Significance
For many communication complexity problems the quantum strategies, distinguished by using Bell nonlocal correlations, provide exponential advantage over the best possible classical strategies. Conversely, for any Bell nonlocal correlations there exists a communication complexity problem that is solved more efficiently using the former. Despite many efforts, there were only two problems for which one could certify that any strategy that outperforms the classical one must harbor Bell nonlocal correlations. We prove that any large advantage over the best known classical strategy makes use of Bell nonlocal correlations. Thus, we provide the missing link to the fundamental equivalence between Bell nonlocality and quantum advantage.
Keywords: quantum, Bell inequality, port-based teleportation, communication complexity, nonlocality
Abstract
We obtain a general connection between a large quantum advantage in communication complexity and Bell nonlocality. We show that given any protocol offering a sufficiently large quantum advantage in communication complexity, there exists a way of obtaining measurement statistics that violate some Bell inequality. Our main tool is port-based teleportation. If the gap between quantum and classical communication complexity can grow arbitrarily large, the ratio of the quantum value to the classical value of the Bell quantity becomes unbounded with the increase in the number of inputs and outputs.
The key element that distinguishes classical from quantum information theory is quantum correlations. The first attempt to quantify their strength was quantitatively expressed in Bell’s theorem (1). They are similar to classical correlations in that one cannot take advantage of them to perform superluminal communication, yet every attempt to explain such correlations from the point of view of classical theory—namely, to find a local hidden variable model—is impossible. For a long time the existence of quantum correlations was merely of interest to philosophically minded physicists and was considered an exotic peculiarity, rather than a useful resource for practical problems in physics or computer science. This has changed dramatically in recent years—it became apparent that quantum correlations can be used as a resource for a number of distributed information processing tasks (2–4), producing surprising results (5, 6).
One area where using quantum correlations has wide-reaching practical implications is communication complexity. A typical instance of a communication complexity problem features two parties, Alice and Bob, who are given binary inputs x and y. They wish to compute the value of by exchanging messages between each other. The minimum amount of communication required to accomplish the task by exchanging classical bits (with bounded probability of success) is called classical communication complexity, denoted as .
There are two ways to account for the communication complexity of computing a function when we want to make use of quantum correlations. In the first one, Alice and Bob share any number of instances of the maximally entangled state beforehand and are allowed to exchange classical bits to solve the problem. Another approach is to have no preshared entanglement, but instead allow Alice and Bob to exchange qubits. The latter type of protocol can always be converted to the former with preshared entanglement and classical communication. We denote the quantum communication complexity of computing the function (with bounded probability of success) by .
For a large number of problems, the respective quantum communication complexity is much lower compared with its classical counterpart (4, 7). In such cases, we say that there exists a quantum advantage for communication complexity. In other words, one achieves a quantum advantage if the quantum communication complexity of the function is lower than its corresponding classical communication complexity.
One of the most striking example of quantum advantage is the famous Raz problem (5, 8), where quantum communication complexity is exponentially smaller than classical. Another example is the “hidden matching” problem for which the quantum advantage leads to one of the strongest possible violations of the Bell inequality (9). The latter inequality plays an important role in detecting quantum correlations and certifying the genuinely quantum nature of resources at hand. Previously, to obtain an unbounded violation of a particular Bell inequality one resorted to problems with the exponential quantum advantage. Here, we show that one can achieve the same result, using only polynomial quantum advantage.
As a matter of fact, the very first protocols offering quantum advantage were based on a quantum violation of certain Bell inequalities (6). It was even shown that for a very large class of multiparty Bell inequalities, correlations that violate them lead to a quantum advantage (perhaps, for a peculiar function) (10). This indicates that Bell nonlocality often leads to a quantum advantage. However, there are more and more communication protocols that offer a quantum advantage, but, nevertheless, they are not known to violate any Bell inequality.
It has long been suspected (6) that quantum communication complexity and Bell nonlocality are the two sides of the same coin. Although it is possible to convert a Bell nonlocality testing experiment to the communication complexity instance, the reverse has been known only for some particular examples. The question is whether this relationship holds in general, namely, Is quantum communication inherently equivalent to Bell nonlocality when solving communication complexity problems?
Until now, there were only two concrete examples where one could certify quantum correlations in the context of communication complexity by providing a quantum state and a set of measurements whose statistics violate some Bell inequality. The first case is the “hidden matching” problem and the second one is a theorem, which states that a special subset of protocols that provide quantum advantage also implies the violation of local realism (6). To get the violation of Bell inequalities obtained from the examples above, one had to perform an involved analysis that relied on a problem-specific set of symmetries. Thus, such an approach cannot be generalized to an arbitrary protocol for achieving a quantum advantage in the communication complexity problem.
In this paper, we show that given any (sufficiently large) quantum advantage in communication complexity, there exists a way of obtaining measurement statistics that violate some linear Bell inequality. This completely resolves the question about the equivalence between the quantum communication and Bell nonlocality: Whenever a protocol computes the value of the function better than the best classical protocol, even with a gap that is only quadratic, then there must exist a Bell inequality that is violated.
We provide a universal method that takes a protocol that achieves the quantum advantage in any single- or multiround communication complexity problem and uses it to derive the violation of some linear Bell inequality. This method can be generalized to a setting with more than two parties. Our Bell inequalities lead to a so-called unbounded violation (11): The ratio of the quantum value to the classical value of the Bell quantity can grow arbitrarily large with the increase of the number of inputs and outputs, whenever the ratio of and grows too. In particular, an exponential advantage leads to an exponential ratio.
Our method consists of two parts. In the first part, we use the quantum protocol based on the given communication complexity game to construct a set of quantum measurements on a maximally entangled state The central ingredient of our construction is the recently discovered port-based teleportation (12, 13). In the second part, given a protocol that computes a function f by using qubits, and the optimal classical error probability achievable with bits, we construct the corresponding linear Bell inequality that is subsequently violated by the above quantum measurements.
For one-way communication complexity problems we develop a much simpler method that is based on the remote state preparation and results in a nonlinear Bell inequality.
Quantum Communication Complexity Protocol
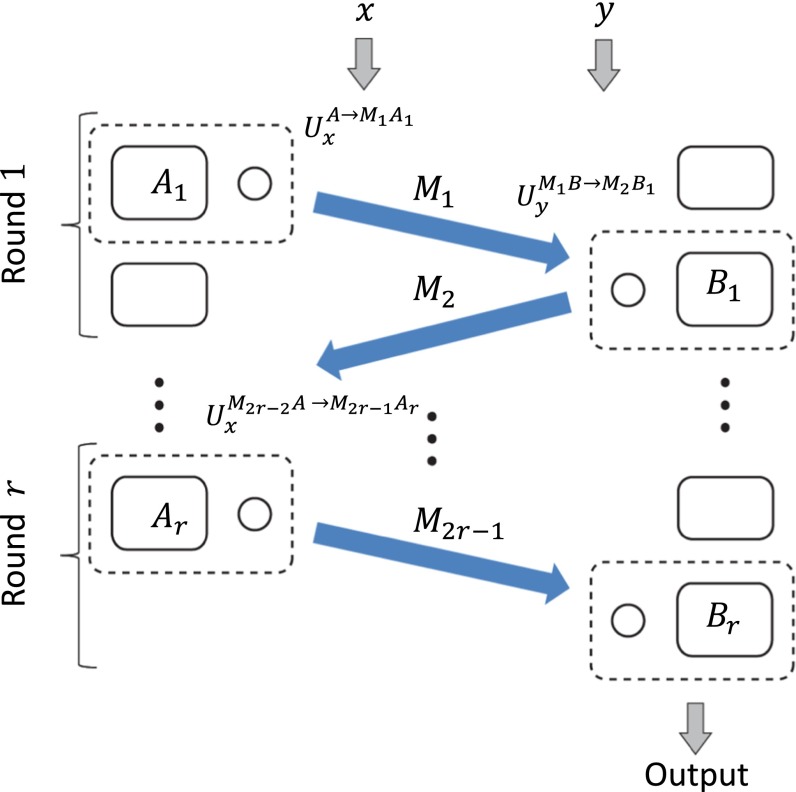
We start by defining a general quantum multiround communication protocol. Two parties, Alice and Bob, receive inputs and according to some distribution μ and their goal is to compute the function by exchanging qubits over multiple rounds. We further use subscripts for the system names to denote the round number. The parties proceed as follows:
-
i)
Alice applies on her local state and sends to Bob. In general, may be entangled with , which remains with Alice.
-
ii)
Bob performs on the state . Then he sends back the system to Alice, keeping .
-
iii)
Parties repeat steps i and ii for rounds. In the last round, instead of communicating back to Alice, Bob measures the observable and outputs the value of the function f. The observable acts on the system and Bob’s memory .
The above protocol may be transformed to the form where a one-qubit system is exchanged between Alice and Bob at any round. To achieve this, we split the Q-qubit message from Alice to Bob (or vice versa) into Q rounds of one-qubit transmission and modify the protocol as follows. We start from the initial state, which has the form
| [1] |
where and describe the memory registers that belong to Alice and Bob, respectively. The state , initially in state with Alice, is a one-qubit system that is used for message passing from Alice to Bob and vice versa. In each round, Alice applies to , and Bob applies to . In the last round, instead of applying a unitary transformation, Bob performs a measurement. One may view unitaries and as controlled gates acting on the memory with the one-qubit register acting as a control. This implies that for given x, in round i the state of Alice’s memory is spanned on at most orthogonal vectors. This observation will be crucial for the construction of a compressed-memory quantum protocol. Thus, we can transform any given protocol that requires Q qubits of communication into one that makes use of one-qubit exchanges.
From an Arbitrary Protocol to a Compressed-Memory Protocol
One shortcoming of the above protocols is that both players possess a local memory, possibly entangled with the message, which can span an arbitrary number of qubits and therefore could be much too big to properly handle in other parts of our construction. We solve this problem by converting an arbitrary protocol, as described above, to a protocol where we can upper bound the maximum size of the local memory.
The following proposition, which is a consequence of the Yao–Kremer lemma (3, 14), shows that it is possible to compress the parties’ local memory each step and that therefore the size of the local memory can be assumed to be at most the total communication. We include the proof in Supporting Information, section IV.
Proposition 1.
For any Q-qubit quantum communication protocol (without prior entanglement) there exists a Q-qubit quantum communication protocol for which Alice and Bob can encode their local memory on at most Q qubits each.
Quantum Measurements from the Quantum Communication Complexity Protocol
We now show how to convert a multiround compressed-memory protocol for computing , which gives a quantum advantage to the violation of a linear Bell inequality. There exist two different protocols to achieve this. The first protocol is based on the recently introduced method of port-based teleportation, which we briefly review in the next section. The second method, discussed at the end of this paper, relies on remote state preparation (15). We base our construction on the port-based teleportation because unlike the remote state preparation it is easily extendible to the multiround protocol and also gives rise to a linear Bell inequality.
Port-Based Teleportation
In deterministic port-based teleportation, the two parties share N pairs of maximally entangled qudits , each of which is called a “port.” To transmit the state , the sender performs the square-root teleportation measurement given by a set of positive operator valued measure (POVM) elements (precisely defined in equation 27 of ref. 13) on all of the systems , , obtaining the result . Then, he or she communicates z to the receiver who traces out the subsystems and remains with the teleported state in the subsystem . Teleportation always succeeds and the fidelity of the teleported state with the original is . The cost of the classical communication from sender to receiver is equal to . The distinctive feature of this protocol is that unlike with original teleportation, it does not require a correction on the receiver’s side.
Constructing Quantum Measurements
Using port-based teleportation we can now construct the relevant quantum measurements. Parties start with the initial state [1] and perform the following protocol:
-
i)
Alice applies on her local state . She obtains the state of size , which is teleported to Bob at once, using ports each of dimension . This consumes ports. Alice does not communicate the classical teleportation outcomes , with to Bob.
-
ii)
Bob applies the local unitary to each of the ports (he does not know the value of ) and teleports each of the states one-by-one by applying the teleportation measurement using ports each of the dimension , where . This consumes ports. Bob keeps the set of teleportation outcomes , , where for each , .
-
iii)
Parties repeat steps i and ii for rounds.
At the end of the protocol we obtain the set of measurements that map the generic communication protocol into the set of correlations,
| [2] |
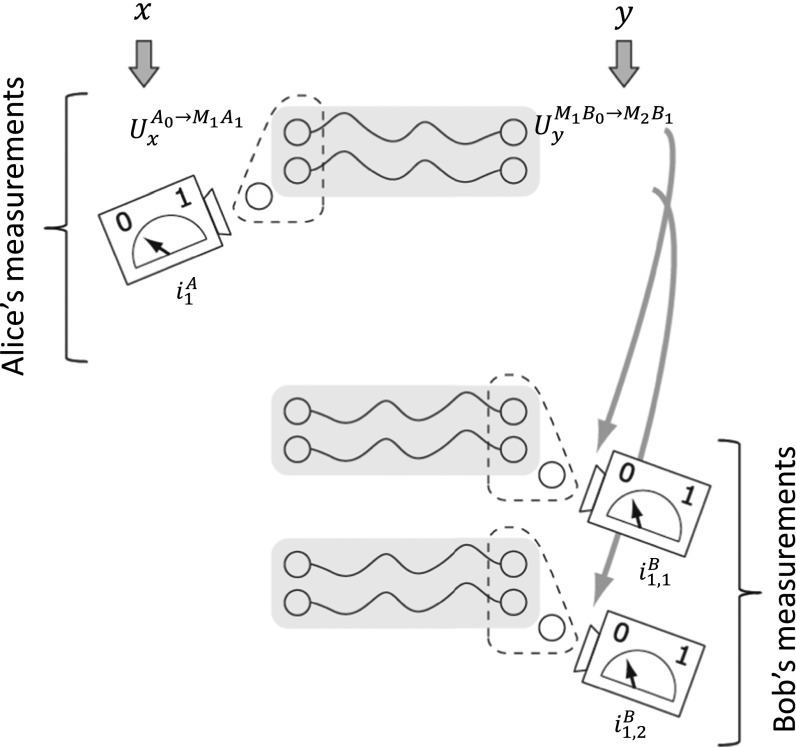
where are the final teleportation measurements in round r on Bob’s side. An important feature of this construction is that all of the quantum measurements are performed simultaneously but the classical information exchange happens sequentially. A single round of the protocol is depicted in Fig. 1 and the entire protocol is depicted in Fig. 2.
Fig. 1.
The structure of a single round of the protocol. Alice applies to her system, which if followed by Bob’s unitary . Bob has no information about the outcome of Alice’s port-based teleportation, , so he teleports each of his qudit subsystems individually, obtaining , ,….
Fig. 2.
Constructing quantum measurements. A and B denote Alice’s and Bob’s local subsystems, respectively. Each measurement , represents the square-root measurement in the port-based teleportation (12).
Simulating the Quantum Protocol
The last part of the puzzle is a method of simulating the compressed-memory quantum protocol, using the above correlations and classical communication.
Lemma 1.
Given a protocol for computing f that uses Q qubits of communication and achieves the success probability , , one can simulate it using correlations [2] and bits of classical communication with the success probability .
Proof:
Having access to correlations [2], Alice and Bob exchange their respective outcomes of the teleportation measurements that amount to bits of communication. This finalizes the port-based teleportation and thus simulates the corresponding quantum protocol. After exchange, Bob returns , where L denotes the last index that he received from Alice.
The above protocol is equivalent to rounds of port-based teleportation used for the compressed-memory protocol. Because by the compression of Proposition 1 for every round i the dimension of the teleported state is at most (the message is encoded in 1 qubit and the local memories are encoded in Q qubits each), we set so that the fidelity of teleportation on each step is . Then the protocol has success probability , where is the success probability of the original quantum protocol. Bounding the number of rounds r by the total amount of quantum communication Q, we get . Thus, the total amount of classical communication is bounded above by .
Construction of a Bell Inequality and Its Violation
Let us sum up the whole construction. First, we start with a quantum multiround protocol to compute f that uses quantum communication and no shared entanglement. This protocol requires Q qubits of communication and achieves . In this protocol, Alice and Bob may use an arbitrary amount of local quantum memory between rounds. Second, we convert it to the protocol with compressed local quantum memory, where the latter can be encoded in Q qubits. The compressed protocol is then used to obtain correlations in the form [2]. These correlations together with classical communication are used to recover the original communication complexity protocol that computes f. This protocol uses bits of classical communication and achieves success probability .
Now, if for a function there exists a gap between and with for the classical communication complexity protocol, and —then we observe the quantum violation of the Bell inequality of the form
| [3] |
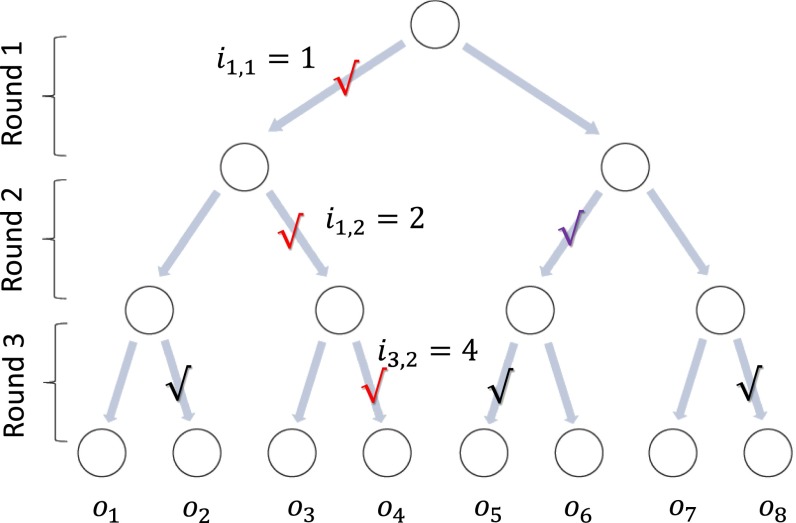
where μ is a probability measure on , the set denotes the set of all paths from the root to the leaves of length of the tree formed by the subsequent outputs of Alice and Bob in the protocol, and is the marginal probability that comes from summing over all indexes that do not explicitly appear in the path q (Fig. 3). With the exception of the last level, every node on the ith level has children that correspond to the outcome of the ith round of teleportation. The index of the first node in the path corresponds to the state being on Alice’s side and each subsequent index corresponds to the state being either on Alice’s or on Bob’s side in the alternating manner. The leaves of the tree correspond to the outcomes of Bob’s binary observable, which is his guess of the value of the function . (Note that in the Bell inequality, only special outputs appear—those given by the paths of length from the root to the leaves—whereas in general, outputs will be given by all sequences composed of choosing one node from every level.)
Fig. 3.
Exchange of the information after simultaneous teleportations to reveal the path of the teleported system in a three-round protocol. After Alice’s teleportation measurement in the first round the state ended up in port 1. Then, Bob teleports each of the two ports from the array that he used in the previous round, obtaining the outcomes 2 and 3 for ports 1 and 2, respectively. Finally, Alice performs a teleportation measurement for each of her four ports, obtaining the outcomes for the ports , respectively. A defines a path q to be a sequence of teleportation outcomes: . The last node of the path points to the system, whose outcome provides Bob’s guess. Recall that the measurements are performed at the same time, and the sequential multiround protocol consists only of the exchange of classical information obtained after teleportation. The latter is required to identify the last node of the path, which is used to make a guess about the value of the function.
The Bell inequality [3] is the central quantity of this paper. The left-hand side of the inequality constitutes the maximal success probability of guessing the value of f that can be achieved with the correlations of the form [2]. If this success probability turns out to be greater than the maximal success probability attained by the best classical protocol (the right-hand side of the inequality), this implies that correlations [3] reveal Bell nonlocality.
Large Violation of a Bell Inequality from Communication Complexity
We now show how to combine the above ingredients to get the main result: Whenever , we obtain an unbounded violation of the Bell inequality—the ratio of the quantum to the classical value of our Bell inequality grows arbitrarily when we increase the number of inputs and outputs (6, 9, 11, 16–18).
To state and proof the main theorem we summarize the above results in the following sequence of steps:
-
i)
Given a quantum protocol with advantage that uses Q bits of communication and achieves , we convert it (using Proposition 1) to the memoryless protocol that uses bits of communication and achieves the same success probability.
-
ii)
From the memoryless protocol using measurements and quantum state we obtain the set of quantum correlations .
-
iii)Using and bits of classical communication, we obtain a new protocol that achieves
Recall that all of the above measurements are done simultaneously, but the exchange of the corresponding classical information happens sequentially. -
iv)We turn protocol into a Bell inequality. To this end, we consider a general construction of Bell inequality given any function and a protocol P that uses communication and correlations. Namely, denote to be a guess of determined by the protocol for given inputs and outputs . Then, consider the probability of success of guessing the correct value of the function f parameterized by the correlations R,
[4] where is the indicator function. Our Bell inequality will simply be a shifted value of guessing probability
| [5] |
-
v)We consider the behavior of the above Bell inequality on classical correlations as a function of the amount of communication used by . To this end we apply Lemma 3 (proved in Supporting Information, section I), which states that given an arbitrary protocol P that uses bits of communication, we have
We apply it to our protocol .
Our main claim is contained in Theorem 1:
Theorem 1.
Suppose two parties can compute a function f, using the protocol P with Q qubits of communication and the success probability . Then there exist a quantum correlation and a Bell inequality such that
| [6] |
where is the classical communication complexity of f with probability , and stands for arbitrary classical correlation.
Remark:
Theorem 1 implies that if is sufficiently smaller than C (i.e., when we have a sufficiently large quantum advantage in communication complexity), then we obtain violation of a Bell inequality.
Proof:
Given the protocol P of computing f with success probability (where we set ) while using Q qubits of communication, we consider protocol from item iii, which uses bits of communication with the same probability of success. If applied to correlations of item ii and using Lemma 1 above, it achieves the success probability . Thus, the Bell inequality constructed in item v evaluated on gives
| [7] |
The next step is to check the value of the same Bell inequality on classical correlations . To this end, we apply item v with , and , obtaining that for any classical correlations
| [8] |
We put together Eqs. 7 and 8, obtaining the required bound for the ratio of Bell value on our particular quantum correlation and arbitrary classical correlation :
| [9] |
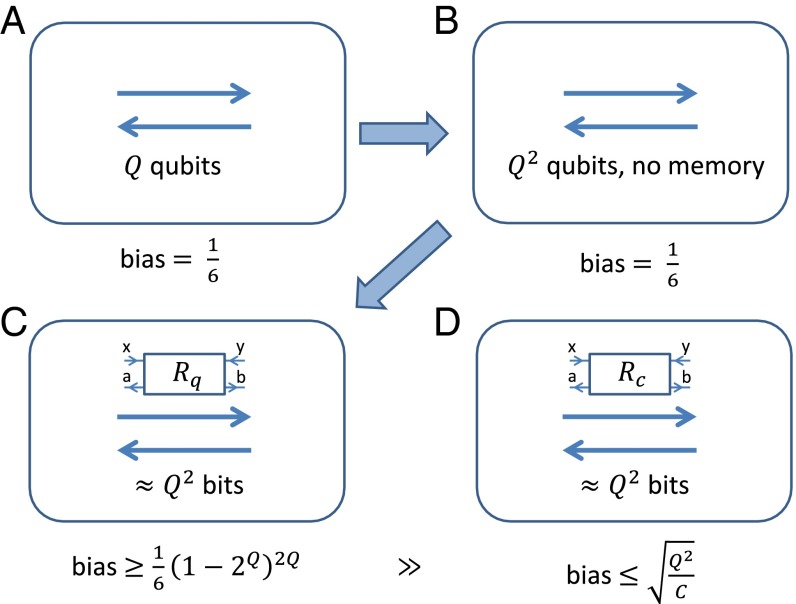
For the right-hand side becomes large, implying large violation of a Bell inequality. The diagrammatic proof of Theorem 1 is depicted in Fig. 4.
Fig. 4.
The scheme of the proof of Theorem 1. (A) an initial protocol evaluating function f with bias , using Q qubits; (B) memoryless protocol, with the same bias, using qubits; (C) protocol using quantum correlations and qubits, with bias still about ; (D) protocol gives small bias for any classical correlation if is sufficiently smaller than .
We provide several examples to demonstrate the power of our result.
Examples
Both of the examples are based on an explicit communication complexity problem called “vector in subspace” that was first introduced in ref. 5. In this problem, Alice and Bob receive the n-dimensional vector v and the description of -dimensional subspace H, respectively, with the promise that either or . The aim of the game is to determine which subspace v belongs to by exchanging messages between the parties. We consider two variants of the problem below.
Vector in Subspace Problem with One-Way Communication.
In this protocol, there is only one round of communication from Alice to Bob. Also, the local memory is not used. The deterministic quantum protocol requires qubits of communication (where n is the length of the vector in the problem), whereas the classical communication complexity is (8).
Knowing the quantum protocol P explicitly, we obtain a stronger Bell inequality because we do not need to invoke any approximations. Using bits of communication and correlations [2], we can achieve the quantum success probability of , whereas the classical protocol using the same amount of communication achieves , where , for some constant A. Thus, the ratio of quantum to classical values of the Bell inequality given in Theorem 1 is
| [10] |
where we use when it does not lead to ambiguity.
Vector in Subspace Problem with Two-Way Communication [Raz Original Problem (5)].
In this protocol, Alice sends Bob a quantum state of size (where n is the length of the vector in the problem) and then receives a state of the same size. As in the previous example, the parties do not use any local memory. There exists a deterministic quantum protocol for this problem. The classical communication complexity is . But using only qubits of communication and correlations [2], we get . The classical protocol using the same amount of communication achieves , where , for some constant A. Thus, the ratio of quantum to classical Bell values is
| [11] |
One-Way Communication Complexity Problems.
We now detail the scenario when Alice is allowed to send a single message to Bob to introduce a very different approach to obtain the violation of a Bell inequality. In this case, state preparation protocol on Alice’s side followed by the measurement of a quantum state by Bob will suffice. Also, there is no need for the local quantum memory on either side because one does not have to preserve the state of the communication protocol. Therefore, the role of the port-based teleportation is played by the remote state preparation.
One marked difference of this approach is that it consumes a significantly smaller amount of entanglement. Also, in this setting, we obtain the nonlinear Bell inequality that explicitly features the probability of Bob guessing the communication from Alice—something that is not possible using the method that relies on the port-based teleportation.
We first outline the remote state preparation protocol and then construct the relevant Bell inequalities below.
Remote State Preparation.
In the remote state preparation, Alice and Bob share a maximally entangled qudit state . Alice wants to prepare a known quantum state on Bob’s side by acting only on her share of the qudit, requiring no postprocessing on his side. To achieve this, she performs a measurement with elements , where is a conjugation of in the computational basis, on her part of , followed by the communication of the classical outcome to Bob if she measured (we denote this outcome as 1). This protocol has a very low probability of success, 1/d. We discuss the techniques to amplify it in Supporting Information, section II.
Correlations.
Applying the remote state preparation protocol to our communication complexity problem, we obtain the correlations
| [12] |
where are the POVM elements from the remote state preparation and describes Bob’s measurements on the shared state . In the current setup, the number of the binary observables of Alice and Bob is equal to the number of inputs x and y. The correlations [12] are obtained by acting on a single instance of the entangled state whereas the multiround approach uses in the order of states. Merging m instances together, we obtain the set of correlations
| [13] |
where , denotes the case when the remote state preparation succeeds and are the respective outputs. Thus, our Bell inequality may be written in the form [3]:
| [14] |
Nonlinear Bell Inequality.
Here we derive a Bell inequality for the case where the parties have the option to abort at any stage of the protocol. Our inequality turns out to be nonlinear and will depend only on two parameters, and , defined as follows:
-
•—probability that Alice succeeded, i.e., her outcome is 1 (averaged over all observables by the measure μ):
This probability turns out to be equal to Bob successfully “guessing” the communication from Alice in the absence of communication from the latter.[15] -
•—conditional probability that Bob’s outcome is equal to value of the function, given that Alice succeeded:
[16]
Using roughly instances of the state , Alice obtains one successful outcome on average. Then, Alice communicates to Bob this successful instance.
To obtain the inequality, we show how Alice and Bob may guess the correct value of the function. In this setup, as in the previous case, Alice uses instances of the state . Then Alice communicates to Bob the first instance where the outcome appeared, using bits. Finally, Bob looks at the outcome for the successful instance and with probability obtains the value of the function f.
If Alice and Bob share a state that admits a local-realistic description, then the used communication cannot be smaller than the value , because it is the optimal value attainable by classical means. Thus, for any local-realistic state, we must necessarily have
| [17] |
See Supporting Information, section III for further details.
Discussion
Examples show that our protocol produces large violations that are a bit weaker than the best known ones such as (16) or (9). This seems to be the price for its universality. However, it is an interesting open question, whether one can find a communication complexity protocol, such that the obtained Bell inequality would admit more dramatic violation than what is currently achievable. Another challenge is to decrease the amount of entanglement used to violate our Bell inequalities, which in our construction is exponential in the quantum communication complexity of the given problem. Similarly, the output size grows exponentially, which gives rise to the question of whether there exists a more efficient method of exhibiting the Bell nonlocality of quantum communication complexity schemes. The last two challenges could be addressed by devising a more efficient teleportation protocol or improving one of the existing ones (19). Finally, our method does not cover the protocols with initial entanglement. This is quite paradoxical, because protocols that use initial entanglement should be Bell nonlocal even more explicitly. It is therefore desirable to search for a method of demonstrating the Bell nonlocality of such protocols.
I) Proof of Lemma
Lemma 3.
For a protocol P supplemented by classical correlations and using bits of communication, the shifted success probability of computing f is bounded above as
| [S1] |
Proof:
Consider the success probability of the protocol P in the statement of Lemma 3 after the exchange of messages:
| [S2] |
To express the ratio [S1] we need to find in terms of communication complexity. We achieve this by using the amplification argument (see Supporting Information, section II for the proof), which boosts the success probability to 2/3 at the expense of sending at most bits of communication:
| [S3] |
Thus,
| [S4] |
II) Communication Complexity for Arbitrary Success Probability from Communication Complexity for Fixed Success Probability
Here we use the amplification (pumping) argument, which is a well-known technique for increasing the success probability of a randomized protocol (20) by repetition, and prove the following bound for the communication required by a randomized algorithm,
| [S5] |
where stands for communication complexity of an arbitrary (quantum or classical) randomized protocol. The bound is valid for . We use the pumping argument to show that a smaller would enable one to construct a protocol that uses less communication than and achieves and hence leads to a contradiction.
Let protocol use bits of communication to achieve . Let us consider protocol in which Alice and Bob repeat protocol l times and then Bob returns as an answer the most common output of . Because we are restricted to Boolean functions, the success probability of is equal to the probability that protocol gives the correct answer no less than times. By the Chernoff bound we get
| [S6] |
Because we require that , we get that
| [S7] |
From the communication complexity bound, it is known that to achieve , the protocol requires at least bits of communication. On the other hand, protocol repeats protocol l times and uses bits of communication. Putting this together, we have
| [S8] |
Using relation [S7] we get finally
| [S9] |
For our estimation leads to a communication complexity bound of which is much below the true value. This discrepancy comes from the nonoptimality of the pumping protocol.
III) Rigorous Derivation of the Nonlinear Bell Inequality and Its Violation
We now derive the nonlinear Bell inequality
| [S10] |
where the classical communication complexity is additionally parameterized by μ and the size of the problem n. First, we construct a one-way protocol with classical communication that makes use of shared entanglement given the set of correlations. We restrict ourselves to the family of correlations with , . As usual, is interpreted as the success on Alice’s side. When the latter occurs, we expect b to hold the value of the function . This restriction does not limit the generality because we may always take negation of , which is a local operation.
We show that for any correlation , characterized by n, , and (defined in the main text) leads to the protocol solving a problem of size n, using bits of communication and achieving for the initial probability distribution .
Protocol works as follows. Let Alice and Bob share copies of the correlations. They use their inputs x, y to select the appropriate measurements. Alice sends to Bob the index i of the first correlation where she obtained . Then, Bob estimates b for the respective correlation i and returns it as an output of protocol . In the case when none of the boxes returned , Alice outputs ABORT and Bob returns a random bit.
The protocol requires bits of communication to encode i of the box and 1 extra bit to encode the message ABORT. The probability that Alice gets for at least one instance is . For this case Bob returns with the probability . If Bob receives ABORT, he returns the proper value with probability . Putting we get an overall success probability of with communication of bits.
For all of the correlations with the local hidden variable model we get
| [S11] |
In the case when the communication complexity is given only for the fixed probability of success , by the pumping argument and the fact that for we obtain
| [S12] |
Using the fact that correlations obtained from a quantum protocol with communication complexity Q and success probability are characterized by and and inserting them into [S11], we make the following observation:
Observation 1.
Let be defined as in Eq. S10. If correlations obtained by construction of Eq. 2 in the main text from a quantum protocol with success probability and communication complexity Q do not violate the Bell inequality [S11], then
| [S13] |
To witness the violation of a Bell inequality constructed for a particular function f, it suffices to know how dominates over for some fixed . [Function dominates if for any constant k there exists such that for any we have .]
IV) Memory Compression of Quantum Communication Protocols
We convert an arbitrary quantum communication protocol into one where on each round Alice and Bob compress their memory and teleport it alongside the message. This ensures that they do not store any information associated with the message between the rounds.
The theoretical underpinning of such conversion is Lemma 2, proved by Yao (3) and Kremer (14) (also ref. 21, lemma 7.2.1 and ref. 22, appendix A). Lemma 2 applies to protocols where only a single qubit is sent per round. One can also derive a version of the latter where the message size is variable per round, which gives a more efficient memoryless version of protocols that need only a small number of rounds.
Lemma 2.
The state of an -qubit protocol (without prior entanglement) on input can be written as
where the and are complex numbers of magnitude , the are unit vectors belonging to Alice and Bob, respectively, and denotes the last bit of the -bit string i.
Consider the state description given by Lemma 2 for our quantum protocol after m rounds. Let describe Alice’s local states encoded in k qubits, for some k. Because there are only different vectors , there exists a unitary and a collection of m-qubit states such that for all we have . [More precisely, we can find some orthonormal basis for the space spanned by the (not necessarily orthogonal) , which consists of at most basis vectors. Then we can write where T is the completion of the unitary transformation on the orthogonal complement of the subspace spanned by the vectors, to the orthogonal complement of the subspace spanned by the vectors.] Similarly on Bob’s side there exists a unitary such that , where is the number of qubits used to encode Bob’s local state in the original protocol and every is an m-qubit state.
Therefore, the state of the protocol after m rounds can be written as
where and are the trivial local states on Alice and Bob, respectively. Then all of the local memory of the m-round protocol can be encoded in m qubits. This proves Proposition 1 in the main text.
Acknowledgments
Part of this work was done at the National Quantum Information Centre of Gdańsk as well as during the Program on Mathematical Challenges in Quantum Information, Isaac Newton Institute for Mathematical Sciences, 2013. This work is supported by European Commission (EC) IP QESSENCE, European Research Council (ERC) AdG QOLAPS, European Union (EU) project RAQUEL, Grant NCN Maestro (DEC- 2011/02/A/ST2/00305), the EU project SIQS, and MNiSW Grant IdP2011 000361. H.B. is partially funded through the Netherlands Organisation for Scientific Research Gravitation Grant Networks. S.S. acknowledges the support of Sidney Sussex College.
Footnotes
The authors declare no conflict of interest.
This article is a PNAS Direct Submission.
This article contains supporting information online at www.pnas.org/lookup/suppl/doi:10.1073/pnas.1507647113/-/DCSupplemental.
References
- 1.Bell JS. On the Einstein-Podolsky-Rosen paradox. Physics. 1964;1(3):195–200. [Google Scholar]
- 2.Yao A-C. Some complexity questions related to distributed computing. In: Fischer MJ, Demillo RA, Lynch NA, Burkhard WA, Aho AV, editors. Proceedings of 11th Annual ACM Symposium on the Theory of Computing. ACM Press; New York: 1979. pp. 209–213. [Google Scholar]
- 3.Yao A-C. 1993. Quantum circuit complexity. Proceedings of 34th IEEE Symposium on Foundations of Computer Science (IEEE Computer Society, Palo Alto, CA), pp 352–360.
- 4.Cleve R, Buhrman H. Substituting quantum entanglement for communication. Phys Rev A. 1997;56(2):1201. [Google Scholar]
- 5.Raz R. Exponential separation of quantum and classical communication. In: Vitter JS, Larmore L, Leighton T, editors. Proceedings of 31st Annual ACM Symposium on the Theory of Computing. ACM; New York: 1999. pp. 358–367. [Google Scholar]
- 6.Buhrman H, Cleve R, Massar S, de Wolf R. Nonlocality and communication complexity. Rev Mod Phys. 2010;82(1):665. [Google Scholar]
- 7.Buhrman H, Cleve R, van Dam W. Quantum entanglement and communication complexity. SIAM J Comput. 2001;30:1829–1841. [Google Scholar]
- 8.Regev O, Klartag B. 2011. Quantum one-way communication can be exponentially stronger than classical communication. Proceedings of 43rd Annual ACM Symposium on Theory of Computing, ed Vadhan S (ACM, New York), Vol 31, pp 31–40.
- 9.Buhrman H, Scarpa G, de Wolf R. 2010. Better non-local games from hidden matching. arXiv:1007.2359.
- 10.Brukner C, Zukowski M, Pan J-W, Zeilinger A. Bell’s inequalities and quantum communication complexity. Phys Rev Lett. 2004;92(12):127901. doi: 10.1103/PhysRevLett.92.127901. [DOI] [PubMed] [Google Scholar]
- 11.Junge M, et al. Unbounded violations of bipartite Bell inequalities via operator space theory. Commun Math Phys. 2010;300(3):715–739. [Google Scholar]
- 12.Ishizaka S, Hiroshima T. Asymptotic teleportation scheme as a universal programmable quantum processor. Phys Rev Lett. 2008;101(24):240501. doi: 10.1103/PhysRevLett.101.240501. [DOI] [PubMed] [Google Scholar]
- 13.Ishizaka S, Hiroshima T. Quantum teleportation scheme by selecting one of multiple output ports. Phys Rev A. 2009;79(4):042306. [Google Scholar]
- 14.Kremer I. 1995. Quantum communication. Master’s thesis (Hebrew University, Jerusalem)
- 15.Bennett C. Remote preparation of quantum states. IEEE Trans Inf Theory. 2005;51(1):56–74. [Google Scholar]
- 16.Buhrman H, Regev O, Scarpa G, de Wolf R. 2011. Near-optimal and explicit Bell inequality violations. IEEE Conference on Computational Complexity (IEEE Computer Society, Washington, DC), Vol 157, pp 157–166.
- 17.Palazuelos C. 2012. On the largest Bell violation attainable by a quantum state. arXiv:1206.3695.
- 18.Junge M, Palazuelos C. Large violation of Bell inequalities with low entanglement. Commun Math Phys. 2011;306:695. [Google Scholar]
- 19.Pirandola S, Eisert J, Weedbrook C, Furusawa A, Braunstein S. 2015. Advances in quantum teleportation. arXiv:1505.07831.
- 20.Kushilevitz E, Nisan N. Communication Complexity. Cambridge Univ Press; Cambridge, UK: 2006. [Google Scholar]
- 21.de Wolf R. 2001. Quantum computing and communication complexity. PhD thesis (University of Amsterdam, Amsterdam)
- 22.Buhrman H, de Wolf R. 2001. Communication complexity lower bounds by polynomials. 16th Annual IEEE Conference on Computational Complexity. [DOI]