Abstract
At present, users can utilize an authenticated key agreement protocol in a Wireless Sensor Network (WSN) to securely obtain desired information, and numerous studies have investigated authentication techniques to construct efficient, robust WSNs. Chang et al. recently presented an authenticated key agreement mechanism for WSNs and claimed that their authentication mechanism can both prevent various types of attacks, as well as preserve security properties. However, we have discovered that Chang et al’s method possesses some security weaknesses. First, their mechanism cannot guarantee protection against a password guessing attack, user impersonation attack or session key compromise. Second, the mechanism results in a high load on the gateway node because the gateway node should always maintain the verifier tables. Third, there is no session key verification process in the authentication phase. To this end, we describe how the previously-stated weaknesses occur and propose a security-enhanced version for WSNs. We present a detailed analysis of the security and performance of our authenticated key agreement mechanism, which not only enhances security compared to that of related schemes, but also takes efficiency into consideration.
Keywords: wireless sensor networks, session key agreement, off-line password guessing attack, lightweight computation, formal proof
1. Introduction
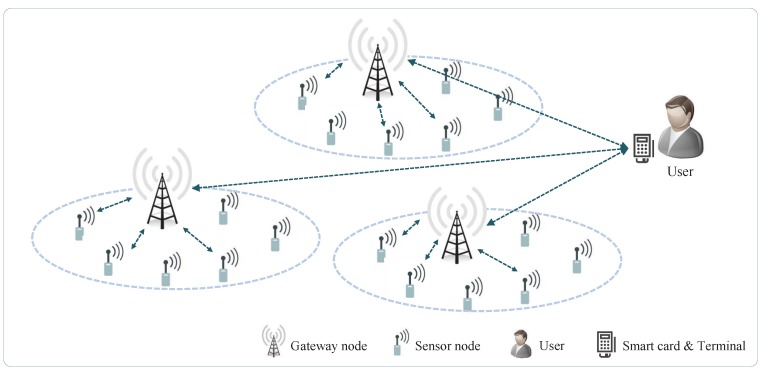
Wireless Sensor Networks (WSNs) are distributed networks composed of tiny autonomous sensors capable of collecting information related to the environment or physical conditions of a target region [1]. WSNs can be implemented in various use cases—including military battlefields, healthcare services and smart grid networks—to provide convenience to users [2]. Figure 1 illustrates the WSN system architecture. As shown in Figure 1, WSN systems are comprised of three parties, including the user, the gateway nodes and the sensor nodes [1,2]. WSN is made of sensor nodes that are wirelessly connected to a gateway that is then connected to a user. On the other hand, in some WSNs, the sensor nodes can also be connected to each other in order to facilitate multi-hop wireless mesh networks.
Figure 1.
WSN system architecture.
Although users enjoy the simplicity and efficiency in WSNs, security has emerged as a major issue in both academia and industry [3]. Specifically, confidential information including the user’s identity and password should not be exposed even if an unauthorized user eavesdrops on data packets transmitted in the WSN [4]. To guarantee reliability among the communicating parties, an authentication mechanism can afford confidentiality and integrity when users access WSNs [3,4]. At this point, in order to design a secure authentication mechanism for WSNs, the following security requirements should be commonly considered [5,6,7,8,9,10,11,12,13].
User anonymity: Even if an attacker extracts some information stored in the user’s smart card or if it eavesdrops on the messages transmitted in the communication group, the user’s identity should be protected.
Mutual authentication: An authentication mechanism should execute several steps to achieve mutual authentication, which is to test all transmitted messages to judging the legitimacies.
Session key agreement: After the mutual authentication process has completed, the session key should be securely assigned to communication parties on the network.
Password verification process: If a user mistakenly enters an incorrect password in the login phase, the password should be promptly detected before performing the authentication phase.
User friendliness: An authentication mechanism provides a password change procedure with which a user can freely update their password without communicating with the gateway node.
Robustness: User authenticated key agreement schemes should withstand different types of attacks, such as off-line password guessing attacks, replay attacks, insider attacks and impersonation attacks.
Furthermore, the efficiency aspect should be considered when applying the authentication mechanism to the WSN environment because the sensor nodes are limited in terms of their computing resources and power [5]. In other words, when constructing an authentication mechanism for WSNs, a hash function-based method is recommended for use since it requires less computation overhead than public-key cryptosystems, such as RSA, elliptic curves cryptography (ECC) and El-gamal, all of which have a high computational overhead [6,7]. Therefore, the authentication protocol implemented for WSNs should be simple and efficient while also conforming to the required security.
1.1. Related Studies
In 2006, Wong et al. [8] first presented a lightweight user authentication protocol for WSNs. Their protocol improved the efficiency by only employing a one-way hash function and exclusive-OR operation. However, Das [9] pointed out that Wong et al.’s scheme [8] could not withstand many logged-in users with the same login identity attacks and stolen-verifier attacks. Das [9] then suggested an improved version that solved the flaws present in Wong et al.’s method. Unfortunately, Khan and Alghathbar [10] demonstrated in 2010 that Das’s scheme [9] could not withstand a privileged-insider attack and gateway node bypass attack and proposed an enhanced new strategy. In the same year, Chen and Shih [11] also demonstrated that Das’s scheme [9] overlooks parallel session attacks and cannot support a mutual authentication property. Chen and Shih [11] then proposed an enhanced version. In 2012, Vaidya et al. [12] pointed out that Das’s scheme [9], Khan and Alghathbar’s scheme [10] and Chen and Shih’s scheme [11] contained the same vulnerabilities against a lost smart card attack and sensor node impersonation attack. To compensate for these defects, Vaidya et al. [12] suggested their own authentication scheme, arguing that it can withstand various attack types. However, Kim et al. [13] proved in 2014 that Vaidya et al.’s scheme [12] has some weaknesses, such as to user impersonation attacks and gateway node bypass attacks, and thus proposed an upgraded scheme. In 2015, Chang et al. [14] demonstrated that Kim et al.’s scheme [13] could not prevent an impersonation attack, lost smart card attack or man-in-the-middle attack, and it did not provide session key security. Chang et al. [14] then proposed an improved scheme. However, Park and Park [15] pointed out recently that Chang et al’s scheme [14] still had some weaknesses, such as off-line password guessing attack, perfect forward secrecy problem and incorrectness of password change, and proposed an enhanced new version.
In particular, various cryptography techniques were employed in their protocols in order to improve the security for WSNs. Lee [16] and Kumari et al. [17] apply a chaotic map technique in their authentication mechanism. In 2015, Cheng et al. [18] presented an RSA-based authentication method for WSNs. In addition, Yeh et al. [19] proposed an authentication protocol based on elliptic curves cryptography (ECC) for WSNs. However, Han [20] pointed out that Yeh et al.’s scheme [19] could not achieve perfect forward secrecy and fails to provide mutual authentication. To address these weaknesses, Shi and Gong [21] presented a new authentication mechanism for WSNs using an ECC technique. However, Choi et al. [22] demonstrated that Shi and Gong’s mechanism [21] could not satisfy security requirements because their scheme is unsafe against lost smart card attacks and does not provide session key security.
1.2. Motivations and Contributions
In 2015, Chang et al. [14] presented a two-factor user authenticated key agreement scheme for WSNs. They claimed that their scheme could resist an off-line password guessing attack and an impersonation attack, as well as provide session key security. However, we have discovered that Chang et al.’s scheme [14] comprises critical security weaknesses. Their scheme (i) still cannot guarantee protection against an off-line password guessing attack or user impersonation attack, (ii) fails to provide session key security, (iii) is faced with a scalability problem because the gateway nodes in their scheme always maintain verifier tables (iv) and cannot provide session key verification processes.
Our main contribution in this study is as follows. First, we concretely explain the weaknesses in Chang et al.’s scheme. Second, we propose a more developed authentication protocol for WSNs. Third, we show that the proposed mechanism satisfies various security requirements. Finally, we demonstrate that the proposed protocol has better performance than other related studies in terms of the computation cost and time consumption.
1.3. Preliminaries
In this subsection, we first introduce the biohash function [23], which is used in our proposed scheme. Then, we list the notations of Chang et al.’s scheme [14] and our proposed scheme in Table 1.
Table 1.
Notations.
| Value | Description |
|---|---|
| Remote user | |
| Sensor node | |
| Gateway node | |
| , | Identity and password of |
| Biometric information of | |
| New password of | |
| u | Random number of |
| Identity of smart card | |
| Temporary identity for ’s next login | |
| Identity of | |
| K | Secret key generated by the |
| Random numbers | |
| One-way hash function | |
| Biohash function | |
| Pseudo-random function of variable s with key k | |
| Concatenate operation | |
| ⊕ | XOR operation |
| , , , | Current time stamp values |
| Session key | |
| The maximum of the transmission delay time |
1.3.1. Biohash Function
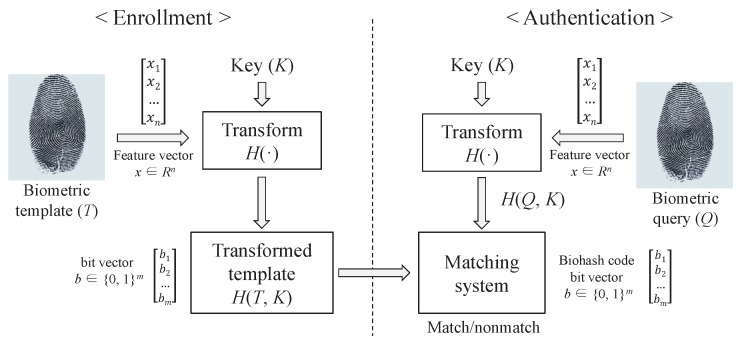
The user’s biometric information is very sensitive data. Thus, when user identification is carried out using biometric data, a secure and sophisticated matching technique is required. In order to handle this concern, in 2004, Jin et al. [23] presented a fingerprint-based function to identify the user’s legitimacy. The biohash technique employs the particular tokenized pseudo-random numbers to each of the users measuring biometric feature arbitrarily onto two-fold strands. Figure 2 describes the user recognition mechanism employing the user’s biometric information and biohashing technique. When a device recognizes user’s biometric template T, it transforms T into the form of feature vector and then transmits to transform function . Transform function creates transformed template by inputting the transmitted template T and random key K. Furthermore, the device creates biohash code, from the random key K and the stored value, which is a biometric query, in order to judge whether the user is registered or not, comparing to the new value, . The biohashing technique is also applied in our scheme, illustrated in Section 5. We use an input value as a combination of the user’s biometric information and a random key for convenience, like other authentication schemes [24,25,26,27] using the biohashing technique.
Figure 2.
Authentication mechanism using the biohashing approach.
The biohash function is a one-way function with a feature that can reduce the probability of the denial of service. That is to say, the identical biometric information creates the identical value of , and it is impossible to calculate an input value from the result value of . Until now, many authentication studies have been conducted [24,25,26,27] based on the biohashing technique. Our proposed scheme also adopts the user’s biometric information applying a biohashing, and the details are given below in Section 5.
1.3.2. Scalability and Practicability in Terms of Authentication Using Biometric Information
The three-factor authentication protocol has been frequently employed in recent days, which complements the two-factor authentication protocol using the identity and password by adding biometric information. Basically, an authentication mechanism using biometric information requires a smart card terminal capable of recognizing a smart card and a device capable of recognizing the user’s biometric (fingerprint) information. To reduce this inconvenience, Baratelli [28] and Kozlay [29] devised a new smart card-based fingerprint identification technology by adding a fingerprint recognition device in the smart card, and Clancy [30] proposed a self-fingerprint authentication technique using a smart card. In other words, a new device that combines a smart card terminal and a fingerprint reader has already been developed. In fact, authentication research does not really mean the inconvenience of fingerprint terminal devices and assumes that devices that can recognize both smart cards and fingerprints are used. In addition, a number of research works with respect to three-factor authentication protocol already [24,25,26,27] have applied user’s biometric information.
First of all, the most important reason for using biometric information in the authentication mechanism is to increase the security of the protocol by preventing identity/password guessing attack. For this reason, our proposed scheme also uses the biometric information of the user, and it is confirmed that the proposed scheme is very safe. A detailed description of the protocol can be found in Section 4, and a security analysis can be found in Section 5.
1.3.3. Notations
The notations used in this paper are listed in Table 1.
1.4. Organization of the Paper
The remainder of this paper is structured as follows. In Section 2, we briefly explain Chang et al.’s authentication scheme. Section 3 demonstrates the vulnerabilities in Chang et al.’s scheme. A detailed explanation of our proposed scheme is provided in Section 4. In Section 5, we evaluate whether our proposed scheme can withstand various attacks. Further, we conduct a formal security proof using the random oracle model in Section 6. In Section 7, we analyze the performance of the proposed scheme, and in Section 8, we provide the conclusion to the paper.
2. Review of Chang et al.’s Scheme
In this section, we briefly review Chang et al.’s authenticated key agreement scheme [14] to then cryptanalyze their scheme. It is composed of four phases: registration, login, authentication and password change. In Chang et al.’s scheme [14], there are three communication parties, including a user , a gateway node and a sensor node . We describe each phase in detail, and Table 1 shows the notations used in Chang et al.’s scheme.
2.1. Registration Phase
-
(1)
selects and , and then generates a random number . computes and sends a registration request to through a secure channel.
-
(2)
computes , , , and and maintains in its database for , where and . chooses a smart card and writes into the smart card’s memory. Then, sends the smart card to through a secure channel.
-
(3)
computes and stores in the smart card’s memory. Finally, the smart card contains the information .
2.2. Login Phase
-
(1)
inserts ’s smart card into a terminal and inputs the and . The smart card computes , , , and compares with the stored value . If this condition is satisfied, the smart card acknowledges the legitimacy of and proceeds with the next step. Otherwise, it terminates this phase.
-
(2)
The smart card computes , and .
-
(3)
Finally, sends a login request to through a public channel.
2.3. Authentication Phase
-
(1)
first checks the validity of the time stamp and retrieves from corresponding to in its database. If cannot search the , retrieves from . , then computes , , , and compares with the received value . If this condition is satisfied, acknowledges the legitimacy of the and proceeds with the next step. Otherwise, it terminates this phase.
-
(2)
computes , , then sends the message to through a public channel.
-
(3)
checks whether . then computes and compares with the received value . If this condition is satisfied, believes that the is authentic. Otherwise, it terminates this phase.
-
(4)
computes , , , and then sends the message to through a public channel.
-
(5)
checks whether . then computes , , and compares with the received value . If true, believes that the is authentic. Otherwise, terminates this phase.
-
(6)
computes , , and updates as in its database. then sends the message to through a public channel.
-
(7)
checks whether . then computes , and compares with the received value . If the verification does not hold, this phase is terminated. Otherwise, believes that the is authentic and computes the shared session key .
-
(8)
computes and . Lastly, updates as and successfully ends the authentication phase.
2.4. Password Change Phase
-
(1)
inserts ’s smart card into a card reader and inputs , the old password and new password . The smart card computes , , , and compares with the stored value . If this condition is not satisfied, it terminates this phase. Otherwise, the smart card proceeds with the next step.
-
(2)
The smart card computes , , and .
-
(3)
The smart card replaces the existing value with the new values .
3. Security Weaknesses of Chang et al.’s Scheme
In this section, we show that Chang et al.’s scheme [14] possesses a number of security vulnerabilities. The following vulnerabilities are based on the two assumptions that
An attacker can extract all parameters stored in the smart card by physically monitoring its power consumption [31].
An attacker can eavesdrop or reform any messages in the public channel [32,33].
Under these two assumptions, the following problems have been found, and their detailed descriptions are given below.
3.1. Off-Line Password Guessing Attack
This attack attempts to input a password until the correct password is discovered because many users have a tendency to employ simple, brief passwords for the sake of convenience. For this reason, the authentication mechanism for all passwords should be invented to guarantee protection against a guessing attack. However, Chang et al.’s scheme [14] has a weakness in this situation, and we therefore propose a scenario for an off-line password-guessing attack. The following is a detailed description:
-
Step 1.
An attacker extracts from ’s stolen smart card by physically monitoring its power consumption [31].
-
Step 2.
The attacker collects a valid login request from the previous session [32,33].
-
Step 3.
The attacker selects a password candidate .
-
Step 4.
The attacker computes using the password candidate .
-
Step 5.The attacker then computes:
-
Step 6.
The attacker repeats the steps above from 3–5 until the computed result equals the breached secret .
-
Step 7.
If they correspond with each other, would be an accurate password. If not, the attacker repeats the above steps until the correct password is found.
Therefore, we can realize that Chang et al.’s scheme [14] is vulnerable to the off-line password guessing attack.
3.2. User Impersonation Attack
The security of the password-based authentication mechanism relies on the complexity of the password. Thus, if an attacker obtains a password, the attacker can pretend to be a legal user. Unfortunately, Chang et al.’s scheme [14] allows an attacker to impersonate a legal user if the attacker obtains the user’s password through a guessing attack. The following is a detailed description of this scenario:
-
Step 1.
An attacker extracts from ’s stolen smart card [31].
-
Step 2.
The attacker collects a valid login request from the previous session.
-
Step 3.
The attacker obtains the user’s through an off-line password guessing attack.
-
Step 4.The smart card computes:
-
Step 5.
The attacker then sends a counterfeited login request to through a public channel.
-
Step 6.
After receiving the , computes , , and .
-
Step 7.
compares the computed value with the received value . Finally, successfully finishes the verification process because , which is computed by the attacker, is correctly equal to , which is computed by the .
Through the aforementioned descriptions, the attacker can successfully pass the checking process and be disguised as a legal user under Chang et al.’s scheme [14].
3.3. Session Key Compromise
In Chang et al.’s scheme [14], if an attacker knows ’s password , the attacker can establish the session key shared between and . First, the attacker can extract from ’s stolen smart card. Second, the attacker can obtain and after eavesdropping on the messages and . Then, the attacker can try to compute using the acquired , which has been previously compromised as in Section 3.1. With the combined values, the attacker can successfully construct the .
3.4. Scalability Problem
In order to provide convenience, Chang et al. [14] suggested that the maintains a verifier table in the database to save the information, such as the user’s temporary identities and value. Accordingly, the should always need to retain each user’s verifier table. However, the increased amount of user information that needs to be retained places greater burden on the since the number of verifier tables will increase as the number of users’ increases. Moreover, the use of the verifier table is inefficient in terms of the computation time since the changed values at each phase need to be updated in the verifier table.
3.5. Absence of a Session Key Verification Process
According to [34,35], the authenticated key agreement mechanism recommends a verification procedure to verify the coherence of the generated session keys between the communicating parties. In the authentication phase in Chang et al.’s scheme [14], generates his/her own session key after verifying the message through . However, in this case, because of the has no information about the session key generated by , and the can hardly be sure whether a new generated session key is precisely the same as the ’s session key or not. Therefore, the following procedures [34] are required to ensure an accurate session key distribution between a and a : (1) after generating a session key, sends a message, including information regarding the generated session key; (2) the should guarantee the accuracy of the session key from the , verifying the received message.
4. The Proposed Scheme
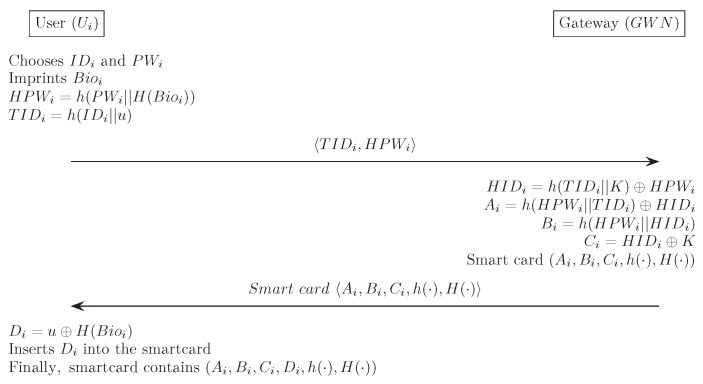
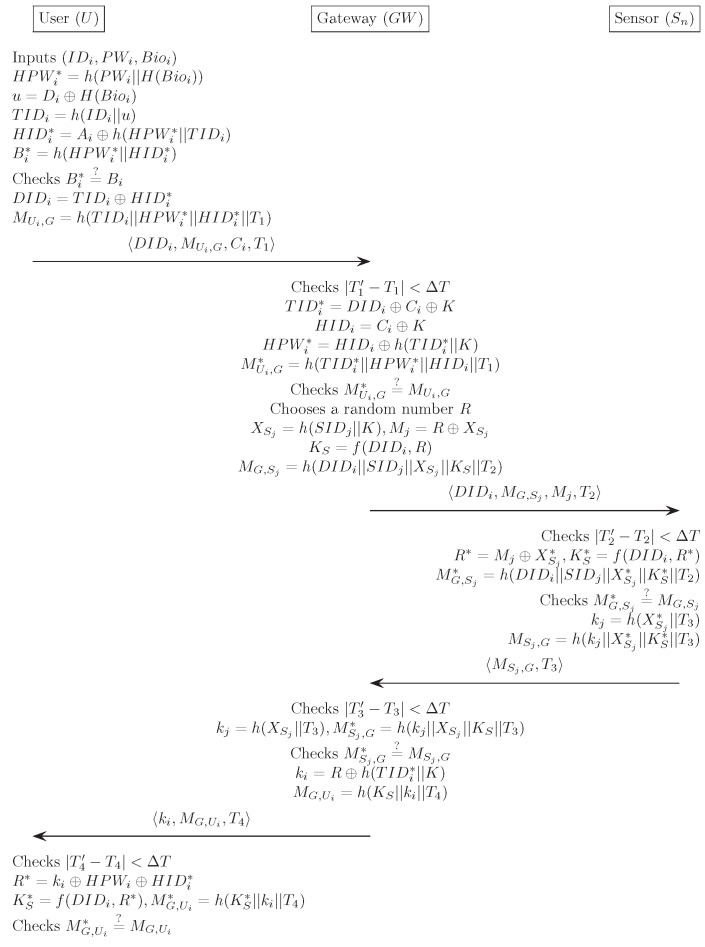
In this section, we suggest an improved version of the authenticated key agreement mechanism for the WSN in order to provide improved security by resolving Chang et al.’s [14] weaknesses. In the proposed scheme, to guarantee protection from the off-line password guessing attack, we employ biometrics information with the biohashing technique [23], as mentioned in Section 1.3. By preventing an off-line password guessing attack, our scheme can guarantee protection against an impersonation attack and against session key compromise. In addition, we remove the verifier table stored in to increase efficiency. Our proposed scheme also consists of four phases: registration, login, authentication and password change. We describe each phase in detail, and Figure 3, Figure 4 and Figure 5 describe our scheme. The notation used in the proposed scheme is displayed in Table 1.
Figure 3.
Registration phase for the proposed scheme.
Figure 4.
Login and authentication phase for the proposed scheme.
Figure 5.
Password change phase for the proposed scheme.
4.1. Registration Phase
The registration phase begins when the sends a request message for registration to through a secure channel. The then issues a smart card, including some information, and sends it to . Meanwhile, stores pre-defined values and in its memory, where . The following describes this process in detail, and Figure 2 illustrates the registration phase for our proposed scheme.
-
(1)
selects and , and then imprints his/her biometrics . computes , generates a random number u and computes . sends a registration request to through a secure channel.
-
(2)
computes , , and . chooses a smart card and writes into the smart card’s memory. Then, sends the smart card to through a secure channel.
-
(3)
Upon receiving the smart card, computes and stores it in the smart card. Finally, the smart card contains the information .
4.2. Login Phase
The login phase is executed whenever the wants to gain access to WSN using his/her , and smart card. In this phase, sends the login request to . Figure 3 illustrates the login and authentication phase for our proposed scheme. The following describes this process in detail.
-
(1)
inserts ’s smart card into a terminal and inputs the , and imprints biometric . The smart card computes , , , , and compares with the stored value . If this condition is satisfied, the smart card acknowledges the legitimacy of the and proceeds to the next step. Otherwise, it terminates this phase.
-
(2)
The smart card computes and .
-
(3)
Finally, sends a login request to through a public channel.
4.3. Authentication Phase
The authentication phase begins when receives the login request from the . This phase performs several steps to achieve mutual authentication, as well as a session key agreement between , and involved within the WSN. The following describes this process in detail.
-
(1)
first checks the validity of the time stamp and computes , and . further computes and compares it with the received value . If this condition is satisfied, acknowledges the legitimacy of the and proceeds with the next step. Otherwise, it terminates this phase.
-
(2)
generates a random number R and computes , , and . then sends the message to through a public channel.
-
(3)
checks whether and computes and . further computes and compares it with the received value . If this condition is satisfied, believes that the is authentic. Otherwise, it terminates this phase.
-
(4)
computes and . then sends the message to through a public channel.
-
(5)
checks whether . computes , and compares with the received value . If true, believes that the is authentic. Otherwise, terminates this phase.
-
(6)
computes and . then sends the message to through a public channel.
-
(7)
checks whether and computes and . further computes and compares it with the received value . If this condition is not satisfied, this phase is terminated. Otherwise, believes that the is authentic and successfully ends the authentication phase
4.4. Password Change Phase
The password change phase begins when the intends to change the original password to a new password . Figure 4 illustrates the password change phase for our proposed scheme. The following describes this process in detail.
-
(1)
inserts ’s smart card into a terminal, inputs , , and then imprints biometric . The smart card computes , , , , and compares with the stored value . If this condition is not satisfied, it terminates this phase. Otherwise, the smart card proceeds with the next step.
-
(2)
The smart card computes , and .
-
(3)
The smart card replaces the existing values and with the new values and , respectively. Finally, the smart card contains the information .
5. Security Analysis and Proof of the Proposed Scheme
In this section, we first describe whether the proposed scheme can withstand various attacks and also satisfy the basic requirements. Moreover, we adopt Burrows–Abadi–Needham (BAN) logic [36] to prove that a session key can be correctly generated between and . The results are described as follows.
5.1. Informal Security Analysis of the Proposed Scheme
In this subsection, our proposed scheme is examined against various attacks and is evaluated according to the suitability of the basic requirements [5,6,7,8,9,10,11,12,13]. We also conduct a comparative analysis [10,12,13,14,15], which is illustrated in Table 2.
Table 2.
Security comparison of our proposed scheme and other related schemes.
| Features | Khan et al. [10] | Vaidya et al. [12] | Kim et al. [13] | Chang et al. [14] | Park et al. [15] | Our Scheme |
|---|---|---|---|---|---|---|
| User anonymity | × | × | √ | √ | √ | √ |
| Mutual authentication | × | √ | √ | √ | √ | √ |
| Stolen smart card attack | × | × | × | × | √ | √ |
| Replay attack | √ | √ | √ | √ | √ | √ |
| Off-line PW guessing attack | × | √ | √ | × | √ | √ |
| impersonation attack | × | × | √ | × | √ | √ |
| impersonation attack | × | √ | × | √ | √ | √ |
| Password verification | √ | √ | √ | √ | √ | √ |
| Session key verification | × | × | × | × | × | √ |
| Privileged-insider attack | √ | √ | √ | √ | √ | √ |
| Session key security | × | × | × | × | √ | √ |
| Efficient password change | √ | √ | √ | √ | √ | √ |
| bypass attack | × | × | √ | √ | √ | √ |
| Off-line ID guessing attack | × | × | √ | √ | √ | √ |
| No verifier table | √ | √ | √ | × | × | √ |
| Formal proof | × | √ | × | √ | √ | √ |
• The proposed scheme preserves user anonymity:
User anonymity is a valuable property for the user authentication protocol because the exposure of a user’s identity can allow an unauthorized party to track the user’s login pattern. Suppose that the attacker has intercepted ’s login request and extracted information in a stolen smart card [31]. The attacker may then try to compute through . However, it is impossible to know since consists of and the secret key K is only known to . In addition, u includes information that is only known to . Therefore, the attacker cannot acquire the user’s .
• The proposed scheme achieves mutual authentication:
In the authentication phase of our scheme, , and authenticate each other through some checking processes. In detail, first verifies the login request by checking whether = . also verifies the message by checking whether = . In addition, and verify the messages and by checking and , respectively. Thus, all transmitted messages in our scheme are successfully verified, and our scheme can achieve mutual authentication.
• The proposed scheme withstands stolen smart card attacks:
In our scheme, even if an attacker extracts secret values stored in a stolen smart card through the power consumption technique [31], the attack cannot lead to other malicious attacks. In order to obtain the , the attack has to know the secret key K and . However, it is impossible to know the K and . Therefore, if the attacker does not know the user’s , the attacker cannot impersonate a legitimate user. Thus, our proposed scheme can withstand a stolen smart card attack.
• The proposed scheme withstands replay attacks:
In our scheme, all transmitted messages include current time stamp values, such as or . Therefore, even if an attacker intercepts the login request message and tries to login , the attacker cannot pass the time stamp checking process during the authentication phase. Thus, our proposed scheme can withstand a replay attack.
• The proposed scheme withstands off-line password guessing attacks:
An off-line password guessing attack occurs when an attacker attempts to guess a password and eventually finds the exact user’s password in an off-line environment. This comes from the tendency that many users create simple and brief passwords for their personal convenience, which makes the attacker easily acquire the users’ password by guessing the off-line password without a time limit [37]. For these reasons, the authentication schemes for all password-based users should be designed to prevent a guessing attack.
In our scheme, the attacker can obtain from the stolen smart card [31] and can intercept the login request . Using these values, the attacker may try to guess the correct identity and password through or . However, without knowing , the attacker cannot guess . In addition, is hashed biometric information, which is only known by . Therefore, our proposed scheme is secure against off-line password guessing attacks.
• The proposed scheme withstands user impersonation attacks:
In order to impersonate a legitimate , the attacker should modify the login request after obtaining the value of . However, as we mentioned above, it is impossible for an attacker to obtain the value of . Thus, the attacker fails to compute and cannot generate a sufficient login request to cheat . Therefore, our proposed scheme can withstand a user impersonation attack.
• The proposed scheme withstands sensor node impersonation attacks with node capture:
Suppose that the attacker captures the sensor node and extracts information [13]. The attacker then tries to modify the message to impersonate a legitimate . However, the attacker cannot generate a valid message because consists of , and it is not feasible to obtain the K. Therefore, the attacker cannot impersonate a valid sensor node.
• The proposed scheme provides password verification process:
There is a possibility that a user inputs an incorrect password by mistake. However, for the password verification procedure, the incorrect password will be detected after performing the authentication phase. Our scheme considers this kind of inefficiency situation, verifying the correctness of password by checking the value at the beginning of the login phase.
• The proposed scheme provides the session key verification process:
In our scheme, after generating a session key , computes and sends the message to . then computes and , and sends the message to . After receiving the message, computes , and and then compares with the received value . Since includes the information of the session key , may be sure that the generated by and is accurate if the comparison result is correct. Therefore, our scheme provides a session key verification process.
• The proposed scheme withstands privileged-insider attacks:
An insider attack means that an insider can directly obtain the user’s password from the server and can then access the user’s account in another server by using the same password. During the registration phase of our scheme, is transmitted not as a revealed condition, but as a form of when sends a registration request to . Accordingly, the insider attacker in cannot identify the ’s . Thus, our scheme can withstand an insider attack.
• The proposed scheme provides session key security:
In our scheme, in order to compromise the session key , the attacker should know the random number R. Therefore, the attacker may try to obtain R through . However, it is impossible for an attacker to compute R because the attacker cannot obtain K, which is only known to . Thus, our authentication scheme ensures session key security.
• The proposed scheme provides an efficient password change phase:
In general, when a password change occurs, it is encouraged for the verification process to be carried out without any assistance from the to ensure user friendliness and efficiency [24]. Our proposed scheme performs existing password checks in the self-verification process within the smart card. After checking the process through , the computed values from the new password will be switched with the existed values in a convenient and efficient way.
• The proposed scheme withstands gateway node bypass attacks:
During the authentication phase of our scheme, the attacker may try to construct the message using the parameters stored in the stolen smart card [31] in order to impersonate a legitimate . However, the attacker cannot compute because K is not public information. Thus, the attacker cannot construct a sufficient message to cheat . Eventually, the attacker cannot impersonate a valid .
• The proposed scheme withstands off-line identity guessing attacks:
Suppose that the attacker extracts all of the secret information from the smart card and intercepts ’s login request . Using these values, the attacker may try to guess the correct identity through , , , and . However, in order to successfully guess the , the attacker should know the random number u. Even though the attacker knows the , the attacker fails to compute because is not public information. Therefore, our proposed scheme can withstand an off-line identity guessing attack.
5.2. Authentication Proof Using BAN Logic
In this subsection, we use BAN logic to verify the legitimacy of the session keys distributed to participants who communicate in the proposed scheme. BAN logic [36] is applied as a well-known formal logic to analyze the security of cryptographic protocols. The basic notation for BAN logic is as follows.
: U sees condition C.
: Condition C is believed by U
: It makes a fresh C.
: U expresses the condition C.
: U and S share a secret key K.
: Condition C is handled by U.
: Perform the hash operation on C using K.
BAN logic also offers five logic rules as follows.
Rule 1. Message-meaning rule: : if U trusts that the key K is shared with S, U sees the C combined with K, then U trusts S once said C.
Rule 2. Nonce-verification rule: : if U trusts that C’s freshness and U trusts S once said C, then U trusts that S trusts C.
Rule 3. Believe rule: : if U trusts C and M, are also trusted by U.
Rule 4. Freshness-conjuncatenation rule: : if freshness of C is trusted by U, then U can trust the freshness of full condition.
Rule 5. Jurisdiction rule: : if U trusts that S has jurisdiction over C, and U trusts that S trusts a condition C, then U also trusts C.
Through our analysis, we will intend to satisfy the following four goals.
Goal 1:
Goal 2:
Goal 3:
Goal 4:
Next, all transmitted messages can be transmuted into an idealized form as follows.
Message 1: :
Message 2: :
Message 3: :
Message 4: :
In order to analyze our authentication mechanism, we define some assumptions as follows.
A1:
A2:
A3:
A4:
A5:
A6:
A7:
A8:
A9:
A10:
Now, we describe our main proof as follows. In order to describe our proof, we use predefined information, including five logic rules, four messages and ten assumptions.
-
According to the Message 1, we could derive the following:
V1:
-
Based on Assumption A8 and Rule 1, we derive:
V2:
-
Based on Assumption A1 and Rule 4, we derive:
V3:
-
Based on V2, V3 and Rule 2, we derive:
V4:
-
According to Message 2, we derive:
V5:
-
Based on Assumption A6 and Rule 1, we derive:
V6:
-
Based on Assumption A2 and Rule 4, we derive:
V7:
-
Based on V6, V7 and Rule 2, we derive:
V8:
-
According to Message 3, we derive:
V9:
-
Based on Assumption A5 and Rule 1, we derive:
V10:
-
Based on Assumption A3 and Rule 4, we derive:
V11:
-
Based on V10, S11 and Rule 2, we derive:
V12:
-
According to Message 4, we derive:
V13:
-
Based on Assumption A7 and Rule 1, we derive:
V14:
-
Based on Assumption A4 and Rule 4, we derive:
V15:
-
Based on V14, V15 and Rule 2, we derive:
V16:
-
Based on V12, V16 and the session key , we derive:
V17: (Goal 3)
-
Based on V4, V8 and the session key , we derive:
V18: (Goal 4)
-
Based on Assumption A9, V17 and Rule 5, we derive:
V19: (Goal 1)
-
Based on assumption A10, V18 and Rule 5, we derive:
V20: (Goal 2)
The above description clearly shows that , and achieve the mutual authentication property. In addition, based on Goal 1, Goal 2, Goal 3 and Goal 4, we can assure that the session key is securely shared between them.
6. Formal Security Proof of the Proposed Scheme
In this section, we have demonstrated that the proposed scheme is secure through a formal proof using the random oracle model. First, we specify a cryptographic one-way hash function as follows.
Definition 1.
A hash function is a one-direction function [38,39] that takes the input of arbitrary length and outputs a bit string with a fixed-length , which is referred to as the “message digest” or “hash value”. When using cryptographic hash functions, the following three common levels of security must be considered:
It is impossible to acquire the input x under the conditions of the hash value and the given hash function .
It is impossible to acquire another input , when given the input x and .
It is impossible to acquire the inputs , where , when given .
Reveal: Given the hash result , this random oracle will unconditionally output the input x.
Theorem 1.
A one-way hash function is assumed to operate like an oracle. Under this assumption, our proposed mechanism is provably secure against an attacker to protect ’s personal information, such as identity , password , biometrics and the ’s secret key K.
Proof.
A similar method as that used in [26] is applied in our authentication mechanism to formally verify the security. For the proof, we assume that an attacker is able to derive ’s identity , password , biometrics and the ’s secret key K. For this, runs the experimental algorithm that is shown in Algorithm 1, for our anonymous user authentication with key agreement scheme (AUAKAS). We define the success probability for as , where means the probability of . The advantage function for this experiment becomes in which the maximum is determined by three factors: all of , the execution time t and the number of queries derived from the Reveal oracle. If attacker is assumed to be able to resolve the hash function problem, could directly obtain ’s identity , password , biometrics and the ’s secret key K. Refer to the attack experiment described in Algorithm 1. In this case, will discover the complete connections between and . However, it is computationally infeasible to invert a one-way hash function , i.e., , . Then, we have , since depends on . Therefore, our proposed scheme is provably secure against the attacker for deriving and K. ☐
Algorithm 1: Algorithm . 1. Eavesdrop login request message during the login phase.
2. Call the Reveal oracle. Let
3. Call the Reveal oracle. Let
4. Computes
5. if then
6. Accepts as the correct of user
7. Call the Reveal oracle. Let
8. Computes
9. if then
10. Accepts and as the correct and of user
11. Call the Reveal oracle. Let
12. if then
13. Accept as the correct secret key K of gateway node
14. return 1 (Success)
15. else
16. return 0
17. end if
18. else
19. return 0
20. end if
21. else
22. return 0
23. end if
Theorem 2.
The one-way hash function is assumed to perform as an oracle, and the smart card for is stolen by an adversary . Under these assumptions, our proposed mechanism is secure against an adversary to derive the password of a user .
Proof.
We assume that an attacker is able to derive the ’s password after extracting the parameters stored in the smart card by physically monitoring its power consumption [31]. then runs the experimental algorithm that is shown in Algorithm 2. We define the success probability for as , where means the probability of . The advantage function for this experiment becomes in which the maximum is determined by three factors: all of , the execution time and the number of queries derived from the Reveal oracle. If , , our scheme is provably secure against the attacker to derive . According to the attack experiment described in Algorithm 2, could obtain ’s password if is able to resolve the hash function problem. However, as shown in Definition 1, it is computationally infeasible to invert a one-way hash function . Then, we have , since depends on . As a result, the proposed scheme is provably secure against attacker to derive even if the smart card is stolen by . ☐
Algorithm 2: Algorithm . 1. Extract the information stored in the smart card
through physically monitoring its power consumption [31].
2. Call the Reveal oracle. Let
3. Call the Reveal oracle. Let
4. Computes
5. Computes
6. if then
7. Accepts as the correct of user
8. return 1 (Success)
9. else
10. return 0
11. end if
7. Performance Analysis of the Proposed Scheme
In this section, we performed a comparison of the computational costs and execution time for the proposed scheme relative to other, related schemes [10,12,13,14,15]. In general, the computational cost is examined based on the respective operations in the authentication protocol. Accordingly, this analysis of the computational cost concentrates on the operations that are conducted by the participant, such as , and . To evaluate the computational costs, we define the following computational parameters.
: the time to execute a one-way hash/pseudo-random function/biohash function.
: the time to execute a XOR operation.
: the time to execute a ECC multiplication.
: the time to execute a fuzzy extractor.
Table 3 provides a summary of the comparison of the computational overhead of the related schemes [10,12,13,14,15]. The results show that Khan and Alghathbar’s scheme [10], Vaidya et al.’s scheme [12], Kim et al.’s scheme [13], Change et al.’s scheme [14], Park and Park’s scheme [15] and the proposed scheme require total computational overheads of , , , , and , respectively.
Table 3.
Comparison of the computational cost between our scheme and other hash-based schemes.
| Phases | Khan et al. [10] | Vaidya et al. [12] | Kim et al. [13] | Chang et al. [14] | Park et al. [15] | Proposed Scheme | |
|---|---|---|---|---|---|---|---|
| Registration | |||||||
| − | − | − | − | − | − | ||
| Login | |||||||
| − | − | − | − | − | − | ||
| − | − | − | − | − | − | ||
| Authen tication | − | ||||||
| Password change | |||||||
| − | − | − | − | − | − | ||
| − | − | − | − | − | − | ||
| Total cost | |||||||
| Execution time | ≈0.008 s | ≈0.015 s | ≈0.0185 s | ≈0.0185 s | ≈0.4605 s | ≈0.017 s | |
Based on the total cost results in Table 3, we have performed an experiment on the execution time to obtain an objective comparison between our scheme and other related schemes [10,12,13,14,15]. The following methods are generally used to measure the execution time for the authentication protocol: (i) determine computational overhead; (ii) measure the execution time of the cryptographic operations used in the protocol; and (iii) substitute the measured time obtained by (ii) into (i). We have measured the execution times using these measurement methods, and the results are shown in the execution time field of Table 3.
The results of the simulation in Li et al.’s and Wazid et al.’s research [40,41] show that the actual execution time for the cryptographic one-way hash function and ECC multiplication is 0.0005 s and 0.063 s, respectively. In addition, according to [41], the execution time of the fuzzy extractor operation is almost the same as the ECC multiplication operation . Thus, we assumed that the time consumption of these two operations is the same. On the other hand, XOR operation is not considered in our measurement because the execution time of the XOR operation is extremely short. Based on the , , and the total computation cost, we finally analyze the execution time. As shown in Table 3, we observed that the execution time of our proposed scheme is of only 0.017 s ( ≈ 34 × 0.0005 s), so it can be considered as a negligible significance. In contrast, the execution times of Kim et al.’s scheme [13], Chang et al.’s scheme [14] and Park and Park’s scheme [15] are 0.0185 s ( ≈ 37 × 0.0005 s), 0.0185 s ( ≈ 37 × 0.0005 s) and 0.4605 s ( ≈ 39 × 0.0005 s + 7 × 0.063 s), respectively. Therefore, our scheme turned out to have a slightly better efficiency than these schemes [13,14,15]. Even if our scheme requires slightly more computation time than Khan and Alghathbar’s scheme [10] and Vaidya et al.’s scheme [12], this is acceptable because our scheme has more effective security features and a higher security level, as shown in Table 2.
8. Conclusions
In this paper, we have demonstrated that Chang et al.’s scheme has a number of critical weaknesses, and we propose an authentication mechanism with enhanced security to overcome these weaknesses. Our proposed scheme has been thoroughly verified in terms of its variety of security features, and the proof result demonstrates that our scheme can guarantee protection against various types of attacks, even if the smart card is stolen by an attacker. In addition, a performance comparison for the proposed scheme in relation to the schemes proposed in other studies was carried out, and we consider that our proposed scheme has sufficient efficiency for WSNs.
Acknowledgments
This work was supported by Institute for Information and Communications Technology Promotion (IITP) grant funded by the Korea government (MSIP) (No. R0126-15-1111, The Development of Risk-based Authentication·Access Control Platform and Compliance Technique for Cloud Security).
Author Contributions
J.J., J.M. and D.L. conceived of and designed the experiments. J.J. performed the experiments. J.J. and Y.M. analyzed the data. J.J. and D.W. wrote the paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Yick J., Mukherjee B., Ghosal D. Wireless sensor network survey. Comput. Netw. 2008;52:2292–2330. doi: 10.1016/j.comnet.2008.04.002. [DOI] [Google Scholar]
- 2.Chong C.Y., Kumar S.P. Sensor networks: Evolution, opportunities, and challenges. Proc. IEEE. 2003;91:1247–1256. doi: 10.1109/JPROC.2003.814918. [DOI] [Google Scholar]
- 3.Choi Y., Nam J., Lee D., Kim J., Jung J., Won D. Security Enhanced Anonymous Multi-Server Authenticated Key Agreement Scheme Using Smart Cards and Biometrics. Sci. World. J. 2014;2014:281305. doi: 10.1155/2014/281305. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 4.Nam J., Kim M., Paik J., Lee Y., Won D. A provably-secure ECC-based authentication scheme for wireless sensor networks. Sensors. 2014;14:21023–21044. doi: 10.3390/s141121023. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 5.Claycomb W.R., Shin D. A novel node level security policy framework for wireless sensor networks. J. Netw. Comput. Appl. 2011;34:418–428. doi: 10.1016/j.jnca.2010.03.004. [DOI] [Google Scholar]
- 6.Watro R., Kong D., Cuti S.F., Gardiner C., Lynn C., Kruus P. TinyPK: Securing sensor networks with public key technology; Proceedings of the 2nd ACM Workshop on Security of Ad Hoc and Sensor Networks; Washington, DC, USA. 25 October 2004; pp. 59–64. [Google Scholar]
- 7.Hwang M.S., Li L.H. A new remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 2000;46:28–30. doi: 10.1109/30.826377. [DOI] [Google Scholar]
- 8.Wong K.H., Zheng Y., Cao J., Wang S. A dynamic user authentication scheme for wireless sensor networks; Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing; Taichung, Taiwan. 5–7 June 2006; pp. 1–9. [Google Scholar]
- 9.Das M.L. Two-factor user authentication scheme in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009;8:1086–1090. doi: 10.1109/TWC.2008.080128. [DOI] [Google Scholar]
- 10.Khan M.K., Alghathbar K. Cryptanalysis and security improvements of two-factor user authentication in wireless sensor networks. Sensors. 2010;10:2450–2459. doi: 10.3390/s100302450. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 11.Chen T.H., Shih W.K. A Robust Mutual Authentication Protocol for Wireless Sensor Networks. ETRI J. 2010;32:704–712. doi: 10.4218/etrij.10.1510.0134. [DOI] [Google Scholar]
- 12.Vaidya B., Makrakis D., Mouftah H. Two-factor mutual authentication with key agreement in wireless sensor networks. Secur. Commun. Netw. 2012;9:171–183. doi: 10.1002/sec.517. [DOI] [Google Scholar]
- 13.Kim J., Lee D., Jeon W., Lee Y., Won D. Security Analysis and Improvements of Two-Factor Mutual Authentication with Key Agreement in Wireless Sensor Networks. Sensors. 2014;14:6443–6462. doi: 10.3390/s140406443. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 14.Chang I.P., Lee T.F., Lin T.H., Liu C.M. Enhanced Two-Factor Authentication and Key Agreement Using Dynamic Identities in Wireless Sensor Networks. Sensors. 2015;15:29841–29854. doi: 10.3390/s151229767. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 15.Park Y., Park Y. Three-Factor User Authentication and Key Agreement Using Elliptic Curve Cryptosystem in Wireless Sensor Networks. Sensors. 2016;16:2123. doi: 10.3390/s16122123. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 16.Lee T.F. Efficient and Secure Temporal Credential-Based Authenticated Key Agreement Using Extended Chaotic Maps for Wireless Sensor Networks. Sensors. 2015;15:14960–14980. doi: 10.3390/s150714960. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 17.Kumari S., Li X., Wu F., Das A.K., Arshad H., Khan M.K. A user friendly mutual authentication and key agreement scheme for wireless sensor networks using chaotic maps. Future Gen. Comput. Syst. 2016;63:56–75. doi: 10.1016/j.future.2016.04.016. [DOI] [Google Scholar]
- 18.Cheng C.Y., Lin I.C., Huang S.Y. An RSA-like scheme for multiuser broadcast authentication in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2015;2015:200. doi: 10.1155/2015/743623. [DOI] [Google Scholar]
- 19.Yeh H.L., Chen T.H., Liu P.C., Kim T.H., Wei H.W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors. 2011;11:4767–4779. doi: 10.3390/s110504767. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 20.Han W. Weakness of a Secured Authentication Protocol for Wireless Sensor Networks Using Elliptic Curves Cryptography. [(accessed on 27 June 2011)]. Available online: http://eprint.iacr.org/2011/293. [DOI] [PMC free article] [PubMed]
- 21.Shi W., Gong P. A new user authentication protocol for wireless sensor networks using elliptic curves cryptography. Int. J. Distrib. Sens. Netw. 2013;2013:730831. doi: 10.1155/2013/730831. [DOI] [Google Scholar]
- 22.Choi Y., Lee D., Kim J., Jung J., Nam J., Won D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors. 2014;14:10081–10106. doi: 10.3390/s140610081. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 23.Jin A.T.B., Ling D.N.C., Goh A. Biohashing: Two factor authentication featuring fingerprint data and tokenised random number. Pattern Recogn. 2004;37:2245–2255. doi: 10.1016/j.patcog.2004.04.011. [DOI] [Google Scholar]
- 24.Moon J., Choi Y., Kim J., Won D. An Improvement of Robust and Efficient Biometrics Based Password Authentication Scheme for Telecare Medicine Information Systems Using Extended Chaotic Maps. J. Med. Syst. 2016;40:1–11. doi: 10.1007/s10916-015-0422-0. [DOI] [PubMed] [Google Scholar]
- 25.Mishra D., Das A.K., Mukhopadhyay S. A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Syst. Appl. 2014;41:8129–8143. doi: 10.1016/j.eswa.2014.07.004. [DOI] [Google Scholar]
- 26.Moon J., Choi Y., Jung J., Won D. An Improvement of Robust Biometrics-Based Authentication and Key Agreement Scheme for Multi-Server Environments Using Smart Cards. PLoS ONE. 2015;10:e0145263. doi: 10.1371/journal.pone.0145263. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 27.Das A.K., Goswami A. A secure and efficient uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J. Med. Syst. 2013;37:1–16. doi: 10.1007/s10916-013-9948-1. [DOI] [PubMed] [Google Scholar]
- 28.Baratelli P.J. Smart Card with Integrated Fingerprint Reader. No. 6325285 B1. U.S. Patent. 2001 Dec 4;
- 29.Kozlay D. Design & Method for Manufacturing Low-Cost Smartcards with Embedded Fingerprint Authentication System Modules. No. US20050139685 A1. U.S. Patent. 2004 Jul 6;
- 30.Clancy T.C., Kiyavash N., Lin D.J. Secure smartcard-based fingerprint authentication; Proceedings of the 2003 ACM SIGMM Workshop on Biometrics Methods and Applications; Berkley, CA, USA. 2–8 November 2003; pp. 45–52. [Google Scholar]
- 31.Kocher P., Jaffe J., Jun B. Differential power analysis; Proceedings of the Advances in Cryptology-CRYPTO’99, LNCS; Santa Barbara, CA, USA. 15–19 December 1999; pp. 388–397. [Google Scholar]
- 32.Chung Y., Choi S., Lee Y., Park N., Won D. An Enhanced Lightweight Anonymous Authentication Scheme for a Scalable Localization Roaming Service in Wireless Sensor Networks. Sensors. 2016;16:1653. doi: 10.3390/s16101653. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 33.Kang D., Jung J., Mun J., Lee D., Choi Y., Won D. Efficient and robust user authentication scheme that achieve user anonymity with a Markov chain. Secur. Commun. Netw. 2016;9:1462–1476. doi: 10.1002/sec.1432. [DOI] [Google Scholar]
- 34.Blake-Wilson S., Johnson D., Menezes A. Key agreement protocols and their security analysis; Proceedings of the IMA International Conference on Cryptography and Coding; Cirencester, UK. 17–19 December 1997; pp. 30–45. [Google Scholar]
- 35.Islam S.H., Khan M.K., Li X. Security analysis and improvement of ‘a more secure anonymous user authentication scheme for the integrated EPR information system’. PLoS ONE. 2015;10:e0131368. doi: 10.1371/journal.pone.0131368. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 36.Burrows M., Abadi M., Needham R.M. A logic of authentication. Proc. R. Soc. Lond. A. Math. Phys. Sci. 1989;426:233–271. doi: 10.1098/rspa.1989.0125. [DOI] [Google Scholar]
- 37.Ma C.G., Wang D., Zhao S.D. Security flaws in two improved remote user authentication schemes using smart cards. Int. J. Commun. Syst. 2014;27:2215–2227. doi: 10.1002/dac.2468. [DOI] [Google Scholar]
- 38.Stallings W. Cryptography and Network Security: Principles and Practices. Pearson Education; Upper Saddle River, NJ, USA: 2006. [Google Scholar]
- 39.FIPS P. 180-1 . Secure Hash Standard. National Institute of Standards and Technology; Gaithersburg, MD, USA: 1995. [Google Scholar]
- 40.Li C.T., Hwang M.S., Chu Y.P. A secure and efficient communication scheme with authenticated key establishment and privacy preserving for vehicular ad hoc networks. Comput. Commun. 2008;31:2803–2814. doi: 10.1016/j.comcom.2007.12.005. [DOI] [Google Scholar]
- 41.Wazid M., Das A.K., Kumari S., Li X., Wu F. Design of an efficient and provably secure anonymity preserving three-factor user authentication and key agreement scheme for TMIS. Secur. Commun. Netw. 2016;9:1983–2001. doi: 10.1002/sec.1452. [DOI] [Google Scholar]