposed scheme provides more functionalities and security properties than other examined schemes, and retains low computational cost.
Table 5.
The comparisons of the related schemes and the proposed scheme.
| Vaidya et al. [15] | Li et al. [9] | Kim et al. [16] | Our Scheme | |
|---|---|---|---|---|
| Resisting replay attacks | Yes | Yes | Yes | Yes |
| Resisting impersonation attacks | No | No | No | Yes |
| Resisting gateway node by passing attacks | No | Yes | Yes | Yes |
| Resisting parallel session attacks | Yes | Yes | Yes | Yes |
| Resisting password guessing attacks | Yes | Yes | Yes | Yes |
| Resisting sensor node capture attacks | No | Yes | Yes | Yes |
| Resisting man-in-the-middle attacks | No | Yes | No | Yes |
| Resisting lost smartcard attacks | No | Yes | No | Yes |
| Resisting privileged-insider attacks | Yes | Yes | Yes | Yes |
| Resisting stolen-verifier attacks | Yes | No | Yes | Yes |
| Providing session key security | No | Yes | No | Yes |
| Providing privacy protection of users | No | No | No | Yes |
6. Conclusions
This study analyzes the weaknesses of the two-factor authentication and key agreement scheme of Kim et al., which include suffering from impersonation attacks, lost smartcard attacks and man-in-the-middle attacks, violation of session key security, and failure to protect user privacy. An efficient and secure authentication and key agreement scheme for WSNs based on the scheme of Kim et al. is proposed. The proposed scheme adopts dynamic identities rather than the constant temporary identity and conceals the user’s constant parameters in login requests, encrypts the communicating messages with temporary secret keys rather than the long-life secret keys of users and sensor nodes, and diminishes redundant variables. Our scheme solves the weaknesses in previous approaches; it provides increased functionality and security properties, making it very suitable for WSNs.
Acknowledgments
This research was supported by Ministry of Science and Technology under the grants MOST 104-2221-E-320-002. Ted Knoy is appreciated for his editorial assistance.
Author Contributions
In this paper, I.P. Chang found the problems in the related schemes for WSNs, collected related data about WSNs, and helped develop the improved scheme. T.F. Lee analyzed the weaknesses of the related schemes for WSNs, developed the improved scheme, provided security proofs and wrote the manuscript. T.H. Lin contributed to security analyses and questions and the discussion. C.M. Liu contributed to the performance analyses and English language correction.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Das M.L. Two-factor user authentication scheme in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009;8:1086–1090. doi: 10.1109/TWC.2008.080128. [DOI] [Google Scholar]
- 2.Delgado-Mohatar O., Fuster-Sabater A., Sierra J.M. A light-weight authentication scheme for wireless sensor networks. Ad Hoc Netw. 2011;9:727–735. doi: 10.1016/j.adhoc.2010.08.020. [DOI] [Google Scholar]
- 3.Li Z., Gong G. Computationally efficient mutual entity authentication in wireless sensor networks. Ad Hoc Netw. 2011;9:204–215. doi: 10.1016/j.adhoc.2010.07.007. [DOI] [Google Scholar]
- 4.Li C.T., Hwang M.S. A lightweight anonymous routing protocol without public key en/decryptions for wireless ad hoc networks. Inform. Sci. 2011;181:5333–5347. doi: 10.1016/j.ins.2011.07.014. [DOI] [Google Scholar]
- 5.Mi Q., Stankovic J.A., Stoleru R. Practical and secure localization and key distribution for wireless sensor networks. Ad Hoc Netw. 2012;10:946–961. doi: 10.1016/j.adhoc.2011.12.008. [DOI] [Google Scholar]
- 6.Han K., Kim K., Choi W., Choi H.H., Seo J., Shon T. Efficient authenticated key agreement protocols for dynamic wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2012;14:251–269. [Google Scholar]
- 7.Poornima A.S., Amberker B.B. Secure end-to-end data aggregation (seeda) protocols for wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2013;17:193–219. [Google Scholar]
- 8.Xue K., Ma C., Hong P., Ding R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013;36:316–323. doi: 10.1016/j.jnca.2012.05.010. [DOI] [Google Scholar]
- 9.Li C.T., Weng C.Y., Lee C.C. An advanced temporal credential-based security scheme with mutual authentication and key agreement for wireless sensor networks. Sensors. 2013;13:9589–9603. doi: 10.3390/s130809589. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 10.He D., Gao Y., Chan S., Chen C., Bu J. An enhanced two-factor user authentication scheme in wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2010;10:361–371. [Google Scholar]
- 11.Chen T.H., Shih W.K. A robust mutual authentication protocol for wireless sensor networks. ETRI J. 2010;32:704–712. doi: 10.4218/etrij.10.1510.0134. [DOI] [Google Scholar]
- 12.Li C.T., Lee C.C., Wang L.J., Liu C.J. A secure billing service with two-factor user authentication in wireless sensor networks. Int. J. Innov. Comput. Inform. Contr. 2011;7:4821–4831. [Google Scholar]
- 13.Li C.T., Lee C.C., Lee C.W. An improved two-factor user authentication protocol for wireless sensor networks using elliptic curve cryptography. Sens. Lett. 2013;11:958–965. doi: 10.1166/sl.2013.2669. [DOI] [Google Scholar]
- 14.Yeh H.L., Chen T.H., Liu P.C., Kim T.H., Wei H.W. A secure authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors. 2011;11:4767–4779. doi: 10.3390/s110504767. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 15.Vaidya B., Makrakis D., Mouftah H. Two-factor mutual authentication with key agreement in wireless sensor networks. Secur. Commun. Netw. 2012 doi: 10.1002/sec.517. [DOI] [Google Scholar]
- 16.Kim J., Lee D., Jeon W., Lee Y., Won D. Security analysis and improvements of two-factor mutual authentication with key agreement in wireless sensor networks. Sensors. 2014;14:6443–6462. doi: 10.3390/s140406443. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 17.Bellare M., Pointcheval D., Rogaway P. Authenticated key exchange secure against dictionary attacks. Proc. Adv. Cryptol. Eurocrypt. 2000;1807:122–138. [Google Scholar]
- 18.Boyko V., MacKenzie P., Patel S. Provably secure password-based authenticated key exchange protocols using Diffie-Hellman. Proc. Adv. Cryptol. Eurocrypt. 2000;1807:156–171. [Google Scholar]
- 19.Lee T.F., Hwang T. Provably secure and efficient authentication techniques for the global mobility network. J. Syst. Soft. 2011;84:1717–1725. doi: 10.1016/j.jss.2011.05.006. [DOI] [Google Scholar]
- 20.Shoup V. Sequences of Games: A Tool for Taming Complexity in Security Proofs, Manuscript. [(accessed on 18 January 2015)]. Available online: http:// www.shoup.net.
- 21.Lee T.F. User authentication scheme with anonymity, unlinkability and untrackability for global mobility networks. Secur. Commun. Netw. 2013;6:1404–1413. doi: 10.1002/sec.734. [DOI] [Google Scholar]