Abstract
BACKGROUND:
Patient safety in hospitals is of equal importance as providing treatments and urgent healthcare. With the development of Cloud technologies and Big Data analytics, it is possible to employ VSaaS technology virtually anywhere, for any given security purpose.
AIM:
For the listed benefits, in this paper, we give an overview of the existing cloud surveillance technologies which can be implemented for improving patient safety.
MATERIAL AND METHODS:
Modern VSaaS systems provide higher elasticity and project scalability in dealing with real-time information processing. Modern surveillance technologies can prove to be an effective tool for prevention of patient falls, undesired movement and tempering with attached life supporting devices. Given a large number of patients who require constant supervision, a cloud-based monitoring system can dramatically reduce the occurring costs. It provides continuous real-time monitoring, increased overall security and safety, improved staff productivity, prevention of dishonest claims and long-term digital archiving.
CONCLUSION:
Patient safety is a growing issue which can be improved with the usage of high-end centralised surveillance systems allowing the staff to focus more on treating health issues rather that keeping a watchful eye on potential incidents.
Keywords: patient safety, healthcare, Video Surveillance as a Service (VSaaS), cloud technology
Introduction
Surveillance systems have been in use for several decades now since the invention of Closed-circuit television (CCTV) cameras and tape recorders. Over time these systems advanced to using the computer system and IP cameras to capture, store and reproduce recordings which quickly reached limits in size, power requirements, processing, analysing and especially storage. The main obstacle is that they are all on-site based solutions. Cloud computing introduced a novel approach to how data is being managed which reflected video surveillance as well. This brought to the idea of utilising the cloud computing enormous network, storage and processing capabilities such as access control and advanced cloud search [1-5].
Video Surveillance as a Service has undergone significant scientific development since its inception. Notable research done in the area covers universal environmental surveillance system [6], intelligent surveillance video analysis service [7, 8], automatic configuration of video-surveillance [9], remote display solution [10]. The authors [11] introduced a novel approach to developing autonomic cloud application platforms, based on the vision of treating cloud platforms as sensor networks. This approach is based on intelligent re-usage of existing solution strategies and products (specifically, Stream Reasoning and the Semantic Web technology stack), to create a general-purpose autonomous framework.
Video surveillance requires high-efficiency compression. The need for it has never been greater as it is estimated that the volume of saved stored and processed video surveillance data will exceed 5,800 Exabytes according to Gantz and Reinsel, 2012 [12] which is more than approximated 1.500 Exabytes by the same author. Wen, et al. 2014 [13] argues that the use of IEEE 1857-2013 encoding standard brings more than twice coding efficiency on surveillance videos compared H.264/AVC HP. One of the solutions for video compression is the Transcoding as a Services (TaaS) provided by an application service provider is Encoding.com. It uses the Amazon Web Services (AWS) platform for transcoding saved surveillance videos into different formats regarding resolution, frame rate, and bandwidth [14]. Key areas of cloud-based video surveillance are video-based detection and tracking [15], video-based person identification, and large-scale surveillance systems. A significant percentage of basic technologies for video-based detection and tracking were developed under a U.S. government-funded program called Video Surveillance and Monitoring (VSAM) [16].
Video Surveillance as a Service (VSaaS)
VSaaS cloud deployment architecture can be public, private or hybrid (a mix of two). Public architecture implies using a cloud service provider with an already set-up platform for video surveillance management. This is the most common usage scenario for VSaaS. Private architecture refers to internally hosted cloud service by a company or enterprise which used the platform for video surveillance purpose. This is rarely the case as it is harder to finance and maintain such a system.
In Fig. 1 an example is given of VSaaS framework developed by Hossain, 2014 [17]. We will briefly describe the underlying mechanism of the given framework:
Figure 1.
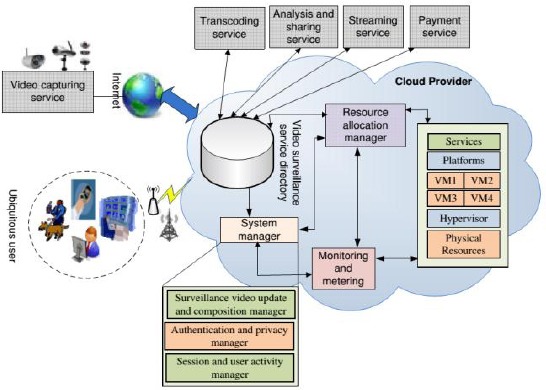
Example of VSaaS framework. Source: (Hossain, 2014)
Video content is provided by sensor devices (cameras) from various sources of the application using push-pull mechanism.
The main component is the Publish-subscribe broker which routes the data from the cloud to clients based on current subscription.
All processes are regulated by the Cloud manager whose purpose is to manage the interaction between clients and components directory
Multimedia surveillance service directory contains all of the functionalities of the service designed service-oriented architecture (SOA) architectural pattern.
Resource allocation manager has a purpose of managing and allocating various VM resources for running the surveillance system and associated services.
Monitoring and metering component tracks resources usage and provides statics of usage and billing.
The beginning of video surveillance was based on Closed-circuit television (CCTV) systems which were developed in the early 1950s. It had no means of storing recording, only monitoring by security employees. With the invention of videocassette recorder in the mid-1960s, it became possible to combine existing CCTV systems with the new device to store and delete surveillance material.
The technology significantly improved video surveillance with the introduction of Digital Video Recorder (DVR). Although first development proposals date the to mid 1980s, first commercial usage started in late 1990s. It offered a lot more storage space and faster seeking of recorded material and native PC support. Internet protocol (IP) networks appeared shortly after the invention of the IP camera in the late 1990s, and by 2005 video surveillance was based on Internet/Intranet systems.
VSaaS appeared in the early 2010s and since then it presents the most advanced surveillance system available for mass usage. The future of surveillance is without doubt intelligent cloud based systems which are currently being developed and examined in small beta tests. Advances in neural networks and machine learning are growing at a rapid pace and will without question bring unprecedented security applications.
Applications of VSaaS in improving patient’s safety
Health is the most valuable possession and should be preserved for as long as possible. Still, even social insurance experts working in healing facilities need to manage issues, for example, robbery, disagreements regarding conceivable negligence or even the abducting of babies. Tragically, not every gathered guest go to the healing centre to wish their friends and family a fast recuperation. The transparently available and for the most part opened rooms make it simple for potential cheats to take the centre as well as patient property, which frequently causes noteworthy budgetary misfortunes for the healing centre. As a rule definite images from surveillance cameras in lobbies, at crisis exits, close lifts or in the compensation office, prompt to a positive distinguishing proof of the culprit.
Particularly in serious care units, patients are for the most part not able to convey a decay of their condition to restorative staff. Video reconnaissance empowers staff to screen patients all day, every day – for in a crisis it is the snappy response of the treating doctors which decides a patient’s odds to survive. In sedative recuperation rooms, the patients’ conditions are likewise just checked from the medical caretakers’ room. AvaSys is a remote patient perception framework that empowers both visual and sound checking of patients at danger of self-mischief, including falls, the expulsion of lifesaving gadgets, and elopement. A versatile truck positioned in the patient room has a camera with skillet and zoom capacity and great, two-way sound (Figure 2). It functions by Wi-Fi to a remote perception station kept an eye on by a PCT that watches over upwards of 10 patients all the while on a solitary screen. At the point when a patient hints at getting up, the screen tech utilises the sound to request that the patient stays put while at the same time alarming a medical attendant using telephone or radio. On the off chance that the sitter can’t divert the patient, a STAT alert on the unit sounds.
Figure 2.

Portable system for critical health patient monitoring
There are numerous cases reporting children being kidnapped from infant nurseries. Keeping in mind the end goal to guarantee that the babies may nap gently as well as their parents may rest in peace; numerous doctors’ facilities utilise video observation frameworks. Thus, no one enters the infant ward unnoticed. The frameworks’ adaptability takes into consideration the checking framework to be associated with a get to control framework so that no unapproved people access the premises. Regularly in the outcome of hard surgeries or complicated births, the question emerges regardless of whether errors were made amid the technique. Any such question can be settled rapidly and definitively on account of cutting edge video reconnaissance. Computerised recording frameworks are much of the time being utilised amid surgeries with a specific end goal to have the capacity to audit the entire methodology at a later date.
In consistence with sterilised instructions, the recorder is not situated in the working area but rather for the most part in an isolated room. Information assurance is likewise ensured at all circumstances. On the pre-operation talk, which must occur before each surgery, the patient is made mindful of the likelihood to record the surgery and after that chooses whether or not he or she needs to make utilisation of it [18]. There are some developed systems which introduce intelligent software systems in hospital surveillance which can increase the number of rooms and areas being monitored by only notifying the operator in case of set rule breach [19, 20]. These systems can further be enhanced by adding robotic sub-systems which can in some cases even replace human operator in charge of notifying the personnel about detected events [21]. According to Brown, 2015 [22] about one million patients fall in USA hospitals facilities every year, which is a devastating number. The greater part of these falls are identified with toileting (45%) and impulsivity (31%), and a disturbing 80% to 90% of patient falls are not seen. Around 30% of patient falls result in harm, and of those, 4% to 6% result in genuine damage. Additionally, falls frequently cause huge patient and family trouble bringing about a postponement in recovery. A low-cost system for prevention of falls is proposed by Rawashdeh et al. 2012 [23]. In Figure 3 is given an example of software detecting a patient fall and raising the alarm to the operator is given.
Figure 3.

Example of fall detection software
Healthcare services offices procure quiet spectators (in some cases called persistent sitters) or dole out staff to screen patients at hazard for falls or on suicide watch, and the individuals who are befuddled or disturbed. Dissimilar to private-obligation individual care associates, a patient onlooker’s sole duty is to advise staff when the patient takes part in conceivably self-damaging conduct, for example, getting up without help or hauling out tubes. Onlookers by and large get time-based compensation, an unreimbursed cost. Some human services offices must request that the patient’s family give sitters, forcing a weight for working relatives. Healthcare services associations can bring down the expenses of patient perception utilising top notch (HD) video reconnaissance and two-way correspondences. With the perception arrangement, prepared staff in a focal operations focus can watch various patients over the office’s current system, rapidly alarming staff when intercession is required. Figure 4 shows the centralised patient observation setup. Healthcare industry can greatly benefit from cloud-based surveillance, especially from video analytics software such as motion analysis. The authors Lee, and Chung, 2012 [24] developed an algorithm capable of detecting falls of patients in healthcare institutions and removing shadows from objects thus greatly increasing false detection. Such a system of detection can be implemented to monitor patients movement in real-time by automatically notifying hospital staff of unfortunate event such as falling or undesired movement.
Figure 4.

Monitoring station for multiple locations with a hospital
Cloud-based video surveillance can serve as a data source for Applied Behavior Analysis (ABA) which can help the researcher to better understand human habits and behaviour patterns. For example, the authors Kröckel and Bodendorf, 2010 [25] presented a concept of using data mining methods on images obtained by video surveillance. The analysis is performed for customer trajectories, paths through the retail environment, while image processing is done using OpenCV Computer Vision Library. Results about patterns and clusters are obtained by the different method of data mining. The health sector has proven to have reduced incidents [26] with installed physical security measures. Application of VSaaS in hospitals can greatly influence the early detection of incidents (fights, falls, unauthorised access, vandalism), reduce overall security costs (less security personnel needed, less hardware and technical maintenance personnel, no Digital Video Recording (DVR) devices required) and can provide behavioural analysis. In research by Anderson et al. 2014 [27] the authors proved that monitoring staff members hygiene routine improved the regularity of washing hands in hospitals. In a paper by Frank, 2013 [28] video surveillance lowered the number of incidents in a psychiatric facility by enabling faster response to incidents by supervising staff. Similar conclusions were extracted from a study by Nolan & Volavka 2006 [29] where video recordings served as a source for analysis to reduce violent events. While monitoring proves successful in mental health facilities, there are also rising concerns about ethical violations which may arise [30].
One of the developed techniques applicable in health provider environments is a 3-D imaging technique which pairs high-resolution night-vision cameras with GPS to increase the capabilities of passive imaging surveillance. The technique was developed by Schwartz, 2011 [31] and uses camera models and GPS to derive a registered point cloud from multiple night-vision images. These point clouds are used to generate 3-D scene models and extract real-world positions of mission critical objects. This enables precise geo-positioning in a low-light environment. A supportive hardware solution comes from company Avigilon, which developed Light Catcher technology capable of capturing video with colour detail in extreme low-light environments.
The authors Xu, and Wu, 2010 [32] proposed new approach for a Smart Video Surveillance System (SVSS) that uses canonical stereo configuration to set up a pair of static cameras to support a salient map to control a Pan-Tilt-Zoom (PTZ) camera/cameras, which captures high-definition image /video of the interesting moving object in the surveillance area for further forensic investigations. Concepts that underlie several of the key techniques, including detection of moving objects in the video, tracking in two and three dimensions, object classification, and object structure analysis [33]. In Table 1 a state-of-the-art technology for smart video surveillance application is given.
Table 1.
List of component technologies and supporting approaches for smart video surveillance
| Component technology | Supporting approach |
|---|---|
| Object detection | Adaptive background subtraction with healing and salient motion detection. |
| Two-dimensional object tracking | Maximum likelihood classification scheme to resolve foreground pixels into the component objects. |
| Three-dimensional wide-baseline stereo object tracking | Using two overlapping views of the scene and locating the same scene point in the two views using two PTZ cameras. 3D night-vision stereoscopic photogrammetry |
| Object classification | An image-based approach and a video tracking-based approach. |
| Object structure analysis | Detection technique uses the smoothed silhouette of the foreground object, as segmented using background subtraction. |
| Face cataloger application | The face cataloger uses computer-controlled PTZ cameras driven by a 3-D wide-baseline stereo tracking system. The PTZ cameras automatically acquire zoomed-in views of a person’s head without constraining the subject to be at a particular location. |
Ethical concerns for video surveillance in hospitals
In an online world the dangers to private data are numerous as they can originate from staff, patients, relatives, or inconsequential people who may attempt to adjust, harm or uncover data to influence its trustworthiness or privacy. This might be because of physical activity or some likeness thereof or subsequently of an advanced assault. For instance, data held carefully is at danger of revelation if an unapproved individual can read classified subtle elements off a PC screen; similarly at hazard is electronic data that is deficiently secured empowering somebody to duplicate, alter or erase secret data.
In both these illustrations, it is more than likely that the revelation will not be-be identified. On account of adjustment or erasure these might be identified by review projects or staff individuals; however, recognition is not ensured, and the outcome could bring about mischief or passing to a patient. The effect on the doctor’s facility could be serious because of the resultant case and terrible reputation [34]. As per driving medicinal services legal counsellor Kirk J. Nahra “A security break that uncovers generous wellbeing data could prompt to different sorts of protection mischief (humiliation, notoriety damage, and so forth.)” [35]. People may pick up data that permits them to trade off, shakedown or influence the notoriety of someone else by furnishing them with medicinal, individual and money related subtle elements that could be utilised against them. In this manner, data security rehearses should be inspected keeping in mind the end goal to dodge breaks that could prompt to case. There is some research done by Thomas 1995 [36] and Vaught, 2004 [37] which discuss privacy and ethical breaches of video surveillance in paediatric facilities and wards. While there are positive sides of monitoring young children, some argue that such surveillance should not be made covert and that all involved parties must be fully informed of existing surveillance systems.
Healing centres need to guarantee that the standards in the Privacy Policy are adhered to by all staff, temporary workers and associations who handle the doctor’s facility’s data. This is especially essential when the data is being handled and put away off-site.
Gauges for assurance of this data should be incorporated into contracts for both staff and contracted associations keeping in mind the end goal to maintain a strategic distance from breaks of the arrangement. Ruptures of arrangement are all the more frequent because of the absence of mindfulness or comprehension of the issues, or staff is working under undue worry than to plain conduct [38]. Instruction and preparing projects ought to be executed to guarantee that absence of mindfulness is not a reason for approach ruptures. Strategies for worthy utilisation of data and data frameworks should be produced, executed and policed.
In conclusion, this paper presented modern applications of Video Surveillance as a Service for healthcare services from both scientific and general public view. Available literature covers a wide scope of application issues and solutions; however, more effort is needed in automation of intelligent data analysis since the amount of data exceeds current software and hardware capabilities. Beside intelligent data analysis more development is needed in the area of video compression and transfer to support high definition streaming without the need of using intermediary storage with pre-compression function. Maintaining secure environments is of imperative importance especially in times of increased terrorist activities, political and economic crisis and unstable conflict regions. VSaaS reduces overall costs and offers unsurpassed technological possibilities compared to traditional systems which should be fully utilised. Patient safety is a growing issue which can be improved with the usage of high-end centralised surveillance systems allowing the staff to focus more on treating health issues rather that keeping a watchful eye on potential incidents.
Footnotes
Funding: This research did not receive any financial support.
Competing Interests: The authors have declared that no competing interests exist.
References
- 1.Dašić P, Dašić J, Crvenković B. Applications of access control as a service for software security. International Journal of Industrial Engineering and Management (IJIEM) 2016;7(3):111–116. [Google Scholar]
- 2.Dašić P, Dašić J, Crvenković B. Some examples of video surveillance as a service applications. In: Proceedings of the 7th International Multidisciplinary Scientific Symposium “Sustainable Development Through Quality and Innovation in Engineering and Research” (SIMPRO-2016); Petroşani, Romania; 14-15 October 2016. Petroşani (Romania): University of Petroşani. 2016:367–370. PMid:26890916. [Google Scholar]
- 3.Dašić P, Dašić J, Crvenković B. Applications of the search as a service (SaaS) Bulletin of the Transilvania University of Brasov, Series I: Engineering Sciences. 2016;9(2):91–98. [Google Scholar]
- 4.Dašić P, Dašić J, Crvenković B. Service models for cloud computing: Search as a service (SaaS) International Journal of Engineering and Technology (IJET) 2016;8(5):2366–2373. https://doi.org/10.21817/ijet/2016/v8i5/160805034 . [Google Scholar]
- 5.Dašić P, Dašić J, Crvenković B. Service models for cloud computing: Video Surveillance as a Service (VSaaS); Bulletin of the Transilvania University of Braşov, Series I: Engineering Sciences. 2016;9(2):83–90. [Google Scholar]
- 6.Chen PJ, Chen CH, Chen YC, Wang JH, Liao TS, Hwang CH Universal environmental surveillance system with instrument cloud technology. International Conference IMT. Minneapolis; USA: IEEE; 2013. pp. 845–849. art. no. 6555534. [Google Scholar]
- 7.Chen T-S, Lin M-F, Chieuh T-C, Chang C-H, Tai W-H An intelligent surveillance video analysis service in cloud environment. International Carnahan Conference on Security Technology. Orlando: Florida, USA, 2016; 2016. pp. 1–6. [Google Scholar]
- 8.Tomforde S, Jänen U, Hähner J, Hoffmann M. SmaCCS: Smart camera cloud services: Towards an intelligent cloud-based surveillance system. 10th International Conference ICINCO. 2013;1:288–293. [Google Scholar]
- 9.Conejero JM, Hernández J, Clemente PJ, Echeverría; R.R., Preciado; J.C, Figueroa F.S. Automatic Configuration of Video-Surveillance Applications: A Model-Driven Experience. IEEE Latin America Transactions. 2015;13(8):2700–2708. https://doi.org/10.1109/TLA.2015.7332152 . [Google Scholar]
- 10.Song B, Hassan MM, Tian Y, Hossain MS, Alamri A. Remote display solution for video surveillance in multimedia cloud. Multimedia Tools and Applications. 2015;22 https://doi.org/10.1007/s11042-015-2816-x . [Google Scholar]
- 11.Dautov R, Paraskakis I. A vision for monitoring cloud application platforms as sensor networks; ACM International Conference Proceeding Series. New Orleans: LA; USA: 2013. https://doi.org/10.1145/2494621.2494647 . [Google Scholar]
- 12.Gantz J, Reinsel D. The IDC Digital Universe in 2020: Big Data. Bigger Digital Shadows; and Biggest Growth in the Far East. 2012. Available at: http://www.emc.com/leadership/digital-universe/index.htm .
- 13.Wen G, Yonghong T, Tiejun H, Siwei M, Xianguo Z. The IEEE 1857 Standard: Empowering Smart Video Surveillance Systems. IEEE Intelligent Systems. 2014;29(5):30–39. https://doi.org/10.1109/MIS.2013.101 . [Google Scholar]
- 14.Hossain MS, Hassan MM, Qurishi MA, Alghamdi A Resource allocation for service composition in cloud-based video surveillance platform. International Conference ICMEW 2012; art. no. 6266418. Melbourne; Australia: IEEE; 2012. pp. 408–412. https://doi.org/10.1109/icmew.2012.77 . [Google Scholar]
- 15.García-Rodríguez J, García-Chamizo JM. Surveillance and human-computer interaction applications of self-growing models. Applied Soft Computing Journal. 2011;11(7):4413–4431. https://doi.org/10.1016/j.asoc.2011.02.007 . [Google Scholar]
- 16.Collins R, et al. VSAM Final Report; Carnegie Mellon Univ. Pittsburgh; PA: Tech. Rep. CMU-RI-TR-00-12; 2000. A system for video surveillance and monitoring. [Google Scholar]
- 17.Hossain MA. Framework for a cloud-based multimedia surveillance system. International Journal of Distributed Sensor Networks. 2014. art. no. 135257. https://doi.org/10.1155/2014/135257 .
- 18.Kennedy S. Electronic surveillance in hospitals: A review. In Proceedings of 4th Australian Information Security Management Conference. 2006 [Google Scholar]
- 19.Huang C-M, Yang C-C, Lin C-W. IIPS-ICC: An intelligent IP-surveillance platform using interactive camera-handoff control. In Proceedings - 2007 IFIP International Conference on Network and Parallel Computing Workshops, NPC. 2007:636–641. [Google Scholar]
- 20.Micheloni C, Remagnino P, Eng H-L, Geng J. Intelligent monitoring of complex environments. IEEE Intelligent Systems. 2010;25(3):12–14. https://doi.org/10.1109/MIS.2010.85 . [Google Scholar]
- 21.Jamaludin SH, Mansor MN, Junoh AK, Ahmed A, Daud WSW, Idris A. Robotic vision for hospital inspection. Advanced Materials Research. 2014;1016:716–720. https://doi.org/10.4028/www.scientific.net/AMR.1016.716 . [Google Scholar]
- 22.Brown S. (2015) Keeping watch: Enhancing fall prevention through targeted video surveillance. American Nurse Today. 2015;10(12):1–5. [Google Scholar]
- 23.Rawashdeh O, Sa’Deh W, Rawashdeh M, Qu G, Ferrari M, Harrison B, et al. Development of a low-cost fall intervention system for hospitalized dementia patients. In IEEE International Conference on Electro Information Technology. 2012. https://doi.org/10.1109/eit.2012.6220763 .
- 24.Lee Y-S, Chung W-Y. Visual sensor based abnormal event detection with moving shadow removal in home healthcare applications. Sensors. 2012;12(1):573–584. doi: 10.3390/s120100573. https://doi.org/10.3390/s120100573 . PMid:22368486. PMCid:PMC3279230. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 25.Kröckel J, Bodendorf F. Extraction and application of person trajectories in retail environments. International Conference IADIS 2010; Part of the MCCSIS. 2010:109–113. PMid:21109283. [Google Scholar]
- 26.Tanner-Smith EE, Fisher BW. Visible School Security Measures and Student Academic Performance; Attendance; and Postsecondary Aspirations. Journal of Youth and Adolescence. 2016;45(1):195–210. doi: 10.1007/s10964-015-0265-5. https://doi.org/10.1007/s10964-015-0265-5 . PMid:25722253. [DOI] [PubMed] [Google Scholar]
- 27.Anderson MEC, Sargeant JM, Weese JS. Video observation of hand hygiene practices during routine companion animal appointments and the effect of a poster intervention on hand hygiene compliance. BMC Veterinary Research. 2014;10 doi: 10.1186/1746-6148-10-106. https://doi.org/10.1186/1746-6148-10-106 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 28.Frank U. Video surveillance in psychiatric hospitals - Pro; contra [Videoüberwachung in der Psychiatrie - Pro; Kontra] Psychiatrische Praxis. 2013;40(3):117–118. doi: 10.1055/s-0032-1332939. https://doi.org/10.1055/s-0032-1332939 . PMid:23559446. [DOI] [PubMed] [Google Scholar]
- 29.Nolan KA, Volavka J. Video recording in the assessment of violent incidents in psychiatric hospitals. Journal of Psychiatric Practice. 2006;12(1):58–63. doi: 10.1097/00131746-200601000-00010. https://doi.org/10.1097/00131746-200601000-00010 . [DOI] [PubMed] [Google Scholar]
- 30.Stolovy T, Melamed Y, Afek A. Video surveillance in mental health facilities: Is it ethical? Israel Medical Association Journal. 2015;17(5):274–276. PMid:26137651. [PubMed] [Google Scholar]
- 31.Schwartz JM. Precise positioning surveillance in 3-D using night-vision stereoscopic photogrammetry. Proceedings of SPIE. 2011;8042 art. no. 80420A. [Google Scholar]
- 32.Xu Z, Wu HR Smart video surveillance system. International Conference ICIT. Chile: IEEE; Vi a del Mar; 2010. pp. 285–290. https://doi.org/10.1109/icit.2010.5472694 . [Google Scholar]
- 33.Hampapur A, et al. Smart video surveillance: exploring the concept of multiscale spatiotemporal tracking. IEEE Signal Processing Magazine. 2005;22(2):38–51. https://doi.org/10.1109/MSP.2005.1406476 . [Google Scholar]
- 34.Aldridge J. Hospital Security: the past, the present, and the future, 2005. SecurityInfoWatch.com. Available on: from http://www.securityinfowatch.com/article/article.jsp-siteSection=357&id=5719 .
- 35.Nahra KJ. Federal Security Breach Legislation Progresses (but slowly) Privacy in Focus. 2005. Available on: http://www.wrf.com/publication_newsletters.cfm-id=10&publication_ID=12393 .
- 36.Thomas T. Child protection, privacy and covert video surveillance. Journal of Social Welfare and Family Law. 1995;17(3):311–324. https://doi.org/10.1080/09649069508413662 . [Google Scholar]
- 37.Vaught W. Parents, lies, and videotape: Covert video surveillance in pediatric care. Journal of Clinical Ethics. 2004;15(2):161–172. PMid:15481167. [PubMed] [Google Scholar]
- 38.Patel A. Barber E.B, Blobel B, Louwerse K, Barber B, editors. IT Security Training in the Healthcare Environment. Security Standards in Healthcare Information Systems. IOS Press. 2002 [Google Scholar]


