Abstract
Nowadays, many hospitals and medical institutes employ an authentication protocol within electronic patient records (EPR) services in order to provide protected electronic transactions in e-medicine systems. In order to establish efficient and robust health care services, numerous studies have been carried out on authentication protocols. Recently, Li et al. proposed a user authenticated key agreement scheme according to EPR information systems, arguing that their scheme is able to resist various types of attacks and preserve diverse security properties. However, this scheme possesses critical vulnerabilities. First, the scheme cannot prevent off-line password guessing attacks and server spoofing attack, and cannot preserve user identity. Second, there is no password verification process with the failure to identify the correct password at the beginning of the login phase. Third, the mechanism of password change is incompetent, in that it induces inefficient communication in communicating with the server to change a user password. Therefore, we suggest an upgraded version of the user authenticated key agreement scheme that provides enhanced security. Our security and performance analysis shows that compared to other related schemes, our scheme not only improves the security level, but also ensures efficiency.
Introduction
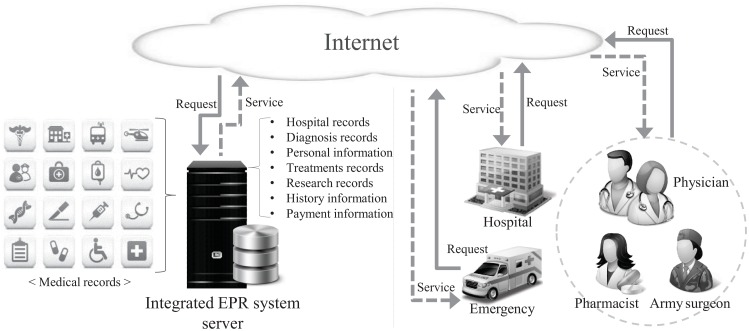
The development of Information and Communication Technology (ICT) with the prevalent use of the mobile Internet, smart devices, social network services, and cloud services has brought remarkable changes to our daily lives. This development has also affected the medical field, which has retained a number of conventional and inefficient methods. Recently, a large number of hospitals providing health care services have instituted EPR systems in order to remotely communicate with patients, and to efficiently process their medical records and disease management [1]. The EPR system allows the sharing of patients’ medical histories, such as hospital records, diagnosis records, personal information, treatment records, and research records. Using the EPR system, all patient information is available electronically, on screen, at any hospital location, at any time. In addition, EPR provides the most recent and accurate information, enabling faster diagnoses, treatment plans and discharge processes for the patient [2]. Fig 1 illustrates the integrated EPR information system.
Fig 1. Integrated EPR information system.
While the users enjoy simplicity and efficiency in EPR information systems, security has emerged as a major issue in both academic and industrial fields [3, 4]. In order to guarantee reliability, authentication protocol provides security and mutual authentication when users access a foreign network.
Lamport [5] first presented an authentication technique based on passwords, and since then, many related studies [6–22] have been conducted to improve security and efficiency for various environments such as wireless environments, Telecare medical information systems (TMIS), health care systems, wireless sensor networks (WSNs), multi-server environments, and mobile pay-TV systems. In 2006, Lee et al. [6] presented a security enhanced authentication mechanism for wireless environments. Wu et al. [7], He et al. [8], Hao et al. [9], Jiang et al. [10] and Moon et al. [11] have proposed authentication method for TMIS. Amin et al. [12] and He et al. [13] proposed user anonymous authentication scheme for health care systems. In 2014, Kim et al. [14], Choi et al. [15] and Nam et al. [16] proposed authenticated key agreement mechanisms for WSN environments. In the same year, Khan [17] presented a fingerprint biometric-based self-authentication and deniable authentication scheme for electronic transaction. In addition, Chaudhry et al. [18], Amin & Biswas [19], Moon et al. [20], and Mishra et al. [21] presented authentication systems for multi-server environments. In 2016, He et al. [22] presented one-to-many authentication using bilinear pairing in mobile pay-TV systems.
Especially, in order to improve the security, various cryptography techniques are used in authentication protocol. Khan et al. [23] and Lee & Hsu [24] apply a chaotic map technique in their scheme. In 2015, Giri et al. [25] presented an RSA-based authentication method for TMIS. However, Amin & Biswas [26] demonstrated that Giri et al.’s scheme [25] cannot guarantee protection against off-line password guessing attacks and insider attacks, and suggested an improved mechanism based on an RSA cryptosystem. In addition, Chaudhry et al. [27], Irshad et al. [28], Islam & Khan [29], Amin & Biswas [30], and Amin et al. [31, 32] presented authentication mechanisms using elliptic curves cryptography (ECC) for TMIS.
In 2012, Wu et al. [33] first presented an efficient user authentication technique for an integrated EPR information system. They used lightweight operations in their protocol including one-way hash operations and bitwise XOR operations in order to enhance efficiency. However, Lee et al. [34] pointed out that Wu et al. [33] overlooked the possibility of stolen smart card attack through power consumption analysis [35]. Lee et al. [34] then suggested an improved version that addressed the issue of Wu et al.’s [33] technique. However, Wen [36] demonstrated that Lee et al.’s scheme [34] still had some weaknesses, such as off-line password guessing attacks and user impersonation attacks, and proposed an enhanced new strategy. Unfortunately, Li et al. [37] demonstrated that Wen’s scheme [36] cannot prevent password disclosure attack nor provide efficient password change. In 2015, Das [38] discovered that Lee et al.’s scheme [34] and Wen’s scheme [36] shared the same three vulnerabilities. First, the password change phase of both schemes had no verification process of the user’s previous password. Second, their schemes were not protected against insider attack. Third, in their studies, formal security analysis was not conducted. In an attempt to compensate for these defects, Das [38] presented an upgraded scheme. However, Mir et al. [39] discovered that Das’s scheme [38] is not protected against off-line/on-line password guessing attacks, and propose a secure anonymous authentication mechanism. Li et al. [40] recently also demonstrated that Das’s scheme [38] could not satisfy security requirements because it is not protected against modification attacks and user duplication attacks. They then suggested an enhanced new authentication mechanism.
However, we have discovered that Li et al.’s scheme [40] comprises critical security weaknesses. Their scheme: (i) cannot prevent off-line password guessing attacks and server spoofing attacks, (ii) is unable to preserve user anonymity, (iii) does not identify incorrect passwords promptly in login stage, and (iv) has non-user-friendly password changing procedure, since it requires communication with the server. In this current research, our main contribution is as follows. First, we describe the weaknesses of the above scheme. Second, we propose a more developed authentication mechanism for an integrated EPR information system. Third, we show that the proposed mechanism satisfies the various security requirements. Finally, we demonstrate that the proposed mechanism has good performance in terms of computation cost and time consumption.
The remainder of this paper is structured as follows. Section 2 provides some background information on prior knowledge. In Section 3, we briefly explain Li et al.’s authentication procedure. Section 4 demonstrates the vulnerabilities of Li et al.’s scheme. A detailed explanation of our proposed scheme is provided in Section 5. In Section 6, we evaluate whether our proposed scheme can withstand various attacks while satisfying our claim that the basic requirements of the security scheme are provided. In Section 7, we analyze the performance of the proposed scheme and in Section 8, we provide a conclusion to the paper.
Preliminary Knowledge
In this section, we will describe basic knowledge in terms of security properties and introduce bio-hash function [41], which is used in our proposed scheme.
Security requirements
Multiple security requirements should be considered in order to implement a secure and efficient authentication mechanism. In this subsection, based on previous researches [33, 34, 36, 38, 40, 42–44], we outline some of the important requirements of an authentication scheme. In Section 6, these requirements will be employed in order to scrutinize the security of prior schemes and our proposed scheme.
User anonymity: In an authentication mechanism, even if an attacker extracts some information stored in a smart card or eavesdrops the exchanged message in the communication group, the user’s identity should be preserved.
Mutual authentication: An authentication mechanism should execute several steps to achieve mutual authentication which is to test all transmitted messages to judging the legitimacies.
Session key agreement: After the verification process has completed, the user and server should assign the session key to each other.
Password verification process: If a user erroneously enters an incorrect password in the login phase, the password should be detected before performing the verification phase.
User friendliness: An authentication mechanism provides a password change procedure with which a user can freely update their password without communicating with the server.
Robustness: An authenticated key agreement mechanism should be immune to different types of attacks, such as insider attacks, off-line password guessing attacks, replay attacks, and user impersonation attacks.
Bio-hash function
Recently, three-factor authentication mechanism has frequently been used, which complements the two-factor authentication mechanism using ID and PW by adding biometric information in order to increase security. In a number of studies on the three-factor authentication mechanism [11, 20, 21, 45, 46], the bio-hash function has been applied to the user’s biometric information. In 2004, Jin et al. [41] suggested a fingerprint-based function to identify the user’s legitimacy. The bio-hash technique employs the particular tokenized pseudo-random numbers to each of users measuring biometric feature arbitrarily onto two fold strands. The bio-hash function H(⋅) is a one-way function with a feature that can reduce the probability of denial of service. In order to improve security, our proposed scheme adopts the user’s biometric information applied in the bio-hash function. The details are as follows in Section 5.
Description of Li et al.’s scheme
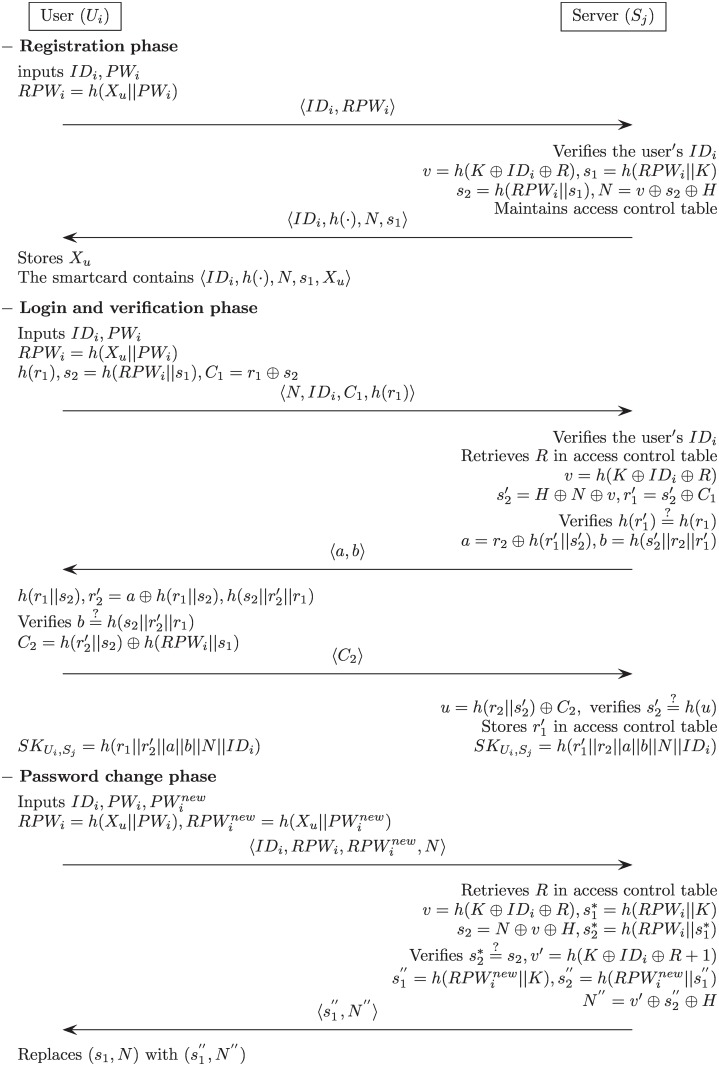
In this section, we briefly review Li et al.’s authentication mechanism [40] in order to cryptanalyze their scheme. Their scheme consists of the following phases: registration, login, verification, and password change. Fig 2 describes Li et al.’s scheme, and Table 1 shows the notations employed in the remainder of this paper.
Fig 2. Li et al.’s authentication scheme.
Table 1. Notations.
| Notations | Description |
|---|---|
| Ui | User |
| Sj | EPR information system server |
| IDi | Identity of Ui |
| PWi | Password of Ui |
| New password of Ui | |
| R | Number of times Ui re-registers to Sj |
| Bi | Biometric information of Ui |
| Xu | Secret number generated by Ui |
| H | Secret number generated by Sj |
| K | Secret key of Sj |
| r1 | Random number generated by Ui |
| r2 | Random number generated by Sj |
| h(⋅) | One-way hash function |
| H(⋅) | Bio-hash function |
| X||Y | Concatenate operation |
| ⊕ | XOR operation |
Registration phase
Ui inputs his/her IDi and PWi, and Ui generates a random secret number Xu that is only retained by user Ui. Ui computes RPWi = h(Xu||PWi) and sends a registration request message 〈IDi, RPWi〉 to Sj through a secure channel.
Sj verifies the user’s IDi. If it is valid, Sj computes v = h(K ⊕ IDi ⊕ R), where the secret number K is chosen by Sj.
Sj computes s1 = h(RPWi||K), s2 = h(RPWi||s1) and N = v ⊕ s2 ⊕ H. Sj then issues a smart card with the parameters {IDi, h(⋅), N, s1} and sends it to Ui through a secure channel. At this time, Sj constructs an access control table. This table includes the user’s identity IDi in the first field and in the case of initial registration of Ui, records null value and R = 0 into the second and third fields, respectively. If it is not an initial registration, Sj records R = R+1 in the existing field.
Upon receiving the smart card, Ui enters the secret number Xu into its memory, and the smart card includes the information {Xu, IDi, h(⋅), N, s1}.
Login phase
Ui inserts Ui’s smart card into a card reader and inputs his/her IDi and PWi. The smart card then computes RPWi = h(Xu||PWi).
The smart card selects a random number r1 and computes h(r1), s2 = h(RPWi||s1) and C1 = r1 ⊕ s2.
Finally, Ui sends the login request message 〈N, IDi, C1, h(r1)〉 to Sj through a public network.
Verification phase
Sj verifies the user’s IDi. If it holds, Sj accepts the login request and proceeds with the next step. Otherwise, Sj rejects the login request and this phase is terminated.
Sj retrieves the R stored in the access control table and computes v = h(K ⊕ IDi ⊕ R), and . Sj then verifies whether . If this holds, Sj proceeds to the next step. Otherwise, this phase is terminated.
Sj selects a random number r2 and computes and . Sj then sends an authentication request message 〈a, b〉 to Ui through a public network.
Ui computes h(r1||s2), and . Ui then verifies whether . If this holds, Ui successfully authenticates Sj. Subsequently, Ui computes and sends the acknowledgement message 〈C2〉 to Sj through a public network.
Sj computes and verifies whether . If this holds, Sj successfully authenticates the Ui and stores in its access control table.
Finally, Sj computes a shared session key and the Ui also computes the same shared session key successfully.
Password change phase
Ui inserts Ui’s smart card into a card reader and inputs IDi, old password PWi and new password . The smart card computes the old masked password RPWi = h(Xu||PWi) and the new masked password . Ui then sends the password change request message to Sj through a secure channel.
Sj retrieves R stored in the access control table and computes v = h(K ⊕ IDi ⊕ R), , s2 = N ⊕ v ⊕ H, and . Sj then verifies whether . If this holds, Sj accepts the password change request and proceeds with the next step. Otherwise, the password change request is rejected and this phase is terminated.
Sj computes v′ = h(K ⊕ IDi ⊕ R+1), , and . Sj then sends the password change update message to Ui through a secure channel.
Upon receiving the password change update message, the smart card replaces the existing values s1 and N with the new values and N′′, respectively. Finally, the smart card contains the information .
Security pitfalls of Li et al.’s scheme
In this section, we show that Li et al.’s scheme [40] possesses some security vulnerabilities. The following attacks are based on the assumptions that an attacker can extract all of the parameters stored in the smart card by physically monitoring its power consumption [35] and that the attacker can intercept or modify any messages in the public channel [11, 14, 15]. Under these two assumptions, the following problems have been observed and their detailed descriptions are given below.
Off-line password guessing attack
This attack is an attempt to identify a password until the correct password is found, and is carried out due to the tendency of many users to create simple, brief passwords for the sake of convenience. For this reason, authentication schemes for all password-based users should be designed to prevent a guessing attack; however, Li et al.’s scheme [40] does not provide sufficient protection against such an attack. We therefore propose a scenario for an off-line password-guessing attack using Li et al.’s scheme. The following is a detailed description of this scenario:
-
Step.1
An attacker extracts {Xu, IDi, h(⋅), N, s1} from Ui’s lost smart card [35].
-
Step.2
The attacker collects a valid login request message 〈N, IDi, C1, h(r1)〉 from the previous session.
-
Step.3
The attacker selects a password candidate .
-
Step.4
The attacker computes h(r1) = h(C1 ⊕ s2) using r1 = C1 ⊕ s2. Note that s2 = h(RPWi||s1), and RPWi = h(Xu||PWi); therefore, the attacker can write h(r1) = h(C1 ⊕ h(h(Xu||PWi)||s1)).
-
Step.5
The attacker then computes using the password candidate .
-
Step.6
The attacker repeats the above steps from 3 to 5 until the computed result h(r1)* is equal to the breached secret h(r1).
-
Step.7
If h(r1)* and h(r1) correspond, would be an accurate password. If not, the attacker repeats the above steps until the correct password is found.
Therefore, Li et al’s scheme [40] is vulnerable to the off-line password guessing attack. In addition, if an attacker obtains the user’s password, they can successfully launch a user impersonation attack.
Server spoofing attack
The security of the password-based user authentication mechanism is based on the intelligence of the password. Thus, if an attacker gains a password, they can pretend to be a legal server. Unfortunately, Li et al.’s scheme allows an attacker to disguise a legal server if the attacker obtains the user’s password PWi through the guessing attack. The following is a detailed description of this scenario:
-
Step.1
An attacker extracts {Xu, IDi, h(⋅), N, s1} from Ui’s lost smart card [35].
-
Step.2
The attacker collects a valid login request message 〈N, IDi, C1, h(r1)〉 from the previous session.
-
Step.3
The attacker obtains the PWi through the off-line password guessing attack.
-
Step.4
The attacker computes RPWi = h(Xu||PWi), s2 = h(RPWi||s1), and r1 = s2 ⊕ C1. The attacker then selects a random number and computes and .
-
Step.5
The attacker then sends an authentication request 〈a*, b*〉 to Ui through a public network.
-
Step.6
After receiving the 〈a*, b*〉, Ui computes h(r1||s2), and .
-
Step.7
Ui verifies whether . Finally, Ui successfully finishes the verification process because b*, which is created by the attacker, is equal to .
Through the aforementioned descriptions, it is demonstrated that the attacker can successfully disguise a legal server in Li et al’s scheme [40].
Lack of user’s anonymity
In modern networks environments, the leakage of user-related information can expedite an outside attacker to identify every specific user. In such a case, the user’s privacy data is at risk of being disclosed to an untrusted third party who disobeys the user’s will. Therefore, user anonymity is highly considered as a essential property for user authentication mechanism. However, in Li et al.’s scheme [40], an attacker can easily obtain the user’s identity through monitoring the public channels [11, 14, 15] because the user’s IDi is in plain text form during the login phase. In addition, if the attacker obtains the smart card, the user’s identity IDi can also be easily exposed through physically monitoring the smart card’s power consumption [35]. With this information, the attacker can also try to launch various types of attacks, which lead to many malicious scenarios. For this reason, user anonymity cannot be preserved in Li et al.’s authentication scheme.
Absence of password verification process
During the Login phase of Li et al.’s scheme [40], if a user enters his/her identity and password, the smart card does not verify the validity of the password itself. This situation leads to other drawbacks as given below.
-
Case.1
Assume that the Ui inputs the IDi and incorrect password during the login phase; the smart card then computes , h(r1), and . Ui then sends a login request to Sj through a public channel. Upon receiving the login request, Sj first checks the validity of the user’s identity IDi. Then, Sj retrieves the stored R in the access control table and computes v = h(K ⊕ IDi ⊕ R), and . Sj then verifies whether . If it holds, Sj accepts the login request. Otherwise, the login request is rejected. However, it is obvious that , since is not equal to . Therefore, Sj belatedly realizes that the entered password is an incorrect value and Sj rejects Ui’s login request. Consequently, if Ui inputs an incorrect password by mistake, the login and verification phases are continued until they have been checked by Sj, leading to unnecessary costs in communication and computation, If the password can be quickly verified at the beginning of the login phase, this situation would not occur and the unnecessary waste would be avoided.
-
Case.2
Assume that an attacker steals a user’s smart card, and logs in to their system using the user’s real IDi and fake password . The smart card computes a fake login request message with a fake password . If the attacker sends a large number of such fake login request messages, Sj will be busy processing these messages, and will meanwhile reject other legitimate users. Therefore, without a password verification process, the system suffer from a clogging attack, which is a type of denial of service (DoS) attack.
Inconvenient password change phase
The ideal authentication scheme based on a password should be designed without restricting the user’s ability to alter their password stored in smart cards [11, 15]. Moreover, after carrying out a verification process on an existing password, the self-alteration procedure should be performed within the smart card, without extra communication to server Sj, in order to enhance efficiency. However, since a password verification procedure functions with assistance from Sj in Li et al.’s scheme, it is considered to be inefficient and not user-friendly.
Scalability problem
Li et al.’s scheme [40], in order to strengthen security, it is suggested that the server comprises an access control table to save the information such as the user’s identity, latest login number, and registration times. Accordingly, the server needs to retain each user’s access control table. However, the increased amount of user information needing to be retained places more burden on the server, since the number of access control table will increase as the number of users’ increases. Moreover, the use of the access control table is inefficient in terms of computation time, since the changed values at each phase need to be recorded in the access control table.
The proposed scheme
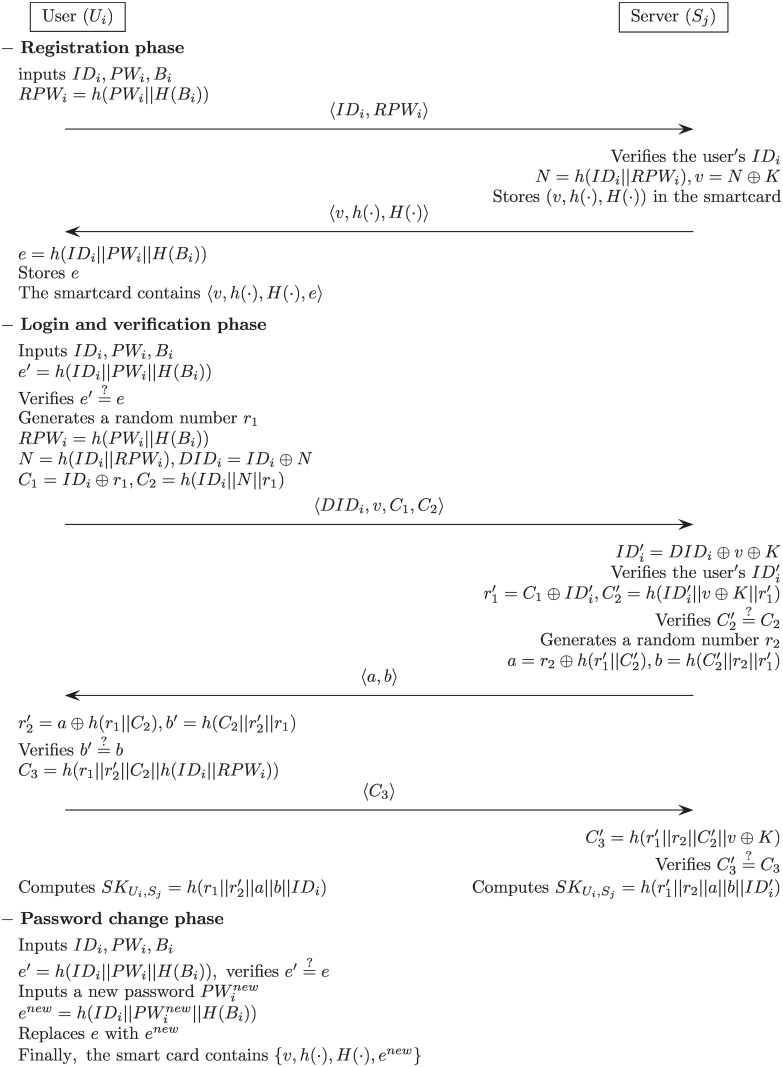
In this section, we suggest a refined version of the authentication protocol to offer enhanced security by resolving the vulnerabilities of Li et al.’s [40] scheme. In the proposed scheme, in order to resist an off-line password guessing attack and server spoofing attack, we use biometrics information with Biohashing H(⋅) [41] to securely conceal the password. We also include a password verification process at the beginning of the login phase to ensure high efficiency and resist a denial of service (DoS) attack. In addition, we remove the access control table to reduce the server load and modify the password change process to provide user-friendly access. Our proposed protocol also consists of four phases: registration, login, verification and password change. Fig 3 describes our proposed scheme, and Table 1 lists the notations employed in the proposed scheme.
Fig 3. Our proposed scheme.
Registration phase
Ui inputs IDi and PWi, and imprints his/her biometrics Bi. Then Ui computes RPWi = h(PWi||H(Bi)) and sends a registration request 〈IDi, RPWi〉 to Sj through a secure channel.
Sj verifies the user’s IDi. If it is valid, Sj computes N = h(IDi||RPWi) and v = N ⊕ K.
Sj issues a smart card with the {v, h(⋅), H(⋅)} and sends it to Ui through a secure channel.
Upon receiving the smart card, Ui computes e = h(IDi||PWi||H(Bi)) and enters it into the smart card’s memory. Finally, the smart card includes the information {v, h(⋅), H(⋅), e}.
Login phase
Ui inserts Ui’s smart card into a card reader and inputs his/her IDi, PWi, and imprints biometric Bi. The smart card then computes e′ = h(IDi||PWi||H(Bi)), and compares it with the stored e in the smart card. If this holds, the smart card acknowledges the legitimacy of user Ui, and proceeds with the next step. Otherwise, it terminates the login process.
The smart card selects a random number r1, and computes RPWi = h(PWi||H(Bi)), N = h(IDi||RPWi), DIDi = IDi ⊕ N, C1 = IDi ⊕ r1 and C2 = h(IDi||N||r1).
Finally, Ui sends the login request message 〈DIDi, v, C1, C2〉 to Sj through a public network.
Verification phase
Sj computes . Sj verifies the user’s . If this holds, Sj accepts the login request and proceeds with the next step. Otherwise, Sj rejects the login request and this phase is terminated.
Sj computes , , and verifies whether . If this holds, Sj proceeds to the next step. Otherwise, this phase is terminated.
Sj selects a random number r2 and computes and . Sj then sends an authentication request message 〈a, b〉 to Ui through a public network.
Ui computes and . Ui then verifies whether b′ = b. If this holds, Ui successfully authenticates Sj. Then, Ui computes and sends the acknowledgement message 〈C3〉 to Sj through a public network.
Sj computes and verifies whether . If this holds, Sj successfully authenticates Ui.
Finally, Sj computes a shared session key and Ui also computes the same shared session key successfully.
Password change phase
Ui inserts Ui’s smart card into a card reader and inputs IDi, and the old password PWi, and then imprints biometric Bi. The smart card computes e′ = h(IDi||PWi||H(Bi)). The smart card then verifies whether , where ei is stored in the smart card. If this condition is not satisfied, it terminates this phase. Otherwise, the smart card proceeds to the next step.
Ui inputs a new password , and the smart card then computes ,
The smart card replaces the existing value e with the new value enew. Finally, the smart card contains the information {v, h(⋅), H(⋅), enew}.
Security analysis of the proposed scheme
In this section, we first adopt Burrows-Abadi-Needham (BAN) logic [47] to prove that a session key can be correctly generated between Ui and Sj. We then verify that our proposed scheme is secure against various attacks through both informal and formal security analysis.
Authentication proof with BAN logic
In this subsection, based on the BAN logic technique, we verify the legitimacy of session keys distributed to the participants who communicate in our proposed protocol. BAN logic [47] is applied, which is a well-known formal logic technique used to analyze the security of cryptographic protocols. Table 2 shows the basic notations to determine BAN logic.
Table 2. Notations.
| Notations | Description |
|---|---|
| U∣≡C | Condition C is believed by U |
| U⊲C | U sees condition C |
| U∣∼C | U expresses the condition C |
| U ⇒ C | Condition C is handled by U |
| ♯(C) | It makes a fresh C |
| U and S share a secret key K | |
| <C>K | Combine condition C using K |
| (C)K | Perform the hash operation on C using K |
In order to determine the reasonable postulates of BAN logic, five logic rules are also offered as follows.
Message-meaning rule: : If U trusts that the key K is shared with S, U sees the C combined with K, then U trusts S once said C.
Nonce-verification rule: : If U trusts that C’s freshness and U trusts S once said C, then U trusts that S trusts C.
Believe rule: : If U trusts C and M, (C, M) are also trusted by U.
Freshness-conjuncatenation rule: : If freshness of C is trusted by U, then U can trust the freshness of full condition.
Jurisdiction rule: : If U trusts that S has jurisdiction over C, and U trusts that S trusts a condition C, then U also trusts C.
Through our analysis, we intend to meet the following two goals.
Goal 1.
Goal 2.
Next, all transmitted messages in our authentication scheme can be transmuted into an idealized form as follows.
Message 1.
Message 2.
Message 3. U → S: (r1, r2, IDi)v
In order to analyze our mechanism, we define the following assumptions.
A1: U ∣≡ ♯(r1)
A2: U ∣≡ ♯(r2)
A3:
A4:
A5:
A6:
Now, we describe our main proof as follows. In order to describe our proof, we use pre-defined information, including five logic rules, three messages and six assumptions.
According to Message 1, we could derive the following:
-
V1:
Based on assumption A4 and the message meaning rule, we derive:
-
V2: S ∣≡ U ∣∼ v
Based on V2 and the message meaning rule, we derive:
-
V3: S ∣≡ U ∣∼ IDi
Based on V3 and the message meaning rule, we derive:
-
V4: S ∣≡ U ∣∼ r1
Based on assumption A1, V4 and the freshness conjuncatenation rule, we derive:
-
V5:
Based on V4, V5 and the nonce verification rule, we derive:
-
V6:
Based on V3, V6 and the jurisdiction rule, we derive:
-
V7: S ∣≡ r1
Based on Message 2, we derive:
-
V8:
Based on assumption A2, V3 and the message meaning rule, we derive:
-
V9: U ∣≡ S∣∼r2
Based on assumption A2 and the freshness conjuncatenation rule, we derive:
-
V10:
Based on V9, V10 and the nonce verification rule, we derive:
-
V11:
Based on V9, V11 and the jurisdiction rule, we derive:
-
V12: U ∣≡ r2
Based on sk, V12 and assumption A1, we derive:
-
V13: (Goal 1.)
Based on Message 3, we derive:
-
V14: S ⊲ (r1, r2, IDi)v
Based on sk, V3, V7 and assumption A2, we derive:
V15: (Goal 2.)
The above description clearly shows that Ui and Sj achieve mutual authentication, and based on (Goal.1) and (Goal.2), Ui and Sj trust that session key sk is securely shared between them.
Informal security analysis
In this subsection, we examine the security our proposed scheme against various attacks, and the suitability of the basic requirements, as described in Section 2.1, are evaluated. Also, we perform a comparative analysis of previous schemes [9, 10, 27, 28, 33, 38, 40], which is illustrated in Table 3. The results are described as follows.
Table 3. Security comparison of the proposed scheme and other related schemes.
| Features | Hao’s [9] |
Jiang’s [10] |
Chaudhry’s [27] |
Irshad’s [28] |
Wu’s [33] |
Das’s [38] |
Li’s [40] |
Proposed Scheme |
|---|---|---|---|---|---|---|---|---|
| Proposition 1. | √ | √ | √ | √ | × | √ | √ | √ |
| Proposition 2. | √ | √ | √ | √ | × | × | × | √ |
| Proposition 3. | √ | √ | √ | √ | √ | √ | √ | √ |
| Proposition 4. | × | × | √ | √ | × | × | × | √ |
| Proposition 5. | × | × | √ | √ | × | × | × | √ |
| Proposition 6. | × | × | √ | √ | × | × | × | √ |
| Proposition 7. | √ | √ | √ | √ | √ | √ | √ | √ |
| Proposition 8. | × | × | √ | √ | × | × | × | √ |
| Proposition 9. | × | √ | √ | × | × | × | × | √ |
| Proposition 10. | √ | √ | √ | √ | √ | √ | √ | √ |
| Proposition 11. | × | × | × | × | √ | √ | √ | √ |
| Proposition 12. | √ | √ | √ | √ | √ | √ | × | √ |
| Formal security proof | × | × | √ | √ | × | √ | √ | √ |
Proposition 1. Resistant to insider attack
Proof. Insider attack means that an insider can directly obtain the user’s password from the server and can then access the user’s account in another server by using the same password. This attack occurs due to the disclosure of Ui’s password PWi during the registration phase. However, in our scheme, PWi is transmitted not as a revealed condition but as a form of RPWi = h(PWi||H(Bi)) with a value of biometrics, H(Bi), when Ui sends a registration request 〈IDi, RPWi〉 to Sj to prohibit insider attack. Thus, our scheme is secure against insider attack.
Proposition 2. Preserve user anonymity
Proof. User anonymity is valuable information for the user authentication mechanism, because the disclosure of a user’s identity can allow an unauthorized party to track the user’s login pattern. Our scheme shields user’s identity IDi transmitted by messages from the potential risks of exposure in order to fulfill user anonymity. Even if an attacker obtains C1 by snatching login request 〈DIDi, v, C1, C2〉, it is impossible to calculate IDi since the random number r1 is not known.
Proposition 3. Provide mutual authentication
Proof. In the verification phase of our proposed scheme, Ui and Sj can authenticate each other by a number of checking processes. In detail, Sj first verifies the login request by checking whether C2 is correct. Ui also verifies the authentication request by checking whether b is correct. Lastly, Sj verifies the acknowledgement message by checking whether or not C3 is valid. If all these verification processes are successfully completed, mutual authentication has been executed properly.
Proposition 4. Resistant to off-line password guessing attack
Proof. An off-line password guessing attack occurs when an attacker attempts to guess a password and eventually finds the exact user’s password in an off-line environment by using the information stored in the smart card or intercepted packets. In our scheme, an attacker can obtain {v, h(⋅), H(⋅), e} from the stolen smart card and intercept the login request 〈DIDi, v, C1, C2〉. Using these values, the attacker may try to guess the correct password PWi. However, without knowing IDi and H(Bi), the attacker cannot guess PWi. In addition, H(Bi) is hashed biometric information, which is only known by Ui. Therefore, our proposed scheme can withstand an off-line password guessing attack.
Proposition 5. Resistant to user impersonation attack
Proof. An user impersonation attack occurs when an attacker pretends to be the legal user with the counterfeited login request by using the information that has accumulated from the smart cards and the intercepted packets. Suppose that an attacker obtains {v, h(⋅), H(⋅), e} from the stolen smart card. The attacker then generates a random number and attempts to compute DIDi = IDi ⊕ N, and . In order to compute DIDi, , and , the attacker must obtain Sj’s secret key K. However, it is impossible to obtain K in our scheme. Therefore, the attacker cannot generate a sufficient login request to deceive Sj.
Proposition 6. Resistant to server spoofing attack
Proof. A server spoofing attack occurs when an attacker masquerades as a legal server with the counterfeited authentication request by using the information stored in the smart card and the intercepted packets. Suppose that an attacker obtains {v, h(⋅), H(⋅), e} from the stolen smart card and intercepts the login request 〈DIDi, v, C1, C2〉. The attacker then generates a random number and attempts to modify the authentication request 〈a, b〉 to impersonate a legal Sj. However, the attacker cannot compute a sufficient authentication request to deceive Ui because it is impossible to obtain r1. In addition, as mentioned above, our scheme can guarantee protection against off-line password guessing attacks. Therefore, our proposed scheme can withstand a sever spoofing attack.
Proposition 7. Resistant to replay attack
Proof. A replay attack occurs when an attacker deceives a legitimate participant by recycling of the same packets acquired in previous sessions. Suppose that an attacker intercepts the previous login request 〈DIDi, v, C1, C2〉. The attacker might then pretend to be a valid user to login to the server by sending the message. However, if the attacker sends the previous login request, the server would obviously reject the request, because our scheme can detect an invalid random number by comparing it to the C2 value. In addition, our scheme uses different random numbers in each session. Therefore, our proposed scheme can withstand a replay attack.
Proposition 8. Provide a password verification process
Proof. It is a possible for a user to input an incorrect password by mistake. However, for the password verification procedure, an incorrect password will be detected after performing the authentication phase. Our scheme overcomes this type of inefficiency problem, evaluating the correctness of the password by verifying the value e in the early login phase.
Proposition 9. Provide an efficient password change phase
Proof. In general, the smart card should carry out the verification process by itself when password alteration occurs. The efficiency of a security scheme can be increased through its own process without communicating to the server Sj. Our proposed scheme performs existing password checks in a self-verification process within the smart card. After examining, it will switch the computed value enew from the new password with the existed value e in a convenient and efficient way.
Proposition 10. Provide session key agreement
Proof. In our scheme, Ui and Sj compute the session key after the mutual authentication process. In addition, the session key is generated by the random number and a one-way hash function. Hence, this session key is different in each session, and it is not possible to derive the session key from the intercepted messages and stolen smart card. Thus, our scheme guarantees that each session key is generated and distributed in a secure way.
Proposition 11. No time synchronization
Proof. In timestamp-based authentication protocols, when transmitting a message between a user and a server, the clocks of all devices should be synchronized. Therefore, the possibility that an error has occurred is high. However, to avoid this problem, our scheme uses a random numbers r1, r2 based authentication mechanism instead of a time-stamp technique.
Proposition 12. No access control table
We analyzed the inefficiency risk of Li et al.’s scheme with respect to the access control table. In order to overcome this weakness, our scheme removes the access control table without loss of protection from various types of attacks.
Formal security analysis
In this subsection, through the formal proof method, we demonstrate that our proposed scheme is secure. First, we specify a hash function as follows.
Definition 1 A hash function f: {0, 1}* → {0, 1}n is a one-direction function [48, 49] that takes the input x ∈ {0, 1}* of arbitrary length and outputs a bit string with a fixed-length f(x)∈{0, 1}n that is referred to as the “message digest” or “hash value”. When using cryptographic hash functions, the following three common levels of security must be considered:
It is impossible to acquire input x under the conditions of the hash value y = h(x) and the given hash function h(⋅).
It is impossible to acquire other input x′, when given the input x and f(x′) = f(x).
It is impossible to acquire the inputs (x, x′), where x ≠ x′, when given f(x) = f(x′).
Theorem 1 It is assumed that the one-way hash function h(⋅) performs like an oracle. Under this assumption, our proposed mechanism is provably secure against an adversary for protecting the user’s personal information, such as identity IDi, password PWi, biometrics Bi, and the server’s secret key K.
Reveal Given the hash result y = h(x), this random oracle will unconditionally output the input x.
Proof The similar method used in [20] is applied in our authentication mechanism for verification. In order to prove it, we assume that an attacker is able to extract the Ui’s identity IDi, password PWi, biometrics Bi, and the server’s secret key K. For this, runs the experimental algorithm that is shown in Table 4, for our anonymous biometric-based user authentication with key agreement scheme, called ABUAKAS.
Table 4. Algorithm .
| 1. Eavesdrop login request message 〈DIDi, v, C1, C2〉 |
| 2. Call the Reveal oracle. Let |
| 3. Eavesdrop login request message 〈a, b〉 |
| 4. Call the Reveal oracle. Let |
| 5. Computes |
| 6. if then |
| 7. Accepts as the correct IDi of user |
| 8. Call the Reveal oracle. Let |
| 9. if then |
| 10. Call the Reveal oracle. Let |
| 11. Computes |
| 12. if then |
| 13. Accept as the correct information of Ui |
| K as the correct key of Sj |
| 14. return 1 |
| 15. else |
| 16. return 0 |
| 17. end if |
| 18. else |
| 19. return 0 |
| 20. end if |
| 21. else |
| 22. return 0 |
| 23. end if |
We define the success probability for as , where means the probability of . The advantage function for this experiment becomes in which the maximum is determined by three factors; all of , the execution time t, and the number of queries qR derived from Reveal oracle. If the attacker is assumed that is able to resolve the hash function problem, could directly obtain Ui’s identity IDi, password PWi, biometrics Bi, and the server’s secret key K. Refer to attack experiment described in Table 4. In this case, will discover the complete connections between Ui and Sj. However, it is a computationally infeasible problem to invert a one-way hash function h(⋅), i.e., , ∀ϵ > 0. Then, we have , since depends on . Therefore, our proposed scheme is provably secure against the attacker for deriving IDi, PWi, Bi and K.
Formal security verification using AVISPA tool
In this subsection, we simulate our scheme for the formal security verification using the Automated Validation of Internet Security Protocols and Applications(AVISPA) tool [50] in order to prove that our scheme can withstand both passive and active attacks. We first overview the structure of the AVISPA tool, and then specify our authentication mechanism using High Level Protocols Specification Language(HLPSL) [51]. Lastly, we conduct a simulation using the AVISPA tool and show that our scheme guarantees safety.
Overview of AVISPA tool
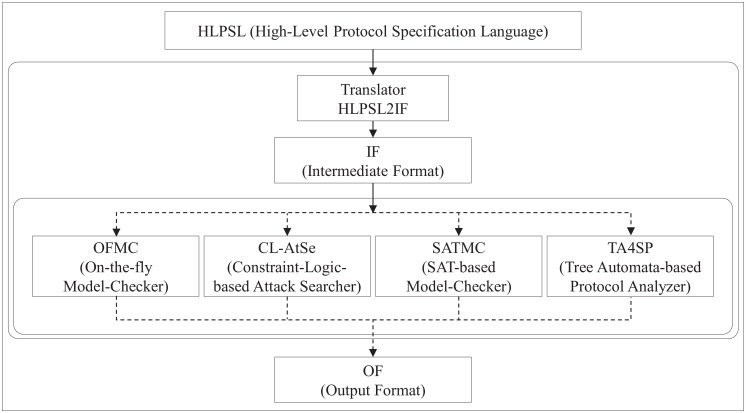
AVISPA is a well-known formal method, which has been used to verify the security of protocols. AVISPA provides the specification of security protocols and properties by using a modular and expressive specification language. A number of authentication studies have been conducted [12, 19, 26, 30–32, 39] based on the AVISPA simulation tool. The AVISPA tool can be utilized by external users because the web-interface is accessible from the website [52]. It is also provided as a package(SPAN) that can be installed on the Linux and Mac OS operating systems. The architecture of the AVISPA tool is illustrated in Fig 4.
Fig 4. Architecture of AVISPA tool.
As shown in Fig 4, the tool takes a specification, as an input, written in HLPSL and produces the results of the test, as an output, from the different back-ends. More specifically, specifications of protocols written in HLPSL are automatically translated by the HLPSL2IF into Intermediate Format (IF) specifications, which are then given as input to the different back-ends. The back-ends consist of four parts [50]: On-the-fly Model-Checker(OFMC), Constraint-Logic-based Attack Searcher(CL-AtSe), SAT based Model Checker(SATMC), and Tree Automata-based on Automatic Approximations for the Analysis of Security Protocols(TA4SP). A detailed description of each part is as follows:
On-the-fly Model-Checker(OFMC): uses different symbolic techniques to explore the state space in a demand-driven way.
Constraint-Logic-based Attack Searcher(CL-AtSe): uses simplification heuristics and redundancy elimination techniques.
SAT based Model Checker(SATMC): uses SAT-solvers in order to find a proposition leading to a fail in the model.
Tree Automata-based on Automatic Approximations for the Analysis of Security Protocols(TA4SP): uses regular tree languages in order to evaluate the intruder knowledge.
Specifying the proposed scheme
This section provides descriptions of the specifications of our scheme in HLPSL. We first implement the basic roles for a user Ui and a server Sj during the registration, login, and verification phase, and then specify the other roles for the session, environment, and goal. In our specifications, the type declaration channel(dy) indicates that the channel is influenced by the Dolev-Yao threat model [53]. The attacker has full manage over the public channel, such that the attacker can intercept or eavesdrop on all messages sent by agents. In addition, the declaration secret({K}, subs1, Sj) indicates that the secret key K is only known to Sj and secret({IDi, PWi, Bi}, subs2, Ui) indicates that 〈IDi, PWi, Bi〉 are only known to Ui. In our implementation, we assume that the bio-hash function H(⋅) is the same as the one-way hash function h(⋅). The role specification of the user Ui is shown in Fig 5.
Fig 5. Role specification in HLPSL for the user Ui.
During the registration phase, Ui sends a registration request message 〈IDi, RPWi〉 to server Sj through a secure channel using Snd() operation, and receives the information {v, h(⋅), H(⋅)} stored in the smart card from Sj using Rcv() operation securely. During the login and verification phase, Ui generates a random number r1 using new() operation and sends the login request message 〈DIDi, v, C1, C2〉 to Sj through a public channel. Ui then receives the authentication request message 〈a, b〉 from Sj through a public channel. Finally, Ui sends the acknowledgement message 〈C3〉 to Sj through a public channel. The declaration witness(Ui, Sj, alice_bob_r1, R1′) indicates that Ui has freshly generated the random number R1 for Sj. The declaration request(Sj, Ui, bob_alice_r2, R2′) denotes that Ui authenticates the server Sj. We similarly implemented the role for the server Sj as shown in Fig 6.
Fig 6. Role specification in HLPSL for the server Sj.
During the registration phase, Sj receives the registration request message 〈IDi, RPWi〉 from the user Ui through a secure channel. After receiving the registration request message, the Sj issues a smart card with the {v, h(⋅), H(⋅)} and sends it to Ui through a secure channel using the Snd() operation. During the login and verification phase, Sj receives the login request message 〈DIDi, v, C1, C2〉 from the user Ui through a public channel. The Sj then generates a random number r2 and sends the authentication request message 〈a, b〉 to Ui through a public channel. Finally, Sj receives the acknowledgement message 〈C3〉 from the user Ui through a public channel using the Rcv() operation. The declaration witness(Sj, Ui, bob_alice_r2, R2′) indicates that Sj has freshly generated the random number R2 for Ui. The declaration request(Ui, Sj, alice_bob_r1, R1′) indicates that Sj authenticates the user Ui.
We have therefore provided the specification in HLPSL for the roles including the session, environment, and gaol. The detailed specification of each role is described in Fig 7.
Fig 7. Role specification in HLPSL for the session, environment and goal.
The session part involves the starting parameters, local variables, and composition of agents. The environment part involves the global constants, attacker knowledge, security goals, and the composition of more than one session run in parallel. In our simulation, the following two secrecy goals and two authentications are verified:
secrecy_of subs1: indicates that the secret key K is only known to the legal server Sj.
secrecy_of subs2: indicates that the information including IDi, PWi and Bi is only known to the legal user Ui.
authentication_on alice_bob_r1: indicates that Ui generates a random number r1, where r1 is only taken to Ui. If the server Sj securely receives it from the message, Sj then authenticates Ui.
authentication_on bob_alice_r2: indicates that Sj generates a random number r2, where r2 is only taken to Sj. If the user Ui securely receives it from the message, Ui also authenticates Sj.
Simulation results
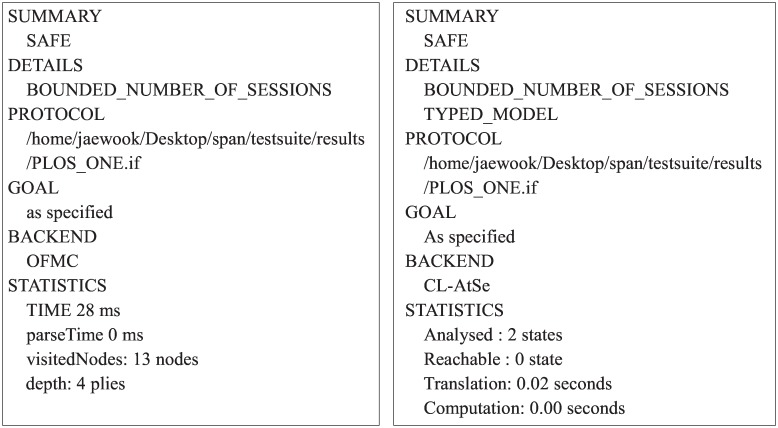
We simulated our proposed scheme using the AVISPA tool in order to check that our scheme can guarantee safety. The simulation results under the OFMC and CL-AtSe back-ends are shown in Fig 8. The results clearly demonstrate that our scheme is SAFE under each bank-end. Therefore, we conclude that our proposed scheme can guarantee protection against passive and active attacks such as replay and man-in-the middle attacks.
Fig 8. Simulation results under the OFMC and CL-AtSe back-ends.
Performance analysis of the proposed scheme
In this section, we have conducted the comparison of the computational costs and execution time for the proposed scheme with other hash-based schemes [34, 38–40]. Generally, the computational cost is examined based on the respective operations in authentication protocol. Accordingly, this analysis of computational cost concentrates on the operations that are conducted by the members, such as user and server. For the evaluation of the computational costs, we define the computational parameter TH as the time taken to execute a one-way hash function/bio-hash function.
Table 5 provides a summary of the comparison of the computational overheads. Table 5 shows that Lee et al. [34], Das [38], Mir et al. [39], Li et al. [40] and our proposed scheme require the total computational overheads of 19TH, 25TH, 27TH, 26TH, and 21TH, respectively.
Table 5. Performance comparison of the proposed scheme and other related schemes.
| Phases/Schemes | Lee et al. [34] |
Das [38] |
Mir et al. [39] |
Li et al. [40] |
Proposed Scheme |
|---|---|---|---|---|---|
| Registration phase | 4TH | 4TH | 5TH | 4TH | 4TH |
| Login phase | 2TH | 3TH | 7TH | 3TH | 5TH |
| Verification phase | 10TH | 11TH | 10TH | 11TH | 9TH |
| Password change phase | 3TH | 7TH | 5TH | 8TH | 3TH |
| Total cost | 19TH | 25TH | 27TH | 26TH | 21TH |
| Execution time | ≈ 3.8ms | ≈ 5.0ms | ≈ 5.4ms | ≈ 5.2ms | ≈ 4.2ms |
The results show that our proposed scheme is relatively superior to that proposed in a number of related studies [38–40]. In addition, as is shown in Table 3, our proposed scheme guarantees safety against a variety of existing attacks. According to [40], the actual execution times for the one-way hash function TH is 0.2ms. In Table 5, we also listed the time consumption of our proposed scheme and of the schemes presented in the other related studies [34, 38–40]. Table 5 shows that the execution time of our proposed scheme requires only 4.2 ms (≈ 21 × 0.2 ms); it can therefore be considered as of minor significance. On the other hand, the execution time of Das’s scheme [38], Mir et al.’s scheme [39] and Li et al.’s scheme [40] require 5.0ms (≈ 25 × 0.2 ms), 5.4 ms (≈ 27 × 0.2 ms) and 5.2 ms (≈ 26 × 0.2 ms), respectively; these schemes are therefore proven to be slightly ineffective compared to our scheme. Table 5 demonstrates that our proposed mechanism considers efficiency.
Conclusions
In this paper, we demonstrate that Li et al.’s scheme has a number of critical vulnerabilities and we propose an extended authentication scheme to overcome these defects. Our proposed scheme has been thoroughly verified in terms of a variety of security features, and the proof result demonstrates that a session key can be correctly generated between the communicating parties. In addition, a performance comparison for the proposed scheme in relation to the schemes proposed in other studies was carried out, and we consider that our proposed scheme has sufficient efficiency and robustness for an integrated EPR information system. In the future, we will propose a new authentication scheme applying the fuzzy extractor technique instead of the biohashing method and analyze the new scheme not only in terms of computation cost, but also in terms of communication and smart card storage cost.
Acknowledgments
All authors, especially the corresponding author Dongho Won, would like to thank the anonymous reviewers for their time and invaluable comments and suggestions on this paper.
Data Availability
All relevant data are within the paper.
Funding Statement
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2010-0020210), http://www.nrf.re.kr/.
References
- 1. Takeda H, Matsumura Y, Kuwata S, Nakano H, Sakamoto N, Yamamoto R. Architecture for networked electronic patient record systems. International journal of medical informatics. 2000;60(2):161–167. 10.1016/S1386-5056(00)00116-7 [DOI] [PubMed] [Google Scholar]
- 2. Gritzalis S, Lambrinoudakis C, Lekkas D, Deftereos S. Technical guidelines for enhancing privacy and data protection in modern electronic medical environments. IEEE Transactions on Information Technology in Biomedicine. 2005;9(3):413–423. 10.1109/TITB.2005.847498 [DOI] [PubMed] [Google Scholar]
- 3. Chan AT, Cao J, Chan H, Young G. A web-enabled framework for smart card applications in health services. Communications of the ACM. 2001;44(9):76–82. 10.1145/383694.383710 [DOI] [Google Scholar]
- 4. Wang DW, Liu DR, Chen YC. A mechanism to verify the integrity of computer-based patient records. J China Assoc Med Inform. 1999;10:71–84. [Google Scholar]
- 5. Lamport L. Password authentication with insecure communication. Communications of the ACM. 1981;24(11):770–772. 10.1145/358790.358797 [DOI] [Google Scholar]
- 6. Lee CC, Hwang MS, Liao IE. Security enhancement on a new authentication scheme with anonymity for wireless environments. IEEE Transactions on Industrial Electronics. 2006;53(5):1683–1687. 10.1109/TIE.2006.881998 [DOI] [Google Scholar]
- 7. Wu ZY, Lee YC, Lai F, Lee HC, Chung Y. A secure authentication scheme for telecare medicine information systems. Journal of medical systems. 2012;36(3):1529–1535. 10.1007/s10916-010-9614-9 [DOI] [PubMed] [Google Scholar]
- 8. He D, Jianhua C, Rui Z. A more secure authentication scheme for telecare medicine information systems. Journal of Medical Systems. 2012;36(3):1989–1995. 10.1007/s10916-011-9658-5 [DOI] [PubMed] [Google Scholar]
- 9. Hao X, Wang J, Yang Q, Yan X, Li P. A Chaotic Map-based Authentication Scheme for Telecare Medicine Information Systems. Journal of Medical Systems. 2013;37(2):9919 10.1007/s10916-012-9919-y [DOI] [PubMed] [Google Scholar]
- 10. Jiang Q, Ma J, Lu X, Tian Y. Robust chaotic map-based authentication and key agreement scheme with strong anonymity for telecare medicine information systems. Journal of medical systems. 2014;38(2):1–8. 10.1007/s10916-014-0012-6 [DOI] [PubMed] [Google Scholar]
- 11. Moon J, Choi Y, Kim J, Won D. An Improvement of Robust and Efficient Biometrics Based Password Authentication Scheme for Telecare Medicine Information Systems Using Extended Chaotic Maps. Journal of medical systems. 2016;40(3):1–11. 10.1007/s10916-015-0422-0 [DOI] [PubMed] [Google Scholar]
- 12. Amin R, Islam SH, Biswas GP, Khan MK, Li X. Cryptanalysis and enhancement of anonymity preserving remote user mutual authentication and session key agreement scheme for e-health care systems. Journal of medical systems. 2015;39(11):1–21. 10.1007/s10916-015-0318-z [DOI] [PubMed] [Google Scholar]
- 13. He D, Zeadally S, Kumar N, Lee JH. Anonymous authentication for wireless body area networks with provable security. IEEE Systems Journal. 2016;PP(99):1–12. 10.1109/JSYST.2016.2544805 [DOI] [Google Scholar]
- 14. Kim J, Lee D, Jeon W, Lee Y, Won D. Security analysis and improvements of two-factor mutual authentication with key agreement in wireless sensor networks. Sensors. 2014;14(4):6443–6462. 10.3390/s140406443 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 15. Choi Y, Lee D, Kim J, Jung J, Nam J, Won D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors. 2014;14(6):10081–10106. 10.3390/s140610081 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 16. Nam J, Kim M, Paik J, Lee Y, Won D. A provably-secure ECC-based authentication scheme for wireless sensor networks. Sensors. 2014;14(11):21023–21044. 10.3390/s141121023 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 17. Khan MK. Fingerprint biometric-based self-authentication and deniable authentication schemes for the electronic world. IETE Technical Review. 2014;26(3):191–195. [Google Scholar]
- 18. Chaudhry SA, Naqvi H, Farash MS, Shon T, Sher M. An improved and robust biometrics-based three factor authentication scheme for multiserver environments. The Journal of Supercomputing. 2015:1–17. [Google Scholar]
- 19. Amin R, Biswas GP. A novel user authentication and key agreement protocol for accessing multi-medical server usable in tmis. Journal of medical systems. 2015;39(3):1–17. 10.1007/s10916-015-0217-3 [DOI] [PubMed] [Google Scholar]
- 20. Moon J, Choi Y, Jung J, Won D. An Improvement of Robust Biometrics-Based Authentication and Key Agreement Scheme for Multi-Server Environments Using Smart Cards. PloS one. 2015;10(12):e0145263 10.1371/journal.pone.0145263 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 21. Mishra D, Das AK, Mukhopadhyay S. A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Systems with Applications. 2014;41(18):8129–8143. 10.1016/j.eswa.2014.07.004 [DOI] [Google Scholar]
- 22. He D, Kumar N, Shen H, Lee JH. One-to-many authentication for access control in mobile pay-TV systems. Science China Information Sciences, 2015:1–14. [Google Scholar]
- 23. Khan I, Chaudhry SA, Sher M, Khan JI, Khan MK. An anonymous and provably secure biometric-based authentication scheme using chaotic maps for accessing medical drop box data. The Journal of Supercomputing. 2016:1–19. [Google Scholar]
- 24. Lee CC, Hsu CW. A secure biometric-based remote user authentication with key agreement scheme using extended chaotic maps. Nonlinear Dynamics. 2013;71(1):201–211. 10.1007/s11071-012-0652-3 [DOI] [Google Scholar]
- 25. Giri D, Maitra T, Amin R, Srivastava PD. An efficient and robust rsa-based remote user authentication for telecare medical information systems. Journal of medical systems. 2015;39(1):1–9. 10.1007/s10916-014-0145-7 [DOI] [PubMed] [Google Scholar]
- 26. Amin R, Biswas GP. An improved rsa based user authentication and session key agreement protocol usable in tmis. Journal of Medical Systems. 2015;39(8):1–14. 10.1007/s10916-015-0262-y [DOI] [PubMed] [Google Scholar]
- 27. Chaudhry SA, Mahmood K, Naqvi H, Khan MK. An improved and secure biometric authentication scheme for telecare medicine information systems based on elliptic curve cryptography. Journal of Medical Systems. 2015;39(11):1–12. 10.1007/s10916-015-0335-y [DOI] [PubMed] [Google Scholar]
- 28. Irshad A, Sher M, Nawaz O, Chaudhry SA, Khan I, Kumari S. A secure and provable multi-server authenticated key agreement for TMIS based on Amin et al. scheme. Multimedia Tools and Applications. 2016:1–27. [Google Scholar]
- 29. Islam SH, Khan MK. Cryptanalysis and improvement of authentication and key agreement protocols for telecare medicine information systems. Journal of medical systems. 2014;38(10):1–16. 10.1007/s10916-014-0135-9 [DOI] [PubMed] [Google Scholar]
- 30. Amin R, Biswas GP. A secure three-factor user authentication and key agreement protocol for tmis with user anonymity. Journal of medical systems. 2015;39(8):1–19. [DOI] [PubMed] [Google Scholar]
- 31. Amin R, Islam SH, Biswas GP, Khan MK, Obaidat MS. Design and analysis of an enhanced patient-server mutual authentication protocol for telecare medical information system. Journal of medical systems. 2015;39(11):1–20. 10.1007/s10916-015-0307-2 [DOI] [PubMed] [Google Scholar]
- 32. Amin R, Islam SH, Biswas GP, Khan MK, Kumar N. An efficient and practical smart card based anonymity preserving user authentication scheme for TMIS using elliptic curve cryptography. Journal of medical systems. 2015;39(11):1–18. 10.1007/s10916-015-0351-y [DOI] [PubMed] [Google Scholar]
- 33. Wu ZY, Chung Y, Lai F, Chen TS. A password-based user authentication scheme for the integrated EPR information system. Journal of medical systems. 2012;36(2):631–638. 10.1007/s10916-010-9527-7 [DOI] [PubMed] [Google Scholar]
- 34. Lee TF, Chang IP, Lin TH, Wang CC. A secure and efficient password-based user authentication scheme using smart cards for the integrated epr information system. Journal of medical systems. 2013;37(3):1–7. [DOI] [PubMed] [Google Scholar]
- 35.Kocher P, Jaffe J, Jun B. Differential power analysis. In: Annual International Cryptology Conference. Springer; 1999. p. 388–397.
- 36. Wen F. A more secure anonymous user authentication scheme for the integrated EPR information system. Journal of medical systems. 2014;38(5):1–7. 10.1007/s10916-014-0042-0 [DOI] [PubMed] [Google Scholar]
- 37. Li CT, Weng CY, Lee CC, Wang CC. Secure user authentication and user anonymity scheme based on quadratic residues for the integrated EPRIS. Procedia Computer Science. 2015;52:21–28. 10.1016/j.procs.2015.05.008 [DOI] [Google Scholar]
- 38. Das AK. A secure and robust password-based remote user authentication scheme using smart cards for the integrated epr information system. Journal of medical systems. 2015;39(3):1–14. 10.1007/s10916-015-0204-8 [DOI] [PubMed] [Google Scholar]
- 39. Mir O, van der Weide T, Lee CC. A secure user anonymity and authentication scheme using AVISPA for telecare medical information systems. Journal of Medical Systems. 2015;39(9):1–16. 10.1007/s10916-015-0265-8 [DOI] [PubMed] [Google Scholar]
- 40. Li CT, Weng CY, Lee CC, Wang CC. A hash based remote user authentication and authenticated key agreement scheme for the integrated EPR information system. Journal of medical systems. 2015;39(11):1–11. 10.1007/s10916-015-0322-3 [DOI] [PubMed] [Google Scholar]
- 41. Jin ATB, Ling DNC, Goh A. Biohashing: two factor authentication featuring fingerprint data and tokenised random number. Pattern recognition. 2004;37(11):2245–2255. 10.1016/j.patcog.2004.04.011 [DOI] [Google Scholar]
- 42. Chung Y, Choi S, Lee Y, Park N, Won D. An Enhanced Lightweight Anonymous Authentication Scheme for a Scalable Localization Roaming Service in Wireless Sensor Networks. Sensors. 2016;16(10):1653 10.3390/s16101653 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 43. Kang D, Jung J, Mun J, Lee D, Choi Y, Won D. Efficient and robust user authentication scheme that achieve user anonymity with a Markov chain. Security and Communication Networks. 2016;9(11):1462–1476. 10.1002/sec.1432 [DOI] [Google Scholar]
- 44. Jung J, Kim J, Choi Y, Won D. An Anonymous User Authentication and Key Agreement Scheme Based on a Symmetric Cryptosystem in Wireless Sensor Networks. Sensors. 2016;16(8):1299 10.3390/s16081299 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 45. Choi Y, Lee Y, Won D. Security improvement on biometric based authentication scheme for wireless sensor networks using fuzzy extraction. International Journal of Distributed Sensor Networks. 2016;2016:2 10.1155/2016/8572410 [DOI] [Google Scholar]
- 46. Das AK, Goswami A. A secure and efficient uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. Journal of medical systems. 2013;37(3):1–16. 10.1007/s10916-013-9948-1 [DOI] [PubMed] [Google Scholar]
- 47. Burrows M, Abadi M, Needham RM. A logic of authentication In: Proceedings of the Royal Society of London A: Mathematical, Physical and Engineering Sciences. vol. 426 The Royal Society; 1989. p. 233–271. [Google Scholar]
- 48.Stallings W. Cryptography and network security: principles and practices. Pearson Education India; 2006.
- 49. FIPS P. 180–1. Secure hash standard. National Institute of Standards and Technology. 1995;17:45. [Google Scholar]
- 50.AVISPA, Automated validation of internet security protocols and applications. http://www.avispa-project.org (accessed October 2014).
- 51.Von Oheimb, D. (2005, September). The high-level protocol specification language HLPSL developed in the EU project AVISPA. In Proceedings of APPSEM 2005 workshop (pp. 1–17).
- 52.AVISPA, AVISPA web tool. http://www.avispa-project.org/web-interface/expert.php (accessed on October 2014).
- 53. Dolev D, Yao AC. On the security of public key protocols. IEEE Transactions on information theory. 1983;29(2):198–208. 10.1109/TIT.1983.1056650 [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
All relevant data are within the paper.