Abstract
Authentication is one of the essential security services in Wireless Sensor Networks (WSNs) for ensuring secure data sessions. Sensor node authentication ensures the confidentiality and validity of data collected by the sensor node, whereas user authentication guarantees that only legitimate users can access the sensor data. In a mobile WSN, sensor and user nodes move across the network and exchange data with multiple nodes, thus experiencing the authentication process multiple times. The integration of WSNs with Internet of Things (IoT) brings forth a new kind of WSN architecture along with stricter security requirements; for instance, a sensor node or a user node may need to establish multiple concurrent secure data sessions. With concurrent data sessions, the frequency of the re-authentication process increases in proportion to the number of concurrent connections. Moreover, to establish multiple data sessions, it is essential that a protocol participant have the capability of running multiple instances of the protocol run, which makes the security issue even more challenging. The currently available authentication protocols were designed for the autonomous WSN and do not account for the above requirements. Hence, ensuring a lightweight and efficient authentication protocol has become more crucial. In this paper, we present a novel, lightweight and efficient key exchange and authentication protocol suite called the Secure Mobile Sensor Network (SMSN) Authentication Protocol. In the SMSN a mobile node goes through an initial authentication procedure and receives a re-authentication ticket from the base station. Later a mobile node can use this re-authentication ticket when establishing multiple data exchange sessions and/or when moving across the network. This scheme reduces the communication and computational complexity of the authentication process. We proved the strength of our protocol with rigorous security analysis (including formal analysis using the BAN-logic) and simulated the SMSN and previously proposed schemes in an automated protocol verifier tool. Finally, we compared the computational complexity and communication cost against well-known authentication protocols.
Keywords: authentication, sensor networks, network security, key distribution, privacy, BAN logic
1. Introduction
Wireless sensor networks (WSNs) consist of a vast number of distributed sensor nodes. Each sensor node is an autonomous system that monitors and collects data from the surrounding environment. In wireless sensor networks, the sensor nodes have limited computational power and communication capabilities; hence, most of the conventional cryptographic mechanisms and security protocols are not suitable for resource limited WSNs. For instance, very efficient public key algorithms, such as ECC [1], need a fraction of a second to execute the encryption/decryption procedures, while a symmetric key algorithm, such as RC5 [2], needs only a fraction of a millisecond to perform encryption and decryption procedures [3,4,5]. In a sensor network where devices have limited resources, the asymmetric cryptographic functions must be used wisely; for instance, use the asymmetric cryptography when an authentication responder already verified the initiator and wants to share secret information. If the responder does not authenticate the initiator and the initiator uses the asymmetric cryptography to exchange a message, the network becomes vulnerable to DOS attacks [5,6]. The WSN related contraints mentioned above are known to the research community. The currently available authentication protocols are designed for the autonomous WSN from the perspective of the above constraints. Moreover, in the near future in the realization of the vision of emerging technologies such as IoT, D2D, smart home and smart cities, WSNs will provide an invaluable service by acting as a virtual layer between the physical world and the computational devices [7,8,9]. However, integration of WSNs with IoT will bring forth a new kind of WSN architecture and stricter security requirements; for instance, in a smart hospital (as shown in Figure 1b) a sensor node or a user node may require the establishment of multiple concurrent secure data sessions. To establish a secure data session, authentication is the first step. In a dynamic, mobile WSN environment, where sensors and user nodes can establish multiple concurrent connections, a node moving across the network undergoes the authentication check multiple times and the frequency of the re-authentication process increases in proportion to the number of concurrent connections. Moreover, to establish multiple data sessions, it is essential that a protocol participant has the capability of running multiple instances of the protocol run, which makes the security issue even more challenging. Thus, it is essential to adopt a secure yet lightweight authentication procedure that especially reduces the computational time and communication at the mobile sensor node. The currently available authentication protocols were designed for the autonomous WSN and do not account for these new emerging challenges. This work presents a novel authentication protocol suite called the Secure Mobile Sensor Network (SMSN) Authentication Protocol. The SMSN protocol suite consists of six protocols: three protocols deal with mobile sensor node authentication with sink nodes and the other three deal with user node activation and authentication with the base station, sink nodes, and sensor nodes. In the SMSN, mobile sensors and user nodes can join and leave the system dynamically and can establish secure multiple concurrent connections. After the initial authentication, a mobile sensor or a user node can move across the network and get re-authenticated by a simple ticket-based re-authentication protocol; for instance, a user node can establish concurrent connections with multiple sink and sensor nodes using a re-authentication ticket issued during the initial-authentication protocol run. To establish multiple connections, a node is allowed to run multiple instances of the protocol; consequently, we introduce extra design requirements to meet the goals of a secure authentication protocol. In this paper, we also present an efficient and lightweight key generation and distribution mechanism. In the key generation protocol, a commitment key is generated by a group of participants (the base station and sink nodes) using an irreversible function; the key agreement and key retrieval protocol are the same as that employed in [10]. The commitment key is further applied to drive multiple time-based encryption keys, for example, the ticket encryption key and session key between the sink and user/sensor are derived from the commitment key. The time dimension in the protocol increases the security of the protocol; although the group members do not need to be tightly or loosely time synchronized. To determine the security of the protocol in this study, we performed a rigorous security analysis and also simulated the SMSN and previously proposed schemes [11,12,13,14,15,16] in an automated security protocol analysis tool called Scyther [17,18], which is a powerful state-of-art tool that finds attacks for defined protocol properties. We observed that our authentication protocol is secure, and it achieves all the objectives of an authentication protocol, which are defined as protocol claims in Section 5.3; for a detailed description of protocol claims, please refer to [19,20]. We also compared the efficiency of the SMSN in terms of computational time and communication complexities as discussed in [11,12,13,14,15,16]. The remainder of this paper is organized as follows. Section 2 presents the related work. In Section 3, we present a brief system overview and problem statement. Section 4 describes the proposed scheme with a detailed discussion. In Section 5, we assess the strength of our scheme against the known attacks. Section 6 presents an efficiency analysis that compares a few interesting schemes with our scheme. Finally, we provide concluding remarks in Section 7.
Figure 1.
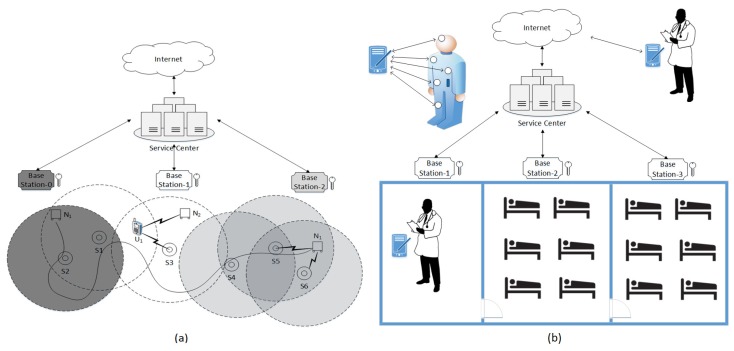
(a) An example scenario of a Wireless Sensor Network (WSN). Sensor node is initially authenticated by ; while moving across the network it is re-authenticated by the re-authentication ticket. At the final destination shares data with multiple sink nodes while user node collects data from sensor node and sink node . (b) An application scenario of Secure Mobile Sensor Network (SMSN) in a smart hospital. Authorised doctors and nursing staff can access the data from sensor nodes using a user device.
2. Related Work
Typically, WSNs are comprised of distributed devices with limited resources. Most of the conventional cryptographic mechanisms and security protocols are computationally expensive and are not suitable for resource-limited WSNs. In the recent past, the research community proposed several authentication protocols [11,12,13,14,15,16,21,22,23,24,25,26,27] that provide security in a WSN environment. Since the sensor nodes have low computational time, storage and communication capabilities, it is essential to design an efficient and lightweight yet secure authentication mechanism. From the point of view of computational and communication complexity, the authentication procedure in a wireless network with a mobile sensor and user node is an expensive task. A node moving across the network undergoes multiple authentication checks. Thus, it is essential to adopt a secure yet lightweight authentication procedure that especially reduces the computational and communication resources at the mobile sensor node. In [28] the authors discussed various anomaly detection techniques for flat and hierarchical wireless sensor networks, but detection techniques are not sufficient for several security threats. However, for a secure system together with detection methods, prevention techniques such as authentication is also vital; various authentication protocols for WSNs were proposed in [11,12,13,14,15,16,21,22,23,24,25,26,27]. In 2006, Wong [21] proposed a user authentication scheme for a dynamic WSN. The scheme is password based and employs lightweight cryptographic hash and XOR operations. Later on, Tesng et al. [11] and Das [22] identified that the Wong [21] scheme had various weaknesses and was vulnerable to replay attacks and forgery attacks, and the user password is known to the sensor node and can be revealed by any sensor node. Tesng et al. [11] proposed an improved version to mitigate the weaknesses that posed security threats in the Wong [21] scheme. The scheme of Tesng et al. [11] is also a password-based scheme, but the password is not revealed to the sensor nodes, and they also introduced a new phase of password change. Nevertheless, the scheme of Tesng et al. [11] is weak against replay attacks, impersonation attacks and forgery attacks [29]. Moreover, the scheme does not provide a mutual authentication between the gateway (GW) and sensor node (SN). In 2009, Das [22] proposed a two-factor user authentication scheme in which legitimate users can register and log in to the remotely deployed sensor nodes to access the collected data. From the point of view of computational and communication complexity, the scheme is reasonably efficient. The author claimed the scheme was secure against various kinds of attacks. However, later work [30,31,32] suggested that the scheme was vulnerable to different types of attacks, including impersonation, password guessing, insider, and parallel session attacks. Moreover, it did not provide the mutual authentication between the GW and sensor nodes. In 2010, Yoo et al. [12] proposed a user authentication scheme for WSNs and analyzed the protocol using BAN logic [33]. However, the BAN logic provided a foundation for the formal analysis of security protocols, but in the case of authentication, various attacks could slip through the BAN logic [34,35]. The scheme of Yoo et al. provided mutual authentication between the GW and the user and established a session key between the GW and SN. The authors claimed that the scheme was safe against insider attacks, impersonation attacks, and parallel session attacks. However, in [27] the authors provided a detailed analysis of the scheme of Yoo et al. and proved that the scheme is susceptible to various attacks, including insider attacks, impersonation attacks, parallel session attacks, password guessing attacks, fake registration attacks, and DOS attacks. Kumar et al. [36] proposed an authentication protocol for WSNs and claimed it could satisfy all the security requirements of the WSN; however, He et al. [37] proved that the scheme was weak against insider attacks and offline password guessing attacks and could not provide user anonymity. Kumar proposed another enhanced scheme in [13] and once again claimed that the scheme could withstand most of the known attacks and provide user privacy. However, with the Scyther implementation, given in Section 5.3, we found that the improved scheme presented in [13] was still vulnerable to insider attacks, parallel session attacks, and impersonation attacks. Farash et al. [15] proposed a key agreement and authentication protocol for WSNs in the Internet of Things (IoT) environment. The scheme was well designed and provided security against several well-known attacks. The author proved the strength of the protocol with BAN logic and further confirmed the theoretical analysis results by implementing the protocol in the AVISPA [38] tool. However, similar to other schemes discussed above, Farash et al. [15] did not consider the requirement of concurrent sessions, which are more likely to occur in an IoT environment. Moreover, our implementation of the scheme of Farash et al. [15] in Scyther revealed that the GW was vulnerable against insider attacks and impersonation attacks. The scheme was insecure in the presence of an intruder as discussed in Section 5.3, which assumed that the initial knowledge set of intruders included the identities of all sensor and user nodes. With known identities, an intruder can impersonate the user node and deceive the GW to falsify the authentication properties. Similarly, the Scyther implementation of the recently published work of Y. Lu et al. [16] and Quan et al. [14] revealed that at least two protocol participants falsified the authentication properties. The majority of the schemes discussed above provided the GW and user authentication schemes; however, Farash et al. [15] and Y. Lu et al. [16] also considered the GW and sensor node authentication, while Farash et al. [15] also allowed the user to access the data from sensor nodes directly. Li et al. [39] proposed an authentication protocol for sensor and user nodes. However, the proposed scheme requires time synchronization among protocol participants, and also employs the asymmetric elliptic curve cryptography, which is not a good design choice for resource limited WSN applications. For instance, very efficient public key algorithms, such as ECC [1], need a fraction of a second to execute the encryption/decryption procedures, while a symmetric key algorithm , such as RC5 [2], needs only a fraction of a millisecond to perform encryption and decryption procedures [3,4,5]. Unlike all the schemes discussed above, our proposed scheme, the SMSN authentication protocol suite, allows the sensor and user nodes to establish multiple concurrent connections with different sensor and sink nodes, which makes our scheme suitable for deploying it in the future to support IoT and related emerging technologies. Moreover, the SMSN authentication protocol suite provides several kinds of mutual authentications; for instance, after the initial authentication, a sensor or the user node receives an authentication ticket issued by the base station. The ticket can be further used for sensor-sink, user-sink, and user-sensor mutual authentication. The SMSN protocol suite consists of six protocols: three protocols deal with mobile sensor node authentication with sink nodes, and the other three deal with user node activation and authentication with the base station, sink nodes, and sensor nodes.
3. System Overview and Problem Statement
A typical WSN consists of the base station (BS), sink node (S), sensor node (N) and user node (). We assume that the knows the public keys of the sink (S), sensor (N) and user ( nodes.
3.1. System Architecture
An IoT smart service provider deploys the WSN with various base stations connected to the internet through a service center (. In the WSN, each forms a group consisting of neighbor base stations and associated sink nodes. All group members share a symmetric group key , which is controlled by the group master using a group key agreement protocol such as discussed in [40]. Furthermore, the base station can access and download the profile of the mobile Sensor (N) and User ( nodes. Each profile has a unique secret number ; besides being know to the base station, this secret number is also known to the corresponding Sensor (N) and User ( nodes. The profile and unique secret number of all legitimate users and sensor nodes are accessible to the base station through the service center.
An example of the overall system architecture is depicted in Figure 1a. creates a group consisting of neighbor and and associated sinks . generates a group key and shares it among all group members. The profiles and the associated unique secret number of and are accessible to and via the service center. An application scenario is given in Figure 1b. In a smart hospital, the health status of a hospitalized patient is continuously monitored by the several sensors mounted over the patient’s body. For the secrecy of patients’ health data it is essential that only authorized users be able to access the data. When a patient takes a walk in the hospital, all the mounted sensors continuously transfer the different sets of data to the nearby sinks. With the SMSN, the sensors do not need to follow the full authentication procedure for each data session; instead, the session continues by sharing a simple re-authentication ticket that provides the sensor-sink mutual authentication. Similarly, when an authorized doctor or nursing staff visits patients, he or she can access the sensor data in real time via a user device by establishing multiple data sessions with various sinks and sensor nodes. While he moves from patient to patient, his device does not need to follow a complete authentication procedure for each data session; rather, a simple re-authentication ticket can be used for re-authentication. From outside of the hospital, an authorized person can log into the hospital system and access the necessary data from sink and base stations by using the same re-authentication ticket.
3.2. Problem Statement
As described earlier, in IoT and other related emerging technologies, a mobile sensor or user node may need to exchange data with multiple nodes and so will experience the authentication process multiple times. With multiple concurrent connections, the authentication process becomes even more expensive while a node moves across the network. As shown in Figure 1a, sensor node is communicating with sink nodes and simultaneously. Likewise, user node is communicating with sink node and sensor node simultaneously. In such an application scenario, when a sensor or the user node moves across the network the frequency of the re-authentication process increases in proportion to the number of concurrent connections. Moreover, to establish multiple data sessions, it is essential that a protocol participant run multiple instances of the protocol run, which makes the security issue even more challenging. To perform multiple parallel re-authentications, it is evident that the protocol participants run multiple instances of the protocol. With the multiple protocol runs, the assurance of security of the protocol becomes more challenging. Therefore, for seamless services, lightweight yet secure re-authentication is vital.
According to our knowledge, we are the first to propose an authentication protocol for concurrent secure connections. To perform multiple parallel re-authentications, the protocol participants must run multiple instances of the protocol. With multiple protocol runs, the assurance of security of the protocol becomes more challenging. We developed our scheme, the SMSN, considering the following constraints: (1) the communication channels are insecure; (2) an intruder with the capabilities as described in Section-5-C is present in the network to launch various attacks; (3) due to the requirements for a WSN deployed in an IoT environment, the protocol participants are allowed to run multiple instances of the protocol; and (4) user and sensor nodes can dynamiclly leave and join the network and can move across the network.
3.3. Notations
= The jth base station
= The jth sink
= The ith sensor node
= The ith user node
= A is associated with B such that B is controlling authority
= Group of all associated entities of jth
= Group of all non-associated entities of jth BS who knows the
= The time-based key generated at ith interval by
= A group key generated by
= session key generated at ith interval
= private session key
= Temporary session key
= Encryption of ’m’, using key
= The index value for interval i
= The kth Ticket
= An intruder Z mimicking the entity A
= ith nonce in a message exchange
4. Proposed Scheme
The SMSN protocol suite consists of two protocol suites, the Keying Protocol suite and an Authentication Protocol suite. The Keying Protocol suit further comprises a key agreement protocol, a key retrieval protocol (which is the same as the one employed in [10]), and a key management protocol; likewise, the authentication protocol further comprises six protocols, three dealing with mobile sensor node authentication with sink nodes and the other three dealing with user node activation and authentication with a base station, sink nodes, and sensor nodes in different scenarios. In subsequent sections, the SMSN protocol suite is described in detail.
4.1. Keying Protocol Suite
In key generation protocol a ’commitment key’ is generated by group participants (the base station and sink nodes) using an irreversible function similar to that as used in [10,41]. The ’commitment key’ is further used to drive multiple time-based keys; for instance, the ticket encryption key and session key between the sink and user/sensor are derived from the ’commitment key’.
4.1.1. Key Agreement Protocol
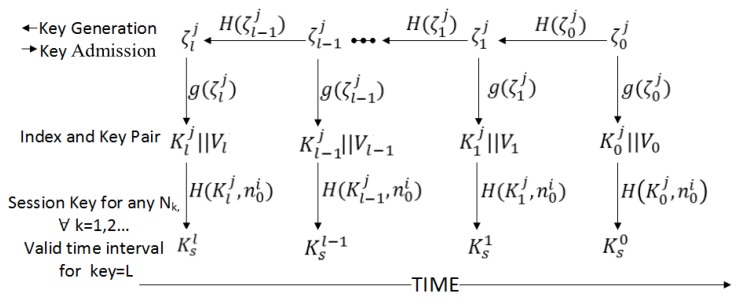
The key generation and distribution mechanism is shown in Figure 2 and consists of the following steps: (1) After every time interval , broadcasts the key generation information () to all members of (2) Using the key generation information (, all members generate a Commitment Key Generator . (3) All members of can now generate a “Chain of Key Generators” of length L by using an irreversible one-way function: ; i.e., (4) Each generator ( in the chain is used by function g at specific intervals to derive indexes and a ticket encryption key pair. For instance, at interval k for any sensor or user node which is requesting the to join the network, the function generates ticket encryption key and index value. In function g the value is a secret nonce sent by node i in a network join message. (5) Furthermore, issues a session key based upon the ticket encryption key and secret nonce , i.e., where is the secret random number assigned to legitimate sensor and user node.
Figure 2.
Time-based keys generation and admission with reference to time passage.
All the symmetric keys generated in the above discussion have a size of 256 bits (32 bytes); hence, in the subsequent section of authentication protocols any symmetric encryption supporting the 256-bit key can be used, e.g., RC5/6 [2]; Rijndael [42], Twofish [43], MARS [44], and Blowfish [45].
4.1.2. The Key Retrieval Protocol
After initial authentication, issues a ticket to the requesting node. The ticket consists of two parts: (1) The first half consists of the sensor node identity (id) , the session key , secret nonce , and the profile. This part of the ticket is encrypted with time-based key . (2) The second half consists of sensor node id , the hash of group id , and the required information to retrieve the time-based key . The hash of group id is an optional field used only if sink nodes can join multiple base stations; in that case, it is used to identify the group and to select the correct keychain. In the key retrieval, information depends on the selected mode and can be the scrambled index value V, index vector , or index value i; the modes of a ticket are explained below.
Mode-01:
In mode-01, the ticket retrieval information comprises the index value , requesting node id , and the hash of the user’s private key. The ticket verifier searches the appended index value within its generated vector . A search hit at the place means that key can decrypt the ticket.
Mode-02:
If the group members are in a fully secure environment, the SMSN employs a simple ticket retrieval strategy. Instead of using a scrambled index value V in mode-02 in the ticket retrieval, the information contains the interval value. In this mode, the ticket verifier does not need to run a search algorithm.
Mode-03:
In mode-03, the ticket retrieval information is the same as in mode-01 except it includes a hash vector of size . These hash values are carefully chosen nodes of the binary hash tree, which is generated such that the leaf nodes are indexed vector values as shown in Figure 3.
Figure 3.
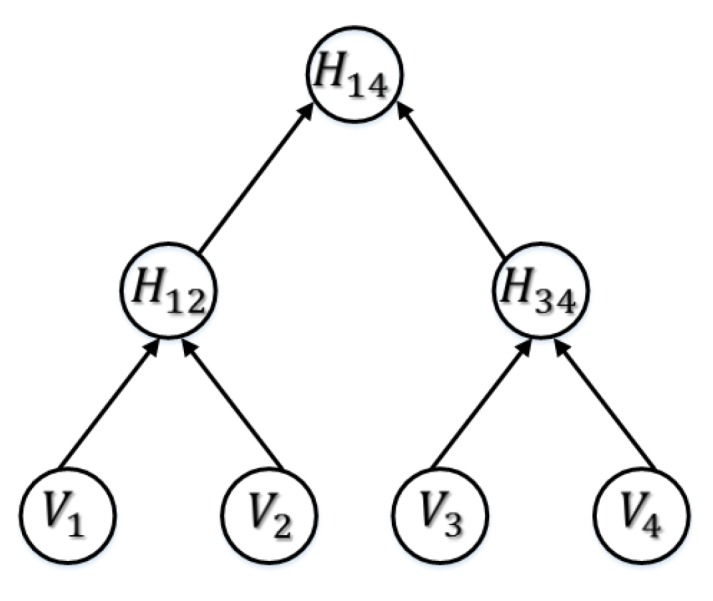
Example of Binary Hash Tree generated with index vector .
Search Algorithm:
Start from the root and move down
Ignore appended values and follow the path of the reconstructed node
Continue until level is reached
At level , select the appended value that is the index value.
Mode-03 is suitable if the Chain of the Key Generator is very long. The tree “root node” is included in (optionally), which ensures that a trusted group member generated .
4.1.3. Key Management Protocol for the Sink Node
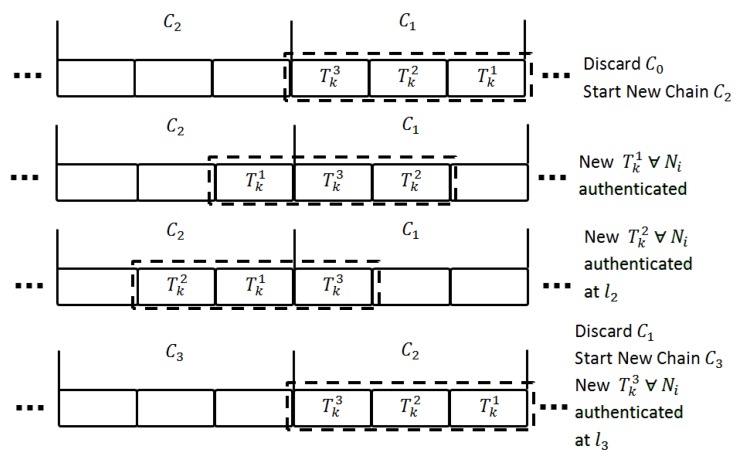
At the start of the Chain of the Key Generator, the sink node reissues the ticket and session keys to associated nodes. To spread out the workload in the time dimension the sink node keeps the history of the previous key chain and issues a ticket/session key based on the moving window algorithm. Let us consider a chain with a length of 3; Figure 4 shows how the sink node spread the workload throughout the chain by adopting the moving window approach.
Figure 4.
Managing the chain of the key generator in the sink.
Step 1: The sink node discards the previous chain and generates the commitment key generator for the next chain . Step 2: The sink node reissues the ticket and session key to all sensor nodes authenticated at interval 1. Step 3: The sink node reissues the ticket and session key to all sensor nodes authenticated at interval 2. Step 4: The sink node reissues the ticket and session key to all sensor nodes authenticated at interval 3 and discards the previous chain and generates the commitment key generator for the next chain.
4.2. Authentication Protocol Suite
When a sensor node joins the system, it goes through the Sensor Activation and Authentication Protocol (SAAP). After SAAP, can establish multiple concurrent secure connections with sink nodes using the authentication ticket (); similarly, uses the for re-authentication while moving across the network. Likewise, when a user node joins the system, it goes through User Activation and Authentication Protocol (UAAP); subsequently, can use the authentication ticket () for authorization to collect data from multiple sink and sensor nodes. In a concurrent run of multiple instances of the protocol, the message authentication plays a critical part in preventing the replay attack and to achieve the objectives of the authentication protocol as defined in [19,20]. In an SMSN message, authentication is accomplished by a secure exchange of a randomly generated nonce challenge. Moreover, in all the protocols discussed below, if the protocol initiator (user or sensor node) does not hear the response to an authentication/switch request, the protocol initiator resends the authentication/switch request including a new nonce and ’resend’ flag. This step helps detect the impersonation, replay, and parallel session attack.
4.2.1. Sensor Activation and Authentication Protocol (SAAP)
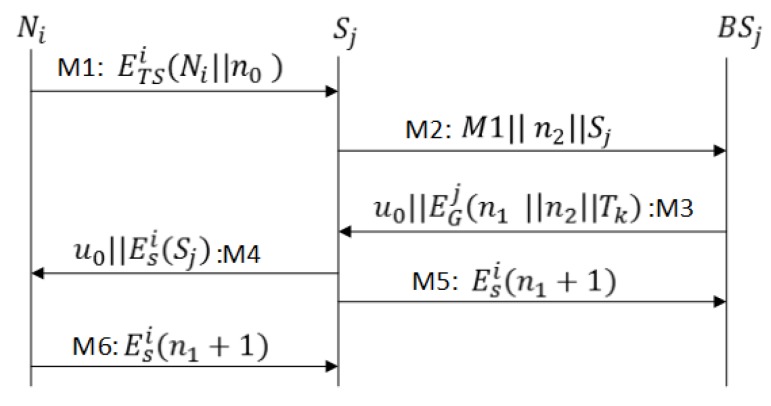
Sink node periodically broadcasts a message (. If a node wants to join the WSN, upon hearing the generates an encryption key , encrypts the joining message with the generated key, and continues as follows:
-
M1
As shown in Figure 5, sends a JOIN message to sink enclosing and encrypted with the generated encryption key .
-
M2
Upon receiving the request from , the forwards the request in conjunction with its identity and challenge to base station .
-
M3
retrieves the profile from the database, and if isa legitimate sensor node, generates the key , and sends to in M3. M3 also includes ticket , (a challenge for ), and (challenge response for the sink node), all encrypted with . The sink node verifies the challenge , stores and retrieves the profile and from the ticket.
-
M4
forwards the to After a challenge ( verification, accepts and may start sending data to .
-
M5
sends the challenge response to for the confirmation of a successful protocol run.
-
M6
After challenge ( confirmation, starts accepting sensor data; otherwise, it marks as an invalid ticket.
Figure 5.
Message exchange for Sensor Activation and Authentication Protocol (SAAP) .
In the SAAP, a secure exchange of ensures the message authentication between the sensor node and the base station, between the sink node and base station, and between the base station and the sink node, while message authentication between the sensor and sink nodes is established by session key encryption and . If is already registered with , in M1 can be replaced with the hash of the password value.
4.2.2. Sensor Re-Authentication Protocol -1 (SRP1)
If sensor node wants to establish multiple secure connections with sinks or when a moves from such that , the Re-Authentication Protocol -1 continues as follows:
-
M1
As shown in Figure 6, sends to . The sink decrypts the ticket, retrieves calculates the hash of , and makes a comparison with received in the switch message. If the value does not match, the will ignore the request and otherwise proceed as follows.
-
M2
sends a challenge response along with the new challenge encrypted with session key .
-
M3
sends the challenge response . After challenge confirmation, starts accepting data; otherwise, it marks as an invalid ticket.
Figure 6.
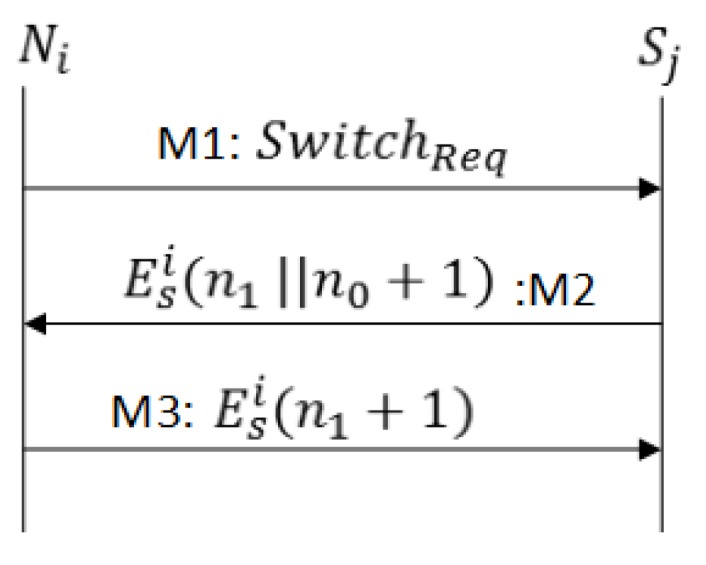
Message exchange for Sensor Re-Authentication Protocol-1 (SRP1).
In the above procedure, secure exchange of ensures the message authentication between the sensor node and the sink node. With this feature, a sensor node can establish multiple secure sessions with various sink nodes as shown in Figure 1.
4.2.3. Sensor Re-Authentication Protocol -2 (SRP2)
If sensor node wants to establish another secure connection with sinks or when a moves from such that , the re-authentication procedure proceeds as follows:
-
M1
As shown in Figure 7, sends to . The sink decrypts the second half of and verifies the identities of and ticket granting base station.
-
M2
After identities verification the sink forwards the request in conjunction with a challenge to base station .
-
M3
retrieves the profile from , and if isa legitimate sensor node, the generates the key , and sends to in M3. M3 also includes ticket , (a challenge for ), and (challenge response for the sink node), all encrypted with . The sink node verifies the challenge , stores and retrieves the profile and from the ticket.
-
M4
forwards to After challenge ( verification accepts and start sending data to .
-
M5
sends the challenge response to ; it confirms a successful protocol run.
-
M6
After challenge ( confirmation start accepting data; otherwise, it marks as an invalid ticket.
Figure 7.
Message exchange for Sensor Re-Authentication Protocol-2 (SRP2).
In the SRP2, a secure exchange of ensures the message authentication between the sensor node and the base station, between the sink node and base station, and between the base station and the sink node, while message authentication between the sensor and sink nodes is established by session key encryption and . If wants to share data in a secret mode, both and generate a private session key . With this feature, a sensor node can establish multiple secure sessions with various sink nodes as shown in Figure 1.
4.2.4. User Activation and Authentication Protocol (UAAP)
In some scenarios a user may desire to access data from the sensor network, for example, in IoT applications such as smart homes and smart buildings, a smartphone user may want to get sensor node data. In SMSN authentication protocol suites, an authenticated user (holding a valid ticket) can access data directly from sensor nodes and/or can collect from the sink node. The ticket structure for is the same as the ticket structure discussed above for where the sensor node identity and profile are replaced with the user node identity and profile. The user profile information includes the permissible accessibility information. In the User Activation and Authentication Protocol (UAAP) a user can acquire a ticket from in two different ways. If the user is not in the communication range of it routes the joining message via the nearest sink node ; the protocol proceeds exactly as in the SAAP. However, if the user is in the communication range of , the user generates an encryption key , encrypts the joining message with the generated key, and proceeds as follows:
-
M1
As shown in Figure 8, sends a JOIN message enclosing and the user identity to base station .
-
M2
retrieves profile from the database, and if is a legitimate user, the generates authentication ticket, and send along with, ( a challenge for ), and (challenge response), all encrypted with . The ticket structure is same except the secret nonce enclosed inside ticket is generated by
-
M3
The user node verifies the challenge , stores and . sends the challenge response to ; it confirms a successful protocol run . After receiving a challenge response the updates the status of from idle to active user.
Figure 8.
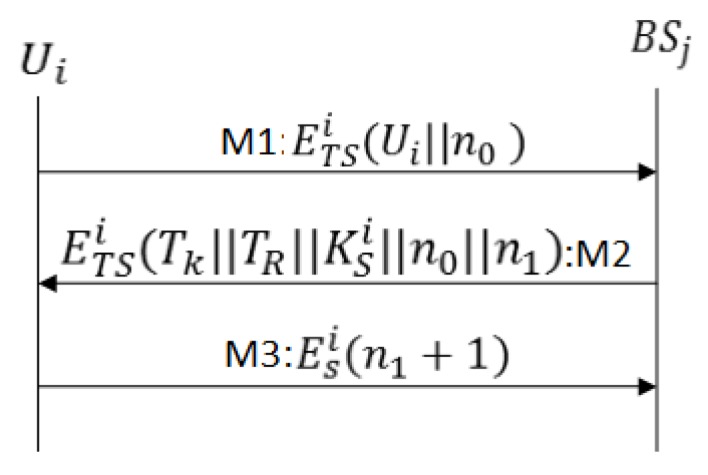
Message exchange for User Activation and Authentication Protocol (UAAP).
In User Activation and Authentication Protocol, secure exchange of ensures the message authentication between user node and base station and between the base station and user node.
4.2.5. User-Sink Authentication Protocol (USiAP)
After acquiring the authentication ticket, if user wants to retrieve data from sink nodes , it sends a JOIN request in conjunction with a ticket to and then follows the same procedure as discussed in Sensor Re-Authentication Protocols 1 and 2; except after ticket verification, can piggyback data with the rest of the messages. Using the authentication ticket, user can also establish multiple concurrent connections with various sink nodes.
4.2.6. User- Sensor Authentication Protocol (USeAP)
After acquiring the authentication ticket, if user wants to access data directly from sensor nodes , it sends a JOIN request in conjunction with a ticket to and the procedure proceeds as follows:
-
M1
As shown in Figure 9, sends a JOIN message in conjunction with ticket and challenge encrypted with its ticket centered session key.
-
M2
Upon receiving the request from the forward the ticket and encrypted challenge to sink node
-
M3
Sink decrypts the ticket and retrieves s profile and session key , and if is a legitimate user node, sends and challenge response to .
-
M4
After challenge verification, generates a private session key and sends a challenge response encrypted with the private session key. also generates the private session key and verifies the challenge response.
Figure 9.
Message exchange for User-Sensor Authentication Protocol (USeAP).
In User-Sensor Authentication Protocol suite, secure exchange of ensures the message authentication between users and sensor node, while the secure exchange of ensures the message authentication between sensor node and sink node.
5. Security Analysis
This section presents the comprehensive security analysis of the SMSN protocol, including an informal security analysis and discussion of a formal security analysis using BAN logic [32], and finally presents the Scyther [17,18] implementation result of the SMSN and previously proposed schemes [11,12,13,14,15,16].
5.1. Informal Analysis and Discussion
To verify the strength of the SMSN protocol against known attacks we introduce an intruder in the network with capabilities as follows: It has an initial information set that contains the IDs of all users, sensor nodes, sink nodes and base stations. It can intercept and record message exchanges between participating entities. It can redirect, spoof, and replay the messages. The subsequent sections show that the intruders, with all the above-mentioned capabilities, fail to launch a successful replay, parallel session, man-in-middle , impersonation, and several other attacks against the SMSN protocol suite.
5.1.1. Replay, Multiplicity, Parallel and Man in Middle Attacks Against the SMSN
We introduce an intruder, as discussed above, in the network and launch replay, multiplicity, parallel session, and man-in-middle attacks against the SMSN for three different scenarios, as shown in Figure 10, Figure 11 and Figure 12. The intruder Zimpersonates a protocol participant, intercepts the messages, and replays them to deceive other protocol participants. Replay, multiplicity, parallel, and man-in-middle attacks against the SAAP for three different scenarios are given below.
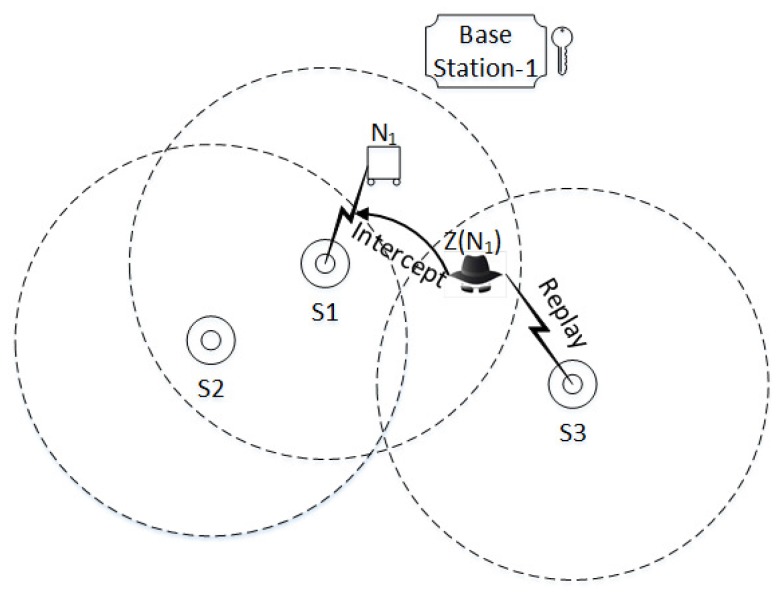
Figure 10.
The intruder Z impersonates the protocol initiator (can be a sensor or user node). Intruder intercepts the messages between and sink and replays them to sink . Both sinks are associated with base station 1 and share the same keychain.
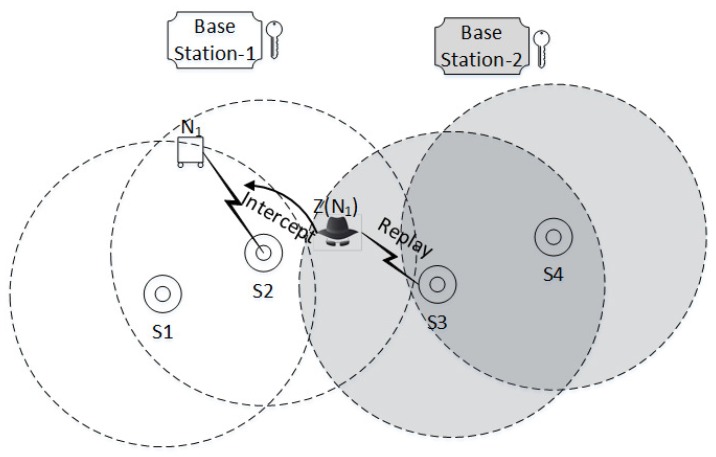
Figure 11.
The intruder Z impersonates the protocol initiator (can be a sensor or user node). Intruder intercepts the messages between and sink and replays them to sink . Sink is associated with base station 1 , and Sink is associated with base station 2.
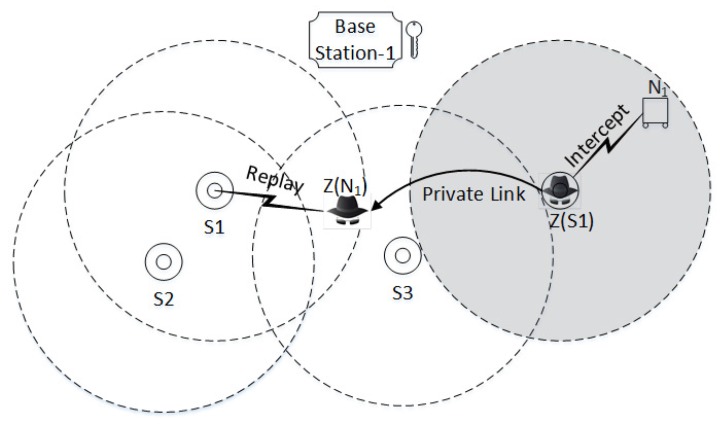
Figure 12.
Two intruders impersonate the sink node and sensor node ; the intruder is within the region of , and intruder is outside somewhere close to node . Both intruders can communicate with zero communication delay via a private link.
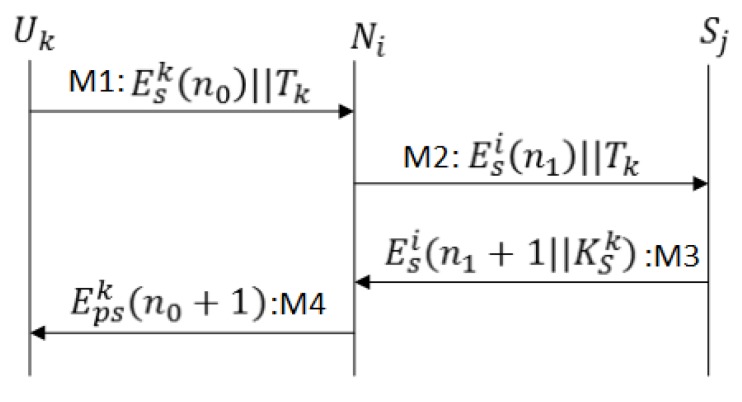
Scenario 1:
For the given scenario in Figure 10, let us suppose a sensor node sends a request for authentication to sink . During the protocol run an intruder intercepts the messages and replays them to another sink ; the attack proceeds as follows: The intruder intercepts M1 and replays it to . The attack is detected immediately when receives two M2 messages enclosing the same M1. sends M3 to both sinks comprising the ’Alert’ flag and a different nonce challenge. intercepts M6 and replays it to ; note that the intercepted message M6 comprises a different which is the only valid response for a sink . Upon receiving the wrong challenge response, the sink identifies the intruder node. The SAAP not only detects the replay attack but also identifies the intruder.
Scenario 2:
For the given scenario in Figure 11, let us suppose a sensor node sends a request for authentication to sink . During the protocol run an intruder intercepts the messages and replays them to another sink ; the attack proceeds as follows: The intruder intercepts M1 and replays it to . Unlike in scenario 1, neither base station and can detect the attack at this stage and replies with a normal M3 to associated sink nodes and respectively. However, both M3 messages comprise a different nonce challenge. intercepts the M6 and replays it to ; note that the intercepted message M6 contains a different which is the only valid response for the sink . Upon receiving the wrong challenge response, the sink identifies the intruder.
Scenario 3:
For the given scenario in Figure 12, let us suppose two intruders impersonate the sink and sensor node ; the intruder is within the region of , and intruder is outside somewhere close to node Furthermore, both intruders can communicate through a private link with zero delay. During the protocol run intruder intercepts the messages sent by sensor node and replays it to ; also shares all the intercepted messages with fellow intruder via a private secure channel; the attack proceeds as follows: The intruder intercepts M1 sent by and shares the intercepted message with . The intruder sends the intercepted message to ; the protocol proceeds normally and upon receiving M4 the intruder sends the message M4 to . The intruder sends M4 to sensor node ; upon receiving M6 the intruder shares the message M6 with . The intruder sends M6 to and the attack is completed. The attack is only successful if the replay of M6 is delivered to within a time interval of where L is the length of the keychain. Moreover, in practice when the private link between fellow intruders adds a communication delay, can detect the attack by comparing the (registration time sent in with the local time.
As the outcome of the above attack, considers that the authentication process was completed successfully. However, the intruders cannot get any useful information during a protocol run: does not know the session key delivered to , so cannot further communicate with . Due to the unavailability of a data link, uses the ticket to run SRP1/2. However, a problem exists on the other side: sink and base station consider that they authenticated a legitimate sensor successfully; from their point of view, the sensor is within the region of but in reality, is in the region of . Similarly, in the case of SRP1, SRP2, UAAP, USiAP, and USeAP the intruder Z fails to launch successful attacks for scenarios 1 and 2; however, the intruder Zcompletes the attack in scenario 3.
In a nutshell, replay, multiplicity, parallel and man-in-middle attacks against the SMSN protocol are not successful. Even though in scenario 3 the intruders completed the attack, they could not cause a serious security issue because after the completion of the protocol run, the intruder could not get useful information such as the session key, ticket, or partial session key. Furthermore, the attack can be avoided by introducing a timestamp in each message exchange. For illustration, the intruders need to wait for a significantly longer time to replay M4 and M6, and this significant delay can be detected with the time stamp, which reveals the existence of the intruder in the network.
5.1.2. Black Hole Attack
In a black hole attack [46,47,48] the intruder impersonates a node and blocks or drops the messages upon receiving them. In the SMSN, the sensor and user nodes can connect to multiple sink nodes simultaneously; hence, failure of data exchange on one route does not block the data delivery towards the base station. Moreover, the black hole attack is detectable in our scheme because the SMSN ensures binding by employing an exchange of secret nonce between , and Consecutive failures of exchange of challenge detects the black hole attack. Once the black hole is detected, the sensor node can send data via another sink node.
5.1.3. Wormhole Attack
In a wormhole attack [49,50], the intruder captures the messages in one location and tunnel to another location to a fellow intruder who replays the tunneled messages in another location area. The attack discussed in scenario 3 can be regarded as a wormhole attack. From the point of view of replay, multiplicity, parallel and man-in-middle attacks, the attack in scenario 3 did not achieve its objectives, but from the point of view of the wormhole attack, the attack is successful. The solution for the problem is similar to the one we discussed earlier: the attack can be avoided by introducing a timestamp in each message exchange.
5.1.4. Analytical Attacks
In an analytic attack [31,51], the intruder intercepts the messages and using cryptanalysis tries to recover a cryptographic key. With the inclusion of a time-based key, our scheme inherits the freshness property, which defies the capability of the intruder to launch analytical attacks, as it has a max time of to acquire the time-based key, which makes it difficult to launch analytical attacks.
5.1.5. Topological Centered Attacks
In [52,53] the authors presented an authentication protocol for a sensor network in which the sink issues a re-authentication ticket that includes a list of neighbor sink nodes. This information can lead to topological centered attacks [27,28] such as identity replication attacks. In our scheme, the topological information is entirely obscured from the sink and sensor nodes.
5.2. Formal Analysis Using BAN Logic
The BAN logic [32] is a widely used formal method for the formal analysis of security protocols. To prove the security of the SMSN protocol suite it is sufficient to demonstrate the security of the SAAP and UAAP protocols; the rest of the protocols are extensions of the SAAP and UAAP and use the ticket and session key established in the SAAP and UAAP protocols run. Hence, proof of SAAP and UAAP protocols concludes the security of the SMSN protocol suite.
The three basic objects of BAN logic are principals, formula/statements, and encryption keys. The principals, the protocol participants, are represented by symbols P and Q. The formula/statements are symbolized by X and Y and represents the content of the message exchanged. The encryption keys are symbolized by K. The logical notations of BAN-logic used for our analysis is given below:
believes X, or P would be enabled to believe X; in conclusion, P can take X as true.
sees/receives X. P initially has or received a message X and P can see the contents of the message and is capable of repeating X.
once said P has sent a message including the statement X. However, the freshness of message is unknown.
controls X and should be trusted for formula/statement X.
is fresh; it says, X never sent by any principal before.
and Q shares a key K to communicate in a secure way and K is only known to P, Q and a trusted principal.
The statement X is encrypted by key
It stand for X combined with Y is anticipated to be secret and its implicit or explicit presence proves the identity of a principal who completes the .
Some primary BAN-logic postulates used in the analysis of the SMSN are given below:
Message meaning rules: ,
Nonce verification rule:
Jurisdiction rule:
Freshness rule:
Believe rule:
Session key rule:
5.2.1. BAN Logic Analysis of SAAP
The SAAP protocol should achieve the following goals:
-
G1
-
G2
-
G3
-
G4
Protocol Idealization:
-
I1
-
I2
-
I3
-
I4
-
I5
-
I6
Initial State Assumptions:
-
A1
-
A2
-
A3
-
A4
-
A5
-
A6
-
A7
-
A8
-
A9
-
A10
-
A11
-
A12
Let us analyze the protocol to show that and share a session key:
From I1, we have
| (1) |
The (1), A6 and message meaning rule infers that
| (2) |
The A1 and freshness conjuncatenation comprehends that
| (3) |
The (2), (3) and nonce verification rule deduces that
| (4) |
The (4) and believe rule infers that
| (5) |
From A2, (5) and jurisdiction rule, it concludes
| (6) |
This belief confirms that has received a message from a legitimate .
From I2, we have
| (7) |
The (7) and message meaning it infers that
| (8) |
The A2, A1, (3) and freshness conjuncatenation comprehends that
| (9) |
According to nonce freshness, this proves that confirms that is recently alive and running the protocol with .
From I3, we have
| (10) |
The A7 and (10) deduce that
| (11) |
The A3, (11) and freshness conjuncatenation comprehends that
| (12) |
The (11), (12) and nonce verification rule infers that
| (13) |
The (13) and believe rule comprehends that
| (14) |
The logic belief proves that is confident and believes that is issued by ; moreover, the freshness of the key also suggests that is alive and running the protocol with and .
The (13), (14) and jurisdiction rule concludes that (15 Goal-3)
| (15) |
From I4, we have
| (16) |
The (16), A5 and message meaning rule comprehends that
| (17) |
The (17), A4 and freshness conjuncatenation rule infers that
| (18) |
The (17), (18) and nonce verification rule deduce that
| (19) |
The (19) and believe rule infers that
| (20) |
The (19), (20) and jurisdiction rule concludes that (21 Goal-1)
| (21) |
From I5, we have
| (22) |
The (15), (21), (22) and meaning rule comprehends that (23 Goal-4)
| (23) |
From I6, we have
| (24) |
The (15), (21), (23) and nonce verification rule deduce that (25 Goal-2)
| (25) |
1. BAN Logic Analysis of UAAPP:
The UAAP protocol should achieve the following goals:
-
G1
-
G2
-
G3
Idealization of UAAP:
-
I1
-
I2
-
I3
Initial State Assumptions of UAAP:
-
A1
-
A2
-
A3
-
A4
-
A5
-
A6
Let us analyze the protocol to show that achieves the mentioned goals:
From I1, we have
| (26) |
The (26), A4 and message meaning rule infers that
| (27) |
The A1 and freshness conjuncatenation comprehend that
| (28) |
The (27), (28) and nonce verification rule deduces that
| (29) |
The (29) and believe rule infers that
| (30) |
From A1, (30) and jurisdiction rule, it concludes
| (31) |
This belief confirms that has received a message from a legitimate .
From M2, we have
| (32) |
The (32), A3 and message meaning rule comprehends that
| (33) |
The (33), A2 and freshness conjuncatenation rule infers that
| (34) |
The (33), (34) and nonce verification rule deduce that
| (35) |
The (35) and believe rule infers that (36 Goal-2)
| (36) |
The (35), (36) and jurisdiction rule concludes that (37 Goal-1)
| (37) |
From I3, we have
| (38) |
The (36), (37), (38) and meaning rule comprehends that (39 Goal-3)
| (39) |
5.3. Verifying Protocol Using Scyther Tool
The previous section proved that according to the BAN logic the SMSN is a secure authentication scheme. The BAN logic provided a foundation for the formal analysis of security protocols, but few attacks can slip through the BAN logic [32]. For further proof of the strength of the SMSN protocol suite, we implemented the SMSN and [11,12,13,14,15,16] schemes in the automated security protocol analysis tool, Scyther [17,18]. Our proposed scheme provides a strong defense against known attacks in the presence of an intruder (Z) which is capable of regulating the communication channel, redirecting, spoofing, replaying or blocking the messages. It has initially known information, e.g., IDs and public keys of all users, and any intercepted message is additional information to the current information set (S), i.e., . It can generate a fresh message from known data, e.g., , and can run multiple instances of the protocol. The Scyther tool verifies the protocol claims and checks the possibility of attacks against the protocol. The claims are the event that describes the design and security properties of the authentication protocol. We consider four claims as defined below; for a detailed description of protocol claims, please refer to [19,20].
In Scyther the protocol is modeled as an exchange of messages among different participating ’roles’; for instance, in sensor node authentication, the sensor node is in the role of initiator, the sink is in the role of responder and the base station is in the role of a server. The Scyther tool integrates the authentication properties into the protocol specification as a claim event. We tested our protocol [11,12,13,14,15,16] employing claims, as mentioned earlier, with the parameter settings given in Table 1.
Table 1.
Scyther tool parameter settings.
| Parameter | Settings |
|---|---|
| Number of Runs | 1∼3 |
| Matching Type | Find all Type Flaws |
| Search pruning | Find All Attacks |
| Number of pattern per claim | 10 |
The results are shown in Table 2. It is clear that in the presence of an intruder (as defined above), our protocol qualifies all the protocol claims and no attacks were found. Hence, for a large number of systems and scenarios, our protocol guarantees safety against a large number of known attacks, such as impersonating, man-in-middle and replay attacks, etc. In contrast, [11,12,13,14,15,16] are susceptible to several attacks and failed to fulfill the authentication claims. Moreover, in protocol schemes [11,12,13,14,15,16], there is a lack of sender-receiver binding verification, and an intruder can exploit this situation to impersonate a sensor node and run multiple instances of the protocol to launch multiplicity and man-in-middle attacks.
Table 2.
Comparison of authentication properties.
| Claims | H. Tseng [11] | Yoo et al. [12] | Kumar et al. [13] | Quan et al. [14] | Farash et al. [15] | Y. Lu et al. [16] | SMSN | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Aliveness | N | N | N | N | N | N | Y | N | N | Y | N | N | Y | Y | N | N | N | Y | Y | Y | Y |
| Weak Agreement | N | N | N | N | N | N | Y | N | N | Y | N | N | Y | Y | N | N | N | Y | O | Y | Y |
| Non-injective Agreement | N | N | N | N | N | N | O | N | N | Y | N | N | Y | Y | N | N | N | Y | O | Y | Y |
| Non-injective Synch. | N | N | N | N | N | N | O | N | N | Y | N | N | Y | Y | N | N | N | Y | O | Y | Y |
N = Authentication claim is not fulfilled; Y = Authentication claim is fulfilled; O = Authentication claim is fulfilled but falsified for protocol instances >3.
6. Performance Analysis
Although the SMSN authentication protocol suite covers authentication procedures for both sensor and user nodes, for the sake of simplicity, we compare the efficiency of the SMSN with user authentication protocols. We compared the efficiency of the SMSN user authentication protocols considering computational cost, message complexity and time synchronization requirements to that of [11,12,13,14,15,16]. Unlike in [11,12,13,14,15,16], the SMSN allows the user to be authenticated with both sensor and sink nodes.
The total computation cost is estimated as the sum of the total number of E = encryptions/decryptions, M = Multiplications, H = hash, X = XOR, and T = Time Synchronization operations. Moreover, we assume that cryptographic hash and symmetric encryption/decryption operations have computational complexity similar to , where m is the size of the message. All the schemes in [11,12,13,14,15,16] considered that the registration process took place via a secure channel. We assume that in all schemes the user node and Gateway exchange the registration information using a secure encrypted channel. Furthermore, one encrypted unicast message requires two E operations, one for encryption and one for decryption. Similarly, a broadcast message to N recipient adds the operations in the total computational complexity.
From Table 3 we can see that computational complexity of SMSN authentication protocols in the registration phase is slightly more expensive compared to Kumar et al. [13] and Farash et al. [15]; however; in the authentication phase, the SMSN authentication protocols completely outperform Kumar et al. [13] and Farash et al. [15]. H. Tseng [11] and Yoo et al. [12] are the most computationally expensive schemes during the registration phase, but in the authentication phase, H. Tseng [11] is the most efficient scheme followed by the SMSN. However, regarding sensor node computational efficiency, in our scheme, the overall workload of a sensor node is very low. Moreover, unlike the [12,13,14,21] schemes, the SMSN does not require time synchronization between the Gateway and user node.
Table 3.
Performance comparison of SMSN with well-known user authentication protocols.
| Schemes | Phase | Comp. Complexity | Comm. Complexity | Comm. Cost in Bytes | Time Synch. |
|---|---|---|---|---|---|
| H. Tseng [11] | Registration | - | |||
| Login-Authentication | |||||
| Yoo et al. [12] | Registration | - | |||
| Login-Authentication | |||||
| Kumar et al. [13] | Registration | - | |||
| Login-Authentication | |||||
| Quan et al. [14] | Registration | ||||
| Login-Authentication | |||||
| Farash et al. [15] | Registration | ||||
| Login-Authentication | |||||
| Y. Lu et al. [16] | Registration | - | |||
| Login-Authentication | |||||
| SMSN (User-Sink) | Registration | - | |||
| Login-Authentication | |||||
| SMSN (User-Sensor) | Registration | - | |||
| Login-Authentication |
Computational Complexity: E = encryptions/decryptions, = modular exponentiations, M = multiplications, H = hash operation, X = operation , N = Total number of nodes , T = Time Synchronization operation; Communication Complexity and Cost: = Broadcast Message, = Unicast Message, = 32 bytes (Represents Size of Cryptographic KeyHash and Signature), = 4 bytes ( Represents Size of nonce, Node Ids and Integers), f = 8 bytes (Represents Size of the floating point real number.
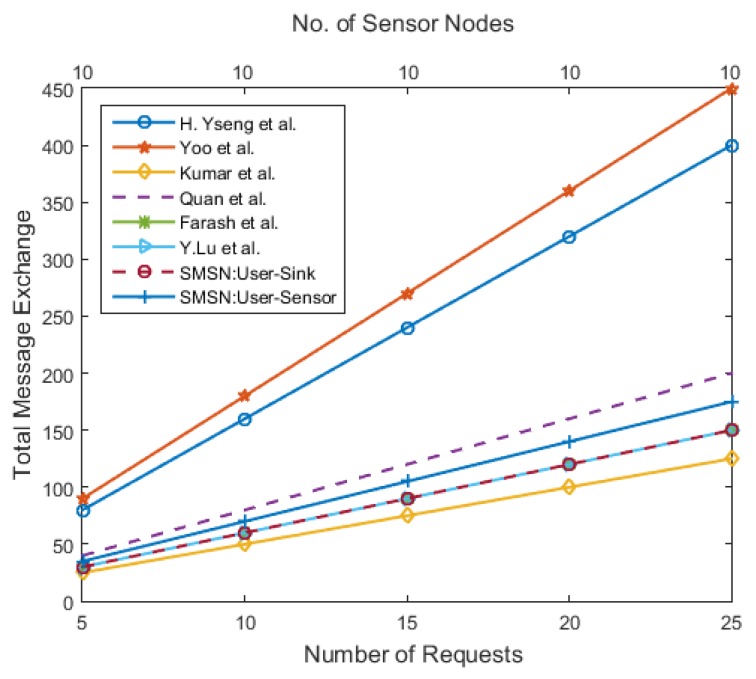
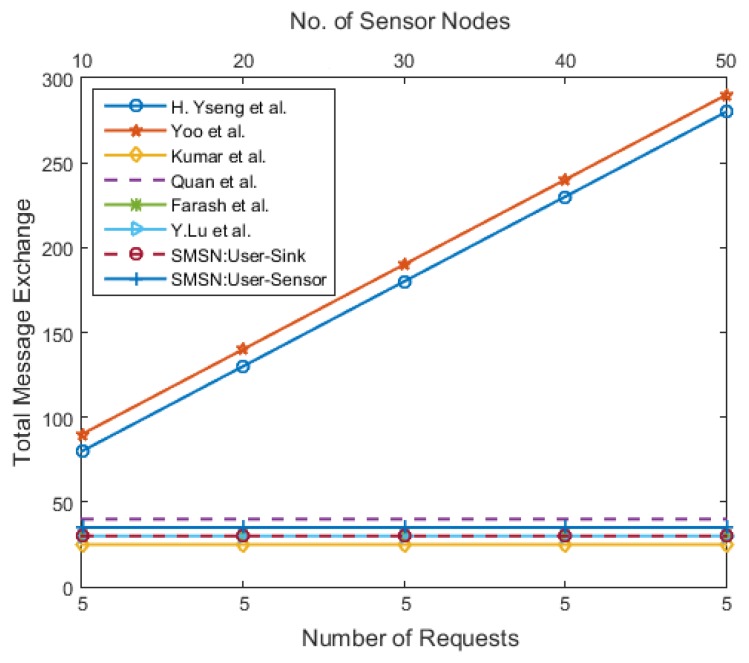
The communication complexity is calculated as the sum of the total unicast and broadcast message exchange. Figure 13 shows the overall communication complexity in a WSN when the number of sensor nodes is fixed in the network, and the number of new users’ requests is constantly increasing. The message complexity of [11,12] increases multiplicatively by increasing the number of nodes; conversely, it grows slowly in the case of the SMSN, [13,14,15]. Figure 14 shows the overall communication complexity for various network sizes with the same number of user requests. This metric is only useful for a WSN with mobile sensor and user nodes. The message complexity of [11,12] increases rapidly with an increase in the number of new users’ requests; conversely, it remains constant with the SMSN, [13,14,15]. This suggests that the schemes proposed in [11,12] are not suitable for highly dynamic mobile WSNs where the frequency of leaving and joining the network is high.
Figure 13.
The total number of message exchanged between constant number of sensor nodes with different number of new users’ requests.
Figure 14.
The total number of message exchanged for constant number of new users request in different network size.
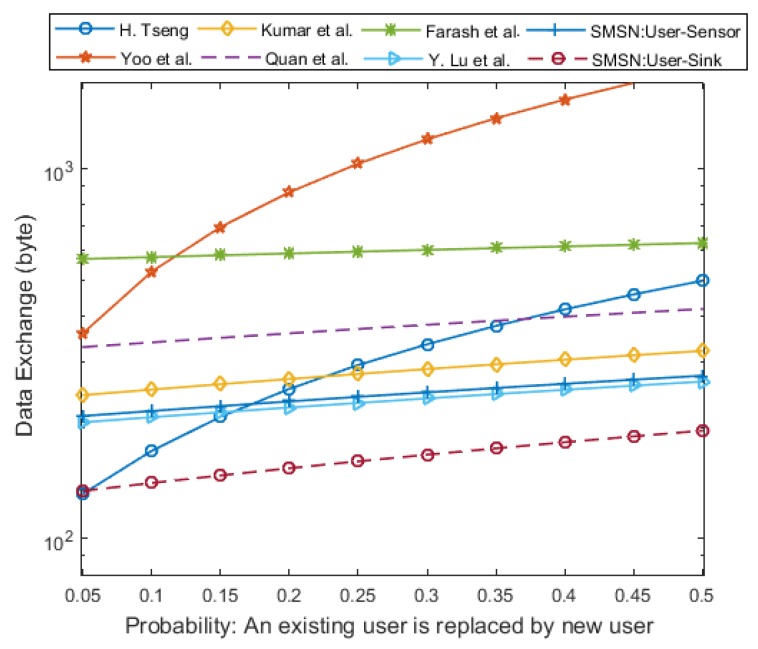
However, a more interesting comparison in terms of communication efficiency is the comparison based on the amount of data exchanged during the protocol run. The numerical results are taken for a dynamic and mobile sensor network consisting of 100 nodes. The probability that a new user may join the network and an existing user may leave the system defines how frequently the users join and leave the network. The average communication cost per user is calculated for the dynamic probability of 0.05 to 0.5, and the results are shown in Figure 15.
Figure 15.
The amount of data exchanged for less to highly dynamic sensor network.
SMSN user-sink authentication outperforms all other schemes from less dynamic to highly dynamic networks. However, in a less dynamic network with a dynamic probability of less than 0.05, the SMSN user-sensor authentication is slightly more expensive than the scheme of H. Tseng [11]. Even though in a less dynamic system the SMSN user-sensor authentication is slightly more expensive than [11], the performance gap decreases, and for highly mobile and dynamic networks, SMSN performs better than the scheme of H. Tseng [11].
7. Conclusions
Due to the recent growth in WSN technologies, we have observed an enormous paradigm shift in sensor network applications. The authentication and security goals of a sensor network have become more crucial and challenging. Most of the user and sensor node authentication schemes for WSNs have been developed without taking into account the requirements of integrating WSNs with emerging technologies such as IoT. We developed an SMSN scheme considering the requirements of mobile and dynamic WSN applications as discussed in Section-III. We noted that the user authentication schemes designed for sensor networks [11,12,13,14,15,16] do not meet the authentication properties; for example, the execution of these schemes in the Scyther tool revealed that the participating entities failed to achieve wider objectives (defined as protocol claims in Section 5-C) of the authentication protocol. Finally, we compared the efficiency of the SMSN user authentication protocols with the schemes in [11,12,13,14,15,16]. We observed that concerning the computational cost, our scheme is slightly more expensive compared to [13,15] during the registration phase but the SMSN totally outperforms both in the authentication phase. Regarding message complexity our proposed scheme totally outperforms [11,12,13,14,15]; however, the performance of the scheme of Y. Lu et al. [16] is close to the SMSN. Finally, unlike the schemes in [11,12,13,14,15,16], the SMSN does not require time synchronization between the Gateway (base station) and the user node. The main focus of this work was to discuss and provide solutions for the emerging challenge that has emerged from the integration of the WSN in IoT applications. To prove the usability of the proposed scheme, we made a comprehensive security and performance analysis and simulated the proposed idea in an automated protocol verifier tool, the Scyther. However, for future work, it will be interesting to investigate the usability of the SMSN by implementing it on an application specific testbed. Moreover, in the near future it will be possible to incorporate the basic Internet functionality in the sensor node. We believe it will further enhance the application scenarios for the SMSN; for instance a user device will be able to collect real-time sensor data remotely via the Internet. Moreover, we are further investigating the usage of SMSN for the promising future internet architecture, known as Name-Data-Networking (NDN), which is extensively studied in the literature [54,55,56,57,58,59]. In NDN the contents verification is achieved by the use of asymmetric cryptography. We argue that in future especially in IoT application scenarios the devices will be resource constraint devices; for instance, the sensor network is going to be the part of IoT. For resource constraint devices the asymmetric cryptography is computationally expensive. We believe that SMSN protocol suit with some modifications can be a suitable candidate for NDN internet architecture.
Acknowledgments
This work was supported by the Ministry of Trade, Industry & Energy (MOTIE, Korea) under Industrial Technology Innovation Program. No. 10065742, Standardization of Vertical and Horizontal Smart-factory Integration.
Abbreviations
The following abbreviations are used in this manuscript:
| WSN | Wireless Sensor Network |
| IoT | Internet of Things |
| SMSN-Protocol | Secure Mobile Sensor Network Protocol |
| BAN-logic | Burrows Abadi Needham logic |
| SAAP | Sensor Activation and Authentication Protocol |
| SRP1 | Sensor Re-Authentication Protocol-1 |
| SRP2 | Sensor Re-Authentication Protocol-2 |
| UAAP | User Activation and Authentication Protocol |
| USiAP | User-Sink Authentication Protocol |
| USeAP | User- Sensor Authentication Protocol |
Author Contributions
Muhammad Bilal proposed the scheme, and performed the security and performance analysis. He also wrote the experiment code, conducted the experiments and evaluated the performance of the proposed scheme. Shin-Gak Kang amended the manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Koyama K., Maurer U.M., Okamoto T., Vanstone S.A. Advances in Cryptology—CRYPTO ’91. Springer; Berlin/Heidelberg, Germany: 1992. New public-key schemes based on elliptic curves over the ring Zn; pp. 252–266. [Google Scholar]
- 2.Rivest R.L. International Workshop on Fast Software Encryption. Springer; Berlin/Heidelberg, Germany: 1994. The RC5 encryption algorithm; pp. 86–96. [Google Scholar]
- 3.Wong Y., Attebury G., Ramamurthy B.A. Survey of security issues in wireless sensor networks. IEEE Commun. Surv. 2006;8:2–23. doi: 10.1109/COMST.2006.315852. [DOI] [Google Scholar]
- 4.Zhang J., Varadharajan V. Wireless sensor network key management survey and taxonomy. J. Netw. Comput. Appl. 2010;33:63–75. doi: 10.1016/j.jnca.2009.10.001. [DOI] [Google Scholar]
- 5.Panic G., Stecklina O., Stamenkovic Z. An embedded sensor node microcontroller with crypto-processors. Sensors. 2016;16:607. doi: 10.3390/s16050607. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 6.Kim D., An S. PKC-Based DoS attacks-resistant scheme in wireless sensor networks. IEEE Sens. J. 2016;16:2217–2218. doi: 10.1109/JSEN.2016.2519539. [DOI] [Google Scholar]
- 7.Hancke G.P., Silva B.C., Hancke G.P., Jr. The Role of Advanced Sensing in Smart Cities. Sensors. 2012;13:393–425. doi: 10.3390/s130100393. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 8.Sagl G., Resch B., Blaschke T. Contextual sensing: Integrating contextual information with human and technical geo-sensor information for smart cities. Sensors. 2015;15:17013–17035. doi: 10.3390/s150717013. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 9.Flammini A., Sisinni E. Wireless sensor networking in the internet of things and cloud computing era. Procedia Eng. 2014;87:672–679. doi: 10.1016/j.proeng.2014.11.577. [DOI] [Google Scholar]
- 10.Bilal M., Kang S.G. Time-Assisted authentication protocol. Int. J. Commun. Syst. 2017 doi: 10.1002/dac.3309. [DOI] [Google Scholar]
- 11.Tseng H.R., Jan R.H., Yang W. An improved dynamic user authentication scheme for wireless sensor networks; Proceedings of the IEEE Global Communications Conference; Washington, DC, USA. 26–30 November 2007. [Google Scholar]
- 12.Yoo S.G., Park K.Y., Kim J. A security-performance-balanced user authentication scheme for wireless sensor networks. Int. J. Distrib. Sens. Netw. 2012;2012:382810. doi: 10.1155/2012/382810. [DOI] [Google Scholar]
- 13.Kumar P., Gurtov A., Ylianttila M., Lee S., Lee H. A strong authentication scheme with user privacy for wireless sensor networks. ETRI J. 2013;35:889–899. doi: 10.4218/etrij.13.0113.0103. [DOI] [Google Scholar]
- 14.Zhou Q., Tang C., Zhen X., Rong C. A secure user authentication protocol for sensor network in data capturing. J. Cloud Comput. Adv. Syst. Appl. 2015;4:6. [Google Scholar]
- 15.Farash M.S., Turkanovi M., Kumari S., Hölbl M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016;36:152–176. doi: 10.1016/j.adhoc.2015.05.014. [DOI] [Google Scholar]
- 16.Lu Y., Li L., Peng H., Yang Y. An energy efficient mutual authentication and key agreement scheme preserving anonymity for wireless sensor networks. Sensors. 2016;16:837. doi: 10.3390/s16060837. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 17.Cremers C. International Conference on Computer Aided Verification. Springer; Berlin/Heidelberg, Germany: 2008. The scyther tool: Verification, falsification, and analysis of security protocols; pp. 414–418. [Google Scholar]
- 18.Cremers C., Mauw S. Operational Semantics and Verification of Security Protocols. Springer Science & Business Media; Berlin/Heidelberg, Germany: 2012. Security properties. [Google Scholar]
- 19.Lowe G. A hierarchy of authentication specifications; Proceedings of the 10th on Computer Security Foundations workshop; Canton, MA, USA. 10–12 June 1997. [Google Scholar]
- 20.Cremers C., Mauw S., De Vink E.P. Injective synchronisation: An extension of the authentication hierarchy. Theor. Comput. Sci. 2006;367:139–161. doi: 10.1016/j.tcs.2006.08.034. [DOI] [Google Scholar]
- 21.Wong K.H.M., Zheng Y., Cao J., Wang S. A dynamic user authentication scheme for wireless sensor networks; Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing; Taichung, Taiwan. 5–7 June 2006. [Google Scholar]
- 22.Das M.L. Two-Factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009;8:1086–1090. doi: 10.1109/TWC.2008.080128. [DOI] [Google Scholar]
- 23.Han K., Kim K., Shon T. Untraceable mobile node authentication in WSN. Sensors. 2010;10:4410–4429. doi: 10.3390/s100504410. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 24.Han K., Shon T. Efficient mobile sensor authentication in smart home and WPAN. IEEE Trans. Consum. Electron. 2010;56:591–596. doi: 10.1109/TCE.2010.5505975. [DOI] [Google Scholar]
- 25.Yeh H., Chen T., Liu P., Kim T., Wei H. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors. 2011;11:4767–4779. doi: 10.3390/s110504767. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 26.Kumari S., Om H. Authentication protocol for wireless sensor networks applications like safety monitoring in coal mines. Compu. Netw. 2016;104:137–154. doi: 10.1016/j.comnet.2016.05.007. [DOI] [Google Scholar]
- 27.Kumari S., Khan M.K., Atiquzzaman M. User authentication schemes for wireless sensor networks: A review. Ad Hoc Netw. 2015;27:159–194. doi: 10.1016/j.adhoc.2014.11.018. [DOI] [Google Scholar]
- 28.Xie M., Han S., Tian B., Parvin S. Anomaly detection in wireless sensor networks: A survey. J. Netw. Comput. Appl. 2011;34:1302–1325. doi: 10.1016/j.jnca.2011.03.004. [DOI] [Google Scholar]
- 29.Ko L. A novel dynamic user authentication scheme for wireless sensor networks; Proceedings of the IEEE International Symposium on Wireless Communication Systems; Reykjavik, Iceland. 21–24 October 2008. [Google Scholar]
- 30.Chen T., Shih W. A robust mutual authentication protocol for wireless sensor networks. ETRI J. 2010;32:704–712. doi: 10.4218/etrij.10.1510.0134. [DOI] [Google Scholar]
- 31.Khan M.K., Alghathbar K. Cryptanalysis and security improvements of ’two-factor user authentication in wireless sensor networks’. Sensors. 2010;10:2450–2459. doi: 10.3390/s100302450. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 32.Burrows M., Abadi M., Needham R.M. Proceedings of the Royal Society of London A: Mathematical, Physical and Engineering Sciences. Volume 426. The Royal Society; London, UK: 1989. A logic of authentication; pp. 233–271. [Google Scholar]
- 33.Lee C.-C., Li C.-T., Chen S.-D. Two attacks on a two-factor user authentication in wireless sensor network. Parallel Process. Lett. 2011;21:21–26. doi: 10.1142/S0129626411000047. [DOI] [Google Scholar]
- 34.Gligor V.D., Kailar R., Stubblebine S., Gong L. Logics for cryptographic protocols-virtues and limitations; Proceedings of the IEEE Computer Security Foundations Workshop IV; Franconia, NH, USA. 18–20 June 1991; pp. 219–226. [Google Scholar]
- 35.Boyd C., Mao W. Advances in Cryptology- EUROCRYPT ’93. Springer; Berlin/Heidelberg, Germany: 1993. On a limitation of BAN logic; pp. 240–247. [Google Scholar]
- 36.Kumar P., Lee S., Lee H. E-SAP: Efficient-Strong authentication protocol for healthcare applications using wireless medical sensor networks. Sensors. 2012;12:1625–1647. doi: 10.3390/s120201625. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 37.He D., Kumar N., Chen J., Lee C., Chilamkurti N., Yeo S. Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimed. Syst. 2015;21:49–60. doi: 10.1007/s00530-013-0346-9. [DOI] [Google Scholar]
- 38.Armando A., Basin D., Boichut Y. The AVISPA Tool for the Automated Validation of Internet Security Protocols and Applications. [(accessed on 22 September 2016)]; Available online: https://www.inf.ethz.ch/personal/basin/pubs/avispa05.pdf.
- 39.Li C.-T., Weng C.-Y., Lee C.-C. An advanced temporal credential-based security scheme with mutual authentication and key agreement for wireless sensor networks. Sensors. 2013;13:9589–9603. doi: 10.3390/s130809589. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 40.Bilal M., Kang S.G. A secure key agreement protocol for dynamic group. Clust. Comput. 2017 doi: 10.1007/s10586-017-0853-0. [DOI] [Google Scholar]
- 41.Perrig A., Canetti R., Tygar J.D., Song D. The TESLA Broadcast Authentication Protocol. [(accessed on 16 June 2016)]; Available online: https://www.cs.berkeley.edu/~tygar/papers/TESLA_broadcast_authentication_protocol.pdf.
- 42.Daemen J., Rijmen V. National Institute of Standards and Technology; [(accessed on 25 September 2016)]. AES Proposal: Rijndael. Available online: https://csrc.nist.gov/archive/aes/rijndael/Rijndael-ammended.pdf. [Google Scholar]
- 43.Schneier B., Kelsey J., Whiting D., Wagner D., Hal C. Twofish: A 128-bit Block Cipher. [(accessed on 25 September 2016)]; Available online: https://www.schneier.com/academic/paperfiles/paper-twofish-paper.pdf.
- 44.Burwick C., Coppersmith D., D’Avignon E., Gennaro R., Halevi S., Jutla C., Matyas S.M., O’Connor L., Peyravian M., Safford D., et al. MARS-a Candidate Cipher for AES. [(accessed on 25 September 2016)]; Available online: http://www.nada.kth.se/kurser/kth/2D1449/99-00/mars.pdf.
- 45.Schneier B. Fast Software Encryption. Springer; Berlin/Heidelberg, Cermany: 1994. Description of a new variable-length key, 64-bit block cipher (Blowfish) pp. 191–204. [Google Scholar]
- 46.Kumar V., Kumar R. An adaptive approach for detection of blackhole attack in mobile Ad hoc network. Proced. Comput. Sci. 2015;48:472–479. doi: 10.1016/j.procs.2015.04.122. [DOI] [Google Scholar]
- 47.Misra S., Bhattarai K., Xue G. BAMBi: Blackhole attacks mitigation with multiple base stations in wireless sensor networks; Proceedings of the IEEE International Conference on Communications; Kyoto, Japan. 5–9 June 2011. [Google Scholar]
- 48.Poongodi T., Karthikeyan M. Localized secure routing architecture against cooperative black hole attack in mobile Ad hoc networks. Wirel. Pers. Commun. 2016;90:1039–1050. doi: 10.1007/s11277-016-3318-5. [DOI] [Google Scholar]
- 49.Hu Y., Perrig A., Johnson D.B. Wormhole attacks in wireless networks. IEEE J. Sel. Areas Commun. 2006;24:370–380. [Google Scholar]
- 50.Imran M., Khan F.A., Jamal T., Durad M.H. Analysis of detection features for wormhole attacks in MANETs. Proced. Comput. Sci. 2015;56:384–390. doi: 10.1016/j.procs.2015.07.224. [DOI] [Google Scholar]
- 51.Choi Y., Lee Y., Won D. Cryptanalysis on Symmetric Key Techniques Based Authentication Scheme for Wireless Sensor Networks. Volume 373. Springer; Berlin/Heidelberg, Germany: 2015. Advances in computer science and ubiquitous computing; pp. 7–13. [Google Scholar]
- 52.Zhou Y., Fang Y. Defend against topological attacks in sensor networks; Proceedings of the IEEE Military Communications Conference; Atlantic City, NJ, USA. 17–20 October 2005. [Google Scholar]
- 53.Gabrielli A., Mancini L.V., Setia S., Jajodia S. Securing Topology Maintenance Protocols for sensor networks. IEEE Trans. Dependable Secur. Comput. 2011;8:450–465. doi: 10.1109/TDSC.2009.46. [DOI] [Google Scholar]
- 54.Bouk H.S., Ahmed S.H., Kim D., Song H. Named-Data-Networking-Based ITS for smart cities. IEEE Commun. Mag. 2017;55:105–111. doi: 10.1109/MCOM.2017.1600230CM. [DOI] [Google Scholar]
- 55.Bilal M., Kang S.G. A cache management scheme for efficient content eviction and replication in cache networks. IEEE Access. 2017;5:1692–1701. doi: 10.1109/ACCESS.2017.2669344. [DOI] [Google Scholar]
- 56.Ahmed S.H., Bouk H.S., yaqub M.A., Kim D., Song H. CODIE: Controlled data and interest evaluation in vehicular named data networks. IEEE Trans. Veh. Technol. 2016;65:3954–3963. doi: 10.1109/TVT.2016.2558650. [DOI] [Google Scholar]
- 57.Bilal M., Kang S.G. Time aware least recent used (TLRU) cache management policy in ICN; Proceedings of the IEEE 16th International Conference on Advanced Communications Technology; Pyeongchang, Korea. 16–19 February 2014; pp. 528–532. [Google Scholar]
- 58.Ahmed S.H., Bouk H.S., Kim D. RUFS: RobUst forwarder selection in vehicular content-centric networks. IEEE Commun. Lett. 2015;19:1616–1619. doi: 10.1109/LCOMM.2015.2451647. [DOI] [Google Scholar]
- 59.Ahmed S.H., Kim D. Named data networking-based smart home. ICT Express. 2016;2:130–134. doi: 10.1016/j.icte.2016.08.007. [DOI] [Google Scholar]