Abstract
Fog-based VANETs (Vehicular ad hoc networks) is a new paradigm of vehicular ad hoc networks with the advantages of both vehicular cloud and fog computing. Real-time navigation schemes based on fog-based VANETs can promote the scheme performance efficiently. In this paper, we propose a secure and privacy-preserving navigation scheme by using vehicular spatial crowdsourcing based on fog-based VANETs. Fog nodes are used to generate and release the crowdsourcing tasks, and cooperatively find the optimal route according to the real-time traffic information collected by vehicles in their coverage areas. Meanwhile, the vehicle performing the crowdsourcing task can get a reasonable reward. The querying vehicle can retrieve the navigation results from each fog node successively when entering its coverage area, and follow the optimal route to the next fog node until it reaches the desired destination. Our scheme fulfills the security and privacy requirements of authentication, confidentiality and conditional privacy preservation. Some cryptographic primitives, including the Elgamal encryption algorithm, AES, randomized anonymous credentials and group signatures, are adopted to achieve this goal. Finally, we analyze the security and the efficiency of the proposed scheme.
Keywords: fog-based VANETs, real-time navigation, privacy-preserving, spatial crowdsourcing
1. Introduction
Traffic congestion in crowded urban areas has had a number of negative effects on society, such as wasting motorists’ time, increasing air pollution from the wasted fuel, and creating a higher chance of collisions, etc. It is reported that commuters in Beijing spent on average 32 min per hour in traffic jams while traveling during rush hours in 2015 [1]. Hence, it is a common experience for a driver to find a better driving route in a congested area. Since real-time traffic information plays a key role in monitoring road conditions and predicting optimal routes of vehicles, it is certainly worth using a real-time navigation system for drivers on the road to find the optimal route of a certain destination.
For the last few years, global positioning system (GPS) [2] technology has been adopted for navigation systems, such as the Autonavi navigation system [3], which provides convenient navigation services based on a local map database. However, since the road conditions are not updated in time in the local map database, conventional GPS-based navigation systems may guide drivers to erroneous routes if some traffic accidents occur in real time.
In the meantime, vehicular ad hoc networks (VANETs), which act as important elements of the intelligent transportation system, has become increasingly popular in many countries. The navigation system based on VANETs can provide more timely and more accurate traffic information. In a typical VANET, vehicles are equipped with on-board units (OBUs) to perform mobile computation and communication with other nearby vehicles, and with road-side units (RSUs) installed along the road. With the support of VANETs and its crowdsensing capability, real-time road conditions can be collected and transmitted to support the real-time navigation. However, RSUs have limited computation and storage capability, while real-time navigation systems based on crowd sourcing require complex computation and large storage. This challenge has motivated researchers to investigate the new paradigm of VANETs.
Recently, the vehicular cloud has been proposed for big data processing and complicated intelligent analysis on VANET environments [4,5,6]. However, centralized cloud computing is unnecessary and inefficient for the interactive navigation system. To relieve the computation and communication burden on vehicular cloud, fog computing can be adopted. Fog computing, which was firstly proposed by Cisco in 2012 [7], is an extension of the cloud-based Internet by introducing an intermediate layer between mobile devices and cloud, aiming at the smooth, low-latency service delivery from the cloud to mobile. In this paper, we combine vehicular cloud with fog computing, and consider a new paradigm called fog-based VANETs.
Although fog-based VANETs can provide many possible advantages for real-time navigation systems, several security concerns also have to be addressed before the implementation of the system. A navigation system requires that the identity of the vehicle and communication messages should be authenticated and maintain secrecy to guard against the impersonation, message forgery attacks, and eavesdropping. Meanwhile, privacy preservation must be achieved because the private information, such as vehicles’ licenses, location, and speed, etc., needs to be protected. In addition, the authorities should be able to reveal the real identity of the disputed vehicles when necessary.
In this paper, we proposed a secure and privacy-preserving navigation scheme (SPNS) in fog-based VANETs, which use spatial crowdsourcing to collect real-time traffic information and analyze the collected data to provide real-time navigation services to drivers. The security and the privacy preservation of the scheme are also analyzed to evaluate the scheme. In particular, we make the following contributions:
First, we present a model for a secure navigation scheme in fog-based VANETs, which takes advantage of vehicular cloud and fog computing to make up for the limitation of the previous VANET-based navigation system.
Second, we construct a specific scheme that can support real-time navigation service to drivers in a congested area. In this way, drivers can quickly find an available route, and, moreover, gasoline and the time wasted in traffic congestion can be reduced. By using the spatial crowdsourcing, the real-time road conditions can be updated in time in fog-based VANETs. Meanwhile, the vehicle performing the crowdsourcing task can get a reasonable reward. Performance analysis shows that the real-time navigation service supported by the proposed scheme is effective.
Third, the proposed scheme can also ensure the conditional privacy preservation of the vehicles (or drivers), which is regarded as the basic security requirement in VANET communications [8,9,10,11].
The rest of the paper is organized as follows: the system model and design goals are described in Section 2. Some preliminaries are given in Section 3. Our scheme is proposed in Section 4. The security analysis is given in Section 5, and the performance analysis is given in Section 6. Related work is reviewed in Section 7. Finally, Section 8 concludes the paper.
2. System Model and Design Goal
In this section, we define the problem by formalizing the system model and the design goal.
2.1. System Model
In this section, we consider the fog-based VANETs and describe our system model, in which communication nodes include trusted authority (TA), navigation servers (NS) and crowdsourcing servers (CS) residing in the fog, and vehicles as shown in Figure 1. The detailed description of system components is as follows:
TA is trusted and the public agency. For example, the transportation authorities with administrative rights can take on the role of the TA. It is responsible for the registration of fog nodes and vehicles deployed in fog-based VANETs, issuing anonymous credentials and tracing the vehicles’ identity in case of rewarding purpose for spatial crowdsourcing, sending fake traffic information for uncongested driving experience, etc.
The cloud is a set of interconnected computing resources. The cloud provides centralized navigation services for drivers, e.g., Google Map.
Fog node is a highly virtualized computing system, which is deployed at the edge of networks, e.g., banks, bus terminals, shopping halls, etc. Similar to a lightweight cloud server, fog node is equipped with the on-board large volume data storage, computers and wireless communication facility [12]. In our fog-based VANETs, the fog node consists of navigation servers (NS) and crowdsourcing servers (CS) and conventional RSU, which are in charge of releasing crowdsourcing tasks, computing the optimal path for the querying vehicles, and rewarding the crowdsourcing contributors.
Vehicles are equipped with irreplaceable and temper-proof OBU device, which enables performing some simple computations, communicating with other vehicles and fog nodes, and these vehicles have a small amount of read-only memory. In our model, OBU is required to generate real-time navigation query, traffic information reports for spatial crowdsourcing tasks, result retrieving query.
Figure 1.
System model.
As shown in Figure 1, the navigation scheme works as the following. Assume each vehicle and fog node have already registered to the TA. Then, a vehicle can send a navigation query generated by the OBU to the nearby fog node, denoted as fog, at time . The navigation server (NS) in Fog forwards the query to the last Fog which covers the destination by relaying fog nodes hop by hop. Upon receiving the navigation query, each crowdsourcing server (CS) generates and releases a crowdsourcing task of collecting real-time traffic information to vehicles in its coverage area. In addition, the vehicle who wants to perform the task returns a crowdsourcing report and can get a reasonable reward from the CS. Upon receiving the report, CS verifies it and shares the valuable traffic information with NS. The NS computes the optimal path for the querying vehicle in its area. Meanwhile, NS analyzes and forwards the traffic information to the cloud for other services. Finally, the querying vehicle can get successive navigation results from fog nodes by sending navigation result retrieving query when entering the coverage of the fog nodes until it ultimately reaches the desired destination.
2.2. Design Goal
Before describing our design goal for the navigation scheme, we first make necessary assumptions in our system model.
Assumption 1.
TA is fully trusted by all vehicles and fog nodes. TA can communicate with fog nodes and vehicles through a secure channel by the internet or any other reliable communication links with high bandwidth. The TA can also inspect all fog nodes and maintain the compromised entities list.
Assumption 2.
Fog nodes are untrusted. For instance, some honest-but-curious fog nodes may learn the position of specific vehicles and also get some sensitive information for some purposes.
Assumption 3.
The adversary can overhear V2V (Vehicle to Vehicle) and V2I (Vehicle to Infrastructure) communications to obtain any messages for their purposes, such as tracing the identity of some vehicles. Some dishonest vehicles may overhear the communications to obtain the navigation results queried by other vehicles to enjoy free navigation services if they happen to have the same destination.
Assumption 4.
TA, fog nodes, and vehicles have clocks for generation of time stamps and check valid time of navigation query and result retrieving query. They can use GPS satellites as a synchronized time source [13].
Our design goal is to develop a secure and privacy-preserving navigation scheme for vehicles, which can achieve the following desirable requirements: (1) real-time route navigation; (2) authentication; (3) confidentiality; and (4) conditional privacy preservation.
Real-time path navigation: With the guidance of the fog nodes, a vehicle can conveniently find the optimal path to the desired destination.
Authentication: Only legitimate entities should take part in the fog-based VANETs. Fog nodes and vehicles should be able to prove themselves by using certificates or credentials. In addition, the origin of the messages should be authenticated to prevent against the impersonation and message forgery attacks. Meanwhile, the identity of the crowdsourcing contributor should be authenticated to get the reward. In addition, only a legitimate subscriber that has service access rights should be able to get navigation service.
Confidentiality: the navigation query, traffic information report, and navigation result should be kept confidential from eavesdroppers who will illegally use the navigation information for their own purposes.
Conditional privacy preservation: the real identity of the querying vehicle and the crowdsourcing vehicle should be kept secret. Although the location and destination would be exposed to fog nodes, the adversary can neither link a navigaiton query to a specific vehicle nor identify two navigation queries from the same vehicle. However, once an exceptional event occurs, the fog nodes can learn the vehicles’ real identifier with the help of TA.
3. Preliminaries
This section describes some cryptographic primitives which are adopted in our proposed scheme. They are bilinear groups, message-locked encryption, randomized signatures and group signatures.
3.1. Bilinear groups
Bilinear groups are a set of three cyclic groups , , of prime order q with a bilinear map with the following properties:
for all , and , ;
for and , ;
the map e is efficiently computable.
There are three types of pairings defined by Galbraith, Paterson, and Smart [14]: in type 1, ; in type 2, , but there exists an efficient homomorphism while no efficient one exists in the other direction; in type 3, and there is no efficiently computable homomorphism between and in either direction. In this paper, we only consider type 3 pairings, which will guarantee the security of the randomized signatures used in our scheme.
3.2. Message-Locked Encryption
A message-locked encryption (MLE) scheme is a symmetric encryption scheme in which the key used for encryption and decryption is itself derived from the message [15]. Instances of this primitive are seeing widespread deployment and application for the purpose of secure deduplication [16,17,18]. A message-locked encryption scheme MLE = is a five-tuple of polynomial time algorithm, the last two deterministic:
On input , the parameter generation algorithm returns a public parameter P.
On input P and a message M, the key-generation algorithm returns a message-derived key .
On input , the encryption algorithm returns a ciphertext .
On input and a ciphertext C, the decryption algorithm returns .
On input , the tag generation algorithm returns a tag .
Bellare [15] has summarized four MLE schemes: convergent encryption (CE), Hash-and-CE1 (HCE1), Hash-and-CE2 (HCE2), and randomized convergent encryption (RCE). In our scheme, we utilize the RCE to encrypt the crowdsourcing traffic information report.
3.3. Randomized Signatures
Randomized signature [19] is both an efficient and secure signature with the same features as Camenisch-Lysyanskaya (CL)-signatures [20] but consists of only two elements in the signature. It takes advantage of the full potential of type 3 pairings, in which the space of the signatures and the one of the public key are seperated. A randomized signature scheme usually consists of four algorithms:
: given a security parameter k, this algorithm outputs public parameter . These bilinear groups must be of type 3.
: selects and , computes , and sets as and as .
: picks a random to compute a signature .
: parses as and checks whether and are both satisfied. If it is the positive case, it outputs 1, and 0 otherwise.
A randomized signature on m can be randomized by selecting a random and computing , which is still a valid signature on m.
3.4. Group Signatures
The group signature scheme was first introduced by David Chaum and Eugene van Heyst in 1991 [21]. In a group signature scheme, there exists a group manager and several group members, essential to which is a group manager, who is in charge of adding group members and has the ability to reveal the original signer in the event of disputes. A group signature scheme is desired to satisfy three security properties: unforgeability, anonymity, and traceability. Unforgeability ensures that only the group member can generate signatures on behalf of the group. Anonymity means that signatures do not reveal their signer’s identity, except the group manager. Traceability shows that all valid signatures, even those generated by the collusion of multiple group members, can be revoked by the group manager.
4. Proposed Secure and Privacy-Preserving Navigation Scheme
In this section, we present a secure and privacy-preserving navigation scheme (SPNS) in fog-based VANETs, which consists of four parts: (1) system setting; (2) real-time navigation querying; (3) vehicular spatial crowdsourcing; and (4) navigation result retrieving.
4.1. System Setting
Let , and be three cyclic groups of the same large prime order q. Suppose that , and are equipped with a type 3 pairing. Let be a public collision-resistant hash function. The TA first chooses as the master key and computes as its public key. In the end, the TA publishes the system parameters .
Each fog node has a unique identifier to identify its position and a map of its coverage. randomly chooses as its secret key and computes as its public key. In addition, maintains a routing table to determine the next fog node to which the vehicle should move forward.
Each vehicle has a unique identifier . The vehicle randomly chooses to compute , , and sends to the TA to prove its knowledge of v. Then, the TA verifies the validity by checking the equation . If the equation does not hold, the TA returns failure and aborts. Otherwise, the TA picks to compute
In addition, the TA stores in a secure database, and returns to through a secure channel. sets its secret key as and the corresponding public key as .
When starts to travel in the city, it will generate some short-life keys for navigation queries according to the following steps:
chooses m random numbers, as the short-life private keys and computes the corresponding public keys for for the travel;
- for each short-life public key , computes the self-delegated certificate as follows:
-
−randomly choose , , , , compute as follows: , , mod q, , , ;
-
−compute and where mod q; mod q; mod q; and the certificate of is .
-
−anyone can check the validity of by computing: ;;;and check whether holds.
-
−
installs and for into the read-only memory of the OBUs.
4.2. Real-Time Navigation Querying
When a vehicle that is equipped with an OBU is driving on the road, it can send a real-time navigation query to the nearby fog node, denoted as . The real-time query utilizes the OBU to generate the navigation information , , , , , , as shown in Table 1.
Table 1.
The description of navigation information elements.
| Element | Description |
|---|---|
| N | Sequence number: records the query number that is used to distinguish different queries from the same OBU. |
| Short-life public key: If a vehicle sends a navigation query at some time, it will randomly choose a short-life public key from the sequence for stored in the OBU. This field is used to record the public key, which will be also used to reward vehicles in the spatial crowdsourcing step. | |
| Current location: records the current position of the querying vehicle on the unique Euclidean plane. | |
| Desired destination: records the destination where the querying vehicle will arrive. | |
| Current time: records the start querying time. | |
| Expired time: records the exact time after which the query is invalid, because the life-time of the navigation query is fixed. |
Using this navigation information, the querier performs the following steps to generate a navigation query:
utilize to encrypt by randomly choosing , and compute , , ;
select randomly to compute the randomized signture , and the hush function , , and output the group signature ;
finally, send the navigation query Q to the fog node , where .
Upon receiving the navigation query Q, firstly checks whether the destination is in its coverage. If the answer is yes, it will generate a crowdsourcing task to find the optimal route to the destination for the querying vehicle . Otherwise, performs the following steps to forward Q to the next fog node according to its routing table. Meanwhile, it will generate a crowdsourcing task to find the optimal route to the next fog node for the querying vehicle.
Decode by computing ;
- verify the validity of the signature by computing
and checking whether the hash holds. If not, returns failure and aborts; Otherwise, it checks the routing table to find the next fog node, denoted as , according to the destination . randomly chooses to compute , , ;
finally, forwards the query to .
When receives , it performs the same operations as and will forward the query to the next fog node until it reaches the last fog node, denoted as , which covers the destination of the querying vehicle .
4.3. Spatial Crowdsourcing
When receiving a navigation query with a sequence number N, the fog node generates and releases a crowdsourcing task of collecting traffic information to all the vehicles in its coverage area. keeps a tag table , which contains all tags of rewarded vehicles for a specific crowdsourcing task. If a vehicle with the secret key wants to perform this task, it performs the operations as follows:
randomly choose a short-life public key from the for stored in its OBU;
generate a traffic information report including the current location, current time, driving speed and the road condition;
randomly choose to calculate the randomized signature , the hash , and ;
encrypt the traffic information report by using a message-lock encryption algorithm. Choose to compute , the tag , , and ;
finally, returns the crowdsourcing response to .
When receives the crowdsourcing response , it will compute the optimal path to the destination by the following operations:
decode the crowdsourcing response by computing , , and the tag ;
- check whether the equation holds. If not, reject the . Otherwise, it compares the tag with the element in the tag table . If there exists a tag in the tag table satisfying , which means the same traffic information report has been stored in the database, will reject the . Otherwise, it verifies the signature by computing
and checking whether the equation holds. If not, returns failure and aborts; otherwise, it keeps in its database; rewards the contributor based on the short-life public key ;
can compute the optimal path by using Dijkstra’s algorithm in its coverage area;
choose , to calculate , and . Finally, the navigation result for is .
4.4. Navigation Result Retrieval
When the querying vehicle enters the coverage area of , it reads in the OBU, computes and generates the retrieving query .
chooses randomly to compute randomized signature , the hash value , in which is the current time. , and sends to the fog node .
Upon receiving , computes
and checks whether the equation holds. If not, returns failure and aborts; otherwise, it searches for the navigation result in the database based on .
signs the navigation result using its secret key . Randomly choose to compute , , . Finally, sends the navigation result to .
Upon receiving the , computes and checks whether holds. If not, returns failure and aborts; otherwise, it decodes by computing .
4.5. Identity Revocation
Once an accepted message has been disputed, the TA can use the self-delegated certificate of to revoke the real identity of the disputed vehicle. The TA uses its secret key to compute
and can trace the identity by looking up the entry in the secure database.
5. Security Analysis
In this section, we discuss security issues of the proposed navigation scheme SPNS, i.e., authentication, confidentiality, and conditional privacy preservation.
(1) Authentication
The identity authentication of vehicles can be guaranteed by the anonymous credentials issued by the TA through the system setting. For the real-time navigation query, vehicles need to generate some anonymous short-life keys by themselves, the authentication of which can also be provided by self-delegated certificates created by using authorized key A. Meanwhile, in the spatial crowdsourcing phase, crowdsourcing contributor can get the reward by showing the certificate of used in the crowdsourcing response . The identity authentication of fog nodes are also guaranteed by the certificates generated by TA.
Message authentication can be guaranteed by using randomized signatures [19] and Schnorr signatures [22]. In the real-time navigation query phase, vehicles generate signature of the navigation information by using short randomized signatures [19]. In the spatial crowdsourcing phase, vehicle , who wants to perform the crowdsourcing task, returns the crowdsourcing report with a randomized signature . In addition, when a fog node finds the optimal path , it will generate a signature by using its secret key to sign the . The security of the signature depends on the discrete algorithm problem in . In the navigation result retrieving phase, vehicles generate signatures of the retrieving query through randomized signatures, and fog nodes create signatures of the navigation result by using Schnorr signatures. Since both short randomized signatures and Schnorr signatures used in our scheme have proven to be unforgeable, the security of signatures generated in our proposed scheme are secure, which guarantees the message authentication.
(2) Confidentiality
To avoid navigation information being illegally obtained by unauthorized vehicles or adversaries, our scheme takes advantage of the Elgamal encryption algorithm, AES algorithm and the message-lock encryption algorithm to encrypt the transmitted information including real-time navigation query, crowdsourcing response and the navigation result. If the encryption algorithms used in the proposed scheme are secure, confidentiality requirements can be satisfied.
First, we consider the anonymous credential. When vehicle requests an anonymous credential from the TA, it first picks a random number to compute , , and sends to the TA along with a zero-knowledge proof to prove its knowledge of v. Thus, the TA cannot tell the secret key v of the vehicle, if the discrete algorithm problem in and is hard. Then, TA computes the anonymous credential and sends it to the vehicle through a secure channel, so other vehicles can not illegally receive the anonymous credential by eavesdropping messages from the air.
Second, we consider the navigation query. utilizes the public key of the fog node to encrypt by computing , , (), which involves the Elgamal encryption algorithm and AES algorithm. Hence, the confidentiality of the navigation query is guaranteed. Similarly, when the fog node can not find the destination in its coverage, it will transmit the navigation query to the next fog node. The fog node will encrypt the by using the Elgamal encryption algorithm and AES algorithm. Therefore, no other vehicle can eavesdrop on the route even if they want to go to the same destination.
Third, we consider the crowdsourcing report. When a vehicle wants to perform the crowdsourcing task, it will generate a traffic information report . To ensure the confidentiality of the report, , we encrypt it by using the message-lock encryption algorithm RCE [15], which can ensure the confidentiality of the report and avoid the repeated rewarding for the same vehicle.
Finally, we consider the navigation result. The navigation result is encrypted as by using the public key of the querying vehicle based on Elgamal encryption. When a vehicle asks for the navigation result, it can decode the navigation result by using its short-life secret key u. However, other vehicles can not decrypt the ciphertext .
(3) Conditional privacy preservation
In our scheme, although fog nodes can decode ’s short-life public key, current location, and the destination by computing , they can not link this information to some specific vehicle. Because querying vehicle utilizes anonymous credentials to prove itself. To prevent dishonest fog nodes or adversaries from linking the navigation query or the retrieving query to a specific vehicle, provides a randomized version of the credential when generating signatures. Different versions of are unlinkable because linking with for some is equivalent to breaking the DDH assumption in . Furthermore, vehicles use the group signature scheme [21] to sign messages as , which provides conditional anonymity of the signer.
In addition, takes advantage of group signatures [21] to generate short-life keys for for anonymous authentication in the proposed scheme, so only TA can distinguish the real identity of . When vehicle performs the crowdsourcing task, its anonymity and identity privacy can also be guaranteed by the randomly chosen public key .
In conclusion, the anonymity, identity privacy and location privacy of the vehicles have been protected in our scheme. However, once an exceptional event occurs, the fog nodes can learn the vehicle’s real identifier with the help of TA. The TA can use the self-delegated certificate used in the navigation query to trace the identity of the disputed vehicle. Hence, conditional privacy preservation is satisfied in our scheme.
6. Performance Analysis
In this section, we evaluate and compare the computational and communication costs of the proposed scheme SPNS with VSPN (VANET-Based Secure and Privacy-Preserving Navigation Scheme) [23].
Firstly, let denote the time to perform one point scalar multiplication in , with the time of AES encryption, the time of a pairing operation, respectively. Since these operations dominate the speed of the proposed scheme SPNS, we only consider the time taken by these operations and neglect other operations such as one-way hash function, addition and scalar value manipulation. The number of the operations required in each phase of the proposed SPNS are shown in Table 2.
Table 2.
Computational cost of each step in SPNS.
| Phases | TA | Fog Node | Vehicle |
|---|---|---|---|
| System setting | |||
| Querying | 0 | ||
| Crowdsourcing | 0 | ||
| Retrieving | 0 | ||
| Tracing | 0 | 0 |
m is the number of the short-life public keys generated by vehicles and n is the number of the fog nodes that relay the navigation query; SPNS is our proposed scheme.
Next, we consider the computational costs of TA, vehicles and fog nodes in our scheme SPNS compared with VSPN [23]. For the TA side, it is only involved in the system setting and tracing phases. The number of the operations are and in SPNS, compared to and in the protocol VSPN. For the participant TA side, SPNS is less efficient than VSPN because we need more secure parameters for self-delegating short-life public keys and crowdsourcing tasks, which are not mentioned in VSPN. As shown in Table 3, for the vehicles’ side, our scheme needs more operations in the system setting phase to generate self-delegating short-life public keys, which can enhance the anonymity of the vehicles and also avoid delegating public key certificates by CA. Since our scheme accomplishes enhanced security and privacy, our scheme needs more operations than VSPN. Considering the experiment in [24] for an MNT (Miyaji, Nakabayashi, Takano) curve [25] with embedding degree , being represented by 161 bits and order q being represented by 160 bits, on an Intel Pentium IV 3.0-GHz machine, there exists the following results: ms, ms. Our scheme needs ms more to realize the navigation query than VSPN. When retrieving the navigation result from each fog node or RSU, our scheme needs ms more than VSPN. For the fog node side, since the computational capability is stronger than common RSU in our fog-based VANET model, it is efficient to realize the operations in each phase of our SPNS scheme.
Table 3.
Comparison of vehicles’ computational cost.
| Phases | SPNS | VSPN |
|---|---|---|
| Setting | ||
| Querying | ||
| Crowdsourcing | 0 | |
| Retrieving |
m is the number of the short-life public keys generated by vehicles and n is the number of the fog nodes that relay the navigation query; SPNS is our proposed scheme; VSPN is the VANET-Based Secure and Privacy-Preserving Navigation Scheme proposed in [23].
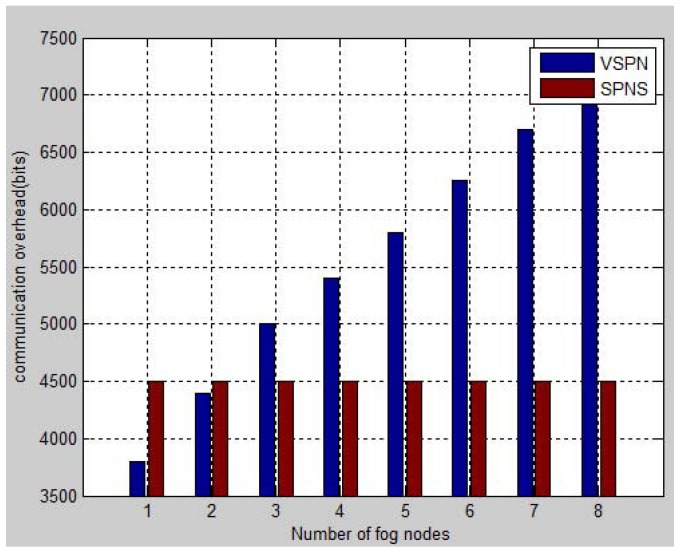
In terms of the communication overhead, VSPN needs the initial RSU, , to forward the navigation request Q to its neighbors until Q reaches the last RSU, covering the destination. After constructs the navigation reply message, it sends the message back along the reverse path to the initial RSU, . Furthermore, the querying vehicle can get the the navigation result from the . This procedure needs much communication among RSUs. In contrast to VSPN, our SPNS does not require the fog nodes to return the navigation results to the first fog node. Instead, the querying vehicle can retrieve the navigation result from each fog node and use it to find a proper route to the destination or to the next fog node. In this way, the communication overhead among fog nodes is significantly reduced. Figure 2 shows the comparison results of SPNS and VSPN with respect to the average communication burden between two fog nodes.
Figure 2.
Communication overhead comparison.
7. Related Works
A number of previous studies have been dedicated to designing real-time VANET-based navigation systems for the last few years. In 2009, Lu [26] presented a VANET-based parking navigation protocol, which tracks available parking spaces and guides drivers to the available parking spaces. In their protocol, three RSUs are fully trusted, which provide the navigation functions for a vehicle to find a vacant parking space in a parking lot. However, the protocol [26] can not be used for our navigation purposes. In 2010, another work [27] gave an application of real-time navigation. In addition to driving guidance, the returned routes of the scheme [27] were used for opportunistically routing multimedia information such as images and videos of a desired scene to vehicles. In addition, VANET-based navigation systems [28,29] also emerged to provide real-time navigation services for drivers on roads. By means of the widely deployed vehicular communication infrastructure, the vehicles only needed the OBUs to enjoy the navigation services. However, the security and privacy issues were not concerned in their schemes.
Recently, several VANET-based vehicle navigation systems [23,30,31,32] have been proposed for drivers’ privacy preservation. Chim et al. [23] proposed a VANET-based secure and privacy-preserving navigation system, which utilizes the anonymous credentials to provide secure navigation services to drivers. Based on anonymous credentials and the destination, the system can use the real-time road information to search for an available route for drivers in a distributed way. Nevertheless, this system is vulnerable to insider attacks since the system master key is shared among all vehicles. To eliminate the system master key distribution and simplify the anonymous credential acquisition, Cho et al. [30] introduced a security-enhanced navigation system based on the concept of two person multisignature [33] and identity-based cryptographic schemes [34]. However, how to collect traffic information was not considered in their scheme. Sur et al. [31] pointed out that prior VANET-based secure navigation protocols cannot provide non transferability of anonymous credentials used in their protocols to prevent an insider attacker from sharing her anonymous credentials, and the protocols [23,30] are vulnerable to an attacker who can compromise roadside units (RSUs) deployed on the roads. Sur et al. [31] proposed a secure navigation system based on vehicular cloud from a trapdoor hash function and zero-knowledge proof. However, the anonymous credentials in this system can only be used once for fear of vehicles’ sharing credentials with unregistered users. Ni et al. [32] proposed a privacy-preserving real-time navigation system using crowdsourcing. However, their scheme does not take advantage of fog computing, which leads to high efficiency and low-latency.
Our scheme is based on the idea of randomizing anonymous credentials. Once the fog nodes are compromised, they can not link the navigation query or a retrieving query to a specific vehicle. In this way, it can preserve the privacy of the vehicles. Moreover, the anonymous credentials need not be updated frequently, whereas it can be used for a long time. In our scheme, we utilize fog nodes to issue spatial crowdsourcing tasks to vehicles in their coverage in order to collect real-time road conditions, which guarantee that the retrieving path is real-time and optimal. In addition, the querying vehicle can successively retrieve the navigation result from each fog node when entering its coverage area. This framework is superior to existing solutions, which mainly depend on the assumption that a moving vehicle has to obtain the results from the first fog node, which is quite challenging in reality due to vehicles’ high moving speed.
8. Conclusions
In this paper, we proposed a secure and privacy-preserving real-time navigation system based on fog-based VANETs. We utilized the real-time traffic information to guid the vehicle to a desired destination in a distributed way: fog nodes generate the spatial crowdsourcing task to collect real-time road conditions. Then, each fog node takes advantage of the collected traffic information provided by the vehicles in its coverage to compute the optimal route to the destination. Vehicles can get the continuous optimal route from the fog nodes until it arrives at the desired destination. Moreover, the vehicle performing the crowdsourcing task can get a reasonable reward. Our scheme adopts some security primitives to provide a number of security features: (1) vehicles are authenticated by using zero-knowledge proof and randomized anonymous credentials; (2) messages provided by the vehicles and fog nodes can also be authenticated by means of signatures; (3) navigation queries, traffic information report and navigation results are protected from eavesdroppers. Besides satisfying all security requirements, our scheme provides the conditional privacy-preserving requirements. No one including TA can link up a vehicle’s navigation query and its identity. However, the TA can trace the identity of the driver who reports false traffic information. Furthermore, our scheme is efficient in terms of computational and communication overhead. For the future work, we will further improve the effectiveness of our scheme and develop a privacy-preserving parking system using vehicular crowdsourcing based on fog-based VANETs.
Acknowledgments
The research was sponsored by the Fund Project of Domestic Visiting Scholars of Excellent Backbone Teachers of Higher Education Institutions in Shandong Province.
Author Contributions
L.L. Wang conceived and designed the schemes; L. Sun performed the experiments; G.Z. Liu analyzed the data; L.L. Wang wrote the paper.
Conflicts of Interest
The authors declare no conflict of interest. The founding sponsors had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, and in the decision to publish the results.
References
- 1.Zheng J.R. Beijing tops domestic list for traffic congestion. China Daily. Aug 27, 2015.
- 2.Global Positioning System Standard Positioning Service Signal Specification. Navtech GPS Supply; Springfield, VA, USA: 1995. [Google Scholar]
- 3.Autonavi Navigation. [(accessed on 17 March 2017)]; Available online: http://www.autonavi.com/ (In Chinese)
- 4.Olariu S., Hristov T., Yan G. The Next Paradigm Shift: From Vehicular Networks to Vehicular Clouds. John Wiley & Sons, Inc.; Hoboken, NJ, USA: 2013. pp. 645–700. [Google Scholar]
- 5.Yan G., Wen D., Olariu S., Weigle M.C. Security challenges in vehicular cloud computing. IEEE Trans. Intell. Transp. Syst. 2013;14:284–294. doi: 10.1109/TITS.2012.2211870. [DOI] [Google Scholar]
- 6.Yu R., Zhang Y., Gjessing S., Xia W. Toward cloud-based vehicular networks with efficient resource management. IEEE Netw. 2013;27:48–55. doi: 10.1109/MNET.2013.6616115. [DOI] [Google Scholar]
- 7.Bonomi F., Milito R., Zhu J., Addepalli S. Fog Computing and Its Role in the Internet of Things. ACM; Helsinki, Finland: Aug 17, 2012. pp. 13–16. Edition of the MCC Workshop on Mobile Cloud Computing. [Google Scholar]
- 8.Lin X., Sun X., Ho P.H., Shen X. GSIS: A secure and privacy-preserving protocol for vehicular communications. IEEE Trans. Veh. Technol. 2007;56:3442–3456. [Google Scholar]
- 9.Lin X., Sun X., Wang X., Ho P.H., Shen X. TSVC: Timed efficient and secure vehicular communications with privacy preserving. IEEE Trans. Wirel. Commun. 2009;7:4987–4998. doi: 10.1109/T-WC.2008.070773. [DOI] [Google Scholar]
- 10.Lin X., Lu R., Zhang C., Ho P.H., Shen X. Security in vehicular ad hoc networks. IEEE Commun. Mag. 2008;46:88–95. [Google Scholar]
- 11.Lu R., Lin X., Zhu H., Ho P.H., Shen X. A novel anonymous mutual authentication protocol with provable link-layer location privacy. IEEE Trans. Veh. Technol. 2009;58:1454–1466. [Google Scholar]
- 12.Luan T.H., Gao L., Li Z., Xiang Y., Wei G., Sun L. Fog computing: Focusing on mobile users at the edge. arXiv. 2015.
- 13.Behrendt K., Fodero K. The perfect time: An examination of time-synchronization techniques; Proceedings of the Distributech; San Diego, CA, USA. 3 January 2005. [Google Scholar]
- 14.Galbraith S.D., Paterson K.G., Smart N.P. Pairings for cryptographers. Discr. Appl. Math. 2008;156:3113–3121. doi: 10.1016/j.dam.2007.12.010. [DOI] [Google Scholar]
- 15.Bellare M., Keelveedhi S., Ristenpart T. Message-Locked Encryption and Secure Deduplication; Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques; Athens, Greece. 26–30 May 2013; pp. 296–312. [Google Scholar]
- 16.Hur J., Koo D., Shin Y., Kang K. Secure Data Deduplication with Dynamic Ownership Management in Cloud Storage. IEEE Trans. Knowl. Data Eng. 2016;28:3113–3125. doi: 10.1109/TKDE.2016.2580139. [DOI] [Google Scholar]
- 17.Mao B., Jiang H., Wu S., Tian L. Leveraging Data Deduplication to Improve the Performance of Primary Storage Systems in the Cloud. IEEE Trans. Comput. 2013;25:1775–1788. [Google Scholar]
- 18.Yan Z., Wang M., Li Y., Vasilakos A.V. Encrypted Data Management with Deduplication in Cloud Computing. IEEE Cloud Comput. 2016;3:28–35. doi: 10.1109/MCC.2016.29. [DOI] [Google Scholar]
- 19.Pointcheval D., Sanders O. Short randomizable signatures; Proceedings of the CT-RSA 2016; San Francisco, CA, USA. 29 February–4 March 2016; pp. 111–126. [Google Scholar]
- 20.Camenisch J., Lysyanskaya A. A signature scheme with efficient protocols; Proceedings of the International Conference on Security in Communication Networks; Amalfi, Italy. 11–13 September 2002; pp. 268–289. [Google Scholar]
- 21.Chaum D., Heyst E.V. Group signatures; Proceedings of the Workshop on the Theory and Application of of Cryptographic Techniques; Brighton, UK. 8–11 April 1991; Berlin/Heidelberg, Germany: Springer; 1991. pp. 257–265. [Google Scholar]
- 22.Schnorr C.P. Advances in Cryptology— EUROCRYPT’89. Springer; Berlin/Heidelberg, Germany: 1990. Efficient Identification and Signatures for Smart Cards; pp. 688–689. [Google Scholar]
- 23.Chim T.W., Yiu S.M., Hui L.C.K., Li V.O. VSPN: VANET-Based Secure and Privacy-Preserving Navigation. IEEE Trans. Comput. 2014;63:510–524. doi: 10.1109/TC.2012.188. [DOI] [Google Scholar]
- 24.Scott M. Efficient Implementation of Cryptographic pairings. [(accessed on 5 June 2016)]; Available online: http://ecrypt-ss07.rhul.ac.uk/Slides/Thursday/mscottsamos07.pdf.
- 25.Miyaji A., Nakabayashi M., Takano S. New explicit conditions of elliptic curve traces for FR-reduction. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2001;84:1234–1243. [Google Scholar]
- 26.Lu R., Lin X., Zhu H., Shen X. SPARK: A new VANET-based smart parking scheme for large parking lots; Proceedings of the IEEE INFOCOM; Rio De Janeiro, Brazil. 19–25 April 2009; pp. 1413–1421. [Google Scholar]
- 27.Leontiadis I., Costa P., Mascolo C. Extending access point connectivity through opportunistic routing in vehicular networks; Proceedings of the Conference on Information Communications; San Diego, CA, USA. 14–19 March 2010; pp. 1–5. [Google Scholar]
- 28.Liu C.G., Liu I.H., Yang T.T., Li J.S. Navigation-aware association control in vehicular wireless networks. J. High Speed Netw. 2013;19:311–324. [Google Scholar]
- 29.Chen P.Y., Guo Y.M., Chen W.T. Fuel-saving navigation system in VANETs; Proceedings of the IEEE Vehicular Technology Conference Fall; Ottawa, ON, Canada. 6–9 September 2010; pp. 1–5. [Google Scholar]
- 30.Cho W., Park Y., Sur C., Rhee K.H. An improved privacy-preserving navigation protocol in VANETs. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2013;4:80–92. [Google Scholar]
- 31.Sur C., Park Y., Rhee K.H. An efficient and secure navigation protocol based on vehicular cloud. Int. J. Comput. Math. 2016;93:1–20. doi: 10.1080/00207160.2014.934685. [DOI] [Google Scholar]
- 32.Ni J.B., Lin X.D., Zhang K., Shen X. Privacy-Preserving Real-Time Navigation System Using Vehicular Crowdsourcing; Proceedings of the IEEE 84th Vehicular Technology Conference (VTC2016-Fall); Montréal, QC, Canada. 18–21 September 2016. [Google Scholar]
- 33.Gentry C., Silverberg A. Advances in Cryptology-ASIACRYPT 2002. Springer; Berlin/Heidelberg, Germany: 2002. Hierarchical ID-Based cryptography; pp. 548–566. [Google Scholar]
- 34.Chen L., Cheng Z., Smart N.P. Identity-based key agreement protocols from pairings. Int. J. Inf. Secur. 2007;6:213–241. doi: 10.1007/s10207-006-0011-9. [DOI] [Google Scholar]