Abstract
WSNs (Wireless sensor networks) are nowadays viewed as a vital portion of the IoTs (Internet of Things). Security is a significant issue in WSNs, especially in resource-constrained environments. AKA (Authentication and key agreement) enhances the security of WSNs against adversaries attempting to get sensitive sensor data. Various AKA schemes have been developed for verifying the legitimate users of a WSN. Firstly, we scrutinize Amin-Biswas’s currently scheme and demonstrate the major security loopholes in their works. Next, we propose a lightweight AKA scheme, using symmetric key cryptography based on smart card, which is resilient against all well known security attacks. Furthermore, we prove the scheme accomplishes mutual handshake and session key agreement property securely between the participates involved under BAN (Burrows, Abadi and Needham) logic. Moreover, formal security analysis and simulations are also conducted using AVISPA(Automated Validation of Internet Security Protocols and Applications) to show that our scheme is secure against active and passive attacks. Additionally, performance analysis shows that our proposed scheme is secure and efficient to apply for resource-constrained WSNs.
Keywords: anonymity, mutual authentication, wireless sensor networks, smart card
1. Introduction
With the advancement of short range radio communication coupled with advances in miniaturization of computing devices, WSNs (Wireless sensor networks) have drawn continuing attention from both academia and industrial areas due to its deployment scalability, power consumption constraint and wide applications. Within the infrastructure of WSNs, privacy and security are the two major challenges since nodes are generally deployed in hostile environments thus making the nodes vulnerable to attacks. From this context, secure information exchange over an untrusted network is a widely discussed issue in WSNs. In order to allow remote authorized users to access reliable sensor nodes which have been verified as legitimate ones, mutual AKA (Authentication and key agreement) between communicating entities is required in the scheme design. An AKA scheme for WSNs is composed of three classes of entity: users, sensor nodes and a gateway node (GWN), and has registration, login, authentication and key agreement, and password change phases. To date, research in an efficient and robust user authentication and session key agreement mechanism has gained a great deal of attention. A number of AKA schemes are developed in an attempt to enhance the security of the WSNs in the literature [1,2,3]. Among different kinds of cryptographic primitives (RSA [4], ECC [5,6] Elgamal [7] etc.) utilized in AKA for WSNs, lower computational cost scheme is even more admired owing to stringent constraints on limited computation capability, energy resources, storage and bandwidth of sensor nodes.
Wong et al. [8] released a hash function based AKA scheme for WSN, which sharply decreases computational load and makes the scheme adapt into a WSN environment. Nevertheless, as the scheme remains the lookup table of the registered user’s private data in the GWN side, it was demonstrated to be defenseless to stolen-verifier attack [9]. Later on, Das [9] developed a better scheme in order to mitigate the security flaws over Wong et al. The scheme concentrates on temporal credential and timestamp under defense mechanism aiming at preventing DoS attack efficiently while maintaining lightweight style. Unfortunately, the scheme was analyzed by many researchers and the results illustrated that it had still some drawbacks and flaws [10,11,12,13,14], such as incapability of achieving mutual authentication, notwithstanding node compromise attack, failing to provide the user password update securely. With the hope of amending aforementioned security weaknesses, several authors developed modifications on Das’s scheme but at the cost of increasing computational complexity [10,11,14]. Motivated by the thought of achieving better security and efficiency, Das et al.’s [15] built an efficient password based user AKA using only the hash function which encompasses the power of smart cards. They justified that compromise of a cluster head is free from node capture attacks. Their scheme allows only updating the password of the user locally without the help of the base station. Further, they evaluated their scheme in support of using no high computation except from the nominal task of assigning identity bits commitments and justified low memory requirement due to small size of identity bits commitment. Nevertheless, Turkanović [16], Wang-Wang [17] and Li [18] came across some additional problems in Das’s scheme, like non resistance to insider, stolen-verifier and node capture attacks. After that, Xue et al. [19] proposed a temporal-credential-based lightweight and resource user AKA scheme for WSNs using hash and XOR computations. In their scheme, the gateway node issues a temporal credential to each user and sensor node with the help of password-based authentication. Unfortunately, He et al. [20] was later remarked that the scheme of Xue et al. is imperfection and not applicable for practical implementation, due to some design defects and susceptibility to some attacks. Most recently, Turkanović et al. [21] proposed a lightweight user authentication scheme for WSN based only on hash and Xor computations that tend to save both computation and communication resources. Such cryptographic techniques scheme launched with a claim of achieving the basic security attributes as well as thwarting many attacks along with better complexities. The AKA scheme drew considerable attention but was subsequently on determined insecure and susceptible. The authors of [22,23,24] studied the vulnerability of the scheme [21] that incurs several security drawbacks and not applicable for practical implementation in the presence of an attacker who can mount a smart card theft attack. Motivated by the thought of preventing the security threats of scheme [21], Amin-Biswas [24] developed a modified version of the hash and Xor operations in order to appropriate for resource constrained environments. The authors addressed both security and efficiency, claimed that their designs possess many attractive features in which the system contains multiple gateway nodes. However, problems related to the leakage of the session short-term secrets accidentally are the fatal pitfalls of such scheme. Our contribution is motivated by the above facts.
2. Review of Amin-Biswas’s Scheme
This section briefly reviews Amin-Biswas’s scheme, which consists of system setup phase, user and sensor node registration phases, login phase, authentication phase (Figure 1), password update phase and dynamic node addition phase. Moreover, their scheme is composed of three entities: user, gateway node, and sensor node. For convenience of description, Table 1 shows the notations used in Amin-Biswas’s scheme.
Figure 1.
Mutual authentication and key agreement of Amin-Biswas’s scheme.
Table 1.
Notations.
| Symbol | Description |
|---|---|
| User | |
| Gateway node | |
| Sensor node | |
| Home gateway node | |
| Identity/Password of | |
| Random identity of generated by for authentication | |
| Identity of | |
| Secret key of | |
| Constant transmission time | |
| Timestamp | |
| r/ | Random numbers of |
| One-way hash function | |
| ⊕ | Xor operation |
2.1. System Setup
The system administrator deploys each which stores into its memory, where , is a random number and is known to all the GWNs and maintains it securely.
2.2. Sensor Node Registration
Step 1: sends to the nearby GWN, where .
Step 2: The GWN stores , where . After that, the GWN sends a confirmation message to each sensor node.
Step 3: Upon receiving the confirmation message from the GWN, each destroys from the memory.
2.3. User Registration
Step 1: The new user computes and sends to the via private channel, where r is a nonce, is the identity and is the password of .
Step 2: The computes , where is a random identity and is the ’s long term secret key.
Step 3: The issues a smart card which contains and sends it to . Further, the stores in its memory.
Step 4: When receiving the smart card, stores in the smart card.
2.4. Login and Authentication
Step 1: inserts the smart card and inputs identity and password to the card reader. After that, the card reader computes and checks whether .
Step 2: If it matches, the card reader computes and sends a login message to the by public channel.
Step 3: When receiving the message , the first checks whether the received timestamp is within the valid time period, the computes , the extracts from the database using . Next, the checks whether . If it holds, the computes and sends to the the sensor node via public channel.
Step 4: After receiving the message , checks whether . If it holds, computes and checks whether . If it matches, computes and sends to the via public channel.
Step 5: Upon receiving the message , the first checks the timestamp validity, i.e., , where is the current timestamp. The computes , . If it is true, the computes and sends to the via public channel.
Step 6: After receiving the message , checks whether the received timestamp is within the valid time intervals. If it holds, extracts . If it is true, confirms the authenticity of and computes between the entities involved in the system.
2.5. Dynamic Node Addition
According to the system setup phase, the system administrator deploys the new sensor node over the target region and the deployed sensor node executes sensor node registration phase to the nearby GWN.
2.6. Password Update
Step 1: A user keys his password , the card reader computes and then computes .
Step 2: The card reader stores the new computed values instead of the old values .
3. Security Analysis of Amin-Biswas’s Scheme
Although Amin-Biswas claimed that their scheme achieves several security requirements including mutual authentication, user anonymity and resilience against some attacks. Unfortunately, we found that there was still something security vulnerability in Amin-Biswas’s scheme.
Known Session-Specific Temporary Information Attack
Cheng et al. [25] has demonstrated that the exposure of session temporary information accidentally should not compromise the secrecy of generated session key. However, we will demonstrate that Amin-Biswas’s scheme contraries to this security property which is necessary for a good or an ideal authentication scheme [26]. Without loss of generality, we assume that a temporary information is compromised by an adversary unintentionally, which may allow the adversary to frame the session key effortlessly and even more acquire the legitimate user’s sensitive data by means of monitoring the transmitted data in the communication. To illustrate the process concretely, you can look at an attack in the next few steps (Figure 2).
Figure 2.
Known session-specific temporary information attack on Amin-Biswas’s schem.
Step 1: The adversary could extract the session ephemeral secrets and from the results of and , where are the known parameters stemmed from the transferred message .
Step 2: Based on the derived the session immediate secret , the adversary has ability to retrieve another important parameter by computing , where is also obtained through the transmitted messages and .
Step 3: The adversary could compute the session key with all those derived data. Not only that, the adversary could easily guess the user’s identity by attempting to check whether until making the equation true, where is a candidate identity and r is extracted with a stolen smart card. The adversary is further capable of retrieving the user’s password on the strength of the extracted secrets by checking from the legal user’s smart card. The aforementioned cryptanalysis is based on the concrete fact that identity and passwords are low-entropy keys [27,28]. As a result, the adversary succeeds to get the user’s identity and the user’s password .
Step 4: The above analysis reveals that, all those information leaks allow the adversary to impersonate as a legitimate user to login the GWN and access the real-time information from sensor nodes. In other words, our analysis demonstrates that their scheme can be free from known session-specific temporary information attack, thereby Amin-Biswas’s scheme is completely insecure.
4. Proposed Improved Scheme
This section will describe our proposed anonymity-preserving AKA scheme in detail. The proposed AKA scheme conceals the user’s real identity in the encryption algorithm along with the hash of random identity and secret key as the symmetric key. The messages, which are transmitted in public channel, are the results of the hash or the encryption, thus avoiding the risk by intercepting the communication channel to acquire the plaintext directly. In order to conquer the known session-specific temporary information attack, each communicate entity only knows the xor results of the others’ generated random numbers in computing the session key. The proposed AKA scheme inherits Amin-Biswas’s scheme aiming at cope with the loopholes of the aforementioned security drawbacks of their scheme. Based on the previous analysis, the functionality of the proposed scheme has been greatly improved with a slight higher computation cost due to the symmetric cryptographic algorithm. Our proposed AKA scheme has five phases: User registration; Sensor node registration; Login; Authentication and key agreement (Figure 3); Password change. We will introduce them as follows.
Figure 3.
Mutual authentication and key agreement of our scheme.
4.1. User Registration
Step 1: A new user chooses his identity and password , then he sends his registration request message to the gateway node GWN, where r is a random number.
Step 2: Upon receipt of the message, GWN computes . Next, GWN issues a smart card for each user after storing into the memory of smart card and thus sends back it to . At last, GWN stores in its memory.
Step 3: After receiving the smart card, adds r to the smart card.
4.2. Sensor Node Registration
Step 1: The sensor node transmits its identity to GWN.
Step 2: GWN computes and returns it to after storing into its memory.
Step 3: When receiving the message from , also keeps them securely.
4.3. Login
When a registered user desires the WSNs services, he needs to be prepare his personal information along with the smart card. The following procedure are required to be done by :
Step 1: enters his identity and password into the smart card after inserting the smart card into the mobile device. The smart card computes and checks whether it is equal to . If it holds, is considered as a legal user.
Step 2: The card reader derives and by computing and , respectively. Based on the two values, the card reader computes by encrypting the information with the derived and computes by putting the information into the hash function, where is the current timestamp at user side and is a random number. Next, the card reader sends a login message to GWN.
Step 3: Upon receiving the login message, GWN decrypts by the symmetric key to retrieve . Next, GWN checks whether , where is the current timestamp at GWN side. If it is valid, GWN verifies . The validation of ensures is a legitimate user. Subsequently, picks a random number and computes , . Next, sends the message to .
Step 4: When receiving the message from , decrypts using the symmetric key to derive . And then, checks the timestamp is within a permissible temporal interval. Next, computes and checks whether it matches with the received . It it holds, computes , , . Finally, transmits the message to .
Step 5: After receiving the message from , also needs to decrypt the received to derive . Upon retrieving , verifies whether is a valid timestamp. If it is valid, computes and checks whether . If it is correct, computes and , where is the current timestamp at side. Next, sends the message to .
Step 6: Once receiving the message from , derives by decrypting using the symmetric key . then checks whether is fresh. The freshness of is verified, proceeds to compute the session key and examine whether is equivalent to the received . If the equation is true, the handshake among three-party is successful, and they negotiate the session key with each other. The establishment of the session key is considered to be encrypted the following packs in their communication channel.
4.4. Password Change
When a user attempts to update his password into a new one, he needs to execute the following steps:
Step 1: The user initially inserts the smart card into the card reader and inputs his identity and old password . Next, the card reader computes and checks whether it is equal to . If it holds, the user is considered as a legal one. And thus, the card reader asks the user to key a new password.
Step 2: After keying the new password, the card reader computes , and . The card reader replaces with .
5. Security Analysis of Our Scheme
In this section, the strength of the proposed AKA scheme by considering the informal and formal analysis has been analyzed. To be specific, our scheme keeps to the system requirements and successfully withstands diverse attacks to enhance the security level. Next, using BAN logic [29] to demonstrate the validity of our AKA scheme. Then, the formal security analysis of our scheme is presented. Besides, the widely-accepted AVISPA tool [28,29] is used to simulated for the security experimental verification of our AKA scheme.
5.1. Informal Security Analysis
This section addresses a detailed security evaluation to indicate that the proposed scheme is secure against various known security attacks. Suppose that an adversary can eavesdrop, intercept, modify, delete or replay the transmission over a public channel.
5.1.1. Session Key Agreement
The session key is established among the user , the sensor node and the gate-way node . Note that and has no way to know other participates’ random numbers excepts themselves. The established session key is to encrypt the real-time data to ensure the transmission are confidential through an unreliable channel. Therefore, the session key is different in each session due to it is generated by various random numbers, and it is challenging for to extract the current session key from the eavesdropped messages because of the one-way property of the hash function.
5.1.2. Mutual Authentication
The gate-way node first checks whether the received timestamp is valid as compare to the decrypted one from when receiving the message . Next, verifies . If both the condition are true, the validity of the user is authenticated by . Similarly, checks the validness of the received timestamp with the derived one from after receiving the message . He then checks whether . If both the equation hold, the validity of is confirmed by and thus the sensor node is also verified due to only the valid would forward the correct random number and thus compute the correct session key. Correspondingly, mutual authentication between and are performed by checking and . With the same verification mode as and , double authentication is utilized, i.e., to verify the freshness of the received timestamp with the retrieved one, to put the retrieved one to substitute in the awaiting verification value and thus checking the hashed value. In this way, has no ability to modify the hashed value and only modify the timestamp, thus impersonating as any participates. Therefore, mutual authentication among the entities are provided in the proposed scheme.
5.1.3. Resistance to Insider Attack
It is probable that the users use the same identity and password across multiple networks. In our case, the GWN plays the role of a trusted third party, but some curious administrator can have access to the database which stores the user’s personal information in order to gain something important. However, during the registration phase, the user transmitted masked password instead of plaintext password. In this way, the insider of system has no ability to derive the privacy of the user because of non-invertible property of one-way hash function. Therefore, the proposed AKA scheme is resilient against the privileged insider attack.
5.1.4. User Anonymity
We adopt two strategies to protect the user’s identity from disclosing. One is the masked identity with the secret key of . Note that the key is essentially a random number generated by and thus it is computationally infeasible for to extract the user’s identity in plaintext. Another is directly the use of dynamic identity selected by , which is hashed in the open channel. In essence, the random identity is no relation with the real one. Consequently, compromise of released one influences nothing on the actual identity of . Therefore, the proposed scheme mechanism is a dynamic identification process and we will verify the point later in simulation.
5.1.5. Resistance to Known Session-Specific Temporary Information Attack
Known session-specific temporary information security means if gets the ephemeral information, such as the random values, and , he still cannot acquire information of the session key. Since has no way to compute the symmetrical key without knowing the identity of and thus decrypting the packs transmitted in communication channel. More seriously, and only receive the results of xor for the random numbers picked by the rest of participates. As such, attempting to intercept any hashed values in the public communication channel but are unhelpful to compute the session key. Therefore, it is not possible for any attacker to compute the session key on leakage or compromise of session specific temporary information.
5.1.6. Resistance to Denial-of-Service Attack
This attack is to secure against since our proposed scheme works on the principle of request-response communication. Additionally, the sensor node will check the received packs and chooses refuse or pass the session from the sender. On the other hand, if does the malicious flooding of the authentication requests to , first knows about malicious dropping of such control messages as a referee. And needs to know the symmetric key between the legal user and the legitimate sensor node unless he can solve the one-way hash functions. Furthermore, we have introduced timestamps into the scheme, which mitigate any consequential request. As such, we say that our scheme has also the ability to withstand the denial-of-service attack.
5.1.7. Resistance to Sensor Node Impersonation Attack
Suppose gets all transmitted information such as and and plans to impersonate as a legitimate sensor node. However, it has no feasible way to decrypt the cryptographic packs like without knowing the symmetry key with the , thus failing to compute the correct session key and thus excluding by . Therefore, can not impersonate as a valid sensor node.
5.1.8. Resistance to Off-Line Password Guessing with Smart Card Breach Attack
The system is secure even if the stored information and the login message are revealed. Since the user’s identity and password are hashed by ’s long-term private . The adversary has no information about these private keys. Therefore, the proposed scheme is secure against off-line password guessing attack.
5.2. Authentication Proof Based on the BAN Logic
The BAN logic, which is the first suggestion to formalize the description and analysis of authentication schemes, is used to analyze existing schemes to bring out their flaws. We analyze the proposed scheme by establishing some required goals, making some assumptions about the initial state of the scheme and transforming the proposed AKA scheme to the idealized form. Some descriptions about its notations and formulas are shown as follows.
Notations & Formulas
·: : P has received message X
·: : P believes X
·: : P once said X
·: : P has jurisdiction over X
·: : P and Q shared key K
·: : X is fresh
·: : the formula X encrypted under the formula K
·: : X or Y is one part of
·: : P and Q share secret K
·: Message meaning rule:
·: Nonce-verification rule:
·: Jurisdiction rule:
·: Belief rule:
·: Freshness distribution rule:
Aims
.
.
.
. ,
.
.
.
.
.
.
Idealization
:
: , :
:
: , :
:
: , :
:
:
:
Assumptions
:
:
:
:
:
:
:
:
:
:
:
:
:
:
:
Derivation process
According to , we get:
.
According to , and message rule, we derive:
.
According to , and freshness distribution rule, we gain:
.
According to - and nonce-verification rule, we achieve:
.
According to and belief rule, we acquire:
.
According to , and jurisdiction rule, we attain:
. ,
According to , and jurisdiction rule, we get:
.
According to , we collect:
.
According to , and message rule, we seek:
.
According to and freshness distribution rule, we receive:
.
According to - and nonce-verification rule, we extract:
.
According to -, and jurisdiction rule, we derive:
.
According to -, and jurisdiction rule, we regain:
.
According to , and
.
According to , and nonce verification rule, we earn:
.
According to , we get:
.
According to , and message rule, we seek:
.
According to , , and freshness distribution rule, we gain:
.
According to - and nonce-verification rule, we derive:
.
According to and belief rule, we get:
.
According to , and jurisdiction rule, we regain:
.
According to , , and
. ,
According to , and nonce-verification rule, we collect:
.
According to , we obtain:
.
According to , , and message meaning rule, we get:
.
According to , and nonce-verification rule, we regain:
.
According to , we attain:
.
According to , and message meaning rule, we reach:
.
According to , and freshness distribution rule, we attain:
.
According to - and nonce-verification rule, we seek:
.
According to and belief rule, we extract:
.
According to , , we get:
.
According to -, and jurisdiction rule, we obtain:
.
According to , and , we gain:
.
According to , we seek:
.
According to , , and message meaning rule, we obtain:
.
According to , and nonce-verification rule, we reach:
:
According to and , we ge
:
According to and , we get:
:
5.3. Formal Security Proof
In order to show that our scheme is secure, we first define the following assumption:
The encryption algorithm Ω assumption: Ω is secure if for any sufficiently small , any probabilistic, polynomial time adversary , where denotes the Ω-advantage.
Theorem 1.
Let Ω be secure. Under the assumption that the one-way hash function closely behaves as an oracle, the proposed scheme is provably secure against an adversary for protecting user anonymity and session key.
We consider the following two random oracles to construct an adversary :
Reveal 1: This oracle will unconditionally output the value x from the given hashed result .
Reveal 2: This oracle will unconditionally output the plaintext x from the given ciphertext .
Proof of Theorem 1.
We assume that has the ability to derive the identity of the user and the session key among , the gateway node and the sensor node . Then he needs to execute the following experimental algorithm, say (Algorithm 1), (Algorithm 2) for our proposed scheme. Define the success for as , as , and the advantage for becomes , the advantage for becomes , where denotes the maximum time interval, denotes the number of queries to the oracle. However, according to Ω assumption and the one-way property of hash function, both they are hard problems within polynomial time, i.e., , , for any sufficiently small . As a result, there is no way for the adversary to retrieve the user identity and the session key ☐
| Algorithm 1 . |
|
| Algorithm 2 . |
|
5.4. Simulation Results Using AVISPA Tool
AVISPA is one of the publicly accepted Internet schemes verification techniques among many developed semi-automated formal security analysis tools and several schemes [30,31] have been analyzed using it. It is a push-button tool for error detection based on the Dolev and Yao model [32] and provides a modular role-based expressive formal language called the HLPSL (High level protocol specification language) for targeting the design of the schemes. The HLPSL presentation of the protocol is translated into the lower level description language called IF (Intermediate Format) by the translator called HLPSL2IF, which is the entrance of architecture of AVISPA. IF presentation of the scheme is used as the start point to the four various back-ends: OFMC (On the-fly Model-Checker), CL-AtSe (CL-based Attack Searcher), SATMC (SAT-based Model-Checker) and TA4SP (Tree-Automata based Protocol Analyzer). These back-ends are utilized to analyze different security properties such as secrecy of the shared session key, authentication, the privacy of user and robustness against replay attacks. The OF (output format) is generated by using one of the four back-ends which measures whether the security scheme is SAFE or UNSAFE and under what conditions it has been obtained.
In order to evaluate the security of the proposed AKA scheme by the AVISPA tools, we have implemented the specifications for the user (Appendix A, Figure A1), the sensor node (Appendix A, Figure A2), the gate-way node (Appendix A, Figure A3), the session (Appendix A, Figure A4), goal and the environment (Appendix A, Figure A5) in HLPSL. The desired goals, mutual authentication between and by checking and , between and by checking and , the secrecy of session key, user’s identity and password are all achieved. We have chosen the widely-accepted OFMC and CL-AtSe back-ends for the execution tests and a bounded number of sessions model checking. In OFMC backend (Figure 4), the depth for the search is 12, the total number of nodes searched in this case is 9143, which takes 44.93 s. In CL-AtSe backend (Figure 5), 7067 states were analyzed and 1360 states were reachable. Further, CL-AtSe backend took 0.46 s for translation and 0.8 s for computation. After simulation of the code through OFMC and CL-AtSe back-ends, the results show the proposed AKA scheme is guard against both the active and passive adversaries.
Figure 4.
Simulation result for the OFMC.
Figure 5.
Simulation result for the CL-AtSe.
6. Performance Analysis
This section summarily presents the performance of the proposed AKA scheme and compares in terms of security analysis and computation overheads with existing hash-function based schemes. While computing the cost of the scheme, we assume the length of the identity is 128 bits, the AES encryption/decryption [33] require each 128 bits, the timestamp is 24 bits and the message digest of SHA-3 [34] is 256 bits. Let be the time for one hashing operation, and be the time for one symmetric cryptography operation, we omit xor operation due to its negligible computational cost.
Table 2 shows the computational complexity and communication overhead analysis along the main security attributes with schemes Aim-Biswas [24], Farash et al. [23], Turkanović et al. [21] and Xue et al. [19] It is noted that the communication parameters of the proposed scheme are bits, the cost of registration is , during the authentication process, the computation cost of the GWN is , the computation cost of the simple resource constrained sensor node is , the total time spent by the proposed scheme is . According to our experiment results using the jPBC library (2.0.0, [35]) (CPU: 3.2 GHz, RAM: 4.0 GB), the arithmetic mean for executing is 0.0359 ms, is 0.1755 ms after running them 1000 times. Thus, the execution time of the user side is 0.6023 ms, the resource constrained sensor node is 0.4946 ms, the GWN is 0.9214 ms and the total execution time of the proposed AKA scheme is 2.0183 ms. The results shows that the computational cost of the user and the gateway node are considered to be taken on more than sensor node part due to its resource constrained environment. From Table 2, we can see that Farash et al.’s scheme [23] achieves more security, that is, resistance to stolen smart card attack and protection of sensor node’s identity, although Farash et al.’s scheme consumes more computations than Turkanović et al. [21]. Even though the efficiency of Aim-Biswas’s scheme [24] is higher than Turkanović et al. [21]’s scheme, Aim-Biswas’s scheme is still vulnerable to known session-specific temporary information attack and no protection of sensor node anonymity. Xue et al. [19] is insecure against sensor node impersonation attack and denial-of-service attack excepts vulnerability to known session-specific temporary information attack even though its computational overheads is lower than Farash et al.’s scheme. Compared with other four schemes which cannot ensure known session-specific temporary information attack resistance, the proposed AKA scheme consumes a slight higher computation cost lies in using symmetric cryptographic operations. In the face of the perspective of practical application, we consider the security of a cryptographic protocol is the most important. It is acceptable with such high level of security at the expense of increasing computational cost moderately. Therefore, the proposed AKA scheme is very efficient and practical for the resource constrained WSNs environment.
Table 2.
Performance analysis.
| Ours | Aim-Biswas [24] | Farash et al. [23] | Turkanović et al. [21] | Xue et al. [19] | |
|---|---|---|---|---|---|
| Communication cost (bits) | 3680 | 3808 | 3808 | 2816 | 3212 |
| Computation cost (user) | |||||
| Computation cost (sensor) | |||||
| Computation cost (GWN) | |||||
| Total (ms) | |||||
| Yes | Yes | Yes | Yes | ||
| Yes | Yes | Yes | Yes | Yes | |
| Yes | Yes | Yes | Yes | ||
| Yes | Yes | Yes | Yes | Yes | |
| Yes | Yes | Yes | Yes | ||
| Yes | Yes | Yes |
: Resiliency of known session-specific temporary information attack; : Resiliency of denial-of-service attack; : Resiliency of insider attack; : Resiliency of sensor node impersonation attack; : User identity protection; : Resiliency of stolen smart card attack; : Sensor node anonymity.
7. Conclusions
In this paper, we review and show that Amin-Biswas’s scheme is susceptible to known session-specific temporary information attack, thus suffering from various kinds of attacks, such as user impersonation, off-line password guessing attacks and leakage of user identity. In order to erase the drawbacks of Amin-Biswas’s scheme, we propose an anonymous AKA scheme for WSNs by using the lightweight operations, such as one-way hash functions, xor and symmetric cryptography. The proposed anonymous AKA scheme is characterized to provide relatively more security features and high security level, simulation results confirmed the efficiency of our proposal in terms of the computation and communication overheads. We are interested in extending the integration of biometrics to design a relatively more efficiency AKA scheme without compromising several security aspects in future.
Acknowledgments
The authors would like to thank all the anonymous reviewers for their helpful advice. This paper is supported by the National Natural Science Foundation of China (Grant Nos. 61472045, 61573067), the Beijing Natural Science Foundation (Grant No. 4142016), the BUPT Excellent Ph.D. Students Foundation (Grant No. CX2015310), and the Asia Foresight Program under NSFC Grant (Grant No. 61411146001).
Appendix A HLPSL Implementation of the Proposed Scheme
This section shows the proposed AKA for the roles of the user (Figure A1), the gateway node (Figure A2), the sensor node (Figure A3), the session (Figure A4) and the environment (Figure A5).
Figure A1.
Role specification for the user .
Figure A2.
Role specification for the sensor node .
Figure A3.
Role specification for the gateway node .
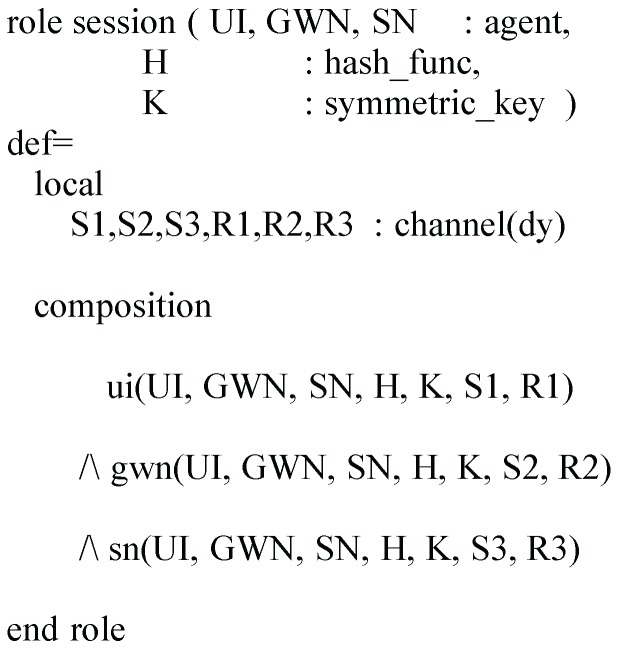
Figure A4.
Role specification for the session.
Figure A5.
Role specification for the environment.
Author Contributions
Conceived and designed the experiments: Yanrong Lu, Lixiang Li, Haipeng Peng, Yixian Yang. Performed the experiments: Yanrong Lu, Lixiang Li, Haipeng Peng and Yixian Yang. Analyzed the data: Yanrong Lu, Lixiang Li, Haipeng Peng and Yixian Yang. Contributed reagents/materials/analysis tools: Yanrong Lu, Lixiang Li, Haipeng Peng and Yixian Yang. Wrote the paper: Yanrong Lu, Lixiang Li, Haipeng Peng and Yixian Yang.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Jiang Q., Ma J.F., Lu X., Tian Y.L. An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-to-Peer Netw. Appl. 2015;8:1070–1081. doi: 10.1007/s12083-014-0285-z. [DOI] [Google Scholar]
- 2.Wang D., Wang P. On the anonymity of two-factor authentication schemes for wireless sensor networks: Attacks, principle and solutions. Comput. Netw. 2014;73:41–57. doi: 10.1016/j.comnet.2014.07.010. [DOI] [Google Scholar]
- 3.He D.B., Zeadally S., Xu B.W., Huang X.Y. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2015;10:2681–2691. doi: 10.1109/TIFS.2015.2473820. [DOI] [Google Scholar]
- 4.Giri D., Maitra T., Amin R., Srivastava P.D. An efficient and robust rsa-based remote user authentication for telecare medical information systems. J. Med. Syst. 2015;39:1–9. doi: 10.1007/s10916-014-0145-7. [DOI] [PubMed] [Google Scholar]
- 5.Yeh H.-L., Chen T.H., Liu P.C., Kim T.-H., Wei H.W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors. 2011;11:4767–4779. doi: 10.3390/s110504767. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 6.Choi Y., Lee D., Kim J., Jung J., Nam J., Won D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors. 2014;14:10081–10106. doi: 10.3390/s140610081. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 7.Watro R., Kong D., Cuti S.F., Gardiner C., Lynn C., Kruus P. Tinypk: Securing sensor networks with public key technology; Proceedings of the 2nd ACM Workshopon Security of Ad Hoc and Sensor Networks (SASN’04); Washington, DC, USA. 25 October 2004; pp. 59–64. [Google Scholar]
- 8.Wong K.H.M., Zheng Y., Cao J., Wang S. A dynamic user authentication scheme for wireless sensor networks; Proceedings of the 2006 IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing; Taichung, Taiwan. 5–7 June 2006. [Google Scholar]
- 9.Das M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009;8:1086–1090. doi: 10.1109/TWC.2008.080128. [DOI] [Google Scholar]
- 10.Nyang D., Lee M.K. Improvement of Das’s two-factor authentication protocol in wireless sensor networks. IACR Cryptol. ePrint Arch. 2009;2009:631. [Google Scholar]
- 11.Huang H.-F., Chang Y.F., Liu C.H. Enhancement of two-factor user authentication in wireless sensor networks; Proceedings of the 2010 Sixth International Conference on Intelligent Information Hiding and Multimedia Signal Processing; Darmstadt, Germany. 15–17 October 2010; pp. 27–30. [Google Scholar]
- 12.Vaidya B., Makrakis D., Mouftah H.T. Improved two-factor user authentication in wireless sensor networks; Proceedings of the IEEE 6th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob); Niagara Falls, ON, Canada. 11–13 October 2010; pp. 600–606. [Google Scholar]
- 13.Khan M.K., Alghathbar K. Cryptanalysis and security improvements of two-factor userauthentication in wireless sensor networks. Sensors. 2010;10:2450–2459. doi: 10.3390/s100302450. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 14.He D.J., Gao Y., Chan S., Chen C., Bu J.J. An enhanced two-factor user authentication scheme in wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2010;10:361–371. [Google Scholar]
- 15.Das A.K., Sharma P., Chatterjee S., Sing J.K. A dynamic password-based user authentication scheme for hierarchical wireless sensor networks. J. Netw. Comput. Appl. 2012;35:1646–1656. doi: 10.1016/j.jnca.2012.03.011. [DOI] [Google Scholar]
- 16.Turkanović M., Hölbl M. Notes on “a temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks”. Wirel. Pers. Commun. 2013;77:907–922. [Google Scholar]
- 17.Wang D., Wang P. Understanding security failures of two-factor authentication schemes for real-time applications in hierarchical wireless sensor networks. Ad Hoc Netw. 2014;20:1–15. doi: 10.1016/j.adhoc.2014.03.003. [DOI] [Google Scholar]
- 18.Li C.-T., Weng C.-Y., Lee C.C. An advanced temporal credential-based security scheme with mutual authentication and key agreement for wireless sensor networks. Sensors. 2013;13:9589–9603. doi: 10.3390/s130809589. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 19.Xue K.P., Ma C.S., Hong P.L., Ding R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013;36:316–323. doi: 10.1016/j.jnca.2012.05.010. [DOI] [Google Scholar]
- 20.He D.B., Kumar N., Chilamkurti N. A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inform. Sci. 2015;321:263–277. doi: 10.1016/j.ins.2015.02.010. [DOI] [Google Scholar]
- 21.Turkanović M., Brumen B., Hölbl M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014;20:96–112. [Google Scholar]
- 22.Chang C.C., Le H.D. A provably secure, efficient, and flexible authentication scheme for ad hoc wireless sensor networks. IEEE Trans. Wirel. Commun. 2016;15:357–366. doi: 10.1109/TWC.2015.2473165. [DOI] [Google Scholar]
- 23.Farash M.S., Turkanović M., Kumari S., Hölbl M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016;36:152–176. doi: 10.1016/j.adhoc.2015.05.014. [DOI] [Google Scholar]
- 24.Amin R., Biswas G.P. A secure lightweight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw. 2015;20:1–23. [Google Scholar]
- 25.Cheng Z., Nistazakis M., Comley R., Vasiu L. On the in distinguishability-based security model of key agreement protocols-simple cases. IACR Cryptology ePrint Arch. 2005;2005:129. [Google Scholar]
- 26.Blake-Wilson S., Johnson D., Menezes A. Key agreement protocols and their security analysis; Proceedings of the Sixth IMA International Conference on Cryptography and Coding; Cirencester, UK. 17–19 December 1997. [Google Scholar]
- 27.Bonneau J. The science of guessing: Analyzing an anonymized corpus of 70 million passwords; Proceedings of the 33th IEEE Symposium on Security and Privacy (S&P 2012); San Francisco, CA, USA. 20–23 May 2012; pp. 538–552. [Google Scholar]
- 28.Dell’Amico M., Michiardi P., Roudier Y. Password strength: An empirical analysis; Proceedings of the 29th IEEE Conference on Computer Communications (INFOCOM 2010); San Diego, CA, USA. 14–19 March 2010; pp. 1–9. [Google Scholar]
- 29.Burrow M., Abadi M., Needham R. A logic of authentication. ACM Trans. Comput. Syst. 1990;8:18–36. doi: 10.1145/77648.77649. [DOI] [Google Scholar]
- 30.AVISPA, Automated Validation of Internet Security Protocols and Applications. [(accessed on 6 June 2016)]. Available online: http://www.avispa-project.org/
- 31.AVISPA, AVISPA Web Tool. [(accessed on 6 June 2016)]. Available online: http://www.avispa-project.org/web-interface/expert.php/
- 32.Dolev D., Yao A.C. On the Security of Public Key Protocols. IEEE Trans. Inform. Theory. 1983;29:198–208. doi: 10.1109/TIT.1983.1056650. [DOI] [Google Scholar]
- 33.Advanced Encryption Standard, FIPS PUB 197, National Institute of Standards and Technology (NIST), U.S. Department of Commerce. [(accessed on 6 June 2016)]; Available online: http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf.
- 34.SHA-3 Standardization NIST. [(accessed on 6 June 2016)]; Available online: http://csrc.nist.gov/groups/ST/hash/sha-3/sha-3-standardization.html.
- 35.Java Pairing Based Cryptography Library (JPBC) [(accessed on 6 June 2016)]. Available online: http://gas.dia.unisa.it/projects/jpbc.