Abstract
In this paper, we proposed a new image encryption algorithm based on parameter-varied logistic chaotic map and dynamical algorithm. The parameter-varied logistic map can cure the weaknesses of logistic map and resist the phase space reconstruction attack. We use the parameter-varied logistic map to shuffle the plain image, and then use a dynamical algorithm to encrypt the image. We carry out several experiments, including Histogram analysis, information entropy analysis, sensitivity analysis, key space analysis, correlation analysis and computational complexity to evaluate its performances. The experiment results show that this algorithm is with high security and can be competitive for image encryption.
Keywords: Chaos, Image encryption, Dynamical algorithm, Parameter-varied logistic map
Background
With the rapid development in internet technology and multimedia technology, multimedia communication has become more and more important. Therefore, image encryption has become an increasingly serious issue and urgently needed (Ye and Wong 2013). However, traditional encryption algorithms, such as RSA, DES and IDEA, are not suitable for image encryption due to image’s intrinsic properties such as bulky data capacity, strong redundancy and strong correlations among adjacent pixels (Wang et al. 2012; Chen et al. 2013; Coppersmith 1994).
Chaotic system has many important properties, such as unpredictability, similar randomness, aperiodicity, sensitive dependence on initial conditions and parameters, these properties make chaotic systems become popular in image encryption (Huang 2012; Wang and Guo 2014; Zhang and Zhao 2014; Zhang and Liu 2011; Hua et al. 2015; Tong et al. 2015; Hussain and Shah 2013). Among all the chaotic encryption image algorithm, the low-dimensional chaotic map are always used for its easily implement, such as logistic map. However, some common weaknesses of the logistic map, including relatively small key space and uneven distribution of sequences, et al, bring some security risks for encryption. On the other hand, for a deterministic chaotic system, the chaos behaviors can be discerned by using some methods in chaos theory. Once we find some information about the chaotic system, we can use such information to help us finding the secret key. In many chaotic ciphers, such as Kanso and Smaoui (2009), Zhou and Liao (2012), Sun et al. (2010), Pareek et al. (2005), Wong et al. (2003), Liu and Wang (2010), Wang et al. (2012), Patidar et al. (2010), Gonzalez and Hernandez (2013), the ciphertext directly depends on the chaotic orbit of a single chaotic system, the orbit sequence comes to be stationary, so the extraction of such information may be possible by using some chaos theory methods such as phase space reconstruction. In Short (1994), short use the phase space reconstruction method, has successfully attacked almost all the low-dimensional chaotic systems. Wang and Luan (2013) propose a three-dimensional coupled logistic maps to overcome the weaknesses of logistic map, however, the system is still deterministic, and is still under the risk of being attacked by phase space reconstruction.
As we know, varying the parameters can disrupt the phase space of a chaotic system, and improve the security to resist the phase space reconstruction attack. Some varying parameter techniques have been proposed, e.g., Murillo-Escobar et al. (2015) use 32 hexadecimal digits to vary the parameter and initial value of logistic map, and the proposed system can avoid the small key space of low dimensional chaotic systems. This varying technique is given by 32 fixed hexadecimal digits, which is not that secure. Using a prediction technique based on wavelet neural network and multiwavelets neural network can predict the parameter-varying chaotic system whose parameters are varying in a simple way (Xiao and Gao 2006). Wang et al. (2009) use the generated sequences by logistic map to control three kinds of typical two-dimensional chaotic maps, but do not show the performances of their parameter-varied chaotic maps.
Therefore, in order to improve the weaknesses of logistic map and resist the phase space reconstruction attack, we propose an image encryption algorithm based on logistic map with varying parameter. The varying technique is based on the zero-mean logistic map, which can make the parameter varying in a random-like way. We show that the parameter-varied logistic map can cure the weaknesses of logistic map and is capable to resist phase space reconstruction. Furthermore, we use a dynamical algorithm in our encryption algorithm. Our encryption algorithm is related to the plaintext, which can resist known and chosen-plaintext attacks. The experimental results show that the proposed algorithm is with high security, and can be competitive to other proposed algorithms.
The rest of this paper is organized as follows. In “Shuffling algorithm” section, a shuffling algorithm based on parameter-varied logistic system is described. We show that the parameter-varied logistic system can cure the common weaknesses and is capable to resist phase space reconstruction. “Dynamical encryption algorithm” section introduce a dynamical algorithm for the image encryption. The experimental results, analysis and comparison are shown in “Experimental analysis” section. Finally, “Conclusion” section concludes the paper.
Shuffling algorithm
In this section, we propose a shuffling method based on parameter-varied chaotic map. Perhaps, the one-dimensional maps are the simplest mathematical objects to display chaotic behavior (Lasota and Mackey 1994). The logistic maps are one kind of one-dimensional maps, which were described in May (1976) and have already been widely used in image encryption
| 1 |
here, a is the parameter of logistic map, xi = f(i)(x0) ∈ I, i = 0, 1, 2,… and f: I → I, where I denotes an interval. For 3.5699 < a ≤ 4, Eq. (1) turns to be chaotic. Using this function, we can obtain a real-valued sequence by iteration of an initial value x0. Since some researches show that the sequences generated by logistic map are not secure with some weaknesses (Wang and Luan 2013), including relatively small key space, an uneven distribution and easily be attacked by phase space reconstruction, therefore, we use the following parameter-varying logistic map in our algorithm.
| 2 |
here, ak is the varied parameter, M is the cardinality of the parameter set. We use the following zero-mean logistic map to vary the parameter ak
| 3 |
Divide the interval [−1, 1] into M sub-intervals τi, i = 0, 1, …, M − 1. Denote τi = [ti, ti+1), i = 0, 1, …, M − 2, and τM−1 = [tM−1, tM], where
| 4 |
Then, α = {τ0, τ1, …, τM−1} is a finite measurable partition of I. Denote a correspondence S: I → {0, 1, 2, …, M − 1} from the set I to the set {0, 1, 2, …, M − 1}. For any uk, define
| 5 |
here s(uk) is the symbol representation of the real number uk according to the partition α. Then, the generated integer sequence is denoted as {sk} and can be proved to be uniformly distributed in set {0, 1,…, M - 1} (Hu et al. 2004). Let the parameter set be {c1, c2,…, cM}, we use the sequence {sk} to vary the parameter a as
| 6 |
Then, the parameter ak of Eq. (2) is varying chaotic in the set {c1, c2,…, cM}. Let n be the steps of iteration with each parameter ak, we can generate the chaotic binary sequences by using the following algorithm.
| 7 |
Figure 1 shows the main frame of our pseudorandom bit generator. As we seen, the number M of different values of the parameter and the iteration step n for each parameter are two important parameters in our parameter-varied logistic map. Studies show that the logistic map can be reconstructed with delay time 1 and embedding dimension 3 (Han et al. 2015). For each parameter, if we don’t generate enough data, the reconstruction will fail. Therefore, we have that n < 3 is more suitable. In this paper, we choose n = 1, which can be regarded as a well-known random logistic map. Obviously, the larger the number M is, the more kinds of iterative rule has. However, it is impossible to choose M to be infinite. In order to determine the value M, we use approximate entropy (ApEn) to evaluate the complexity of the generated sequences. Before this experiment, we first calculate the ApEns of sequences generated by different parameter ak in Fig. 2, which indicates that the generated sequence has approximately the same complexity with different parameter. The ApEns with different M is shown in Fig. 3. From Fig. 3 we have that, when M is close to 9, the complexity approximately remains the same. As the complexity has almost no relation to the value of parameter, thus, is only influenced by the number of different parameters. Therefore, in this paper, we choose M = 9.
Fig. 1.
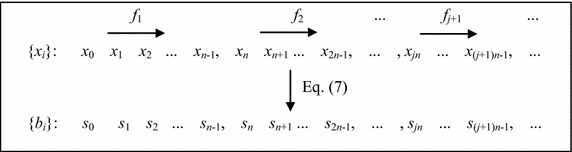
The output of logistic map with varying parameter
Fig. 2.
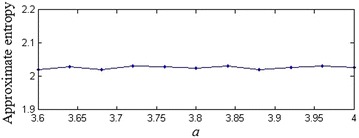
The ApEns of logistic map with different parameters
Fig. 3.
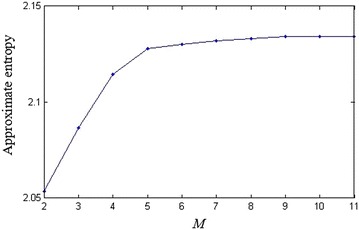
The ApEns of logistic map with different M
Next, we show that our logistic map with varying parameter can improve the weaknesses of logistic map. Firstly, the initial values x0, u0 and nine different parameters a1,…, a9 can be selected as the secret keys, which has greatly improved the key space of logistic map. Then, we have that the distribution of the generated sequences of our logistic map with varying parameter is uniform. We take x0 = 0.1, u0 = 0.2 and ak = 3.9 + 0.01*k, k = 1, 2,…, 9 as an example, the distribution of the generated sequence is shown in Fig. 4. Furthermore, we would show that our chaotic map can resist the phase space reconstruction. There are two key parameters in the phase space reconstruction, delay time and embedding dimension. By using auto-correlation function and false neighbor method, we have the optimal delay time be 1 and the embedding dimension be 3. We use use these two parameters to reconstruct the phase space in Fig. 5. From Fig. 5 we have that the reconstructed phase space has a significant structure of logistic map, while for the logistic map with varying parameter, the reconstructed phase space is disordered with no significant structure. Thus, the logistic map with varying parameter can resist the phase space reconstruction. Moreover, for other delay time and embedding dimension, the phase space is still disordered with no significant structure, which we do not repeat it here. Finally, we discuss the stable and unstable manifolds proposed in (Ragulskis and Navickas 2011) of our logistic map with varying parameter. For the logistic map, (Ragulskis and Navickas 2011) shows that the misplacement of the initial condition could potentially lead to the non-asymptotic convergence to a finite length periodic orbit, which makes the logistic sequence weak to be used in encryption. As (Ragulskis and Navickas 2011) shown, the initial conditions leading to the period solution in different forward iterations with different parameters are all different. Thus, our logistic map with varying parameter can naturally overcome such weakness. If the value of xi falls into the set which will lead to a period solution after several iterations with fixed parameter a, the generated sequence will jump out from the period solution because of the varying of parameter a, as well as the initial conditions leading to the period solution with different parameters are different.
Fig. 4.
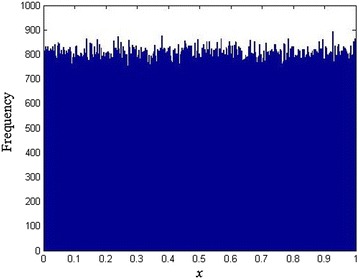
The distribution of the generated sequence
Fig. 5.

Reconstructed phase space of (a) logistic map (b) logistic map with varying parameter
Now we can introduce the shuffling algorithm. Let the size of the gray image g is p × q, and g(x, y) is the value of pixel at the xth row and yth column of the plain image. Reshape the plain image into one-dimensional array g(i), i = 1, 2, …, p × q. By using the binary sequence {bi}, we can shuffle the image.
Set L, R, Z be three empty arrays. Begin with i = 1, add 1 every time, and end with i = p × q. If si = 1, g(i) is put into array L in sequence. If bi = 0, g(i) is put into array R in sequence. Merge L and R into the array Z. If round T is odd, put L in front of R, else, put R in front of L. Finally, change the array Z into two-dimensional matrix G with p × q. Then the image G is the shuffled image. This method is first proposed in (Wang and Guo 2014).
Dynamical encryption algorithm
We use the following dynamical algorithm to encrypt the shuffled image G. The steps are
- Initialization: Denote the initial code book as follow.
here, B0(i) = bi(0), and {bi(0)} is an arbitrary permutation from 1 to 2N.8 -
Code transformation: Consider the array Z(i), change Z(i) into binary representation, Z(i) = (Zi1Zi2…ZiN)2. Denote qi = 2α (α = Zi1Zi2Zi3), and wi = 8*β (β = Zi4Zi5…ZiN). Use the following two algorithms R(·) and C(·) to transform the code book.
9 10 Then Bi+1 = Bi(C(w)R(q))−1.
Search the code book: For any driven element Z(i), we have k(i) = bZ(i)(i);
Stop command: If i ≠ NULL, then i = i + 1, back to step 2); Otherwise, stop the algorithm.
Figure 6 shows the main frame of our dynamic algorithm.
Fig. 6.
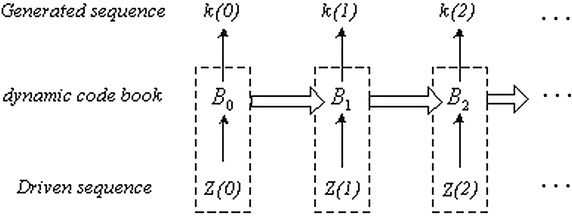
The main frame of our dynamic algorithm
The shuffled array {Z(i)} is used as the driven sequence. Change the array {k(i)} into two-dimensional matrix G’ by sequential scanning. The image G’ is the ciphered image. In this encryption algorithm, the initial values x0 and u0, different parameters a1,…, a9, and the initial code book can be selected as the secret keys. Both shuffling and dynamical encryption algorithm are reversible, thus, the decryption algorithm is just the inverse process of the encryption algorithm with using the same secret keys.
Experimental analysis
In our experiments, we select the gray-scale image “Lena.bmp” sized 256 × 256 as the plain image. Choose key parameters ak = {3.991, 3.992, 3.993, 3.994, 3.995, 3.996, 3.997, 3.998, 3.999}, T = 1, and the initial code book as
Figure 7 shows the encryption effect of each step in the proposed method. Furthermore, we use several security tests to show the good performances of our algorithm.
Fig. 7.
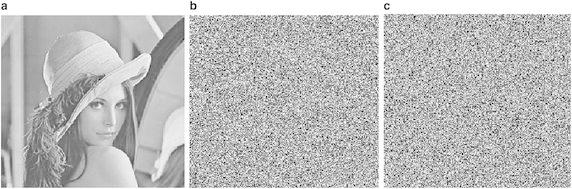
a Plain image, b Shuffled image when T = 2; c Ciphered image
Histogram of the image
The distribution of the ciphered image is a major concern. Here, we use the histogram to show the distribution of the plain image and the cipher image. From Fig. 8 we know that the proposed scheme results in very flat distributions of ciphered images, which can resist cipher-only attack.
Fig. 8.

Histogram of the images a Plain image, b Ciphered image
Information entropy analysis
Information entropy is the most significant measure to disorder, or unpredictability. The information entropy can be calculated as
here, M is the total number if symbols, and p(mi) is the probability of symbol mi. For a random image with 256 gray levels, M = 256, the entropy should ideally be 8.
The entropies of plain image and ciphered image are calculated. The results are shown in Table 1. From Table 1 we know that the entropies of the ciphered image produced by our algorithm are very close to the value of 8, which means that the ciphered images are close to a random source, and performs better than the algorithms in Wang and Guo (2014), Zhou and Liao (2012) and Sun et al. (2010).
Table 1.
Information entropy of the ciphered images
Sensitivity analysis
In order to resist differential analysis, the cipher text should be sensitive to both plain text and secret key.
Plaintext sensitivity
The Number of Pixels Change Rate (NPCR) and Unified Average Changing Intensity (UACI) are commonly used to evaluate the sensitivity to plain text. For two images x = {x1, x2, …, xn} and y = {y1, y2, …, yn}, the NPCR and UACI are defined as follows
here, D(xi, yi) = 0 if xi = yi and D(xi, yi) = 1 if xi ≠ yi. For the gray image, the ideal value of NPCR and UACI are 0.9961 and 0.3346, respectively.
We randomly change only 1 bit in the original plain image, and use the same secret key to encrypt the modified image and the original image. Then we calculate their NPCR and UACI values. The results are shown in Table 2.
Table 2.
NPCR and UACI when T takes different values
| Round T | NPCR | UACI |
|---|---|---|
| 1 | 0.9949 | 0.3156 |
| 2 | 0.9971 | 0.3398 |
| 3 | 0.9963 | 0.3371 |
From Table 2 we find that both the NPCR and UACI value are close to the ideal value when shuffling round T > 1. This means that the proposed scheme can effectively resist the differential attack and chosen-plaintext attack.
Key sensitivity
We test the sensitivity to secret key using one of the keys that is a little different from the original one. As we shown, the initial values x0 and u0, different parameters a1,…, a9, and the initial code book can be used as the secret key. We decrypt the encrypted image with x0 be different with 10−14, the decrypted image is shown in Fig. 9a. The decrypted image with u0 and a1 be different with 10−14 is shown in Fig. 9b, c, respectively. Furthermore, randomly exchange two codes in the initial code book, the decrypted image is shown in Fig. 9d. From Fig. 9 we can see that all the decrypted images can not be recognized, which indicates that the secret keys are highly sensitive.
Fig. 9.

Key sensitivity analysis. a decrypted image with x 0 be different with 10−14 b decrypted image with u 0 be different with 10−14 c decrypted image with a 1 be different with 10−14 d decrypted image by randomly exchanging two codes in the initial code book
Key space
The key space should be large enough to withstand attacks. In our proposed encryption algorithm, the initial values x0, u0, the varied parameters ak and the initial code book can be selected as secret keys. Let the largest precision be 10−14, the key space is about
On the other hand, the experimental results show that our scheme is highly sensitive to the secret key. Therefore, The key space of our algorithm is much larger than 2128, and is also larger than 2160 of (Wang and Guo 2014) and 2140 of (Tong et al. 2015), under the same precision, which concludes that our algorithm can sufficiently resist all kinds of brute-force attacks.
Correlation analysis
A good image encryption algorithm should remove this strong correlation between adjacent pixels. The correlation property can be quantified by means of correlation coefficients as
where
xi and yi are two adjacent pixels, n is the total number of adjacent pixel pairs (xi, yi). Table 3 gives the correlation coefficients of plain image and encrypted image. It is clear that all the correlation coefficients of encrypted images are close to zero, which means that our proposed algorithm can effectively remove the correlations among the adjacent pixels of the plain image, and can resist statistical attacks. Also, our algorithm performs better than the algorithms in Wang and Guo (2014), Hua et al. (2015) and Tong et al. (2015) in this sense.
Table 3.
Correlation coefficients of the plain and ciphered images
| Images | Horizontal | Vertical | Diagonal |
|---|---|---|---|
| Plain image | 0.98496 | 0.97179 | 0.96853 |
| Encrypt with T = 1 | 0.0088 | 0.0083 | 0.0121 |
| Encrypt with T = 2 | 0.0053 | 0.0040 | 0.0062 |
| Encrypt with T = 3 | 0.0021 | 0.0046 | 0.0033 |
| Ref. (Wang and Guo 2014) | 0.0063 | 0.0063 | 0.0069 |
| Ref. (Hua et al. 2015) | 0.0024 | −0.0086 | 0.0402 |
| Ref. (Tong et al. 2015) | 0.0038 | 0.0058 | 0.0133 |
Computational complexity
Here, we compare the computational complexity of our algorithm with the traditional DES and AES algorithms. All the algorithms are experiment by Matlab R2014a on the computer with 3.6 GHz CPU and 8 GB memory. The test results are shown in Table 4. From Table 4 we can see that the time of our algorithm with T = 1 and 2 are both less than the DES and AES algorithms, and is quite acceptable for image encryption. Certainly, the larger the T is, the more the time needed, and more secure the algorithm is. Therefore, users can choose a suitable T for their different security demand.
Table 4.
Encryption speed of each scheme
| Different algorithms | Encryption time (s) |
|---|---|
| Our algorithm with T = 1 | 0.05944 |
| Our algorithm with T = 2 | 0.06569 |
| DES | 0.59784 |
| AES | 0.11297 |
Conclusions
In this paper, we propose a new image encryption algorithm based on parameter-varied chaotic map and dynamical algorithm. The varied parameters are controlled by zero-mean logistic map and hopping in the given parameter set. We show that the proposed logistic map can overcome the common weaknesses of and is capable to resist phase space reconstruction. We carry out many experiments, including Histogram analysis, information entropy analysis, sensitivity analysis, key space analysis, correlation analysis and computational complexity, to show the security and performance of the proposed image encryption scheme. The experimental results show that our algorithm is with high security, and can be competitive with some other proposed image encryption algorithms.
Authors’ contributions
Lingfeng Liu propose this idea and write this paper, Suoxia Miao do the numerical experiments. Both authors read and approval the final manuscript.
Competing interests
The authors declare that they have no competing interests.
Contributor Information
Lingfeng Liu, Email: vatanoilcy@163.com.
Suoxia Miao, Email: miaosuoxia1215@163.com.
References
- Chen CS, Wang T, Kou YZ, Chen XC, Li X. Improvement of trace-driven I-Cache timing attack on the RSA algorithm. J Syst Softw. 2013;86:100–107. doi: 10.1016/j.jss.2012.07.020. [DOI] [Google Scholar]
- Coppersmith D. The data encryption standard (DES) and its strength against attacks. IBM J Res Dev. 1994;38:243–250. doi: 10.1147/rd.383.0243. [DOI] [Google Scholar]
- Gonzalez EI, Hernandez CC. Double hyperchaotic encryption for security in biometric systems. Nonlinear Dyn Syst Theory. 2013;13:55–68. [Google Scholar]
- Han YJ, Li TF, Yang XQ. Short-term wind power prediction based on logistic mapping neural network of phase space reconstruction. Exp Technol Manag. 2015;32:40–45. [Google Scholar]
- Hu HP, Liu SH, Wang ZX, Wu XG. A chaotic poly phase pseudorandom sequence. Math Phys. 2004;24:251–256. [Google Scholar]
- Hua ZY, Zhou YC, Pun CM, Philip Chen CL. 2D Sine logistic modulation map for image encryption. Inf Sci. 2015;297:80–94. doi: 10.1016/j.ins.2014.11.018. [DOI] [Google Scholar]
- Huang XL. Image encryption algorithm using chaotic chebyshev generator. Nonlinear Dyn. 2012;67:2411–2417. doi: 10.1007/s11071-011-0155-7. [DOI] [Google Scholar]
- Hussain I, Shah T. Application of S-box and chaotic map for image encryption. Math Comput Model. 2013;57:2576–2579. doi: 10.1016/j.mcm.2013.01.009. [DOI] [Google Scholar]
- Kanso A, Smaoui N. Logistic chaotic maps for binary numbers generations. Chaos Solitons Fractals. 2009;40:2557–2568. doi: 10.1016/j.chaos.2007.10.049. [DOI] [Google Scholar]
- Lasota A, Mackey MC. Chaos, fractals, and noise. New York: Springer; 1994. [Google Scholar]
- Liu HJ, Wang XY. Color image encryption based on one-time keys and robust chaotic maps. Comput Math Appl. 2010;59:3320–3327. doi: 10.1016/j.camwa.2010.03.017. [DOI] [Google Scholar]
- May RM. Simple mathematical models with very complicated dynamics. Nature. 1976;261:459–467. doi: 10.1038/261459a0. [DOI] [PubMed] [Google Scholar]
- Murillo-Escobar MA, Hernandez CC, Perz FA, Gutierrez RML, Acosta Del Campo OR. A RGB image encryption algorithm based on total plain image characteristics and chaos. Signal Process. 2015;109:119–131. doi: 10.1016/j.sigpro.2014.10.033. [DOI] [Google Scholar]
- Pareek NK, Patidar V, Sud KK. Cryptography using multiple one-dimensional chaotic maps. Commun Nonlinear Sci Numer Simul. 2005;10:715–723. doi: 10.1016/j.cnsns.2004.03.006. [DOI] [Google Scholar]
- Patidar V, Pareek NK, Purohit G, Sud KK. Modified substitution-diffusion image cipher using chaotic standard and logistic maps. Commun Nonlinear Sci Numer Simul. 2010;15:2755–2765. doi: 10.1016/j.cnsns.2009.11.010. [DOI] [Google Scholar]
- Ragulskis M, Navickas Z. The rank of a sequence as an indicator of chaos in discret nonlinear dynamical systems. Commun Nonlinear Sci Numer Simul. 2011;16:2894–2906. doi: 10.1016/j.cnsns.2010.10.008. [DOI] [Google Scholar]
- Short KM. Steps toward unmasking secure communications. Int J Bifurc Chaos. 1994;4:959–977. doi: 10.1142/S021812749400068X. [DOI] [Google Scholar]
- Sun F, Lu Z, Liu S. A new cryptosystem based on spatial chaotic system. Opt Commun. 2010;283:2066–2073. doi: 10.1016/j.optcom.2010.01.028. [DOI] [Google Scholar]
- Tong XG, Wang Z, Zhang M, Liu Y, Xu H, Ma J. An image encryption algorithm based on the perturbed high-dimensional chaotic map. Nonlinear Dyn. 2015;80:1493–1508. doi: 10.1007/s11071-015-1957-9. [DOI] [Google Scholar]
- Wang XY, Guo K. A new image alternate encryption algorithm based on chaotic map. Nonlinear Dyn. 2014;76:1943–1950. doi: 10.1007/s11071-014-1259-7. [DOI] [Google Scholar]
- Wang XY, Luan DP. A novel image encryption algorithm using chaos and reversible cellular automata. Commun Nonlinear Sci Numer Simul. 2013;18:3075–3085. doi: 10.1016/j.cnsns.2013.04.008. [DOI] [Google Scholar]
- Wang Y, Wong KK, Liao XF, Xiang T, Chen GR. A chaos-based image encryption algorithm with variable control parameters. Chaos Solitons Fractals. 2009;41:1773–1783. doi: 10.1016/j.chaos.2008.07.031. [DOI] [Google Scholar]
- Wang X, Teng L, Qin X. A novel color image encryption algorithm based on chaos. Signal Process. 2012;93:1101–1108. doi: 10.1016/j.sigpro.2011.10.023. [DOI] [Google Scholar]
- Wang XY, Teng L, Qin X. A novel colour image encryption algorithm based on chaos. Signal Process. 2012;92:1101–1108. doi: 10.1016/j.sigpro.2011.10.023. [DOI] [Google Scholar]
- Wong KW, Ho SW, Yung CK. A chaotic cryptography scheme for generating short ciphertext. Phys Lett A. 2003;310:67–73. doi: 10.1016/S0375-9601(03)00259-7. [DOI] [Google Scholar]
- Xiao F, Gao XP. An approach for short-term prediction on time series from parameter-varying systems. J Softw. 2006;17:1042–1050. doi: 10.1360/jos171042. [DOI] [Google Scholar]
- Ye G, Wong KW. An image encryption scheme based on time-delay and hyperchaotic system. Nonlinear Dyn. 2013;71:259–267. doi: 10.1007/s11071-012-0658-x. [DOI] [Google Scholar]
- Zhang G, Liu Q. A novel image encryption method based on total shuffling scheme. Opt Commun. 2011;284:2775–2780. doi: 10.1016/j.optcom.2011.02.039. [DOI] [Google Scholar]
- Zhang XP, Zhao ZM. Chaos-based image encryption with total shuffling and bidirectional diffusion. Nonlinear Dyn. 2014;75:319–330. doi: 10.1007/s11071-013-1068-4. [DOI] [Google Scholar]
- Zhou Q, Liao X. Collision-based flexible image encryption algorithm. J Syst Softw. 2012;85:400–407. doi: 10.1016/j.jss.2011.08.032. [DOI] [Google Scholar]


