Abstract
The Internet of Things (IoT) has made it possible for devices around the world to acquire information and store it, in order to be able to use it at a later stage. However, this potential opportunity is often not exploited because of the excessively big interval between the data collection and the capability to process and analyse it. In this paper, we review the current IoT technologies, approaches and models in order to discover what challenges need to be met to make more sense of data. The main goal of this paper is to review the surveys related to IoT in order to provide well integrated and context aware intelligent services for IoT. Moreover, we present a state-of-the-art of IoT from the context aware perspective that allows the integration of IoT and social networks in the emerging Social Internet of Things (SIoT) term.
Keywords: internet of things, big data, ontology, semantics, data mining with big data, services for big data, social internet of things, cloud computing
1. Introduction
There are no doubts about how rapidly technology has grown in the last decade. Nowadays, a wide variety of devices, including sensor-enabled smart devices, and all types of wearables, connect to the Internet and power newly connected applications and solutions. On the one hand, the cost of technology has sharply decreased, making it possible for everybody to engage in sensing data. On the other hand, in every area we need to access the Internet, which delivers an amount of real time information. Furthermore, some of the environments are just online, like social media, where all the information is in the Cloud. As a result, new words as well as new expressions have appeared such as Big Data [1,2], Cloud Computing [3] or Internet of Things (IoT) [4,5,6], among others.
With the recent advances in radio-frequency identification (RFID), low-cost wireless sensor devices, and Web technologies, the IoT approach has gained momentum in connecting everyday objects to the Internet and facilitating machine-to-human and machine-to-machine communication with the physical world.
According to the Gartner Research report on the IoT, billions of connected things are already in use in 2015 and that number will reach 25 billion in just a few short years [7]. In addition, we can appreciate how easily the data can be generated currently to create a huge amount of information (e.g., Smart Cities [8], Business Intelligence [9], IoT [10]), generating big data [11,12].
There are several definitions or visions of IoT from different perspectives. From the viewpoint of services provided by things, IoT means “a world where things can automatically communicate to computers and each other providing services to the benefit of the human kind” [13]. From the viewpoint of connectivity, IoT means “from anytime, anyplace connectivity for anyone, we will now have connectivity for anything” [14]. From the viewpoint of communication, IoT refers to “a world-wide network of interconnected objects uniquely addressable, based on standard communication protocols” [15]. Finally, from the viewpoint of networking, IoT is the Internet evolved “from a network of interconnected computers to a network of interconnected objects” [16].
As shown in Figure 1, data is processed differently in the IoT and traditional Internet environments (i.e., Internet of Computers). In the Internet of Computers, both main data producers and consumers are human beings. However, in the IoT, the main actors become things, which mean things are the majority of data producers and consumers. As pointed out by Ashton [10] IoT “has the potential to change the world, just as the Internet did”. Figure 1 shows the “things” able to generate data.
Figure 1.
Illustration of data acquisition equipment in IoT.
Although some reviews about IoT have been published recently (e.g., the most recent in [17]), they focus on high level general issues and are mostly fragmented. Therefore, the main objective of our paper is to carry out a complete survey of IoT, including the different types of technology for IoT; to review the previous surveys of IoT, including papers dealing with applications of IoT; and to indicate the number of services in order to incorporate context data to the information obtained both by sensors and/or created by the user (click worldwide) so as to enrich and give meaning to otherwise empty data.
The remainder of this paper is structured as follows: in the next section, the related work is reviewed. In particular, due to the number of surveys carried out, we establish classification criteria, which provide an index, facilitating easy access based on the key survey specifications. In the following section, we review the work on context aware computing in IoT applications. Thereafter, we explore the variety of services for the Internet of Things, including concepts such as data mining and big data in order to provide value and meaning to the simple data obtained by the IoT technology. Finally, we include a discussion with a summary of every section explaining our contribution to IoT.
2. Background on IoT Surveys
Given that some reviews of the IoT have been conducted recently, in this section the purpose is instead to perform a new survey, to summarize the most influential of reviews and work conducted recently in order to identify what are the shortcomings (if there are), the greatest opportunities and challenges that have not yet been addressed. In order to achieve this aim, we have grouped the IoT work in the following categories: general purpose IoT surveys, data oriented surveys, IoT vs. cloud computing surveys and IoT vs. data mining surveys. These categories are developed in the following subsections, which are concluded by a subsection that details potential IoT applications, and a final subsection that summarizes the open research issues for IoT.
2.1. General Purpose IoT Surveys
Diverse surveys give a picture of the current state of the art on the IoT. In general, they deal with issues of the basic features of IoT including architectures and technologies used. For example, Atzori et al. [6] provided the readers with a description of the different visions of the IoT paradigm coming from different scientific communities and reviews the enabling technologies and illustrates which are the major benefits of spread of this paradigm in everyday-life.
The work by [18] identifies the following key system-level features that IoT needs to support:
Devices heterogeneity supported at both architectural and protocol levels.
Scalability issues: (i) naming and addressing; (ii) data communication and networking; (iii) information and knowledge, and (iv) services provisioning and management.
Ubiquitous data exchange through proximity wireless technologies.
Energy-optimized solutions.
Localization and tracking capabilities: to track the location (and the movement) of smart objects in the physical realm.
Self-organization capabilities: making smart objects able to autonomously react to a wide range of different situations, in order to minimize human intervention.
Semantic interoperability and data management among different applications: it is necessary to provide data with adequate and standardized formats, models and semantic description of their content (meta-data), using well-defined languages and formats.
Embedded security and privacy-preserving mechanisms.
The survey in [19] reviews the three different phases with which the physical-cyber world interaction takes place: (i) collection phase (procedures for sensing the physical environment, collecting real-time physical data and reconstructing a general perception of it); (ii) transmission phase (mechanisms to deliver the collected data to applications and to different external servers); and (iii) process, management and utilization phase (by service-oriented architecture, cloud computing or peer-to-peer systems).
2.2. Surveys Oriented to Data
With regard to the characteristics of the data in IoT, surveys show the different types of data used and the main problems to be addressed related to them: generation, interoperability, storage, quality, and processing. The work in [20] presents five IoT technologies that are essential in the deployment of successful IoT-based products and services and discusses three IoT categories for enterprise applications used to enhance customer value. Because of the potential but uncertain benefits and high investment costs of the IoT, firms need to carefully assess every IoT-induced opportunity and challenge to ensure that their resources are spent judiciously. The authors of [21] study and discusses state-of-the-art techniques of IoT from the data-centric perspective.
A data stream, which is described in [21,22], is a sequence of data objects of which the number is potentially unbounded, continuously generated at a rapid rate. In the data stream, each data object can be described by a multi-dimensional attribute vector within a continuous, categorical, or mixed attribute space. In addition, there are some typical characteristics of data streams:
Continuous arrival of data objects.
Disordered arrival of data objects.
Potentially unbounded size of a stream.
Normally no persistence of data objects after being processed.
Changing probability distributions of the unknown data generation process.
In general data stream processing one of the challenging issues is power constraints. In a typical sensor data processing system, techniques, including data aggregation, data compression, modeling and online querying, should be performed on-site or in-network to reduce communication cost [23].
RDF [24] as a general method for conceptual description and its predominant query language, graphs SPARQL [25,26], are standard in IoT and very often have been referenced in many studies.
Linked Data is a method for publishing structured data and interlink such data to make it more useful with the purpose of extracting RDF triples from unstructured data streams. Although the current Linked Open Data (LOD) cloud has tremendously grown over the last few years, it delivers mostly encyclopedic information (such as albums, places, and kings) and fails to provide up-to-date information [27]. Based on such observation, they develop RdfLiveNews, an approach that allows extracting RDF from unstructured (i.e., textual) data streams in a fashion similar to the live versions of the DBpedia and LinkedGeoData datasets.
In Table 1, we can see a data taxonomy representation, by identifying the intrinsic characteristics of IoT data and classify them into three categories, including data generation, data quality, and data interoperability. This three categories described in [21] are summarized in this Table 1.
Table 1.
IoT Data Taxonomy.
| IoT Data Taxonomy | |
|---|---|
| Data Generation | |
| Velocity | Generated at different rates |
| Scalability | Large scale expectation |
| Dynamics | Mobile location, change Environments, connections intermittent. |
| Heterogeneity | Things generate data in different formats |
| Data Interoperability | |
| Incompleteness | Determine best data sources to address the incompleteness |
| Semantics | Injecting semantics into data is an initial step in IoT |
| Data Quality | |
| Uncertainty | Comes from different sources |
| Redundancy | Multiple measures |
| Ambiguity | Interpreted in different ways due to different data needs |
| Inconsistency | It can occur due: to missing readings, multiple sensors |
In [21], the authors address storage issues in large scale systems. An interesting discussion arises about the solutions on how to replicate data across globally distributed data centres. For instance the idea of replicating all data to all locations requires using huge amounts of resources since users from different locations may have different data consumption needs [28]. In order to satisfy exceptional requirements of data storage in IoT, the distributed storage systems are crucial. There are three factors or requirements to be considered when designing a distributed storage system [1] which are consistency, availability and partition tolerance.
The work in [21] reviews the state-of-the-art research in IoT focusing on data, involving the processing of data stream, management and modeling of data storage. They identify the intrinsic characteristics of IoT data and classify them into three categories, including data generation, data quality, and data interoperability (see Table 1). They also discuss data stream research efforts that can help handle IoT data, including general data stream processing (analysing power constraints challenges), RFID data stream processing (analysing high-rate data streams processing challenges), and RDF triple stream processing (analysing linked data challenges). with regard to issues about data storage models, they examine traditional database management systems (DBMSs) and data warehouses, in contrast to large-scale storage in distributed environments, especially due to the arrival of the big data era. Moreover, they also discusses state-of-the-art techniques in searching things in the IoT environments, both in keywords based search on the textual description of the object whose sensor is attached, and in the collaborative search of things (e.g., through the collaboration of mobile phones).
2.3. Surveys about the Integration of Cloud Computing and IoT
Due to the relationships between IoT and cloud computing, some surveys show the connections between them and how they benefit each other. As the work in [29] states, cloud computing and IoT are often referenced as synonymous words. This is probably because they are complementary as they need each other, creating the Cloud-IoT concept. IoT can benefit from the virtually unlimited capabilities and resources of clouds to compensate its technological constraints (e.g., storage, processing and communication). On the other hand, clouds can benefit from IoT by extending their scope to deal with real world things in a more distributed and dynamic manner, and for delivering new services in a large number of real life scenarios.
The authors in [30] also consider that the Cloud will be a sort of intermediate layer to make connections between smart objects and applications. The goal is to make an efficient use of data and all the resources that these objects provide. They review the integration of IoT and cloud computing paradigms; provide an overview of the current state of research on this topic; and identify important gaps in the existing approaches.
Similarly, the work in [31] highlights how the IoT is capable to produce rapidly vast quantity of heterogenous data when there are millions of smarts obejcts providing data to cloud computing. The authors show a survey of integration components that consists of platforms and infrastructures for the Cloud and IoT middleware.
2.4. Surveys Oriented to Data Mining
The analysis of the large amount of data generated by IoT is a crucial problem. For this reason, new approaches of data mining for this kind of data are being developed. The survey presented in [32] summarizes the features of data mining for IoT. The authors present the relationship between data mining, Knowledge Discovery in Databases (KDD) and big data for IoT. The different mining technologies for IoT are also discussed in that work. The first reflexion is that the data from IoT are mostly too big and too tricky to be processed by the tools available currently [33,34,35,36]. Baraniuk in [37] describes that the bottleneck of data processing will be shifted from sensor to the data processing, communication, and storage capability of sensor. This observation also implies that the design and implementation issues of information system will be changed because of IoT.
Obviously, it is always much easier to create data than to analyze it. The flood of data it is certainly a serious problem of IoT. KDD systems available today and most traditional mining algorithms cannot be applied directly in order to process the large amount of data of IoT. Likewise, data mining technologies that exist currently work properly when they are applied to small scale IoT system. Therefore KDD and data mining technologies need to be redesigned for IoT in order to deal with large amount of data. New framework is presented in [32] to understand data mining algorithms [38,39,40,41,42].
The survey of data stream clustering in [22] presents an overview focused on data stream mining. The main goal is to find patterns and knowledge from huge amounts of unceasingly generated data. They review, with a deep analysis, data stream clustering algorithms to carry out unsupervised learning. They present a section of data stream clustering in practice presenting applications, data repositories and software packages.
2.5. Potential IoT Applications
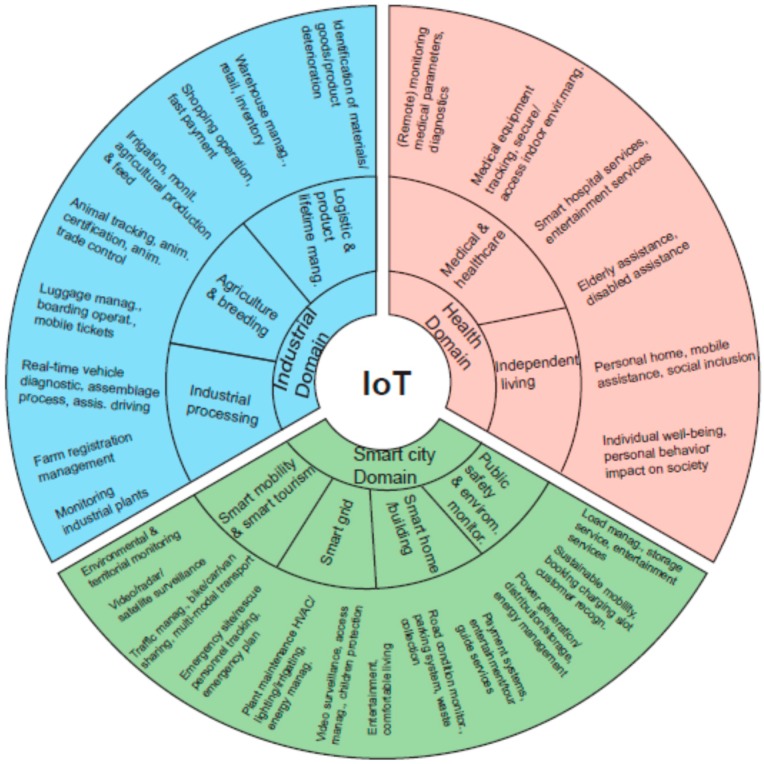
The huge potential of IoT is evident; therefore, many surveys have focused on IoT applications. From our point of view, we conclude that they could be divided into three big sets: smart city, industry and business, and health. The authors in [21] consider the following main groups of potential general IoT applications: smart cities and homes; environment monitoring; health; energy; business. In a similar way, the work in [6] groups these applications into the following domains: transportation and logistics domain; healthcare domain; smart environment (home, office, plant) domain; personal and social domain. In [43], the authors describe another IoT application: security and surveillance for enterprise buildings, shopping malls, factory floors, car parks and many other public places, as well as homeland security scenarios. The authors enumerate some specific applications such as the use of ambient sensors to monitor the presence of dangerous chemicals; sensors monitoring the behaviour of people may be used to assess the presence of people acting in a suspicious way; or personal identification by means of RFID or similar technologies. The work in [19] explores the IoT application domains and related applications is presented, where we can see a huge spectrum of application of IoT. Figure 2 shows the IoT application domains.
Figure 2.
IoT application domains.
The main contribution of the survey presented in [44] is to show the state-of-the-art IoT in industries. In its background and current research of IoT section, RFID technology is considered as a foundational technology for IoT. RFID technology has been possible to identify, track and monitor any objects attached with RFID tags automatically [45]. RFID has been widely used in many and diverse areas, such as logistics, pharmaceutical production, retailing and supply chain management, since 1980s [46]. Another basic technology, contribute to the development of IoT, is the wireless sensor networks (WSN). WSN use interconnected intelligent sensors to sense and monitoring. Similarly to RFID, its applications are developed in many areas including environmental monitoring, healthcare, industrial monitoring, traffic monitoring, etc. [47,48].
Apart from RFID and WSN, many other technologies and devices are available today, such as barcodes, smart phones, social networks, and cloud computing. All these technologies are being used to establish an extensive network for supporting IoT [49,50,51,52].
Figure 2 illustrates some application scenarios. There exist some common challenges apart from the specific domains, which are: security, privacy, data integrity, analytics, mobility support, heterogeneity of objects and scalability. In addition to these challenges, there are technology specific challenges such as architecture, energy efficiency and quality of service. More applications can be found in [53] where a model-based methodology for the development of IoT applications in WSN is presented providing the development tools and software component libraries to describe the high-level application architecture, graphical definition, etc.
In [20], the authors categorize the IoT enterprise applications in three groups: (1) monitoring and control (where the smart home is known to be at the forefront of innovation regarding IoT monitoring and control systems); (2) big data and business analytics (to discover changes in customer behaviors and market conditions, to increase customer satisfaction, and to provide value-added services to customers); (3) information sharing and collaboration.
As mentioned, the survey reported in [44] focuses on the interest of using IoT technologies in various industries, as IoT is expected to offer promising solutions to transform the operation and role of many existing industrial systems such as transportation systems and manufacturing systems. Specifically, they review the IoT interests in agriculture, food processing industry, environmental monitoring, security surveillance, logistics, manufacturing, retailing, and pharmaceutics industries. They classify these interests in the following groups:
IoT in the healthcare service industry: powered by IoT’s ubiquitous identification, sensing, and communication capacities, all objects in the healthcare systems (people, equipment, medicine, etc.) can be tracked and monitored constantly.
Using IoT in food supply chain (FSC) to address the traceability, visibility, and controllability challenges. The so-called food-IoT comprises three parts: (a) the field devices such as WSN nodes, RFID readers/tags, user interface terminals, etc.; (b) the backbone system such as databases, servers, and many kinds of terminals connected by distributed computer networks, etc.; and (c) the communication infrastructures such as WLAN, cellular, satellite, power line, Ethernet, etc. As the IoT system offers ubiquitous networking capacity, all of these elements can be distributed throughout the entire FSC. Other work related to this issue are [54,55,56].
IoT for safer mining production to sense mine disaster signals in order to make early warning, disaster forecasting, and safety improvement of underground production possible. For example, the effective communication between surface and underground in order to track the location of underground miners and analyze critical safety data collected from sensors to enhance safety measures. Another useful application is to use chemical and biological sensors for the early disease detection and diagnosis of underground miners, as they work in a hazardous environment.
Using IoT in transportation and logistics to conduct real-time monitoring of the move of physical objects from an origin to a destination across the entire supply chain including manufacturing, shipping, distribution, and so on. Furthermore, IoT is expected to offer promising solutions to transform transportation systems and automobile services.
IoT in firefighting to detect potential fire and provide early warning for possible fire disasters. By leveraging RFID tags, mobile RFID readers, intelligent video cameras, sensor networks, and wireless communication networks, the firefighting authority or related organizations could perform automatic diagnosis to realize real-time environmental monitoring.
In [57] they use IoT in the healthcare service industry. They insist on the importance of establishing an ecosystem in advance to take advantage optimally of opportunities. IoT provides new opportunities to improve healthcare [58]. Powered by IoT’s ubiquitous identification, sensing, and communication capacities, all objects in the healthcare systems (people, equipment, medicine, etc.) can be tracked and monitored constantly [59]. The healthcare-related information (logistics, diagnosis, therapy, recovery, medication, management, finance and even daily activity) can be collected, managed, and shared efficiently. The personal computing devices, such as laptop, mobile phone, tablet, wearables, etc. and mobile internet access (WiFi, optical fiber, 3G or 4G, LTE, etc.), the IoT-based healthcare services can be mobile and personalized [60]. They claim that since most societies are aging, IoT in the health sector could contribute to making elderly people’s lives easier.
There are other studies that focus in offering a framework for general applications. In the survey of Integration of cloud computing and Internet of Things [29], the authors explain that a cloud-based data access is able to cover the latency energy requirements of low power and the ubiquitous and fast access to data. In [61], the authors present the functional design and implementation of a complete WSN platform. The advantages of this proposal is not only the use for environmental monitoring IoT applications but also to take into account the requirements of design and specification such as low cost, high number of sensors, fast deployment, etc. The varied range of devices in IoT, with very heterogeneous capabilities whose response times are difficult to predict, are described in this work [62], which aims to respond to this issue by developing a computational model that formalizes the problem and that defines adjusting computing methods. The work presented in [62] describes the variety of devices in IoT. A computational model validate the problem in order to adjust computing methods.
In [63], López-Matencio proposes and studies a new node placement algorithm as this is a critical aspects of WSN design. The node placement determines sensing capacities, network connectivity, network lifetime and other capabilities of the WSN. WSNs are considered an enabling technology for unattended, long-lasting and rough terrain monitoring and have been widely studied in recent years [64] taking into account several considerations of design for optimization.
The authors of [65] present a computational architecture based on RFID Sensors. This study is applied to the traceability in smart cities. The aim of this distributed system is to obtain, represent and provide the flow and movement of people in densely populated geographical areas.
2.6. Open Research Issues for IoT
The general purpose surveys of IoT coincide in a set of open research issues for IoT, such as standardization, quality, security, or mobilization. For example, the survey by [6] enumerates the following: standardization, mobility support (e.g., scalability and adaptability to heterogeneous technologies), naming (i.e., mapping a reference to a description of a specific object), transport protocol, traffic characterization, authentication, data integrity, privacy and digital forgetting. The survey by [43], as a consequence of the previously described key system-level features that IoT needs to support, considers the following research challenges in IoT: computing, communication and identification technologies; distributed systems technology; distributed intelligence; security; data confidentiality; privacy; trust.
The work by [21] also discusses open research issues for IoT, but again focuses in data management issues. Specifically they enumerate the following issues: data quality and uncertainty (e.g., inconsistency detection); co-space data (e.g., to synchronize data in both real and virtual worlds); transaction handling (e.g., interaction between different networked computers/smart things with differing update policies); frequently updated timestamped structured (FUTS) data (e.g., real-time traffic reports, air pollution detection, temperature monitoring, and crops monitoring); distributed and mobile data (which makes IoT much more highly distributed and data intensive); semantic enrichment and semantic event processing (e.g., the progress of semantic Web to process and understand data through the semantic enrichment of sensing data); mining (e.g., the exploration and analysis of huge volume of IoT data); knowledge discovery (e.g., automatic extraction of relational facts from natural-language text and multi-modal contexts); security (e.g., RFID security); privacy (e.g., the lack of mechanisms to help people expose appropriate amounts of their identity information); social concerns (e.g., online social networks with personal things information may incur social concerns as well, such as disclosures of personal activities and hobbies).
Similarly, the survey reported in [44] focuses on research challenges for industrial use such as technology, standardization, security, and privacy. In particular, the authors consider as the main technical challenges: the design of a service-oriented architecture (SOA) for IoT (e.g., scalability issues, and situations in which service-based things might suffer from performance and cost limitations); to develop networking technologies and standards that can allow data gathered by a large number of devices to move efficiently within IoT networks; the lack of a commonly accepted service description language that facilitates the service development and integration of resources of physical objects into value-added services; the development of service discovery methods and object naming services; the integration of IoT with existing IT systems or legacy systems into a unified information infrastructure (e.g., the development of various middleware solutions in order to integrate IoT devices with external resources such as existing software systems and Web services); the development of green IoT technologies (e.g., energy-efficient techniques or approaches that can reduce the consumed power by sensors). Table 2 shows a summary of the different surveys studied along this section.
Table 2.
Summary of surveys.
| References | Description | Main Proposals |
|---|---|---|
| [6,18,19] | General purpose IoT surveys | General visions of IoT. Key features and the driver technologies of IoT. Phases and interaction with the physical-cyber world. |
| [10,20,22,23,24,25,26,27] | Surveys oriented to data | Technologies in IoT-based products. Techniques of IoT from the data perspective. Data stream and data stream processing. RDF and SPARQL as method for conceptual description and query language respectively in IoT. Extraction of RDF triples from unstructured data streams. |
| [29,30,31] | Surveys about the integration of Cloud computing and IoT | Cloud computing and IoT are different technologies, but are complementary. Cloud becomes an intermediate layer between smart objects and applications. Integration components: cloud platforms, cloud infrastructures and IoT middleware. |
| [22,32,33,34,35,36,37,38,39,40,41,42,66] | Surveys oriented to data mining | Relationships between data mining, KDD and big data for IoT. Processing of big data and sensor information. Data mining algorithms. Data stream clustering. |
| [6,19,20,21,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,67] | Potential IoT applications | General IoT applications: smart cities and homes, environment monitoring, health, energy, business. Classification according several domains: transportation and logistics, healthcare, smart environment (home, office, plant), personal and social. Security and surveillance. Huge spectrum of applications of IoT. IoT applications in industries. RFID technology, wireless sensor networks, barcodes, smart phones, social networks, and cloud computing. Food supply chain. Different devices (capabilities) in IoT. Architectures based on WSN and RFID. |
| [6,19,21,43,44] | Open research issues for IoT | Standardization, mobility support, naming, transport protocol, traffic characterization, authentication, data integrity, privacy and digital forgetting. Computing, communication and identification technologies, distributed systems technology, distributed intelligence, security, data confidentiality, privacy and trust. Data quality and uncertainty, co-space data, transaction handling, Frequently updated timestamped structured data, distributed and mobile data, semantic enrichment and semantic event processing, mining, knowledge discovery, security, privacy and social concerns. Challenges for industrial use: technology, standardization, security and privacy. IoT and social networks and IoT and context-aware computing. |
3. Context Aware IoT
Given the work reviewed in previous section about IoT surveys, in this section we explore the recent work developed on context aware intelligent services, in which the things in IoT dispose of enough intelligence to interact as social networks (as the capacities enumerated in [29]: self-configuration, self-optimization, self-protection, and self-healing). To the best of our knowledge, this is the first article that surveys the state-of-the-art of IoT from the context aware perspective that allows the integration of IoT and social networks in the emerging paradigm called Social IoT (SIoT) [68,69,70]. This section is concluded with the findings on this issue.
3.1. From Context Aware IoT to Social IoT
The context data add more meaning and value to the sensor data [71,72]. Borgia [19] highlights two IoT emerging research directions: IoT and social networks; and IoT and context-aware computing. The former reviews the interaction among smart objects following the social network paradigm. The main idea is that objects may have a social consciousness and may exhibit social behaviors allowing them to build their own social network of objects. This social network of objects can be exploited to enhance the trust level between objects that are “friends”, to guarantee a higher network navigability, and to make applications and services more efficient. Regarding the latter, the context awareness may provide a great support to process and store the big data, and to make their interpretation easier.
As the authors in [21] remark, they consider social concerns as a research challenge for IoT, specifically regarding the interaction of things in social networks. Likewise, Botta et al. [29] highlight the necessity of integrating social networking with IoT solutions, because they consider that there is a strong interest in using social networking to enhance communication among different IoT things. There is a trend for the move from IoT to a new vision named Web of Things that allows IoT objects to become active actors and peers on the Web.
The interpretation of SIoT in [73] attempts utilize users’ intuitive understanding of social networks to make the interconnected nature of IoT understandable and acceptable. In this line, the work in [74] makes use of an interactive IoT service on mobile devices. The concept of Social Web of Things (SWoT) is its foundation in order to do users capable of interacting with IoT in the same manner they use the social network services. As Rau et al. state, in SWoT, devices are presented as “beings” in social networks, with their interconnections compared to social relations. In addition, users can comment on the messages with natural language.
Atzori et al.’s work [75] identifies policies in order to establish as well as to manage social relationships to become a navigable social network. In addition, they describe an architecture for the IoT with the required functionalities of social network, and finally, they carry out simulations to study the characteristics of the SIoT network. The work in [76] introduces the idea of objects able to participate in conversations by discussing about the technology needed to guarantee an efficient interaction between the physical, social and virtual worlds. To ensure this interaction it is required the development of a data-centric architecture available for the people when and where they really require it.
Regarding the interconnections required between things, information retrieval (IR) techniques are introduced in the smart things. For example, Zhao et al. [77] propose an IR system based on topic discovery and semantic awareness in IoT environment. In this work and the one by [74], the state-of-the-art in IR for IoT is summarized. For example, the OCH system [78] allows users to query the current location of lost real-world objects; Dyser [79] is a search engine for the Web of Things, which allows real-world entities (i.e., people, places, and objects) to be searched by their current state; Snoogle [80] and Microsearch [81] are two systems that maintain an aggregate view of all sensors in a certain geographical area such as a room.
Context-aware approach is widely used for searching in IoT. For example, Covington et al. [82] proposed a role-based access control framework for context-aware applications. Giannikos and Kokoli [83] proposed and implemented a secure and context aware information lookup architecture for the IoT, which uses attributes to define access control policies, as well as, to semantically determine users and information items. In [84], the authors propose a context-aware service framework on top of IoT controlled systems, which is applied on the fault management process in electric power distribution networks. Their proposal takes automate actions depending on contextual information sensed from the IoT environment and received by the framework through its controlled systems. In [85], a context-aware and multi-service trust management system fitting the new requirements of the IoT is designed.
Information extraction (IE) is another artificial intelligence technique that is required for achieving the required high level of intelligence in things. For example in [77] proposal, the IE goal is to get metadata, such as the location and the topics, from the collected contents. These authors also use topic discovery tools to achieve topic self-adaptive retrieval, in which the theme information hidden in the texts is discovered and parsed out. Automatic classification and clustering for dividing the collected contents into two categories is also used in their approach: one category is the contents collected by topic focused collector (used to access data from predefined topic objects whose contents belong to a specific area) from topic websites or related IoT devices; the other category is the contents collected by general search engines-based collector (used to access general information on application-layer). Finally, natural language processing is an active research area used in this issue, which covers all the processing, understanding and interaction tasks [86,87,88,89].
3.2. Findings and Analysis on Context Aware IoT
After the reviewing of the work related on context aware IoT, next we summarize the main and open issues in this area:
There are two IoT emerging research directions: IoT and social networks; and IoT and context-aware computing.
The integration of IoT and social networks generates the emerging SIoT term.
There is a strong interest in using social networking to enhance communication among different IoT things.
There is a trend for the move from IoT to a new vision named Web of Things that allows IoT objects to become active actors and peers on the Web.
An agreed architecture is required, which includes the functionalities required to integrate things into a social network.
A further development of the technology is required to ensure an efficient interaction between the physical, social and virtual worlds by extending the Internet by means of interconnected objects.
Context-aware techniques are widely used for searching in IoT, such as information retrieval, information extraction and natural language processing techniques.
The main work reviewed in this section is summarized in Table 3.
Table 3.
Recent work on Context Aware IoT.
| Work | Discussion |
|---|---|
| Internet of things marries social media [73] | Utilize users׳ intuitive understanding of social networks to make the interconnected nature of IoT understandable and acceptable |
| Social web of things of Chinese users [74] | An interactive IoT service on mobile devices based upon the concept of SWoT |
| The social internet of things [75] | It identifies appropriate policies for the establishment and the management of social relationships between objects in such a way that the resulting social network is navigable. They describe an architecture for the IoT that includes the functionalities required to integrate things into a social network |
| Social-driven internet of connected objects [76] | It introduces the idea of objects able to participate in conversations, and discusses about the technology required to ensure an efficient interaction between the physical, social and virtual worlds. |
| Topic-centric and semantic-aware retrieval system [74,77] | An IR system based on topic discovery and semantic awareness in IoT environment |
| The OCH system [78] | It allows users to query the current location of lost real-world objects |
| Dyser [79] | It is a search engine for the Web of things, which allows real-world entities to be searched by their current state |
| Snoogle [80] and Microsearch [81] | Systems that maintain an aggregate view of all sensors in a certain geographical area such as a room |
| Covington et al. [82] | A role-based access control framework for context-aware applications |
| Secure and context-aware information lookup for the IoT [83] | A secure and context aware information lookup architecture for the IoT |
| A context-aware dispatcher for the IoT [84] | A context-aware service framework on top of IoT controlled systems, which is applied on the fault management process in electric power distribution networks |
| A context-aware and multi-service approach [85] | A context-aware and multi-service trust management system fitting the new requirements of the IoT |
| Topic-centric and semantic-aware retrieval system for IoT [77] | Information Extraction techniques are applied to get metadata, such as the location and the topics, from the collected contents |
| Natural Language Processing for IoT [86,87,88,89] | NLP techniques applied on the processing, understanding and interaction tasks |
4. Services for IoT
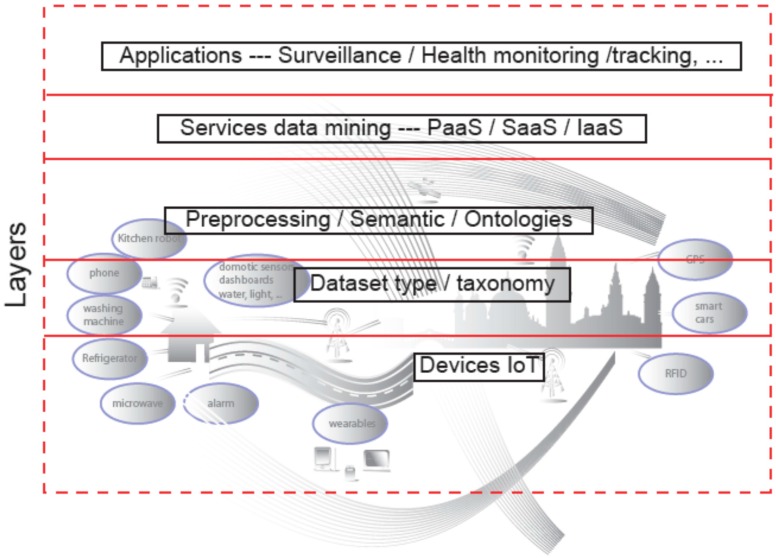
Figure 3 shows the overall scheme and layers of the combination of IoT deployments, Cloud Computing technologies and end-user applications. As it can be seen, it is based on Figure 1 and it includes the different layers than can be integrated as the services we will explain in this section.
Figure 3.
Overall architecture for IoT deployments and Applications.
As it has been shown in previous sections, there are a lot of surveys related to the IoT technologies. However, the contribution of the review presented in this section is the global as well as comprehensive vision where all the techniques are integrated in order to provide services to the final users. In addition, many of those services will be able to be used by the applications developed in many diverse areas, such as surveillance, health, etc. Many of these applications were also reviewed in the former section. The layers of the Figure represent different acting areas of the services that will be explained in the next sections.
4.1. Service-Oriented Architecture (SOA) of IoT
The decentralized and heterogeneous nature of IoT (IoT connects different things over the networks) requires that the architecture provides IoT efficient event-driven capability. As a key technology in integrating heterogeneous systems or devices, SOA can be applied to support IoT because it is appropriate method to achieve integrity and reliability among all the heterogeneous sources provided by multitude of devices [6,43,90]. SOA has been fruitfully settled in research areas such as cloud computing, WSNs and vehicular network [90,91,92]. In [44] it is explained how the International Telecommunication Union recommends that IoT architecture consists of five different layers: sensing, accessing, networking, middleware, and application layers. It is very suitability to represent SOA architecture by means of layers. Other studies suggest other number of layers. Jia et al. [45] and Domingo [58] propose to divide the IoT system architecture into three layers instead the former five layers. These are perception layer, network layer, and service layer (or application layer). Atzori et al. [6] established a three-layered architectural model for IoT which consists of the application layer, the network layer, and the sensing layer. Liu et al. [93] designed an IoT application foundation that comprises a four-layered SOA of IoT, physical layer, transport layer, middleware layer and applications layer.
4.2. Service Models for Big Data Generated by IoT
The data produced by interconnected devices which sensing and interacting capabilities with the environment can be analyzed through data strategies. Its possibilities and opportunities are now endless. Today, the significance of IoT is not only a lot of devices interconnected. It is that the data generated from these devices is analysed upon new big data techniques to provide new perspectives on the environment around us. These scenarios of big data analysis on IoT systems provide enriched information to understand the dynamics of IoT applications, assist decision-making and management.
However, some of the operating characteristics of the IoT applications represent a challenge for IoT analysis: in first place, the communication needs of the connected things; secondly, the scale deployment of IoT applications can be very large; and finally, the variety of information sources and large amount of data generated in many of its implementation scenarios (smart city, smart transport, retail and logistics, etc.). In these cases, the ability of performing real-time analytics are out of reach of many organizations with limited resources. Here is where service models for big data come into play. This idea consists on providing big data services over the Cloud [5]. Currently, more and more companies are exploring cloud computing opportunities, using resources only when and where needed, as a way to reduce the cost and complexity of their IT services [94].
The definition provided by Patidar et al. defines cloud computing as a type of computing in which massively scalable IT-related capabilities are provided “as a service” by using Internet technologies to multiple external customers [95]. In other words, cloud computing is an IT paradigm for offering internet services. The adoption of cloud computing services is characterized by the following features [96,97]: on demand service, QoS guaranteed offer, autonomous system and scalability.
In general terms, this technology paradigm can be deployed according three service models: software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS) [97,98]. Infrastructure as a service (IaaS) provides IT hardware to the organizations. These resources meet the end-user requirements in terms of memory, computing and storage; platform as a service (PaaS) offers a development platform where end-users can build their own applications in the Cloud. Normally, PaaS contracts are complemented with IaaS to create cloud solutions for companies; software as a service (SaaS) delivers software or applications across the Internet. The end-users do not need to install and run the application on their local computers.
4.3. Data as a Service
Data and information are the most valuable resources in today information society. There are new service models that have arisen to provide specific services on data to the end-users thought Internet. In these scenarios, the Cloud providers are responsible for protect and supply the data in an affordable manner. In this way, useful data can be supplied to users on demand.
The Cloud, combined with other key technologies, enables companies to radically change how they service consumers and run their business [99]. A first step towards adopting cloud services is to perform data storage through an IaaS model and ubiquitous data access with a SaaS model. This case is known as ‘data as a service’ (DaaS) and it means that the data from multiple sources in several formats can be accessible via Cloud services. Allowing the data to be stored in the Cloud and be accessed without geographical and scalability limitations will remove many bottlenecks in bringing data-oriented innovations. DaaS aims to overcome drawbacks on data storage and access from repositories.
There are two approaches for DaaS: (a) on one hand, the data are collected and stored into the cloud by a third party and are rented to the organizations to perform analysis, graphs, maps, etc. For example, the data produced by a network of IoT devices in a smart city environment is provided on the Cloud to organizations which analyze them to generate added-value services to the citizen and city administrators; (b) On the other hand, the organizations decouple their data from applications and store them on the Cloud to be accessible for whole processes, and even, offer it to other partners. For example, the data generated by an ERP about the habits of their customers can be sold to other companies for offering commercial proposals or targeting marketing campaigns.
Combinations of they both can exists according to the business models around data [100]. In addition, a new concept of ‘open data’ has emerged. This term defines new ways to share information, which involves more transparency and wider access to information [101]. In this way, typical DaaS providers support from generic data assets, such as Amazon Web Services [102] or Microsoft Azure Data Marketplace [103].
The new scenarios introduced by the IoT paradigm involve that the data could be generated by a huge amount of ‘things’ all the time (in a city environment for example: weather stations, traffic cameras, metering devices, smart urban furniture, street lights, etc.) [8].
This changed reality of distributed sensing devices and their working contexts raise new challenges on data processing that must be addressed [99,104,105]. This list is not exhaustive and singles out the issues related with IoT and meaning extraction: structuring, interoperability, portability, decoupling:
Structuring and classification: allows extracting meaningful content out of it and perform to make queries about it. In IoT scenarios, the data from sensors and other devices can be in an unstructured form. It is needed to define structures and protocols to add semantics such as tags, contextual info and other additional information.
Interoperability: improves the data utilization. Collecting data from multiple sources can cause compatibility problems. The data can be heterogeneous in content and fashion. The standardization plays a key role in transforming the data towards a common interface to enable portability and facilitate accessing to it and re-use of data assets across different applications. This normalization produces data that can be handled by different services, applications and users.
Decoupling data from applications: facilitates transparency, privacy and effectivity, and the developing of business models around the collected data. The data must be anonymized and decoupled from the sensing technology and its owner. For example, RFID tags on clothes.
Integration: enables the data assimilation from different sources. The data is combined into valuable information. This process can involve adapting data fields and/or dimensionality reduction. Large scale data sets can be created by acquiring data from many sources, for example, from a network of IoT devices deployed on a smart city.
Table 4 summarizes a list of recent work on these issues only from a data management point of view as a representative example of the intense research that is currently being done.
Table 4.
Recent work on issues for offering quality DaaS.
| Work | Discussion | Main Proposals |
|---|---|---|
| XCLOUDX [99] | Data structuring, management, data services | Cloud-assisted data model |
| DaaS [106] | Large data sets challenges; decoupling data location | DaaS approach for abstracting the data location; fully decouple the data |
| Potential of Data [101] | Open standards, interoperability | Best practices recommendations to enhance manageability, discovery, accessibility and usability |
| Open Data as Universal Service [101] | Open data, interoperability | New roles for data queries |
| Data services [107] | SOA architectures and Cloud computing for data processing | Conceptual framework for service oriented decision support systems |
| Data management in the Cloud [108] | Data management and data analysis in the Cloud | Parallel databases features for cloud data computing environments |
| Data as a Service Framework [109] | Integration, interoperability, data services | A framework for providing reusable enterprise data services |
| Demods [110] | Service and data discovery, data integration | Model for data-as-a-service |
| DaaS concerns [111] | Data services issues | Modelling concerns for DaaS. Evaluation of current Daas publishing |
| Data Integration [112] | Data services, interoperability, integration | Ontology-based framework for describing and integrating data |
| Privacy-Preserving DaaS [113] | Decoupling, privacy preserving, anonymization | A framework for privacy-preserving data-as-a-service |
| SOA data mashup [114] | Data services, privacy preserving, data integration | SOA architecture for high-dimensional private data mashup |
| Data integration [115] | Data integration, multidimensional data | Semantic foundation for multidimensional data integration, query operators and optimization |
In addition, there is work that specifically deals with sensing and IoT data acquisition issues. Table 5 describes an illustrative list of recent proposals.
Table 5.
Recent work on sensing and IoT data acquisition issues.
| Work | Discussion | Main proposals |
|---|---|---|
| Sensor Data as a Service [116] | Sensor network and service platforms | Sensor data federation as a service featuring interoperability, reusability and decoupling |
| Sensor Data Services Query [117] | Data structuring, sensor data services | Service model for query sensor data |
| DaaS IoT [118] | Data structuring, integration, dimensionality reduction, data services | Data-as-a-service framework for IoT |
| Service model for smart cities [8] | Service model, data services, data acquisition, privacy preservation, decoupling | Model for sensing as a service supported by Internet of Things |
| CityWatch [119] | Sensor data, data acquisition, interoperability, integration | Data sensing and sensor dissemination framework |
| IoT Data distribution [120] | Data acquisition, interoperability, integration | Data framework to distribute context data |
| IoT Cloud Computing [29] | Integration, data Interoperability, structuring, large scale, interoperability | Analyssis of cloud IoT paradigm and identify the open issues and future directions in this field |
| Data Analysis as a Service [121] | Data acquisition, integration, interoperability | Infrastructure for storing and analyzing data from the Internet of Things |
Other challenges related with pricing the data, security of the data, data governance, and management of the services are also important issues in order to provide a quality data as a service.
4.4. Service Models of Data Mining with Big Data
In this section, we examine the different techniques and methods to be able to carry out experiment with the taxonomy of the IoT dataset. There are several initiatives that explore this objective [122,123,124,125,126]. After the study of those approaches, the idea is to offer services of data mining with all the data generated by IoT.
Table 6 includes a selection of the most common and employed programs for data mining and machine learning. Some of the software of the table is more advanced in the big data technologies than others, but all of them have approaches in order to deal with it. However, as will be explained later, data mining for big data (generated basically by IoT) is an outstanding issue and a big challenge for all the current technologies which are investing a lot of resources to deal with it.
Table 6.
Data Mining for IoT.
| Work | Name | Description |
|---|---|---|
| [127,128] | R | Open source programming language and software environment, is designed for data mining/analysis and visualization. It is used for data exploration, statistical analysis, and drawing plots. |
| [40,123,129,130] | Weka | Weka is a free and open-source machine learning and datamining software written in Java. Weka provides such functions as data processing, feature selection, classification, regression, clustering, association rule, and visualization, etc. |
| [131] | Rapid-I Rapidminer | Rapidminer is an open source software used for data mining, machine learning, and predictive analysis. Data mining and machine learning programs provided by RapidMiner include Extract, Transform and Load (ETL), data pre-processing and visualization, modeling, evaluation, and deployment. |
| [132] | KNMINE | It is a user-friendly, intelligent, and open-source-rich data integration, data processing, data analysis, and data mining platform. |
Although many devices are mainly capable of generating data, some of the latest studies indicate that most of the things of IoT are supposed to have intelligence, thus are called “smart objects” (SO) and are assumed capable of being identified, sensing events, interacting with others, and making decisions by themselves [43,133,134,135]. One of the questions which arises in this survey is how do we convert the data generated or captured by IoT into knowledge. This is where KDD and data mining technologies come into play to find out the information hidden in the data of IoT. For this task a lot of researches have been using or developing effective data mining technologies for the IoT. The results described in [34,136,137,138] show that data mining algorithms can be used to make IoT more intelligent, thus providing smarter services.
4.5. Findings and Analysis on Services for IoT
After we have reviewed the services offered by IoT, here we present the opportunities and challenges:
The data generated from the different devices are analysed with new big data techniques to make easier the decision-making process. Data mining (DM) and machine learning (ML) techniques can be used.
Real-time analytics is possible through big data services over the Cloud.
The data are generated by a huge amount of ‘things’ all the time (in a city environment for example: weather stations, traffic cameras, metering devices, smart urban furniture, street lights, etc.). Depending on their characteristics, different techniques will be used: (1) natural language processing techniques (for example information extraction or question answering) to extract relevant information from textual unstructured information; (2) DM and ML techniques to make predictions about collected data; (3) Visualization techniques (dashboards or Google Analytics) to view graphically the data in order to facilitate the decision-making process.
Data from multiple sources in several formats are accessible via cloud services (data as a service, DaaS). The data are collected and stored into the Cloud and can be used/rented by other organizations to perform analysis, graphs, maps, etc.
Integration of information. It is a big challenge. The major idea is to integrate structured and unstructured information from different sources. Moreover, general/domain ontologies and reasoning techniques to match equivalent concepts among all the collected information can be used.
5. Conclusions
There are a considerable number of reviews about IoT and so far most of them have been conducted focusing on high level general issues. Furthermore, these articles do not specifically cover techniques on data processing and management, which is fundamentally critical to fully embrace IoT. In this paper, we have presented a systematic review of the diverse surveys of IoT. The huge volume of surveys that appear in the literature makes it easy to obtain a general picture of the current state of the art on the IoT but it is more difficult to discover the more promising parts of IoT, which is the key to succeeding when making a decision on IoT.
We review the current IoT technologies, approaches and models in order to discover what opportunities and challenges need to be met to make more sense of data. The revision of the available surveys in order to provide well integrated and context aware intelligent services for IoT has been carried out. Moreover, we propose an exhaustive state-of-the-art of IoT from the context aware perspective that allows the integration of IoT and social networks in the emerging social internet of things (SIoT) term, in which the things in IoT dispose of enough intelligence to interact as social networks. To the best of our knowledge, this is the first article that surveys the state-of-the-art of IoT from the context aware perspective that includes SIoT.
Finally, the diverse variety of services for IoT has been described. An overview and particular description of each service is has been developed concluding with a summary of those services and their opportunities.
This new field offers a lot of research challenges, but the main goal of this line of research is to make sense of data in any IoT environment. It has been pointed out that it is always much easier to create data than to analyze them. With this in mind, new conceptual modelling, (provided by ontologies, semantic, etc.) as well as new paradigms of data mining techniques, will be crucial to provide value and meaning to initially empty data.
Acknowledgments
This work has been partially funded by the Spanish Ministry of Economy and Competitiveness (MINECO/FEDER) under the granted Project SEQUOIA-UA (Management requirements and methodology for Big Data analytics) TIN2015-63502-C3-3-R, by the University of Alicante, within the program of support for research, under project GRE14-10, and by the Conselleria de Educación, Investigación, Cultura y Deporte, Comunidad Valenciana, Spain, within the program of support for research, under project GV/2016/087. This work has also been partially funded by projects from the Spanish Ministry of Education and Competitivity TIN2015-65100-R and DIIM2.0 (PROMETEOII/2014/001).
Author Contributions
All the authors wrote the paper and read and approved the final manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Chen M., Mao S., Liu Y. Big data: A survey. Mob. Netw. Appl. 2014;19:171–209. doi: 10.1007/s11036-013-0489-0. [DOI] [Google Scholar]
- 2.Sagiroglu S., Sinanc D. Big data: A review; Proceedings of the 2013 International Conference on Collaboration Technologies and Systems (CTS); San Diego, CA, USA. 20–24 May 2013; pp. 42–47. [Google Scholar]
- 3.Armbrust M., Fox A., Griffith R., Joseph A.D., Katz R., Konwinski A., Lee G., Patterson D., Rabkin A., Stoica I. A view of cloud computing. Commun. ACM. 2010;53:50–58. doi: 10.1145/1721654.1721672. [DOI] [Google Scholar]
- 4.Sundmaeker H., Guillemin P., Friess P., Woelfflé S. Vision and Challenges for Realising the Internet of Things. European Commission; Brussels, Belgium: 2010. [Google Scholar]
- 5.Zaslavsky A., Perera C., Georgakopoulos D. Sensing as a Service and Big Data; Proceedings of the International Conference on Advances in Cloud Computing (ACC); Bangalore, India. 26–28 July 2012. [Google Scholar]
- 6.Atzori L., Iera A., Morabito G. The internet of things: A survey. Comput. Netw. 2010;54:2787–2805. doi: 10.1016/j.comnet.2010.05.010. [DOI] [Google Scholar]
- 7.Middleton P., Kjeldsen P., Tully J. Forecast: The Internet of Things, Worldwide, 2013. Gartner; Stamford, CT, USA: Nov 18, 2013. [Google Scholar]
- 8.Perera C., Zaslavsky A., Christen P., Georgakopoulos D. Sensing as a service model for smart cities supported by internet of things. Trans. Emerg. Telecommun. Technol. 2014;25:81–93. doi: 10.1002/ett.2704. [DOI] [Google Scholar]
- 9.Chen H., Chiang R.H.L., Storey V.C. Business Intelligence and Analytics: From Big Data to Big Impact. MIS Q. 2012;36:1165–1188. [Google Scholar]
- 10.Ashton K. That ‘internet of things’ thing. RFiD J. 2009;22:97–114. [Google Scholar]
- 11.Manyika J., Chui M., Brown B., Bughin J., Dobbs R., Roxburgh C., Byer A.H. Big Data: The Next Frontier for Innovation, Competition, and Productivity. [(accessed on 11 July 2016)]. Available online: http://www.mckinsey.com/business-functions/business-technology/our-insights/big-data-the-next-frontier-for-innovation.
- 12.Labrinidis A., Jagadish H.V. Challenges and opportunities with big data. Proc. VLDB Endow. 2012;5:2032–2033. doi: 10.14778/2367502.2367572. [DOI] [Google Scholar]
- 13.Furness A. A Framework Model for the Internet of Things. GRIFS/CASAGRAS; Hong Kong, China: 2008. [Google Scholar]
- 14.International Telecommunication Union (ITU) Internet Reports 2005 “The Internet of Things”. [(accessed on 11 July 2016)]. Available online: https://www.itu.int/net/wsis/tunis/newsroom/stats/The-Internet-of-Things-2005.pdf.
- 15.INFSO D. 4 Networked Enterprise & RFID INFSO G. 2 Micro & Nanosystems, in Co-operation with the Working Group RFID of the ETP EPoSS. Internet of Things in 2020: A Roadmap for the Future. [(accessed on 11 July 2016)]. Available online: http://www.smart-systems-integration.org/public/documents/publications/Internet-of-Things_in_2020_EC-EPoSS_Workshop_Report_2008_v3.pdf.
- 16.De Saint-Exupery A. Internet of Things, Strategic Research Roadmap. European Commission Social Media; Brussels, Belgium: 2009. [Google Scholar]
- 17.Li S., Xu-Da L., Zhao S. The internet of things: A survey. Inf. Syst. Front. 2015;17:243–259. doi: 10.1007/s10796-014-9492-7. [DOI] [Google Scholar]
- 18.Jain A.K., Murty M.N., Flynn P.J. Data clustering: A review. ACM Comput. Surv. 1999;31:264–323. doi: 10.1145/331499.331504. [DOI] [Google Scholar]
- 19.Borgia E. The Internet of Things vision: Key features, applications and open issues. Comput. Commun. 2014;54:1–31. doi: 10.1016/j.comcom.2014.09.008. [DOI] [Google Scholar]
- 20.Lee I., Lee K. The Internet of Things (IoT): Applications, investments, and challenges for enterprises. Bus. Horiz. 2015;58:431–440. doi: 10.1016/j.bushor.2015.03.008. [DOI] [Google Scholar]
- 21.Qin Y., Sheng Q.Z., Falkner N.J., Dustdar S., Wang H., Vasilakos A.V. When things matter: A survey on data-centric internet of things. J. Netw. Comput. Appl. 2016;64:137–153. doi: 10.1016/j.jnca.2015.12.016. [DOI] [Google Scholar]
- 22.Silva J., Faria E., Barros R. Data stream clustering: A survey. ACM Comput. Surv. 2013;46:13. doi: 10.1145/2522968.2522981. [DOI] [Google Scholar]
- 23.Subramaniam S., Gunopulos D. Data Streams. Springer US; New York, NY, USA: 2007. A survey of stream processing problems and techniques in sensor networks. [Google Scholar]
- 24.Klyne G., Carroll J. Resource Description Framework (RDF): Concepts and Abstract Syntax. W3C; Cambridge, MA, USA: 2006. [Google Scholar]
- 25.Prud’Hommeaux E., Seaborne A. SPARQL Query Language for RDF. W3C; Cambridge, MA, USA: 2008. [Google Scholar]
- 26.Quilitz B., Leser U. Querying Distributed RDF Data Sources with SPARQL. Springer; Berlin, Germany: 2008. [Google Scholar]
- 27.Gerber D., Hellmann S., Bühmann L., Soru T., Usbeck R., Ngomo A.C.N. The Semantic Web–ISWC 2013. Springer; Berlin, Germany: 2013. Real-time rdf extraction from unstructured data streams; pp. 135–150. [Google Scholar]
- 28.Kadambi S., Chen J., Cooper B.F., Lomax D., Ramakrishnan R., Silberstein A., Tam E., García-Molina H. Where in the world is my data; Proceedings of the 37th International Conference on Very Large Data Bases; Seattle, WA, USA. 29 August–3 September 2011. [Google Scholar]
- 29.Botta A., de Donato W., Persico V., Pescapé A. Integration of cloud computing and internet of things: A survey. Future Gener. Comput. Syst. 2016;56:684–700. doi: 10.1016/j.future.2015.09.021. [DOI] [Google Scholar]
- 30.Cavalcante E., Pereira J., Alves M.P., Maia P., Moura R., Batista T., Delicato F.C., Pires P.F. On the interplay of Internet of Things and Cloud Computing: A systematic mapping study. Comput. Commun. 2016;89–90:17–33. doi: 10.1016/j.comcom.2016.03.012. [DOI] [Google Scholar]
- 31.Díaz M., Martín C., Rubio B. State-of-the-art, challenges, and open issues in the integration of Internet of things and cloud computing. J. Netw. Comput. Appl. 2016;67:99–117. doi: 10.1016/j.jnca.2016.01.010. [DOI] [Google Scholar]
- 32.Tsai C.-W., Lai C.-F., Chiang M.-C., Yang L.T. Data mining for internet of things: A survey. Commun. Surv. Tutor. IEEE. 2014;16:77–97. doi: 10.1109/SURV.2013.103013.00206. [DOI] [Google Scholar]
- 33.Bandyopadhyay D., Sen J. Internet of things: Applications and challenges in technology and standardization. Wirel. Pers. Commun. 2011;58:49–69. doi: 10.1007/s11277-011-0288-5. [DOI] [Google Scholar]
- 34.Cantoni V., Lombardi L., Lombardi P. Challenges for data mining in distributed sensor networks; Proceedings of the 18th International Conference on Pattern Recognition, ICPR; Hong Kong, China. 20–24 August 2006; pp. 1000–1007. [Google Scholar]
- 35.Madden S. From databases to big data. IEEE Internet Comput. 2012;3:4–6. doi: 10.1109/MIC.2012.50. [DOI] [Google Scholar]
- 36.Chen Y.K. Challenges and opportunities of internet of things; Proceedings of the 17th Asia and South Pacific Design Automation Conference (ASP-DAC); Sydney, Australia. 30 January–2 February 2012; pp. 383–388. [Google Scholar]
- 37.Baraniuk R.G. More is less: Signal processing and the data deluge. Science. 2011;331:717–719. doi: 10.1126/science.1197448. [DOI] [PubMed] [Google Scholar]
- 38.Xu R., Wunsch D. Survey of clustering algorithms. Neural Netw. IEEE Trans. 2005;16:645–678. doi: 10.1109/TNN.2005.845141. [DOI] [PubMed] [Google Scholar]
- 39.Han J., Kamber M., Pei J. Data Mining: Concepts and Techniques. Elsevier; Amsterdam, The Netherlands: 2011. [Google Scholar]
- 40.Witten I.H., Frank E. Data Mining: Practical Machine Learning Tools and Techniques. Morgan Kaufmann; San Fransisco, CA, USA: 2005. [Google Scholar]
- 41.Liu B. Web Data Mining: Exploring Hyperlinks, Contents, and Usage Data. Springer Science & Business Media; Boston, MA, USA: 2007. [Google Scholar]
- 42.Wu X., Kumar V., Quinlan J.R., Ghosh J., Yang Q., Motoda H., McLachlan G.J., Ng A., Liu B., Philip S.Y., Zhi-Hua Z., Steinbach M., Hand D.J., Steinberg D. Top 10 algorithms in data mining. Knowl. Inf. Syst. 2008;14:1–37. doi: 10.1007/s10115-007-0114-2. [DOI] [Google Scholar]
- 43.Miorandi D., Sicari S., de Pellegrini F., Chlamtac I. Internet of things: Vision, applications and research challenges. Ad Hoc Netw. 2012;10:1497–1516. doi: 10.1016/j.adhoc.2012.02.016. [DOI] [Google Scholar]
- 44.Da-Xu L., He W., Li S. Internet of things in industries: A survey. Ind. Inform. IEEE Trans. 2014;10:2233–2243. [Google Scholar]
- 45.Jia X., Feng Q., Fan T., Lei Q. RFID technology and its applications in Internet of Things (IoT); Proceedings of the 2nd International Conference on Consumer Electronics, Communications and Networks (CECNet); Yichang, China. 21–23 April 2012; pp. 1282–1285. [Google Scholar]
- 46.Ngai E., Moon K. RFID research: An academic literature review (1995–2005) and future research directions. Int. J. Prod. Econ. 2008;112:510–520. doi: 10.1016/j.ijpe.2007.05.004. [DOI] [Google Scholar]
- 47.Li S., Da-Xu L., Wang X. Compressed sensing signal and data acquisition in wireless sensor networks and internet of things. Ind. Inform. IEEE Trans. 2013;9:2177–2186. doi: 10.1109/TII.2012.2189222. [DOI] [Google Scholar]
- 48.He W., Da-Xu L. Integration of distributed enterprise applications: A survey. Ind. Inform. IEEE Trans. 2014;10:35–42. doi: 10.1109/TII.2012.2189221. [DOI] [Google Scholar]
- 49.Uckelmann D., Harrison M., Michahelles F. An Architectural Approach towards the Future Internet of Things. Springer; Berlin, Germany: 2011. [Google Scholar]
- 50.Li S., Xu L., Wang X., Wang J. Integration of hybrid wireless networks in cloud services oriented enterprise information systems. Enterp. Inf. Syst. 2012;6:165–187. doi: 10.1080/17517575.2011.654266. [DOI] [Google Scholar]
- 51.Wang L., Da-Xu L., Bi Z., Xu Y. Data cleaning for RFID and WSN integration. Ind. Inform. IEEE Trans. 2014;10:408–418. doi: 10.1109/TII.2013.2250510. [DOI] [Google Scholar]
- 52.Li Q., Wang Z.Y., Li W.H., Li J., Wang C., Du R.Y. Applications integration in a hybrid cloud computing environment: Modelling and platform. Enterp. Inf. Syst. 2013;7:237–271. doi: 10.1080/17517575.2012.677479. [DOI] [Google Scholar]
- 53.Song Z., Lazarescu M.T., Tomasi R., Lavagno L., Spirito M.A. Internet of Things. Springer International Publishing; Madrid, Spain: 2014. High-Level Internet of Things Applications Development Using Wireless Sensor Networks; pp. 75–109. [Google Scholar]
- 54.Pang Z., Chen Q., Han W., Zheng L. Value-centric design of the internet-of-things solution for food supply chain: Value creation, sensor portfolio and information fusion. Inf. Syst. Front. 2015;17:289–319. doi: 10.1007/s10796-012-9374-9. [DOI] [Google Scholar]
- 55.Dada A., Thiesse F. The Internet of Things. Springer; Berlin, Germany: 2008. Sensor applications in the supply chain: The example of quality-based issuing of perishables; pp. 140–154. [Google Scholar]
- 56.Ilic A., Staake T., Fleisch E. Using sensor information to reduce the carbon footprint of perishable goods. IEEE Pervasive Comput. 2009;1:22–29. doi: 10.1109/MPRV.2009.20. [DOI] [Google Scholar]
- 57.Pang Z., Chen Q., Tian J. Ecosystem analysis in the design of open platform-based in-home healthcare terminals towards the internet-of-things; Proceedings of the 15th International Conference on Advanced Communication Technology (ICACT); PyeongChang, Korea. 27–30 January 2013. [Google Scholar]
- 58.Domingo M.C. An overview of the Internet of Things for people with disabilities. J. Netw. Comput. Appl. 2012;35:584–596. doi: 10.1016/j.jnca.2011.10.015. [DOI] [Google Scholar]
- 59.Alemdar H., Ersoy C. Wireless sensor networks for healthcare: A survey. Comput. Netw. 2010;54:2688–2710. doi: 10.1016/j.comnet.2010.05.003. [DOI] [Google Scholar]
- 60.Plaza I., Martín L., Martin S., Medrano C. Mobile applications in an aging society: Status and trends. J. Syst. Softw. 2011;84:1977–1988. doi: 10.1016/j.jss.2011.05.035. [DOI] [Google Scholar]
- 61.Lazarescu M.T. Design of a WSN platform for long-term environmental monitoring for IoT applications. IEEE J. Emerg. Sel. Top. Circuits Syst. 2013;31:45–54. doi: 10.1109/JETCAS.2013.2243032. [DOI] [Google Scholar]
- 62.Mora H.M., Gil D., López J.F.C., Pont M.T.S. Flexible Framework for Real-Time Embedded Systems Based on Mobile Cloud Computing Paradigm. Mob. Inf. Syst. 2015;2015:1–14. doi: 10.1155/2015/652462. [DOI] [Google Scholar]
- 63.López-Matencio P. An ACOR-Based Multi-Objective WSN Deployment Example for Lunar Surveying. Sensors. 2016;16 doi: 10.3390/s16020209. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 64.Lazarescu M.T. Design and Field Test of a WSN Platform Prototype for Long-Term Environmental Monitoring. Sensors. 2015;15:9481–9518. doi: 10.3390/s150409481. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 65.Mora-Mora H., Gilart-Iglesias V., Gil D., Sirvent-Llamas A. A Computational Architecture Based on RFID Sensors for Traceability in Smart Cities. Sensors. 2015;15:13591–13626. doi: 10.3390/s150613591. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 66.Perera C., Zaslavsky A., Christen P., Georgakopoulos D. Context aware computing for the internet of things: A survey. IEEE Commun. Surv. Tutor. 2014;16:414–454. doi: 10.1109/SURV.2013.042313.00197. [DOI] [Google Scholar]
- 67.Tao F., LaiLi Y., Xu L., Zhang L. FC-PACO-RM: A parallel method for service composition optimal-selection in cloud manufacturing system. IEEE Trans. Ind. Inform. 2013;9:2023–2033. doi: 10.1109/TII.2012.2232936. [DOI] [Google Scholar]
- 68.Atzori L., Iera A., Morabito G. SIoT: Giving a social structure to the internet of things. IEEE Commun. Lett. 2011;15:1193–1195. doi: 10.1109/LCOMM.2011.090911.111340. [DOI] [Google Scholar]
- 69.Atzori L., Carboni D., Iera A. Smart things in the social loop: Paradigms, technologies, and potentials. Ad Hoc Netw. 2014;18:121–132. doi: 10.1016/j.adhoc.2013.03.012. [DOI] [Google Scholar]
- 70.Mashal I., Alsaryrah O., Chung T.Y., Yang C.Z., Kuo W.H., Agrawal D. Choices for interaction with things on Internet and underlying issues. Ad Hoc Netw. 2015;28:68–90. doi: 10.1016/j.adhoc.2014.12.006. [DOI] [Google Scholar]
- 71.Zhou M., Zhang R., Zeng D., Qian W. Services in the cloud computing era: A survey; Proceedings of the 4th International Universal Communication Symposium (IUCS); Beijing, China. 18–19 October 2010; pp. 40–46. [Google Scholar]
- 72.Calbimonte J.P., Jeung H., Corcho O., Aberer K. Semantic Sensor Data Search in a Large-Scale Federated Sensor Network; Proceedings of the 4th International Conference on Semantic Sensor Networks. CEUR-WS; Bonn, Germany. 23–27 October 2011; pp. 23–38. [Google Scholar]
- 73.Formo J., Laaksolahti J., Gårdman M. Internet of things marries social media; Proceedings of the 13th International Conference on Human Computer Interaction with Mobile Devices and Services; Stockholm, Sweden. 30 August–2 September 2011; pp. 753–755. [Google Scholar]
- 74.Rau P.L.P., Huang E., Mao M., Gao Q., Feng C., Zhang Y. Exploring interactive style and user experience design for social web of things of Chinese users: A case study in Beijing. Int. J. Hum. Comput. Stud. 2015;80:24–35. doi: 10.1016/j.ijhcs.2015.02.007. [DOI] [Google Scholar]
- 75.Atzori L., Iera A., Morabito G., Nitti M. The social internet of things (siot)–when social networks meet the internet of things: Concept, architecture and network characterization. Comput. Netw. 2012;56:3594–3608. doi: 10.1016/j.comnet.2012.07.010. [DOI] [Google Scholar]
- 76.Mendes P. Social-driven internet of connected objects; Proceedings of the Interconnecting Smart Objects with the Internet Workshop; Prague, Czech Republic. 25 March 2011; pp. 1–3. [Google Scholar]
- 77.Zhao F., Sun Z., Jin H. Topic-centric and semantic-aware retrieval system for internet of things. Inf. Fusion. 2015;23:33–42. doi: 10.1016/j.inffus.2014.01.001. [DOI] [Google Scholar]
- 78.Frank C., Bolliger P., Mattern F., Kellerer W. The sensor internet at work: Locating everyday items using mobile phones. Pervasive Mob. Comput. 2008;4:421–447. doi: 10.1016/j.pmcj.2007.12.002. [DOI] [Google Scholar]
- 79.Römer K., Ostermaier B. Real-time search for real-world entities: A survey. Proc. IEEE. 2010;98:1887–1902. doi: 10.1109/JPROC.2010.2062470. [DOI] [Google Scholar]
- 80.Wang H., Tan C., Li Q. Snoogle: A search engine for pervasive environments. IEEE Trans. Parallel Distrib. Syst. 2010;21:1188–1202. doi: 10.1109/TPDS.2009.145. [DOI] [Google Scholar]
- 81.Tan C., Sheng B., Wang H., Li Q. Microsearch: A search engine for embedded devices used in pervasive computing. ACM Trans. Embed. Comput. Syst. 2010;9:43. doi: 10.1145/1721695.1721709. [DOI] [Google Scholar]
- 82.Covington M.J., Long W., Srinivasan S., Dev A.K., Ahamad M., Abowd G.D. Securing context-aware applications using environment roles; Proceedings of the Sixth ACM Symposium on Access Control Models and Technologies; Chantilly, VA, USA. 3–4 May 2001; pp. 10–20. [Google Scholar]
- 83.Giannikos M., Kokoli K., Fotiou N., Marias G.F., Polyzos G.C. Towards secure and context-aware information lookup for the Internet of Things; Proceedings of the 2013 International Conference on Computing, Networking and Communications (ICNC); San Diego, CA, USA. 28–31 January 2013. [Google Scholar]
- 84.Amin S., Ali-Eldin A., Ali H. A context-aware dispatcher for the Internet of Things: The case of electric power distribution systems. Comput. Electr. Eng. 2015;52:183–198. doi: 10.1016/j.compeleceng.2015.05.012. [DOI] [Google Scholar]
- 85.Saied Y., Olivereau A., Zeghlache D., Laurent M. Trust management system design for the internet of things: A context-aware and multi-service approach. Comput. Secur. 2013;39:351–365. doi: 10.1016/j.cose.2013.09.001. [DOI] [Google Scholar]
- 86.Zhang C., Cheng C., Ji Y. Architecture design for social web of things; Proceedings of the 1st International Workshop on Context Discovery and Data Mining; Beijing, China. 12–16 August 2012. [Google Scholar]
- 87.Pintus A., Carboni D., Piras A. Paraimpu: A platform for a social web of things; Proceedings of the 21st International Conference on World Wide Web; Lyon, France. 16–20 April 2012; pp. 401–404. [Google Scholar]
- 88.Guinard D., Fischer M., Trifa V. Sharing using social networks in a composable web of things; Proceedings of the 8th IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOM Workshops); Mannheim, Germany. 29 March–2 April 2010; pp. 702–707. [Google Scholar]
- 89.Chung T.Y., Mashal I., Alsaryrah O., Chang C.H., Hsu T.H., Li P.S., Kuo W.H. MUL-SWoT: A Social Web of Things Platform for Internet of Things Application Development; Proceedings of the 2014 IEEE International Conference on Internet Things (iThings) and IEEE Cyber, Physical Social Computing (CPSCom) Green Computing Communication (GreenCom); Taipei, Taiwan. 1–3 September 2014. [Google Scholar]
- 90.Da-Xu L. Enterprise systems: State-of-the-art and future trends. IEEE Trans. Ind. Inform. 2011;7:630–640. [Google Scholar]
- 91.Da-Xu L. Using propositional logic for requirements verification of service workflow. IEEE Trans. Ind. Inform. 2012;8:639–646. [Google Scholar]
- 92.Panetto H., Cecil J. Information systems for enterprise integration, interoperability and networking: Theory and applications. Enterp. Inf. Syst. 2013;7:1–6. doi: 10.1080/17517575.2012.684802. [DOI] [Google Scholar]
- 93.Liu C., Yang B., Liu T. Efficient naming, addressing and profile services in Internet-of-Things sensory environments. Ad Hoc Netw. 2014;18:85–101. doi: 10.1016/j.adhoc.2013.02.008. [DOI] [Google Scholar]
- 94.Yang Z., Yin C., Liu Y. A cost-based resource scheduling paradigm in cloud computing; Proceedings of the 12th International Conference on Parallel and Distributed Computing, Applications and Technologies; Gwangju, Korea. 20–22 October 2011; pp. 417–422. [Google Scholar]
- 95.Patidar S., Rane D., Jain P. A survey paper on cloud computing; Proceedings of the 2012 Second International Conference on Advanced Computing & Communication Technologies; Rohtak, Haryana, India. 7–8 January 2012; pp. 394–398. [Google Scholar]
- 96.Wang L., Tao J., Kunze M., Castellanos A.C., Kramer D., Karl W. Scientific Cloud Computing: Early Definition and Experience. HPCC. 2008;8:825–830. [Google Scholar]
- 97.Shawish A., Salama M. Inter-Cooperative Collective Intelligence: Techniques and Applications. Springer; Berlin, Germany: 2014. Cloud computing: Paradigms and technologies; pp. 39–67. [Google Scholar]
- 98.Youseff L., Butrico M., da Silva D. Toward a unified ontology of cloud computing; Proceedings of the Grid Computing Environments Workshop; Austin, TX, USA. 12–16 November 2008; pp. 1–10. [Google Scholar]
- 99.Sharma S. Expanded cloud plumes hiding Big Data ecosystem. Future Gener. Comput. Syst. 2016;59:63–92. doi: 10.1016/j.future.2016.01.003. [DOI] [Google Scholar]
- 100.Wolfe A. Why Database-as-a-Service (DBaaS) Will Be The Breakaway Technology of 2014. [(accessed on 11 July 2016)]. Available online: http://www.forbes.com/sites/oracle/2013/12/05/why-database-as-a-service-dbaas-will-be-the-breakaway-technology-of-2014/#5b0f5f833b1e.
- 101.Simón L.F.R., Avilés R.A., Botezan I., del Valle Gastaminza F., Serrano S.C. Open data as universal service. new perspectives in the information profession. Procedia Soc. Behav. Sci. 2014;147:126–132. doi: 10.1016/j.sbspro.2014.07.128. [DOI] [Google Scholar]
- 102.Cloud A.E.C. Amazon Web Services. Nov 9, 2011. [(accessed on 11 July 2016)]. Available online: http://aws.amazon.com/
- 103.Copeland M., Soh J., Puca A., Manning M., Gollob D. Microsoft Azur. Apress; New York, NY, USA: 2015. Overview of Microsoft Azure Services. [Google Scholar]
- 104.Assunção M.D., Calheiros R.N., Bianchi S., Netto M.A.S., Buyya R. Big Data computing and clouds: Trends and future directions. J. Parallel Distrib. Comput. 2015;79:3–15. doi: 10.1016/j.jpdc.2014.08.003. [DOI] [Google Scholar]
- 105.Arunkumar G., Venkataraman N. A novel approach to address interoperability concern in cloud computing. Procedia Comput. Sci. 2015;50:554–559. doi: 10.1016/j.procs.2015.04.083. [DOI] [Google Scholar]
- 106.Terzo O., Ruiu P., Bucci E., Xhafa F. Data as a service (DaaS) for sharing and processing of large data collections in the cloud; Proceedings of the Seventh International Conference on Complex, Intelligent, and Software Intensive Systems (CISIS); Taichung, Taiwan. 3–5 July 2013; pp. 475–480. [Google Scholar]
- 107.Delen D., Demirkan H. Data, information and analytics as services. Decis. Support Syst. 2013;55:359–363. doi: 10.1016/j.dss.2012.05.044. [DOI] [Google Scholar]
- 108.Abadi D.J. Data management in the cloud: Limitations and opportunities. IEEE Data Eng. Bull. 2009;32:3–12. [Google Scholar]
- 109.Sarkar P. Data as a Service: A Framework for Providing Re-Usable Enterprise Data Services. John Wiley & Sons; New York, NY, USA: 2015. [Google Scholar]
- 110.Vu Q.H., Pham T.V., Truong H.L., Dustdar S., Asal R. Demods: A description model for data-as-a-service; Proceedings of the IEEE 26th International Conference on Advanced Information Networking and Applications; Fukuoka, Japan. 26–29 March 2012; pp. 605–612. [Google Scholar]
- 111.Truong H., Dustdar S. On analyzing and specifying concerns for data as a service; Proceedings of the APSCC 2009 IEEE Asia-Pacific Services Computing Conference; Singapore. 7–11 December 2009; pp. 87–94. [Google Scholar]
- 112.Ghafour S. On-demand data integration on the cloud; Proceedings of the IEEE 7th International Conference on Cloud Computing; Anchorage, AK, USA. 27 June–2 July 2014; pp. 924–927. [Google Scholar]
- 113.Arafati M., Dagher G.G., Fung B.C.M., Hung P.C.K. D-mash: A framework for privacy-preserving data-as-a-service mashups; Proceedings of the IEEE 7th International Conference on Cloud Computing; Anchorage, AK, USA. 27 June–2 July 2014; pp. 498–505. [Google Scholar]
- 114.Fung B., Trojer T., Hung P.C.K., Xiong L., Al-Hussaeni K., Dssouli R. Service-oriented architecture for high-dimensional private data mashup. IEEE Trans. Serv. Comput. 2012;5:373–386. doi: 10.1109/TSC.2011.13. [DOI] [Google Scholar]
- 115.Pedersen T., Pedersen D., Riis K. On-demand multidimensional data integration: Toward a semantic foundation for cloud intelligence. J. Supercomput. 2013;65:217–257. doi: 10.1007/s11227-011-0712-3. [DOI] [Google Scholar]
- 116.Zhang J., Iannucci B., Hennessy M., Gopal K., Xiao S., Kumar S., Pfeffer D., Aljedia B., Ren Y., Griss M. Sensor data as a service—A federated platform for mobile data-centric service development and sharing; Proceedings of the 2013 IEEE International Conference on Services Computing (SCC); Santa Clara, CA, USA. 28 June–3 July 2013; pp. 446–453. [Google Scholar]
- 117.Chen X., Han Y., Wei Y., Zhang F., Wen Y. A Method of Sensor Data Services Query in Emergency Management; Proceedings of the 2013 IEEE and Internet of Things (iThings/CPSCom) Green Computing and Communications (GreenCom), IEEE International Conference on and IEEE Cyber, Physical and Social Computing; Beijing, China. 20–23 August 2013; pp. 2024–2028. [Google Scholar]
- 118.Yang L. A Data-as-a-Service framework for IoT big data; Proceedings of the 2013 International Conference on Security and Cryptography (SECRYPT); Reykjavik, Iceland. 29–31 July 2013. [Google Scholar]
- 119.Manzoor A., Patsakis C., Morris A., McCarthy J., Mullarkey G., Pham H., Clarke S., Cahill V., Bouroche M. CityWatch: Exploiting sensor data to manage cities better. Trans. Emerg. Telecommun. Technol. 2014;25:64–80. doi: 10.1002/ett.2786. [DOI] [Google Scholar]
- 120.Marie P., Lim L., Manzoor A., Chabridon S., Conan D., Desprats T. QoC-aware context data distribution in the internet of things; Proceedings of the 1st ACM Workshop on Middleware for Context-Aware Applications in the IoT; Bordeaux, France. 8–12 December 2014; pp. 13–18. [Google Scholar]
- 121.Lehmann M., Biørn-Hansen A., Ghinea G., Grønli T.M., Younas M. Mobile Web and Information Systems. Springer International Publishing; Cham, Switzerland: 2015. Data Analysis as a Service: An Infrastructure for Storing and Analyzing the Internet of Things; pp. 161–169. [Google Scholar]
- 122.Wu X., Zhu X., Wu G.-Q., Ding W. Data mining with big data. IEEE Trans. Knowl. Data Eng. 2014;26:97–107. [Google Scholar]
- 123.Dean J. Big Data, Data Mining, and Machine Learning: Value Creation for Business Leaders and Practitioners. John Wiley & Sons; New York, NY, USA: 2014. [Google Scholar]
- 124.Fan W., Bifet A. Mining big data: Current status, and forecast to the future. ACM SIGKDD Explor. Newsl. 2013;14:1–5. doi: 10.1145/2481244.2481246. [DOI] [Google Scholar]
- 125.Merceron A. Educational Data Mining/Learning Analytics: Methods, Tasks and Current Trends; Proceedings of the DeLFI Workshops 2015 Co-Located with 13th e-Learning Conference of the German Computer Society (DeLFI 2015); München, Germany. 1–4 September 2015; pp. 101–109. [Google Scholar]
- 126.Liao S.-H., Chu P.-H., Hsiao P.-Y. Data mining techniques and applications—A decade review from 2000 to 2011. Expert Syst. Appl. 2012;39:11303–11311. doi: 10.1016/j.eswa.2012.02.063. [DOI] [Google Scholar]
- 127.Ihaka R., Gentleman R. R: A language for data analysis and graphics. J. Comput. Graph. Stat. 2009;5:299–314. [Google Scholar]
- 128.Milne D., Witten I.H. An open-source toolkit for mining Wikipedia. Artif. Intell. 2013;194:222–239. doi: 10.1016/j.artint.2012.06.007. [DOI] [Google Scholar]
- 129.Hall M., Frank E., Holmes G., Pfahringer B., Reutemann P., Witten I.H. The WEKA data mining software: An update. ACM SIGKDD Explor. Newsl. 2009;11:10–18. doi: 10.1145/1656274.1656278. [DOI] [Google Scholar]
- 130.Frank E., Hall M., Trigg L., Holmes G., Witten I.H. Data mining in bioinformatics using Weka. Bioinformatics. 2004;20:2479–2481. doi: 10.1093/bioinformatics/bth261. [DOI] [PubMed] [Google Scholar]
- 131.Hofmann M., Klinkenberg R. RapidMiner: Data Mining Use Cases and Business Analytics Applications. CRC Press; Boca Raton, FL, USA: 2013. [Google Scholar]
- 132.Berthold M.R., Cebron N., Dill F., Gabriel T.R., Kötter T., Meinl T., Ohl P., Sieb C., Thiel K., Wiswedel B. Data Analysis, Machine Learning and Applications: Proceedings of the 31st Annual Conference of the Gesellschaft für Klassifikation. Springer; Berlin, Germany: 2007. KNIME: The Konstanz information miner; pp. 319–326. [Google Scholar]
- 133.López T.S., Ranasinghe D.C., Harrison M., McFarlane D. Adding sense to the Internet of Things. Pers. Ubiquitous Comput. 2012;16:291–308. doi: 10.1007/s00779-011-0399-8. [DOI] [Google Scholar]
- 134.López T.S., Ranasinghe D.C., Patkai B., McFarlane D. Taxonomy, technology and applications of smart objects. Inf. Syst. Front. 2011;13:281–300. doi: 10.1007/s10796-009-9218-4. [DOI] [Google Scholar]
- 135.Kortuem G., Kawsar F., Sundramoorthy V., Fitton D. Smart objects as building blocks for the internet of things. IEEE Internet Comput. 2010;14:44–51. doi: 10.1109/MIC.2009.143. [DOI] [Google Scholar]
- 136.Masciari E. A Framework for Outlier Mining in RFID data; Proceedings of the 11th International Database Engineering and Applications Symposium; Banff, AB, Canada. 6–8 September 2007; pp. 263–267. [Google Scholar]
- 137.Shen B., Liu Y., Wang X. Research on data mining models for the internet of things; Proceedings of the 2010 International Conference on Image Analysis and Signal Processing; Xiamen, China. 12–14 April 2010; pp. 127–132. [Google Scholar]
- 138.Han J., Cheng H., Xin D., Yan X. Frequent pattern mining: Current status and future directions. Data Min. Knowl. Discov. 2007;15:55–86. doi: 10.1007/s10618-006-0059-1. [DOI] [Google Scholar]